mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-27 02:30:10 +08:00
commit
50ac27f024
published
sources/tech
20160516 Securing Your Server.md20161005 GETTING STARTED WITH ANSIBLE.md20161012 Introduction to FirewallD on CentOS.md20161021 Getting started with Inkscape on Fedora.md20161024 How to Use Old Xorg Apps in Unity 8 on Ubuntu 16.10.md20161110 How to check if port is in use on Linux or Unix.md20161128 Mir is not only about Unity8.md20161201 Using the NTP time synchronization.md20161206 How to Find Recent or Today’s Modified Files in Linux.md20161216 Kprobes Event Tracing on ARMv8.md
translated/tech
20161005 GETTING STARTED WITH ANSIBLE.md20161021 Getting started with Inkscape on Fedora.md20161024 How to Use Old Xorg Apps in Unity 8 on Ubuntu 16.10.md20161110 How to check if port is in use on Linux or Unix.md20161128 Mir is not only about Unity8.md20161206 How to Find Recent or Today’s Modified Files in Linux.md
365
published/20160516 Securing Your Server.md
Normal file
365
published/20160516 Securing Your Server.md
Normal file
@ -0,0 +1,365 @@
|
||||
Linux 服务器安全简明指南
|
||||
============================================================
|
||||
|
||||
现在让我们强化你的服务器以防止未授权访问。
|
||||
|
||||
### 经常升级系统
|
||||
|
||||
保持最新的软件是你可以在任何操作系统上采取的最大的安全预防措施。软件更新的范围从关键漏洞补丁到小 bug 的修复,许多软件漏洞实际上是在它们被公开的时候得到修补的。
|
||||
|
||||
### 自动安全更新
|
||||
|
||||
有一些用于服务器上自动更新的参数。[Fedora 的 Wiki][15] 上有一篇很棒的剖析自动更新的利弊的文章,但是如果你把它限制到安全更新上,自动更新的风险将是最小的。
|
||||
|
||||
自动更新的可行性必须你自己判断,因为它归结为**你**在你的服务器上做什么。请记住,自动更新仅适用于来自仓库的包,而不是自行编译的程序。你可能会发现一个复制了生产服务器的测试环境是很有必要的。可以在部署到生产环境之前,在测试环境里面更新来检查问题。
|
||||
|
||||
* CentOS 使用 [yum-cron][2] 进行自动更新。
|
||||
* Debian 和 Ubuntu 使用 [无人值守升级][3]。
|
||||
* Fedora 使用 [dnf-automatic][4]。
|
||||
|
||||
### 添加一个受限用户账户
|
||||
|
||||
到目前为止,你已经作为 `root` 用户访问了你的服务器,它有无限制的权限,可以执行**任何**命令 - 甚至可能意外中断你的服务器。 我们建议创建一个受限用户帐户,并始终使用它。 管理任务应该使用 `sudo` 来完成,它可以临时提升受限用户的权限,以便管理你的服务器。
|
||||
|
||||
> 不是所有的 Linux 发行版都在系统上默认包含 `sudo`,但大多数都在其软件包仓库中有 `sudo`。 如果得到这样的输出 `sudo:command not found`,请在继续之前安装 `sudo`。
|
||||
|
||||
要添加新用户,首先通过 SSH [登录到你的服务器][16]。
|
||||
|
||||
#### CentOS / Fedora
|
||||
|
||||
1、 创建用户,用你想要的名字替换 `example_user`,并分配一个密码:
|
||||
|
||||
```
|
||||
useradd example_user && passwd example_user
|
||||
```
|
||||
|
||||
2、 将用户添加到具有 sudo 权限的 `wheel` 组:
|
||||
|
||||
```
|
||||
usermod -aG wheel example_user
|
||||
```
|
||||
|
||||
#### Ubuntu
|
||||
|
||||
1、 创建用户,用你想要的名字替换 `example_user`。你将被要求输入用户密码:
|
||||
|
||||
```
|
||||
adduser example_user
|
||||
```
|
||||
|
||||
2、 添加用户到 `sudo` 组,这样你就有管理员权限了:
|
||||
|
||||
```
|
||||
adduser example_user sudo
|
||||
```
|
||||
|
||||
#### Debian
|
||||
|
||||
1、 Debian 默认的包中没有 `sudo`, 使用 `apt-get` 来安装:
|
||||
|
||||
```
|
||||
apt-get install sudo
|
||||
```
|
||||
|
||||
2、 创建用户,用你想要的名字替换 `example_user`。你将被要求输入用户密码:
|
||||
|
||||
```
|
||||
adduser example_user
|
||||
```
|
||||
|
||||
3、 添加用户到 `sudo` 组,这样你就有管理员权限了:
|
||||
|
||||
```
|
||||
adduser example_user sudo
|
||||
```
|
||||
|
||||
创建完有限权限的用户后,断开你的服务器连接:
|
||||
|
||||
```
|
||||
exit
|
||||
```
|
||||
|
||||
重新用你的新用户登录。用你的用户名代替 `example_user`,用你的服务器 IP 地址代替例子中的 IP 地址:
|
||||
|
||||
```
|
||||
ssh example_user@203.0.113.10
|
||||
```
|
||||
|
||||
现在你可以用你的新用户帐户管理你的服务器,而不是 `root`。 几乎所有超级用户命令都可以用 `sudo`(例如:`sudo iptables -L -nv`)来执行,这些命令将被记录到 `/var/log/auth.log` 中。
|
||||
|
||||
### 加固 SSH 访问
|
||||
|
||||
默认情况下,密码认证用于通过 SSH 连接到您的服务器。加密密钥对更加安全,因为它用私钥代替了密码,这通常更难以暴力破解。在本节中,我们将创建一个密钥对,并将服务器配置为不接受 SSH 密码登录。
|
||||
|
||||
#### 创建验证密钥对
|
||||
|
||||
1、这是在你本机上完成的,**不是**在你的服务器上,这里将创建一个 4096 位的 RSA 密钥对。在创建过程中,您可以选择使用密码加密私钥。这意味着它不能在没有输入密码的情况下使用,除非将密码保存到本机桌面的密钥管理器中。我们建议您使用带有密码的密钥对,但如果你不想使用密码,则可以将此字段留空。
|
||||
|
||||
**Linux / OS X**
|
||||
|
||||
> 如果你已经创建了 RSA 密钥对,则这个命令将会覆盖它,这可能会导致你不能访问其它的操作系统。如果你已创建过密钥对,请跳过此步骤。要检查现有的密钥,请运行 `ls〜/ .ssh / id_rsa *`。
|
||||
|
||||
```
|
||||
ssh-keygen -b 4096
|
||||
```
|
||||
|
||||
在输入密码之前,按下 **回车**使用 `/home/your_username/.ssh` 中的默认名称 `id_rsa` 和 `id_rsa.pub`。
|
||||
|
||||
**Windows**
|
||||
|
||||
这可以使用 PuTTY 完成,在我们指南中已有描述:[使用 SSH 公钥验证][6]。
|
||||
|
||||
2、将公钥上传到您的服务器上。 将 `example_user` 替换为你用来管理服务器的用户名称,将 `203.0.113.10` 替换为你的服务器的 IP 地址。
|
||||
|
||||
**Linux**
|
||||
|
||||
在本机上:
|
||||
|
||||
```
|
||||
ssh-copy-id example_user@203.0.113.10
|
||||
```
|
||||
|
||||
**OS X**
|
||||
|
||||
在你的服务器上(用你的权限受限用户登录):
|
||||
|
||||
```
|
||||
mkdir -p ~/.ssh && sudo chmod -R 700 ~/.ssh/
|
||||
```
|
||||
|
||||
在本机上:
|
||||
|
||||
```
|
||||
scp ~/.ssh/id_rsa.pub example_user@203.0.113.10:~/.ssh/authorized_keys
|
||||
```
|
||||
|
||||
> 如果相对于 `scp` 你更喜欢 `ssh-copy-id` 的话,那么它也可以在 [Homebrew][5] 中找到。使用 `brew install ssh-copy-id` 安装。
|
||||
|
||||
**Windows**
|
||||
|
||||
* **选择 1**:使用 [WinSCP][1] 来完成。 在登录窗口中,输入你的服务器的 IP 地址作为主机名,以及非 root 的用户名和密码。单击“登录”连接。
|
||||
|
||||
一旦 WinSCP 连接后,你会看到两个主要部分。 左边显示本机上的文件,右边显示服务区上的文件。 使用左侧的文件浏览器,导航到你已保存公钥的文件,选择公钥文件,然后点击上面工具栏中的“上传”。
|
||||
|
||||
系统会提示你输入要将文件放在服务器上的路径。 将文件上传到 `/home/example_user/.ssh /authorized_keys`,用你的用户名替换 `example_user`。
|
||||
|
||||
* **选择 2**:将公钥直接从 PuTTY 键生成器复制到连接到你的服务器中(作为非 root 用户):
|
||||
|
||||
```
|
||||
mkdir ~/.ssh; nano ~/.ssh/authorized_keys
|
||||
```
|
||||
|
||||
上面命令将在文本编辑器中打开一个名为 `authorized_keys` 的空文件。 将公钥复制到文本文件中,确保复制为一行,与 PuTTY 所生成的完全一样。 按下 `CTRL + X`,然后按下 `Y`,然后回车保存文件。
|
||||
|
||||
最后,你需要为公钥目录和密钥文件本身设置权限:
|
||||
|
||||
```
|
||||
sudo chmod 700 -R ~/.ssh && chmod 600 ~/.ssh/authorized_keys
|
||||
```
|
||||
|
||||
这些命令通过阻止其他用户访问公钥目录以及文件本身来提供额外的安全性。有关它如何工作的更多信息,请参阅我们的指南[如何修改文件权限][7]。
|
||||
|
||||
3、 现在退出并重新登录你的服务器。如果你为私钥指定了密码,则需要输入密码。
|
||||
|
||||
#### SSH 守护进程选项
|
||||
|
||||
1、 **不允许 root 用户通过 SSH 登录。** 这要求所有的 SSH 连接都是通过非 root 用户进行。当以受限用户帐户连接后,可以通过使用 `sudo` 或使用 `su -` 切换为 root shell 来使用管理员权限。
|
||||
|
||||
```
|
||||
# Authentication:
|
||||
...
|
||||
PermitRootLogin no
|
||||
```
|
||||
|
||||
2、 **禁用 SSH 密码认证。** 这要求所有通过 SSH 连接的用户使用密钥认证。根据 Linux 发行版的不同,它可能需要添加 `PasswordAuthentication` 这行,或者删除前面的 `#` 来取消注释。
|
||||
|
||||
```
|
||||
# Change to no to disable tunnelled clear text passwords
|
||||
PasswordAuthentication no
|
||||
```
|
||||
|
||||
> 如果你从许多不同的计算机连接到服务器,你可能想要继续启用密码验证。这将允许你使用密码进行身份验证,而不是为每个设备生成和上传密钥对。
|
||||
|
||||
3、 **只监听一个互联网协议。** 在默认情况下,SSH 守护进程同时监听 IPv4 和 IPv6 上的传入连接。除非你需要使用这两种协议进入你的服务器,否则就禁用你不需要的。 _这不会禁用系统范围的协议,它只用于 SSH 守护进程。_
|
||||
|
||||
使用选项:
|
||||
|
||||
* `AddressFamily inet` 只监听 IPv4。
|
||||
* `AddressFamily inet6` 只监听 IPv6。
|
||||
|
||||
默认情况下,`AddressFamily` 选项通常不在 `sshd_config` 文件中。将它添加到文件的末尾:
|
||||
|
||||
```
|
||||
echo 'AddressFamily inet' | sudo tee -a /etc/ssh/sshd_config
|
||||
```
|
||||
|
||||
4、 重新启动 SSH 服务以加载新配置。
|
||||
|
||||
如果你使用的 Linux 发行版使用 systemd(CentOS 7、Debian 8、Fedora、Ubuntu 15.10+)
|
||||
|
||||
```
|
||||
sudo systemctl restart sshd
|
||||
```
|
||||
|
||||
如果您的 init 系统是 SystemV 或 Upstart(CentOS 6、Debian 7、Ubuntu 14.04):
|
||||
|
||||
```
|
||||
sudo service ssh restart
|
||||
```
|
||||
|
||||
#### 使用 Fail2Ban 保护 SSH 登录
|
||||
|
||||
[Fail2Ban][17] 是一个应用程序,它会在太多的失败登录尝试后禁止 IP 地址登录到你的服务器。由于合法登录通常不会超过三次尝试(如果使用 SSH 密钥,那不会超过一个),因此如果服务器充满了登录失败的请求那就表示有恶意访问。
|
||||
|
||||
Fail2Ban 可以监视各种协议,包括 SSH、HTTP 和 SMTP。默认情况下,Fail2Ban 仅监视 SSH,并且因为 SSH 守护程序通常配置为持续运行并监听来自任何远程 IP 地址的连接,所以对于任何服务器都是一种安全威慑。
|
||||
|
||||
有关安装和配置 Fail2Ban 的完整说明,请参阅我们的指南:[使用 Fail2ban 保护服务器][18]。
|
||||
|
||||
### 删除未使用的面向网络的服务
|
||||
|
||||
大多数 Linux 发行版都安装并运行了网络服务,监听来自互联网、回环接口或两者兼有的传入连接。 将不需要的面向网络的服务从系统中删除,以减少对运行进程和对已安装软件包攻击的概率。
|
||||
|
||||
#### 查明运行的服务
|
||||
|
||||
要查看服务器中运行的服务:
|
||||
|
||||
```
|
||||
sudo netstat -tulpn
|
||||
```
|
||||
|
||||
> 如果默认情况下 `netstat` 没有包含在你的 Linux 发行版中,请安装软件包 `net-tools` 或使用 `ss -tulpn` 命令。
|
||||
|
||||
以下是 `netstat` 的输出示例。 请注意,因为默认情况下不同发行版会运行不同的服务,你的输出将有所不同:
|
||||
|
||||
|
||||
```
|
||||
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
|
||||
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 7315/rpcbind
|
||||
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 3277/sshd
|
||||
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 3179/exim4
|
||||
tcp 0 0 0.0.0.0:42526 0.0.0.0:* LISTEN 2845/rpc.statd
|
||||
tcp6 0 0 :::48745 :::* LISTEN 2845/rpc.statd
|
||||
tcp6 0 0 :::111 :::* LISTEN 7315/rpcbind
|
||||
tcp6 0 0 :::22 :::* LISTEN 3277/sshd
|
||||
tcp6 0 0 ::1:25 :::* LISTEN 3179/exim4
|
||||
udp 0 0 127.0.0.1:901 0.0.0.0:* 2845/rpc.statd
|
||||
udp 0 0 0.0.0.0:47663 0.0.0.0:* 2845/rpc.statd
|
||||
udp 0 0 0.0.0.0:111 0.0.0.0:* 7315/rpcbind
|
||||
udp 0 0 192.0.2.1:123 0.0.0.0:* 3327/ntpd
|
||||
udp 0 0 127.0.0.1:123 0.0.0.0:* 3327/ntpd
|
||||
udp 0 0 0.0.0.0:123 0.0.0.0:* 3327/ntpd
|
||||
udp 0 0 0.0.0.0:705 0.0.0.0:* 7315/rpcbind
|
||||
udp6 0 0 :::111 :::* 7315/rpcbind
|
||||
udp6 0 0 fe80::f03c:91ff:fec:123 :::* 3327/ntpd
|
||||
udp6 0 0 2001:DB8::123 :::* 3327/ntpd
|
||||
udp6 0 0 ::1:123 :::* 3327/ntpd
|
||||
udp6 0 0 :::123 :::* 3327/ntpd
|
||||
udp6 0 0 :::705 :::* 7315/rpcbind
|
||||
udp6 0 0 :::60671 :::* 2845/rpc.statd
|
||||
```
|
||||
|
||||
`netstat` 告诉我们服务正在运行 [RPC][19](`rpc.statd` 和 `rpcbind`)、SSH(`sshd`)、[NTPdate][20](`ntpd`)和[Exim][21](`exim4`)。
|
||||
|
||||
##### TCP
|
||||
|
||||
请参阅 `netstat` 输出的 `Local Address` 那一列。进程 `rpcbind` 正在侦听 `0.0.0.0:111` 和 `:::111`,外部地址是 `0.0.0.0:*` 或者 `:::*` 。这意味着它从任何端口和任何网络接口接受来自任何外部地址(IPv4 和 IPv6)上的其它 RPC 客户端的传入 TCP 连接。 我们看到类似的 SSH,Exim 正在侦听来自回环接口的流量,如所示的 `127.0.0.1` 地址。
|
||||
|
||||
##### UDP
|
||||
|
||||
UDP 套接字是[无状态][14]的,这意味着它们只有打开或关闭,并且每个进程的连接是独立于前后发生的连接。这与 TCP 的连接状态(例如 `LISTEN`、`ESTABLISHED`和 `CLOSE_WAIT`)形成对比。
|
||||
|
||||
我们的 `netstat`输出说明 NTPdate :1)接受服务器的公网 IP 地址的传入连接;2)通过本地主机进行通信;3)接受来自外部的连接。这些连接是通过端口 123 进行的,同时支持 IPv4 和 IPv6。我们还看到了 RPC 打开的更多的套接字。
|
||||
|
||||
#### 查明该移除哪个服务
|
||||
|
||||
如果你在没有启用防火墙的情况下对服务器进行基本的 TCP 和 UDP 的 [nmap][22] 扫描,那么在打开端口的结果中将出现 SSH、RPC 和 NTPdate 。通过[配置防火墙][23],你可以过滤掉这些端口,但 SSH 除外,因为它必须允许你的传入连接。但是,理想情况下,应该禁用未使用的服务。
|
||||
|
||||
* 你可能主要通过 SSH 连接管理你的服务器,所以让这个服务需要保留。如上所述,[RSA 密钥][8]和 [Fail2Ban][9] 可以帮助你保护 SSH。
|
||||
* NTP 是服务器计时所必需的,但有个替代 NTPdate 的方法。如果你喜欢不开放网络端口的时间同步方法,并且你不需要纳秒精度,那么你可能有兴趣用 [OpenNTPD][10] 来代替 NTPdate。
|
||||
* 然而,Exim 和 RPC 是不必要的,除非你有特定的用途,否则应该删除它们。
|
||||
|
||||
> 本节针对 Debian 8。默认情况下,不同的 Linux 发行版具有不同的服务。如果你不确定某项服务的功能,请尝试搜索互联网以了解该功能是什么,然后再尝试删除或禁用它。
|
||||
|
||||
#### 卸载监听的服务
|
||||
|
||||
如何移除包取决于发行版的包管理器:
|
||||
|
||||
**Arch**
|
||||
|
||||
```
|
||||
sudo pacman -Rs package_name
|
||||
```
|
||||
|
||||
**CentOS**
|
||||
|
||||
```
|
||||
sudo yum remove package_name
|
||||
```
|
||||
|
||||
**Debian / Ubuntu**
|
||||
|
||||
```
|
||||
sudo apt-get purge package_name
|
||||
```
|
||||
|
||||
**Fedora**
|
||||
|
||||
```
|
||||
sudo dnf remove package_name
|
||||
```
|
||||
|
||||
再次运行 `sudo netstat -tulpn`,你看到监听的服务就只会有 SSH(`sshd`)和 NTP(`ntpdate`,网络时间协议)。
|
||||
|
||||
### 配置防火墙
|
||||
|
||||
使用防火墙阻止不需要的入站流量能为你的服务器提供一个高效的安全层。 通过指定入站流量,你可以阻止入侵和网络测绘。 最佳做法是只允许你需要的流量,并拒绝一切其他流量。请参阅我们的一些关于最常见的防火墙程序的文档:
|
||||
|
||||
* [iptables][11] 是 netfilter 的控制器,它是 Linux 内核的包过滤框架。 默认情况下,iptables 包含在大多数 Linux 发行版中。
|
||||
* [firewallD][12] 是可用于 CentOS/Fedora 系列发行版的 iptables 控制器。
|
||||
* [UFW][13] 为 Debian 和 Ubuntu 提供了一个 iptables 前端。
|
||||
|
||||
### 接下来
|
||||
|
||||
这些是加固 Linux 服务器的最基本步骤,但是进一步的安全层将取决于其预期用途。 其他技术可以包括应用程序配置,使用[入侵检测][24]或者安装某个形式的[访问控制][25]。
|
||||
|
||||
现在你可以按你的需求开始设置你的服务器了。 我们有一个文档库来以帮助你从[从共享主机迁移][26]到[启用两步验证][27]到[托管网站] [28]等各种主题。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linode.com/docs/security/securing-your-server/
|
||||
|
||||
作者:[Phil Zona][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linode.com/docs/security/securing-your-server/
|
||||
[1]:http://winscp.net/
|
||||
[2]:https://fedoraproject.org/wiki/AutoUpdates#Fedora_21_or_earlier_versions
|
||||
[3]:https://help.ubuntu.com/lts/serverguide/automatic-updates.html
|
||||
[4]:https://dnf.readthedocs.org/en/latest/automatic.html
|
||||
[5]:http://brew.sh/
|
||||
[6]:https://www.linode.com/docs/security/use-public-key-authentication-with-ssh#windows-operating-system
|
||||
[7]:https://www.linode.com/docs/tools-reference/modify-file-permissions-with-chmod
|
||||
[8]:https://www.linode.com/docs/security/securing-your-server/#create-an-authentication-key-pair
|
||||
[9]:https://www.linode.com/docs/security/securing-your-server/#use-fail2ban-for-ssh-login-protection
|
||||
[10]:https://en.wikipedia.org/wiki/OpenNTPD
|
||||
[11]:https://www.linode.com/docs/security/firewalls/control-network-traffic-with-iptables
|
||||
[12]:https://www.linode.com/docs/security/firewalls/introduction-to-firewalld-on-centos
|
||||
[13]:https://www.linode.com/docs/security/firewalls/configure-firewall-with-ufw
|
||||
[14]:https://en.wikipedia.org/wiki/Stateless_protocol
|
||||
[15]:https://fedoraproject.org/wiki/AutoUpdates#Why_use_Automatic_updates.3F
|
||||
[16]:https://www.linode.com/docs/getting-started#logging-in-for-the-first-time
|
||||
[17]:http://www.fail2ban.org/wiki/index.php/Main_Page
|
||||
[18]:https://www.linode.com/docs/security/using-fail2ban-for-security
|
||||
[19]:https://en.wikipedia.org/wiki/Open_Network_Computing_Remote_Procedure_Call
|
||||
[20]:http://support.ntp.org/bin/view/Main/SoftwareDownloads
|
||||
[21]:http://www.exim.org/
|
||||
[22]:https://nmap.org/
|
||||
[23]:https://www.linode.com/docs/security/securing-your-server/#configure-a-firewall
|
||||
[24]:https://linode.com/docs/security/ossec-ids-debian-7
|
||||
[25]:https://en.wikipedia.org/wiki/Access_control#Access_Control
|
||||
[26]:https://www.linode.com/docs/migrate-to-linode/migrate-from-shared-hosting
|
||||
[27]:https://www.linode.com/docs/security/linode-manager-security-controls
|
||||
[28]:https://www.linode.com/docs/websites/hosting-a-website
|
||||
@ -1,380 +0,0 @@
|
||||
Securing Your Server
|
||||
============================================================
|
||||
|
||||
### Update Your System–Frequently
|
||||
|
||||
Keeping your software up to date is the single biggest security precaution you can take for any operating system. Software updates range from critical vulnerability patches to minor bug fixes, and many software vulnerabilities are actually patched by the time they become public.
|
||||
|
||||
### Automatic Security Updates
|
||||
|
||||
There are arguments for and against automatic updates on servers. [Fedora’s Wiki][15] has a good breakdown of the pros and cons, but the risk of automatic updates will be minimal if you limit them to security updates.
|
||||
|
||||
The practicality of automatic updates is something you must judge for yourself because it comes down to what _you_ do with your Linode. Bear in mind that automatic updates apply only to packages sourced from repositories, not self-compiled applications. You may find it worthwhile to have a test environment that replicates your production server. Updates can be applied there and reviewed for issues before being applied to the live environment.
|
||||
|
||||
* CentOS uses _[yum-cron][2]_ for automatic updates.
|
||||
|
||||
* Debian and Ubuntu use _[unattended upgrades][3]_.
|
||||
|
||||
* Fedora uses _[dnf-automatic][4]_.
|
||||
|
||||
### Add a Limited User Account
|
||||
|
||||
Up to this point, you have accessed your Linode as the `root` user, which has unlimited privileges and can execute _any_ command–even one that could accidentally disrupt your server. We recommend creating a limited user account and using that at all times. Administrative tasks will be done using `sudo` to temporarily elevate your limited user’s privileges so you can administer your server.
|
||||
|
||||
> Not all Linux distributions include `sudo` on the system by default, but all the images provided by Linode have sudo in their package repositories. If you get the output `sudo: command not found`, install sudo before continuing.
|
||||
|
||||
To add a new user, first [log in to your Linode][16] via SSH.
|
||||
|
||||
### CentOS / Fedora
|
||||
|
||||
1. Create the user, replacing `example_user` with your desired username, and assign a password:
|
||||
|
||||
```
|
||||
useradd example_user && passwd example_user
|
||||
```
|
||||
|
||||
2. Add the user to the `wheel` group for sudo privileges:
|
||||
|
||||
```
|
||||
usermod -aG wheel example_user
|
||||
```
|
||||
|
||||
### Ubuntu
|
||||
|
||||
1. Create the user, replacing `example_user` with your desired username. You’ll then be asked to assign the user a password:
|
||||
|
||||
```
|
||||
adduser example_user
|
||||
```
|
||||
|
||||
2. Add the user to the `sudo` group so you’ll have administrative privileges:
|
||||
|
||||
|
||||
```
|
||||
adduser example_user sudo
|
||||
```
|
||||
|
||||
### Debian
|
||||
|
||||
1. Debian does not include `sudo` among their default packages. Use `apt-get` to install it:
|
||||
|
||||
|
||||
```
|
||||
apt-get install sudo
|
||||
```
|
||||
|
||||
2. Create the user, replacing `example_user` with your desired username. You’ll then be asked to assign the user a password:
|
||||
|
||||
```
|
||||
adduser example_user
|
||||
```
|
||||
|
||||
3. Add the user to the `sudo` group so you’ll have administrative privileges:
|
||||
|
||||
```
|
||||
adduser example_user sudo
|
||||
```
|
||||
|
||||
After creating your limited user, disconnect from your Linode:
|
||||
|
||||
```
|
||||
exit
|
||||
```
|
||||
|
||||
Log back in as your new user. Replace `example_user` with your username, and the example IP address with your Linode’s IP address:
|
||||
|
||||
```
|
||||
ssh example_user@203.0.113.10
|
||||
```
|
||||
|
||||
Now you can administer your Linode from your new user account instead of `root`. Nearly all superuser commands can be executed with `sudo` (example: `sudo iptables -L -nv`) and those commands will be logged to `/var/log/auth.log`.
|
||||
|
||||
### Harden SSH Access
|
||||
|
||||
By default, password authentication is used to connect to your Linode via SSH. A cryptographic key-pair is more secure because a private key takes the place of a password, which is generally much more difficult to brute-force. In this section we’ll create a key-pair and configure the Linode to not accept passwords for SSH logins.
|
||||
|
||||
### Create an Authentication Key-pair
|
||||
|
||||
1. This is done on your local computer, **not** your Linode, and will create a 4096-bit RSA key-pair. During creation, you will be given the option to encrypt the private key with a passphrase. This means that it cannot be used without entering the passphrase, unless you save it to your local desktop’s keychain manager. We suggest you use the key-pair with a passphrase, but you can leave this field blank if you don’t want to use one.
|
||||
|
||||
**Linux / OS X**
|
||||
|
||||
> If you’ve already created an RSA key-pair, this command will overwrite it, potentially locking you out of other systems. If you’ve already created a key-pair, skip this step. To check for existing keys, run `ls ~/.ssh/id_rsa*`.
|
||||
|
||||
```
|
||||
ssh-keygen -b 4096
|
||||
```
|
||||
|
||||
|
||||
Press **Enter** to use the default names `id_rsa` and `id_rsa.pub` in `/home/your_username/.ssh` before entering your passphrase.
|
||||
|
||||
**Windows**
|
||||
|
||||
This can be done using PuTTY as outlined in our guide: [Use Public Key Authentication with SSH][6].
|
||||
|
||||
2. Upload the public key to your Linode. Replace `example_user` with the name of the user you plan to administer the server as, and `203.0.113.10` with your Linode’s IP address.
|
||||
|
||||
**Linux**
|
||||
|
||||
From your local computer:
|
||||
|
||||
```
|
||||
ssh-copy-id example_user@203.0.113.10
|
||||
```
|
||||
|
||||
**OS X**
|
||||
|
||||
On your Linode (while signed in as your limited user):
|
||||
|
||||
```
|
||||
mkdir -p ~/.ssh && sudo chmod -R 700 ~/.ssh/
|
||||
```
|
||||
|
||||
From your local computer:
|
||||
|
||||
```
|
||||
scp ~/.ssh/id_rsa.pub example_user@203.0.113.10:~/.ssh/authorized_keys
|
||||
```
|
||||
|
||||
> `ssh-copy-id` is available in [Homebrew][5] if you prefer it over SCP. Install with `brew install ssh-copy-id`.
|
||||
|
||||
**Windows**
|
||||
|
||||
* **Option 1**: This can be done using [WinSCP][1]. In the login window, enter your Linode’s public IP address as the hostname, and your non-root username and password. Click _Login_ to connect.
|
||||
|
||||
Once WinSCP has connected, you’ll see two main sections. The section on the left shows files on your local computer and the section on the right shows files on your Linode. Using the file explorer on the left, navigate to the file where you’ve saved your public key, select the public key file, and click _Upload_ in the toolbar above.
|
||||
|
||||
You’ll be prompted to enter a path where you’d like to place the file on your Linode. Upload the file to `/home/example_user/.ssh/authorized_keys`, replacing `example_user` with your username.
|
||||
|
||||
* **Option 2:** Copy the public key directly from the PuTTY key generator into the terminal emulator connected to your Linode (as a non-root user):
|
||||
|
||||
```
|
||||
mkdir ~/.ssh; nano ~/.ssh/authorized_keys
|
||||
```
|
||||
|
||||
|
||||
The above command will open a blank file called `authorized_keys` in a text editor. Copy the public key into the text file, making sure it is copied as a single line exactly as it was generated by PuTTY. Press **CTRL+X**, then **Y**, then **Enter** to save the file.
|
||||
|
||||
Finally, you’ll want to set permissions for the public key directory and the key file itself:
|
||||
|
||||
```
|
||||
sudo chmod 700 -R ~/.ssh && chmod 600 ~/.ssh/authorized_keys
|
||||
```
|
||||
|
||||
These commands provide an extra layer of security by preventing other users from accessing the public key directory as well as the file itself. For more information on how this works, see our guide on [how to modify file permissions][7].
|
||||
|
||||
3. Now exit and log back into your Linode. If you specified a passphrase for your private key, you’ll need to enter it.
|
||||
|
||||
### SSH Daemon Options
|
||||
|
||||
1. **Disallow root logins over SSH.** This requires all SSH connections be by non-root users. Once a limited user account is connected, administrative privileges are accessible either by using `sudo` or changing to a root shell using `su -`.
|
||||
|
||||
```
|
||||
# Authentication:
|
||||
...
|
||||
PermitRootLogin no
|
||||
```
|
||||
|
||||
|
||||
2. **Disable SSH password authentication.** This requires all users connecting via SSH to use key authentication. Depending on the Linux distribution, the line `PasswordAuthentication` may need to be added, or uncommented by removing the leading `#`.
|
||||
|
||||
|
||||
```
|
||||
# Change to no to disable tunnelled clear text passwords
|
||||
PasswordAuthentication no
|
||||
```
|
||||
|
||||
> You may want to leave password authentication enabled if you connect to your Linode from many different computers. This will allow you to authenticate with a password instead of generating and uploading a key-pair for every device.
|
||||
|
||||
3. **Listen on only one internet protocol.** The SSH daemon listens for incoming connections over both IPv4 and IPv6 by default. Unless you need to SSH into your Linode using both protocols, disable whichever you do not need. _This does not disable the protocol system-wide, it is only for the SSH daemon._
|
||||
|
||||
Use the option:
|
||||
|
||||
* `AddressFamily inet` to listen only on IPv4.
|
||||
* `AddressFamily inet6` to listen only on IPv6.
|
||||
|
||||
The `AddressFamily` option is usually not in the `sshd_config` file by default. Add it to the end of the file:
|
||||
|
||||
```
|
||||
echo 'AddressFamily inet' | sudo tee -a /etc/ssh/sshd_config
|
||||
```
|
||||
|
||||
|
||||
4. Restart the SSH service to load the new configuration.
|
||||
|
||||
If you’re using a Linux distribution which uses systemd (CentOS 7, Debian 8, Fedora, Ubuntu 15.10+)
|
||||
|
||||
```
|
||||
sudo systemctl restart sshd
|
||||
```
|
||||
|
||||
If your init system is SystemV or Upstart (CentOS 6, Debian 7, Ubuntu 14.04):
|
||||
|
||||
```
|
||||
sudo service ssh restart
|
||||
```
|
||||
|
||||
### Use Fail2Ban for SSH Login Protection
|
||||
|
||||
[_Fail2Ban_][17] is an application that bans IP addresses from logging into your server after too many failed login attempts. Since legitimate logins usually take no more than three tries to succeed (and with SSH keys, no more than one), a server being spammed with unsuccessful logins indicates attempted malicious access.
|
||||
|
||||
Fail2Ban can monitor a variety of protocols including SSH, HTTP, and SMTP. By default, Fail2Ban monitors SSH only, and is a helpful security deterrent for any server since the SSH daemon is usually configured to run constantly and listen for connections from any remote IP address.
|
||||
|
||||
For complete instructions on installing and configuring Fail2Ban, see our guide: [Securing Your Server with Fail2ban][18].
|
||||
|
||||
### Remove Unused Network-Facing Services
|
||||
|
||||
Most Linux distributions install with running network services which listen for incoming connections from the internet, the loopback interface, or a combination of both. Network-facing services which are not needed should be removed from the system to reduce the attack surface of both running processes and installed packages.
|
||||
|
||||
### Determine Running Services
|
||||
|
||||
To see your Linode’s running network services:
|
||||
|
||||
```
|
||||
sudo netstat -tulpn
|
||||
```
|
||||
|
||||
|
||||
> If netstat isn’t included in your Linux distribution by default, install the package `net-tools` or use the `ss -tulpn`command instead.
|
||||
|
||||
The following is an example of netstat’s output. Note that because distributions run different services by default, your output will differ:
|
||||
|
||||
|
||||
```
|
||||
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
|
||||
tcp 0 0 0.0.0.0:111 0.0.0.0:* LISTEN 7315/rpcbind
|
||||
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 3277/sshd
|
||||
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN 3179/exim4
|
||||
tcp 0 0 0.0.0.0:42526 0.0.0.0:* LISTEN 2845/rpc.statd
|
||||
tcp6 0 0 :::48745 :::* LISTEN 2845/rpc.statd
|
||||
tcp6 0 0 :::111 :::* LISTEN 7315/rpcbind
|
||||
tcp6 0 0 :::22 :::* LISTEN 3277/sshd
|
||||
tcp6 0 0 ::1:25 :::* LISTEN 3179/exim4
|
||||
udp 0 0 127.0.0.1:901 0.0.0.0:* 2845/rpc.statd
|
||||
udp 0 0 0.0.0.0:47663 0.0.0.0:* 2845/rpc.statd
|
||||
udp 0 0 0.0.0.0:111 0.0.0.0:* 7315/rpcbind
|
||||
udp 0 0 192.0.2.1:123 0.0.0.0:* 3327/ntpd
|
||||
udp 0 0 127.0.0.1:123 0.0.0.0:* 3327/ntpd
|
||||
udp 0 0 0.0.0.0:123 0.0.0.0:* 3327/ntpd
|
||||
udp 0 0 0.0.0.0:705 0.0.0.0:* 7315/rpcbind
|
||||
udp6 0 0 :::111 :::* 7315/rpcbind
|
||||
udp6 0 0 fe80::f03c:91ff:fec:123 :::* 3327/ntpd
|
||||
udp6 0 0 2001:DB8::123 :::* 3327/ntpd
|
||||
udp6 0 0 ::1:123 :::* 3327/ntpd
|
||||
udp6 0 0 :::123 :::* 3327/ntpd
|
||||
udp6 0 0 :::705 :::* 7315/rpcbind
|
||||
udp6 0 0 :::60671 :::* 2845/rpc.statd
|
||||
```
|
||||
|
||||
Netstat tells us that services are running for [Remote Procedure Call][19] (rpc.statd and rpcbind), SSH (sshd), [NTPdate][20] (ntpd) and [Exim][21] (exim4).
|
||||
|
||||
#### TCP
|
||||
|
||||
See the **Local Address** column of the netstat readout. The process `rpcbind` is listening on `0.0.0.0:111` and `:::111` for a foreign address of `0.0.0.0:*` or `:::*`. This means that it’s accepting incoming TCP connections from other RPC clients on any external address, both IPv4 and IPv6, from any port and over any network interface. We see similar for SSH, and that Exim is listening locally for traffic from the loopback interface, as shown by the `127.0.0.1` address.
|
||||
|
||||
#### UDP
|
||||
|
||||
UDP sockets are _[stateless][14]_, meaning they are either open or closed and every process’s connection is independent of those which occurred before and after. This is in contrast to TCP connection states such as _LISTEN_, _ESTABLISHED_ and _CLOSE_WAIT_.
|
||||
|
||||
Our netstat output shows that NTPdate is: 1) accepting incoming connections on the Linode’s public IP address; 2) communicates over localhost; and 3) accepts connections from external sources. These are over port 123, and both IPv4 and IPv6\. We also see more sockets open for RPC.
|
||||
|
||||
### Determine Which Services to Remove
|
||||
|
||||
If you were to do a basic TCP and UDP [nmap][22] scan of your Linode without a firewall enabled, SSH, RPC and NTPdate would be present in the result with ports open. By [configuring a firewall][23] you can filter those ports, with the exception of SSH because it must allow your incoming connections. Ideally, however, the unused services should be disabled.
|
||||
|
||||
* You will likely be administering your server primarily through an SSH connection, so that service needs to stay. As mentioned above, [RSA keys][8] and [Fail2Ban][9] can help protect SSH.
|
||||
|
||||
* NTP is necessary for your server’s timekeeping but there are alternatives to NTPdate. If you prefer a time synchronization method which does not hold open network ports, and you do not need nanosecond accuracy, then you may be interested in replacing NTPdate with [OpenNTPD][10].
|
||||
|
||||
* Exim and RPC, however, are unnecessary unless you have a specific use for them, and should be removed.
|
||||
|
||||
> This section focused on Debian 8\. Different Linux distributions have different services enabled by default. If you are unsure of what a service does, do an internet search to understand what it is before attempting to remove or disable it.
|
||||
|
||||
### Uninstall the Listening Services
|
||||
|
||||
How to remove the offending packages will differ depending on your distribution’s package manager.
|
||||
|
||||
**Arch**
|
||||
|
||||
```
|
||||
sudo pacman -Rs package_name
|
||||
```
|
||||
|
||||
**CentOS**
|
||||
|
||||
|
||||
```
|
||||
sudo yum remove package_name
|
||||
```
|
||||
|
||||
|
||||
**Debian / Ubuntu**
|
||||
|
||||
```
|
||||
sudo apt-get purge package_name
|
||||
```
|
||||
|
||||
**Fedora**
|
||||
|
||||
|
||||
```
|
||||
sudo dnf remove package_name
|
||||
```
|
||||
|
||||
Run `sudo netstat -tulpn` again. You should now only see listening services for SSH (sshd) and NTP (ntpdate, network time protocol).
|
||||
|
||||
### Configure a Firewall
|
||||
|
||||
Using a _firewall_ to block unwanted inbound traffic to your Linode provides a highly effective security layer. By being very specific about the traffic you allow in, you can prevent intrusions and network mapping. A best practice is to allow only the traffic you need, and deny everything else. See our documentation on some of the most common firewall applications:
|
||||
|
||||
* [Iptables][11] is the controller for netfilter, the Linux kernel’s packet filtering framework. Iptables is included in most Linux distributions by default.
|
||||
|
||||
* [FirewallD][12] is the iptables controller available for the CentOS / Fedora family of distributions.
|
||||
|
||||
* [UFW][13] provides an iptables frontend for Debian and Ubuntu.
|
||||
|
||||
### Next Steps
|
||||
|
||||
These are the most basic steps to harden any Linux server, but further security layers will depend on its intended use. Additional techniques can include application configurations, using [intrusion detection][24] or installing a form of [access control][25].
|
||||
|
||||
Now you can begin setting up your Linode for any purpose you choose. We have a library of documentation to assist you with a variety of topics ranging from [migration from shared hosting][26] to [enabling two-factor authentication][27] to [hosting a website][28].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linode.com/docs/security/securing-your-server/
|
||||
|
||||
作者:[Phil Zona ][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linode.com/docs/security/securing-your-server/
|
||||
[1]:http://winscp.net/
|
||||
[2]:https://fedoraproject.org/wiki/AutoUpdates#Fedora_21_or_earlier_versions
|
||||
[3]:https://help.ubuntu.com/lts/serverguide/automatic-updates.html
|
||||
[4]:https://dnf.readthedocs.org/en/latest/automatic.html
|
||||
[5]:http://brew.sh/
|
||||
[6]:https://www.linode.com/docs/security/use-public-key-authentication-with-ssh#windows-operating-system
|
||||
[7]:https://www.linode.com/docs/tools-reference/modify-file-permissions-with-chmod
|
||||
[8]:https://www.linode.com/docs/security/securing-your-server/#create-an-authentication-key-pair
|
||||
[9]:https://www.linode.com/docs/security/securing-your-server/#use-fail2ban-for-ssh-login-protection
|
||||
[10]:https://en.wikipedia.org/wiki/OpenNTPD
|
||||
[11]:https://www.linode.com/docs/security/firewalls/control-network-traffic-with-iptables
|
||||
[12]:https://www.linode.com/docs/security/firewalls/introduction-to-firewalld-on-centos
|
||||
[13]:https://www.linode.com/docs/security/firewalls/configure-firewall-with-ufw
|
||||
[14]:https://en.wikipedia.org/wiki/Stateless_protocol
|
||||
[15]:https://fedoraproject.org/wiki/AutoUpdates#Why_use_Automatic_updates.3F
|
||||
[16]:https://www.linode.com/docs/getting-started#logging-in-for-the-first-time
|
||||
[17]:http://www.fail2ban.org/wiki/index.php/Main_Page
|
||||
[18]:https://www.linode.com/docs/security/using-fail2ban-for-security
|
||||
[19]:https://en.wikipedia.org/wiki/Open_Network_Computing_Remote_Procedure_Call
|
||||
[20]:http://support.ntp.org/bin/view/Main/SoftwareDownloads
|
||||
[21]:http://www.exim.org/
|
||||
[22]:https://nmap.org/
|
||||
[23]:https://www.linode.com/docs/security/securing-your-server/#configure-a-firewall
|
||||
[24]:https://linode.com/docs/security/ossec-ids-debian-7
|
||||
[25]:https://en.wikipedia.org/wiki/Access_control#Access_Control
|
||||
[26]:https://www.linode.com/docs/migrate-to-linode/migrate-from-shared-hosting
|
||||
[27]:https://www.linode.com/docs/security/linode-manager-security-controls
|
||||
[28]:https://www.linode.com/docs/websites/hosting-a-website
|
||||
@ -1,602 +0,0 @@
|
||||
GETTING STARTED WITH ANSIBLE
|
||||
==========
|
||||
|
||||
|
||||
This is a crash course on Ansible that you can also use as a template for small projects or to get you into this awesome tool. By the end of this guide, you will know enough to automate server configurations, deployments and more.
|
||||
|
||||
### What is Ansible and why you should care ?
|
||||
|
||||
Ansible is a configuration management system known for its simplicity. You only need ssh access to your servers or equipment. It also differs from other options because it pushes changes instead of pulling like puppet or chef normally do. You can deploy code to any number of servers, configure network equipment or automate anything in your infrastructure.
|
||||
|
||||
#### Requirements
|
||||
|
||||
It’s assumed that you are using Mac or Linux as your workstation, Ubuntu Trusty for your servers and have some experience installing packages. Also, you will need the following software on your computer. So, if you don’t have them already, go ahead and install:
|
||||
|
||||
- Virtualbox
|
||||
- Vagrant
|
||||
- Mac users: Homebrew
|
||||
|
||||
#### Scenario
|
||||
We are going to emulate 2 web application servers connecting to a MySQL database. The web application uses Rails 5 with Puma.
|
||||
|
||||
### Preparations
|
||||
|
||||
#### Vagrantfile
|
||||
|
||||
Create a folder for this project and save the following content in a file called: Vagrantfile
|
||||
|
||||
```
|
||||
VMs = [
|
||||
[ "web1", "10.1.1.11"],
|
||||
[ "web2", "10.1.1.12"],
|
||||
[ "dbserver", "10.1.1.21"],
|
||||
]
|
||||
|
||||
Vagrant.configure(2) do |config|
|
||||
VMs.each { |vm|
|
||||
config.vm.define vm[0] do |box|
|
||||
box.vm.box = "ubuntu/trusty64"
|
||||
box.vm.network "private_network", ip: vm[1]
|
||||
box.vm.hostname = vm[0]
|
||||
box.vm.provider "virtualbox" do |vb|
|
||||
vb.memory = "512"
|
||||
end
|
||||
end
|
||||
}
|
||||
end
|
||||
```
|
||||
|
||||
### Configure your virtual network
|
||||
|
||||
We want our VMs to talk to each other, but don’t let that traffic go out to your real network, so we are going to create aHost-Only adapter in Virtualbox.
|
||||
|
||||
1. Open Virtualbox
|
||||
2. Go to Preferences
|
||||
3. Go to Network
|
||||
4. Click on Host-Only networks
|
||||
5. Click to add a network
|
||||
6. Click on Adapter
|
||||
7. Set IPv4 to 10.1.1.1, IPv4 Network Mark: 255.255.255.0
|
||||
8. Click Ok
|
||||
|
||||
#### Test your VMs and virtual network
|
||||
|
||||
In a terminal, in the directory for this project where you have the Vagrantfile, type the following command:
|
||||
|
||||
```
|
||||
vagrant up
|
||||
```
|
||||
|
||||
This will create your VMs so it may take a while. Check that everything worked by typing this command and verifying the output:
|
||||
|
||||
```
|
||||
$ vagrant status
|
||||
Current machine states:
|
||||
|
||||
web1 running (virtualbox)
|
||||
web2 running (virtualbox)
|
||||
master running (virtualbox)
|
||||
|
||||
This environment represents multiple VMs. The VMs are all listed
|
||||
above with their current state. For more information about a specific
|
||||
VM, run `vagrant status NAME`.
|
||||
```
|
||||
|
||||
Now log into each one of the VMs using user & password vagrant and the IPs in the Vagrantfile, this will validate the VMs and add their keys to your known hosts file.
|
||||
|
||||
```
|
||||
ssh vagrant@10.1.1.11 # password is `vagrant`
|
||||
ssh vagrant@10.1.1.12
|
||||
ssh vagrant@10.1.1.21
|
||||
```
|
||||
|
||||
Congratulations! Now you have servers to play with. Here comes the exiting part!
|
||||
|
||||
### Install Ansible
|
||||
|
||||
For Mac users:
|
||||
|
||||
```
|
||||
$ brew install ansible
|
||||
```
|
||||
|
||||
For Ubuntu users:
|
||||
|
||||
```
|
||||
$ sudo apt install ansible
|
||||
```
|
||||
|
||||
Make sure you got a recent version of ansible that is 2.1 or superior:
|
||||
|
||||
```
|
||||
$ ansible --version
|
||||
ansible 2.1.1.0
|
||||
```
|
||||
|
||||
### The Inventory
|
||||
|
||||
Ansible uses an inventory to know what servers to work with and how to group them to perform tasks(in parallel). Let’s create our inventory for this project and name it inventory in the same folder as the Vagrantfile:
|
||||
|
||||
```
|
||||
[all:children]
|
||||
webs
|
||||
db
|
||||
|
||||
[all:vars]
|
||||
ansible_user=vagrant
|
||||
ansible_ssh_pass=vagrant
|
||||
|
||||
[webs]
|
||||
web1 ansible_host=10.1.1.11
|
||||
web2 ansible_host=10.1.1.12
|
||||
|
||||
[db]
|
||||
dbserver ansible_host=10.1.1.21
|
||||
```
|
||||
|
||||
- `[all:children]` defines a group(all) of groups
|
||||
- `[all:vars]` defines variables that belong to the group all
|
||||
- `[webs]` defines a group just like [dbs]
|
||||
- The rest of the file is just declarations of hosts, with their names and IPs
|
||||
- A blank line means end of a declaration
|
||||
|
||||
Now that we have an inventory we can start using ansible from the command line, specifying a host or a group to perform commands. Here is a typical example of a command to check connectivity to your servers:
|
||||
|
||||
```
|
||||
$ ansible -i inventory all -m ping
|
||||
```
|
||||
|
||||
- `-i` specifies the inventory file
|
||||
- `all` specifies the server or group of servers to operate
|
||||
- `-m` specifies an ansible module, in this case ping
|
||||
|
||||
Here is the output of this command:
|
||||
|
||||
```
|
||||
dbserver | SUCCESS => {
|
||||
"changed": false,
|
||||
"ping": "pong"
|
||||
}
|
||||
web1 | SUCCESS => {
|
||||
"changed": false,
|
||||
"ping": "pong"
|
||||
}
|
||||
web2 | SUCCESS => {
|
||||
"changed": false,
|
||||
"ping": "pong"
|
||||
}
|
||||
```
|
||||
|
||||
Note that servers respond with a different order. This only depends on who responds first, but is not relevant, because ansible keeps the status of each server separate.
|
||||
|
||||
You can also run any command using another switch:
|
||||
|
||||
- `-a <command>`
|
||||
|
||||
```
|
||||
$ ansible -i inventory all -a uptime
|
||||
web1 | SUCCESS | rc=0 >>
|
||||
21:43:27 up 25 min, 1 user, load average: 0.00, 0.01, 0.05
|
||||
|
||||
dbserver | SUCCESS | rc=0 >>
|
||||
21:43:27 up 24 min, 1 user, load average: 0.00, 0.01, 0.05
|
||||
|
||||
web2 | SUCCESS | rc=0 >>
|
||||
21:43:27 up 25 min, 1 user, load average: 0.00, 0.01, 0.05
|
||||
```
|
||||
|
||||
Here is another example with only one server:
|
||||
|
||||
```
|
||||
$ ansible -i inventory dbserver -a "df -h /"
|
||||
dbserver | SUCCESS | rc=0 >>
|
||||
Filesystem Size Used Avail Use% Mounted on
|
||||
/dev/sda1 40G 1.4G 37G 4% /
|
||||
```
|
||||
|
||||
### Playbooks
|
||||
|
||||
Playbooks are just YAML files that associate groups of servers in an inventory with commands. The correct word in ansible is tasks, and it can be a desired state, a shell command, or many other options. For a list of all the things you can do with ansible take a look at the list of all modules.
|
||||
|
||||
Here is an example of a playbook for running a shell command, save this as playbook1.yml:
|
||||
|
||||
```
|
||||
---
|
||||
- hosts: all
|
||||
tasks:
|
||||
- shell: uptime
|
||||
```
|
||||
|
||||
- `---` is the start of the YAML file
|
||||
- `- hosts`: specifies what group is going to be used
|
||||
- `tasks`: marks the start of a list of tasks
|
||||
- `- shell`: specifies the first task using the shell module
|
||||
- REMEMBER: YAML requires indentation so make sure you are always following the correct structure in your playbooks
|
||||
|
||||
Run it with:
|
||||
|
||||
```
|
||||
$ ansible-playbook -i inventory playbook1.yml
|
||||
|
||||
PLAY [all] *********************************************************************
|
||||
|
||||
TASK [setup] *******************************************************************
|
||||
ok: [web1]
|
||||
ok: [web2]
|
||||
ok: [dbmaster]
|
||||
|
||||
TASK [command] *****************************************************************
|
||||
changed: [web1]
|
||||
changed: [web2]
|
||||
changed: [dbmaster]
|
||||
|
||||
PLAY RECAP *********************************************************************
|
||||
dbmaster : ok=2 changed=1 unreachable=0 failed=0
|
||||
web1 : ok=2 changed=1 unreachable=0 failed=0
|
||||
web2 : ok=2 changed=1 unreachable=0 failed=0
|
||||
```
|
||||
|
||||
As you can see ansible ran 2 tasks, instead of just one we have in our playbook. The TASK [setup] is an implicit task that runs first to capture information of the servers like hostnames, IPs, distributions, and many more details, that information can then be used to run conditional tasks.
|
||||
|
||||
There is also a final PLAY RECAP where ansible shows how many tasks ran and the corresponding state for each. In our case, since we ran a shell command, ansible doesn’t know the resulting state and it’s then considered as changed.
|
||||
|
||||
|
||||
### Installing Software
|
||||
|
||||
We are going to use apt to install software on our servers, for this we need to be root, so we have to use the become statement, save this content in playbook2.yml and run it(ansible-playbook playbook2.yml):
|
||||
|
||||
```
|
||||
---
|
||||
- hosts: webs
|
||||
become_user: root
|
||||
become: true
|
||||
tasks:
|
||||
- apt: name=git state=present
|
||||
```
|
||||
|
||||
There are statements you can apply to all modules in ansible; one is the name statement that let’s you print a more descriptive text about the task being executed. In order to use it you keep your task the same but add name: descriptive text as the first line, so our previous text will be:
|
||||
|
||||
```
|
||||
---
|
||||
- hosts: webs
|
||||
become_user: root
|
||||
become: true
|
||||
tasks:
|
||||
- name: This task will make sure git is present on the system
|
||||
apt: name=git state=present
|
||||
```
|
||||
|
||||
### Using `with_items`
|
||||
|
||||
When you are dealing with a list of items, packages to install, files to create, etc. ansible provides with_items. Here is how we use it in our playbook3.yml, adding at the same time some other statements we already know:
|
||||
|
||||
```
|
||||
---
|
||||
- hosts: all
|
||||
become_user: root
|
||||
become: true
|
||||
tasks:
|
||||
- name: Installing dependencies
|
||||
apt: name={{item}} state=present
|
||||
with_items:
|
||||
- git
|
||||
- mysql-client
|
||||
- libmysqlclient-dev
|
||||
- build-essential
|
||||
- python-software-properties
|
||||
```
|
||||
|
||||
### Using `template` and `vars`
|
||||
|
||||
`vars` is one statement that defines variables you can use either in `task` statements or inside `template` files. Jinja2 is the templating engine used in Ansible, but you don’t need to learn a lot about it to use it. Define variables in your playbook like this:
|
||||
|
||||
```
|
||||
---
|
||||
- hosts: all
|
||||
vars:
|
||||
- secret_key: VqnzCLdCV9a3jK
|
||||
- path_to_vault: /opt/very/deep/path
|
||||
tasks:
|
||||
- name: Setting a configuration file using template
|
||||
template: src=myconfig.j2 dest={{path_to_vault}}/app.conf
|
||||
```
|
||||
|
||||
As you can see I can use {{path_to_vault}} as part of the playbook, but also since I am using a template statement, I can use any variable inside the myconfig.j2 file, which has to be stored in a subfolder called templates. Your project tree should look like:
|
||||
|
||||
```
|
||||
├── Vagrantfile
|
||||
├── inventory
|
||||
├── playbook1.yml
|
||||
├── playbook2.yml
|
||||
└── templates
|
||||
└── myconfig.j2
|
||||
```
|
||||
|
||||
When ansible finds a template statement it will look into the templates folder and expand the variables surrounded by{{ and }}.
|
||||
|
||||
Example template:
|
||||
|
||||
```
|
||||
this is just an example vault_dir: {{path_to_vault}} secret_password: {{secret_key}}
|
||||
```
|
||||
|
||||
You can also use `template` even if you are not expanding variables. I do this in advance considering I may add them later. For example, let’s create a `hosts.j2` template and add the hostnames and IPs:
|
||||
|
||||
```
|
||||
10.1.1.11 web1
|
||||
10.1.1.12 web2
|
||||
10.1.1.21 dbserver
|
||||
```
|
||||
|
||||
This will require a statement like this:
|
||||
|
||||
```
|
||||
- name: Installing the hosts file in all servers
|
||||
template: src=hosts.j2 dest=/etc/hosts mode=644
|
||||
```
|
||||
|
||||
### Shell commands
|
||||
|
||||
You should always try to use modules because Ansible can track the state of the task and avoid repeating it unnecessarily, but there are times when a shell command is unavoidable. For those cases Ansible offers two options:
|
||||
|
||||
- command: Literally just running a command without environment variables or redirections (|, <, >, etc.)
|
||||
- shell: Runs /bin/sh and expands variables and redirections
|
||||
|
||||
#### Other useful modules
|
||||
|
||||
- apt_repository – Add/Remove package repositories in Debian family
|
||||
- yum_repository – Add/Remove package repositories in RedHat family
|
||||
- service – Start/Stop/Restart/Enable/Disable services
|
||||
- git – Deploy code from a git server
|
||||
- unarchive – Unarchive packages from the web or local sources
|
||||
|
||||
#### Running a task only in one server
|
||||
|
||||
Rails uses `migrations` to make gradual changes to your DB, but since you have more than one app server, these migrations can not be assigned as a group task, instead we need only one server to run the migrations. In cases like this is when run_once is used, run_once will delegate the task to one server and continue with the next task until this task is done. You only need to set run_once: true in your task.
|
||||
|
||||
```
|
||||
- name: 'Run db:migrate'
|
||||
shell: cd {{appdir}};rails db:migrate
|
||||
run_once: true
|
||||
```
|
||||
|
||||
##### Tasks that can fail
|
||||
|
||||
By specifying ignore_errors: true you can run a task that may fail but doesn’t affect the completion of the rest of your playbook. This is useful, for example, when deleting a log file that initially will not exist.
|
||||
|
||||
```
|
||||
- name: 'Delete logs'
|
||||
shell: rm -f /var/log/nginx/errors.log
|
||||
ignore_errors: true
|
||||
```
|
||||
|
||||
##### Putting it all together
|
||||
|
||||
Now using what we previously learned, here is the final version of each file:
|
||||
|
||||
Vagrantfile:
|
||||
|
||||
```
|
||||
VMs = [
|
||||
[ "web1", "10.1.1.11"],
|
||||
[ "web2", "10.1.1.12"],
|
||||
[ "dbserver", "10.1.1.21"],
|
||||
]
|
||||
|
||||
Vagrant.configure(2) do |config|
|
||||
VMs.each { |vm|
|
||||
config.vm.define vm[0] do |box|
|
||||
box.vm.box = "ubuntu/trusty64"
|
||||
box.vm.network "private_network", ip: vm[1]
|
||||
box.vm.hostname = vm[0]
|
||||
box.vm.provider "virtualbox" do |vb|
|
||||
vb.memory = "512"
|
||||
end
|
||||
end
|
||||
}
|
||||
end
|
||||
```
|
||||
|
||||
inventory:
|
||||
|
||||
```
|
||||
[all:children]
|
||||
webs
|
||||
db
|
||||
|
||||
[all:vars]
|
||||
ansible_user=vagrant
|
||||
ansible_ssh_pass=vagrant
|
||||
|
||||
[webs]
|
||||
web1 ansible_host=10.1.1.11
|
||||
web2 ansible_host=10.1.1.12
|
||||
|
||||
[db]
|
||||
dbserver ansible_host=10.1.1.21
|
||||
```
|
||||
|
||||
templates/hosts.j2:
|
||||
|
||||
```
|
||||
10.1.1.11 web1
|
||||
10.1.1.12 web2
|
||||
10.1.1.21 dbserver
|
||||
```
|
||||
|
||||
templates/my.cnf.j2:
|
||||
|
||||
```
|
||||
[client]
|
||||
port = 3306
|
||||
socket = /var/run/mysqld/mysqld.sock
|
||||
|
||||
[mysqld_safe]
|
||||
socket = /var/run/mysqld/mysqld.sock
|
||||
nice = 0
|
||||
|
||||
[mysqld]
|
||||
server-id = 1
|
||||
user = mysql
|
||||
pid-file = /var/run/mysqld/mysqld.pid
|
||||
socket = /var/run/mysqld/mysqld.sock
|
||||
port = 3306
|
||||
basedir = /usr
|
||||
datadir = /var/lib/mysql
|
||||
tmpdir = /tmp
|
||||
lc-messages-dir = /usr/share/mysql
|
||||
skip-external-locking
|
||||
bind-address = 0.0.0.0
|
||||
key_buffer = 16M
|
||||
max_allowed_packet = 16M
|
||||
thread_stack = 192K
|
||||
thread_cache_size = 8
|
||||
myisam-recover = BACKUP
|
||||
query_cache_limit = 1M
|
||||
query_cache_size = 16M
|
||||
log_error = /var/log/mysql/error.log
|
||||
expire_logs_days = 10
|
||||
max_binlog_size = 100M
|
||||
|
||||
[mysqldump]
|
||||
quick
|
||||
quote-names
|
||||
max_allowed_packet = 16M
|
||||
|
||||
[mysql]
|
||||
|
||||
[isamchk]
|
||||
key_buffer = 16M
|
||||
|
||||
!includedir /etc/mysql/conf.d/
|
||||
|
||||
final-playbook.yml:
|
||||
|
||||
- hosts: all
|
||||
become_user: root
|
||||
become: true
|
||||
tasks:
|
||||
- name: 'Install common software on all servers'
|
||||
apt: name={{item}} state=present
|
||||
with_items:
|
||||
- git
|
||||
- mysql-client
|
||||
- libmysqlclient-dev
|
||||
- build-essential
|
||||
- python-software-properties
|
||||
- name: 'Install hosts file'
|
||||
template: src=hosts.j2 dest=/etc/hosts mode=644
|
||||
|
||||
- hosts: db
|
||||
become_user: root
|
||||
become: true
|
||||
tasks:
|
||||
- name: 'Software for DB server'
|
||||
apt: name={{item}} state=present
|
||||
with_items:
|
||||
- mysql-server
|
||||
- percona-xtrabackup
|
||||
- mytop
|
||||
- mysql-utilities
|
||||
- name: 'MySQL config file'
|
||||
template: src=my.cnf.j2 dest=/etc/mysql/my.cnf
|
||||
- name: 'Restart MySQL'
|
||||
service: name=mysql state=restarted
|
||||
- name: 'Grant access to web app servers'
|
||||
shell: echo 'GRANT ALL PRIVILEGES ON *.* TO "root"@"%" WITH GRANT OPTION;FLUSH PRIVILEGES;'|mysql -u root mysql
|
||||
|
||||
- hosts: webs
|
||||
vars:
|
||||
- appdir: /opt/dummyapp
|
||||
become_user: root
|
||||
become: true
|
||||
tasks:
|
||||
- name: 'Add ruby-ng repo'
|
||||
apt_repository: repo='ppa:brightbox/ruby-ng'
|
||||
- name: 'Install rails software'
|
||||
apt: name={{item}} state=present
|
||||
with_items:
|
||||
- ruby-dev
|
||||
- ruby-all-dev
|
||||
- ruby2.2
|
||||
- ruby2.2-dev
|
||||
- ruby-switch
|
||||
- libcurl4-openssl-dev
|
||||
- libssl-dev
|
||||
- zlib1g-dev
|
||||
- nodejs
|
||||
- name: 'Set ruby to 2.2'
|
||||
shell: ruby-switch --set ruby2.2
|
||||
- name: 'Install gems'
|
||||
shell: gem install bundler rails
|
||||
- name: 'Kill puma if running'
|
||||
shell: file /run/puma.pid >/dev/null && kill `cat /run/puma.pid` 2>/dev/null
|
||||
ignore_errors: True
|
||||
- name: 'Clone app repo'
|
||||
git:
|
||||
repo=https://github.com/c0d5x/rails_dummyapp.git
|
||||
dest={{appdir}}
|
||||
version=staging
|
||||
force=yes
|
||||
- name: 'Run bundler'
|
||||
shell: cd {{appdir}};bundler
|
||||
- name: 'Run db:setup'
|
||||
shell: cd {{appdir}};rails db:setup
|
||||
run_once: true
|
||||
- name: 'Run db:migrate'
|
||||
shell: cd {{appdir}};rails db:migrate
|
||||
run_once: true
|
||||
- name: 'Run rails server'
|
||||
shell: cd {{appdir}};rails server -b 0.0.0.0 -p 80 --pid /run/puma.pid -d
|
||||
```
|
||||
|
||||
### Turn up your environment
|
||||
|
||||
Having these files in the same directory, turn up your dev environment by running:
|
||||
|
||||
```
|
||||
vagrant up
|
||||
ansible-playbook -i inventory final-playbook.yml
|
||||
```
|
||||
|
||||
#### Deployment of new code
|
||||
|
||||
Make changes to your code and push those changes to your repo. Then, simply make sure you have the correct branch in your git statement:
|
||||
|
||||
```
|
||||
- name: 'Clone app repo'
|
||||
git:
|
||||
repo=https://github.com/c0d5x/rails_dummyapp.git
|
||||
dest={{appdir}}
|
||||
version=staging
|
||||
force=yes
|
||||
```
|
||||
|
||||
As an example, you can change the version field with master, run the playbook again:
|
||||
|
||||
```
|
||||
ansible-playbook -i inventory final-playbook.yml
|
||||
```
|
||||
|
||||
Check that the page has changed on any of the web servers: `http://10.1.1.11` or `http://10.1.1.12`. Change it back to `version=staging` and rerun the playbook and check the page again.
|
||||
|
||||
You can also create an alternative playbook that has only the tasks related to the deployment so that it runs faster.
|
||||
|
||||
### What is next !?
|
||||
|
||||
This is a very small portion of what ansible can do. We didn’t touch roles, filters, debugor many other awesome features that it offers, but hopefully it gives you a good start! So, go ahead and start using it and learn as you go. If you have any questions you can reach me on twitter or comment below and let me know what else you’d like to find out about ansible!
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://gorillalogic.com/blog/getting-started-with-ansible/?utm_source=webopsweekly&utm_medium=email
|
||||
|
||||
作者:[JOSE HIDALGO][a]
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 组织编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://gorillalogic.com/author/josehidalgo/
|
||||
@ -1,3 +1,5 @@
|
||||
translating---geekpi
|
||||
|
||||
Introduction to FirewallD on CentOS
|
||||
============================================================
|
||||
|
||||
|
||||
@ -1,112 +0,0 @@
|
||||
### [Getting started with Inkscape on Fedora][2]
|
||||
|
||||

|
||||
|
||||
Inkscape is a popular, full-featured, free and open source vector [graphics editor][3] available in the official Fedora repositories. It’s specifically tailored for creating vector graphics in the [SVG format][4]. Inkscape is great for creating and manipulating pictures and illustrations. It’s also good for creating diagrams, and user interface mockups.
|
||||
|
||||
[
|
||||

|
||||
][5]
|
||||
|
||||
[Windmill Landscape][1]illustration created using inkscape
|
||||
|
||||
The [screenshots page on the official website][6] has some great examples of what can be done with Inkscape. The majority of the featured images here on the Fedora Magazine are also created using Inkscape, including this recent featured image:
|
||||
|
||||
[
|
||||

|
||||
][7]
|
||||
|
||||
A recent featured image here on the Fedora Magazine that was created with Inkscape
|
||||
|
||||
### Installing Inkscape on Fedora
|
||||
|
||||
Inkscape is [available in the official Fedora repositories][8], so it’s super easy to install using the Software app in Fedora Workstation**:**
|
||||
|
||||
[
|
||||
|
||||
][9]
|
||||
|
||||
Alternatively, if you are comfortable with the command line, you can install using the following `dnf` command:
|
||||
|
||||
```
|
||||
sudo dnf install inkscape
|
||||
```
|
||||
|
||||
### Dive into Inkscape (getting started)
|
||||
|
||||
When opening the app for the first time, you are greeted with a blank page, and a bunch of different toolbars. For beginners, the three most important of these toolbars are the Toolbar, the Tools Control Bar, and the Colour Palette:
|
||||
|
||||
[
|
||||
|
||||
][10]
|
||||
|
||||
The **Toolbar** provides all the basic tools for creating drawings, including tools such as:
|
||||
|
||||
* The rectangle tool, for drawing rectangles and squares
|
||||
* The star / polygon (shapes) tool
|
||||
* The circle tool, for drawing ellipses and circles
|
||||
* The text tool, for adding labels and other text
|
||||
* The path tool, for creating or editing more complex or customized shapes
|
||||
* The select tool for selecting objects in your drawing
|
||||
|
||||
The **Colour Palette** provides a quick way to set the colour of the currently selected object. The **Tools Control Bar** provides all the settings for the currently selected tool in the Toolbar. Each time you select a new tool, the Tools Control Bar will update with the settings for that tool:
|
||||
|
||||
[
|
||||
|
||||
][11]
|
||||
|
||||
### Drawing shapes
|
||||
|
||||
Next, let’s draw a star with Inkscape. First, choose the star tool from the **Toolbar, **and click and drag on the main drawing area**.**
|
||||
|
||||
You’ll probably notice your star looks a lot like a triangle. To change this, play with the Corners option in the **Tools Control Bar**, and add a few more points. Finally, when you’re done, with the star still selected choose a colour from the **Palette** to change the colour of your star:
|
||||
|
||||
[
|
||||
|
||||
][12]
|
||||
|
||||
Next, experiment with some of the other shapes tools in the Toolbar, such as the rectangle tool, the spiral tool and the circle tool. Also play around with some of the settings for each tool to create a bunch of unique shapes.
|
||||
|
||||
### Selecting and moving objects in your drawing
|
||||
|
||||
Now you have a bunch of shapes, and can use the Select tool to move them around. To use the select tool, first select it from the toolbar, and then click on the shape you want to manipulate. Then click and drag the shape to where you want it to be.
|
||||
|
||||
When a shape is selected, you can also use the resize handles to scale the shape. Additionally, if you click on a shape that is selected, the resize handles change to rotate mode, allowing you to spin your shape:
|
||||
|
||||
[
|
||||
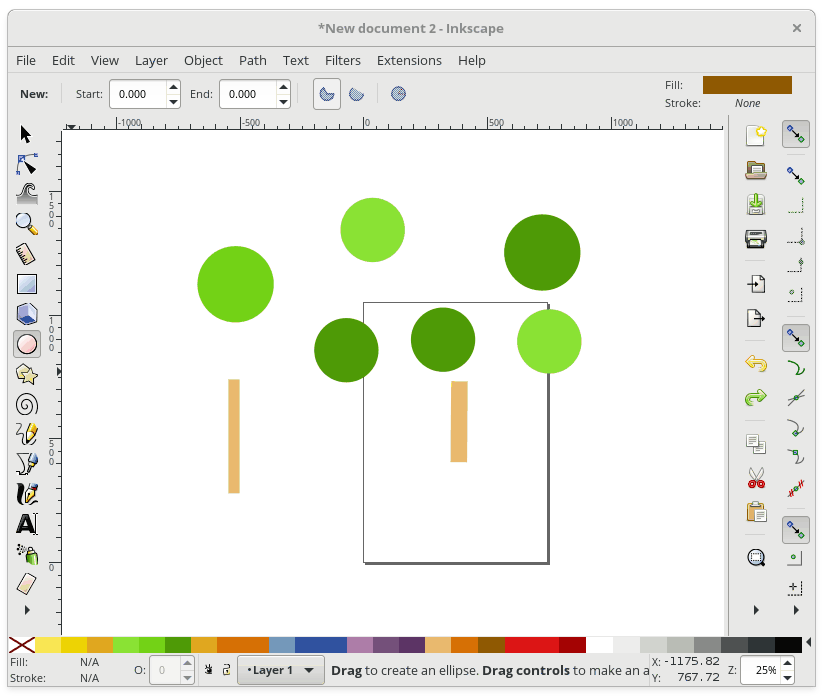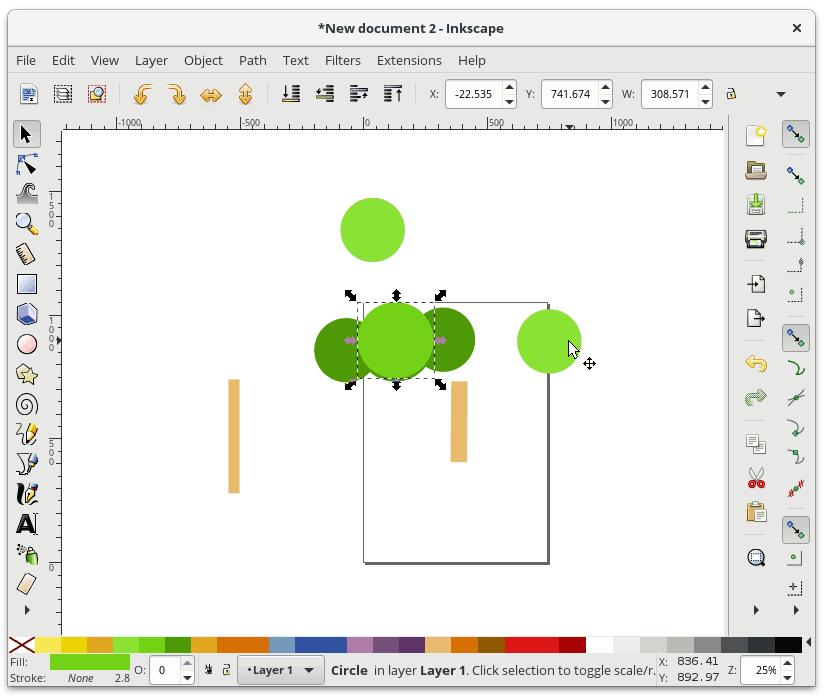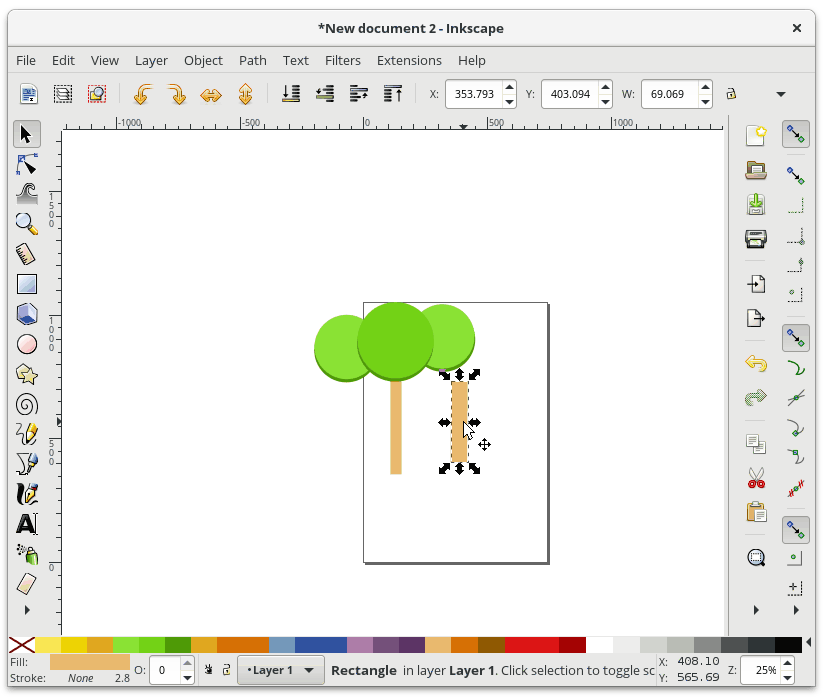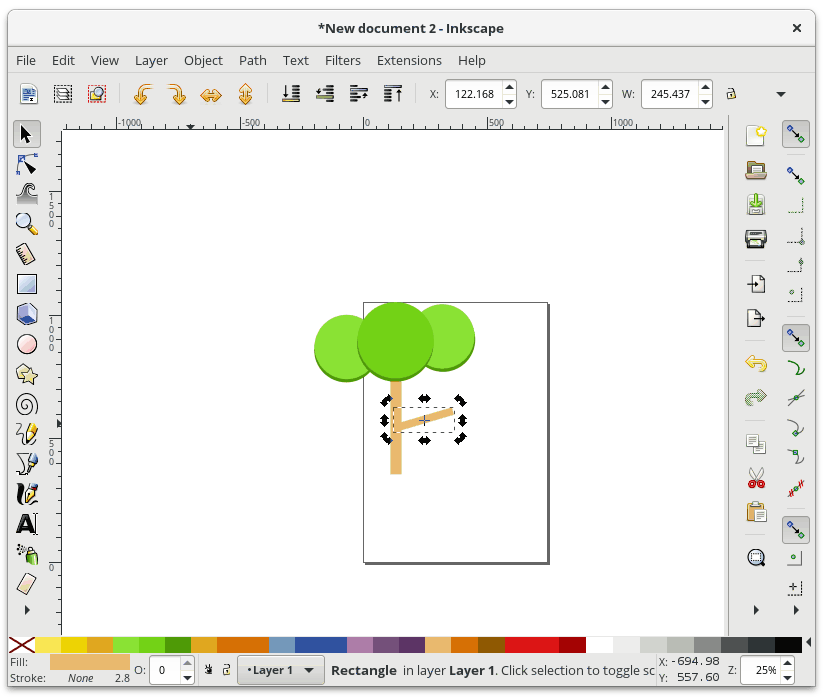
|
||||
][13]
|
||||
|
||||
* * *
|
||||
|
||||
Inkscape is an awesome piece of software that is packed with many more tools and features. In the next articles in this series, we will cover more of the features and options you can use to create awesome illustrations and documents.
|
||||
|
||||
-----------------------
|
||||
|
||||
作者简介:Ryan is a designer that works on stuff for Fedora. He uses Fedora Workstation as his primary desktop, along with the best tools from the Libre Graphics world, notably, the vector graphics editor, Inkscape.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/getting-started-inkscape-fedora/
|
||||
|
||||
作者:[Ryan Lerch][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ryanlerch.id.fedoraproject.org/
|
||||
[1]:https://openclipart.org/detail/185885/windmill-in-landscape
|
||||
[2]:https://fedoramagazine.org/getting-started-inkscape-fedora/
|
||||
[3]:https://inkscape.org/
|
||||
[4]:https://en.wikipedia.org/wiki/Scalable_Vector_Graphics
|
||||
[5]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/10/cyberscoty-landscape-800px.png
|
||||
[6]:https://inkscape.org/en/about/screenshots/
|
||||
[7]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/09/communty.png
|
||||
[8]:https://apps.fedoraproject.org/packages/inkscape
|
||||
[9]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/10/inkscape-gnome-software.png
|
||||
[10]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/10/inkscape_window.png
|
||||
[11]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/10/inkscape-toolscontrolbar.gif
|
||||
[12]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/10/inkscape-drawastar.gif
|
||||
[13]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/10/inkscape-movingshapes.gif
|
||||
@ -1,76 +0,0 @@
|
||||
translating by ypingcn.
|
||||
|
||||
How to Use Old Xorg Apps in Unity 8 on Ubuntu 16.10
|
||||
====
|
||||
|
||||

|
||||
|
||||
With the release of Ubuntu 16.10, Unity 8 has been getting more attention than usual. This is because the latest release of everyone’s favorite Linux distribution comes with an experimental desktop to play with. This desktop is the Unity environment most are used to, with a twist. It no longer is making use of X11 graphics technology and instead the makers of Ubuntu have gone a different way.
|
||||
|
||||
In its place, Unity 8 is using Mir, Ubuntu’s answer to calls for a better-performing display server on Linux. This technology has been in heavy use already on the Ubuntu phone and tablet, but this new release is the first time we’ve seen it on the desktop.
|
||||
|
||||
This technology is new and shiny. As a result, not a lot of established Linux programs can work on it, as most, if not all, of these tools are built to work with Xorg and X11\. However, if you’ve been wanting to try out Unity 8, you’ll be happy to know that it is indeed possible to get these old Xorg apps working in Unity 8\. Here’s how!
|
||||
|
||||
### Logging Into Unity 8
|
||||
|
||||

|
||||
|
||||
Unity 8 comes as an optional session in Ubuntu 16.10\. There’s one key thing to keep in mind before using it: it will not load with AMD graphics drivers, or Intel for that matter. The only supported graphics drivers as of now are the open source Nvidia drivers. To use the Unity 8 session, start up Ubuntu like normal. Then, before logging in, click the Ubuntu icon above your username and select “Unity8.” If all goes well, the new, experimental desktop will load.
|
||||
|
||||
**Note**: Unity 8 is very new and unstable. Use at your own risk.
|
||||
|
||||
### Installing Libertine
|
||||
|
||||
Xorg programs (like Firefox, etc.) do work in Unity 8; they just need a little tweak before anything will run. Start off by opening a terminal on the Mir desktop. This is done by clicking the terminal icon in the “scopes” window. Once open, enter your password. After that, enter the following commands:
|
||||
|
||||

|
||||
|
||||
```
|
||||
sudo apt install libertine-tools libertine-scope libertine
|
||||
```
|
||||
|
||||
When these programs finish installing, click and drag the scope window to refresh it. Then, click on the top-hat to launch libertine.
|
||||
|
||||
### Creating Xorg Containers
|
||||
|
||||
With Libertine open, it’s time to create some containers. These containers are special, as they allow X11 based Linux programs to run inside of a container on the Mir/Unity 8 desktop. Additionally, check the “i386 multiarch support” box for 32bit support. Otherwise, leave everything as is (or give it a name and password), and click OK.
|
||||
|
||||

|
||||
|
||||
From this point on, the Xorg container is ready to use. Look for it in Libertine and launch the container. It also should be noted that containers can be erased by right-clicking on them, then selecting the “Delete” option.
|
||||
|
||||
**Note**: each Xorg container has a maximum memory limit of 500 megabytes, so multiple containers may be necessary.
|
||||
|
||||
### Installing Software
|
||||
|
||||

|
||||
|
||||
Software is installed in Libertine containers in two ways. The first way allows for users to launch the container and select “Enter package name or Debian file,” meaning it is possible to find the name of a program in the software center or terminal and enter it into Libertine to install it. It is also possible to specify a .DEB package file for installation. It is also possible to search for the package directly within the Libertine LXC container.
|
||||
|
||||
**Note**: Unity 8 is very new, and some programs may not load or fully install with Libertine.
|
||||
|
||||
### Conclusion
|
||||
|
||||
Unity 8 shows a lot of promise. It’s modern, sleek, and faster than any iteration of Unity that came before it. The only thing that is holding it back is adoption. The simple fact is that most users would rather have programs that work instead of a fancy, fresh desktop. To an extent, using Libertine solves this issue, but it won’t work forever. Sooner or later Canonical will need to start porting programs on their own or reach out to the community as as whole to make this happen.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.maketecheasier.com/use-old-xorg-apps-unity-8/
|
||||
|
||||
作者:[Derrik Diener][a]
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 组织编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.maketecheasier.com/author/derrikdiener/
|
||||
[1]:https://www.maketecheasier.com/use-old-xorg-apps-unity-8/#respond
|
||||
|
||||
[3]:https://www.maketecheasier.com/shimo-vpn-client-for-mac/
|
||||
[4]:https://www.maketecheasier.com/schedule-windows-empty-recycle-bin/
|
||||
[5]:mailto:?subject=How%20to%20Use%20Old%20Xorg%20Apps%20in%20Unity%208%20on%20Ubuntu%2016.10&body=https%3A%2F%2Fwww.maketecheasier.com%2Fuse-old-xorg-apps-unity-8%2F
|
||||
[6]:http://twitter.com/share?url=https%3A%2F%2Fwww.maketecheasier.com%2Fuse-old-xorg-apps-unity-8%2F&text=How+to+Use+Old+Xorg+Apps+in+Unity+8+on+Ubuntu+16.10
|
||||
[7]:http://www.facebook.com/sharer.php?u=https%3A%2F%2Fwww.maketecheasier.com%2Fuse-old-xorg-apps-unity-8%2F
|
||||
[8]:https://www.maketecheasier.com/category/linux-tips/
|
||||
@ -1,127 +0,0 @@
|
||||
GHLandy Translating
|
||||
|
||||
How to check if port is in use on Linux or Unix
|
||||
============================================================
|
||||
|
||||
[
|
||||

|
||||
][1]
|
||||
|
||||
How do I determine if a port is in use under Linux or Unix-like system? How can I verify which ports are listening on Linux server?
|
||||
|
||||
It is important you verify which ports are listing on the server’s network interfaces. You need to pay attention to open ports to detect an intrusion. Apart from an intrusion, for troubleshooting purposes, it may be necessary to check if a port is already in use by a different application on your servers. For example, you may install Apache and Nginx server on the same system. So it is necessary to know if Apache or Nginx is using TCP port # 80/443\. This quick tutorial provides steps to use the netstat, nmap and lsof command to check the ports in use and view the application that is utilizing the port.
|
||||
|
||||
### How to check the listening ports and applications on Linux:
|
||||
|
||||
1. Open a terminal application i.e. shell prompt.
|
||||
2. Run any one of the following command:
|
||||
|
||||
```
|
||||
sudo lsof -i -P -n | grep LISTEN
|
||||
sudo netstat -tulpn | grep LISTEN
|
||||
sudo nmap -sTU -O IP-address-Here
|
||||
```
|
||||
|
||||
Let us see commands and its output in details.
|
||||
|
||||
### Option #1: lsof command
|
||||
|
||||
The syntax is:
|
||||
|
||||
```
|
||||
$ sudo lsof -i -P -n
|
||||
$ sudo lsof -i -P -n | grep LISTEN
|
||||
$ doas lsof -i -P -n | grep LISTEN
|
||||
```
|
||||
|
||||
### [OpenBSD] ###
|
||||
|
||||
Sample outputs:
|
||||
|
||||
[
|
||||
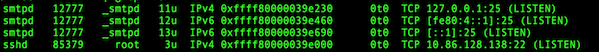
|
||||
][2]
|
||||
|
||||
Fig.01: Check the listening ports and applications with lsof command
|
||||
|
||||
Consider the last line from above outputs:
|
||||
|
||||
```
|
||||
sshd 85379 root 3u IPv4 0xffff80000039e000 0t0 TCP 10.86.128.138:22 (LISTEN)
|
||||
```
|
||||
|
||||
- sshd is the name of the application.
|
||||
- 10.86.128.138 is the IP address to which sshd application bind to (LISTEN)
|
||||
- 22 is the TCP port that is being used (LISTEN)
|
||||
- 85379 is the process ID of the sshd process
|
||||
|
||||
### Option #2: netstat command
|
||||
|
||||
You can check the listening ports and applications with netstat as follows.
|
||||
|
||||
### Linux netstat syntax
|
||||
|
||||
```
|
||||
$ netstat -tulpn | grep LISTEN
|
||||
```
|
||||
|
||||
### FreeBSD/MacOS X netstat syntax
|
||||
|
||||
```
|
||||
$ netstat -anp tcp | grep LISTEN
|
||||
$ netstat -anp udp | grep LISTEN
|
||||
```
|
||||
|
||||
### OpenBSD netstat syntax
|
||||
|
||||
````
|
||||
$ netstat -na -f inet | grep LISTEN
|
||||
$ netstat -nat | grep LISTEN
|
||||
```
|
||||
|
||||
### Option #3: nmap command
|
||||
|
||||
The syntax is:
|
||||
|
||||
```
|
||||
$ sudo nmap -sT -O localhost
|
||||
$ sudo nmap -sU -O 192.168.2.13 ##[ list open UDP ports ]##
|
||||
$ sudo nmap -sT -O 192.168.2.13 ##[ list open TCP ports ]##
|
||||
```
|
||||
|
||||
Sample outputs:
|
||||
|
||||
[
|
||||
|
||||
][3]
|
||||
|
||||
Fig.02: Determines which ports are listening for TCP connections using nmap
|
||||
|
||||
You can combine TCP/UDP scan in a single command:
|
||||
|
||||
`$ sudo nmap -sTU -O 192.168.2.13`
|
||||
|
||||
### A note about Windows users
|
||||
|
||||
You can check port usage from Windows operating system using following command:
|
||||
|
||||
```
|
||||
netstat -bano | more
|
||||
netstat -bano | grep LISTENING
|
||||
netstat -bano | findstr /R /C:"[LISTING]"
|
||||
````
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.cyberciti.biz/faq/unix-linux-check-if-port-is-in-use-command/
|
||||
|
||||
作者:[ VIVEK GITE][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.cyberciti.biz/faq/unix-linux-check-if-port-is-in-use-command/
|
||||
[1]:https://www.cyberciti.biz/faq/category/linux/
|
||||
[2]:http://www.cyberciti.biz/faq/unix-linux-check-if-port-is-in-use-command/lsof-outputs/
|
||||
[3]:http://www.cyberciti.biz/faq/unix-linux-check-if-port-is-in-use-command/nmap-outputs/
|
||||
@ -1,84 +0,0 @@
|
||||
Mir is not only about Unity8
|
||||
============================================================
|
||||
|
||||

|
||||
|
||||
_This is a guest post by Alan Griffiths, Software engineer at Canonical. If you would like to contribute a guest post, please contact ubuntu-devices@canonical.com_
|
||||
|
||||
Mir is a project to support the management applications on the display(s) of a computer. It can be compared to the more familiar X-Windows used on the current Ubuntu desktop (and many others). I’ll discuss some of the motivation for Mir below, but the point of this post is to clarify the relationship between Mir and Unity8.
|
||||
|
||||
Most of the time you hear about Mir it is mentioned alongside Unity8\. This is not surprising as Unity8 is Canonical’s new user interface shell and the thing end-users interact with. Mir “only” makes this possible. Unity8 is currently used on phones and tablets and is also available as a “preview” on the Ubuntu 16.10 desktop.
|
||||
|
||||
Here I want to explain that Mir is available to use without Unity8\. Either for an alternative shell, or as a simpler interface for embedded environments: information kiosks, electronic signage, etc. The evidence for this is proved by the Mir “Abstraction Layer” which provides three important elements:
|
||||
|
||||
1.libmiral.so – a stable interface to Mir providing basic window management;
|
||||
2\. miral-shell – a sample shell offering both “traditional” and “tiling” window management; and,
|
||||
3\. miral-kiosk – a sample “kiosk” offering only basic window management.
|
||||
|
||||
The miral-shell and miral-kiosk sample servers are available from the zesty archive and Kevin Gunn has been [blogging][1] about providing a miral-kiosk based “kiosk” snap on “Voices”. I’ll give a bit more detail about using these examples below, but there is more (including “how to” develop your own alternative Mir server) on [my “voices” blog][2].
|
||||
|
||||
**USING MIR**
|
||||
|
||||
Mir is a set of programming libraries, not an application in its own right. That means it needs applications to use it for anything to happen. There are two ways to use the Mir libraries: as a “client” when writing an application, or as a “server” when implementing a shell. Clients (as with X11) typically use a toolkit rather than using Mir (or X11) directly.
|
||||
|
||||
There’s Mir support available in GTK, Qt and SDL2\. This means that applications using these toolkits should “just work” on Mir when that support is enabled in the toolkit (which is the default in Ubuntu). In addition there’s Xmir: an X11 server that runs on Mir, this allows X based applications to run on Mir servers.
|
||||
|
||||
But a Mir client needs a corresponding Mir server before anything can happen. Over the last development cycle the Mir team has produced MirAL as the recommended way to write Mir servers and a package “miral-examples” by way of demonstration. For zesty, the development version of Ubuntu, you can install from the archive:
|
||||
|
||||
```
|
||||
$ sudo apt install miral-examples mir-graphics-drivers-desktop qtubuntu-desktop
|
||||
```
|
||||
|
||||
_For other platforms you would need to build MirAL this yourself (see An Example Mir Desktop Environment for details)._
|
||||
|
||||
With miral-examples installed you can run a Mir server as a window on your Unity7 desktop and start clients (such as gedit) within it as follows:
|
||||
|
||||
```
|
||||
$ miral-shell&
|
||||
$ miral-run gedit
|
||||
```
|
||||
|
||||
This will give you (very basic) “traditional” desktop window management. Alternatively, you can try “tiling” window management:
|
||||
|
||||
```
|
||||
$ miral-shell --window-manager tiling&
|
||||
$ miral-run qterminal
|
||||
```
|
||||
|
||||
Or the (even more basic) kiosk:
|
||||
|
||||
```
|
||||
$ miral-kiosk&
|
||||
$ miral-run 7kaa
|
||||
```
|
||||
|
||||
None of these Mir servers provide a complete “desktop” with support for a “launcher”, notifications, etc. but they demonstrate the potential to use Mir without Unity8.
|
||||
|
||||
**THE PROBLEM MIR SOLVES**
|
||||
|
||||
The X-Windows system has been, and remains, immensely successful in providing a way to interact with computers. It provides a consistent abstraction across a wide range of hardware and drivers. This underlies many desktop environments and graphical user interface toolkits and lets them work together on an enormous range of computers.
|
||||
|
||||
But it comes from an era when computers were used very differently from now, and there are real concerns today that are hard to meet given the long legacy that X needs to support.
|
||||
In 1980 most computers were big things managed by specialists and connecting them to one another was “bleeding edge”. In that era the cost of developing software was such that any benefit to be gained by one application “listening in” on another was negligible: there were few computers, they were isolated, and the work they did was not open to financial exploitation.
|
||||
|
||||
X-Windows developed in this environment and, through a series of extensions, has adapted to many changes. But it is inherently insecure: any application can find out what happening on the display (and affect it). You can write applications like Xeyes (that tracks the cursor with its “eyes”) or “Tickeys” (that listens to the keyboard to generate typewriter noises). The reality is that any and all applications can track and manipulate almost all of what is happening. That is how X based desktops like Unity7, Gnome, KDE and the rest work.
|
||||
|
||||
The open nature of window management in X-Windows is poorly adapted to a world with millions of computers connected to the Internet, being used for credit card transactions and online banking, and managed by non-experts who willingly install programs from complete strangers. There has been a growing realization that adapting X-Windows to the new requirements of security and graphics performance isn’t feasible.
|
||||
|
||||
There are at least two open source projects aimed at providing a replacement: Mir and Wayland. While some see these as competing, there are a lot of areas where they have common interests: They both need to interact with other software that previously assumed X11, and much of the work needed to introduce support alternatives benefits both projects.
|
||||
|
||||
Canonical’s replacement for X-Windows, Mir, only exposes the information to an application that it needs to have (so no snooping on keystrokes, or tracking the cursor). It can meet the needs of the current age and can exploit modern hardware such as graphics processors.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://insights.ubuntu.com/2016/11/28/mir-is-not-only-about-unity8/
|
||||
|
||||
作者:[ Guest][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 组织编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://insights.ubuntu.com/author/guest/
|
||||
[1]:http://voices.canonical.com/kevin.gunn/
|
||||
[2]:http://voices.canonical.com/alan.griffiths/
|
||||
@ -1,3 +1,5 @@
|
||||
GHLandy Translating
|
||||
|
||||
使用 NTP 进行时间同步
|
||||
============================================================
|
||||
|
||||
|
||||
@ -1,120 +0,0 @@
|
||||
translating---geekpi
|
||||
|
||||
How to Find Recent or Today’s Modified Files in Linux
|
||||
============================================================
|
||||
|
||||
In this article, we will explain two, simple [command line tips][5] that enable you to only list all today’s files.
|
||||
|
||||
One of the common problems Linux users encounter on the command line is [locating files with a particular name][6], it can be much easier when you actually know the filename.
|
||||
|
||||
However, assuming that you have forgotten the name of a file that you created (in your `home` folder which contains hundreds of files) at an earlier time during the day and yet you need to use urgently.
|
||||
|
||||
Below are different ways of only [listing all files that you created or modified][7] (directly or indirectly) today.
|
||||
|
||||
1. Using the [ls command][8], you can only list today’s files in your home folder as follows, where:
|
||||
|
||||
1. `-a` – list all files including hidden files
|
||||
2. `-l` – enables long listing format
|
||||
3. `--time-style=FORMAT` – shows time in the specified FORMAT
|
||||
4. `+%D` – show/use date in %m/%d/%y format
|
||||
|
||||
```
|
||||
# ls -al --time-style=+%D | grep 'date +%D'
|
||||
```
|
||||
[
|
||||
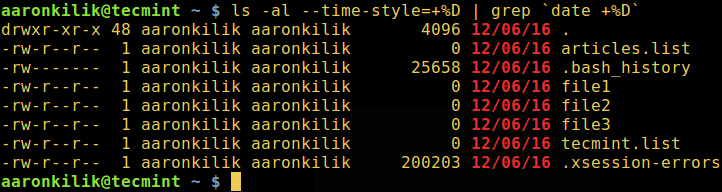
|
||||
][9]
|
||||
|
||||
Find Recent Files in Linux
|
||||
|
||||
In addition, you can [sort the resultant list alphabetically][10] by including the `-X` flag:
|
||||
|
||||
```
|
||||
# ls -alX --time-style=+%D | grep 'date +%D'
|
||||
```
|
||||
|
||||
You can also list based on size (largest first) using the `-S` flag:
|
||||
|
||||
```
|
||||
# ls -alS --time-style=+%D | grep 'date +%D'
|
||||
```
|
||||
|
||||
2. Again, it is possible to use the [find command][11] which is practically more flexible and offers plenty of options than ls, for the same purpose as below.
|
||||
|
||||
1. `-maxdepth` level is used to specify the level (in terms of sub-directories) below the starting point (current directory in this case) to which the search operation will be carried out.
|
||||
2. `-newerXY`, this works if timestamp X of the file in question is newer than timestamp Y of the file reference. X and Y represent any of the letters below:
|
||||
1. a – access time of the file reference
|
||||
2. B – birth time of the file reference
|
||||
3. c – inode status change time of reference
|
||||
4. m – modification time of the file reference
|
||||
5. t – reference is interpreted directly as a time
|
||||
|
||||
This means that, only files modified on 2016-12-06 will be considered:
|
||||
|
||||
```
|
||||
# find . -maxdepth 1 -newermt "2016-12-06"
|
||||
```
|
||||
[
|
||||
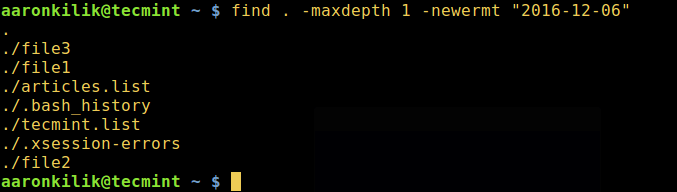
|
||||
][12]
|
||||
|
||||
Find Today’s Files in Linux
|
||||
|
||||
Important: Use the correct date format as reference in the [find command][13] above, once you use a wrong format, you will get an error as the one below:
|
||||
|
||||
```
|
||||
# find . -maxdepth 1 -newermt "12-06-2016"
|
||||
find: I cannot figure out how to interpret '12-06-2016' as a date or time
|
||||
```
|
||||
|
||||
Alternatively, use the correct formats below:
|
||||
|
||||
```
|
||||
# find . -maxdepth 1 -newermt "12/06/2016"
|
||||
OR
|
||||
# find . -maxdepth 1 -newermt "12/06/16"
|
||||
```
|
||||
[
|
||||
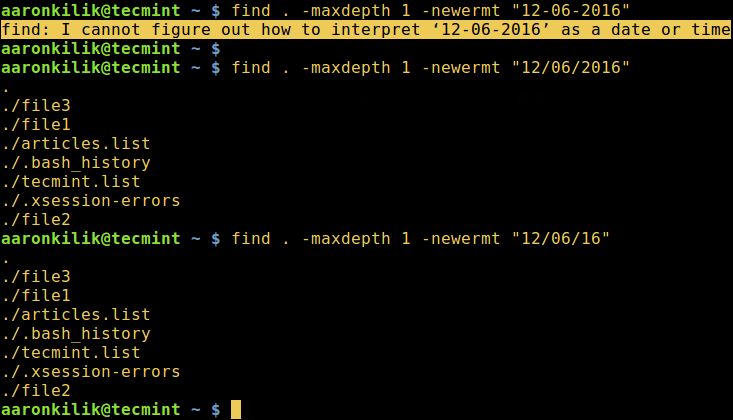
|
||||
][14]
|
||||
|
||||
Find Todays Modified Files in Linux
|
||||
|
||||
You can get more usage information for `ls` and `find` commands in our following series of articles on same.
|
||||
|
||||
1. [Master Linux ‘ls’ Command with This 15 Examples][1]
|
||||
2. [Useful 7 Quirky ‘ls’ Tricks for Linux Users][2]
|
||||
3. [Master Linux ‘find’ Command with This 35 Examples][3]
|
||||
4. [Ways to Find Multiple Filenames with Extensions in Linux][4]
|
||||
|
||||
In this article, we explained two important tips of how to list only today’s files with the help of ls and find commands. Make use of the feedback form below to send us any question(s) or comments about the topic. You can as well inform us of any commands used for the same goal.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:Aaron Kili is a Linux and F.O.S.S enthusiast, an upcoming Linux SysAdmin, web developer, and currently a content creator for TecMint who loves working with computers and strongly believes in sharing knowledge.
|
||||
|
||||
------------------
|
||||
|
||||
via: http://www.tecmint.com/find-recent-modified-files-in-linux/
|
||||
|
||||
作者:[ Aaron Kili][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/aaronkili/
|
||||
[1]:http://www.tecmint.com/15-basic-ls-command-examples-in-linux/
|
||||
[2]:http://www.tecmint.com/linux-ls-command-tricks/
|
||||
[3]:http://www.tecmint.com/35-practical-examples-of-linux-find-command/
|
||||
[4]:http://www.tecmint.com/linux-find-command-to-search-multiple-filenames-extensions/
|
||||
[5]:http://www.tecmint.com/tag/linux-tricks/
|
||||
[6]:http://www.tecmint.com/linux-find-command-to-search-multiple-filenames-extensions/
|
||||
[7]:http://www.tecmint.com/sort-ls-output-by-last-modified-date-and-time/
|
||||
[8]:http://www.tecmint.com/tag/linux-ls-command/
|
||||
[9]:http://www.tecmint.com/wp-content/uploads/2016/12/Find-Recent-Files-in-Linux.png
|
||||
[10]:http://www.tecmint.com/sort-command-linux/
|
||||
[11]:http://www.tecmint.com/35-practical-examples-of-linux-find-command/
|
||||
[12]:http://www.tecmint.com/wp-content/uploads/2016/12/Find-Todays-Files-in-Linux.png
|
||||
[13]:http://www.tecmint.com/find-directory-in-linux/
|
||||
[14]:http://www.tecmint.com/wp-content/uploads/2016/12/Find-Todays-Modified-Files.png
|
||||
@ -1,5 +1,6 @@
|
||||
# Kprobes Event Tracing on ARMv8
|
||||
|
||||
Timeszoro Translating
|
||||
|
||||

|
||||
|
||||
|
||||
603
translated/tech/20161005 GETTING STARTED WITH ANSIBLE.md
Normal file
603
translated/tech/20161005 GETTING STARTED WITH ANSIBLE.md
Normal file
@ -0,0 +1,603 @@
|
||||
开始使用Ansible
|
||||
==========
|
||||
|
||||
|
||||
这是一篇关于 Ansible 的课程,你也可以用来作小项目的模板,或者继续深入这个工具。在本指南的最后,你将了解足够的自动化服务器配置、部署等。
|
||||
|
||||
### Ansible 是什么,为什么你该了解?
|
||||
|
||||
Ansible是一个简单的配置管理系统。你只需要访问你的服务器或设备的ssh。它也不同于其他工具,因为它使用push的方式,而不是像chef那样使用pull的方式。你可以将代码部署到任意数量的服务器上,配置网络设备或在基础架构中自动执行任何操作。
|
||||
|
||||
#### 要求
|
||||
|
||||
假设你使用 Mac 或 Linux 作为你的工作站,Ubuntu Trusty为你的服务器,并有一些安装软件包的经验。此外,你的计算机上将需要以下软件。所以,如果你还没有它们,请先安装:
|
||||
|
||||
- Virtualbox
|
||||
- Vagrant
|
||||
- Mac 用户: Homebrew
|
||||
|
||||
#### 情景
|
||||
我们将模拟2个连接到MySQL数据库的Web应用程序服务器。Web应用程序使用Rails 5和Puma。
|
||||
|
||||
### 准备
|
||||
|
||||
#### Vagrantfile
|
||||
|
||||
为这个项目创建一个文件夹并将下面的内容保存到:Vagrantfile
|
||||
|
||||
```
|
||||
VMs = [
|
||||
[ "web1", "10.1.1.11"],
|
||||
[ "web2", "10.1.1.12"],
|
||||
[ "dbserver", "10.1.1.21"],
|
||||
]
|
||||
|
||||
Vagrant.configure(2) do |config|
|
||||
VMs.each { |vm|
|
||||
config.vm.define vm[0] do |box|
|
||||
box.vm.box = "ubuntu/trusty64"
|
||||
box.vm.network "private_network", ip: vm[1]
|
||||
box.vm.hostname = vm[0]
|
||||
box.vm.provider "virtualbox" do |vb|
|
||||
vb.memory = "512"
|
||||
end
|
||||
end
|
||||
}
|
||||
end
|
||||
```
|
||||
|
||||
### 配置你的虚拟网络
|
||||
|
||||
我们希望我们的虚拟机能互相交互,但不要让流量流出到真实的网络,所以我们将在Virtualbox中创建一个仅在主机的网络适配器。
|
||||
|
||||
1. 打开 Virtualbox
|
||||
2. 转到 Preferences
|
||||
3. 转到 Network
|
||||
4. 单击 Host-Only
|
||||
5. 单击添加网络
|
||||
6. 单击 Adapter
|
||||
7. 将IPv4设置为 10.1.1.1,IPv4网络掩码:255.255.255.0
|
||||
8. 单击 “OK”
|
||||
|
||||
#### 测试虚拟机及虚拟网络
|
||||
|
||||
在终端中,在具有Vagrantfile的目录中,输入下面的命令:
|
||||
|
||||
```
|
||||
vagrant up
|
||||
```
|
||||
|
||||
这回创建你的虚拟机,因此会花费一会时间。输入下面的命令并验证输出来检查是否已经工作:
|
||||
|
||||
```
|
||||
$ vagrant status
|
||||
Current machine states:
|
||||
|
||||
web1 running (virtualbox)
|
||||
web2 running (virtualbox)
|
||||
master running (virtualbox)
|
||||
|
||||
This environment represents multiple VMs. The VMs are all listed
|
||||
above with their current state. For more information about a specific
|
||||
VM, run `vagrant status NAME`.
|
||||
```
|
||||
|
||||
现在使用用户名和密码为vagrant,Vagrantfile中的IP登录其中一台虚拟机,这将验证虚拟机并将它们的密钥添加到你的已知主机文件中。
|
||||
|
||||
|
||||
```
|
||||
ssh vagrant@10.1.1.11 # password is `vagrant`
|
||||
ssh vagrant@10.1.1.12
|
||||
ssh vagrant@10.1.1.21
|
||||
```
|
||||
|
||||
恭喜你!现在你已经有可以实验的服务器了。下面的剩下的部分!
|
||||
|
||||
### 安装 Ansible
|
||||
|
||||
对于 Mac 用户:
|
||||
|
||||
```
|
||||
$ brew install ansible
|
||||
```
|
||||
|
||||
对于 Ubuntu 用户:
|
||||
|
||||
```
|
||||
$ sudo apt install ansible
|
||||
```
|
||||
|
||||
确保你使用了ansible最近的版本 2.1 或者更高的版本:
|
||||
|
||||
```
|
||||
$ ansible --version
|
||||
ansible 2.1.1.0
|
||||
```
|
||||
|
||||
### inventory
|
||||
|
||||
Ansible 使用 inventory 来了解要使用的服务器,以及如何将它们分组以并行执行任务。让我们为这个项目创建我们的 inventory,并将 inventory 放在与 Vagrantfile 相同的文件夹中:
|
||||
|
||||
```
|
||||
[all:children]
|
||||
webs
|
||||
db
|
||||
|
||||
[all:vars]
|
||||
ansible_user=vagrant
|
||||
ansible_ssh_pass=vagrant
|
||||
|
||||
[webs]
|
||||
web1 ansible_host=10.1.1.11
|
||||
web2 ansible_host=10.1.1.12
|
||||
|
||||
[db]
|
||||
dbserver ansible_host=10.1.1.21
|
||||
```
|
||||
|
||||
- `[all:children]` 定义一个组(all)的组
|
||||
- `[all:vars]` 定义属于组all的变量
|
||||
- `[webs]` 定义一个组,就像[dbs]
|
||||
- 文件的其余部分只是主机的声明,带有它们的名称和IP
|
||||
- 空行表示声明结束
|
||||
|
||||
现在我们有了一个inventory,我们可以从命令行开始使用 ansible,指定一个主机或一个组来执行命令。以下是检查与服务器的连接的命令示例:
|
||||
|
||||
```
|
||||
$ ansible -i inventory all -m ping
|
||||
```
|
||||
|
||||
- `-i` 指定inventory文件
|
||||
- `all` 指定要操作的服务器或服务器组
|
||||
- `-m' 指定一个ansible模块,在这种情况下为ping
|
||||
|
||||
下面是命令输出:
|
||||
|
||||
```
|
||||
dbserver | SUCCESS => {
|
||||
"changed": false,
|
||||
"ping": "pong"
|
||||
}
|
||||
web1 | SUCCESS => {
|
||||
"changed": false,
|
||||
"ping": "pong"
|
||||
}
|
||||
web2 | SUCCESS => {
|
||||
"changed": false,
|
||||
"ping": "pong"
|
||||
}
|
||||
```
|
||||
|
||||
服务器以不同的顺序响应,这只取决于谁先响应,但是这个没有相关,因为ansible独立保持每台服务器的状态。
|
||||
|
||||
你也可以使用另外一个选项运行任何命令:
|
||||
|
||||
- `-a <command>`
|
||||
|
||||
```
|
||||
$ ansible -i inventory all -a uptime
|
||||
web1 | SUCCESS | rc=0 >>
|
||||
21:43:27 up 25 min, 1 user, load average: 0.00, 0.01, 0.05
|
||||
|
||||
dbserver | SUCCESS | rc=0 >>
|
||||
21:43:27 up 24 min, 1 user, load average: 0.00, 0.01, 0.05
|
||||
|
||||
web2 | SUCCESS | rc=0 >>
|
||||
21:43:27 up 25 min, 1 user, load average: 0.00, 0.01, 0.05
|
||||
```
|
||||
|
||||
这是只有一台服务器的另外一个例子:
|
||||
|
||||
```
|
||||
$ ansible -i inventory dbserver -a "df -h /"
|
||||
dbserver | SUCCESS | rc=0 >>
|
||||
Filesystem Size Used Avail Use% Mounted on
|
||||
/dev/sda1 40G 1.4G 37G 4% /
|
||||
```
|
||||
|
||||
### Playbook
|
||||
|
||||
Playbook 只是 YAML 文件,它将inventory中的服务器组与命令关联。ansible的正确用法是任务,它可以是期望的状态,shell 命令或许多其他选项。有关 ansible 可做的所有事情列表,可以查看所有模块的列表。
|
||||
|
||||
下面是一个运行 shell 命令的 playbook 示例,将其保存为 playbook1.yml:
|
||||
|
||||
```
|
||||
---
|
||||
- hosts: all
|
||||
tasks:
|
||||
- shell: uptime
|
||||
```
|
||||
|
||||
- `---` 是 YAML 文件的开始
|
||||
- ` - hosts`:指定要使用的组
|
||||
- `tasks`:标记任务列表的开始
|
||||
- ` - shell`:指定使用shell模块的第一个任务
|
||||
- 记住:YAML 需要缩进,确保你始终遵循playbook中的正确结构
|
||||
|
||||
用下面的命令运行它:
|
||||
|
||||
```
|
||||
$ ansible-playbook -i inventory playbook1.yml
|
||||
|
||||
PLAY [all] *********************************************************************
|
||||
|
||||
TASK [setup] *******************************************************************
|
||||
ok: [web1]
|
||||
ok: [web2]
|
||||
ok: [dbmaster]
|
||||
|
||||
TASK [command] *****************************************************************
|
||||
changed: [web1]
|
||||
changed: [web2]
|
||||
changed: [dbmaster]
|
||||
|
||||
PLAY RECAP *********************************************************************
|
||||
dbmaster : ok=2 changed=1 unreachable=0 failed=0
|
||||
web1 : ok=2 changed=1 unreachable=0 failed=0
|
||||
web2 : ok=2 changed=1 unreachable=0 failed=0
|
||||
```
|
||||
|
||||
正如你所见,ansible 运行了 2 个任务,而不是只有 playbook 中的一个。TASK [setup]是一个隐式任务,它会首先运行以捕获服务器的信息,如主机名、IP、分布和更多详细信息,然后可以使用该信息运行条件任务。
|
||||
|
||||
还有一个最后的PLAY RECAP,其中 ansible 显示了有多少个运行的任务以及每个对应的状态。在我们的例子中,因为我们运行了一个 shell 命令,ansible 不知道结果的状态,它被认为是 changed。
|
||||
|
||||
|
||||
### 安装软件
|
||||
|
||||
我们将使用 apt 在我们的服务器上安装软件,因为我们需要root,所以我们必须使用 become 语句,将这个内容保存在 playbook2.yml 中并运行它(ansible-playbook playbook2.yml):
|
||||
|
||||
```
|
||||
---
|
||||
- hosts: webs
|
||||
become_user: root
|
||||
become: true
|
||||
tasks:
|
||||
- apt: name=git state=present
|
||||
```
|
||||
|
||||
有可以应用于 ansible 中所有模块的语句; 一个是 name 语句,让我们可以打印关于正在执行的任务的更具描述性的文本。要使用它,任务还是一样,但是添加 name 字段:描述性文本作为第一行,所以我们以前的文本将是:
|
||||
|
||||
```
|
||||
---
|
||||
- hosts: webs
|
||||
become_user: root
|
||||
become: true
|
||||
tasks:
|
||||
- name: This task will make sure git is present on the system
|
||||
apt: name=git state=present
|
||||
```
|
||||
|
||||
### 使用 `with_items`
|
||||
|
||||
当你在处理一个项目列表、要安装的包、要创建的文件等时可以用 ansible 提供的 with_items。下面是我们如何在 playbook3.yml 中使用它,同时添加一些我们已经知道的其他语句:
|
||||
|
||||
```
|
||||
---
|
||||
- hosts: all
|
||||
become_user: root
|
||||
become: true
|
||||
tasks:
|
||||
- name: Installing dependencies
|
||||
apt: name={{item}} state=present
|
||||
with_items:
|
||||
- git
|
||||
- mysql-client
|
||||
- libmysqlclient-dev
|
||||
- build-essential
|
||||
- python-software-properties
|
||||
```
|
||||
|
||||
### 使用 `template` 和 `vars`
|
||||
|
||||
`vars` 是一个定义变量语句,可以在 `task` 语句或 `template` 文件中使用。 Jinja2 是 Ansible 中使用的模板引擎,但是关于它你不需要学习很多。在你的 playbook 中定义变量,如下所示:
|
||||
|
||||
```
|
||||
---
|
||||
- hosts: all
|
||||
vars:
|
||||
- secret_key: VqnzCLdCV9a3jK
|
||||
- path_to_vault: /opt/very/deep/path
|
||||
tasks:
|
||||
- name: Setting a configuration file using template
|
||||
template: src=myconfig.j2 dest={{path_to_vault}}/app.conf
|
||||
```
|
||||
|
||||
正如你看到的,我可以使用 {{path_to_vault}} 作为 playbook 的一部分,但也因为我使用了模板语句,我可以使用 myconfig.j2 中的任何变量,它必须存在一个名为 templates 的子文件夹中。你项目树应该如下所示:
|
||||
|
||||
```
|
||||
├── Vagrantfile
|
||||
├── inventory
|
||||
├── playbook1.yml
|
||||
├── playbook2.yml
|
||||
└── templates
|
||||
└── myconfig.j2
|
||||
```
|
||||
|
||||
当 ansible 找到一个模板语句后它会在模板文件夹内查找,并将把被“{{”和“}}”括起来的变量展开来。
|
||||
|
||||
示例模板:
|
||||
|
||||
```
|
||||
this is just an example vault_dir: {{path_to_vault}} secret_password: {{secret_key}}
|
||||
```
|
||||
|
||||
即使你不扩展变量你也可以使用`模板`。考虑到将来会添加所以我先做了。比如创建一个 `hosts.j2` 模板并加入主机名和IP。
|
||||
|
||||
```
|
||||
10.1.1.11 web1
|
||||
10.1.1.12 web2
|
||||
10.1.1.21 dbserver
|
||||
```
|
||||
|
||||
这里要求像这样的语句:
|
||||
|
||||
```
|
||||
- name: Installing the hosts file in all servers
|
||||
template: src=hosts.j2 dest=/etc/hosts mode=644
|
||||
```
|
||||
|
||||
### shell 命令
|
||||
|
||||
你应该总是尝试使用模块,因为 Ansible 可以跟踪任务的状态,并避免不必要的重复,但有时 shell 命令是不可避免的。 对于这些情况,Ansible 提供两个选项:
|
||||
|
||||
- command:直接运行一个命令,没有环境变量或重定向(|,<,>等)
|
||||
- shell:运行 /bin/sh 并展开变量和重定向
|
||||
|
||||
#### 其他有用的模块
|
||||
|
||||
- apt_repository - Debian家族中添加/删除包仓库
|
||||
- yum_repository - RedHat系列中添加/删除包仓库
|
||||
- service - 启动/停止/重新启动/启用/禁用服务
|
||||
- git - 从git服务器部署代码
|
||||
- unarchive - 从Web或本地源解开软件包
|
||||
|
||||
#### 只在一台服务器中运行任务
|
||||
|
||||
Rails 使用 `migrations` 来逐步更改数据库,但由于你有多个应用程序服务器,因此这些迁移不能被分配为组任务,而只需要一个服务器来运行迁移。在这种情况下,当使用 run_once 时,run_once 将分派任务到一个服务器,并继续下一个任务,直到这个任务完成。你只需要在你的任务中设置 run_once:true。
|
||||
|
||||
```
|
||||
- name: 'Run db:migrate'
|
||||
shell: cd {{appdir}};rails db:migrate
|
||||
run_once: true
|
||||
```
|
||||
|
||||
##### 会失败的任务
|
||||
|
||||
通过指定 ignore_errors:true,你可以运行可能会失败但不影响剩余 playbook 完成的任务。这是非常有用的,例如,当删除最初不存在的日志文件时。
|
||||
|
||||
```
|
||||
- name: 'Delete logs'
|
||||
shell: rm -f /var/log/nginx/errors.log
|
||||
ignore_errors: true
|
||||
```
|
||||
|
||||
##### 放到一起
|
||||
|
||||
现在用我们先前学到的,这里是每个文件的最终版:
|
||||
|
||||
Vagrantfile:
|
||||
|
||||
```
|
||||
VMs = [
|
||||
[ "web1", "10.1.1.11"],
|
||||
[ "web2", "10.1.1.12"],
|
||||
[ "dbserver", "10.1.1.21"],
|
||||
]
|
||||
|
||||
Vagrant.configure(2) do |config|
|
||||
VMs.each { |vm|
|
||||
config.vm.define vm[0] do |box|
|
||||
box.vm.box = "ubuntu/trusty64"
|
||||
box.vm.network "private_network", ip: vm[1]
|
||||
box.vm.hostname = vm[0]
|
||||
box.vm.provider "virtualbox" do |vb|
|
||||
vb.memory = "512"
|
||||
end
|
||||
end
|
||||
}
|
||||
end
|
||||
```
|
||||
|
||||
inventory:
|
||||
|
||||
```
|
||||
[all:children]
|
||||
webs
|
||||
db
|
||||
|
||||
[all:vars]
|
||||
ansible_user=vagrant
|
||||
ansible_ssh_pass=vagrant
|
||||
|
||||
[webs]
|
||||
web1 ansible_host=10.1.1.11
|
||||
web2 ansible_host=10.1.1.12
|
||||
|
||||
[db]
|
||||
dbserver ansible_host=10.1.1.21
|
||||
```
|
||||
|
||||
templates/hosts.j2:
|
||||
|
||||
```
|
||||
10.1.1.11 web1
|
||||
10.1.1.12 web2
|
||||
10.1.1.21 dbserver
|
||||
```
|
||||
|
||||
templates/my.cnf.j2:
|
||||
|
||||
```
|
||||
[client]
|
||||
port = 3306
|
||||
socket = /var/run/mysqld/mysqld.sock
|
||||
|
||||
[mysqld_safe]
|
||||
socket = /var/run/mysqld/mysqld.sock
|
||||
nice = 0
|
||||
|
||||
[mysqld]
|
||||
server-id = 1
|
||||
user = mysql
|
||||
pid-file = /var/run/mysqld/mysqld.pid
|
||||
socket = /var/run/mysqld/mysqld.sock
|
||||
port = 3306
|
||||
basedir = /usr
|
||||
datadir = /var/lib/mysql
|
||||
tmpdir = /tmp
|
||||
lc-messages-dir = /usr/share/mysql
|
||||
skip-external-locking
|
||||
bind-address = 0.0.0.0
|
||||
key_buffer = 16M
|
||||
max_allowed_packet = 16M
|
||||
thread_stack = 192K
|
||||
thread_cache_size = 8
|
||||
myisam-recover = BACKUP
|
||||
query_cache_limit = 1M
|
||||
query_cache_size = 16M
|
||||
log_error = /var/log/mysql/error.log
|
||||
expire_logs_days = 10
|
||||
max_binlog_size = 100M
|
||||
|
||||
[mysqldump]
|
||||
quick
|
||||
quote-names
|
||||
max_allowed_packet = 16M
|
||||
|
||||
[mysql]
|
||||
|
||||
[isamchk]
|
||||
key_buffer = 16M
|
||||
|
||||
!includedir /etc/mysql/conf.d/
|
||||
|
||||
final-playbook.yml:
|
||||
|
||||
- hosts: all
|
||||
become_user: root
|
||||
become: true
|
||||
tasks:
|
||||
- name: 'Install common software on all servers'
|
||||
apt: name={{item}} state=present
|
||||
with_items:
|
||||
- git
|
||||
- mysql-client
|
||||
- libmysqlclient-dev
|
||||
- build-essential
|
||||
- python-software-properties
|
||||
- name: 'Install hosts file'
|
||||
template: src=hosts.j2 dest=/etc/hosts mode=644
|
||||
|
||||
- hosts: db
|
||||
become_user: root
|
||||
become: true
|
||||
tasks:
|
||||
- name: 'Software for DB server'
|
||||
apt: name={{item}} state=present
|
||||
with_items:
|
||||
- mysql-server
|
||||
- percona-xtrabackup
|
||||
- mytop
|
||||
- mysql-utilities
|
||||
- name: 'MySQL config file'
|
||||
template: src=my.cnf.j2 dest=/etc/mysql/my.cnf
|
||||
- name: 'Restart MySQL'
|
||||
service: name=mysql state=restarted
|
||||
- name: 'Grant access to web app servers'
|
||||
shell: echo 'GRANT ALL PRIVILEGES ON *.* TO "root"@"%" WITH GRANT OPTION;FLUSH PRIVILEGES;'|mysql -u root mysql
|
||||
|
||||
- hosts: webs
|
||||
vars:
|
||||
- appdir: /opt/dummyapp
|
||||
become_user: root
|
||||
become: true
|
||||
tasks:
|
||||
- name: 'Add ruby-ng repo'
|
||||
apt_repository: repo='ppa:brightbox/ruby-ng'
|
||||
- name: 'Install rails software'
|
||||
apt: name={{item}} state=present
|
||||
with_items:
|
||||
- ruby-dev
|
||||
- ruby-all-dev
|
||||
- ruby2.2
|
||||
- ruby2.2-dev
|
||||
- ruby-switch
|
||||
- libcurl4-openssl-dev
|
||||
- libssl-dev
|
||||
- zlib1g-dev
|
||||
- nodejs
|
||||
- name: 'Set ruby to 2.2'
|
||||
shell: ruby-switch --set ruby2.2
|
||||
- name: 'Install gems'
|
||||
shell: gem install bundler rails
|
||||
- name: 'Kill puma if running'
|
||||
shell: file /run/puma.pid >/dev/null && kill `cat /run/puma.pid` 2>/dev/null
|
||||
ignore_errors: True
|
||||
- name: 'Clone app repo'
|
||||
git:
|
||||
repo=https://github.com/c0d5x/rails_dummyapp.git
|
||||
dest={{appdir}}
|
||||
version=staging
|
||||
force=yes
|
||||
- name: 'Run bundler'
|
||||
shell: cd {{appdir}};bundler
|
||||
- name: 'Run db:setup'
|
||||
shell: cd {{appdir}};rails db:setup
|
||||
run_once: true
|
||||
- name: 'Run db:migrate'
|
||||
shell: cd {{appdir}};rails db:migrate
|
||||
run_once: true
|
||||
- name: 'Run rails server'
|
||||
shell: cd {{appdir}};rails server -b 0.0.0.0 -p 80 --pid /run/puma.pid -d
|
||||
```
|
||||
|
||||
### 打开你的环境
|
||||
|
||||
将这些文件放在相同的目录,运行下面的命令打开你的开发环境:
|
||||
|
||||
```
|
||||
vagrant up
|
||||
ansible-playbook -i inventory final-playbook.yml
|
||||
```
|
||||
|
||||
#### 部署新的代码
|
||||
|
||||
确保修改了代码并push到了仓库中。接下来,确保你git语句中有正确的分支:
|
||||
|
||||
```
|
||||
- name: 'Clone app repo'
|
||||
git:
|
||||
repo=https://github.com/c0d5x/rails_dummyapp.git
|
||||
dest={{appdir}}
|
||||
version=staging
|
||||
force=yes
|
||||
```
|
||||
|
||||
作为一个例子,你可以在master上修改version字段,再次运行 playbook:
|
||||
|
||||
```
|
||||
ansible-playbook -i inventory final-playbook.yml
|
||||
```
|
||||
|
||||
检查所有的 web 服务器上的页面是否已更改:`http:// 10.1.1.11` 或 `http:// 10.1.1.12`。将其更改为 `version = staging` 并重新运行 playbook 并再次检查页面。
|
||||
|
||||
你还可以创建只包含与部署相关的任务的替代 playbook,以便其运行更快。
|
||||
|
||||
### 接下来是什么 ?!
|
||||
|
||||
这只是可以做的很小一部分。我们没有接触角色、过滤器、调试器等许多其他很棒的功能,但我希望它给了你一个良好的开始!所以,请继续学习并使用它。如果你有任何问题,你可以在 twitter 或评论栏联系我,让我知道你还想知道哪些关于 ansible 的东西!
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://gorillalogic.com/blog/getting-started-with-ansible/?utm_source=webopsweekly&utm_medium=email
|
||||
|
||||
作者:[JOSE HIDALGO][a]
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 组织编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://gorillalogic.com/author/josehidalgo/
|
||||
@ -0,0 +1,112 @@
|
||||
### [在 Fedora 中使用 Inkscape][2]
|
||||
|
||||

|
||||
|
||||
Inkscape 是一个流行的、功能齐全、免费和开源的矢量[图形编辑器][3],它已经在 Fedora 官方仓库中。它专门为[SVG格式][4]中创建矢量图形而定制。Inkscape 非常适合创建和操作图片和插图。它也适用于创建图表和模拟用户界面。
|
||||
|
||||
[
|
||||

|
||||
][5]
|
||||
|
||||
使用inkscape创建的[风车景色][1]的插图
|
||||
|
||||
[官方网站上的截图页][6]上有一些很好的例子,说明Inkscape可以做些什么。Fedora杂志上的大多数精选图片也是使用 Inkscape 创建的,包括最近的精选图片:
|
||||
|
||||
[
|
||||

|
||||
][7]
|
||||
|
||||
最近使用 Inkscape 创建的 Fedora 杂志精选图片
|
||||
|
||||
### 在 Fedora 中安装 Inkscape
|
||||
|
||||
**Inkscape 已经[在 Fedora 官方仓库中了][8],因此可以非常简单地在 Fedora Workstation 使用 Software 这个程序安装它:**
|
||||
|
||||
[
|
||||

|
||||
][9]
|
||||
|
||||
另外,如果你习惯用命令行,你可以使用 `dnf` 命令来安装:
|
||||
|
||||
```
|
||||
sudo dnf install inkscape
|
||||
```
|
||||
|
||||
### (开始)深入 Inkscape
|
||||
|
||||
当第一次打开程序是,你会看到一个空白页面,并且有一组不同的工具栏。对于初学者,最重要的三个工具栏是:Toolbar、Tools Control Bar、 Colour Palette:
|
||||
|
||||
[
|
||||

|
||||
][10]
|
||||
|
||||
**Toolbar**提供了创建绘图的所有基本工具,包括以下工具:
|
||||
|
||||
* 矩形工具:用于绘制矩形和正方形
|
||||
* 星/多边形(形状)工具
|
||||
* 圆形工具:用于绘制椭圆和圆
|
||||
* 文本工具:用于添加标签和其他文本
|
||||
* 路径工具:用于创建或编辑更复杂或自定义的形状
|
||||
* 选择工具:用于选择图形中的对象
|
||||
|
||||
**Colour Palette** 提供了一种快速方式来设置当前选定对象的颜色。 **Tools Control Bar** 提供了工具栏中当前选定工具的所有设置。每次选择新工具时,Tools Control Bar 会变成该工具的设置:
|
||||
|
||||
[
|
||||

|
||||
][11]
|
||||
|
||||
### 绘画图形
|
||||
|
||||
接下来,让我们使用 Inkscape 绘制一个星星。 首先,从 **Toolbar** 中选择星形工具,**然后单击并拖动主绘图区域。**
|
||||
|
||||
你可能会注意到你的星看起来很像一个三角形。要更改它,请使用 “Tools Control Bar” 中的 “Corners” 选项,然后再添加几个点。 最后,当你完成后,当星星仍被选中时,从“调色板”中选择一种颜色来改变星星的颜色:
|
||||
|
||||
[
|
||||

|
||||
][12]
|
||||
|
||||
接下来,在Toolbar中实验一些其他形状工具,如矩形工具,螺旋工具和圆形工具。每个工具都设置下来创建一些独特的图形。
|
||||
|
||||
### 在绘图中选择移动对象
|
||||
|
||||
现在你有一堆图形了,你使用选择工具来移动它们。要使用选择工具,首先从工具栏中选择它,然后单击要操作的形状,接着将图形拖动到您想要的位置。
|
||||
|
||||
选择形状时,你还可以使用调整大小手柄来缩放图形。此外,如果你单击所选的图形,调整大小控点将变为旋转模式,并允许你旋转图形:
|
||||
|
||||
[
|
||||

|
||||
][13]
|
||||
|
||||
* * *
|
||||
|
||||
Inkscape是一个很棒的软件,它还包含了更多的工具和功能。在本系列的下一篇文章中,我们将介绍更多可用来创建插图和文档的功能和选项。
|
||||
|
||||
-----------------------
|
||||
|
||||
作者简介:Ryan是一名 Fedora 设计师。他使用 Fedora Workstation 作为他的主要桌面,还有来自Libre Graphics 世界的最好的工具,尤其是矢量图形编辑器 Inkscape。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/getting-started-inkscape-fedora/
|
||||
|
||||
作者:[Ryan Lerch][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ryanlerch.id.fedoraproject.org/
|
||||
[1]:https://openclipart.org/detail/185885/windmill-in-landscape
|
||||
[2]:https://fedoramagazine.org/getting-started-inkscape-fedora/
|
||||
[3]:https://inkscape.org/
|
||||
[4]:https://en.wikipedia.org/wiki/Scalable_Vector_Graphics
|
||||
[5]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/10/cyberscoty-landscape-800px.png
|
||||
[6]:https://inkscape.org/en/about/screenshots/
|
||||
[7]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/09/communty.png
|
||||
[8]:https://apps.fedoraproject.org/packages/inkscape
|
||||
[9]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/10/inkscape-gnome-software.png
|
||||
[10]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/10/inkscape_window.png
|
||||
[11]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/10/inkscape-toolscontrolbar.gif
|
||||
[12]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/10/inkscape-drawastar.gif
|
||||
[13]:https://cdn.fedoramagazine.org/wp-content/uploads/2016/10/inkscape-movingshapes.gif
|
||||
@ -0,0 +1,74 @@
|
||||
如何在 Ubuntu 16.10 的 Unity 8 上使用之前的 Xorg 程序
|
||||
====
|
||||
|
||||

|
||||
|
||||
随着 Ubuntu 16.10 的发布,Unity 8 吸引到了比平时更多的目光。这是因为这个大家最爱的 Linux 发行版的最新版本进行着一项桌面显示实验。桌面发行版是人们最熟悉的 Unity 环境,但有一点点不同。它不再使用 X11 图形技术,Ubuntu的开发者选择了另一种截然不同的方式。
|
||||
|
||||
原来,Unity 8 用的是 Mir,这是 Ubuntu 对 Linux 上更好显示服务的号召所做出的回答。这项技术已经 Ubuntu phone 和平板上大量使用,但是这次新版是我们在桌面环境上第一次见到 Mir 。
|
||||
|
||||
这项技术相当新颖,结果是没多少 Linux 程序能运行在它之上。不是所有,那也是大部分的程序被设计在 Xorg 和 X11 之上运行。如果你一直尝试在 Unity 8 上运行这些程序,当你了解到在 Unity 8上确实有可能运行之前的 Xorg 程序时,你会很开心的。接下来是如何做!
|
||||
|
||||
### 登录进 Unity 8
|
||||
|
||||

|
||||
|
||||
Unity 8 在 Ubuntu 16.10 上是一个可选会话。在使用之前只须牢记一件事情:它不会加载 AMD 的图形驱动,Intel 的同样不会加载。唯一支持的图形驱动是 Nvidia 的开源驱动。要用 Unity 8 的话,只要像往常那样启动 Ubuntu,然后,在登录进去之前,点击用户名上面的 Ubuntu 图标,选择 Unity8 选项。如果万事顺利的话,这个新的、试验性的桌面环境将会加载。
|
||||
|
||||
**注意**: Unity 8 非常新而且不稳定,自行承担使用风险。
|
||||
|
||||
### 安装 Libertine
|
||||
|
||||
Xorg 程序(例如 Firefox 等)确实能在 Unity 8 上使用,在使用之前需要一点小调整。在 Mir 桌面上用终端打开 Libertine ,在 scopes 窗口中点击终端图标就能完成。一旦打开,输入你的密码。接下来,输入以下的命令:
|
||||
|
||||

|
||||
|
||||
```
|
||||
sudo apt install libertine-tools libertine-scope libertine
|
||||
```
|
||||
|
||||
当这些程序完成安装后,点击并拖动 scopes 窗口以刷新内容。然后,在面板上点击来启动libertine。
|
||||
|
||||
### 新建 Xorg 容器
|
||||
|
||||
打开 Libertine,就到时间来新建一些容器了。这些容器很特别,因为他们能让基于 X11 的 Linux 程序在 Mir/Unity 8 桌面上的容器之中运行。另外,点击“i386 multiarch support"复选框来获得 32 位支持。否则,什么都不要动(或者输入名字和密码),点击”OK”。
|
||||
|
||||

|
||||
|
||||
在这之后,这个 Xorg 容器就准备好以供使用了。在 Libertine 找到它并启动。删除也很容易,右键点击容器,选择“删除”选项。
|
||||
|
||||
**注意**:每一个 Xorg 容器有 500 MB的最大内存限制。所以多个容器是有必要的。
|
||||
|
||||
### 安装软件
|
||||
|
||||

|
||||
|
||||
两天内在 Libertine 容器中安装好软件。第一步允许用户启动容器后选择“输入包名或者 Debian 文件”,这意味着用户可以在软件中心或者终端找到一个软件的名字,然后输入 Libertine 来安装,也可以指定特定的 DEB 文件来安装,也可以在Libertine LXC 容器中直接搜索安装包。
|
||||
|
||||
**注意**:Unity 8 非常新,一些程序或许不能在 Libertine 里加载或者完全安装。
|
||||
|
||||
### 结论
|
||||
|
||||
Unity 8展现了不少的新特性,它现代、时髦,而且比之前任何一个 Unity 迭代版本都快。唯一限制它的就是使用率。事实是大部分用户更乐意选择实用的应用程序,而不是一个别致新颖的桌面环境。某种程度上来说,使用 Libertine 能解决这个问题,但它不会永久有效。早晚有一天,Canonical 将有必要自行引进程序或者向社区求助来彻底解决这个问题。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.maketecheasier.com/use-old-xorg-apps-unity-8/
|
||||
|
||||
作者:[Derrik Diener][a]
|
||||
|
||||
译者:[ypingcn](https://github.com/ypingcn)
|
||||
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 组织编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.maketecheasier.com/author/derrikdiener/
|
||||
[1]:https://www.maketecheasier.com/use-old-xorg-apps-unity-8/#respond
|
||||
|
||||
[3]:https://www.maketecheasier.com/shimo-vpn-client-for-mac/
|
||||
[4]:https://www.maketecheasier.com/schedule-windows-empty-recycle-bin/
|
||||
[5]:mailto:?subject=How%20to%20Use%20Old%20Xorg%20Apps%20in%20Unity%208%20on%20Ubuntu%2016.10&body=https%3A%2F%2Fwww.maketecheasier.com%2Fuse-old-xorg-apps-unity-8%2F
|
||||
[6]:http://twitter.com/share?url=https%3A%2F%2Fwww.maketecheasier.com%2Fuse-old-xorg-apps-unity-8%2F&text=How+to+Use+Old+Xorg+Apps+in+Unity+8+on+Ubuntu+16.10
|
||||
[7]:http://www.facebook.com/sharer.php?u=https%3A%2F%2Fwww.maketecheasier.com%2Fuse-old-xorg-apps-unity-8%2F
|
||||
[8]:https://www.maketecheasier.com/category/linux-tips/
|
||||
@ -0,0 +1,119 @@
|
||||
如何在 \*nix 系统中验证端口是否被占用
|
||||
==========
|
||||
|
||||
[][1]
|
||||
|
||||
在 Linux 或者类 Unix 中,我该如何检查某个端口是否被占用?我又该如何验证 Linux 服务器中有哪些端口处于监听状态?
|
||||
|
||||
验证哪些端口在服务器的网络接口上处于监听状态是非常重要的。你需要注意那些用于监听指令的开放端口。暂且不说那些用于排除故障的指令,确认服务器上的某个端口是否被其他应用程序占用也是必要的。比方说,你可能会在同一个系统中安装了 Apache 和 Nginx 服务,所以了解是 Apache 还是 Nginx 占用 # 80/443 TCP端口真的很重要。本文会提及使用 netstat、nmap 和 lsof 命令来检查端口是否被占用以及查看程序使用了那些端口。
|
||||
|
||||
### 如何检查 Linux 中的监听端口和程序
|
||||
|
||||
1. 打开一个终端,如 shell 命令窗口。
|
||||
2. 运行一下任意一行命令:
|
||||
|
||||
```
|
||||
sudo lsof -i -P -n | grep LISTEN
|
||||
sudo netstat -tulpn | grep LISTEN
|
||||
sudo nmap -sTU -O IP-address-Here
|
||||
```
|
||||
|
||||
下面我们看看这些命令输出的详细内容:
|
||||
|
||||
### 选择 #1:lsof 命令
|
||||
|
||||
语法如下:
|
||||
|
||||
```
|
||||
$ sudo lsof -i -P -n
|
||||
$ sudo lsof -i -P -n | grep LISTEN
|
||||
$ doas lsof -i -P -n | grep LISTEN
|
||||
```
|
||||
|
||||
### [OpenBSD] ###
|
||||
|
||||
输出如下:
|
||||
|
||||
[][2]
|
||||
|
||||
图 1:使用 lsof 命令检查监听端口和程序
|
||||
|
||||
如上图输出的最后一行:
|
||||
|
||||
```
|
||||
sshd 85379 root 3u IPv4 0xffff80000039e000 0t0 TCP 10.86.128.138:22 (LISTEN)
|
||||
```
|
||||
|
||||
- sshd 是程序的名称
|
||||
- 10.86.128.138 是 sshd 程序绑定监听 (LISTEN) 的 IP 地址
|
||||
- 22 是被占用 (LISTEN) 的 TCP 端口
|
||||
- 85379 是 sshd 进程的进程 ID (PID)
|
||||
|
||||
### 选择 #2:netstat 命令
|
||||
|
||||
netstat 命令检查监听端口和程序的用法如下:
|
||||
|
||||
### Linux 中 netstat 语法如下:
|
||||
|
||||
```
|
||||
$ netstat -tulpn | grep LISTEN
|
||||
```
|
||||
|
||||
### FreeBSD/MacOS X 中 netstat 语法如下:
|
||||
|
||||
```
|
||||
$ netstat -anp tcp | grep LISTEN
|
||||
$ netstat -anp udp | grep LISTEN
|
||||
```
|
||||
|
||||
### OpenBSD 中 netstat 语法如下:
|
||||
|
||||
```
|
||||
$ netstat -na -f inet | grep LISTEN
|
||||
$ netstat -nat | grep LISTEN
|
||||
```
|
||||
|
||||
### 选择 #3:nmap 命令
|
||||
|
||||
语法如下:
|
||||
|
||||
```
|
||||
$ sudo nmap -sT -O localhost
|
||||
$ sudo nmap -sU -O 192.168.2.13 ##[ list open UDP ports ]##
|
||||
$ sudo nmap -sT -O 192.168.2.13 ##[ list open TCP ports ]##
|
||||
```
|
||||
|
||||
输出如下:
|
||||
|
||||
[][3]
|
||||
|
||||
图 2:使用 nmap 探测那些端口用于监听 TCP 连接
|
||||
|
||||
你可以在单个命令中同时探测 TCP/UDP 连接:
|
||||
|
||||
`$ sudo nmap -sTU -O 192.168.2.13`
|
||||
|
||||
### 关于 Windows 用户
|
||||
|
||||
你可以使用以下 Windows 自带的命令来检查端口的使用情况:
|
||||
|
||||
```
|
||||
netstat -bano | more
|
||||
netstat -bano | grep LISTENING
|
||||
netstat -bano | findstr /R /C:"[LISTING]"
|
||||
```
|
||||
|
||||
----------------------------------------------------
|
||||
|
||||
via: https://www.cyberciti.biz/faq/unix-linux-check-if-port-is-in-use-command/
|
||||
|
||||
作者:[ VIVEK GITE][a]
|
||||
译者:[GHLandy](https://github.com/GHLandy)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.cyberciti.biz/faq/unix-linux-check-if-port-is-in-use-command/
|
||||
[1]:https://www.cyberciti.biz/faq/category/linux/
|
||||
[2]:http://www.cyberciti.biz/faq/unix-linux-check-if-port-is-in-use-command/lsof-outputs/
|
||||
[3]:http://www.cyberciti.biz/faq/unix-linux-check-if-port-is-in-use-command/nmap-outputs/
|
||||
85
translated/tech/20161128 Mir is not only about Unity8.md
Normal file
85
translated/tech/20161128 Mir is not only about Unity8.md
Normal file
@ -0,0 +1,85 @@
|
||||
Mir 并不只关于Unity8
|
||||
============================================================
|
||||
|
||||

|
||||
|
||||
_这是一篇来自 Canonical 的软件工程师 Alan Griffiths 的一篇游客文章。如果你也想投稿,请联系 ubuntu-devices@canonical.com_
|
||||
|
||||
Mir 是管理程序显示的项目。它可以与当前 Ubuntu 桌面(及很多其他)上使用的我们更熟悉的X-Windows进行比较。我下面会讨论使用 Mir 的一些动机,但本篇的目的是澄清 Mir 和 Unity8 之间的关系。
|
||||
|
||||
大多数时候你听说 Mir 时都会提到 Unity8。这并不奇怪,因为 Unity8 是 Canonical 的用户shell,用户会一直与它交互。 Mir “只”使这成为可能。Unity8 目前用于手机和平板电脑,也可作为 Ubuntu 16.10 桌面上的“预览”。
|
||||
|
||||
在这里我想解释一下使用 Mir 是可以使用Unity8 的。或者作为替代 shell,或者作为嵌入式环境的更简单的接口:信息窗口,电子标牌等。Mir “抽象层”证明了这一点,它提供了三个重要的元素:
|
||||
|
||||
1\. libmiral.so - Mir 的稳定接口,提供基本的窗口管理;
|
||||
2\. miral-shell - 一个提供“传统”和“平铺”窗口管理的示例shell;
|
||||
3\. miral-kiosk - 一个仅提供基本窗口管理的示例“kiosk”。
|
||||
|
||||
miral-shell 和 miral-kiosk 示例服务器可从 zesty 的归档文件中获得,Kevin Gunn已经在[记录][1]关于在“Voices”上提供基于 miral-kiosk 的“kiosk”。我将在下面给出更多关于使用这些例子的细节,但在[我的“voices”博客][2]上有更多(包括“如何”开发自己的替代Mir服务器)。
|
||||
|
||||
**使用 MIR**
|
||||
|
||||
Mir 是一套编程库,而不是独立的程序。这意味着这需要程序去调用它实现相应的功能。有两种方式去使用Mir库:编写程序的时候作为“客户端”,或者在实现shell的实现“服务端”。客户端(和X11一起)典型是使用工具库,而不是直接使用 Mir(或者 X11)。
|
||||
|
||||
Mir支持GTK、Qt 和 SDL2 中有支持。当在那些工具集中支持它时(默认在Ubuntu中存在),意味着使用这些工具的程序应该“可以工作”于 Mir 中。除此之外还有一个 Xmir:一个运行于 Mir 的 X11 服务器,这允许基于 X 的服务运行在 Mir服务端上。
|
||||
|
||||
但是开始之前 Mir 客户端需要与 Mir 服务端通信。在最后一个开发周期中,Mir 团队在演示中将 MirAL 作为推荐的方法编写了一个 Mir 服务端和一个“miral-examples”包。关于 Ubuntu 的开版 zesty,你可以从归档中安装:
|
||||
|
||||
|
||||
```
|
||||
$ sudo apt install miral-examples mir-graphics-drivers-desktop qtubuntu-desktop
|
||||
```
|
||||
|
||||
_对于其他平台,你需要自己构建MirAL(有关详细信息,请参阅 Mir 桌面环境示例)。_
|
||||
|
||||
miral-examples 安装后你可以在 Unity7 中运行一个 Mir 服务端作为一个窗口,然后运行一个客户端(比如 gedit):
|
||||
|
||||
```
|
||||
$ miral-shell&
|
||||
$ miral-run gedit
|
||||
```
|
||||
|
||||
这会给你(非常基础)“传统” 的桌面窗口管理。另外你可以试下“tiling” 窗口管理器:
|
||||
|
||||
```
|
||||
$ miral-shell --window-manager tiling&
|
||||
$ miral-run qterminal
|
||||
```
|
||||
|
||||
或者(甚至更基础的)kiosk:
|
||||
|
||||
```
|
||||
$ miral-kiosk&
|
||||
$ miral-run 7kaa
|
||||
```
|
||||
|
||||
这些 Mir 服务端都不会提供带有“启动器”、通知等的完整“桌面”。但是它们演示了不使用 Unity8 使用 Mir 的可能。
|
||||
|
||||
**MIR 解决的问题**
|
||||
|
||||
X-Windows 系统已经并且仍然非常成功地提供了与计算机的交互方式。它提供了广泛的硬件和驱动程序一致的抽象。它支持许多桌面环境和图形用户界面工具包,并允许他们在大量计算机上一起工作。
|
||||
|
||||
但它来自一个与当前电脑使用方式不同的时代,现在有一些问题是很难满足的,因为它需要支持老旧的系统。
|
||||
在 1980 年,大多数计算机是由专家管理的大型事物,将它们连接在一起“是非常困难的”。在那个时代,开发软件的成本是这样的,一个程序“监听”另一个程序获得的好处是可以忽略不计的:此时几乎没有计算机,同时它们是独立的,它们所有的工作不对金融开放。
|
||||
|
||||
X-Windows 在这种环境下开发,通过一系列扩展,已经适应了许多变化。但它本质上是不安全的:任何应用程序可以找出在显示器上显示了什么(并影响它)。你可以编写像 Xeyes(用“眼睛”跟踪光标)或“Tickeys”(通过键盘来生成打字机噪声)等应用程序。现实是,任何和所有应用程序可以跟踪和操纵几乎所有的事情。这就是基于X的桌面如 Unity7、Gnome、KDE和其余工作。
|
||||
|
||||
X-Windows 中的窗口管理的开放性质不适合用于具有数百万计算机连接到因特网的世界,它们用于信用卡交易和网上银行,且由非专家管理,并自愿安装来自陌生人的程序。人们越来越意识到让 X-Windows 适应新的安全性和图形性能的要求是不可行的。
|
||||
|
||||
现在至少有两个开源项目旨在提供替代它:Mir 和 Wayland。虽然有些人认为两者是竞争关系,但在很多领域,它们有共同的利益:它们都需要那些假设使用 X11 的软件交互,并且许多支持工作对两者都有益。
|
||||
|
||||
Canonical 对 X-Windows 的替换品 Mir,它只将信息暴露给它需要的应用程序(因此没有按键监听或光标跟踪)。它可以满足当前时代的需求,并可以利用现代硬件,如图形处理器。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://insights.ubuntu.com/2016/11/28/mir-is-not-only-about-unity8/
|
||||
|
||||
作者:[ Guest][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 组织编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://insights.ubuntu.com/author/guest/
|
||||
[1]:http://voices.canonical.com/kevin.gunn/
|
||||
[2]:http://voices.canonical.com/alan.griffiths/
|
||||
@ -0,0 +1,119 @@
|
||||
如何在Linux中找出最近或今天被修改的文件
|
||||
============================================================
|
||||
|
||||
在本文中,我们将解释两个简单的[命令行小贴士][5],它可以帮你列出今天的所有文件。
|
||||
|
||||
Linux用户在命令行上遇到的常见问题之一是[定位具有特定名称的文件][6],当你知道真实的文件名时可能会容易得多。
|
||||
|
||||
但是,假设你忘记了在白天早些时候创建的文件的名称(在你包含了数百个文件的`home`文件夹中),但你有急用。
|
||||
|
||||
下面用不同的方式只[列出所有你今天创建或修改的文件][7](直接或间接)。
|
||||
|
||||
1.使用[ls命令][8],你只能按如下所示在你的home文件夹中列出今天的文件,其中:
|
||||
|
||||
1. `-a` - 列出所有文件,包括隐藏文件
|
||||
2. `-l` - 启用长列表格式
|
||||
3. `--time-style = FORMAT` - 显示指定FORMAT的时间
|
||||
4. `+%D` - 以%m/%d/%y格式显示/使用日期
|
||||
|
||||
```
|
||||
# ls -al --time-style=+%D | grep 'date +%D'
|
||||
```
|
||||
[
|
||||

|
||||
][9]
|
||||
|
||||
在Linux中找出最近的文件
|
||||
|
||||
In addition, you can [sort the resultant list alphabetically][10] by including the `-X` flag:
|
||||
此外,你使用可以`-X`标志来[按字母顺序对结果排序][10]:
|
||||
|
||||
```
|
||||
# ls -alX --time-style=+%D | grep 'date +%D'
|
||||
```
|
||||
|
||||
你也可以使用`-S`标志来基于大小(大的优先)来排序:
|
||||
|
||||
```
|
||||
# ls -alS --time-style=+%D | grep 'date +%D'
|
||||
```
|
||||
|
||||
2. 另外使用[find命令][11]会更灵活,并且提供比ls更多的选项,用于以下相同的目的。
|
||||
|
||||
1. `-maxdepth`级别用于指定要执行搜索操作的起点(在这个情况下为当前目录)下的搜索层级(按子目录)。
|
||||
2. `-newerXY`,如果有问题的文件的时间戳X比引用文件的时间戳Y更新,那么这个就能用了。 X和Y表示以下任何字母:
|
||||
1. a - 文件引用的访问时间
|
||||
2. B - 文件引用的创建时间
|
||||
3. c - 文件引用的inode状态改变时间
|
||||
4.m - 文件引用的修改时间
|
||||
5. t - 引用直接解释为一个时间
|
||||
|
||||
下面的命令意味着只有在2016-12-06修改的文件将被找出:
|
||||
|
||||
```
|
||||
# find . -maxdepth 1 -newermt "2016-12-06"
|
||||
```
|
||||
[
|
||||

|
||||
][12]
|
||||
|
||||
在Linux中找出今天的文件
|
||||
|
||||
重要:使参考上面的[find命令][13]中正确的日期格式,一旦你使用了错误的格式,你会得到如下错误:
|
||||
|
||||
```
|
||||
# find . -maxdepth 1 -newermt "12-06-2016"
|
||||
find: I cannot figure out how to interpret '12-06-2016' as a date or time
|
||||
```
|
||||
|
||||
或者使用下面正确的格式:
|
||||
|
||||
```
|
||||
# find . -maxdepth 1 -newermt "12/06/2016"
|
||||
或者
|
||||
# find . -maxdepth 1 -newermt "12/06/16"
|
||||
```
|
||||
[
|
||||

|
||||
][14]
|
||||
|
||||
在Linux中找出今天修改的文件
|
||||
|
||||
你可以在我们的下面一系列文章中获得`ls`和`find`命令的更多使用信息。
|
||||
|
||||
1. [用15例子的掌握Linux ‘ls’ 命令][1]
|
||||
2. [对Linux用户有用的7个奇怪的技巧][2]
|
||||
3. [用35个例子掌握Linux ‘find’ 命令][3]
|
||||
4. [在Linux中使用扩展查找多个文件名的方法][4]
|
||||
|
||||
在本文中,我们解释了如何使用ls和find命令帮助只列出今天的文件。 使用以下反馈栏向我们发送有关该主题的任何问题或意见。 你也可以提醒我们其他可以用于这个目的的命令。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:Aaron Kili是一名Linux和F.O.S.S的爱好者,将来的Linux系统管理员、网站开发人员,目前是TecMint的内容创作者,他喜欢用电脑工作,并坚信分享知识。
|
||||
|
||||
------------------
|
||||
|
||||
via: http://www.tecmint.com/find-recent-modified-files-in-linux/
|
||||
|
||||
作者:[Aaron Kili][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/aaronkili/
|
||||
[1]:http://www.tecmint.com/15-basic-ls-command-examples-in-linux/
|
||||
[2]:http://www.tecmint.com/linux-ls-command-tricks/
|
||||
[3]:http://www.tecmint.com/35-practical-examples-of-linux-find-command/
|
||||
[4]:http://www.tecmint.com/linux-find-command-to-search-multiple-filenames-extensions/
|
||||
[5]:http://www.tecmint.com/tag/linux-tricks/
|
||||
[6]:http://www.tecmint.com/linux-find-command-to-search-multiple-filenames-extensions/
|
||||
[7]:http://www.tecmint.com/sort-ls-output-by-last-modified-date-and-time/
|
||||
[8]:http://www.tecmint.com/tag/linux-ls-command/
|
||||
[9]:http://www.tecmint.com/wp-content/uploads/2016/12/Find-Recent-Files-in-Linux.png
|
||||
[10]:http://www.tecmint.com/sort-command-linux/
|
||||
[11]:http://www.tecmint.com/35-practical-examples-of-linux-find-command/
|
||||
[12]:http://www.tecmint.com/wp-content/uploads/2016/12/Find-Todays-Files-in-Linux.png
|
||||
[13]:http://www.tecmint.com/find-directory-in-linux/
|
||||
[14]:http://www.tecmint.com/wp-content/uploads/2016/12/Find-Todays-Modified-Files.png
|
||||
Loading…
Reference in New Issue
Block a user