mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-25 23:11:02 +08:00
commit
4b83b8a313
@ -0,0 +1,50 @@
|
||||
鲜为人知的 Apache Mesos 项目帮助 Mesosphere 公司得到了千万美元投资
|
||||
================================================================================
|
||||

|
||||
|
||||
[Mesosphere][1],一家试图围绕鲜为人知的 Apache Mesos 项目开展商业活动的公司,刚刚从 Andreessen Horowitz 那里获得了 1000 万美元投资。以下是为什么这个项目能够吸引如此巨款的原因。
|
||||
|
||||
事实上 Mesos 这款自动扩放软件已经出现了五年了。据 Mesosphere 的CEO及联合创始人 Florian Leibert 所述,Mesos 已经在 Twitter 内已经管理了超过 50,000 个以上的CPU。此外, EBay, AirBnB, Netflix 还有 HubSpot 也是这款软件的使用者。
|
||||
|
||||
当那些互联网巨头发现 Mesos 的时候,这项技术却并不为大多数企业所知。但它确实可以满足一些公司在他们内部的数据中心上应用公共云的一些技术的需求。
|
||||
|
||||
Mesos 管理集群机器,根据需要自动扩放应用。它在每台机器上只依赖很少的软件,它由一个主调度程序协调。据 Leibert 所说,其CPU 占用为 0 并且几乎不消耗任何内存。在其工作的每台机器上的该软件会向调度程序报告关于虚拟机或者服务器的容量信息,接着调度程序向目标机器分派任务。
|
||||
|
||||
“如果一项任务终断并且没有返回任何结果,主调度程序知道如何重新调度它和它所用的资源在哪里。” Mesosphere 的资深副总裁 Matt Trifiro 说。
|
||||
|
||||
Mesos 能自动扩放一系列的任务,包括 Hadoop 数据库,Ruby on Rails 节点,以及 Cassandra 。
|
||||
|
||||
使用 Mesos 使得 Hubspot 削减了一半的 AWS(Amazon Web Services) 的费用支出,Liebert 说道。这是因为 Mesos 能够在目标机器之间有效地分配作业量的原因。
|
||||
|
||||
然而,Mesos 更有可能应用到那些试图真正地在内部创建一个类 AWS 环境的企业,一位来自 451 Research 的分析员 Jay Lyman 说。AWS 提供一些[自动扩放工具][3],但大多数公司对于在公共云基础设施上运行所有东西还是感到不安。与此同时,他们并不想着反对他们的开发者采用 AWS 那样的公共云中可用的优异性能。他们希望他们的私有云能集成这些可用的优点。
|
||||
|
||||
“如你所见,类似 AWS 风格的界面风格,与监控、命令、操控以及稳定性相融合,” Liebert 继续说道。
|
||||
|
||||
Mesos 既可以在一个私有云上也可以在 AWS 上运行,向企业提供最有效率地使用其内部云的方法,并在需要扩放时自动切换到 AWS 去。
|
||||
|
||||
但是,从另外的方面说 Mesos 也是有一些缺点的。它[并不能运行][4]任何 Windows 操作系统或者比较古老的应用比如说 SAP 软件。
|
||||
|
||||
不过,Lyman 说,“假如一个团队拥有长时期使用云的经历,他们大概早就对 Linux 操作系统情有独钟了。”
|
||||
|
||||
在将来,Mesosphere 能够支持 Windows 操作系统是很有可能的。最初,像 Puppet 和 Chef 这样的技术也只支持 Linux 操作系统,Lyman 表示。“这只是早期 Mesosphere 的特性。现在它还是不太成熟,” 他又说道。
|
||||
|
||||
Mesosphere 正瞄向大部分使用现代编程技术构建了越来越多的运行于 Linux 的应用的企业,以及 Twitter 和 Netflix 这种在初创时还没有 Mesos 类似技术的第一代 Web 2.0 公司。“这是早期两类最常见的客户概况,” Trifiro 说。
|
||||
|
||||
年终之前,Mesosphere 希望发布包含文档的商业产品,通过技术支持与颁发许可证来获得营收。Mesosphere 已开发一款名为 Marathon 的大规模扩放编制工具,并且支持 Docker 集成。它现在免费提供打包好的 Mesos 发行版,希望以此占有未来的市场。
|
||||
|
||||
Mesosphere 同时也正在为少数早期的顾客工作。它帮助 HubSpot 实施有关 Mesos 的搭建。
|
||||
|
||||
Mesosphere 在这个领域并不唯一。Rightscale,Scalr 以及现在归 Dell 所有的 Enstratius,全都提供了一些各种版本的扩放或云管理技术。Mesosphere 强调说,Mesos 及其公司自己开发的技术在单独机器中创建服务器集群方面的表现远胜于市场上的其他同类软件。来自 Andreessen 的新投资一定会帮助 Meos 获得更大的动力。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://thenewstack.io/little-known-apache-mesos-project-helps-mesosphere-raise-10m-from-andreessen/
|
||||
|
||||
译者:[SteveArcher](https://github.com/SteveArcher) 校对:[ wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://mesosphere.io/
|
||||
[2]:http://mesos.apache.org/
|
||||
[3]:http://aws.amazon.com/autoscaling/
|
||||
[4]:http://mesosphere.io/learn/
|
||||
@ -1,43 +1,42 @@
|
||||
2q1w2007翻译中
|
||||
搭建并运行OpenVPN,享受你的隐私生活
|
||||
十步搭建 OpenVPN,享受你的隐私生活
|
||||
================================================================================
|
||||

|
||||
|
||||
> 我们支持保护隐私,不为我们有自己的秘密需要保护,只是我们认为保护隐私应该成为一项基本人权。所以我们坚信无论谁在什么时候行使这项权利,都应该不受拘束的获取必须的工具和服务。OpenVPN就是这样一种服务并且有多种工具(客户端) 来让我们利用并享受这种服务。
|
||||
> 我们支持保护隐私,不为我们有自己的秘密需要保护,只是我们认为保护隐私应该成为一项基本人权。所以我们坚信无论谁在什么时候行使这项权利,都应该不受拘束的获取必须的工具和服务。OpenVPN就是这样一种服务并且有多种工具(客户端) 来让我们利用并享受这种服务。
|
||||
|
||||
通过与一个[OpenVPN][1]服务器建立连接,我们基本上在我们的设备和远端运行OpenVPN的主机之间建立了一个安全的通信通道。尽管在两个端点之间的通信可能被截获,但是信息是经过高强度加密的所以实际上它对于攻击者没什么用。OpenVPN除了扮演加密通信通道的调解人,我们也可以通过设置使服务器扮演因特网网管的角色。通过这种方式,我们可以连接任何不安全的Wifi,然后迅速的链接到远程的OpenVPN服务器并在不需要考虑偷窥的人或者无聊的管理员的情况下运行需要上网的程序。(注意:OpenVPN服务器旁还是需要信任的管理员的。)
|
||||
通过与一个[OpenVPN][1]服务器建立连接,我们基本上在我们的设备和远端运行OpenVPN的主机之间建立了一个安全的通信通道。尽管在两个端点之间的通信可能被截获,但是信息是经过高强度加密的所以实际上它对于攻击者没什么用。OpenVPN除了扮演加密通信通道的调解人,我们也可以通过设置使服务器扮演互联网网关的角色。通过这种方式,我们可以**连接任何不安全的Wifi**,然后迅速的链接到远程的OpenVPN服务器,然后在不需要考虑偷窥的人或者无聊的管理员的情况下运行需要上网的程序。(注意:OpenVPN服务器旁还是需要信任的管理员的。)
|
||||
|
||||
这篇文章将一步一步的教会你如何在[Ubuntu Server 14.04 LTS][2]上安装OpenVPN。OpenVPN所在的主机可能是云上的一台VPS,一台在我们家里某台电脑上运行的虚拟机,或者是一个老到你都快忘了的设备。
|
||||
这篇文章将一步一步的教会你如何在[Ubuntu Server 14.04 LTS][2]上安装OpenVPN。OpenVPN所在的主机可能是云上的一台VPS,一台在我们家里某台电脑上运行的虚拟机,或者是一个老到你都快忘了的设备。
|
||||
|
||||
### 第一步 -- 准备系统 ###
|
||||
### 第一步 准备系统 ###
|
||||
|
||||
我们需要Ubuntu Server主机的一个命令行终端,比如通过SSH从远程访问它。首先需要更新它的本地仓库数据:
|
||||
我们需要Ubuntu Server主机的一个命令行终端,比如通过SSH从远程访问它。首先需要更新它的本地仓库数据:
|
||||
|
||||
sub0@delta:~$ sudo apt-get update
|
||||
|
||||
进行操作系统和已安装的包的升级,输入:
|
||||
进行操作系统和已安装的包的升级,输入:
|
||||
|
||||
sub0@delta:~$ sudo apt-get dist-upgrade
|
||||
|
||||
如果升级了新内核,那就需要重启。当更新完成后,就该安装OpenVPN了:
|
||||
如果升级了新内核,那就需要重启。当更新完成后,就该安装OpenVPN了:
|
||||
|
||||
sub0@delta:~$ sudo apt-get -y install openvpn easy-rsa dnsmasq
|
||||
|
||||
注意,我们用apt-get安装了三个包:
|
||||
注意,我们用apt-get安装了三个包:
|
||||
|
||||
- openvpn提供了OpenVPN的核心
|
||||
- easy-rsa包含了一些有用的密钥管理脚本
|
||||
- dnsmasq是当我们的OpenVPN所在的主机将扮演客户端的路由器时会用到的域名服务器
|
||||
|
||||
### 第二步 -- 生成证书和私钥 ###
|
||||
### 第二步 生成证书和私钥 ###
|
||||
|
||||
这是安装OpenVPN中最重要和最关键的一步,目的是建立公钥基础设施(PKI)。包括如下内容:
|
||||
这是安装OpenVPN中最重要和最关键的一步,目的是建立公钥基础设施(PKI)。包括如下内容:
|
||||
|
||||
- 为OpenVPN服务器创建一个证书(公钥)和一个私钥
|
||||
- 为每个OpenVPN客户端创建证书和私钥
|
||||
- 建立一个证书颁发机构(CA)并创建证书和私钥。这个私钥用来给OpenVPN服务器和客户端的证书签名
|
||||
|
||||
从最后一个做起,我们先建立一个目录:
|
||||
从最后一个做起,我们先建立一个目录:
|
||||
|
||||
sub0@delta:~$ sudo mkdir /etc/openvpn/easy-rsa
|
||||
|
||||
@ -45,11 +44,11 @@
|
||||
|
||||
sub0@delta:~$ sudo cp -r /usr/share/easy-rsa/* /etc/openvpn/easy-rsa
|
||||
|
||||
在我们创建CA的私钥之前,我们先编辑/etc/openvpn/easy-rsa/vars(我们喜欢用nano,不过这只是我们的喜好,你爱用什么用什么):
|
||||
在我们创建CA的私钥之前,我们先编辑/etc/openvpn/easy-rsa/vars(我们喜欢用nano编辑器,不过这只是我们的喜好,你爱用什么用什么):
|
||||
|
||||
sub0@delta:~$ sudo nano /etc/openvpn/easy-rsa/vars
|
||||
|
||||
在文件的尾部,我们设置主证书和密钥的信息:
|
||||
在文件的尾部,我们设置主证书和密钥的信息:
|
||||
|
||||
export KEY_COUNTRY="GR"
|
||||
export KEY_PROVINCE="Central Macedonia"
|
||||
@ -61,9 +60,9 @@
|
||||
export KEY_OU="Parabing"
|
||||
export KEY_ALTNAMES="VPNsRUS"
|
||||
|
||||
你可以根据自己的情况设置不同的值。特别注意最后KEY_ALTNAMES这一行,尽管这不是原本vars文件中有的但是我们还是把它加到文件的尾部,不然build-ca脚本会运行失败。
|
||||
你可以根据自己的情况设置不同的值。特别注意最后KEY_ALTNAMES这一行,尽管这不是原本vars文件中有的但是我们还是把它加到文件的尾部,不然build-ca脚本会运行失败。
|
||||
|
||||
保存更改,我们得按[CTRL+O]然后按[Enter]。想退出nano,请按[CTRL+X]。现在,我们要获得root访问权限,继续生成主证书和私钥(LCTT译注:请注意命令行账户发生了改变):
|
||||
保存更改,我们得按[CTRL+O]然后按[Enter]。想退出nano,请按[CTRL+X]。现在,我们要获得root访问权限,继续生成主证书和私钥(LCTT译注:请注意命令行账户发生了改变):
|
||||
|
||||
sub0@delta:~$ sudo su
|
||||
root@delta:/home/sub0# cd /etc/openvpn/easy-rsa
|
||||
@ -93,11 +92,11 @@
|
||||
Email Address [nobody@parabing.com]:
|
||||
root@delta:/etc/openvpn/easy-rsa#
|
||||
|
||||
在我们的实例中,所有问题的答案都选择了默认的。在运行了build-ca脚本后,我们就获得了主证书文件(keys/ca.crt)和对应的私钥(keys/ca.key)。私钥必须不计代价的保密。
|
||||
在我们的例子中,所有问题的答案都选择了默认的。在运行了build-ca脚本后,我们就获得了主证书文件(keys/ca.crt)和对应的私钥(keys/ca.key)。私钥必须不计代价的保密。
|
||||
|
||||
### 第三步 -- 生成OpenVPN服务器的证书和私钥 ###
|
||||
### 第三步 生成OpenVPN服务器的证书和私钥 ###
|
||||
|
||||
在我们为OpenVPN服务器生成证书和密钥之前,我们得给他起个名。我决定把它叫"delta",然后运行build-key-server脚本来获取证书和密钥:
|
||||
在我们为OpenVPN服务器生成证书和密钥之前,我们得给他起个名。我决定把它叫"delta",然后运行build-key-server脚本来获取证书和密钥:
|
||||
|
||||
root@delta:/etc/openvpn/easy-rsa# sh build-key-server delta
|
||||
Generating a 1024 bit RSA private key
|
||||
@ -145,11 +144,11 @@
|
||||
Data Base Updated
|
||||
root@delta:/etc/openvpn/easy-rsa#
|
||||
|
||||
当脚本成功运行完的时候,我们就得到了服务器的证书(keys/delta.crt)和私钥(keys/delta.key)。注意服务器证书被CA的私钥签名了。
|
||||
当脚本成功运行完的时候,我们就得到了服务器的证书(keys/delta.crt)和私钥(keys/delta.key)。注意服务器证书被CA的私钥签名了。
|
||||
|
||||
### 第四步 -- 生成Diffie-Hellman参数 ###
|
||||
### 第四步 生成Diffie-Hellman参数 ###
|
||||
|
||||
幸亏有了Diffie-Hellman参数,我们才能在不安全的通信通道里安全的交换密钥。为了生成它我们需要键入:
|
||||
幸亏有了Diffie-Hellman参数,我们才能在不安全的通信通道里安全的交换密钥。为了生成它我们需要键入:
|
||||
|
||||
root@delta:/etc/openvpn/easy-rsa# sh build-dh
|
||||
Generating DH parameters, 2048 bit long safe prime, generator 2
|
||||
@ -162,7 +161,7 @@
|
||||
.......................................++*++*++*
|
||||
root@delta:/etc/openvpn/easy-rsa#
|
||||
|
||||
证书,私钥和包含Diffie-Hellman参数的文件已生成,它们都储存在/etc/openvpn/easy-rsa/keys,所以我们到现在为止已经有如下五个文件了:
|
||||
证书,私钥和包含Diffie-Hellman参数的文件已生成,它们都储存在/etc/openvpn/easy-rsa/keys,所以我们到现在为止已经有如下五个文件了:
|
||||
|
||||
1. **ca.crt** – 证书颁发机构(CA)的证书
|
||||
2. **ca.key** – CA的私钥
|
||||
@ -177,9 +176,9 @@
|
||||
root@delta:/etc/openvpn/easy-rsa/keys# cd ..
|
||||
root@delta:/etc/openvpn/easy-rsa#
|
||||
|
||||
### 第五步 -- 为OpenVPN客户端生成证书和私钥 ###
|
||||
### 第五步 为OpenVPN客户端生成证书和私钥 ###
|
||||
|
||||
试想我们的笔记本要连接OpenVPN服务器。为了实现这个很常见的情况,我们首先需要为客户端(比如:我们的笔记本)生成证书和私钥,在/etc/openvpn/easy-rsa有一个脚本帮我们完成这项工作:
|
||||
试想我们的笔记本要连接OpenVPN服务器。为了实现这个很常见的情况,我们首先需要为客户端(比如:我们的笔记本)生成证书和私钥,在/etc/openvpn/easy-rsa有一个脚本帮我们完成这项工作:
|
||||
|
||||
root@delta:/etc/openvpn/easy-rsa# source vars
|
||||
NOTE: If you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/keys
|
||||
@ -229,7 +228,7 @@
|
||||
Data Base Updated
|
||||
root@delta:/etc/openvpn/easy-rsa#
|
||||
|
||||
我们为密钥选取的名字是"laptop",当build-key脚本运行完之后,我们就得到了在keys/laptop.crt的证书和在keys/laptop.key的私钥。有了这两个文件和CA的证书,我们得把这三个文件拷贝到用户有(比如用户sub0)权访问的地方。比如我们可以在用户的home目录中新建一个目录并把三个文件拷贝过去:
|
||||
我们为密钥选取的名字是"laptop",当build-key脚本运行完之后,我们就得到了在keys/laptop.crt的证书和在keys/laptop.key的私钥。有了这两个文件和CA的证书,我们得把这三个文件拷贝到用户有(比如用户sub0)权访问的地方。比如我们可以在用户的home目录中新建一个目录并把三个文件拷贝过去:
|
||||
|
||||
root@delta:/etc/openvpn/easy-rsa# mkdir /home/sub0/ovpn-client
|
||||
root@delta:/etc/openvpn/easy-rsa# cd keys
|
||||
@ -238,11 +237,11 @@
|
||||
root@delta:/etc/openvpn/easy-rsa/keys# cd ..
|
||||
root@delta:/etc/openvpn/easy-rsa#
|
||||
|
||||
ovpn-client文件夹必须安全的拷贝到我们的笔记本电脑上。我们可以给多个客户端分发这三个文件。当然了,等我们需要一个不一样的证书-私钥对的时候只要再次运行build-key脚本即可。
|
||||
ovpn-client文件夹必须安全的拷贝到我们的笔记本电脑上。我们可以给多个客户端分发这三个文件。当然了,等我们需要一个不一样的证书-私钥对的时候只要再次运行build-key脚本即可。
|
||||
|
||||
### 第六步 -- OpenVPN服务器设置 ###
|
||||
|
||||
等会我们的OpenVPN服务器就要启动并运行了。但是开始的时候,我们需要更改一些设置。在/usr/share/doc/openvpn/examples/sample-config-files中有一个示例配置文件,它很适合我们的教程,这个文件叫server.conf.gz:
|
||||
等会我们的OpenVPN服务器就要启动并运行了。但是开始的时候,我们需要更改一些设置。在/usr/share/doc/openvpn/examples/sample-config-files中有一个示例配置文件,它很适合我们的教程,这个文件叫server.conf.gz:
|
||||
|
||||
root@delta:/etc/openvpn/easy-rsa# cd /etc/openvpn
|
||||
root@delta:/etc/openvpn# cp /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz .
|
||||
@ -250,18 +249,18 @@ ovpn-client文件夹必须安全的拷贝到我们的笔记本电脑上。我们
|
||||
root@delta:/etc/openvpn# mv server.conf delta.conf
|
||||
root@delta:/etc/openvpn#
|
||||
|
||||
如你所见,我们把server.conf.gz拷贝到/etc/openvpn,解压并重命名到delta.conf。你可以按个人喜好给OpenVPN服务器配置文件取名字,但是它必须有".conf"扩展名。我们现在用nano打开配置文件:
|
||||
如你所见,我们把server.conf.gz拷贝到/etc/openvpn,解压并重命名到delta.conf。你可以按个人喜好给OpenVPN服务器配置文件取名字,但是它必须有".conf"扩展名。我们现在用nano打开配置文件:
|
||||
|
||||
root@delta:/etc/openvpn# nano delta.conf
|
||||
|
||||
下面是我们应该做出的更改。
|
||||
|
||||
- 首先,定位到这一行
|
||||
- 首先,定位到这一行
|
||||
|
||||
cert server.crt
|
||||
key server.key
|
||||
|
||||
确认OpenVPN服务器证书和私钥的位置和名称,在我们的例子中,这两行要改成
|
||||
确认OpenVPN服务器证书和私钥的位置和名称,在我们的例子中,这两行要改成
|
||||
|
||||
cert delta.crt
|
||||
key delta.key
|
||||
@ -274,18 +273,18 @@ ovpn-client文件夹必须安全的拷贝到我们的笔记本电脑上。我们
|
||||
|
||||
dh dh2048.pem
|
||||
|
||||
- 在配置文件的末尾,我们添加下面这两行:
|
||||
- 在配置文件的末尾,我们添加下面这两行:
|
||||
|
||||
push "redirect-gateway def1"
|
||||
push "dhcp-option DNS 10.8.0.1"
|
||||
|
||||
最后这两行指示客户端用OpenVPN作为默认的网关,并用10.8.0.1作为DNS服务器。注意10.8.0.1是OpenVPN启动时自动创建的隧道接口的IP。如果客户用别的域名解析服务,那么我们就得提防不安全的DNS服务器。为了避免这种泄露,我们建议所有OpenVPN客户端使用10.8.0.1作为DNS服务器。
|
||||
最后这两行指示客户端用OpenVPN作为默认的网关,并用10.8.0.1作为DNS服务器。注意10.8.0.1是OpenVPN启动时自动创建的隧道接口的IP。如果客户用别的域名解析服务,那么我们就得提防不安全的DNS服务器。为了避免这种泄露,我们建议所有OpenVPN客户端使用10.8.0.1作为DNS服务器。
|
||||
|
||||
我们以这种方式来开始运行OpenVPN服务器:
|
||||
|
||||
root@delta:/etc/openvpn# service openvpn start
|
||||
|
||||
默认的,OpenVPN服务器监听1194/UDP端口。一种查看的方法是使用netstat工具:
|
||||
默认的,OpenVPN服务器监听1194/UDP端口。一种查看的方法是使用netstat工具:
|
||||
|
||||
root@delta:/etc/openvpn# netstat -anup
|
||||
Active Internet connections (servers and established)
|
||||
@ -297,11 +296,11 @@ ovpn-client文件夹必须安全的拷贝到我们的笔记本电脑上。我们
|
||||
udp6 0 0 :::60622 :::* 555/dhclient
|
||||
udp6 0 0 :::53 :::* 2756/dnsmasq
|
||||
|
||||
看起来一切运行的不错,但是我们还没设置DNS服务器呢。
|
||||
看起来一切运行的不错,但是我们还没设置DNS服务器呢。
|
||||
|
||||
### 第七步 -- 为OpenVPN客户端搭建DNS ###
|
||||
### 第七步 为OpenVPN客户端搭建DNS ###
|
||||
|
||||
这就是为什么我们要安装dnsmasq,打开它的配置文件。
|
||||
这就是为什么我们要安装dnsmasq的原因,打开它的配置文件。
|
||||
|
||||
root@delta:/etc/openvpn# nano /etc/dnsmasq.conf
|
||||
|
||||
@ -321,13 +320,13 @@ ovpn-client文件夹必须安全的拷贝到我们的笔记本电脑上。我们
|
||||
|
||||
bind-interfaces
|
||||
|
||||
为了让dnsmasq应用这些更改,我们重启它:
|
||||
为了让dnsmasq应用这些更改,我们重启它:
|
||||
|
||||
root@delta:/etc/openvpn# service dnsmasq restart
|
||||
* Restarting DNS forwarder and DHCP server dnsmasq [ OK ]
|
||||
root@delta:/etc/openvpn#
|
||||
|
||||
现在,dnamasq在本地回环(lo)和隧道(tun0)接口监听DNS请求。netstat的输出看起来是这个样子的:
|
||||
现在,dnamasq在本地回环(lo)和隧道(tun0)接口监听DNS请求。netstat的输出看起来是这个样子的:
|
||||
|
||||
root@delta:/etc/openvpn# netstat -anup
|
||||
Active Internet connections (servers and established)
|
||||
@ -339,13 +338,13 @@ ovpn-client文件夹必须安全的拷贝到我们的笔记本电脑上。我们
|
||||
udp 0 0 0.0.0.0:68 0.0.0.0:* 638/dhclient
|
||||
udp6 0 0 :::39148 :::* 638/dhclient
|
||||
|
||||
### 第八步 -- 路由功能 ###
|
||||
### 第八步 路由功能 ###
|
||||
|
||||
我们希望在一些"盒子"或虚拟机上运行的OpneVPN有路由的功能,这意味着要开启IP转发.为了打开它,我们用root账户键入:
|
||||
我们希望在一些机器或虚拟机上运行的OpneVPN有路由的功能,这意味着要开启IP转发。为了打开它,我们用root账户键入:
|
||||
|
||||
root@delta:/etc/openvpn# echo "1" > /proc/sys/net/ipv4/ip_forward
|
||||
|
||||
为了让这个设置重启也好用,我们编辑 /etc/sysctl.conf:
|
||||
为了让这个设置重启也好用,我们编辑 /etc/sysctl.conf:
|
||||
|
||||
root@delta:/etc/openvpn# nano /etc/sysctl.conf
|
||||
|
||||
@ -365,7 +364,7 @@ ovpn-client文件夹必须安全的拷贝到我们的笔记本电脑上。我们
|
||||
root@delta:/etc/openvpn# iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
|
||||
root@delta:/etc/openvpn#
|
||||
|
||||
当然了,我们希望每次Ubuntu启动的时候,这些规则都好用。所以我们得把它们加到/etc/rc.local里:
|
||||
当然了,我们希望每次Ubuntu启动的时候,这些规则都好用。所以我们得把它们加到/etc/rc.local里:
|
||||
|
||||
#!/bin/sh -e
|
||||
#
|
||||
@ -393,11 +392,11 @@ ovpn-client文件夹必须安全的拷贝到我们的笔记本电脑上。我们
|
||||
|
||||
service dnsmasq restart
|
||||
|
||||
> 这非常重要:在系统启动时,dnsmasq会尝试在OpenVPN之前启动。但是OpenVPN启动之前是没有隧道(tun0)接口的,所以dnsmasq自然就挂了。过了一阵,当/etc/rc.local读到隧道(tun0)接口出现时,它会在这时重启dnsmasq然后就一切如你所愿了。
|
||||
> 这非常重要:在系统启动时,dnsmasq会尝试在OpenVPN之前启动。但是OpenVPN启动之前是没有隧道(tun0)接口的,所以dnsmasq自然就挂了。过了一阵,当/etc/rc.local读到隧道(tun0)接口出现时,它会在这时重启dnsmasq然后就一切如你所愿了。
|
||||
|
||||
### 第九步 -- 客户端设置 ###
|
||||
### 第九步 客户端设置 ###
|
||||
|
||||
在第五步,我们在用户的home目录里我们建立了ovpn-client文件夹(在我们的例子里是/home/sub0)。在哪里有CA的证书和客户端证书和私钥。现在只缺客户端配置文件了,在/usr/share/doc/openvpn/examples/sample-config-files有一个示例配置文件:
|
||||
在第五步,我们在用户的home目录里我们建立了ovpn-client文件夹(在我们的例子里是/home/sub0)。在哪里有CA的证书和客户端证书和私钥。现在只缺客户端配置文件了,在/usr/share/doc/openvpn/examples/sample-config-files有一个示例配置文件:
|
||||
|
||||
root@delta:/etc/openvpn# exit
|
||||
exit
|
||||
@ -405,19 +404,19 @@ service dnsmasq restart
|
||||
sub0@delta:~/ovpn-client$ cp /usr/share/doc/openvpn/examples/sample-config-files/client.conf .
|
||||
sub0@delta:~/ovpn-client$
|
||||
|
||||
我们编需要辑client.conf,定位到这一行:
|
||||
我们需要编辑client.conf,定位到这一行:
|
||||
|
||||
remote my-server-1 1194
|
||||
|
||||
"my-server-1"是一个占位符,现在我们要把它换成我们自己服务器的公网域名或IP。如果我们已经给服务器分配域名了,那只要把它填到my-server-1的位置。如果没有域名,那么得获取公网IP。如何获取呢?一种方式是键入下列命令:
|
||||
"my-server-1"是一个占位符,现在我们要把它换成我们自己服务器的公网域名或IP。如果我们已经给服务器分配域名了,那只要把它填到my-server-1的位置。如果没有域名,那么得获取公网IP。如何获取呢?一种方式是键入下列命令:
|
||||
|
||||
sub0@delta:~/ovpn-client$ curl ipecho.net/plain ; echo
|
||||
|
||||
(如果不是一个数字的IP地址, 或是发生错误,那就等会再试。)所以我们现在知道我们的服务器公网IP了,但是它是动态的还是静态的呢?当我们把服务器架设在家或者办公室的时候,极有可能就是动态IP。如果是动态IP的话,可以用免费的动态域名服务(DDNS),比如[No-IP](http://www.noip.com)的服务。如果使用No-IP,假设我们选择了免费的域名dnsalias.net,那么这一行应该像这样填写:
|
||||
(如果不是一个数字的IP地址, 或是发生错误,那就等会再试。)所以我们现在知道我们的服务器公网IP了,但是它是动态的还是静态的呢?当我们把服务器架设在家或者办公室的时候,极有可能就是动态IP。如果是动态IP的话,可以用免费的动态域名服务(DDNS),比如[No-IP](http://www.noip.com)的服务。如果使用No-IP,假设我们选择了免费的域名dnsalias.net,那么这一行应该像这样填写:
|
||||
|
||||
remote ovpn.dnsalias.net 1194
|
||||
|
||||
"ovpn"是我们给服务器起的主机名。如果我们的服务器在云上,那么它可能有一个静态IP。如果有静态IP的话,那么这一行应该是这样的:
|
||||
"ovpn"是我们给服务器起的主机名。如果我们的服务器在云上,那么它可能有一个静态IP。如果有静态IP的话,那么这一行应该是这样的:
|
||||
|
||||
remote 1.2.3.4 1194
|
||||
|
||||
@ -426,56 +425,56 @@ service dnsmasq restart
|
||||
cert client.crt
|
||||
key client.key
|
||||
|
||||
在我们的例子里,客户端的证书和密钥的名字分别是laptop.crt和laptop.key所以我们的client.conf要包含下面这两行:
|
||||
在我们的例子里,客户端的证书和密钥的名字分别是laptop.crt和laptop.key所以我们的client.conf要包含下面这两行:
|
||||
|
||||
cert laptop.crt
|
||||
key laptop.key
|
||||
|
||||
在确认保存client.conf的修改之后,我们需要安全的把整个ovpn-client文件夹传输到客户端。一种方式是使用scp命令(安全拷贝或在SSH上拷贝)。另一种方式由优秀而免费的软件FileZilla提供,使用在SSH上运行的FTP(SFTP)。
|
||||
在确认保存client.conf的修改之后,我们需要安全的把整个ovpn-client文件夹传输到客户端。一种方式是使用scp命令(安全拷贝或在SSH上拷贝)。另一种方式由优秀而免费的软件FileZilla提供,使用在SSH上运行的FTP(SFTP)。
|
||||
|
||||
### 第十步 -- 连接并测试 ###
|
||||
### 第十步 连接并测试 ###
|
||||
|
||||

|
||||
|
||||
|
||||
所以我们到底怎么样才能链接到远程的OpenVPN服务器的呢?它完全取决于我们手中现有的设备类型,当然也取决于所运行的操作系统。我们将在四种不同类别的操作系统上运行,Linux, Windows, OS X和iOS/Android。注意,无论在什么设备和系统上,我们都得在OpenVPN服务器的本地网络外才能连接成功。此外,如果在服务器前有防火墙,我们需要增加一条这样的规则:
|
||||
所以我们到底怎么样才能链接到远程的OpenVPN服务器的呢?它完全取决于我们手中现有的设备类型,当然也取决于所运行的操作系统。我们将在四种不同类别的操作系统上运行,Linux, Windows, OS X和iOS/Android。注意,无论在什么设备和系统上,我们都得在OpenVPN服务器的本地网络外才能连接成功。此外,如果在服务器前有防火墙,我们需要增加一条这样的规则:
|
||||
|
||||
*把所有从1194/UDP端口收到的包转发到服务器公网接口的1194/UDP端口。*
|
||||
|
||||
这是一个简单的防火墙规则。事不宜迟,让我们与我们难以置信的OpenVPN服务器建立第一个连接吧。
|
||||
这是一个简单的防火墙规则。事不宜迟,让我们与我们难以置信的OpenVPN服务器建立第一个连接吧。
|
||||
|
||||
**Linux**: 我们只需安装openvpn包。一种连接远程OpenVPN服务器的方式是新建一个终端,切换到ovpn-client文件夹并以root身份或使用sudo来键入下列命令:
|
||||
**Linux**: 我们只需安装openvpn包。一种连接远程OpenVPN服务器的方式是新建一个终端,切换到ovpn-client文件夹并以root身份或使用sudo来键入下列命令:
|
||||
|
||||
/usr/sbin/openvpn --config client.conf
|
||||
|
||||
任何时候,如果我们需要终止OpenVPN,按[CTRL+C]就行了。
|
||||
任何时候如果我们需要终止OpenVPN,按[CTRL+C]就行了。
|
||||
|
||||
**Windows**: 有一个免费的OpenVPN客户端软件叫做[OpenVPN Desktop Client][3]。 配置文件client.conf需要重命名成client.ovpn,这就是我们需要提供给OpenVPN Desktop Client的文件。程序会读取client.ovpn并给OpenVPN服务器生成一个新的连接配置。
|
||||
**Windows**: 有一个免费的OpenVPN客户端软件叫做[OpenVPN Desktop Client][3]。 配置文件client.conf需要重命名成client.ovpn,这就是我们需要提供给OpenVPN Desktop Client的文件。程序会读取client.ovpn并给OpenVPN服务器生成一个新的连接配置。
|
||||
|
||||

|
||||
|
||||
**OS X**: [tunnelblick][4]是一款可以连接OpenVPN的免费开源OS X软件。[Viscosity][5]也可以但它是商业软件,不过我们喜欢。Viscosity会读取client.conf并给OpenVPN服务器生成一个新的连接配置。
|
||||
**OS X**: [tunnelblick][4]是一款可以连接OpenVPN的免费开源OS X软件。[Viscosity][5]也可以但它是商业软件,不过我们喜欢。Viscosity会读取client.conf并给OpenVPN服务器生成一个新的连接配置。
|
||||
|
||||
**iOS/Android**: OpenVPN connect是绝佳的选择。它是免费的且可以从[App Store][6]和[Google Play store][7]获得
|
||||
|
||||
不管是什么平台,有时我们想检验我们是否真的使用OpenVPN连接了。一种检验方法是完成下面这简单的4步:
|
||||
不管是什么平台,有时我们想检验我们是否真的使用OpenVPN连接了。一种检验方法是完成下面这简单的4步:
|
||||
|
||||
在连接到OpenVPN服务器前我们需要…
|
||||
|
||||
- 打开[whatip.com][8]记录我们的公网IP
|
||||
- 打开[dnsleaktest.com][10],运行标准测试(standard test),记录我们的域名解析服务器
|
||||
- 打开[dnsleaktest.com][10],运行标准测试(standard test),记录我们的域名解析服务器
|
||||
|
||||

|
||||
|
||||
在连接到OpenVPN服务器后重复这两部。如果我们获取到两个不同的公网IP,这意味着我们的网络出口已在远端OpenVPN服务器那。此外,如果获取了两个不同的域名解析服务器,那么就不存在DNS泄露的问题了。
|
||||
在连接到OpenVPN服务器后重复这两部。如果我们获取到两个不同的公网IP,这意味着我们的网络出口已在远端OpenVPN服务器那。此外,如果获取了两个不同的域名解析服务器,那么就不存在DNS泄露的问题了。
|
||||
|
||||
### 感言 ###
|
||||
|
||||
我用三个不同的OpenVPN服务器,都是定制的。 一个运行在希腊Thessaloniki的家庭办公室的pfSense路由。当我不在办公室时,我用这个服务器安全的连接到局域网。剩下的两个服务器在两个不同的VPS上,一个在冰岛雷克雅未克,另一个在美国纽泽西州。当我在外且需要任意用一个WiFi热点的时候,我不必考虑安全问题:我只需简单的连接到雷克雅未克的服务器然后正常上网。有时我想看看限制用户地理位置在美国的服务。在这种不太常见的情况下,新泽西的服务器就派上用场了,当我连接时,我就获得了美国的一个公网IP,这样就可以访问有地理位置限制的服务了。值得注意的是,一些服务会把一些知名的VPN公司的IP列入黑名单。这是在你选的VPS提供商建立自己的OpenVPN*十分重要*的一个优点:这不大可能被列入黑名单.
|
||||
我用了三个不同的OpenVPN服务器,都是定制的。 一个运行在希腊Thessaloniki的家庭办公室的pfSense路由。当我不在办公室时,我用这个服务器安全的连接到局域网。剩下的两个服务器在两个不同的VPS上,一个在冰岛雷克雅未克,另一个在美国纽泽西州。当我在外面且需要任意用一个WiFi热点的时候,我不必考虑安全问题:我只需简单的连接到雷克雅未克的服务器然后正常上网。有时我想看看那些限制用户地理位置在美国的服务。在这种不太常见的情况下,新泽西的服务器就派上用场了,当我连接时,我就获得了美国的一个公网IP,这样就可以访问有地理位置限制的服务了。值得注意的是,一些服务会把一些知名的VPN公司的IP列入黑名单。这是在你选的VPS提供商建立自己的OpenVPN*十分重要*的一个优点:这不大可能被列入黑名单。
|
||||
|
||||
无论你的物理位置在哪, OpenVPN确保客户端和服务器之间的数据流是高度加密的。没有OpenVPN的数据则是另一种情况。 取决于不同的应用层协议,它可能仍然是加密的,但它也可能是未加密的。所以除非你对OpenVPN服务器和它的本地网络有绝对的控制权,你不能完全相信另一端的管理员。这种精神是显而易见的:如果你真的在乎你自己的隐私,那么你需要注意你的行为可能在破坏它。
|
||||
无论你的物理位置在哪, OpenVPN确保客户端和服务器之间的数据流是高度加密的。没有OpenVPN的数据则是另一种情况。 取决于不同的应用层协议,它可能仍然是加密的,但它也可能是未加密的。所以除非你对OpenVPN服务器和它的本地网络有绝对的控制权,你不能完全相信另一端的管理员。这种精神是显而易见的:如果你真的在乎你自己的隐私,那么你需要注意你的行为可能在破坏它。
|
||||
|
||||
一个例子是我们有希望点对点传输。我们有一个在云上配置好的OpenVPN服务器。当需要任意用一个WiFi热点的时候,你没有丝毫的担心,因为你连在OpenVPN服务器上。然后你打开你最喜欢的电子邮件客户端从一个依然使用SMTP的老服务器收信。你猜会发生什么?你的用户名和密码以未加密的纯文本格式离开OpenVPN服务器。与此同时一个在你OpenVPN服务器附近的带宽管理员很容易就嗅探出你的证书并记录到他们越来越长的名叫"random happy people.txt"的列表。
|
||||
一个例子是我们希望点对点传输。我们有一个在云上配置好的OpenVPN服务器。当需要任意用一个WiFi热点的时候,你没有丝毫的担心,因为你连在OpenVPN服务器上。然后你打开你最喜欢的电子邮件客户端从一个依然使用SMTP的老服务器收信。你猜会发生什么?你的用户名和密码以未加密的纯文本格式离开OpenVPN服务器。与此同时一个在你OpenVPN服务器附近的鬼鬼祟祟的管理员很容易就嗅探出你的证书并记录到他们越来越长的名叫"random happy people.txt"的列表。
|
||||
|
||||
所以你该做什么?很简单。你应该继续使用OpenVPN服务器,但不要使用应用了旧的或不安全的协议的应用程序。
|
||||
|
||||
@ -485,7 +484,7 @@ service dnsmasq restart
|
||||
|
||||
via: http://parabing.com/2014/06/openvpn-on-ubuntu/
|
||||
|
||||
译者:[2q1w2007](https://github.com/2q1w2007) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[2q1w2007](https://github.com/2q1w2007) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,45 @@
|
||||
GIMP 2.8.12 Released — Here’s How to Install it on Ubuntu
|
||||
================================================================================
|
||||
**A [new update][1] to the popular open-source Photoshop alternative The GIMP is now available for download.**
|
||||
|
||||

|
||||
GIMP is a Free Photoshop Alternative
|
||||
|
||||
As the latest entry in the GIMP 2.8.x series — [released back in 2012][2] and notable for introducing the long-sought ‘single window mode’ — version 2.8.12 continues to refine rather than reinvent. As such there are no new user-facing features to be found.
|
||||
|
||||
Instead, developers bring a fresh batch of bug fixes to the table aimed at improving the overall stability, security and style of the famous app.
|
||||
|
||||
- Brush sizes from plugins are no longer distorted
|
||||
- ‘More robust’ loading of .XCF files
|
||||
- Widget direction now matches interface language (e.g. RTL)
|
||||
- Security improvements to the script-fu-server
|
||||
|
||||
Documentation, help and translation updates are also included. For a complete change log of everything fixed between 2.8.10 and 2.8.12, see [the GNOME Git notes][2].
|
||||
|
||||
### Install Latest GIMP in Ubuntu ###
|
||||
|
||||
Source for the latest release can be downloaded from the official website or via [an official torrent][3].
|
||||
|
||||
On Ubuntu? You can install GIMP 2.8.12 in Ubuntu 12.04 LTS and 14.04 LTS by adding the [following third-party PPA][4] to Software Sources:
|
||||
|
||||
sudo add-apt-repository ppa:otto-kesselgulasch/gimp
|
||||
|
||||
sudo apt-get update && sudo apt-get install gimp
|
||||
|
||||
After installation has complete you can proceed to open GIMP 2.8.12 from the Unity Dash (or equivalent).
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/08/whats-new-in-gimp-2-8-12-plus-install-ubuntu
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.omgubuntu.co.uk/2012/05/gimp-2-8-released
|
||||
[2]:https://git.gnome.org/browse/gimp/plain/NEWS?h=gimp-2-8
|
||||
[3]:http://download.gimp.org/pub/gimp/v2.8/gimp-2.8.12.tar.bz2.torrent
|
||||
[4]:https://launchpad.net/~otto-kesselgulasch/+archive/ubuntu/gimp
|
||||
@ -0,0 +1,31 @@
|
||||
Red Hat Shake-up, Desktop Users, and Outta Time
|
||||
================================================================================
|
||||

|
||||
|
||||
Our top story tonight is the seemingly sudden resignation of Red Hat CTO Brian Stevens. In other news, John C. Dvorak says "Linux has run out of time" and Infoworld.com says there may be problems with Red Hat Enterprise 7. OpenSource.com has a couple of interesting interviews and Nick Heath has five big names that use Linux on the desktop.
|
||||
|
||||
**In a late afternoon** [press release][1], Red Hat announced the resignation of long-time CTO Brian Stevens. Paul Cormier will be handling CTO duties until Stevens' replacement is named. No reason for the sudden resignation was given although CEO Whitehurst said, "We want to thank Brian for his years of service and numerous contributions to Red Hat’s business. We wish him well in his future endeavors." However, Steven J. Vaughan-Nichols says some rumors are flying. One says friction between Stevens and Cormier caused the resignation and others say Stevens had higher ambitions than Red Hat could provide. He'd been with Red Hat since 2001 and had been CTO at Mission Critical Linux before that [according to Vaughan-Nichols][2] who also said Stevens' Red Hat page was gone within seconds of the announcement.
|
||||
|
||||
**Speaking of Red Hat**, InfoWorld.com has a review of RHEL 7 available to the general public today. Reviewer Paul Venezia runs down the new features, but soon mentions systemd as one of the many new features "certain to cause consternation." After offering his opinion on several other key features and even throwing in a tip or two, [Venezia concludes][3], "RHEL 7 is a fairly significant departure from the expected full-revision release from Red Hat. This is not merely a reskinning of the previous release with updated packages, a more modern kernel, and some new toolkits and widgets. This is a very different release than RHEL 6 in any form, mostly due to the move to Systemd."
|
||||
|
||||
**Our own Sam Dean** [today said][4] that Linux doesn't need to own the desktop because of its success in many other key areas. While that may be true, Nick Heath today listed "five big names that use Linux on the desktop." He said besides Munich, there's Google for one and they even have their own Ubuntu derivative. He lists a couple of US government agencies and then mentions CERN and others. See that [full story][5] for more.
|
||||
|
||||
Despite that feel-good report, John C. Dvorak said he's tired of waiting for someone to develop that one "killer app" that would bring in the masses or satisfy his needs. [He says][6] he has to make podcasts and "photographic art" and he just can't do that with Linux. Our native applications "do not cut it in the end."
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ostatic.com/blog/red-hat-shake-up-desktop-users-and-outta-time
|
||||
|
||||
作者:[Susan Linton][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ostatic.com/member/susan-linton
|
||||
[1]:http://www.businesswire.com/news/home/20140827006134/en/Brian-Stevens-Step-CTO-Red-Hat#.U_5AlvFdX0p
|
||||
[2]:http://www.zdnet.com/red-hat-chief-technology-officer-resigns-7000033058/
|
||||
[3]:http://www.infoworld.com/d/data-center/review-rhel-7-lands-jolt-249219
|
||||
[4]:http://ostatic.com/blog/linux-doesnt-need-to-own-the-desktop
|
||||
[5]:http://www.techrepublic.com/article/five-big-names-that-use-linux-on-the-desktop/
|
||||
[6]:http://www.pcmag.com/article2/0,2817,2465125,00.asp
|
||||
@ -1,3 +1,5 @@
|
||||
chi1shi2 is translating.
|
||||
|
||||
China Will Change The Way All Software Is Bought And Sold
|
||||
================================================================================
|
||||

|
||||
|
||||
@ -1,51 +0,0 @@
|
||||
Linus Torvalds is my hero, says 13 year old Zachary DuPont
|
||||
================================================================================
|
||||

|
||||
|
||||
Zachary DuPon is a 6th grader who will turn 13 years old soon. He used to be an Arch Linux user and is looking forward to installing Gentoo Linux soon.
|
||||
|
||||
The story of Zach goes like this – his school organized a project where students were asked to write a letter to their heroes, while most kids wrote to celebrities, Zach wrote to the ‘real’ hero of the modern technology world – Linus Torvalds.
|
||||
|
||||
Since Linus works from home he doesn’t disclose his ‘work’ address, so Zach’s letter went to The Linux Foundation, which scans all letters before sending them to Linus. When the foundation saw this letter they contacted Zach’s school and, being as generous as they are, invited him to LinuxCon so that he could meet his hero in person.
|
||||
|
||||
Jim Zemlin, the executive director of the Linux Foundation, introduced Zach to the crowd right after the keynote panel discussion. Zach met Linus and got his Linux Bible signed by the father of Linux; he also received a signed copy of Linus’ own book [Just for Fun: The Story of an Accidental Revolutionary][1]
|
||||
|
||||

|
||||
Linus Torvalds signing a book for Zachary DuPont
|
||||
|
||||

|
||||
The DuPont family
|
||||
|
||||

|
||||
Swapnil Bhartiya with Zachary DuPont
|
||||
|
||||
I didn’t want to miss this opportunity so I approached the DuPont family as soon as they finished talking to Linus and arranged this video interview. I am a father of a 2 year old son and as a father, I was truly amazed how confident, articulate and clear Zach is in his thoughts.
|
||||
|
||||
Instead of me telling you what all we discussed, I am offering you this video interview.
|
||||
|
||||
注:Youtube 视频,发布的时候不行改成一个链接吧
|
||||
<iframe scrolling="no" frameborder="0" allowfullscreen="" mozallowfullscreen="" webkitallowfullscreen="" src="//www.youtube-nocookie.com/embed/pHK5mfLdmRs?autoplay=0" class="arve-inner"></iframe>
|
||||
|
||||
Here is some trivia from the interview:
|
||||
|
||||
- He used Arch Linux once
|
||||
- He plans to contribute once he becomes good at programming
|
||||
- He hasn’t filed any bug reports and thinks he should. He also said that he didn’t come across any bugs
|
||||
- He is not a huge fan of WINE
|
||||
- He likes KDE’s Plasma desktop, but it doesn’t work well on his Gateway machine
|
||||
- He is a Debian GNU/Linux user with XFCE desktop environment
|
||||
|
||||
Linus may be Zach’s hero, but Zach is the hero of the entire GNU/Linux and Free Software community, who continues to remind us that our future is in great hands.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.themukt.com/2014/08/24/linus-torvalds-hero-says-13-years-old-zachary-dupont/
|
||||
|
||||
作者:[wapnil Bhartiya][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.themukt.com/author/swapnil_bhartiya/
|
||||
[1]:http://www.amazon.com/gp/product/0066620732/ref=as_li_tl?ie=UTF8&camp=1789&creative=9325&creativeASIN=0066620732&linkCode=as2&tag=muktware-20&linkId=HBKEBIFVZQC35GGK
|
||||
85
sources/talk/20140828 Interesting facts about Linux.md
Normal file
85
sources/talk/20140828 Interesting facts about Linux.md
Normal file
@ -0,0 +1,85 @@
|
||||
Interesting facts about Linux
|
||||
================================================================================
|
||||
Today, August, 25th, is the 23rd birthday of Linux. The modest [Usenet post][1] made by a 21 year old student at the University of Helsinki on August 25th, 1991, marks the birth of the venerable Linux as we know it today.
|
||||
|
||||
Fast forward 23 years, and now Linux is everywhere, not only installed on end user desktops, [smartphones][2] and embedded systems, but also fulfilling the needs of [leading enterprises][3] and powering mission-critical systems such as [US Navy's nuclear submarines][4] and [FAA's air traffic control][5]. Entering the era of ubiquitous cloud computing, Linux is continuing [its dominance][6] as by far the most popular platform for the cloud.
|
||||
|
||||
Celebrating the 23rd birthday of Linux today, let me show you **some interesting facts and history you may not know about Linux**. If there is anything to add, feel free to share it in the comments. In this article, I will use the terms "Linux", "kernel" or "Linux kernel" interchangeably to mean the same thing.
|
||||
|
||||
1. There is a never-ending debate on whether or not Linux is an operating system. Technically, the term "Linux" refers to the kernel, a core component of an operating system. Folks who argue that Linux is not an operating system are operating system purists who think that the kernel alone does not make the whole operating system, or free software ideologists who believe that the largest free operating system should be named "[GNU/Linux][7]" to give credit where credit is due (i.e., [GNU project][8]). On the other hand, some developers and programmers have a view that Linux qualifies as an operating system in a sense that it implements the [POSIX standard][9].
|
||||
|
||||
2. According to openhub.net, the majority (95%) of Linux is written in C language. The second popular language for Linux is assembly language (2.8%). The dominance of C lanaguage over C++ is no surprise given Linus's stance on C++. Here is the programming language breakdown for Linux.
|
||||
|
||||

|
||||
|
||||
3. Linux has been built by a total of [13,036 contributors][10] worldwide. The most prolific contributor is, of course, Linus Torvalds himself, who has committed code more than 20,000 times over the course of the lifetime of Linux. The following figures show the all-time top-10 contributors of Linux in terms of commit counts.
|
||||
|
||||

|
||||
|
||||
4. The total source lines of code (SLOC) of Linux is over 17 million. The estimated cost for the entire code base is 5,526 person-years, or over 300M USD according to [basic COCOMO model][11].
|
||||
|
||||
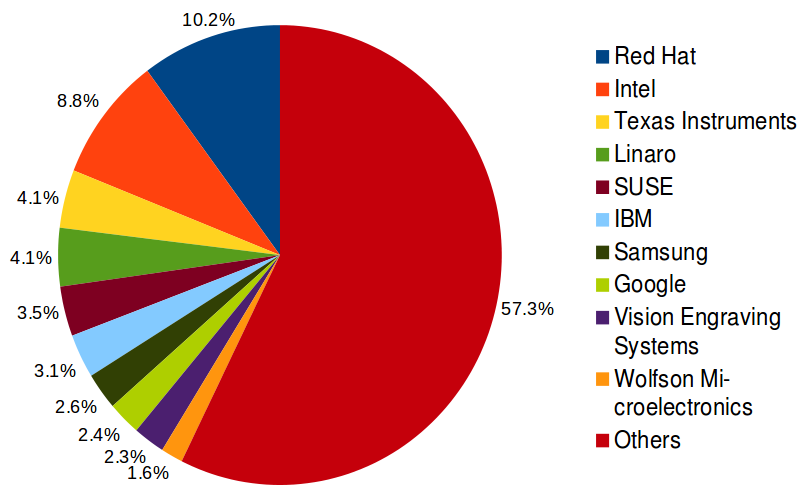
5. Enterprises have not been simply consumers of Linux. Their employees have been [actively participated][12] in the development of Linux. The figure below shows the top-10 corporate sponsors of Linux kernel development, in terms of total commit counts from their employees, as of year 2013. They include commercial Linux distributors (Red Hat, SUSE), chip/embedded system makers (Intel, Texas Instruments, Wolfson), non-profits (Linaro), and other IT power houses (IBM, Samsung, Google).
|
||||
|
||||
|
||||
|
||||
6. The official mascot of Linux is "Tux", a friendly penguin character. The idea of using a cuddly penguin as a mascot/logo was in fact [first conceived and asserted][13] by Linus himself. Why penguin? Personally Linus is fond of penguins, despite the fact that he once was bitten by a ferocious penguin, causing him infected with a disease.
|
||||
|
||||
7. A Linux "distribution" contains the Linux kernel, supporting GNU utilities/libraries, and other third-party applications. According to [distrowatch.com][14], there are a total of 286 actively maintained Linux distrutions. The oldest among them is [Slackware][15] whose very first release 1.0 became available in 1993.
|
||||
|
||||
8. Kernel.org, which is the main repository of Linux source code, was [compromised][16] by an unknown attacker in August, 2011, who managed to tamper with several kernel.org's servers. In an effort to tighten up access policies of the Linux kernel, Linux foundation recently [turned on][17] two-factor authentication at the official Git repositories hosting the Linux kernel.
|
||||
|
||||
9. The dominance of Linux on top 500 supercomputers [continues to rise][18]. As of June 2014, 97% of the world-fastest computers are powered by Linux.
|
||||
|
||||
10. Spacewatch, a research group of Lunar and Planetary Laboratory at the University of Arizona, named several asteroids ([9793 Torvalds][19], [9882 Stallman][20], [9885 Linux][21] and [9965 GNU][22]) after GNU/Linux and their creators, in recognition of the free operating system which was instrumental in their asteroid survey activities.
|
||||
|
||||
11. In the modern history of Linux kernel development, there was a big jump in kernel version: from 2.6 to 3.0. The [renumbering to version 3][23] actually did not signify any major restructuring in kernel code, but was simply to celebrate the 20 year milestone of the Linux kernel.
|
||||
|
||||
12. In 2000, Steve Jobs at Apple Inc. [tried to hire][24] Linus Torvalds to have him drop Linux development and instead work on "Unix for the biggest user base," which was OS X back then. Linus declined the offer.
|
||||
|
||||
13. The [reboot()][25] system call in the Linux kernel requires two magic numbers. The second magic number comes from the [birth dates][26] of Linus Torvalds and his three daughters.
|
||||
|
||||
14. With so many fans of Linux around the world, there are [criticisms][27] on current Linux distributions (mainly desktops), such as limited hardware support, lack of standardization, instability due to short upgrade/release cycles, etc. During the [Linux kernel panel][28] at LinuxCon 2014, Linus was quoted as saying "I still want the desktop" when asked where he thinks Linux should go next.
|
||||
|
||||
If you know any interesting facts about Linux, feel free to share them in the comments.
|
||||
|
||||
Happy birthday, Linux!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/08/interesting-facts-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:https://groups.google.com/forum/message/raw?msg=comp.os.minix/dlNtH7RRrGA/SwRavCzVE7gJ
|
||||
[2]:http://developer.android.com/about/index.html
|
||||
[3]:http://fortune.com/2013/05/06/how-linux-conquered-the-fortune-500/
|
||||
[4]:http://www.linuxjournal.com/article/7789
|
||||
[5]:http://fcw.com/Articles/2006/05/01/FAA-manages-air-traffic-with-Linux.aspx
|
||||
[6]:http://thecloudmarket.com/stats
|
||||
[7]:http://www.gnu.org/gnu/why-gnu-linux.html
|
||||
[8]:http://www.gnu.org/gnu/gnu-history.html
|
||||
[9]:http://en.wikipedia.org/wiki/POSIX
|
||||
[10]:https://www.openhub.net/p/linux/contributors/summary
|
||||
[11]:https://www.openhub.net/p/linux/estimated_cost
|
||||
[12]:http://www.linuxfoundation.org/publications/linux-foundation/who-writes-linux-2013
|
||||
[13]:http://www.sjbaker.org/wiki/index.php?title=The_History_of_Tux_the_Linux_Penguin
|
||||
[14]:http://distrowatch.com/search.php?ostype=All&category=All&origin=All&basedon=All¬basedon=None&desktop=All&architecture=All&status=Active
|
||||
[15]:http://www.slackware.com/info/
|
||||
[16]:http://pastebin.com/BKcmMd47
|
||||
[17]:http://www.linux.com/news/featured-blogs/203-konstantin-ryabitsev/784544-linux-kernel-git-repositories-add-2-factor-authentication
|
||||
[18]:http://www.top500.org/statistics/details/osfam/1
|
||||
[19]:http://ssd.jpl.nasa.gov/sbdb.cgi?sstr=9793
|
||||
[20]:http://ssd.jpl.nasa.gov/sbdb.cgi?sstr=9882
|
||||
[21]:http://ssd.jpl.nasa.gov/sbdb.cgi?sstr=9885
|
||||
[22]:http://ssd.jpl.nasa.gov/sbdb.cgi?sstr=9965
|
||||
[23]:https://lkml.org/lkml/2011/5/29/204
|
||||
[24]:http://www.wired.com/2012/03/mr-linux/2/
|
||||
[25]:http://lxr.free-electrons.com/source/kernel/reboot.c#L199
|
||||
[26]:http://www.nndb.com/people/444/000022378/
|
||||
[27]:http://linuxfonts.narod.ru/why.linux.is.not.ready.for.the.desktop.current.html
|
||||
[28]:https://www.youtube.com/watch?v=8myENKt8bD0
|
||||
@ -0,0 +1,32 @@
|
||||
Linux Doesn't Need to Own the Desktop
|
||||
================================================================================
|
||||
Linus Torvalds issued Linux 3.17 rc-2 on Monday of this week, and [he deviated from his normal schedule][1] in doing so, because August 25 happens to mark the 23rd anniversary of the original Linux announcement. "Hello everybody out there using minix," Torvalds wrote.
|
||||
|
||||
Meanwhile, PCMag.com has proclaimed that [Linux has run out of time][2]. But isn't it true that the endless discussions of whether Linux is a success on the desktop are moot? Linux is in supercomputers and cars, it formed the basis for Android and is the most popular platform to run emerging cloud platforms like OpenStack on--just to name a few of its successes. The desktop is not the only battleground for Linux.
|
||||
|
||||
Jon Buys took note of specialization and the Linux desktop [in a recent post][3], where he wrote:
|
||||
|
||||
> "Recently, IT World asked “[Does it still make sense for Linus to want the desktop for Linux?][4]”, and Matt Asay from Tech Repubic asked “[Can we please stop talking about the Linux desktop?][5]”. Both publishers are critical of the claim that there is still room for Linux on Personal Computers, and point to Android as a Linux success story...What both articles miss though is that the flexibility of Linux, and the permissiveness of its open source license may be the things that save Linux on the desktop."
|
||||
|
||||
That may be true, but Linux is so much to so many people beyond the desktop. Linux's opportunity for great market share on the desktop has come and gone.
|
||||
|
||||
The simple fact is that Linux has changed the world and been a tremendous success outside the desktop, and there is nothing wrong with that. Android is hardly the only Linux-based platform that has made a big mark. Linux is huge on servers, in embedded technology, and is a constant prompt for innovation on emerging platforms. Ubuntu is the most popular platform for building OpenStack deployments on. Supercomputers all over the world run Linux, and Chrome OS is based on it.
|
||||
|
||||
So Linux is making a huge difference globally, and it is time for detractors to stop focusing exclusively on its status on the desktop.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ostatic.com/blog/linux-doesnt-need-to-own-the-desktop
|
||||
|
||||
作者:[Sam Dean][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ostatic.com/member/samdean
|
||||
[1]:http://www.theregister.co.uk/2014/08/26/linux_turns_23_and_linus_torvalds_celebrates_as_only_he_can/
|
||||
[2]:http://www.pcmag.com/article2/0,2817,2465125,00.asp
|
||||
[3]:http://ostatic.com/blog/specialization-and-the-linux-desktop
|
||||
[4]:http://www.itworld.com/open-source/432816/does-it-still-make-sense-linus-want-desktop-linux
|
||||
[5]:http://www.techrepublic.com/article/can-we-please-stop-talking-about-the-linux-desktop/
|
||||
@ -1,112 +0,0 @@
|
||||
[translating by KayGuoWhu]
|
||||
How to remove file metadata on Linux
|
||||
================================================================================
|
||||
A typical data file often has associated "metadata" which is descriptive information about the file, represented in the form of a set of name-value pairs. Common metadata include creator's name, tools used to generate the file, file creation/update date, location of creation, editing history, etc. EXIF (images), RDF (web resources), DOI (digital documents) are some of popular metadata standards.
|
||||
|
||||
While metadata has its own merits in data management fields, it can actually affect your privacy [adversely][1]. EXIF data in photo images can reveal personally identifiable information such as your camera model, GPS coordinate of shooting, your favorite photo editor software, etc. Metadata in documents and spreadsheets contain author/affiliation information and other editing history. Not to be paranoid, but metadata gathering tools such as [metagoofil][2] are often exploited during information gathering stage as part of penetration testing.
|
||||
|
||||
For those of you who want to strip any personalizing metadata from any shared data, there are ways to remove metadata from data files. You can use existing document or image editor software which typically have built-in metadata editing capability. In this tutorial, let me introduce a nice standalone **metadata cleaner tool** which is developed for a single goal: **anonymize all metadata for your privacy**.
|
||||
|
||||
[MAT][3] (Metadata Anonymisation Toolkit) is a dedicated metadata cleaner written in Python. It was developed under the umbrella of the Tor project, and comes standard on [Tails][4], privacy-enhanced live OS.
|
||||
|
||||
Compared to other tools such as [exiftool][5] which can write to only a limited number of file types, MAT can eliminate metadata from all kinds of files: images (png, jpg), documents (odt, docx, pptx, xlsx, pdf), archives (tar, tar.bz2), audio (mp3, ogg, flac), etc.
|
||||
|
||||
### Install MAT on Linux ###
|
||||
|
||||
On Debian-based systems (Ubuntu or Linux Mint), MAT comes packaged, so installation is straightforward:
|
||||
|
||||
$ sudo apt-get install mat
|
||||
|
||||
On Fedora, MAT does not come as a pre-built package, so you need to build it from the source. Here is how I built MAT on Fedora (with some limited success; see the bottom of the tutorial):
|
||||
|
||||
$ sudo yum install python-devel intltool python-pdfrw perl-Image-ExifTool python-mutagen
|
||||
$ sudo pip install hachoir-core hachoir-parser
|
||||
$ wget https://mat.boum.org/files/mat-0.5.tar.xz
|
||||
$ tar xf mat-0.5.tar.xz
|
||||
$ cd mat-0.5
|
||||
$ python setup.py install
|
||||
|
||||
### Anonymize Metadata with MAT-GUI ###
|
||||
|
||||
Once installed, MAT can be accessible via GUI as well as from the command line. To launch MAT's GUI, simply type:
|
||||
|
||||
$ mat-gui
|
||||
|
||||
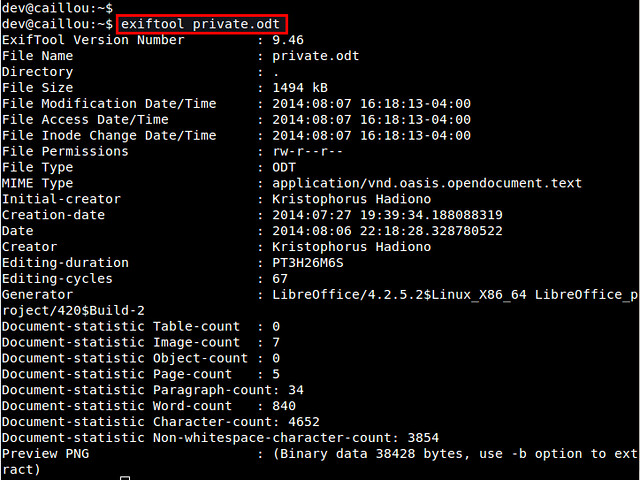
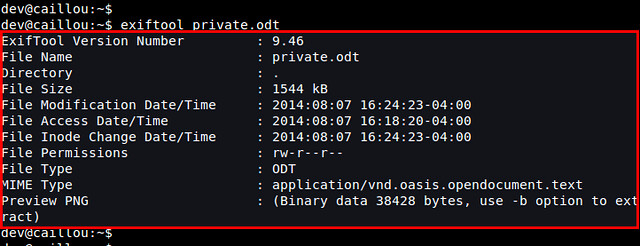
Let's clean up a sample document file (e.g., private.odt) which has the following metadata embedded.
|
||||
|
||||
|
||||
|
||||
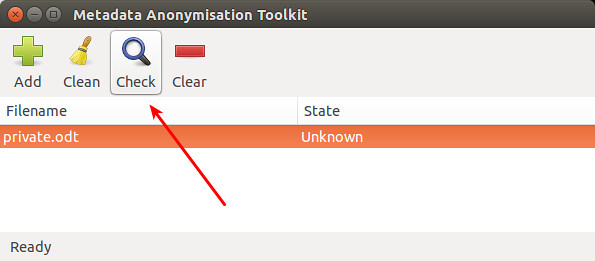
To add the file to MAT for cleanup, click on "Add" icon. Once the file is loaded, click on "Check" icon to scan for any hidden metadata information.
|
||||
|
||||
|
||||
|
||||
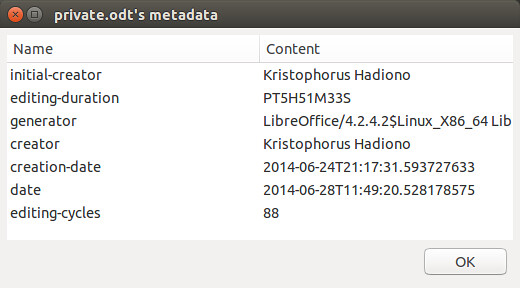
Once any metadata is detected by MAT, "State" will be marked as "Dirty". You can double click the file to see detected metadata.
|
||||
|
||||
|
||||
|
||||
To clean up metadata from the file, click on "Clean" icon. MAT will automatically empty all private metadata fields from the file.
|
||||
|
||||
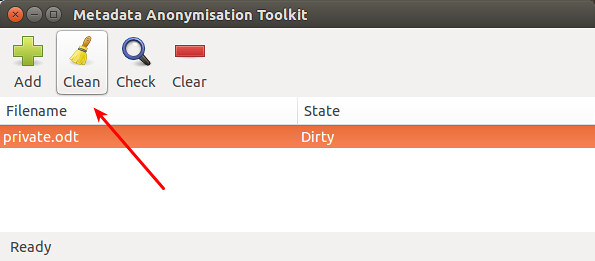
|
||||
|
||||
The cleaned up state is without any personally identifiable traces:
|
||||
|
||||
|
||||
|
||||
### Anonymize Metadata from the Command Line ###
|
||||
|
||||
As mentioned before, another way to invoke MAT is from the command line, and for that, use mat command.
|
||||
|
||||
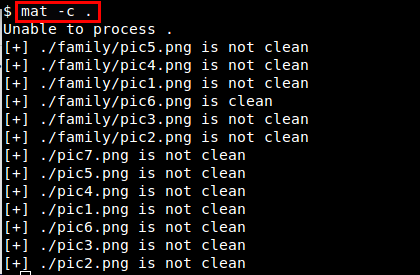
To check for any sensitive metadata, first go to the directory where your files are located, and then run:
|
||||
|
||||
$ mat -c .
|
||||
|
||||
It will scan all files in the current directory and its sub directories, and report their state (clean or unclean).
|
||||
|
||||
|
||||
|
||||
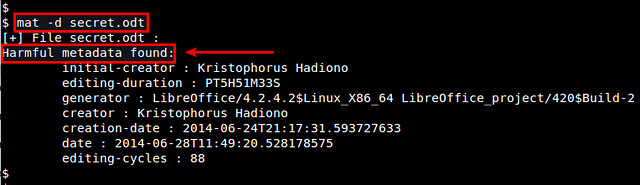
You can check actual metadata detected by using '-d' option:
|
||||
|
||||
$ mat -d <input_file>
|
||||
|
||||
|
||||
|
||||
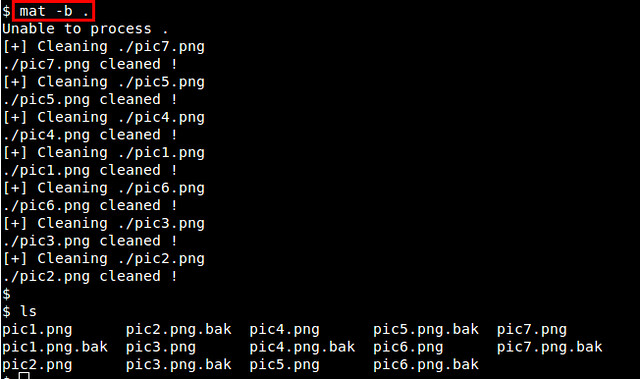
If you don't supply any option with mat command, the default action is to remove metadata from files. If you want to keep a backup of original files during cleanup, use '-b' option. The following command cleans up all files, and stores original files as '*.bak" files.
|
||||
|
||||
$ mat -b .
|
||||
|
||||
|
||||
|
||||
To see a list of all supported file types, run:
|
||||
|
||||
$ mat -l
|
||||
|
||||
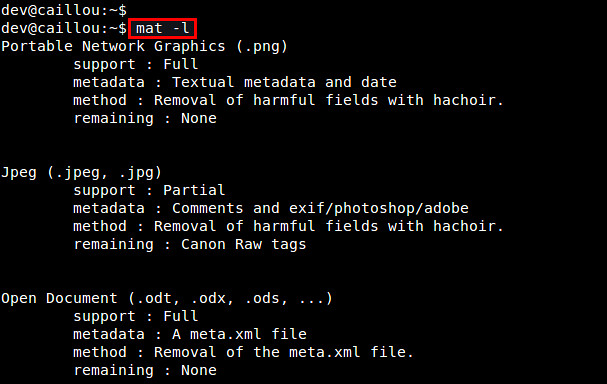
|
||||
|
||||
### Troubleshooting ###
|
||||
|
||||
Currently I have the following issue with a compiled version of MAT on Fedora. When I attempt to clean up archive/document files (e.g., *.gz, *.odt, *.docx) on Fedora, MAT fails with the following error. If you know how to fix this problem, let me know in the comment.
|
||||
|
||||
File "/usr/lib64/python2.7/zipfile.py", line 305, in __init__
|
||||
raise ValueError('ZIP does not support timestamps before 1980')
|
||||
ValueError: ZIP does not support timestamps before 1980
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
MAT is a simple, yet extremely useful tool to prevent any inadvertent privacy leaks from metadata. Note that it is still your responsibility to anonymize file content, if necessary. All MAT does is to eliminate metadata associated with your files, but does nothing with the files themselves. In short, MAT can be a life saver as it can handle most common metadata removal, but you shouldn't rely solely on it to guarantee your privacy.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/08/remove-file-metadata-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://www.theguardian.com/world/2013/sep/30/nsa-americans-metadata-year-documents
|
||||
[2]:http://code.google.com/p/metagoofil/
|
||||
[3]:https://mat.boum.org/
|
||||
[4]:https://tails.boum.org/
|
||||
[5]:http://xmodulo.com/2013/08/view-or-edit-pdf-and-image-metadata-from-command-line-on-linux.html
|
||||
@ -1,120 +0,0 @@
|
||||
How to configure Access Control Lists (ACLs) on Linux
|
||||
================================================================================
|
||||
Working with permissions on Linux is rather a simple task. You can define permissions for users, groups or others. This works really well when you work on a desktop PC or a virtual Linux instance which typically doesn't have a lot of users, or when users don't share files among themselves. However, what if you are a big organization where you operate NFS or Samba servers for diverse users. Then you will need to be neat picky and set up more complex configurations and permissions to meet the requirements of your organization.
|
||||
|
||||
Linux (and other Unixes, that are POSIX compliant) has so-called Access Control Lists (ACLs), which are a way to assign permissions beyond the common paradigm. For example, by default you apply three permission groups: owner, group, and others. With ACLs, you can add permissions for other users or groups that are not simple "others" or any other group that the owner is not part of it. You can allow particular users A, B and C to have write permissions without letting their whole group to have writing permission.
|
||||
|
||||
ACLs are available for a variety of Linux filesystems including ext2, ext3, ext4, XFS, Btfrs, etc. If you are not sure if the filesystem you are using supports ACLs, just read the documentation.
|
||||
|
||||
### Enable ACLs on your Filesystem ###
|
||||
|
||||
First of all, we need to install the tools to manage ACLs.
|
||||
|
||||
On Ubuntu/Debian:
|
||||
|
||||
$ sudo apt-get install acl
|
||||
|
||||
On CentOS/Fedora/RHEL:
|
||||
|
||||
# yum -y install acl
|
||||
|
||||
On Archlinux:
|
||||
|
||||
# pacman -S acl
|
||||
|
||||
For demonstration purpose, I will use Ubuntu server, but other distributions should work the same.
|
||||
|
||||
After installing ACL tools, it is necessary to enable ACL feature on our disk partitions so that we can start using it.
|
||||
|
||||
First, we can check if ACL feature is already enabled:
|
||||
|
||||
$ mount
|
||||
|
||||
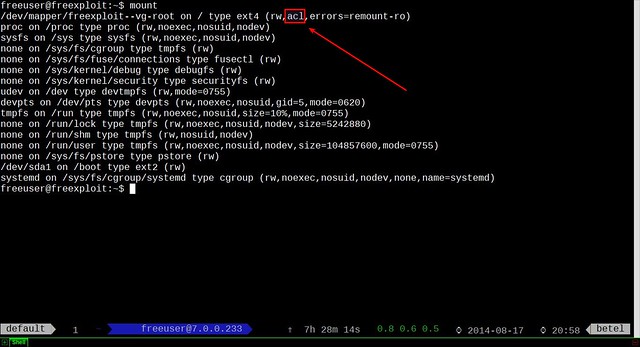
|
||||
|
||||
As you noticed, my root partition has the ACL attribute enabled. In case yours doesn't, you need to edit your /etc/fstab file. Add acl flag in front of your options for the partition you want to enable ACL.
|
||||
|
||||
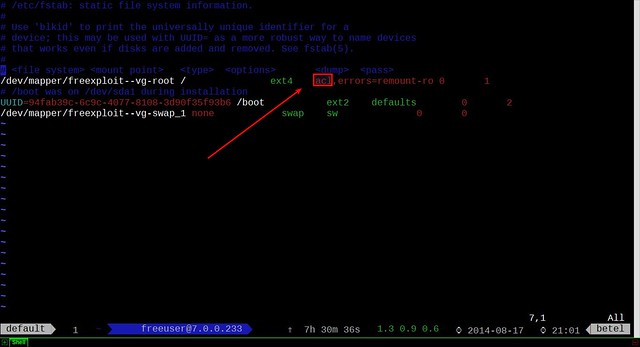
|
||||
|
||||
Now we need to re-mount the partition (I prefer to reboot completely, because I don't like losing data). If you enabled ACL for any other partitions, you have to remount them as well.
|
||||
|
||||
$ sudo mount / -o remount
|
||||
|
||||
Awesome! Now that we have enable ACL in our system, let's start to work with it.
|
||||
|
||||
### ACL Examples ###
|
||||
|
||||
Basically ACLs are managed by two commands: **setfacl** which is used to add or modify ACLs, and getfacl which shows assigned ACLs. Let's do some testing.
|
||||
|
||||
I created a directory /shared owned by a hypothetical user named freeuser.
|
||||
|
||||
$ ls -lh /
|
||||
|
||||
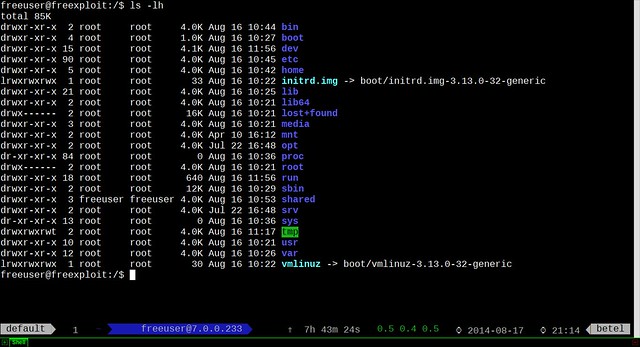
|
||||
|
||||
I want to share this directory with two other users test and test2, one with full permissions and the other with just read permission.
|
||||
|
||||
First, to set ACLs for user test:
|
||||
|
||||
$ sudo setfacl -m u:test:rwx /shared
|
||||
|
||||
Now user test can create directories, files, and access anything under /shared directory.
|
||||
|
||||
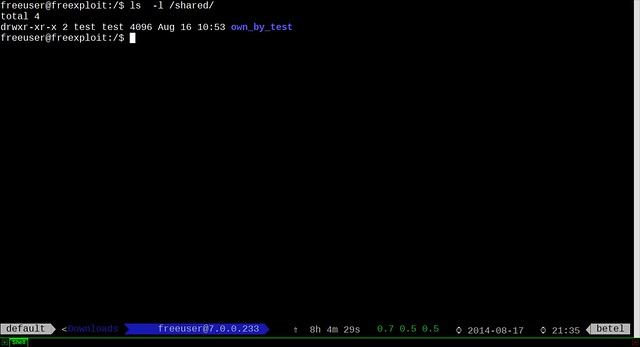
|
||||
|
||||
Now we will add read-only permission for user test2:
|
||||
|
||||
$ sudo setfacl -m u:test2:rx /shared
|
||||
|
||||
Note that execution permission is necessary so test2 can read directories.
|
||||
|
||||
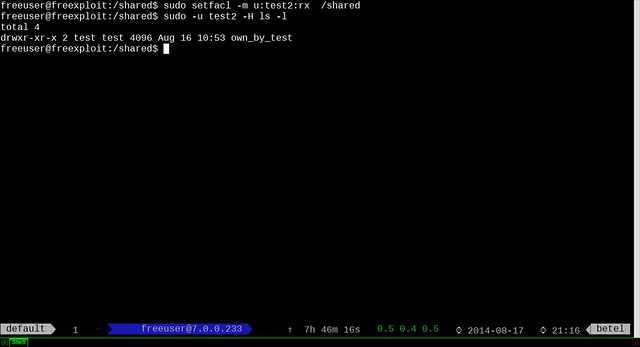
|
||||
|
||||
Let me explain the syntax of setfacl command:
|
||||
|
||||
- **-m** means modify ACL. You can add new, or modify existing ACLs.
|
||||
- **u:** means user. You can use **g** to set group permissions.
|
||||
- **test** is the name of the user.
|
||||
- **:rwx** represents permissions you want to set.
|
||||
|
||||
Now let me show you how to read ACLs.
|
||||
|
||||
$ ls -lh /shared
|
||||
|
||||

|
||||
|
||||
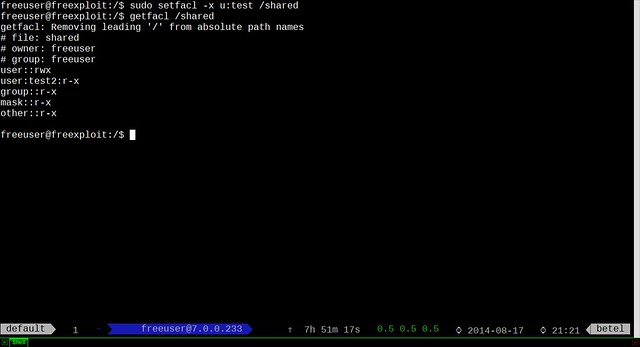
As you noticed, there is a + (plus) sign after normal permissions. It means that there are ACLs set up. To actually read ACLs, we need to run:
|
||||
|
||||
$ sudo getfacl /shared
|
||||
|
||||
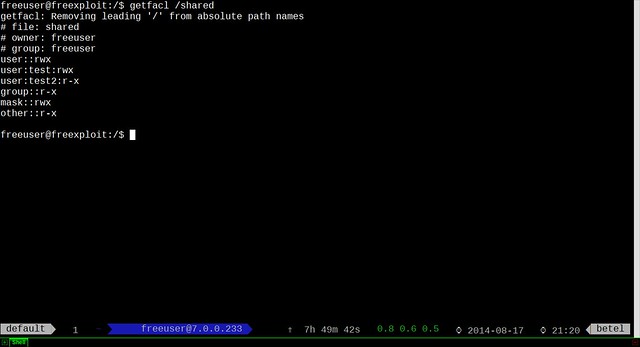
|
||||
|
||||
Finally if you want to remove ACL:
|
||||
|
||||
$ sudo setfacl -x u:test /shared
|
||||
|
||||
|
||||
|
||||
If you want to wipe out all ACL entries at once:
|
||||
|
||||
$ sudo setfacl -b /shared
|
||||
|
||||

|
||||
|
||||
One last thing. The commands cp and mv can change their behavior when they work over files or directories with ACLs. In the case of cp, you need to add the '-p' parameter to copy ACLs. If this is not posible, it will show you a warning. mv will always move the ACLs, and also if it is not posible, it will show you a warning.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Using ACLs gives you a tremendous power and control over files you want to share, especially on NFS/Samba servers. Moreover, if you administer shared hosting, this tool is a must have.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/08/configure-access-control-lists-acls-linux.html
|
||||
|
||||
作者:[Christopher Valerio][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/valerio
|
||||
@ -1,151 +0,0 @@
|
||||
[su-kaiyao]翻译中
|
||||
|
||||
Linux Terminal: speedtest_cli checks your real bandwidth speed.
|
||||
================================================================================
|
||||

|
||||
|
||||
What’s your upload and download speed at home (or in your office) ?
|
||||
Are you really sure that you get what do you pay for to your ISP ?
|
||||
|
||||
To test the speed of our internet connection There are several internet services such as SpeedTest a web service that is available both from Web browsers and mobile application.
|
||||
|
||||
Now you can easily check it also with speedtest_cli a command line interface for testing internet [bandwidth][1] using [speedtest.net][2]. In this way you can do the test also on servers that don’t have a Browser or a graphical interface.
|
||||
|
||||
### Installation ###
|
||||
|
||||
speedtest_cli it’s just a python script, so it’s really easy to install and use it, and you have different ways to do it:
|
||||
|
||||
#### 1) pip / easy_install ####
|
||||
|
||||
Open a terminal and give the command:
|
||||
|
||||
pip install speedtest-cli
|
||||
|
||||
or
|
||||
|
||||
easy_install speedtest-cli
|
||||
|
||||
#### 2) Github ####
|
||||
|
||||
To install directly from github you can use these commands:
|
||||
|
||||
pip install git+https://github.com/sivel/speedtest-cli.git
|
||||
|
||||
or
|
||||
|
||||
git clone https://github.com/sivel/speedtest-cli.git
|
||||
python speedtest-cli/setup.py install
|
||||
|
||||
#### 3) As Ubuntu/Debian or Mint package ####
|
||||
|
||||
The [package][3] is available on the getdeb repository, you can easily add it with these steps:
|
||||
|
||||
- Install the [getdeb package][4].
|
||||
Or
|
||||
- Configure the repository manually:
|
||||
Go to System-Administration-Software Sources, Third-Party Software tab, Add:
|
||||
|
||||
deb http://archive.getdeb.net/ubuntu trusty-getdeb apps
|
||||
|
||||
Add the repository GPG key, open a terminal window and type:
|
||||
|
||||
wget -q -O- http://archive.getdeb.net/getdeb-archive.key | sudo apt-key add -
|
||||
|
||||
And now you can install the speedtest-cli package with the commands:
|
||||
|
||||
sudo apt-get update
|
||||
sudo apt-get install python-speedtest-cli
|
||||
|
||||
#### 4) Just download (Like the way it used to be) ####
|
||||
|
||||
As last option, just download the python script where you prefer and run it from there:
|
||||
|
||||
wget -O speedtest-cli https://raw.github.com/sivel/speedtest-cli/master/speedtest_cli.py
|
||||
chmod +x speedtest-cli
|
||||
|
||||
or
|
||||
|
||||
curl -o speedtest-cli https://raw.github.com/sivel/speedtest-cli/master/speedtest_cli.py
|
||||
chmod +x speedtest-cli
|
||||
|
||||
### Basic Usage ###
|
||||
|
||||
You can simply run the command speedtest_cli.py without any option and you’ll get a report on the terminal of your bandwidth speed, this is the output of my crappy Italian Adsl:
|
||||
|
||||
$ ./speedtest_cli.py
|
||||
Retrieving speedtest.net configuration...
|
||||
Retrieving speedtest.net server list...
|
||||
Testing from Telecom Italia (87.13.73.66)...
|
||||
Selecting best server based on latency...
|
||||
Hosted by LepidaSpA (Bologna) [12.20 km]: 104.347 ms
|
||||
Testing download speed........................................
|
||||
Download: 6.35 Mbits/s
|
||||
Testing upload speed..................................................
|
||||
Upload: 0.34 Mbits/s
|
||||
|
||||
So this is the basic usage, and it’s good enough to know how great (or bad) is your connection, but maybe you want to share this information with your friends, to do this just use the option –share
|
||||
|
||||
./speedtest_cli.py --share
|
||||
Retrieving speedtest.net configuration...
|
||||
Retrieving speedtest.net server list...
|
||||
Testing from Telecom Italia (87.13.73.66)...
|
||||
Selecting best server based on latency...
|
||||
Hosted by LepidaSpA (Bologna) [12.20 km]: 93.778 ms
|
||||
Testing download speed........................................
|
||||
Download: 6.20 Mbits/s
|
||||
Testing upload speed..................................................
|
||||
Upload: 0.33 Mbits/s
|
||||
Share results: http://www.speedtest.net/result/3700218352.png
|
||||
|
||||
This will produce an image similar to this one (but I hope for you with better values):
|
||||
|
||||

|
||||
|
||||
Another interesting option it’s the –list that shows a list of speedtest.net servers sorted by distance, these are my results:
|
||||
|
||||
Retrieving speedtest.net configuration...
|
||||
Retrieving speedtest.net server list...
|
||||
2872) LepidaSpA (Bologna, Italy) [12.20 km]
|
||||
1561) MYNETWAY S.R.L. (Cesena, Italy) [80.97 km]
|
||||
2710) ReteIVO by D.t.s. Srl (Florence, Italy) [90.90 km]
|
||||
4826) Inteplanet Srl (Verona, Italy) [100.45 km]
|
||||
3998) Wolnext srl (Verona, Italy) [100.45 km]
|
||||
2957) Wifiweb s.r.l. (Altavilla Vicentina, Italy) [103.11 km]
|
||||
3103) E4A s.r.l. (Vicenza, Italy) [107.17 km]
|
||||
3804) Interplanet Srl (Vicenza, Italy) [107.17 km]
|
||||
1014) NTRnet (Vicenza, Italy) [107.17 km]
|
||||
3679) Hynet s r l (Vicenza, Italy) [107.17 km]
|
||||
3745) Comeser Srl (Fidenza, Italy) [114.00 km]
|
||||
5011) Welcomeitalia spa (Massarosa, Italy) [119.26 km]
|
||||
2864) ReteIVO by D.t.s. Srl (Massa, Italy) [120.92 km]
|
||||
2918) ReteIVO by D.t.s. Srl (Arezzo, Italy) [129.79 km]
|
||||
...
|
||||
|
||||
Now that I know the ID of the servers that are located near my location I can pick up a specific server with the option –server, so to chose the server located at Florence (ID 2710) I can use the command:
|
||||
|
||||
./speedtest_cli.py --server 2710
|
||||
Retrieving speedtest.net configuration...
|
||||
Retrieving speedtest.net server list...
|
||||
Testing from Telecom Italia (87.13.73.66)...
|
||||
Hosted by ReteIVO by D.t.s. Srl (Florence) [90.90 km]: 106.505 ms
|
||||
Testing download speed........................................
|
||||
Download: 6.18 Mbits/s
|
||||
Testing upload speed..................................................
|
||||
Upload: 0.35 Mbits/s
|
||||
|
||||
Article sponsored by [Asapy Programming Company][5]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linuxaria.com/howto/linux-terminal-speedtest_cli-checks-your-real-bandwidth-speed
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://linuxaria.com/article/tool-command-line-bandwidth-linux
|
||||
[2]:http://linuxaria.com/howto/speedtest.net
|
||||
[3]:http://www.getdeb.net/
|
||||
[4]:http://archive.getdeb.net/install_deb/getdeb-repository_0.1-1~getdeb1_all.deb
|
||||
[5]:http://www.asapy.com/
|
||||
@ -0,0 +1,218 @@
|
||||
How to create a site-to-site IPsec VPN tunnel using Openswan in Linux
|
||||
================================================================================
|
||||
A virtual private network (VPN) tunnel is used to securely interconnect two physically separate networks through a tunnel over the Internet. Tunneling is needed when the separate networks are private LAN subnets with globally non-routable private IP addresses, which are not reachable to each other via traditional routing over the Internet. For example, VPN tunnels are often deployed to connect different NATed branch office networks belonging to the same institution.
|
||||
|
||||
Sometimes VPN tunneling may be used simply for its security benefit as well. Service providers or private companies may design their networks in such a way that vital servers (e.g., database, VoIP, banking servers) are placed in a subnet that is accessible to trusted personnel through a VPN tunnel only. When a secure VPN tunnel is required, [IPsec][1] is often a preferred choice because an IPsec VPN tunnel is secured with multiple layers of security.
|
||||
|
||||
This tutorial will show how we can easily create a site-to-site VPN tunnel using [Openswan][2] in Linux.
|
||||
|
||||
### Topology ###
|
||||
|
||||
This tutorial will focus on the following topologies for creating an IPsec tunnel.
|
||||
|
||||
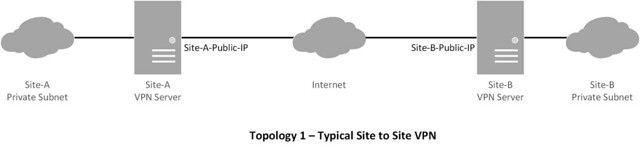
|
||||
|
||||
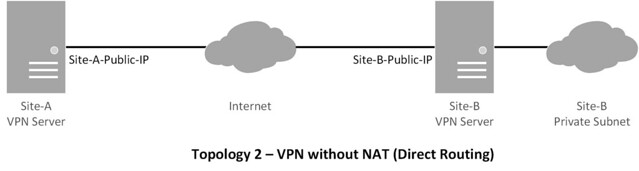
|
||||
|
||||
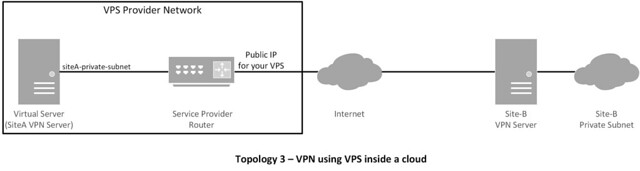
|
||||
|
||||
### Installing Packages and Preparing VPN Servers ###
|
||||
|
||||
Usually, you will be managing site-A only, but based on the requirements, you could be managing both site-A and site-B. We start the process by installing Openswan.
|
||||
|
||||
On Red Hat based Systems (CentOS, Fedora or RHEL):
|
||||
|
||||
# yum install openswan lsof
|
||||
|
||||
On Debian based Systems (Debian, Ubuntu or Linux Mint):
|
||||
|
||||
# apt-get install openswan
|
||||
|
||||
Now we disable VPN redirects, if any, in the server using these commands:
|
||||
|
||||
# for vpn in /proc/sys/net/ipv4/conf/*;
|
||||
# do echo 0 > $vpn/accept_redirects;
|
||||
# echo 0 > $vpn/send_redirects;
|
||||
# done
|
||||
|
||||
Next, we modify the kernel parameters to allow IP forwarding and disable redirects permanently.
|
||||
|
||||
# vim /etc/sysctl.conf
|
||||
|
||||
----------
|
||||
|
||||
net.ipv4.ip_forward = 1
|
||||
net.ipv4.conf.all.accept_redirects = 0
|
||||
net.ipv4.conf.all.send_redirects = 0
|
||||
|
||||
Reload /etc/sysctl.conf:
|
||||
|
||||
# sysctl -p
|
||||
|
||||
We allow necessary ports in the firewall. Please make sure that the rules are not conflicting with existing firewall rules.
|
||||
|
||||
# iptables -A INPUT -p udp --dport 500 -j ACCEPT
|
||||
# iptables -A INPUT -p tcp --dport 4500 -j ACCEPT
|
||||
# iptables -A INPUT -p udp --dport 4500 -j ACCEPT
|
||||
|
||||
Finally, we create firewall rules for NAT.
|
||||
|
||||
# iptables -t nat -A POSTROUTING -s site-A-private-subnet -d site-B-private-subnet -j SNAT --to site-A-Public-IP
|
||||
|
||||
Please make sure that the firewall rules are persistent.
|
||||
|
||||
#### Note: ####
|
||||
|
||||
- You could use MASQUERADE instead of SNAT. Logically it should work, but it caused me to have issues with virtual private servers (VPS) in the past. So I would use SNAT if I were you.
|
||||
- If you are managing site-B as well, create similar rules in site-B server.
|
||||
- Direct routing does not need SNAT.
|
||||
|
||||
### Preparing Configuration Files ###
|
||||
|
||||
The first configuration file that we will work with is ipsec.conf. Regardless of which server you are configuring, always consider your site as 'left' and remote site as 'right'. The following configuration is done in siteA's VPN server.
|
||||
|
||||
# vim /etc/ipsec.conf
|
||||
|
||||
----------
|
||||
|
||||
## general configuration parameters ##
|
||||
|
||||
config setup
|
||||
plutodebug=all
|
||||
plutostderrlog=/var/log/pluto.log
|
||||
protostack=netkey
|
||||
nat_traversal=yes
|
||||
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/16
|
||||
## disable opportunistic encryption in Red Hat ##
|
||||
oe=off
|
||||
|
||||
## disable opportunistic encryption in Debian ##
|
||||
## Note: this is a separate declaration statement ##
|
||||
include /etc/ipsec.d/examples/no_oe.conf
|
||||
|
||||
## connection definition in Red Hat ##
|
||||
conn demo-connection-redhat
|
||||
authby=secret
|
||||
auto=start
|
||||
ike=3des-md5
|
||||
## phase 1 ##
|
||||
keyexchange=ike
|
||||
## phase 2 ##
|
||||
phase2=esp
|
||||
phase2alg=3des-md5
|
||||
compress=no
|
||||
pfs=yes
|
||||
type=tunnel
|
||||
left=<siteA-public-IP>
|
||||
leftsourceip=<siteA-public-IP>
|
||||
leftsubnet=<siteA-private-subnet>/netmask
|
||||
## for direct routing ##
|
||||
leftsubnet=<siteA-public-IP>/32
|
||||
leftnexthop=%defaultroute
|
||||
right=<siteB-public-IP>
|
||||
rightsubnet=<siteB-private-subnet>/netmask
|
||||
|
||||
## connection definition in Debian ##
|
||||
conn demo-connection-debian
|
||||
authby=secret
|
||||
auto=start
|
||||
## phase 1 ##
|
||||
keyexchange=ike
|
||||
## phase 2 ##
|
||||
esp=3des-md5
|
||||
pfs=yes
|
||||
type=tunnel
|
||||
left=<siteA-public-IP>
|
||||
leftsourceip=<siteA-public-IP>
|
||||
leftsubnet=<siteA-private-subnet>/netmask
|
||||
## for direct routing ##
|
||||
leftsubnet=<siteA-public-IP>/32
|
||||
leftnexthop=%defaultroute
|
||||
right=<siteB-public-IP>
|
||||
rightsubnet=<siteB-private-subnet>/netmask
|
||||
|
||||
Authentication can be done in several different ways. This tutorial will cover the use of pre-shared key, which is added to the file /etc/ipsec.secrets.
|
||||
|
||||
# vim /etc/ipsec.secrets
|
||||
|
||||
----------
|
||||
|
||||
siteA-public-IP siteB-public-IP: PSK "pre-shared-key"
|
||||
## in case of multiple sites ##
|
||||
siteA-public-IP siteC-public-IP: PSK "corresponding-pre-shared-key"
|
||||
|
||||
### Starting the Service and Troubleshooting ###
|
||||
|
||||
The server should now be ready to create a site-to-site VPN tunnel. If you are managing siteB as well, please make sure that you have configured the siteB server with necessary parameters. For Red Hat based systems, please make sure that you add the service into startup using chkconfig command.
|
||||
|
||||
# /etc/init.d/ipsec restart
|
||||
|
||||
If there are no errors in both end servers, the tunnel should be up now. Taking the following into consideration, you can test the tunnel with ping command.
|
||||
|
||||
1. The siteB-private subnet should not be reachable from site A, i.e., ping should not work if the tunnel is not up.
|
||||
1. After the tunnel is up, try ping to siteB-private-subnet from siteA. This should work.
|
||||
|
||||
Also, the routes to the destination's private subnet should appear in the server's routing table.
|
||||
|
||||
# ip route
|
||||
|
||||
----------
|
||||
|
||||
[siteB-private-subnet] via [siteA-gateway] dev eth0 src [siteA-public-IP]
|
||||
default via [siteA-gateway] dev eth0
|
||||
|
||||
Additionally, we can check the status of the tunnel using the following useful commands.
|
||||
|
||||
# service ipsec status
|
||||
|
||||
----------
|
||||
|
||||
IPsec running - pluto pid: 20754
|
||||
pluto pid 20754
|
||||
1 tunnels up
|
||||
some eroutes exist
|
||||
|
||||
----------
|
||||
|
||||
# ipsec auto --status
|
||||
|
||||
----------
|
||||
|
||||
## output truncated ##
|
||||
000 "demo-connection-debian": myip=<siteA-public-IP>; hisip=unset;
|
||||
000 "demo-connection-debian": ike_life: 3600s; ipsec_life: 28800s; rekey_margin: 540s; rekey_fuzz: 100%; keyingtries: 0; nat_keepalive: yes
|
||||
000 "demo-connection-debian": policy: PSK+ENCRYPT+TUNNEL+PFS+UP+IKEv2ALLOW+SAREFTRACK+lKOD+rKOD; prio: 32,28; interface: eth0;
|
||||
|
||||
## output truncated ##
|
||||
000 #184: "demo-connection-debian":500 STATE_QUICK_R2 (IPsec SA established); EVENT_SA_REPLACE in 1653s; newest IPSEC; eroute owner; isakmp#183; idle; import:not set
|
||||
|
||||
## output truncated ##
|
||||
000 #183: "demo-connection-debian":500 STATE_MAIN_I4 (ISAKMP SA established); EVENT_SA_REPLACE in 1093s; newest ISAKMP; lastdpd=-1s(seq in:0 out:0); idle; import:not set
|
||||
|
||||
The log file /var/log/pluto.log should also contain useful information regarding authentication, key exchanges and information on different phases of the tunnel. If your tunnel doesn't come up, you could check there as well.
|
||||
|
||||
If you are sure that all the configuration is correct, and if your tunnel is still not coming up, you should check the following things.
|
||||
|
||||
1. Many ISPs filter IPsec ports. Make sure that UDP 500, TCP/UDP 4500 ports are allowed by your ISP. You could try connecting to your server IPsec ports from a remote location by telnet.
|
||||
1. Make sure that necessary ports are allowed in the firewall of the server/s.
|
||||
1. Make sure that the pre-shared keys are identical in both end servers.
|
||||
1. The left and right parameters should be properly configured on both end servers.
|
||||
1. If you are facing problems with NAT, try using SNAT instead of MASQUERADING.
|
||||
|
||||
To sum up, this tutorial focused on the procedure of creating a site-to-site IPSec VPN tunnel in Linux using Openswan. VPN tunnels are very useful in enhancing security as they allow admins to make critical resources available only through the tunnels. Also VPN tunnels ensure that the data in transit is secured from eavesdropping or interception.
|
||||
|
||||
Hope this helps. Let me know what you think.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/08/create-site-to-site-ipsec-vpn-tunnel-openswan-linux.html
|
||||
|
||||
作者:[Sarmed Rahman][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/sarmed
|
||||
[1]:http://en.wikipedia.org/wiki/IPsec
|
||||
[2]:https://www.openswan.org/
|
||||
@ -0,0 +1,138 @@
|
||||
How to listen to Internet radio from the command line on Linux
|
||||
================================================================================
|
||||
For those of you system admins and Linux aficionados who spend a great deal of your time in front of Linux screen, do you know that ambient noise from online/local radio station can actually be a productivity booster? Believe or not, it is known that moderate level of ambient sound such as music or chatter can actually fuel your creativity at your workplace. If you like the idea of working with music on, maybe this tutorial is useful to you, as I am going to show you **how to listen to Pandora online radio from the command lin**e.
|
||||
|
||||
As you already know, Pandora is one of the most well-known Internet radio services, streaming tons of different genres of music for free, with its powerful music recommendation engine. While Pandora can be accessed in different ways such as via web browser, desktop clients or mobile apps, the open-source community has come up with yet another way to access Pandora: Linux command-line.
|
||||
|
||||
[pianobar][1] is an open-source CLI music player for Pandora Internet radio. It comes with a simple terminal interface for playing and managing music stations. Other features include song rating, upcoming song list, song history, custom keybindings, remote control, etc. For those listeners who live in the region where Pandora is not available (i.e., outside US, Australia and New Zealand), pianobar also comes with proxy support.
|
||||
|
||||
### Install Pianobar on Linux ###
|
||||
|
||||
On Debian and other Debian-derivatives such as Ubuntu or Linux Mint, pianobar comes as a pre-built package, so installation is as easy as typing:
|
||||
|
||||
$ sudo apt-get install pianobar
|
||||
|
||||
On Fedora, pianobar is not available in base repositories. So you need to build it from the source. The whole installation process is a bit involved, but the following instructions will do it. The instructions were tested on fresh Fedora 20.
|
||||
|
||||
First, compile and install FFmpeg from the source using [this guide][2].
|
||||
|
||||
Next, [enable RPM Fusion repo][3], and install other prerequisites:
|
||||
|
||||
$ sudo yum install wget gcc-c++ pkgconfig gnutls-devel json-c-devel libgcrypt-devel make libao-devel faad2-devel libmad-devel libao faad2-libs
|
||||
|
||||
Compile and install pianobar:
|
||||
|
||||
$ wget http://6xq.net/projects/pianobar/pianobar-2014.06.08.tar.bz2
|
||||
$ tar xvfvj pianobar-2014.06.08.tar.bz2
|
||||
$ cd pianobar-2014.06.08
|
||||
$ PKG_CONFIG_PATH=/usr/local/lib/pkgconfig:$PKG_CONFIG_PATH make
|
||||
$ sudo make install
|
||||
|
||||
Finally, to allow pianobar to load shared FFmpeg libraries installed in /usr/local/lib, add the following line in /etc/ld.so.conf:
|
||||
|
||||
/usr/local/lib
|
||||
|
||||
and reload all shared libraries:
|
||||
|
||||
That's it.
|
||||
|
||||
### Listen to Pandora from the Command Line ###
|
||||
|
||||
The basic usage of pianobar is as simple as typing the command:
|
||||
|
||||
$ pianobar
|
||||
|
||||
You will be asked to log in to Pandora, and choose a station from your personalized station list. Once you pick a station, music streaming will start automatically.
|
||||
|
||||

|
||||
|
||||
Pressing '?' key during streaming will show you a list of available command keys. Some of them are:
|
||||
|
||||
- s: change to a different station.
|
||||
- u: view a list of upcoming songs.
|
||||
- h: view plaback history.
|
||||
- n: go to the next song.
|
||||
- b: bookmark a song or an artist.
|
||||
- ( or ): decrease or increase music volume.
|
||||
- S: pause streaming.
|
||||
- P: resume streaming.
|
||||
- v: create a new station from song or artist.
|
||||
- + or -: thumb up or down a song.
|
||||
- a: add music to a station.
|
||||
- q: quit pianobar.
|
||||
|
||||
|
||||
|
||||
### Configure Pianobar for Automatic Setup ###
|
||||
|
||||
You can define various default settings of pianobar in a separate configuration file. For example, you can put your Pandora login information in the configuration file, so you don't have to type it manually. Here is how to create a sample configuration file.
|
||||
|
||||
$ mkdir -p ~/.config/pianobar
|
||||
|
||||
----------
|
||||
|
||||
$ vi ~/.config/pianobar/config
|
||||
|
||||
----------
|
||||
|
||||
# Example pianobar configuration file
|
||||
|
||||
# Pandora login info
|
||||
user = your@email_address
|
||||
password = plaintext_password
|
||||
|
||||
# Users who cannot access Pandora in their region can set a proxy.
|
||||
control_proxy = http://user:password@host:port/
|
||||
|
||||
# Initial volume in dB: between -30 and +5
|
||||
volume = 0
|
||||
|
||||
# Audio quality: high, medium or low
|
||||
audio_quality = high
|
||||
|
||||
For full configuration options, refer to its man page.
|
||||
|
||||
$ man pianobar
|
||||
|
||||
### Remote Control Pianobar ###
|
||||
|
||||
Another excellent feature of pianobar is remote control support. You can send a command to a running instance of pianobar via a named pipe (FIFO). Here is how to remote control pianobar.
|
||||
|
||||
First create a FIFO in ~/.config/pianobar:
|
||||
|
||||
$ mkfifo ~/.config/pianobar/ctl
|
||||
|
||||
Then launch pianobar.
|
||||
|
||||
Now you can send any single-character command key to pianobar by using echo command. For example, to go to the next song:
|
||||
|
||||
$ echo -n 'n' > ~/.config/pianobar/ctl
|
||||
|
||||
You can easily extend this setup to a remote machine. When pianobar is running on host X, you can remote control pianobar from another host Y over SSH as follows.
|
||||
|
||||
On host Y, run:
|
||||
|
||||
$ ssh user@host_X "echo -n 'n' > ~/.config/pianobar/ctl"
|
||||
|
||||
Of course, you want to [enable key authentication][4] for SSH login to host X, so that you don't have to type an SSH password.
|
||||
|
||||
This remote control feature can come in handy when you want to set up a remote controllable Internet radio player on [Raspberry Pi][5].
|
||||
|
||||
Hope you enjoy pianobar as much as I do. Let me know what you think of it in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/08/listen-to-internet-radio-command-line-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://6xq.net/projects/pianobar/
|
||||
[2]:http://ask.xmodulo.com/compile-ffmpeg-centos-fedora-rhel.html
|
||||
[3]:http://xmodulo.com/2013/06/how-to-install-rpm-fusion-on-fedora.html
|
||||
[4]:http://xmodulo.com/2012/04/how-to-enable-ssh-login-without.html
|
||||
[5]:http://xmodulo.com/go/raspberrypi
|
||||
@ -0,0 +1,213 @@
|
||||
Setup Thin Provisioning Volumes in Logical Volume Management (LVM) – Part IV
|
||||
================================================================================
|
||||
Logical Volume management has great features such as snapshots and Thin Provisioning. Previously in (Part – III) we have seen how to snapshot the logical volume. Here in this article, we will going to see how to setup thin Provisioning volumes in LVM.
|
||||
|
||||

|
||||
Setup Thin Provisioning in LVM
|
||||
|
||||
### What is Thin Provisioning? ###
|
||||
|
||||
Thin Provisioning is used in lvm for creating virtual disks inside a thin pool. Let us assume that I have a **15GB** storage capacity in my server. I already have 2 clients who has 5GB storage each. You are the third client, you asked for 5GB storage. Back then we use to provide the whole 5GB (Thick Volume) but you may use 2GB from that 5GB storage and 3GB will be free which you can fill it up later.
|
||||
|
||||
But what we do in thin Provisioning is, we use to define a thin pool inside one of the large volume group and define the thin volumes inside that thin pool. So, that whatever files you write will be stored and your storage will be shown as 5GB. But the full 5GB will not allocate the entire disk. The same process will be done for other clients as well. Like I said there are 2 clients and you are my 3rd client.
|
||||
|
||||
So, let us assume how much total GB I have assigned for clients? Totally 15GB was already completed, If someone comes to me and ask for 5GB can I give? The answer is “**Yes**“, here in thin Provisioning I can give 5GB for 4th Client even though I have assigned 15GB.
|
||||
|
||||
**Warning**: From 15GB, if we are Provisioning more than 15GB it is called Over Provisioning.
|
||||
|
||||
### How it Works? and How we provide storage to new Clients? ###
|
||||
|
||||
I have provided you 5GB but you may used only 2GB and other 3GB will be free. In Thick Provisioning we can’t do this, because it will allocate the whole space at first itself.
|
||||
|
||||
In thin Provisioning if I’m defining 5GB for you it won’t allocate the whole disk space while defining a volume, it will grow till 5GB according to your data write, Hope you got it! same like you, other clients too won’t use the full volumes so there will be a chance to add 5GB to a new client, This is called over Provisioning.
|
||||
|
||||
But it’s compulsory to monitored each and every volume growth, if not it will end-up in a disaster. While over Provisioning is done if the all 4 clients write the data’s badly to disk you may face an issue because it will fill up your 15GB and overflow to get drop the volumes.
|
||||
|
||||
### Requirements ###
|
||||
|
||||
注:此三篇文章如果发布后可换成发布后链接,原文在前几天更新中
|
||||
|
||||
- [Create Disk Storage with LVM in Linux – PART 1][1]
|
||||
- [How to Extend/Reduce LVM’s in Linux – Part II][2]
|
||||
- [How to Create/Restore Snapshot of Logical Volume in LVM – Part III][3]
|
||||
|
||||
#### My Server Setup ####
|
||||
|
||||
Operating System – CentOS 6.5 with LVM Installation
|
||||
Server IP – 192.168.0.200
|
||||
|
||||
### Step 1: Setup Thin Pool and Volumes ###
|
||||
|
||||
Let’s do it practically how to setup the thin pool and thin volumes. First we need a large size of Volume group. Here I’m creating Volume group with **15GB** for demonstration purpose. Now, list the volume group using the below command.
|
||||
|
||||
# vgcreate -s 32M vg_thin /dev/sdb1
|
||||
|
||||

|
||||
Listing Volume Group
|
||||
|
||||
Next, check for the size of Logical volume availability, before creating the thin pool and volumes.
|
||||
|
||||
# vgs
|
||||
# lvs
|
||||
|
||||

|
||||
Check Logical Volume
|
||||
|
||||
We can see there is only default logical volumes for file-system and swap is present in the above lvs output.
|
||||
|
||||
### Creating a Thin Pool ###
|
||||
|
||||
To create a Thin pool for 15GB in volume group (vg_thin) use the following command.
|
||||
|
||||
# lvcreate -L 15G --thinpool tp_tecmint_pool vg_thin
|
||||
|
||||
- **-L** – Size of volume group
|
||||
- **–thinpool** – To o create a thinpool
|
||||
- **tp_tecmint_poolThin** - pool name
|
||||
- **vg_thin** – Volume group name were we need to create the pool
|
||||
|
||||

|
||||
Create Thin Pool
|
||||
|
||||
To get more detail we can use the command ‘lvdisplay’.
|
||||
|
||||
# lvdisplay vg_thin/tp_tecmint_pool
|
||||
|
||||

|
||||
Logical Volume Information
|
||||
|
||||
Here we haven’t created Virtual thin volumes in this thin-pool. In the image we can see Allocated pool data showing **0.00%**.
|
||||
|
||||
### Creating Thin Volumes ###
|
||||
|
||||
Now we can define thin volumes inside the thin pool with the help of ‘lvcreate’ command with option -V (Virtual).
|
||||
|
||||
# lvcreate -V 5G --thin -n thin_vol_client1 vg_thin/tp_tecmint_pool
|
||||
|
||||
I have created a Thin virtual volume with the name of **thin_vol_client1** inside the **tp_tecmint_pool** in my **vg_thin** volume group. Now, list the logical volumes using below command.
|
||||
|
||||
# lvs
|
||||
|
||||

|
||||
List Logical Volumes
|
||||
|
||||
Just now, we have created the thin volume above, that’s why there is no data showing i.e. **0.00%M**.
|
||||
|
||||
Fine, let me create 2 more Thin volumes for other 2 clients. Here you can see now there are 3 thin volumes created under the pool (**tp_tecmint_pool**). So, from this point, we came to know that I have used all 15GB pool.
|
||||
|
||||

|
||||
|
||||
### Creating File System ###
|
||||
|
||||
Now, create mount points and mount these three thin volumes and copy some files in it using below commands.
|
||||
|
||||
# mkdir -p /mnt/client1 /mnt/client2 /mnt/client3
|
||||
|
||||
List the created directories.
|
||||
|
||||
# ls -l /mnt/
|
||||
|
||||
|
||||
Creating Mount Points
|
||||
|
||||
Create the file system for these created thin volumes using ‘mkfs’ command.
|
||||
|
||||
# mkfs.ext4 /dev/vg_thin/thin_vol_client1 && mkfs.ext4 /dev/vg_thin/thin_vol_client2 && mkfs.ext4 /dev/vg_thin/thin_vol_client3
|
||||
|
||||

|
||||
Create File System
|
||||
|
||||
Mount all three client volumes to the created mount point using ‘mount’ command.
|
||||
|
||||
# mount /dev/vg_thin/thin_vol_client1 /mnt/client1/ && mount /dev/vg_thin/thin_vol_client2 /mnt/client2/ && mount /dev/vg_thin/thin_vol_client3 /mnt/client3/
|
||||
|
||||
List the mount points using ‘df’ command.
|
||||
|
||||
# df -h
|
||||
|
||||

|
||||
Print Mount Points
|
||||
|
||||
Here, we can see all the 3 clients volumes are mounted and therefore only 3% of data are used in every clients volumes. So, let’s add some more files to all 3 mount points from my desktop to fill up some space.
|
||||
|
||||

|
||||
Add Files To Volumes
|
||||
|
||||
Now list the mount point and see the space used in every thin volumes & list the thin pool to see the size used in pool.
|
||||
|
||||
# df -h
|
||||
# lvdisplay vg_thin/tp_tecmint_pool
|
||||
|
||||

|
||||
Check Mount Point Size
|
||||
|
||||

|
||||
Check Thin Pool Size
|
||||
|
||||
The above command shows, the three mount pints along with their sizes in percentage.
|
||||
|
||||
13% of datas used out of 5GB for client1
|
||||
29% of datas used out of 5GB for client2
|
||||
49% of datas used out of 5GB for client3
|
||||
|
||||
While looking into the thin-pool we can see only **30%** of data is written totally. This is the total of above three clients virtual volumes.
|
||||
|
||||
### Over Provisioning ###
|
||||
|
||||
Now the **4th** client came to me and asked for 5GB storage space. Can I give? Because I had already given 15GB Pool to 3 clients. Is it possible to give 5GB more to another client? Yes it is possible to give. This is when we use **Over Provisioning**, which means giving the space more than what I have.
|
||||
|
||||
Let me create 5GB for the 4th Client and verify the size.
|
||||
|
||||
# lvcreate -V 5G --thin -n thin_vol_client4 vg_thin/tp_tecmint_pool
|
||||
# lvs
|
||||
|
||||

|
||||
Create thin Storage
|
||||
|
||||
I have only 15GB size in pool, but I have created 4 volumes inside thin-pool up-to 20GB. If all four clients start to write data to their volumes to fill up the pace, at that time, we will face critical situation, if not there will no issue.
|
||||
|
||||
Now I have created file system in **thin_vol_client4**, then mounted under **/mnt/client4** and copy some files in it.
|
||||
|
||||
# lvs
|
||||
|
||||

|
||||
Verify Thin Storage
|
||||
|
||||
We can see in the above picture, that the total used size in newly created client 4 up-to **89.34%** and size of thin pool as **59.19%** used. If all these users are not writing badly to volume it will be free from overflow, drop. To avoid the overflow we need to extend the thin-pool size.
|
||||
|
||||
**Important**: Thin-pools are just a logical volume, so if we need to extend the size of thin-pool we can use the same command like, we’ve used for logical volumes extend, but we can’t reduce the size of thin-pool.
|
||||
|
||||
# lvextend
|
||||
|
||||
Here we can see how to extend the logical thin-pool (**tp_tecmint_pool**).
|
||||
|
||||
# lvextend -L +15G /dev/vg_thin/tp_tecmint_pool
|
||||
|
||||

|
||||
Extend Thin Storage
|
||||
|
||||
Next, list the thin-pool size.
|
||||
|
||||
# lvs
|
||||
|
||||

|
||||
Verify Thin Storage
|
||||
|
||||
Earlier our **tp_tecmint_pool** size was 15GB and 4 thin volumes which was over Provision by 20GB. Now it has extended to 30GB so our over Provisioning has been normalized and thin volumes are free from overflow, drop. This way you can add ever more thin volumes to the pool.
|
||||
|
||||
Here, we have seen how to create a thin-pool using a large size of volume group and create thin-volumes inside a thin-pool using Over-Provisioning and extending the pool. In the next article we will see how to setup a lvm Striping.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/setup-thin-provisioning-volumes-in-lvm/
|
||||
|
||||
作者:[Babin Lonston][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/babinlonston/
|
||||
[1]:http://www.tecmint.com/create-lvm-storage-in-linux/
|
||||
[2]:http://www.tecmint.com/extend-and-reduce-lvms-in-linux/
|
||||
[3]:http://www.tecmint.com/take-snapshot-of-logical-volume-and-restore-in-lvm/
|
||||
@ -0,0 +1,106 @@
|
||||
6 Interesting Funny Commands of Linux (Fun in Terminal) – Part II
|
||||
================================================================================
|
||||
In our past following articles, we’ve shown some useful articles on some funny commands of Linux, which shows that Linux is not as complex as it seems and can be fun if we know how to use it. Linux command line can perform any complex task very easily and with perfection and can be interesting and joyful.
|
||||
|
||||
- [20 Funny Commands of Linux – Part I][1]注,此篇的原文应该翻译过,文件名应该是:20 Funny Commands of Linux or Linux is Fun in Terminal
|
||||
- [Fun in Linux Terminal – Play with Word and Character Counts][2]注:这篇文章刚刚补充上
|
||||
|
||||

|
||||
Funny Linux Commands
|
||||
|
||||
The former Post comprises of 20 funny Linux Commands/Script (and subcommands) which was highly appreciated by our readers. The other post, though not that much popular as former comprises of Commands/ Scripts and Tweaks which lets you play with text files, words and strings.
|
||||
|
||||
This post aims at bringing some new fun commands and one-liner scripts which is going to rejoice you.
|
||||
|
||||
### 1. pv Command ###
|
||||
|
||||
You might have seen simulating text in movies. It appears as, it is being typed in real time. Won’t it be nice, if you can have such an effect in terminal?
|
||||
|
||||
This can be achieved, by installing ‘**pv**‘ command in your Linux system by using ‘**apt**‘ or ‘**yum**‘ tool. Let’s install ‘**pv**‘ command as shown.
|
||||
|
||||
# yum install pv [On RedHat based Systems]
|
||||
|
||||
# sudo apt-get install pv [On Debian based Systems]
|
||||
|
||||
Once, ‘**pv**‘ command installed successfully on your system, let’s try to run the following one liner command to see the real time text effect on the screen.
|
||||
|
||||
$ echo "Tecmint[dot]com is a community of Linux Nerds and Geeks" | pv -qL 10
|
||||
|
||||

|
||||
pv command in action
|
||||
|
||||
**Note**: The ‘**q**‘ option means ‘quite’, no output information and option ‘**L**‘ means the Limit of Transfer of bytes per second. The number value can be adjusted in either direction (must be integer) to get desired simulation of text.
|
||||
|
||||
### 2. toilet Command ###
|
||||
|
||||
How about printing text with border in terminal, using an one-liner script command ‘**toilet**‘. Again, you must have ‘**toilet**‘ command installed on your system, if not use apt or yum to install it.
|
||||
|
||||
$ while true; do echo “$(date | toilet -f term -F border –Tecmint)”; sleep 1; done
|
||||
|
||||

|
||||
toilet command in action
|
||||
|
||||
**Note**: The above script needs to be suspended using **ctrl+z** key.
|
||||
|
||||
### 3. rig Command ###
|
||||
|
||||
This command generates a random identity and address, every time. To run, this command you need to install ‘**rig**‘ using apt or yum.
|
||||
|
||||
# rig
|
||||
|
||||

|
||||
rig command in action
|
||||
|
||||
### 4. aview Command ###
|
||||
|
||||
How about viewing an image in ASCII format on the terminal? We must have a package ‘**aview**‘ installed, just apt or yum it. I’ve an image named ‘**elephant.jpg**‘ in my current working directory and I want view it on terminal as ASCII format.
|
||||
|
||||
$ asciiview elephant.jpg -driver curses
|
||||
|
||||

|
||||
aview command in action
|
||||
|
||||
### 5. xeyes Command ###
|
||||
|
||||
In last article we introduced a command ‘**oneko**‘ which attaches jerry with mouse pointer and keeps on chasing it. A similar program ‘**xeyes**‘ which is a graphical programs and as soon as you fire the command you will see two monster eyes chasing your movement.
|
||||
|
||||
$ xeyes
|
||||
|
||||

|
||||
xeyes command in action
|
||||
|
||||
### 6. cowsay Command ###
|
||||
|
||||
Do you remember last time we introduced command, which is useful in output of desired text with animated character cow. What if you want other animal in place of cow? Check a list of available animals.
|
||||
|
||||
$ cowsay -l
|
||||
|
||||
How about Elephant inside ASCII Snake?
|
||||
|
||||
$ cowsay -f elephant-in-snake Tecmint is Best
|
||||
|
||||

|
||||
cowsay command in action
|
||||
|
||||
How about Elephant inside ASCII goat?
|
||||
|
||||
$ cowsay -f gnu Tecmint is Best
|
||||
|
||||

|
||||
cowsay goat in action
|
||||
|
||||
That’s all for now. I’ll be here again with another interesting article. Till then stay update and connected to Tecmint. Don’t forget to provide us with your valuable feedback in the comments below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/linux-funny-commands/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:http://www.tecmint.com/20-funny-commands-of-linux-or-linux-is-fun-in-terminal/
|
||||
[2]:http://www.tecmint.com/play-with-word-and-character-counts-in-linux/
|
||||
@ -0,0 +1,176 @@
|
||||
Fun in Linux Terminal – Play with Word and Character Counts
|
||||
================================================================================
|
||||
Linux command line has a lot of fun around itself and many tedious task can be performed very easily yet with perfection. Playing with words and characters, their frequency in a text file, etc is what we are going to see in this article.
|
||||
|
||||
The only command that comes to our mind, for tweaking Linux command line to manipulate words and characters from a text file is [wc command][1].
|
||||
|
||||

|
||||
|
||||
A ‘**wc**‘ command which stands for word count is capable of Printing Newline, word & byte counts from a text file.
|
||||
|
||||
To work with the small scripts to analyze text file, we must have a text file. To maintain uniformity, we are creating a text file with the output of man command, as described below.
|
||||
|
||||
$ man man > man.txt
|
||||
|
||||
The above command creates a text file ‘**man.txt**‘ with the content of ‘**manual page**‘ for ‘man‘ command.
|
||||
|
||||
We want to check the most common words, in the above created ‘**Text File**‘ by running the below script.
|
||||
|
||||
$ cat man.txt | tr ' ' '\012' | tr '[:upper:]' '[:lower:]' | tr -d '[:punct:]' | grep -v '[^a-z]' | sort | uniq -c | sort -rn | head
|
||||
|
||||
### Sample Output ###
|
||||
|
||||
7557
|
||||
262 the
|
||||
163 to
|
||||
112 is
|
||||
112 a
|
||||
78 of
|
||||
78 manual
|
||||
76 and
|
||||
64 if
|
||||
63 be
|
||||
|
||||
The above one liner simple script shows, ten most frequently appearing words and their frequency of appearance, in the text file.
|
||||
|
||||
How about breaking down a word into individual using following command.
|
||||
|
||||
$ echo 'tecmint team' | fold -w1
|
||||
|
||||
### Sample Output ###
|
||||
|
||||
t
|
||||
e
|
||||
c
|
||||
m
|
||||
i
|
||||
n
|
||||
t
|
||||
t
|
||||
e
|
||||
a
|
||||
m
|
||||
|
||||
**Note**: Here, ‘-w1′ is for width.
|
||||
|
||||
Now we will be breaking down every single word in a text file, sort the result and get the desired output with the frequency of ten most frequent characters.
|
||||
|
||||
$ fold -w1 < man.txt | sort | uniq -c | sort -rn | head
|
||||
|
||||
### Sample Output ###
|
||||
|
||||
8579
|
||||
2413 e
|
||||
1987 a
|
||||
1875 t
|
||||
1644 i
|
||||
1553 n
|
||||
1522 o
|
||||
1514 s
|
||||
1224 r
|
||||
1021 l
|
||||
|
||||
How about getting most frequent characters in the text file with uppercase and lowercase differently along with their occurrence frequency.
|
||||
|
||||
$ fold -w1 < man.txt | sort | tr '[:lower:]' '[:upper:]' | uniq -c | sort -rn | head -20
|
||||
|
||||
### Sample Output ###
|
||||
|
||||
11636
|
||||
2504 E
|
||||
2079 A
|
||||
2005 T
|
||||
1729 I
|
||||
1645 N
|
||||
1632 S
|
||||
1580 o
|
||||
1269 R
|
||||
1055 L
|
||||
836 H
|
||||
791 P
|
||||
766 D
|
||||
753 C
|
||||
725 M
|
||||
690 U
|
||||
605 F
|
||||
504 G
|
||||
352 Y
|
||||
344 .
|
||||
|
||||
Check the above output, where punctuation mark is included. Lets strip out punctuation, with ‘**tr**‘ command. Here we go:
|
||||
|
||||
$ fold -w1 < man.txt | tr '[:lower:]' '[:upper:]' | sort | tr -d '[:punct:]' | uniq -c | sort -rn | head -20
|
||||
|
||||
### Sample Output ###
|
||||
|
||||
11636
|
||||
2504 E
|
||||
2079 A
|
||||
2005 T
|
||||
1729 I
|
||||
1645 N
|
||||
1632 S
|
||||
1580 O
|
||||
1550
|
||||
1269 R
|
||||
1055 L
|
||||
836 H
|
||||
791 P
|
||||
766 D
|
||||
753 C
|
||||
725 M
|
||||
690 U
|
||||
605 F
|
||||
504 G
|
||||
352 Y
|
||||
|
||||
Now I have three text files, lets run the above one liner script to see the output.
|
||||
|
||||
$ cat *.txt | fold -w1 | tr '[:lower:]' '[:upper:]' | sort | tr -d '[:punct:]' | uniq -c | sort -rn | head -8
|
||||
|
||||
### Sample Output ###
|
||||
|
||||
11636
|
||||
2504 E
|
||||
2079 A
|
||||
2005 T
|
||||
1729 I
|
||||
1645 N
|
||||
1632 S
|
||||
1580 O
|
||||
|
||||
Next we will be generating those infrequent letters that are at least ten letters long. Here is the simple script.
|
||||
|
||||
$ cat man.txt | tr '' '\012' | tr '[:upper:]' '[:lower:]' | tr -d '[:punct:]' | tr -d '[0-9]' | sort | uniq -c | sort -n | grep -E '..................' | head
|
||||
|
||||
### Sample Output ###
|
||||
|
||||
1 ──────────────────────────────────────────
|
||||
1 a all
|
||||
1 abc any or all arguments within are optional
|
||||
1 able see setlocale for precise details
|
||||
1 ab options delimited by cannot be used together
|
||||
1 achieved by using the less environment variable
|
||||
1 a child process returned a nonzero exit status
|
||||
1 act as if this option was supplied using the name as a filename
|
||||
1 activate local mode format and display local manual files
|
||||
1 acute accent
|
||||
|
||||
**Note**: The more and more dots in the above script till all the results are generated. We can use .{10} to get ten character matches.
|
||||
|
||||
These simple scripts, also make us know most frequent appearing words and characters in English.
|
||||
|
||||
That’s all for now. I’ll be here again with another interesting and off the beat topic worth knowing, which you people will love to read. Don’t forget to provide us with your valuable feedback in comment section, below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/play-with-word-and-character-counts-in-linux/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:http://www.tecmint.com/wc-command-examples/
|
||||
@ -1,50 +0,0 @@
|
||||
有人知道 Apache Mesos 项目帮助 Mesosphere 公司从 Andreessen Horowitz 那里筹集了 1000 万美元吗?
|
||||
================================================================================
|
||||

|
||||
|
||||
[Mesosphere][1],一家试图以鲜为人知的 Apache Mesos 项目为中心开展商业活动的公司,刚刚从 Andreessen Horowitz 那里获得了 1000 万美元投资。以下是为什么这个项目能够吸引如此巨款的原因。
|
||||
|
||||
事实上 Mesos 这款自动扩放软件在五年前就开发出来了。据 Mesosphere 的首席执行官及联合创始人 Florian Leibert 所述,Mesos 已经在 Twitter 上被超过 50,000 的核心使用。同时 EBay, AirBnB, Netflix 还有 HubSpot 也是这款软件的使用者。
|
||||
|
||||
当那些互联网巨头发现发现 Mesos 的时候,这项技术却并不为大多数企业所知。但它确实可以满足一些公司试图在公共云采取技术措施,使得他们自己可以访问内部数据中心的需求。
|
||||
|
||||
Mesos 管理集群机器,根据需要自动扩放应用。它在每台机器上只依赖很少的软件 ———— 据 Leibert 所说,其处理器的占用为 0 并且几乎不消耗任何内存 ———— 会与一个主调度程序相协调。在其工作的每台机器上的该软件会向调度程序报告关于虚拟机或者服务器的容量信息,接着调度程序向目标机器分派任务。
|
||||
|
||||
“如果一项任务终断并且没有返回任何结果,在 Mesos 的协助下,管理员将重启该任务并能知道该任务在何处终断,” Mesosphere 的资深副总裁 Matt Trifiro 说。
|
||||
|
||||
Mesos 能自动扩放一系列的工作包括 Hadoop 数据库,Ruby 运行干线上的节点,以及 Cassandra 。
|
||||
|
||||
使用 Mesos 使得 Hubspot 在 AWS(Amazon Web Services) 的账单上削减了一半的支出,Liebert 说道。这是因为 Mesos 能够在目标机器之间有效地分配作业量的原因。
|
||||
|
||||
然而,Mesos 更有可能应用于企业中去,这些企业试图实质地内部创建一个类 AWS 环境,一位来自 451 Research 的分析员 Jay Lyman 说。AWS 提供一些[自动扩放工具][3]。但大多数公司对于在公共云基础设施上运行所有东西还是感到不安。与此同时,他们并不企图阻止他们的开发者采用 AWS 那样的公共云中可用的优异性能。他们希望他们的私有云能集成这些可用的优点。
|
||||
|
||||
“如你所见,AWS 风格的界面风格与守旧主义、命令、操控以及稳定性相融合,” Liebert 继续说道。
|
||||
|
||||
Mesos 既可以在一个私有云上也可以在 AWS 上运行,向企业提供最有效率地使用其内部云的方法,并在需要扩放时自动切换到 AWS 去。
|
||||
|
||||
但是,以某种角度观察 Mesos 也是有一些缺点的。它[并不能运行][4]任何 Windows 操作系统或者比较古老的应用比如说 SAP 软件。
|
||||
|
||||
不过,Lyman 说,“假如一个团队拥有长时期使用云的经历,他们大概早就对 Linux 操作系统情有独钟了。”
|
||||
|
||||
在将来,Mesosphere 能够支持 Windows 操作系统是很有可能的。最初,像 Puppet 和 Chef 这样的技术也只支持 Linux 操作系统,Lyman 表示。“这预示了早期 Mesosphere 的特性。现在它还是不太成熟,” 他又说道。
|
||||
|
||||
Mesosphere 正瞄向大部分构建了与日俱增的运行于 Linux 操作系统的应用的企业,以及使用现代编程语言如同 Twitter 和 Netflix 这类刚成立不久还未具备 Mesos 这种技术的初代 Web 2.0 公司。“这是早期两类最常见的客户概况,” Trifiro 说。
|
||||
|
||||
年终之前,Mesosphere 希望发布包含文档的商务产品,通过技术支持与颁发许可证来获得收入。Mesosphere 已开发一款名为 Marathon 的大规模扩放编制工具,并且支持融入 Docker 中。它现在免费提供打包过的 Mesos 分发,希望以此占有未来的市场。
|
||||
|
||||
Mesosphere 同时也正在为少数早期的顾客工作。它帮助 HubSpot 实施有关 Mesos 的搭建。
|
||||
|
||||
Mesosphere 在这个领域并不唯一。Rightscale,Scalr 以及现在归 Dell 所有的 Enstratius,全都提供了一些扩放或云管理技术的版本实例。Mesosphere 强调说其开发的技术 Mesos 在单独机器中创建服务器集群方面的表现远胜于市场上的其他同类软件。来自 Andreessen 的新投资一定会帮助 Meos 获得新生。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://thenewstack.io/little-known-apache-mesos-project-helps-mesosphere-raise-10m-from-andreessen/
|
||||
|
||||
译者:[SteveArcher](https://github.com/SteveArcher) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://mesosphere.io/
|
||||
[2]:http://mesos.apache.org/
|
||||
[3]:http://aws.amazon.com/autoscaling/
|
||||
[4]:http://mesosphere.io/learn/
|
||||
@ -0,0 +1,54 @@
|
||||
“Linux之父——莱纳斯•托瓦德斯是我的英雄”说这话的是13岁的扎卡里杜邦
|
||||
================================================================================
|
||||

|
||||
|
||||
Zachary DuPon是一个6年级学生他马上满13岁。他是使用Arch liunx的用户并期待着安装Gentoo Linux
|
||||
|
||||
Zachary DuPon的故事是这样的-他的学校组织了一个计划给哪里的学生,要求他们写一封信给他们的英雄,大多数孩子写给名人,而Zachary DuPon写了现代科技世界的“真”英雄-莱纳斯•托瓦德斯
|
||||
|
||||
由于莱纳斯在家工作,他没有透露工作的地点,Zach的信来到了Linux基金会,在浏览的信件之前,发送给了莱纳斯。当基金会看到了这封信,他们联系了扎克的学校然后,being as generous as they are,邀请他到LinuxCon,以便他能遇到他的英雄。
|
||||
|
||||
linux的执行董事长Jim Zemlin,引领Zach到讨论小组的人群之后。Zach遇到了莱纳斯并得到了经过linux之父签名的linux圣经;他也收到了莱纳自己书的签名 [只为了好玩:一个意外的革命][1]
|
||||
|
||||

|
||||
莱纳斯•托沃兹为扎克里杜邦签名书
|
||||
|
||||

|
||||
扎克里杜邦的家人
|
||||
|
||||

|
||||
Swapnil Bhartiya和扎克里杜邦
|
||||
|
||||
我不想失去这个机会,所以我走近了杜邦家族,他们已经和莱纳斯开始谈话,于是安排了这个采访视频。
|
||||
|
||||
我是一个两岁孩子的父亲,而作为一名父亲,我是真正的惊讶怎样的信心,在善于表达和聪明的扎克的思想里
|
||||
|
||||
相反我告诉你我们谈论什么,我提供给你这个视屏采访
|
||||
|
||||
注:Youtube 视频,发布的时候不行改成一个链接吧
|
||||
<iframe scrolling="no" frameborder="0" allowfullscreen="" mozallowfullscreen="" webkitallowfullscreen="" src="//www.youtube-nocookie.com/embed/pHK5mfLdmRs?autoplay=0" class="arve-inner"></iframe>
|
||||
|
||||
这是一些采访的事件:
|
||||
|
||||
- 他使用Arch linux
|
||||
他计划他一旦变成好的程序员做出的贡献
|
||||
他没有提交任何漏洞报告,并认为他应该。他也表示他没有出现任何漏
|
||||
(这行未翻译)
|
||||
他喜欢KDE的原始桌面,但是它在他的网关机器上工作不时很好
|
||||
他是一个Debian GNU/linux用户和XFCE桌面环境
|
||||
|
||||
|
||||
莱纳斯也是扎克英雄,但是扎克是整个GNU/linux和自由软件社区的英雄,谁不断地提醒我们,我们的未来是在伟大的支持里。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.themukt.com/2014/08/24/linus-torvalds-hero-says-13-years-old-zachary-dupont/
|
||||
|
||||
作者:[wapnil Bhartiya][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.themukt.com/author/swapnil_bhartiya/
|
||||
[1]:http://www.amazon.com/gp/product/0066620732/ref=as_li_tl?ie=UTF8&camp=1789&creative=9325&creativeASIN=0066620732&linkCode=as2&tag=muktware-20&linkId=HBKEBIFVZQC35GGK
|
||||
115
translated/tech/20140813 How to remove file metadata on Linux.md
Normal file
115
translated/tech/20140813 How to remove file metadata on Linux.md
Normal file
@ -0,0 +1,115 @@
|
||||
移除Linux系统上的文件元数据
|
||||
================================================================================
|
||||
|
||||
典型的数据文件通常关联着“元数据”,其包含这个文件的描述信息,表现为一系列属性-值的集合。元数据一般包括创建者名称、生成文件的工具、文件创建/修改时期、创建位置和编辑历史等等。EXIF(镜像标准)、RDF(web资源)和DOI(数字文档)是几种流行的元数据标准。
|
||||
|
||||
|
||||
虽然元数据在数据管理领域有它的优点,但事实上它会[危害][1]你的隐私。相机图片中的EXIF格式数据会泄露出可识别的个人信息,比如相机型号、拍摄相关的GPS坐标和用户偏爱的照片编辑软件等。在文档和电子表格中的元数据包含作者/所属单位信息和相关的编辑历史。不一定这么绝对,但诸如[metagoofil][2]一类的元数据收集工具在信息收集的过程中常最作为入侵测试的一部分被利用。
|
||||
|
||||
对那些想要从共享数据中擦除一切个人元数据的用户来说,有一些方法从数据文件中移除元数据。你可以使用已有的文档或图片编辑软件,通常有自带的元数据编辑功能。在这个教程里,我会介绍一种不错的、单独的**元数据清理工具**,其目标只有一个:**匿名一切私有元数据**。
|
||||
|
||||
[MAT][3](元数据匿名工具箱)是一款专业的元数据清理器,使用Python编写。它在Tor工程旗下开发而成,在[Trails][4]上衍生出标准,后者是一种私人增强的live操作系统。【翻译得别扭,麻烦修正:)】
|
||||
|
||||
与诸如[exiftool][5]等只能对有限数量的文件类型进行写入的工具相比,MAT支持从各种各样的文件中消除元数据:图片(png、jpg)、文档(odt、docx、pptx、xlsx和pdf)、归档文件(tar、tar.bz2)和音频(mp3、ogg、flac)等。
|
||||
|
||||
### 在Linux上安装MAT ###
|
||||
|
||||
在基于Debian的系统(Ubuntu或Linux Mint)上,已经打包好MAT,所以安装很直接:
|
||||
|
||||
$ sudo apt-get install mat
|
||||
|
||||
在Fedora上,并没有预先生成的MAT包,所以你需要从源码生成。这是我在Fedora上生成MAT的步骤(不成功的话,请查看教程底部):
|
||||
|
||||
$ sudo yum install python-devel intltool python-pdfrw perl-Image-ExifTool python-mutagen
|
||||
$ sudo pip install hachoir-core hachoir-parser
|
||||
$ wget https://mat.boum.org/files/mat-0.5.tar.xz
|
||||
$ tar xf mat-0.5.tar.xz
|
||||
$ cd mat-0.5
|
||||
$ python setup.py install
|
||||
|
||||
### 使用MAT-GUI匿名元数据 ###
|
||||
|
||||
一旦安装好,通过GUI和命令行都可以使用MAT。输入这个命令启动MAT的GUI:
|
||||
|
||||
$ mat-gui
|
||||
|
||||
尝试清理一个包含如下内置元数据的实例文档文件(如private.odt)。
|
||||
|
||||

|
||||
|
||||
点击“添加”按钮来添加需要清理的文件到MAT中。一旦载入文件,点击“确认”按钮对所有隐藏的元数据信息进行扫描。
|
||||
|
||||

|
||||
|
||||
只要元数据被MAT检测到,“State”状态就会被标记成“Dirty”。双击文件可以查看检测到的元数据。
|
||||
|
||||

|
||||
|
||||
点击“清理”按钮来清除文件中的元数据。MAT会自动清空文件中的所有私有元数据字段。
|
||||
|
||||

|
||||
|
||||
清除后的状态中不包含任何私有可辨识的痕迹:
|
||||
|
||||

|
||||
|
||||
### 从命令行匿名元数据 ###
|
||||
|
||||
$ mat -c .
|
||||
|
||||
正如前面提到的,另一种调用MAT的方式是从命令行,使用mat命令可达到。
|
||||
|
||||
为了检查任何敏感的元数据,先前往文件所在的目录,然后运行:
|
||||
|
||||
$ mat -c .
|
||||
|
||||
这样会扫描当前目录和其子目录下的所有文件,并报告它们的状态(已清理或未清理)。
|
||||
|
||||

|
||||
|
||||
你可以使用“-d”选项来查看检测到的真实元数据:
|
||||
|
||||
$ mat -d <input_file>
|
||||
|
||||

|
||||
|
||||
如果不为mat命令提供任何选项,默认操作会移除文件的元数据。如果要在清理的过程中保留原始文件的备份,使用“-b”选项。下面命令会清除所有文件的元数据,并将原始文件存储为“*.bak”文件。
|
||||
|
||||
$ mat -b .
|
||||
|
||||

|
||||
|
||||
查看所支持的文件类型,请运行:
|
||||
|
||||
$ mat -l
|
||||
|
||||

|
||||
|
||||
### 故障排除 ###
|
||||
|
||||
当前我在Fedora上使用编译版本的MAT遇到了下列问题。当我尝试在Fedora清除归档/文档文件的元数据时(如*.gz、*.odt、*.docx),MAT因为下列错误失败。如果你知道如何解决这个问题,请在评论里回复我。
|
||||
|
||||
File "/usr/lib64/python2.7/zipfile.py", line 305, in __init__
|
||||
raise ValueError('ZIP does not support timestamps before 1980')
|
||||
ValueError: ZIP does not support timestamps before 1980
|
||||
|
||||
### 总结 ###
|
||||
|
||||
MAT是一款简单但非常好用的工具,用来预防从元数据中无意泄露私人数据。请注意如果有必要,还是需要你去隐藏文件内容。MAT能做的是消除与文件相关的元数据,但并不会对文件本身进行任何操作。简而言之,MAT是一名救生员,因为它可以处理大多数常见的元数据移除,但不应该只指望它来保证你的隐私。[译者注:养成良好的隐私保护意识和习惯才是最好的方法]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/08/remove-file-metadata-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[KayGuoWhu](https://github.com/KayGuoWhu)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://www.theguardian.com/world/2013/sep/30/nsa-americans-metadata-year-documents
|
||||
[2]:http://code.google.com/p/metagoofil/
|
||||
[3]:https://mat.boum.org/
|
||||
[4]:https://tails.boum.org/
|
||||
[5]:http://xmodulo.com/2013/08/view-or-edit-pdf-and-image-metadata-from-command-line-on-linux.html
|
||||
@ -0,0 +1,121 @@
|
||||
配置Linux访问控制列表(ACL)
|
||||
================================================================================
|
||||
使用拥有权限控制的Liunx,工作是一件轻松的任务。它可以定义任何user,group和other的权限。无论是在桌面电脑或者不会有很多用户的虚拟Linux实例,或者当用户不愿意分享他们之间的文件时,这样的工作是很棒的。然而,如果你是在一个大型组织,你运行了NFS或者Samba服务给不同的用户。然后你将会需要灵活的挑选并设置很多复杂的配置和权限去满足你的组织不同的需求。
|
||||
|
||||
Linux(和其他Unix,兼容POSIX的)所以拥有访问控制列表(ACL),它是一种分配权限之外的普遍范式。例如,默认情况下你需要确认3个权限组:owner,group和other。使用ACL,你可以增加权限给其他用户或组别,而不单只是简单的"other"或者是拥有者不存在的组别。可以允许指定的用户A、B、C拥有写权限而不再是让他们整个组拥有写权限。
|
||||
|
||||
ACL支持多种Linux文件系统,包括ext2, ext3, ext4, XFS, Btfrs, 等。如果你不确定你的文件系统是否支持ACL,请参考文档。
|
||||
|
||||
### 在文件系统使ACL生效 ###
|
||||
|
||||
首先,我们需要安装工具来管理ACL。
|
||||
|
||||
Ubuntu/Debian 中:
|
||||
|
||||
$ sudo apt-get install acl
|
||||
|
||||
CentOS/Fedora/RHEL 中:
|
||||
|
||||
# yum -y install acl
|
||||
|
||||
Archlinux 中:
|
||||
|
||||
# pacman -S acl
|
||||
|
||||
出于演示目的,我将使用ubuntu server版本,其他版本类似。
|
||||
|
||||
安装ACL完成后,需要激活我们磁盘分区的ACL功能,这样我们才能使用它。
|
||||
|
||||
首先,我们检查ACL功能是否已经开启。
|
||||
|
||||
$ mount
|
||||
|
||||

|
||||
|
||||
你可以注意到,我的root分区中ACL属性已经开启。万一你没有开启,你需要编辑/etc/fstab文件。增加acl标记,在你需要开启ACL的分区之前。
|
||||
|
||||

|
||||
|
||||
现在我们需要重新挂载分区(我喜欢完全重启,因为我不想丢掉数据),如果你对任何分区开启ACL,你必须也重新挂载它。
|
||||
|
||||
$ sudo mount / -o remount
|
||||
|
||||
令人敬佩!现在我们已经在我们的系统中开启ACL,让我们开始和它一起工作。
|
||||
|
||||
### ACL 范例 ###
|
||||
|
||||
基础ACL通过两条命令管理:**setfacl**用于增加或者修改ACL,**getfacl**用于显示分配完的ACL。让我们来做一些测试。
|
||||
|
||||
我创建一个目录/shared给一个假设的用户,名叫freeuser
|
||||
|
||||
$ ls -lh /
|
||||
|
||||

|
||||
|
||||
我想要分享这个目录给其他两个用户test和test2,一个拥有完整权限,另一个只有读权限。
|
||||
|
||||
First, to set ACLs for user test:
|
||||
首先,为用户test设置ACL:
|
||||
|
||||
$ sudo setfacl -m u:test:rwx /shared
|
||||
|
||||
现在用户test可以随意创建文件夹,文件和访问在/shared目录下的任何地方。
|
||||
|
||||

|
||||
|
||||
现在我们增加只读权限给用户test2:
|
||||
|
||||
$ sudo setfacl -m u:test2:rx /shared
|
||||
|
||||
注意test2读取目录需要执行(x)权限
|
||||
|
||||

|
||||
|
||||
让我来解释下setfacl命令格式:
|
||||
|
||||
- **-m** 表示修改ACL。你可以增加新的,或修改存在的ACL
|
||||
- **u:** 表示用户。你可以使用 **g** 来设置组权限
|
||||
- **test** 用户名
|
||||
- **:rwx** 需要设置的权限。
|
||||
|
||||
现在让我向你展示如何读取ACL:
|
||||
|
||||
$ ls -lh /shared
|
||||
|
||||

|
||||
|
||||
你可以注意到,正常权限后多一个+标记。这表示ACL已经设置成功。为了真正读取ACL,我们需要运行:
|
||||
|
||||
$ sudo getfacl /shared
|
||||
|
||||

|
||||
|
||||
最后,如果你需要移除ACL:
|
||||
|
||||
$ sudo setfacl -x u:test /shared
|
||||
|
||||

|
||||
|
||||
如果你想要立即擦除所有ACL条目:
|
||||
|
||||
$ sudo setfacl -b /shared
|
||||
|
||||

|
||||
|
||||
最后一件事。在设置了ACL文件或目录工作时,cp和mv命令会改变这些设置。在cp的情况下,需要添加“p”参数来复制ACL设置。如果这不可行,它将会展示一个警告。mv默认移动ACL设置,如果这也不可行,它也会向您展示一个警告。
|
||||
|
||||
### 总结 ###
|
||||
|
||||
使用ACL给了在你想要分享的文件上巨大的权利和控制,特别是在NFS/Samba服务。此外,如果你的主管共享主机,这个工具是必备的。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/08/configure-access-control-lists-acls-linux.html
|
||||
|
||||
作者:[Christopher Valerio][a]
|
||||
译者:[VicYu](http://www.vicyu.net)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/valerio
|
||||
@ -1,27 +1,27 @@
|
||||
Linux Systemd —— 在RHEL/CentOS 7中启动/停止/重启服务
|
||||
================================================================================
|
||||
|
||||
RHEL/CentOS 7.0中一个最主要的改变,就是切换到了**systemd**。它用于替代红帽企业版Linux的前任版本中的SysV和Upstart,对系统和服务进行管理。systemd兼容SysV和Linux标准组的启动脚本。
|
||||
RHEL/CentOS 7.0中一个最主要的改变,就是切换到了**systemd**。它用于替代红帽企业版Linux前任版本中的SysV和Upstart,对系统和服务进行管理。systemd兼容SysV和Linux标准组的启动脚本。
|
||||
|
||||
**Systemd**是一个Linux操作系统下的系统和服务管理器。它被设计成向后兼容SysV启动脚本,并提供了大量的特性,如开机时平行启动系统服务,按需启动守护进程,支持系统状态快照,或者基于依赖的服务控制逻辑。
|
||||
|
||||
先前的使用SysV初始化或Upstart的红帽企业版Linux版本中,使用位于/etc/rc.d/init.d/目录中的bash初始化脚本进行管理。而在RHEL 7/CentOS 7中,这些启动脚本被服务单元取代了。服务单元以.service扩展结束,提供了与初始化脚本同样的用途。要查看、启动、停止、重启、启用或者禁用系统服务,你要使用systemctl来代替旧的service命令。
|
||||
先前的使用SysV初始化或Upstart的红帽企业版Linux版本中,使用位于/etc/rc.d/init.d/目录中的bash初始化脚本进行管理。而在RHEL 7/CentOS 7中,这些启动脚本被服务单元取代了。服务单元以.service文件扩展结束,提供了与初始化脚本同样的用途。要查看、启动、停止、重启、启用或者禁用系统服务,你要使用systemctl来代替旧的service命令。
|
||||
|
||||
> 注:为了向后兼容,旧的service命令在CentOS 7中仍然可用,它会重定向所有命令到新的systemctl工具。
|
||||
>
|
||||
|
||||
### 使用systemctl来启动/停止/重启服务 ###
|
||||
|
||||
要启动一个服务,你需要使用像这样的命令:
|
||||
要启动一个服务,你需要使用如下命令:
|
||||
|
||||
# systemctl start httpd.service
|
||||
|
||||
这会启动httpd服务,就我们而言,Apache HTTP服务器。
|
||||
|
||||
要停掉它,可以以root身份使用该命令:
|
||||
要停掉它,需要以root身份使用该命令:
|
||||
|
||||
# systemctl stop httpd.service
|
||||
|
||||
要重启,你可以使用restart选项,如果服务在运行中,它将重启服务;或者使用start,如果服务不在运行。你也可以使用try-start选项,它只会在服务已经在运行中的时候重启服务。同时,reload选项你也可以有,它会重新加载配置文件。
|
||||
要重启,你可以使用restart选项,如果服务在运行中,它将重启服务;如果服务不在运行中,它将会启动。你也可以使用try-start选项,它只会在服务已经在运行中的时候重启服务。同时,reload选项你也可以有,它会重新加载配置文件。
|
||||
|
||||
# systemctl restart httpd.service
|
||||
# systemctl try-restart httpd.service
|
||||
@ -54,7 +54,7 @@ RHEL/CentOS 7.0中一个最主要的改变,就是切换到了**systemd**。它
|
||||
|
||||

|
||||
|
||||
虽然在过去的几年中,对systemd的采用饱受争议,然而大多数主流发行版都已经逐渐采用或打算在下一个发行版中采用它。所以,它是一个有用的工具,我们需要好好熟悉它。
|
||||
虽然在过去的几年中,对systemd的采用饱受争议,然而大多数主流发行版都已经逐渐采用或打算在下一个发行版中采用它。所以,它是一个有用的工具,我们需要好好熟悉它。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -62,7 +62,7 @@ via: http://linoxide.com/linux-command/start-stop-services-systemd/
|
||||
|
||||
作者:[Adrian Dinu][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
|
||||
@ -0,0 +1,152 @@
|
||||
Linux终端:speedtest_cli检测你的实时带宽速度
|
||||
===
|
||||
|
||||

|
||||
|
||||
什么是你在家(或者办公室)的上传和下载速度?你能保证,你支付费用给ISP的同时,你得到了等价的回报?
|
||||
|
||||
为了测试我们因特网连接的速度,当下存在着一些因特网服务,比如说SpeedTest,这是一种可以通过Web浏览器和手机应用程序浏览的web服务
|
||||
|
||||
现在,你可以很容易地检测你的网速,使用speedtest_cli同样很简单,它是一个使用[speedtest.net][2]来测试因特网[带宽][1]的命令行界面。通过这种方式,你也可以在没有浏览器或者图形化界面的服务器上做带宽测试
|
||||
|
||||
### 安装 ###
|
||||
|
||||
speedtest_cli是一个python脚本,所以它真的很容易安装和使用,你拥有许多方式安装它:
|
||||
|
||||
#### 1)pip / easy_install ####
|
||||
|
||||
打开一个终端,输入下面的命令:
|
||||
|
||||
pip install speedtest_cli
|
||||
|
||||
或者
|
||||
|
||||
easy_install speedtest_cli
|
||||
|
||||
#### 2)Github ####
|
||||
|
||||
想要直接从github安装,你得这么做:
|
||||
|
||||
pip install git+https://github.com/sivel/speedtest-cli.git
|
||||
|
||||
或者
|
||||
|
||||
git clone https://github.com/sivel/speedtest-cli.git
|
||||
python speedtest-cli/setup.py install
|
||||
|
||||
#### 3)作为Ubuntu/Debian或者Mint包 ####
|
||||
|
||||
getdeb仓库给我们提供了[安装包][3],按照下面的步骤,就可以轻松安装:
|
||||
|
||||
- 安装[getdeb包][4]
|
||||
或者
|
||||
- 手动地配置仓库:
|
||||
进入系统管理软件源,第三方软件选项,加上:
|
||||
|
||||
deb http://archive.getdeb.net/ubuntu trusty-getdeb apps
|
||||
|
||||
增加仓库GPG钥匙,打开终端窗口,然后输入:
|
||||
|
||||
wget -q -O- http://archive.getdeb.net/getdeb-archive.key | sudo apt-key add -
|
||||
|
||||
现在,你就可以使用下面的命令安装speedtest_cli包了:
|
||||
|
||||
sudo apt-get update
|
||||
sudo apt-get install python-speedtest-cli
|
||||
|
||||
#### 4)下载(和以前的方式一样) ####
|
||||
|
||||
作为最后的选择,只需要下载python脚本,然后在你想运行的地方运行脚本:
|
||||
|
||||
wget -O speedtest-cli https://raw.github.com/sivel/speedtest-cli/master/speedtest_cli.py
|
||||
chmod +x speedtest-cli
|
||||
|
||||
或者
|
||||
|
||||
curl -o speedtest-cli https://raw.github.com/sivel/speedtest-cli/master/speedtest_cli.py
|
||||
chmod +x speedtest-cli
|
||||
|
||||
### 基本用法 ###
|
||||
|
||||
你可以不带任何选项地运行speedtest_cli.py,然后你会在终端获得关于你带宽速度的报告,这就是我蹩脚的意大利Adsl输出:
|
||||
|
||||
$ ./speedtest_cli.py
|
||||
Retrieving speedtest.net configuration...
|
||||
Retrieving speedtest.net server list...
|
||||
Testing from Telecom Italia (87.13.73.66)...
|
||||
Selecting best server based on latency...
|
||||
Hosted by LepidaSpA (Bologna) [12.20 km]: 104.347 ms
|
||||
Testing download speed........................................
|
||||
Download: 6.35 Mbits/s
|
||||
Testing upload speed...............................................
|
||||
Upload: 0.34 Mbits/s
|
||||
|
||||
这就是简简单单的基本用法,这足以让你知道你因特网连接的好坏,但是有可能,你需要和朋友分享这条信息,为了到达此目的,只需要-share选项
|
||||
|
||||
./speedtest_cli.py --share
|
||||
Retrieving speedtest.net configuration...
|
||||
Retrieving speedtest.net server list...
|
||||
Testing from Telecom Italia (87.13.73.66)...
|
||||
Selecting best server based on latency...
|
||||
Hosted by LepidaSpA (Bologna) [12.20 km]: 93.778 ms
|
||||
Testing download speed........................................
|
||||
Download: 6.20 Mbits/s
|
||||
Testing upload speed...............................................
|
||||
Upload: 0.33 Mbits/s
|
||||
Share results: http://www.speedtest.net/result/3700218352.png
|
||||
|
||||
这将会产生一个类似于下面的图像(但是我希望你图像里面的值更好):
|
||||
|
||||

|
||||
|
||||
另一个有趣的选项是-list,它会按照距离列出所有speedtest.net服务器,下面是我运行的结果:
|
||||
|
||||
Retrieving speedtest.net configuration...
|
||||
Retrieving speedtest.net server list...
|
||||
2872) LepidaSpA (Bologna, Italy) [12.20 km]
|
||||
1561) MYNETWAY S.R.L. (Cesena, Italy) [80.97 km]
|
||||
2710) ReteIVO by D.t.s. Srl (Florence, Italy) [90.90 km]
|
||||
4826) Inteplanet Srl (Verona, Italy) [100.45 km]
|
||||
3998) Wolnext srl (Verona, Italy) [100.45 km]
|
||||
2957) Wifiweb s.r.l. (Altavilla Vicentina, Italy) [103.11 km]
|
||||
3103) E4A s.r.l. (Vicenza, Italy) [107.17 km]
|
||||
3804) Interplanet Srl (Vicenza, Italy) [107.17 km]
|
||||
1014) NTRnet (Vicenza, Italy) [107.17 km]
|
||||
3679) Hynet s r l (Vicenza, Italy) [107.17 km]
|
||||
3745) Comeser Srl (Fidenza, Italy) [114.00 km]
|
||||
5011) Welcomeitalia spa (Massarosa, Italy) [119.26 km]
|
||||
2864) ReteIVO by D.t.s. Srl (Massa, Italy) [120.92 km]
|
||||
2918) ReteIVO by D.t.s. Srl (Arezzo, Italy) [129.79 km]
|
||||
...
|
||||
|
||||
现在,我知道围绕在我周围的服务器的ID,我可以使用-server选项选择一个特定的服务器,所以,为了选择位于Florence(ID 2710)的服务器,我使用下面的命令:
|
||||
|
||||
./speedtest_cli.py --server 2710
|
||||
Retrieving speedtest.net configuration...
|
||||
Retrieving speedtest.net server list...
|
||||
Testing from Telecom Italia (87.13.73.66)...
|
||||
Hosted by ReteIVO by D.t.s. Srl (Florence) [90.90 km]: 106.505 ms
|
||||
Testing download speed........................................
|
||||
Download: 6.18 Mbits/s
|
||||
Testing upload speed..............................................
|
||||
Upload: 0.35 Mbits/s
|
||||
|
||||
文章由[Asapy Programming Company][5]发表
|
||||
|
||||
---
|
||||
|
||||
via: http://linuxaria.com/howto/linux-terminal-speedtest_cli-checks-you
|
||||
r-real-bandwidth-speed
|
||||
|
||||
译者:[su-kaiyao](https://github.com/su-kaiyao)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://linuxaria.com/article/tool-command-line-bandwidth-linux
|
||||
[2]:http://linuxaria.com/howto/speedtest.net
|
||||
[3]:http://www.getdeb.net/
|
||||
[4]:http://archive.getdeb.net/install_deb/getdeb-repository_0.1-1~getde
|
||||
b1_all.deb
|
||||
[5]:http://www.asapy.com/
|
||||
|
||||
Loading…
Reference in New Issue
Block a user