mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-24 02:20:09 +08:00
Merge remote-tracking branch 'LCTT/master'
This commit is contained in:
commit
58b150cd6c
published
20141027 Closures Objects and the Fauna of the Heap.md20180406 How To Register The Oracle Linux System With The Unbreakable Linux Network (ULN).md20180612 What version of Linux am I running.md
sources/tech
20180115 How debuggers really work.md20180411 Make your first contribution to an open source project.md20180424 How to share files between Linux and Windows.md20180519 Python Debugging Tips.md20180525 15 books for kids who (you want to) love Linux and open source.md20180525 How insecure is your router.md20180531 How To Disable Built-in Webcam In Linux.md20180601 8 basic Docker container management commands.md20180611 How to partition a disk in Linux.md20180615 4 tools for building embedded Linux systems.md20180615 5 Commands for Checking Memory Usage in Linux.md20180615 BLUI- An easy way to create game UI.md20180615 Complete Sed Command Guide [Explained with Practical Examples].md20180615 How To Rename Multiple Files At Once In Linux.md20180615 How to Mount and Use an exFAT Drive on Ubuntu Linux.md20180618 5 open source alternatives to Dropbox.md
translated/tech
20180406 How To Register The Oracle Linux System With The Unbreakable Linux Network (ULN).md20180525 15 books for kids who (you want to) love Linux and open source.md20180525 How insecure is your router.md20180531 How To Disable Built-in Webcam In Linux.md20180601 8 basic Docker container management commands.md20180611 How to partition a disk in Linux.md
@ -1,10 +1,8 @@
|
||||
#[闭包,对象,以及堆“族”][1]
|
||||
|
||||
闭包、对象,以及堆“族”
|
||||
======================
|
||||
|
||||
在上篇文章中我们提到了闭包、对象、以及栈外的其它东西。我们学习的大部分内容都是与特定编程语言无关的元素,但是,我主要还是专注于 JavaScript,以及一些 C。让我们以一个简单的 C 程序开始,它的功能是读取一首歌曲和乐队名字,然后将它们输出给用户:
|
||||
|
||||
stackFolly.c [下载][2]
|
||||
|
||||
```
|
||||
#include <stdio.h>
|
||||
#include <string.h>
|
||||
@ -29,6 +27,8 @@ int main(int argc, char *argv[])
|
||||
}
|
||||
```
|
||||
|
||||
*stackFolly.c [下载][2]*
|
||||
|
||||
如果你运行这个程序,你会得到什么?(=> 表示程序输出):
|
||||
|
||||
```
|
||||
@ -43,23 +43,23 @@ of Montreal
|
||||
|
||||
(曾经的 C 新手说)发生了错误?
|
||||
|
||||
事实证明,函数的栈变量的内容仅在栈帧活动期间才是可用的,也就是说,仅在函数返回之前。在上面的返回中,被栈帧使用的内存 [被认为是可用的][3],并且在下一个函数调用中可以被覆写。
|
||||
事实证明,函数的栈变量的内容仅在栈帧活动期间才是可用的,也就是说,仅在函数返回之前。在上面的返回中,被栈帧使用过的内存 [被认为是可用的][3],并且在下一个函数调用中可以被覆写。
|
||||
|
||||
下面的图展示了这种情况下究竟发生了什么。这个图现在有一个镜像映射,因此,你可以点击一个数据片断去看一下相关的 GDB 输出(GDB 命令在 [这里][4])。只要 `read()` 读取了歌曲的名字,栈将是这个样子:
|
||||
下面的图展示了这种情况下究竟发生了什么。这个图现在有一个图片映射(LCTT 译注:译文中无法包含此映射,上下两个矩形区域分别链接至输出的 [#47][18] 行和 [#70][19] 行),因此,你可以点击一个数据片断去看一下相关的 GDB 输出(GDB 命令在 [这里][4])。只要 `read()` 读取了歌曲的名字,栈将是这个样子:
|
||||
|
||||
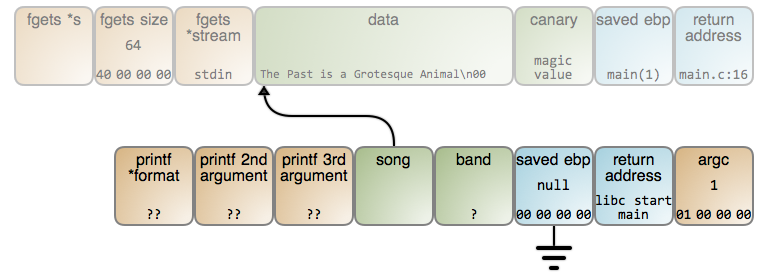
|
||||
|
||||
在这个时候,这个 `song` 变量立即指向到歌曲的名字。不幸的是,存储字符串的内存位置准备被下次调用的任意函数的栈帧重用。在这种情况下,`read()` 再次被调用,而且使用的是同一个位置的栈帧,因此,结果变成下图的样子:
|
||||
在这个时候,这个 `song` 变量立即指向到歌曲的名字。不幸的是,存储字符串的内存位置准备被下次调用的任意函数的栈帧重用。在这种情况下,`read()` 再次被调用,而且使用的是同一个位置的栈帧,因此,结果变成下图的样子(LCTT 译注:上下两个矩形映射分别链接至 [#76][20] 行和 [#79][21] 行):
|
||||
|
||||
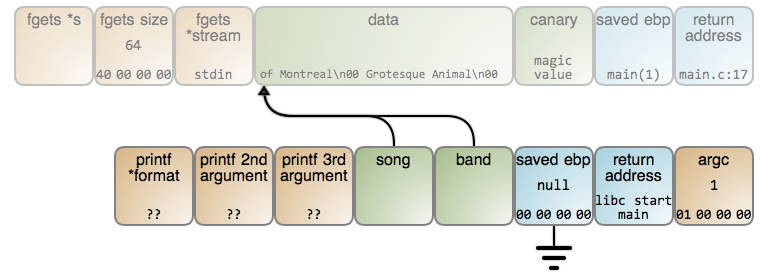
|
||||
|
||||
乐队名字被读入到相同的内存位置,并且覆盖了前面存储的歌曲名字。`band` 和 `song` 最终都准确指向到相同点。最后,我们甚至都不能得到 “of Montreal”(译者注:一个欧美乐队的名字) 的正确输出。你能猜到是为什么吗?
|
||||
乐队名字被读入到相同的内存位置,并且覆盖了前面存储的歌曲名字。`band` 和 `song` 最终都准确指向到相同点。最后,我们甚至都不能得到 “of Montreal”(LCTT 译注:一个欧美乐队的名字) 的正确输出。你能猜到是为什么吗?
|
||||
|
||||
因此,即使栈很有用,但也有很重要的限制。它不能被一个函数用于去存储比该函数的运行周期还要长的数据。你必须将它交给 [堆][5],然后与热点缓存、明确的瞬时操作、以及频繁计算的偏移等内容道别。有利的一面是,它是[工作][6] 的:
|
||||
|
||||
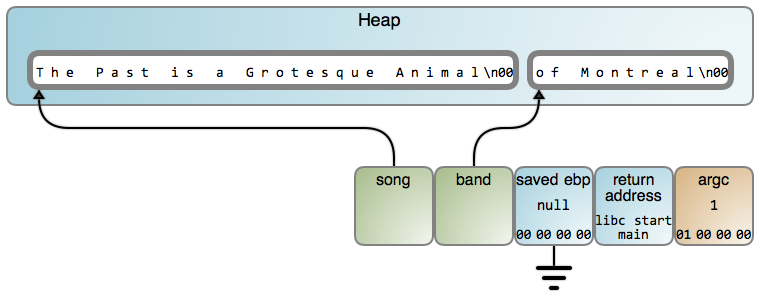
|
||||
|
||||
这个代价是你必须记得去`free()` 内存,或者由一个垃圾回收机制花费一些性能来随机回收,垃圾回收将去找到未使用的堆对象,然后去回收它们。那就是栈和堆之间在本质上的权衡:性能 vs. 灵活性。
|
||||
这个代价是你必须记得去 `free()` 内存,或者由一个垃圾回收机制花费一些性能来随机回收,垃圾回收将去找到未使用的堆对象,然后去回收它们。那就是栈和堆之间在本质上的权衡:性能 vs. 灵活性。
|
||||
|
||||
大多数编程语言的虚拟机都有一个中间层用来做一个 C 程序员该做的一些事情。栈被用于**值类型**,比如,整数、浮点数、以及布尔型。这些都按特定值(像上面的 `argc` )的字节顺序被直接保存在本地变量和对象字段中。相比之下,堆被用于**引用类型**,比如,字符串和 [对象][7]。 变量和字段包含一个引用到这个对象的内存地址,像上面的 `song` 和 `band`。
|
||||
|
||||
@ -72,11 +72,12 @@ function fn()
|
||||
var b = { name: 'foo', n: 10 };
|
||||
}
|
||||
```
|
||||
它可能的结果如下:
|
||||
|
||||
它可能的结果如下(LCTT 译注:图片内“object”、“string”和“a”的映射分别链接至 [#1671][22] 行、 [#8656][23] 行和 [#1264][24] 行):
|
||||
|
||||
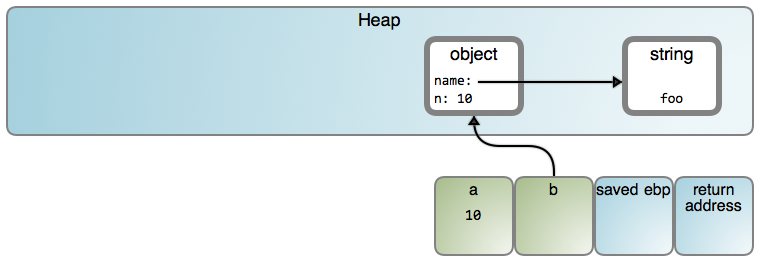
|
||||
|
||||
我之所以说“可能”的原因是,特定的行为高度依赖于实现。这篇文章使用的许多图形是以一个 V8 为中心的方法,这些图形都链接到相关的源代码。在 V8 中,仅 [小整数][8] 是 [以值的方式保存][9]。因此,从现在开始,我将在对象中直接以字符串去展示,以避免引起混乱,但是,请记住,正如上图所示的那样,它们在堆中是分开保存的。
|
||||
我之所以说“可能”的原因是,特定的行为高度依赖于实现。这篇文章使用的许多流程图形是以一个 V8 为中心的方法,这些图形都链接到相关的源代码。在 V8 中,仅 [小整数][8] 是 [以值的方式保存][9]。因此,从现在开始,我将在对象中直接以字符串去展示,以避免引起混乱,但是,请记住,正如上图所示的那样,它们在堆中是分开保存的。
|
||||
|
||||
现在,我们来看一下闭包,它其实很简单,但是由于我们将它宣传的过于夸张,以致于有点神化了。先看一个简单的 JS 函数:
|
||||
|
||||
@ -88,7 +89,7 @@ function add(a, b)
|
||||
}
|
||||
```
|
||||
|
||||
这个函数定义了一个词法域(lexical scope),它是一个快乐的小王国,在这里它的名字 a,b,c 是有明确意义的。它有两个参数和由函数声明的一个本地变量。程序也可以在别的地方使用相同的名字,但是在 `add` 内部它们所引用的内容是明确的。尽管词法域是一个很好的术语,它符合我们直观上的理解:毕竟,我们从字面意义上看,我们可以像词法分析器一样,把它看作在源代码中的一个文本块。
|
||||
这个函数定义了一个<ruby>词法域<rt>lexical scope</rt></ruby>,它是一个快乐的小王国,在这里它的名字 `a`、`b`、`c` 是有明确意义的。它有两个参数和由函数声明的一个本地变量。程序也可以在别的地方使用相同的名字,但是在 `add` 内部它们所引用的内容是明确的。尽管词法域是一个很好的术语,它符合我们直观上的理解:毕竟,我们从字面意义上看,我们可以像词法分析器一样,把它看作在源代码中的一个文本块。
|
||||
|
||||
在看到栈帧的操作之后,很容易想像出这个名称的具体实现。在 `add` 内部,这些名字引用到函数的每个运行实例中私有的栈的位置。这种情况在一个虚拟机中经常发生。
|
||||
|
||||
@ -120,11 +121,11 @@ var heya = makeGreeter('HEYA');
|
||||
heya('dear reader'); // prints "HEYA, dear reader"
|
||||
```
|
||||
|
||||
虽然有点不习惯,但是很酷。即便这样违背了我们的直觉:`greeting` 确实看起来像一个栈变量,这种类型应该在 `makeGreeter()` 返回后消失。可是因为 `greet()` 一直保持工作,出现了一些奇怪的事情。进入闭包:
|
||||
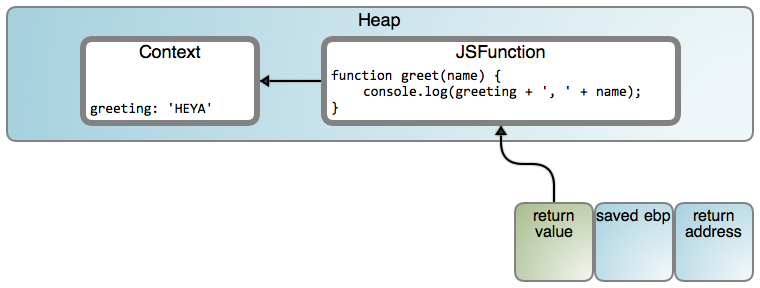
虽然有点不习惯,但是很酷。即便这样违背了我们的直觉:`greeting` 确实看起来像一个栈变量,这种类型应该在 `makeGreeter()` 返回后消失。可是因为 `greet()` 一直保持工作,出现了一些奇怪的事情。进入闭包(LCTT 译注:“Context” 和 “JSFunction” 映射分别链接至 [#188][25] 行和 [#7245][26] 行):
|
||||
|
||||
|
||||
|
||||
虚拟机分配一个对象去保存被里面的 `greet()` 使用的父级变量。它就好像是 `makeGreeter` 的词法作用域在那个时刻被关闭了,一旦需要时被具体化到一个堆对象(在这个案例中,是指返回的函数的生命周期)。因此叫做闭包,当你这样去想它的时候,它的名字就有意义了。如果使用(或者捕获)了更多的父级变量,对象内容将有更多的属性,每个捕获的变量有一个。当然,发送到 `greet()` 的代码知道从对象内容中去读取问候语,而不是从栈上。
|
||||
虚拟机分配一个对象去保存被里面的 `greet()` 使用的父级变量。它就好像是 `makeGreeter` 的词法作用域在那个时刻被<ruby>关闭<rt>closed over</rt></ruby>了,一旦需要时被具体化到一个堆对象(在这个案例中,是指返回的函数的生命周期)。因此叫做<ruby>闭包<rt>closure</rt></ruby>,当你这样去想它的时候,它的名字就有意义了。如果使用(或者捕获)了更多的父级变量,对象内容将有更多的属性,每个捕获的变量有一个。当然,发送到 `greet()` 的代码知道从对象内容中去读取问候语,而不是从栈上。
|
||||
|
||||
这是完整的示例:
|
||||
|
||||
@ -154,13 +155,11 @@ greeter.hello('darling');// prints "howdy, darling"
|
||||
greeter.count(); // returns 2
|
||||
```
|
||||
|
||||
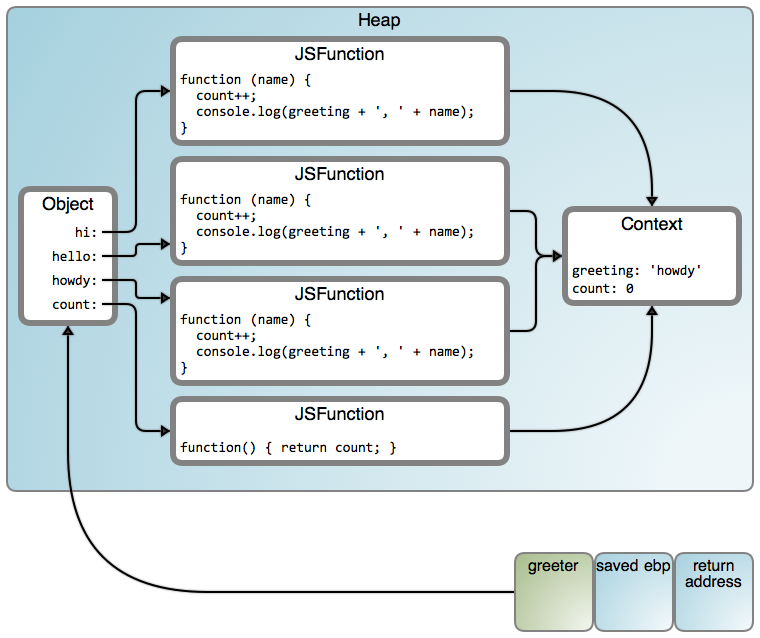
是的,`count()` 在工作,但是我们的 `greeter` 是在 `howdy` 中的栈上。你能告诉我为什么吗?我们使用 `count` 是一条线索:尽管词法域进入一个堆对象中被关闭,但是变量(或者对象属性)带的值仍然可能被改变。下图是我们拥有的内容:
|
||||
是的,`count()` 在工作,但是我们的 `greeter` 是在 `howdy` 中的栈上。你能告诉我为什么吗?我们使用 `count` 是一条线索:尽管词法域进入一个堆对象中被关闭,但是变量(或者对象属性)带的值仍然可能被改变。下图是我们拥有的内容(LCTT 译注:映射从左到右“Object”、“JSFunction”和“Context”分别链接至 [#1671][22] 行、[#7245][26] 行和 [#188][25] 行):
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
这是一个被所有函数共享的公共内容。那就是为什么 `count` 工作的原因。但是,`greeting` 也是被共享的,并且它被设置为迭代结束后的最后一个值,在这个案例中是“howdy”。这是一个很常见的一般错误,避免它的简单方法是,引用一个函数调用,以闭包变量作为一个参数。在 CoffeeScript 中, [do][10] 命令提供了一个实现这种目的的简单方式。下面是对我们的 `greeter` 的一个简单的解决方案:
|
||||
这是一个被所有函数共享的公共内容。那就是为什么 `count` 工作的原因。但是,`greeting` 也是被共享的,并且它被设置为迭代结束后的最后一个值,在这个案例中是 “howdy”。这是一个很常见的一般错误,避免它的简单方法是,引用一个函数调用,以闭包变量作为一个参数。在 CoffeeScript 中, [do][10] 命令提供了一个实现这种目的的简单方式。下面是对我们的 `greeter` 的一个简单的解决方案:
|
||||
|
||||
```
|
||||
function makeGreeter(greetings)
|
||||
@ -186,21 +185,21 @@ greeter.hello('darling'); // prints "hello, darling"
|
||||
greeter.count(); // returns 2
|
||||
```
|
||||
|
||||
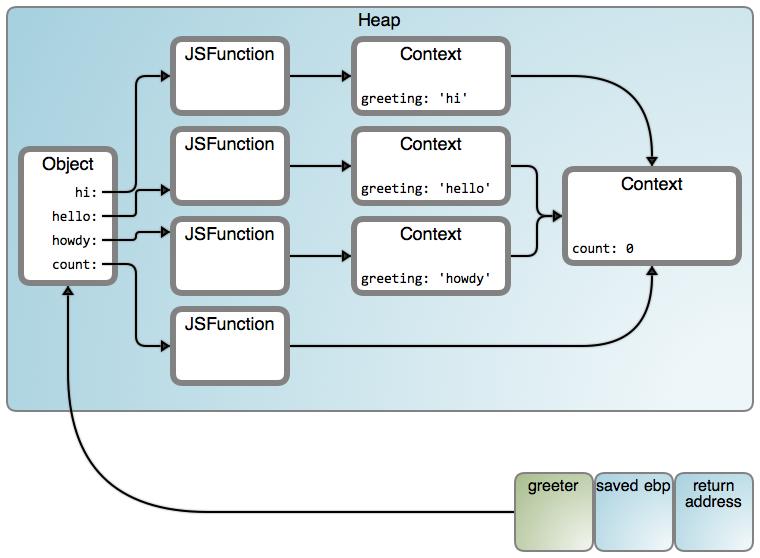
它现在是工作的,并且结果将变成下图所示:
|
||||
它现在是工作的,并且结果将变成下图所示(LCTT 译注:映射从左到右“Object”、“JSFunction”和“Context”分别链接至 [#1671][22] 行、[#7245][26] 行和 [#188][25] 行):
|
||||
|
||||
|
||||
|
||||
这里有许多箭头!在这里我们感兴趣的特性是:在我们的代码中,我们闭包了两个嵌套的词法内容,并且完全可以确保我们得到了两个链接到堆上的对象内容。你可以嵌套并且闭包任何词法内容、“俄罗斯套娃”类型、并且最终从本质上说你使用的是所有那些对象内容的一个链表。
|
||||
这里有许多箭头!在这里我们感兴趣的特性是:在我们的代码中,我们闭包了两个嵌套的词法内容,并且完全可以确保我们得到了两个链接到堆上的对象内容。你可以嵌套并且闭包任何词法内容,像“俄罗斯套娃”似的,并且最终从本质上说你使用的是所有那些 Context 对象的一个链表。
|
||||
|
||||
当然,就像受信鸽携带信息启发实现了 TCP 一样,去实现这些编程语言的特性也有很多种方法。例如,ES6 规范定义了 [词法环境][11] 作为 [环境记录][12]( 大致相当于在一个块内的本地标识)的组成部分,加上一个链接到外部环境的记录,这样就允许我们看到的嵌套。逻辑规则是由规范(一个希望)所确定的,但是其实现取决于将它们变成比特和字节的转换。
|
||||
|
||||
你也可以检查具体案例中由 V8 产生的汇编代码。[Vyacheslav Egorov][13] 有一篇很好的文章,它在细节中使用 V8 的 [闭包内部构件][14] 解释了这一过程。我刚开始学习 V8,因此,欢迎指教。如果你熟悉 C#,检查闭包产生的中间代码将会很受启发 - 你将看到显式定义的 V8 内容和实例化的模拟。
|
||||
你也可以检查具体案例中由 V8 产生的汇编代码。[Vyacheslav Egorov][13] 有一篇很好的文章,它使用 V8 的 [闭包内部构件][14] 详细解释了这一过程。我刚开始学习 V8,因此,欢迎指教。如果你熟悉 C#,检查闭包产生的中间代码将会很受启发 —— 你将看到显式定义的 V8 内容和实例化的模拟。
|
||||
|
||||
闭包是个强大的“家伙”。它在被一组函数共享期间,提供了一个简单的方式去隐藏来自调用者的信息。我喜欢它们真正地隐藏你的数据:不像对象字段,调用者并不能访问或者甚至是看到闭包变量。保持接口清晰而安全。
|
||||
|
||||
但是,它们并不是“银弹”(译者注:意指极为有效的解决方案,或者寄予厚望的新技术)。有时候一个对象的拥护者和一个闭包的狂热者会无休止地争论它们的优点。就像大多数的技术讨论一样,他们通常更关注的是自尊而不是真正的权衡。不管怎样,Anton van Straaten 的这篇 [史诗级的公案][15] 解决了这个问题:
|
||||
但是,它们并不是“银弹”(LCTT 译注:意指极为有效的解决方案,或者寄予厚望的新技术)。有时候一个对象的拥护者和一个闭包的狂热者会无休止地争论它们的优点。就像大多数的技术讨论一样,他们通常更关注的是自尊而不是真正的权衡。不管怎样,Anton van Straaten 的这篇 [史诗级的公案][15] 解决了这个问题:
|
||||
|
||||
> 德高望重的老师 Qc Na 和它的学生 Anton 一起散步。Anton 希望将老师引入到一个讨论中,Anton 说:“老师,我听说对象是一个非常好的东西,是这样的吗?Qc Na 同情地看了一眼,责备它的学生说:“可怜的孩子 - 对象不过是穷人的闭包。” Anton 待它的老师走了之后,回到他的房间,专心学习闭包。他认真地阅读了完整的 “Lambda:The Ultimate…" 系列文章和它的相关资料,并使用一个基于闭包的对象系统实现了一个小的架构解释器。他学到了很多的东西,并期待告诉老师他的进步。在又一次和 Qc Na 散步时,Anton 尝试给老师留下一个好的印象,说“老师,我仔细研究了这个问题,并且,现在理解了对象真的是穷人的闭包。”Qc Na 用它的手杖打了一下 Anton 说:“你什么时候才能明白?闭包是穷人的对象。”在那个时候,Anton 顿悟了。Anton van Straaten 说:“原来架构这么酷啊?”
|
||||
> 德高望重的老师 Qc Na 和它的学生 Anton 一起散步。Anton 希望将老师引入到一个讨论中,Anton 说:“老师,我听说对象是一个非常好的东西,是这样的吗?Qc Na 同情地看了一眼,责备它的学生说:“可怜的孩子 —— 对象不过是穷人的闭包而已。” Anton 待它的老师走了之后,回到他的房间,专心学习闭包。他认真地阅读了完整的 “Lambda:The Ultimate…" 系列文章和它的相关资料,并使用一个基于闭包的对象系统实现了一个小的架构解释器。他学到了很多的东西,并期待告诉老师他的进步。在又一次和 Qc Na 散步时,Anton 尝试给老师留下一个好的印象,说“老师,我仔细研究了这个问题,并且,现在理解了对象真的是穷人的闭包。”Qc Na 用它的手杖打了一下 Anton 说:“你什么时候才能明白?闭包是穷人的对象。”在那个时候,Anton 顿悟了。Anton van Straaten 说:“原来架构这么酷啊?”
|
||||
|
||||
探秘“栈”系列文章到此结束了。后面我将计划去写一些其它的编程语言实现的主题,像对象绑定和虚表。但是,内核调用是很强大的,因此,明天将发布一篇操作系统的文章。我邀请你 [订阅][16] 并 [关注我][17]。
|
||||
|
||||
@ -210,7 +209,7 @@ via:https://manybutfinite.com/post/closures-objects-heap/
|
||||
|
||||
作者:[Gustavo Duarte][a]
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -231,4 +230,13 @@ via:https://manybutfinite.com/post/closures-objects-heap/
|
||||
[14]:http://mrale.ph/blog/2012/09/23/grokking-v8-closures-for-fun.html
|
||||
[15]:http://people.csail.mit.edu/gregs/ll1-discuss-archive-html/msg03277.html
|
||||
[16]:https://manybutfinite.com/feed.xml
|
||||
[17]:http://twitter.com/manybutfinite
|
||||
[17]:http://twitter.com/manybutfinite
|
||||
[18]:https://github.com/gduarte/blog/blob/master/code/x86-stack/stackFolly-gdb-output.txt#L47
|
||||
[19]:https://github.com/gduarte/blog/blob/master/code/x86-stack/stackFolly-gdb-output.txt#L70
|
||||
[20]:https://github.com/gduarte/blog/blob/master/code/x86-stack/stackFolly-gdb-output.txt#L76
|
||||
[21]:https://github.com/gduarte/blog/blob/master/code/x86-stack/stackFolly-gdb-output.txt#L79
|
||||
[22]:https://code.google.com/p/v8/source/browse/trunk/src/objects.h#1671
|
||||
[23]:https://code.google.com/p/v8/source/browse/trunk/src/objects.h#8656
|
||||
[24]:https://code.google.com/p/v8/source/browse/trunk/src/objects.h#1264
|
||||
[25]:https://code.google.com/p/v8/source/browse/trunk/src/contexts.h#188
|
||||
[26]:https://code.google.com/p/v8/source/browse/trunk/src/objects.h#7245
|
||||
@ -0,0 +1,309 @@
|
||||
Oracle Linux 系统如何去注册使用坚不可摧 Linux 网络(ULN)
|
||||
======
|
||||
|
||||
大多数人都知道 RHEL 的订阅 ,但是知道 Oracle 订阅及细节的人却很少。
|
||||
|
||||
甚至我也不知道关于它的信息,我是最近才了解了有关它的信息,想将这些内容共享给其他人。因此写了这篇文章,它将指导你去注册 Oracle Linux 系统去使用坚不可摧 Linux 网络(ULN) 。
|
||||
|
||||
这将允许你去注册系统以尽快获得软件更新和其它的补丁。
|
||||
|
||||
### 什么是坚不可摧 Linux 网络
|
||||
|
||||
ULN 代表<ruby>坚不可摧 Linux 网络<rt>Unbreakable Linux Network</rt></ruby>,它是由 Oracle 所拥有的。如果你去 Oracle OS 支持中去激活这个订阅,你就可以注册你的系统去使用坚不可摧 Linux 网络(ULN)。
|
||||
|
||||
ULN 为 Oracle Linux 和 Oracle VM 提供软件补丁、更新、以及修复,此外还有在 yum、Ksplice、以及支持策略上的信息。你也可以通过它来下载原始发行版中没有包含的有用的安装包。
|
||||
|
||||
ULN 的告警提示工具会周期性地使用 ULN 进行检查,当有更新的时候它给你发送警报信息。
|
||||
|
||||
如果你想在 yum 上使用 ULN 仓库去管理你的系统,需要确保你的系统已经注册到 ULN 上,并且订阅了一个或多个 ULN 频道。当你注册一个系统使用 ULN,它将基于你的系统架构和操作系统去自动选择频道中最新的版本。
|
||||
|
||||
### 如何注册为一个 ULN 用户
|
||||
|
||||
要注册为一个 ULN 用户,需要你有一个 Oracle Linux 支持或者 Oracle VM 支持的有效客户支持代码(CSI)。
|
||||
|
||||
请按以下步骤去注册为一个 ULN 用户。
|
||||
|
||||
请访问 [linux.oracle.com][1]:
|
||||
|
||||
![][3]
|
||||
|
||||
如果你已经有一个 SSO 帐户,请点击 “Sign On”。
|
||||
|
||||
![][4]
|
||||
|
||||
如果你没有帐户,点击 “Create New Single Signon Account” 然后按屏幕上的要求去创建一个帐户。
|
||||
|
||||
![][5]
|
||||
|
||||
验证你的电子邮件地址以完成帐户设置。
|
||||
|
||||
使用你的 SSO 帐户的用户名和密码去登入。在 “Create New ULN User” 页面上,输入你的 CSI 然后点击 “Create New User”。
|
||||
|
||||
![][6]
|
||||
|
||||
**注意:**
|
||||
|
||||
* 如果当前没有分配管理员去管理 CSI,将会提示你去点击确认让你成为 CSI 管理员。
|
||||
* 如果你的用户名已经在系统上存在,你将被提示通过点击坚不可摧 Linux 网络的链接去操作 ULN。
|
||||
|
||||
|
||||
### 如何注册 Oracle Linux 6/7 系统使用 ULN
|
||||
|
||||
只需要运行下列的命令,并按随后的指令提示去注册系统。
|
||||
|
||||
```
|
||||
# uln_register
|
||||
```
|
||||
|
||||
确保你的系统有一个激活的因特网连接。同时准备好你的 Oracle 单点登录帐户(SSO)的用户名和密码,然后点击 `Next`。
|
||||
|
||||
```
|
||||
Copyright □© 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□¤ Setting up software updates □□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
□ This assistant will guide you through connecting your system to Unbreakable Linux Network (ULN) to receive software updates, □
|
||||
□ including security updates, to keep your system supported and compliant. You will need the following at this time: □
|
||||
□ □
|
||||
□ * A network connection □
|
||||
□ * Your Oracle Single Sign-On Login & password □
|
||||
□ □
|
||||
□ □
|
||||
□ □
|
||||
□ □
|
||||
□ □
|
||||
□ □
|
||||
□ □
|
||||
□ □
|
||||
□ □□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□ □□□□□□□□ □□□□□□□□□□ □
|
||||
□ □ Why Should I Connect to ULN? ... □ □ Next □ □ Cancel □ □
|
||||
□ □□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□ □□□□□□□□ □□□□□□□□□□ □
|
||||
□ □
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
```
|
||||
|
||||
输入你的 ULN 登录信息,然后点击 `Next`。
|
||||
|
||||
```
|
||||
Copyright □© 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□¤ Setting up software updates □□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
□ □
|
||||
□ Please enter your login information for Unbreakable Linux Network (http://linux.oracle.com/): □
|
||||
□ □
|
||||
□ □
|
||||
□ Oracle Single Sign-On Login: thamuthu@gmail.com_ □
|
||||
□ Password: **********__________ □
|
||||
□ CSI: 12345678____________ □
|
||||
□ Tip: Forgot your login or password? Visit: http://www.oracle.com/corporate/contact/getaccthelp.html □
|
||||
□ □
|
||||
□ □□□□□□□□ □□□□□□□□ □□□□□□□□□□ □
|
||||
□ □ Next □ □ Back □ □ Cancel □ □
|
||||
□ □□□□□□□□ □□□□□□□□ □□□□□□□□□□ □
|
||||
□ □
|
||||
□ □
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
```
|
||||
|
||||
注册一个系统概要 – 硬件信息,然后点击 `Next`。
|
||||
|
||||
```
|
||||
Copyright □© 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□¤ Register a System Profile - Hardware □□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
□ □
|
||||
□ A Profile Name is a descriptive name that you choose to identify this □
|
||||
□ System Profile on the Unbreakable Linux Network web pages. Optionally, □
|
||||
□ include a computer serial or identification number. □
|
||||
□ Profile name: 2g-oracle-sys___________________________ □
|
||||
□ □
|
||||
□ [*] Include the following information about hardware and network: □
|
||||
□ Press to deselect the option. □
|
||||
□ □
|
||||
□ Version: 6 CPU model: Intel(R) Xeon(R) CPU E5-5650 0 @ 2.00GHz □
|
||||
□ Hostname: 2g-oracle-sys □
|
||||
□ CPU speed: 1199 MHz IP Address: 192.168.1.101 Memory: □
|
||||
□ □
|
||||
□ Additional hardware information including PCI devices, disk sizes and mount points will be included in the profile. □
|
||||
□ □
|
||||
□ □□□□□□□□ □□□□□□□□ □□□□□□□□□□ □
|
||||
□ □ Next □ □ Back □ □ Cancel □ □
|
||||
□ □□□□□□□□ □□□□□□□□ □□□□□□□□□□ □
|
||||
□ □
|
||||
□ □
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
```
|
||||
|
||||
注册一个系统概要 – 包配置,然后点击 `Next`。
|
||||
|
||||
```
|
||||
Copyright □© 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□¤ Register a System Profile - Packages □□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
□ □
|
||||
□ RPM information is important to determine what updated software packages are relevant to this system. □
|
||||
□ □
|
||||
□ [*] Include RPM packages installed on this system in my System Profile □
|
||||
□ □
|
||||
□ You may deselect individual packages by unchecking them below. □
|
||||
□ [*] ConsoleKit-0.4.1-6.el6 □ □
|
||||
□ [*] ConsoleKit-libs-0.4.1-6.el6 □ □
|
||||
□ [*] ConsoleKit-x11-0.4.1-6.el6 □ □
|
||||
□ [*] DeviceKit-power-014-3.el6 □ □
|
||||
□ [*] GConf2-2.28.0-7.el6 □ □
|
||||
□ [*] GConf2-2.28.0-7.el6 □ □
|
||||
□ [*] GConf2-devel-2.28.0-7.el6 □ □
|
||||
□ [*] GConf2-gtk-2.28.0-7.el6 □ □
|
||||
□ [*] MAKEDEV-3.24-6.el6 □ □
|
||||
□ [*] MySQL-python-1.2.3-0.3.c1.1.el6 □ □
|
||||
□ [*] NessusAgent-7.0.3-es6 □ □
|
||||
□ [*] ORBit2-2.14.17-6.el6_8 □ □
|
||||
□ [*] ORBit2-2.14.17-6.el6_8 □ □
|
||||
□ [*] ORBit2-devel-2.14.17-6.el6_8 □ □
|
||||
□ [*] PackageKit-0.5.8-26.0.1.el6 □ □
|
||||
□ [*] PackageKit-device-rebind-0.5.8-26.0.1.el6 □ □
|
||||
□ [*] PackageKit-glib-0.5.8-26.0.1.el6 □ □
|
||||
□ □
|
||||
□ □□□□□□□□ □□□□□□□□ □□□□□□□□□□ □
|
||||
□ □ Next □ □ Back □ □ Cancel □ □
|
||||
□ □□□□□□□□ □□□□□□□□ □□□□□□□□□□ □
|
||||
□ □
|
||||
□ □
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
```
|
||||
|
||||
按下 “Next” 去发送系统概要到 ULN。
|
||||
|
||||
```
|
||||
Copyright □© 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□¤ Send Profile Information to Unbreakable Linux Network □□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
□ □
|
||||
□ We are finished collecting information for the System Profile. □
|
||||
□ □
|
||||
□ Press "Next" to send this System Profile to Unbreakable Linux Network. Click "Cancel" and no information will be sent. You □
|
||||
□ can run the registration program later by typing `uln_register` at the command line. □
|
||||
□ □
|
||||
□ □□□□□□□□ □□□□□□□□ □□□□□□□□□□ □
|
||||
□ □ Next □ □ Back □ □ Cancel □ □
|
||||
□ □□□□□□□□ □□□□□□□□ □□□□□□□□□□ □
|
||||
□ □
|
||||
□ □
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
```
|
||||
|
||||
发送概要到 ULN 是如下的一个过程。
|
||||
|
||||
```
|
||||
Copyright □© 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
|
||||
|
||||
□□¤ Sending Profile to Unbreakable Linux Network □
|
||||
□ □
|
||||
□ 75% □
|
||||
□ □
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
```
|
||||
|
||||
ULN 注册做完后,重新回顾系统订阅的详细情况。如果一切正确,然后点击 `ok`。
|
||||
|
||||
```
|
||||
Copyright □© 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□¤ Review system subscription details □□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
□ □
|
||||
□ □
|
||||
□ Note: yum-rhn-plugin has been enabled. □
|
||||
□ □
|
||||
□ Please review the subscription details below: □
|
||||
□ □
|
||||
□ Software channel subscriptions: □
|
||||
□ This system will receive updates from the following Unbreakable Linux Network software channels: □
|
||||
□ Oracle Linux 6 Latest (x86_64) □
|
||||
□ Unbreakable Enterprise Kernel Release 4 for Oracle Linux 6 (x86_64) □
|
||||
□ □
|
||||
□ Warning: If an installed product on this system is not listed above, you will not receive updates or support for that product. If □
|
||||
□ you would like to receive updates for that product, please visit http://linux.oracle.com/ and subscribe this system to the □
|
||||
□ appropriate software channels to get updates for that product. □
|
||||
□ □
|
||||
□ □
|
||||
□ □
|
||||
□ □
|
||||
□ □
|
||||
□ □
|
||||
□ □
|
||||
□ □□□□□□ □
|
||||
□ □ OK □ □
|
||||
□ □□□□□□ □
|
||||
□ □
|
||||
□ □
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
```
|
||||
|
||||
最后点击 `Finish` 完成注册。
|
||||
|
||||
```
|
||||
Copyright □© 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□¤ Finish setting up software updates □□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
□ □
|
||||
□ You may now run 'yum update' from this system's command line to get the latest software updates from Unbreakable Linux Network. □
|
||||
□ You will need to run this periodically to get the latest updates. □
|
||||
□ □
|
||||
□ □□□□□□□□□□ □
|
||||
□ □ Finish □ □
|
||||
□ □□□□□□□□□□ □
|
||||
□ □
|
||||
□ □
|
||||
□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□□
|
||||
```
|
||||
|
||||
ULN 注册已经成功,为了从 ULN 中得到仓库,运行如下的命令。
|
||||
|
||||
```
|
||||
# yum repolist
|
||||
Loaded plugins: aliases, changelog, presto, refresh-packagekit, rhnplugin, security, tmprepo, ulninfo, verify, versionlock
|
||||
This system is receiving updates from ULN.
|
||||
ol6_x86_64_UEKR3_latest | 1.2 kB 00:00
|
||||
ol6_x86_64_UEKR3_latest/primary | 35 MB 00:14
|
||||
ol6_x86_64_UEKR3_latest 874/874
|
||||
repo id repo name status
|
||||
ol6_x86_64_UEKR3_latest Unbreakable Enterprise Kernel Release 3 for Oracle Linux 6 (x86_64) - Latest 874
|
||||
ol6_x86_64_latest Oracle Linux 6 Latest (x86_64) 40,092
|
||||
repolist: 40,966
|
||||
```
|
||||
|
||||
另外,你也可以在 ULN 网站上查看到相同的信息。转到 `System` 标签页去查看已注册的系统列表。
|
||||
|
||||
![][7]
|
||||
|
||||
去查看已经启用的仓库列表。转到 `System` 标签页,然后点击相应的系统。另外,你也能够看到系统勘误及可用更新。
|
||||
|
||||
![][8]
|
||||
|
||||
去管理订阅的频道。转到 `System` 标签页,然后点击有关的 `system name`,最后点击 `Manage Subscriptions`。
|
||||
|
||||
![][9]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/how-to-register-the-oracle-linux-system-with-the-unbreakable-linux-network-uln/
|
||||
|
||||
作者:[Vinoth Kumar][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.2daygeek.com/author/vinoth/
|
||||
[1]:https://linux.oracle.com/register
|
||||
[2]:data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[3]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-1.png
|
||||
[4]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-3.png
|
||||
[5]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-2.png
|
||||
[6]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-4.png
|
||||
[7]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-5a.png
|
||||
[8]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-6a.png
|
||||
[9]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-7a.png
|
||||
@ -1,95 +1,80 @@
|
||||
我正在运行的 Linux 是什么版本?
|
||||
=====
|
||||
|
||||
> 掌握这些快捷命令以找出你正在运行的 Linux 系统的内核版本和发行版。
|
||||
|
||||
|
||||
|
||||
“Linux 是什么版本?”这个问题可能意味着两个不同的东西。严格地说,Linux 是内核,所以问题可以特指内核的版本号,或者 “Linux” 可以更通俗地用来指整个发行版,就像在 Fedora Linux 或 Ubuntu Linux 中一样。
|
||||
“什么版本的 Linux ?”这个问题可能意味着两个不同的东西。严格地说,Linux 是内核,所以问题可以特指内核的版本号,或者 “Linux” 可以更通俗地用来指整个发行版,就像在 Fedora Linux 或 Ubuntu Linux 中一样。
|
||||
|
||||
两者都很重要,你可能需要知道其中一个或全部答案来修复系统中的问题。例如,了解已安装的内核版本可能有助于诊断带有专有驱动程序的问题,并且确定正在运行的发行版将帮助你快速确定是否应该使用 `apt`, `dnf`, `yum` 或其他命令来安装软件包。
|
||||
两者都很重要,你可能需要知道其中一个或全部答案来修复系统中的问题。例如,了解已安装的内核版本可能有助于诊断带有专有驱动程序的问题,并且确定正在运行的发行版将帮助你快速确定是否应该使用 `apt`、 `dnf`、 `yum` 或其他命令来安装软件包。
|
||||
|
||||
以下内容将帮助你了解 Linux 内核的版本和/或系统上正在运行的 Linux 发行版是什么。
|
||||
|
||||
### 如何找到 Linux 内核版本
|
||||
|
||||
要找出哪个 Linux 内核版本正在运行,运行以下命令:
|
||||
|
||||
```
|
||||
uname -srm
|
||||
|
||||
```
|
||||
|
||||
或者,可以使用更长,更具描述性的各种标志的版本来运行该命令:
|
||||
|
||||
```
|
||||
uname --kernel-name --kernel-release --machine
|
||||
|
||||
```
|
||||
|
||||
无论哪种方式,输出都应该类似于以下内容:
|
||||
|
||||
```
|
||||
Linux 4.16.10-300.fc28.x86_64 x86_64
|
||||
|
||||
```
|
||||
|
||||
这为你提供了(按顺序):内核名称,内核版本以及运行内核的硬件类型。在上面的情况下,内核是 Linux 4.16.10-300.fc28.x86_64 ,运行于 x86_64 系统。
|
||||
这为你提供了(按顺序):内核名称、内核版本以及运行内核的硬件类型。在上面的情况下,内核是 Linux ,版本 4.16.10-300.fc28.x86_64 ,运行于 x86_64 系统。
|
||||
|
||||
有关 `uname` 命令的更多信息可以通过运行 `man uname` 找到。
|
||||
|
||||
### 如何找出 Linux 发行版
|
||||
|
||||
有几种方法可以确定系统上运行的是哪个发行版,但最快的方法是检查 `/etc/os-release` 文件的内容。此文件提供有关发行版的信息,包括但不限于发行版名称及其版本号。某些发行版的 os-release 文件包含比其他发行版更多的细节,但任何包含 os-release 文件的发行版都应该提供发行版的名称和版本。
|
||||
有几种方法可以确定系统上运行的是哪个发行版,但最快的方法是检查 `/etc/os-release` 文件的内容。此文件提供有关发行版的信息,包括但不限于发行版名称及其版本号。某些发行版的 `os-release` 文件包含比其他发行版更多的细节,但任何包含 `os-release` 文件的发行版都应该提供发行版的名称和版本。
|
||||
|
||||
要查看 `os-release` 文件的内容,运行以下命令:
|
||||
|
||||
要查看 os-release 文件的内容,运行以下命令:
|
||||
```
|
||||
cat /etc/os-release
|
||||
|
||||
```
|
||||
|
||||
在 Fedora 28 中,输出如下所示:
|
||||
|
||||
```
|
||||
NAME=Fedora
|
||||
|
||||
VERSION="28 (Workstation Edition)"
|
||||
|
||||
ID=fedora
|
||||
|
||||
VERSION_ID=28
|
||||
|
||||
PLATFORM_ID="platform:f28"
|
||||
|
||||
PRETTY_NAME="Fedora 28 (Workstation Edition)"
|
||||
|
||||
ANSI_COLOR="0;34"
|
||||
|
||||
CPE_NAME="cpe:/o:fedoraproject:fedora:28"
|
||||
|
||||
HOME_URL="https://fedoraproject.org/"
|
||||
|
||||
SUPPORT_URL="https://fedoraproject.org/wiki/Communicating_and_getting_help"
|
||||
|
||||
BUG_REPORT_URL="https://bugzilla.redhat.com/"
|
||||
|
||||
REDHAT_BUGZILLA_PRODUCT="Fedora"
|
||||
|
||||
REDHAT_BUGZILLA_PRODUCT_VERSION=28
|
||||
|
||||
REDHAT_SUPPORT_PRODUCT="Fedora"
|
||||
|
||||
REDHAT_SUPPORT_PRODUCT_VERSION=28
|
||||
|
||||
PRIVACY_POLICY_URL="https://fedoraproject.org/wiki/Legal:PrivacyPolicy"
|
||||
|
||||
VARIANT="Workstation Edition"
|
||||
|
||||
VARIANT_ID=workstation
|
||||
|
||||
```
|
||||
|
||||
如上面那个例子展示的那样,Fedora 的 os-release 文件提供了发行版的名称和版本,但它也标识已安装的变体("Workstation Edition")。如果我们在 Fedora 28 服务器版本上运行相同的命令,os-release 文件的内容会反映在 `VARIANT` 和 `VARIANT_ID` 行中。
|
||||
如上面那个例子展示的那样,Fedora 的 `os-release` 文件提供了发行版的名称和版本,但它也标识这个安装的变体(“Workstation Edition”)。如果我们在 Fedora 28 服务器版本上运行相同的命令,`os-release` 文件的内容会反映在 `VARIANT` 和 `VARIANT_ID` 行中。
|
||||
|
||||
有时候知道一个发行版是否与另一个发行版相似非常有用,因此 os-release 文件可以包含一个 `ID_LIKE` 行,用于标识正在运行的是基于什么的发行版或类似的发行版。例如,Red Hat Linux 企业版的 os-release 文件包含 `ID_LIKE` 行,声明 RHEL 与 Fedora 类似;CentOS 的 os-release 文件声明 CentOS 与 RHEL 和 Fedora 类似。如果你正在使用基于另一个发行版的发行版并需要查找解决问题的说明,那么 `ID_LIKE` 行非常有用。
|
||||
有时候知道一个发行版是否与另一个发行版相似非常有用,因此 `os-release` 文件可以包含一个 `ID_LIKE` 行,用于标识正在运行的是基于什么的发行版或类似的发行版。例如,Red Hat Linux 企业版的 `os-release` 文件包含 `ID_LIKE` 行,声明 RHEL 与 Fedora 类似;CentOS 的 `os-release` 文件声明 CentOS 与 RHEL 和 Fedora 类似。如果你正在使用基于另一个发行版的发行版并需要查找解决问题的说明,那么 `ID_LIKE` 行非常有用。
|
||||
|
||||
CentOS 的 os-release 文件清楚地表明它就像 RHEL 一样,所以在各种论坛中关于 RHEL 的文档,问题和答案应该(大多数情况下)适用于 CentOS。CentOS 被设计成一个克隆版 RHEL,因此相比 `ID_LIKE` 字段中的某些记录,它与 `LIKE` 字段更兼容。如果你找不到正在运行的发行版的信息,检查有关 “like” 发行版的答案总是一个好主意。
|
||||
CentOS 的 `os-release` 文件清楚地表明它就像 RHEL 一样,所以在各种论坛中关于 RHEL 的文档,问题和答案应该(大多数情况下)适用于 CentOS。CentOS 被设计成一个 RHEL 近亲,因此在某些字段它更兼容其 `ID_LIKE` 系统的字段。如果你找不到正在运行的发行版的信息,检查有关 “类似” 发行版的答案总是一个好主意。
|
||||
|
||||
有关 os-release 文件的更多信息可以通过运行 `man os-release` 命令来查找。
|
||||
有关 `os-release` 文件的更多信息可以通过运行 `man os-release` 命令来查找。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
@ -99,7 +84,7 @@ via: https://opensource.com/article/18/6/linux-version
|
||||
作者:[Joshua Allen Holm][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[MjSeven](https://github.com/MjSeven)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
translating by sunxi
|
||||
How debuggers really work
|
||||
======
|
||||
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
Translating
|
||||
Make your first contribution to an open source project
|
||||
============================================================
|
||||
|
||||
|
||||
@ -1,3 +1,6 @@
|
||||
Translating by MjSeven
|
||||
|
||||
|
||||
How to share files between Linux and Windows
|
||||
======
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
translating----geekpi
|
||||
|
||||
Python Debugging Tips
|
||||
======
|
||||
When it comes to debugging, there’s a lot of choices that you can make. It is hard to give generic advice that always works (other than “Have you tried turning it off and back on?”).
|
||||
|
||||
@ -1,116 +0,0 @@
|
||||
pinewall translating
|
||||
|
||||
15 books for kids who (you want to) love Linux and open source
|
||||
======
|
||||
|
||||

|
||||
In my job I've heard professionals in tech, from C-level executives to everyone in between, say they want their own kids to learn more about [Linux][1] and [open source][2]. Some of them seem to have an easy time with their kids following closely in their footsteps. And some have a tough time getting their kids to see what makes Linux and open source so cool. Maybe their time will come, maybe it won't. There's a lot of interesting, valuable stuff out there in this big world.
|
||||
|
||||
Either way, if you have a kid or know a kid that may be interested in learning more about making something with code or hardware, from games to robots, this list is for you.
|
||||
|
||||
### 15 books for kids with a focus on Linux and open source
|
||||
|
||||
[Adventures in Raspberry Pi][3] by Carrie Anne Philbin
|
||||
|
||||
The tiny, credit-card sized Raspberry Pi has become a huge hit among kids—and adults—interested in programming. It does everything your desktop can do, but with a few basic programming skills you can make it do so much more. With simple instructions, fun projects, and solid skills, Adventures in Raspberry Pi is the ultimate kids' programming guide! (Recommendation by [Joshua Allen Holm][4] | Review is an excerpt from the book's abstract)
|
||||
|
||||
[Automate the Boring Stuff with Python][5] by Al Sweigart
|
||||
|
||||
This is a classic introduction to programming that's written clearly enough for a motivated 11-year-old to understand and enjoy. Readers will quickly find themselves working on practical and useful tasks while picking up good coding practices almost by accident. The best part: If you like, you can read the whole book online. (Recommendation and review by [DB Clinton][6])
|
||||
|
||||
[Coding Games in Scratch][7] by Jon Woodcock
|
||||
|
||||
Written for children ages 8-12 with little to no coding experience, this straightforward visual guide uses fun graphics and easy-to-follow instructions to show young learners how to build their own computer projects using Scratch, a popular free programming language. (Recommendation by [Joshua Allen Holm][4] | Review is an excerpt from the book's abstract)
|
||||
|
||||
[Doing Math with Python][8] by Amit Saha
|
||||
|
||||
Whether you're a student or a teacher who's curious about how you can use Python for mathematics, this book is for you. Beginning with simple mathematical operations in the Python shell to the visualization of data using Python libraries like matplotlib, this books logically takes the reader step by easily followed step from the basics to more complex operations. This book will invite your curiosity about the power of Python with mathematics. (Recommendation and review by [Don Watkins][9])
|
||||
|
||||
[Girls Who Code: Learn to Code and Change the World][10] by Reshma Saujani
|
||||
|
||||
From the leader of the movement championed by Sheryl Sandberg, Malala Yousafzai, and John Legend, this book is part how-to, part girl-empowerment, and all fun. Bursting with dynamic artwork, down-to-earth explanations of coding principles, and real-life stories of girls and women working at places like Pixar and NASA, this graphically animated book shows what a huge role computer science plays in our lives and how much fun it can be. (Recommendation by [Joshua Allen Holm][4] | Review is an excerpt from the book's abstract)
|
||||
|
||||
[Invent Your Own Computer Games with Python][11] by Al Sweigart
|
||||
|
||||
This book will teach you how to make computer games using the popular Python programming language—even if you’ve never programmed before! Begin by building classic games like Hangman, Guess the Number, and Tic-Tac-Toe, and then work your way up to more advanced games, like a text-based treasure hunting game and an animated collision-dodging game with sound effects. (Recommendation by [Joshua Allen Holm][4] | Review is an excerpt from the book's abstract)
|
||||
|
||||
[Lauren Ipsum: A Story About Computer Science and Other Improbable Things][12] by Carlos Bueno
|
||||
|
||||
Written in the spirit of Alice in Wonderland, Lauren Ipsum takes its heroine through a slightly magical world whose natural laws are the laws of logic and computer science and whose puzzles can be solved only through learning and applying the principles of computer code. Computers are never mentioned, but they're at the center of it all. (Recommendation and review by [DB Clinton][6])
|
||||
|
||||
[Learn Java the Easy Way: A Hands-On Introduction to Programming][13] by Bryson Payne
|
||||
|
||||
Java is the world's most popular programming language, but it’s known for having a steep learning curve. This book takes the chore out of learning Java with hands-on projects that will get you building real, functioning apps right away. (Recommendation by [Joshua Allen Holm][4] | Review is an excerpt from the book's abstract)
|
||||
|
||||
[Lifelong Kindergarten][14] by Mitchell Resnick
|
||||
|
||||
Kindergarten is becoming more like the rest of school. In this book, learning expert Mitchel Resnick argues for exactly the opposite: The rest of school (even the rest of life) should be more like kindergarten. To thrive in today's fast-changing world, people of all ages must learn to think and act creatively―and the best way to do that is by focusing more on imagining, creating, playing, sharing, and reflecting, just as children do in traditional kindergartens. Drawing on experiences from more than 30 years at MIT's Media Lab, Resnick discusses new technologies and strategies for engaging young people in creative learning experiences. (Recommendation by [Don Watkins][9] | Review from Amazon)
|
||||
|
||||
[Python for Kids][15] by Jason Briggs
|
||||
|
||||
Jason Briggs has taken the art of teaching Python programming to a new level in this book that can easily be an introductory text for teachers and students as well as parents and kids. Complex concepts are presented with step-by-step directions that will have even neophyte programmers experiencing the success that invites you to learn more. This book is an extremely readable, playful, yet powerful introduction to Python programming. You will learn fundamental data structures like tuples, lists, and maps. The reader is shown how to create functions, reuse code, and use control structures like loops and conditional statements. Kids will learn how to create games and animations, and they will experience the power of Tkinter to create advanced graphics. (Recommendation and review by [Don Watkins][9])
|
||||
|
||||
[Scratch Programming Playground][16] by Al Sweigart
|
||||
|
||||
Scratch programming is often seen as a playful way to introduce young people to programming. In this book, Al Sweigart demonstrates that Scratch is in fact a much more powerful programming language than most people realize. Masterfully written and presented in his own unique style, Al will have kids exploring the power of Scratch to create complex graphics and animation in no time. (Recommendation and review by [Don Watkins][9])
|
||||
|
||||
[Secret Coders][17] by Mike Holmes
|
||||
|
||||
From graphic novel superstar (and high school computer programming teacher) Gene Luen Yang comes a wildly entertaining new series that combines logic puzzles and basic programming instruction with a page-turning mystery plot. Stately Academy is the setting, a school that is crawling with mysteries to be solved! (Recommendation by [Joshua Allen Holm][4] | Review is an excerpt from the book's abstract)
|
||||
|
||||
[So, You Want to Be a Coder?: The Ultimate Guide to a Career in Programming, Video Game Creation, Robotics, and More!][18] by Jane Bedell
|
||||
|
||||
Love coding? Make your passion your profession with this comprehensive guide that reveals a whole host of careers working with code. (Recommendation by [Joshua Allen Holm][4] | Review is an excerpt from the book's abstract)
|
||||
|
||||
[Teach Your Kids to Code][19] by Bryson Payne
|
||||
|
||||
Are you looking for a playful way to introduce children to programming with Python? Bryson Payne has written a masterful book that uses the metaphor of turtle graphics in Python. This book will have you creating simple programs that are the basis for advanced Python programming. This book is a must-read for anyone who wants to teach young people to program. (Recommendation and review by [Don Watkins][9])
|
||||
|
||||
[The Children's Illustrated Guide to Kubernetes][20] by Matt Butcher, illustrated by Bailey Beougher
|
||||
|
||||
Introducing Phippy, an intrepid little PHP app, and her journey to Kubernetes. (Recommendation by [Chris Short][21] | Review from [Matt Butcher's blog post][20].)
|
||||
|
||||
### Bonus books for babies
|
||||
|
||||
[CSS for Babies][22], [Javascript for Babies][23], and [HTML for Babies][24] by Sterling Children's
|
||||
|
||||
These concept books familiarize young ones with the kind of shapes and colors that make up web-based programming languages. This beautiful book is a colorful introduction to coding and the web, and it's the perfect gift for any technologically minded family. (Recommendation by [Chris Short][21] | Review from Amazon)
|
||||
|
||||
Have other books for babies or kids to share? Let us know in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/5/books-kids-linux-open-source
|
||||
|
||||
作者:[Jen Wike Huger][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/remyd
|
||||
[1]:https://opensource.com/resources/linux
|
||||
[2]:https://opensource.com/article/18/3/what-open-source-programming
|
||||
[3]:https://www.amazon.com/Adventures-Raspberry-Carrie-Anne-Philbin/dp/1119046025
|
||||
[4]:https://opensource.com/users/holmja
|
||||
[5]:https://automatetheboringstuff.com/
|
||||
[6]:https://opensource.com/users/dbclinton
|
||||
[7]:https://www.goodreads.com/book/show/25733628-coding-games-in-scratch
|
||||
[8]:https://nostarch.com/doingmathwithpython
|
||||
[9]:https://opensource.com/users/don-watkins
|
||||
[10]:https://www.amazon.com/Girls-Who-Code-Learn-Change/dp/042528753X
|
||||
[11]:http://inventwithpython.com/invent4thed/
|
||||
[12]:https://www.amazon.com/gp/product/1593275749/ref=as_li_tl?ie=UTF8&tag=projemun-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=1593275749&linkId=e05e1f12176c4959cc1aa1a050908c4a
|
||||
[13]:https://nostarch.com/learnjava
|
||||
[14]:http://lifelongkindergarten.net/
|
||||
[15]:https://nostarch.com/pythonforkids
|
||||
[16]:https://nostarch.com/scratchplayground
|
||||
[17]:http://www.secret-coders.com/
|
||||
[18]:https://www.amazon.com/So-You-Want-Coder-Programming/dp/1582705798?tag=ad-backfill-amzn-no-or-one-good-20
|
||||
[19]:https://opensource.com/education/15/9/review-bryson-payne-teach-your-kids-code
|
||||
[20]:https://deis.com/blog/2016/kubernetes-illustrated-guide/
|
||||
[21]:https://opensource.com/users/chrisshort
|
||||
[22]:https://www.amazon.com/CSS-Babies-Code-Sterling-Childrens/dp/1454921560/
|
||||
[23]:https://www.amazon.com/Javascript-Babies-Code-Sterling-Childrens/dp/1454921579/
|
||||
[24]:https://www.amazon.com/HTML-Babies-Code-Sterling-Childrens/dp/1454921552
|
||||
@ -1,81 +0,0 @@
|
||||
Translating by qhwdw
|
||||
How insecure is your router?
|
||||
======
|
||||

|
||||
|
||||
I've always had a problem with the t-shirt that reads, "There's no place like 127.0.0.1." I know you're supposed to read it as "home," but to me, it says, "There's no place like localhost," which just doesn't have the same ring to it. And in this post, I want to talk about something broader: the entry point to your home network, which for most people will be a cable or broadband router.1 The UK and U.S. governments just published advice that "Russia"2 is attacking routers. This attack will be aimed mostly, I suspect, at organisations (see my previous post "[What's a state actor, and should I care?][1]"), rather than homes, but it's a useful wake-up call for all of us.
|
||||
|
||||
### What do routers do?
|
||||
|
||||
Routers are important. They provide the link between one network (in this case, our home network) and another one (in this case, the internet, via our ISP's network). In fact, for most of us, the box we think of as "the router"3 is doing a lot more than that. The "routing" bit is what is sounds like; it helps computers on your network find routes to send data to computers outside the network—and vice-versa, for when you're getting data back.
|
||||
|
||||
High among a router's other functions, many also perform as a modem. Most of us4 connect to the internet via a phone line—whether cable or standard landline—though there is a growing trend for mobile internet to the home. When you're connecting via a phone line, the signals we use for the internet must be converted to something else and then (at the other end) back again. For those of us old enough to remember the old "dial-up" days, that's what the screechy box next to your computer used to do.
|
||||
|
||||
But routers often do more things, sometimes many more things, including traffic logging, acting as a WiFi access point, providing a VPN for external access to your internal network, child access, firewalling, and all the rest.
|
||||
|
||||
Home routers are complex things these days; although state actors may not be trying to get into them, other people may.
|
||||
|
||||
Does this matter, you ask? Well, if other people can get into your system, they have easy access to attacking your laptops, phones, network drives, and the rest. They can access and delete unprotected personal data. They can plausibly pretend to be you. They can use your network to host illegal data or launch attacks on others. Basically, all the bad things.
|
||||
|
||||
Luckily, routers tend to come set up by your ISP, with the implication being that you can leave them, and they'll be nice and safe.
|
||||
|
||||
### So we're safe, then?
|
||||
|
||||
Unluckily, we're really not.
|
||||
|
||||
The first problem is that ISPs are working on a budget, and it's in their best interests to provide cheap kit that just does the job. The quality of ISP-provided routers tends to be pretty terrible. It's also high on the list of things to try to attack by malicious actors: If they know that a particular router model is installed in several million homes, there's a great incentive to find an attack, because an attack on that model will be very valuable to them.
|
||||
|
||||
Other problems that arise include:
|
||||
|
||||
* Slowness to fix known bugs or vulnerabilities. Updating firmware can be costly to your ISP, so fixes may be slow to arrive (if they do at all).
|
||||
* Easily derived or default admin passwords, which means attackers don't even need to find a real vulnerability—they can just log in.
|
||||
|
||||
|
||||
|
||||
### Measures to take
|
||||
|
||||
Here's a quick list of steps you can take to try to improve the security of your first hop to the internet. I've tried to order them in terms of ease—simplest first. Before you do any of these, however, save the configuration data so you can bring it back if you need it.
|
||||
|
||||
1. **Passwords:** Always, always, always change the admin password for your router. It's probably going to be one you rarely use, so you'll want to record it somewhere. This is one of the few times where you might want to consider taping it to the router itself, as long as the router is in a secure place where only authorised people (you and your family5) have access.
|
||||
2. **Internal admin access only:** Unless you have very good reasons and you know what you're doing, don't allow machines to administer the router unless they're on your home network. There should be a setting on your router for this.
|
||||
3. **WiFi passwords:** Once you've done item 2, also ensure that WiFi passwords on your network—whether set on your router or elsewhere—are strong. It's easy to set a "friendly" password to make it easy for visitors to connect to your network, but if a malicious person who happens to be nearby guesses it, the first thing that person will do is to look for routers on the network. As they're on the internal network, they'll have access to it (hence why item 1 is important).
|
||||
4. **Turn on only the functions that you understand and need:** As I noted above, modern routers have all sorts of cool options. Disregard them. Unless you really need them, and you actually understand what they do and the dangers of turning them on, then leave them off. Otherwise, you're just increasing your attack surface.
|
||||
5. **Buy your own router:** Replace your ISP-supplied router with a better one. Go to your local computer store and ask for suggestions. You can pay an awful lot, but you can also get something fairly cheap that does the job and is more robust, performant, and easy to secure than the one you have at the moment. You may also want to buy a separate modem. Generally, setting up your modem or router is simple, and you can copy the settings from the ISP-supplied one and it will "just work."
|
||||
6. **Firmware updates:** I'd love to move this further up the list, but it's not always easy. From time to time, firmware updates appear for your router. Most routers will check automatically and may prompt you to update when you next log in. The problem is that failure to update correctly can cause catastrophic results6 or lose configuration data that you'll need to re-enter. But you really do need to consider keeping a lookout for firmware updates that fix severe security issues and implement them.
|
||||
7. **Go open source:** There are some great open source router projects out there that allow you to take an existing router and replace all of its firmware/software with open source alternatives. You can find many of them on [Wikipedia][2], and a search for ["router" on Opensource.com][3] will open your eyes to a set of fascinating opportunities. This isn't a step for the faint-hearted, as you'll definitely void the warranty on your router, but if you want to have real control, open source is always the way to go.
|
||||
|
||||
|
||||
|
||||
### Other issues
|
||||
|
||||
I'd love to pretend that once you've improved the security of your router, all's well and good on your home network, but it's not. What about IoT devices in your home (Alexa, Nest, Ring doorbells, smart lightbulbs, etc.?) What about VPNs to other networks? Malicious hosts via WiFi, malicious apps on your children's phones…?
|
||||
|
||||
No, you won't be safe. But, as we've discussed before, although there is no such thing as "secure," it doesn't mean we shouldn't raise the bar and make it harder for the Bad Folks.™
|
||||
|
||||
1. I'm simplifying—but read on, we'll get there.
|
||||
2. "Russian state-sponsored cyber actors"
|
||||
3. Or, in my parents' case, "the internet box," I suspect.
|
||||
4. This is one of these cases where I don't want comments telling me how you have a direct, 1TB/s connection to your local backbone, thank you very much.
|
||||
5. Maybe not the entire family.
|
||||
6. Your router is now a brick, and you have no access to the internet.
|
||||
|
||||
|
||||
|
||||
This article originally appeared on [Alice, Eve, and Bob – a security blog][4] and is republished with permission.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/5/how-insecure-your-router
|
||||
|
||||
作者:[Mike Bursell][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/mikecamel
|
||||
[1]:https://aliceevebob.com/2018/03/13/whats-a-state-actor-and-should-i-care/
|
||||
[2]:https://en.wikipedia.org/wiki/List_of_router_firmware_projects
|
||||
[3]:https://opensource.com/sitewide-search?search_api_views_fulltext=router
|
||||
[4]:https://aliceevebob.com/2018/04/17/defending-our-homes/
|
||||
@ -1,102 +0,0 @@
|
||||
translating---geekpi
|
||||
|
||||
How To Disable Built-in Webcam In Linux
|
||||
======
|
||||
|
||||

|
||||
|
||||
Today, we’ll see how to disable built-in webcam or external webcam when it’s not used, and how to enable it back when it’s required in your Linux box. Disabling web cam can help you in many ways. You can prevent from the malware taking control of your integrated webcam and spy on you and your home. We have read countless stories in the past that some hackers can spy on you using your webcam without your knowledge. By hacking your webcam, the user can share your private photos and videos online. There could be many reasons. If you’re ever wondered how to disable the web cam in your Laptop or desktop, you’re in luck. This brief tutorial will show you how. Read on.
|
||||
|
||||
I tested this guide on Arch Linux and Ubuntu. It worked exactly as described below. I hope this will work on other Linux distributions as well.
|
||||
|
||||
### Disable Built-in webcam in Linux
|
||||
|
||||
First, find the web cam driver using command:
|
||||
```
|
||||
$ sudo lsmod | grep uvcvideo
|
||||
|
||||
```
|
||||
|
||||
**Sample output:**
|
||||
```
|
||||
uvcvideo 114688 1
|
||||
videobuf2_vmalloc 16384 1 uvcvideo
|
||||
videobuf2_v4l2 28672 1 uvcvideo
|
||||
videobuf2_common 53248 2 uvcvideo,videobuf2_v4l2
|
||||
videodev 208896 4 uvcvideo,videobuf2_common,videobuf2_v4l2
|
||||
media 45056 2 uvcvideo,videodev
|
||||
usbcore 286720 9 uvcvideo,usbhid,usb_storage,ehci_hcd,ath3k,btusb,uas,ums_realtek,ehci_pci
|
||||
|
||||
```
|
||||
|
||||
Here, **uvcvideo** is my web cam driver.
|
||||
|
||||
Now, let us disable webcam.
|
||||
|
||||
To do so, edit the following file (if the file is not exists, just create it):
|
||||
```
|
||||
$ sudo nano /etc/modprobe.d/blacklist.conf
|
||||
|
||||
```
|
||||
|
||||
Add the following lines:
|
||||
```
|
||||
##Disable webcam.
|
||||
blacklist uvcvideo
|
||||
|
||||
```
|
||||
|
||||
The line **“##Disable webcam”** is not necessary. I have added it for the sake of easy understanding.
|
||||
|
||||
Save and exit the file. Reboot your system to take effect the changes.
|
||||
|
||||
To verify, whether Webcam is really disabled or not, open any instant messenger applications or web cam software such as Cheese or Guvcview. You will see a blank screen like below.
|
||||
|
||||
**Cheese output:**
|
||||
|
||||
![][2]
|
||||
|
||||
**Guvcview output:**
|
||||
|
||||
![][3]
|
||||
|
||||
See? The web cam is disabled and is not working.
|
||||
|
||||
To enable it back, edit:
|
||||
```
|
||||
$ sudo nano /etc/modprobe.d/blacklist.conf
|
||||
|
||||
```
|
||||
|
||||
Comment the lines which you have added earlier.
|
||||
```
|
||||
##Disable webcam.
|
||||
#blacklist uvcvideo
|
||||
|
||||
```
|
||||
|
||||
Save and close the file. Then, reboot your Computer to enable your Webcam.
|
||||
|
||||
Does it enough? No. Why? If someone can remotely access your system, they can easily enable the webcam back. So, It is always a good idea to cover it up with a tape or unplug the camera or disable it in the BIOS when it’s not used. This method is not just for disabling the built-in webcam, but also for external web camera.
|
||||
|
||||
And, that’s all for now. Hope this was useful. More good stuffs to come. Stay tuned!
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/how-to-disable-built-in-webcam-in-ubuntu/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.ostechnix.com/author/sk/
|
||||
[1]:data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[2]:http://www.ostechnix.com/wp-content/uploads/2015/08/cheese.jpg
|
||||
[3]:http://www.ostechnix.com/wp-content/uploads/2015/08/guvcview.jpg
|
||||
@ -1,175 +0,0 @@
|
||||
Translating by lonaparte-CHENG
|
||||
|
||||
8 basic Docker container management commands
|
||||
======
|
||||
Learn basic Docker container management with the help of these 8 commands. Useful guide for Docker beginners which includes sample command outputs.
|
||||
|
||||
![Docker container management commands][1]
|
||||
|
||||
In this article we will walk you through 6 basic Docker container commands which are useful in performing basic activities on Docker containers like run, list, stop, view logs, delete etc. If you are new to Docker concept then do check our [introduction guide][2] to know what is Docker & [how-to guide][3] to install Docker in Linux. Without further delay lets directly jump into commands :
|
||||
|
||||
### How to run Docker container?
|
||||
|
||||
As you know, Docker container is just a application process running on host OS. For Docker container, you need a image to run from. Docker image when runs as process called as Docker container. You can have Docker image available locally or you have to download it from Docker hub. Docker hub is a centralized repository which has public and private images stored to pull from. Docker’s official hub is at [hub.docker.com][4]. So whenever you instruct Docker engine to run a container, it looks for image locally and if not found it pulls it from Docker hub.
|
||||
|
||||
Let’s run a Docker container for Apache web-server i.e httpd process. You need to run command `docker container run`. Old command was just `docker run` but lately Docker added sub-command section so new versions supports below command –
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container run -d -p 80:80 httpd
|
||||
Unable to find image 'httpd:latest' locally
|
||||
latest: Pulling from library/httpd
|
||||
3d77ce4481b1: Pull complete
|
||||
73674f4d9403: Pull complete
|
||||
d266646f40bd: Pull complete
|
||||
ce7b0dda0c9f: Pull complete
|
||||
01729050d692: Pull complete
|
||||
014246127c67: Pull complete
|
||||
7cd2e04cf570: Pull complete
|
||||
Digest: sha256:f4610c3a1a7da35072870625733fd0384515f7e912c6223d4a48c6eb749a8617
|
||||
Status: Downloaded newer image for httpd:latest
|
||||
c46f2e9e4690f5c28ee7ad508559ceee0160ac3e2b1688a61561ce9f7d99d682
|
||||
```
|
||||
|
||||
Docker `run` command takes image name as a mandatory argument along with many other optional ones. Commanly used arguments are –
|
||||
|
||||
* `-d` : Detach container from current shell
|
||||
* `-p X:Y` : Bind container port Y with host’s port X
|
||||
* `--name` : Name your container. If not used, it will be assigned randomly generated name
|
||||
* `-e` : Pass environmental variables and their values while starting container
|
||||
|
||||
|
||||
|
||||
In above output you can see, we supply `httpd` as a image name to run container from. Since, image was not locally found, Docker engine pulled it from Docker Hub. Now, observe it downloaded image **httpd:latest **where : is followed by version. That’s the naming convention of Docker container image. If you want specific version container to run from then you can provide version name along with image name. If not supplied, Docker engine will always pull latest one.
|
||||
|
||||
The very last line of output shown unique container ID of your newly running httpd container.
|
||||
|
||||
### How to list all running Docker containers?
|
||||
|
||||
Now, your container is running, you may want to check it or you want to list all running containers on your machine. You can list all running containers using `docker container ls` command. In old Docker version, `docker ps` does this task for you.
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container ls
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
c46f2e9e4690 httpd "httpd-foreground" 11 minutes ago Up 11 minutes 0.0.0.0:80->80/tcp cranky_cori
|
||||
```
|
||||
|
||||
Listing output is presented in column-wise format. Where column-wise values are –
|
||||
|
||||
1. Container ID : First few digits of unique container ID
|
||||
2. Image : Name of image used to run container
|
||||
3. Command : Command ran by container after it ran
|
||||
4. Created : Time created
|
||||
5. Status : Current status of container
|
||||
6. Ports : Port binding details with host’s ports
|
||||
7. Names : Name of container (since we haven’t named our container you can see randomly generated name assigned to our container)
|
||||
|
||||
|
||||
|
||||
### How to view logs of Docker container?
|
||||
|
||||
Since during first step we used -d switch to detach container from current shell once it ran its running in background. In this case, we are clueless whats happening inside container. So to view logs of container, Docker provided `logs` command. It takes container name or ID as an argument.
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container logs cranky_cori
|
||||
AH00558: httpd: Could not reliably determine the server's fully qualified domain name, using 172.17.0.2. Set the 'ServerName' directive globally to suppress this message
|
||||
AH00558: httpd: Could not reliably determine the server's fully qualified domain name, using 172.17.0.2. Set the 'ServerName' directive globally to suppress this message
|
||||
[Thu May 31 18:35:07.301158 2018] [mpm_event:notice] [pid 1:tid 139734285989760] AH00489: Apache/2.4.33 (Unix) configured -- resuming normal operations
|
||||
[Thu May 31 18:35:07.305153 2018] [core:notice] [pid 1:tid 139734285989760] AH00094: Command line: 'httpd -D FOREGROUND'
|
||||
```
|
||||
|
||||
I used container name in my command as argument. You can see Apache related log within our httpd container.
|
||||
|
||||
### How to identify Docker container process?
|
||||
|
||||
Container is a process which uses host resources to run. If its true, then you will be able to locate container process on host’s process table. Lets see how to check container process on host.
|
||||
|
||||
Docker used famous `top` command as its sub-command’s name to view processes spawned by container. It takes container name/ID as an argument. In old Docker version only `docker top` command works. In newer versions, `docker top` and `docker container top` both works.
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container top cranky_cori
|
||||
UID PID PPID C STIME TTY TIME CMD
|
||||
root 15702 15690 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
bin 15729 15702 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
bin 15730 15702 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
bin 15731 15702 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
|
||||
root@kerneltalks # ps -ef |grep -i 15702
|
||||
root 15702 15690 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
bin 15729 15702 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
bin 15730 15702 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
bin 15731 15702 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
root 15993 15957 0 18:59 pts/0 00:00:00 grep --color=auto -i 15702
|
||||
```
|
||||
|
||||
In the first output, list of processes spawned by that container. It has all details like use, pid, ppid, start time, command etc. All those PID you can search in your host’s process table and you can find them there. That’s what we did in second command. So, this proves containers are indeed just processes on Host’s OS.
|
||||
|
||||
### How to stop Docker container?
|
||||
|
||||
Its simple `stop` command! Again it takes container name /ID as an argument.
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container stop cranky_cori
|
||||
cranky_cori
|
||||
```
|
||||
|
||||
### How to list stopped or not running Docker containers?
|
||||
|
||||
Now we stopped our container if we try to list container using `ls` command, we wont be able to see it.
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container ls
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
```
|
||||
|
||||
So in this case to view stopped or non running container you need to use `-a` switch along with `ls` command.
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container ls -a
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
c46f2e9e4690 httpd "httpd-foreground" 33 minutes ago Exited (0) 2 minutes ago cranky_cori
|
||||
```
|
||||
|
||||
With `-a` switch we can see stopped container now. Notice status of this container is mentioned ‘Exited’. Since container is just a process its termed as ‘exited’ rather than stopped!
|
||||
|
||||
### How to start Docker container?
|
||||
|
||||
Now, we will start this stopped container. There is difference with running and starting a container. When you run a container, you are starting a command in fresh container. When you start a container, you are starting old stopped container which has old state saved in it. It will start it from that state forward.
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container start c46f2e9e4690
|
||||
c46f2e9e4690
|
||||
|
||||
root@kerneltalks # docker container ls -a
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
c46f2e9e4690 httpd "httpd-foreground" 35 minutes ago Up 8 seconds 0.0.0.0:80->80/tcp cranky_cori
|
||||
```
|
||||
|
||||
### How to remove Docker container?
|
||||
|
||||
To remove container from your Docker engine use `rm` command. You can not remove running container. You have to first stop the container and then remove it. You can remove it forcefully using `-f` switch with `rm` command but that’s not recommended.
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container rm cranky_cori
|
||||
cranky_cori
|
||||
root@kerneltalks # docker container ls -a
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
```
|
||||
|
||||
You can see once we remove container, its not visible in `ls -a` listing too.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://kerneltalks.com/virtualization/8-basic-docker-container-management-commands/
|
||||
|
||||
作者:[Shrikant Lavhate][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://kerneltalks.com
|
||||
[1]:https://a4.kerneltalks.com/wp-content/uploads/2018/06/basic-Docker-container-management-commands.png
|
||||
[2]:https://kerneltalks.com/virtualization/what-is-docker-introduction-guide-to-docker/
|
||||
[3]:https://kerneltalks.com/virtualization/how-to-install-docker-in-linux/
|
||||
[4]:https://hub.docker.com/
|
||||
@ -1,185 +0,0 @@
|
||||
How to partition a disk in Linux
|
||||
======
|
||||

|
||||
|
||||
Creating and deleting partitions in Linux is a regular practice because storage devices (such as hard drives and USB drives) must be structured in some way before they can be used. In most cases, large storage devices are divided into separate sections called partitions. Partitioning also allows you to divide your hard drive into isolated sections, where each section behaves as its own hard drive. Partitioning is particularly useful if you run multiple operating systems.
|
||||
|
||||
There are lots of powerful tools for creating, removing, and otherwise manipulating disk partitions in Linux. In this article, I'll explain how to use the `parted` command, which is particularly useful with large disk devices and many disk partitions. Differences between `parted` and the more common `fdisk` and `cfdisk` commands include:
|
||||
|
||||
* **GPT format:** The `parted` command can create a Globally Unique Identifiers Partition Table [GPT][1]), while `fdisk` and `cfdisk` are limited to DOS partition tables.
|
||||
* **Larger disks:** A DOS partition table can format up to 2TB of disk space, although up to 16TB is possible in some cases. However, a GPT partition table can address up to 8ZiB of space.
|
||||
* **More partitions:** Using primary and extended partitions, DOS partition tables allow only 16 partitions. With GPT, you get up to 128 partitions by default and can choose to have many more.
|
||||
* **Reliability:** Only one copy of the partition table is stored in a DOS partition. GPT keeps two copies of the partition table (at the beginning and the end of the disk). The GPT also uses a [CRC][2] checksum to check the partition table integrity, which is not done with DOS partitions.
|
||||
|
||||
|
||||
|
||||
With today's larger disks and the need for more flexibility in working with them, using `parted` to work with disk partitions is recommended. Most of the time, disk partition tables are created as part of the operating system installation process. Direct use of the `parted` command is most useful when adding a storage device to an existing system.
|
||||
|
||||
### Give 'parted' a try
|
||||
|
||||
`parted` command. To try these steps, I strongly recommend using a brand new storage device or one where you don't mind wiping out the contents.
|
||||
|
||||
The following explains the process of partitioning a storage device with thecommand. To try these steps, I strongly recommend using a brand new storage device or one where you don't mind wiping out the contents.
|
||||
|
||||
**1\. List the partitions:** Use `parted -l` to identify the storage device you want to partition. Typically, the first hard disk (`/dev/sda` or `/dev/vda`) will contain the operating system, so look for another disk to find the one you want (e.g., `/dev/sdb`, `/dev/sdc`, `/dev/vdb`, `/dev/vdc`, etc.).
|
||||
```
|
||||
$ sudo parted -l
|
||||
|
||||
[sudo] password for daniel:
|
||||
|
||||
Model: ATA RevuAhn_850X1TU5 (scsi)
|
||||
|
||||
Disk /dev/vdc: 512GB
|
||||
|
||||
Sector size (logical/physical): 512B/512B
|
||||
|
||||
Partition Table: msdos
|
||||
|
||||
Disk Flags:
|
||||
|
||||
|
||||
|
||||
Number Start End Size Type File system Flags
|
||||
|
||||
1 1049kB 525MB 524MB primary ext4 boot
|
||||
|
||||
2 525MB 512GB 512GB primary lvm
|
||||
|
||||
```
|
||||
|
||||
**2\. Open the storage device:** Use `parted` to begin working with the selected storage device. In this example, the device is the third disk on a virtual system (`/dev/vdc`). It is important to indicate the specific device you want to use. If you just type `parted` with no device name, it will randomly select a storage device to modify.
|
||||
```
|
||||
$ sudo parted /dev/vdc
|
||||
|
||||
GNU Parted 3.2
|
||||
|
||||
Using /dev/vdc
|
||||
|
||||
Welcome to GNU Parted! Type 'help' to view a list of commands.
|
||||
|
||||
(parted)
|
||||
|
||||
```
|
||||
|
||||
**3\. Set the partition table:** Set the partition table type to GPT, then type "Yes" to accept it.
|
||||
```
|
||||
(parted) mklabel gpt
|
||||
|
||||
Warning: the existing disk label on /dev/vdc will be destroyed
|
||||
|
||||
and all data on this disk will be lost. Do you want to continue?
|
||||
|
||||
Yes/No? Yes
|
||||
|
||||
```
|
||||
|
||||
The `mklabel` and `mktable` commands are used for the same purpose (making a partition table on a storage device). The supported partition tables are: aix, amiga, bsd, dvh, gpt, mac, ms-dos, pc98, sun, and loop. Remember `mklabel` will not make a partition, rather it will make a partition table.
|
||||
|
||||
**4\. Review the partition table:** Show information about the storage device.
|
||||
```
|
||||
(parted) print
|
||||
|
||||
Model: Virtio Block Device (virtblk)
|
||||
|
||||
Disk /dev/vdc: 1396MB
|
||||
|
||||
Sector size (logical/physical): 512B/512B
|
||||
|
||||
Partition Table: gpt
|
||||
|
||||
Disk Flags:
|
||||
|
||||
Number Start End Size File system Name Flags
|
||||
|
||||
```
|
||||
|
||||
**5\. Get help:** To find out how to make a new partition, type: `(parted) help mkpart`.
|
||||
```
|
||||
(parted) help mkpart
|
||||
|
||||
mkpart PART-TYPE [FS-TYPE] START END make a partition
|
||||
|
||||
|
||||
|
||||
PART-TYPE is one of: primary, logical, extended
|
||||
|
||||
FS-TYPE is one of: btrfs, nilfs2, ext4, ext3, ext2, fat32, fat16, hfsx, hfs+, hfs, jfs, swsusp,
|
||||
|
||||
linux-swap(v1), linux-swap(v0), ntfs, reiserfs, hp-ufs, sun-ufs, xfs, apfs2, apfs1, asfs, amufs5,
|
||||
|
||||
amufs4, amufs3, amufs2, amufs1, amufs0, amufs, affs7, affs6, affs5, affs4, affs3, affs2, affs1,
|
||||
|
||||
affs0, linux-swap, linux-swap(new), linux-swap(old)
|
||||
|
||||
START and END are disk locations, such as 4GB or 10%. Negative values count from the end of the
|
||||
|
||||
disk. For example, -1s specifies exactly the last sector.
|
||||
|
||||
|
||||
|
||||
'mkpart' makes a partition without creating a new file system on the partition. FS-TYPE may be
|
||||
|
||||
specified to set an appropriate partition ID.
|
||||
|
||||
```
|
||||
|
||||
**6\. Make a partition:** To make a new partition (in this example, 1,396MB on partition 0), type the following:
|
||||
```
|
||||
(parted) mkpart primary 0 1396MB
|
||||
|
||||
|
||||
|
||||
Warning: The resulting partition is not properly aligned for best performance
|
||||
|
||||
Ignore/Cancel? I
|
||||
|
||||
|
||||
|
||||
(parted) print
|
||||
|
||||
Model: Virtio Block Device (virtblk)
|
||||
|
||||
Disk /dev/vdc: 1396MB
|
||||
|
||||
Sector size (logical/physical): 512B/512B
|
||||
|
||||
Partition Table: gpt
|
||||
|
||||
Disk Flags:
|
||||
|
||||
Number Start End Size File system Name Flags
|
||||
|
||||
1 17.4kB 1396MB 1396MB primary
|
||||
|
||||
```
|
||||
|
||||
Filesystem type (fstype) will not create an ext4 filesystem on `/dev/vdc1`. A DOS partition table's partition types are primary, logical, and extended. In a GPT partition table, the partition type is used as the partition name. Providing a partition name under GPT is a must; in the above example, primary is the name, not the partition type.
|
||||
|
||||
**7\. Save and quit:** Changes are automatically saved when you quit `parted`. To quit, type the following:
|
||||
```
|
||||
(parted) quit
|
||||
|
||||
Information: You may need to update /etc/fstab.
|
||||
|
||||
$
|
||||
|
||||
```
|
||||
|
||||
### Words to the wise
|
||||
|
||||
Make sure to identify the correct disk before you begin changing its partition table when you add a new storage device. If you mistakenly change the disk partition that contains your computer's operating system, you could make your system unbootable.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/6/how-partition-disk-linux
|
||||
|
||||
作者:[Daniel Oh][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/daniel-oh
|
||||
[1]:https://en.wikipedia.org/wiki/GUID_Partition_Table
|
||||
[2]:https://en.wikipedia.org/wiki/Cyclic_redundancy_check
|
||||
@ -0,0 +1,183 @@
|
||||
4 tools for building embedded Linux systems
|
||||
======
|
||||

|
||||
|
||||
Linux is being deployed into a much wider array of devices than Linus Torvalds anticipated when he was working on it in his dorm room. The variety of supported chip architectures is astounding and has led to Linux in devices large and small; from [huge IBM mainframes][1] to [tiny devices][2] no bigger than their connection ports and everything in between. It is used in large enterprise data centers, internet infrastructure devices, and personal development systems. It also powers consumer electronics, mobile phones, and many Internet of Things devices.
|
||||
|
||||
When building Linux software for desktop and enterprise-class devices, developers typically use a desktop distribution such as [Ubuntu][3] on their build machines to have an environment as close as possible to the one where the software will be deployed. Tools such as [VirtualBox][4] and [Docker][5] allow even better alignment between development, testing, and productions environments.
|
||||
|
||||
### What is an embedded system?
|
||||
|
||||
Wikipedia defines an [embedded system][6] as: "A computer system with a dedicated function within a larger mechanical or electrical system, often with real-time computing constraints."
|
||||
|
||||
I find it simple enough to say that an embedded system is a computer that most people don't think of as a computer. Its primary role is to serve as an appliance of some sort, and it is not considered a general-purpose computing platform.
|
||||
|
||||
The development environment in embedded systems programming is usually very different from the testing and production environments. They may use different chip architectures, software stacks, and even operating systems. Development workflows are very different for embedded developers vs. desktop and web developers. Typically, the build output will consist of an entire software image for the target device, including the kernel, device drivers, libraries, and application software (and sometimes the bootloader).
|
||||
|
||||
In this article, I will present a survey of four commonly available options for building embedded Linux systems. I will give a flavor for what it's like to work with each and provide enough information to help readers decide which tool to use for their design. I won't teach you how to use any of them; there are plenty of in-depth online learning resources once you have narrowed your choices. No option is right for all use cases, and I hope to present enough details to direct your decision.
|
||||
|
||||
### Yocto
|
||||
|
||||
The [Yocto][7] project is [defined][8] as "an open source collaboration project that provides templates, tools, and methods to help you create custom Linux-based systems for embedded products regardless of the hardware architecture." It is a collection of recipes, configuration values, and dependencies used to create a custom Linux runtime image tailored to your specific needs.
|
||||
|
||||
Full disclosure: most of my work in embedded Linux has focused on the Yocto project, and my knowledge and bias to this system will likely be evident.
|
||||
|
||||
Yocto uses [Openembedded][9] as its build system. Technically the two are separate projects; in practice, however, users do not need to understand the distinction, and the project names are frequently used interchangeably.
|
||||
|
||||
The output of a Yocto project build consists broadly of three components:
|
||||
|
||||
* **Target run-time binaries:** These include the bootloader, kernel, kernel modules, root filesystem image. and any other auxiliary files needed to deploy Linux to the target platform.
|
||||
* **Package feed:** This is the collection of software packages available to be installed on your target. You can select the package format (e.g., deb, rpm, ipk) based on your needs. Some of them may be preinstalled in the target runtime binaries, however, it is possible to build packages for installation into a deployed system.
|
||||
* **Target SDK:** These are the collection of libraries and header files representing the software installed on your target. They are used by application developers when building their code to ensure they are linked with the appropriate libraries
|
||||
|
||||
|
||||
|
||||
#### Advantages
|
||||
|
||||
The Yocto project is widely used in the industry and has backing from many influential companies. Additionally, it has a large and vibrant developer [community][10] and [ecosystem][11] contributing to it. The combination of open source enthusiasts and corporate sponsors helps drive the Yocto project.
|
||||
|
||||
There are many options for getting support with Yocto. There are books and other training materials if you wish to do-it-yourself. Many engineers with experience in Yocto are available if you want to hire expertise. And many commercial organizations provide turnkey Yocto-based products or services-based implementation and customization for your design.
|
||||
|
||||
The Yocto project is easily expanded through [layers][12], which can be published independently to add additional functionality, to target platforms not available in the project releases, or to store customizations unique to your system. Layers can be added to your configuration to add unique features that are not specifically included in the stock releases; for example, the "[meta-browser][13]" layer contains recipes for web browsers, which can be easily built for your system. Because they are independently maintained, layers can be on a different release schedule (tuned to the layers' development velocity) than the standard Yocto releases.
|
||||
|
||||
Yocto has arguably the widest device support of any of the options discussed in this article. Due to support from many semiconductor and board manufacturers, it's likely Yocto will support any target platform you choose. The direct Yocto [releases][14] support only a few boards (to allow for proper testing and release cycles), however, a standard working model is to use external board support layers.
|
||||
|
||||
Finally, Yocto is extremely flexible and customizable. Customizations for your specific application can be stored in a layer for encapsulation and isolation. Customizations unique to a feature layer are generally stored as part of the layer itself, which allows the same settings to be applied simultaneously to multiple system configurations. Yocto also provides a well-defined layer priority and override capability. This allows you to define the order in which layers are applied and searched for metadata. It also enables you to override settings in layers with higher priority; for instance, many customizations to existing recipes will be added in your private layers, with the order precisely controlled by the priorities.
|
||||
|
||||
#### Disadvantages
|
||||
|
||||
The biggest disadvantage with the Yocto project is the learning curve. It takes significant time and effort to learn the system and truly understand it. Depending on your needs, this may be too large of an investment in technologies and competence that are not central to your application. In such cases, working with one of the commercial vendors may be a good option.
|
||||
|
||||
Development build times and resources are fairly high for Yocto project builds. The number of packages that need to be built, including the toolchain, kernel, and all target runtime components, is significant. Development workstations for Yocto developers tend to be large systems. Using a compact notebook is not recommended. This can be mitigated by using cloud-based build servers available from many providers. Additionally, Yocto has a built-in caching mechanism that allows it to reuse previously built components when it determines that the parameters for building a particular package have not changed.
|
||||
|
||||
#### Recommendation
|
||||
|
||||
Using the Yocto project for your next embedded Linux design is a strong choice. Of the options presented here, it is the most broadly applicable regardless of your target use case. The broad industry support, active community, and wide platform support make this a good choice for must designers.
|
||||
|
||||
### Buildroot
|
||||
|
||||
The [Buildroot][15] project is defined as "a simple, efficient, and easy-to-use tool to generate embedded Linux systems through cross-compilation." It shares many of the same objectives as the Yocto project, however it is focused on simplicity and minimalism. In general, Buildroot will disable all optional compile-time settings for all packages (with a few notable exceptions), resulting in the smallest possible system. It will be up to the system designer to enable the settings that are appropriate for a given device.
|
||||
|
||||
Buildroot builds all components from source but does not support on-target package management. As such, it is sometimes called a firmware generator since the images are largely fixed at build time. Applications can update the target filesystem, but there is no mechanism to install new packages into a running system.
|
||||
|
||||
The Buildroot output consists broadly of three components:
|
||||
|
||||
* The root filesystem image and any other auxiliary files needed to deploy Linux to the target platform
|
||||
* The kernel, boot-loader, and kernel modules appropriate for the target hardware
|
||||
* The toolchain used to build all the target binaries.
|
||||
|
||||
|
||||
|
||||
#### Advantages
|
||||
|
||||
Buildroot's focus on simplicity means that, in general, it is easier to learn than Yocto. The core build system is written in Make and is short enough to allow a developer to understand the entire system while being expandable enough to meet the needs of embedded Linux developers. The Buildroot core generally only handles common use cases, but it is expandable via scripting.
|
||||
|
||||
The Buildroot system uses normal Makefiles and the Kconfig language for its configuration. Kconfig was developed by the Linux kernel community and is widely used in open source projects, making it familiar to many developers.
|
||||
|
||||
Due to the design goal of disabling all optional build-time settings, Buildroot will generally produce the smallest possible images using the out-of-the-box configuration. The build times and build host resources will likewise be smaller, in general, than those of the Yocto project.
|
||||
|
||||
#### Disadvantages
|
||||
|
||||
The focus on simplicity and minimal enabled build options imply that you may need to do significant customization to configure a Buildroot build for your application. Additionally, all configuration options are stored in a single file, which means if you have multiple hardware platforms, you will need to make each of your customization changes for each platform.
|
||||
|
||||
Any change to the system configuration file requires a full rebuild of all packages. This is somewhat mitigated by the minimal image sizes and build times compared with Yocto, but it can result in long builds while you are tweaking your configuration.
|
||||
|
||||
Intermediate package state caching is not enabled by default and is not as thorough as the Yocto implementation. This means that, while the first build may be shorter than an equivalent Yocto build, subsequent builds may require rebuilding of many components.
|
||||
|
||||
#### Recommendation
|
||||
|
||||
Using Buildroot for your next embedded Linux design is a good choice for most applications. If your design requires multiple hardware types or other differences, you may want to reconsider due to the complexity of synchronizing multiple configurations, however, for a system consisting of a single setup, Buildroot will likely work well for you.
|
||||
|
||||
### OpenWRT/LEDE
|
||||
|
||||
The [OpenWRT][16] project was started to develop custom firmware for consumer routers. Many of the low-cost routers available at your local retailer are capable of running a Linux system, but maybe not out of the box. The manufacturers of these routers may not provide frequent updates to address new threats, and even if they do, the mechanisms to install updated images are difficult and error-prone. The OpenWRT project produces updated firmware images for many devices that have been abandoned by their manufacturers and gives these devices a new lease on life.
|
||||
|
||||
The OpenWRT project's primary deliverables are binary images for a large number of commercial devices. There are network-accessible package repositories that allow device end users to add new software to their systems. The OpenWRT build system is a general-purpose build system, which allows developers to create custom versions to meet their own requirements and add new packages, but its primary focus is target binaries.
|
||||
|
||||
#### Advantages
|
||||
|
||||
If you are looking for replacement firmware for a commercial device, OpenWRT should be on your list of options. It is well-maintained and may protect you from issues that the manufacturer's firmware cannot. You can add extra functionality as well, making your devices more useful.
|
||||
|
||||
If your embedded design is networking-focused, OpenWRT is a good choice. Networking applications are the primary use case for OpenWRT, and you will likely find many of those software packages available in it.
|
||||
|
||||
#### Disadvantages
|
||||
|
||||
OpenWRT imposes significant policy decisions on your design (vs. Yocto and Buildroot). If these decisions don't meet your design goals, you may have to do non-trivial modifications.
|
||||
|
||||
Allowing package-based updates in a fleet of deployed devices is difficult to manage. This, by definition, results in a different software load than what your QA team tested. Additionally, it is difficult to guarantee atomic installs with most package managers, and an ill-timed power cycle can leave your device in an unpredictable state.
|
||||
|
||||
#### Recommendation
|
||||
|
||||
OpenWRT is a good choice for hobbyist projects or for reusing commercial hardware. It is also a good choice for networking applications. If you need significant customization from the default setup, you may prefer Buildroot or Yocto.
|
||||
|
||||
### Desktop distros
|
||||
|
||||
A common approach to designing embedded Linux systems is to start with a desktop distribution, such as [Debian][17] or [Red Hat][18], and remove unneeded components until the installed image fits into the footprint of your target device. This is the approach taken for the popular [Raspbian][19] distribution for the [Raspberry Pi][20] platform.
|
||||
|
||||
#### Advantages
|
||||
|
||||
The primary advantage of this approach is familiarity. Often, embedded Linux developers are also desktop Linux users and are well-versed in their distro of choice. Using a similar environment on the target may allow developers to get started more quickly. Depending on the chosen distribution, many additional tools can be installed using standard packaging tools such as apt and yum.
|
||||
|
||||
It may be possible to attach a display and keyboard to your target device and do all your development directly there. For developers new to the embedded space, this is likely to be a more familiar environment and removes the need to configure and use a tricky cross-development setup.
|
||||
|
||||
The number of packages available for most desktop distributions is generally greater than that available for the embedded-specific builders discussed previously. Due to the larger user base and wider variety of use cases, you may be able to find all the runtime packages you need for your application already built and ready for use.
|
||||
|
||||
#### Disadvantages
|
||||
|
||||
Using the target as your primary development environment is likely to be slow. Running compiler tools is a resource-intensive operation and, depending on how much code you are building, may hinder your performance.
|
||||
|
||||
With some exceptions, desktop distributions are not designed to accommodate low-resource systems, and it may be difficult to adequately trim your target images. Similarly, the expected workflow in a desktop environment is not ideal for most embedded designs. Getting a reproducible environment in this fashion is difficult. Manually adding and deleting packages is error-prone. This can be scripted using distribution-specific tools, such as [debootstrap][21] for Debian-based systems. To further improve [reproducibility][21], you can use a configuration management tool, such as [CFEngine][22] (which, full disclosure, is made by my employer, [Mender.io][23]). However, you are still at the mercy of the distribution provider, who will update packages to meet their needs, not yours.
|
||||
|
||||
#### Recommendation
|
||||
|
||||
Be wary of this approach for a product you plan to take to market. This is a fine model for hobbyist applications; however, for products that need support, this approach is likely going to be trouble. While you may be able to get a faster start, it may cost you time and effort in the long run.
|
||||
|
||||
### Other considerations
|
||||
|
||||
This discussion has focused on build systems' functionality, but there are usually non-functional requirements that may affect your decision. If you have already selected your system-on-chip (SoC) or board, your choice will likely be dictated by the vendor. If your vendor provides a board support package (BSP) for a given system, using it will normally save quite a bit of time, but please research the BSP's quality to avoid issues later in your development cycle.
|
||||
|
||||
If your budget allows, you may want to consider using a commercial vendor for your target OS. There are companies that will provide a validated and supported configuration of many of the options discussed here, and, unless you have expertise in embedded Linux build systems, this is a good choice and will allow you to focus on your core competency.
|
||||
|
||||
As an alternative, you may consider commercial training for your development staff. This is likely to be cheaper than a commercial OS provider and will allow you to be more self-sufficient. This is a quick way to get over the learning curve for the basics of the build system you choose.
|
||||
|
||||
Finally, you may already have some developers with experience with one or more of the systems. If you have engineers who have a preference, it is certainly worth taking that into consideration as you make your decision.
|
||||
|
||||
### Summary
|
||||
|
||||
There are many choices available for building embedded Linux systems, each with advantages and disadvantages. It is crucial to prioritize this part of your design, as it is extremely costly to switch systems later in the process. In addition to these options, new systems are being developed all the time. Hopefully, this discussion will provide some context for reviewing new systems (and the ones mentioned here) and help you make a solid decision for your next project.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/6/embedded-linux-build-tools
|
||||
|
||||
作者:[Drew Moseley][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/drewmoseley
|
||||
[1]:https://en.wikipedia.org/wiki/Linux_on_z_Systems
|
||||
[2]:http://www.picotux.com/
|
||||
[3]:https://www.ubuntu.com/
|
||||
[4]:https://www.virtualbox.org/
|
||||
[5]:https://www.docker.com/
|
||||
[6]:https://en.wikipedia.org/wiki/Embedded_system
|
||||
[7]:https://yoctoproject.org/
|
||||
[8]:https://www.yoctoproject.org/about/
|
||||
[9]:https://www.openembedded.org/
|
||||
[10]:https://www.yoctoproject.org/community/
|
||||
[11]:https://www.yoctoproject.org/ecosystem/participants/
|
||||
[12]:https://layers.openembedded.org/layerindex/branch/master/layers/
|
||||
[13]:https://layers.openembedded.org/layerindex/branch/master/layer/meta-browser/
|
||||
[14]:https://yoctoproject.org/downloads
|
||||
[15]:https://buildroot.org/
|
||||
[16]:https://openwrt.org/
|
||||
[17]:https://www.debian.org/
|
||||
[18]:https://www.redhat.com/
|
||||
[19]:https://www.raspbian.org/
|
||||
[20]:https://www.raspberrypi.org/
|
||||
[21]:https://wiki.debian.org/Debootstrap
|
||||
[22]:https://cfengine.com/
|
||||
[23]:http://Mender.io
|
||||
@ -0,0 +1,195 @@
|
||||
5 Commands for Checking Memory Usage in Linux
|
||||
======
|
||||
|
||||

|
||||
The Linux operating system includes a plethora of tools, all of which are ready to help you administer your systems. From simple file and directory tools to very complex security commands, there’s not much you can’t do on Linux. And, although regular desktop users may not need to become familiar with these tools at the command line, they’re mandatory for Linux admins. Why? First, you will have to work with a GUI-less Linux server at some point. Second, command-line tools often offer far more power and flexibility than their GUI alternative.
|
||||
|
||||
Determining memory usage is a skill you might need should a particular app go rogue and commandeer system memory. When that happens, it’s handy to know you have a variety of tools available to help you troubleshoot. Or, maybe you need to gather information about a Linux swap partition or detailed information about your installed RAM? There are commands for that as well. Let’s dig into the various Linux command-line tools to help you check into system memory usage. These tools aren’t terribly hard to use, and in this article, I’ll show you five different ways to approach the problem.
|
||||
|
||||
I’ll be demonstrating on the [Ubuntu Server 18.04 platform][1]. You should, however, find all of these commands available on your distribution of choice. Even better, you shouldn’t need to install a single thing (as most of these tools are included).
|
||||
|
||||
With that said, let’s get to work.
|
||||
|
||||
### top
|
||||
|
||||
I want to start out with the most obvious tool. The top command provides a dynamic, real-time view of a running system. Included in that system summary is the ability to check memory usage on a per-process basis. That’s very important, as you could easily have multiple iterations of the same command consuming different amounts of memory. Although you won’t find this on a headless server, say you’ve opened Chrome and noticed your system slowing down. Issue the top command to see that Chrome has numerous processes running (one per tab - Figure 1).
|
||||
|
||||
![top][3]
|
||||
|
||||
Figure 1: Multiple instances of Chrome appearing in the top command.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
Chrome isn’t the only app to show multiple processes. You see the Firefox entry in Figure 1? That’s the primary process for Firefox, whereas the Web Content processes are the open tabs. At the top of the output, you’ll see the system statistics. On my machine (a [System76 Leopard Extreme][5]), I have a total of 16GB of RAM available, of which just over 10GB is in use. You can then comb through the list and see what percentage of memory each process is using.
|
||||
|
||||
One of the things top is very good for is discovering Process ID (PID) numbers of services that might have gotten out of hand. With those PIDs, you can then set about to troubleshoot (or kill) the offending tasks.
|
||||
|
||||
If you want to make top a bit more memory-friendly, issue the command top -o %MEM, which will cause top to sort all processes by memory used (Figure 2).
|
||||
|
||||
![top][7]
|
||||
|
||||
Figure 2: Sorting process by memory used in top.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
The top command also gives you a real-time update on how much of your swap space is being used.
|
||||
|
||||
### free
|
||||
|
||||
Sometimes, however, top can be a bit much for your needs. You may only need to see the amount of free and used memory on your system. For that, there is the free command. The free command displays:
|
||||
|
||||
* Total amount of free and used physical memory
|
||||
|
||||
* Total amount of swap memory in the system
|
||||
|
||||
* Buffers and caches used by the kernel
|
||||
|
||||
|
||||
|
||||
|
||||
From your terminal window, issue the command free. The output of this command is not in real time. Instead, what you’ll get is an instant snapshot of the free and used memory in that moment (Figure 3).
|
||||
|
||||
![free][9]
|
||||
|
||||
Figure 3: The output of the free command is simple and clear.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
You can, of course, make free a bit more user-friendly by adding the -m option, like so: free -m. This will report the memory usage in MB (Figure 4).
|
||||
|
||||
![free][11]
|
||||
|
||||
Figure 4: The output of the free command in a more human-readable form.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
Of course, if your system is even remotely modern, you’ll want to use the -g option (gigabytes), as in free -g.
|
||||
|
||||
If you need memory totals, you can add the t option like so: free -mt. This will simply total the amount of memory in columns (Figure 5).
|
||||
|
||||
![total][13]
|
||||
|
||||
Figure 5: Having free total your memory columns for you.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
### vmstat
|
||||
|
||||
Another very handy tool to have at your disposal is vmstat. This particular command is a one-trick pony that reports virtual memory statistics. The vmstat command will report stats on:
|
||||
|
||||
* Processes
|
||||
|
||||
* Memory
|
||||
|
||||
* Paging
|
||||
|
||||
* Block IO
|
||||
|
||||
* Traps
|
||||
|
||||
* Disks
|
||||
|
||||
* CPU
|
||||
|
||||
|
||||
|
||||
|
||||
The best way to issue vmstat is by using the -s switch, like vmstat -s. This will report your stats in a single column (which is so much easier to read than the default report). The vmstat command will give you more information than you need (Figure 6), but more is always better (in such cases).
|
||||
|
||||
![vmstat][15]
|
||||
|
||||
Figure 6: Using the vmstat command to check memory usage.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
### dmidecode
|
||||
|
||||
What if you want to find out detailed information about your installed system RAM? For that, you could use the dmidecode command. This particular tool is the DMI table decoder, which dumps a system’s DMI table contents into a human-readable format. If you’re unsure as to what the DMI table is, it’s a means to describe what a system is made of (as well as possible evolutions for a system).
|
||||
|
||||
To run the dmidecode command, you do need sudo privileges. So issue the command sudo dmidecode -t 17. The output of the command (Figure 7) can be lengthy, as it displays information for all memory-type devices. So if you don’t have the ability to scroll, you might want to send the output of that command to a file, like so: sudo dmidecode -t 17 > dmi_infoI, or pipe it to the less command, as in sudo dmidecode | less.
|
||||
|
||||
![dmidecode][17]
|
||||
|
||||
Figure 7: The output of the dmidecode command.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
### /proc/meminfo
|
||||
|
||||
You might be asking yourself, “Where do these commands get this information from?”. In some cases, they get it from the /proc/meminfo file. Guess what? You can read that file directly with the command less /proc/meminfo. By using the less command, you can scroll up and down through that lengthy output to find exactly what you need (Figure 8).
|
||||
|
||||
![/proc/meminfo][19]
|
||||
|
||||
Figure 8: The output of the less /proc/meminfo command.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
One thing you should know about /proc/meminfo: This is not a real file. Instead /pro/meminfo is a virtual file that contains real-time, dynamic information about the system. In particular, you’ll want to check the values for:
|
||||
|
||||
* MemTotal
|
||||
|
||||
* MemFree
|
||||
|
||||
* MemAvailable
|
||||
|
||||
* Buffers
|
||||
|
||||
* Cached
|
||||
|
||||
* SwapCached
|
||||
|
||||
* SwapTotal
|
||||
|
||||
* SwapFree
|
||||
|
||||
|
||||
|
||||
|
||||
If you want to get fancy with /proc/meminfo you can use it in conjunction with the egrep command like so: egrep --color 'Mem|Cache|Swap' /proc/meminfo. This will produce an easy to read listing of all entries that contain Mem, Cache, and Swap ... with a splash of color (Figure 9).
|
||||
|
||||
![/proc/meminfo][21]
|
||||
|
||||
Figure 9: Making /proc/meminfo easier to read.
|
||||
|
||||
[Used with permission][4]
|
||||
|
||||
### Keep learning
|
||||
|
||||
One of the first things you should do is read the manual pages for each of these commands (so man top, man free, man vmstat, man dmidecode). Starting with the man pages for commands is always a great way to learn so much more about how a tool works on Linux.
|
||||
|
||||
Learn more about Linux through the free ["Introduction to Linux" ][22]course from The Linux Foundation and edX.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/learn/5-commands-checking-memory-usage-linux
|
||||
|
||||
作者:[Jack Wallen][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/jlwallen
|
||||
[1]:https://www.ubuntu.com/download/server
|
||||
[2]:/files/images/memory1jpg
|
||||
[3]:https://www.linux.com/sites/lcom/files/styles/rendered_file/public/memory_1.jpg?itok=fhhhUL_l (top)
|
||||
[4]:/licenses/category/used-permission
|
||||
[5]:https://system76.com/desktops/leopard
|
||||
[6]:/files/images/memory2jpg
|
||||
[7]:https://www.linux.com/sites/lcom/files/styles/rendered_file/public/memory_2.jpg?itok=zuVkQfvv (top)
|
||||
[8]:/files/images/memory3jpg
|
||||
[9]:https://www.linux.com/sites/lcom/files/styles/rendered_file/public/memory_3.jpg?itok=rvuQp3t0 (free)
|
||||
[10]:/files/images/memory4jpg
|
||||
[11]:https://www.linux.com/sites/lcom/files/styles/rendered_file/public/memory_4.jpg?itok=K_luLLPt (free)
|
||||
[12]:/files/images/memory5jpg
|
||||
[13]:https://www.linux.com/sites/lcom/files/styles/rendered_file/public/memory_5.jpg?itok=q50atcsX (total)
|
||||
[14]:/files/images/memory6jpg
|
||||
[15]:https://www.linux.com/sites/lcom/files/styles/rendered_file/public/memory_6.jpg?itok=bwFnUVmy (vmstat)
|
||||
[16]:/files/images/memory7jpg
|
||||
[17]:https://www.linux.com/sites/lcom/files/styles/rendered_file/public/memory_7.jpg?itok=UNHIT_P6 (dmidecode)
|
||||
[18]:/files/images/memory8jpg
|
||||
[19]:https://www.linux.com/sites/lcom/files/styles/rendered_file/public/memory_8.jpg?itok=t87jvmJJ (/proc/meminfo)
|
||||
[20]:/files/images/memory9jpg
|
||||
[21]:https://www.linux.com/sites/lcom/files/styles/rendered_file/public/memory_9.jpg?itok=t-iSMEKq (/proc/meminfo)
|
||||
[22]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||
57
sources/tech/20180615 BLUI- An easy way to create game UI.md
Normal file
57
sources/tech/20180615 BLUI- An easy way to create game UI.md
Normal file
@ -0,0 +1,57 @@
|
||||
BLUI: An easy way to create game UI
|
||||
======
|
||||
|
||||

|
||||
|
||||
Game development engines have become increasingly accessible in the last few years. Engines like Unity, which has always been free to use, and Unreal, which recently switched from a subscription-based service to a free service, allow independent developers access to the same industry-standard tools used by AAA publishers. While neither of these engines is open source, each has enabled the growth of open source ecosystems around it.
|
||||
|
||||
Within these engines are plugins that allow developers to enhance the base capabilities of the engine by adding specific applications. These apps can range from simple asset packs to more complicated things, like artificial intelligence (AI) integrations. These plugins widely vary across creators. Some are offered by the engine development studios and others by individuals. Many of the latter are open source plugins.
|
||||
|
||||
### What is BLUI?
|
||||
|
||||
As part of an indie game development studio, I've experienced the perks of using open source plugins on proprietary game engines. One open source plugin, [BLUI][1] by Aaron Shea, has been instrumental in our team's development process. It allows us to create user interface (UI) components using web-based programming like HTML/CSS and JavaScript. We chose to use this open source plugin, even though Unreal Engine (our engine of choice) has a built-in UI editor that achieves a similar purpose. We chose to use open source alternatives for three main reasons: their accessibility, their ease of implementation, and the active, supportive online communities that accompany open source programs.
|
||||
|
||||
In Unreal Engine's earliest versions, the only means we had of creating UI in the game was either through the engine's native UI integration, by using Autodesk's Scaleform application, or via a few select subscription-based Unreal integrations spread throughout the Unreal community. In all those cases, the solutions were either incapable of providing a competitive UI solution for indie developers, too expensive for small teams, or exclusively for large-scale teams and AAA developers.
|
||||
|
||||
After commercial products and Unreal's native integration failed us, we looked to the indie community for solutions. There we discovered BLUI. It not only integrates with Unreal Engine seamlessly but also maintains a robust and active community that frequently pushes updates and ensures the documentation is easily accessible for indie developers. BLUI gives developers the ability to import HTML files into the Unreal Engine and program them even further while inside the program. This allows UI created through web languages to integrate with the game's code, assets, and other elements with the full power of HTML, CSS, JavaScript, and other web languages. It also provides full support for the open source [Chromium Embedded Framework][2].
|
||||
|
||||
### Installing and using BLUI
|
||||
|
||||
The basic process for using BLUI involves first creating the UI via HTML. Developers may use any tool at their disposal to achieve this, including bootstrapped JavaScript code, external APIs, or any database code. Once this HTML page is ready, you can install the plugin the same way you would install any Unreal plugin and load or create a project. Once the project is loaded, you can place a BLUI function anywhere within an Unreal UI blueprint or hardcoded via C++. Developers can call functions from within their HTML page or change variables easily using BLUI's internal functions.
|
||||
|
||||
![Integrating BLUI into Unreal Engine 4 blueprints][4]
|
||||
|
||||
Integrating BLUI into Unreal Engine 4 blueprints.
|
||||
|
||||
In our current project, we use BLUI to sync UI elements with the in-game soundtrack to provide visual feedback to the rhythm aspects of the game mechanics. It's easy to integrate custom engine programming with the BLUI plugin.
|
||||
|
||||
![Using BLUI to sync UI elements with the soundtrack.][6]
|
||||
|
||||
Using BLUI to sync UI elements with the soundtrack.
|
||||
|
||||
Implementing BLUI into Unreal Engine 4 is a trivial process thanks to the [documentation][7] on the BLUI GitHub page. There is also [a forum][8] populated with supportive Unreal Engine developers eager to both ask and answer questions regarding the plugin and any issues that appear when implementing the tool.
|
||||
|
||||
### Open source advantages
|
||||
|
||||
Open source plugins enable expanded creativity within the confines of proprietary game engines. They continue to lower the barrier of entry into game development and can produce in-game mechanics and assets no one has seen before. As access to proprietary game development engines continues to grow, the open source plugin community will become more important. Rising creativity will inevitably outpace proprietary software, and open source will be there to fill the gaps and facilitate the development of truly unique games. And that novelty is exactly what makes indie games so great!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/6/blui-game-development-plugin
|
||||
|
||||
作者:[Uwana lkaiddi][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/uwikaiddi
|
||||
[1]:https://github.com/AaronShea/BLUI
|
||||
[2]:https://bitbucket.org/chromiumembedded/cef
|
||||
[3]:/file/400616
|
||||
[4]:https://opensource.com/sites/default/files/uploads/blui_gaming_plugin-integratingblui.png (Integrating BLUI into Unreal Engine 4 blueprints)
|
||||
[5]:/file/400621
|
||||
[6]:https://opensource.com/sites/default/files/uploads/blui_gaming_plugin-syncui.png (Using BLUI to sync UI elements with the soundtrack.)
|
||||
[7]:https://github.com/AaronShea/BLUI/wiki
|
||||
[8]:https://forums.unrealengine.com/community/released-projects/29036-blui-open-source-html5-js-css-hud-ui
|
||||
File diff suppressed because it is too large
Load Diff
@ -0,0 +1,186 @@
|
||||
How To Rename Multiple Files At Once In Linux
|
||||
======
|
||||
|
||||

|
||||
|
||||
As you may already know, we use **mv** command to rename or move files and directories in Unix-like operating systems. But, the mv command won’t support renaming multiple files at once. Worry not. In this tutorial, we are going to learn to rename multiple files at once using **“mmv”** command in Linux. This command is used to move, copy, append and rename files in bulk using standard wildcards in Unix-like operating systems.
|
||||
|
||||
### Rename Multiple Files At Once In Linux
|
||||
|
||||
The mmv utility is available in the default repositories of Debian-based systems. To install it on Debian, Ubuntu, Linux Mint, run the following command:
|
||||
```
|
||||
$ sudo apt-get install mmv
|
||||
|
||||
```
|
||||
|
||||
Let us say, you have the following files in your current directory.
|
||||
```
|
||||
$ ls
|
||||
a1.txt a2.txt a3.txt
|
||||
|
||||
```
|
||||
|
||||
Now you want to rename all files that starts with letter “a” to “b”. Of course, you can do this manually in few seconds. But just think if you have hundreds of files and want to rename them? It is quite time consuming process. Here is where **mmv** command comes in help.
|
||||
|
||||
To rename all files starting with letter “a” to “b”, simply run:
|
||||
```
|
||||
$ mmv a\* b\#1
|
||||
|
||||
```
|
||||
|
||||
Let us check if the files have been renamed or not.
|
||||
```
|
||||
$ ls
|
||||
b1.txt b2.txt b3.txt
|
||||
|
||||
```
|
||||
|
||||
As you can see, all files starts with letter “a” (i.e a1.txt, a2.txt, a3.txt) are renamed to b1.txt, b2.txt, b3.txt.
|
||||
|
||||
**Explanation**
|
||||
|
||||
In the above example, the first parameter (a\\*) is the ‘from’ pattern and the second parameter is ‘to’ pattern ( b\\#1 ). As per the above example, mmv will look for any filenames staring with letter ‘a’ and rename the matched files according to second parameter i.e ‘to’ pattern. We use wildcards, such as ‘*’, ‘?’ and ‘[]‘, to match one or more arbitrary characters. Please be mindful that you must escape the wildcard characters, otherwise they will be expanded by the shell and mmv won’t understand them.
|
||||
|
||||
The ‘#1′ in the ‘to’ pattern is a wildcard index. It matches the first wildcard found in the ‘from’ pattern. A ‘#2′ in the ‘to’ pattern would match the second wildcard and so on. In our example, we have only one wildcard (the asterisk), so we write a #1. And, the hash sign should be escaped as well. Also, you can enclose the patterns with quotes too.
|
||||
|
||||
You can even rename all files with a certain extension to a different extension. For example, to rename all **.txt** files to **.doc** file format in the current directory, simply run:
|
||||
```
|
||||
$ mmv \*.txt \#1.doc
|
||||
|
||||
```
|
||||
|
||||
Here is an another example. Let us say you have the following files.
|
||||
```
|
||||
$ ls
|
||||
abcd1.txt abcd2.txt abcd3.txt
|
||||
|
||||
```
|
||||
|
||||
You want to replace the the first occurrence of **abc** with **xyz** in all files in the current directory. How would you do?
|
||||
|
||||
Simple.
|
||||
```
|
||||
$ mmv '*abc*' '#1xyz#2'
|
||||
|
||||
```
|
||||
|
||||
Please note that in the above example, I have enclosed the patterns in single quotes.
|
||||
|
||||
Let us check if “abc” is actually replaced with “xyz” or not.
|
||||
```
|
||||
$ ls
|
||||
xyzd1.txt xyzd2.txt xyzd3.txt
|
||||
|
||||
```
|
||||
|
||||
See? The files **abcd1.txt** , **abcd2.txt** , and **abcd3.txt** have been renamed to **xyzd1.txt** , **xyzd2.txt** , and **xyzd3.txt**.
|
||||
|
||||
Another notable feature of mmv command is you can just print output instead of renaming the files using **-n** option like below.
|
||||
```
|
||||
$ mmv -n a\* b\#1
|
||||
a1.txt -> b1.txt
|
||||
a2.txt -> b2.txt
|
||||
a3.txt -> b3.txt
|
||||
|
||||
```
|
||||
|
||||
This way you can simply verify what mmv command would actually do before renaming the files.
|
||||
|
||||
For more details, refer man pages.
|
||||
```
|
||||
$ man mmv
|
||||
|
||||
```
|
||||
|
||||
**Update:**
|
||||
|
||||
The **Thunar file manager** has built-in **bulk rename** option by default. If you’re using thunar, it much easier to rename files than using mmv command.
|
||||
|
||||
Thunar is available in the default repositories of most Linux distributions.
|
||||
|
||||
To install it on Arch-based systems, run:
|
||||
```
|
||||
$ sudo pacman -S thunar
|
||||
|
||||
```
|
||||
|
||||
On RHEL, CentOS:
|
||||
```
|
||||
$ sudo yum install thunar
|
||||
|
||||
```
|
||||
|
||||
On Fedora:
|
||||
```
|
||||
$ sudo dnf install thunar
|
||||
|
||||
```
|
||||
|
||||
On openSUSE:
|
||||
```
|
||||
$ sudo zypper install thunar
|
||||
|
||||
```
|
||||
|
||||
On Debian, Ubuntu, Linux Mint:
|
||||
```
|
||||
$ sudo apt-get install thunar
|
||||
|
||||
```
|
||||
|
||||
Once installed, you can launch bulk rename utility from menu or from the application launcher. To launch it from Terminal, use the following command:
|
||||
```
|
||||
$ thunar -B
|
||||
|
||||
```
|
||||
|
||||
This is how bulk rename looks like.
|
||||
|
||||
[![][1]][2]
|
||||
|
||||
Click the plus sign and choose the list of files you want to rename. Bulk rename can rename the name of the files, the suffix of the files or both the name and the suffix of the files. Thunar currently supports the following Bulk Renamers:
|
||||
|
||||
* Insert Date or Time
|
||||
|
||||
* Insert or Overwrite
|
||||
|
||||
* Numbering
|
||||
|
||||
* Remove Characters
|
||||
|
||||
* Search & Replace
|
||||
|
||||
* Uppercase / Lowercase
|
||||
|
||||
|
||||
|
||||
|
||||
When you select one of these criteria from the picklist, you will see a preview of your changes in the New Name column, as shown in the below screenshot.
|
||||
|
||||
![][3]
|
||||
|
||||
Once you choose the criteria, click on **Rename Files** option to rename the files.
|
||||
|
||||
You can also open bulk renamer from within Thunar by selecting two or more files. After choosing the files, press F2 or right click and choose **Rename**.
|
||||
|
||||
And, that’s all for now. Hope this was useful. More good stuffs to come. Stay tuned!
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/how-to-rename-multiple-files-at-once-in-linux/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.ostechnix.com/author/sk/
|
||||
[1]:data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[2]:http://www.ostechnix.com/wp-content/uploads/2018/06/bulk-rename.png
|
||||
[3]:http://www.ostechnix.com/wp-content/uploads/2018/06/bulk-rename-1.png
|
||||
@ -0,0 +1,56 @@
|
||||
How to Mount and Use an exFAT Drive on Ubuntu Linux
|
||||
======
|
||||
**Brief: This quick tutorial shows you how to enable exFAT file system support on Ubuntu and other Ubuntu-based Linux distributions. This way you won’t see any error while mounting exFAT drives on your system.**
|
||||
|
||||
### Problem mounting exFAT disk on Ubuntu
|
||||
|
||||
The other day, I tried to use an external USB key formatted in exFAT format that contained a file of around 10 GB in size. As soon as I plugged the USB key, my Ubuntu 16.04 throw an error complaining that it **cannot mount unknown filesystem type ‘exfat’**.
|
||||
|
||||
![Fix exfat drive mount error on Ubuntu Linux][1]
|
||||
|
||||
The exact error message was this:
|
||||
**Error mounting /dev/sdb1 at /media/abhishek/SHADI DATA: Command-line `mount -t “exfat” -o “uhelper=udisks2,nodev,nosuid,uid=1001,gid=1001,iocharset=utf8,namecase=0,errors=remount-ro,umask=0077” “/dev/sdb1” “/media/abhishek/SHADI DATA”‘ exited with non-zero exit status 32: mount: unknown filesystem type ‘exfat’**
|
||||
|
||||
### The reason behind this exFAT mount error
|
||||
|
||||
Microsoft’s favorite [FAT file system][2] is limited to files up to 4GB in size. You cannot transfer a file bigger than 4 GB in size to a FAT drive. To overcome the limitations of the FAT filesystem, Microsoft introduced [exFAT][3] file system in 2006.
|
||||
|
||||
As most of the Microsoft related stuff are proprietary, exFAT file format is no exception to that. Ubuntu and many other Linux distributions don’t provide the proprietary exFAT file support by default. This is the reason why you see the mount error with exFAT files.
|
||||
|
||||
### How to mount exFAT drive on Ubuntu Linux
|
||||
|
||||
![Fix exFAT mount error on Ubuntu Linux][4]
|
||||
|
||||
The solution to this problem is simple. All you need to do is to enable exFAT support.
|
||||
|
||||
I am going to show the commands for Ubuntu but this should be applicable to other Ubuntu-based distributions such as [Linux Mint][5], elementary OS etc.
|
||||
|
||||
Open a terminal (Ctrl+Alt+T shortcut in Ubuntu) and use the following command:
|
||||
```
|
||||
sudo apt install exfat-fuse exfat-utils
|
||||
|
||||
```
|
||||
|
||||
Once you have installed these packages, go to file manager and click on the USB disk again to mount it. There is no need to replug the USB. It should be mounted straightaway.
|
||||
|
||||
#### Did it help you?
|
||||
|
||||
I hope this quick tip helped you to fix the exFAT mount error for your Linux distribution. If you have any further questions, suggestions or a simple thanks, please use the comment box below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/mount-exfat/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[1]:https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/06/exfat-mount-error-linux.jpeg
|
||||
[2]:http://www.ntfs.com/fat-systems.htm
|
||||
[3]:https://en.wikipedia.org/wiki/ExFAT
|
||||
[4]:https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/06/exfat-mount-error-featured-800x450.jpeg
|
||||
[5]:https://linuxmint.com/
|
||||
122
sources/tech/20180618 5 open source alternatives to Dropbox.md
Normal file
122
sources/tech/20180618 5 open source alternatives to Dropbox.md
Normal file
@ -0,0 +1,122 @@
|
||||
5 open source alternatives to Dropbox
|
||||
======
|
||||
|
||||

|
||||
|
||||
Dropbox is the 800-pound gorilla of filesharing applications. Even though it's a massively popular tool, you may choose to use an alternative.
|
||||
|
||||
Maybe that's because you're dedicated to the [open source way][1] for all the good reasons, including security and freedom, or possibly you've been spooked by data breaches. Or perhaps the pricing plan doesn't work out in your favor for the amount of storage you actually need.
|
||||
|
||||
Fortunately, there are a variety of open source filesharing applications out there that give you more storage, security, and control over your data at a far lower price than Dropbox charges. How much lower? Try free, if you're a bit tech savvy and have a Linux server to use.
|
||||
|
||||
Here are five of the best open source alternatives to Dropbox, plus a few others that you might want to consider.
|
||||
|
||||
### ownCloud
|
||||
|
||||
|
||||
|
||||
[ownCloud][2], launched in 2010, is the oldest application on this list, but don't let that fool you: It's still very popular (with over 1.5 million users, according to the company) and actively maintained by a community of 1,100 contributors, with updates released regularly.
|
||||
|
||||
Its primary features—file and folding sharing, document collaboration—are similar to Dropbox's. Its primary difference (aside from its [open source license][3]) is that your files are hosted on your private Linux server or cloud, giving users complete control over your data. (Self-hosting is a common thread among the apps on this list.)
|
||||
|
||||
With ownCloud, you can sync and access files through clients for Linux, MacOS, or Windows computers or mobile apps for Android and iOS devices, and provide password-protected links to others for collaboration or file upload/download. Data transfers are secured by end-to-end encryption (E2EE) and SSL encryption. You can also expand its functionality with a wide variety of third-party apps available in its [marketplace][4], and there is also a paid, commercially licensed enterprise edition.
|
||||
|
||||
ownCloud offers comprehensive [documentation][5], including an installation guide and manuals for users, admins, and developers, and you can access its [source code][6] in its GitHub repository.
|
||||
|
||||
### NextCloud
|
||||
|
||||
|
||||
|
||||
[NextCloud][7] spun out of ownCloud in 2016 and shares much of the same functionality. Nextcloud [touts][8] its high security and regulatory compliance as a distinguishing feature. It has HIPAA (healthcare) and GDPR (privacy) compliance features and offers extensive data-policy enforcement, encryption, user management, and auditing capabilities. It also encrypts data during transfer and at rest and integrates with mobile device management and authentication mechanisms (including LDAP/AD, single-sign-on, two-factor authentication, etc.).
|
||||
|
||||
Like the other solutions on this list, NextCloud is self-hosted, but if you don't want to roll your own NextCloud server on Linux, the company partners with several [providers][9] for setup and hosting and sells servers, appliances, and support. A [marketplace][10] offers numerous apps to extend its features.
|
||||
|
||||
NextCloud's [documentation][11] page offers thorough information for users, admins, and developers as well as links to its forums, IRC channel, and social media pages for community-based support. If you'd like to contribute, access its source code, report a bug, check out its (AGPLv3) license, or just learn more, visit the project's [GitHub repository][12].
|
||||
|
||||
### Seafile
|
||||
|
||||
|
||||
|
||||
[Seafile][13] may not have the bells and whistles (or app ecosystem) of ownCloud or Nextcloud, but it gets the job done. Essentially, it acts as a virtual drive on your Linux server to extend your desktop storage and allow you to share files selectively with password protection and various levels of permission (i.e., read-only or read/write).
|
||||
|
||||
Its collaboration features include per-folder access control, password-protected download links, and Git-like version control and retention. Files are secured with two-factor authentication, file encryption, and AD/LDAP integration, and they're accessible from Windows, MacOS, Linux, iOS, or Android devices.
|
||||
|
||||
For more information, visit Seafile's [GitHub repository][14], [server manual][15], [wiki][16], and [forums][17]. Note that Seafile's community edition is licensed under [GPLv2][18], but its professional edition is not open source.
|
||||
|
||||
### OnionShare
|
||||
|
||||
|
||||
|
||||
[OnionShare][19] is a cool app that does one thing: It allows you to share individual files or folders securely and, if you want, anonymously. There's no server to set up or maintain—all you need to do is [download and install][20] the app on MacOS, Windows, or Linux. Files are always hosted on your own computer; when you share a file, OnionShare creates a web server, makes it accessible as a Tor Onion service, and generates an unguessable .onion URL that allows the recipient to access the file via [Tor browser][21].
|
||||
|
||||
You can set limits on your fileshare, such as limiting the number of times it can be downloaded or using an auto-stop timer, which sets a strict expiration date/time after which the file is inaccessible (even if it hasn't been accessed yet).
|
||||
|
||||
OnionShare is licensed under [GPLv3][22]; for more information, check out its GitHub [repository][22], which also includes [documentation][23] that covers the features in this easy-to-use filesharing application.
|
||||
|
||||
### Pydio Cells
|
||||
|
||||
|
||||
|
||||
[Pydio Cells][24], which achieved stability in May 2018, is a complete overhaul of the Pydio filesharing application's core server code. Due to limitations with Pydio's PHP-based backend, the developers decided to rewrite the backend in the Go server language with a microservices architecture. (The frontend is still based on PHP.)
|
||||
|
||||
Pydio Cells includes the usual filesharing and version control features, as well as in-app messaging, mobile apps (Android and iOS), and a social network-style approach to collaboration. Security includes OpenID Connect-based authentication, encryption at rest, security policies, and more. Advanced features are included in the enterprise distribution, but there's plenty of power for most small and midsize businesses and home users in the community (or "Home") version.
|
||||
|
||||
You can [download][25] Pydio Cells for Linux and MacOS. For more information, check out the [documentation FAQ][26], [source code][27] repository, and [AGPLv3 license][28].
|
||||
|
||||
### Others to consider
|
||||
|
||||
If these choices don't meet your needs, you may want to consider these open source filesharing-type applications.
|
||||
|
||||
* If your main goal is to sync files between devices, rather than to share files, check out [Syncthing][29]).
|
||||
* If you're a Git fan and don't need a mobile app, you might appreciate [SparkleShare][30].
|
||||
* If you primarily want a place to aggregate all your personal data, take a look at [Cozy][31].
|
||||
* And, if you're looking for a lightweight or dedicated filesharing tool, peruse [Scott Nesbitt's review][32] of some lesser-known options.
|
||||
|
||||
|
||||
|
||||
What is your favorite open source filesharing application? Let us know in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/alternatives/dropbox
|
||||
|
||||
作者:[OPensource.com][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com
|
||||
[1]:https://opensource.com/open-source-way
|
||||
[2]:https://owncloud.org/
|
||||
[3]:https://www.gnu.org/licenses/agpl-3.0.html
|
||||
[4]:https://marketplace.owncloud.com/
|
||||
[5]:https://doc.owncloud.com/
|
||||
[6]:https://github.com/owncloud
|
||||
[7]:https://nextcloud.com/
|
||||
[8]:https://nextcloud.com/secure/
|
||||
[9]:https://nextcloud.com/providers/
|
||||
[10]:https://apps.nextcloud.com/
|
||||
[11]:https://nextcloud.com/support/
|
||||
[12]:https://github.com/nextcloud
|
||||
[13]:https://www.seafile.com/en/home/
|
||||
[14]:https://github.com/haiwen/seafile
|
||||
[15]:https://manual.seafile.com/
|
||||
[16]:https://seacloud.cc/group/3/wiki/
|
||||
[17]:https://forum.seafile.com/
|
||||
[18]:https://github.com/haiwen/seafile/blob/master/LICENSE.txt
|
||||
[19]:https://onionshare.org/
|
||||
[20]:https://onionshare.org/#downloads
|
||||
[21]:https://www.torproject.org/
|
||||
[22]:https://github.com/micahflee/onionshare/blob/develop/LICENSE
|
||||
[23]:https://github.com/micahflee/onionshare/wiki
|
||||
[24]:https://pydio.com/en
|
||||
[25]:https://pydio.com/download/
|
||||
[26]:https://pydio.com/en/docs/faq
|
||||
[27]:https://github.com/pydio/cells
|
||||
[28]:https://github.com/pydio/pydio-core/blob/develop/LICENSE
|
||||
[29]:https://syncthing.net/
|
||||
[30]:http://www.sparkleshare.org/
|
||||
[31]:https://cozy.io/en/
|
||||
[32]:https://opensource.com/article/17/3/file-sharing-tools
|
||||
@ -1,302 +0,0 @@
|
||||
Oracle Linux 系统如何去注册使用坚不可摧 Linux 网络(ULN)
|
||||
======
|
||||
大多数人都知道 RHEL 的订阅 ,但是知道 Oracle 订阅及细节的人却很少。
|
||||
|
||||
甚至我也不知道关于它的信息,我是最近才了解了有关它的信息,想将这些内容共享给其他人。因此写了这篇文章,它将指导你去注册 Oracle Linux 系统去使用坚不可摧 Linux 网络(ULN) 。
|
||||
|
||||
这将允许你去注册系统以获得软件更新和其它的 ASAP 补丁。
|
||||
|
||||
### 什么是坚不可摧 Linux 网络
|
||||
|
||||
ULN 代表坚不可摧 Linux 网络,它是由 Oracle 所拥有的。如果你去 Oracle OS 支持中去激活这个订阅,你就可以注册你的系统去使用坚不可摧 Linux 网络(ULN)。
|
||||
|
||||
ULN 为 Oracle Linux 和 Oracle VM 提供软件补丁、更新、以及修复,此外还有在 yum、Ksplice、以及支持策略上的信息。你也可以通过它来下载原始发行版中没有包含的有用的安装包。
|
||||
|
||||
ULN 的告警提示工具周期性地使用 ULN 去检查,当有更新的时候它给你发送警报信息。
|
||||
|
||||
如果你想在 yum 上使用 ULN 仓库去管理你的系统,需要确保你的系统已经注册到 ULN 上,并且订阅了一个或多个 ULN 频道。当你注册一个系统使用 ULN,它将基于你的系统架构和操作系统去自动选择频道中最新的版本。
|
||||
|
||||
### 如何注册为一个 ULN 用户
|
||||
|
||||
去注册为一个 ULN 用户,需要你有一个 Oracle Linux 支持或者 Oracle VM 支持的有效客户支持代码(CSI)。
|
||||
|
||||
请按以下步骤去注册为一个 ULN 用户。
|
||||
|
||||
请访问 [linux.oracle.com][1]
|
||||
![][3]
|
||||
|
||||
如果你已经有一个 SSO 帐户,请点击 “Sign On”。
|
||||
![][4]
|
||||
|
||||
如果你没有帐户,点击 “Create New Single Signon Account” 然后按屏幕上的要求去创建一个帐户。
|
||||
![][5]
|
||||
|
||||
验证你的电子邮件地址以完成帐户设置。
|
||||
|
||||
使用你的 SSO 帐户的用户名和密码去登入。在 “Create New ULN User” 页面上,输入你的 CSI 然后点击 “Create New User”。
|
||||
![][6]
|
||||
|
||||
**注意:**
|
||||
|
||||
* 如果当前没有分配管理员去管理 CSI,将会提示你去点击确认让你成为 CSI 管理员。
|
||||
* 如果你的用户名已经在系统上存在,你将被提示通过点击坚不可摧 Linux 网络的链接去操作 ULN。
|
||||
|
||||
|
||||
|
||||
### 如何注册 Oracle Linux 6/7 系统使用 ULN
|
||||
|
||||
只需要运行下列的命令,并按随后的指令提示去注册系统。
|
||||
```
|
||||
# uln_register
|
||||
|
||||
```
|
||||
|
||||
确保你的系统有一个活动的因特网连接。同时准备好你的 Oracle 单点登陆帐户(SSO)的用户名和密码,然后点击 `Next`。
|
||||
```
|
||||
Copyright © 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
ââââââââââââââââââââââââââââââââââââââââââââââââââââ⤠Setting up software updates âââââââââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
â This assistant will guide you through connecting your system to Unbreakable Linux Network (ULN) to receive software updates, â
|
||||
â including security updates, to keep your system supported and compliant. You will need the following at this time: â
|
||||
â â
|
||||
â * A network connection â
|
||||
â * Your Oracle Single Sign-On Login & password â
|
||||
â â
|
||||
â â
|
||||
â â
|
||||
â â
|
||||
â â
|
||||
â â
|
||||
â â
|
||||
â â
|
||||
â ââââââââââââââââââââââââââââââââââââ ââââââââ ââââââââââ â
|
||||
â â Why Should I Connect to ULN? ... â â Next â â Cancel â â
|
||||
â ââââââââââââââââââââââââââââââââââââ ââââââââ ââââââââââ â
|
||||
â â
|
||||
ââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
|
||||
```
|
||||
|
||||
输入你的 ULN 登陆信息,然后点击 `Next`。
|
||||
```
|
||||
Copyright © 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
ââââââââââââââââââââââââââââââââââââââââââââââââââââ⤠Setting up software updates âââââââââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
â â
|
||||
â Please enter your login information for Unbreakable Linux Network (http://linux.oracle.com/): â
|
||||
â â
|
||||
â â
|
||||
â Oracle Single Sign-On Login: [email protected] â
|
||||
â Password: **********__________ â
|
||||
â CSI: 12345678____________ â
|
||||
â Tip: Forgot your login or password? Visit: http://www.oracle.com/corporate/contact/getaccthelp.html â
|
||||
â â
|
||||
â ââââââââ ââââââââ ââââââââââ â
|
||||
â â Next â â Back â â Cancel â â
|
||||
â ââââââââ ââââââââ ââââââââââ â
|
||||
â â
|
||||
â â
|
||||
ââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
|
||||
```
|
||||
|
||||
注册一个系统概要 – 硬件信息,然后点击 `Next`。
|
||||
```
|
||||
Copyright © 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
âââââââââââââââââââââââââââââââââââââââââââââ⤠Register a System Profile - Hardware ââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
â â
|
||||
â A Profile Name is a descriptive name that you choose to identify this â
|
||||
â System Profile on the Unbreakable Linux Network web pages. Optionally, â
|
||||
â include a computer serial or identification number. â
|
||||
â Profile name: 2g-oracle-sys___________________________ â
|
||||
â â
|
||||
â [*] Include the following information about hardware and network: â
|
||||
â Press to deselect the option. â
|
||||
â â
|
||||
â Version: 6 CPU model: Intel(R) Xeon(R) CPU E5-5650 0 @ 2.00GHz â
|
||||
â Hostname: 2g-oracle-sys â
|
||||
â CPU speed: 1199 MHz IP Address: 192.168.1.101 Memory: â
|
||||
â â
|
||||
â Additional hardware information including PCI devices, disk sizes and mount points will be included in the profile. â
|
||||
â â
|
||||
â ââââââââ ââââââââ ââââââââââ â
|
||||
â â Next â â Back â â Cancel â â
|
||||
â ââââââââ ââââââââ ââââââââââ â
|
||||
â â
|
||||
â â
|
||||
âââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
|
||||
```
|
||||
|
||||
注册一个系统概要 – 包配置,然后点击 `Next`。
|
||||
```
|
||||
Copyright © 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
âââââââââââââââââââââââââââââââââââââââââââââ⤠Register a System Profile - Packages âââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
â â
|
||||
â RPM information is important to determine what updated software packages are relevant to this system. â
|
||||
â â
|
||||
â [*] Include RPM packages installed on this system in my System Profile â
|
||||
â â
|
||||
â You may deselect individual packages by unchecking them below. â
|
||||
â [*] ConsoleKit-0.4.1-6.el6 â â
|
||||
â [*] ConsoleKit-libs-0.4.1-6.el6 â â
|
||||
â [*] ConsoleKit-x11-0.4.1-6.el6 â â
|
||||
â [*] DeviceKit-power-014-3.el6 â â
|
||||
â [*] GConf2-2.28.0-7.el6 â â
|
||||
â [*] GConf2-2.28.0-7.el6 â â
|
||||
â [*] GConf2-devel-2.28.0-7.el6 â â
|
||||
â [*] GConf2-gtk-2.28.0-7.el6 â â
|
||||
â [*] MAKEDEV-3.24-6.el6 â â
|
||||
â [*] MySQL-python-1.2.3-0.3.c1.1.el6 â â
|
||||
â [*] NessusAgent-7.0.3-es6 â â
|
||||
â [*] ORBit2-2.14.17-6.el6_8 â â
|
||||
â [*] ORBit2-2.14.17-6.el6_8 â â
|
||||
â [*] ORBit2-devel-2.14.17-6.el6_8 â â
|
||||
â [*] PackageKit-0.5.8-26.0.1.el6 â â
|
||||
â [*] PackageKit-device-rebind-0.5.8-26.0.1.el6 â â
|
||||
â [*] PackageKit-glib-0.5.8-26.0.1.el6 â â
|
||||
â â
|
||||
â ââââââââ ââââââââ ââââââââââ â
|
||||
â â Next â â Back â â Cancel â â
|
||||
â ââââââââ ââââââââ ââââââââââ â
|
||||
â â
|
||||
â â
|
||||
âââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
|
||||
```
|
||||
|
||||
按下 “Next” 去发送系统概要到 ULN。
|
||||
```
|
||||
Copyright © 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
âââââââââââââââââââââââââââââââââââ⤠Send Profile Information to Unbreakable Linux Network âââââââââââââââââââââââââââââââââââââ
|
||||
â â
|
||||
â We are finished collecting information for the System Profile. â
|
||||
â â
|
||||
â Press "Next" to send this System Profile to Unbreakable Linux Network. Click "Cancel" and no information will be sent. You â
|
||||
â can run the registration program later by typing `uln_register` at the command line. â
|
||||
â â
|
||||
â ââââââââ ââââââââ ââââââââââ â
|
||||
â â Next â â Back â â Cancel â â
|
||||
â ââââââââ ââââââââ ââââââââââ â
|
||||
â â
|
||||
â â
|
||||
ââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
|
||||
```
|
||||
|
||||
发送概要到 ULN 是如下的一个过程。
|
||||
```
|
||||
Copyright © 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
|
||||
|
||||
â⤠Sending Profile to Unbreakable Linux Network â
|
||||
â â
|
||||
â 75% â
|
||||
â â
|
||||
ââââââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
|
||||
```
|
||||
|
||||
ULN 注册做完后,重新回顾系统订阅的详细情况。如果一切正确,然后点击 `ok`。
|
||||
```
|
||||
Copyright © 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
ââââââââââââââââââââââââââââââââââââââââââââââââââ⤠Review system subscription details ââââââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
â â
|
||||
â â
|
||||
â Note: yum-rhn-plugin has been enabled. â
|
||||
â â
|
||||
â Please review the subscription details below: â
|
||||
â â
|
||||
â Software channel subscriptions: â
|
||||
â This system will receive updates from the following Unbreakable Linux Network software channels: â
|
||||
â Oracle Linux 6 Latest (x86_64) â
|
||||
â Unbreakable Enterprise Kernel Release 4 for Oracle Linux 6 (x86_64) â
|
||||
â â
|
||||
â Warning: If an installed product on this system is not listed above, you will not receive updates or support for that product. If â
|
||||
â you would like to receive updates for that product, please visit http://linux.oracle.com/ and subscribe this system to the â
|
||||
â appropriate software channels to get updates for that product. â
|
||||
â â
|
||||
â â
|
||||
â â
|
||||
â â
|
||||
â â
|
||||
â â
|
||||
â â
|
||||
â ââââââ â
|
||||
â â OK â â
|
||||
â ââââââ â
|
||||
â â
|
||||
â â
|
||||
ââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
|
||||
```
|
||||
|
||||
最后点击 `Finish` 完成注册。
|
||||
```
|
||||
Copyright © 2006--2010 Red Hat, Inc. All rights reserved.
|
||||
|
||||
|
||||
ââââââââââââââââââââââââââââââââââââââââââââââ⤠Finish setting up software updates âââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
â â
|
||||
â You may now run 'yum update' from this system's command line to get the latest software updates from Unbreakable Linux Network. â
|
||||
â You will need to run this periodically to get the latest updates. â
|
||||
â â
|
||||
â ââââââââââ â
|
||||
â â Finish â â
|
||||
â ââââââââââ â
|
||||
â â
|
||||
â â
|
||||
âââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââââ
|
||||
|
||||
```
|
||||
|
||||
ULN 注册已经成功,为了从 ULN 中得到仓库,运行如下的命令。
|
||||
```
|
||||
# yum repolist
|
||||
Loaded plugins: aliases, changelog, presto, refresh-packagekit, rhnplugin, security, tmprepo, ulninfo, verify, versionlock
|
||||
This system is receiving updates from ULN.
|
||||
ol6_x86_64_UEKR3_latest | 1.2 kB 00:00
|
||||
ol6_x86_64_UEKR3_latest/primary | 35 MB 00:14
|
||||
ol6_x86_64_UEKR3_latest 874/874
|
||||
repo id repo name status
|
||||
ol6_x86_64_UEKR3_latest Unbreakable Enterprise Kernel Release 3 for Oracle Linux 6 (x86_64) - Latest 874
|
||||
ol6_x86_64_latest Oracle Linux 6 Latest (x86_64) 40,092
|
||||
repolist: 40,966
|
||||
|
||||
```
|
||||
|
||||
另外,你也可以在 ULN 网站上查看到相同的信息。转到 `System` 标签页去查看已注册的系统列表。
|
||||
![][7]
|
||||
|
||||
去查看已经启用的仓库列表。转到 `System` 标签页,然后点击相应的系统。另外,你也能够看到系统勘误及可用更新。
|
||||
![][8]
|
||||
|
||||
去管理订阅的频道。转到 `System` 标签页,然后点击有关的 `system name`,最后点击 `Manage Subscriptions`。
|
||||
![][9]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/how-to-register-the-oracle-linux-system-with-the-unbreakable-linux-network-uln/
|
||||
|
||||
作者:[Vinoth Kumar][a]
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.2daygeek.com/author/vinoth/
|
||||
[1]:https://linux.oracle.com/register
|
||||
[2]:data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[3]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-1.png
|
||||
[4]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-3.png
|
||||
[5]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-2.png
|
||||
[6]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-4.png
|
||||
[7]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-5a.png
|
||||
[8]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-6a.png
|
||||
[9]:https://www.2daygeek.com/wp-content/uploads/2018/04/How-To-Register-The-Oracle-Linux-System-With-The-Unbreakable-Linux-Network-ULN-7a.png
|
||||
@ -0,0 +1,114 @@
|
||||
面向 Linux 和开源爱好者的书单(儿童版)
|
||||
======
|
||||
|
||||

|
||||
在工作之余,我听说不少技术专家透露出让他们自己的孩子学习更多关于 [Linux][1] 和 [开源][2]知识的意愿,他们中有的来自高管层,有的来自普通岗位。其中一些似乎时间比较充裕,伴随其孩子一步一步成长。另一些人可能没有充足的时间让他们的孩子看到为何 Linux 和 开源如此之酷。也许他们能抽出时间,但这不一定。在这个大世界中,有太多有趣、有价值的事物。
|
||||
|
||||
不论是哪种方式,如果你的或你认识的孩子愿意学习使用编程和硬件,实现游戏或机器人之类东西,那么这份书单很适合你。
|
||||
|
||||
### 面向儿童 Linux 和 开源爱好者的 15 本书
|
||||
|
||||
[零基础学 Raspberry Pi][3],作者 Carrie Anne Philbin
|
||||
|
||||
在对编程感兴趣的儿童和成人中,体积小小的、仅信用卡一般大的 Raspberry Pi 引起了强烈的反响。你台式机能做的事情它都能做,具备一定的基础编程技能后,你可以让它做更多的事情。本书操作简明、项目风趣、技能扎实,是一本儿童可用的终极编程指南。([Joshua Allen Holm][4] 推荐,评论节选于本书的内容提要)
|
||||
|
||||
[Python 编程快速上手:让繁琐工作自动化][5],作者 Al Sweigart
|
||||
|
||||
这是一本经典的编程入门书,行文足够清晰,11 岁及以上的编程爱好者都可以读懂本书并从中受益。读者很快就会投入到真实且实用的任务中,在此过程中顺便掌握了优秀的编程实践。最好的一点是,如果你愿意,你可以在互联网上阅读本书。([DB Clinton][6] 推荐并评论)
|
||||
|
||||
[Scratch 游戏编程][7],作者 Jon Woodcock
|
||||
|
||||
本书适用于 8-12 岁没有或仅有有限编程经验的儿童。作为一本直观的可视化入门书,它使用有趣的图形和易于理解的操作,教导年轻的读者如何使用 Scratch 这款流行的自由编程语言构建他们自己的编程项目。([Joshua Allen Holm][4] 推荐,评论节选于本书的内容提要)
|
||||
|
||||
[用 Python 巧学数学][8],作者 Amit Saha
|
||||
|
||||
无论你是一名学生还是教师,只要你对使用 Python 学习数学感兴趣,不妨读读本书。在逻辑上,本书带领读者一步一步地从基础到更为复杂的操作,从最开始简单的 Python shell 数字运算,到使用类似 matplotlib 这样的 Python 库实现数据可视化,读者可以很容易跟上作者的思路。本书充分调动你的好奇心,感叹 Python 与 数学结合的威力。([Don Watkins][9] 推荐并评论)
|
||||
|
||||
[编程女生:学习编程,改变世界][10],作者 Reshma Saujani
|
||||
|
||||
作者是 Girls Who Code 运动的发起人,该运动得到 Sheryl Sandberg, Malala Yousafzai, and John Legend 支持。本书一部分是编程介绍,一部分女生赋能,这两部分都写得很有趣。本书包括动态艺术作品、零基础的编程原理讲解以及在 Pixar 和 NASA 等公司工作的女生的真实故事。这本书形象生动,向读者展示了计算机科学在我们生活中发挥的巨大作用以及其中的趣味。([Joshua Allen Holm][4] 推荐,评论节选于本书的内容提要)
|
||||
|
||||
[Python 游戏编程快速上手][11],作者 Al Sweigart
|
||||
|
||||
本书将让你学会如何使用流行的 Python 编程语言编写计算机游戏,不要求具有编程经验!入门阶段编写<ruby>刽子手<rt>Hangman</rt></ruby>,猜数字,<ruby>井字游戏<rt>Tic-Tac-Toe</rt></ruby>这样的经典游戏,后续更进一步编写高级一些的游戏,例如文字版寻宝游戏,以及带音效和动画的<ruby>碰撞与闪避<rt>collision-dodgoing</rt></ruby>游戏。([Joshua Allen Holm][4] 推荐,评论节选于本书的内容提要)
|
||||
|
||||
[Lauren Ipsum:关于计算机科学和一些不可思议事物的故事][12],作者 Carlos Bueno
|
||||
|
||||
本书采用爱丽丝梦游仙境的风格,女主角 Lauren Ipsum 来到一个稍微具有魔幻色彩的世界。世界的自然法则是逻辑学和计算机科学,世界谜题只能通过学习计算机编程原理并编写代码完成。书中没有提及计算机,但其作为世界的核心存在。([DB Clinton][6] 推荐并评论)
|
||||
|
||||
[Java 轻松学][13],作者 Bryson Payne
|
||||
|
||||
Java 是全世界最流行的编程语言,但众所周知上手比较难。本书让 Java 学习不再困难,通过若干实操项目,让你马上学会构建真实可运行的应用。([Joshua Allen Holm][4] 推荐,评论节选于本书的内容提要)
|
||||
|
||||
[终身幼儿园][14],作者 Mitchell Resnick
|
||||
|
||||
幼儿园正变得越来越像学校。在本书中,学习专家 Mitchel Resnick 提出相反的看法:学校(甚至人的一生)应该更像幼儿园。要适应当今快速变化的世界,各个年龄段的人们都必须学会开创性思维和行动;想要达到这个目标,最好的方式就是更加专注于想象、创造、玩耍、分享和反馈,就像孩子在传统幼儿园中那样。基于在 MIT <ruby>媒体实验室<rt>Media Lab</rt></ruby> 30 多年的经历, Resnick 讨论了新的技术和策略,可以让年轻人拥有开创性的学习体验。([Don Watkins][9] 推荐,评论来自 Amazon 书评)
|
||||
|
||||
[趣学 Python:教孩子学编程][15],作者 Jason Briggs
|
||||
|
||||
在本书中,Jason Briggs 将 Python 编程教学艺术提升到新的高度。我们可以很容易地将本书用作入门书,适用群体可以是教师/学生,也可以是父母/儿童。通过一步步引导的方式介绍复杂概念,让编程新手也可以成功完成,进一步激发学习欲望。本书是一本极为易读、寓教于乐但又强大的 Python 编程入门书。读者将学习基础数据结构,包括<ruby>元组<rt>turples</rt></ruby>、<ruby>列表<rt>lists</rt></ruby>和<ruby>映射<rt>maps</rt></ruby>等,学习如何创建函数、重用代码或者使用包括循环和条件语句在内的控制结构。孩子们还将学习如何创建游戏和动画,体验 Tkinter 的强大并创建高级图形。([Don Watkins][9] 推荐并评论)
|
||||
|
||||
[Scratch 编程园地][16],作者 Al Sweigart
|
||||
|
||||
Scratch 编程一般被视为一种寓教于乐的教年轻人编程的方式。在本书中,Al Sweigart 告诉我们 Scratch 是一种超出绝大多数人想象的强大编程语言。独特的风格,大师级的编写和呈现。Al 让孩子通过创造复杂图形和动画,短时间内认识到 Scratch 的强大之处。([Don Watkins][9] 推荐并评论)
|
||||
|
||||
[秘密编程者][17],作者 Gene Luen Yang,插图作者 Mike Holmes
|
||||
|
||||
Gene Luen Yang 是漫画小说超级巨星,也是一所高中的计算机编程教师。他推出了一个非常有趣的系列作品,将逻辑谜题、基础编程指令与引入入胜的解谜情节结合起来。故事发生在 Stately Academy 这所学校,其中充满有待解开的谜团。([Joshua Allen Holm][4] 推荐,评论节选于本书的内容提要)
|
||||
|
||||
[想成为编程者吗?编程、视频游戏制作、机器人等职业终极指南!][18],作者 Jane Bedell
|
||||
|
||||
酷爱编程?这本书易于理解,描绘了以编程为生的完整图景,激发你的热情,磨练你的专业技能。(Joshua Allen Holm][4] 推荐,评论节选于本书的内容提要)
|
||||
|
||||
[教孩子编程][19],作者 Bryson Payne
|
||||
|
||||
你是否在寻找一种寓教于乐的方式教你的孩子 Python 编程呢?Bryson Payne 已经写了这本大师级的书。本书通过乌龟图形打比方,引导你编写一些简单程序,为高级 Python 编程打下基础。如果你打算教年轻人编程,这本书不容错过。([Don Watkins][9] 推荐并评论)
|
||||
|
||||
[图解 Kubernetes(儿童版)][20],作者 Matt Butcher, 插画作者 Bailey Beougher
|
||||
|
||||
介绍了 Phippy 这个勇敢的 PHP 小应用及其 Kubernetes 之旅。([Chris Short][21] 推荐,评论来自 [Matt Butcher 的博客][20])
|
||||
|
||||
### 给宝宝的福利书
|
||||
|
||||
[宝宝的 CSS][22],[宝宝的 Javascript][23],[宝宝的 HTML][24],作者 Sterling Children's
|
||||
|
||||
这本概念书让宝宝熟悉图形和颜色的种类,这些是互联网编程语言的基石。这本漂亮的书用富有色彩的方式介绍了编程和互联网,对于技术人士的家庭而言,本书是一份绝佳的礼物。([Chris Short][21] 推荐,评论来自 Amazon 书评)
|
||||
|
||||
你是否有想要分享的适合宝宝或儿童的书呢?请在评论区留言告诉我们。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/5/books-kids-linux-open-source
|
||||
|
||||
作者:[Jen Wike Huger][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[pinewall](https://github.com/pinewall)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/remyd
|
||||
[1]:https://opensource.com/resources/linux
|
||||
[2]:https://opensource.com/article/18/3/what-open-source-programming
|
||||
[3]:https://www.amazon.com/Adventures-Raspberry-Carrie-Anne-Philbin/dp/1119046025
|
||||
[4]:https://opensource.com/users/holmja
|
||||
[5]:https://automatetheboringstuff.com/
|
||||
[6]:https://opensource.com/users/dbclinton
|
||||
[7]:https://www.goodreads.com/book/show/25733628-coding-games-in-scratch
|
||||
[8]:https://nostarch.com/doingmathwithpython
|
||||
[9]:https://opensource.com/users/don-watkins
|
||||
[10]:https://www.amazon.com/Girls-Who-Code-Learn-Change/dp/042528753X
|
||||
[11]:http://inventwithpython.com/invent4thed/
|
||||
[12]:https://www.amazon.com/gp/product/1593275749/ref=as_li_tl?ie=UTF8&tag=projemun-20&camp=1789&creative=9325&linkCode=as2&creativeASIN=1593275749&linkId=e05e1f12176c4959cc1aa1a050908c4a
|
||||
[13]:https://nostarch.com/learnjava
|
||||
[14]:http://lifelongkindergarten.net/
|
||||
[15]:https://nostarch.com/pythonforkids
|
||||
[16]:https://nostarch.com/scratchplayground
|
||||
[17]:http://www.secret-coders.com/
|
||||
[18]:https://www.amazon.com/So-You-Want-Coder-Programming/dp/1582705798?tag=ad-backfill-amzn-no-or-one-good-20
|
||||
[19]:https://opensource.com/education/15/9/review-bryson-payne-teach-your-kids-code
|
||||
[20]:https://deis.com/blog/2016/kubernetes-illustrated-guide/
|
||||
[21]:https://opensource.com/users/chrisshort
|
||||
[22]:https://www.amazon.com/CSS-Babies-Code-Sterling-Childrens/dp/1454921560/
|
||||
[23]:https://www.amazon.com/Javascript-Babies-Code-Sterling-Childrens/dp/1454921579/
|
||||
[24]:https://www.amazon.com/HTML-Babies-Code-Sterling-Childrens/dp/1454921552
|
||||
80
translated/tech/20180525 How insecure is your router.md
Normal file
80
translated/tech/20180525 How insecure is your router.md
Normal file
@ -0,0 +1,80 @@
|
||||
你的路由器有多不安全?
|
||||
======
|
||||

|
||||
|
||||
我一直对写在 T 恤上的“127.0.0.1 这个地方是独一无二的” 这句话持有异议。我知道你可能会认为应该将它读作是“家”,但是对于我来说,我认为应该是“本地主机是独一无二的地方”,就像世界上没有完全相同的二个戒指一样。在本文中,我想去讨论一些宽泛的问题:家庭网络的入口,对大多数人来说它是线缆或宽带路由器。英国和美国政府刚公布了“俄罗斯”攻击路由器的通告。我估计这次的攻击主要针对的是机构,而不是家庭,(看我以前的文章 "[国家行为者是什么,我们应该注意些什么?][1]"),但这对我们所有人都是一个警示。
|
||||
|
||||
### 路由器有什么用?
|
||||
|
||||
路由器很重要。它用于将一个网络(在本文中,是我们的家庭网络)与另外一个网络(在本文中,是指因特网,通过我们的因特网服务提供商的网络)连接。事实上,对于大多数人来说,我们所谓的”路由器“这个小盒子能够做的事情远比我们想到的要多。"routing" 比特就像它的发音一样;它让网络中的计算机能够找到一条向外部网络中计算机发送数据的路径 —— 当你接收数据时,正好是相反的方式。
|
||||
|
||||
在路由器的其它功能中,大多数时候也作为一台调制解调器来使用。在英国大部分到因特网的连接是通过电话线来实现的 —— 无论是电缆还是标准电话线 —— 尽管现在的最新趋势是通过移动互联网连接到家庭中。当你通过电话线连接时,我们所使用的因特网信号必须转换成其它的一些东西,(从另一端来的)返回信号也是如此。对于那些还记得过去的”拨号上网“时代的人来说,它就是你的电脑边上那个用于上网的发出刺耳声音的小盒子。
|
||||
|
||||
但是路由器能做的事情很多,有时候很多的事情,包括流量记录、作为一个无线接入点、提供 VPN 功能以便于从外部访问你的内网、儿童上网控制、防火墙等等。
|
||||
|
||||
现在的家用路由器越来越复杂;虽然国家行为者并不想参与其中,但是其它人可以。
|
||||
|
||||
你会问,这很重要吗?如果其它人可以进入你的系统,他们可以很容易地攻击你的笔记本电脑、电话、网络设备等等。他们可以访问和删除未被保护的个人数据。他们可以假装是你。他们使用你的网络去寄存非法数据或者用于攻击其它人。基本上所有的坏事都可以做。
|
||||
|
||||
幸运的是,现在的路由器趋向于因特网提供商来做设置,言外之意是你可以忘了它的存在,他们将保证它是运行良好和安全的。
|
||||
|
||||
### 因此,我们是安全的吗?
|
||||
|
||||
不幸的是,事实并非如此。
|
||||
|
||||
第一个问题是,因特网提供商是在有限的预算范围内做这些事情,而使用便宜的设备来做这些事可以让他们的利益最大化。因特网提供商的路由器质量越来越差。它是恶意攻击者的首选目标:如果他们知道特定型号的路由器被安装在几百万个家庭使用,那么很容易找到攻击的动机,因为攻击那个型号的路由器对他们来说是非常有价值的。
|
||||
|
||||
产生的其它问题还包括:
|
||||
|
||||
* 修复 bug 或者漏洞的过程很缓慢。升级固件可能会让因特网提供商产生较高的成本,因此,修复过程可能非常缓慢(如果他们打算修复的话)。
|
||||
* 非常容易获得或者默认的管理员密码,这意味着攻击者甚至都不需要去找到真实的漏洞 —— 他们就可以登入到路由器中。
|
||||
|
||||
|
||||
|
||||
### 对策
|
||||
|
||||
对于进入因特网第一跳的路由器,如何才能提升它的安全性,这里给你提供一个快速应对的清单。我是按从简单到复杂的顺序来列出它们的。在你对路由器做任何改变之前,需要先保存配置数据,以便于你需要的时候回滚它们。
|
||||
|
||||
1. **密码:** 一定,一定,一定要改变你的路由器的管理员密码。你可能很少会用到它,所以你一定要把密码记录在某个地方。它用的次数很少,你可以考虑将密码粘贴到路由器上,因为路由器一般都放置在仅授权的人(你和你的家人)才可以接触到的地方。
|
||||
2. **仅允许管理员从内部进行访问:** 除非你有足够好的理由和你知道如何去做,否则不要允许任何机器从外部的因特网上管理你的路由器。在你的路由器上有一个这样的设置。
|
||||
3. **WiFi 密码:** 一旦你做到了第 2 点,也要确保在你的网络上的那个 WiFi 密码 —— 无论是设置为你的路由器管理密码还是别的 —— 一定要是强密码。为了简单,为连接你的网络的访客设置一个”友好的“简单密码,但是,如果附近一个恶意的人猜到了密码,他做的第一件事情就是查找网络中的路由器。由于他在内部网络,他是可以访问路由器的(因此,第 1 点很重要)。
|
||||
4. **仅打开你知道的并且是你需要的功能:** 正如我在上面所提到的,现代的路由器有各种很酷的选项。不要使用它们。除非你真的需要它们,并且你真正理解了它们是做什么的,并且打开它们后有什么危险。否则,将增加你的路由器被攻击的风险。
|
||||
5. **购买你自己的路由器:** 用一个更好的路由器替换掉因特网提供商给你的路由器。去到你本地的电脑商店,让他们给你一些建议。你可能会花很多钱,但是也可能会遇到一些非常便宜的设备,而且比你现在拥有的更好、性能更强、更安全。你也可以只买一个调制解调器。一般设置调制解调器和路由器都很简单,并且,你可以从你的因特网提供商给你的设备中复制配置,它一般就能”正常工作“。
|
||||
6. **更新固件:** 我喜欢使用最新的功能,但是通常这并不容易。有时,你的路由器上会出现固件更新的提示。大多数的路由器会自动检查并且提示你在下次登入的时候去更新它。问题是如果更新失败则会产生灾难性后果或者丢失配置数据,那就需要你重新输入。但是你真的需要考虑去持续关注修复安全问题的固件更新,并更新它们。
|
||||
7. **转向开源:** 有一些非常好的开源路由器项目,可以让你用在现有的路由器上,用开源的软件去替换它的固件/软件。你可以在 [Wikipedia][2] 上找到许多这样的项目,以及在 [Opensource.com 上搜索 "router"][3],你将看到很多非常好的东西。对于谨慎的人来说要小心,这将会让你的路由器失去保修,但是如果你想真正控制你的路由器,开源永远是最好的选择。
|
||||
|
||||
|
||||
|
||||
### 其它问题
|
||||
|
||||
一旦你提升了你的路由器的安全性,你的家庭网络将变的很好,这是假像,事实并不是如此。你家里的物联网设备(Alexa、Nest、门铃、智能灯泡、等等)安全性如何?连接到其它网络的 VPN 安全性如何?通过 WiFi 的恶意主机、你的孩子手机上的恶意应用程序 …?
|
||||
|
||||
不,你永远不会有绝对的安全。但是正如我们前面讨论的,虽然没有绝对的”安全“这种事情,但是并不意味着我们不需要去提升安全标准,以让坏人干坏事更困难。
|
||||
|
||||
1. 我写的很简单 — 但请继续读下去,我们将达到目的。
|
||||
2. "俄罗斯政府赞助的信息技术国家行为者"
|
||||
3. 或者,以我父母的例子来说,我不相信 ”这个路由器“。
|
||||
4. 这里还有一种这样的情况,我不希望在评论区告诉我,你是直接以 1TB/s 的带宽连接到本地骨干网络的。非常感谢!
|
||||
5. 或许并没有包含全部的家庭。
|
||||
6. 你的路由器现在是一块”砖“,并且你不想访问因特网。
|
||||
|
||||
|
||||
|
||||
这篇文章最初发表在 [Alice, Eve, 和 Bob – 安全博客][4] 并授权重发布。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/5/how-insecure-your-router
|
||||
|
||||
作者:[Mike Bursell][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/mikecamel
|
||||
[1]:https://aliceevebob.com/2018/03/13/whats-a-state-actor-and-should-i-care/
|
||||
[2]:https://en.wikipedia.org/wiki/List_of_router_firmware_projects
|
||||
[3]:https://opensource.com/sitewide-search?search_api_views_fulltext=router
|
||||
[4]:https://aliceevebob.com/2018/04/17/defending-our-homes/
|
||||
@ -0,0 +1,100 @@
|
||||
如何在 Linux 中禁用内置摄像头
|
||||
======
|
||||
|
||||

|
||||
|
||||
今天,我们将看到如何禁用未使用的内置网络摄像头或外置摄像头,以及如何在 Linux 中需要时启用它。禁用网络摄像头可以在很多方面为你提供帮助。你可以防止恶意软件控制你的集成摄像头,并监视你和你的家庭。我们已经阅读过无数的故事,一些黑客可以在你不知情的情况下使用你的摄像头监视你。通过黑客攻击你的网络摄像头,用户可以在线共享你的私人照片和视频。可能有很多原因。如果你想知道如何禁用笔记本电脑或台式机中的网络摄像头,那么你很幸运。这个简短的教程将告诉你如何做。请继续阅读。
|
||||
|
||||
我在 Arch Linux 和 Ubuntu 上测试了这个指南。它的工作原理如下所述。我希望这也可以用在其他 Linux 发行版上。
|
||||
|
||||
### 在 Linux 中禁用内置摄像头
|
||||
|
||||
首先,使用如下命令找到网络摄像头驱动:
|
||||
```
|
||||
$ sudo lsmod | grep uvcvideo
|
||||
|
||||
```
|
||||
|
||||
**示例输出:**
|
||||
```
|
||||
uvcvideo 114688 1
|
||||
videobuf2_vmalloc 16384 1 uvcvideo
|
||||
videobuf2_v4l2 28672 1 uvcvideo
|
||||
videobuf2_common 53248 2 uvcvideo,videobuf2_v4l2
|
||||
videodev 208896 4 uvcvideo,videobuf2_common,videobuf2_v4l2
|
||||
media 45056 2 uvcvideo,videodev
|
||||
usbcore 286720 9 uvcvideo,usbhid,usb_storage,ehci_hcd,ath3k,btusb,uas,ums_realtek,ehci_pci
|
||||
|
||||
```
|
||||
|
||||
这里,**uvcvideo** 是我的网络摄像头驱动。
|
||||
|
||||
现在,让我们禁用网络摄像头。
|
||||
|
||||
为此,请编辑以下文件(如果文件不存在,只需创建它):
|
||||
```
|
||||
$ sudo nano /etc/modprobe.d/blacklist.conf
|
||||
|
||||
```
|
||||
|
||||
添加以下行:
|
||||
```
|
||||
##Disable webcam.
|
||||
blacklist uvcvideo
|
||||
|
||||
```
|
||||
|
||||
**“##Disable webcam”** 这行不是必需的。为了便于理解,我添加了它。
|
||||
|
||||
保存并退出文件。重启系统以使更改生效。
|
||||
|
||||
要验证网络摄像头是否真的被禁用,请打开任何即时通讯程序或网络摄像头软件,如 Cheese 或 Guvcview。你会看到如下的空白屏幕。
|
||||
|
||||
**Cheese 输出:**
|
||||
|
||||
![][2]
|
||||
|
||||
**Guvcview 输出:**
|
||||
|
||||
![][3]
|
||||
|
||||
看见了么?网络摄像头被禁用而无法使用。
|
||||
|
||||
要启用它,请编辑:
|
||||
```
|
||||
$ sudo nano /etc/modprobe.d/blacklist.conf
|
||||
|
||||
```
|
||||
|
||||
注释掉你之前添加的行。
|
||||
```
|
||||
##Disable webcam.
|
||||
#blacklist uvcvideo
|
||||
|
||||
```
|
||||
|
||||
保存并关闭文件。然后,重启计算机以启用网络摄像头。
|
||||
|
||||
这样够了吗?不。为什么?如果有人可以远程访问你的系统,他们可以轻松启用网络摄像头。所以,在不使用时用胶带覆盖它或者拔掉相机或者在 BIOS 中禁用它是一个不错的主意。此方法不仅用于禁用内置摄像头,还用于外部网络摄像头。
|
||||
|
||||
就是这些了。希望对你有用。还有更好的东西。敬请关注!
|
||||
|
||||
干杯!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/how-to-disable-built-in-webcam-in-ubuntu/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.ostechnix.com/author/sk/
|
||||
[1]:data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[2]:http://www.ostechnix.com/wp-content/uploads/2015/08/cheese.jpg
|
||||
[3]:http://www.ostechnix.com/wp-content/uploads/2015/08/guvcview.jpg
|
||||
@ -0,0 +1,174 @@
|
||||
8 个基本的 Docker 容器管理命令
|
||||
======
|
||||
利用这 8 个命令可以学习 Docker 容器的基本管理方式。这是一个为 Docker 初学者准备的,带有示范命令输出的指南。
|
||||
|
||||
![Docker 容器管理命令][1]
|
||||
|
||||
在这篇文章中,我们将带你学习 8 个基本的 Docker 容器命令,它们操控着 Docker 容器的基本活动,例如 <ruby>运行<rt>run</rt></ruby>, <ruby>列举<rt>list</rt></ruby>, <ruby>停止<rt>stop</rt></ruby>, <ruby>查看历史纪录<rt>view logs</rt></ruby>, <ruby>删除<rt>delete</rt></ruby>, 等等。如果你对 Docker 的概念很陌生,推荐你看看我们的 [介绍指南][2],来了解 Docker 的基本内容以及 [如何][3] 在 Linux 上安装 Docker. 现在让我们赶快进入要了解的命令:
|
||||
|
||||
### 如何运行 Docker 容器?
|
||||
|
||||
众所周知,Docker 容器只是一个运行于<ruby>宿主操作系统<rt>host OS</rt></ruby>上的应用进程,所以你需要一个镜像来运行它。Docker 镜像运行时的进程就叫做 Docker 容器。你可以加载本地 Docker 镜像,也可以从 Docker Hub 上下载。Docker Hub 是一个提供公有和私有镜像来进行<ruby>拉取<rt>pull</rt></ruby>操作的集中仓库。官方的 Docker Hub 位于 [hub.docker.com][4]. 当你指示 Docker 引擎运行容器时,它会首先搜索本地镜像,如果没有找到,它会从 Docker Hub 上拉取相应的镜像。
|
||||
|
||||
让我们运行一个 Apache web-server 的 Docker 镜像,比如 httpd 进程。你需要运行 `docker container run` 命令。旧的命令为 `docker run`, 但后来 Docker 添加了子命令部分,所以新版本支持<ruby>附属命令<rt>below command</rt></ruby> -
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container run -d -p 80:80 httpd
|
||||
Unable to find image 'httpd:latest' locally
|
||||
latest: Pulling from library/httpd
|
||||
3d77ce4481b1: Pull complete
|
||||
73674f4d9403: Pull complete
|
||||
d266646f40bd: Pull complete
|
||||
ce7b0dda0c9f: Pull complete
|
||||
01729050d692: Pull complete
|
||||
014246127c67: Pull complete
|
||||
7cd2e04cf570: Pull complete
|
||||
Digest: sha256:f4610c3a1a7da35072870625733fd0384515f7e912c6223d4a48c6eb749a8617
|
||||
Status: Downloaded newer image for httpd:latest
|
||||
c46f2e9e4690f5c28ee7ad508559ceee0160ac3e2b1688a61561ce9f7d99d682
|
||||
```
|
||||
|
||||
Docker 的 `run` 命令将镜像名作为强制参数,另外还有很多可选参数。常用的参数有 -
|
||||
|
||||
* `-d` : Detach container from current shell
|
||||
* `-p X:Y` : Bind container port Y with host’s port X
|
||||
* `--name` : Name your container. If not used, it will be assigned randomly generated name
|
||||
* `-e` : Pass environmental variables and their values while starting container
|
||||
|
||||
|
||||
|
||||
通过以上输出你可以看到,我们将 `httpd` 作为镜像名来运行容器。接着,本地镜像没有找到,Docker 引擎从 Docker Hub 拉取了它。注意,它下载了镜像 **httpd:latest**, 其中 : 后面跟着版本号。如果你需要运行特定版本的容器,你可以在镜像名后面注明版本名。如果不提供版本名,Docker 引擎会自动拉取最新的版本。
|
||||
|
||||
输出的最后一行显示了你新运行的 httpd 容器的特有 ID。
|
||||
|
||||
### 如何列出所有运行中的 Docker 容器?
|
||||
|
||||
现在,你的容器已经运行起来了,你可能想要确认这一点,或者你想要列出你的机器上运行的所有容器。你可以使用 `docker container ls` 命令。在旧的 Docker 版本中,对应的命令为 `docker ps`。
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container ls
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
c46f2e9e4690 httpd "httpd-foreground" 11 minutes ago Up 11 minutes 0.0.0.0:80->80/tcp cranky_cori
|
||||
```
|
||||
|
||||
列出的结果是按列显示的。每一列的值分别为 -
|
||||
|
||||
1. Container ID :一开始的几个字符对应你特有的容器 ID
|
||||
2. Image :你运行容器的镜像名
|
||||
3. Command :容器启动后运行的命令
|
||||
4. Created :创建时间
|
||||
5. Status :容器当前状态
|
||||
6. Ports :与宿主端口相连接的端口信息
|
||||
7. Names :容器名(如果你没有命名你的容器,那么会随机创建)
|
||||
|
||||
|
||||
|
||||
### 如何查看 Docker 容器的历史纪录?
|
||||
|
||||
在第一步我们使用了 -d 参数来将容器,在它一开始运行的时候,就从当前的 shell 中分离出来。在这种情况下,我们不知道容器里面发生了什么。所以为了查看容器的历史纪录,Docker 提供了 `logs` 命令。它采用容器名称或 ID 作为参数。
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container logs cranky_cori
|
||||
AH00558: httpd: Could not reliably determine the server's fully qualified domain name, using 172.17.0.2. Set the 'ServerName' directive globally to suppress this message
|
||||
AH00558: httpd: Could not reliably determine the server's fully qualified domain name, using 172.17.0.2. Set the 'ServerName' directive globally to suppress this message
|
||||
[Thu May 31 18:35:07.301158 2018] [mpm_event:notice] [pid 1:tid 139734285989760] AH00489: Apache/2.4.33 (Unix) configured -- resuming normal operations
|
||||
[Thu May 31 18:35:07.305153 2018] [core:notice] [pid 1:tid 139734285989760] AH00094: Command line: 'httpd -D FOREGROUND'
|
||||
```
|
||||
|
||||
这里我使用了容器名称作为参数。你可以看到在我们的 httpd 容器中与 Apache 相关的历史纪录。
|
||||
|
||||
### 如何确定 Docker 容器的进程?
|
||||
|
||||
容器是一个使用宿主资源来运行的进程。这样,你可以在宿主系统的进程表中定位容器的进程。让我们在宿主系统上确定容器进程。
|
||||
|
||||
Docker 使用著名的 `top` 命令作为子命令的名称,来查看容器产生的进程。它采用容器的名称或 ID 作为参数。在旧版本的 Docker 中,只可运行 `docker top` 命令。在新版本中,`docker top` 和 `docker container top` 命令都可以生效。
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container top cranky_cori
|
||||
UID PID PPID C STIME TTY TIME CMD
|
||||
root 15702 15690 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
bin 15729 15702 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
bin 15730 15702 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
bin 15731 15702 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
|
||||
root@kerneltalks # ps -ef |grep -i 15702
|
||||
root 15702 15690 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
bin 15729 15702 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
bin 15730 15702 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
bin 15731 15702 0 18:35 ? 00:00:00 httpd -DFOREGROUND
|
||||
root 15993 15957 0 18:59 pts/0 00:00:00 grep --color=auto -i 15702
|
||||
```
|
||||
|
||||
在第一个输出中,列出了容器产生的进程的列表。它包含了所有细节,包括用途,<ruby>进程号<rt>pid</rt></ruby>,<ruby>父进程号<rt>ppid</rt></ruby>,开始时间,命令,等等。这里所有的进程号你都可以在宿主的进程表里搜索到。这就是我们在第二个命令里做得。这证明了容器确实是宿主系统中的进程。
|
||||
|
||||
### 如何停止 Docker 容器?
|
||||
|
||||
只需要 `stop` 命令!同样,它采用容器名称或 ID 作为参数。
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container stop cranky_cori
|
||||
cranky_cori
|
||||
```
|
||||
|
||||
### 如何列出停止的或不活动的 Docker 容器?
|
||||
|
||||
现在我们停止了我们的容器,这时如果我们使用 `ls` 命令,它将不会出现在列表中。
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container ls
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
```
|
||||
|
||||
所以,在这种情况下,如果想要查看停止的或不活动的容器,你需要在 `ls` 命令里同时使用 `-a` 参数。
|
||||
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container ls -a
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
c46f2e9e4690 httpd "httpd-foreground" 33 minutes ago Exited (0) 2 minutes ago cranky_cori
|
||||
```
|
||||
|
||||
有了 `-a` 参数,现在我们可以查看已停止的容器。注意这些容器的状态被标注为 <ru by>已退出<rt>exited</rt></ruby>。既然容器只是一个进程,那么用“退出”比“停止”更合适!
|
||||
|
||||
### 如何(重新)启动 Docker 容器?
|
||||
|
||||
现在,我们来启动这个已停止的容器。这和运行一个容器有所区别。当你运行一个容器时,你将启动一个全新的容器。当你启动一个容器时,你将开始一个已经停止并保存了当时运行状态的容器。它将以停止时的状态重新开始运行。
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container start c46f2e9e4690
|
||||
c46f2e9e4690
|
||||
|
||||
root@kerneltalks # docker container ls -a
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
c46f2e9e4690 httpd "httpd-foreground" 35 minutes ago Up 8 seconds 0.0.0.0:80->80/tcp cranky_cori
|
||||
```
|
||||
|
||||
### 如何移除 Docker 容器?
|
||||
|
||||
我们使用 `rm` 命令来移处容器。你不可以移除运行中的容器。移除之前需要先停止容器。你可以使用 `-f` 参数搭配 `rm` 命令来强制移除容器,但并不推荐这么做。
|
||||
|
||||
```
|
||||
root@kerneltalks # docker container rm cranky_cori
|
||||
cranky_cori
|
||||
root@kerneltalks # docker container ls -a
|
||||
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
|
||||
```
|
||||
|
||||
你看,一旦移除了容器,即使再使用 `ls -a` 命令也查看不到容器了。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://kerneltalks.com/virtualization/8-basic-docker-container-management-commands/
|
||||
|
||||
作者:[Shrikant Lavhate][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[lonaparte](https://github.com/译者ID/lonaparte)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://kerneltalks.com
|
||||
[1]:https://a4.kerneltalks.com/wp-content/uploads/2018/06/basic-Docker-container-management-commands.png
|
||||
[2]:https://kerneltalks.com/virtualization/what-is-docker-introduction-guide-to-docker/
|
||||
[3]:https://kerneltalks.com/virtualization/how-to-install-docker-in-linux/
|
||||
[4]:https://hub.docker.com/
|
||||
190
translated/tech/20180611 How to partition a disk in Linux.md
Normal file
190
translated/tech/20180611 How to partition a disk in Linux.md
Normal file
@ -0,0 +1,190 @@
|
||||
# Linux 磁盘分区
|
||||
|
||||

|
||||
|
||||
在 Linux 中创建和删除分区是一种常见的操作,因为存储设备(如硬盘驱动器和USB驱动器)在使用之前必须以某种方式进行结构化。在大多数情况下,大型存储设备被分为称为分区的独立部分。分区还允许您将硬盘分割成独立的部分,每个部分都作为自己的硬盘驱动器。如果您运行多个操作系统,那么分区是非常有用的。
|
||||
|
||||
在 Linux 中有许多强大的工具可以创建、删除和操作磁盘分区。在本文中,我将解释如何使用 `parted` 命令,这对于大型磁盘设备和许多磁盘分区尤其有用。`parted` 与更常见的 `fdisk` 和 `cfdisk` 命令之间的区别包括:
|
||||
|
||||
* **GPT 格式:**`parted` 命令可以创建全局惟一的标识符分区表 [GPT][1],而 `fdisk` 和 `cfdisk` 则仅限于 DOS 分区表。
|
||||
* **更大的磁盘:** DOS 分区表可以格式化最多 2TB 的磁盘空间,尽管在某些情况下最多可以达到 16TB。然而,一个 GPT 分区表可以处理最多 8ZiB 的空间。
|
||||
* **更多的分区:** 使用主分区和扩展分区,DOS 分区表只允许 16 个分区。在 GPT 中,默认情况下您可以得到 128 个分区,并且可以选择更多的分区。
|
||||
* **可靠性:** 在 DOS 分区表中,只保存了一份分区表备份,在 GPT 中保留了两份分区表的备份(在磁盘的起始和结束部分),同时 GPT 还使用了 [CRC][2] 校验和来检查分区表的完整性,在 DOS 分区中并没有实现。
|
||||
|
||||
由于现在的磁盘更大,需要更灵活地使用它们,建议使用 `parted` 来处理磁盘分区。大多数时候,磁盘分区表是作为操作系统安装过程的一部分创建的。在向现有系统添加存储设备时,直接使用parted命令非常有用。
|
||||
|
||||
### 尝试一下 parted
|
||||
|
||||
`parted` 命令。为了尝试这些步骤,我强烈建议使用一种全新的存储设备或一种您不介意将内容删除的设备。
|
||||
|
||||
下面解释了使用该命令对存储设备进行分区的过程。为了尝试这些步骤,我强烈建议使用一种全新的存储设备或一种您不介意将内容删除的设备。
|
||||
|
||||
**1\. 列出分区:** 使用 `parted -l` 来标识你要进行分区的设备。一般来说,第一个硬盘 (`/dev/sda` 或 `/dev/vda` )保存着操作系统, 因此寻找另一个磁盘,以找到你想要分区的磁盘 (例如, `/dev/sdb`, `/dev/sdc`, `/dev/vdb `,`/dev/vdc`, 等。)。
|
||||
|
||||
```
|
||||
$ sudo parted -l
|
||||
|
||||
[sudo] password for daniel:
|
||||
|
||||
Model: ATA RevuAhn_850X1TU5 (scsi)
|
||||
|
||||
Disk /dev/vdc: 512GB
|
||||
|
||||
Sector size (logical/physical): 512B/512B
|
||||
|
||||
Partition Table: msdos
|
||||
|
||||
Disk Flags:
|
||||
|
||||
|
||||
|
||||
Number Start End Size Type File system Flags
|
||||
|
||||
1 1049kB 525MB 524MB primary ext4 boot
|
||||
|
||||
2 525MB 512GB 512GB primary lvm
|
||||
|
||||
```
|
||||
|
||||
**2\. 打开存储设备:** 使用 `parted` 选中您要分区的设备。在这里例子中,是虚拟系统上的第三个磁盘(`/dev/vdc`)。指明你要使用哪一个设备非常重要。 如果你仅仅输入了 `parted` 命令而没有指定设备名字, 它会随机选择一个设备进行操作。
|
||||
|
||||
```
|
||||
$ sudo parted /dev/vdc
|
||||
|
||||
GNU Parted 3.2
|
||||
|
||||
Using /dev/vdc
|
||||
|
||||
Welcome to GNU Parted! Type 'help' to view a list of commands.
|
||||
|
||||
(parted)
|
||||
|
||||
```
|
||||
|
||||
**3\. 设定分区表:** 设置分区表为 GPT ,然后输入 "Yes" 开始执行
|
||||
|
||||
```
|
||||
(parted) mklabel gpt
|
||||
|
||||
Warning: the existing disk label on /dev/vdc will be destroyed
|
||||
|
||||
and all data on this disk will be lost. Do you want to continue?
|
||||
|
||||
Yes/No? Yes
|
||||
|
||||
```
|
||||
|
||||
`mklabel` 和 `mktable` 命令用于相同的目的(在存储设备上创建分区表)。支持的分区表有:aix、amiga、bsd、dvh、gpt、mac、ms-dos、pc98、sun 和 loop。记住 `mklabel` 不会创建一个分区,而是创建一个分区表。
|
||||
|
||||
**4\. 检查分区表:** 查看存储设备信息
|
||||
|
||||
```
|
||||
(parted) print
|
||||
|
||||
Model: Virtio Block Device (virtblk)
|
||||
|
||||
Disk /dev/vdc: 1396MB
|
||||
|
||||
Sector size (logical/physical): 512B/512B
|
||||
|
||||
Partition Table: gpt
|
||||
|
||||
Disk Flags:
|
||||
|
||||
Number Start End Size File system Name Flags
|
||||
|
||||
```
|
||||
|
||||
**5\.获取帮助:** 为了知道如何去创建一个新分区,输入: `(parted) help mkpart` 。
|
||||
|
||||
```
|
||||
(parted) help mkpart
|
||||
|
||||
mkpart PART-TYPE [FS-TYPE] START END make a partition
|
||||
|
||||
|
||||
|
||||
PART-TYPE is one of: primary, logical, extended
|
||||
|
||||
FS-TYPE is one of: btrfs, nilfs2, ext4, ext3, ext2, fat32, fat16, hfsx, hfs+, hfs, jfs, swsusp,
|
||||
|
||||
linux-swap(v1), linux-swap(v0), ntfs, reiserfs, hp-ufs, sun-ufs, xfs, apfs2, apfs1, asfs, amufs5,
|
||||
|
||||
amufs4, amufs3, amufs2, amufs1, amufs0, amufs, affs7, affs6, affs5, affs4, affs3, affs2, affs1,
|
||||
|
||||
affs0, linux-swap, linux-swap(new), linux-swap(old)
|
||||
|
||||
START and END are disk locations, such as 4GB or 10%. Negative values count from the end of the
|
||||
|
||||
disk. For example, -1s specifies exactly the last sector.
|
||||
|
||||
|
||||
|
||||
'mkpart' makes a partition without creating a new file system on the partition. FS-TYPE may be
|
||||
|
||||
specified to set an appropriate partition ID.
|
||||
|
||||
```
|
||||
|
||||
**6\. 创建分区:** 为了创建一个新分区(在这个例子中,分区 0 有 1396MB),输入下面的命令:
|
||||
|
||||
```
|
||||
(parted) mkpart primary 0 1396MB
|
||||
|
||||
|
||||
|
||||
Warning: The resulting partition is not properly aligned for best performance
|
||||
|
||||
Ignore/Cancel? I
|
||||
|
||||
|
||||
|
||||
(parted) print
|
||||
|
||||
Model: Virtio Block Device (virtblk)
|
||||
|
||||
Disk /dev/vdc: 1396MB
|
||||
|
||||
Sector size (logical/physical): 512B/512B
|
||||
|
||||
Partition Table: gpt
|
||||
|
||||
Disk Flags:
|
||||
|
||||
Number Start End Size File system Name Flags
|
||||
|
||||
1 17.4kB 1396MB 1396MB primary
|
||||
|
||||
```
|
||||
|
||||
文件系统类型(fstype)不会在 `/dev/vdc1`上创建 ext4 文件系统。 DOS 分区表的分区类型是主分区,逻辑分区和扩展分区。 在 GPT 分区表中,分区类型用作分区名称。 在 GPT 下提供分区名称是必须的;在上例中,primary 是名称,而不是分区类型。
|
||||
|
||||
**7\. 保存推出:** 当你退出 `parted` 时,修改会自动保存。退出请输入如下命令:
|
||||
|
||||
```
|
||||
(parted) quit
|
||||
|
||||
Information: You may need to update /etc/fstab.
|
||||
|
||||
$
|
||||
|
||||
```
|
||||
|
||||
### 谨记
|
||||
|
||||
当您添加新的存储设备时,请确保在开始更改其分区表之前确定正确的磁盘。如果您错误地更改包含计算机操作系统的磁盘分区,您可以使您的系统无法启动。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/6/how-partition-disk-linux
|
||||
|
||||
作者:[Daniel Oh][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[amwps290](https://github.com/amwps290)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/daniel-oh
|
||||
[1]:https://en.wikipedia.org/wiki/GUID_Partition_Table
|
||||
[2]:https://en.wikipedia.org/wiki/Cyclic_redundancy_check
|
||||
Loading…
Reference in New Issue
Block a user