mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-28 23:20:10 +08:00
commit
4cbe2ee5b9
@ -1,8 +1,8 @@
|
||||
Linux 下如何处理包含空格和特殊字符的文件名
|
||||
================================================================================
|
||||
我们经常会看到文件名和文件夹名。大多数时候文件/文件夹的名字和内容相关并以数字和字母开头。字母-数字文件名最常见,应用也很广泛,但总会需要处理一些包含特殊字符的文件名/文件夹名。
|
||||
我们经常会看到文件名和文件夹名。大多数时候文件/文件夹的名字和内容相关并以数字和字母开头。字母加数字的文件名最常见,应用也很广泛,但总会需要处理一些包含特殊字符的文件名/文件夹名。
|
||||
|
||||
** 注意 **:我们可能有各种类型的文件,但是为了简单以及方便实现,在本文中我们只处理文本文件(.txt)。
|
||||
** 注意 **:我们可能有各种类型的文件,但是为了简单以及方便实现,在本文中我们只用文本文件(.txt)做演示。
|
||||
|
||||
最常见的文件名例子:
|
||||
|
||||
@ -38,9 +38,9 @@ Linux 下如何处理包含空格和特殊字符的文件名
|
||||
--bk34.txt
|
||||
...
|
||||
|
||||
一个显而易见的问题是 - 在这个星球上有谁会创建/处理包含井号`(#)`,分号`(;)`,破折号`(-)`或其他特殊字符的文件/文件夹啊。
|
||||
一个显而易见的问题是 - 在这个星球上有谁会创建和处理包含井号`(#)`,分号`(;)`,破折号`(-)`或其他特殊字符的文件/文件夹啊。
|
||||
|
||||
我和你想的一样,这种文件名确实不常见,不过在你必须得处理这种文件名的时候你的 shell 也不应该出错或罢工。而且技术上来说,Linux 下的一切比如文件夹,驱动器或其他所有的都被当作文件处理。
|
||||
我和你想的一样,这种文件名确实不常见,不过在你必须得处理这种文件名的时候你的 shell 也不应该出错或罢工。而且技术上来说,Linux 下的一切比如文件夹、驱动器或其他所有的都被当作文件处理。
|
||||
|
||||
### 处理名字包含破折号(-)的文件 ###
|
||||
|
||||
@ -99,9 +99,9 @@ Linux 下如何处理包含空格和特殊字符的文件名
|
||||
|
||||
**重要:**
|
||||
|
||||
1. 上面讨论的规则可以同样应用于名字中包含任意数量以及位置连接符号的文件。就是说,-a-b-c.txt,ab-c.txt,abc-.txt,等等。
|
||||
1. 上面讨论的规则可以同样应用于名字中包含任意数量以及任意位置的连接符号的文件。就是说,-a-b-c.txt,ab-c.txt,abc-.txt,等等。
|
||||
|
||||
2. 上面讨论的规则可以同样应用于名字中包含任意数量以及位置连接符号的文件夹,除了一种情况,在删除一个文件夹的时候你得这样使用`rm -rf`:
|
||||
2. 上面讨论的规则可以同样应用于名字中包含任意数量以及任意位置连接符号的文件夹,除了一种情况,在删除一个文件夹的时候你得这样使用`rm -rf`:
|
||||
|
||||
$ rm -rf -- -abc
|
||||
或者
|
||||
@ -124,7 +124,7 @@ Linux 下如何处理包含空格和特殊字符的文件名
|
||||
|
||||
出现上面错误的原因是,BASH 将 #abc.txt 解释为评论而忽略了。所以[命令 touch][2]没有收到任何文件作为参数,所以导致这个错误。
|
||||
|
||||
要解决这个问题,你肯能需要告诉 BASH 不要将 # 解释为评论。
|
||||
要解决这个问题,你可能需要告诉 BASH 不要将 # 解释为评论。
|
||||
|
||||
$ touch ./#abc.txt
|
||||
或者
|
||||
@ -140,8 +140,7 @@ Linux 下如何处理包含空格和特殊字符的文件名
|
||||
现在创建名字中除了开头的其他地方包含 # 的文件。
|
||||
|
||||
$ touch ./a#bc.txt
|
||||
$ touch ./abc#.txt
|
||||
|
||||
$ touch ./abc#.txt
|
||||
或者
|
||||
$ touch 'a#bc.txt'
|
||||
$ touch 'abc#.txt'
|
||||
@ -197,8 +196,6 @@ Linux 下如何处理包含空格和特殊字符的文件名
|
||||
或者
|
||||
$ vi '#cd.txt'
|
||||
|
||||
----------
|
||||
|
||||
$ nano ./#cd.txt
|
||||
或者
|
||||
$ nano '#cd.txt'
|
||||
@ -261,7 +258,7 @@ Linux 下如何处理包含空格和特殊字符的文件名
|
||||
|
||||
#### 文件名包含星号 (*) ####
|
||||
|
||||
名字包含星号的文件没有改变太多,你仍然可以把它当作一个普通文件。(注:星号在 shell 里有特殊意义,用作文件名最好用单引号括起来或使用反斜杠转义)
|
||||
需要用单引号括起来或使用反斜杠转义。(LCTT 译注:此处原文有误,已修改。)
|
||||
|
||||
$ touch *12.txt
|
||||
|
||||
@ -271,9 +268,9 @@ Linux 下如何处理包含空格和特殊字符的文件名
|
||||
或者
|
||||
$ rm -rf *
|
||||
|
||||
而是用这样的命令,(注:这个命令是删除当前目录所有.txt文件。。。)
|
||||
而是用这样的命令,(LCTT 译注:此处原文有误,已修改)
|
||||
|
||||
$ rm ./*.txt
|
||||
$ rm ./'*.txt'
|
||||
|
||||
#### 文件名包含叹号 (!) ####
|
||||
|
||||
@ -307,9 +304,9 @@ Linux 下如何处理包含空格和特殊字符的文件名
|
||||
|
||||
#### 文件名包含花括号 {} ####
|
||||
|
||||
不需要特别注意。可以当作普通文件处理。(注:花括号在 shell 里有特殊意义,用作文件名最好用单引号括起来或使用反斜杠转义)
|
||||
用单引号括起来或使用反斜杠转义。(LCTT 译注:此处原文有误,已修改)
|
||||
|
||||
$ touch {12.txt}
|
||||
$ touch '{12.txt}'
|
||||
|
||||
#### 文件名包含尖括号 <> ####
|
||||
|
||||
@ -319,21 +316,21 @@ Linux 下如何处理包含空格和特殊字符的文件名
|
||||
|
||||
#### 文件名包含方括号 [ ] ####
|
||||
|
||||
名字包含方括号的文件可以当作普通文件,不用特别处理。(注:方括号在 shell 里有特殊意义,用作文件名最好用单引号括起来或使用反斜杠转义)
|
||||
用单引号括起来或使用反斜杠转义。(LCTT 译注:此处原文有误,已修改)
|
||||
|
||||
$ touch [12.txt]
|
||||
$ touch '[12.txt]'
|
||||
|
||||
#### 文件名包含下划线 (_) ####
|
||||
|
||||
这个非常普遍不需要特殊对待。当作普通文件随意处理。
|
||||
这个非常普遍,不需要特殊对待。当作普通文件随意处理。
|
||||
|
||||
$ touch _12.txt
|
||||
|
||||
#### 文件名包含等号 (=) ####
|
||||
|
||||
文件名包含等号不会改变任何事情,你可以当作普通文件。(注:等号在 shell 里有特殊意义,用作文件名最好用单引号括起来或使用反斜杠转义)
|
||||
用单引号括起来或使用反斜杠转义。(LCTT 译注:此处原文有误,已修改)
|
||||
|
||||
$ touch =12.txt
|
||||
$ touch '=12.txt'
|
||||
|
||||
#### 处理反斜杠 (\) ####
|
||||
|
||||
@ -349,9 +346,9 @@ Linux 下如何处理包含空格和特殊字符的文件名
|
||||
|
||||
#### 文件名包含问号 (?) ####
|
||||
|
||||
再一次,这个也是不需要特别处理的情况。名字包含问号的文件可以和大多数情况一样对待。(注:问号在 shell 里有特殊意义,用作文件名最好用单引号括起来或使用反斜杠转义)
|
||||
用单引号括起来或使用反斜杠转义。(LCTT 译注:此处原文有误,已修改)
|
||||
|
||||
$ touch ?12.txt
|
||||
$ touch '?12.txt'
|
||||
|
||||
#### 文件名包含点 (.) ####
|
||||
|
||||
@ -382,25 +379,25 @@ Linux 下如何处理包含空格和特殊字符的文件名
|
||||
|
||||
#### 文件名包含冒号 (:) ####
|
||||
|
||||
你可以在文件名中使用冒号,可以有任意多个而不用特殊对待。就像平时普通名字文件那样处理。(注:冒号在 shell 里有特殊意义,用作文件名最好用单引号括起来或使用反斜杠转义)
|
||||
用单引号括起来或使用反斜杠转义。(LCTT 译注:此处原文有误,已修改)
|
||||
|
||||
$ touch :12.txt
|
||||
$ touch ':12.txt'
|
||||
或者
|
||||
$ touch :12:.txt
|
||||
$ touch ':12:.txt'
|
||||
|
||||
#### 文件名包含引号(单引号和双引号) ####
|
||||
|
||||
要在文件名里使用引号,我们需要使用交替规则。例如,如果你需要在文件名里使用单引号,那就用双引号把文件名括起来。而如果你需要在文件名里使用双引号,那就用单引号把文件名括起来。
|
||||
要在文件名里使用引号,我们需要使用交替规则。例如,如果你需要在文件名里使用单引号,那就用双引号把文件名括起来。而如果你需要在文件名里使用双引号,那就用单引号把文件名括起来。(LCTT 译注:或者如果单引号和双引号混杂的情况,你也可以用反斜杠转义。)
|
||||
|
||||
$ touch "15'.txt"
|
||||
|
||||
以及
|
||||
|
||||
$ touch '15”.txt'
|
||||
$ touch '15".txt'
|
||||
|
||||
#### 文件名包含波浪号 (~) ####
|
||||
|
||||
Linux 下一些像 emacs 这样的文本编辑器在编辑文件的时候会创建备份文件。这个备份文件的名字是在原文件名后面附加一个波浪号。你可以在文件名任意位置使用波浪号,例如:(注:波浪号在 shell 里有特殊意义,用作文件名最好用单引号括起来或使用反斜杠转义)
|
||||
Linux 下一些像 emacs 这样的文本编辑器在编辑文件的时候会创建备份文件。这个备份文件的名字是在原文件名后面附加一个波浪号。你可以在文件名任意位置使用波浪号,例如:
|
||||
|
||||
$ touch ~1a.txt
|
||||
或者
|
||||
@ -426,10 +423,10 @@ via: http://www.tecmint.com/manage-linux-filenames-with-special-characters/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[zpl1025](https://github.com/zpl1025)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:http://www.tecmint.com/15-basic-ls-command-examples-in-linux/
|
||||
[1]:https://linux.cn/article-5349-1.html
|
||||
[2]:http://www.tecmint.com/8-pratical-examples-of-linux-touch-command/
|
||||
@ -0,0 +1,240 @@
|
||||
在 RHEL/CentOS 7.0 中安装 LAMP(Linux、 Apache、 MariaDB、 PHP/PhpMyAdmin)
|
||||
================================================================================
|
||||
|
||||
跳过 LAMP 的介绍,因为我认为你们大多数已经知道了。这个教程会集中在如何在升级到 Apache 2.4 的 Red Hat Enterprise Linux 7.0 和 CentOS 7.0 中安装和配置 LAMP:Linux、Apache、 MariaDB、 PHP/PhpMyAdmin。
|
||||
|
||||

|
||||
|
||||
*在 RHEL/CentOS 7.0 中安装 LAMP*
|
||||
|
||||
#### 前置要求 ####
|
||||
|
||||
根据使用的发行版是 RHEL 还是 CentOS 7.0,按照下面的链接来进行最小化的系统安装,网络使用静态 IP。
|
||||
|
||||
**对于 RHEL 7.0**
|
||||
|
||||
- [RHEL 7.0 安装过程][1]
|
||||
- [在 RHEL 7.0 中注册和启用订阅仓库][2]
|
||||
|
||||
**对于 CentOS 7.0**
|
||||
|
||||
- [CentOS 7.0 安装过程][3]
|
||||
|
||||
### 第一步:使用基本配置安装apache ###
|
||||
|
||||
1、在完成最小化系统安装,并[在 RHEL/CentOS 7.0 上配置静态 IP][4] 后,就可以使用下面的命令从官方仓库安装最新的 Apache 2.4 httpd 服务了。
|
||||
|
||||
# yum install httpd
|
||||
|
||||
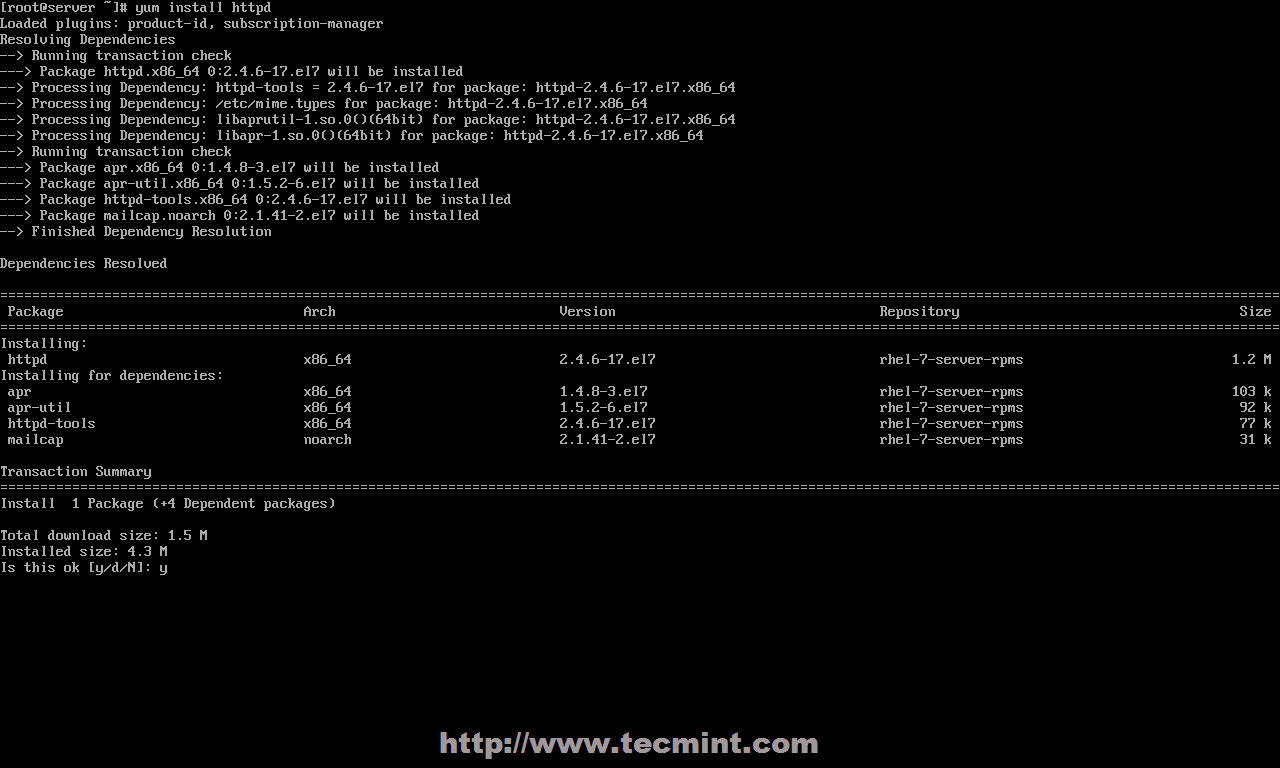
|
||||
|
||||
*安装 apache 服务*
|
||||
|
||||
2、安装完成后,使用下面的命令来管理apache守护进程,因为 RHEL 和 CentOS 7.0 都将 init 脚本从 SysV 升级到了systemd,所以同时你还可以使用 SysV 脚本和 Apache 脚本来管理服务。
|
||||
|
||||
# systemctl status|start|stop|restart|reload httpd
|
||||
|
||||
或者
|
||||
|
||||
# service httpd status|start|stop|restart|reload
|
||||
|
||||
或者
|
||||
|
||||
# apachectl configtest| graceful
|
||||
|
||||

|
||||
|
||||
*启动apache服务*
|
||||
|
||||
3、在使用 systemd 初始化脚本来启动 apache 服务后,要用 `firewall-cmd` 打开 RHEL/CentOS 7.0 防火墙规则, 这是通过 [firewalld][7] 守护进程管理 iptables 的默认命令。**
|
||||
|
||||
# firewall-cmd --add-service=http
|
||||
|
||||
**注意**:上面的命令会在系统重启或者 firewalld 服务重启后失效,因为它是即时的规则,它不会永久生效。要使 iptables 规则在 fiewalld 中持久化,使用 `--permanent` 选项并重启 firewalld 服务来生效。(LCTT 译注:也可以不重启 firewalld 服务,而是再执行一遍不带 ` --permanent` 选项的命令。)
|
||||
|
||||
# firewall-cmd --permanent --add-service=http
|
||||
# systemctl restart firewalld
|
||||
|
||||

|
||||
|
||||
*在 CentOS 7 中启用防火墙*
|
||||
|
||||
下面是 firewalld 其他的重要选项:
|
||||
|
||||
# firewall-cmd --state
|
||||
# firewall-cmd --list-all
|
||||
# firewall-cmd --list-interfaces
|
||||
# firewall-cmd --get-service
|
||||
# firewall-cmd --query-service service_name
|
||||
# firewall-cmd --add-port=8080/tcp
|
||||
|
||||
4、要验证 apache 的功能,打开一个远程浏览器并使用 http 协议访问你服务器的 IP 地址(http://server_IP), 应该会显示下图中的默认页面。
|
||||
|
||||

|
||||
|
||||
*Apache 默认页*
|
||||
|
||||
5、现在 apache 的根地址在 `/var/www/html`,该目录中没有提供任何索引文件。如果你想要看见根目录下的文件夹列表,打开 apache 欢迎配置文件并设置 `<LocationMach>` 下 `Indexes` 前的状态从`-`到`+`,下面的截图就是一个例子。
|
||||
|
||||
# nano /etc/httpd/conf.d/welcome.conf
|
||||
|
||||

|
||||
|
||||
*Apache 目录列出*
|
||||
|
||||
6、关闭文件,重启 apache 服务来使设置生效,重载页面来看最终效果。
|
||||
|
||||
# systemctl restart httpd
|
||||
|
||||

|
||||
|
||||
*Apache 索引文件*
|
||||
|
||||
### 第二步:为 Apache 安装 php5 支持 ###
|
||||
|
||||
7、在为 apache 安装 php 支持之前,使用下面的命令的得到所有可用的php模块和扩展。
|
||||
|
||||
# yum search php
|
||||
|
||||

|
||||
|
||||
在 CentOS 7 上安装 PHP*
|
||||
|
||||
8、根据你所要使用的应用类型,安装上述列表中所需的 PHP 模块。对于 PHP 中的基本的 MariaDB 支持和 PhpMyAdmin,你需要安装如下模块。
|
||||
|
||||
# yum install php php-mysql php-pdo php-gd php-mbstring
|
||||
|
||||

|
||||
|
||||
*安装 PHP 模块*
|
||||
|
||||

|
||||
|
||||
*安装 PHP mbstring 模块*
|
||||
|
||||
9、 要在你的浏览器上显示 PHP 的全部信息,用 root 账号执行如下命令在 Apache 的文档根目录下创建一个 `info.php` 文件,然后重启 httpd 服务,并在你的浏览器里面访问 http://server_IP/info.php 。
|
||||
|
||||
# echo "<?php phpinfo(); ?>" > /var/www/html/info.php
|
||||
# systemctl restart httpd
|
||||
|
||||

|
||||
|
||||
*查看 CentOS 7 上的 PHP 信息*
|
||||
|
||||
10、如果你得到一个 PHP 的日期和时区错误,打开配置文件 `php.ini`,取消 `date.timezone` 语句的注释,加上你的实际时区参数,然后重启 Apache 守护进程。
|
||||
|
||||
# nano /etc/php.ini
|
||||
|
||||
找到并如下修改`date.timezone`,参考 [PHP 支持的时区列表][5]。(LCTT 译注:对于中国,可以使用 Asia/Shanghai、Asia/Chongqing 等,但是不建议使用向后兼容而保留的 PRC。)
|
||||
|
||||
date.timezone = Continent/City
|
||||
|
||||

|
||||
|
||||
*设置 PHP 的时区*
|
||||
|
||||
###第三步:安装和配置 MariaDB 数据库 ###
|
||||
|
||||
11、 Red Hat Enterprise Linux/CentOS 7.0 使用 MariaDB 替换 MySQL 为默认数据库管理系统。使用如下命令安装 MariaDB 数据库。
|
||||
|
||||
# yum install mariadb-server mariadb
|
||||
|
||||

|
||||
|
||||
*在 CentOS 7中安装 MariaDB*
|
||||
|
||||
12、安装 MariaDB 后,启动数据库守护进程并使用 mysql_secure_installation 脚本来保护数据库(设置数据库的 root 密码、禁止远程 root 登录、移除测试数据库、移除匿名用户等)。
|
||||
|
||||
# systemctl start mariadb
|
||||
# mysql_secure_installation
|
||||
|
||||

|
||||
|
||||
*启动 MariaDB 数据库*
|
||||
|
||||

|
||||
|
||||
*MariaDB 安全设置*
|
||||
|
||||
13、要测试数据库功能,使用 root 账户登录 MariaDB 并用 quit 退出。
|
||||
|
||||
mysql -u root -p
|
||||
MariaDB > SHOW VARIABLES;
|
||||
MariaDB > quit
|
||||
|
||||

|
||||
|
||||
*连接 MariaDB 数据库*
|
||||
|
||||
### 第四步:安装 PhpMyAdmin ###
|
||||
|
||||
14、 RHEL 7.0 或者 CentOS 7.0 仓库默认没有提供 PhpMyAdmin 二进制安装包。如果你不适应使用 MySQL 命令行来管理你的数据库,你可以通过下面的命令启用 CentOS 7.0 rpmforge 仓库来安装 PhpMyAdmin。
|
||||
|
||||
# yum install http://pkgs.repoforge.org/rpmforge-release/rpmforge-release-0.5.3-1.el7.rf.x86_64.rpm
|
||||
|
||||
启用 rpmforge 仓库后,下面安装 PhpMyAdmin。
|
||||
|
||||
# yum install phpmyadmin
|
||||
|
||||

|
||||
|
||||
*启用 RPMForge 仓库*
|
||||
|
||||
15、下面配置 PhpMyAdmin 的 `phpmyadmin.conf` 来允许远程连接,它位于 Apache 的 `conf.d` 目录下,并注释掉下面的行。
|
||||
|
||||
# nano /etc/httpd/conf.d/phpmyadmin.conf
|
||||
|
||||
使用#来注释掉下列行。
|
||||
|
||||
# Order Deny,Allow
|
||||
# Deny from all
|
||||
# Allow from 127.0.0.1
|
||||
|
||||

|
||||
|
||||
*允许远程 PhpMyAdmin 访问*
|
||||
|
||||
16、 要使用 cookie 验证来登录 PhpMyAdmin,像下面的截图那样使用[生成的秘密字符串][6]来添加一个 blowfish 字符串到 `config.inc.php` 文件中,重启 apache 服务并打开 URL:http://server_IP/phpmyadmin/。
|
||||
|
||||
# nano /etc/httpd/conf.d/phpmyadmin.conf
|
||||
# systemctl restart httpd
|
||||
|
||||

|
||||
|
||||
*在 PhpMyAdmin 中添加 Blowfish*
|
||||
|
||||

|
||||
|
||||
*PhpMyAdmin 面板*
|
||||
|
||||
### 第五步:在系统范围内启用 LAMP ###
|
||||
|
||||
17、 如果你需要在重启后自动运行 MariaDB 和 Apache 服务,你需要在系统级地启用它们。
|
||||
|
||||
# systemctl enable mariadb
|
||||
# systemctl enable httpd
|
||||
|
||||

|
||||
|
||||
*系统级启用服务*
|
||||
|
||||
这就是在 Red Hat Enterprise 7.0 或者 CentOS 7.0 中安装 LAMP 的过程。在 CentOS/RHEL 7.0 上关于 LAMP 的系列文章接下来将会讨论在 Apache 中创建虚拟主机,生成 SSL 证书、密钥和添加 SSL 事务支持。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/install-lamp-in-centos-7/
|
||||
|
||||
作者:[Matei Cezar][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/cezarmatei/
|
||||
[1]:http://www.tecmint.com/redhat-enterprise-linux-7-installation/
|
||||
[2]:http://www.tecmint.com/enable-redhat-subscription-reposiories-and-updates-for-rhel-7/
|
||||
[3]:http://www.tecmint.com/centos-7-installation/
|
||||
[4]:https://linux.cn/article-3977-1.html
|
||||
[5]:http://php.net/manual/en/timezones.php
|
||||
[6]:http://www.question-defense.com/tools/phpmyadmin-blowfish-secret-generator
|
||||
[7]:https://linux.cn/article-4425-1.html
|
||||
@ -0,0 +1,215 @@
|
||||
Tor浏览器:Linux下用于匿名Web浏览的终极浏览器
|
||||
================================================================================
|
||||
我们大多数人都在上网方面花费很多时间。上网使用的应用程序主要是浏览器,更确切的说是一个Web浏览器。我们在网络上的大部分活动要以客户端/服务器的方式登录,这个过程会包括IP地址、地理信息、搜索、活动以及许多潜在的信息,这些信息如果以其他方式被故意使用,会存在潜在的危险性。
|
||||
|
||||

|
||||
|
||||
*Tor浏览器:匿名浏览器*
|
||||
|
||||
此外,美国国家安全局(NSA)这样的国际间谍机构会记录我们的数字足迹。更不必说受到控制的代理服务器也会被用来做为数据搜集服务器。并且大多数企业和公司不会允许您访问代理服务器(使您能保障自己的隐私)。
|
||||
|
||||
因此,我们需要的最好是一个小型、独立、可携带的应用程序,它能达到匿名的效果。Tor浏览器便是这样的一个应用,它拥有上面提到的所有功能,甚至不止于此。
|
||||
|
||||
这篇文章里我们会讨论Tor浏览器,它的功能、使用方式、领域、安装以及其他关于Tor浏览器的重要方面。
|
||||
|
||||
### 什么是Tor浏览器? ###
|
||||
|
||||
Tor是一个自由分发的应用软件,以BSD许可证发布,通过其安全可靠的洋葱式的结构,允许用户匿名的进行网络浏览。从前,由于它的结构和运作机制,Tor被称为‘洋葱路由器’。这个应用是由C语言写成的。
|
||||
|
||||
#### Tor浏览器的功能 ####
|
||||
|
||||
- 跨平台可用。例如,这个应用程序在Linux、Windows和Mac下都可用。
|
||||
- 在发送数据到因特网前进行复杂的数据加密。
|
||||
- 在客户端进行数据自动解密。
|
||||
- 它是火狐浏览器和Tor工程的结合。
|
||||
- 对服务器和网站提供匿名性。
|
||||
- 可以访问被限制的网站。
|
||||
- 无需暴露源IP便可以执行任务。
|
||||
- 可以将数据路由至/从防火墙后隐藏的服务和应用程序。
|
||||
- 便携性 - 可以直接从USB存储棒上运行一个预配置的web浏览器。无需本地安装。
|
||||
- 在x86和x86_64平台均可用
|
||||
- 可以配置为一个运行在“localhost”的“9050”端口上的“socks4a”代理来让FTP跑在Tor 上。
|
||||
- Tor拥有处理上千的中继和上百万用户的能力。
|
||||
|
||||
#### Tor浏览器如何工作? ####
|
||||
|
||||
Tor的工作方式基于洋葱路由的概念。洋葱路由的结构类似洋葱,它的每一层都嵌套在另一层里面,就像洋葱一样。这种嵌套的结构负责多次加密数据并将其通过虚拟电路进行发送。在客户端一侧每一层都在将他传递到下一层之前解密数据。最后一层在将原始数据传递到目的地前解密最里面一层的加密数据。
|
||||
|
||||
在这个过程里,这种解密整个层的功能设计的如此高明以至于无法追踪IP以及用户的地理位置,因此可以限制任何人观察您访问站点的网络连接。
|
||||
|
||||
所有这些过程看起来有些复杂,但用户使用Tor浏览器时没有必要担心。实际上,Tor浏览器的功能像其他浏览器一样(尤其是Mozilla的Firefox)。
|
||||
|
||||
### 在Linux中安装Tor浏览器 ###
|
||||
|
||||
就像上面讨论的一样,Tor浏览器在Linux和Windows以及Mac下都可用。用户需要根据系统和架构的不同在下面的链接处下载最新的版本(例如,Tor浏览器4.0.4)。
|
||||
|
||||
- [https://www.torproject.org/download/download-easy.html.en][1]
|
||||
|
||||
在下载Tor浏览器后,按说我们需要安装它,但是Tor的好处是我们不需要安装它。它能直接从随身设备中运行,并且该浏览器可以被预配置。这意味着插件和运行的特性可以完美的移植。
|
||||
|
||||
下载打包文件(*.tar.xz)后我们需要解压它。
|
||||
|
||||
**32位系统**
|
||||
|
||||
$ wget https://www.torproject.org/dist/torbrowser/4.0.4/tor-browser-linux32-4.0.4_en-US.tar.xz
|
||||
$ tar xpvf tor-browser-linux32-4.0.4_en-US.tar.xz
|
||||
|
||||
**64位系统**
|
||||
|
||||
$ wget https://www.torproject.org/dist/torbrowser/4.0.4/tor-browser-linux64-4.0.4_en-US.tar.xz
|
||||
$ tar -xpvf tor-browser-linux64-4.0.4_en-US.tar.xz
|
||||
|
||||
**注意** : 在上面的命令中,我们使用‘$‘意味着这个压缩包应以普通用户而不是root用户来解压。我们强烈建议您不要以root用户解压和运行Tor浏览器。
|
||||
|
||||
###开始使用Tor浏览器###
|
||||
|
||||
在成功的解压后,我们便可以将解压后的浏览器移动到任何地方/USB存储设备中。并从解压的文件夹以非root用户直接运行‘start-tor-browser’。
|
||||
|
||||
$ cd tor-browser_en-US
|
||||
$ ./start-tor-browser
|
||||
|
||||
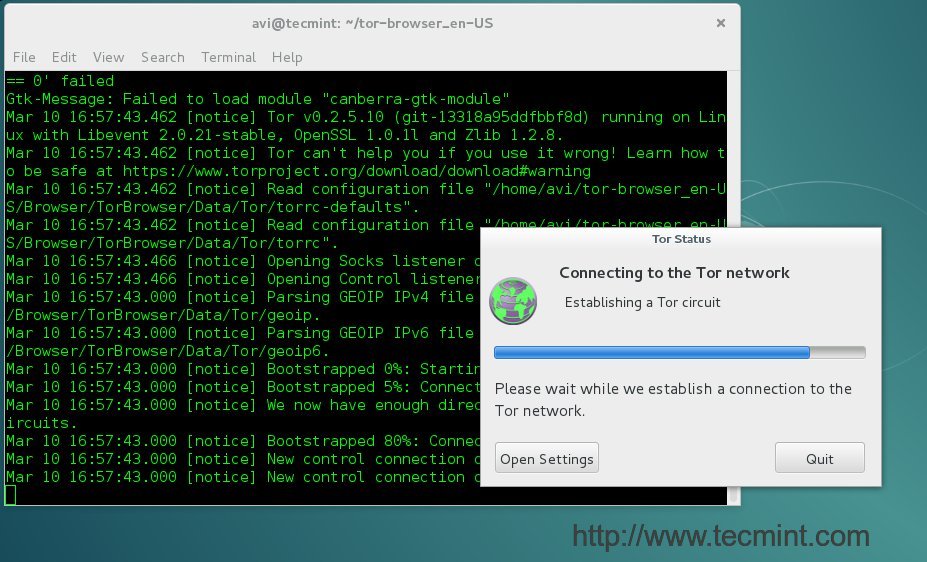
|
||||
|
||||
*开始使用Tor浏览器*
|
||||
|
||||
####1. 尝试连接到Tor网络####
|
||||
|
||||
点击“连接”之后Tor将按照设置帮您做剩下的事情。**
|
||||
|
||||

|
||||
|
||||
*连接到Tor网络*
|
||||
|
||||
####2. 欢迎窗口/标签。####
|
||||
|
||||
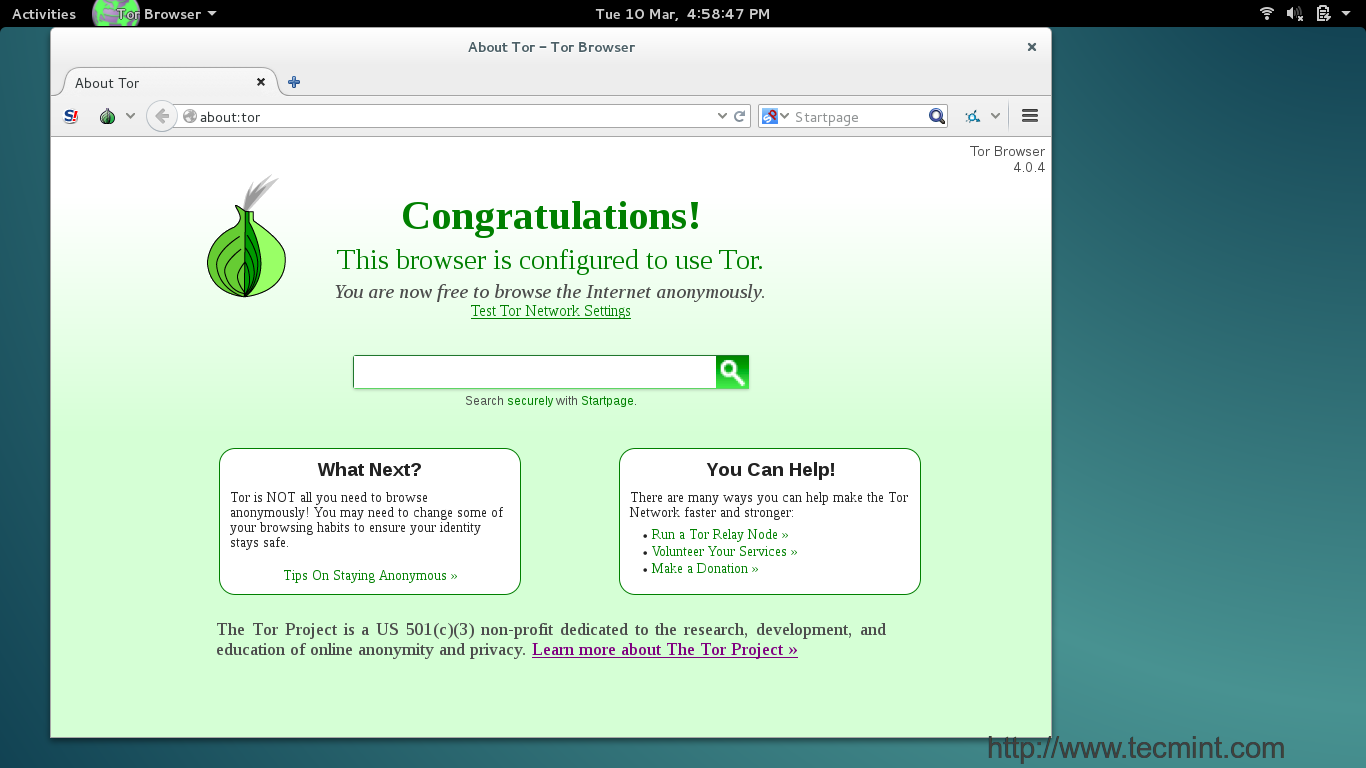
|
||||
|
||||
*Tor欢迎界面*
|
||||
|
||||
**3. 用Tor浏览器在Youtube上看视频**
|
||||
|
||||

|
||||
|
||||
*在Youtube上看视频*
|
||||
|
||||
####4. 打开银行网址以进行在线购物和交易####
|
||||
|
||||

|
||||
|
||||
*浏览银行站点*
|
||||
|
||||
####5. 浏览器显示我当前的代理IP####
|
||||
|
||||
注意其中的文字为“Proxy Server detected”。**
|
||||
|
||||
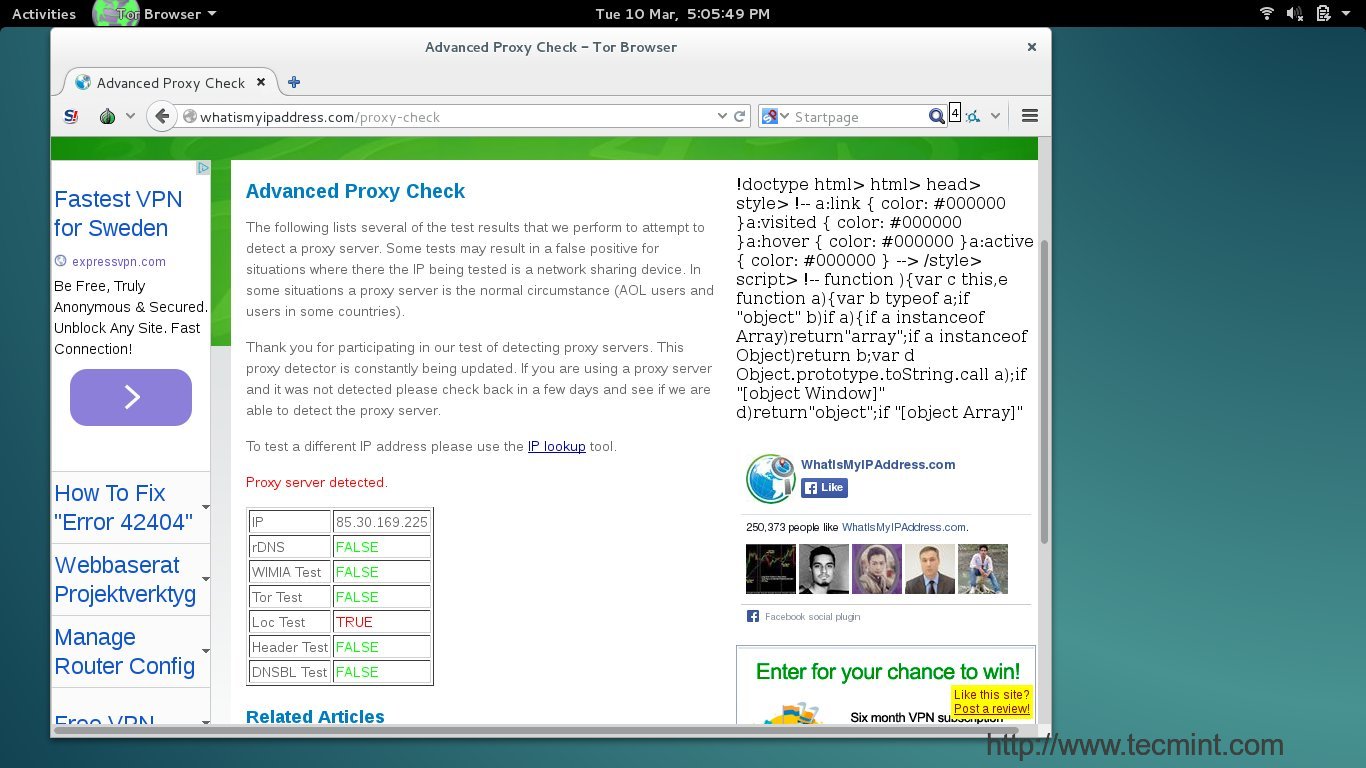
|
||||
|
||||
*检查IP地址*
|
||||
|
||||
**注意**: 每次您想运行Tor时,您需要在文本模式上运行Tor启动脚本。并且该终端在您运行Tor时会一直被占用。如何克服这些,并创建一个桌面/Dock栏图标呢?
|
||||
|
||||
####6. 我们需要在解压的文件夹中创建`tor.desktop`####
|
||||
|
||||
$ touch tor.desktop
|
||||
|
||||
接着使用您喜欢的编辑器编辑这个文件,加入下面的文本,这里我使用nano。
|
||||
|
||||
$ nano tor.desktop
|
||||
|
||||
----------
|
||||
|
||||
#!/usr/bin/env xdg-open
|
||||
[Desktop Entry]
|
||||
Encoding=UTF-8
|
||||
Name=Tor
|
||||
Comment=Anonymous Browse
|
||||
Type=Application
|
||||
Terminal=false
|
||||
Exec=/home/avi/Downloads/tor-browser_en-US/start-tor-browser
|
||||
Icon=/home/avi/Downloads/tor-browser_en-US/Browser/browser/icons/mozicon128.png
|
||||
StartupNotify=true
|
||||
Categories=Network;WebBrowser;
|
||||
|
||||
**注意**: 确保将上面的tor浏览器的路径替换为您的环境中的路径。
|
||||
|
||||
####7. 一旦搞定后,您就可以双击`tor.desktop`文件来运行Tor浏览器了####
|
||||
|
||||
您可能需要在第一次运行时信任该文件。
|
||||
|
||||

|
||||
|
||||
*Tor应用启动器*
|
||||
|
||||
####8. 一旦您选择了信任,请注意`tor.desktop`文件的图标则会改变###
|
||||
|
||||

|
||||
|
||||
*Tor图标已改变*
|
||||
|
||||
####9. 您可以通过拖拽`tor.desktop`的图标在桌面和Dock栏中创建快捷方式####
|
||||
|
||||

|
||||
|
||||
*在桌面添加Tor快捷方式*
|
||||
|
||||
####10. 关于Tor浏览器####
|
||||
|
||||

|
||||
|
||||
*关于Tor浏览器*
|
||||
|
||||
**注意**: 如果您在使用旧版本的Tor,您可以从上面的窗口更新它。
|
||||
|
||||
#### 应用的可用性和领域 ####
|
||||
|
||||
- 匿名使用网络。
|
||||
- 浏览被封锁的页面。
|
||||
- 连接其他应用,即(FTP)来保证网络安全的访问。
|
||||
|
||||
#### 关于Tor浏览器的争论 ####
|
||||
|
||||
- 在Tor应用的边界上并没有什么安全措施。比如,数据入口点和出口点。
|
||||
- 一项2011年的研究发现一种特殊的针对Tor浏览器的攻击可以得到BitTorrent用户的IP地址。
|
||||
- 在一些研究中发现某些特定的协议有泄漏IP地址的倾向。
|
||||
- 早些的Tor版本绑定了旧版本的Firefox浏览器,这被证明较易受JavaScript攻击。
|
||||
- Tor浏览器运行起来比较慢。
|
||||
|
||||
#### 真实世界中Tor浏览器的实现 ####
|
||||
|
||||
- [Vuze BitTorrent Client][3]
|
||||
- Anonymous Os
|
||||
- Os’es from Scratch
|
||||
- whonix 等
|
||||
|
||||
#### Tor浏览器的未来 ####
|
||||
|
||||
Tor浏览器是前途无量的。也许第一个该类应用程序的实现是非常出色的,但Tor浏览器必须加大对支持、伸缩性、以及对近期的攻击进行数据安全的研究的投入。这个应用程序是未来的需要。
|
||||
|
||||
#### 下载免费的电子书 ####
|
||||
|
||||
非官方的Tor私密浏览指南:
|
||||
|
||||
[][2]
|
||||
|
||||
### 结论 ###
|
||||
|
||||
如果您工作的部门不允许您访问某网站,或者如果您不希望别人知道您的私人事务,或您不想向NSA提供您的个人数字足迹,那么Tor浏览器在目前是必须的。
|
||||
|
||||
**注意**: Tor浏览器提供的安全性不能抵御病毒、木马或其他类似这样的安全威胁。写这篇文章的目的也不是希望通过在互联网上隐藏我们的身份来放纵非法活动。这篇文章纯粹是为了教学的目的,作者和Tecmint均不会为任何非法的使用负责。这是用户自己的责任。
|
||||
|
||||
Tor浏览器是一个非常不错的应用,您值得尝试!这就是我要说的全部了,我还会在这里写一些您感兴趣的文章,所以请继续关注。别忘了在留言区提供给我们您有价值的反馈。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/tor-browser-for-anonymous-web-browsing/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[wwy-hust](https://github.com/wwy-hust)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:https://www.torproject.org/download/download-easy.html.en
|
||||
[2]:http://tecmint.tradepub.com/free/w_make129/prgm.cgi
|
||||
[3]:http://www.tecmint.com/install-vuze-torrent-client-in-linux/
|
||||
@ -0,0 +1,186 @@
|
||||
没有 Linus,Linux 的未来是什么样子?
|
||||
==============================================================================
|
||||

|
||||
|
||||
这次采访是《Linux For You》杂志在2007年进行的,现在我们发表在这里是为了存档的目的。
|
||||
|
||||
**Q:对于 Linux 内核,未来的计划/道路/提升是怎样的?**
|
||||
|
||||
Linus:我从来没有太多的预见性 — 与其从宏大的计划上看未来,我倾向于从一个相对短的时间框架,比如“几个月之后的事情”。我是一个忠实的‘细节成败论’的信仰者,如果你抓住了细节,再大的问题也会大事化小,小事化无。
|
||||
|
||||
所以,对于五年后内核会是什么样,我真的没有任何远见 — 仅仅是希望我们能够持续专注于Linux的发展。实际上,对于我个人来说,我最担心的事情之一甚至不是技术问题,而是确保这个‘过程’正常,这样人们才可以相互协作好。
|
||||
|
||||
**Q:你怎么看 Linux 和 Solaris 之间的关系在未来的发展?它会如何使用户受益?**
|
||||
|
||||
Linus:我并没有看到太多交叉的地方,除了我认为 Solaris 会使用更多的 Linux 用户空间工具(对我自己来说并没有太多关注这个,因为我真的只关心内核)。Linux 桌面比起传统 Solaris 桌面好多了,而且我希望 Solaris 移植越来越多的 Linux 的东西,朝着一个更加类 Linux 的模式前进。(LCTT 译注:时至今日,我们还需要讨论 Solaris 吗?/cry ,但是当时,整个开源社区确实期望接受 Solaris 一些遗产。)
|
||||
|
||||
从纯内核方面讲,许可证的存在意味着没有太多的合作空间,但是如果这种情况发生改变将会变得很有趣。Sun 已经声称将在 GPL(v2 或 v3)下授权 Solaris,如果这种许可证的差异消失,那么会导致一些有趣的技术出现。但对此,我持观望态度。
|
||||
|
||||
**Q:现在 GPL v3 已经完成并发布了,你是否预见有什么情况会鼓励你开始移植内核到 Solaris 上去?或者,从你的角度看,它是否很糟糕以至于你从来没考虑过它?**
|
||||
|
||||
Linus:我觉得相比于早先的草稿,v3 有了很多提高,并且我也不认为它是一个糟糕的许可证。我只是认为它没有 GPLv2 一样‘伟大’。
|
||||
|
||||
所以,如果没有 GPLv2,我觉得自己将会使用 GPLv3。不过,既然我已经有了一个更好的选择,我为什么还要考虑它呢?
|
||||
|
||||
这就是说,我始终秉承实用主义精神,并且我认为“ GPLv3 不像 GPLv2 一样好”这件事并不是一个‘非黑即白’的问题。这就像是一个天平,如果 GPLv3 有了其他的优点作为砝码,很有可能那些优点会让我对 GPLv3 更偏爱一些。
|
||||
|
||||
恕我直言,我到现在还并没有看到任何优点,但是如果 Solaris 真的在 GPLv3 下发布,可能避免不必要的许可证不兼容性这一条就分量足够了,足以值得我们去尝试将 Linux 的内核重新在 GPLv3 许可证下发布。不过,请不要误解,我认为这是不大可能的。但是我确实想澄清我本质上并不是一个许可证偏执者。我认为 GPLv2 是毫无疑问的好许可证,但是许可证并不是一切。(LCTT 译注:事实上,Solaris/OpenSolaris 最终也没采用 GPL 许可协议发布,而 20100年之后,已经没有什么动静了。而 Linux 内核最终也没有更换到 GPLv3 上。)
|
||||
|
||||
总的来说,我使用很多其他许可证下的程序。我可能没有把任何一个我自己做的项目放在 BSD(或 X11—MIT)许可证下,但是我认为它是一个伟大的许可证,对于其他项目来说,它可能是最佳的选择。
|
||||
|
||||
**Q:目前有没有任何你想特别提出作为 Linux 内核的关键贡献者的印度人?**
|
||||
|
||||
(LCTT 译注:本篇访谈中提到多次印度,是因为访谈者是印度人。)
|
||||
|
||||
Linus:我不得不承认,我并没有与来自印度的任何人直接合作过,尽管我已经非常有意识地努力建立一个规模庞大的内核开发团队,这样我不用总是独自工作。
|
||||
|
||||
我相信大多数人的社交基本上是受限制的,只对很少的人十分了解(比如你最亲近的家人和朋友),我也努力构造这样一个开发模型来改变这种状况:通过一个‘开发者网络’,人们可以在此互动,可能是与一批你信任的人,而且那些人反过来与他们信任的一群人互动。
|
||||
|
||||
所以,我偶然会与上百个发给我一两个不确定的补丁的开发者联系。我试着去建立一些由我熟知的人组成的小团体,我认为那就是人们工作的方式,当然也是我喜欢工作的方式。
|
||||
|
||||
同时,坦白地说,我甚至不知道许多与我一起工作的人生活在哪里。地理位置成了十分次要的东西。所以我很确信与我工作最紧密的前10—15个人中,没有印度的,可能这话稍后传到公众耳里,然后被指出确实有一些人来自那里!
|
||||
|
||||
**Q:因为 Linux 的内核开发对你依赖如此严重,你如何计划组织或重组,让它在没有你的情况下继续发展,假设你决定花更多的时间在你自己的生活和家庭上面的话?**
|
||||
|
||||
Linus:现在 Linux 比我重要得多,为了今天这一步我已经工作了很长时间。是的,我仍然十分密切地参与其中,而且我对其有着想当大的日常影响,我最终会是这样一个人——在某种程度上,扮演着许多内核开发活跃者的中心;但是,我不会说 Linux “严重依赖”于我。
|
||||
|
||||
所以,如果我得了心脏病并且明天就死了(很高兴没这种可能:我显然在任何方面都很健康),人们肯定会注意到,但是有成千上万的人为内核工作,并且不止一两个人能够毫无困难地接替我的角色。
|
||||
|
||||
**Q:印度是软件工程师的主要产地之一,但是我们没有在 Linux 领域做太多贡献。你觉得为什么印度人没有积极参与Linux?如果我们鼓励印度人参与并为 Linux 做更大的贡献,你觉得如何?你会乐意用你个人作为榜样激励印度工程师吗?**
|
||||
|
||||
Linus:对我来说,这确实是一个不好回答的问题。参与开源取决于两方面的基础条件:信息流和文化(用你的话说是互联网和教育),我甚至不知道这其中哪个是最大的障碍。
|
||||
|
||||
在很多方面,至少在那些印度讲英语文化的地方,参与 Linux 和其他开源项目是相对容易的,如果仅仅是由于语言门槛的话。这当然比起亚洲的许多地方,甚至欧洲的一些地方要容易些。
|
||||
|
||||
当然,这只是一些人,并不等同于印度的大部分群体,而且我自己关于印度的情况也知道不多,甚至没法不太负责的猜测最好的途径是什么。我猜一个热情的本地用户社区会是最好的途径,而且我猜测你们已经拥有这样的社区了。
|
||||
|
||||
至于我的‘偶像’形象,我自己不以为然。我不是一个伟大的公众演讲者,而且我最近些年已经避免出游,因为被看做符号化的‘偶像’让我很不自在。我就是一个工程师而已,而且我仅仅是喜欢我做的事情,并与社会上其他人一起工作。
|
||||
|
||||
**Q:什么样的理由会让你考虑去访问印度?**
|
||||
|
||||
Linus:如前一个回答中提到,我十分讨厌公开演讲,所以我才想避免开会等等这些事。我更愿意某天去印度度个假,但是如果我这样做,我可能悄悄地干 — 出行之前不告诉任何人,仅仅作为一个游客去游览印度!(LCTT 译注:所以 Linus 不来中国的道理是同样的,除非在中国召开一次世界性的 LinuxCon。)
|
||||
|
||||
**Q:最近你好像在抨击 Subversion 与 CVS,质问他们的架构基础。现在你已经从 Subversion 和 CVS 社区那里得到回应,你是否改变了看法,还是说并没有被说服?**
|
||||
|
||||
Linus:因为我发现这个争论很有趣,所以我想做一个强硬的声明。换句话说,我确实‘喜欢’争论。并不是不经思考的,但是我确实想要让争论更热烈些,而不仅仅是完全的柏拉图式的。
|
||||
|
||||
做出强硬的争论有时会引来一个非常合理的反驳,然后我会很高兴地说:“噢,好吧,你是对的。”
|
||||
|
||||
但是话说回来,对 SVN/CVS 并不会发生这种情况。我怀疑很多人并不是真的很喜欢 CVS,所以我真的不觉得会有谁坚持认为 CVS 就是一切,而不是一个老旧系统。要是我知道之前就有人这样认为的话,我就不会那么不礼貌地反对 SVN(嘿,这么说没错 — 我真的不是一个非常礼貌的家伙!),我不相信任何人会认为 SVN 是‘好的’。
|
||||
|
||||
我认为,SVN 就是一个‘还好’的经典案例。人们过去经常使用 SVN,并且它也‘还好’地广泛使用,但是它的‘还好’就如 DOS 与 Windows 的‘还好’一样。不是什么伟大的技术,只是普遍适用而已,同时它对人们来说运行良好,看着十分熟悉。但是很少有人以此为傲,或者对其感到兴奋。
|
||||
|
||||
Git,从另外方面讲,其身后有一些‘UNIX 哲学’,这和 UNIX 无关。实质上,就像原始的 UNIX,在它身后有一个基本理念。对 UNIX 来说,最底层的哲学就是,“所有东西只是一个文件”。对 Git 来说,“则是每个东西只是内容寻址数据库中的一个对象”。
|
||||
|
||||
**Q:现在如此多的发行是好事还是坏事?选择是很有意思的,但是选择太多了就是干扰。相较于这么多的人每天花费数小时去构建成百上千的发行版,如果人们可以一起来支持少数的发行版,这样在企业级市场去挑战微软是不是更容易些呢?对此你怎么看?**
|
||||
|
||||
Linus:我认为多个发行版是开源不可回避的部分。它会造成困惑吗?当然。它会变得低效率吗?是的。但是我喜欢拿它与政治比较:‘民主’也有那些令人困惑的选择,往往没有任何一个选择是你‘真正’想要的。而且有时候,如果你不需要操心选举、不同党派和联合等等方面的困惑的话,你可能会感觉事情更加容易一些,更有效率一些。
|
||||
|
||||
但是最后我想说,选择可能会导致低效率,但是它也让每个人至少保留了‘所谓的’诚信。我们可能都希望我们的政治家更诚信,我们也希望不同的发行版可以让我们有一天有其他的选择,而如果没有选择的话,事情可能会更糟。
|
||||
|
||||
**Q:为什么你觉得 CFS 比 SD 更好?**
|
||||
|
||||
Linus:一部分原因是我与 Ingo [Molnar] 工作过很长一段时间,也就是说,我了解他,并且知道他会对发生的任何问题非常负责。那种品质是非常重要的。
|
||||
|
||||
但是一部分原因就简单的与用户有关,大多数人实际上表示 CFS 比 SD 好。包括许多 3D 游戏方面(这是人们声称 SD 最强的一点)。
|
||||
|
||||
尽管如此,我认为并不是任何一段代码都十分‘完美’。最好的情况是,想成为 SD 支持者的人会努力提高 SD,从而通过其它方式取得了平衡 — 而我们会保持两个阵营都尝试有趣的事情,因为内部的竞争会刺激他们。
|
||||
|
||||
**Q:在 Google 的一次关于 Git 的访谈中,有人问你如何将当前集中存放的超大代码库迁移到 git 上,而不用将开发工作停止六个月。你对此的回答是什么?**
|
||||
|
||||
Linus:啊哈,那个问题我在现场没有听清楚(在录音里,问题会听得更清楚些),当我回头去听录制的音频,注意到了我没有回答他的问题,但是我觉得这问题他问过。
|
||||
|
||||
无论如何,我们确实有很多导入的工具,所以你实际上可以仅仅是将一个大的项目从任何其他的早期的 SCM (源代码控制系统)导入到 git 里,但问题显然不是经常以导入动作本身结束,而是需要‘习惯’这种新模式!
|
||||
|
||||
坦白来说,我认为关于如何‘习惯它’没有任何其他答案,而只能是去开始使用和尝试它。显然,你不会冒险率先导入你现有的最大、最重要的项目,那确实会导致工作停顿下来,然后使得每个人都很不高兴。
|
||||
|
||||
所以没有任何理智健全的人会拥护在一夜之间将一切移到 git 上去,并强迫人们改变他们的环境。是的,你需要从公司里的小项目开始,可能是一些由一个小组主要控制和维护的项目,然后开始转移其到 git。这是你能让人们习惯这种模式的方式,你应该以一个核心的组开始,他们知道 git 如何工作,如何在公司里面使用它。
|
||||
|
||||
接着,你就会铺展开来。并不需要一次到位。你会导入越来越多的项目 — 甚至是在你公司里采用‘单一大型仓库’模式;那个仓库基本上是作为许多模块的集合,因为让每个人去检查每件事不是一个可执行的工作模型(除非这个‘每件事’并不非常大)。
|
||||
|
||||
所以,你基本上只会一次转移一个模块,直到你发现使用 git 是如此酸爽,这时你可以移植余下的所有(或者‘余下’的太旧了,没有人用了)。
|
||||
|
||||
git 最赞的一个功能是,它实际上可以同很多其他 SCM 相处很好。很多 git 用户使用它的时候,与他们一起工作的人并没有发现,因为他们看到 git 的结果,会联想到一些传统的 SCM 上去。
|
||||
|
||||
**Q:Linux 用了你在 Transmeta(全美达)上实现备用指令集的经验吗?[Transmeta Crusoe 芯片看起来像一个非常轻量级的 CPU — 记得有一台 Burroughs B1000 解释器,它实际上实现了多个虚拟机。有的用于系统软件,有的用于 Cobol,还有的用于 Fortran;如果没错的话,那么人们可以在芯片上实现 Burroughs 6/7000 或者 HP3000 类似的堆栈架构,或适用于 JVM 的指令集,等等。(LCTT 译注:Linus 于 1997-2003 期间就职于全美达)]**
|
||||
|
||||
Linus:我们确实有一些备选的结构集合,不过我不打算谈论太多这个,我可以说的是我们已经做了一个混合结构集合的公开演示。我们有一个技术展示,在那里你同时可以跑 x86 指令和 Java 字节码(实际上,它是一个轻量的扩展 pico—java,iirc)。
|
||||
|
||||
我想我们展示的这个应用会在 Linux 上运行 DOOM,这里 Linux 的部分是一个完全标准 x86 发行版。但是 DOOM 的二进制程序是一个特定的编译版本,它实际上编译为 pico-java 代码。而 CPU 最终以相同的方式来运行它们——从 JIT 到原生 VLIW 指令集。
|
||||
|
||||
(选择 DOOM 的原因仅仅是其源代码可用,并且游戏的核心部分非常小,足以很容易拿它来做一个验证 — 而且它也显然看起来十分有趣。)
|
||||
|
||||
有更多的事情是在内部运作,但是我不能谈论他们。而且实际上,就我个人而言,对 Java 不怎么感冒。
|
||||
|
||||
**Q:386BSD 衍生了 NetBSD,FreeBSD 和 OpenBSD,在 Linux 出现之前已经发展不错了,但是 Linux 传播比 386BSD 及其衍生者更为广泛。这在多大程度上左右你对许可证的选择,这个选择的发展过程是怎样的?你不认为比起 GPLv2 来,是 GPLv3 创造了发展空间,迄今为止,让 Linux 比 BSD 变得更好?**
|
||||
|
||||
Linus:我认为这不仅是一个许可证问题,也是一个社区及人格问题。BSD 的许可证总是鼓励分叉,但是这也意味着,如果某些人取得了成功并做了商业性的分叉,他并不需要将他的修改返回来。因此,哪怕实际上这种事情没有(而实际上,这种事情的确发生了,比如 BSDi),人们也难以建立彼此信任。
|
||||
|
||||
相比之下,GPLv2 也鼓励分叉,但是它不仅仅鼓励分叉出去,它也鼓励(并‘要求’)能够融合回来。所以,我们现在达到了新的层次的信任:你‘知道’每个人都被许可证所约束,所以每个人都不会占你便宜。
|
||||
|
||||
所以,在我看来,GPLv2 作为许可证来说,它允许人们在要求总是回馈贡献的前提下,在另外的方面取得了最大可能的自由。没有人能阻止你对源代码的改进。
|
||||
|
||||
那么,BSD 许可证是更‘自由’的吗?是的,毫无疑问。但是我不会在我在意的任何项目里面使用 BSD 许可证,因为我不仅仅想要自由,我也想要信任,可以让我总是能使用其他人为我的项目所写的代码。
|
||||
|
||||
所以对于我来说,GPLv2 最终在‘尽可能自由’上取得了完美的平衡,这样,我们做到了让每个人都能信任,他们总是可以取得源代码并使用它。
|
||||
|
||||
这就是为什么我认为 GPLv3 最终并没多大意思,它不再是那种‘返回源代码’的信任;它退化成了‘我写了这些代码,所以我能控制你如何使用它’。
|
||||
|
||||
换言之,我只是觉得 GPLv3 太狭隘和自私了。我认为 GPLv2 在‘自由’和‘信任’之间取得伟大的平衡。它不如 BSD 许可证自由,但是它让你安心回馈,而且它符合我认为的‘以德报德’:我给你源代码,你也回馈我源代码。
|
||||
|
||||
而 GPLv3 试着控制源代码的‘使用’。现在它就是“我给你我的源代码,如果你使用它的话,你就准备好让我对你的设备动手动脚吧”,看见了没?在我看来,不但小气,而且小心眼。
|
||||
|
||||
**Q:-rt 代码树的功能正在缓慢而稳定地逐渐集成到主线代码中。你对将剩余的 -rt 树合并到主线代码的看法是什么?(我说的不是 CFS)**
|
||||
|
||||
Linus: 我不能保证来自 -rt 的一切‘都’会被合并进入标准内核(有一些部分肯定不适合常规的内核),不过是的,这些年来我们实际上将它的大部分都集成进去了,剩下的部分最终以后也会合并进去。
|
||||
|
||||
我提倡高效工作,但是我同时也很保守。我退回了一些激进的合并请求,只是因为我需要确保它们对我们所有人都有意义,不仅仅是用于极端情况下的实时环境,而且也对并不需要这种环境的‘普通’用户有用。这解释了为什么这个过程相当缓慢却稳定不断地合并代码,因为它需要足够稳定和有意义。
|
||||
|
||||
顺便说一句,这不仅仅是针对 -rt ,它也出现在许多开发中。-rt 出现这种情况是因为它是更‘直接’的内核项目,而且也是因为它的一个主要开发者直接参与到了常规内核开发。通常其它功能的迁移(安全、虚拟内核变化、虚拟化,等等)也遵循类似的方式:他们针对特定的环境进行开发,然后这些功能片段缓慢而稳步地合并到标准内核。
|
||||
|
||||
**Q:我对 Linux 内核所支持的文件系统发展很感兴趣。你觉得 Reiser4、XFS4、ZFS 以及 Oracle 的新项目哪个更有前途?这些天 ZFS 有不少新闻,Reiser4 也发布了很不错的性能基准测试,XFS4 正紧随其后,而 Oracle 发布的那个也有很多像 Sun 的 ZFS 一样的特性。我们将走向何方呢?以你的观点来看,哪个文件系统更有前途?**
|
||||
|
||||
Linus: 实际上,就在昨天我们发现了一个 git 的性能问题,有一个用户发现他采用 ZFS 要比 UFS 慢一个数量级(不是在 Linux 下,git 已经得到了许多关注,甚至是来自内核开发团队之外)。所以,我认为许多‘新文件系统’的拥护者部分原因是因为他们了解到旧文件系统的不足,然后(有点不切实际地)期望一个‘崭新的、改进的’文件系统能使一切都完美。
|
||||
|
||||
最后,这是一个永无止境的领域,看看谁是最终的赢家——也许并不需要(看起来不需要)一个赢家。几乎总是这样,对文件系统的选择最终取决于负载和环境。
|
||||
|
||||
相比你提到的这些文件系统,我个人对基于闪存的硬盘很快就可以供甚至是‘普通’用户使用的这个事实更感到兴奋。当然,它们仍然很昂贵(而且相当的小),但是基于闪存的存储和传统硬盘的性能完全不可同日而语,我怀疑它们最终将对文件系统的设计有巨大的影响。而现在,多数文件系统的设计都是在考虑如何处理硬盘延迟。
|
||||
|
||||
**Q:操作系统变得越来越不重要。你说过好几次用户根本不应该‘看见’操作系统。应用更为重要。基于浏览器的应用,如 Google 的办公软件影响力越来越大。你认为操作系统将走向何方?**
|
||||
|
||||
Linus:我并不真的认可‘浏览器 OS’,因为我认为人们总是需要在本地做一些事情。也许是因为安全,或者仅仅是因为隐私的原因。而且即便当到处可以接入时,它也并不是‘无处不在’。
|
||||
|
||||
所以我认为,整个‘Web OS’这件事有一部分是真实的,但是另外一部分人们也许忘记了操作系统已经存在了几十年,它已经相当稳定,而且它的发展是有目共睹的。人们真的不应该期望操作系统有魔法般的变化,现在已经不是操作系统刚刚起步的六十年代,甚至连硬件也和过去完全不同了!
|
||||
|
||||
所以,别指望一场革命。我认为操作系统将在很大程度上继续它们所擅长的,当然,我们也会进步,但是我不认为会从根本上改变。也许会发生巨变的是界面和操作系统顶层的那些东西(当然,操作系统下面的硬件也会继续进步),这显然才是人们所关心的。
|
||||
|
||||
至于操作系统?它显然是应该尽可能隐藏起来的东西。你真的不应该在意它,除非你特别想知道在机器里面真正在发生什么。
|
||||
|
||||
**Q:最近我听说你正在使用一台 PPC G4/5 作为个人计算机,你使用它来做什么?为什么呢?**
|
||||
|
||||
Linus:我最终放弃了那台 PowerPC,因为没有人能在这台工作站上做到更多,特别是,自从 x86-64 开始变得越来越强大了。所以这些天,我在用一台标准的 PC,里面是一个普通的 Core 2 Duo CPU。
|
||||
|
||||
在其它架构下运行是非常有趣的(alpha 作为我的主要架构运行了好几年,所以这并不是第一次),但是这种 CPU 得当成商品买得到才行。我认为,唯一能取代 x86 架构的,也许未来十年并不需要使用 x86 作为主要架构,我认为或许是 ARM,这得益于移动设备市场的发展。
|
||||
|
||||
**Q:Linux 对你意味着什么?一种业余爱好、哲学、人生意义、工作、最好的操作系统,还是什么?**
|
||||
|
||||
Linus:它是所有的这一切。它是爱好,而且是具有深刻意义的爱好。最好的爱好是你‘真的’非常在意它。这些日子里,它显然也是我的工作,我非常高兴工作和兴趣能合二为一。
|
||||
|
||||
我不了解所谓的‘哲学’,我并不真的是因为深层次的道德或哲学的原因才做的 Linux,但是可以肯定的是,对开源的深层思考是我非常重视的。所以我并不是因为什么明确的理由做 Linux,也不能说是它在激励我,但是我的确在思考开源是如何工作。
|
||||
|
||||
**Q:微软的‘黑衣人’有没有和你交谈过?**
|
||||
|
||||
Linus:我从来没有真正和微软交谈过,没有。我偶尔会和一些微软的人出现再同一个会议上(我比以前参加的会议更多了),但是我从来和他们没有任何关系。我认为彼此都很谨慎吧。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxveda.com/2015/06/17/what-happens-to-linux-after-linus/
|
||||
|
||||
作者:[Swapnil Bhartiya][a]
|
||||
译者:[wi-cuckoo](https://github.com/wi-cuckoo),[wxy](https://github.com/wxy)
|
||||
校对:mahua, [wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxveda.com/author/arnieswap/
|
||||
|
||||
@ -0,0 +1,33 @@
|
||||
Linus Torvalds Says People Who Believe in AI Singularity Are on Drugs
|
||||
================================================================================
|
||||
*As usual, his comments should not be taken literally*
|
||||
|
||||

|
||||
|
||||
**AI is a very hot topic right now, and many high profile people, including Elon Musk, the head of Tesla, have said that we're going to get sentient AIs soon and that it's going to be a dangerous threshold. It seems that Linus Torvalds doesn't feel the same way, and he thinks that it's just bad Sci-Fi.**
|
||||
|
||||
The idea of AIs turning on their human creators is not something new, but recently the so-called AI singularity has been discussed, and people like Elon Musk and Stephen Hawking expressed concerns about the possibility of creating a monster. And it's not just them, forums and comments sections are full of alarmist people who don't know what to believe or who take for granted the opinions of much smarter people.
|
||||
|
||||
As it turns out, Linus Torvalds, the creator of the Linux project, has a completely different opinion on this matter. In fact, he says that nothing like this will happen, and we have a much better reason to believe him. AI means that someone wrote its code, and Linus knows the power and the obstacles of writing an AI code. He's much likely to guess what's involved and to understands why an AI won't be a threat.
|
||||
|
||||
### Linus Torvalds and AIs ###
|
||||
|
||||
Linus Torvalds answered some questions from the community on [slashdot.org][1], and all his ideas were very interesting. He talked about the [future of gaming and Valve][2], but he also tackled stuff like AI. He's usually asked stuff about the kernel or open source, but he has opinions on other topics as well. As a matter a fact, the AI subject is something that he can actually talk about as a programmer.
|
||||
|
||||
"So I'd expect just more of (and much fancier) rather targeted AI, rather than anything human-like at all. Language recognition, pattern recognition, things like that. I just don't see the situation where you suddenly have some existential crisis because your dishwasher is starting to discuss Sartre with you. The whole 'Singularity' kind of event? Yeah, it's science fiction, and not very good Sci-Fi at that, in my opinion. Unending exponential growth? What drugs are those people on? I mean, really" wrote Linus on Slashdot.
|
||||
|
||||
It's your choice whether to believe Elon Musk or Linus, but if betting were involved, I would put my money on Linus.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/linus-torvalds-says-people-who-believe-in-an-ai-singularity-are-on-drugs-486373.shtml
|
||||
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
[1]:http://classic.slashdot.org/story/15/06/30/0058243
|
||||
[2]:http://news.softpedia.com/news/linus-torvalds-said-valve-is-exploring-a-second-source-against-microsoft-486266.shtml
|
||||
@ -1,153 +0,0 @@
|
||||
translating by ZTinoZ
|
||||
Screen Capture Made Easy with these Dedicated Tools
|
||||
================================================================================
|
||||
"A picture is worth a thousand words", a phrase which emerged in the USA in the early part of the 20th century, refers to the notion that a single still image can present as much information as a large amount of descriptive text. Essentially, pictures convey information more effectively and efficiently than words can.
|
||||
|
||||
A screenshot (or screengrab) is a snapshot or picture captured by a computer to record the output of a visual device. Screen capture software enable screenshots to be taken on a computer. This type of software has lots of uses. As an image can illustrate the operation of computer software well, screenshots play an important role in software development and documentation. Alternatively, if you have a technical problem with your computer, a screenshot allows a technical support department to understand the problems you are facing. Writing computer-related articles, documentation and tutorials is nigh on impossible without a good tool for creating screenshots. Screenshots are also useful to save snippets of anything you have on your screen, particularly when it can not be easily printed.
|
||||
|
||||
Linux has a good selection of open source dedicated screenshot programs, both graphical and console based. For a feature-rich dedicated screenshot utility, look no further than Shutter. This tool is a superb example of a small open source tool. But there are some great alternatives too.
|
||||
|
||||
Screen capture functionality is not only provided by dedicated applications. GIMP and ImageMagick, two programs which are primarily image manipulation tools, also offer competent screen capturing functionality.
|
||||
|
||||
----------
|
||||
|
||||
### Shutter ###
|
||||
|
||||

|
||||
|
||||
Shutter is a feature-rich screenshot application. You can take a screenshot of a specific area, window, your whole screen, or even of a website - apply different effects to it, draw on it to highlight points, and then upload to an image hosting site, all within one window.
|
||||
|
||||
Features include:
|
||||
|
||||
|
||||
- Take a screenshot of:
|
||||
- a specific area
|
||||
- window
|
||||
- the complete desktop
|
||||
- web pages from a script
|
||||
- Apply different effects to the screenshot
|
||||
- Hotkeys
|
||||
- Print
|
||||
- Take screenshot directly or with a specified delay time
|
||||
- Save the screenshots to a specified directory and name them in a convenient way (using special wild-cards)
|
||||
- Fully integrated into the GNOME Desktop (TrayIcon etc)
|
||||
- Generate thumbnails directly when you are taking a screenshot and set a size level in %
|
||||
- Shutter session collection:
|
||||
- Keep track of all screenshots during session
|
||||
- Copy screeners to clipboard
|
||||
- Print screenshots
|
||||
- Delete screenshots
|
||||
- Rename your file
|
||||
- Upload your files directly to Image-Hosters (e.g. http://ubuntu-pics.de), retrieve all the needed links and share them with others
|
||||
- Edit screenshots directly using the embedded drawing tool
|
||||
|
||||
- Website: [shutter-project.org][1]
|
||||
- Developer: Mario Kemper and Shutter Team
|
||||
- License: GNU GPL v3
|
||||
- Version Number: 0.93.1
|
||||
|
||||
----------
|
||||
|
||||
### HotShots ###
|
||||
|
||||

|
||||
|
||||
HotShots is an application for capturing screens and saving them in a variety of image formats as well as adding annotations and graphical data (arrows, lines, texts, ...).
|
||||
|
||||
You can also upload your creations to the web (FTP/some web services). HotShots is written with Qt.
|
||||
|
||||
HotShots is not available in Ubuntu's Software Center. But it's easy to install by typing at the command line:
|
||||
|
||||
sudo add-apt-repository ppa:ubuntuhandbook1/apps
|
||||
|
||||
sudo apt-get update
|
||||
|
||||
sudo apt-get install hotshots
|
||||
|
||||
Features include:
|
||||
|
||||
- Simple to use
|
||||
- Full featured
|
||||
- Built-in editor
|
||||
- Hotkeys
|
||||
- Built-in magnification
|
||||
- Freehand and multi-screen capture
|
||||
- Supported Output Formats: Black & Whte (bw), Encapsulated PostScript (eps, epsf), Encapsulated PostScript Interchange (epsi), OpenEXR (exr), PC Paintbrush Exchange (pcx), Photoshop Document (psd), ras, rgb, rgba, Irix RGB (sgi), Truevision Targa (tga), eXperimental Computing Facility (xcf), Windows Bitmap (bmp), DirectDraw Surface (dds), Graphic Interchange Format (gif), Icon Image (ico), Joint Photographic Experts Group 2000 (jp2), Joint Photographic Experts Group (jpeg, jpg), Multiple-image Network Graphics (mng), Portable Pixmap (ppm), Scalable Vector Graphics (svg), svgz, Tagged Image File Format (tif, tiff), webp, X11 Bitmap (xbm), X11 Pixmap (xpm), and Khoros Visualization (xv)
|
||||
- Internationalization support: Basque, Chinese, Czech, French, Galician, German, Greek, Italian, Japanese, Lithuanian, Polish, Portuguese, Romanian, Russian, Serbian, Singhalese, Slovak, Spanish, Turkish, Ukrainian, and Vietnamese
|
||||
|
||||
- Website: [thehive.xbee.net][2]
|
||||
- Developer: xbee
|
||||
- License: GNU GPL v2
|
||||
- Version Number: 2.2.0
|
||||
|
||||
----------
|
||||
|
||||
### ScreenCloud ###
|
||||
|
||||

|
||||
|
||||
ScreenCloud is an easy to use open source screenshot tool.
|
||||
|
||||
With this software, users can take a screenshot using one of the 3 hotkeys or simply click the ScreenCloud tray icon. Users can choose where you want to save the screenshot.
|
||||
|
||||
If you choose to upload your screenshot to the screencloud website, a link will automatically be copied to your clipboard. This can be shared with friends or colleagues via email or in an IM conversation. All they have to do is click the link and look at your screenshot.
|
||||
|
||||
Features include:
|
||||
|
||||
- Capture full screen, window or selection
|
||||
- Fast and easy: Snap a photo, paste the link, done
|
||||
- Free hosting of your screenshots
|
||||
- Hotkeys
|
||||
- Set timer delay
|
||||
- Enable 'Capture window borders'
|
||||
- Enable/Disable Notifications
|
||||
- Set app to run on start up
|
||||
- Adjust account/upload/filename/shortcut settings
|
||||
- Cross platform tool
|
||||
- Plugin support, save to Dropbox, Imgur, and more
|
||||
- Supports uploading to FTP and SFTP servers
|
||||
|
||||
- Website: [screencloud.net][3]
|
||||
- Developer: Olav S Thoresen
|
||||
- License: GNU GPL v2
|
||||
- Version Number: 1.2.1
|
||||
|
||||
----------
|
||||
|
||||
### KSnapshot ###
|
||||
|
||||

|
||||
|
||||
KSnapshot is a simple utility for taking screenshots. It can capture images of the whole desktop, a single window, a section of a window or a selected region. Images can then be saved in a variety of different formats.
|
||||
|
||||
KSnapshot also allows users to use hotkeys to take a screenshot. Besides saving the screenshot, it can be copied to the clipboard or opened with any program that is associated with image files.
|
||||
|
||||
KSnapshot is part of the KDE 4 graphics module.
|
||||
|
||||
Features include:
|
||||
|
||||
- Save snapshot in multiple formats
|
||||
- Snapshot delay
|
||||
- Exclude window decorations
|
||||
- Copy the snapshot to the clipboard
|
||||
- Hotkeys
|
||||
- Can be scripted using its D-Bus interface
|
||||
|
||||
- Website: [www.kde.org][4]
|
||||
- Developer: KDE, Richard J. Moore, Aaron J. Seigo, Matthias Ettrich
|
||||
- License: GNU GPL v2
|
||||
- Version Number: 0.8.2
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/2015062316235249/ScreenCapture.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://shutter-project.org/
|
||||
[2]:http://thehive.xbee.net/
|
||||
[3]:https://screencloud.net/
|
||||
[4]:https://www.kde.org/applications/graphics/ksnapshot/
|
||||
@ -0,0 +1,184 @@
|
||||
Interviews: Linus Torvalds Answers Your Question
|
||||
================================================================================
|
||||
Last Thursday you had a chance to [ask Linus Torvalds][1] about programming, hardware, and all things Linux. You can read his answers to those questions below. If you'd like to see what he had to say the last time we sat down with him, [you can do so here][2].
|
||||
|
||||
**Productivity**
|
||||
by DoofusOfDeath
|
||||
|
||||
> You've somehow managed to originate two insanely useful pieces of software: Linux, and Git. Do you think there's anything in your work habits, your approach to choosing projects, etc., that have helped you achieve that level of productivity? Or is it just the traditional combination of talent, effort, and luck?
|
||||
|
||||
**Linus**: I'm sure it's pretty much always that "talent, effort and luck". I'll leave it to others to debate how much of each...
|
||||
|
||||
I'd love to point out some magical work habit that makes it all happen, but I doubt there really is any. Especially as the work habits I had wrt the kernel and Git have been so different.
|
||||
|
||||
With Git, I think it was a lot about coming at a problem with fresh eyes (not having ever really bought into the traditional SCM mindset), and really trying to think about the issues, and spending a fair amount of time thinking about what the real problems were and what I wanted the design to be. And then the initial self-hosting code took about a day to write (ok, that was "self-hosting" in only the weakest sense, but still).
|
||||
|
||||
And with Linux, obviously, things were very different - the big designs came from the outside, and it took half a year to host itself, and it hadn't even started out as a kernel to begin with. Clearly not a lot of thinking ahead and planning involved ;). So very different circumstances indeed.
|
||||
|
||||
What both the kernel and Git have, and what I think is really important (and I guess that counts as a "work habit"), is a maintainer that stuck to it, and was responsive, responsible and sane. Too many projects falter because they don't have people that stick with them, or have people who have an agenda that doesn't match reality or the user expectations.
|
||||
|
||||
But it's very important to point out that for Git, that maintainer was not me. Junio Hamano really should get pretty much all the credit for Git. Credit where credit is due. I'll take credit for the initial implementation and design of Git - it may not be perfect, but ten years on it still is very solid and very clearly the same basic design. But I'll take even _more_ credit for recognizing that Junio had his head screwed on right, and was the person to drive the project. And all the rest of the credit goes to him.
|
||||
|
||||
Of course, that kind of segues into something else the kernel and Git do have in common: while I still maintain the kernel, I did end up finding a lot of smart people to maintain all the different parts of it. So while one important work habit is that "stick to it" persistence that you need to really take a project from a not-quite-usable prototype to something bigger and better, another important work-habit is probably to also "let go" and not try to own and control the project too much. Let other people really help you - guide the process but don't get in their way.
|
||||
|
||||
**init system**
|
||||
by lorinc
|
||||
|
||||
> There wasn't a decent unix-like kernel, you wrote one which ultimately became the most used. There wasn't a decent version control software, you wrote one which ultimately became the most love. Do you think we already have a decent init system, or do you have plan to write one that will ultimately settle the world on that hot topic?
|
||||
|
||||
**Linus**: You can say the word "systemd", It's not a four-letter word. Seven letters. Count them.
|
||||
|
||||
I have to say, I don't really get the hatred of systemd. I think it improves a lot on the state of init, and no, I don't see myself getting into that whole area.
|
||||
|
||||
Yeah, it may have a few odd corners here and there, and I'm sure you'll find things to despise. That happens in every project. I'm not a huge fan of the binary logging, for example. But that's just an example. I much prefer systemd's infrastructure for starting services over traditional init, and I think that's a much bigger design decision.
|
||||
|
||||
Yeah, I've had some personality issues with some of the maintainers, but that's about how you handle bug reports and accept blame (or not) for when things go wrong. If people thought that meant that I dislike systemd, I will have to disappoint you guys.
|
||||
|
||||
**Can Valve change the Linux gaming market?**
|
||||
by Anonymous Coward
|
||||
|
||||
> Do you think Valve is capable of making Linux a primary choice for gamers?
|
||||
|
||||
**Linus**: "Primary"? Probably not where it's even aiming. I think consoles (and all those handheld and various mobile platforms that "real gamers" seem to dismiss as toys) are likely much more primary, and will stay so.
|
||||
|
||||
I think Valve wants to make sure they can control their own future, and Linux and ValveOS is probably partly to explore a more "console-like" Valve experience (ie the whole "get a box set up for a single main purpose", as opposed to a more PC-like experience), and partly as a "second source" against Microsoft, who is a competitor in the console area. Keeping your infrastructure suppliers honest by making sure you have alternatives sounds like a good strategy, and particularly so when those suppliers may be competing with you directly elsewhere.
|
||||
|
||||
So I don't think the aim is really "primary". "Solid alternative" is I think the aim. Of course, let's see where it goes after that.
|
||||
|
||||
But I really have not been involved. People like Greg and the actual graphics driver guys have been in much more direct contact with Valve. I think it's great to see gaming on Linux, but at the same time, I'm personally not really much of a gamer.
|
||||
|
||||
**The future of RT-Linux?**
|
||||
by nurhussein
|
||||
|
||||
> According to Thomas Gleixner, [the future of the realtime patchset to Linux is in doubt][2], as it is difficult to secure funding from interested parties on this functionality even though it is both useful and important: What are your thoughts on this, and what do you think we need to do to get more support behind the RT patchset, especially considering Linux's increasing use in embedded systems where realtime functionality is undoubtedly useful.
|
||||
|
||||
**Linus**: So I think this is one of those things where the markets decide how important rtLinux ends up being, and I suspect there are more than enough companies who end up wanting and using rtLinux that the project isn't really going anywhere. The complaints by Thomas were - I think - a wake-up call to the companies who end up wanting the extended hard realtime patches.
|
||||
|
||||
So I suspect there are companies and groups like OSADL that end up funding and helping with rtLinux, and that it isn't going away.
|
||||
|
||||
**Rigor and developments**
|
||||
by hcs_$reboot
|
||||
|
||||
> The most complex program running on a machine is arguably its OS, especially the kernel. Linux (kernel) reached the top level in terms of performance, reliability and versatility. You have been criticized quite a few times for some virulent mails addressed to developers. Do you think Linux would be where it is without managing the project with an iron fist? To go further, do you think some other main OSS project would benefit from a more rigorous management approach?
|
||||
|
||||
**Linus**: One of the nice things about open source is how it allows people to really concentrate on what they are good at, and it has been a huge advantage for Linux that we've had people who are interested in the marketing side and selling Linux, as well as the legal side etc.
|
||||
|
||||
And that is all in addition, of course, to the original "we're motivated by the technology" people like me. And even within that "we're motivated by technology" group, you most certainly don't need to find _everything_ interesting, you can find the area you are passionate about and really care about and want to work on.
|
||||
|
||||
That's _fundamentally_ how open source works.
|
||||
|
||||
Now, if somebody is passionate about some "good management" thing, go wild, and try to get involved, and try to manage things. It's not what _I_ am interested in, but hey, the proof is in the pudding - anybody who thinks they have a new rigorous management approach that they think will help some part of the process, go wild.
|
||||
|
||||
Now, I personally suspect that it wouldn't work - not only are tech people an ornery lot to begin with (that whole "herding cats" thing), just look at all the crazy arguments on the internet. And ask yourself what actually holds an open source project like the kernel together? I think you need to be very oriented towards the purely technical solutions, simply because then you have tangible and real issues you can discuss (and argue about) with fairly clear-cut hard answers. It's the only thing people can really agree on in the big picture.
|
||||
|
||||
So the Linux approach to "management" has been to put technology first. That's rigorous enough for me. But as mentioned, it's a free-for-all. Anybody can come in and try to do better. Really.
|
||||
|
||||
And btw, it's worth noting that there are obviously specific smaller development teams where other management models work fine. Most of the individual developers are parts of teams inside particular companies, and within the confines of that company, there may well be a very strict rigorous management model. Similarly, within the confines of a particular productization effort there may be particular goals and models for that particular team that transcend that general "technical issues" thing.
|
||||
|
||||
Just to give a concrete example, the "development kernel" tree that I maintain works fundamentally differently and with very different rules from the "stable tree" that Greg does, which in turn is maintained very differently from what a distribution team within a Linux company does inside its maintenance kernel team.
|
||||
|
||||
So there's certainly room for different approaches to managing those very different groups. But do I think you can "rigorously manage" people on the internet? No.
|
||||
|
||||
**Functional languages?**
|
||||
by EmeraldBot
|
||||
|
||||
> While historically you've been a C and Assembly guy (and the odd shell scripting and such), what do you think of functional languages such as Lisp, Closure, Haskell, etc? Do you see any advantages to them, or do you view them as frivolous and impractical? If you decide to do so, thanks for taking the time to answer my question! You're a legend at what you do, and I think it's awesome that the significantly less interesting me can ask you a question like this.
|
||||
|
||||
**Linus**: I may be a fan of C (with a certain fondness for assembly, just because it's so close to the machine), but that's very much about a certain context. I work at a level where those languages make sense. I certainly don't think that tools like Haskell etc are "frivolous and impractical" in general, although on a kernel level (or in a source control management system) I suspect they kind of are.
|
||||
|
||||
Many moons ago I worked on sparse (the C parser and analyzer), and one of my coworkers was a Haskell fan, and did incredible example transformations in very simple (well, to him) code - stuff that is just nasty to write in C because it's pretty high-level, there's tons of memory management, and you're really talking about implementing fairly abstract and high-level rules with pattern matching etc.
|
||||
|
||||
So I'm definitely not a functional language kind of guy - it's not how I learnt programming, and it really isn't very relevant to what I do, and I wouldn't recognize Haskell code if it bit me in the ass and called me names. But no, I wouldn't call them frivolous.
|
||||
|
||||
**Critical software to the use of Linux**
|
||||
by TWX
|
||||
|
||||
> Mr. Torvalds, For many uses of Linux such as on the desktop, other software beyond the kernel and the base GNU tools are required. What other projects would you like to see given priority, and what would you like to see implemented or improved? Admittedly I thought most about X-Windows when asking this question; but I don't doubt that other daemons or systems can be just as important to the user experience. Thank you for your efforts all these years.
|
||||
|
||||
**Linus**: Hey, I don't really have any particular project I would want to champion, largely because we all have so different requirements on the desktop. There's just no single thing that stands out as being hugely more important than others to me.
|
||||
|
||||
What I do wish particularly desktop developers cared about is "consistency of experience". And by that I don't mean some kind of enforced visual consistency between different applications to make things "look coherent". No, I'm just talking about the pain and uncertainty users go through with upgrades, and understanding that while your project may be the most important project to *you* (because it's what you do), to your users, your project is likely just a fairly small and irrelevant part of their experience, and it's not very central at all, and they've learnt the quirks about that thing they don't even care about, and you really shouldn't break their expectations. Because it turns out that that is how you really make people hate their desktop.
|
||||
|
||||
This is not at all Linux-specific, of course - just look at the less than enthusiastic reception that other operating system redesigns have received. But I really wish that we hadn't had *both* of the major Linux desktop environments have to learn this (well, I hope they learnt) the hard way, and both of them ending up blaming their users rather than themselves.
|
||||
|
||||
**"anykernel"-style portable drivers?**
|
||||
by staalmannen
|
||||
|
||||
> What do you think about the "anykernel" concept (invented by another Finn btw) used in NetBSD? Basically, they have modularized the code so that a driver can be built either in a monolithic kernel or for user space without source code changes ( rumpkernel.org ). The drivers are highly portable and used in Genode os (L4 type kernels), minix etc... Would this be possible or desirable for Linux? Apparently there is one attempt called "libos"...
|
||||
|
||||
**Linus**: So I have bad experiences with "portable" drivers. Writing drivers to some common environment tends to force some ridiculously nasty impedance matching abstractions that just get in the way and make things really hard to read and modify. It gets particularly nasty when everybody ends up having complicated - and differently so - driver subsystems to handle a lot of commonalities for a certain class of drivers (say a network driver, or a USB driver), and the different operating systems really have very different approaches and locking rules etc.
|
||||
|
||||
I haven't seen anykernel drivers, but from past experience my reaction to "portable device drivers" is to run away, screaming like little girl. As they say in Swedish "Bränt barn luktar illa".
|
||||
|
||||
**Processor Architecture**
|
||||
by swv3752
|
||||
|
||||
> Several years ago, you were employed by Transmeta designing the Crusoe processor. I understand you are quite knowledgeable about cpu architecture. What are your thoughts on the Current Intel and AMD x86 CPUs particularly in comparison with ARM and IBM's Power8 CPUs? Where do you see the advantages of each one?
|
||||
|
||||
**Linus**: I'm no CPU architect, I just play one on TV.
|
||||
|
||||
But yes, I've been close to the CPU both as part of my kernel work, and as part of a processor company, and working at that level for a long time just means that you end up having fairly strong opinions. One of the things that my experiences at Transmeta convinced me of, for example, was that there's definitely very much a limit to what software should care about. I loved working at Transmeta, I loved the whole startup company environment, I loved working with really smart people, but in the end I ended up absolutely *not* loving to work with overly simple hardware (I also didn't love the whole IPO process, and what that did to the company culture, but that's a different thing).
|
||||
|
||||
Because there's only so much that software can do to compensate.
|
||||
|
||||
Something similar happened with my kernel work on the alpha architecture, which also started out as being an overly simplified implementation in the name of being small and supposedly running really fast. While I really started out liking the alpha architecture for being so clean, I ended up detesting how fragile the architecture implementations were (and by the time that got fixed in the 21264, I had given up on alpha).
|
||||
|
||||
So I've come to absolutely detest CPU's that need a lot of compiler smarts or special tuning to go fast. Life is too short to waste on in-order CPU's, or on hardware designers who think software should take care of the pieces that they find to be too complicated to handle themselves, and as a result just left undone. "Weak memory ordering" is just another example.
|
||||
|
||||
Thankfully, most of the industry these days seems to agree. Yes, there are still in-order cores, but nobody tries to make excuses for them any more: they are for the truly cheap and low-end market.
|
||||
|
||||
I tend to really like the modern Intel cores in particular, which tend to take that "let's not be stupid" really to heart. With the kernel being so threaded, I end up caring a lot about things like memory ordering etc, and the Intel big-core CPU's tend to be in a class of their own there. As a software person who cares about performance and looks at instruction profiles etc, it's just so *nice* to see that the CPU doesn't have some crazy glass jaw where you have to be very careful.
|
||||
|
||||
**GPU kernels**
|
||||
by maraist
|
||||
|
||||
> Is there any inspiration that a GPU based kernel / scheduler has for you? How might Linux be improved to better take advantage of GPU-type batch execution models. Given that you worked transmeta and JIT compiled host-targeted runtimes. GPUs 1,000-thread schedulers seem like the next great paradigm for the exact type of machines that Linux does best on.
|
||||
|
||||
**Linus**: I don't think we'll see the kernel ever treat GPU threads the way we treat CPU threads. Not with the current model of GPU's (and that model doesn't really seem to be changing all that much any more).
|
||||
|
||||
Yes, GPU's are getting much better, and now generally have virtual memory and the ability to preempt execution, and you could run an OS on them. But the scheduling latencies are pretty high, and the threads are not really "independent" (ie they tend to share a lot of state - like the virtual address space and a large shared register set), so GPU "threads" don't tend to work like CPU threads. You'd schedule them all-or-nothing, so if you were to switch processes, you'd treat the GPU as one entity where you switch all the threads at once.
|
||||
|
||||
So it really wouldn't look like a thousand threads to the kernel. The GPU would still be scheduled as one single entity (or maybe a couple of entities depending on how the GPU is partitioned). The fact that that single entity works by doing a lot of things in massive parallelism is kind of immaterial for the kernel that doesn't end up seeing that parallelism as separate threads.
|
||||
|
||||
**alleged danger of Artificial Intelligence**
|
||||
by peter303
|
||||
|
||||
> Some computer experts like Marvin Minsky, Larry Page, Ray Kuzweil think A.I. will be a great gift to Mankind. Others like Bill Joy and Elon Musk are fearful of potential danger. Where do you stand, Linus?
|
||||
|
||||
**Linus**: I just don't see the thing to be fearful of.
|
||||
|
||||
We'll get AI, and it will almost certainly be through something very much like recurrent neural networks. And the thing is, since that kind of AI will need training, it won't be "reliable" in the traditional computer sense. It's not the old rule-based prolog days, when people thought they'd *understand* what the actual decisions were in an AI.
|
||||
|
||||
And that all makes it very interesting, of course, but it also makes it hard to productize. Which will very much limit where you'll actually find those neural networks, and what kinds of network sizes and inputs and outputs they'll have.
|
||||
|
||||
So I'd expect just more of (and much fancier) rather targeted AI, rather than anything human-like at all. Language recognition, pattern recognition, things like that. I just don't see the situation where you suddenly have some existential crisis because your dishwasher is starting to discuss Sartre with you.
|
||||
|
||||
The whole "Singularity" kind of event? Yeah, it's science fiction, and not very good SciFi at that, in my opinion. Unending exponential growth? What drugs are those people on? I mean, really..
|
||||
|
||||
It's like Moore's law - yeah, it's very impressive when something can (almost) be plotted on an exponential curve for a long time. Very impressive indeed when it's over many decades. But it's _still_ just the beginning of the "S curve". Anybody who thinks any different is just deluding themselves. There are no unending exponentials.
|
||||
|
||||
**Is the kernel basically a finished project?**
|
||||
by NaCh0
|
||||
|
||||
> Aside from adding drivers and refactoring algorithms when performance limits are discovered, is there anything left for the kernel? Maybe it's a failure of tech journalism but we never hear about the next big thing in kernel land anymore.
|
||||
|
||||
**Linus**: I don't think there's much of a "next big thing" in the kernel.
|
||||
|
||||
I wouldn't say that there is nothing but drivers (and architectures are kind of "CPU drivers) and improving scalability left, because I'm constantly amazed by how many new things people figure out are still good ideas. But they tend to still be pretty incremental improvements. An OS kernel doesn't look *that* radically different from what it was 40 years ago, and that's fine. I think radical new ideas are often overrated, and the thing that really matters in the end is that plodding detail work. That's how technology evolves.
|
||||
|
||||
And judging by how our kernel releases are going, there's no end in sight for that "plodding detail work". And it's still as interesting as it ever was.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linux.slashdot.org/story/15/06/30/0058243/interviews-linus-torvalds-answers-your-question
|
||||
|
||||
作者:[samzenpus][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:samzenpus@slashdot.org
|
||||
[1]:http://interviews.slashdot.org/story/15/06/24/1718247/interview-ask-linus-torvalds-a-question
|
||||
[2]:http://meta.slashdot.org/story/12/10/11/0030249/linus-torvalds-answers-your-questions
|
||||
[3]:https://lwn.net/Articles/604695/
|
||||
@ -0,0 +1,79 @@
|
||||
7 command line tools for monitoring your Linux system
|
||||
================================================================================
|
||||
**Here is a selection of basic command line tools that will make your exploration and optimization in Linux easier. **
|
||||
|
||||

|
||||
|
||||
### Dive on in ###
|
||||
|
||||
One of the great things about Linux is how deeply you can dive into the system to explore how it works and to look for opportunities to fine tune performance or diagnose problems. Here is a selection of basic command line tools that will make your exploration and optimization easier. Most of these commands are already built into your Linux system, but in case they aren’t, just Google “install”, the command name, and the name of your distro and you’ll find which package needs installing (note that some commands are bundled with other commands in a package that has a different name from the one you’re looking for). If you have any other tools you use, let me know for our next Linux Tools roundup.
|
||||
|
||||
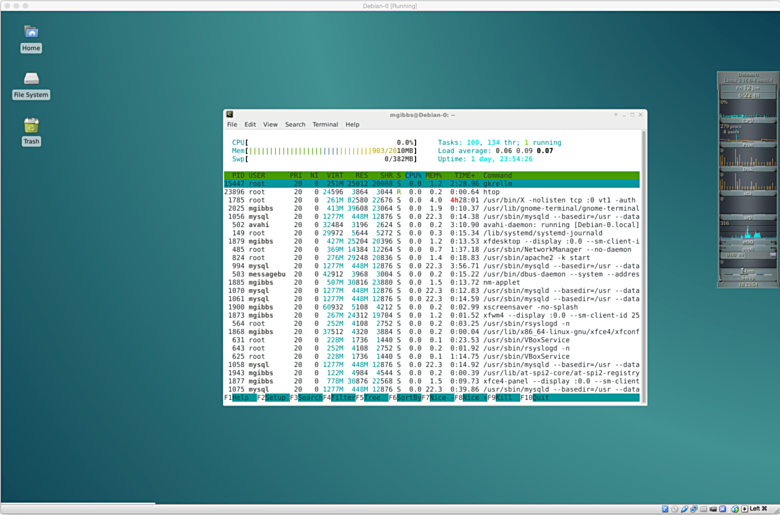
|
||||
|
||||
### How we did it ###
|
||||
|
||||
FYI: The screenshots in this collection were created on [Debian Linux 8.1][1] (“Jessie”) running in a virtual machine under [Oracle VirtualBox 4.3.28][2] under [OS X 10.10.3][3] (“Yosemite”). See my next slideshow “[How to install Debian Linux in a VirtualBox VM][4]” for a tutorial on how to build your own Debian VM.
|
||||
|
||||
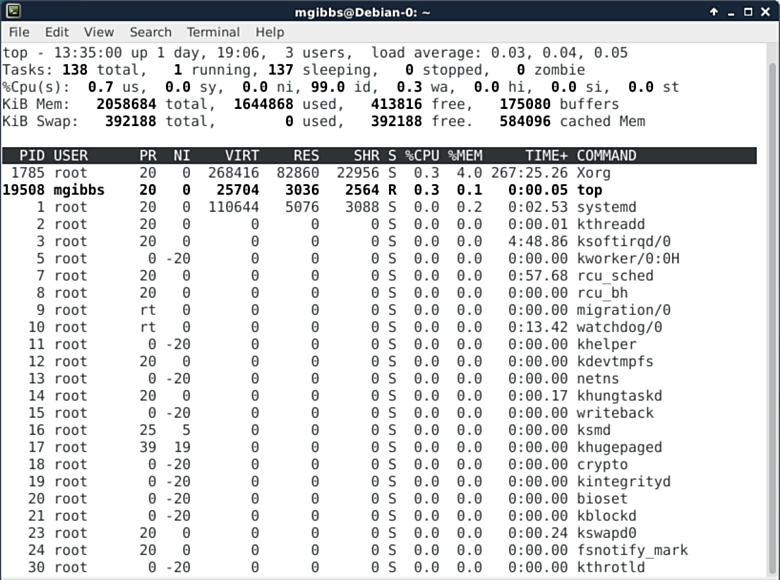
|
||||
|
||||
### Top command ###
|
||||
|
||||
One of the simpler Linux system monitoring tools, the **top command** comes with pretty much every flavor of Linux. This is the default display, but pressing the “z” key switches the display to color. Other hot keys and command line switches control things such as the display of summary and memory information (the second through fourth lines), sorting the list according to various criteria, killing tasks, and so on (you can find the complete list at [here][5]).
|
||||
|
||||
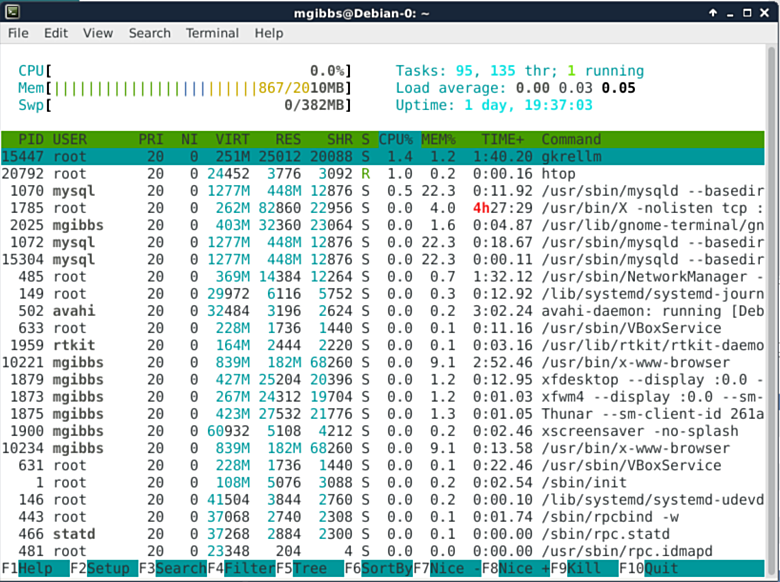
|
||||
|
||||
### htop ###
|
||||
|
||||
Htop is a more sophisticated alternative to top. Wikipedia: “Users often deploy htop in cases where Unix top does not provide enough information about the systems processes, for example when trying to find minor memory leaks in applications. Htop is also popularly used interactively as a system monitor. Compared to top, it provides a more convenient, cursor-controlled interface for sending signals to processes.” (For more detail go [here][6].)
|
||||
|
||||
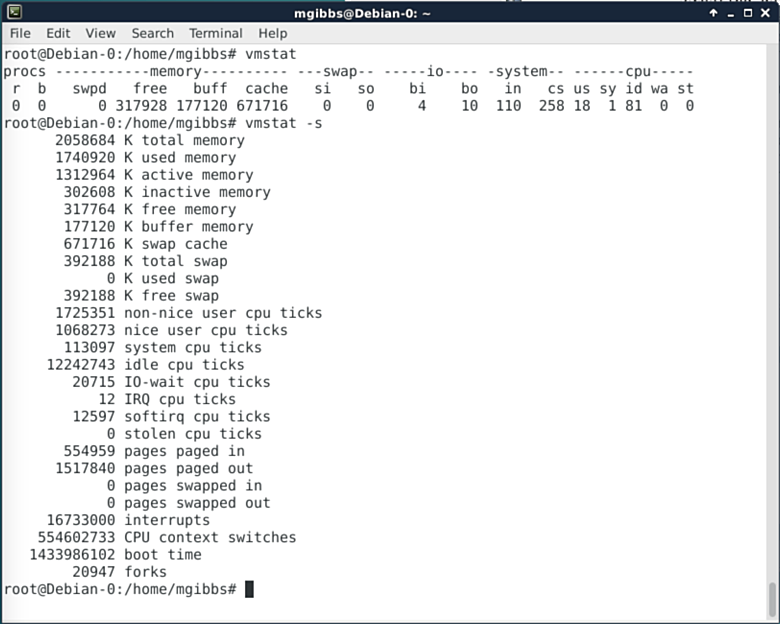
|
||||
|
||||
### Vmstat ###
|
||||
|
||||
Vmstat is a simpler tool for monitoring your Linux system performance statistics but that makes it highly suitable for use in shell scripts. Fire up your regex-fu and you can do some amazing things with vmstat and cron jobs. “The first report produced gives averages since the last reboot. Additional reports give information on a sampling period of length delay. The process and memory reports are instantaneous in either case” (go [here][7] for more info.).
|
||||
|
||||
|
||||
|
||||
### ps ###
|
||||
|
||||
The ps command shows a list of running processes. In this case, I’ve used the “-e”switch to show everything, that is, all processes running (I’ve scrolled back to the top of the output otherwise the column names wouldn’t be visible). This command has a lot of switches that allow you to format the output as needed. Add a little of the aforementioned regex-fu and you’ve got a powerful tool. Go [here][8] for the full details.
|
||||
|
||||
|
||||
|
||||
### Pstree ###
|
||||
|
||||
Pstree “shows running processes as a tree. The tree is rooted at either pid or init if pid is omitted. If a user name is specified, all process trees rooted at processes owned by that user are shown.”This is a really useful tool as the tree helps you sort out which process is dependent on which process (go [here][9]).
|
||||
|
||||
|
||||
|
||||
### pmap ###
|
||||
|
||||
Understanding just how an app uses memory is often crucial in debugging, and the pmap produces just such information when given a process ID (PID). The screenshot shows the medium weight output generated by using the “-x”switch. You can get pmap to produce even more detailed information using the “-X”switch but you’ll need a much wider terminal window.
|
||||
|
||||
|
||||
|
||||
### iostat ###
|
||||
|
||||
A crucial factor in your Linux system’s performance is processor and storage usage, which are what the iostat command reports on. As with the ps command, iostat has loads of switches that allow you to select the output format you need as well as sample performance over a time period and then repeat that sampling a number of times before reporting. See [here][10].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.networkworld.com/article/2937219/linux/7-command-line-tools-for-monitoring-your-linux-system.html
|
||||
|
||||
作者:[Mark Gibbs][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.networkworld.com/author/Mark-Gibbs/
|
||||
[1]:https://www.debian.org/releases/stable/
|
||||
[2]:https://www.virtualbox.org/
|
||||
[3]:http://www.apple.com/osx/
|
||||
[4]:http://www.networkworld.com/article/2937148/how-to-install-debian-linux-8-1-in-a-virtualbox-vm
|
||||
[5]:http://linux.die.net/man/1/top
|
||||
[6]:http://linux.die.net/man/1/htop
|
||||
[7]:http://linuxcommand.org/man_pages/vmstat8.html
|
||||
[8]:http://linux.die.net/man/1/ps
|
||||
[9]:http://linux.die.net/man/1/pstree
|
||||
[10]:http://linux.die.net/man/1/iostat
|
||||
@ -1,3 +1,5 @@
|
||||
FSSlc Translating
|
||||
|
||||
Autojump – An Advanced ‘cd’ Command to Quickly Navigate Linux Filesystem
|
||||
================================================================================
|
||||
Those Linux users who mainly work with Linux command Line via console/terminal feels the real power of Linux. However it may sometimes be painful to navigate inside Linux Hierarchical file system, specially for the newbies.
|
||||
@ -219,4 +221,4 @@ via: http://www.tecmint.com/autojump-a-quickest-way-to-navigate-linux-filesystem
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:http://www.tecmint.com/cd-command-in-linux/
|
||||
[2]:http://www.tecmint.com/how-to-enable-epel-repository-for-rhel-centos-6-5/
|
||||
[3]:http://www.tecmint.com/manage-linux-filenames-with-special-characters/
|
||||
[3]:http://www.tecmint.com/manage-linux-filenames-with-special-characters/
|
||||
|
||||
359
sources/tech/20150706 PHP Security.md
Normal file
359
sources/tech/20150706 PHP Security.md
Normal file
@ -0,0 +1,359 @@
|
||||
PHP Security
|
||||
================================================================================
|
||||

|
||||
|
||||
### Introduction ###
|
||||
|
||||
When offering an Internet service, you must always keep security in mind as you develop your code. It may appear that most PHP scripts aren't sensitive to security concerns; this is mainly due to the large number of inexperienced programmers working in the language. However, there is no reason for you to have an inconsistent security policy based on a rough guess at your code's significance. The moment you put anything financially interesting on your server, it becomes likely that someone will try to casually hack it. Create a forum program or any sort of shopping cart, and the probability of attack rises to a dead certainty.
|
||||
|
||||
### Background ###
|
||||
|
||||
Here are a few general security guidelines for securing your web content:
|
||||
|
||||
#### Don't trust forms ####
|
||||
|
||||
Hacking forms is trivial. Yes, by using a silly JavaScript trick, you may be able to limit your form to allow only the numbers 1 through 5 in a rating field. The moment someone turns JavaScript off in their browser or posts custom form data, your client-side validation flies out the window.
|
||||
|
||||
Users interact with your scripts primarily through form parameters, and therefore they're the biggest security risk. What's the lesson? Always validate the data that gets passed to any PHP script in the PHP script. In this article, we show you how to analyze and protect against cross-site scripting (XSS) attacks, which can hijack your user's credentials (and worse). You'll also see how to prevent the MySQL injection attacks that can taint or destroy your data.
|
||||
|
||||
#### Don't trust users ####
|
||||
|
||||
Assume that every piece of data your website gathers is laden with harmful code. Sanitize every piece, even if you're positive that nobody would ever try to attack your site.
|
||||
|
||||
#### Turn off global variables ####
|
||||
|
||||
The biggest security hole you can have is having the register_globals configuration parameter enabled. Mercifully, it's turned off by default in PHP 4.2 and later. If **register_globals** is on, then you can disable this feature by turning the register_globals variable to Off in your server's php.ini file :
|
||||
|
||||
register_globals = Off
|
||||
|
||||
Novice programmers view registered globals as a convenience, but they don't realize how dangerous this setting is. A server with global variables enabled automatically assigns global variables to any form parameters. For an idea of how this works and why this is dangerous, let's look at an example.
|
||||
|
||||
Let's say that you have a script named process.php that enters form data into your user database. The original form looked like this:
|
||||
|
||||
<input name="username" type="text" size="15" maxlength="64">
|
||||
|
||||
When running process.php, PHP with registered globals enabled places the value of this parameter into the $username variable. This saves some typing over accessing them through **$_POST['username']** or **$_GET['username']**. Unfortunately, this also leaves you open to security problems, because PHP sets a variable for any value sent to the script via a GET or POST parameter, and that is a big problem if you didn't explicitly initialize the variable and you don't want someone to manipulate it.
|
||||
|
||||
Take the script below, for example—if the $authorized variable is true, it shows confidential data to the user. Under normal circumstances, the $authorized variable is set to true only if the user has been properly authenticated via the hypothetical authenticated_user() function. But if you have **register_globals** active, anyone could send a GET parameter such as authorized=1 to override this:
|
||||
|
||||
<?php
|
||||
// Define $authorized = true only if user is authenticated
|
||||
if (authenticated_user()) {
|
||||
$authorized = true;
|
||||
}
|
||||
?>
|
||||
|
||||
The moral of the story is that you should pull form data from predefined server variables. All data passed on to your web page via a posted form is automatically stored in a large array called $_POST, and all GET data is stored in a large array called **$_GET**. File upload information is stored in a special array called $_FILES. In addition, there is a combined variable called $_REQUEST.
|
||||
|
||||
To access the username field from a POST method form, use **$_POST['username']**. Use **$_GET['username']** if the username is in the URL. If you don't care where the value came from, use **$_REQUEST['username']**.
|
||||
|
||||
<?php
|
||||
$post_value = $_POST['post_value'];
|
||||
$get_value = $_GET['get_value'];
|
||||
$some_variable = $_REQUEST['some_value'];
|
||||
?>
|
||||
|
||||
$_REQUEST is a union of the $_GET, $_POST, and $_COOKIE arrays. If you have two or more values of the same parameter name, be careful of which one PHP uses. The default order is cookie, POST, then GET.
|
||||
|
||||
#### Recommended Security Configuration Options ####
|
||||
|
||||
There are several PHP configuration settings that affect security features. Here are the ones that should obviously be used for production servers:
|
||||
|
||||
- **register_globals** set to off
|
||||
- **safe_mode** set to off
|
||||
- **error_reporting** set to off. This is visible error reporting that sends a message to the user's browser if something goes wrong. For production servers, use error logging instead. Development servers can enable error logging as long as they're behind a firewall.
|
||||
- Disable these functions: system(), exec(), passthru(), shell_exec(), proc_open(), and popen().
|
||||
- **open_basedir** set for both the /tmp directory (so that session information can be stored) and the web root so that scripts cannot access files outside a selected area.
|
||||
- **expose_php** set to off. This feature adds a PHP signature that includes the version number to the Apache headers.
|
||||
- **allow_url_fopen** set to off. This isn't strictly necessary if you're careful about how you access files in your code—that is, you validate all input parameters.
|
||||
- **allow_url_include** set to off. There's really no sane reason for anyone to want to access include files via HTTP.
|
||||
|
||||
In general, if you find code that wants to use these features, you shouldn't trust it. Be especially careful of anything that wants to use a function such as system()—it's almost certainly flawed.
|
||||
|
||||
With these settings now behind us, let's look at some specific attacks and the methods that will help you protect your server.
|
||||
|
||||
### SQL Injection Attacks ###
|
||||
|
||||
Because the queries that PHP passes to MySQL databases are written in the powerful SQL programming language, you run the risk of someone attempting an SQL injection attack by using MySQL in web query parameters. By inserting malicious SQL code fragments into form parameters, an attacker attempts to break into (or disable) your server.
|
||||
|
||||
Let's say that you have a form parameter that you eventually place into a variable named $product, and you create some SQL like this:
|
||||
|
||||
$sql = "select * from pinfo where product = '$product'";
|
||||
|
||||
If that parameter came straight from the form, use database-specific escapes with PHP's native functions, like this:
|
||||
|
||||
$sql = 'Select * from pinfo where product = '"'
|
||||
mysql_real_escape_string($product) . '"';
|
||||
|
||||
If you don't, someone might just decide to throw this fragment into the form parameter:
|
||||
|
||||
39'; DROP pinfo; SELECT 'FOO
|
||||
|
||||
Then the result of $sql is:
|
||||
|
||||
select product from pinfo where product = '39'; DROP pinfo; SELECT 'FOO'
|
||||
|
||||
Because the semicolon is MySQL's statement delimiter, the database processes these three statements:
|
||||
|
||||
select * from pinfo where product = '39'
|
||||
DROP pinfo
|
||||
SELECT 'FOO'
|
||||
|
||||
Well, there goes your table.
|
||||
|
||||
Note that this particular syntax won't actually work with PHP and MySQL, because the **mysql_query()** function allows just one statement to be processed per request. However, a subquery will still work.
|
||||
|
||||
To prevent SQL injection attacks, do two things:
|
||||
|
||||
- Always validate all parameters. For example, if something needs to be a number, make sure that it's a number.
|
||||
- Always use the mysql_real_escape_string() function on data to escape any quotes or double quotes in your data.
|
||||
|
||||
**Note: To automatically escape any form data, you can turn on Magic Quotes.**
|
||||
|
||||
Some MySQL damage can be avoided by restricting your MySQL user privileges. Any MySQL account can be restricted to only do certain kinds of queries on selected tables. For example, you could create a MySQL user who can select rows but nothing else. However, this is not terribly useful for dynamic data, and, furthermore, if you have sensitive customer information, it might be possible for someone to have access to some data that you didn't intend to make available. For example, a user accessing account data could try to inject some code that accesses another account number instead of the one assigned to the current session.
|
||||
|
||||
### Preventing Basic XSS Attacks ###
|
||||
|
||||
XSS stands for cross-site scripting. Unlike most attacks, this exploit works on the client side. The most basic form of XSS is to put some JavaScript in user-submitted content to steal the data in a user's cookie. Since most sites use cookies and sessions to identify visitors, the stolen data can then be used to impersonate that user—which is deeply troublesome when it's a typical user account, and downright disastrous if it's the administrative account. If you don't use cookies or session IDs on your site, your users aren't vulnerable, but you should still be aware of how this attack works.
|
||||
|
||||
Unlike MySQL injection attacks, XSS attacks are difficult to prevent. Yahoo!, eBay, Apple, and Microsoft have all been affected by XSS. Although the attack doesn't involve PHP, you can use PHP to strip user data in order to prevent attacks. To stop an XSS attack, you have to restrict and filter the data a user submits to your site. It is for this precise reason that most online bulletin boards don't allow the use of HTML tags in posts and instead replace them with custom tag formats such as **[b]** and **[linkto]**.
|
||||
|
||||
Let's look at a simple script that illustrates how to prevent some of these attacks. For a more complete solution, use SafeHTML, discussed later in this article.
|
||||
|
||||
function transform_HTML($string, $length = null) {
|
||||
// Helps prevent XSS attacks
|
||||
// Remove dead space.
|
||||
$string = trim($string);
|
||||
// Prevent potential Unicode codec problems.
|
||||
$string = utf8_decode($string);
|
||||
// HTMLize HTML-specific characters.
|
||||
$string = htmlentities($string, ENT_NOQUOTES);
|
||||
$string = str_replace("#", "#", $string);
|
||||
$string = str_replace("%", "%", $string);
|
||||
$length = intval($length);
|
||||
if ($length > 0) {
|
||||
$string = substr($string, 0, $length);
|
||||
}
|
||||
return $string;
|
||||
}
|
||||
|
||||
This function transforms HTML-specific characters into HTML literals. A browser renders any HTML run through this script as text with no markup. For example, consider this HTML string:
|
||||
|
||||
<STRONG>Bold Text</STRONG>
|
||||
|
||||
Normally, this HTML would render as follows:
|
||||
|
||||
Bold Text
|
||||
|
||||
However, when run through **transform_HTML()**, it renders as the original input. The reason is that the tag characters are HTML entities in the processed string. The resulting string from **HTML()** in plaintext looks like this:
|
||||
|
||||
<STRONG>Bold Text</STRONG>
|
||||
|
||||
The essential piece of this function is the htmlentities() function call that transforms <, >, and & into their entity equivalents of **<**, **>**, and **&**. Although this takes care of the most common attacks, experienced XSS hackers have another sneaky trick up their sleeve: Encoding their malicious scripts in hexadecimal or UTF-8 instead of normal ASCII text, hoping to circumvent your filters. They can send the code along as a GET variable in the URL, saying, "Hey, this is hexadecimal code, but could you run it for me anyway?" A hexadecimal example looks something like this:
|
||||
|
||||
<a href="http://host/a.php?variable=%22%3e %3c%53%43%52%49%50%54%3e%44%6f%73%6f%6d%65%74%68%69%6e%67%6d%61%6c%69%63%69%6f%75%73%3c%2f%53%43%52%49%50%54%3e">
|
||||
|
||||
But when the browser renders that information, it turns out to be:
|
||||
|
||||
<a href="http://host/a.php?variable="> <SCRIPT>Dosomethingmalicious</SCRIPT>
|
||||
|
||||
To prevent this, transform_HTML() takes the additional steps of converting # and % signs into their entity, shutting down hex attacks, and converting UTF-8–encoded data.
|
||||
|
||||
Finally, just in case someone tries to overload a string with a very long input, hoping to crash something, you can add an optional $length parameter to trim the string to the maximum length you specify.
|
||||
|
||||
### Using SafeHTML ###
|
||||
|
||||
The problem with the previous script is that it is simple, and it does not allow for any kind of user markup. Unfortunately, there are hundreds of ways to try to sneak JavaScript past someone's filters, and short of stripping all HTML from someone's input, there's no way of stopping it.
|
||||
|
||||
Currently, there's no single script that's guaranteed to be unbreakable, though there are some that are better than most. There are two approaches to security, whitelisting and blacklisting, and whitelisting tends to be less complicated and more effective.
|
||||
|
||||
One whitelisting solution is the SafeHTML anti-XSS parser from PixelApes.
|
||||
|
||||
SafeHTML is smart enough to recognize valid HTML, so it can hunt and strip any dangerous tags. It does its parsing with another package called HTMLSax.
|
||||
|
||||
To install and use SafeHTML, do the following:
|
||||
|
||||
1. Go to [http://pixel-apes.com/safehtml/?page=safehtml][1] and download the latest version of SafeHTML.
|
||||
1. Put the files in the classes directory on your server. This directory contains everything that SafeHTML and HTMLSax need to function.
|
||||
1. Include the SafeHTML class file (safehtml.php) in your script.
|
||||
1. Create a new SafeHTML object called $safehtml.
|
||||
1. Sanitize your data with the $safehtml->parse() method.
|
||||
|
||||
Here's a complete example:
|
||||
|
||||
<?php
|
||||
/* If you're storing the HTMLSax3.php in the /classes directory, along
|
||||
with the safehtml.php script, define XML_HTMLSAX3 as a null string. */
|
||||
define(XML_HTMLSAX3, '');
|
||||
// Include the class file.
|
||||
require_once('classes/safehtml.php');
|
||||
// Define some sample bad code.
|
||||
$data = "This data would raise an alert <script>alert('XSS Attack')</script>";
|
||||
// Create a safehtml object.
|
||||
$safehtml = new safehtml();
|
||||
// Parse and sanitize the data.
|
||||
$safe_data = $safehtml->parse($data);
|
||||
// Display result.
|
||||
echo 'The sanitized data is <br />' . $safe_data;
|
||||
?>
|
||||
|
||||
If you want to sanitize any other data in your script, you don't have to create a new object; just use the $safehtml->parse() method throughout your script.
|
||||
|
||||
#### What Can Go Wrong? ####
|
||||
|
||||
The biggest mistake you can make is assuming that this class completely shuts down XSS attacks. SafeHTML is a fairly complex script that checks for almost everything, but nothing is guaranteed. You still want to do the parameter validation that applies to your site. For example, this class doesn't check the length of a given variable to ensure that it fits into a database field. It doesn't check for buffer overflow problems.
|
||||
|
||||
XSS hackers are creative and use a variety of approaches to try to accomplish their objectives. Just look at RSnake's XSS tutorial at [http://ha.ckers.org/xss.html][2] to see how many ways there are to try to sneak code past someone's filters. The SafeHTML project has good programmers working overtime to try to stop XSS attacks, and it has a solid approach, but there's no guarantee that someone won't come up with some weird and fresh approach that could short-circuit its filters.
|
||||
|
||||
**Note: For an example of the powerful effects of XSS attacks, check out [http://namb.la/popular/tech.html][3], which shows a step-by-step approach to creating the JavaScript XSS worm that overloaded the MySpace servers. **
|
||||
|
||||
### Protecting Data with a One-Way Hash ###
|
||||
|
||||
This script performs a one-way transformation on data—in other words, it can make a hash signature of someone's password, but you can't ever decrypt it and go back to the original password. Why would you want to do that? The application is in storing passwords. An administrator doesn't need to know users' passwords—in fact, it's a good idea that only the user knows his or her password. The system (and the system alone) should be able to identify a correct password; this has been the Unix password security model for years. One-way password security works as follows:
|
||||
|
||||
1. When a user or administrator creates or changes an account password, the system hashes the password and stores the result. The host system discards the plaintext password.
|
||||
1. When the user logs in to a system via any means, the entered password is again hashed.
|
||||
1. The host system throws away the plaintext password entered.
|
||||
1. This newly hashed password is compared against the stored hash.
|
||||
1. If the hashed passwords match, then the system grants access.
|
||||
|
||||
The host system does this without ever knowing the original password; in fact, the original value is completely irrelevant. As a side effect, should someone break into your system and steal your password database, the intruder will have a bunch of hashed passwords without any way of reversing them to find the originals. Of course, given enough time, computer power, and poorly chosen user passwords, an attacker could probably use a dictionary attack to figure out the passwords. Therefore, don't make it easy for people to get their hands on your password database, and if someone does, have everyone change their passwords.
|
||||
|
||||
#### Encryption Vs Hashing ####
|
||||
|
||||
Technically speaking, this process is not encryption. It is a hash, which is different from encryption for two reasons:
|
||||
|
||||
Unlike in encryption, data cannot be decrypted.
|
||||
|
||||
It's possible (but extremely unlikely) that two different strings will produce the same hash. There's no guarantee that a hash is unique, so don't try to use a hash as something like a unique key in a database.
|
||||
|
||||
function hash_ish($string) {
|
||||
return md5($string);
|
||||
}
|
||||
|
||||
The md5() function returns a 32-character hexadecimal string, based on the RSA Data Security Inc. Message-Digest Algorithm (also known, conveniently enough, as MD5). You can then insert that 32-character string into your database, compare it against other md5'd strings, or just adore its 32-character perfection.
|
||||
|
||||
#### Hacking the Script ####
|
||||
|
||||
It is virtually impossible to decrypt MD5 data. That is, it's very hard. However, you still need good passwords, because it's still easy to make a database of hashes for the entire dictionary. There are online MD5 dictionaries where you can enter **06d80eb0c50b49a509b49f2424e8c805** and get a result of "dog." Thus, even though MD5s can't technically be decrypted, they're still vulnerable—and if someone gets your password database, you can be sure that they'll be consulting an MD5 dictionary. Thus, it's in your best interests when creating password-based systems that the passwords are long (a minimum of six characters and preferably eight) and contain both letters and numbers. And make sure that the password isn't in the dictionary.
|
||||
|
||||
### Encrypting Data with Mcrypt ###
|
||||
|
||||
MD5 hashes work just fine if you never need to see your data in readable form. Unfortunately, that's not always an option—if you offer to store someone's credit card information in encrypted format, you need to decrypt it at some later point.
|
||||
|
||||
One of the easiest solutions is the Mcrypt module, an add-in for PHP that allows high-grade encryption. The Mcrypt library offers more than 30 ciphers to use in encryption and the possibility of a passphrase that ensures that only you (or, optionally, your users) can decrypt data.
|
||||
|
||||
Let's see some hands-on use. The following script contains functions that use Mcrypt to encrypt and decrypt data:
|
||||
|
||||
<?php
|
||||
$data = "Stuff you want encrypted";
|
||||
$key = "Secret passphrase used to encrypt your data";
|
||||
$cipher = "MCRYPT_SERPENT_256";
|
||||
$mode = "MCRYPT_MODE_CBC";
|
||||
function encrypt($data, $key, $cipher, $mode) {
|
||||
// Encrypt data
|
||||
return (string)
|
||||
base64_encode
|
||||
(
|
||||
mcrypt_encrypt
|
||||
(
|
||||
$cipher,
|
||||
substr(md5($key),0,mcrypt_get_key_size($cipher, $mode)),
|
||||
$data,
|
||||
$mode,
|
||||
substr(md5($key),0,mcrypt_get_block_size($cipher, $mode))
|
||||
)
|
||||
);
|
||||
}
|
||||
function decrypt($data, $key, $cipher, $mode) {
|
||||
// Decrypt data
|
||||
return (string)
|
||||
mcrypt_decrypt
|
||||
(
|
||||
$cipher,
|
||||
substr(md5($key),0,mcrypt_get_key_size($cipher, $mode)),
|
||||
base64_decode($data),
|
||||
$mode,
|
||||
substr(md5($key),0,mcrypt_get_block_size($cipher, $mode))
|
||||
);
|
||||
}
|
||||
?>
|
||||
|
||||
The **mcrypt()** function requires several pieces of information:
|
||||
|
||||
- The data to encrypted.
|
||||
- The passphrase used to encrypt and unlock your data, also known as the key.
|
||||
- The cipher used to encrypt the data, which is the specific algorithm used to encrypt the data. This script uses **MCRYPT_SERPENT_256**, but you can choose from an array of fancy-sounding ciphers, including **MCRYPT_TWOFISH192**, **MCRYPT_RC2**, **MCRYPT_DES**, and **MCRYPT_LOKI97**.
|
||||
- The mode used to encrypt the data. There are several modes you can use, including Electronic Codebook and Cipher Feedback. This script uses **MCRYPT_MODE_CBC**, Cipher Block Chaining.
|
||||
- An **initialization vector**—also known as an IV, or a seed—an additional bit of binary data used to seed the encryption algorithm. That is, it's something extra thrown in to make the algorithm harder to crack.
|
||||
- The length of the string needed for the key and IV, which vary by cipher and block. Use the **mcrypt_get_key_size()** and **mcrypt_get_block_size()** functions to find the appropriate length; then trim the key value to the appropriate length with a handy **substr()** function. (If the key is shorter than the required value, don't worry—Mcrypt pads it with zeros.)
|
||||
|
||||
If someone steals both your data and your passphrase, they can just cycle through the ciphers until finding the one that works. Thus, we apply the additional security of using the **md5()** function on the key before we use it, so even having both data and passphrase won't get the intruder what she wants.
|
||||
|
||||
An intruder would need the function, the data, and the passphrase all at once—and if that is the case, they probably have complete access to your server, and you're hosed anyway.
|
||||
|
||||
There's a small data storage format problem here. Mcrypt returns its encrypted data in an ugly binary format that causes horrific errors when you try to store it in certain MySQL fields. Therefore, we use the **base64encode()** and **base64decode()** functions to transform the data into a SQL-compatible alphabetical format and retrieve rows.
|
||||
|
||||
#### Hacking the Script ####
|
||||
|
||||
In addition to experimenting with various encryption methods, you can add some convenience to this script. For example, rather than providing the key and mode every time, you could declare them as global constants in an included file.
|
||||
|
||||
### Generating Random Passwords ###
|
||||
|
||||
Random (but difficult-to-guess) strings are important in user security. For example, if someone loses a password and you're using MD5 hashes, you won't be able to, nor should you want to, look it up. Instead, you should generate a secure random password and send that to the user. Another application for random number generation is creating activation links in order to access your site's services. Here is a function that creates a password:
|
||||
|
||||
<?php
|
||||
function make_password($num_chars) {
|
||||
if ((is_numeric($num_chars)) &&
|
||||
($num_chars > 0) &&
|
||||
(! is_null($num_chars))) {
|
||||
$password = '';
|
||||
$accepted_chars = 'abcdefghijklmnopqrstuvwxyz1234567890';
|
||||
// Seed the generator if necessary.
|
||||
srand(((int)((double)microtime()*1000003)) );
|
||||
for ($i=0; $i<=$num_chars; $i++) {
|
||||
$random_number = rand(0, (strlen($accepted_chars) -1));
|
||||
$password .= $accepted_chars[$random_number] ;
|
||||
}
|
||||
return $password;
|
||||
}
|
||||
}
|
||||
?>
|
||||
|
||||
#### Using the Script ####
|
||||
|
||||
The **make_password()** function returns a string, so all you need to do is supply the length of the string as an argument:
|
||||
|
||||
<?php
|
||||
$fifteen_character_password = make_password(15);
|
||||
?>
|
||||
|
||||
The function works as follows:
|
||||
|
||||
- The function makes sure that **$num_chars** is a positive nonzero integer.
|
||||
- The function initializes the **$password** variable to an empty string.
|
||||
- The function initializes the **$accepted_chars** variable to the list of characters the password may contain. This script uses all lowercase letters and the numbers 0 through 9, but you can choose any set of characters you like.
|
||||
- The random number generator needs a seed, so it gets a bunch of random-like values. (This isn't strictly necessary on PHP 4.2 and later.)
|
||||
- The function loops **$num_chars** times, one iteration for each character in the password to generate.
|
||||
- For each new character, the script looks at the length of **$accepted_chars**, chooses a number between 0 and the length, and adds the character at that index in **$accepted_chars** to $password.
|
||||
- After the loop completes, the function returns **$password**.
|
||||
|
||||
### License ###
|
||||
|
||||
This article, along with any associated source code and files, is licensed under [The Code Project Open License (CPOL)][4]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.codeproject.com/Articles/363897/PHP-Security
|
||||
|
||||
作者:[SamarRizvi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.codeproject.com/script/Membership/View.aspx?mid=7483622
|
||||
[1]:http://pixel-apes.com/safehtml/?page=safehtml
|
||||
[2]:http://ha.ckers.org/xss.html
|
||||
[3]:http://namb.la/popular/tech.html
|
||||
[4]:http://www.codeproject.com/info/cpol10.aspx
|
||||
@ -0,0 +1,67 @@
|
||||
Install Google Hangouts Desktop Client In Linux
|
||||
================================================================================
|
||||

|
||||
|
||||
Earlier, we have seen how to [install Facebook Messenger in Linux][1] and [WhatsApp desktop client in Linux][2]. Both of these were unofficial apps. I have one more unofficial app for today and it is [Google Hangouts][3].
|
||||
|
||||
Of course, you can use Google Hangouts in the web browser but it is more fun to use the desktop client than the web browser one. Curious? Let’s see how to **install Google Hangouts desktop client in Linux** and how to use it.
|
||||
|
||||
### Install Google Hangouts in Linux ###
|
||||
|
||||
We are going to use an open source project called [yakyak][4] which is unofficial Google Hangouts client for Linux, Windows and OS X. I’ll show you how to use yakyak in Ubuntu but I believe that you can use the same method to use it in other Linux distributions. Before we see how to use it, let’s first take a look at main features of yakyak:
|
||||
|
||||
- Send and receive chat messages
|
||||
- Create and change conversations (rename, add people)
|
||||
- Leave and/or delete conversation
|
||||
- Desktop notifications
|
||||
- Toggle notifications on/off
|
||||
- Drag-drop, copy-paste or attach-button for image upload.
|
||||
- Hangupsbot sync room aware (actual user pics)
|
||||
- Shows inline images
|
||||
- History scrollback
|
||||
|
||||
Sounds good enough? Download the installation files from the link below:
|
||||
|
||||
- [Download Google Hangout client yakyak][5]
|
||||
|
||||
The downloaded file would be compressed. Extract it and you will see a directory like linux-x64 or linux-x32 based on your system. Go in to this directory and you should see a file named yakyak. Double click on it to run it.
|
||||
|
||||

|
||||
|
||||
You’ll have to enter your Google Account credentials of course.
|
||||
|
||||

|
||||
|
||||
Once you are through, you’ll see a screen like the one below where you can chat with your Google contacts.
|
||||
|
||||

|
||||
|
||||
If you want to show profile pictures of the contacts, you can select View->Show conversation thumbnails.
|
||||
|
||||

|
||||
|
||||
You’ll also get desktop notification for new messages.
|
||||
|
||||

|
||||
|
||||
### Worth a try? ###
|
||||
|
||||
I let you give it a try and decide whether or not it is worth to **install Google Hangouts client in Linux**. If you want official apps, take a look at these [instant messaging applications with native Linux clients][6]. Don’t forget to share your experience with Google Hangouts in Linux.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/install-google-hangouts-linux/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/abhishek/
|
||||
[1]:http://itsfoss.com/facebook-messenger-linux/
|
||||
[2]:http://itsfoss.com/whatsapp-linux-desktop/
|
||||
[3]:http://www.google.com/+/learnmore/hangouts/
|
||||
[4]:https://github.com/yakyak/yakyak
|
||||
[5]:https://github.com/yakyak/yakyak
|
||||
[6]:http://itsfoss.com/best-messaging-apps-linux/
|
||||
@ -0,0 +1,36 @@
|
||||
Linux FAQs with Answers--How to fix “tar: Exiting with failure status due to previous errors”
|
||||
================================================================================
|
||||
> **Question**: When I try to create an archive using tar command, it fails in the middle, and throws an error saying: "tar: Exiting with failure status due to previous errors." What causes this error, and how can I solve this error?
|
||||
|
||||

|
||||
|
||||
If you encounter the following error while running tar command, the most likely reason is that you do not have read permission on one of the files you are trying to archive with tar.
|
||||
|
||||
tar: Exiting with failure status due to previous errors
|
||||
|
||||
Then how can we pin down the file(s) causing the errors, or identify any other cause?
|
||||
|
||||
The tar command should actually print out what those "previous errors" are, but you can easily miss printed error messages if you run tar in verbose mode (e.g., -cvf). To catch error messages more easily, you can filter out tar's stdout messages as follows.
|
||||
|
||||
$ tar cvzfz backup.tgz my_program/ > /dev/null
|
||||
|
||||
You will then see only error messages sent by tar to stderr.
|
||||
|
||||
tar: my_program/src/lib/.conf.db.~lock~: Cannot open: Permission denied
|
||||
tar: Exiting with failure status due to previous errors
|
||||
|
||||
As you can see in the above example, the cause for the errors is indeed "denied read permission."
|
||||
|
||||
To solve the problem, simply adjust the permission of the problematic file (or remove it), and re-run tar.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/tar-exiting-with-failure-status-due-to-previous-errors.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
@ -0,0 +1,109 @@
|
||||
Linux FAQs with Answers--How to install a Brother printer on Linux
|
||||
================================================================================
|
||||
> **Question**: I have a Brother HL-2270DW laser printer, and want to print documents from my Linux box using this printer. How can I install an appropriate Brother printer driver on my Linux computer, and use it?
|
||||
|
||||
Brother is well known for its affordable [compact laser printer lineup][1]. You can get a high-quality WiFi/duplex-capable laser printer for less than 200USD, and the price keeps going down. On top of that, they provide reasonably good Linux support, so you can download and install their printer driver on your Linux computer. I bought [HL-2270DW][2] model more than a year ago, and I have been more than happy with its performance and reliability.
|
||||
|
||||
Here is how to install and configure a Brother printer driver on Linux. In this tutorial, I am demonstrating the installation of a USB driver for Brother HL-2270DW laser printer. So first connect your printer to a Linux computer via USB cable.
|
||||
|
||||
### Preparation ###
|
||||
|
||||
In this preparation step, go to the official [Brother support website][3], and search for the driver of your Brother printer by typing printer model name (e.g., HL-2270DW).
|
||||
|
||||
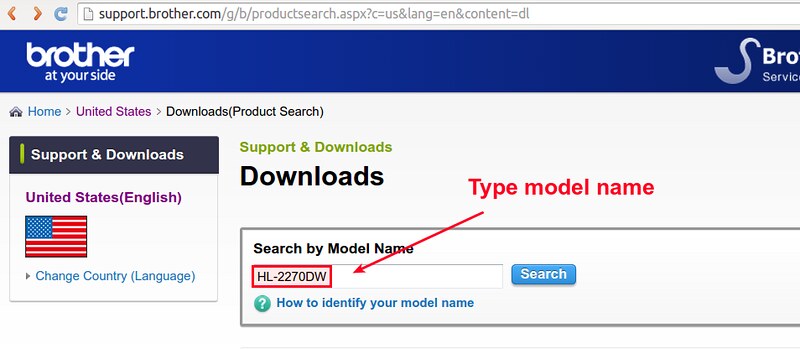
|
||||
|
||||
Once you go to the download page for your Brother printer, choose your Linux platform. For Debian, Ubuntu or their derivatives, choose "Linux (deb)". For Fedora, CentOS or RHEL, choose "Linux (rpm)".
|
||||
|
||||
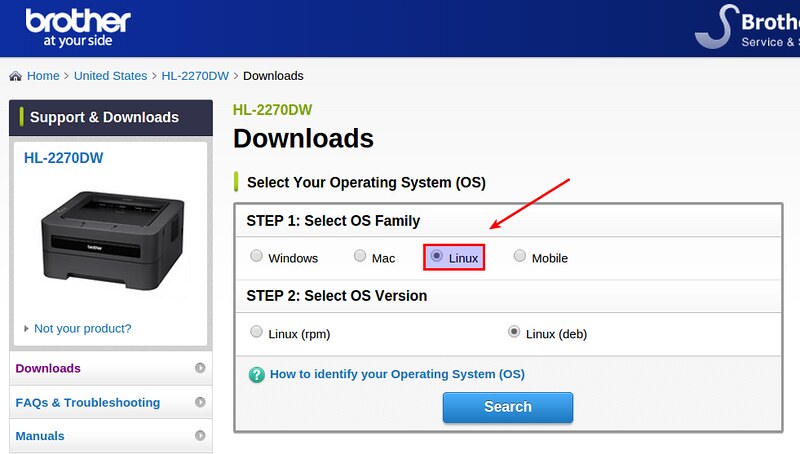
|
||||
|
||||
On the next page, you will find a LPR driver as well as CUPS wrapper driver for your printer. The former is a command-line driver, while the latter allows you to configure and manage your printer via web-based administration interface. Especially the CUPS-based GUI is quite useful for (local or remote) printer maintenance. It is recommended that you install both drivers. So click on "Driver Install Tool" and download the installer file.
|
||||
|
||||
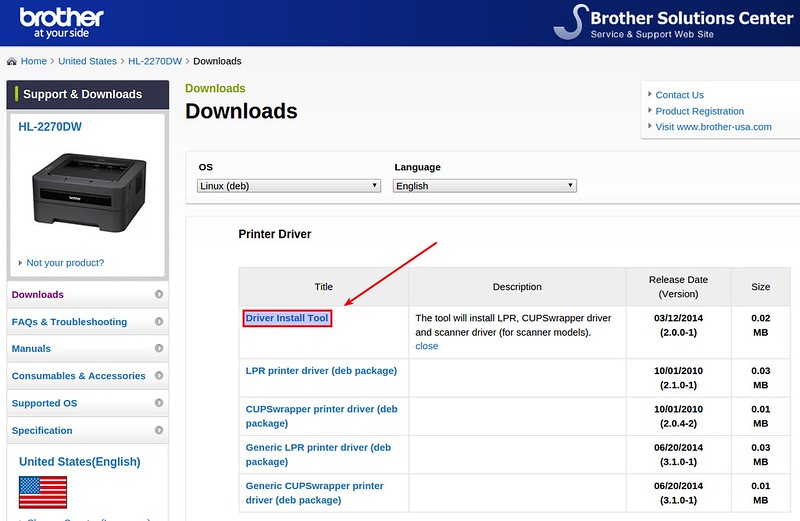
|
||||
|
||||
Before proceeding to run the installer file, you need to do one additional step if you are using a 64-bit Linux system.
|
||||
|
||||
Since Brother printer drivers are developed for 32-bit Linux, you need to install necessary 32-bit libraries on 64-bit Linux as follows.
|
||||
|
||||
On older Debian (6.0 or earlier) or Ubuntu (11.04 or earlier), install the following package.
|
||||
|
||||
$ sudo apt-get install ia32-libs
|
||||
|
||||
On newer Debian or Ubuntu which has introduced multiarch, you can install the following package instead:
|
||||
|
||||
$ sudo apt-get install lib32z1 lib32ncurses5
|
||||
|
||||
which replaces ia32-libs package. Or, you can install just:
|
||||
|
||||
$ sudo apt-get install lib32stdc++6
|
||||
|
||||
If you are using a Red Hat based Linux, you can install:
|
||||
|
||||
$ sudo yum install glibc.i686
|
||||
|
||||
### Driver Installation ###
|
||||
|
||||
Now go ahead and extract a downloaded driver installer file.
|
||||
|
||||
$ gunzip linux-brprinter-installer-2.0.0-1.gz
|
||||
|
||||
Next, run the driver installer file as follows.
|
||||
|
||||
$ sudo sh ./linux-brprinter-installer-2.0.0-1
|
||||
|
||||
You will be prompted to type a printer model name. Type the model name of your printer, for example "HL-2270DW".
|
||||
|
||||

|
||||
|
||||
After agreeing to GPL license agreement, accept default answers to any subsequent questions.
|
||||
|
||||

|
||||
|
||||
Now LPR/CUPS printer drivers are installed. Proceed to configure your printer next.
|
||||
|
||||
### Printer Configuration ###
|
||||
|
||||
We are going to configure and manage a Brother via CUPS-based web management interface.
|
||||
|
||||
First, verify that CUPS daemon is running successfully.
|
||||
|
||||
$ sudo netstat -nap | grep 631
|
||||
|
||||
Open a web browser window, and go to http://localhost:631. You will see the following CUPS printer management interface.
|
||||
|
||||

|
||||
|
||||
Go to "Administration" tab, and click on "Manage Printers" under Printers section.
|
||||
|
||||
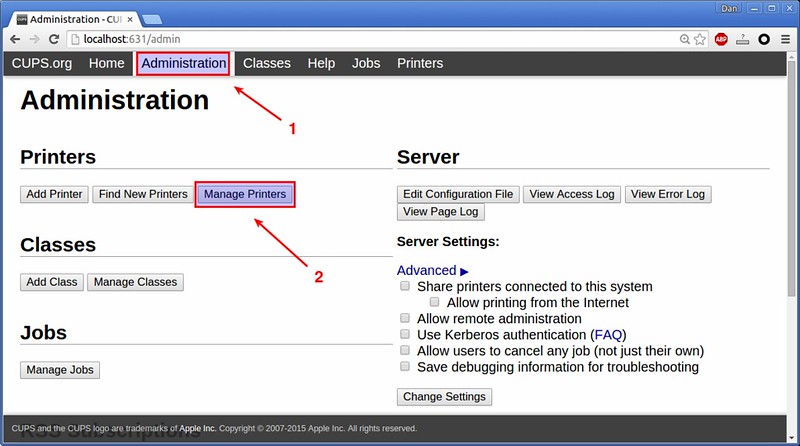
|
||||
|
||||
You must see your printer (HL-2270DW) listed in the next page. Click on the printer name.
|
||||

|
||||
|
||||
In the dropdown menu titled "Administration", choose "Set As Server Default" option. This will make your printer system-wide default.
|
||||
|
||||

|
||||
|
||||
When asked to authenticate yourself, type in your Linux login information.
|
||||
|
||||
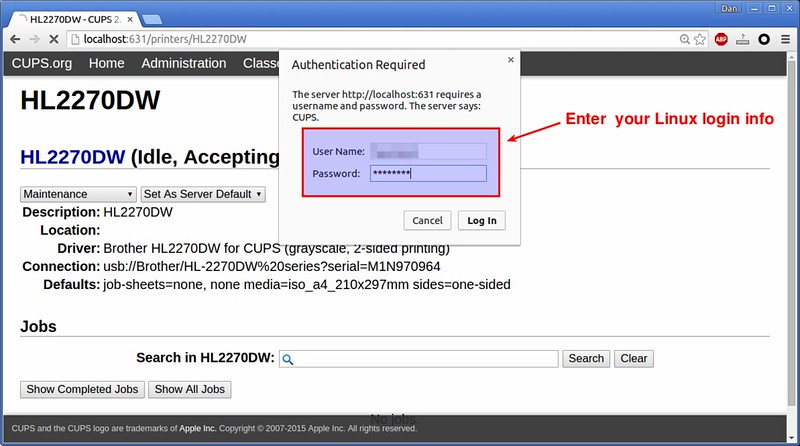
|
||||
|
||||
Now the basic configuration step is mostly done. To test print, open any document viewer application (e.g., PDF viwer), and print it. You will see "HL-2270DW" listed and chosen by default in printer setting.
|
||||
|
||||
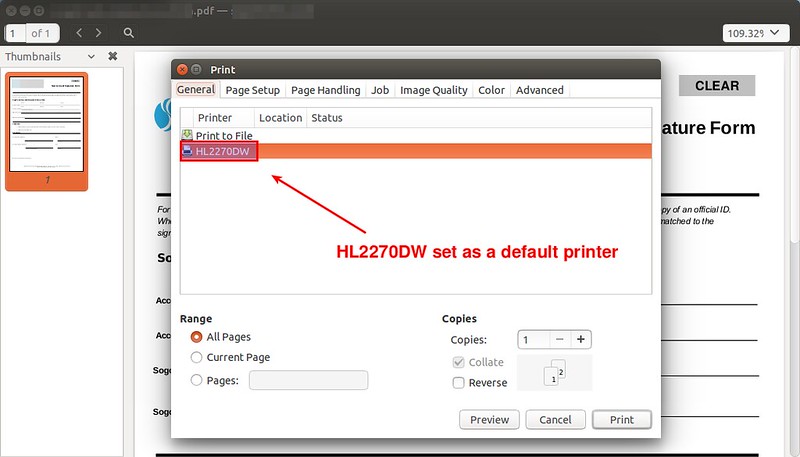
|
||||
|
||||
Print should work now. You can see the printer status and manage printer jobs via the same CUPS web interface.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/install-brother-printer-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/go/brother_printers
|
||||
[2]:http://xmodulo.com/go/hl_2270dw
|
||||
[3]:http://support.brother.com/
|
||||
@ -0,0 +1,38 @@
|
||||
Linux FAQs with Answers--How to open multiple tabs in a GNOME terminal on Ubuntu 15.04
|
||||
================================================================================
|
||||
> **Question**: I used to be able to open multiple tabs inside gnome-terminal on my Ubuntu desktop. On Ubuntu 15.04, however, I can no longer open a new tab in my terminal window. How can I open tabs in gnome-terminal on Ubuntu 15.04?
|
||||
|
||||
On Ubuntu 14.10 or earlier, gnome-terminal allowed you to open either a new terminal or a tab inside a terminal window. However, starting with Ubuntu 15.04, gnome-terminal has removed "New Tab" menu option. This is actually not a bug, but a feature that attempts to unify new tab and new window. GNOME 3.12 has introduced a [single "Open Terminal" option][1]. The ability to open a new terminal tab has been migrated from the terminal menu to Preferences.
|
||||
|
||||
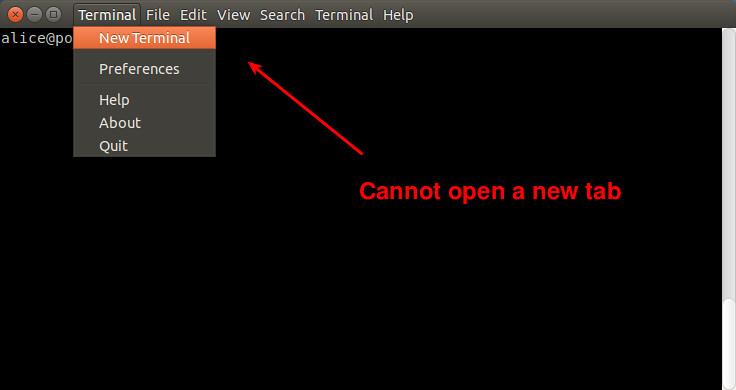
|
||||
|
||||
### Open Tabs via Preferences ###
|
||||
|
||||
To be able to open a new tab in new gnome-terminal of Ubuntu 15.04, go to "Edit" -> "Preferences", and change "Open new terminals in: Window" to "Open new terminals in: Tab".
|
||||
|
||||
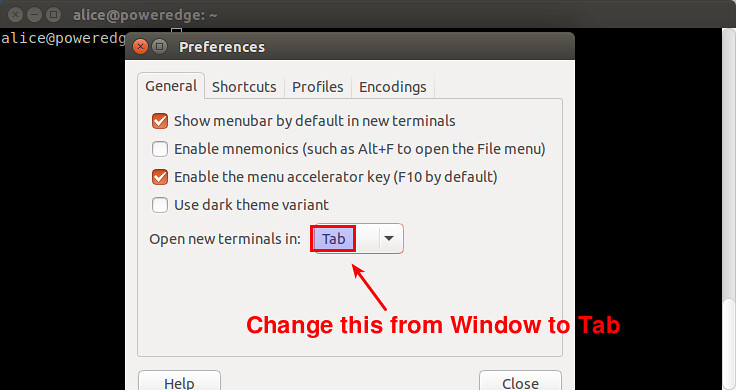
|
||||
|
||||
Now if you open a new terminal via menu, it will automatically open a new tab inside the terminal.
|
||||
|
||||

|
||||
|
||||
### Open Tabs via a Keyboard Shortcut ###
|
||||
|
||||
If you do not want to change Preferences, you can hold down <Ctrl> to "invert" Preferences setting temporarily. For example, under the default Preferences, if you hold down <Ctrl> and click on "New Terminal", it will open a new tab, not a terminal.
|
||||
|
||||
Alternatively, you can simply use a keyboard shortcut <Shift+Ctrl+T> to open a new tab in a terminal.
|
||||
|
||||
In my view, this UI change in gnome-terminal is not quite an improvement. For example, you are no longer able to customize the name of individual terminal tabs. This feature is useful when you have many tabs open in a terminal. With the default tab name fixed to the current prompt (whose length can grow quickly), you easily cannot see the whole prompt string in the limited tab name space. Hope this feature will become available soon.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/open-multiple-tabs-gnome-terminal-ubuntu.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ask.xmodulo.com/author/nanni
|
||||
[1]:http://worldofgnome.org/opening-a-new-terminal-tabwindow-in-gnome-3-12/
|
||||
@ -0,0 +1,115 @@
|
||||
wyangsun 翻译中
|
||||
Why is the ibdata1 file continuously growing in MySQL?
|
||||
================================================================================
|
||||

|
||||
|
||||
We receive this question about the ibdata1 file in MySQL very often in [Percona Support][1].
|
||||
|
||||
The panic starts when the monitoring server sends an alert about the storage of the MySQL server – saying that the disk is about to get filled.
|
||||
|
||||
After some research you realize that most of the disk space is used by the InnoDB’s shared tablespace ibdata1. You have [innodb_file_per_table][2] enabled, so the question is:
|
||||
|
||||
### What is stored in ibdata1? ###
|
||||
|
||||
When you have innodb_file_per_table enabled, the tables are stored in their own tablespace but the shared tablespace is still used to store other InnoDB’s internal data:
|
||||
|
||||
- data dictionary aka metadata of InnoDB tables
|
||||
- change buffer
|
||||
- doublewrite buffer
|
||||
- undo logs
|
||||
|
||||
Some of them can be configured on [Percona Server][3] to avoid becoming too large. For example you can set a maximum size for change buffer with [innodb_ibuf_max_size][4] or store the doublewrite buffer on a separate file with [innodb_doublewrite_file][5].
|
||||
|
||||
In MySQL 5.6 you can also create external UNDO tablespaces so they will be in their own files instead of stored inside ibdata1. Check following [documentation link][6].
|
||||
|
||||
### What is causing the ibdata1 to grow that fast? ###
|
||||
|
||||
Usually the first command that we need to run when there is a MySQL problem is:
|
||||
|
||||
SHOW ENGINE INNODB STATUSG
|
||||
|
||||
That will show us very valuable information. We start checking the **TRANSACTIONS** section and we find this:
|
||||
|
||||
---TRANSACTION 36E, ACTIVE 1256288 sec
|
||||
MySQL thread id 42, OS thread handle 0x7f8baaccc700, query id 7900290 localhost root
|
||||
show engine innodb status
|
||||
Trx read view will not see trx with id >= 36F, sees < 36F
|
||||
|
||||
This is the most common reason, a pretty old transaction created 14 days ago. The status is **ACTIVE**, that means InnoDB has created a snapshot of the data so it needs to maintain old pages in **undo** to be able to provide a consistent view of the database since that transaction was started. If your database is heavily write loaded that means lots of undo pages are being stored.
|
||||
|
||||
If you don’t find any long-running transaction you can also monitor another variable from the INNODB STATUS, the “**History list length.**” It shows the number of pending purge operations. In this case the problem is usually caused because the purge thread (or master thread in older versions) is not capable to process undo records with the same speed as they come in.
|
||||
|
||||
### How can I check what is being stored in the ibdata1? ###
|
||||
|
||||
Unfortunately MySQL doesn’t provide information of what is being stored on that ibdata1 shared tablespace but there are two tools that will be very helpful. First a modified version of innochecksum made by Mark Callaghan and published in [this bug report][7].
|
||||
|
||||
It is pretty easy to use:
|
||||
|
||||
# ./innochecksum /var/lib/mysql/ibdata1
|
||||
0 bad checksum
|
||||
13 FIL_PAGE_INDEX
|
||||
19272 FIL_PAGE_UNDO_LOG
|
||||
230 FIL_PAGE_INODE
|
||||
1 FIL_PAGE_IBUF_FREE_LIST
|
||||
892 FIL_PAGE_TYPE_ALLOCATED
|
||||
2 FIL_PAGE_IBUF_BITMAP
|
||||
195 FIL_PAGE_TYPE_SYS
|
||||
1 FIL_PAGE_TYPE_TRX_SYS
|
||||
1 FIL_PAGE_TYPE_FSP_HDR
|
||||
1 FIL_PAGE_TYPE_XDES
|
||||
0 FIL_PAGE_TYPE_BLOB
|
||||
0 FIL_PAGE_TYPE_ZBLOB
|
||||
0 other
|
||||
3 max index_id
|
||||
|
||||
It has 19272 UNDO_LOG pages from a total of 20608. **That’s the 93% of the tablespace**.
|
||||
|
||||
The second way to check the content of a tablespace are the [InnoDB Ruby Tools][8] made by Jeremy Cole. It is a more advanced tool to examine the internals of InnoDB. For example we can use the space-summary parameter to get a list with every page and its data type. We can use standard Unix tools to get the number of **UNDO_LOG** pages:
|
||||
|
||||
# innodb_space -f /var/lib/mysql/ibdata1 space-summary | grep UNDO_LOG | wc -l
|
||||
19272
|
||||
|
||||
Altough in this particular case innochecksum is faster and easier to use I recommend you to play with Jeremy’s tools to learn more about the data distribution inside InnoDB and its internals.
|
||||
|
||||
OK, now we know where the problem is. The next question:
|
||||
|
||||
### How can I solve the problem? ###
|
||||
|
||||
The answer to this question is easy. If you can still commit that query, do it. If not you’ll have to kill the thread to start the rollback process. That will just stop ibdata1 from growing but it is clear that your software has a bug or someone made a mistake. Now that you know how to identify where is the problem you need to find who or what is causing it using your own debugging tools or the general query log.
|
||||
|
||||
If the problem is caused by the purge thread then the solution is usually to upgrade to a newer version where you can use a dedicated purge thread instead of the master thread. More information on the following [documentation link][9].
|
||||
|
||||
### Is there any way to recover the used space? ###
|
||||
|
||||
No, it is not possible at least in an easy and fast way. InnoDB tablespaces never shrink… see the following [10-year old bug report][10] recently updated by James Day (thanks):
|
||||
|
||||
When you delete some rows, the pages are marked as deleted to reuse later but the space is never recovered. The only way is to start the database with fresh ibdata1. To do that you would need to take a full logical backup with mysqldump. Then stop MySQL and remove all the databases, ib_logfile* and ibdata* files. When you start MySQL again it will create a new fresh shared tablespace. Then, recover the logical dump.
|
||||
|
||||
### Summary ###
|
||||
|
||||
When the ibdata1 file is growing too fast within MySQL it is usually caused by a long running transaction that we have forgotten about. Try to solve the problem as fast as possible (commiting or killing a transaction) because you won’t be able to recover the wasted disk space without the painfully slow mysqldump process.
|
||||
|
||||
Monitoring the database to avoid these kind of problems is also very recommended. Our [MySQL Monitoring Plugins][11] includes a Nagios script that can alert you if it finds a too old running transaction.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.percona.com/blog/2013/08/20/why-is-the-ibdata1-file-continuously-growing-in-mysql/
|
||||
|
||||
作者:[Miguel Angel Nieto][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.percona.com/blog/author/miguelangelnieto/
|
||||
[1]:https://www.percona.com/products/mysql-support
|
||||
[2]:http://dev.mysql.com/doc/refman/5.5/en/innodb-parameters.html#sysvar_innodb_file_per_table
|
||||
[3]:https://www.percona.com/software/percona-server
|
||||
[4]:https://www.percona.com/doc/percona-server/5.5/scalability/innodb_insert_buffer.html#innodb_ibuf_max_size
|
||||
[5]:https://www.percona.com/doc/percona-server/5.5/performance/innodb_doublewrite_path.html?id=percona-server:features:percona_innodb_doublewrite_path#innodb_doublewrite_file
|
||||
[6]:http://dev.mysql.com/doc/refman/5.6/en/innodb-performance.html#innodb-undo-tablespace
|
||||
[7]:http://bugs.mysql.com/bug.php?id=57611
|
||||
[8]:https://github.com/jeremycole/innodb_ruby
|
||||
[9]:http://dev.mysql.com/doc/innodb/1.1/en/innodb-improved-purge-scheduling.html
|
||||
[10]:http://bugs.mysql.com/bug.php?id=1341
|
||||
[11]:https://www.percona.com/software/percona-monitoring-plugins
|
||||
@ -1,3 +1,4 @@
|
||||
[translating by KevinSJ]
|
||||
Linux_Logo – A Command Line Tool to Print Color ANSI Logos of Linux Distributions
|
||||
================================================================================
|
||||
linuxlogo or linux_logo is a Linux command line utility that generates a color ANSI picture of Distribution logo with a few system information.
|
||||
@ -180,4 +181,4 @@ via: http://www.tecmint.com/linux_logo-tool-to-print-color-ansi-logos-of-linux/
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:http://www.tecmint.com/screenfetch-system-information-generator-for-linux/
|
||||
[1]:http://www.tecmint.com/screenfetch-system-information-generator-for-linux/
|
||||
@ -0,0 +1,152 @@
|
||||
用这些专用工具让你截图更简单
|
||||
================================================================================
|
||||
"一图胜过千万句",这句二十世纪早期在美国应运而生的名言,说的是一张单一的静止图片所蕴含的信息足以匹敌大量的描述性文字。本质上说,图片所传递的信息量的确是比文字更有效更高效。
|
||||
|
||||
截图(或抓帧)是一种捕捉自计算机所录制可视化设备输出的快照或图片,屏幕捕捉软件能让计算机获取到截图。此类软件有很多用处,因为一张图片能很好地说明计算机软件的操作,截图在软件开发过程和文档中扮演了一个很重要的角色。或者,如果你的电脑有了个技术性问题,一张截图能让技术支持理解你碰到的这个问题。要写好计算机相关的文章、文档和教程,没有一款好的截图工具是几乎不可能的。如果你想在保存屏幕上任意一些零星的信息,特别是不方便打字时,截图也很有用。
|
||||
|
||||
在开源世界,Linux有许多专注于截图功能的工具供选择,基于图形的和控制台的都有。如果要说一个功能丰富的专用截图工具,那就来看看Shutter吧。这款工具是小型开源工具的杰出代表,当然也有其它的选择。
|
||||
|
||||
屏幕捕捉功能不仅仅只有专业的工具提供,GIMP和ImageMagick这两款主攻图像处理的工具,也能提供像样的屏幕捕捉功能。
|
||||
|
||||
----------
|
||||
|
||||
### Shutter ###
|
||||
|
||||

|
||||
|
||||
Shutter是一款功能丰富的截图软件。你可以给你的特殊区域、窗口、整个屏幕甚至是网站截图 - 在其中应用不用的效果,比如用高亮的点在上面绘图,然后上传至一个图片托管网站,一切尽在这个小窗口内。
|
||||
|
||||
包含特性:
|
||||
|
||||
|
||||
- 截图范围:
|
||||
- 一块特殊区域
|
||||
- 窗口
|
||||
- 完整的桌面
|
||||
- 脚本生成的网页
|
||||
- 在截图中应用不同效果
|
||||
- 热键
|
||||
- 打印
|
||||
- 直接截图或指定一个延迟时间
|
||||
- 将截图保存至一个指定目录并用一个简便方法重命名它(用特殊的通配符)
|
||||
- 完成集成在GNOME桌面中(TrayIcon等等)
|
||||
- 当你截了一张图并以%设置了尺寸时,直接生成缩略图
|
||||
- Shutter会话选项:
|
||||
- 会话中保持所有截图的痕迹
|
||||
- 复制截图至剪贴板
|
||||
- 打印截图
|
||||
- 删除截图
|
||||
- 重命名文件
|
||||
- 直接上传你的文件至图像托管网站(比如http://ubuntu-pics.de),取回所有需要的图像并将它们与其他人分享
|
||||
- 用内置的绘画工具直接编辑截图
|
||||
|
||||
- 主页: [shutter-project.org][1]
|
||||
- 开发者: Mario Kemper和Shutter团队
|
||||
- 许可证: GNU GPL v3
|
||||
- 版本号: 0.93.1
|
||||
|
||||
----------
|
||||
|
||||
### HotShots ###
|
||||
|
||||

|
||||
|
||||
HotShots是一款捕捉屏幕并能以各种图片格式保存的软件,同时也能添加注释和图形数据(箭头、行、文本, ...)。
|
||||
|
||||
你也可以把你的作品上传到网上(FTP/一些web服务),HotShots是用Qt开发而成的。
|
||||
|
||||
HotShots无法从Ubuntu的Software Center中获取,不过用以下命令可以轻松地来安装它:
|
||||
|
||||
sudo add-apt-repository ppa:ubuntuhandbook1/apps
|
||||
|
||||
sudo apt-get update
|
||||
|
||||
sudo apt-get install hotshots
|
||||
|
||||
包含特性:
|
||||
|
||||
- 简单易用
|
||||
- 全功能使用
|
||||
- 嵌入式编辑器
|
||||
- 热键
|
||||
- 内置放大功能
|
||||
- 徒手和多屏捕捉
|
||||
- 支持输出格式:Black & Whte (bw), Encapsulated PostScript (eps, epsf), Encapsulated PostScript Interchange (epsi), OpenEXR (exr), PC Paintbrush Exchange (pcx), Photoshop Document (psd), ras, rgb, rgba, Irix RGB (sgi), Truevision Targa (tga), eXperimental Computing Facility (xcf), Windows Bitmap (bmp), DirectDraw Surface (dds), Graphic Interchange Format (gif), Icon Image (ico), Joint Photographic Experts Group 2000 (jp2), Joint Photographic Experts Group (jpeg, jpg), Multiple-image Network Graphics (mng), Portable Pixmap (ppm), Scalable Vector Graphics (svg), svgz, Tagged Image File Format (tif, tiff), webp, X11 Bitmap (xbm), X11 Pixmap (xpm), and Khoros Visualization (xv)
|
||||
- 国际化支持:巴斯克语、中文、捷克语、法语、加利西亚语、德语、希腊语、意大利语、日语、立陶宛语、波兰语、葡萄牙语、罗马尼亚语、俄罗斯语、塞尔维亚语、僧伽罗语、斯洛伐克语、西班牙语、土耳其语、乌克兰语和越南语
|
||||
|
||||
- 主页: [thehive.xbee.net][2]
|
||||
- 开发者 xbee
|
||||
- 许可证: GNU GPL v2
|
||||
- 版本号: 2.2.0
|
||||
|
||||
----------
|
||||
|
||||
### ScreenCloud ###
|
||||
|
||||

|
||||
|
||||
ScreenCloud是一款易于使用的开源截图工具。
|
||||
|
||||
在这款软件中,用户可以用三个热键中的其中一个或只需点击ScreenCloud托盘图标就能进行截图,用户也可以自行选择保存截图的地址。
|
||||
|
||||
如果你选择上传你的截图到screencloud主页,链接会自动复制到你的剪贴板上,你能通过email或在一个聊天对话框里和你的朋友同事分享它,他们肯定会点击这个链接来看你的截图的。
|
||||
|
||||
包含特性:
|
||||
|
||||
- 捕捉整个屏幕,窗口和截选区域
|
||||
- 快速又简单:截取图片,粘贴链接,完成
|
||||
- 免费托管你的截图
|
||||
- 热键
|
||||
- 设置定时器延迟
|
||||
- 允许 '捕捉窗口边框'
|
||||
- 启用/禁用通知
|
||||
- 设置开机自启动
|
||||
- 调整账户/上传/文件名/快捷方式的设置
|
||||
- 跨平台工具
|
||||
- 插件支持:保存至Dropbox,Imgur等等
|
||||
- 支持上传至FTP和SFTP服务器
|
||||
|
||||
- 主页: [screencloud.net][3]
|
||||
- 开发者: Olav S Thoresen
|
||||
- 许可证: GNU GPL v2
|
||||
- 版本号: 1.2.1
|
||||
|
||||
----------
|
||||
|
||||
### KSnapshot ###
|
||||
|
||||

|
||||
|
||||
KSnapshot也是一款易于使用的截图工具,它能给整个桌面、一个单一窗口、窗口的一部分或一块所选区域捕捉图像。,图像能以各种不用的格式保存。
|
||||
|
||||
KSnapshot也允许用户用热键来进行截图。除了保存截图之外,它也可以被复制到剪贴板或用任何与图像文件关联的程序打开。
|
||||
|
||||
KSnapshot是KDE 4图形模块的一部分。
|
||||
|
||||
包含特性:
|
||||
|
||||
- 以多种格式保存截图
|
||||
- 延迟截图
|
||||
- 剔除窗口装饰图案
|
||||
- 复制截图至剪贴板
|
||||
- 热键
|
||||
- 能用它的D-Bus界面进行脚本化
|
||||
|
||||
- 主页: [www.kde.org][4]
|
||||
- 开发者: KDE, Richard J. Moore, Aaron J. Seigo, Matthias Ettrich
|
||||
- 许可证: GNU GPL v2
|
||||
- 版本号: 0.8.2
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/2015062316235249/ScreenCapture.html
|
||||
|
||||
译者:[ZTinoZ](https://github.com/ZTinoZ)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://shutter-project.org/
|
||||
[2]:http://thehive.xbee.net/
|
||||
[3]:https://screencloud.net/
|
||||
[4]:https://www.kde.org/applications/graphics/ksnapshot/
|
||||
@ -1,189 +0,0 @@
|
||||
没有 Linus,Linux 的未来是什么样子?
|
||||
==============================================================================
|
||||

|
||||
|
||||
这次采访是《Linux For You》杂志在2007年进行的,现在我们发表在这里是为了存档的目的。
|
||||
|
||||
**Q:对于 Linux 内核,未来的计划/道路/提升是怎样的?**
|
||||
|
||||
Linus:我从来没有太多的预见性 — 与其从宏大的计划上看未来,我倾向于从一个相对短的时间框架,比如“几个月之后的事情”。我是一个忠实的‘细节成败论’的信仰者,如果你抓住了细节,再大的问题也会大事化小,小事化无。
|
||||
|
||||
所以,对于五年后内核会是什么样,我真的没有任何远见 — 仅仅是一个非常普遍的计划,确保我们对其保持关注。实际上,对于我个人来说,我最担心的事情之一甚至不是技术问题,而是确保这个‘过程’正常,这样人们才可以相互协作好。
|
||||
|
||||
**Q:你怎么看 Linux 和 Solaris 之间的关系在未来的发展?它会如何使用户受益?**
|
||||
|
||||
Linus:我并不能看到整个重叠的地方,除了我认为 Solaris 会开始使用更多的 Linux 用户空间的工具(显然对我自己来说没有太多关注这个 — 我真的只关心内核)。Linux 的桌面比起传统 Solaris 拥有的好多了,而且我希望 Solaris 移植越来越多的Linux的东西,朝着一个更加类 Linux 的模型前进。(LCTT 译注:时至今日,我们还需要讨论 Solaris 吗?/cry )
|
||||
|
||||
从纯内核方面讲,许可证的差异意味着没有太多的合作,但是如果看到这种情况改变会很有趣。Sun 已经声明在 GPL(v2 或 v3)下授权 Solaris,如果这种许可证差异消失,那么会导致一些有趣的技术出现。但对此,我持观望态度。
|
||||
|
||||
**Q:现在 GPL v3 已经完成并发布了,你是否预见有什么情况会鼓励你开始移植内核到 Solaris 上去?或者,从你的角度看,它是否很糟糕以至于你从来没考虑过它?**
|
||||
|
||||
Linus:我觉得相比于早先的草稿,v3 有了很多提高,并且我也认为它不是一个糟糕的许可证。我只是认为它没有 GPLv2一般的‘伟大’。
|
||||
|
||||
所以,由于没有了 GPLv2,我觉得自己将会使用 GPLv3。不过,如果我有了一个更好的选择,我为什么不应该考虑一下呢?
|
||||
|
||||
这就是说,我努力保持实用主义精神,并且我认为 GPLv3 不像 GPLv2 一样好这件事并不是一个‘非黑即白’的问题。这是一个平衡做法。如果 GPLv3 有其他的优点,可能那些优点会在很大程度上扭转喜爱 GPLv3 的天平。
|
||||
|
||||
恕我直言,我并没有看到任何优点,但是如果 Solaris 真的在 GPLv3 下发布,可能避免不必要的非兼容的许可证这条足够称为一个优点,可能也许值得去尝试将Linux的内核重新在 GPLv3 许可证下发布。
|
||||
|
||||
不要误解我 — 我认为这是不大可能的。但是我确实想澄清我本质上不是一个许可证偏执者。我认为 GPLv2 是毫无疑问的好许可证,但是许可证并不是一切。
|
||||
|
||||
总的来说,我使用很多其他许可证下的程序。我可能没有把一个我自己做的项目放在 BSD(或 X11—MIT)许可证下,但是我认为它是一个伟大的许可证,对于其他项目来说,它可能是最佳的选择。
|
||||
|
||||
**Q:目前有没有任何你想特别提出作为 Linux 内核的关键贡献者的印度人?**
|
||||
|
||||
(LCTT 译注:本篇访谈中提到多次印度,是因为访谈者是印度人。)
|
||||
|
||||
Linus:我不得不承认,我并没有与实际认识的来自印度的任何人直接工作。换句话说,我应该稍微澄清下:我已经非常有意识地努力建立一个规模庞大的内核开发团队,这样我不用以独自地工作而告终。
|
||||
|
||||
我非常相信大多数人的社交基本上是受限制的,只对很少的人十分了解(你最亲近的家人和朋友),我也努力构造这样一个开发模型影响这种状况:通过一个‘开发者网络’,人们可以在此互动,可能是与一批你信任的人,而且那些人反过来与他们信任的一群人互动。
|
||||
|
||||
所以,当我偶然会与上百个开发者联系,他们发给我一两个随机的补丁,我已经努力去建立这样一个环境,在这里我做的一堆事,发生在我熟知的人组成的一个较小的群体间,仅仅因为我认为那就是人们工作的方式。当然也是我喜欢工作的方式。
|
||||
|
||||
同时,坦白地说,我甚至不知道许多与我一起工作的人生活在哪里。地理位置成了十分次要的东西。所以我很确信与我工作最亲密的前10—15个人中,没有印度的,可能这话稍后传到公众耳里,然后被指出确实有一些人来自那里!
|
||||
|
||||
**Q:因为 Linux 的内核开发对你依赖如此严重,你如何计划组织或重组,让它在没有你的情况下继续发展,假设你决定花更多的时间在你自己的生活和家庭上面?**
|
||||
|
||||
Linus:现在 Linux 比我重要得多,为了今天这一步我已经工作了很长时间。是的,我仍然十分密切地参与其中,而且我对其有着想当大的日常影响,我最终会是这样一个人——在某种程度上,扮演着许多内核开发活跃者的中心;但是,我不会说Linux“严重依赖”于我。
|
||||
|
||||
所以,如果我得了心脏病并且明天就死了(很高兴没这种可能:我显然在任何方面都还健康),人们肯定会注意到,但是有成千上万的人为内核工作,并且不止一两个人能够没有什么困难地接替我。
|
||||
|
||||
**Q:印度是软件工程师的主要产地之一,当然我们没有在 Linux 领域做太多贡献。你觉得什么是让印度人在Linux领域变得主动的?如果我们鼓励印度人参与并为Linux做更大的贡献,你觉得如何?假如你有一个在印度的粉丝;你会用你的形象来顾问那些爱好者吗?**
|
||||
|
||||
Linus:对我来说,这确实是一个不好回答的问题。参与开源取决于两方面的基础条件(互联网和教育,如你说的):信息流和文化,我甚至不知道这其中哪个是最大的障碍。
|
||||
|
||||
在很多方面,至少那些在印度讲英语文化的地方,参与 Linux 和其他开源项目是相对容易的,如果仅仅是由于语言门槛的话。这当然比起亚洲的许多地方,甚至欧洲的一些地方要容易些。
|
||||
|
||||
当然,这只是一些人,并不等同于印度的大部分群体,而且我自己关于印度的情况也知道不多,甚至没法不太负责的猜测最好的途径是什么。我猜一个热情的本地用户社区一直是最好的途径,我认为你们已经拥有这样的社区了。
|
||||
|
||||
至于我的‘形象’,我自己不以为然。我不是一个伟大的公众演讲者,而且我最近些年已经避免出游,因为被看做符号化的‘形象’让我很不自在。我就是一个工程师而已,而且我仅仅是喜欢我做的事情,并与社会上其他人一起工作。
|
||||
|
||||
**Q:什么样的理由会让你考虑去访问印度?**
|
||||
|
||||
Linus:如第一个回答中提到,我十分讨厌公开演讲,所以我才想避免开会等等这些事。我更愿意某天去印度度个假,但是如果我这样做,我可能悄悄地干 — 出行之前不告诉任何人,仅仅作为一个游客去游览印度!(LCTT 译注:所以 Linus 不来中国的道理是同样的,除非世界性的 LinuxCon 在中国召开一次。)
|
||||
|
||||
**Q:最近,你好像在抨击 Subversion 与 CVS,质问他们的基础架构。现在你已经从 Subversion 和 CVS 社区那里得到回应,你仍然在坚持自己正确,或者没有被说服吗?**
|
||||
|
||||
Linus:因为我发现这个争论很有趣,所以我想做一个强硬的声明。换句话说,我确实‘喜欢’争论。并不是不经思考的,但是我确实想要让争论更热烈些,而不仅仅是完全的柏拉图式的。
|
||||
|
||||
做出强硬的争论有时会引来一个非常合理的反驳,然后我会很高兴地说:“噢,好吧,你是对的。”
|
||||
|
||||
但是话说回来,对 SVN/CVS 并不会发生这种情况。我怀疑很多人并不是真的很喜欢 CVS,所以我真的不觉得会有谁坚持认为 CVS 就是一切,而不是一个老旧系统。要是我知道少数人确实这样争论过了,我之前就不该那么不礼貌地反对 SVN(嘿,这么说没错 — 我真的不是一个非常礼貌的家伙!),我不认为任何人都可以争论 SVN 是‘好的’。
|
||||
|
||||
我认为,SVN 就是一个‘足够好’的经典案例。人们过去经常使用 SVN,并且它也‘足够好’地广泛使用,但是它的足够好完全如 DOS 与 Windows 的‘足够好’一样。不是什么伟大的技术,只是普遍适用而已,同时它对人们来说运行良好,看着十分熟悉。但是很少有人以此为傲,或者对其有兴奋感。
|
||||
|
||||
Git,从另外方面讲,其身后有一些‘UNIX 哲学’。它并不关系到 UNIX,实质上,只是像原始的 UNIX,在它身后有一个基本理念。对 UNIX 来说,最底层的哲学就是,“所有东西只是一个文件”。对 Git 来说,“则是每个东西仅仅是内容寻址数据库中的一个对像”。
|
||||
|
||||
**Q:现在如此多的发行是好事还是坏事?选择是很有意思的,但是没有人想被选择给撑着。相较于这么多的人每天花费数小时去构建成百上千的发行版,如果人们可以一起来支持少数的发行版(可能每一个有一个人),这样进入企业,接受微软的挑战是不是更容易些呢?对此你怎么看?**
|
||||
|
||||
Linus:我认为多个发行版是开源不可回避的部分。它会造成困惑吗?当然。它会变得低效率吗?是的。但是我喜欢拿它与政治比较:‘民主’也有那些令人困惑的选择,往往没有任何一个选择是你‘真正’想要的。而且有时候,如果你不需要操心选举、不同党派和联合等等方面的困惑的话,你可能会感觉事情更加容易一些,更有效率一些。
|
||||
|
||||
但是最后我想说,选择可能会导致低效率,但是它也让每个人至少保留了‘所谓的’诚信。我们可能都希望我们的政治家更诚信,我们也希望不同的发行版可以让我们有一天有其他的选择,而如果没有选择的话,事情可能会更糟。
|
||||
|
||||
**Q:为什么你觉得 CFS 比 SD 更好?**
|
||||
|
||||
Linus:一部分原因是我与 Ingo [Molnar] 工作过很长一段时间,也就是说,我了解他,并且知道他会对发生的任何问题非常负责。那种品质是非常重要的。
|
||||
|
||||
但是一部分原因就简单的与用户有关。其他地方的大多数人实际上表示 CFS 比 SD 好。包括许多 3D 游戏方面(这是人们声称SD 最强的一点)。
|
||||
|
||||
同时,尽管如此,我认为并不是任何一段代码都十分‘完美’。最好的情况是,想成为 SD 支持者的人会努力提高 SD,从而通过其它方式取得了平衡 — 而我们会保持两个阵营都尝试有趣的事情,因为内部的竞争会刺激他们。
|
||||
|
||||
**Q:在 Google 一次关于 Git 的访谈中,有人问你如何将当前集中存放的超大代码库迁移到 git 上,而不用将开发工作停止六个月。你对此的回答是什么?**
|
||||
|
||||
Linus:啊哈。那个问题我在现场没有听清楚(在录音里,问题会听得更清楚些),当我回头去听录制的音频,注意到了我没有回答他的问题,但是我觉得这问题他问过。
|
||||
|
||||
无论如何,我们确实有很多导入的工具,所以你实际上可以仅仅是将一个大的项目从任何其他的早期 SCM 导入到 git 里,但问题显然不是经常以导入动作本身结束,而是需要‘习惯’这种新模式!
|
||||
|
||||
坦白来说,我认为关于‘习惯它’没有任何其他答案,而只是去开始使用和尝试它。显然,你不想以导入你现有的最大且最重要的项目为开端;那确实会使每件事出现停顿,然后使得每个人都很不高兴。
|
||||
|
||||
所以没有任何理智健全的人会拥护在一夜之间将一切移到 git 上去,并强迫人们改变他们的环境。是的,你需要以公司里的小项目开始,可能是一些由一个小组主要控制和维护的项目,然后开始转移其到 git。这是你能让人们习惯这种模式的方式,你应该以一个核心的组开始,他们知道 git 如何工作,如何在公司里面使用它。
|
||||
|
||||
接着,你就会铺展开来。并不需要一次到位。你会导入越来越多的项目 — 甚至是在你公司里采用‘单一大型仓库’模式;那个仓库基本上是作为许多模块的集合,因为让每个人去检查每件事不是一个可执行的工作模型(除非这个‘每件事’并不非常大)。
|
||||
|
||||
所以,你基本上有一次转移一个模块,直到你发现你使用git如此舒服的那个点,你可以移植余下的所有(或者‘余下’的太旧了,没有人用了)。
|
||||
|
||||
git 最赞的一个功能是,它实际上可以同很多其他 SCM(源代码控制管理)相处很好。这就是很多git用户使用它的时候:‘他们’可能只是使用 git ,但有时候与他们一起工作的人并没有发现,因为他们看到git的结果,联想到一些传统的 SCM 上去。
|
||||
|
||||
**Q:在 Transmeta(全美达)上他们有备用指令集实现的经验吗?[Transmeta Crusoe 芯片看起来像一个非常弱的 CPU — 记得有一台 Burroughs B1000 的解释器,它实际上实现了多个虚拟机。有一台是用于系统软件,一台是用于 Cobol,一台用于 Fortran;如果没错的话,那么一个人可以在芯片上实现 Burroughs 6/7000 或者 HP3000 类似的堆栈架构或适用于 JVM 的指令集,等等。]**
|
||||
|
||||
Linus:我们确实有一些备选的结构集合,我仍然不打算谈论这个,我可以说我们已经做了一个混合结构集合的公开演示。我们有一个技术展示,在那里你同时可以跑x86结构和 Java 字节码(实际上,它是一个轻量的扩展 pico—java,iirc)。
|
||||
|
||||
我想我们展示的这个应用会在 Linux 上运行 DOOM,这里 Linux 的部分是一个完全标准 x86 发行版。但是 DOOM 的二进制程序是一个 test 编译版本,它实际上编译为 pico-java 代码。而 CPU 最终以相同的方式来运行它们——从 JIT 到原生 VLIW 指令集。
|
||||
|
||||
(选择 DOOM 的原因仅仅是其源代码可用,并且游戏的核心部分非常小,足以很容易拿它来做一个验证 — 而且它也显然看起来十分有趣。)
|
||||
|
||||
有更多的事情是在内部运作,但是我不能谈论他们。而且实际上,就我个人而言,对 Java 不怎么感冒。
|
||||
|
||||
**Q:386BSD 衍生了 NetBSD,FreeBSD 和 OpenBSD,在 Linux 出现之前已经发展不错了,但是 Linux 传播比 386BSD 及其衍生者更为广泛。这在多大程度上左右你对许可证的选择,这个选择的发展过程是怎样的?你不认为比起 GPLv2 来,是 GPLv3 保护了自由,迄今为止,让 Linux 比 BSD 变得更好?**
|
||||
|
||||
Linus:我认为这是一个许可证问题和一个社区及人格问题。BSD 的许可证总是鼓励分叉,但是这也意味着,如果某些人取得了成功并做了商业性的分叉,他并不需要将将他的修改返回来。因此,实际上并不会真的发生这种事情(以 BSD 而言,如 BSDi),人们并不真的彼此‘信任’。
|
||||
|
||||
相比之下,GPLv2 也鼓励分叉,但是它不仅仅鼓励分叉出去,它也鼓励(并‘要求’)能够融合回来。所以,我们现在达到了新的层次的信任:你‘知道’每个人都被许可证所约束,所以不会试着从你这里白白占走好处。
|
||||
|
||||
所以,在我看来,GPLv2 作为许可证来说,它允许人们在要求总是回馈贡献的前提下,在另外的方面取得了最大可能的自由。没有人能阻止你对源代码的改进。
|
||||
|
||||
那么,BSD 许可证是更‘自由’的吗?是的,毫无疑问。但是我不会在我在意的任何项目里面使用 BSD 许可证,因为我不仅仅想要自由,我也想要信任,可以让我总是能使用其他人为我的项目所写的代码。
|
||||
|
||||
所以对于我来说,GPLv2 最终在‘尽可能自由’上取得了完美的平衡,这样,我们做到了让每个人都能信任,他们总是可以取得源代码并使用它。
|
||||
|
||||
这就是为什么我认为 GPLv3 最终并没多大意思,它不再是那种‘返回源代码’的信任;它退化成了‘我写了这些代码,所以我能控制你如何使用它’。
|
||||
|
||||
换言之,我只是觉得 GPLv3 太狭隘和自私了。我认为 GPLv2 在‘自由’和‘信任’之间取得伟大的平衡。它不如 BSD 许可证自由,但是它让你安心回馈,而且它符合我认为的‘以德报德’:我给你源代码,你也回馈我源代码。
|
||||
|
||||
而 GPLv3 试着控制源代码的‘使用’。现在它就是“我给你我的源代码,如果你使用它的话,你最好可以让我对你的设备动手动脚”,看见了没?在我看来,不但小气,而且小心眼。
|
||||
|
||||
**Q:-rt 树的功能正在缓慢而稳定地逐渐集成到主线代码中。你当前对合并剩余的 -rt 树到主线代码的看法是什么?(我说的不是 CFS)**
|
||||
|
||||
Linus: 我不能保证来自 -rt 的一切‘都’会被合并进入标准内核(有一些部分肯定不适合常规的内核),不过是的,这些年来我们实际上将它的大部分都集成进去了,剩下的部分最终以后也会合并进去。
|
||||
|
||||
我提倡高效工作,但是我同时也很保守。我退回了一些激进的合并请求,只是因为我需要确保它们对所有人都有意义,不仅仅是用于极端情况下的实时环境,而且也对并不需要这种环境的‘普通’用户有用。这解释了为什么这个过程相当缓慢却稳定不断地合并代码,因为它需要足够稳定和有意义。
|
||||
|
||||
顺便说一句,这不仅仅是针对 -rt ,它也在许多开发中出现。-rt 出现这种情况是因为它是更‘直接’的内核项目,而且也是因为它的一个主要开发者也直接涉及到了普通的内核开发。通常其它功能的迁移(安全、虚拟内核变化、虚拟化,等等)也遵循类似的方式:他们针对特定的环境进行开发,然后这些功能片段缓慢而稳步地合并到标准内核。
|
||||
|
||||
|
||||
**Q:我对 Linux 内核支持的文件系统的发展很感兴趣。你觉得 Reiser4、XFS4、ZFS 以及 Oracle 发起那个新项目那个更有前途?这些天 ZFS 有不少新闻,Reiser4 也发布了很不错的性能基准测试,XFS4 正紧随其后,而 Oracle 发布的那个也有很多像 Sun 的 ZFS 一样的特性。我们将走向何方呢?以你的观点来看,哪个文件系统更有前途?**
|
||||
|
||||
Linus: 实际上,就在昨天我们发现了一个 git 的性能问题,有一个用户他采用 ZFS 要比 UFS 慢一个数量级(不是在 Linux 下,git 已经得到了许多关注,甚至是在内核开发团队之外)。所以,我认为许多‘新文件系统’的拥护者部分原因是因为他们了解到旧文件系统的不足,然后(有点不切实际地)期望一个‘崭新的、改进的’文件系统能使一切都完美。
|
||||
|
||||
最后,这是一个永无止境的领域,看看谁是最终的赢家——也许并不需要(看起来不需要)一个赢家。几乎总是这样,对文件系统的选择最终取决于负载和环境。
|
||||
|
||||
相比你提到的这些文件系统,我个人对基于闪存的硬盘很快就可以供甚至是‘普通’用户使用的这个事实更感到兴奋。当然,它们仍然很昂贵(而且相当的小),但是基于闪存的存储和旋转介质的性能完全不可同日而语,我怀疑它们最终将对文件系统的设计有巨大的影响。而现在,多数文件系统的设计都是在考虑如何处理旋转介质的延迟。
|
||||
|
||||
**Q:操作系统变得越来越不重要。你说过好几次用户根本不应该‘看见’操作系统。应用更为重要。基于浏览器的应用,如 Google 的基本办公软件正在发挥影响力。你认为操作系统将走向何方?**
|
||||
|
||||
Linus:我并不真的相信‘浏览器 OS’,因为我认为人们总是需要在本地做一些事情。也许是因为安全,或者仅仅是因为隐私的原因。而且当到处可以接入时,它也并不是‘无处不在’。
|
||||
|
||||
所以我认为,整个‘Web OS’这件事有一部分是真实的,但是另外一部分人们也许忘记了操作系统已经存在了几十年,它已经相当稳定,而且它的发展是有目共睹的。人们真的不应该期望操作系统有魔法般的变化:人们并不能回到‘傻傻的’六十年代,甚至连硬件也和过去的‘那个’完全不同了!
|
||||
|
||||
所以,别指望一场革命。我认为操作系统将更多继续它们所做哪些事情,当然,我们也会进步,但是我不认为会从根本上改变。也许会发生根本性改变的是界面和操作系统顶层的哪些东西(当然,操作系统下面的硬件也会继续进步),这显然才是人们所关心的。
|
||||
|
||||
至于操作系统?它显然是应该尽可能隐藏起来的东西。你真的不应该在意它,除非你非常想知道在机器里面真正在做什么。
|
||||
|
||||
**Q:最近我听说,你正在使用一台 PPC G4/5 作为个人计算机,你使用它来做什么?为什么呢?**
|
||||
|
||||
Linus:我最终放弃了那台 PowerPC,因为没有人能在这台工作站上做的更多,特别是,自从 x86-64 开始变得越来越强大了。所以这些天,我在用一台标准的 PC,里面是一个普通的 Core 2 Duo CPU。
|
||||
|
||||
在其它架构下运行是非常有趣的(我把 alpha 作为我的主要架构运行了好几年,所以这并不是第一次),但是这种 CPU 得当成商品买得到才行。我认为,唯一能取代 x86 架构的将来自以下,比如也许我们将来十年并不需要使用 x86 作为我们的主要架构,我认为也许是 ARM,这得益于移动设备市场。
|
||||
|
||||
**Q:Linux 对你意味着什么?一种业余爱好、哲学、人生意义、工作、最好的操作系统,还是什么?**
|
||||
|
||||
Linus:它是所有的这一切。它是爱好,而且是具有深刻意义的爱好。最好的爱好是你‘真的’非常在意它。这些日子里,它显示也是我的工作,我非常高兴工作和兴趣能合二为一。
|
||||
|
||||
我不了解所谓的‘哲学’,我并不真的是因为深层次的道德或哲学的原因才做的 Linux (字面上的做是因为它有趣),但是可以肯定的是,我欣赏我认为开源为何这么棒的深层原因。所以我并不是因为什么高大上的理由做 Linux 的,而且我不能诚恳地说是它在激励我,但是我最终会思考为什么会这样。
|
||||
|
||||
**Q:微软的‘黑衣人’有没有和你交谈过?**
|
||||
|
||||
Linus:我从来没有真正和微软交谈过,没有。我偶尔会和一些微软的人出现再同一个会议上(我比以前参加的会议更多了),但是我从来和他们没有任何关系。我认为彼此都很谨慎吧。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxveda.com/2015/06/17/what-happens-to-linux-after-linus/
|
||||
|
||||
作者:[Swapnil Bhartiya][a]
|
||||
译者:[wi-cuckoo](https://github.com/wi-cuckoo),[wxy](https://github.com/wxy)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxveda.com/author/arnieswap/
|
||||
|
||||
@ -1,239 +0,0 @@
|
||||
在RHEL/CentOS 7.0中安装LAMP(Linux、 Apache、 MariaDB、 PHP/PhpMyAdmin)
|
||||
================================================================================
|
||||
跳过LAMP的介绍因为我认为你们大多数已经知道了。这个教程会集中在如何在升级到Apache 2.4的 Red Hat Enterprise Linux 7.0 和 CentOS 7.0中安装和配置LAMP-Linux Apache、 MariaDB、 PHP、PhpMyAdmin。
|
||||
|
||||

|
||||
|
||||
在RHEL/CentOS 7.0中安装LAMP
|
||||
|
||||
#### 要求 ####
|
||||
|
||||
根据使用的发行版,RHEL 或者 CentOS 7.0使用下面的链接来执行最小的系统安装,网络使用静态ip
|
||||
|
||||
**对于RHEL 7.0**
|
||||
|
||||
- [RHEL 7.0安装过程][1]
|
||||
- [在RHEL 7.0中注册和启用订阅仓库][2]
|
||||
|
||||
**对于 CentOS 7.0**
|
||||
|
||||
- [CentOS 7.0 安装过程][3]
|
||||
|
||||
### 第一步: 使用基本配置安装apache ###
|
||||
|
||||
**1. 在执行最小系统安装并配置[在RHEL/CentOS 7.0中配置静态ip][4]**就可以从使用下面的命令从官方仓库安装最新的Apache 2.4 httpd服务。
|
||||
|
||||
# yum install httpd
|
||||
|
||||

|
||||
|
||||
安装apache服务
|
||||
|
||||
**2. 安装安城后,使用下面的命令来管理apache守护进程,因为RHEL and CentOS 7.0都将init脚本从SysV升级到了systemd - 你也可以同事使用SysV和Apache脚本来管理服务。**
|
||||
|
||||
# systemctl status|start|stop|restart|reload httpd
|
||||
|
||||
或者
|
||||
|
||||
# service httpd status|start|stop|restart|reload
|
||||
|
||||
或者
|
||||
|
||||
# apachectl configtest| graceful
|
||||
|
||||

|
||||
|
||||
启动apache服务
|
||||
|
||||
**3. 下一步使用systemd初始化脚本来启动apache服务并用firewall-cmd打开RHEL/CentOS 7.0防火墙规则, 这是通过firewalld守护进程管理iptables的默认命令。**
|
||||
|
||||
# firewall-cmd --add-service=http
|
||||
|
||||
**注意**:上面的命令会在系统重启或者firewalld服务重启后失效,因为它是即时的规则,它不会永久生效。要使iptables规则在fiewwall中持久化,使用-permanent选项并重启firewalld服务来生效。
|
||||
|
||||
# firewall-cmd --permanent --add-service=http
|
||||
# systemctl restart firewalld
|
||||
|
||||

|
||||
|
||||
在CentOS 7中启用Firewall
|
||||
|
||||
下面是firewalld其他的重要选项:
|
||||
|
||||
# firewall-cmd --state
|
||||
# firewall-cmd --list-all
|
||||
# firewall-cmd --list-interfaces
|
||||
# firewall-cmd --get-service
|
||||
# firewall-cmd --query-service service_name
|
||||
# firewall-cmd --add-port=8080/tcp
|
||||
|
||||
**4. 要验证apache的功能,打开一个远程浏览器并使用http协议输入你服务器的ip地址(http://server_IP), 应该会显示下图中的默认页面。**
|
||||
|
||||

|
||||
|
||||
Apache默认页
|
||||
|
||||
**5. 现在apache的根地址在/var/www/html,该目录中没有提供任何index文件。如果你想要看见根目录下的文件夹列表,打开apache欢迎配置文件并设置 <LocationMach>下Indexes前的状态从-到+,下面的截图就是一个例子。**
|
||||
|
||||
# nano /etc/httpd/conf.d/welcome.conf
|
||||
|
||||

|
||||
|
||||
Apache目录列出
|
||||
|
||||
**6. 关闭文件,重启apache服务来使设置生效,重载页面来看最终效果。**
|
||||
|
||||
# systemctl restart httpd
|
||||
|
||||

|
||||
|
||||
Apache Index 文件
|
||||
|
||||
### 第二步: 为Apache安装php5支持 ###
|
||||
|
||||
|
||||
**7. 在为apache安装php支持之前,使用下面的命令的得到所有可用的php模块和扩展。**
|
||||
|
||||
# yum search php
|
||||
|
||||

|
||||
|
||||
在
|
||||
|
||||
**8. Depending on what type of applications you want to use, install the required PHP modules from the above list, but for a basic MariaDB support in PHP and PhpMyAdmin you need to install the following modules.**
|
||||
|
||||
# yum install php php-mysql php-pdo php-gd php-mbstring
|
||||
|
||||

|
||||
|
||||
Install PHP Modules
|
||||
|
||||

|
||||
|
||||
Install PHP mbstring Module
|
||||
|
||||
**9. To get a full information list on PHP from your browser, create a info.php file on Apache Document Root using the following command from root account, restart httpd service and direct your browser to the http://server_IP/info.php address.**
|
||||
|
||||
# echo "<?php phpinfo(); ?>" > /var/www/html/info.php
|
||||
# systemctl restart httpd
|
||||
|
||||

|
||||
|
||||
Check PHP Info in CentOS 7
|
||||
|
||||
**10. If you get an error on PHP Date and Timezone, open php.ini configuration file, search and uncomment date.timezone statement, append your physical location and restart Apache daemon.**
|
||||
|
||||
# nano /etc/php.ini
|
||||
|
||||
Locate and change date.timezone line to look like this, using [PHP Supported Timezones list][5].
|
||||
|
||||
date.timezone = Continent/City
|
||||
|
||||

|
||||
|
||||
Set Timezone in PHP
|
||||
|
||||
### Step 3: Install and Configure MariaDB Database ###
|
||||
|
||||
**11. Red Hat Enterprise Linux/CentOS 7.0 switched from MySQL to MariaDB for its default database management system. To install MariaDB database use the following command.**
|
||||
|
||||
# yum install mariadb-server mariadb
|
||||
|
||||

|
||||
|
||||
在CentOS 7中安装PHP
|
||||
|
||||
***12. 安装MariaDB后,开启数据库守护进程并使用mysql_secure_installation脚本来保护数据库(设置root密码、禁止远程root登录、移除测试数据库、移除匿名用户)**
|
||||
|
||||
# systemctl start mariadb
|
||||
# mysql_secure_installation
|
||||
|
||||

|
||||
|
||||
启动MariaDB数据库
|
||||
|
||||

|
||||
|
||||
MySQL安全设置
|
||||
|
||||
**13. 要测试数据库功能,使用root账户登录MariaDB并用quit退出。**
|
||||
|
||||
mysql -u root -p
|
||||
MariaDB > SHOW VARIABLES;
|
||||
MariaDB > quit
|
||||
|
||||

|
||||
|
||||
连接MySQL数据库
|
||||
|
||||
### 第四步: 安装PhpMyAdmin ###
|
||||
|
||||
**14. RHEL 7.0 或者 CentOS 7.0仓库默认没有提供PhpMyAdmin二进制安装包。如果你不适应使用MySQL命令行来管理你的数据库,你可以通过下面的命令启用CentOS 7.0 rpmforge仓库来安装PhpMyAdmin。**
|
||||
|
||||
# yum install http://pkgs.repoforge.org/rpmforge-release/rpmforge-release-0.5.3-1.el7.rf.x86_64.rpm
|
||||
|
||||
启用rpmforge仓库后,下面安装PhpMyAdmin。
|
||||
|
||||
# yum install phpmyadmin
|
||||
|
||||

|
||||
|
||||
启用RPMForge仓库
|
||||
|
||||
**15. 下面配置PhpMyAdmin的phpmyadmin.conf来允许远程连接,它位于Apache conf.d目录下,并注释掉下面的行。**
|
||||
|
||||
# nano /etc/httpd/conf.d/phpmyadmin.conf
|
||||
|
||||
使用#来注释掉行。
|
||||
|
||||
# Order Deny,Allow
|
||||
# Deny from all
|
||||
# Allow from 127.0.0.1
|
||||
|
||||

|
||||
|
||||
允许远程PhpMyAdmin访问
|
||||
|
||||
**16. 要使用cookie验证来登录PhpMyAdmin,像下面的截图那样使用[生成字符串][6]添加一个blowfish字符串到config.inc.php文件下,重启apache服务并打开URL:http://server_IP/phpmyadmin/。**
|
||||
|
||||
# nano /etc/httpd/conf.d/phpmyadmin.conf
|
||||
# systemctl restart httpd
|
||||
|
||||

|
||||
|
||||
在PhpMyAdmin中添加Blowfish
|
||||
|
||||

|
||||
|
||||
PhpMyAdmin面板
|
||||
|
||||
### 第五步: 系统范围启用LAMP ###
|
||||
|
||||
**17. 如果你需要在重启后自动运行MariaDB和Apache服务,你需要系统级地启用它们。**
|
||||
|
||||
# systemctl enable mariadb
|
||||
# systemctl enable httpd
|
||||
|
||||

|
||||
|
||||
系统级启用服务
|
||||
|
||||
这就是在Red Hat Enterprise 7.0或者CentOS 7.0中安装LAMP的过程。CentOS/RHEL 7.0上关于LAMP洗系列文章将会讨论在Apache中创建虚拟主机,生成SSL证书、密钥和添加SSL事物支持。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/install-lamp-in-centos-7/
|
||||
|
||||
作者:[Matei Cezar][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/cezarmatei/
|
||||
[1]:http://www.tecmint.com/redhat-enterprise-linux-7-installation/
|
||||
[2]:http://www.tecmint.com/enable-redhat-subscription-reposiories-and-updates-for-rhel-7/
|
||||
[3]:http://www.tecmint.com/centos-7-installation/
|
||||
[4]:http://www.tecmint.com/configure-network-interface-in-rhel-centos-7-0/
|
||||
[5]:http://php.net/manual/en/timezones.php
|
||||
[6]:http://www.question-defense.com/tools/phpmyadmin-blowfish-secret-generator
|
||||
@ -1,206 +0,0 @@
|
||||
Tor浏览器:Linux下用于匿名Web浏览的终极浏览器
|
||||
================================================================================
|
||||
我们大多数人都在上网方面花费很多时间。上网使用的应用程序主要是浏览器,一个Web浏览器则更加完美。我们网络的活动要以客户端/服务器的方式登录,这个过程会包括IP地址、地理信息、搜索、活动以及许多潜在的信息,这些信息如果以其他方式被故意使用,会存在潜在的危险性。
|
||||
|
||||

|
||||
|
||||
Tor浏览器:匿名浏览器
|
||||
|
||||
此外,美国国家安全局(NSA)即国际间谍机构会记录我们的数字足迹。更不必说某个受限的代理服务器也会被用来做为数据搜集服务器。并且大多数企业和公司不会允许您访问代理服务器(使您能保障自己的隐私)。
|
||||
|
||||
因此,我们需要的最好是一个小型、独立、可携带的应用程序,它能达到匿名的效果。Tor浏览器便是这样的一个应用,它拥有上面提到的所有功能,甚至不止于此。
|
||||
|
||||
这篇文章里我们会讨论Tor浏览器,它的功能、使用方式、领域、安装以及其他关于Tor浏览器的重要方面。
|
||||
|
||||
#### 什么是Tor浏览器? ####
|
||||
|
||||
Tor是一个自由分发的应用软件,以BSD式的许可证发布,通过其安全可靠的洋葱式的结构,允许用户匿名的进行网络浏览。从前,由于它的结构和运作机制,Tor被称为‘洋葱路由器’。这个应用是由C语言写成的。
|
||||
|
||||
#### Tor浏览器的功能 ####
|
||||
|
||||
- 跨平台可用。例如,这个应用程序在Linux、Windows和Mac下都可用。
|
||||
- 在发送数据到因特网前进行复杂的数据加密。
|
||||
- 在客户端进行的数据自动解密。
|
||||
- 它是火狐浏览器和Tor工程的结合。
|
||||
- 对服务器和网站提供匿名性。
|
||||
- 可以访问被锁定的网站。
|
||||
- 无需暴露源IP便可以执行任务。
|
||||
- 可以在防火墙后将数据路由至/从隐藏的服务和应用程序。
|
||||
- 便携性 - 可以直接从USB存储器运行一个预配置的web浏览器。无需本地安装。
|
||||
- 在x86和x86_64平台均可用
|
||||
- 可以通过使用Tor以“socks4a”的方式在“localhost”的“9050”端口上配置代理以设置FTP。
|
||||
- Tor拥有处理上千的转播和上百万用户的能力。
|
||||
|
||||
#### Tor浏览器如何工作? ####
|
||||
|
||||
Tor的工作方式基于洋葱路由的概念。洋葱路由的结构类似洋葱,它的每一层都嵌套在另一层里面,就像洋葱一样。这种嵌套的结构负责多次加密数据并将其通过虚拟电路进行发送。在客户端一边每一层都在将他传递到下一层之前解密数据。最后一层在将原始数据传递到目的地前解密最里面一层的加密数据。
|
||||
|
||||
在这个过程里,这种解密整个层的功能设计的如此高明以至于无法追踪IP以及用户的地理位置,因此可以限制任何人观察您访问站点的网络连接。
|
||||
|
||||
所有这些过程看起来有些复杂,但用户使用Tor浏览器时没有必要担心。实际上,Tor浏览器的功能像其他浏览器一样(尤其是Mozilla的Firefox)。
|
||||
|
||||
### 在Linux中安装Tor浏览器 ###
|
||||
|
||||
就像上面讨论的一样,Tor浏览器在Linux和Windows以及Mac下都可用。用户需要根据系统和架构的不同在下面的链接处下载最新的版本(例如,Tor浏览器4.0.4)。
|
||||
|
||||
- [https://www.torproject.org/download/download-easy.html.en][1]
|
||||
|
||||
在下载Tor浏览器后,我们需要安装它。但好的是我们不需要安装‘Tor’。它能直接从随身设备中运行,并且该浏览器可以被预配置。这意味着插件和运行的特性可以完美的移植。
|
||||
|
||||
下载打包文件(*.tar.xz)后我们需要解压它。
|
||||
|
||||
**32位系统**
|
||||
|
||||
$ wget https://www.torproject.org/dist/torbrowser/4.0.4/tor-browser-linux32-4.0.4_en-US.tar.xz
|
||||
$ tar xpvf tor-browser-linux32-4.0.4_en-US.tar.xz
|
||||
|
||||
**64位系统**
|
||||
|
||||
$ wget https://www.torproject.org/dist/torbrowser/4.0.4/tor-browser-linux64-4.0.4_en-US.tar.xz
|
||||
$ tar -xpvf tor-browser-linux64-4.0.4_en-US.tar.xz
|
||||
|
||||
**注意** : 在上面的命令中,我们使用‘$‘意味着这个压缩包应以普通用户而不是root用户来解压。我们强烈建议您不要以root用户解压和运行Tor浏览器。
|
||||
|
||||
在成功的解压后,我们便可以将解压后的浏览器移动到任何地方/USB存储设备中。并从解压的文件夹以非root用户直接运行‘start-tor-browser’。
|
||||
|
||||
$ cd tor-browser_en-US
|
||||
$ ./start-tor-browser
|
||||
|
||||

|
||||
|
||||
开始使用Tor浏览器
|
||||
|
||||
**1. 尝试连接到Tor网络。点击“连接”之后Tor将按照设置帮您做剩下的事情。**
|
||||
|
||||

|
||||
|
||||
连接到Tor网络
|
||||
|
||||
**2. 欢迎窗口/标签。**
|
||||
|
||||

|
||||
|
||||
Tor欢迎界面
|
||||
|
||||
**3. Tor浏览器从Youtube处加载视频。**
|
||||
|
||||

|
||||
|
||||
在Youtube上看视频
|
||||
|
||||
**4. 打开银行网址以进行在线购物和交易。**
|
||||
|
||||

|
||||
|
||||
浏览银行站点
|
||||
|
||||
**5. 浏览器显示我当前的代理IP。注意文本为“Proxy Server detected”。**
|
||||
|
||||

|
||||
|
||||
检查IP地址
|
||||
|
||||
**注意**: 每次您想运行Tor时,您需要使用文本模式来指向Tor启动脚本。并且该终端在您运行Tor时会持续保持忙碌状态。如何克服这些,并创建一个桌面/Dock栏图标呢?
|
||||
|
||||
**6. 我们需要在解压的文件夹中创建`tor.desktop`。**
|
||||
|
||||
$ touch tor.desktop
|
||||
|
||||
接着使用您喜欢的编辑器编辑这个文件,加入下面的文本,这里我使用nano。
|
||||
|
||||
$ nano tor.desktop
|
||||
|
||||
----------
|
||||
|
||||
#!/usr/bin/env xdg-open
|
||||
[Desktop Entry]
|
||||
Encoding=UTF-8
|
||||
Name=Tor
|
||||
Comment=Anonymous Browse
|
||||
Type=Application
|
||||
Terminal=false
|
||||
Exec=/home/avi/Downloads/tor-browser_en-US/start-tor-browser
|
||||
Icon=/home/avi/Downloads/tor-browser_en-US/Browser/browser/icons/mozicon128.png
|
||||
StartupNotify=true
|
||||
Categories=Network;WebBrowser;
|
||||
|
||||
**注意**: 确保将上面的tor浏览器的路径替换为您的环境中的路径。
|
||||
|
||||
**7. 一旦搞定后,您就可以双击`tor.desktop`文件来运行Tor浏览器了,您可能需要在第一次运行时信任该文件。**
|
||||
|
||||

|
||||
|
||||
Tor应用启动器
|
||||
|
||||
**8. 一旦您选择了信任,请注意`tor.desktop`文件的图标则会改变。**
|
||||
|
||||

|
||||
|
||||
Tor图标已改变
|
||||
|
||||
**9. 您可以通过拖拽`tor.desktop`的图标在桌面和Dock栏中创建快捷方式。**
|
||||
|
||||

|
||||
|
||||
在桌面添加Tor快捷方式
|
||||
|
||||
**10. 关于Tor浏览器。**
|
||||
|
||||

|
||||
|
||||
关于Tor浏览器
|
||||
|
||||
**注意**: 如果您在使用旧版本的Tor,您可以从上面的窗口更新它。
|
||||
|
||||
#### 应用的可用性和领域 ####
|
||||
|
||||
- 匿名使用网络。
|
||||
- 浏览被阻挡的页面。
|
||||
- 连接其他应用,即(FTP)来保证网络安全的访问。
|
||||
|
||||
#### 关于Tor浏览器的争论 ####
|
||||
|
||||
- 在Tor浏览器的周边并没有什么安全措施。比如,数据入口点和出口点。
|
||||
- 一项2011年的研究发现一种特殊的针对Tor浏览器的攻击可以得到BitTorrent用户的IP地址。
|
||||
- 在一些研究中发现某些特定的协议有泄漏IP地址的倾向。
|
||||
- Tor早些的版本绑定了旧版本的Firefox浏览器,这被证明较易受JavaScript攻击。
|
||||
- Tor浏览器工作的比较缓慢。
|
||||
|
||||
#### 真实世界中Tor浏览器的实现 ####
|
||||
|
||||
- Vuze BitTorrent Client
|
||||
- Anonymous Os
|
||||
- Os’es from Scratch
|
||||
- whonix 等
|
||||
|
||||
#### Tor浏览器的未来 ####
|
||||
|
||||
Tor浏览器是前途无量的。也许它实现的第一个应用程序非常出色,但Tor浏览器必须加大对伸缩性的支持以及对近期的攻击进行研究以保证数据安全。这个应用程序是未来的需要。
|
||||
|
||||
#### 下载免费的电子书 ####
|
||||
|
||||
非官方的Tor私密浏览指南
|
||||
|
||||
[][2]
|
||||
|
||||
### 结论 ###
|
||||
|
||||
如果您工作的部门不允许您访问某网站或者如果您不希望别人知道您的私人事务或您不想向NSA提供您的个人数字足迹,那么Tor浏览器在目前是必须的。
|
||||
|
||||
**注意**: Tor浏览器提供的安全性不能抵御病毒、木马或其他类似这样的安全威胁。写这篇文章的目的也不是希望通过在互联网上隐藏我们的身份来放纵非法活动。这篇文章纯粹是为了教学的目的,作者和Tecmint均不会为任何非法的使用负责。这是用户的唯一责任。
|
||||
|
||||
Tor浏览器是一个非常不错的应用,您值得尝试!这就是我要说的全部了,我还会在这里写一些您感兴趣的文章,所以请继续关注Tecmint。别忘了在留言区提供给我们您有价值的反馈。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/tor-browser-for-anonymous-web-browsing/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[wwy-hust](https://github.com/wwy-hust)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:https://www.torproject.org/download/download-easy.html.en
|
||||
[2]:http://tecmint.tradepub.com/free/w_make129/prgm.cgi
|
||||
Loading…
Reference in New Issue
Block a user