diff --git a/sources/news/20141208 U.S. Marine Corps Wants to Change OS for Radar System from Windows XP to Linux.md b/sources/news/20141208 U.S. Marine Corps Wants to Change OS for Radar System from Windows XP to Linux.md
deleted file mode 100644
index 2be8c37e18..0000000000
--- a/sources/news/20141208 U.S. Marine Corps Wants to Change OS for Radar System from Windows XP to Linux.md
+++ /dev/null
@@ -1,49 +0,0 @@
-Traslating by H-mudcup
-
-U.S. Marine Corps Wants to Change OS for Radar System from Windows XP to Linux
-================================================================================
-**A new radar system has been sent back for upgrade**
-
-
-
-
-
-
-
-
-
-
-
-
-
-> When it comes to stability and performance, nothing can really beat Linux. This is why the U.S. Marine Corps leaders have decided to ask Northrop Grumman Corp. Electronic Systems to change the operating system of the newly delivered Ground/Air Task-Oriented Radar (G/ATOR) from Windows XP to Linux.
-
-The Ground/Air Task-Oriented Radar (G/ATOR) system has been in the works for many years and it's very likely that when the project was started, Windows XP could have been considered the logical choice. In the mean time, things changed. Microsoft has pulled the support for Windows XP and very few entities still use it. The operating system is either upgraded or replaced. In this case, Linux is the logical choice, especially since the replacement cost are probably much smaller than an eventual upgrade.
-
-It's interesting to note that the Ground/Air Task-Oriented Radar (G/ATOR) was just delivered to the U.S. Marine Corps, but the company that built it chose to keep that aging operating system. Someone must have noticed the fact that it was a poor decision and the chain of command was informed of the problems that might have appeared.
-
-### G/ATOR radar software will be Linux-based ###
-
-Unix systems, like BSD-based or Linux-based OSes, are usually found in critical areas and technologies that can't fail, under any circumstances. That's why most of the servers out there are running Linux servers, for example. Having a radar system with an operating systems that is very unlikely to crash seems to fit the bill perfectly.
-
-"Officials of the Marine Corps Systems Command at Quantico Marine Base, Va., announced a $10.2 million contract modification Wednesday to the Northrop Grumman Corp. Electronic Systems segment in Linthicum Heights, Md., to convert the Ground/Air Task-Oriented Radar (G/ATOR) operator command and control computer from Windows XP to Linux. The contract modification will incorporate a change order to switch the G/ATOR control computer from the Microsoft Windows XP operating system to a Defense Information Systems Agency (DISA)-compliant Linux operating system."
-
-'G/ATOR is an expeditionary, three-dimensional, short-to-medium-range multi-role radar system designed to detect low-observable targets with low radar cross sections such as rockets, artillery, mortars, cruise missiles, and UAVs," reads the entry on [militaryaerospace.com][1].
-
-This piece of military technology, the Ground/Air Task-Oriented Radar (G/ATOR) was first contracted from the Northrop Grumman Corp. back in 2005, so it's easy to understand why the US Marines might want to hurry this up. No time frame has been proposed for the switch.
-
-视频链接:[http://youtu.be/H2ppl4x-eu8][2]
-
---------------------------------------------------------------------------------
-
-via: http://news.softpedia.com/news/U-S-Marine-Corps-Want-to-Change-OS-for-Radar-System-from-Windows-XP-to-Linux-466756.shtml
-
-作者:[Silviu Stahie][a]
-译者:[译者ID](https://github.com/译者ID)
-校对:[校对者ID](https://github.com/校对者ID)
-
-本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
-
-[a]:http://news.softpedia.com/editors/browse/silviu-stahie
-[1]:http://www.militaryaerospace.com/articles/2014/12/gator-linux-software.html
-[2]:http://youtu.be/H2ppl4x-eu8
diff --git a/sources/share/20141106 Flow' N Play Movie Player Has a Stylish Interface Ubuntu Installation.md b/sources/share/20141106 Flow' N Play Movie Player Has a Stylish Interface Ubuntu Installation.md
deleted file mode 100644
index 357a3b6e6c..0000000000
--- a/sources/share/20141106 Flow' N Play Movie Player Has a Stylish Interface Ubuntu Installation.md
+++ /dev/null
@@ -1,55 +0,0 @@
-Flow ‘N Play Movie Player Has a Stylish Interface [Ubuntu Installation]
-================================================================================
-**Flow ‘N Play** is a new video player written in Qt which features a pretty slick and simple interface which provides only the basic features for playing movies.
-
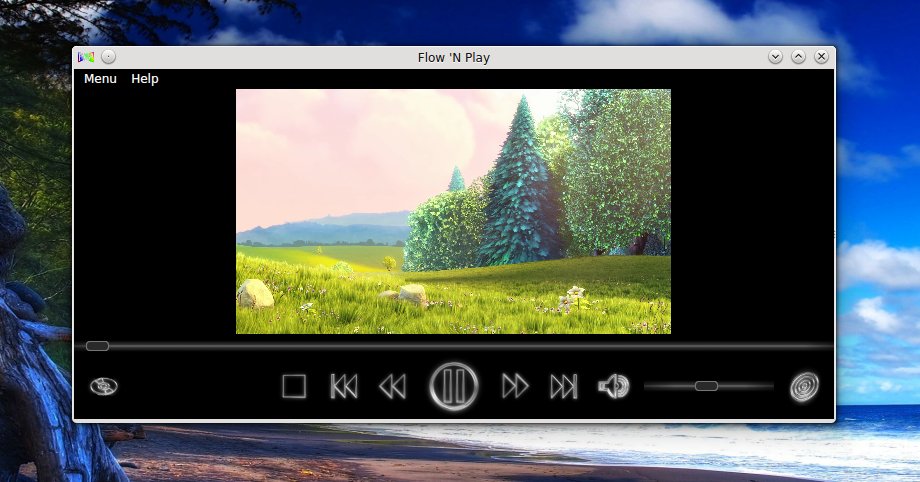
-
-
-[Flow ‘N Play][1] is relatively new video player (the first release was made earlier this year in March) with a beautiful interface and a pretty simple approach, with one of the features being the possibility to slide over the list of movies by dragging the mouse. The player comes with basic functionality, a search function, support for colored themes.
-
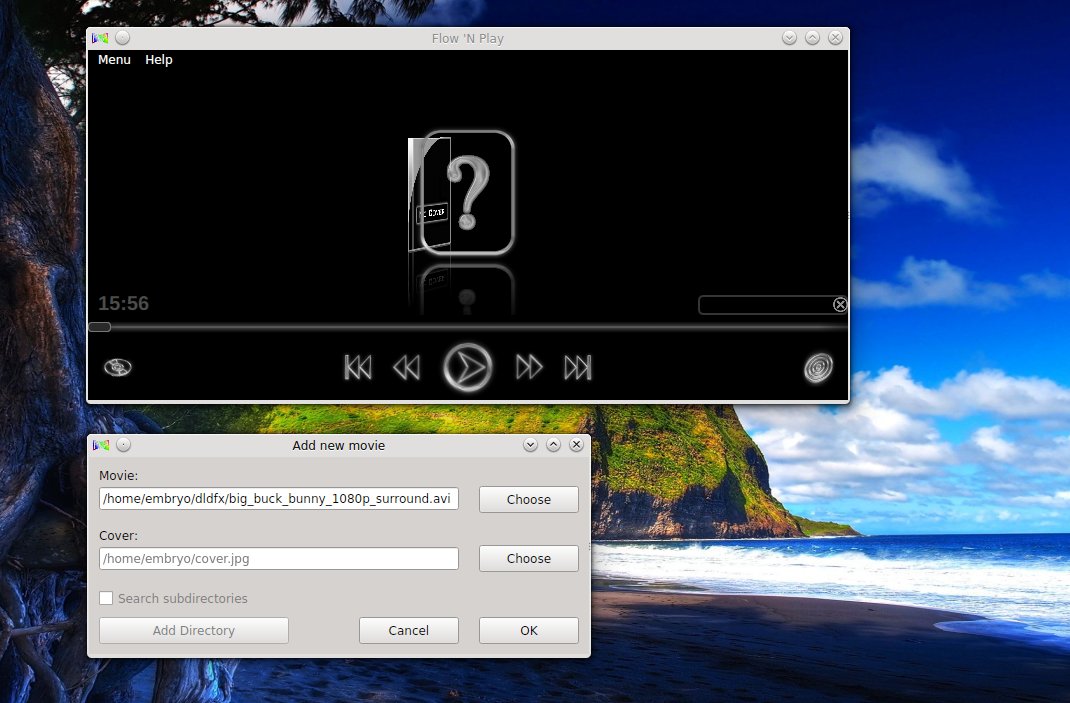
-Opening a new video – you can also choose a custom cover in the same dialog:
-
-
-
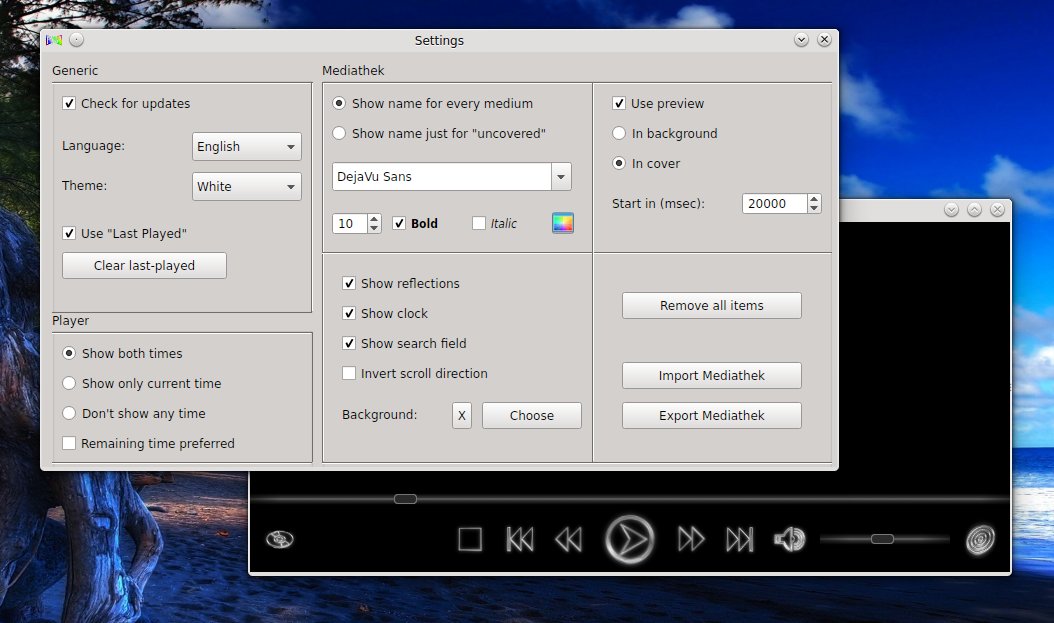
-The Settings dialog – customize some basic options here:
-
-
-
-Flow ‘N Play is still in early development though, and as such it has a few downsides over more advanced players. There are few options to customize it, no support for subtitles or video and audio filters. Currently there seems to be either a bug or strange behavior upon opening a new movie, which doesn’t always start automatically.
-
-I believe a few more features could be added before it gets to being usable as a decent alternative to other players, but given the time, Flow ‘N Play looks really promising.
-
-### Install Flow ‘N Play 0.922 in Ubuntu 14.04 ###
-
-There are several different ways to install Flow N’ Play in Ubuntu. There are DEB packages, RUN Bash installers, and standalone binaries available on the [Qt-Apps page][2].
-
-To install Flow ‘N Play first get the dependencies:
-
- sudo apt-get install libqt5multimediaquick-p5 qtdeclarative5-controls-plugin qtdeclarative5 qtmultimedia-plugin qtdeclarative5-qtquick2-plugin qtdeclarative5-quicklayouts-plugin
-
-Then download the DEB package and either double click it or change the working directory to the one where you saved it and type the following in a terminal (for 64-bit, replace the DEB file for 32-bit):
-
- sudo dpkg -i flow-n-play_v0.926_qt-5.3.2_x64.deb
-
-Then type **flow-n-play** in a terminal to run it. Notice that in case you get dependency errors when trying to install the DEB file, you can run **sudo apt-get -f install**, which will fetch the missing dependencies automatically and will install Flow ‘N Play as well.
-
-To install Flow ‘N Play using the RUN script, install the dependencies mentioned above and then run the script:
-
- wget -O http://www.prest1ge-c0ding.24.eu/programs/Flow-N-Play/v0.926/bin/flow-n-play_v0.926_qt-5.3.2_x64.run
- sudo ./flow-n-play_v0.926_qt-5.3.2_x64.run
-
-The third method is to install it manually to a location of your choice (just download the binary provided after installing the dependencies) e.g. for 32-bit:
-
- wget -O http://www.prest1ge-c0ding.24.eu/programs/Flow-N-Play/v0.926/bin/Flow-N-Play_v0.926_Qt-5.3.2_x86
-
---------------------------------------------------------------------------------
-
-via: http://www.tuxarena.com/2014/11/flow-n-play-movie-player-has-a-stylish-interface-ubuntu-installation/
-
-作者:Craciun Dan
-译者:[译者ID](https://github.com/译者ID)
-校对:[校对者ID](https://github.com/校对者ID)
-
-本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
-
-[1]:http://www.prest1ge-c0ding.24.eu/programme-php/app-flow_n_play.php?lang=en
-[2]:http://qt-apps.org/content/show.php/Flow+%27N+Play?content=167736
\ No newline at end of file
diff --git a/sources/talk/20141222 A brief history of Linux malware.md b/sources/talk/20141222 A brief history of Linux malware.md
index f9898b3734..07c8d82907 100644
--- a/sources/talk/20141222 A brief history of Linux malware.md
+++ b/sources/talk/20141222 A brief history of Linux malware.md
@@ -1,3 +1,4 @@
+[translating by KayGuoWhu]
A brief history of Linux malware
================================================================================
A look at some of the worms and viruses and Trojans that have plagued Linux throughout the years.
diff --git a/sources/tech/20141027 ntpq -p output.md b/sources/tech/20141027 ntpq -p output.md
deleted file mode 100644
index 6b70e90235..0000000000
--- a/sources/tech/20141027 ntpq -p output.md
+++ /dev/null
@@ -1,301 +0,0 @@
-“ntpq -p” output
-================================================================================
-The [Gentoo][1] (and others?) [incomplete man pages for “ntpq -p”][2] merely give the description: “*Print a list of the peers known to the server as well as a summary of their state.*”
-
-I had not seen this documented, hence here is a summary that can be used in addition to the brief version of the man page “[man ntpq][3]“. More complete details are given on: “[ntpq – standard NTP query program][4]” (source author), and [other examples of the man ntpq pages][5].
-
-[NTP][6] is a protocol designed to synchronize the clocks of computers over a ([WAN][7] or [LAN][8]) [udp][9] network. From [Wikipedia – NTP][10]:
-
-> The Network Time Protocol (NTP) is a protocol and software implementation for synchronizing the clocks of computer systems over packet-switched, variable-latency data networks. Originally designed by David L. Mills of the University of Delaware and still maintained by him and a team of volunteers, it was first used before 1985 and is one of the oldest Internet protocols.
-
-For an awful lot more than you might ever want to know about time and NTP, see “[The NTP FAQ, Time, what Time?][11]” and the current [RFCs for NTP][12]. The earlier “Network Time Protocol (Version 3) RFC” ([txt][13], or [pdf][14], Appendix E, The NTP Timescale and its Chronometry, p70) includes an interesting explanation of the changes in, and relations between, our timekeeping systems over the past 5000 years or so. Wikipedia gives a broader view in the articles [Time][15] and [Calendar][16].
-
-The command “ntpq -p” outputs a table such as for example:
-
- remote refid st t when poll reach delay offset jitter
- ==============================================================================
- LOCAL(0) .LOCL. 10 l 96h 64 0 0.000 0.000 0.000
- *ns2.example.com 10.193.2.20 2 u 936 1024 377 31.234 3.353 3.096
-
-### Further detail: ###
-
-#### Table headings: ####
-
-
-- **remote** – The remote peer or server being synced to. “LOCAL” is this local host (included in case there are no remote peers or servers available);
-- **refid** – Where or what the remote peer or server is itself synchronised to;
-- **st** – The remote peer or server [Stratum][17]
-- **t** – Type (u: [unicast][18] or [manycast][19] client, b: [broadcast][20] or [multicast][21] client, l: local reference clock, s: symmetric peer, A: manycast server, B: broadcast server, M: multicast server, see “[Automatic Server Discovery][22]“);
-- **when** – When last polled (seconds ago, “h” hours ago, or “d” days ago);
-- **poll** – Polling frequency: [rfc5905][23] suggests this ranges in NTPv4 from 4 (16s) to 17 (36h) (log2 seconds), however observation suggests the actual displayed value is seconds for a much smaller range of 64 (26) to 1024 (210) seconds;
-- **reach** – An 8-bit left-shift shift register value recording polls (bit set = successful, bit reset = fail) displayed in [octal][24];
-- **delay** – Round trip communication delay to the remote peer or server (milliseconds);
-- **offset** – Mean offset (phase) in the times reported between this local host and the remote peer or server ([RMS][25], milliseconds);
-- **jitter** – Mean deviation (jitter) in the time reported for that remote peer or server (RMS of difference of multiple time samples, milliseconds);
-
-#### Select Field tally code: ####
-
-The first character displayed in the table (Select Field tally code) is a state flag (see [Peer Status Word][26]) that follows the sequence ” “, “x”, “-“, “#”, “+”, “*”, “o”:
-
-
-- ”** **” – No state indicated for:
- - non-communicating remote machines,
- - “LOCAL” for this local host,
- - (unutilised) high stratum servers,
- - remote machines that are themselves using this host as their synchronisation reference;
-- “**x**” – Out of tolerance, do not use (discarded by intersection algorithm);
-- “**-**” – Out of tolerance, do not use (discarded by the cluster algorithm);
-- “**#**” – Good remote peer or server but not utilised (not among the first six peers sorted by synchronization distance, ready as a backup source);
-- “**+**” – Good and a preferred remote peer or server (included by the combine algorithm);
-- “*****” – The remote peer or server presently used as the primary reference;
-- “**o**” – PPS peer (when the prefer peer is valid). The actual system synchronization is derived from a pulse-per-second (PPS) signal, either indirectly via the PPS reference clock driver or directly via kernel interface.
-
-See the [Clock Select Algorithm][27].
-
-#### “refid”: ####
-
-The **refid** can have the status values:
-
-
-- An IP address – The [IP address][28] of a remote peer or server;
-- **.LOCL.** – This local host (a place marker at the lowest stratum included in case there are no remote peers or servers available);
-- **.PPS.** – “[Pulse Per Second][29]” from a time standard;
-- **.IRIG.** – [Inter-Range Instrumentation Group][30] time code;
-- **.ACTS.** – American [NIST time standard][31] telephone modem;
-- **.NIST.** – American NIST time standard telephone modem;
-- **.PTB.** – German [PTB][32] time standard telephone modem;
-- **.USNO.** – American [USNO time standard][33] telephone modem;
-- **.CHU.** – [CHU][34] ([HF][35], Ottawa, ON, Canada) time standard radio receiver;
-- **.DCFa.** – [DCF77][36] ([LF][37], Mainflingen, Germany) time standard radio receiver;
-- **.HBG.** – [HBG][38] (LF Prangins, Switzerland) time standard radio receiver;
-- **.JJY.** – [JJY][39] (LF Fukushima, Japan) time standard radio receiver;
-- **.LORC.** – [LORAN][40]-C station ([MF][41]) time standard radio receiver. Note, [no longer operational][42] (superseded by [eLORAN][43]);
-- **.MSF.** – [MSF][44] (LF, Anthorn, Great Britain) time standard radio receiver;
-- **.TDF.** – [TDF][45] (MF, Allouis, France) time standard radio receiver;
-- **.WWV.** – [WWV][46] (HF, Ft. Collins, CO, America) time standard radio receiver;
-- **.WWVB.** – [WWVB][47] (LF, Ft. Collins, CO, America) time standard radio receiver;
-- **.WWVH.** – [WWVH][48] (HF, Kauai, HI, America) time standard radio receiver;
-- **.GOES.** – American [Geosynchronous Orbit Environment Satellite][49];
-- **.GPS.** – American [GPS][50];
-- **.GAL.** – [Galileo][51] European [GNSS][52];
-- **.ACST.** – manycast server;
-- **.AUTH.** – authentication error;
-- **.AUTO.** – Autokey sequence error;
-- **.BCST.** – broadcast server;
-- **.CRYPT.** – Autokey protocol error;
-- **.DENY.** – access denied by server;
-- **.INIT.** – association initialized;
-- **.MCST.** – multicast server;
-- **.RATE.** – (polling) rate exceeded;
-- **.TIME.** – association timeout;
-- **.STEP.** – step time change, the offset is less than the panic threshold (1000ms) but greater than the step threshold (125ms).
-
-#### Operation notes ####
-
-A time server will report time information with no time updates from clients (unidirectional updates), whereas a peer can update fellow participating peers to converge upon a mutually agreed time (bidirectional updates).
-
-During [initial startup][53]:
-
-> Unless using the iburst option, the client normally takes a few minutes to synchronize to a server. If the client time at startup happens to be more than 1000s distant from NTP time, the daemon exits with a message to the system log directing the operator to manually set the time within 1000s and restart. If the time is less than 1000s but more than 128s distant, a step correction occurs and the daemon restarts automatically.
-
-> When started for the first time and a frequency file is not present, the daemon enters a special mode in order to calibrate the frequency. This takes 900s during which the time is not [disciplined][54]. When calibration is complete, the daemon creates the frequency file and enters normal mode to amortize whatever residual offset remains.
-
-Stratum 0 devices are such as atomic (caesium, rubidium) clocks, GPS clocks, or other time standard radio clocks providing a time signal to the Stratum 1 time servers. NTP reports [UTC][55] (Coordinated Universal Time) only. Client programs/utilities then use [time zone][56] data to report local time from the synchronised UTC.
-
-The protocol is highly accurate, using a resolution of less than a nanosecond (about 2-32 seconds). The time resolution achieved and other parameters for a host (host hardware and operating system limited) is reported by the command “ntpq -c rl” (see [rfc1305][57] Common Variables and [rfc5905][58]).
-
-#### “ntpq -c rl” output parameters: ####
-
-- **precision** is rounded to give the next larger integer power of two. The achieved resolution is thus 2precision (seconds)
-- **rootdelay** – total roundtrip delay to the primary reference source at the root of the synchronization subnet. Note that this variable can take on both positive and negative values, depending on clock precision and skew (seconds)
-- **rootdisp** – maximum error relative to the primary reference source at the root of the synchronization subnet (seconds)
-- **tc** – NTP algorithm [PLL][59] (phase locked loop) or [FLL][60] (frequency locked loop) time constant (log2)
-- **mintc** – NTP algorithm PLL/FLL minimum time constant or ‘fastest response’ (log2)
-- **offset** – best and final offset determined by the combine algorithm used to discipline the system clock (ms)
-- **frequency** – system clock period (log2 seconds)
-- **sys_jitter** – best and final jitter determined by the combine algorithm used to discipline the system clock (ms)
-- **clk_jitter** – host hardware(?) system clock jitter (ms)
-- **clk_wander** – host hardware(?) system clock wander ([PPM][61] – parts per million)
-
-Jitter (also called timing jitter) refers to short-term variations in frequency with components greater than 10Hz, while wander refers to long-term variations in frequency with components less than 10Hz. (Stability refers to the systematic variation of frequency with time and is synonymous with aging, drift, trends, etc.)
-
-#### Operation notes (continued) ####
-
-The NTP software maintains a continuously updated drift correction. For a correctly configured and stable system, a reasonable expectation for modern hardware synchronising over an uncongested internet connection is for network client devices to be synchronised to within a few milliseconds of UTC at the time of synchronising to the NTP service. (What accuracy can be expected between peers on an uncongested Gigabit LAN?)
-
-Note that for UTC, a [leap second][62] can be inserted into the reported time up to twice a year to allow for variations in the Earth’s rotation. Also beware of the one hour time shifts for when local times are reported for “[daylight savings][63]” times. Also, the clock for a client device will run independently of UTC until resynchronised oncemore, unless that device is calibrated or a drift correction is applied.
-
-#### [What happens during a Leap Second?][64] ####
-
-> During a leap second, either one second is removed from the current day, or a second is added. In both cases this happens at the end of the UTC day. If a leap second is inserted, the time in UTC is specified as 23:59:60. In other words, it takes two seconds from 23:59:59 to 0:00:00 instead of one. If a leap second is deleted, time will jump from 23:59:58 to 0:00:00 in one second instead of two. See also [The Kernel Discipline][65].
-
-So… What actually is the value for the step threshold: 125ms or 128ms? And what are the PLL/FLL tc units (log2 s? ms?)? And what accuracy can be expected between peers on an uncongested Gigabit LAN?
-
-
-
-Thanks for comments from Camilo M and Chris B. Corrections and further details welcomed.
-
-Cheers,
-Martin
-
-### Apocrypha: ###
-
-- The [epoch for NTP][66] starts in year 1900 while the epoch in UNIX starts in 1970.
-- [Time corrections][67] are applied gradually, so it may take up to three hours until the frequency error is compensated.
-- [Peerstats and loopstats][68] can be logged to [summarise/plot time offsets and errors][69]
-- [RMS][70] – Root Mean Square
-- [PLL][71] – Phase locked loop
-- [FLL][72] – Frequency locked loop
-- [PPM][73] – Parts per million, used here to describe rate of time drift
-- [man ntpq (Gentoo brief version)][74]
-- [man ntpq (long version)][75]
-- [man ntpq (Gentoo long version)][76]
-
-### See: ###
-
-- [ntpq – standard NTP query program][77]
-- [The Network Time Protocol (NTP) Distribution][78]
-- A very brief [history][79] of NTP
-- A more detailed brief history: “Mills, D.L., A brief history of NTP time: confessions of an Internet timekeeper. Submitted for publication; please do not cite or redistribute” ([pdf][80])
-- [NTP RFC][81] standards documents
-- Network Time Protocol (Version 3) RFC – [txt][82], or [pdf][83]. Appendix E, The NTP Timescale and its Chronometry, p70, includes an interesting explanation of the changes in, and relations between, our timekeeping systems over the past 5000 years or so
-- Wikipedia: [Time][84] and [Calendar][85]
-- [John Harrison and the Longitude problem][86]
-- [Clock of the Long Now][87] – The 10,000 Year Clock
-- John C Taylor – [Chronophage][88]
-- [Orders of magnitude of time][89]
-- The [Greenwich Time Signal][90]
-
-### Others: ###
-
-SNTP (Simple Network Time Protocol, [RFC 4330][91]) is basically also NTP, but lacks some internal algorithms for servers where the ultimate performance of a full NTP implementation based on [RFC 1305][92] is neither needed nor justified.
-
-The W32Time [Windows Time Service][93] is a non-standard implementation of SNTP, with no accuracy guarantees, and an assumed accuracy of no better than about a 1 to 2 second range. (Is that due to there being no system clock drift correction and a time update applied only once every 24 hours assumed for a [PC][94] with typical clock drift?)
-
-There is also the [PTP (IEEE 1588)][95] Precision Time Protocol. See Wikipedia: [Precision Time Protocol][96]. A software demon is [PTPd][97]. The significant features are that it is intended as a [LAN][98] high precision master-slave synchronisation system synchronising at the microsecond scale to a master clock for [International Atomic Time][99] (TAI, [monotonic][100], no leap seconds). Data packet timestamping can be appended by hardware at the physical layer by a network interface card or switch for example. Network kit supporting PTP can timestamp data packets in and out in a way that removes the delay effect of processing within the switch/router. You can run PTP without hardware timestamping but it might not synchronise if the time errors introduced are too great. Also it will struggle to work through a router (large delays) for the same reason.
-
-### Older time synchronization protocols: ###
-
-- DTSS – Digital Time Synchronisation Service by Digital Equipment Corporation, superseded by NTP. See an example of [DTSS VMS C code c2000][101]. (Any DTSS articles/documentation anywhere?)
-- [DAYTIME protocol][102], synchronization protocol using [TCP][103] or [UDP][104] port 13
-- [ICMP Timestamp][105] and [ICMP Timestamp Reply][106], synchronization protocol using [ICMP][107]
-- [Time Protocol][108], synchronization protocol using TCP or UDP port 37
-
---------------------------------------------------------------------------------
-
-via: http://nlug.ml1.co.uk/2012/01/ntpq-p-output/831
-
-作者:Martin L
-译者:[译者ID](https://github.com/译者ID)
-校对:[校对者ID](https://github.com/校对者ID)
-
-本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
-
-[1]:http://www.gentoo.org/
-[2]:http://nlug.ml1.co.uk/2012/01/man-ntpq-gentoo-brief-version/853
-[3]:http://www.thelinuxblog.com/linux-man-pages/1/ntpq
-[4]:http://www.eecis.udel.edu/~mills/ntp/html/ntpq.html
-[5]:http://linux.die.net/man/8/ntpq
-[6]:http://www.ntp.org/
-[7]:http://en.wikipedia.org/wiki/Wide_area_network
-[8]:http://en.wikipedia.org/wiki/Local_area_network
-[9]:http://en.wikipedia.org/wiki/User_Datagram_Protocol
-[10]:http://en.wikipedia.org/wiki/Network_Time_Protocol
-[11]:http://www.ntp.org/ntpfaq/NTP-s-time.htm
-[12]:http://www.ntp.org/rfc.html
-[13]:http://www.ietf.org/rfc/rfc1305.txt
-[14]:http://www.rfc-editor.org/rfc/rfc1305.pdf
-[15]:http://en.wikipedia.org/wiki/Time
-[16]:http://en.wikipedia.org/wiki/Calendar
-[17]:http://en.wikipedia.org/wiki/Network_Time_Protocol#Clock_strata
-[18]:http://en.wikipedia.org/wiki/Unicast
-[19]:http://www.eecis.udel.edu/~mills/ntp/html/manyopt.html#mcst
-[20]:http://en.wikipedia.org/wiki/Broadcasting_%28computing%29
-[21]:http://en.wikipedia.org/wiki/Multicast
-[22]:http://www.eecis.udel.edu/~mills/ntp/html/manyopt.html
-[23]:http://www.ietf.org/rfc/rfc5905.txt
-[24]:http://en.wikipedia.org/wiki/Octal#In_computers
-[25]:http://en.wikipedia.org/wiki/Root_mean_square
-[26]:http://www.eecis.udel.edu/~mills/ntp/html/decode.html#peer
-[27]:http://www.eecis.udel.edu/~mills/ntp/html/select.html
-[28]:http://en.wikipedia.org/wiki/Ip_address
-[29]:http://en.wikipedia.org/wiki/Pulse_per_second
-[30]:http://en.wikipedia.org/wiki/Inter-Range_Instrumentation_Group
-[31]:http://en.wikipedia.org/wiki/Standard_time_and_frequency_signal_service
-[32]:http://www.ptb.de/index_en.html
-[33]:http://en.wikipedia.org/wiki/United_States_Naval_Observatory#Time_service
-[34]:http://en.wikipedia.org/wiki/CHU_%28radio_station%29
-[35]:http://en.wikipedia.org/wiki/High_frequency
-[36]:http://en.wikipedia.org/wiki/DCF77
-[37]:http://en.wikipedia.org/wiki/Low_frequency
-[38]:http://en.wikipedia.org/wiki/HBG_%28time_signal%29
-[39]:http://en.wikipedia.org/wiki/JJY#Time_standards
-[40]:http://en.wikipedia.org/wiki/LORAN#Timing_and_synchronization
-[41]:http://en.wikipedia.org/wiki/Medium_frequency
-[42]:http://en.wikipedia.org/wiki/LORAN#The_future_of_LORAN
-[43]:http://en.wikipedia.org/wiki/LORAN#eLORAN
-[44]:http://en.wikipedia.org/wiki/Time_from_NPL#The_.27MSF_signal.27_and_the_.27Rugby_clock.27
-[45]:http://en.wikipedia.org/wiki/T%C3%A9l%C3%A9_Distribution_Fran%C3%A7aise
-[46]:http://en.wikipedia.org/wiki/WWV_%28radio_station%29#Time_signals
-[47]:http://en.wikipedia.org/wiki/WWVB
-[48]:http://en.wikipedia.org/wiki/WWVH
-[49]:http://en.wikipedia.org/wiki/GOES#Further_reading
-[50]:http://en.wikipedia.org/wiki/Gps#Timekeeping
-[51]:http://en.wikipedia.org/wiki/Galileo_%28satellite_navigation%29#The_concept
-[52]:http://en.wikipedia.org/wiki/Gnss
-[53]:http://www.eecis.udel.edu/~mills/ntp/html/debug.html
-[54]:http://www.ntp.org/ntpfaq/NTP-s-algo-kernel.htm
-[55]:http://en.wikipedia.org/wiki/Coordinated_Universal_Time
-[56]:http://en.wikipedia.org/wiki/Time_zone
-[57]:http://www.ietf.org/rfc/rfc1305.txt
-[58]:http://www.ietf.org/rfc/rfc5905.txt
-[59]:http://en.wikipedia.org/wiki/PLL
-[60]:http://en.wikipedia.org/wiki/Frequency-locked_loop
-[61]:http://en.wikipedia.org/wiki/Parts_per_million
-[62]:http://en.wikipedia.org/wiki/Leap_second
-[63]:http://en.wikipedia.org/wiki/Daylight_saving_time
-[64]:http://www.ntp.org/ntpfaq/NTP-s-time.htm#Q-TIME-LEAP-SECOND
-[65]:http://www.ntp.org/ntpfaq/NTP-s-algo-kernel.htm
-[66]:http://www.ntp.org/ntpfaq/NTP-s-algo.htm#AEN1895
-[67]:http://www.ntp.org/ntpfaq/NTP-s-algo.htm#Q-ACCURATE-CLOCK
-[68]:http://www.ntp.org/ntpfaq/NTP-s-trouble.htm#Q-TRB-MON-STATFIL
-[69]:http://www.ntp.org/ntpfaq/NTP-s-trouble.htm#AEN5086
-[70]:http://en.wikipedia.org/wiki/Root_mean_square
-[71]:http://en.wikipedia.org/wiki/PLL
-[72]:http://en.wikipedia.org/wiki/Frequency-locked_loop
-[73]:http://en.wikipedia.org/wiki/Parts_per_million
-[74]:http://nlug.ml1.co.uk/2012/01/man-ntpq-gentoo-brief-version/853
-[75]:http://nlug.ml1.co.uk/2012/01/man-ntpq-long-version/855
-[76]:http://nlug.ml1.co.uk/2012/01/man-ntpq-gentoo-long-version/856
-[77]:http://www.eecis.udel.edu/~mills/ntp/html/ntpq.html
-[78]:http://www.eecis.udel.edu/~mills/ntp/html/index.html
-[79]:http://www.ntp.org/ntpfaq/NTP-s-def-hist.htm
-[80]:http://www.eecis.udel.edu/~mills/database/papers/history.pdf
-[81]:http://www.ntp.org/rfc.html
-[82]:http://www.ietf.org/rfc/rfc1305.txt
-[83]:http://www.rfc-editor.org/rfc/rfc1305.pdf
-[84]:http://en.wikipedia.org/wiki/Time
-[85]:http://en.wikipedia.org/wiki/Calendar
-[86]:http://www.rmg.co.uk/harrison
-[87]:http://longnow.org/clock/
-[88]:http://johnctaylor.com/
-[89]:http://en.wikipedia.org/wiki/Orders_of_magnitude_%28time%29
-[90]:http://en.wikipedia.org/wiki/Greenwich_Time_Signal
-[91]:http://tools.ietf.org/html/rfc4330
-[92]:http://tools.ietf.org/html/rfc1305
-[93]:http://en.wikipedia.org/wiki/Network_Time_Protocol#Microsoft_Windows
-[94]:http://en.wikipedia.org/wiki/Personal_computer
-[95]:http://www.nist.gov/el/isd/ieee/ieee1588.cfm
-[96]:http://en.wikipedia.org/wiki/IEEE_1588
-[97]:http://ptpd.sourceforge.net/
-[98]:http://en.wikipedia.org/wiki/Local_area_network
-[99]:http://en.wikipedia.org/wiki/International_Atomic_Time
-[100]:http://en.wikipedia.org/wiki/Monotonic_function
-[101]:http://antinode.info/ftp/dtss_ntp/
-[102]:http://en.wikipedia.org/wiki/DAYTIME
-[103]:http://en.wikipedia.org/wiki/Transmission_Control_Protocol
-[104]:http://en.wikipedia.org/wiki/User_Datagram_Protocol
-[105]:http://en.wikipedia.org/wiki/ICMP_Timestamp
-[106]:http://en.wikipedia.org/wiki/ICMP_Timestamp_Reply
-[107]:http://en.wikipedia.org/wiki/Internet_Control_Message_Protocol
-[108]:http://en.wikipedia.org/wiki/Time_Protocol
diff --git a/sources/tech/20150104 Auditd--Tool for Security Auditing on Linux Server.md b/sources/tech/20150104 Auditd--Tool for Security Auditing on Linux Server.md
new file mode 100644
index 0000000000..9375385927
--- /dev/null
+++ b/sources/tech/20150104 Auditd--Tool for Security Auditing on Linux Server.md
@@ -0,0 +1,203 @@
+Auditd - Tool for Security Auditing on Linux Server
+================================================================================
+First of all , we wish all our readers **Happy & Prosperous New YEAR 2015** from our Linoxide team. So lets start this new year explaining about Auditd tool.
+
+Security is one of the main factor that we need to consider. We must maintain it because we don't want someone steal our data. Security includes many things. Audit, is one of it.
+
+On Linux system, we know that we have a tool named **auditd**. This tool is by default exist in most of Linux operating system. What is auditd tool and how to use it? We will cover it below.
+
+### What is auditd? ###
+
+Auditd or audit daemon, is a userspace component to the Linux Auditing System. It’s responsible for writing audit records to the disk.
+
+
+
+### Installing auditd ###
+
+On Ubuntu based system , we can use [wajig][1] tool or **apt-get tool** to install auditd.
+
+
+
+Just follow the instruction to get it done. Once it finish it will install some tools related to auditd tool. Here are the tools :
+
+- **auditctl ;** is a tool to control the behaviour of the daemon on the fly, adding rules, etc
+- **/etc/audit/audit.rules ;** is the file that contains audit rules
+- **aureport ;** is tool to generate and view the audit report
+- **ausearch ;** is a tool to search various events
+- **auditspd ;** is a tool which can be used to relay event notifications to other applications instead of writing them to disk in the audit log
+- **autrace ;** is a command that can be used to trace a process
+- **/etc/audit/auditd.conf ;** is the configuration file of auditd tool
+- When the first time we install **auditd**, there will be no rules available yet.
+
+We can check it using this command :
+
+ $ sudo auditctl -l
+
+
+
+To add rules on auditd, let’s continue to the section below.
+
+### How to use it ###
+
+#### Audit files and directories access ####
+
+One of the basic need for us to use an audit tool are, how can we know if someone change a file(s) or directories? Using auditd tool, we can do with those commands (please remember, we will need root privileges to configure auditd tool):
+
+**Audit files**
+
+ $ sudo auditctl -w /etc/passwd -p rwxa
+
+
+
+**With :**
+
+- **-w path ;** this parameter will insert a watch for the file system object at path. On the example above, auditd will wacth /etc/passwd file
+- **-p ; **this parameter describes the permission access type that a file system watch will trigger on
+- **rwxa ;** are the attributes which bind to -p parameter above. r is read, w is write, x is execute and a is attribute
+
+#### Audit directories ####
+
+To audit directories, we will use a similar command. Let’s take a look at the command below :
+
+ $ sudo auditctl -w /production/
+
+
+
+The above command will watch any access to the **/production folder**.
+
+Now, if we run **auditctl -l** command again, we will see that new rules are added.
+
+
+
+Now let’s see the audit log says.
+
+### Viewing the audit log ###
+
+After rules are added, now we can see how auditd in action. To view audit log, we can use **ausearch** tool.
+
+We already add rule to watch /etc/passwd file. Now we will try to use **ausearch** tool to view the audit log.
+
+ $ sudo ausearch -f /etc/passwd
+
+- **-f** parameter told ausearch to investigate /etc/passwd file
+- The result is shown below :
+> **time**->Mon Dec 22 09:39:16 2014
+> type=PATH msg=audit(1419215956.471:194): item=0 **name="/etc/passwd"** inode=142512 dev=08:01 mode=0100644 ouid=0 ogid=0 rdev=00:00 nametype=NORMAL
+> type=CWD msg=audit(1419215956.471:194): **cwd="/home/pungki"**
+> type=SYSCALL msg=audit(1419215956.471:194): arch=40000003 **syscall=5** success=yes exit=3 a0=b779694b a1=80000 a2=1b6 a3=b8776aa8 items=1 ppid=2090 pid=2231 **auid=4294967295 uid=1000 gid=1000** euid=0 suid=0 fsuid=0 egid=1000 sgid=1000 fsgid=1000 tty=pts0 ses=4294967295 **comm="sudo" exe="/usr/bin/sudo"** key=(null)
+
+ Now let’s we understand the result.
+
+- **time ;** is when the audit is done
+- **name ;** is the object name to be audited
+- **cwd ;** is the current directory
+- **syscall ;** is related syscall
+- **auid ;** is the audit user ID
+- **uid and gid ;** are User ID and Group ID of the user who access the file
+- **comm ;** is the command that the user is used to access the file
+- **exe ;** is the location of the command of comm parameter above
+- The above audit log is the original file.
+
+ Next, we are going to add a new user, to see how the auditd record the activity to /etc/passwd file.
+
+> **time->**Mon Dec 22 11:25:23 2014
+> type=PATH msg=audit(1419222323.628:510): item=1 **name="/etc/passwd.lock"** inode=143992 dev=08:01 mode=0100600 ouid=0 ogid=0 rdev=00:00 nametype=DELETE
+> type=PATH msg=audit(1419222323.628:510): item=0 **name="/etc/"** inode=131073 dev=08:01 mode=040755 ouid=0 ogid=0 rdev=00:00 nametype=PARENT
+> type=CWD msg=audit(1419222323.628:510): **cwd="/root"**
+> type=SYSCALL msg=audit(1419222323.628:510): arch=40000003 **syscall=10** success=yes exit=0 a0=bfc0ceec a1=0 a2=bfc0ceec a3=897764c items=2 ppid=2978 pid=2994 **auid=4294967295 uid=0 gid=0** euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=pts0 ses=4294967295 **comm="chfn" exe="/usr/bin/chfn"** key=(null)
+
+As we can see above, that on that particular time, **/etc/passwd was accessed** by user root (uid = 0 and gid = 0) **from** directory /root (cwd = /root). The /etc/passwd file was accessed using **chfn** command which located in **/usr/bin/chfn**
+
+If we type **man chfn** on the console, we will see more detail about what is chfn.
+
+
+
+Now we take a look at another example.
+
+We already told auditd to watch directory /production/ . That is a new directory. So when we try to use ausearch tool at the first time, it found nothing.
+
+
+
+Next, root account try to list the /production directory using ls command. The second time we use ausearch tool, it will show us some information.
+
+
+
+> **time->**Mon Dec 22 14:18:28 2014
+> type=PATH msg=audit(1419232708.344:527): item=0 **name="/production/"** inode=797104 dev=08:01 mode=040755 ouid=0 ogid=0 rdev=00:00 nametype=NORMAL
+> type=CWD msg=audit(1419232708.344:527): cwd="/root"
+> type=SYSCALL msg=audit(1419232708.344:527): arch=40000003 syscall=295 success=yes exit=3 a0=ffffff9c a1=95761e8 a2=98800 a3=0 items=1 ppid=3033 pid=3444 **auid=4294967295 uid=0 gid=0** euid=0 suid=0 fsuid=0 egid=0 sgid=0 fsgid=0 tty=pts0 ses=4294967295 **comm="ls" exe="/bin/ls"** key=(null)
+
+Similar with the previous one, we can determine that **/production folder was looked** by root account (uid=0 gid=0) **using ls command** (comm = ls) and the ls command is **located in /bin/ls folder**.
+
+### Viewing the audit reports ###
+
+Once we put the audit rules, it will run automatically. And after a period of time, we want to see how auditd can help us to track them.
+
+Auditd comes with another tool called **aureport**. As we can guess from its name, **aureport** is a tool that produces summary reports of the audit system log.
+
+We already told auditd to track /etc/passwd before. And a moment after the auditd parameter is developed, the audit.log file is created.
+
+To generate the report of audit, we can use aureport tool. Without any parameters, aureport will generate a summary report of audit activity.
+
+ $ sudo aureport
+
+
+
+As we can see, there are some information available which cover most important area.
+
+On the picture above we see there are **3 times failed authentication**. Using aureport, we can drill down to that information.
+
+We can use this command to look deeper on failed authentication :
+
+ $ sudo aureport -au
+
+
+
+As we can see on the picture above, there are two users which at the particular time are failed to authenticated
+
+If we want to see all events related to account modification, we can use -m parameter.
+
+ $ sudo aureport -m
+
+
+
+### Auditd configuration file ###
+
+Previously we already added :
+
+- $ sudo auditctl -w /etc/passwd -p rwxa
+- $ sudo auditctl -w /production/
+- Now, if we sure the rules are OK, we can add it into
+
+**/etc/audit/audit.rules** to make them permanently.Here’s how to put them into the /etc/audit/audit.rules fileSample of audit rule file
+
+
+
+**Then don’t forget to restart auditd daemon.**
+
+ # /etc/init.d/auditd restart
+
+OR
+
+ # service auditd restart
+
+
+
+### Conclusion ###
+
+Auditd is one of the audit tool that available on Linux system. You can explore more detail about auditd and its related tools by reading its manual page. For example, just type **man auditd** to see more detail about auditd. Or type **man ausearch** to see more detail about ausearch tool.
+
+**Please be careful before creating rules**. It will increase your log file size significantly if too much information to record.
+
+--------------------------------------------------------------------------------
+
+via: http://linoxide.com/how-tos/auditd-tool-security-auditing/
+
+作者:[Pungki Arianto][a]
+译者:[译者ID](https://github.com/译者ID)
+校对:[校对者ID](https://github.com/校对者ID)
+
+本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
+
+[a]:http://linoxide.com/author/pungki/
+[1]:http://linoxide.com/tools/wajig-package-management-debian/
\ No newline at end of file
diff --git a/sources/tech/20150104 Docker Image Insecurity.md b/sources/tech/20150104 Docker Image Insecurity.md
new file mode 100644
index 0000000000..261718f9c8
--- /dev/null
+++ b/sources/tech/20150104 Docker Image Insecurity.md
@@ -0,0 +1,132 @@
+Docker Image Insecurity
+================================================================================
+Recently while downloading an “official” container image with Docker I saw this line:
+
+ ubuntu:14.04: The image you are pulling has been verified
+
+I assumed this referenced Docker’s [heavily promoted][1] image signing system and didn’t investigate further at the time. Later, while researching the cryptographic digest system that Docker tries to secure images with, I had the opportunity to explore further. What I found was a total systemic failure of all logic related to image security.
+
+Docker’s report that a downloaded image is “verified” is based solely on the presence of a signed manifest, and Docker never verifies the image checksum from the manifest. An attacker could provide any image alongside a signed manifest. This opens the door to a number of serious vulnerabilities.
+
+Images are downloaded from an HTTPS server and go through an insecure streaming processing pipeline in the Docker daemon:
+
+ [decompress] -> [tarsum] -> [unpack]
+
+This pipeline is performant but completely insecure. Untrusted input should not be processed before verifying its signature. Unfortunately Docker processes images three times before checksum verification is supposed to occur.
+
+However, despite [Docker’s claims][2], image checksums are never actually checked. This is the only section[0][3] of Docker’s code related to verifying image checksums, and I was unable to trigger the warning even when presenting images with mismatched checksums.
+
+ if img.Checksum != "" && img.Checksum != checksum {
+ log.Warnf("image layer checksum mismatch: computed %q,
+ expected %q", checksum, img.Checksum)
+ }
+
+### Insecure processing pipeline ###
+
+**Decompress**
+
+Docker supports three compression algorithms: gzip, bzip2, and xz. The first two use the Go standard library implementations, which are [memory-safe][4], so the exploit types I’d expect to see here are denial of service attacks like crashes and excessive CPU and memory usage.
+
+The third compression algorithm, xz, is more interesting. Since there is no native Go implementation, Docker [execs][5] the `xz` binary to do the decompression.
+
+The xz binary comes from the [XZ Utils][6] project, and is built from approximately[1][7] twenty thousand lines of C code. C is not a memory-safe language. This means malicious input to a C program, in this case the Docker image XZ Utils is unpacking, could potentially execute arbitrary code.
+
+Docker exacerbates this situation by *running* `xz` as root. This means that if there is a single vulnerability in `xz`, a call to `docker pull` could result in the complete compromise of your entire system.
+
+**Tarsum**
+
+The use of tarsum is well-meaning but completely flawed. In order to get a deterministic checksum of the contents of an arbitrarily encoded tar file, Docker decodes the tar and then hashes specific portions, while excluding others, in a [deterministic order][8].
+
+Since this processing is done in order to generate the checksum, it is decoding untrusted data which could be designed to exploit the tarsum code[2][9]. Potential exploits here are denial of service as well as logic flaws that could cause files to be injected, skipped, processed differently, modified, appended to, etc. without the checksum changing.
+
+**Unpacking**
+
+Unpacking consists of decoding the tar and placing files on the disk. This is extraordinarily dangerous as there have been three other vulnerabilities reported[3][10] in the unpack stage at the time of writing.
+
+There is no situation where data that has not been verified should be unpacked onto disk.
+
+### libtrust ###
+
+[libtrust][11] is a Docker package that claims to provide “authorization and access control through a distributed trust graph.” Unfortunately no specification appears to exist, however it looks like it implements some parts of the [Javascript Object Signing and Encryption][12] specifications along with other unspecified algorithms.
+
+Downloading an image with a manifest signed and verified using libtrust is what triggers this inaccurate message (only the manifest is checked, not the actual image contents):
+
+ ubuntu:14.04: The image you are pulling has been verified
+
+Currently only “official” image manifests published by Docker, Inc are signed using this system, but from discussions I participated in at the last Docker Governance Advisory Board meeting[4][13], my understanding is that Docker, Inc is planning on deploying this more widely in the future. The intended goal is centralization with Docker, Inc controlling a Certificate Authority that then signs images and/or client certificates.
+
+I looked for the signing key in Docker’s code but was unable to find it. As it turns out the key is not embedded in the binary as one would expect. Instead the Docker daemon fetches it [over HTTPS from a CDN][14] before each image download. This is a terrible approach as a variety of attacks could lead to trusted keys being replaced with malicious ones. These attacks include but are not limited to: compromise of the CDN vendor, compromise of the CDN origin serving the key, and man in the middle attacks on clients downloading the keys.
+
+### Remediation ###
+
+I [reported][15] some of the issues I found with the tarsum system before I finished this research, but so far nothing I have reported has been fixed.
+
+Some steps I believe should be taken to improve the security of the Docker image download system:
+Drop tarsum and actually verify image digests
+
+Tarsum should not be used for security. Instead, images must be fully downloaded and their cryptographic signatures verified before any processing takes place.
+
+**Add privilege isolation**
+
+Image processing steps that involve decompression or unpacking should be run in isolated processes (containers?) that have only the bare minimum required privileges to operate. There is no scenario where a decompression tool like `xz` should be run as root.
+
+**Replace libtrust**
+
+Libtrust should be replaced with [The Update Framework][16] which is explicitly designed to solve the real problems around signing software binaries. The threat model is very comprehensive and addresses many things that have not been considered in libtrust. There is a complete specification as well as a reference implementation written in Python, and I have begun work on a [Go implementation][17] and welcome contributions.
+
+As part of adding TUF to Docker, a local keystore should be added that maps root keys to registry URLs so that users can have their own signing keys that are not managed by Docker, Inc.
+
+I would like to note that using non-Docker, Inc hosted registries is a very poor user experience in general. Docker, Inc seems content with relegating third party registries to second class status when there is no technical reason to do so. This is a problem both for the ecosystem in general and the security of end users. A comprehensive, decentralized security model for third party registries is both necessary and desirable. I encourage Docker, Inc to take this into consideration when redesigning their security model and image verification system.
+
+### Conclusion ###
+
+Docker users should be aware that the code responsible for downloading images is shockingly insecure. Users should only download images whose provenance is without question. At present, this does *not* include “trusted” images hosted by Docker, Inc including the official Ubuntu and other base images.
+
+The best option is to block `index.docker.io` locally, and download and verify images manually before importing them into Docker using `docker load`. Red Hat’s security blog has [a good post about this][18].
+
+Thanks to Lewis Marshall for pointing out the tarsums are never verified.
+
+- [Checksum code context][19].
+- [cloc][20] says 18,141 non-blank, non-comment lines of C and 5,900 lines of headers in v5.2.0.
+- Very similar bugs been [found in Android][21], which allowed arbitrary files to be injected into signed packages, and [the Windows Authenticode][22] signature system, which allowed binary modification.
+- Specifically: [CVE-2014-6407][23], [CVE-2014-9356][24], and [CVE-2014-9357][25]. There were two Docker [security releases][26] in response.
+- See page 8 of the [notes from the 2014-10-28 DGAB meeting][27].
+
+--------------------------------------------------------------------------------
+
+via: https://titanous.com/posts/docker-insecurity
+
+作者:[titanous][a]
+译者:[译者ID](https://github.com/译者ID)
+校对:[校对者ID](https://github.com/校对者ID)
+
+本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
+
+[a]:https://twitter.com/titanous
+[1]:https://blog.docker.com/2014/10/docker-1-3-signed-images-process-injection-security-options-mac-shared-directories/
+[2]:https://blog.docker.com/2014/10/docker-1-3-signed-images-process-injection-security-options-mac-shared-directories/
+[3]:https://titanous.com/posts/docker-insecurity#fn:0
+[4]:https://en.wikipedia.org/wiki/Memory_safety
+[5]:https://github.com/docker/docker/blob/0874f9ab77a7957633cd835241a76ee4406196d8/pkg/archive/archive.go#L91-L95
+[6]:http://tukaani.org/xz/
+[7]:https://titanous.com/posts/docker-insecurity#fn:1
+[8]:https://github.com/docker/docker/blob/0874f9ab77a7957633cd835241a76ee4406196d8/pkg/tarsum/tarsum_spec.md
+[9]:https://titanous.com/posts/docker-insecurity#fn:2
+[10]:https://titanous.com/posts/docker-insecurity#fn:3
+[11]:https://github.com/docker/libtrust
+[12]:https://tools.ietf.org/html/draft-ietf-jose-json-web-signature-11
+[13]:https://titanous.com/posts/docker-insecurity#fn:4
+[14]:https://github.com/docker/docker/blob/0874f9ab77a7957633cd835241a76ee4406196d8/trust/trusts.go#L38
+[15]:https://github.com/docker/docker/issues/9719
+[16]:http://theupdateframework.com/
+[17]:https://github.com/flynn/go-tuf
+[18]:https://securityblog.redhat.com/2014/12/18/before-you-initiate-a-docker-pull/
+[19]:https://github.com/docker/docker/blob/0874f9ab77a7957633cd835241a76ee4406196d8/image/image.go#L114-L116
+[20]:http://cloc.sourceforge.net/
+[21]:http://www.saurik.com/id/17
+[22]:http://blogs.technet.com/b/srd/archive/2013/12/10/ms13-098-update-to-enhance-the-security-of-authenticode.aspx
+[23]:https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6407
+[24]:https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-9356
+[25]:https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-9357
+[26]:https://groups.google.com/d/topic/docker-user/nFAz-B-n4Bw/discussion
+[27]:https://docs.google.com/document/d/1JfWNzfwptsMgSx82QyWH_Aj0DRKyZKxYQ1aursxNorg/edit?pli=1
\ No newline at end of file
diff --git a/sources/tech/20150104 How To Install Websvn In CentOS 7.md b/sources/tech/20150104 How To Install Websvn In CentOS 7.md
new file mode 100644
index 0000000000..8b77577dd6
--- /dev/null
+++ b/sources/tech/20150104 How To Install Websvn In CentOS 7.md
@@ -0,0 +1,123 @@
+How To Install Websvn In CentOS 7
+================================================================================
+**WebSVN** offers a view onto your subversion repositories that’s been designed to reflect the Subversion methodology. You can view the log of any file or directory and see a list of all the files changed, added or deleted in any given revision. You can also view the differences between two versions of a file so as to see exactly what was changed in a particular revision.
+
+### Features ###
+
+WebSVN offers the following features:
+
+- Easy to use interface;
+- Customisable templating system;
+- Colourisation of file listings;
+- Blame view;
+- Log message searching;
+- RSS feed support.
+
+### Installation ###
+
+I use the following link to install Subversion on CentOS 7.
+
+- [How To install Subversion On CentOS 7][1]
+
+**1 – Download the websvn to /var/www/html.**
+
+ cd /var/www/html
+
+----------
+
+ wget http://websvn.tigris.org/files/documents/1380/49057/websvn-2.3.3.zip
+
+**2 – Extract the zip package.**
+
+ unzip websvn-2.3.3.zip
+
+----------
+
+ mv websvn-2.3.3 websvn
+
+**3 – Installl php to your system.**
+
+ yum install php
+
+**4 – Edit web svn config.**
+
+ cd /var/www/html/websvn/include
+
+----------
+
+ cp distconfig.php config.php
+
+----------
+
+ vi config.php
+
+----------
+
+ // Configure these lines if your commands aren't on your path.
+ //
+ $config->setSVNCommandPath('/usr/bin'); // e.g. c:\\program files\\subversion\\bin
+ $config->setDiffPath('/usr/bin');
+----------
+ // For syntax colouring, if option enabled...
+ $config->setEnscriptPath('/usr/bin');
+ $config->setSedPath('/bin');
+----------
+ // For delivered tarballs, if option enabled...
+ $config->setTarPath('/bin');
+----------
+ // For delivered GZIP'd files and tarballs, if option enabled...
+ $config->setGZipPath('/bin');
+----------
+ //
+ $config->parentPath('/svn/');
+----------
+ $extEnscript[".pl"] = "perl";
+ $extEnscript[".py"] = "python";
+ $extEnscript[".sql"] = "sql";
+ $extEnscript[".java"] = "java";
+ $extEnscript[".html"] = "html";
+ $extEnscript[".xml"] = "html";
+ $extEnscript[".thtml"] = "html";
+ $extEnscript[".tpl"] = "html";
+ $extEnscript[".sh"] = "bash";
+ ~
+
+save and exit.
+
+**6 – Reload apache and start websvn link http://ip/websvn.**
+
+
+
+That’s it.
+
+--------------------------------------------------------------------------------
+
+via: http://www.unixmen.com/install-websvn-centos-7/
+
+作者:[M.el Khamlichi][a]
+译者:[译者ID](https://github.com/译者ID)
+校对:[校对者ID](https://github.com/校对者ID)
+
+本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
+
+[a]:http://www.unixmen.com/author/pirat9/
+[1]:http://www.unixmen.com/install-subversion-centos-7/
+[2]:
+[3]:
+[4]:
+[5]:
+[6]:
+[7]:
+[8]:
+[9]:
+[10]:
+[11]:
+[12]:
+[13]:
+[14]:
+[15]:
+[16]:
+[17]:
+[18]:
+[19]:
+[20]:
\ No newline at end of file
diff --git a/sources/tech/20150104 How to configure fail2ban to protect Apache HTTP server.md b/sources/tech/20150104 How to configure fail2ban to protect Apache HTTP server.md
new file mode 100644
index 0000000000..9bbf00198b
--- /dev/null
+++ b/sources/tech/20150104 How to configure fail2ban to protect Apache HTTP server.md
@@ -0,0 +1,207 @@
+How to configure fail2ban to protect Apache HTTP server
+================================================================================
+An Apache HTTP server in production environments can be under attack in various different ways. Attackers may attempt to gain access to unauthorized or forbidden directories by using brute-force attacks or executing evil scripts. Some malicious bots may scan your websites for any security vulnerability, or collect email addresses or web forms to send spams to.
+
+Apache HTTP server comes with comprehensive logging capabilities capturing various abnormal events indicative of such attacks. However, it is still non-trivial to systematically parse detailed Apache logs and react to potential attacks quickly (e.g., ban/unban offending IP addresses) as they are perpetrated in the wild. That is when `fail2ban` comes to the rescue, making a sysadmin's life easier.
+
+`fail2ban` is an open-source intrusion prevention tool which detects various attacks based on system logs and automatically initiates prevention actions e.g., banning IP addresses with `iptables`, blocking connections via /etc/hosts.deny, or notifying the events via emails. fail2ban comes with a set of predefined "jails" which use application-specific log filters to detect common attacks. You can also write custom jails to deter any specific attack on an arbitrary application.
+
+In this tutorial, I am going to demonstrate how you can configure fail2ban to protect your Apache HTTP server. I assume that you have Apache HTTP server and fail2ban already installed. Refer to [another tutorial][1] for fail2ban installation.
+
+### What is a Fail2ban Jail ###
+
+Let me go over more detail on fail2ban jails. A jail defines an application-specific policy under which fail2ban triggers an action to protect a given application. fail2ban comes with several jails pre-defined in /etc/fail2ban/jail.conf, for popular applications such as Apache, Dovecot, Lighttpd, MySQL, Postfix, [SSH][2], etc. Each jail relies on application-specific log filters (found in /etc/fail2ban/fileter.d) to detect common attacks. Let's check out one example jail: SSH jail.
+
+ [ssh]
+ enabled = true
+ port = ssh
+ filter = sshd
+ logpath = /var/log/auth.log
+ maxretry = 6
+ banaction = iptables-multiport
+
+This SSH jail configuration is defined with several parameters:
+
+- **[ssh]**: the name of a jail with square brackets.
+- **enabled**: whether the jail is activated or not.
+- **port**: a port number to protect (either numeric number of well-known name).
+- **filter**: a log parsing rule to detect attacks with.
+- **logpath**: a log file to examine.
+- **maxretry**: maximum number of failures before banning.
+- **banaction**: a banning action.
+
+Any parameter defined in a jail configuration will override a corresponding `fail2ban-wide` default parameter. Conversely, any parameter missing will be assgined a default value defined in [DEFAULT] section.
+
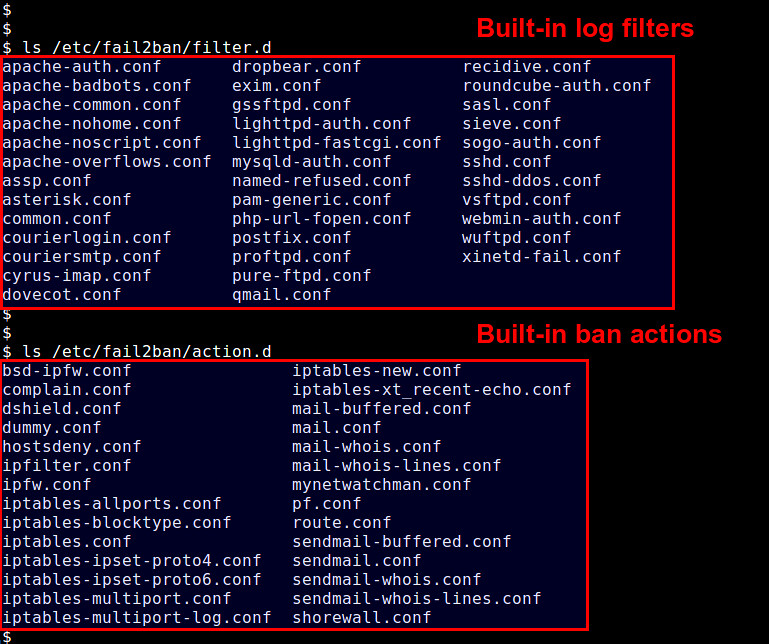
+Predefined log filters are found in /etc/fail2ban/filter.d, and available actions are in /etc/fail2ban/action.d.
+
+
+
+If you want to overwrite `fail2ban` defaults or define any custom jail, you can do so by creating **/etc/fail2ban/jail.local** file. In this tutorial, I am going to use /etc/fail2ban/jail.local.
+
+### Enable Predefined Apache Jails ###
+
+Default installation of `fail2ban` offers several predefined jails and filters for Apache HTTP server. I am going to enable those built-in Apache jails. Due to slight differences between Debian and Red Hat configurations, let me provide fail2ban jail configurations for them separately.
+
+#### Enable Apache Jails on Debian or Ubuntu ####
+
+To enable predefined Apache jails on a Debian-based system, create /etc/fail2ban/jail.local as follows.
+
+ $ sudo vi /etc/fail2ban/jail.local
+
+----------
+
+ # detect password authentication failures
+ [apache]
+ enabled = true
+ port = http,https
+ filter = apache-auth
+ logpath = /var/log/apache*/*error.log
+ maxretry = 6
+
+ # detect potential search for exploits and php vulnerabilities
+ [apache-noscript]
+ enabled = true
+ port = http,https
+ filter = apache-noscript
+ logpath = /var/log/apache*/*error.log
+ maxretry = 6
+
+ # detect Apache overflow attempts
+ [apache-overflows]
+ enabled = true
+ port = http,https
+ filter = apache-overflows
+ logpath = /var/log/apache*/*error.log
+ maxretry = 2
+
+ # detect failures to find a home directory on a server
+ [apache-nohome]
+ enabled = true
+ port = http,https
+ filter = apache-nohome
+ logpath = /var/log/apache*/*error.log
+ maxretry = 2
+
+Since none of the jails above specifies an action, all of these jails will perform a default action when triggered. To find out the default action, look for "banaction" under [DEFAULT] section in /etc/fail2ban/jail.conf.
+
+ banaction = iptables-multiport
+
+In this case, the default action is iptables-multiport (defined in /etc/fail2ban/action.d/iptables-multiport.conf). This action bans an IP address using iptables with multiport module.
+
+After enabling jails, you must restart fail2ban to load the jails.
+
+ $ sudo service fail2ban restart
+
+#### Enable Apache Jails on CentOS/RHEL or Fedora ####
+
+To enable predefined Apache jails on a Red Hat based system, create /etc/fail2ban/jail.local as follows.
+
+ $ sudo vi /etc/fail2ban/jail.local
+
+----------
+
+ # detect password authentication failures
+ [apache]
+ enabled = true
+ port = http,https
+ filter = apache-auth
+ logpath = /var/log/httpd/*error_log
+ maxretry = 6
+
+ # detect spammer robots crawling email addresses
+ [apache-badbots]
+ enabled = true
+ port = http,https
+ filter = apache-badbots
+ logpath = /var/log/httpd/*access_log
+ bantime = 172800
+ maxretry = 1
+
+ # detect potential search for exploits and php vulnerabilities
+ [apache-noscript]
+ enabled = true
+ port = http,https
+ filter = apache-noscript
+ logpath = /var/log/httpd/*error_log
+ maxretry = 6
+
+ # detect Apache overflow attempts
+ [apache-overflows]
+ enabled = true
+ port = http,https
+ filter = apache-overflows
+ logpath = /var/log/httpd/*error_log
+ maxretry = 2
+
+ # detect failures to find a home directory on a server
+ [apache-nohome]
+ enabled = true
+ port = http,https
+ filter = apache-nohome
+ logpath = /var/log/httpd/*error_log
+ maxretry = 2
+
+ # detect failures to execute non-existing scripts that
+ # are associated with several popular web services
+ # e.g. webmail, phpMyAdmin, WordPress
+ port = http,https
+ filter = apache-botsearch
+ logpath = /var/log/httpd/*error_log
+ maxretry = 2
+
+Note that the default action for all these jails is iptables-multiport (defined as "banaction" under [DEFAULT] in /etc/fail2ban/jail.conf). This action bans an IP address using iptables with multiport module.
+
+After enabling jails, you must restart fail2ban to load the jails in fail2ban.
+
+On Fedora or CentOS/RHEL 7:
+
+ $ sudo systemctl restart fail2ban
+
+On CentOS/RHEL 6:
+
+ $ sudo service fail2ban restart
+
+### Check and Manage Fail2ban Banning Status ###
+
+Once jails are activated, you can monitor current banning status with fail2ban-client command-line tool.
+
+To see a list of active jails:
+
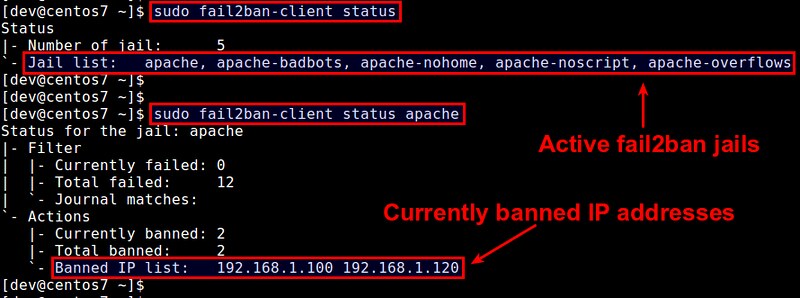
+ $ sudo fail2ban-client status
+
+To see the status of a particular jail (including banned IP list):
+
+ $ sudo fail2ban-client status [name-of-jail]
+
+
+
+You can also manually ban or unban IP addresses.
+
+To ban an IP address with a particular jail:
+
+ $ sudo fail2ban-client set [name-of-jail] banip [ip-address]
+
+To unban an IP address blocked by a particular jail:
+
+ $ sudo fail2ban-client set [name-of-jail] unbanip [ip-address]
+
+### Summary ###
+
+This tutorial explains how a fail2ban jail works and how to protect an Apache HTTP server using built-in Apache jails. Depending on your environments and types of web services you need to protect, you may need to adapt existing jails, or write custom jails and log filters. Check outfail2ban's [official Github page][3] for more up-to-date examples of jails and filters.
+
+Are you using fail2ban in any production environment? Share your experience.
+
+--------------------------------------------------------------------------------
+
+via: http://xmodulo.com/configure-fail2ban-apache-http-server.html
+
+作者:[Dan Nanni][a]
+译者:[译者ID](https://github.com/译者ID)
+校对:[校对者ID](https://github.com/校对者ID)
+
+本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
+
+[a]:http://xmodulo.com/author/nanni
+[1]:http://xmodulo.com/how-to-protect-ssh-server-from-brute-force-attacks-using-fail2ban.html
+[2]:http://xmodulo.com/how-to-protect-ssh-server-from-brute-force-attacks-using-fail2ban.html
+[3]:https://github.com/fail2ban/fail2ban
\ No newline at end of file
diff --git a/sources/tech/20150104 How to debug a C or C++ program with Nemiver debugger.md b/sources/tech/20150104 How to debug a C or C++ program with Nemiver debugger.md
new file mode 100644
index 0000000000..cf232b5b7c
--- /dev/null
+++ b/sources/tech/20150104 How to debug a C or C++ program with Nemiver debugger.md
@@ -0,0 +1,109 @@
+How to debug a C/C++ program with Nemiver debugger
+================================================================================
+If you read [my post on GDB][1], you know how important and useful a debugger I think can be for a C/C++ program. However, if a command line debugger like GDB sounds more like a problem than a solution to you, you might be more interested in Nemiver. [Nemiver][2] is a GTK+-based standalone graphical debugger for C/C++ programs, using GDB as its back-end. Admirable for its speed and stability, Nemiver is a very reliable debugger filled with goodies.
+
+### Installation of Nemiver ###
+
+For Debian based distributions, it should be pretty straightforward:
+
+ $ sudo apt-get install nemiver
+
+For Arch Linux:
+
+ $ sudo pacman -S nemiver
+
+For Fedora:
+
+ $ sudo yum install nemiver
+
+If you prefer compiling yourself, the latest sources are available from [GNOME website][3].
+
+As a bonus, it integrates very well with the GNOME environment.
+
+### Basic Usage of Nemiver ###
+
+Start Nemiver with the command:
+
+ $ nemiver
+
+You can also summon it with an executable with:
+
+ $ nemiver [path to executable to debug]
+
+Note that Nemiver will be much more helpful if the executable is compiled in debug mode (the -g flag with GCC).
+
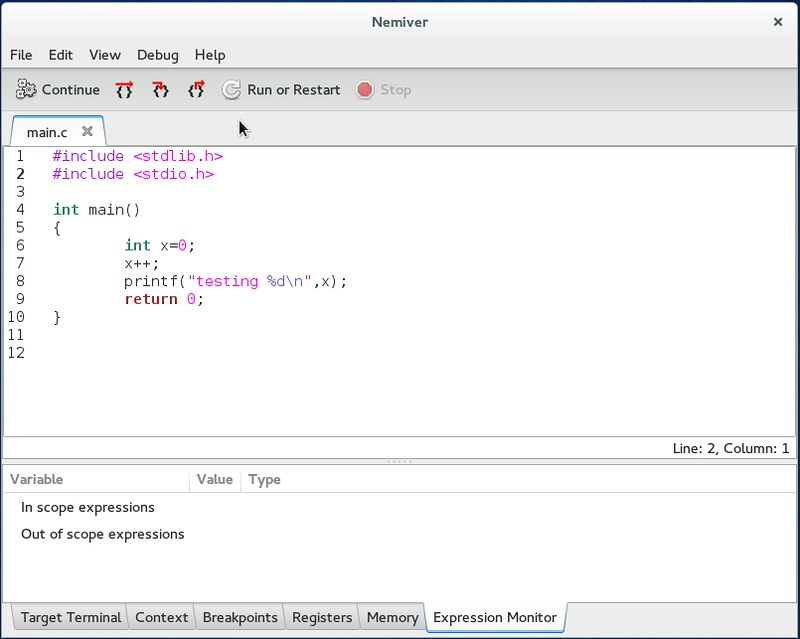
+A good thing is that Nemiver is really fast to load, so you should instantly see the main screen in the default layout.
+
+
+
+By default, a breakpoint has been placed in the first line of the main function. This gives you the time to recognize the basic debugger functions:
+
+
+
+- Next line (mapped to F6)
+- Step inside a function (F7)
+- Step out of a function (Shift+F7)
+
+But maybe my personal favorite is the option "Run to cursor" which makes the program run until a precise line under your cursor, and is by default mapped to F11.
+
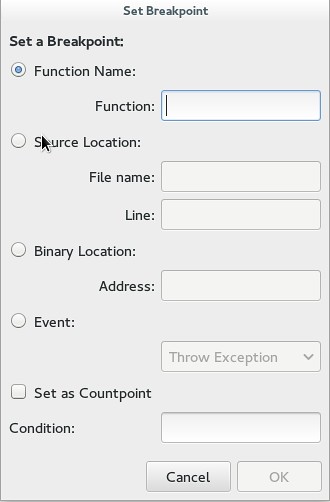
+Next, the breakpoints are also easy to use. The quick way to lay a breakpoint at a line is using F8. But Nemiver also has a more complex menu under "Debug" which allows you to set up a breakpoint at a particular function, line number, location of binary file, or even at an event like an exception, a fork, or an exec.
+
+
+
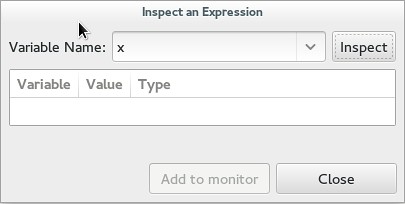
+You can also watch a variable by tracking it. In "Debug" you can inspect an expression by giving its name and examining it. It is then possible to add it to the list of controlled variable for easy access. This is probably one of the most useful aspects as I have never been a huge fan of hovering over a variable to get its value. Note that hovering does work though. And to make it even better, Nemiver is capable of watching a struct, and giving you the values of all the member variables.
+
+
+
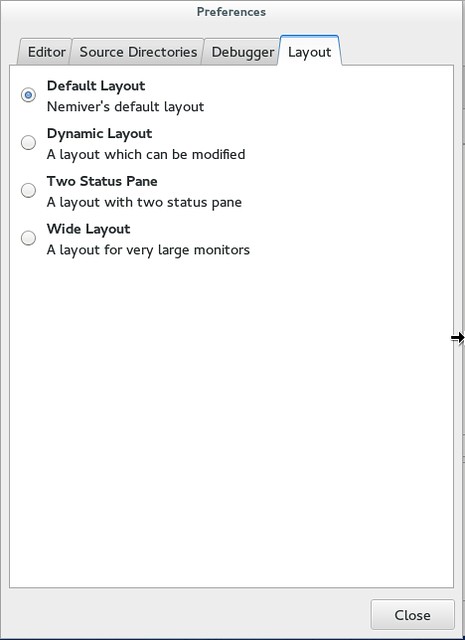
+Talking about easy access to information, I also really appreciate the layout of the program. By default, the code is in the upper half and the tabs in the lower part. This grants you access to a terminal for output, a context tracker, a breakpoints list, register addresses, memory map, and variable control. But note that under "Edit" "Preferences" "Layout" you can select different layouts, including a dynamic one for you to modify.
+
+
+
+
+
+And naturally, once you set up all your breakpoints, watch-points, and layout, you can save your session under “File” for easy retrieval in case you close Nemiver.
+
+### Advanced Usage of Nemiver ###
+
+So far, we talked about the basic features of Nemiver, i.e., what you need to get started and debug simple programs immediately. If you have more advanced needs, and especially more complex programs, you might be more interested in some of these features mentioned here.
+
+#### Debugging a running process ####
+
+Nemiver allows you to attach to a running process for debugging. Under the "File" menu, you can filter the list of running processes, and connect to a process.
+
+
+
+#### Debugging a program remotely over a TCP connection ####
+
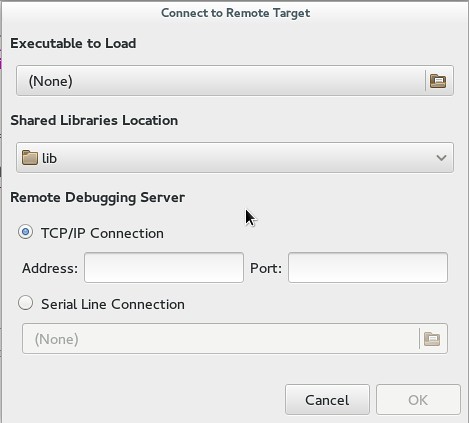
+Nemiver supports remote-debugging, where you set up a lightweight debug server on a remote machine, and launch Nemiver from another machine to debug a remote target hosted by the debug server. Remote debugging can be useful if you cannot run full-fledged Nemiver or GDB on the remote machine for some reason. Under the "File" menu, specify the binary, shared library location, and the address and port.
+
+
+
+#### Using your own GDB binary to debug ####
+
+In case you compiled Nemiver yourself, you can specify a new location for GDB under "Edit" "Preferences" "Debug". This option can be useful if you want to use a custom version of GDB in Nemiver for some reason.
+
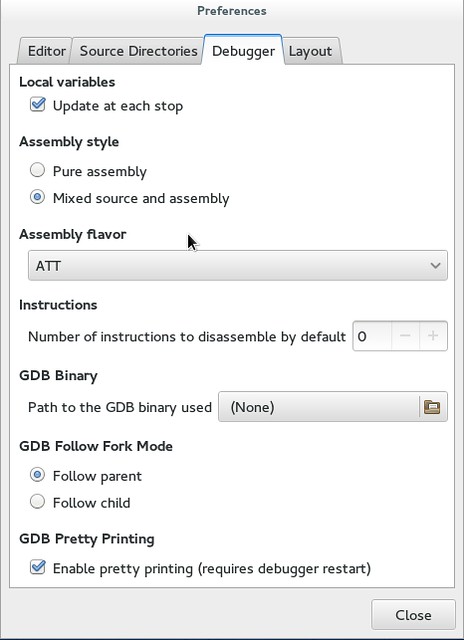
+#### Follow a child or parent process ####
+
+Nemiver is capable of following a child or parent process in case your program forks. To enable this feature, go to "Preferences" under "Debugger" tab.
+
+
+
+To conclude, Nemiver is probably my favorite program for debugging without an IDE. It even beats GDB in my opinion, and [command line][4] programs generally have a good grip on me. So if you have never used it, I really recommend it. I can only congratulate the team behind it for giving us such a reliable and stable program.
+
+What do you think of Nemiver? Would you consider it for standalone debugging? Or do you still stick to an IDE? Let us know in the comments.
+
+--------------------------------------------------------------------------------
+
+via: http://xmodulo.com/debug-program-nemiver-debugger.html
+
+作者:[Adrien Brochard][a]
+译者:[译者ID](https://github.com/译者ID)
+校对:[校对者ID](https://github.com/校对者ID)
+
+本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
+
+[a]:http://xmodulo.com/author/adrien
+[1]:http://xmodulo.com/gdb-command-line-debugger.html
+[2]:https://wiki.gnome.org/Apps/Nemiver
+[3]:https://download.gnome.org/sources/nemiver/0.9/
+[4]:http://xmodulo.com/recommend/linuxclibook
\ No newline at end of file
diff --git a/sources/tech/20150104 How to set up a cross-platform backup server on Linux with BackupPC.md b/sources/tech/20150104 How to set up a cross-platform backup server on Linux with BackupPC.md
new file mode 100644
index 0000000000..48df08fa3b
--- /dev/null
+++ b/sources/tech/20150104 How to set up a cross-platform backup server on Linux with BackupPC.md
@@ -0,0 +1,134 @@
+How to set up a cross-platform backup server on Linux with BackupPC
+================================================================================
+Just in case you haven't been able to tell from my earlier posts on [backupninja][1] and [backup-manager][2], I am a big backup fan. When it comes to backup, I'd rather have too much than not enough, because if the need arises, you will be grateful that you took the time and effort to generate extra copies of your important data.
+
+In this post, I will introduce you to [BackupPC][3], a cross-platform backup server software which can perform pull backup of Linux, Windows and MacOS client hosts over network. BackupPC adds a number of features that make managing backups an almost fun thing to do.
+
+### Features of BackupPC ###
+
+BackupPC comes with a robust web interface that allows you to collect and manage backups of other remote client hosts in a centralized fashion. Using the web interface, you can examine logs and configuration files, start/cancel/schedule backups of other remote hosts, and visualize current status of backup tasks. You can also browse through archived files and restore individual files or entire jobs from backup archives very easily. To restore individual single files, you can download them from any previous backup directly from the web interface. As if this weren't enough, no special client-side software is needed for client hosts. On Windows clients, the native SMB protocol is used, whereas on *nix clients, you will use `rsync` or tar over SSH, RSH or NFS.
+
+### Installing BackupPC ###
+
+On Debian, Ubuntu and their derivatives, run the following command.
+
+ # aptitude install backuppc
+
+On Fedora, use `yum` command. Note the case sensitive package name.
+
+On CentOS/RHEL 6, first enable [EPEL repository][4]. On CentOS/RHEL 7, enable [Nux Dextop][5] repository instead. Then go ahead with `yum` command:
+
+ # yum install BackupPC
+
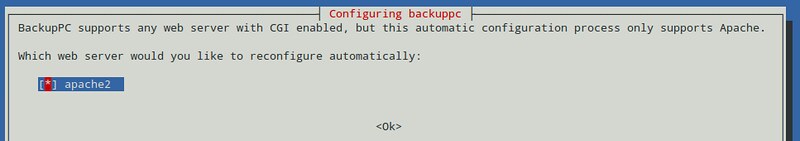
+As usual, both package management systems will take care of dependency resolution automatically. In addition, as part of the installation process, you may be asked to configure, or reconfigure the web server that will be used for the graphical user interface. The following screenshot is from a Debian system:
+
+
+
+Select your choice by pressing the space bar, and then move to Ok with the tab key and hit ENTER.
+
+You will then be presented with the following screen informing you that an administrative user account 'backuppc', along with its corresponding password (which can be changed later if desired), has been created to manage BackupPC. Note that both a HTTP user account and a regular Linux account of the same name 'backuppc' will be created with an identical password. The former is needed to access BackupPC's protected web interface, while the latter is needed to perform backup using rsync over SSH.
+
+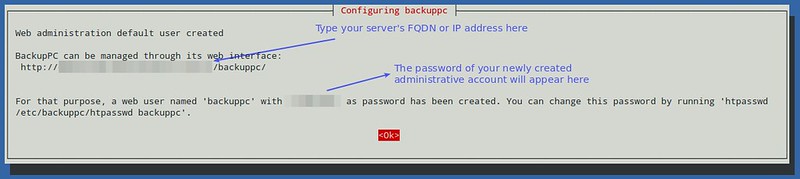
+
+You can change the default password for the HTTP user 'backuppc' with the following command:
+
+ # htpasswd /path/to/hash/file backuppc
+
+As for a regular 'backuppc' [Linux][6] user account, use passwd command to change its default password.
+
+ # passwd backuppc
+
+Note that the installation process creates the web and the program's configuration files automatically.
+
+### Launching BackupPC and Configuring Backups ###
+
+To start, open a browser window and point to http:///backuppc/. When prompted, enter the default HTTP user credentials that were supplied to you earlier. If the authentication succeeds, you will be taken to the main page of the web interface.
+
+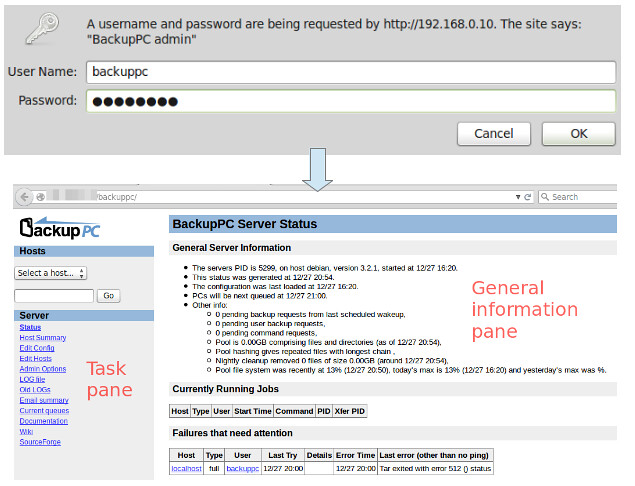
+
+Most likely the first thing that you will want to do is add a new client host to back up. Go to "Edit Hosts" in the Task pane. We will add two client hosts:
+
+- Host #1: CentOS 7 [IP 192.168.0.17]
+- Host #2: Windows 7 [IP 192.168.0.103]
+
+We will back up the CentOS host using rsync over SSH and the Windows host using SMB. Prior to performing the backup, we need to set up [key-based authentication][7] to our CentOS host and a shared folder in our Windows machine.
+
+Here are the instructions for setting up key-based authentication for a remote CentOS host. We create the 'backuppc' user's RSA key pair, and transfer its public key to the root account of the CentOS host.
+
+ # usermod -s /bin/bash backuppc
+ # su - backuppc
+ # ssh-keygen -t rsa
+ # ssh-copy-id root@192.168.0.17
+
+When prompted, type yes and enter root's password for 192.168.0.17.
+
+
+
+You will need root access for a remote CentOS host to grant write access to all its file system in case of restoring a backup of files or directories owned by root.
+
+Once the CentOS and Windows hosts are ready, add them to BackupPC using the web interface:
+
+
+
+The next step consists of modifying each host's backup settings:
+
+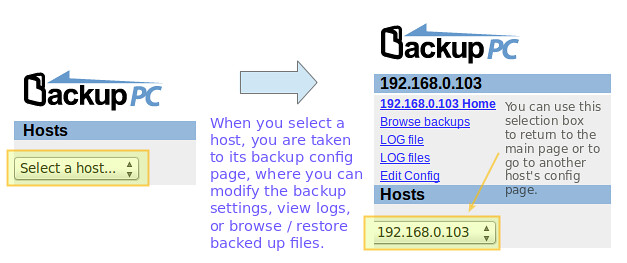
+
+The following image shows the configuration for the backup of the Windows machine:
+
+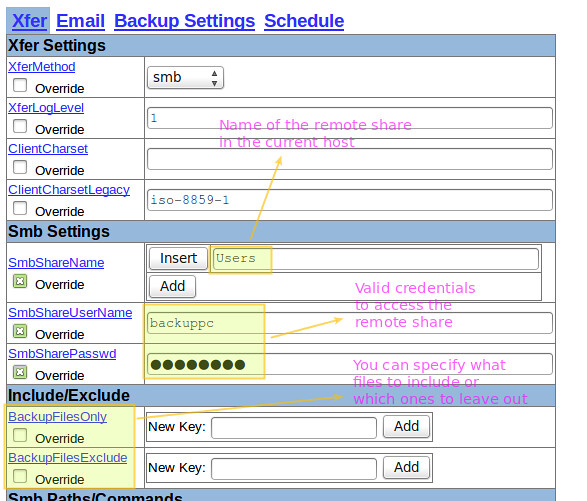
+
+And the following screenshot shows the settings for the backup of the CentOS box:
+
+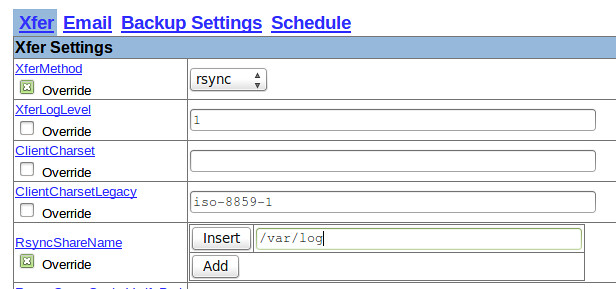
+
+### Starting a Backup ###
+
+To start each backup, go to each host's settings, and then click "Start Full Backup":
+
+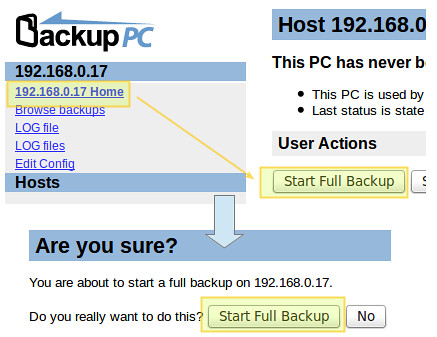
+
+At any time, you can view the status of the process by clicking on the host's home as shown in the image above. If it fails for some reason, a link to a page with the error message(s) will appear in the host menu as well. When a backup completes successfully, a directory with the host's name or IP address is created under /var/lib/backuppc/pc in the server:
+
+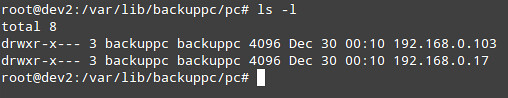
+
+Feel free to browse those directories for the files from the command line, but there is an easier way to look for those files and restore them.
+
+### Restoring Backup ###
+
+To view the files that have been saved, go to "Browse backups" under each host's main menu. You can visualize the directories and files at a glance, and select those that you want to restore. Alternatively, you can click on files to open them with the default program, or right click and choose Save link as to download it to the machine where you're working at the time:
+
+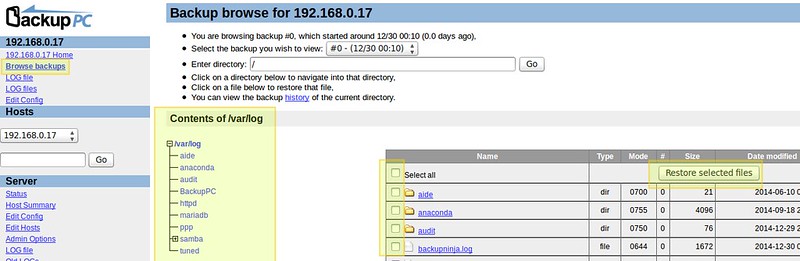
+
+If you want, you can download a zip or tar file containing the backup's contents:
+
+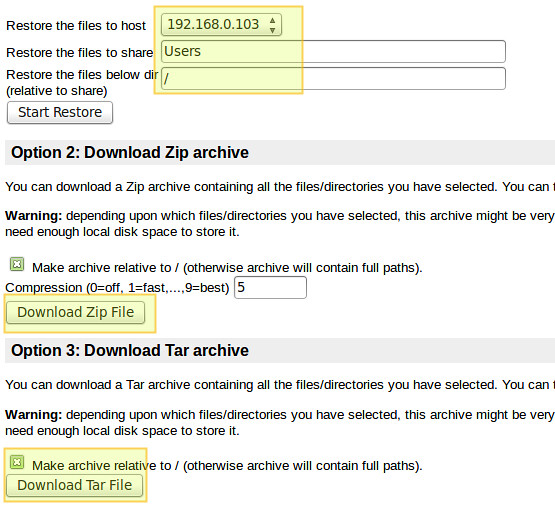
+
+or just restore the file(s):
+
+
+
+### Conclusion ###
+
+There is a saying that goes, "the simpler, the better", and that is just what BackupPC has to offer. In BackupPC, you will not only find a backup tool but also a very versatile interface to manage your backups of several operating systems without needing any client-side application. I believe that's more than reason enough for you to give it at least a try.
+
+Feel free to leave your comments and questions, if you have any, using the form below. I am always happy to hear what readers have to say!
+
+--------------------------------------------------------------------------------
+
+via: http://xmodulo.com/backuppc-cross-platform-backup-server-linux.html
+
+作者:[Gabriel Cánepa][a]
+译者:[译者ID](https://github.com/译者ID)
+校对:[校对者ID](https://github.com/校对者ID)
+
+本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
+
+[a]:http://xmodulo.com/author/gabriel
+[1]:http://xmodulo.com/backup-debian-system-backupninja.html
+[2]:http://xmodulo.com/linux-backup-manager.html
+[3]:http://backuppc.sourceforge.net/
+[4]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
+[5]:http://ask.xmodulo.com/enable-nux-dextop-repository-centos-rhel.html
+[6]:http://xmodulo.com/recommend/linuxguide
+[7]:http://xmodulo.com/how-to-enable-ssh-login-without.html
\ No newline at end of file
diff --git a/sources/tech/20150114 How to Configure Chroot Environment in Ubuntu 14.04.md b/sources/tech/20150114 How to Configure Chroot Environment in Ubuntu 14.04.md
new file mode 100644
index 0000000000..63acd23a67
--- /dev/null
+++ b/sources/tech/20150114 How to Configure Chroot Environment in Ubuntu 14.04.md
@@ -0,0 +1,146 @@
+How to Configure Chroot Environment in Ubuntu 14.04
+================================================================================
+There are many instances when you may wish to isolate certain applications, user, or environments within a Linux system. Different operating systems have different methods of achieving isolation, and in Linux, a classic way is through a `chroot` environment.
+
+In this guide, we'll show you step wise on how to setup an isolated environment using chroot in order to create a barrier between your regular operating system and a contained environment. This is mainly useful for testing purposes. We will teach you the steps on an **Ubuntu 14.04** VPS instance.
+
+Most system administrators will benefit from knowing how to accomplish a quick and easy chroot environment and it is a valuable skill to have.
+
+### The chroot environment ###
+
+A chroot environment is an operating system call that will change the root location temporarily to a new folder. Typically, the operating system's conception of the root directory is the actual root located at "/". However, with `chroot`, you can specify another directory to serve as the top-level directory for the duration of a chroot.
+
+Any applications that are run from within the `chroot` will be unable to see the rest of the operating system in principle.
+
+#### Advantages of Chroot Environment ####
+
+> - Test applications without the risk of compromising the entire host system.
+>
+> - From the security point of view, whatever happens in the chroot environment won't affect the host system (not even under root user).
+>
+> - A different operating system running in the same hardware.
+
+For instance, it allows you to build, install, and test software in an environment that is separated from your normal operating system. It could also be used as a method of **running 32-bit applications in a 64-bit environment**.
+
+But while chroot environments will certainly make additional work for an unprivileged user, they should be considered a hardening feature instead of a security feature, meaning that they attempt to reduce the number of attack vectors instead of creating a full solution. If you need full isolation, consider a more complete solution, such as Linux containers, Docker, vservers, etc.
+
+### Debootstrap and Schroot ###
+
+The necessary packages to setup the chroot environment are **debootstrap** and **schroot**, which are available in the ubuntu repository. The schroot command is used to setup the chroot environment.
+
+**Debootstrap** allows you to install a new fresh copy of any Debian (or debian-based) system from a repository in a directory with all the basic commands and binaries needed to run a basic instance of the operating system.
+
+The **schroot** allows access to chroots for normal users using the same mechanism, but with permissions checking and allowing additional automated setup of the chroot environment, such as mounting additional filesystems and other configuration tasks.
+
+These are the steps to implement this functionality in Ubuntu 14.04 LTS:
+
+### 1. Installing the Packages ###
+
+Firstly, We're gonna install debootstrap and schroot in our host Ubuntu 14.04 LTS.
+
+ $ sudo apt-get install debootstrap
+ $ sudo apt-get install schroot
+
+### 2. Configuring Schroot ###
+
+Now that we have the appropriate tools, we just need to specify a directory that we want to use as our chroot environment. We will create a directory called linoxide in our root directory to setup chroot there:
+
+ sudo mkdir /linoxide
+
+We have to configure schroot to suit our needs in the configuration file .we will modify the schroot configuration file with the information we require to get configured.
+
+ sudo nano /etc/schroot/schroot.conf
+
+We are on an Ubuntu 14.04 LTS (Trusty Tahr) system currently, but let's say that we want to test out some packages available on Ubuntu 13.10, code named "Saucy Salamander". We can do that by creating an entry that looks like this:
+
+ [saucy]
+ description=Ubuntu Saucy
+ location=/linoxide
+ priority=3
+ users=arun
+ root-groups=root
+
+
+
+Modify the values of the configuration parameters in the above example to fit your system:
+
+### 3. Installing 32 bit Ubuntu with debootstrap ###
+
+Debootstrap downloads and installs a minimal operating system inside your **chroot environment**. You can install any debian-based distro of your choice, as long as you have a repository available.
+
+Above, we placed the chroot environment under the directory **/linoxide** and this is the root directory of the chroot environment. So we'll need to run debootstrap inside that directory which we have already created:
+
+ cd /linoxide
+ sudo debootstrap --variant=buildd --arch amd64 saucy /linoxide/ http://archive.ubuntu.com/ubuntu/
+ sudo chroot /linoxide /debootstrap/debootstrap --second-stage
+
+You can replace amd64 in --arch as i386 or other bit OS you wanna setup available in the repository. You can replace the mirror http://archive.ubuntu.com/ubuntu/ above as the one closest, you can get the closest one from the official [Ubuntu Mirror Page][1].
+
+**Note: You will need to add --foreign above 3rd line command if you choose to setup i386 bit OS choot in your 64 bit Host Ubuntu as:**
+
+ sudo debootstrap --variant=buildd --foreign --arch i386 saucy /linoxide/ http://archive.ubuntu.com/ubuntu/
+
+It takes some time (depending on your bandwidth) to download, install and configure the complete system. It takes about 500 MBs for a minimal installation.
+
+### 4. Finallizing the chroot environment ###
+
+After the system is installed, we'll need to do some final configurations to make sure the system functions correctly. First, we'll want to make sure our host `fstab` is aware of some pseudo-systems in our guest.
+
+ sudo nano /etc/fstab
+
+Add the below lines like these to the bottom of your fstab:
+
+ proc /linoxide/proc proc defaults 0 0
+ sysfs /linoxide/sys sysfs defaults 0 0
+
+Save and close the file.
+
+Now, we're going to need to mount these filesystems within our guest:
+
+ $ sudo mount proc /linoxide/proc -t proc
+ $sudo mount sysfs /linoxide/sys -t sysfs
+
+We'll also want to copy our /etc/hosts file so that we will have access to the correct network information:
+
+ $ sudo cp /etc/hosts /linoxide/etc/hosts
+
+Finally, You can list the available chroot environments using the schroot command.
+
+ $ schroot -l
+
+We can enter the chroot environment through a command like this:
+
+ $ sudo chroot /linoxide/ /bin/bash
+
+You can test the chroot environment by checking the version of distributions installed.
+
+ # lsb_release -a
+ # uname -a
+
+To finish this tutorial, in order to run a graphic application from the chroot, you have to export the DISPLAY environment variable.
+
+ $ DISPLAY=:0.0 ./apps
+
+Here, we have successfully installed Chrooted Ubuntu 13.10(Saucy Salamander) in your host Ubuntu 14.04 LTS (Trusty Tahr).
+
+You can exit chroot environment successfully by running the commands below:
+
+ # exit
+
+Afterwards, we need to unmount our proc and sys filesystems:
+
+ $ sudo umount /test/proc
+ $ sudo umount /test/sys
+
+--------------------------------------------------------------------------------
+
+via: http://linoxide.com/ubuntu-how-to/configure-chroot-environment-ubuntu-14-04/
+
+作者:[Arun Pyasi][a]
+译者:[译者ID](https://github.com/译者ID)
+校对:[校对者ID](https://github.com/校对者ID)
+
+本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
+
+[a]:http://linoxide.com/author/arunp/
+[1]:https://launchpad.net/ubuntu/+archivemirrors
\ No newline at end of file
diff --git a/translated/news/20141208 U.S. Marine Corps Wants to Change OS for Radar System from Windows XP to Linux.md b/translated/news/20141208 U.S. Marine Corps Wants to Change OS for Radar System from Windows XP to Linux.md
new file mode 100644
index 0000000000..01c8d0d4f4
--- /dev/null
+++ b/translated/news/20141208 U.S. Marine Corps Wants to Change OS for Radar System from Windows XP to Linux.md
@@ -0,0 +1,49 @@
+Traslated by H-mudcup
+
+美国海军陆战队想把雷达操作系统从Windows XP换成Linux
+================================================================================
+**一个新的雷达系统已经被送回去升级了**
+
+
+
+
+
+
+
+
+
+
+
+
+
+>一谈到稳定性和性能,没什么能真的比得过Linux。这就是为什么美国海军陆战队的领导们已经决定让Northrop Grumman Corp. Electronic Systems把新送到的地面/空中任务导向雷达(G/ATOR)的操作系统从Windows XP换成Linux。
+
+地面/空中任务导向雷达(G/ATOR)系统已经研制了很多年。很可能在这项工程启动的时候Windows XP被认为是合理的选择。在研制的这段时间,事情发生了变化。微软已经撤销了对Windows XP的支持而且只有极少的几个组织会使用它。操作系统要么升级要么被换掉。在这种情况下,Linux成了合理的选择。特别是当替换的费用很可能远远少于更新的费用。
+
+有个很有趣的地方值得注意一下。地面/空中任务导向雷达(G/ATOR)才刚刚送到美国海军陆战队,但是制造它的公司却还是选择了保留这个过时的操作系统。一定有人注意到的这样一个事实。这是一个糟糕的决定,并且指挥系统已经被告知了可能出现的问题了。
+
+### G/ATOR雷达的软件将是基于Linux的 ###
+
+Unix类系统,比如基于BSD或者基于Linux的操作系统,通常会出现在条件苛刻的领域,或者任何情况下都不能失败的的技术中。例如,这就是为什么大多数的服务器都运行着Linux。一个雷达系统配上一个几乎不可能崩溃的操作系统看起来非常相配。
+
+“弗吉尼亚州Quantico海军基地海军陆战队系统司令部的官员,在周三宣布了一项与Northrop Grumman Corp. Electronic Systems在林西科姆高地的部分的总经理签订的价值1020万美元的修正合同。这个合同的修改将包括这样一项,把G/ATOR的控制电脑从微软的Windows XP操作系统换成与国防信息局(DISA)兼容的Linux操作系统。”
+
+‘G/ATOR是一个远征三维中短距离多用途雷达系统。这个系统被设计成能够探测拥有低雷达截面的低可观测目标,比如火箭弹,火炮,迫击炮,巡航导弹以及无人机。”这些内容可以在[militaryaerospace.com][1]看到。
+
+这项军用科技,即地面/空中任务导向雷达(G/ATOR),早在2005年就与Northrop Grumman签订了第一次合同。所以不难理解为什么美国海军可能想把这件事快点弄完。这次更换的时间限制还没有被提议。
+
+视频链接:[http://youtu.be/H2ppl4x-eu8][2]
+
+--------------------------------------------------------------------------------
+
+via: http://news.softpedia.com/news/U-S-Marine-Corps-Want-to-Change-OS-for-Radar-System-from-Windows-XP-to-Linux-466756.shtml
+
+作者:[Silviu Stahie][a]
+译者:[H-mudcup](https://github.com/H-mudcup)
+校对:[校对者ID](https://github.com/校对者ID)
+
+本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
+
+[a]:http://news.softpedia.com/editors/browse/silviu-stahie
+[1]:http://www.militaryaerospace.com/articles/2014/12/gator-linux-software.html
+[2]:http://youtu.be/H2ppl4x-eu8
diff --git a/translated/share/20141106 Flow' N Play Movie Player Has a Stylish Interface Ubuntu Installation.md b/translated/share/20141106 Flow' N Play Movie Player Has a Stylish Interface Ubuntu Installation.md
new file mode 100644
index 0000000000..ccd9a474d5
--- /dev/null
+++ b/translated/share/20141106 Flow' N Play Movie Player Has a Stylish Interface Ubuntu Installation.md
@@ -0,0 +1,57 @@
+Translated by H-mudcup
+
+Flow 'N Play视频播放器有着独具风格的界面【Ubuntu上的安装】
+================================================================================
+**Flow ‘N Play**是个用Qt编写的新视频播放器。它有着漂亮又简洁的只提供基本播放功能的界面。
+
+
+
+[Flow ‘N Play][1]是个比较新的有着漂亮的界面和简单操作的视频播放器(今年三月份第一次发行)。其中一个功能就是能通过拖动鼠标滑动视频列表。播放器带有基本功能,一个搜索功能,支持彩色主题。
+
+打开一个新的视频——你还可以在同一个对话框下自定义一个封面:
+
+
+
+设置对话框——在这里设置基本的选项:
+
+
+
+Flow ‘N Play仍然处在早起开发中,因此相对于更高级的播放器它有一些瑕疵。可以设置的选项少,不支持加载字幕或视频和声音的过滤器。目前,在打开一个新的视频时偶尔会出错或是表现异常。
+
+我相信在它变得能替代其他播放器之前,会先添加几个功能。但从长远来看,Flow ‘N Play很有前途。
+
+### 在Ubuntu 14.04上安装Flow ‘N Play 0.922 ###
+
+在Ubuntu上有几种不同的方法安装Flow ‘N Play,可以用DEB包,或用Bash命令编写的RUN安装文件,或在[Qt-Apps页面][2]上获得单独的二进制安装文件。
+
+要安装Flow ‘N Play得先获取依赖项:
+
+ sudo apt-get install libqt5multimediaquick-p5 qtdeclarative5-controls-plugin qtdeclarative5 qtmultimedia-plugin qtdeclarative5-qtquick2-plugin qtdeclarative5-quicklayouts-plugin
+
+Then download the DEB package and either double click it or change the working directory to the one where you saved it and type the following in a terminal (for 64-bit, replace the DEB file for 32-bit)然后下载DEB安装包,可以双击或在终端里把正操作的目录换到你保存安装包的目录下并输入以下命令(这个是64位的命令,对于32位的系统请将DEB文件换成32位的):
+
+ sudo dpkg -i flow-n-play_v0.926_qt-5.3.2_x64.deb
+
+然后在终端里输入**flow-n-play**来运行它。注意:为防止产生依赖项错误,当你试图安装DEB问件事你可以运行**sudo apt-get -f install**,这样可以自动获取丢失的依赖项并安装Flow ‘N Play。
+
+若用RUN脚本安装,先安装上边提到的依赖项,然后运行这个脚本:
+
+ wget -O http://www.prest1ge-c0ding.24.eu/programs/Flow-N-Play/v0.926/bin/flow-n-play_v0.926_qt-5.3.2_x64.run
+ sudo ./flow-n-play_v0.926_qt-5.3.2_x64.run
+
+第三种方法是手动安装到你选择的地方(在安装完依赖项后下载提供的二进制文件)以32位版本为例:
+
+ wget -O http://www.prest1ge-c0ding.24.eu/programs/Flow-N-Play/v0.926/bin/Flow-N-Play_v0.926_Qt-5.3.2_x86
+
+--------------------------------------------------------------------------------
+
+via: http://www.tuxarena.com/2014/11/flow-n-play-movie-player-has-a-stylish-interface-ubuntu-installation/
+
+作者:Craciun Dan
+译者:[H-mudcup](https://github.com/H-mudcup)
+校对:[校对者ID](https://github.com/校对者ID)
+
+本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
+
+[1]:http://www.prest1ge-c0ding.24.eu/programme-php/app-flow_n_play.php?lang=en
+[2]:http://qt-apps.org/content/show.php/Flow+%27N+Play?content=167736
diff --git a/translated/tech/20141027 ntpq -p output.md b/translated/tech/20141027 ntpq -p output.md
new file mode 100644
index 0000000000..955b010cdc
--- /dev/null
+++ b/translated/tech/20141027 ntpq -p output.md
@@ -0,0 +1,298 @@
+“ntpq -p”命令输出详解
+================================================================================
+[Gentoo][1](也许其他发行版也是?)中 ["ntp -q" 的 man page][2] 只有简短的描述:“*打印出服务器已知的节点列表和它们的状态概要信息。*”
+
+我还没见到关于这个命令的说明文档,因此这里对此作一个总结,可以补充进 "[man ntpq][3]" man page 中。更多的细节见这里 “[ntpq – standard NTP query program][4]”(原作者),和 [其他关于 man ntpq 的例子][5].
+
+[NTP][6] 是一个设计用于通过 [udp][9] 网络 ([WAN][7] 或者 [LAN][8]) 来同步计算机时钟的协议。引用 [Wikipedia – NTP][10]:
+[NTP][6] is a protocol designed to synchronize the clocks of computers over a ([WAN][7] or [LAN][8]) [udp][9] network. From [Wikipedia – NTP][10]:
+
+> 网络时间协议(英语:Network Time Protocol,NTP)一种协议和软件实现,用于通过使用有网络延迟的报文交换网络同步计算机系统间的时钟。最初由美国特拉华大学的 David L. Mills 设计,现在仍然由他和志愿者小组维护,它于 1985 年之前开始使用,是因特网中最老的协议之一。
+
+想了解更多有关时间和 NTP 协议的知识,可以参考 “[The NTP FAQ, Time, what Time?][11]”和 [RFCs for NTP][12]。早期的“Network Time Protocol (Version 3) RFC” ([txt][13], or [pdf][14], Appendix E, The NTP Timescale and its Chronometry, p70) 包含了对过去 5000 年我们的计时系统的变化和关系的有趣解释。维基百科的文章 [Time][15] 和 [Calendar][16] 提供了更宏观的视角。
+
+命令 "ntpq -q" 输出下面这样的一个表:
+
+ remote refid st t when poll reach delay offset jitter
+ ==============================================================================
+ LOCAL(0) .LOCL. 10 l 96h 64 0 0.000 0.000 0.000
+ *ns2.example.com 10.193.2.20 2 u 936 1024 377 31.234 3.353 3.096
+
+### 更多细节 ###
+
+#### 表头 ####
+
+
+- **remote** – 用于同步的远程节点或服务器。“LOCAL”表示本机 (当没有远程服务器可用时会出现)
+- **refid** – 远程的服务器进行同步的更高一级服务器
+- **st** – 远程节点或服务器的 [Stratum][17](级别,NTP 时间同步是分层的)
+- **t** – 类型 (u: [unicast(单播)][18] 或 [manycast(选播)][19] 客户端, b: [broadcast(广播)][20] 或 [multicast(多播)][21] 客户端, l: 本地时钟, s: 对称节点(用于备份), A: 选播服务器, B: 广播服务器, M: 多播服务器, 参见“[Automatic Server Discovery][22]“)
+- **when** – 最后一次同步到现在的时间 (默认单位为秒, “h”表示小时,“d”表示天)
+- **poll** – 同步的频率:[rfc5905][23]建议在 NTPv4 中这个值的范围在 4 (16s) 至 17 (36h) 之间(2的指数次秒),然而观察发现这个值的实际大小在一个小的多的范围内 :64 (2的6次方)秒 至 1024 (2的10次方)秒
+- **reach** – 一个8位的左移移位寄存器值,用来测试能否和服务器连接,每成功连接一次它的值就会增加,以 [8 进制][24]显示
+- **delay** – 从本地到远程节点或服务器通信的往返时间(毫秒)
+- **offset** – 主机与远程节点或服务器时间源的时间偏移量,offset 越接近于0,主机和 NTP 服务器的时间越接近([方均根][25]表示,单位为毫秒)
+- **jitter** – 与远程节点同步的时间源的平均偏差(多个时间样本中的 offset 的偏差,单位是毫秒),这个数值的绝对值越小,主机的时间就越精确
+
+#### 字段的统计代码 ####
+
+表中第一个字符(统计代码)是状态标识(参见 [Peer Status Word][26]),包含 " ","x","-","#","+","*","o":
+
+- " " – 无状态,表示:
+ - 没有远程通信的主机
+ - "LOCAL" 即本机
+ - (未被使用的)高层级服务器
+ - 远程主机使用的这台机器作为同步服务器
+- “**x**” – 已不再使用
+- “**-**” – 已不再使用
+- “**#**” – 良好的远程节点或服务器但是未被使用 (不在按同步距离排序的前六个节点中,作为备用节点使用)
+- “**+**” – 良好的且优先使用的远程节点或服务器(包含在组合算法中)
+- “*****” – 当前作为优先主同步对象的远程节点或服务器
+- “**o**” – PPS 节点 (当优先节点是有效时)。实际的系统同步是源于秒脉冲信号(pulse-per-second,PPS),可能通过PPS 时钟驱动或者通过内核接口。
+
+参考 [Clock Select Algorithm][27].
+
+#### refid ####
+
+**refid** 有下面这些状态值
+
+- 一个IP地址 – 远程节点或服务器的 [IP 地址][28]
+- **.LOCL.** – 本机 (当没有远程节点或服务器可用时)
+- **.PPS.** – 时间标准中的“[Pulse Per Second][29]”(秒脉冲)
+- **.IRIG.** – [Inter-Range Instrumentation Group][30] 时间码
+- **.ACTS.** – 美国 [NIST 标准时间][31] 电话调制器
+- **.NIST.** –美国 NIST 标准时间电话调制器
+- **.PTB.** – 德国 [PTB][32] 时间标准电话调制器
+- **.USNO.** – 美国 [USNO 标准时间][33] 电话调制器
+- **.CHU.** – [CHU][34] ([HF][35], Ottawa, ON, Canada) 标准时间无线电接收器
+- **.DCFa.** – [DCF77][36] ([LF][37], Mainflingen, Germany) 标准时间无线电接收器
+- **.HBG.** – [HBG][38] (LF Prangins, Switzerland) 标准时间无线电接收器
+- **.JJY.** – [JJY][39] (LF Fukushima, Japan) 标准时间无线电接收器
+- **.LORC.** – [LORAN][40]-C station ([MF][41]) 标准时间无线电接收器,注: [不再可用][42] (被 [eLORAN][43] 废弃)
+- **.MSF.** – [MSF][44] (LF, Anthorn, Great Britain) 标准时间无线电接收器
+- **.TDF.** – [TDF][45] (MF, Allouis, France)标准时间无线电接收器
+- **.WWV.** – [WWV][46] (HF, Ft. Collins, CO, America) 标准时间无线电接收器
+- **.WWVB.** – [WWVB][47] (LF, Ft. Collins, CO, America) 标准时间无线电接收器
+- **.WWVH.** – [WWVH][48] (HF, Kauai, HI, America) 标准时间无线电接收器
+- **.GOES.** – 美国 [静止环境观测卫星][49];
+- **.GPS.** – 美国 [GPS][50];
+- **.GAL.** – [伽利略定位系统][51] 欧洲 [GNSS][52];
+- **.ACST.** – 选播服务器
+- **.AUTH.** – 认证错误
+- **.AUTO.** – Autokey (NTP 的一种认证机制)顺序错误
+- **.BCST.** – 广播服务器
+- **.CRYPT.** – Autokey 协议错误
+- **.DENY.** – 服务器拒绝访问;
+- **.INIT.** – 关联初始化
+- **.MCST.** – 多播服务器
+- **.RATE.** – (轮询) 速率超出限定
+- **.TIME.** – 关联超时
+- **.STEP.** – 间隔时长改变,偏移量比危险阈值小(1000ms) 比间隔时间 (125ms)大
+
+#### 操作要点 ####
+
+一个时间服务器只会报告时间信息而不会从客户端更新时间(单向更新),而一个节点可以更新其他同级节点的时间,结合出一个彼此同意的时间(双向更新)。
+
+[初次启动][53]时:
+
+> 除非使用 iburst 选项,客户端通常需要花几分钟来和服务器同步。如果客户端在启动时时间与 NTP 服务器的时间差大于 1000 秒,守护进程会退出并在系统日志中记录,让操作者手动设置时间差小于 1000 秒后再重新启动。如果时间差小于 1000 秒,但是大于 128 秒,会自动矫正间隔,并自动重启守护进程。
+
+> 当第一次启动时,时间频率文件(通常是 ntp.drift 文件,记录时间偏移)不存在,守护进程进入一个特殊模式来矫正频率。当时钟不符合[规范][54]时这会需要 900 秒。当校正完成后,守护进程创建时间频率文件进入普通模式,并分步校正剩余的偏差。
+
+NTP 0 层(Stratum 0 )的设备如原子钟(铯,铷),GPS 时钟或者其他标准时间的无线电时钟为 1 层(Stratum 1)的时间服务器提供时间信号。NTP 只报告[UTC][55] 时间(统一协调时,Coordinated Universal Time)。客户端程序使用[时区][56]从 UTC 导出本地时间。
+
+NTP 协议是高精度的,使用的精度小于纳秒(2的 -32 次方)。主机的时间精度和其他参数(受硬件和操作系统限制)使用命令 “ntpq -c rl” 查看(参见 [rfc1305][57] 通用变量和 [rfc5905][58])。
+
+#### “ntpq -c rl”输出参数 ####
+
+- **precision** 为四舍五入值,且为 2 的幂数。因此精度为 2 的 *precision* 此幂(秒)
+- **rootdelay** – 与同步网络中主同步服务器的总往返延时。注意这个值可以是正数或者负数,取决于时钟的精度。
+- **rootdisp** – 相对于同步网络中主同步服务器的偏差(秒)
+- **tc** – NTP 算法 [PLL][59] (phase locked loop,锁相环路) 或 [FLL][60] (frequency locked loop,锁频回路) 时间常量
+- **mintc** – NTP 算法 PLL/FLL 最小时间常亮或“最快响应
+- **offset** – 由结合算法得出的系统时钟偏移量(毫秒)
+- **frequency** – 系统时钟频率
+- **sys_jitter** – 由结合算法得出的系统时钟平均偏差(毫秒)
+- **clk_jitter** – 硬件时钟平均偏差(毫秒)
+- **clk_wander** – 硬件时钟偏移([PPM][61] – 百分之一)
+
+Jitter (也叫 timing jitter) 表示短期变化大于10HZ 的频率, wander 表示长期变化大于10HZ 的频率 (Stability 表示系统的频率随时间的变化,和 aging, drift, trends 等是同义词)
+
+#### 操作要点(续) ####
+
+NTP 软件维护一系列连续更新的频率变化的校正值。对于设置正确的稳定系统,在非拥塞的网络中,现代硬件的 NTP 时钟同步通常与 UTC 标准时间相差在毫秒内。(在千兆 LAN 网络中可以达到何种精度?)
+
+对于 UTC 时间,[闰秒][62] 可以每两年插入一次用于同步地球自传的变化。注意本地时间为[夏令时][63]时时间会有一小时的变化。在重同步之前客户端设备会使用独立的 UTC 时间,除非客户端使用了偏移校准。
+
+#### [闰秒发生时会怎样][64] ####
+
+> 闰秒发生时,会对当天时间增加或减少一秒。闰秒的调整在 UTC 时间当天的最后一秒。如果增加一秒,UTC 时间会出现 23:59:60。即 23:59:59 到 0:00:00 之间实际上需要 2 秒钟。如果减少一秒,时间会从 23:59:58 跳至 0:00:00 。另见 [The Kernel Discipline][65].
+
+好了… 间隔阈值(step threshold)的真实值是多少: 125ms 还是 128ms? PLL/FLL tc 的单位是什么 (log2 s? ms?)?在非拥塞的千兆 LAN 中时间节点间的精度能达到多少?
+
+感谢 Camilo M 和 Chris B的评论。 欢迎校正错误和更多细节的探讨。
+
+谢谢
+Martin
+
+### 外传 ###
+
+- [NTP 的纪元][66] 从 1900 开始而 UNIX 的从 1970开始.
+- [时间校正][67] 是逐渐进行的,因此时间的完全同步可能会画上几个小时。
+- [节点状态][68] 可以被记录到 [summarise/plot time offsets and errors][69]
+- [RMS][70] – 均方根
+- [PLL][71] – 锁相环路
+- [FLL][72] – 锁频回路
+- [PPM][73] – 百万分之一,用于描述频率的变化
+- [man ntpq (Gentoo 简明版本)][74]
+- [man ntpq (长期维护版本)][75]
+- [man ntpq (Gentoo 长期维护版本)][76]
+
+### 另见 ###
+
+- [ntpq – 标准 NTP 查询程序][77]
+- [The Network Time Protocol (NTP) 分布][78]
+- NTP 的简明 [历史][79]
+- 一个更多细节的简明历史 “Mills, D.L., A brief history of NTP time: confessions of an Internet timekeeper. Submitted for publication; please do not cite or redistribute” ([pdf][80])
+- [NTP RFC][81] 标准文档
+- Network Time Protocol (Version 3) RFC – [txt][82], or [pdf][83]. Appendix E, The NTP Timescale and its Chronometry, p70, 包含了对过去 5000 年我们的计时系统的变化和关系的有趣解释。
+- 维基百科: [Time][84] 和 [Calendar][85]
+- [John Harrison and the Longitude problem][86]
+- [Clock of the Long Now][87] – The 10,000 Year Clock
+- John C Taylor – [Chronophage][88]
+- [Orders of magnitude of time][89]
+- [Greenwich Time Signal][90]
+
+### 其他 ###
+
+SNTP (Simple Network Time Protocol, [RFC 4330][91],简单未落协议)基本上也是NTP,但是缺少一些基于 [RFC 1305][92] 实现的 NTP 的一些不再需要的内部算法。
+
+Win32 时间 [Windows Time Service][93] 是 SNTP 的非标准实现,没有精度的保证,并假设精度几乎有 1-2 秒的范围。(因为没有系统时间变化校正)
+
+还有一个[PTP (IEEE 1588)][95] Precision Time Protocol(精准时间协议)。见维基百科:[Precision Time Protocol][96]。软件程序为 [PTPd][97]。虫咬的功能是这是一个 [LAN][98] 高精度主从同步系统,精度在毫秒级,使用 [International Atomic Time][99] (TAI, [monotonic][100],无闰秒)。数据报时间戳需要在网卡中启用。支持 PTP 的网络会对数据报记录时间戳以减少交换机路由器的影响。也可以在不记录时间戳的网络中使用 PTP 但可能应为时间偏差太大而无法同步。因此使用这个需要对网络进行设置。
+
+### 更老的时间同步协议 ###
+
+- DTSS – DEC公司的数字时间同步服务, 被 NTP 所取代。例子: [DTSS VMS C code c2000][101]。 (哪里有关于 DTSS 的文章或文档吗?)
+- [DAYTIME protocol][102],使用 [TCP][103] 或 [UDP][104] 13 端口同步
+- [ICMP Timestamp][105] 和 [ICMP Timestamp Reply][106],使用 [ICMP][107] 协议同步
+- [Time Protocol][108],使用 TCP 或 UDP 37 号端口同步
+
+--------------------------------------------------------------------------------
+
+via: http://nlug.ml1.co.uk/2012/01/ntpq-p-output/831
+
+作者:Martin L
+译者:[Liao](https://github.com/liaosishere)
+校对:[校对者ID](https://github.com/校对者ID)
+
+本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
+
+[1]:http://www.gentoo.org/
+[2]:http://nlug.ml1.co.uk/2012/01/man-ntpq-gentoo-brief-version/853
+[3]:http://www.thelinuxblog.com/linux-man-pages/1/ntpq
+[4]:http://www.eecis.udel.edu/~mills/ntp/html/ntpq.html
+[5]:http://linux.die.net/man/8/ntpq
+[6]:http://www.ntp.org/
+[7]:http://en.wikipedia.org/wiki/Wide_area_network
+[8]:http://en.wikipedia.org/wiki/Local_area_network
+[9]:http://en.wikipedia.org/wiki/User_Datagram_Protocol
+[10]:http://en.wikipedia.org/wiki/Network_Time_Protocol
+[11]:http://www.ntp.org/ntpfaq/NTP-s-time.htm
+[12]:http://www.ntp.org/rfc.html
+[13]:http://www.ietf.org/rfc/rfc1305.txt
+[14]:http://www.rfc-editor.org/rfc/rfc1305.pdf
+[15]:http://en.wikipedia.org/wiki/Time
+[16]:http://en.wikipedia.org/wiki/Calendar
+[17]:http://en.wikipedia.org/wiki/Network_Time_Protocol#Clock_strata
+[18]:http://en.wikipedia.org/wiki/Unicast
+[19]:http://www.eecis.udel.edu/~mills/ntp/html/manyopt.html#mcst
+[20]:http://en.wikipedia.org/wiki/Broadcasting_%28computing%29
+[21]:http://en.wikipedia.org/wiki/Multicast
+[22]:http://www.eecis.udel.edu/~mills/ntp/html/manyopt.html
+[23]:http://www.ietf.org/rfc/rfc5905.txt
+[24]:http://en.wikipedia.org/wiki/Octal#In_computers
+[25]:http://en.wikipedia.org/wiki/Root_mean_square
+[26]:http://www.eecis.udel.edu/~mills/ntp/html/decode.html#peer
+[27]:http://www.eecis.udel.edu/~mills/ntp/html/select.html
+[28]:http://en.wikipedia.org/wiki/Ip_address
+[29]:http://en.wikipedia.org/wiki/Pulse_per_second
+[30]:http://en.wikipedia.org/wiki/Inter-Range_Instrumentation_Group
+[31]:http://en.wikipedia.org/wiki/Standard_time_and_frequency_signal_service
+[32]:http://www.ptb.de/index_en.html
+[33]:http://en.wikipedia.org/wiki/United_States_Naval_Observatory#Time_service
+[34]:http://en.wikipedia.org/wiki/CHU_%28radio_station%29
+[35]:http://en.wikipedia.org/wiki/High_frequency
+[36]:http://en.wikipedia.org/wiki/DCF77
+[37]:http://en.wikipedia.org/wiki/Low_frequency
+[38]:http://en.wikipedia.org/wiki/HBG_%28time_signal%29
+[39]:http://en.wikipedia.org/wiki/JJY#Time_standards
+[40]:http://en.wikipedia.org/wiki/LORAN#Timing_and_synchronization
+[41]:http://en.wikipedia.org/wiki/Medium_frequency
+[42]:http://en.wikipedia.org/wiki/LORAN#The_future_of_LORAN
+[43]:http://en.wikipedia.org/wiki/LORAN#eLORAN
+[44]:http://en.wikipedia.org/wiki/Time_from_NPL#The_.27MSF_signal.27_and_the_.27Rugby_clock.27
+[45]:http://en.wikipedia.org/wiki/T%C3%A9l%C3%A9_Distribution_Fran%C3%A7aise
+[46]:http://en.wikipedia.org/wiki/WWV_%28radio_station%29#Time_signals
+[47]:http://en.wikipedia.org/wiki/WWVB
+[48]:http://en.wikipedia.org/wiki/WWVH
+[49]:http://en.wikipedia.org/wiki/GOES#Further_reading
+[50]:http://en.wikipedia.org/wiki/Gps#Timekeeping
+[51]:http://en.wikipedia.org/wiki/Galileo_%28satellite_navigation%29#The_concept
+[52]:http://en.wikipedia.org/wiki/Gnss
+[53]:http://www.eecis.udel.edu/~mills/ntp/html/debug.html
+[54]:http://www.ntp.org/ntpfaq/NTP-s-algo-kernel.htm
+[55]:http://en.wikipedia.org/wiki/Coordinated_Universal_Time
+[56]:http://en.wikipedia.org/wiki/Time_zone
+[57]:http://www.ietf.org/rfc/rfc1305.txt
+[58]:http://www.ietf.org/rfc/rfc5905.txt
+[59]:http://en.wikipedia.org/wiki/PLL
+[60]:http://en.wikipedia.org/wiki/Frequency-locked_loop
+[61]:http://en.wikipedia.org/wiki/Parts_per_million
+[62]:http://en.wikipedia.org/wiki/Leap_second
+[63]:http://en.wikipedia.org/wiki/Daylight_saving_time
+[64]:http://www.ntp.org/ntpfaq/NTP-s-time.htm#Q-TIME-LEAP-SECOND
+[65]:http://www.ntp.org/ntpfaq/NTP-s-algo-kernel.htm
+[66]:http://www.ntp.org/ntpfaq/NTP-s-algo.htm#AEN1895
+[67]:http://www.ntp.org/ntpfaq/NTP-s-algo.htm#Q-ACCURATE-CLOCK
+[68]:http://www.ntp.org/ntpfaq/NTP-s-trouble.htm#Q-TRB-MON-STATFIL
+[69]:http://www.ntp.org/ntpfaq/NTP-s-trouble.htm#AEN5086
+[70]:http://en.wikipedia.org/wiki/Root_mean_square
+[71]:http://en.wikipedia.org/wiki/PLL
+[72]:http://en.wikipedia.org/wiki/Frequency-locked_loop
+[73]:http://en.wikipedia.org/wiki/Parts_per_million
+[74]:http://nlug.ml1.co.uk/2012/01/man-ntpq-gentoo-brief-version/853
+[75]:http://nlug.ml1.co.uk/2012/01/man-ntpq-long-version/855
+[76]:http://nlug.ml1.co.uk/2012/01/man-ntpq-gentoo-long-version/856
+[77]:http://www.eecis.udel.edu/~mills/ntp/html/ntpq.html
+[78]:http://www.eecis.udel.edu/~mills/ntp/html/index.html
+[79]:http://www.ntp.org/ntpfaq/NTP-s-def-hist.htm
+[80]:http://www.eecis.udel.edu/~mills/database/papers/history.pdf
+[81]:http://www.ntp.org/rfc.html
+[82]:http://www.ietf.org/rfc/rfc1305.txt
+[83]:http://www.rfc-editor.org/rfc/rfc1305.pdf
+[84]:http://en.wikipedia.org/wiki/Time
+[85]:http://en.wikipedia.org/wiki/Calendar
+[86]:http://www.rmg.co.uk/harrison
+[87]:http://longnow.org/clock/
+[88]:http://johnctaylor.com/
+[89]:http://en.wikipedia.org/wiki/Orders_of_magnitude_%28time%29
+[90]:http://en.wikipedia.org/wiki/Greenwich_Time_Signal
+[91]:http://tools.ietf.org/html/rfc4330
+[92]:http://tools.ietf.org/html/rfc1305
+[93]:http://en.wikipedia.org/wiki/Network_Time_Protocol#Microsoft_Windows
+[94]:http://en.wikipedia.org/wiki/Personal_computer
+[95]:http://www.nist.gov/el/isd/ieee/ieee1588.cfm
+[96]:http://en.wikipedia.org/wiki/IEEE_1588
+[97]:http://ptpd.sourceforge.net/
+[98]:http://en.wikipedia.org/wiki/Local_area_network
+[99]:http://en.wikipedia.org/wiki/International_Atomic_Time
+[100]:http://en.wikipedia.org/wiki/Monotonic_function
+[101]:http://antinode.info/ftp/dtss_ntp/
+[102]:http://en.wikipedia.org/wiki/DAYTIME
+[103]:http://en.wikipedia.org/wiki/Transmission_Control_Protocol
+[104]:http://en.wikipedia.org/wiki/User_Datagram_Protocol
+[105]:http://en.wikipedia.org/wiki/ICMP_Timestamp
+[106]:http://en.wikipedia.org/wiki/ICMP_Timestamp_Reply
+[107]:http://en.wikipedia.org/wiki/Internet_Control_Message_Protocol
+[108]:http://en.wikipedia.org/wiki/Time_Protocol