mirror of
https://github.com/LCTT/TranslateProject.git
synced 2024-12-26 21:30:55 +08:00
last translation attempt
This commit is contained in:
parent
988d949278
commit
4f938ccaaf
@ -1,5 +1,5 @@
|
|||||||
【Translating by JanzenLiu】
|
【Translating by JanzenLiu】
|
||||||
Beyond public key encryption
|
公钥加密之外
|
||||||
============================================================
|
============================================================
|
||||||
|
|
||||||
关于应用密码学最令人扼腕也最引人入胜的一件事就是*我们在现实中实际使用的密码学是多么的少*。这并不是指密码学在业界没有被广泛的应用————事实上它的应用很广泛。我想指出的是,迄今为止密码学研究人员开发了如此多实用的技术,但工业界平常使用的却少之又少。实际上,除了少数个别情况,我们现今使用的绝大部分密码学技术是在 21 世纪初*就已经存在的技术。
|
关于应用密码学最令人扼腕也最引人入胜的一件事就是*我们在现实中实际使用的密码学是多么的少*。这并不是指密码学在业界没有被广泛的应用————事实上它的应用很广泛。我想指出的是,迄今为止密码学研究人员开发了如此多实用的技术,但工业界平常使用的却少之又少。实际上,除了少数个别情况,我们现今使用的绝大部分密码学技术是在 21 世纪初*就已经存在的技术。
|
||||||
@ -64,36 +64,38 @@ Shamir 的想法因此要求稍微更多一点的手段。相比期望身份可
|
|||||||
|
|
||||||
当然,如果你给密码学家以一个类似 IBE 的工具,那么首先他们要做的将是找到一种~~让事情更复杂~~改进它的方法。
|
当然,如果你给密码学家以一个类似 IBE 的工具,那么首先他们要做的将是找到一种~~让事情更复杂~~改进它的方法。
|
||||||
|
|
||||||
One of the biggest such improvements is due to [Sahai and Waters][23]. It’s called Attribute-Based Encryption, or ABE.
|
最大的改进之一要归功于 [Sahai 和 Waters][23]。我们称之为基于特征加密,或者 ABE (Attribute-Based Encryption).
|
||||||
|
|
||||||
The origin of this idea was not actually to encrypt with attributes. Instead Sahai and Waters were attempting to develop an _Identity-Based_ encryption scheme that could encrypt using biometrics. To understand the problem, imagine I decide to use a biometric like your [iris scan][24] as the “identity” to encrypt you a ciphertext. Later on you’ll ask the authority for a decryption key that corresponds to your own iris scan — and if everything matches up and you’ll be able to decrypt.
|
这个想法最初并不是为了用特征来加密。相反,Sahai 和 Waters 试图开发一种使用生物辨识特征来加密的*基于身份的*加密方案。为了理解这个问题,想象一下我决定使用某种生物辨识特征,比如你的 [虹膜扫描影像][24],来作为你的“身份”来加密一则给你的密文。然后你将向权威机构请求一个对应你的虹膜的解密密钥————如果一切都匹配得上,你就可以解密信息了。
|
||||||
|
|
||||||
The problem is that this will almost never work.
|
问题就在于这几乎不能奏效。
|
||||||
|
|
||||||
The issue here is that biometric readings (like iris scans or fingerprint templates) are inherently error-prone. This means every scan will typically be very _close_ , but often there will be a few bits that disagree. With standard IBE
|
因为生物辨识特征的读取(比如虹膜扫描或者指纹模板)本来就是易出错的。这意味着每一次的读取通常都是十分接近的,但却总是会几个对不上的比特。在标准的 IBE 系统中
|
||||||
|
|
||||||

|

|
||||||
Tell me this isn’t giving you nightmares.
|
告诉我这不会给你带来噩梦
|
||||||
|
|
||||||
this is _fatal_ : if the encryption identity differs from your key identity by even a single bit, decryption will not work. You’re out of luck.
|
这是灾难性的:如果加密使用的身份和你的密钥身份有哪怕是一个比特的不同,解密都会失效。你就不走运了。
|
||||||
|
|
||||||
Sahai and Waters decided that the solution to this problem was to develop a form of IBE with a “threshold gate”. In this setting, each bit of the identity is represented as a different “attribute”. Think of each of these as components you’d encrypt under — something like “bit 5 of your iris scan is a 1” and “bit 23 of your iris scan is a 0”. The encrypting party lists all of these bits and encrypts under each one. The decryption key generated by the authority embeds a similar list of bit values. The scheme is defined so that decryption will work if and only if the number of matching attributes (between your key and the ciphertext) exceeds some pre-defined threshold: _e.g.,_ any 2024 out of 2048 bits must be identical in order to decrypt.
|
Sahai 和 Waters 决定通过开发一种包含“阈值门”的 IBE 形式来解决这个问题。在这个背景下,一个身份的每一个字节都被表示为一个不同的“特征”。把每一个这种特征看作是你用于加密的一个元件————譬如“你的虹膜扫描的 5 号字节是 1”和“你的虹膜扫描的 23 号字节是 0”。加密方罗列出所有这些字节,然后将它们中的每一个都用于加密中。权威机构生成的解密密钥也嵌入了一连串相似的字节值。根据这个方案的定义,当且仅当(你的身份密钥与密文解密密钥之间)配对的特征数量超过某个预先定义的阈值时,才能顺利解密:*比如*为了能解密,2048 个字节中的(至少) 2024 个要是对应相同的。
|
||||||
|
|
||||||
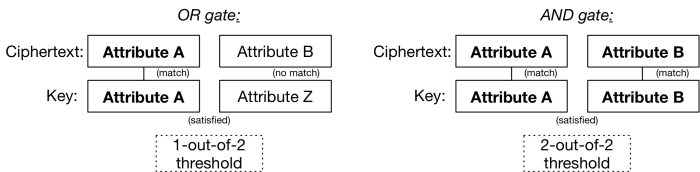
The beautiful thing about this idea is not fuzzy IBE. It’s that once you have a threshold gate and a concept of “attributes”, you can more interesting things. The [main observation][25] is that a threshold gate can be used to implement the boolean AND and OR gates, like so:
|
这个想法的优美之处不在于模糊 IBE,在于一旦你有了一个阈值门和一个“特征”的概念,你就能做更有趣的事情。[主要的观察结论][25] 是阈值门可以拥有实现 boolean 的 AND 门和 OR 门(译者认为此处应为用 AND 门和
|
||||||
|
OR 门实现, 原文: a threshold gate can be used to implement the boolean AND and OR gates),就像这样:
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
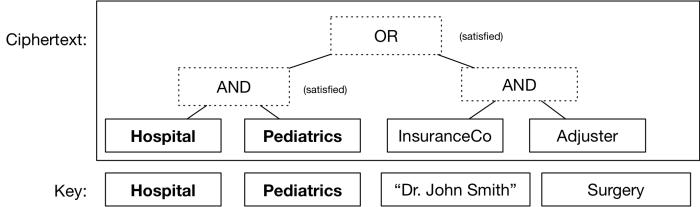
Even better, you can _stack_ these gates on top of one another to assign a fairly complex boolean formula — which will itself determine what conditions your ciphertext can be decrypted under. For example, switching to a more realistic set of attributes, you could encrypt a medical record so that either a pediatrician in a hospital could read it, _or_ an insurance adjuster could. All you’d need is to make sure people received keys that correctly described _their_ attributes (which are just arbitrary strings, like identities).
|
甚至你还可以将这些逻辑闸门*堆叠*起来,一些在另一些之上,来表示一些相当复杂的 boolean 表达式————这些表达式本身就用于判定在什么情况下你的密文可以被解密。举个例子,考虑一组更为现实的特征,你可以这样加密一份医学记录,使医院的儿科医生*或者*保险理算员都可以阅读它。你所需要做的只不过是保证人们可以得到正确描述*他们的*特征的密钥(就是一些任意的字符串,如同身份那样)。
|
||||||
|
|
||||||
|

|
||||||
A simple “ciphertext policy”, in which the ciphertext can be decrypted if and only if a key matches an appropriate set of attributes. In this case, the key satisfies the formula and thus the ciphertext decrypts. The remaining key attributes are ignored.
|
一个简单的“密文规定”。在这个规定中当且仅当一个密钥与一组特定的特征匹配时,密文才能被解密。在这个案例中,密钥满足公式的条件,因此密文将被解密。其余用不到的特征在这里忽略掉。
|
||||||
|
|
||||||
The other direction can be implemented as well. It’s possible to encrypt a ciphertext under a long list of attributes, such as creation time, file name, and even GPS coordinates indicating where the file was created. You can then have the authority hand out keys that correspond to a very precise slice of your dataset — for example, “this key decrypts any radiology file encrypted in Chicago between November 3rd and December 12th that is tagged with ‘pediatrics’ or ‘oncology'”.
|
其他的条件判断也能实现。通过一长串特征,比如文件创建时间,文件名,甚至指示文件创建位置的 GPS 坐标, 来加密密文也是有可能的。于是你可以让权威机构分发一部分对应你的数据集非常精确的一部分的密钥————比如说,“该密钥用于解密所有在 11 月 3 号和 12 月 12 号之间在芝加哥被加密的包含‘小儿科’或者‘肿瘤科’标记的放射科文件”。
|
||||||
|
|
||||||
### Functional Encryption
|
### 函数式加密
|
||||||
|
|
||||||
Once you have a related of primitives like IBE and ABE, the researchers’ instinct is to both extend and generalize. Why stop at simple boolean formulae? Can we make keys (or ciphertexts) that embed _arbitrary computer programs? _ The answer, it turns out, is yes — though not terribly efficiently. A set of [recent][26] [works][27] show that it is possible to build ABE that works over arbitrary polynomial-size circuits, using various lattice-based assumptions. So there is certainly a lot of potential here.
|
一旦拥有一个相关的基础工具,像 IBE 和 ABE,研究人员的本能是去扩充和一般化它。为什么要止步于简单的 boolean 表达式?我们能不能制作嵌入了*任意的计算机程序*的密钥(或者密文)?答案被证明是肯定的————尽管不是非常高效。一组 [近几年的][26] [研究][27] 显示可以根据各种各样的基于格的密码假设,构建在任意多项式大小线路运作的 ABE。所以这一方向毫无疑问非常有发展潜力。
|
||||||
|
|
||||||
|
这一潜力启发了研究人员将所有以上的想法一般化成为一个被称作 “[函数式加密]” 的单独的类。函数式加密更多是一种抽象的概念而没有具体所指————它不过是一种将所有这些系统看作是一个特定的累的实例的方式。它基本的想法是,
|
||||||
This potential has inspired researchers to generalize all of the above ideas into a single class of encryption called “[functional encryption][28]“. Functional encryption is more conceptual than concrete — it’s just a way to look at all of these systems as instances of a specific class. The basic idea is to represent the decryption procedure as an algorithm that computes an arbitary function _F_ over (1) the plaintext inside of a ciphertext, and (2) the data embedded in the key. This function has the following profile:
|
This potential has inspired researchers to generalize all of the above ideas into a single class of encryption called “[functional encryption][28]“. Functional encryption is more conceptual than concrete — it’s just a way to look at all of these systems as instances of a specific class. The basic idea is to represent the decryption procedure as an algorithm that computes an arbitary function _F_ over (1) the plaintext inside of a ciphertext, and (2) the data embedded in the key. This function has the following profile:
|
||||||
|
|
||||||
_output = F(key data, plaintext data)_
|
_output = F(key data, plaintext data)_
|
||||||
|
|||||||
Loading…
Reference in New Issue
Block a user