mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-28 01:01:09 +08:00
20141017-2 选题
This commit is contained in:
parent
8640cdf9ab
commit
542f1c958d
@ -0,0 +1,147 @@
|
||||
How to verify the authenticity and integrity of a downloaded file on Linux
|
||||
================================================================================
|
||||
When you download a file (e.g., an installer, an ISO image, or a compressed archive) from the web, the file can be corrupted under a variety of error conditions, e.g., due to transmission errors on the wire, interrupted download, faulty storage hardware, file system errors, etc. Such failure cases aside, a file can also be deliberately tampered with by determined attackers during or before download. For example, an attacker with a compromised certificate authority could mount a man-in-the-middle (MITM) attack, tricking you into downloading a malware-ridden file from a bogus HTTPS website.
|
||||
|
||||
To protect yourself against these kinds of problems, it is often recommended that you verify the authenticity and integrity of a file when you download it from the web. Especially when you downloaded rather sensitive files (e.g., OS images, application binaries, executable installers, etc), blindly trusting downloaded files is not a good habit.
|
||||
|
||||
One quick and easy way to verify the integrity of a downloaded file is to use various checksum tools (e.g., md5sum, sha256sum, cksum) to compute and compare checksums (e.g., MD5, SHA or CRC). However, checksums are vulnerable to [collision attacks][1], and also cannot be used to verify the authenticity (i.e., owner) of a file.
|
||||
|
||||
If you would like to verify both authenticity (owner) and integrity (content) of a downloaded file, you need to rely on cryptographic signatures instead. In this tutorial, I am going to describe how to check file authenticity and integrity by using GnuPG (GNU Privacy Guard).
|
||||
|
||||
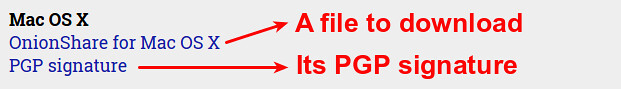
In this example, I am going to verify a disk image file available for download from https://onionshare.org. In this website, the publisher offers their official public key, as well as its fingerprint for key verification purpose.
|
||||
|
||||

|
||||
|
||||
As for a file to download, the publisher offers its corresponding PGP signature as well.
|
||||
|
||||
|
||||
|
||||
### Install GnuPG and Generate a Key Pair ###
|
||||
|
||||
Let's start by installing GnuPG on your Linux system.
|
||||
|
||||
On Debian, Ubuntu, and other Debian-derivatives:
|
||||
|
||||
$ sudo apt-get install gnupg
|
||||
|
||||
On Fedora, CentOS or RHEL:
|
||||
|
||||
$ sudo yum install gnupg
|
||||
|
||||
After installation, generate a key pair which you will be using in this tutorial.
|
||||
|
||||
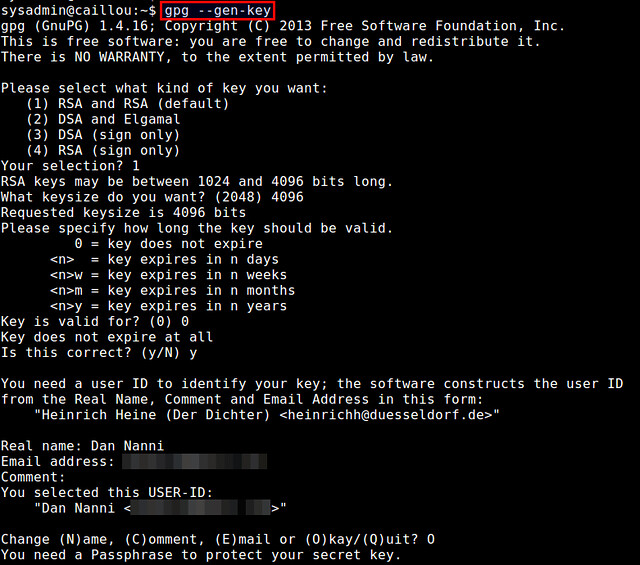
$ gpg --gen-key
|
||||
|
||||
|
||||
|
||||
During key generation, you will be asked to provide your name and email address, as well as a passphrase to protect your private key. You can also choose when the key pair will expire (no expiration by default). Depending on keysize you choose (between 1024 to 4096 bits), the key generation process can take a couple of minutes or more, as it requires collecting a sufficient amount of random data, which come from your desktop activities (e.g., keyboard typing, mouse movement, disk access).
|
||||
|
||||
After key generation is finished, a public and a private key will be stored in ~/.gnupg directory for use.
|
||||
|
||||

|
||||
|
||||
### Establish Trust with a File Owner ###
|
||||
|
||||
The first step in verifying a downloaded file is to establish trust with whoever is offering the file for download. For this purpose, we download the public key of a file owner, and verify that the owner of the public key is who he or she claims to be.
|
||||
|
||||
After downloading the public key of a file owner:
|
||||
|
||||
$ wget https://onionshare.org/signing-key.asc
|
||||
|
||||
go ahead and import the public key into your keyring with gpg command:
|
||||
|
||||
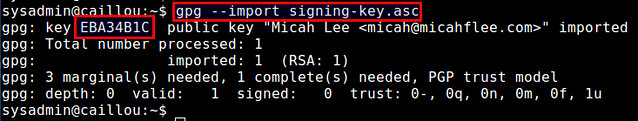
$ gpg --import signing-key.asc
|
||||
|
||||
|
||||
|
||||
Once the public key of the owner is imported, it will print out a key ID (e.g., "EBA34B1C") as shown above. Make a note of this key ID.
|
||||
|
||||
Now, check the fingerprint of the imported public key by running:
|
||||
|
||||
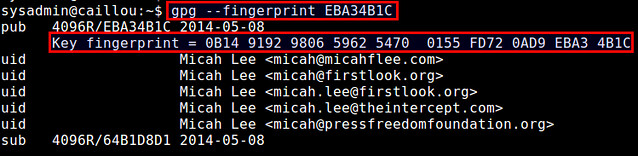
$ gpg --fingerprint EBA34B1C
|
||||
|
||||
|
||||
|
||||
You will see the fingerprint string of the key. Compare this string with the fingerprint displayed in the website. If they match, you may choose to trust the file owner's public key.
|
||||
|
||||
Once you decided to trust the public key, you can mark that so explicitly, by editing the key:
|
||||
|
||||
$ gpg --edit-key EBA34B1C
|
||||
|
||||
This command will show you GPG prompt:
|
||||
|
||||

|
||||
|
||||
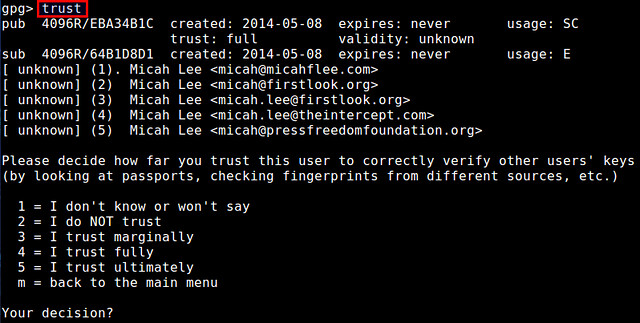
Type "trust" at GPG prompt, which will allow you to choose the trust level of this key from 1 to 5.
|
||||
|
||||
|
||||
|
||||
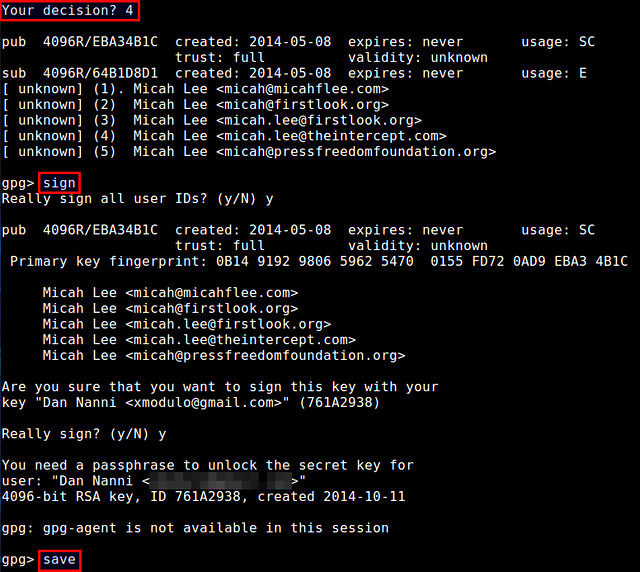
In this case, I decided to assign trust "4". After that, sign it with your own private key by typing "sign", and then finalize by typing "save" at GPG prompt:
|
||||
|
||||
|
||||
|
||||
Note that this way of explicitly assigning a trust to a public key is not required, and implicit trust by simply importing the key is often sufficient.
|
||||
|
||||
The implication of assigning a "full" trust to the key is that if another key X is signed with this fully trusted key, the key X will be also considered valid by you. In general, key validation relies on a sophisticated mechanism known as "[web of trust][2]".
|
||||
|
||||
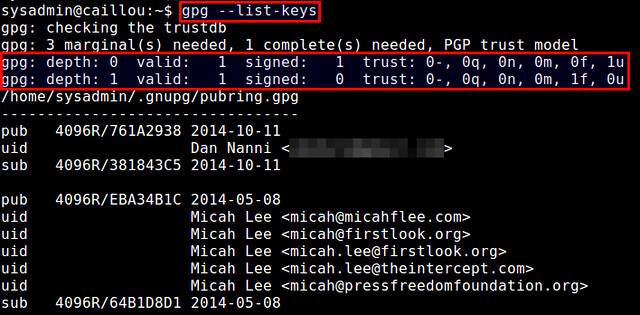
Coming back to the tutorial, now let's check a list of imported keys.
|
||||
|
||||
$ gpg --list-keys
|
||||
|
||||
|
||||
|
||||
You should see at least two keys: one key with depth 0 and ultimate trust ("1u"), which is your own key, and the other key with depth 1 and full trust ("1f"), which is the key signed by yourself earlier.
|
||||
|
||||
### Verify the Authenticity/Integrity of a File ###
|
||||
|
||||
Once you have established a trust relationship with a file owner using his/her public key, we are now ready to verify the authenticity and integrity of a file that you downloaded from the owner.
|
||||
|
||||
In our example, the file owner publishes a file and a corresponding PGP signature (*.asc) separately. The role of the signature is to certify and put a timestamp on the file.
|
||||
|
||||
A typical signature (*.asc) looks like the following.
|
||||
|
||||
-----BEGIN PGP SIGNATURE-----
|
||||
|
||||
iQIcBAABCgAGBQJUJGhsAAoJEP1yCtnro0sc1jUP/ixNY/lKdrcMIAUoqlWKNE8f
|
||||
sj4SFiwREMew76w66GASDF03fa5zPX6EsS2kucgx8ZsfEiSmN5T0y2P/aSaXwZqF
|
||||
kywZVEzirKtca5AJ4DBzu6qrt9GgSw6JBJVv1oBJCMNyO+eAj341paR3MudvnyQz
|
||||
H/N5tc4Qcilzy6M184opGIzy4ipEmMXfLHsd7WJpAyn+tO/z3uhh9NkNuygZpaFr
|
||||
olpSWPE8revdDJyfMfSmb3ZrFmhLn7FCEltOi+a7SluvrMclizfnbec9rgLJtjo0
|
||||
CPDZY7tsWmmL0DA3VvpMVqGvkg/Dyhpn2IIDrNaLAlvGQ5aovf+4tjad5IHvyaWx
|
||||
4Gds93G6Hqvv5RwGx7OR3hgt2o0Y+qFsVDxVnPxerGhXeJXHzSDwLQMpdj9IoSU
|
||||
Ae/53XXnxqSN6POZcwHiHvbsv0pdlg0Ea0dDAAN0ZeINNyZf1R0tLjWkcgpvGCtv
|
||||
qkJuYFF9W9cWHraPY2ov5Hs/JZzPcG0eVpnDdzfOOH1gDKADq9A5D2X5QJCulsh9
|
||||
WwU3X+E43OqIsoRzBucItD9HhZbEH7t8Q0xAqnAkgU3hriZp3dN4cnMfhM6I9hli
|
||||
EmpSpLKCceMexu2o9QgzGXVm+AGZJe4QkuwAhRIccp5JDMVny61UlKTasjy6co8h
|
||||
5GBhhYybPEFM+G1BODMd
|
||||
=c9wo
|
||||
-----END PGP SIGNATURE-----
|
||||
|
||||
Let's download both the file and its signature:
|
||||
|
||||
$ wget https://onionshare.org/files/0.6/OnionShare.dmg
|
||||
$ wget https://onionshare.org/files/0.6/OnionShare.dmg.asc
|
||||
|
||||
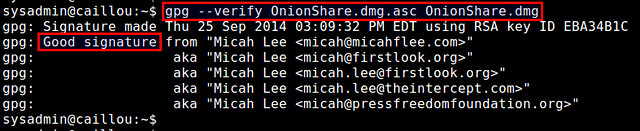
Now verify the PGP signature of the downloaded file.
|
||||
|
||||
$ gpg --verify OnionShare.dmg.asc OnionShare.dmg
|
||||
|
||||
|
||||
|
||||
If the output of the command contains "Good signature from <file owner>", the downloaded .dmg file has been successfully authenticated and verified. If the downloaded file were tampered with in any way after the signature has been generated, the verification would fail.
|
||||
|
||||
At this point you can be rest assured and trust the downloaded file.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/verify-authenticity-integrity-downloaded-file.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://en.wikipedia.org/wiki/Collision_attack
|
||||
[2]:https://www.gnupg.org/gph/en/manual/x334.html
|
||||
@ -0,0 +1,78 @@
|
||||
How to create a video DVD on Linux desktop
|
||||
================================================================================
|
||||
> **Question**: I want to create a video DVD from MP4 movie files. Is there an open-source DVD authoring tool that I can use to create a video DVD in the Linux desktop environment?
|
||||
|
||||
[DeVeDe][1] is an open-source (GPLv3) DVD authoring software that allows you to create video DVD, VCD, SVCD or DivX from any number of video files. DeVeDe relies on other software such as Mplayer, FFMpeg, MEncoder, DVDAuthor, VCDImager and MKisofs for format conversion. As such, it supports a variety of popular input video/audio formats (e.g., .mp4, .avi, .mpg, .mkv). You can choose between PAL and NTSC video formats, and can add menus or subtitles.
|
||||
|
||||
DeVeDe can come in handy if you want to preserve or give away a copy of your vacation, family or entertainment videos.
|
||||
|
||||
### Installing Devede ###
|
||||
|
||||
#### Debian, Ubuntu and derivatives: ####
|
||||
|
||||
# aptitude install devede
|
||||
|
||||
#### RHEL or CentOS: ####
|
||||
|
||||
Enable [EPEL][2] and [Nux Dextop][3] repositories, and then run:
|
||||
|
||||
# yum install devede
|
||||
|
||||
#### Fedora: ####
|
||||
|
||||
Enable [RPM Fusion][4] repository, and then run:
|
||||
|
||||
# yum install devede
|
||||
|
||||
### Creating a Video DVD with DeVeDe ###
|
||||
|
||||
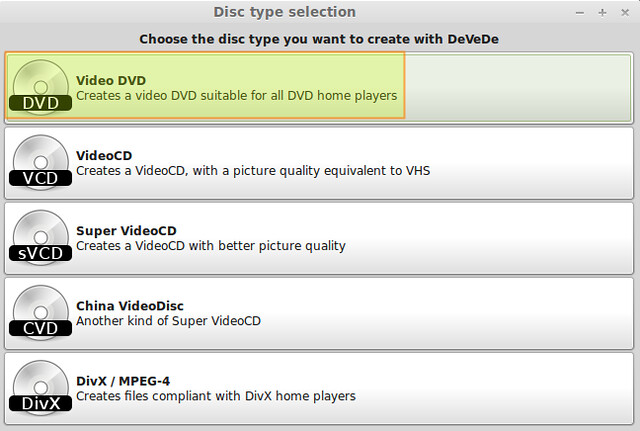
Launch DeVeDe and choose Video DVD from the menu.
|
||||
|
||||
|
||||
|
||||
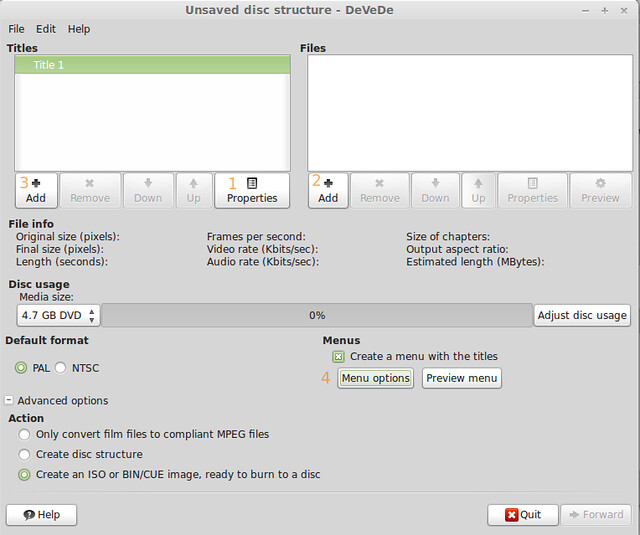
On the next screen, a title is automatically added to the collection by DeVeDe. You can edit its caption (1), add a file (2), and then add another title. Repeat this process as many times as needed.
|
||||
|
||||
|
||||
|
||||
The "Title properties" box allows you to choose between six actions to be performed when the current title ends. Click OK when you're done:
|
||||
|
||||

|
||||
|
||||
The "File properties" box is used to add a file to the current title. Click on the folder icon (upper right corner), and browse your computer for a desired file. You can also add a subtitle file by clicking the Add button right next to the subtitles box. Once you have selected a video file (and alternatively a subtitle file as well), click on OK at the bottom right corner.
|
||||
|
||||

|
||||
|
||||
You can add as many files as needed (only limited by the DVD capacity).
|
||||
|
||||

|
||||
|
||||
Next, edit the menu options. You can choose a background image and audio file to play while the main menu is displayed (which is as soon as the DVD is inserted into the player).
|
||||
|
||||

|
||||
|
||||
Finally, click on OK in the Menu options box to go back to the main disk structure, where you will need to click Forward in order to begin creating an .iso image with a video DVD structure.
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
When DeVeDe is done creating a video DVD, we will be presented with the following box:
|
||||
|
||||

|
||||
|
||||
Now we can burn the .iso file (which contains a video DVD) to a disk, using [growisofs][5] or another DVD burning tool.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/create-video-dvd-linux-desktop.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.rastersoft.com/programas/devede.html
|
||||
[2]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
|
||||
[3]:http://ask.xmodulo.com/enable-nux-dextop-repository-centos-rhel.html
|
||||
[4]:http://xmodulo.com/how-to-install-rpm-fusion-on-fedora.html
|
||||
[5]:http://ask.xmodulo.com/burn-iso-nrg-image-dvd-command-line.html
|
||||
@ -0,0 +1,65 @@
|
||||
Linux ss Tool to Identify Sockets / Network Connections with Examples
|
||||
================================================================================
|
||||
ss is part of the iproute2 (utilities for controlling TCP/IP networking and traffic) package. iproute2 is intended to replace an entire suite of standard Unix networking tools (often called "net-tools") that were previously used for the tasks of configuring network interfaces, routing tables, and managing the ARP table. The ss utility is used to dump socket statistics, it allows showing information similar to netstat and its able display more TCP and state information. It should also be faster as it gets its information directly from kernel space. The options used with the ss commands are very similar to netstat making it an easy replacement.
|
||||
|
||||
### Usage and common options ###
|
||||
|
||||
ss is very similar to netstat, by default it will show you a list of open non-listening TCP sockets that have established connection and you can shape the output with the following options:
|
||||
|
||||
- **-n** - Do now try to resolve service names.
|
||||
- **-r** - Try to resolve numeric address/ports.
|
||||
- **-a** - Display all sockets.
|
||||
- **-l** - Display listening sockets.
|
||||
- **-p** - Show process using socket.
|
||||
- **-s** - Print summary statistics.
|
||||
- **-t** - Display only TCP sockets.
|
||||
- **-u** - Display only UDP sockets.
|
||||
- **-d** - Display only DCCP sockets.
|
||||
- **-w** - Display only RAW sockets.
|
||||
- **-x** - Display only Unix domain sockets.
|
||||
- **-f FAMILY** - Display sockets of type FAMILY. Currently the following families are supported: unix, inet, inet6, link, netlink.
|
||||
- **-A QUERY** - List of socket tables to dump, separated by commas. The following identifiers are understood: all, inet, tcp, udp, raw, unix, packet, netlink, unix_dgram, unix_stream, packet_raw, packet_dgram.
|
||||
|
||||
### ss command examples ###
|
||||
|
||||
**1.** Display all open TCP ports and the process that uses them:
|
||||
|
||||
# ss -tnap
|
||||
|
||||

|
||||
|
||||
**2.** You can use -4 flag to display the IPv4 connections and the -6 flag to display IPv6 connections, for example:
|
||||
|
||||
# ss -tnap6
|
||||
|
||||

|
||||
|
||||
**3.** In the same manner, to show all open UDP ports you just have to replace t with n.
|
||||
|
||||
# ss -tnap
|
||||
|
||||

|
||||
|
||||
**4.** To print various useful statistics you can use the -s flag:
|
||||
|
||||
# ss -s
|
||||
|
||||

|
||||
|
||||
**5.** To check all connections in a different state you can use the -o flag, for example to display all the established connection:
|
||||
|
||||
# ss -tn -o state established -p
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/ss-sockets-network-connection/
|
||||
|
||||
作者:[Adrian Dinu][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/adriand/
|
||||
@ -0,0 +1,88 @@
|
||||
pidstat - Monitor and Find Statistics for Linux Procesess
|
||||
================================================================================
|
||||
The **pidstat** command is used for monitoring individual tasks currently being managed by the Linux kernel. It writes to standard output activities for every task managed by the Linux kernel. The pidstat command can also be used for monitoring the child processes of selected tasks. The interval parameter specifies the amount of time in seconds between each report. A value of 0 (or no parameters at all) indicates that tasks statistics are to be reported for the time since system startup (boot).
|
||||
|
||||
### How to Install pidstat ###
|
||||
|
||||
pidstat is part of the sysstat suite that contains various system performance tools for Linux, it's available on the repository of most Linux distributions.
|
||||
|
||||
To install it on Debian / Ubuntu Linux systems you can use the following command:
|
||||
|
||||
# apt-get install sysstat
|
||||
|
||||
If you are using CentOS / Fedora / RHEL Linux you can install the packages like this:
|
||||
|
||||
# yum install sysstat
|
||||
|
||||
### Using pidstat ###
|
||||
|
||||
Running pidstat without any argument is equivalent to specifying -p ALL but only active tasks (tasks with non-zero statistics values) will appear in the report.
|
||||
|
||||
# pidstat
|
||||
|
||||

|
||||
|
||||
In the output you can see:
|
||||
|
||||
- **PID** - The identification number of the task being monitored.
|
||||
- **%usr** - Percentage of CPU used by the task while executing at the user level (application), with or without nice priority. Note that this field does NOT include time spent running a virtual processor.
|
||||
- **%system** - Percentage of CPU used by the task while executing at the system level.
|
||||
- **%guest** - Percentage of CPU spent by the task in virtual machine (running a virtual processor).
|
||||
- **%CPU** - Total percentage of CPU time used by the task. In an SMP environment, the task's CPU usage will be divided by the total number of CPU's if option -I has been entered on the command line.
|
||||
- **CPU** - Processor number to which the task is attached.
|
||||
- **Command** - The command name of the task.
|
||||
|
||||
### I/O Statistics ###
|
||||
|
||||
We can use pidstat to get I/O statistics about a process using the -d flag. For example:
|
||||
|
||||
# pidstat -d -p 8472
|
||||
|
||||

|
||||
|
||||
The IO output will display a few new columns:
|
||||
|
||||
- **kB_rd/s** - Number of kilobytes the task has caused to be read from disk per second.
|
||||
- **kB_wr/s** - Number of kilobytes the task has caused, or shall cause to be written to disk per second.
|
||||
- **kB_ccwr/s** - Number of kilobytes whose writing to disk has been cancelled by the task.
|
||||
|
||||
### Page faults and memory usage ###
|
||||
|
||||
Using the -r flag you can get information about memory usage and page faults.
|
||||
|
||||

|
||||
|
||||
Important columns:
|
||||
|
||||
- **minflt/s** - Total number of minor faults the task has made per second, those which have not required loading a memory page from disk.
|
||||
- **majflt/s** - Total number of major faults the task has made per second, those which have required loading a memory page from disk.
|
||||
- **VSZ** - Virtual Size: The virtual memory usage of entire task in kilobytes.
|
||||
- **RSS** - Resident Set Size: The non-swapped physical memory used by the task in kilobytes.
|
||||
|
||||
### Examples ###
|
||||
|
||||
**1.** You can use pidstat to find a memory leek using the following command:
|
||||
|
||||
# pidstat -r 2 5
|
||||
|
||||
This will give you 5 reports, one every 2 seconds, about the current page faults statistics, it should be easy to spot the problem process.
|
||||
|
||||
**2.** To show all children of the mysql server you can use the following command
|
||||
|
||||
# pidstat -T CHILD -C mysql
|
||||
|
||||
**3.** To combine all statistics in a single report you can use:
|
||||
|
||||
# pidstat -urd -h
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/linux-pidstat-monitor-statistics-procesess/
|
||||
|
||||
作者:[Adrian Dinu][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/adriand/
|
||||
Loading…
Reference in New Issue
Block a user