mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-30 02:40:11 +08:00
commit
53a2c34532
sources/tech
20151012 Linux FAQs with Answers--How to change USB device permission permanently on Linux.md20151012 Linux FAQs with Answers--How to find information about built-in kernel modules on Linux.md20151012 Linux FAQs with Answers--How to force password change at the next login on Linux.md
translated/tech
@ -1,55 +0,0 @@
|
||||
translating----geekpi
|
||||
|
||||
Linux FAQs with Answers--How to change USB device permission permanently on Linux
|
||||
================================================================================
|
||||
> **Question**: I am trying to run gpsd on my Linux with a USB GPS receiver. However, I am getting the following errors from gpsd.
|
||||
>
|
||||
> gpsd[377]: gpsd:ERROR: read-only device open failed: Permission denied
|
||||
> gpsd[377]: gpsd:ERROR: /dev/ttyUSB0: device activation failed.
|
||||
> gpsd[377]: gpsd:ERROR: device open failed: Permission denied - retrying read-only
|
||||
>
|
||||
> Looks like gpsd does not have permission to access the USB device (/dev/ttyUSB0). How can I change its default permission mode permanently on Linux?
|
||||
|
||||
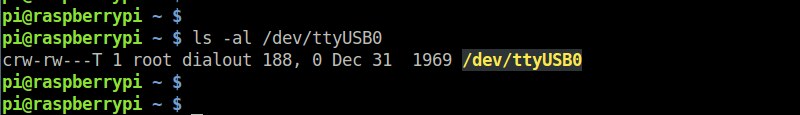
When you run a process that wants to read or write to a USB device, the user/group of the process must have appropriate permission to do so. Of course you can change the permission of your USB device manually with chmod command, but such manual permission change will be temporary. The USB device will revert to its default permission mode when you reboot your Linux machine.
|
||||
|
||||
|
||||
|
||||
As a permanent solution, you can create a udev-based USB permission rule which assigns any custom permission mode of your choice. Here is how to do it.
|
||||
|
||||
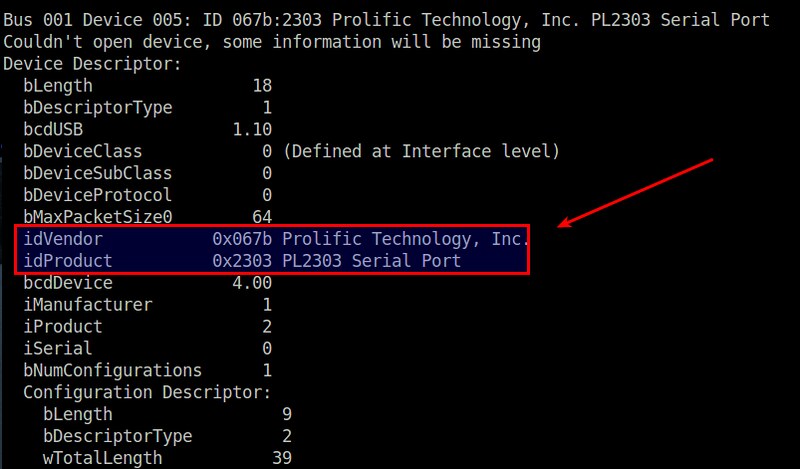
First, you need to identify the vendorID and productID of your USB device. For that, use lsusb command.
|
||||
|
||||
$ lsusb -vvv
|
||||
|
||||
|
||||
|
||||
From the lsusb output, find your USB device's entry, and look for "idVendor" and "idProduct" fields. In this example, we have idVendor (0x067b) and idProduct (0x2303).
|
||||
|
||||
Next, create a new udev rule as follows.
|
||||
|
||||
$ sudo vi /etc/udev/rules.d/50-myusb.rules
|
||||
|
||||
----------
|
||||
|
||||
SUBSYSTEMS=="usb", ATTRS{idVendor}=="067b", ATTRS{idProduct}=="2303", GROUP="users", MODE="0666"
|
||||
|
||||
Replace "idVendor" and "idProduct" values with your own. **MODE="0666"** indicates the preferred permission of the USB device.
|
||||
|
||||
Now reboot your machine or reload udev rules:
|
||||
|
||||
$ sudo udevadm control --reload
|
||||
|
||||
Then verify the permission of the USB device.
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/change-usb-device-permission-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
@ -1,55 +0,0 @@
|
||||
translating----geekpi
|
||||
|
||||
Linux FAQs with Answers--How to find information about built-in kernel modules on Linux
|
||||
================================================================================
|
||||
> **Question**: I would like to know what modules are built into the kernel of my Linux system, and what parameters are available in each module. Is there a way to get a list of all built-in kernel modules and device drivers, and find detailed information about them?
|
||||
|
||||
The modern Linux kernel has been growing significantly over the years to support a wide variety of hardware devices, file systems and networking functions. During this time, "loadable kernel modules (LKM)" came into being in order to keep the kernel from getting bloated, while flexibly extending its capabilities and hardware support under different environments, without having to rebuild it.
|
||||
|
||||
The Linux kernel shipped with the latest Linux distributions comes with relatively a small number of "built-in modules", while the rest of hardware-specific drivers or custom capabilities exist as "loadable modules" which you can selectively load or unload.
|
||||
|
||||
The built-in modules are statically compiled into the kernel. Unlike loadable kernel modules which can be dynamically loaded, unloaded, looked up or listed using commands like modprobe, insmod, rmmod, modinfo or lsmod, built-in kernel modules are always loaded in the kernel upon boot-up, and cannot be managed with these commands.
|
||||
|
||||
### Find a List of Built-in Kernel Modules ###
|
||||
|
||||
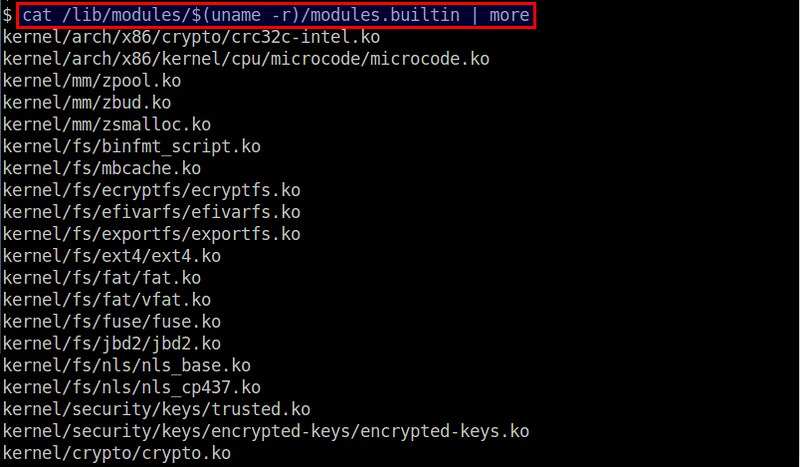
To get a list of all built-in modules, run the following command.
|
||||
|
||||
$ cat /lib/modules/$(uname -r)/modules.builtin
|
||||
|
||||
|
||||
|
||||
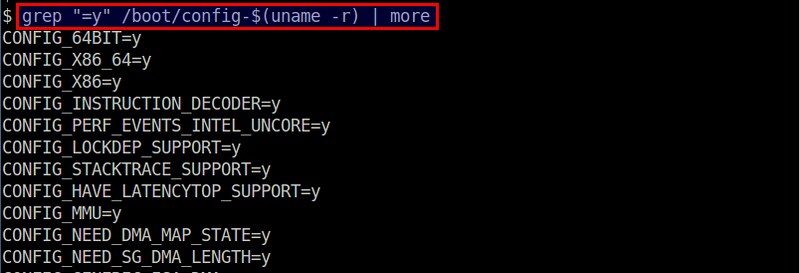
You can also get a hint on what modules are built-in by running:
|
||||
|
||||
|
||||
|
||||
### Find Parameters of Built-in Kernel Modules ###
|
||||
|
||||
Each kernel module, whether it's built-in or loadable, comes with a set of parameters. For loadable kernel modules, the modinfo command will show parameter information about them. However, this command will not work with built-in modules. You will simply get the following error.
|
||||
|
||||
modinfo: ERROR: Module XXXXXX not found.
|
||||
|
||||
If you want to check what parameters are available in a given built-in module, and what their values are, you can instead examine the content in **/sys/module** directory.
|
||||
|
||||
Under /sys/module directory, you will find sub-directories named after existing kernel modules (both built-in and loadable). Then in each module directory, there is a directory named "parameters", which lists all available parameters for the module.
|
||||
|
||||
For example, let's say you want to find out parameters of a built-in module called tcp_cubic (the default TCP implementation of the kernel). Then you can do this:
|
||||
|
||||
$ ls /sys/module/tcp_cubic/parameters
|
||||
|
||||
And check the value of each parameter by reading a corresponding file.
|
||||
|
||||
$ cat /sys/module/tcp_cubic/parameters/tcp_friendliness
|
||||
|
||||
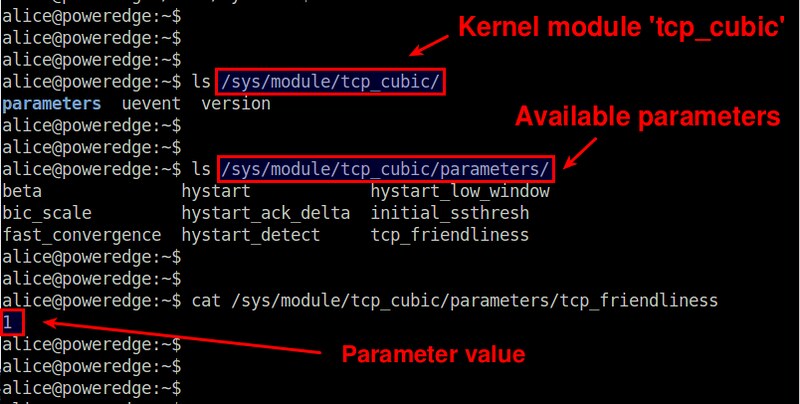
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/find-information-builtin-kernel-modules-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
@ -1,56 +0,0 @@
|
||||
translating----geekpi
|
||||
|
||||
Linux FAQs with Answers--How to force password change at the next login on Linux
|
||||
================================================================================
|
||||
> **Question**: I manage a Linux server for multiple users to share. I have just created a new user account with some default password, and I want the user to change the default password immediately after the first login. Is there a way to force a user to change his/her password at the next login?
|
||||
|
||||
In multi-user Linux environment, it's a standard practice to create user accounts with some random default password. Then after a successful login, a new user can change the default password to his or her own. For security reasons, it is often recommended to "force" users to change the default password after the first login to make sure that the initial one-time password is no longer used.
|
||||
|
||||
Here is **how to force a user to change his or her password on the next login**.
|
||||
|
||||
Every user account in Linux is associated with various password-related configurations and information. For example, it remembers the date of the last password change, the minimum/maximum number of days between password changes, and when to expire the current password, etc.
|
||||
|
||||
A command-line tool called chage can access and adjust password expiration related configurations. You can use this tool to force password change of any user at the next login.
|
||||
|
||||
To view password expiration information of a particular user (e.g., alice), run the following command. Note that you need root privilege only when you are checking password age information of any other user than yourself.
|
||||
|
||||
$ sudo chage -l alice
|
||||
|
||||
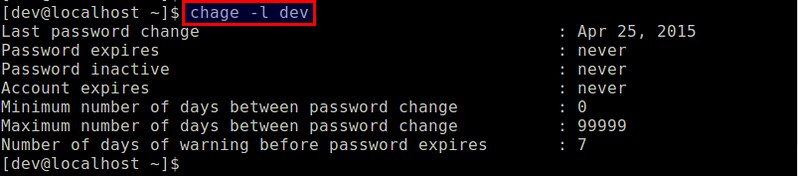
|
||||
|
||||
### Force Password Change for a User ###
|
||||
|
||||
If you want to force a user to change his or her password, use the following command.
|
||||
|
||||
$ sudo chage -d0 <user-name>
|
||||
|
||||
Originally the "-d <N>" option is supposed to set the "age" of a password (in terms of the number of days since January 1st, 1970 when the password was last changed). So "-d0" indicates that the password was changed on January 1st, 1970, which essentially expires the current password, and causes it to be changed on the next login.
|
||||
|
||||
Another way to expire the current password is via passwd command.
|
||||
|
||||
$ sudo passwd -e <user-name>
|
||||
|
||||
The above command has the same effect of "chage -d0", making the current password of the user expire immediately.
|
||||
|
||||
Now check the password information of the user again, and you will see:
|
||||
|
||||
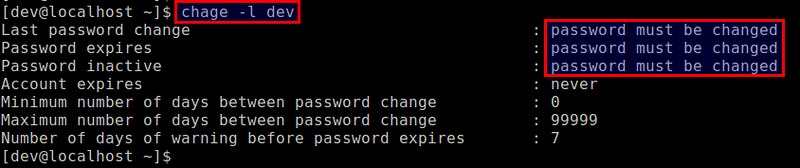
|
||||
|
||||
When you log in again, you will be asked to change the password. You will need to verify the current password one more time before the change.
|
||||
|
||||
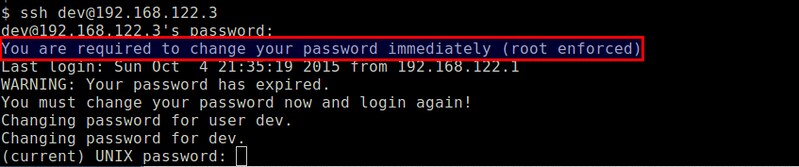
|
||||
|
||||
To set more comprehensive password policies (e.g., password complexity, reuse prevention), you can use PAM. See [the article][1] for more detail.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/force-password-change-next-login-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/set-password-policy-linux.html
|
||||
@ -0,0 +1,54 @@
|
||||
Linux有问必答 -- 如何在LInux中永久修改USB设备权限
|
||||
================================================================================
|
||||
> **提问**:当我尝试在Linux中运行USB GPS接收器时我遇到了下面来自gpsd的错误。
|
||||
>
|
||||
> gpsd[377]: gpsd:ERROR: read-only device open failed: Permission denied
|
||||
> gpsd[377]: gpsd:ERROR: /dev/ttyUSB0: device activation failed.
|
||||
> gpsd[377]: gpsd:ERROR: device open failed: Permission denied - retrying read-only
|
||||
>
|
||||
> 看上去gpsd没有权限访问USB设备(/dev/ttyUSB0)。我该如何永久修改它在Linux上的权限?
|
||||
|
||||
当你在运行一个会读取或者写入USB设备的进程时,进程的用户/组必须有权限这么做。当然你可以手动用chmod命令改变USB设备的权限,但是手动的权限改变只是暂时的。USB设备会在下次重启时恢复它的默认权限。
|
||||
|
||||

|
||||
|
||||
作为一个永久的方式,你可以创建一个基于udev的USB权限规则,它可以根据你的选择分配任何权限模式。下面是该如何做。
|
||||
|
||||
首先,你需要找出USB设备的vendorID和productID。使用lsusb命令。
|
||||
|
||||
$ lsusb -vvv
|
||||
|
||||

|
||||
|
||||
上面lsusb的输出中,找出你的USB设备,并找出"idVendor"和"idProduct"字段。本例中,我们的结果是idVendor (0x067b)和 idProduct (0x2303)
|
||||
|
||||
下面创建一个新的udev规则。
|
||||
|
||||
$ sudo vi /etc/udev/rules.d/50-myusb.rules
|
||||
|
||||
----------
|
||||
|
||||
SUBSYSTEMS=="usb", ATTRS{idVendor}=="067b", ATTRS{idProduct}=="2303", GROUP="users", MODE="0666"
|
||||
|
||||
用你自己的"idVendor"和"idProduct"来替换。**MODE="0666"**表示USB设备的权限。
|
||||
|
||||
现在重启电脑并重新加载udev规则:
|
||||
|
||||
$ sudo udevadm control --reload
|
||||
|
||||
Then verify the permission of the USB device.
|
||||
接着验证USB设备的权限。
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/change-usb-device-permission-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
@ -0,0 +1,53 @@
|
||||
Linux有问必答--如何找出Linux中内置模块的信息
|
||||
================================================================================
|
||||
> **提问**:我想要知道Linux系统中内核内置的模块,以及每个模块的参数。有什么方法可以得到内置模块和设备驱动的列表,以及它们的详细信息呢?
|
||||
|
||||
现代Linux内核正在随着时间迅速地增长来支持大量的硬件、文件系统和网络功能。在此期间,“可加载模块”的引入防止内核变得越来越臃肿,以及在不同的环境中灵活地扩展功能及硬件支持,而不必重新构建内核。
|
||||
|
||||
最新的Linux发型版的内核只带了相对较小的“内置模块”,其余的特定硬件驱动或者自定义功能作为“可加载模块”来让你选择地加载或卸载。
|
||||
|
||||
内置模块被静态地编译进了内核。不像可加载内核模块可以动态地使用modprobe、insmod、rmmod、modinfo或者lsmod等命令地加载、卸载、查询模块,内置的模块总是在启动是就加载进了内核,不会被这些命令管理。
|
||||
|
||||
### 找出内置模块列表 ###
|
||||
|
||||
要得到内置模块列表,运行下面的命令。
|
||||
|
||||
$ cat /lib/modules/$(uname -r)/modules.builtin
|
||||
|
||||

|
||||
|
||||
你也可以用下面的命令来查看有哪些内置模块:
|
||||
|
||||

|
||||
|
||||
### 找出内置模块参数 ###
|
||||
|
||||
每个内核模块无论是内置的还是可加载的都有一系列的参数。对于可加载模块,modinfo命令显示它们的参数信息。然而这个命令不对内置模块管用。你会得到下面的错误。
|
||||
|
||||
modinfo: ERROR: Module XXXXXX not found.
|
||||
|
||||
如果你想要查看内置模块的参数,以及它们的值,你可以在**/sys/module** 下检查它们的内容。
|
||||
|
||||
在 /sys/module目录下,你可以找到内核模块(包含内置和可加载的)命名的子目录。结合则进入每个模块目录,这里有个“parameters”目录,列出了这个模块所有的参数。
|
||||
|
||||
比如你要找出tcp_cubic(内核默认的TCP实现)模块的参数。你可以这么做:
|
||||
|
||||
$ ls /sys/module/tcp_cubic/parameters
|
||||
|
||||
接着阅读这个文件查看每个参数的值。
|
||||
|
||||
$ cat /sys/module/tcp_cubic/parameters/tcp_friendliness
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/find-information-builtin-kernel-modules-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
@ -0,0 +1,55 @@
|
||||
Linux有问必答--如何强制在下次登录Linux时更换密码
|
||||
================================================================================
|
||||
> **提问**:我管理着一台多人共享的Linux服务器。我刚使用默认密码创建了一个新用户,但是我想用户在第一次登录时更换密码。有没有什么方法可以让他/她在下次登录时修改密码呢?
|
||||
|
||||
在多用户Linux环境中,标准实践是使用一个默认的随机密码创建一个用户账户。成功登录后,新用户自己改变默认密码。出于安全里有,经常建议“强制”用户在第一次登录时修改密码来确保这个一次性使用的密码不会再被使用。
|
||||
|
||||
下面是**如何强制用户在下次登录时修改他/她的密码**。
|
||||
|
||||
changes, and when to expire the current password, etc.
|
||||
每个Linux用户都关联这不同的密码相关配置和信息。比如,记录着上次密码更改的日期、最小/最大的修改密码的天数、密码何时过期等等。
|
||||
|
||||
一个叫chage的命令行工具可以访问并调整密码过期相关配置。你可以使用这个工具来强制用户在下次登录修改密码、
|
||||
|
||||
要查看特定用户的过期信息(比如:alice),运行下面的命令。注意的是除了你自己之外查看其他任何用户的密码信息都需要root权限。
|
||||
|
||||
$ sudo chage -l alice
|
||||
|
||||

|
||||
|
||||
### 强制用户修改密码 ###
|
||||
|
||||
如果你想要强制用户去修改他/她的密码,使用下面的命令。
|
||||
|
||||
$ sudo chage -d0 <user-name>
|
||||
|
||||
原本“-d <N>”参数是用来设置密码的“年龄”(也就是上次修改密码起到1970 1.1起的天数)。因此“-d0”的意思是上次密码修改的时间是1970 1.1,这就让当前的密码过期了,也就强制让他在下次登录的时候修改密码了。
|
||||
|
||||
另外一个过期当前密码的方式是用passwd命令。
|
||||
|
||||
$ sudo passwd -e <user-name>
|
||||
|
||||
上面的命令和“chage -d0”作用一样,让当前用户的密码立即过期。
|
||||
|
||||
现在检查用户的信息,你会发现:
|
||||
|
||||

|
||||
|
||||
当你再次登录时候,你会被要求修改密码。你会在修改前被要求再验证一次当前密码。
|
||||
|
||||

|
||||
|
||||
要设置更全面的密码策略(如密码复杂性,防止重复使用),则可以使用PAM。参见[这篇文章][1]了解更多详情。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/force-password-change-next-login-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/set-password-policy-linux.html
|
||||
Loading…
Reference in New Issue
Block a user