mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-21 02:10:11 +08:00
commit
572dd9b3de
@ -1,58 +0,0 @@
|
||||
translating by ZTinoZ
|
||||
LibreOffice 4.3.4 Released With 60 Bug Fixes, v4.4 Shaping Up Nicely
|
||||
================================================================================
|
||||

|
||||
|
||||
**Two weeks on [from the last][1], The Document Foundation is back with yet another minor release of its open-source LibreOffice productivity suite.**
|
||||
|
||||
LibreOffice 4.3.4, the fourth such minor release in the ‘fresh’ series, is composed solely of bug fixes, which is par for the course in these point releases.
|
||||
|
||||
Adding to the sense of deja vu is the number of bugs the foundation say have been caught in the developers’ butterfly net: around 60 or so.
|
||||
|
||||
- Sorting behaviour now defaults to old style again (Calc)
|
||||
- Restore focus window after preview (Impress)
|
||||
- Chart wizard dialog no longer ‘cut off’
|
||||
- Word count with recorded changes fixed (Writer)
|
||||
- Various RTF fixes, including image border import (Writer)
|
||||
|
||||
A full list of changes can be [found on the LibreOffice Wiki page][2].
|
||||
|
||||
### Download ###
|
||||
|
||||
Many folks have the whole LibreOffice schaboodle installed but rarely ever use it. If you count yourself among them, you could hold off on this release and never notice.
|
||||
|
||||
If you do fancy upgrading you can find all of the relevant download links on the official project website.
|
||||
|
||||
- [Download LibreOffice 4.3.4][3]
|
||||
|
||||
### Looking Ahead to LibreOffice 4.4 ###
|
||||
|
||||

|
||||
|
||||
Info bar coming in LibreOffice 4.4
|
||||
|
||||
LibreOffice 4.4 should be a little more promising.
|
||||
|
||||
[A wiki page details][4] the ongoing GUI tweaks in progress, with a new color picker, restyled paragraph line-spacing selector and an info bar to denote ‘read only’ mode among the many, many highlights.
|
||||
|
||||
While the sum of these won’t amount to the huge wholesale interface changes I know the desktop community clamours for, they are sure-footed steps in the right direction.
|
||||
|
||||
It’s also salient to remember that LibreOffice is a staple — in some cases integral — software for businesses and institutions. Any dramatic overhaul in look or layout would have a big knock on effect.
|
||||
|
||||
Thanks Tim W!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/11/libreoffice-4-3-4-arrives-bundle-bug-fixes
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.omgubuntu.co.uk/2014/10/libreoffice-4-3-3-released-62-bug-fixes
|
||||
[2]:https://wiki.documentfoundation.org/Releases/4.3.4/RC1
|
||||
[3]:http://www.libreoffice.org/download/libreoffice-fresh/
|
||||
[4]:https://wiki.documentfoundation.org/ReleaseNotes/4.4#GUI
|
||||
@ -0,0 +1,42 @@
|
||||
Systemd fallout: Two Debian technical panel members resign
|
||||
================================================================================
|
||||

|
||||
|
||||
**Two well-known and experienced Debian developers, both members of the project's technical committee, have announced they will be leaving the committee.**
|
||||
|
||||
The resignations of [Colin Watson][1] and [Russ Allberry][2] from the panel come soon after senior developer Joey Hess [resigned][3] from the project altogether.
|
||||
|
||||
There has been much acrimony recently over the adoption of the systemd init system as the default for Jessie, the next release of Debian, which is expected to come out in the next few months.
|
||||
|
||||
The Debian Technical Committee [decided][4] back in February, via the casting vote of panel chief Bdale Garbee, to adopt systemd as the default. This decision came after months of discussion.
|
||||
|
||||
Recently, there has been [another push][5] for reconsideration led by another technical committee member, Ian Jackson, and [a general resolution][6] was put up for vote. It is open for voting until midnight on November 18, UTC (10am on Wednesday AEST). There are a few options proposed by others, including one from the Debian Project leader Lucas Nussbaum, besides the main resolution.
|
||||
|
||||
In the initial vote back in February, Allberry supported systemd as the default, while Watson, an employee of Canonical, the company that creates the Ubuntu GNU/Linux distribution, expressed a preference for upstart. Jackson also backed upstart.
|
||||
|
||||
In [a post][7] explaining his decision, Watson, one of the first batch to join Canonical, attributed it to a general move on his part to start spending his Debian time on things he found enjoyable. Late last month, [he asked][8] to be moved from the Ubuntu Foundations team to the Launchpad engineering team. Watson has given the Debian Technical Committee time to appoint someone in his place before he moves on.
|
||||
|
||||
In contrast, Allberry's [resignation post][9] said he wanted to leave immediately, though he later added that he would stay on for a while if needed.
|
||||
|
||||
His frustration was clear: "If any part of this doesn't make sense, or if any of it feels like an attack or a reaction to any single person or event, I'm happy to clarify. I would appreciate it if people would ask for clarification rather than making assumptions, as assumptions about other people's motives are one of the things that I find the most demoralising about the Debian project right now."
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.itwire.com/business-it-news/open-source/66153-systemd-fallout-two-debian-technical-panel-members-resign
|
||||
|
||||
作者:[Sam Varghese][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.itwire.com/business-it-news/open-source/itemlist/user/902-samvarghese
|
||||
[1]:https://lists.debian.org/debian-ctte/2014/11/msg00052.html
|
||||
[2]:https://lists.debian.org/debian-ctte/2014/11/msg00071.html
|
||||
[3]:http://www.itwire.com/business-it-news/open-source/66014-systemd-fallout-joey-hess-quits-debian-project
|
||||
[4]:http://www.itwire.com/business-it-news/open-source/63121-garbees-casting-vote-means-systemd-is-debian-init
|
||||
[5]:http://www.itwire.com/business-it-news/open-source/65781-pushback-against-systemd-in-debian-gathers-steam
|
||||
[6]:https://www.debian.org/vote/2014/vote_003
|
||||
[7]:https://lists.debian.org/debian-ctte/2014/11/msg00052.html
|
||||
[8]:http://www.chiark.greenend.org.uk/ucgi/~cjwatson/blosxom/ubuntu/2014-10-26-moving-on-but-not-too-far.html
|
||||
[9]:https://lists.debian.org/debian-ctte/2014/11/msg00071.html
|
||||
@ -0,0 +1,86 @@
|
||||
5 Best Open Source Web Browser Security Apps
|
||||
================================================================================
|
||||
The Web browser acts as the gateway for myriad online services these days. Computer security problems are far from solved, and technology advances provide new ways for malware to infect our devices and enter our business networks. For example, smartphones and tablets offer fresh new fields for malware—and its malicious cousin, "[malvertising][1]"—to exploit.
|
||||
|
||||
Malvertising, or malicious advertising, injects malware into legitimate ads and ad networks. Granted, you could argue that there's a thin line between "legitimate" ads and ad networks and not-legitimate ads and ad networks. But don’t get distracted. Privacy and security are inextricably linked, and protecting your privacy is part of protecting your security.
|
||||
|
||||
Firefox, Chrome, and Opera are the best Web browsers; they offer the best performance, the most compatibility, and the best security. These five open source security apps install in your Web browser, and they protect you from a variety of threats.
|
||||
|
||||
### Protect Your Privacy: Open Source Web Browser Security Apps ###
|
||||
|
||||
#### 1. [AdBlock][2] ####
|
||||
|
||||
Ad networks are wonderful malware vectors. A single ad network serves thousands of sites, so compromising one ad network equals many thousands of compromised machines. AdBlock, and its derivatives—[AdBlock Plus][2], [AdBlock Pro][3], and [AdBlock Edge][4]—are all great tools for blocking ads, which has the added benefit of making cluttery annoying ads-infested sites more usable.
|
||||
|
||||
Of course there is a downside: harming sites that depend on ad revenues. All of them have one-click whitelists, so you can selectively turn off ad-blocking on sites that you want to support. (Really, my dear Webmeisters, if you don't want your site visitors blocking your ads then don't be obnoxious.)
|
||||
|
||||

|
||||
|
||||
Figure 1: Selecting additional filters for your Ad Blocker.
|
||||
|
||||
Ad blockers do more than block ads; they also block Web-tracking bugs and malicious domains. To turn on additional filter lists, click on your ad blocker icon > click **Preferences**, and go to the **Filter Subscriptions** tab. Click the **Add Filter Subscription** button, and then add **Easy Privacy + EasyList**. The Malware Domains filter is a good one to include as well; it blocks domains that are known to host malware and spyware. Adblock works with Firefox, Chrome, Opera, Safari, Internet Explorer, and Android.
|
||||
|
||||
#### 2. [HTTPS Everywhere][5] ####
|
||||
|
||||
HTTPS Everywhere browser extension ensures that you will never accidentally connect to a Web site with HTTP when HTTPS is available. HTTPS means your connection is encrypted with SSL (secure sockets layer), which is a commonly-used protocol for encrypting Web and email connections. HTTPS Everywhere is available for Firefox, Chrome, and Opera.
|
||||
|
||||
When you install HTTPS Everywhere, it asks if you want to enable the SSL Observatory. Say yes, as it offers additional protections against man-in-the-middle and bogus SSL certificate attacks. HTTPS Everywhere works with Firefox, Chrome, Opera, Android.
|
||||
|
||||
#### 3. [Social Fixer][6] ####
|
||||
|
||||
Social Fixer tames Facebook. It gives you mighty powers to filter your news feed so that you see what you want to see, creates tabbed feeds organized by topic, hides whatever you don't want to see, displays pictures full-sized on mouse-over, disables the Theater view of images, and lots more.
|
||||
|
||||
It's not really designed to be a security tool, but Social Fixer offers two important security features:
|
||||
|
||||
- It anonymizes Facebook pages for screenshots by replacing profile pictures with generic icons, and it changes usernames to fake names
|
||||
- It reliably blocks Facebook games, which are notorious sources of trouble
|
||||
|
||||

|
||||
|
||||
Figure 2: Anonymizing a Facebook screen with Social Fixer.
|
||||
|
||||
#### 4. [Privacy Badger][7] ####
|
||||
|
||||
The Electronic Frontier Foundation's Privacy Badger is a superb tracker-and spy-ads blocker. These days Web pages are composed of content from multiple sources: ad servers, comments servers, content farms, image farms, third-party login servers, and gosh knows what-all.
|
||||
|
||||
AdBlock is good at blocking this junk, but Privacy Badger is better. It doesn't rely on filter lists, which have to be maintained by humans somewhere, but rather algorithms and policy methods, and you can easily override it if it blocks something in error. Privacy Badger works with Firefox and Chrome.
|
||||
|
||||

|
||||
|
||||
Figure 3: Privacy Badger blocks tracking sites.
|
||||
|
||||
Privacy Badger should just work. Click on its icon to see what it's blocking on any site you're visiting. Try it on Huffingtonpost.com, one of the champions of stuffing the maximum number of third-party components into each and every page (Figure 3).
|
||||
|
||||
The sliders tell the status of each site: red means that site is completely blocked, so it can't set cookies or serve up any content to you. Yellow indicates a third-party domain that appears to be trying to track you, but it is on Privacy Badger's whitelist of allowed domains. Green is for a third-party domain that is not yet classified as a tracker, but this could change as you visit **multiple** sites and Privacy Badger observes its behavior.
|
||||
|
||||
You can set the sliders yourself according to your preference; for example, on one site I visited Privacy Badger blocked bazaarvoice.com, which some shopping sites use to host their customer reviews.
|
||||
|
||||
#### 5. [Disconnect][8] ####
|
||||
|
||||
Disconnect is another anti-tracker and anti-cookie tool with a great feature set. It runs on Firefox, Chrome, Internet Explorer, and Safari, and offers special iOS and Android versions. Not only does it foil trackers, it also secures your wireless transmissions (Wi-fi, 3G, and 4G) with its own virtual private network, protecting you from wiretapping and malvertising. It protects you from widgetjacking, which is a technique used by attackers to gain access to your sites that require logins. With widgetjacking they don't even need your password; they use stolen cookies.
|
||||
|
||||
Disconnect also provides a safe search feature that lets you use your favorite search engines while blocking their snoopy data-mining habits.
|
||||
|
||||
Just assume that everyone on the Web is out to get you. It's all abstract and behind the scenes, and not obvious like someone bashing a window to get into your house. But the threats are numerous and real, and you have to take precautions to protect yourself.
|
||||
|
||||
Carla Schroder is the author of The Book of Audacity, Linux Cookbook, Linux Networking Cookbook,and hundreds of Linux how-to articles. She's the former managing editor of Linux Planet and Linux Today.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.smallbusinesscomputing.com/biztools/5-best-open-source-web-browser-security-apps.html
|
||||
|
||||
作者:[Carla Schroder][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.smallbusinesscomputing.com/author/Carla-Schroder-6080.html
|
||||
[1]:http://www.webopedia.com/TERM/M/malvertising.html
|
||||
[2]:https://getadblock.com/
|
||||
[3]:https://chrome.google.com/webstore/detail/adblock-pro/ocifcklkibdehekfnmflempfgjhbedch?hl=en-US
|
||||
[4]:https://addons.mozilla.org/en-us/firefox/addon/adblock-edge/
|
||||
[5]:https://www.eff.org/Https-everywhere
|
||||
[6]:http://socialfixer.com/
|
||||
[7]:https://www.eff.org/privacybadger
|
||||
[8]:https://disconnect.me/
|
||||
@ -0,0 +1,141 @@
|
||||
How to configure and secure your Postfix email server
|
||||
================================================================================
|
||||

|
||||
|
||||
Once you have your application server up and running, you are going to need a good email server to deliver your emails. I have been using postfix for all my servers and below is the configuration I generally use.
|
||||
|
||||
### Installation of Postfix on CentOS 6 ###
|
||||
|
||||
yum install postfix
|
||||
|
||||
Sendmail is installed by default, so it is better to stop and remove it
|
||||
|
||||
service sendmail stop
|
||||
yum remove sendmail
|
||||
|
||||
Postfix contains **two configuration files main.cf and master.cf**, you will need to modify main.cf for basic configuration. Also, postfix parameters can be defined like shell variables and can be used with a dollar sign preceding them. They do not need to be defined before they are used. Postfix will only look for a parameter when it is needed at rumtime.
|
||||
|
||||
### Configuring postfix ###
|
||||
|
||||
vim /etc/postfix/main.cf
|
||||
|
||||
Uncomment the lines below
|
||||
|
||||
#Add the hostname of your machine
|
||||
myhostname = yourhostname.com
|
||||
|
||||
#From Domain to be used when mail is sent from this linux machine
|
||||
myorigin = $myhostname
|
||||
|
||||
#The network interface to receive mail on, I prefer localhost as I only want emails from this system to be delivered
|
||||
inet_interfaces = localhost
|
||||
|
||||
# The protocol to use when postfix will make or accept a connection. You can use “all” if you want to enable IPv6 support
|
||||
inet_protocols = ipv4
|
||||
|
||||
|
||||
#Domains to receive email for
|
||||
mydestination = $myhostname, localhost.$mydomain, localhost
|
||||
|
||||
#Only forward emails for the local machine and not machines on the network.
|
||||
mynetworks_style = host
|
||||
|
||||
Start postfix
|
||||
|
||||
service postfix start
|
||||
|
||||
This basic postfix configuration should enable your machine to send emails. You can verify the same by sending an email and checking “maillog” log file.
|
||||
|
||||
echo test mail | mail -s "test" leo@techarena51.com && sudo tail -f /var/log/maillog
|
||||
|
||||
#Logs should output the following
|
||||
Aug 25 14:16:21 vps postfix/smtp[32622]: E6A372DC065D: to=, relay=smtp.mailserver.org[50.56.21.176], delay=0.8, delays=0.1/0/0.43/0.27, dsn=2.0.0, status=sent (250 Great success)
|
||||
Aug 25 14:16:21 vps postfix/qmgr[5355]: E6A372DC065D: removed
|
||||
|
||||
But this configuration is not enough, as your emails will mostly end up in spam. You will need to add an SPF, PTR and DKIM record. You may still get emails delivered in spam due to your IP address being blacklisted, mostly due to a previous abuse of your vps.
|
||||
|
||||
An alternative or a better way would be to use a third party provider like Gmail or even Mailgun.
|
||||
I use Mailgun as they give you 10,000 emails free every month as compared to Gmails 100 or so per day.
|
||||
|
||||
In “/etc/postfix/main.cf” you will need to add “smtp.mailgun.com” as your “relayhost”, enable “SASL” authentication so postfix can connect and authenticate to the remote Mailgun server.
|
||||
|
||||
Add or uncomment the following lines.
|
||||
|
||||
relayhost = [smtp.mailgun.org]
|
||||
smtp_sasl_auth_enable = yes
|
||||
smtp_sasl_password_maps=static:your_username:your_password
|
||||
smtp_sasl_security_options=noanonymous
|
||||
|
||||
Postfix does not implement “SASL” authentication by itself, hence you will need to install “cyrus-sasl-plain”.
|
||||
|
||||
sudo yum install cyrus-sasl-plain
|
||||
|
||||
If you do not install this package on Centos 6 then you will get an error “SASL authentication failed; cannot authenticate to server smtp.mailgun.org[50.56.21.176]: no mechanism available)”
|
||||
|
||||
Restart postfix
|
||||
|
||||
sudo service postfix restart
|
||||
|
||||
### Securing Postfix with TLS ###
|
||||
|
||||
Postfix supports TLS a successor to SSL which allows you to encrypt data using key based authentication. I recommend reading http://www.postfix.org/TLS_README.html on how tls works with postfix.
|
||||
|
||||
In order to use TLS you will need to generate a private key and a certificate which is signed by a Certificate Authority. In this example, I will be using a Self Signed Certificate.
|
||||
|
||||
sudo yum install mod_ssl openssl
|
||||
# Generate private key
|
||||
openssl genrsa -out smtp.key 2048
|
||||
|
||||
# Generate CSR
|
||||
openssl req -new -key smtp.key -out smtp.csr
|
||||
|
||||
# Generate Self Signed Key
|
||||
openssl x509 -req -days 365 -in smtp.csr -signkey smtp.key -out smtp.crt
|
||||
|
||||
# Copy the files to the correct locations
|
||||
cp smtp.crt /etc/pki/tls/certs
|
||||
cp smtp.key /etc/pki/tls/private/smtp.key
|
||||
cp smtp.csr /etc/pki/tls/private/smtp.csr
|
||||
|
||||
Open the postfix configuration files and add the following parameteres
|
||||
|
||||
sudo vim /etc/postfix/main.cf
|
||||
|
||||
smtp_tls_security_level = may
|
||||
smtpd_tls_security_level = may
|
||||
smtp_tls_note_starttls_offer = yes
|
||||
|
||||
smtpd_tls_key_file = /etc/pki/tls/private/smtp.key
|
||||
smtpd_tls_cert_file = /etc/pki/tls/certs
|
||||
smtp_tls_CAfile = /etc/ssl/certs/ca.crt
|
||||
smtp_tls_loglevel = 1
|
||||
|
||||
Security level “may” means announce STARTTLS support to remote SMTP clients, but clients do no need to use encryption., I have used it here as per [mailgun docs][1], but you can use “encrypt” if you want to force TLS encryption.
|
||||
|
||||
service postfix restart
|
||||
#Send a test email
|
||||
echo test mail | mail -s "test" test@yourdomain.com && sudo tail -f /var/log/maillog
|
||||
|
||||
You should see the below message
|
||||
|
||||
Aug 21 00:00:06 vps postfix/smtp[4997]: setting up TLS connection to smtp.mailgun.org[50.56.21.176]:587
|
||||
Aug 21 00:00:06 vps postfix/smtp[4997]: Trusted TLS connection established to smtp.mailgun.org[50.56.21.176]:587: TLSv1.2 with cipher AES256-GCM-SHA384 (256/256 bits)
|
||||
|
||||
You can comment out the below parameter once everything is successful.
|
||||
“smtp_tls_loglevel = 1”
|
||||
|
||||
For Troubleshooting I recommend you read [Postfix tips and Troubleshooting Commands][2](注:此文在同一个原文更新中)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://techarena51.com/index.php/configure-secure-postfix-email-server/
|
||||
|
||||
作者:[Leo G][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://techarena51.com/
|
||||
[1]:http://documentation.mailgun.com/user_manual.html#smtp-relay
|
||||
[2]:http://techarena51.com/index.php/postfix-configuration-and-explanation-of-parameters/
|
||||
@ -0,0 +1,228 @@
|
||||
How to install Xen hypervisor on unused old hardware
|
||||
================================================================================
|
||||
Xen is a bare metal hypervisor, meaning that you must prepare a bare machine to install and run Xen. KVM is a little different - you can add it to any machine already running Linux. This tutorial describes how to install and configure Xen hypervisor on unused hardware.
|
||||
|
||||
This procedure uses Debian Jessie (their testing distribution) as the host OS (also known as [Dom0][1]). Jessie is not the only choice - Xen support is built into the Linux kernel, and [plenty of Linux distributions][2] include one of these Xen-enabled kernels.
|
||||
|
||||
### Find unused hardware ###
|
||||
|
||||
As a start, find a suitable workstation which can be wiped out, such as an old laptop or desktop. Older hardware may not be good for gaming, but it is good enough for a host OS and a couple of guests. A PC with these specifications works fine.
|
||||
|
||||
- 1 CPU with 2 cores (64-bit)
|
||||
- 4GB memory
|
||||
- 80GB hard disk
|
||||
- ability to boot from CD, DVD or USB
|
||||
- a network interface
|
||||
|
||||
Note that the CPU must be a 64-bit processor since Debian dropped support for 32-bit Xen packages. If you don't have spare hardware, you could invest in an old machine. 2010's $1000 flagship laptop is today's $100 bargain. A second-hand laptop from eBay and a memory upgrade will do fine.
|
||||
|
||||
### Burn a bootable CD/USB ###
|
||||
|
||||
Download the ISO image for Debian Jessie. The small netinst image available from the [official Debian website][3] works fine.
|
||||
|
||||
$ wget http://cdimage.debian.org/cdimage/jessie_di_beta_2/amd64/iso-cd/debian-jessie-DI-b2-amd64-netinst.iso
|
||||
|
||||
Next, identify the device name assigned to your [CD/DVD][4] or [USB drive][5] (e.g., /dev/sdc).
|
||||
|
||||
Burn the downloaded ISO image into a bootable CD or a USB using dd command. Replace /dev/sdc with the device name you identified above.
|
||||
|
||||
$ sudo dd if=debian-jessie-DI-b2-amd64-netinst.iso of=/dev/sdc
|
||||
|
||||
### Start the installation ###
|
||||
|
||||
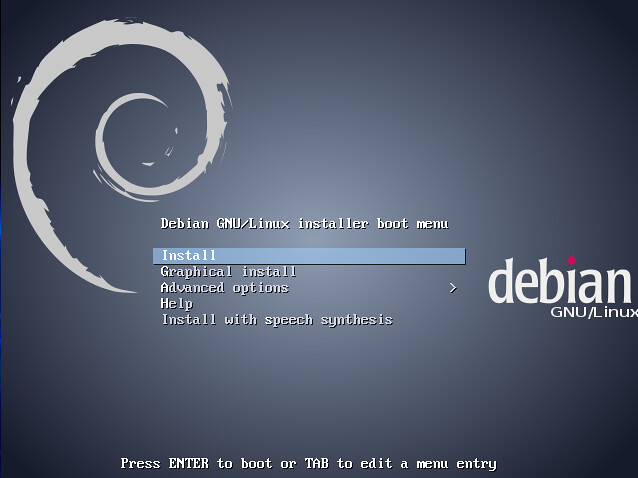
To start the installation, boot with the Debian installer CD/USB.
|
||||
|
||||
It's a good idea to use a wired connection, not WiFi. If the WiFi won't connect because firmware or driver software is missing, you won't get very far.
|
||||
|
||||
|
||||
|
||||
### Partition the disk ###
|
||||
|
||||
This setup uses four primary disk partitions. Automatic OS installers usually set up an extended partition that contains logical partitions. Set up the four partitions like this.
|
||||
|
||||
- sda1 mount on /boot, 200MB
|
||||
- sda2 /, 20GB, Ubuntu uses 4GB
|
||||
- sda3 swap, 6GB (4GB of memory x 1.5 = 6)
|
||||
- sda4 reserved for LVM, not mounted, all the rest of the disk space
|
||||
|
||||
### Install the base system ###
|
||||
|
||||
It's a good idea to make the install as simple and short as possible. A basic working system can always be added to later. Debian's APT (Advanced Package Tool) makes adding software easy. Installing Debian on a workstation can cause pretty obscure time-wasting issues. Perhaps a graphics driver does not agree with the kernel or maybe the old CD-ROM drive only works intermittently.
|
||||
|
||||
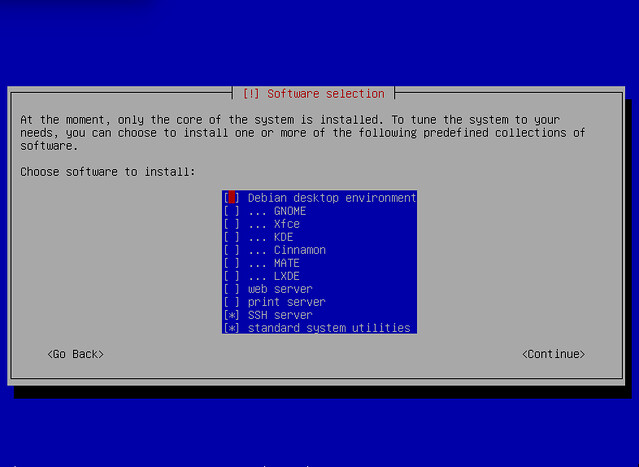
When it comes to choosing what to install, do install an SSH server and don't install a desktop like Gnome.
|
||||
|
||||
|
||||
|
||||
A graphical desktop requires hundreds of package installs - it's a lot of extra work that can be done later. If you run into problems, waiting for that desktop install is a waste of time. Also, without desktop component, the system boot will be much quicker - seconds rather than minutes. This procedure requires a few reboots, so that's a handy time-saver.
|
||||
|
||||
An SSH server lets you configure the workstation from another computer. This allows you to avoid some of the problems with old hardware - perhaps the old machine's keyboard is missing keys, the LCD screen has dead pixels or the trackpad is unresponsive etc.
|
||||
|
||||
### Add LVM (Logical Volume Manager) ###
|
||||
|
||||
Install the LVM tools as the root.
|
||||
|
||||
# apt-get update
|
||||
# apt-get install lvm2
|
||||
|
||||
Pick a physical volume to work with.
|
||||
|
||||
# pvcreate /dev/sda4
|
||||
|
||||
Create a volume group.
|
||||
|
||||
# vgcreate vg0 /dev/sda4
|
||||
|
||||
You don't need to create a logical volume. If you want to test LVM works, create a volume then delete it.
|
||||
|
||||
# lvcreate -nmytempvol -L10G vg0
|
||||
# lvremove /dev/vg0/mytempvol
|
||||
|
||||
Check LVM status.
|
||||
|
||||
# pvs (to view information about physical volumes)
|
||||
# vgs (to view information about volume groups)
|
||||
# lvs (to view information about logical volumes)
|
||||
|
||||
### Add a Linux Ethernet bridge ###
|
||||
|
||||
We are going to set up a Linux bridge so that all Xen's guest domains can be connected to, and communicate through the bridge.
|
||||
|
||||
Install the bridge tools.
|
||||
|
||||
# apt-get install bridge-utils
|
||||
|
||||
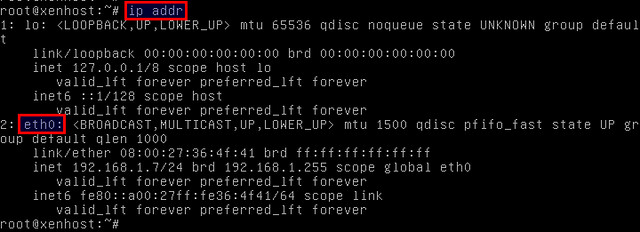
See what interfaces are configured.
|
||||
|
||||
# ip addr
|
||||
|
||||
|
||||
|
||||
In this example, we have one primary interface assigned eth0. We are going to add eth0 to the Linux bridge by editing the network configuration file (/etc/network/interfaces).
|
||||
|
||||
Before making any change, back up the network configuration file to keep the original working configuration safe.
|
||||
|
||||
# cd /etc/network/
|
||||
# cp interfaces interfaces.backup
|
||||
# vi /etc/network/interfaces
|
||||
|
||||
The file contents look something like this.
|
||||
|
||||
auto lo
|
||||
iface lo inet loopback
|
||||
|
||||
allow-hotplug eth0
|
||||
iface eth0 inet dhcp
|
||||
|
||||
Change the file to this.
|
||||
|
||||
auto lo
|
||||
iface lo inet loopback
|
||||
|
||||
auto eth0
|
||||
iface eth0 inet manual
|
||||
|
||||
auto xenbr0
|
||||
iface xenbr0 inet dhcp
|
||||
bridge_ports eth0
|
||||
|
||||
Activate the network configuration change:
|
||||
|
||||
# systemctl restart networking
|
||||
|
||||
### Verify networking settings ###
|
||||
|
||||
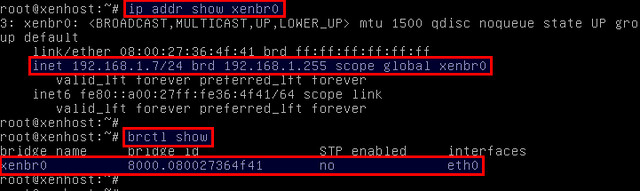
Verify that a Linux bridge xenbr0 is created successfully.
|
||||
|
||||
# ip addr show xenbr0
|
||||
|
||||
Also check that the primary interface eth0 is successfully added to the bridge.
|
||||
|
||||
# brctl show
|
||||
|
||||
|
||||
|
||||
You now have a working machine with Jessie installed. Xen is not yet installed at this point. Let's proceed to install Xen next.
|
||||
|
||||
### Install the Xen hypervisor ###
|
||||
|
||||
Install Xen and QEMU packages, and update the GRUB bootloader.
|
||||
|
||||
# apt-get install xen-linux-system
|
||||
|
||||
Reboot.
|
||||
|
||||
When the GRUB screen appears, you can see extra booting options listed.
|
||||
|
||||
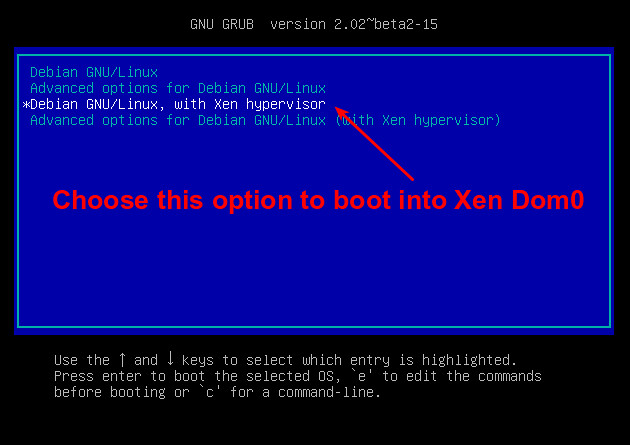
|
||||
|
||||
The first option will boot automatically in five seconds (see the GRUB_TIMEOUT line in /etc/default/grub), so this is not the time to get a coffee.
|
||||
|
||||
Press the down arrow to highlight the option "Debian GNU/Linux, with Xen hypervisor", and press RETURN. Many lines of information appear, followed by the usual login screen.
|
||||
|
||||
### Check Xen works ###
|
||||
|
||||
Xen hypervisor comes with Xen management command-line tool called xl, which can be used to create and manage Xen guest domains. Let's use xl command to check if Xen is successfully installed.
|
||||
|
||||
Log in as root, and run:
|
||||
|
||||
# xl info
|
||||
|
||||
which will display various information about Xen host.
|
||||
|
||||
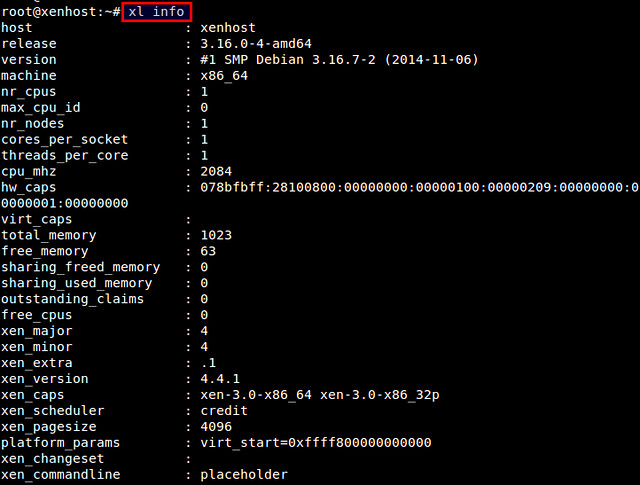
|
||||
|
||||
To see a list of existing Xen domains:
|
||||
|
||||
# xl list
|
||||
|
||||
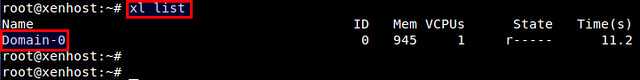
|
||||
|
||||
A little table of domains appears. Without any Xen guest domain created, the only entry should be Domain-0, your Debian installation.
|
||||
|
||||
### Change the boot order ###
|
||||
|
||||
When you reach this point, the Xen install is complete. There is one more thing to fix - the default boot will not load Xen. GRUB chooses the first item in the boot menu (Debian GNU/Linux), not the third (Debian GNU/Linux, with Xen hypervisor).
|
||||
|
||||
The default option in the boot menu is defined in the grub configuration file /boot/grub/grub.cfg. To change the default option, don't edit that file, but edit /etc/default/grub instead. A little helper program called grub-mkconfig reads in this default configuration file and all the templates in /etc/grub.d/, then writes the grub.cfg file.
|
||||
|
||||
Edit Debian's configuration file for grub-mkconfig.
|
||||
|
||||
# vi /etc/default/grub
|
||||
|
||||
Change the line:
|
||||
|
||||
GRUB_DEFAULT=0
|
||||
|
||||
to
|
||||
|
||||
GRUB_DEFAULT='Debian GNU/Linux, with Xen hypervisor'
|
||||
|
||||
Then update the grub configuration file.
|
||||
|
||||
# grub-mkconfig -o /boot/grub/grub.cfg
|
||||
|
||||
Finally reboot. After a few seconds, the grub boot menu appears. Check that the third option "Debian GNU/Linux, with Xen hypervisor" is highlighted automatically.
|
||||
|
||||
### Final note ###
|
||||
|
||||
If you use this machine as your hands-on workstation, install a graphical desktop. The Debian library includes a few [desktop environments][6]. If you want a graphical desktop that includes everything and the kitchen sink, go for Gnome. If graphics just get in your way, try Awesome.
|
||||
|
||||
Note that the Debian Jessie default environment Gnome comes with a huge amount of extra applications including the productivity suite LibreOffice, the Iceweasel web browser and the Rhythmbox music player. The install command "apt-get install gnome" adds 1,000 packages and takes up nearly 2GB of disk space. Running this heavyweight desktop takes up 1GB of memory.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/install-xen-hypervisor.html
|
||||
|
||||
作者:[Nick Hardiman][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nick
|
||||
[1]:http://wiki.xen.org/wiki/Dom0
|
||||
[2]:http://wiki.xen.org/wiki/Dom0_Kernels_for_Xen
|
||||
[3]:https://www.debian.org/devel/debian-installer/
|
||||
[4]:http://ask.xmodulo.com/detect-dvd-writer-device-name-writing-speed-command-line-linux.html
|
||||
[5]:http://ask.xmodulo.com/find-device-name-usb-drive-linux.html
|
||||
[6]:https://wiki.debian.org/DesktopEnvironment
|
||||
@ -0,0 +1,87 @@
|
||||
How to visualize memory usage on Linux
|
||||
================================================================================
|
||||
Lack of sufficient physical memory can significantly hamper the performance of Linux desktop and server environments. When your desktop is sluggish, one of the first things to do is to free up RAMs. Memory usage is even more critical in multi-user shared hosting or mission-critical server environments, where different users or application threads constantly compete for more memory.
|
||||
|
||||
When it comes to monitoring any type of system resources such as memory or CPUs, visualization is an effective means to help understand quickly how they are consumed by different processes and users. In this tutorial, I describe **how to visualize memory usage in Linux environment** using a command-line tool called [smem][1].
|
||||
|
||||
### Physical Memory Usage: RSS vs. PSS vs. USS ###
|
||||
|
||||
In the presence of virtual memory abstraction, accurately quantifying physical memory usage of a process is actually not straightforward. The virtual memory size of a process is not meaningful because it does not tell how much of it is actually allocated physical memory.
|
||||
|
||||
**Resident set size (RSS)**, reported by top command, is one popular metric which captures what portion of a process' reported memory is residing in RAM. However, aggregating RSS of existing processes can easily overestimate the overall physical memory usage of the Linux system because the same physical memory page can be shared by different processes. **Proportional set size (PSS)** is a more accurate measurement of effective memory usage of Linux processes since PSS properly discounts the memory page shared by more than one process. **Unique set size (USS)** of a process is a subset of the process' PSS, which is not shared by any other processes.
|
||||
|
||||
### Install Smem on Linux ###
|
||||
|
||||
The command-line tool smem can generate a variety of reports related to memory PSS/USS usage by pulling information from /proc. It comes with built-in graphical chart generation capabilities, so one can easily visualize overall memory consumption status.
|
||||
|
||||
#### Install Smem on Debian, Ubuntu or Linux Mint ####
|
||||
|
||||
$ sudo apt-get install smem
|
||||
|
||||
#### Install Smem on Fedora or CentOS/RHEL ####
|
||||
|
||||
On CentOS/RHEL, you need to [enable][2] EPEL repository first.
|
||||
|
||||
$ sudo yum install smem python-matplotlib
|
||||
|
||||
### Check Memory Usage with Smem ###
|
||||
|
||||
When you run smem as a unprivileged user, it will report physical memory usage of every process launched by the current user, in an increasing order of PSS.
|
||||
|
||||
$ smem
|
||||
|
||||
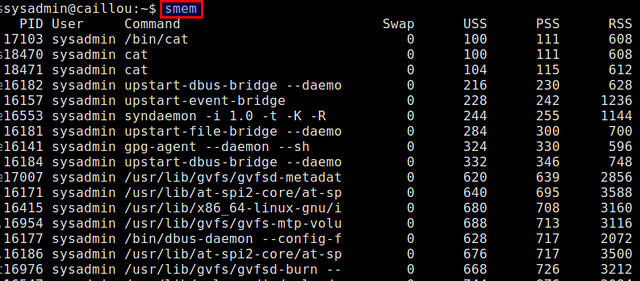
|
||||
|
||||
If you want to check the overall system memory usage for all users, run smem as the root.
|
||||
|
||||
$ sudo smem
|
||||
|
||||
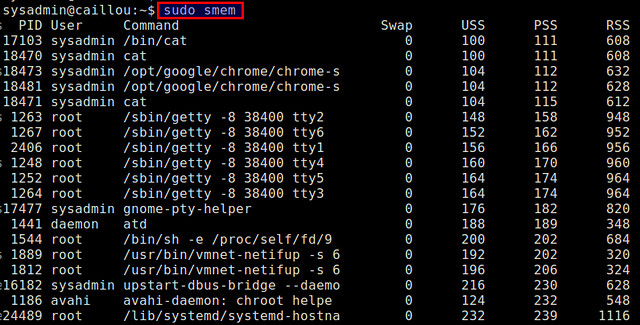
|
||||
|
||||
To view per-user memory usage:
|
||||
|
||||
$ sudo smem -u
|
||||
|
||||
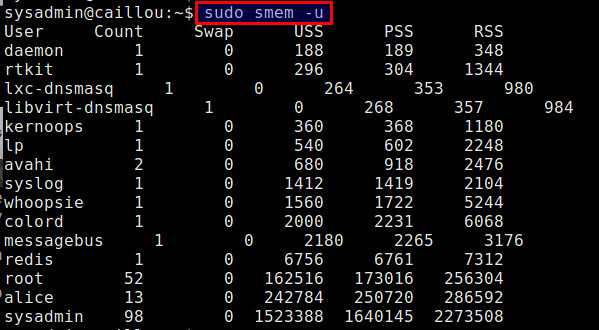
|
||||
|
||||
smem allows you to filter memory usage results based on mapping, processes or users in the following format:
|
||||
|
||||
- -M <mapping-filtering-regular-expression>
|
||||
- -P <process-filtering-regular-expression>
|
||||
- -U <user-filtering-regular-expression>
|
||||
|
||||
For a complete usage of smem, refer to its man page.
|
||||
|
||||
### Visualize Memory Usage with Smem ###
|
||||
|
||||
Visualized reports are often easier to read to identify the memory hogs of your system quickly. smem supports two kinds of graphical reports for memory usage visualization: bar and pie graphs.
|
||||
|
||||
Here are examples of memory usage visualization.
|
||||
|
||||
The following command will generate a bar graph that visualizes the PSS/USS memory usage of a user alice.
|
||||
|
||||
$ sudo smem --bar name -c "pss uss" -U alice
|
||||
|
||||
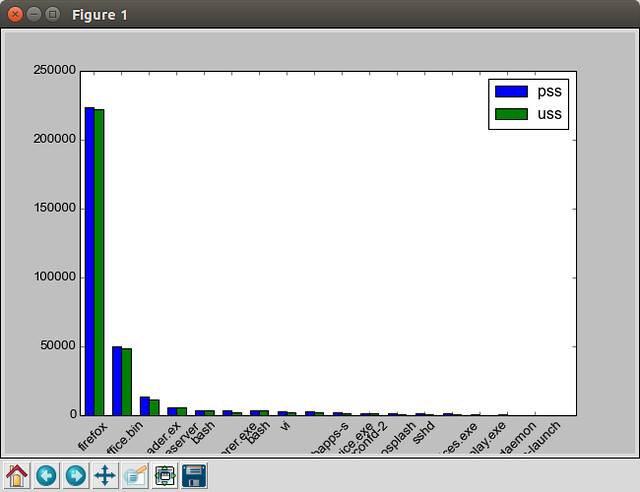
|
||||
|
||||
The next command will plot a pie graph of the overall PSS memory usage of different processes.
|
||||
|
||||
$ sudo smem --pie name -c "pss"
|
||||
|
||||
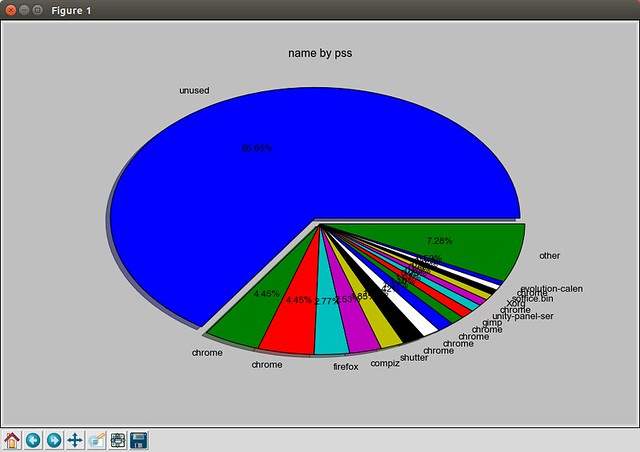
|
||||
|
||||
As a summary, smem is a simple and effective memory analysis tool that comes in handy in various circumstances. Using its formatted output, you can run smem to identify any memory issues and take an action in an automatic fashion. If you know of any good memory monitoring tool, share it in the comment.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/visualize-memory-usage-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://www.selenic.com/smem/
|
||||
[2]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
|
||||
@ -0,0 +1,57 @@
|
||||
Vic020
|
||||
|
||||
Postfix tips and Troubleshooting Commands
|
||||
================================================================================
|
||||
Here’s a list of stuff I user everyday and other email admins will also be using, Let me know if I missed anything
|
||||
|
||||
List/Print current mail queue
|
||||
|
||||
# postqueue –p
|
||||
|
||||
# mailq
|
||||
|
||||
If it’s a huge que, you can pipe it with tail
|
||||
|
||||
# mailq | tail
|
||||
|
||||
Flush the queue
|
||||
|
||||
# postqueue -f
|
||||
|
||||
Schedule immediate delivery of all mail that is queued for the named as domain.come.
|
||||
|
||||
# postqueue -s domain.com
|
||||
|
||||
TO delete all queue
|
||||
|
||||
# postsuper -d ALL
|
||||
|
||||
To delete a particular message
|
||||
|
||||
# postsuper -d messageid
|
||||
|
||||
Reque the mail or resend particular mail
|
||||
|
||||
#postfix -r msgid
|
||||
|
||||
To find mail version
|
||||
|
||||
#postconf -d mail_version
|
||||
mail_version = 2.6.6
|
||||
|
||||
You can also follow the steps in the link below which is the most simple and well explained documentation available with regards to Configuring postfix.
|
||||
|
||||
[Postfix Configuration - ][1]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://techarena51.com/index.php/postfix-configuration-and-explanation-of-parameters/
|
||||
|
||||
作者:[Leo G][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://techarena51.com/
|
||||
[1]:http://www.apricot.net/apricot2004/doc/cd_content/24th%20February%202004/04%20-%20TTF%20Anti%20Spam%20&%20Anti%20Net%20Abuse%20-%20Suresh%20Ramasubramaniam/Devdas%20Bhagat.pdf
|
||||
@ -0,0 +1,57 @@
|
||||
修复了60个bug的LibreOffice 4.3.4正式发布,4.4版本开发工作有序进行中
|
||||
================================================================================
|
||||

|
||||
|
||||
**[上两周][1], 文档基金会带着它的开源LibreOffice生产力套件的又一个次版本回来了。**
|
||||
|
||||
LibreOffice 4.3.4,新系列中的第四个次版本,是单独由修复好的bug构成的一个版本,不出乎意料地以点版本形式发行。
|
||||
|
||||
除了增加了即视感,基金会所说的在developers’ butterfly net上被揪出来并且修复的bug数量大概有:60个左右。
|
||||
|
||||
- 排序操作现在还是默认为旧的样式(Calc)
|
||||
- 在预览后恢复焦点窗口(Impress)
|
||||
- 图表向导对话框不再是‘切除’式
|
||||
- 修复了记录改变时的字数统计问题 (Writer)
|
||||
- 各种各样的RTF修复,包括图像边框导入(Writer)
|
||||
|
||||
完整列表可以在 [LibreOffice Wiki 页面][2]查看。
|
||||
|
||||
### 下载 ###
|
||||
|
||||
许多家伙有完整的LibreOffice安装程序但是从来没用过它。如果你是其中一份子,你就当做没看到。
|
||||
|
||||
如果你喜欢升级,你可以在官方网站上找到所有相关的下载链接。
|
||||
|
||||
- [下载LibreOffice 4.3.4][3]
|
||||
|
||||
### 预测一下LibreOffice 4.4 ###
|
||||
|
||||

|
||||
|
||||
来自LibreOffice 4.4的信息栏
|
||||
|
||||
LibreOffice 4.4应该给予大家多一点希望。
|
||||
|
||||
[维基上讲述了][4]正在进行中的不间断大范围GUI调整,包括一个新的颜色选择器,重新设计的段落行距选择器和一个在凸显部位表示该文件是否为只读模式的信息栏。
|
||||
|
||||
虽然以上大规模的界面变动我知道一些桌面社区的抗议声不断,但是他们还是朝着正确的方向稳步前进。
|
||||
|
||||
要记住,在一些必要情况下,LibreOffice对于企业和机构来说是一款非常重要的软件。在外观和布局上有任何引人注目的修改都会引发一串连锁效应。
|
||||
|
||||
感谢Tim W!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/11/libreoffice-4-3-4-arrives-bundle-bug-fixes
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[ZTinoZ](https://github.com/ZTinoZ)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.omgubuntu.co.uk/2014/10/libreoffice-4-3-3-released-62-bug-fixes
|
||||
[2]:https://wiki.documentfoundation.org/Releases/4.3.4/RC1
|
||||
[3]:http://www.libreoffice.org/download/libreoffice-fresh/
|
||||
[4]:https://wiki.documentfoundation.org/ReleaseNotes/4.4#GUI
|
||||
@ -0,0 +1,71 @@
|
||||
如何在Linux上安装一个开源VPN服务器
|
||||
================================================================================
|
||||

|
||||
|
||||
我上网时最担心的一件事情是,我该如何确保我的数据安全和隐私。在搜索答案的过程中,我找到了很多保持匿名的方法,比如使用代理网站。但是使用第三方的服务不能完全保证。我需要的是有一款软件可以我自己安装并运行,那样我就能确保只有我才能访问数据。
|
||||
|
||||
这款软件叫什么呢?
|
||||
|
||||
它叫VPN服务,就是虚拟隐私网络的简称。它允许访问时通过SSL加密你的数据。因为是加密的连接,所以你的ISP不能看到你的浏览信息。
|
||||
|
||||
在本篇Linux教程中,我会在CentOS 7上安装一个OpenVPN服务。OpenVPN很容易使用,开源且拥有基于社区的支持。它的客户端有Windows、Android和Mac。
|
||||
|
||||
### 第一步: 在你的Linux机器或者 [VPS][1]上安装OpenVPN服务 ###
|
||||
|
||||
从https://openvpn.net/index.php/access-server/download-openvpn-as-sw.html下载安装包,Ubuntu用户也可以找到合适的安装包并安装。
|
||||
|
||||
[leo@vps ]$ cd /tmp
|
||||
[leo@vps tmp]$ wget http://swupdate.openvpn.org/as/openvpn-as-2.0.10-CentOS7.x86_64.rpm
|
||||
[leo@vps tmp]$ sudo rpm -Uvh openvpn-as-2.0.10-CentOS7.x86_64.rpm
|
||||
Preparing... ################################# [100%]
|
||||
Updating / installing...
|
||||
1:openvpn-as-0:2.0.10-CentOSrelease################################# [100%]
|
||||
The Access Server has been successfully installed in /usr/local/openvpn_as
|
||||
Configuration log file has been written to /usr/local/openvpn_as/init.log
|
||||
Please enter "passwd openvpn" to set the initial
|
||||
administrative password, then login as "openvpn" to continue
|
||||
configuration here: https://yourhostIP:943/admin
|
||||
To reconfigure manually, use the /usr/local/openvpn_as/bin/ovpn-init tool.
|
||||
|
||||
Access Server web UIs are available here:
|
||||
Admin UI: https://yourhostIP:943/admin
|
||||
Client UI: https://yourhostIP:943/
|
||||
|
||||
### 第二步: 为 OpenVPN 客户端设置密码 ###
|
||||
|
||||
[leo_g@vps ]$passwd openvpn
|
||||
|
||||
### 第三步: 通过管理URL https://yourhostIP:943/admin 登录并启动服务 ###
|
||||
|
||||

|
||||
|
||||
输入用户名 “openvpn” 和你先前设置的密码
|
||||
|
||||

|
||||
|
||||
### 第四步: 从客户端URL安装客户端 (它会给你一个选项下载安装程序) ###
|
||||
|
||||

|
||||
|
||||
你可以在[这里][3]看指导来了解如何在你的操作系统上安装。
|
||||
|
||||
### 第五步: 用你先前创建的用户名和密码连接你的服务器 ###
|
||||
|
||||

|
||||
|
||||
就是这样,你可以访问whatismyip.com来查看你的IP,应该已经是你的CentOS 7上的OpenVPN的地址了。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://techarena51.com/index.php/how-to-install-an-opensource-vpn-server-on-linux/
|
||||
|
||||
作者:[Leo G][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://techarena51.com/
|
||||
[1]:https://play.google.com/store/apps/details?id=net.openvpn.openvpn&hl=en
|
||||
[2]:http://supportinc.net/vps-hosting.php
|
||||
[3]:https://openvpn.net/index.php/access-server/docs/admin-guides-sp-859543150/howto-connect-client-configuration.html
|
||||
Loading…
Reference in New Issue
Block a user