mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-24 02:20:09 +08:00
commit
45b2cf5b39
@ -0,0 +1,29 @@
|
||||
Canonical和华硕在美国建立合作关系
|
||||
================================================================================
|
||||
**Canonical和华硕刚刚建立了合作关系,将在两款笔记本上搭载Ubuntu操作系统。**
|
||||
|
||||
华硕现在提供了X201E和1015E两款搭载了Ubuntu操作系统的笔记本,企图强势进军教育市场。
|
||||
|
||||
“和Ubuntu以及捆绑在她之上的其他免费软件一样,在购买价格中不包括licence的费用,这将明显降低成本。这会十分对学生和各大院校的胃口,他们的经济都比较困难。”
|
||||
|
||||
“办公类应用软件将会由LIbreOffice来提供。和通常一样,他们提供学生和工作人员需要的所有功能且与现有的文件完全兼容,他们也为邮件和浏览器捆绑了免费软件。”摘自ubuntu网站的[官方公告][1]。
|
||||
|
||||
这两款笔记本设计定位不在于性能强悍,设计定位为办公型,同时还可能针对一些多媒体内容的需求。华硕的1015E笔记本配备了Intel的Celeron 847 1.1GHz的处理器,2GB DDR3内存,320GB 5400转硬盘,以及一个10.1英寸的屏幕。
|
||||
|
||||
另一款已经脱销的产品华硕X201E则提供不多的性能提升:Intel Celeron 847(1.1GHz)Sandy Bridge处理器,4GB DDR3内存,320GB 5400转硬盘,11.6英寸的屏幕和Intel GMA HD显卡。
|
||||
|
||||
“成千上万的开源免费应用程序满足了从图像处理、3D动画到杀毒和会计的各类需求。”
|
||||
|
||||
“我们知道高效的个人计算对于学生和各类院校来说是十分重要的。所以,和我们的小伙伴们一起为教育行业提供低成本而高效的应用是一件另人很兴奋的事。”
|
||||
|
||||
Canonical在亚马逊的主页上发表了声明。但是如果你对于这些产品感兴趣,你应该了解他们同时在其他的商店中也能买到。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Canonical-and-ASUS-Have-Formed-a-Partnership-in-USA-404483.shtml
|
||||
|
||||
译者:[stduolc](https://github.com/stduolc) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://insights.ubuntu.com/resources/article/asus-and-ubuntu-deliver-affordable-world-class-laptops-to-usa-education/
|
||||
@ -1,6 +1,7 @@
|
||||
每日Ubuntu小技巧 - 使用Ubuntu拷贝CD和DVD光盘
|
||||
================================================================================
|
||||
Ubuntu,一个功能强大的现代操作系统,可以执行很多任务。你可以使用Ubuntu创建文档,浏览网页,聆听音乐,以及烧录或拷贝媒体光盘。
|
||||
|
||||
Ubuntu是一个功能强大的现代操作系统,可以执行很多任务。你可以使用Ubuntu创建文档,浏览网页,聆听音乐,以及烧录或拷贝媒体光盘。
|
||||
|
||||
就像Windows和Max OS X一样,Ubuntu是无所不能的!
|
||||
|
||||
@ -12,14 +13,14 @@ Brasero光盘烧录机安装在UBuntu的每一个版本上。它是Ubuntu上默
|
||||
|
||||
下面列出来的是Brasero的一些特性:
|
||||
- 创建数据CD/DVD时自动过滤隐藏和损坏的文件
|
||||
- 同时支持多个绘画,可以执行磁盘文件的完整性
|
||||
- 可以在忙碌中烧录视频CD/DVD[on the fly翻译不合适]
|
||||
- 可以拷贝CD/DVD到系统硬盘
|
||||
- 可以擦除CD/DVD
|
||||
- 同时支持多个会话,可以执行磁盘文件的完整性检查
|
||||
- 可以即时烧录视频CD/DVD
|
||||
- 可以镜像CD/DVD内容到硬盘
|
||||
- 可以擦除可擦写CD/DVD
|
||||
|
||||
还有很多其它的功能。如果你想找一个Ubuntu上简便的磁盘刻录机,在做任何操作前请先检查这个软件。
|
||||
还有很多其它的功能。如果你想找一个Ubuntu上简便的磁盘刻录机,在做任何操作前请先看看这个软件。
|
||||
|
||||
为了开始使用Brasero去烧录CD/DVD光盘,请确保你的电脑安装了CD/DVD烧录机。如果没有,你将无法成功烧录。如果你的电脑符合要求,将你想要翻录的数据插入CD/DVD,然后进入Dash,搜索Brasero。
|
||||
要开始使用Brasero去烧录CD/DVD光盘,请确保你的电脑安装了CD/DVD烧录机。如果没有,显然你无法烧录。如果你的电脑符合要求,将你想要翻录的数据光盘插入CD/DVD,然后进入Dash,搜索Brasero。
|
||||
|
||||
当Brasero打开后,选择磁盘拷贝。这个功能会拷贝一个光盘里的内容,然后将其写入到另一个光盘中。如果这是你想要的,请继续。
|
||||
|
||||
@ -36,10 +37,11 @@ Brasero光盘烧录机安装在UBuntu的每一个版本上。它是Ubuntu上默
|
||||
安装完成后,Brasero会开始拷贝光盘。如果最终光盘完成拷贝,系统会提示你插入一张空白的可写入的CD/DVD光盘以便写入拷贝。插入它然后等待完成将内容写入光盘的操作。
|
||||
|
||||
当你完成以上操作时,移除光盘,就可以使用烧录好的光盘了!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/12/daily-ubuntu-tips-copy-cd-dvd-discs-using-ubuntu/
|
||||
|
||||
译者:[KayGuoWhu](https://github.com/KayGuoWhu) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[KayGuoWhu](https://github.com/KayGuoWhu) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,40 +1,42 @@
|
||||
[翻译中]by stduolc
|
||||
如何使用BackTrack破解WIFI无线网络的WEP密钥
|
||||
================================================================================
|
||||
|
||||

|
||||
|
||||
你可能已经知道如果你想要加锁自己的WIFI无线网络,你最好选择[WPA加密][3]方式,因为WEP加密很容易被人破解。但是,你知道有多么的容易么?下面我们来看看吧。
|
||||
|
||||
*注意:此帖是验证如何破解使用老的使用较少的WEP加密协议加密的密码。如果你希望破解的网络采用了更受欢迎的WPA加密,请看这篇[使用Reaver(掠夺者)破解WIFI的WPA加密指南][2].*
|
||||
*注意:此帖是验证如何破解很少使用而陈旧的WEP加密协议。如果你希望破解的网络采用了更受欢迎的WPA加密,请看这篇:[如何使用Reaver破解Wi-Fi网络的WPA密码][2]。*
|
||||
|
||||
今天我们来看看如何一步一步的破解采用WEP加密方法加密的WIFI网络。但是,有言在先:知识是一种力量,但是力量并不意味着你应该成为一个混球或者做任何违法的事。知道[如何挑选一把锁具][3]并不会让你成为一个贼。请将此帖看成是教育性质或者概念验证性试验。
|
||||
今天我们来看看如何一步一步的破解采用WEP加密方法加密的WIFI网络。但是,有言在先:知识是一种力量,但是力量并不意味着你应该成为一个混球或者做任何违法的事。知道[如何挑选一把锁具][3]并不会让你成为一个贼。请将此帖用于教育性质或者概念验证性试验。
|
||||
|
||||
关于如何使用这个方案破解WEP加密的教程在互联网上有很多。认认真真的谷歌下。这个并不能被称作新闻。但是,让人惊讶的是如笔者一般的只有很少的网络经验的菜鸟,也可以使用一些免费的软件和廉价的WIFI适配器来完成这个做破解。下面就来看看吧!
|
||||
关于如何使用这个方案破解WEP加密的教程在互联网上有很多。认认真真的谷歌下,这个并不能被称作新闻。但是,让人惊讶的是如笔者一般的只有很少的网络经验的菜鸟,也可以使用一些免费的软件和廉价的WIFI适配器来完成这个做破解。下面就来看看吧!
|
||||
|
||||
### 你需要写什么 ###
|
||||
### 你需要些什么 ###
|
||||

|
||||
|
||||
除非你是一个电脑网络安全的忍者,否则你不太可能具有完成实验的所有工具。一下是你需要的:
|
||||
除非你是一个电脑网络安全的忍者,否则你不太可能具有完成实验的所有工具。以下是你需要的:
|
||||
|
||||
- **一个可兼容的无线适配器**.这是最主要的需求。你需要一个无线适配器,能用来完成包注入,你的电脑很可能不具备这个功能。在和我的安全专家邻居讨论了以后,我从亚马逊上花了50美元购买了一个Alfa AWUS050NH适配器,图片如下。更新:别学我,应该买[Alfa AWUS036H][4]而不是US050NH。[视频][5]里的哥们儿用$12美金在Ebay上买了一个解调器(同时可以选择把[自己的路由器][6]卖掉).网上有很多可以[兼容aircrack的适配器][7].
|
||||
- **一个兼容的无线适配器**.这是最主要的需求。你需要一个无线适配器,能用来完成包注入,你的电脑很可能不具备这个功能。在和我的安全专家邻居讨论了以后,我从亚马逊上花了50美元购买了一个Alfa AWUS050NH适配器,图片如上。更新:别学我,其实应该买[Alfa AWUS036H][4]而不是US050NH。[视频][5]里的哥们儿用$12美金在Ebay上买了一个解调器(同时可以选择把[自己的路由器][6]卖掉)。网上有很多可以[兼容aircrack的适配器][7]。
|
||||
|
||||
- **[一个BackTrack Live CD][8]**. 我们已经提供了一个完整的[BackTrack 3的安装使用教程][9],Linux Live CD可以让你完成所有的安全测试和测试工作。请自行下载一个CD,然后刻录或者从VMware中启动它。
|
||||
- **[一个BackTrack Live CD][8]**. 我们已经提供了一个完整的[BackTrack 3的安装使用教程][9],Linux Live CD可以让你完成所有的安全测试和测试工作。请自行下载一个CD镜像,然后刻录或者从VMware中启动它。
|
||||
|
||||
- **一个靠近的WEP加密的WIFI网络**. 信号需要足够的强,理想的情况下最好有用户正在使用、连接和断开设备。越多的人使用网络,你就可以的到更多的破解数据,这样你就更可能成功。
|
||||
|
||||
- **使用命令行的耐心**. 这里总共有10步,总共需要出入很长、很难懂的命令,然后等你的wifi网卡手机足够破解密码的数据。就像一个医生和一个急躁的病人说,有点耐心。
|
||||
- **使用命令行的耐心**. 这里总共有10步,总共需要输入很长、很难懂的命令,然后等你的wifi网卡收集足够破解密码的数据。就像一个医生和一个急躁的病人说,要有点耐心。
|
||||
|
||||
### 破解WEP ###
|
||||
|
||||
为了破解WEP,你需要启动一个Konsole,BackTrack内置的命令行。现在,就剩下命令了。
|
||||
为了破解WEP,你需要启动一个Konsole,它是BackTrack内置的命令行界面,它在任务栏的左下角,从左往右第二个图标。现在,输入命令吧。
|
||||
|
||||
第一步,运行下面的命令,获得你网卡列表:
|
||||
|
||||
airmon-ng
|
||||
|
||||
笔者只看见了一个ra0的结果。你的可能不一样;记录下这些label(找个纸或者截图)。现在开始,更改替换掉命令中每一个包括(interface)的地方。
|
||||
笔者只看见了一个ra0的结果。你的可能不一样;记录下这些内容(找个纸或者截图)。现在开始,更改替换掉命令中每一个包括(interface)的地方。
|
||||
|
||||
现在,运行下面的四个命令。看看截图里的输入结果。
|
||||
|
||||
|
||||
airmon-ng stop (interface)
|
||||
ifconfig (interface) down
|
||||
macchanger —mac 00:11:22:33:44:55 (interface)
|
||||
@ -42,20 +44,22 @@
|
||||
|
||||

|
||||
|
||||
如果你没有获得截图一样的结果,最可能的情况就是你的无线网卡不能在特殊破解模式下工作。如果你成功了,你应该已经有效的在你的无线网卡上伪造了一个新的MAC地址,00:11:22:33:44:55.
|
||||
如果你没有获得像截图一样的结果,最可能的情况就是你的无线网卡不能在特殊破解模式下工作。如果你成功了,你应该已经成功的在你的无线网卡上伪造了一个新的MAC地址,00:11:22:33:44:55.
|
||||
|
||||
现在,开始使用的你网络接口,运行:(译者注:interface在范例中就是ra0)
|
||||
|
||||
现在,开始使用的你网络接口,运行:(译者注:interface在示范中就是ra0)
|
||||
airodump-ng (interface)
|
||||
|
||||
就可以看见你周围的wifi网络列表了。当你认准了你的目标后,按Ctrl+C结束列表。高亮你感兴趣的网络,同时记录下两样数据:它的BSSID和它的Channel(讯道,标签为CH的那列),就像下面的截图。很明显你想要破解的网络需要是WEP加密的,而不是WPA或者其他加密方式。
|
||||
就可以看见你周围的wifi网络列表了。当你认准了你的目标后,按Ctrl+C结束列表。高亮你感兴趣的网络,同时记录下两样数据:它的BSSID和它的Channel(讯道,标签为CH的那列),就像下面的截图。很明显你想要破解的网络需要是WEP加密的,而不是WPA或者其他加密方式。
|
||||
|
||||

|
||||
|
||||
就像我说的,按Ctrl+C来终止列表。(我需要重复一两次来找到我需要的网络)一旦你找到了你需要破解的网络,高亮BSSID然后复制它到你的剪切板来为将要输入的命令做准备。
|
||||
|
||||
现在我们需要观察你选中的目标网络,并捕捉信息存入一个文件里,运行如下命令:
|
||||
|
||||
airodump-ng -c (channel) -w (file name) —bssid (bssid) (interface)
|
||||
|
||||
Where (channel) is your network's channel, and (bssid) is the BSSID you just copied to clipboard. You can use the Shift+Insert key combination to paste it into the command. Enter anything descriptive for (file name). I chose "yoyo," which is the network's name I'm cracking.
|
||||
其中,(channel),(bssid)就是你之前获取的那些信息。你可以使用Shift+Insert来将剪切板中的bssid信息粘贴到命令行中。随便给你的文件取个名字。我用的是“YoYo”,我破解的网络的名字。
|
||||
|
||||

|
||||
@ -72,14 +76,15 @@ Where (channel) is your network's channel, and (bssid) is the BSSID you just cop
|
||||
|
||||
aireplay-ng -3 -b (bssid) -h 00:11:22:33:44:55 (interface)
|
||||
|
||||
现在,我们创建了一个路由通路来更快的抓取数据,从而加快我们的破解过程。几分钟以后,前台的窗口会开始疯狂的读写数据包。(同时,我可以利用YoYo的网络在另一台机器上上网)这里,你可以喝杯Java牌儿咖啡,然后出去走走。一般来说,你需要收集到足够的数据后再运行你的破解程序。看着“#Data”列里的数据,你需要它在10,000以上。(图里的数据只有854)
|
||||
现在,我们创建了一个路由通路来更快的抓取数据,从而加快我们的破解过程。几分钟以后,前台的窗口会开始疯狂的读写数据包。(这时,我也不能用YoYo的网络在另一台机器上上网)这里,你可以喝杯Java牌儿咖啡,然后出去走走。一般来说,你需要收集到足够的数据后再运行你的破解程序。看着“#Data”列里的数据,你需要它在10,000以上。(图里的数据只有854)
|
||||
|
||||
这个过程可能需要一些时间,这取决于你的网络信号强度(截图中可以看到,我的信号强度低于-32DB,虽然YoYo的AP和我的适配器在同一间屋里)。等待直到包数据到达10K,因为在此之前破解过程不会成功。实际上,你可能需要超过10K,虽然他可能是大多数情况下都足够了。
|
||||
|
||||

|
||||
|
||||
一旦你收集了足够多的数据,就是见证奇迹的时刻了。启动第三个终端窗口,同时输入下面的命令来破解你收集到的数据:
|
||||
aircrack-ng -b (bssid) (file name-01.cap)
|
||||
|
||||
aircrack-ng -b (bssid) (filename-01.cap)
|
||||
|
||||
这里的filename就是你在上面输入的文件名。你可以在自己的Home目录下看到。他应该是一个.cap后缀名的文件。
|
||||
|
||||
@ -90,7 +95,7 @@ WEP密钥会接着显示“KEY FOUND”。去掉引号,然后输入他就可
|
||||
|
||||
### 这个过程中的问题 ###
|
||||
|
||||
通过这篇文章,我们可以证明想要破解WEP加密的网络对于任何一个具有硬件和软件人来说是如此简单的过程。我仍然认为是这样的。但是不像下面视频里的伙计,这个过程中我遇到了很多的问题。实际上,你应该可以注意到最后一张截图和其他的不一样,因为它不是我的截图。虽然我破解的AP是我自己的AP,和我的Alfa在同一间屋子里,而且读取的信号强度一直在-30左右,但是数据的收集速度依然很缓慢,而在数据收集完成以前,BackTrack不能破解他。在尝试了各种方案(在我的MAC和PC上),我始终没能抓取到足够的数据量来破解密钥。
|
||||
通过这篇文章,我们可以证明想要破解WEP加密的网络对于任何一个具有硬件和软件人来说是如此简单的过程。我一直认为是这样的,但是不像下面视频里的伙计,这个过程中我遇到了很多的问题。实际上,你应该可以注意到最后一张截图和其他的不一样,因为它不是我的截图。虽然我破解的AP是我自己的AP,和我的Alfa在同一间屋子里,而且读取的信号强度一直在-30左右,但是数据的收集速度依然很缓慢,而在数据收集完成以前,BackTrack不能破解他。在尝试了各种方案(在我的MAC和PC上),我始终没能抓取到足够的数据量来破解密钥。
|
||||
|
||||
所以,这个过程在理论上是很简单的,实际上因为设备、到AP的距离却又因人而异.
|
||||
|
||||
@ -98,18 +103,18 @@ WEP密钥会接着显示“KEY FOUND”。去掉引号,然后输入他就可
|
||||
|
||||
[http://www.youtube.com/embed/kDD9PjiQ2_U?wmode=transparent&rel=0&autohide=1&showinfo=0&enablejsapi=1][10]
|
||||
|
||||
感受到一点使用BackTrack破解WEP加密的作用了么?你想说些什么呢?赶快换掉它把。
|
||||
感受到一点使用BackTrack破解WEP加密的作用了么?你想说些什么呢?赶快换掉它吧。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://lifehacker.com/5305094/how-to-crack-a-wi+fi-networks-wep-password-with-backtrack
|
||||
|
||||
译者:[stduolc](https://github.com/stduolc) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[stduolc](https://github.com/stduolc) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://lifehacker.com/386675/secure-your-home-wi+fi-network
|
||||
[2]:http://lifehacker.com/5873407/how-to-crack-a-wi+fi-networks-wpa-password-with-reaver
|
||||
[2]:http://linux.cn/article-2335-1.html
|
||||
[3]:http://lifehacker.com/399735/how-to-pick-a-lock-with-a-bump-key
|
||||
[4]:http://www.amazon.com/Alfa-AWUS036H-802-11b-Wireless-network/dp/B002WCEWU8?tag=lifehackeramzn-20&ascsubtag=[referrer|lifehacker.com[type|link[postId|5305094[asin|B002WCEWU8[authorId|5774310829120954491
|
||||
[5]:http://www.youtube.com/watch?v=oHq-cKoYcr8
|
||||
@ -1,6 +1,7 @@
|
||||
洞悉需求最高的三大IT技能组
|
||||
================================================================================
|
||||

|
||||
|
||||
据[IT技能清单][1]调查报告结果显示,雇主所需的Linux人才应具备的IT技能可分成相对独立的组群。本文将着重介绍在上一个季度(2013年7月-9月)需求度最高的3组IT技能,这些技能在包括美国在内的被选国家招聘广告中都有所提及,同时结果表明这三组技能可以和Linux相关的工作领域需求相匹配。
|
||||
|
||||
报告指出在上一季度具有嵌入式开发人员相关技能的人才是Linux专业雇主亟需的一类。排在第二位和第三位涉及的技能领域分别对应虚拟化技术和LAMP管理。本文将基于这三类工作清单涉及到的技能需求加以讨论,并对分析后的三组技能间的依赖结构关系加以洞悉。
|
||||
@ -8,41 +9,52 @@
|
||||
> 如果您尚未阅读[IT技能清单][1],我们强烈建议您在阅读以下内容前先熟悉这篇文章。它详细阐明了本次研究中用到的方法,本文也是基于[IT技能清单][1]的材料才得以进一步分析。
|
||||
|
||||
### 2013年8月IT技能分类更新 ###
|
||||
|
||||
|
||||
|
||||
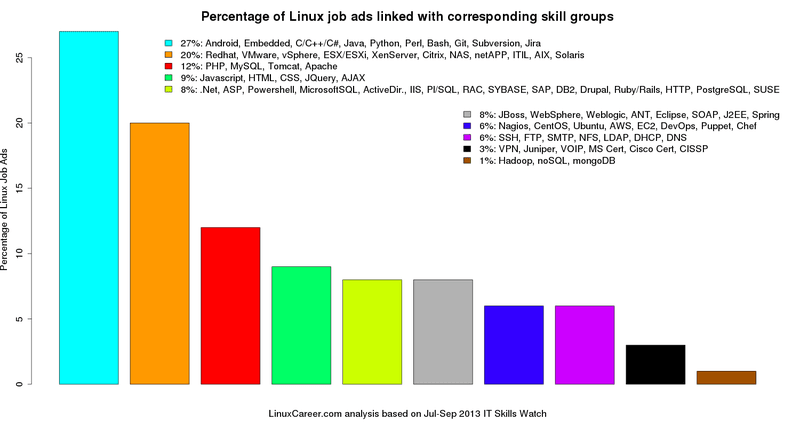
在IT技能清单这篇文章中,LinuxCareer.com分析了2013年5月到6月底的Linux工作清单,我们在这个基础上将2013年7月到9月底这个时间段的更新也加至分类分析中。10类相关的IT技能在Linux招聘广告中出现的比率列于如上[条形图][1]中。[IT分类][2]图表表明如何基于分类设计出此条形图。我们可以看到,IT技能需求前三组为:占据27%的Linux就业市场份额的嵌入式开发人员需求,占20%就业份额的虚拟化技术工程师和占12%Linux就业份额的LAMP管理员。文章接下来的三部分将围绕这三项IT技能需求组及三者的相互关系展开详细的讨论。例如,MySQL和PHP这两项技能有强关联性,通常雇主都会一起考虑。另外要指出的是,LinuxCareer.com的这项调查里掌握Linux的基础知识已默认存在于任一招聘需求中。
|
||||
|
||||
### 嵌入式开发人员及程序员 ###
|
||||
|
||||
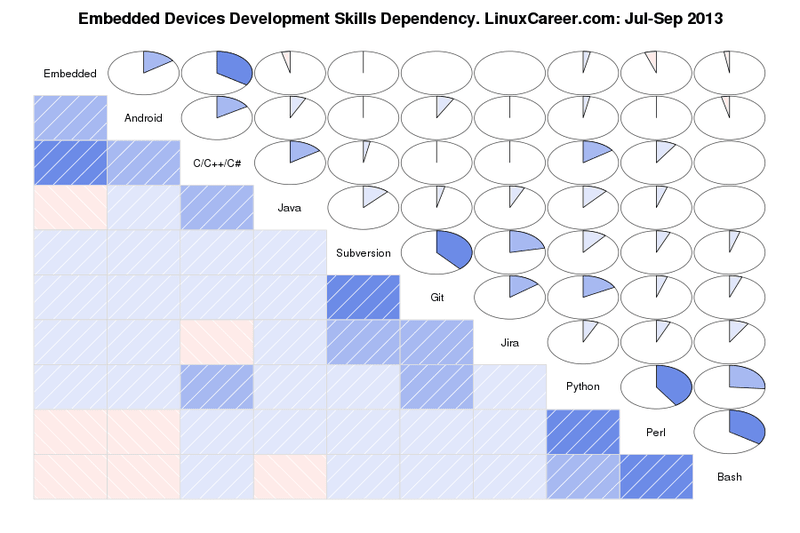
需求最高的第一类技能组是针对嵌入式开发人员及程序员的。如下的[依赖图][2]详细阐明了技能间的关联关系,尤其表明了哪几项技能更可能同时出现在Linux招聘需求中。例如,嵌入式开发非常需要C/C++/C#相关技能,而这些语言要么在图表下部的深色矩形区域,要么在图表上部的对应圆形阴影中聚集。
|
||||
|
||||
总体来说,这组技能可以进一步细分成如下三类:
|
||||
1. **Android, Embedded, C/C++/C# and Java**.如果您准备在嵌入式领域发展,这些是你需要掌握的核心技能,而C/C++/C#或Java掌握其一便可满足雇主需求,因为Java是基于部分C/C++/C#性能的扩展性语言。如果您阅读了8月的IT技能表,就会发现,Java以9513分居于编程语言的榜首,而C/C++/C#是5403分。如果您尚在犹豫是掌握C/C++/C#还是Java,从技能表得分看起来Java应该是更好的选择。但根据如下图表显示,C/C++/C#似乎在嵌入式领域的招聘需求中更受欢迎。总结可得尽管Java在IT技能表中有更高的得分,但在嵌入式开发职位上掌握C/C++/C#会比Java更有用。
|
||||
|
||||
1.** Python, Perl and Bash**.这些是对脚本编程语言技能的补充。对Perl和Python语言的需求经常会在招聘中同时出现,当然,也可以理解成这两种语言技能都是需要掌握的。
|
||||
1. **Android, Embedded, C/C++/C# 和 Java**。如果您准备在嵌入式领域发展,这些是你需要掌握的核心技能,而C/C++/C#或Java掌握其一便可满足雇主需求,因为Java是基于部分C/C++/C#性能的扩展性语言。如果您阅读了8月的IT技能表,就会发现,Java以9513分居于编程语言的榜首,而C/C++/C#是5403分。如果您尚在犹豫是掌握C/C++/C#还是Java,从技能表得分看起来Java应该是更好的选择。但根据如下图表显示,C/C++/C#似乎在嵌入式领域的招聘需求中更受欢迎。总结可得尽管Java在IT技能表中有更高的得分,但在嵌入式开发职位上掌握C/C++/C#会比Java更有用。
|
||||
|
||||
2. **Python, Perl 和 Bash**。这些是对脚本编程语言技能的补充。对Perl和Python语言的需求经常会在招聘中同时出现,当然,也可以理解成这两种语言技能都是需要掌握的。
|
||||
|
||||
3. **Git, Subversion 和 Jira**。这些软件知识会应用到源码管理、调试和项目管理中,同时了解这几个方面的知识对相关项目的编程大有裨益。目前,主流开源项目和大量合作项目都在用类似的软件管理他们的源码。
|
||||
|
||||
2. **Git, Subversion and Jira**.这些软件知识会应用到源码管理、调试和项目管理中,同时了解这几个方面的知识对相关项目的编程大有裨益。目前,主流开源项目和大量合作项目都在用类似的软件管理他们的源码。
|
||||
|
||||
|
||||
### 涉及数据仓储及管理的虚拟化技术工程师 ###
|
||||
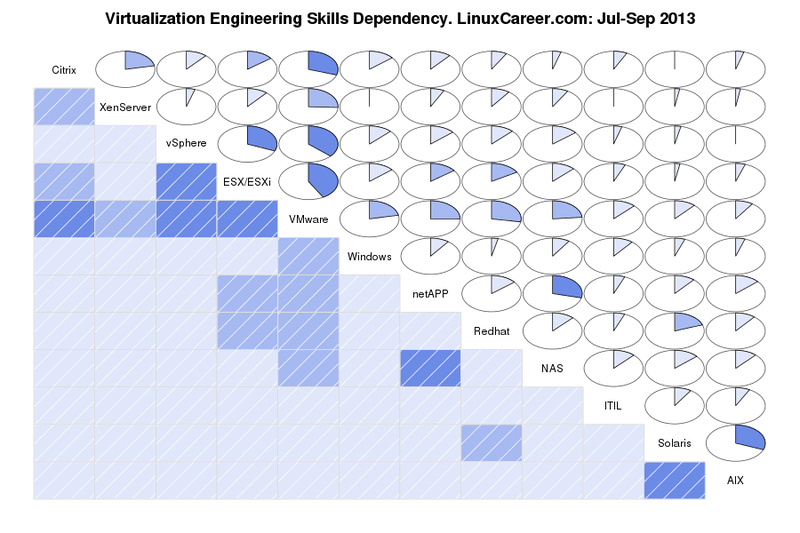
目前第二大需求技能组是如下[依赖图][2]所示与虚拟化技术工程师相关的技能。这一组可进一步细分成两部分,第一部分是Redhat, VMware, vSphere, ESX/ESXi, XenServer and Citrix,这些技能对寻求虚拟化技术工程师的工作很重要;第二部分是同Unix系统、数据仓储及管理相关的技能。同时这两部分是紧密联系的。显然VMware和ESX/ESXi及vSphere是相关的,因为ESX/ESXi是VMware虚拟机下提供的虚拟产品,而vSphere是VMware虚拟机的云端虚拟操作系统。Redhat和VMware、Citrix产品被分到同一部分同样有其原因。这里Solaris和AIX具有密切关系的原因可以理解为它们都是专有的Unix系统,掌握其一便可。
|
||||
|
||||
目前第二大需求技能组是如下[依赖图][2]所示与虚拟化技术工程师相关的技能。这一组可进一步细分成两部分,第一部分是Redhat, VMware, vSphere, ESX/ESXi, XenServer 和 Citrix,这些技能对寻求虚拟化技术工程师的工作很重要;第二部分是同Unix系统、数据仓储及管理相关的技能。同时这两部分是紧密联系的。显然VMware和ESX/ESXi及vSphere是相关的,因为ESX/ESXi是VMware虚拟机下提供的虚拟产品,而vSphere是VMware虚拟机的云端虚拟操作系统。Redhat和VMware、Citrix产品被分到同一部分同样有其原因。这里Solaris和AIX具有密切关系的原因可以理解为它们都是专有的Unix系统,掌握其一便可。
|
||||
|
||||
|
||||
|
||||
### LAMP管理员 ###
|
||||
|
||||
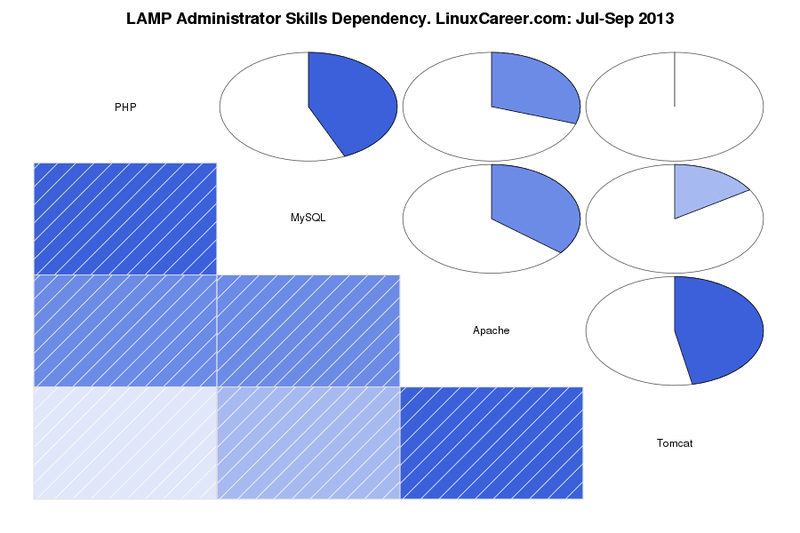
最后,第三大技能组是如下[依赖图][2]中显示雇主需求的LAMP管理员应具备的技能。LAMP是Linux、Apache、MySQL和PHP的简称,所有这四项内容是作为一名LAMP管理员所要了解的核心。这是一组相对来说小规模却会引领你至在Linux路途中发展更远的技能。实际上,PHP和MySQL的密切关系表明这些技能中的任一项都不能脱离其它技能来单独掌握。
|
||||
|
||||
|
||||
|
||||
### 总结 ###
|
||||
|
||||
本文基于就业能力和Linux专业人员需求技能分组阐明了两点。第一点是对经常出现的IT技能通过集群分析划出了10类IT技能组;第二点是基于Linux工作需求与相应技能组的对应结果,嵌入式程序员在Linux招聘需求比率最高,第二及第三技能需求比率最高的领域分别对应虚拟化技术工程师及LAMP管理员领域。这三大技能组即为上一季度分析出的Linux技能需求的核心。
|
||||
|
||||
### 参考 ###
|
||||
[1] Percentage of Linux job ads linked with corresponding skill groups created by [GNU R][3]. Relevant package: graphics.
|
||||
|
||||
[2] Dependency charts created by [GNU R][3]. Relevant package: corrgram.
|
||||
\[1] Percentage of Linux job ads linked with corresponding skill groups created by [GNU R][3]. Relevant package: graphics.
|
||||
|
||||
\[2] Dependency charts created by [GNU R][3]. Relevant package: corrgram.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxcareer.com/insights-into-top-3-it-skills-groups-in-highest-demand
|
||||
|
||||
译者:[icybreaker](https://github.com/icybreaker) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[icybreaker](https://github.com/icybreaker) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,89 @@
|
||||
使用PPA在Elementary OS 'Luna'上安装Oracle Java 7
|
||||
================================================================================
|
||||
|
||||
**问题**: 我该如何在 Elemetary OS Luna 上安装Oracle Java 7?
|
||||
|
||||
**回答**: 在 Elementary OS Luna 安装 Java 7 的步骤如下:
|
||||
由于Elementary OS是基于Ubuntu,所以我们允许使用具有多种Java包的**WEPUD8 PPA**。
|
||||
|
||||
1. 打开终端。
|
||||
|
||||
2. 运行以下指令添加Java的PPA到你的软件仓:
|
||||
|
||||
$ sudo add-apt-repository ppa:webupd8team/java
|
||||
|
||||
You are about to add the following PPA to your system:
|
||||
Oracle Java (JDK) Installer (automatically downloads and installs Oracle JDK6 / JDK7 / JDK8). There are no actual Java files in this PPA. More info: http://www.webupd8.org/2012/01/install-oracle-java-jdk-7-in-ubuntu-via.html
|
||||
Debian installation instructions: http://www.webupd8.org/2012/06/how-to-install-oracle-java-7-in-debian.html
|
||||
More info: https://launchpad.net/~webupd8team/+archive/java
|
||||
Press [ENTER] to continue or ctrl-c to cancel adding it
|
||||
|
||||
3. 按回车继续
|
||||
|
||||
gpg: keyring `/tmp/tmpB5WwDG/secring.gpg' created
|
||||
gpg: keyring `/tmp/tmpB5WwDG/pubring.gpg' created
|
||||
gpg: requesting key EEA14886 from hkp server keyserver.ubuntu.com
|
||||
gpg: /tmp/tmpB5WwDG/trustdb.gpg: trustdb created
|
||||
gpg: key EEA14886: public key "Launchpad VLC" imported
|
||||
gpg: Total number processed: 1
|
||||
gpg: imported: 1 (RSA: 1)
|
||||
OK
|
||||
|
||||
4. 现在更新你的系统
|
||||
|
||||
$ sudo apt-get update
|
||||
|
||||
5. 运行以下命令安装Java 7:
|
||||
|
||||
$ sudo apt-get install oracle-java7-installer
|
||||
|
||||
[sudo] password for enock:
|
||||
Reading package lists... Done
|
||||
Building dependency tree
|
||||
Reading state information... Done
|
||||
The following packages were automatically installed and are no longer required:
|
||||
gir1.2-gstreamer-0.10 libilmbase6 libmagickcore4 libmagickwand4 libcdt4
|
||||
libmagickcore4-extra liblqr-1-0 imagemagick-common libpathplan4 libopenexr6
|
||||
rsync netpbm libgvc5 libnetpbm10 libgraph4
|
||||
Use 'apt-get autoremove' to remove them.
|
||||
The following extra packages will be installed:
|
||||
gsfonts-x11 java-common
|
||||
Suggested packages:
|
||||
default-jre equivs binfmt-support visualvm ttf-baekmuk ttf-unfonts
|
||||
ttf-unfonts-core ttf-kochi-gothic ttf-sazanami-gothic ttf-kochi-mincho
|
||||
ttf-sazanami-mincho ttf-arphic-uming
|
||||
The following NEW packages will be installed:
|
||||
gsfonts-x11 java-common oracle-java7-installer
|
||||
0 upgraded, 3 newly installed, 0 to remove and 196 not upgraded.
|
||||
Need to get 88.5 kB of archives.
|
||||
After this operation, 473 kB of additional disk space will be used.
|
||||
Do you want to continue [Y/n]?
|
||||
|
||||
6. 输入代表Yes的**Y**以及回车键继续安装。
|
||||
|
||||
7. 在安装过程中,你需要同意条款才能继续。选择**OK**。
|
||||
|
||||

|
||||
|
||||
8. 然后选择**Yes**继续。
|
||||
|
||||

|
||||
|
||||
9. 现在请等待安装包的下载与自动安装:
|
||||
|
||||

|
||||
|
||||
10. 安装完成。你可以在终端上查看Java版本:
|
||||
|
||||
$ java -version
|
||||
java version "1.7.0_45"
|
||||
Java(TM) SE Runtime Environment (build 1.7.0_45-b18)
|
||||
Java HotSpot(TM) 64-Bit Server VM (build 24.45-b08, mixed mode)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/install-oracle-java-7-elementary-os-luna-via-ppa/
|
||||
|
||||
译者:[whatever1992](https://github.com/whatever1992) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,36 +1,38 @@
|
||||
Linux sheel 贴士和技巧
|
||||
Linux shell中的那些小把戏
|
||||
================================================================================
|
||||
我日常使用Linux shell(Bash),但是我经常忘记一些有用的命令或者shell技巧。是的,我能记住一些命令但是我不能说只在特定的任务上使用一次。那么我就开始在我的Dropbox账号里用文本文件写下这些Linux shell的贴士,现在我决定共享它。这个表我以后还会更新。记住,这里的一些贴士需要在你的Linux发行版上安装额外的软件。
|
||||
我日常使用Linux shell(Bash),但是我经常忘记一些有用的命令或者shell技巧。是的,我能记住一些命令,但是肯定不会只在特定的任务上使用一次,所以我就开始在我的Dropbox账号里用文本文件写下这些Linux shell的小技巧,现在我决定共享它给你。这个表我以后还会更新。记住,这里的一些贴士需要在你的Linux发行版上安装额外的软件。
|
||||
|
||||
在bash中检查远程端口是否打开:
|
||||
|
||||
echo >/dev/tcp/8.8.8.8/53 && echo "open"
|
||||
|
||||
终止进程:
|
||||
将进程挂起:
|
||||
|
||||
Ctrl + z
|
||||
|
||||
将进程移到前台:
|
||||
|
||||
fg
|
||||
|
||||
(译注,挂起的进程是不执行的,如果希望在后台执行,可以使用bg命令,并且指定通过jobs命令获得的任务号。)
|
||||
|
||||
生成随机16进制数字,n是字符的数量:
|
||||
|
||||
openssl rand -hex n
|
||||
|
||||
在当前shell中从一个文件中执行命令:
|
||||
在当前shell中执行一个文件中的命令(译注:这个文件不是一个bash脚本,比如.bashrc、bash_profile等):
|
||||
|
||||
source /home/user/file.name
|
||||
|
||||
提取前5个字符的字串:
|
||||
提取字符串的前5个字符:
|
||||
|
||||
${variable:0:5}
|
||||
|
||||
SSH调试模式:
|
||||
打开SSH调试模式(译注:当你遇到SSH连接问题时很有用):
|
||||
|
||||
ssh -vvv user@ip_address
|
||||
|
||||
带pem key的SSH
|
||||
使用pem key的进行SSH连接:
|
||||
|
||||
ssh user@ip_address -i key.pem
|
||||
|
||||
@ -38,11 +40,11 @@ SSH调试模式:
|
||||
|
||||
wget -r --no-parent --reject "index.html*" http://hostname/ -P /home/user/dirs
|
||||
|
||||
创建多个目录:
|
||||
同时创建多个目录:
|
||||
|
||||
mkdir -p /home/user/{test,test1,test2}
|
||||
|
||||
列出带子进程的进程树:
|
||||
以树状列出进程及子进程:
|
||||
|
||||
ps axwef
|
||||
|
||||
@ -58,7 +60,7 @@ SSH调试模式:
|
||||
|
||||
hdparm -Tt /dev/sda
|
||||
|
||||
从文本中获取md5值:
|
||||
获取文本的md5值:
|
||||
|
||||
echo -n "text" | md5sum
|
||||
|
||||
@ -66,7 +68,7 @@ SSH调试模式:
|
||||
|
||||
xmllint --noout file.xml
|
||||
|
||||
在新的目录中提取tar.gz文件:
|
||||
将tar.gz文件解压到指定目录:
|
||||
|
||||
tar zxvf package.tar.gz -C new_dir
|
||||
|
||||
@ -74,7 +76,7 @@ SSH调试模式:
|
||||
|
||||
curl -I http://www.example.com
|
||||
|
||||
修改一些文件或目录的时间戳 (YYMMDDhhmm):
|
||||
修改一些文件或目录的时间戳 (格式为:YYMMDDhhmm):
|
||||
|
||||
touch -t 0712250000 file
|
||||
|
||||
@ -86,7 +88,7 @@ SSH调试模式:
|
||||
|
||||
LANG=c < /dev/urandom tr -dc _A-Z-a-z-0-9 | head -c${1:-16};echo;
|
||||
|
||||
快速创建一个文件的备份:
|
||||
快速创建一个文件的备份(扩展名是.bkp):
|
||||
|
||||
cp some_file_name{,.bkp}
|
||||
|
||||
@ -94,7 +96,7 @@ SSH调试模式:
|
||||
|
||||
smbclient -U "DOMAIN\user" //dc.domain.com/share/test/dir
|
||||
|
||||
在历史中运行命令 (这里在第100行):
|
||||
运行history中的命令 (这里在history中的第100个):
|
||||
|
||||
!100
|
||||
|
||||
@ -102,11 +104,11 @@ unzip到目录中:
|
||||
|
||||
unzip package_name.zip -d dir_name
|
||||
|
||||
多行文字 (按 CTRL + d 退出):
|
||||
输入多行文字 (按 CTRL + d 退出):
|
||||
|
||||
cat > test.txt
|
||||
|
||||
创建空白的文件或者已存在的文件:
|
||||
创建空白的文件或者清空已存在的文件:
|
||||
|
||||
> test.txt
|
||||
|
||||
@ -114,16 +116,16 @@ unzip到目录中:
|
||||
|
||||
ntpdate ntp.ubuntu.com
|
||||
|
||||
netstat 显示所有tcp4监听的端口:
|
||||
netstat 显示所有IPv4的TCP监听的端口:
|
||||
|
||||
netstat -lnt4 | awk '{print $4}' | cut -f2 -d: | grep -o '[0-9]*'
|
||||
|
||||
将qcow2图像转化成raw:
|
||||
将qcow2的镜像转化成raw格式:
|
||||
|
||||
qemu-img convert -f qcow2 -O raw precise-server-cloudimg-amd64-disk1.img \
|
||||
precise-server-cloudimg-amd64-disk1.raw
|
||||
|
||||
重复运行命令,显示它的输出 (默认2s刷新):
|
||||
重复运行命令并显示它的输出 (默认2秒重复一次):
|
||||
|
||||
watch ps -ef
|
||||
|
||||
@ -131,17 +133,17 @@ netstat 显示所有tcp4监听的端口:
|
||||
|
||||
getent passwd
|
||||
|
||||
以读写模式挂载root:
|
||||
以读写模式挂载根文件系统:
|
||||
|
||||
mount -o remount,rw /
|
||||
|
||||
挂在目录 (适合于符号链接不成功的情况下):
|
||||
挂载目录 (适合于符号链接不能工作的情况下):
|
||||
|
||||
mount --bind /source /destination
|
||||
|
||||
发送动态更新给DNS:
|
||||
发送DNS动态更新给DNS:
|
||||
|
||||
nsupdate < <EOF
|
||||
nsupdate <<EOF
|
||||
update add $HOST 86400 A $IP
|
||||
send
|
||||
EOF
|
||||
@ -150,7 +152,7 @@ netstat 显示所有tcp4监听的端口:
|
||||
|
||||
grep -r "some_text" /path/to/dir
|
||||
|
||||
列出10个最大的已打开的文件:
|
||||
列出10个最大的系统中已打开的文件:
|
||||
|
||||
lsof / | awk '{ if($7 > 1048576) print $7/1048576 "MB "$9 }' | sort -n -u | tail
|
||||
|
||||
@ -162,15 +164,15 @@ netstat 显示所有tcp4监听的端口:
|
||||
|
||||
vim + some_file_name
|
||||
|
||||
git clone特定branch (master):
|
||||
git clone特定branch (本例是master分支):
|
||||
|
||||
git clone git@github.com:name/app.git -b master
|
||||
|
||||
git切换到另外一个branch (develop):
|
||||
git切换到另外一个branch (本例是develop分支):
|
||||
|
||||
git checkout develop
|
||||
|
||||
git删除一个branch(myfeature):
|
||||
git删除一个branch(本例是myfeature):
|
||||
|
||||
git branch -d myfeature
|
||||
|
||||
@ -198,23 +200,23 @@ Git push 新的branch到远程:
|
||||
|
||||
< test.txt sed -n '50,60p'
|
||||
|
||||
运行最后的命令 (如果是: mkdir /root/test, 下面会运行: sudo mkdir /root/test):
|
||||
以sudo权限重新运行上一个执行的命令 (如果是: mkdir /root/test, 下面会运行: sudo mkdir /root/test)(译注:当你执行一个命令忘记sudo时,可以这样重新执行,而不必再把完整命令敲一遍):
|
||||
|
||||
sudo !!
|
||||
|
||||
创建临时RAM文件系统 - ramdisk (首先创建在 /tmpram 目录):
|
||||
创建临时RAM文件系统 - ramdisk (请先创建 /tmpram 目录):
|
||||
|
||||
mount -t tmpfs tmpfs /tmpram -o size=512m
|
||||
|
||||
Grep完整单词:
|
||||
Grep完整的单词(译注:而不是其它单词的一部分):
|
||||
|
||||
grep -w "name" test.txt
|
||||
|
||||
需要特权模式在一个文件后追加文本:
|
||||
提升权限后在一个文件后追加文本:
|
||||
|
||||
echo "some text" | sudo tee -a /path/file
|
||||
|
||||
列出所有的kill信号:
|
||||
列出所有支持的kill信号:
|
||||
|
||||
kill -l
|
||||
|
||||
@ -226,7 +228,7 @@ Grep完整单词:
|
||||
|
||||
kill -9 $$
|
||||
|
||||
扫描网络找出打开的端口:
|
||||
扫描网络来找出开放的端口:
|
||||
|
||||
nmap -p 8081 172.20.0.0/16
|
||||
|
||||
@ -234,15 +236,15 @@ Grep完整单词:
|
||||
|
||||
git config --global user.email "me@example.com"
|
||||
|
||||
如果你有未提交的commit,与master同步:
|
||||
如果你有未提交的commit,与master同步:
|
||||
|
||||
git pull --rebase origin master
|
||||
|
||||
将文件中含有txt的所有文件移动到/home/user:
|
||||
将文件名中含有txt的所有文件移动到/home/user:
|
||||
|
||||
find -iname "*txt*" -exec mv -v {} /home/user \;
|
||||
|
||||
一行行合并文件:
|
||||
按行将两个文件中的对应行合并显示:
|
||||
|
||||
paste test.txt test1.txt
|
||||
|
||||
@ -254,19 +256,19 @@ shell中的进度条:
|
||||
|
||||
echo "hosts.sampleHost 10 `date +%s`" | nc 192.168.200.2 3000
|
||||
|
||||
转换tab到空格:
|
||||
转换tab为空格:
|
||||
|
||||
expand test.txt > test1.txt
|
||||
|
||||
跳过bash历史:
|
||||
|
||||
< <space>>cmd
|
||||
<<空格>>cmd
|
||||
|
||||
回到先前的工作目录:
|
||||
回到之前的工作目录:
|
||||
|
||||
cd -
|
||||
|
||||
切割大的tar.gz文件 (每个 100MB) 并还原:
|
||||
切割大的tar.gz文件为几个文件 (每个100MB),并还原:
|
||||
|
||||
split –b 100m /path/to/large/archive /path/to/output/files
|
||||
cat files* > archive
|
||||
@ -287,7 +289,7 @@ shell中的进度条:
|
||||
|
||||
lsblk -f
|
||||
|
||||
找出末尾空格的文件:
|
||||
找出文件中带有末尾空格的文件:
|
||||
|
||||
find . -type f -exec egrep -l " +$" "{}" \;
|
||||
|
||||
@ -305,6 +307,6 @@ shell中的进度条:
|
||||
|
||||
via: http://www.techbar.me/linux-shell-tips/
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
25
published/Proprietary Unix Continues to Fall.md
Normal file
25
published/Proprietary Unix Continues to Fall.md
Normal file
@ -0,0 +1,25 @@
|
||||
Unix 持有量持续缩减
|
||||
================================================================================
|
||||
|
||||
国际数据公司(IDC)的分析师在周三投寄了一篇[新闻稿][1]凸显出IBM 的 AIX 系统和 P-系列的硬件持有量已经快速下降。伴随着专有 Unix 系统下跌的同时,相关的运行着 Linux 系统的 X86 服务器销量却在崛起。IBM 已经明确指出这是一个长期趋势,所以投资了10亿美元用在基于 Power 系统的 Linux 开发。与新闻报道的 AIX 20%销售额下降的同时,我的这篇文章终于发布出来了。
|
||||
|
||||
过去数年中,我在管理 AIX 和 Linux 系统上一点都不顺利,如果能让我挑选的话,会选择灵活性和易用性更好的 Linux 系统和稳定性更高的 Power 机器。根据我的经验, AIX 很难设置,在设置好后要变动也很困难,但一旦设置好并启动起来,它就会一直很好的运行下去。一台配置合适的 AIX 服务器可以正常运行数年而无需干预,但是需要修改配置的时候,并且经常需要修改配置,就准备好长期的艰苦跋涉吧。相比之下,经过这么多年来,成千上万的开发人员和系统管理员,以及大牌公司的贡献,使得Linux更易于管理。根据[Infoworld][2]报道:
|
||||
|
||||
> Linux服务器市场正在健步崛起,服务器总销量占总收入的百分比高达28%,所以任何可以提高市场占有率的投资,将会非常有价值,即使大部分份额的Linux服务器仍然是商用 x86 硬件。
|
||||
|
||||
Intel 和 AMD 的硬件也现跨越式发展,正在缩小与 Power 机器的性能差距。当我听到一个新的刀片上配置 10GB 的以太网卡已经成为标准、256GB 的 RAM 已经很正常了,以及普通业务需要订购装有 16 核 CPU 的服务器已经成为常态时,吃惊不小。Intel 服务器和 IBM 的 Power 服务器性能差不多,但价格低很多。因为企业的关注点在于是否逃脱“顾问软件”及 IBM 的供应商锁定,所以在行业标准的x86硬件上运行的开源软件正变得越来越有吸引力。不过,IBM已经降低了 Power 系列机器的价格来保持竞争力。
|
||||
|
||||
这说明, IBM 选择投入在基于 Power 机器的 Linux 系统而不是 AIX 系统。 IBM 可能已经开发出现代版的 AIX,并使用通用的开源工具以使交互操作性更好。尽管 IBM 声明 AIX 仍然是重要的,但在 Power 机器的销售额持续下降,伴随的是 Linux 方面的投入,这一切的一切都正在翻开新故事的新篇章。
|
||||
|
||||
IBM 不可能一切都以 AIX 为核心,但他们可能会无限期的延长其使用寿命。如果 AIX 做为开源系统发布,看看市场的反映,将会十分精彩。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ostatic.com/blog/proprietary-unix-continues-to-fall
|
||||
|
||||
译者:[runningwater](https://github.com/runningwater) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.idc.com/getdoc.jsp?containerId=prUS24476413
|
||||
[2]:http://www.infoworld.com/t/unix/ibms-losing-ground-unix-and-oracle-may-follow-232234
|
||||
240
published/Setup a jailed shell with jailkit on ubuntu.md
Normal file
240
published/Setup a jailed shell with jailkit on ubuntu.md
Normal file
@ -0,0 +1,240 @@
|
||||
在Ubuntu下用jailkit建立一个受限Shell
|
||||
================================================================================
|
||||
|
||||
### Jailkit和jailed Shell ###
|
||||
|
||||
受限shell(Jailed Shell)是一类被限制的shell,它看起来非常像真实的Shell,但是它不允许查看和修改真实的文件系统的任何部分。Shell内的文件系统不同于底层的文件系统。这种功能是通过chroot和其他多种程序实现的。举例来说,给用户建立一个linux shell去让他“玩玩”,或者在一个限定的环境里运行一些程序的所有功能等等。
|
||||
|
||||
在这个教程里我们将会探讨在Ubuntu下用jailkit建立一个受限shell。Jailkit是一个让你快速建立一个受限shell的工具,将受限用户放到里面,并配置那些要在受限制环境里运行的程序。
|
||||
|
||||
Jailkit 从这里下载:[http://olivier.sessink.nl/jailkit/][1]
|
||||
|
||||
|
||||
###在Ubuntu/Debian 上安装 jailkit ###
|
||||
|
||||
1. 因为jaikit需要在系统上编译,首先,我们需要有用于编译的那些工具。所以,安装如下包:
|
||||
|
||||
$ sudo apt-get install build-essential autoconf automake libtool flex bison debhelper binutils-gold
|
||||
|
||||
2. 从下述URL下载Jailkit,或者访问它的网站以下载最新版本的,如果有了更新版本的话。http://olivier.sessink.nl/jailkit/jailkit-2.16.tar.gz
|
||||
|
||||
$ wget http://olivier.sessink.nl/jailkit/jailkit-2.16.tar.gz
|
||||
|
||||
3. 解压
|
||||
|
||||
$ tar -vxzf jailkit-2.16.tar.gz
|
||||
|
||||
4. 编译并创建deb软件包
|
||||
|
||||
Jailkit已经包含了用于编译成deb软件包的代码和配置,可以直接安装在Debian系的Linux上。运行下列命令来完成它。
|
||||
|
||||
$ cd jailkit-2.16/
|
||||
$ sudo ./debian/rules binary
|
||||
|
||||
5. 安装deb软件包
|
||||
|
||||
上述命令创建的deb软件包叫做: jailkit_2.16-1_amd64.deb.
|
||||
|
||||
$ cd ..
|
||||
$ sudo dpkg -i jailkit_2.16-1_amd64.deb
|
||||
|
||||
就是这样,现在Jailkit已经安装完成了。Jailkit有许多命令可以用来设置一个基于chroot的受限环境,如下是这些命令:
|
||||
|
||||
$ jk_
|
||||
jk_addjailuser jk_chrootlaunch jk_cp jk_jailuser jk_lsh jk_uchroot
|
||||
jk_check jk_chrootsh jk_init jk_list jk_socketd jk_update
|
||||
|
||||
上述命令都有man帮助信息,如果你使用它们时,可以参考。
|
||||
|
||||
### 配置Jailed Shell ###
|
||||
|
||||
1. 配置受限环境
|
||||
|
||||
我们需要建立一个目录来存放所有受限环境的配置。目录随便放在什么地方,比如我们可以创建个/opt/jail的目录。
|
||||
|
||||
$ sudo mkdir /opt/jail
|
||||
|
||||
这个目录应为Root所有。用chown改变属主。
|
||||
|
||||
$ sudo chown root:root /opt/jail
|
||||
|
||||
2. 设置在受限环境中可用的程序
|
||||
|
||||
任何程序想要在受限环境中执行则必须用jk_init命令拷贝到目录中。
|
||||
|
||||
例如:
|
||||
|
||||
$ sudo jk_init -v /jail basicshell
|
||||
$ sudo jk_init -v /jail editors
|
||||
$ sudo jk_init -v /jail extendedshell
|
||||
$ sudo jk_init -v /jail netutils
|
||||
$ sudo jk_init -v /jail ssh
|
||||
$ sudo jk_init -v /jail sftp
|
||||
$ sudo jk_init -v /jail jk_lsh
|
||||
|
||||
或一次性解决:
|
||||
|
||||
$ sudo jk_init -v /opt/jail netutils basicshell jk_lsh openvpn ssh sftp
|
||||
|
||||
像basicshell, editors, netutils是一些组名,其中包含多个程序。复制到jail shell中的每个组都是可执行文件、库文件等的集合。比如**basicshell**就在jail提供有bash, ls, cat, chmod, mkdir, cp, cpio, date, dd, echo, egrep等程序。
|
||||
|
||||
完整的程序列表设置,你可以在/etc/jailkit/jk_init.ini中查看。
|
||||
|
||||
> jk_lsh (Jailkit limited shell) - 这是一个重要的部分,必须添加到受限环境中。
|
||||
|
||||
3. 创建将被监禁的用户
|
||||
|
||||
需要将一个用户放入jail里。可以先创建一个
|
||||
|
||||
$ sudo adduser robber
|
||||
Adding user `robber' ...
|
||||
Adding new group `robber' (1005) ...
|
||||
Adding new user `robber' (1006) with group `robber' ...
|
||||
Creating home directory `/home/robber' ...
|
||||
Copying files from `/etc/skel' ...
|
||||
Enter new UNIX password:
|
||||
Retype new UNIX password:
|
||||
passwd: password updated successfully
|
||||
Changing the user information for robber
|
||||
Enter the new value, or press ENTER for the default
|
||||
Full Name []:
|
||||
Room Number []:
|
||||
Work Phone []:
|
||||
Home Phone []:
|
||||
Other []:
|
||||
Is the information correct? [Y/n] y
|
||||
|
||||
注意:目前创建的是一个在实际文件系统中的普通用户,并没有添加到受限环境中。
|
||||
|
||||
在下一步这个用户会被放到受限环境里。
|
||||
|
||||
这时候如果你查看/etc/passwd文件,你会在文件最后看到跟下面差不多的一个条目。
|
||||
|
||||
robber:x:1006:1005:,,,:/home/robber:/bin/bash
|
||||
|
||||
这是我们新创建的用户,最后部分的/bin/bash指示了这个用户如果登入了那么它可以在系统上正常的Shell访问
|
||||
|
||||
4. 限制用户
|
||||
|
||||
现在是时候将用户限制
|
||||
|
||||
$ sudo jk_jailuser -m -j /opt/jail/ robber
|
||||
|
||||
执行上列命令后,用户robber将会被限制。
|
||||
|
||||
如果你现在再观察/etc/passwd文件,会发现类似下面的最后条目。
|
||||
|
||||
robber:x:1006:1005:,,,:/opt/jail/./home/robber:/usr/sbin/jk_chrootsh
|
||||
|
||||
注意:最后两部分表明用户主目录和shell类型已经被改变了。现在用户的主目录在/opt/jail(受限环境)中。用户的Shell是一个名叫jk_chrootsh的特殊程序,会提供Jailed Shell。
|
||||
|
||||
jk_chrootsh这是个特殊的shell,每当用户登入系统时,它都会将用户放入受限环境中。
|
||||
|
||||
到目前为止受限配置已经几乎完成了。但是如果你试图用ssh连接,那么注定会失败,像这样:
|
||||
|
||||
$ ssh robber@localhost
|
||||
robber@localhost's password:
|
||||
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-25-generic x86_64)
|
||||
* Documentation: https://help.ubuntu.com/
|
||||
13 packages can be updated.
|
||||
0 updates are security updates.
|
||||
*** /dev/sda7 will be checked for errors at next reboot ***
|
||||
*** /dev/sda8 will be checked for errors at next reboot ***
|
||||
Last login: Sat Jun 23 12:45:13 2012 from localhost
|
||||
Connection to localhost closed.
|
||||
$
|
||||
|
||||
连接会立马关闭,这意味着用户已经活动在一个受限制的shell中。
|
||||
|
||||
5. 给在jail中的用户Bash Shell
|
||||
|
||||
下个重要的事情是给用户在限制环境中的一个正确的bash shell。
|
||||
|
||||
打开下面的文件
|
||||
|
||||
/opt/jail/etc/passwd
|
||||
|
||||
这是个jail中的password文件。类似如下
|
||||
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
robber:x:1006:1005:,,,:/home/robber:/usr/sbin/jk_lsh
|
||||
|
||||
将/usr/sbin/jk_lsh改为/bin/bash
|
||||
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
robber:x:1006:1005:,,,:/home/robber:/bin/bash
|
||||
|
||||
保存文件并退出。
|
||||
|
||||
6. 登入限制环境
|
||||
|
||||
现在让我们再次登入受限环境
|
||||
|
||||
$ ssh robber@localhost
|
||||
robber@localhost's password:
|
||||
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-25-generic x86_64)
|
||||
* Documentation: https://help.ubuntu.com/
|
||||
13 packages can be updated.
|
||||
0 updates are security updates.
|
||||
*** /dev/sda7 will be checked for errors at next reboot ***
|
||||
*** /dev/sda8 will be checked for errors at next reboot ***
|
||||
Last login: Sat Jun 23 12:46:01 2012 from localhost
|
||||
bash: groups: command not found
|
||||
I have no name!@desktop:~$
|
||||
|
||||
受限环境说'I have no name!',哈哈。现在我们在受限环境中有了个完整功能的bash shell。
|
||||
|
||||
现在看看实际的环境。受限环境中的根目录实际就是真实文件系统中的/opt/jail。但这只有我们自己知道,受限用户并不知情。
|
||||
|
||||
I have no name!@desktop:~$ cd /
|
||||
I have no name!@desktop:/$ ls
|
||||
bin dev etc home lib lib64 run usr var
|
||||
I have no name!@desktop:/$
|
||||
|
||||
也只有我们通过jk_cp拷贝到jail中的命令能使用。
|
||||
|
||||
如果登入失败,请检查一下/var/log/auth.log的错误信息。
|
||||
|
||||
现在尝试运行一些网络命令,类似wget的命令。
|
||||
|
||||
$ wget http://www.google.com/
|
||||
|
||||
如果你获得类似的错误提示:
|
||||
|
||||
$ wget http://www.google.com/
|
||||
--2012-06-23 12:56:43-- http://www.google.com/
|
||||
Resolving www.google.com (www.google.com)... failed: Name or service not known.
|
||||
wget: unable to resolve host address `www.google.com'
|
||||
|
||||
你可以通过运行下列两条命令来解决这个问题:
|
||||
|
||||
$ sudo jk_cp -v -j /opt/jail /lib/x86_64-linux-gnu/libnss_files.so.2
|
||||
$ sudo jk_cp -v -j /opt/jail /lib/x86_64-linux-gnu/libnss_dns.so.2
|
||||
|
||||
这样才能正确的定位到libnss_files.so和libnss_dns.so
|
||||
|
||||
### 在限制环境中运行程序或服务 ###
|
||||
|
||||
现在配置已经完成了。可以在限制/安全的环境里运行程序或服务。要在限制环境中启动一个程序或守护进程可以用**jk_chrootlaunch**命令。
|
||||
|
||||
$ sudo jk_chrootlaunch -j /opt/jail -u robber -x /some/command/in/jail
|
||||
|
||||
jk_chrootlaunch工具可以在限制环境中启动一个特殊的进程同时指定用户特权。如果守护进程启动失败,请检查/var/log/syslog/错误信息。
|
||||
|
||||
在限制环境中运行程序之前,该程序必须已经用jk_cp命令复制到jail中。
|
||||
|
||||
> jk_cp - 将文件包括权限信息和库文件复制到jail的工具
|
||||
|
||||
进一步阅读有关其他jailkit命令信息,可以阅读文档,[http://olivier.sessink.nl/jailkit/][1]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
via: http://www.binarytides.com/install-jailkit-ubuntu-debian/
|
||||
|
||||
via: http://www.binarytides.com/setup-jailed-shell-jailkit-ubuntu/
|
||||
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://olivier.sessink.nl/jailkit/
|
||||
|
||||
@ -0,0 +1,101 @@
|
||||
TeamViewer 9发布-在Linux下安装运行
|
||||
================================================================================
|
||||
这篇指南介绍了怎么样在 **RedHat、 CentOS、 Fedora** 和 **Debian**、 **Ubuntu**、 **Linux Mint**、 **Xubuntu** 等这些系统中安装 **Teamviewer 9**。**Teamviewer** 是一款流行的应用软件,用于远程辅助、桌面共享、计算机之间互传文件、网络会议及在线会议等方面,并且它是一款专业应用程序。而且,个人用户可以免费使用。Teamviewer可以运行在 **Windows、Linux、Mac OS、Android** 系统以及 **iPhone** 设备上,它使用它自己集成的 **WINE** 环境来运行,所以我们用的时候不需单独[安装 WINE 程序][1]了。 **Teamviewer** 并不是原生的 **Linux** 应用程序。
|
||||
|
||||
最新的稳定版本 **TeamViewer 9** 近期已经发布了,有了些新的功能和性能的改进。在 **TeamViewer 9** 中增加的一些新功能特性,其要点如下:
|
||||
|
||||
### Windows、Linux 和 Mac 系统下的功能特性 ###
|
||||
|
||||
- 在不同的选项卡中打开多个链接
|
||||
- 支持局域网唤醒
|
||||
- 支持为 TeamViewer 帐户添加双因子身份验证
|
||||
- 支持 Windows 8.1 和 Mac OS X Mavericks 系统
|
||||
- 能保存自定义模块,如uickSupport、QuickJoin等等
|
||||
- 集成了应用程序编程接口(API)
|
||||
- 更强的 Teamviewer 账户安全
|
||||
- 通过桌面快捷方式快速连接
|
||||
- 可视化通知信息
|
||||
- 不同计算机间复制和粘贴文件和文本
|
||||
- 不同计算机间的初始化文件传输
|
||||
- 视频传输更快
|
||||
|
||||
### 在 RedHat、 CentOS、 Fedora 上安装 Teamviewer 9 ###
|
||||
|
||||
你可以在 [teamviewer_linux.rpm][2] 上下载到基于 Linux 发行版本的 rpm 包。
|
||||
|
||||
# wget http://www.teamviewer.com/download/teamviewer_linux.rpm
|
||||
|
||||
然后开始安装。进入你的下载包所在的目录,执行如下的 yum 命令来安装,它将会自动安装需要的依赖包。
|
||||
|
||||
# yum install teamviewer_linux.rpm
|
||||
|
||||
如果出现公钥缺失错误,你可以用如下命令来下载,并导入之。
|
||||
|
||||
# wget http://www.teamviewer.com/link/?url=354858
|
||||
# rpm --import TeamViewer_Linux_PubKey.asc
|
||||
|
||||
在导入公钥后,请再一次运行 “ **yum install** ” 命令来安装 Teamviewer rpm 包。
|
||||
|
||||
要启动运行 Teamviewer 应用,从终端中运行如下命令。
|
||||
|
||||
# teamviewer
|
||||
|
||||
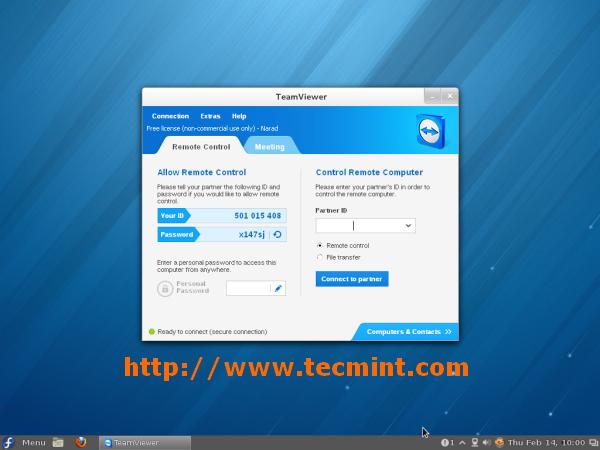
Teamviewer 应用程序正运行在我的 **Fedora 18** 系统上。
|
||||
|
||||
|
||||
|
||||
*Fedora 18 系统上运行的 TeamViewer*
|
||||
|
||||
### 在 Ubuntu, Linux Mint, Xubuntu 上安装 Teamviewer 9 ###
|
||||
|
||||
你可以在 [teamviewer linux .deb][3] 上下载到基于 **32-位** 系统或 **64-位** 系统的 teamviewer 安装包,或者你可以用如下所示的 **wget** 命令来下载安装包。
|
||||
|
||||
## 32 位系统 ##
|
||||
$ sudo wget http://www.teamviewer.com/download/teamviewer_linux.deb
|
||||
|
||||
## 64 位系统 ##
|
||||
$ sudo wget http://www.teamviewer.com/download/teamviewer_linux_x64.deb
|
||||
|
||||
一旦下载好,就可以进入你下载的 Teamviewer 包所在的目录,然后运行如下命令来安装。
|
||||
|
||||
## 32 位系统 ##
|
||||
$ sudo dpkg -i teamviewer_linux.deb
|
||||
|
||||
## 64 位系统 ##
|
||||
$ sudo dpkg -i teamviewer_linux_x64.deb
|
||||
|
||||
如果出现有缺失依赖包错误这种情况,请使用如下命令来安装这些依赖包。
|
||||
|
||||
sudo apt-get install -f
|
||||
|
||||
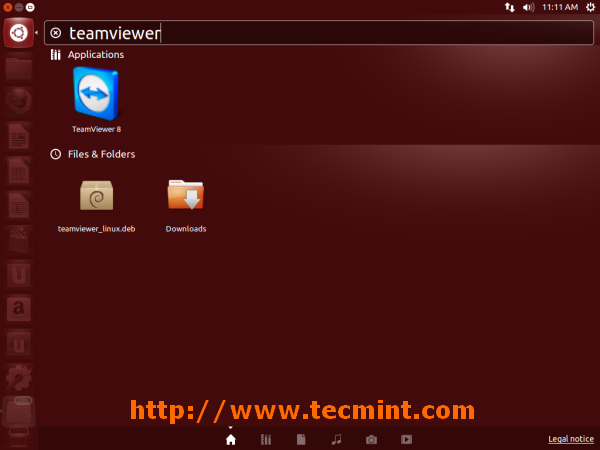
一旦全部都安装成功,在 **Ubuntu** 系统中要启动 Teamviewer,打开 **Dash 主窗口**,输入 **teamviewer** ,然后点击出现的 **teamviewer** 图标,程序就启动运行了。
|
||||
|
||||
|
||||
|
||||
*Ubuntu 13.10 系统上运行的 TeamViewer*
|
||||
|
||||
Teamviewer 应用程序正运行在我的 **Ubuntu 13.10** 系统上。
|
||||
|
||||
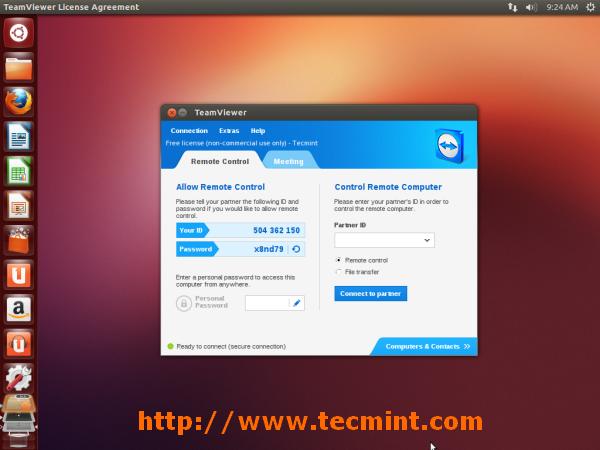
|
||||
|
||||
*在 Ubuntu 13.10 下的 TeamViewer 9*
|
||||
|
||||
要在 **Linux Mint** 上启动,进入 **菜单 >> 网络 >> Teamviewer**, 并点击 **接受许可协议** 来启动运行 TeamViewer。
|
||||
|
||||
Teamviewer 应用程序正运行在我的 **Linux Mint 15** 系统上。
|
||||
|
||||
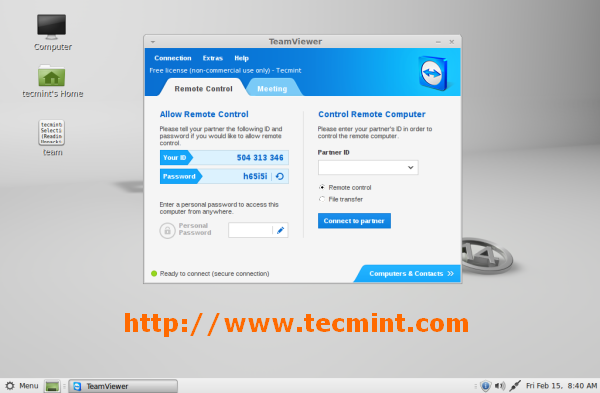
|
||||
|
||||
*Linux Mint 15 系统上运行的 TeamViewer*
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/how-to-install-teamviewer-on-linux-distributions/
|
||||
|
||||
译者:[runningwater](https://github.com/runningwater) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.tecmint.com/install-wine-in-rhel-centos-and-fedora/
|
||||
[2]:http://www.teamviewer.com/download/teamviewer_linux.rpm
|
||||
[3]:http://www.teamviewer.com/hi/download/linux.aspx
|
||||
@ -1,4 +1,4 @@
|
||||
11 Linux内核: 配置内核 (Part 7)
|
||||
戴文的Linux内核专题:11 配置内核(7)
|
||||
================================================================================
|
||||

|
||||
|
||||
@ -6,11 +6,11 @@
|
||||
|
||||
进程地址空间标识符(Process Address Space Identifiers (PASIDs))允许PCI设备同时访问多个IO地址空间(PCI PASID support)。这个特性需要一个支持PASIDs支持的IOMMU。
|
||||
|
||||
下面我们可以启用/禁用"PCI IO-APIC hotplug support"。APIC代表高级可编程中断控制器(Advanced Programmable Interrupt Controllers)。可编程中断控制器(PIC)收集所有来自不同源发给一个或者多个CPU流水线的中断。高级PIC与PIC一样,但是它们有更多的特性像高级中断管理和更多的优先级模型。热插拔一种在系统在运行时加入一件设备的能力并且不需要重启。这个驱动是为了PCI主板能拥有处理输入/输出APIC热插拔的能力。
|
||||
下面我们可以启用/禁用"PCI IO-APIC hotplug support"。APIC代表高级可编程中断控制器(Advanced Programmable Interrupt Controllers)。可编程中断控制器(PIC)收集所有来自不同源发给一个或者多个CPU流水线的中断。高级PIC与PIC一样,但是它们有更多的特性像高级中断管理和更多的优先级模型。热插拔是一种在系统在运行时加入一件设备的能力并且不需要重启。这个驱动是为了PCI主板能拥有处理输入/输出APIC热插拔的能力。
|
||||
|
||||
在这之后,下面的问题询问的是启用"ISA-style DMA support"。在前文中提到过,DMA是直接内存访问,它是一种设备无需借助CPU直接访问内存的能力。ISA代表的是工业标准架构(Industry Standard Architecture),它是一种像PCI的总线标准。这个特性允许在ISA主板上支持DMA。
|
||||
|
||||
现在,我们可以移步到"PCCard (PCMCIA/CardBus) support"。PCMCIA代表的是个人计算机存储卡国际协会(Personal Computer Memory Card International Association)。PC卡、PCMCIA卡和Cardbus卡都是卡片形状的笔记本外设。
|
||||
现在,我们可以移步到"PC Card (PCMCIA/CardBus) support"。PCMCIA代表的是个人计算机存储卡国际协会(Personal Computer Memory Card International Association)。PC卡、PCMCIA卡和Cardbus卡都是卡片形状的笔记本外设。
|
||||
|
||||
下一个PCMCIA选项处理"16-bit PCMCIA support"。一些旧的计算机使用16位PCMCIA卡。
|
||||
|
||||
@ -38,7 +38,7 @@ CardBus是16位PCMCIA的更新32位版本。这个驱动提供对这类设备的
|
||||
|
||||
对于带有支持CompactPCI热插拔支持的CompactPCI卡的系统,启用"CompactPCI Hotplug driver"。
|
||||
|
||||
下面,我们有一个选项对于另一种COmpactPCI系统卡(Ziatech ZT5550 CompactPCI Hotplug)。
|
||||
下面,我们有一个选项对于另一种CompactPCI系统卡(Ziatech ZT5550 CompactPCI Hotplug)。
|
||||
|
||||
使用#ENUM热插拔信号通过标准IO口作为系统注册位的CompactPCI卡需要这个驱动(Generic port I/O CompactPCI Hotplug)。
|
||||
|
||||
@ -100,15 +100,15 @@ IPsec安全联合定位器可以当这个特性启用时(Transformation migrate
|
||||
|
||||
如果这是一个路由器Linux系统的内核,那就启用这个选项(IP: advanced router)。
|
||||
|
||||
下面的特性启用了,那么IP地址会在启动时自动配置(IP: kernel level autoconfiguration)。当用户希望不用配置就能连接到一个网络时是很有用的。
|
||||
如果下面的特性启用了,那么IP地址会在启动时自动配置(IP: kernel level autoconfiguration)。当用户希望不用配置就能连接到一个网络时是很有用的。
|
||||
|
||||
启用另外DHCP协议支持,那么Linux系统可以通过网络像NFS挂载它的根文件系统并且使用DHCP发现IP地址(IP: DHCP support)。这允许Linux系统通过网络拥有它的远程根文件系统而不必用户在每次系统启动时手动管理进程。
|
||||
启用了DHCP协议支持,那么Linux系统可以通过网络像NFS挂载它的根文件系统并且使用DHCP发现IP地址(IP: DHCP support)。这允许Linux系统通过网络拥有它的远程根文件系统而不必用户在每次系统启动时手动管理进程。
|
||||
|
||||
下面的选项和上面的类似除了使用的是BOOTP而不是DHCP(IP: BOOTP support。BOOTP是自举协议;这个协议使用UDP而不是TCP并且只能使用IPv4网络
|
||||
|
||||
RARP是一个由于BOOTP和DHCP如今已经废除了的旧协议,但是它仍可以加到内核中(IP: RARP support)。
|
||||
RARP是一个被BOOTP和DHCP替代了的旧协议,但是它仍可以加到内核中(IP: RARP support)。
|
||||
|
||||
网络协议可以在另一个概念中使用,称作"隧道"。这个特性可以用在Linux内核中(IP: tunneling)。安全shell协议(The secure shell protocol (SSH))就是隧道协议的一个例子。这个特性需要SSH。
|
||||
网络协议可以在另一个概念中使用,称作"隧道"。这个特性可以用在Linux内核中(IP: tunneling)。安全shell协议(The secure shell protocol (SSH))就是隧道协议的一个例子。SSH需要这个特性。
|
||||
|
||||
下面的驱动可以多路复用通用路由封装包(GRE (Generic Routing Encapsulation))(IP: GRE demultiplexer)。多路复用是一个使单个信号进入不同部分的过程(这不会复制消息,只是分解它)。GRE是一种隧道协议。
|
||||
|
||||
@ -122,6 +122,6 @@ RARP是一个由于BOOTP和DHCP如今已经废除了的旧协议,但是它仍
|
||||
|
||||
via: http://www.linux.org/threads/the-linux-kernel-configuring-the-kernel-part-7.4490/
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,4 +1,4 @@
|
||||
12 Linux内核: 配置内核 (Part 8)
|
||||
戴文的Linux内核专题:12 配置内核(8)
|
||||
================================================================================
|
||||
|
||||
|
||||
@ -12,7 +12,7 @@
|
||||
|
||||
下一个要配置的网络特性是"ARP daemon support"。这让内核有一张IP地址表以及它们相应的在内部缓存中的硬件地址。ARP代表的是地址解析协议(Address-Resolution-Protocol)。
|
||||
|
||||
为了额外的安全,"TCP syncookie support"应该要启用。这保护计算机免于受到SVN洪水攻击。黑客或者恶意软件可能会发送SVN信息给一台服务器来消耗它的资源,以便让真实的访客无法使用服务器提供的服务。SVN消息会打开一个计算机和服务器之间的连接。Syncookie会阻断不正当的SVN消息。那么,真实的用户可以仍旧访问访问网站而没有黑客消耗带宽。服务器应该启用这个特性。
|
||||
为了额外的安全,"TCP syncookie support"应该要启用。这保护计算机免于受到SYN洪水攻击。黑客或者恶意软件可能会发送SYN信息给一台服务器来消耗它的资源,以便让真实的访客无法使用服务器提供的服务。SYN消息会打开一个计算机和服务器之间的连接。Syncookie会阻断不正当的SYN消息。那么,真实的用户可以仍旧访问访问网站,而黑客则没办法浪费你的带宽。服务器应该启用这个特性。
|
||||
|
||||
下面的特性是用于 "Virtual (secure) IP: tunneling"。隧道是一个网络协议到另外一个网络协议的封装。当在使用虚拟私人网络(VPN)时需要使用安全隧道。
|
||||
|
||||
@ -20,7 +20,7 @@
|
||||
|
||||
在这之后,启用"ESP transformation"增加对IPSec封装安全协议的支持。这是加密与可选择的数据验证的安全措施。
|
||||
|
||||
如果启用了这个特性(IP: IPComp transformation),Linux内核会支持IP负载压缩协议。这是一种无损压缩系统。无损指的是数据仍在它的完整形式。在解压缩后,数据在压缩前后没有变化。压缩在加密前先执行。由于更少的数据传输,所以这个压缩协议可以加速网络。
|
||||
如果启用了这个特性(IP: IPComp transformation),Linux内核会支持IP负载压缩协议。这是一种无损压缩系统。无损指的是数据仍会保持完整,在解压缩后,数据在压缩前后没有变化。压缩在加密前先执行。由于更少的数据传输,所以这个压缩协议可以加速网络。
|
||||
|
||||
下面三个设置用于处理不同的IPsec特性("IP: IPsec transport mode"、"IP: IPsec tunnel mode"和"IP: IPsec BEET mode")。IPSec代表的是因特网安全协议(Internet Protocol SECurity).两台计算机之间并且/或者服务器间的传输模式是默认的IPSec模式。传输模式使用AH或者ESP头并且只加密IP头。在隧道模式下,IP头和负载会被加密。隧道模式通常用于连接网关到服务器/服务器或者服务器到服务器。BEET模式(Bound End-to-End Tunnel)不会在IP地址改变时重连。BEET模式下的连接会仍然存在。BEET模式比其他几种模式使用更少的字节。
|
||||
|
||||
@ -38,7 +38,7 @@ TCP连接可以被MD5保护(TCP: MD5 Signature Option support)。这用于保护
|
||||
|
||||
下面的特性是一个特殊的隐私特性(IPv6: Privacy Extensions (RFC 3041) support)。这使得系统在网络接口中生成并使用不同的随即地址。
|
||||
|
||||
注意:没有计算机是真正随机的。计算机中随机数和随机字串通常称为伪随机。
|
||||
注意:计算机中没有数据是真正随机的。计算机中随机数和随机字串通常称为伪随机。
|
||||
|
||||
在多路由的网络中,这个特性允许系统能够更有效地计算出该使用哪一个(IPv6: Router Preference (RFC 4191))。
|
||||
|
||||
@ -132,6 +132,6 @@ LAN仿真(LANE)仿真了ATM网络上的LAN服务(LAN Emulation (LANE) support)
|
||||
|
||||
via: http://www.linux.org/threads/the-linux-kernel-configuring-the-kernel-part-8.4525/
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,10 +1,10 @@
|
||||
戴文的Linux内核专题:13 内核配置(9)
|
||||
戴文的Linux内核专题:13 配置内核(9)
|
||||
================================================================================
|
||||
|
||||
|
||||
Novell网络协议,IPX通常用于Windows系统和NetWare服务器(The IPX protocol)。IPX代表网间分组交换(Internetwork Packet Exchange)。这是一个网络层协议通常与传输层的SPX协议同时使用。
|
||||
Novell的网络协议IPX通常用于Windows系统和NetWare服务器(The IPX protocol)。IPX代表网间分组交换(Internetwork Packet Exchange)。这是一个网络层协议通常与传输层的SPX协议同时使用。
|
||||
|
||||
为了是NetWare服务器在服务的网络中有相同的IPX地址,启用下一个特性(IPX: Full internal IPX network)。不然,每个网络都会看到服务器一个不同的IPX地址。
|
||||
为了使NetWare服务器在服务的网络中有相同的IPX地址,启用下一个特性(IPX: Full internal IPX network)。不然,每个网络都会看到服务器一个不同的IPX地址。
|
||||
|
||||
注意:IPX协议使用IPX寻址,而不是IP寻址。IP地址不是计算机网络中唯一的网络地址。
|
||||
|
||||
@ -30,7 +30,7 @@ Nokia调制解调器使用的电话网络协议通常称作"PhoNet"(Phonet proto
|
||||
|
||||
支持物理层 IEEE 802.15.4协议的SoftMac设备可以启用这个特性(Generic IEEE 802.15.4 Soft Networking Stack (mac802154))。
|
||||
|
||||
当有许多包需要传输是,内核必须决定先发送哪一个(它们不能一次全部发送),所以这个特性帮助内核区分包的优先级(QoS and/or fair queuing)。如果不启用这个,那么内核会使用"first come, first serve approach"("谁先到,谁先服务")。这可能意味着紧急的网络消息需要等待轮到它们传输。
|
||||
当有许多包需要传输时,内核必须决定先发送哪一个(它们不能一次全部发送),所以这个特性帮助内核区分包的优先级(QoS and/or fair queuing)。如果不启用这个,那么内核会使用"first come, first serve approach"("谁先到,谁先服务")。这可能意味着紧急的网络消息需要等待才能轮到它们传输。
|
||||
|
||||
在有数据中心服务器的网络中,这个特性强烈建议启用(Data Center Bridging support)。这个特性增强了以太网对数据中心网络的连接。
|
||||
|
||||
@ -76,20 +76,19 @@ NET/ROM的一个替代是"Packet Layer Protocol (PLP)"(包层协议),它可以
|
||||
|
||||
如果启用了(一些选项),Linux内核可以支持很多CAN设备(主要是控制器)和接口。所有的CAN驱动都是对于这些设备的不同品牌和型号。在配置工具中,它们有以下这些标题。
|
||||
|
||||
|
||||
Virtual Local CAN Interface (vcan)
|
||||
Serial / USB serial CAN Adaptors (slcan)
|
||||
Platform CAN drivers with Netlink support
|
||||
Enable LED triggers for Netlink based drivers
|
||||
Microchip MCP251x SPI CAN controllers
|
||||
Janz VMOD-ICAN3 Intelligent CAN controller
|
||||
Intel EG20T PCH CAN controller
|
||||
Philips/NXP SJA1000 devices
|
||||
Bosch C_CAN/D_CAN devices
|
||||
Bosch CC770 and Intel AN82527 devices
|
||||
CAN USB interfaces
|
||||
Softing Gmbh CAN generic support
|
||||
Softing Gmbh CAN pcmcia cards
|
||||
- Virtual Local CAN Interface (vcan)
|
||||
- Serial / USB serial CAN Adaptors (slcan)
|
||||
- Platform CAN drivers with Netlink support
|
||||
- Enable LED triggers for Netlink based drivers
|
||||
- Microchip MCP251x SPI CAN controllers
|
||||
- Janz VMOD-ICAN3 Intelligent CAN controller
|
||||
- Intel EG20T PCH CAN controller
|
||||
- Philips/NXP SJA1000 devices
|
||||
- Bosch C_CAN/D_CAN devices
|
||||
- Bosch CC770 and Intel AN82527 devices
|
||||
- CAN USB interfaces
|
||||
- Softing Gmbh CAN generic support
|
||||
- Softing Gmbh CAN pcmcia cards
|
||||
|
||||
像Linux中的其他许多特性,CAN设备同样可以启用调试能力(CAN devices debugging messages)。再说一次,记住你内核的目的,你需要调试还是需要性能?
|
||||
|
||||
@ -150,6 +149,6 @@ mac80211同样支持debugfs特性(Export mac80211 internals in DebugFS)。
|
||||
|
||||
via: http://www.linux.org/threads/the-linux-kernel-configuring-the-kernel-part-9.4568/
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -20,7 +20,7 @@ Unigine 引擎正是由 Unigine 公司开发的, 同时这公司还开发了 H
|
||||
- 密杂草丛的高度现已实现同步。
|
||||
- 修复了在渲染非 Flash 闪屏时崩溃的漏洞。
|
||||
|
||||
所有平台的完整新特性列表,可以在官方的[公告]中找到。[1].
|
||||
所有平台的完整新特性列表,可以在官方的[公告][1]中找到。.
|
||||
|
||||
要记住 UNIGINE 引擎只针对商业企业,并不向广大用户提供试用版。
|
||||
|
||||
@ -28,19 +28,9 @@ Unigine 引擎正是由 Unigine 公司开发的, 同时这公司还开发了 H
|
||||
|
||||
via: http://news.softpedia.com/news/UNIGINE-Is-Probably-the-Best-Gaming-Engine-on-Linux-404484.shtml
|
||||
|
||||
译者:[hyaocuk](https://github.com/hyaocuk) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[hyaocuk](https://github.com/hyaocuk) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.unigine.com/devlog/2013/11/27/113
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
|
||||
@ -1,30 +0,0 @@
|
||||
[translated BY stduolc]
|
||||
Canonical and ASUS Have Formed a Partnership in USA
|
||||
================================================================================
|
||||
**Canonical and ASUS have formed a partnership that would enable the hardware vendor to equip a couple of its laptops with the Ubuntu operating system.**
|
||||
|
||||
ASUS is now providing the X201E and 1015E laptops with Ubuntu preinstalled in an effort to penetrate the education market.
|
||||
|
||||
“As Ubuntu, and all the software bundled on it is free, there’s no licence fees in the purchase price which significantly reduces cost. This is perfect for students and institutions, both of whose finances can be hard pressed.”
|
||||
|
||||
“Productivity applications are taken care of by LibreOffice. Familiar feeling, they offer all the functionality students and staff need and are fully compatible with existing files from the leading proprietary alternative. There are also bundled free applications for email and web browsing,” reads the official [announcement][1] on Ubuntu’s website.
|
||||
|
||||
The two laptops are not exactly powerhouses and are aimed at productivity, and maybe multimedia content. The ASUS 1015E laptop features a Intel Celeron 847 1.1 GHz processor, 2 GB DDR3 Memory, a 320 GB 5400 rpm Hard Drive, and a 10.1-Inch screen.
|
||||
|
||||
The other model, which is currently out of stock, ASUS X201E, is a little bit more powerful, but not by much: Intel Celeron 847 (1.1GHz) Sandy Bridge processor, 4 GB DDR3, 320 GB 5400 rpm Hard Drive, an 11.6-Inch screen, and Intel GMA HD graphics solution.
|
||||
|
||||
“Beyond the basics thousands of other free, open-source applications are available to meet more specific needs from image processing and 3D animation to anti-virus or accounting.”
|
||||
|
||||
“We know that effective personal computing is vital to students and Institutions, so it’s exciting for us to work with our partners to bring these low-cost, high-performance packages into the education sector,” is also stated in the announcement.
|
||||
|
||||
Canonical announcement sends to a couple of Amazon pages, but if you’re interested in these products than you should know that they are available in a number of other stores.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Canonical-and-ASUS-Have-Formed-a-Partnership-in-USA-404483.shtml
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://insights.ubuntu.com/resources/article/asus-and-ubuntu-deliver-affordable-world-class-laptops-to-usa-education/
|
||||
@ -0,0 +1,41 @@
|
||||
Daily Ubuntu Tips – Take Screenshots Of your Desktop
|
||||
================================================================================
|
||||
Ubuntu, a powerful and modern operating system allows you to perform many tasks. From creating and editing documents using LibreOffice Productivity Suite to enhancing an image with GIMP, Ubuntu is super!
|
||||
|
||||
If you need a super operating system to carry out your tasks, you may want to choose Ubuntu.
|
||||
|
||||
Another thing you can do when using Ubuntu is to take screenshots of your desktop and/or active application windows. There are many third-party tools you can install to perform such tasks, but you don’t have to, because Ubuntu comes with one already installed.
|
||||
|
||||
This program is useful if you want to show someone how do something in Ubuntu. Screenshots are just normal image files that can stored and send via email programs to others.
|
||||
|
||||
To use the screenshots program, go to Dash or press the Windows key on your keyboard to bring up Dash. The Windows key is the key left of the spacebar with Windows logo.
|
||||
|
||||
When Dash opens, search for Screenshot, select Screenshot to open it.
|
||||
|
||||
Here are some of the screen you can capture:
|
||||
|
||||
- You can grab the whole screen
|
||||
- You can grab the current program windows
|
||||
- You can select a particular area and grab it
|
||||
|
||||
If you wan to include the mouse pointer, check the box next to it and enable it.
|
||||
|
||||

|
||||
|
||||
When you want to capture a screen, click ‘**Take Screenshot**’. The program will disappear and automatically take a screenshot.
|
||||
|
||||
If you want to capture a particular area, choose that option and when you click ‘**Take Screenshot**’, the mouse pointer will change into a crosshair. You can then be drag the curser to desired size. When you stop, the image is captured automatically.
|
||||
|
||||
This is how you do it when you’re using Ubuntu
|
||||
|
||||
Hope this helps and please come back again.
|
||||
|
||||
Enjoy!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/12/daily-ubuntu-tips-take-screenshots-of-your-desktop/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
44
sources/GNOME`s File Manager Will Be More User Friendly.md
Normal file
44
sources/GNOME`s File Manager Will Be More User Friendly.md
Normal file
@ -0,0 +1,44 @@
|
||||
translating by zsJacky
|
||||
|
||||
GNOME’s File Manager Will Be More User Friendly
|
||||
================================================================================
|
||||
**Allan Day, a GNOME designer, posted a few days ago on his blog a very long article about [what’s coming next in the Nautilus (now known as Files) file manager for the GNOME desktop environment][1].**
|
||||
|
||||
What you will read in this article is a short summary of the new design features that will be implemented in upcoming releases of Nautilus, which will be part of the GNOME 3.12 desktop environment.
|
||||
|
||||
Apparently, a team of GNOME developers decided to revamp the default file manager of the controversial desktop environment, and bring some of its background functionality to the spotlight, making them obvious to new users.
|
||||
|
||||
Believe it or not, there are a lot of new users, those who are trying to discover the wonders of the Linux world, that have no idea what to do in Nautilus, how to copy, paste, rename, move or even access their files… and this is a big and embarrassing problem that needs to be fixed!
|
||||
|
||||
Therefore, future versions of the Nautilus file manager will have improved, responsive grids and lists views with big and clear thumbnails, as well as helpful zoom levels, so you can easily recognize your files. An updated View menu, with nicer controls, will also be implemented.
|
||||
|
||||
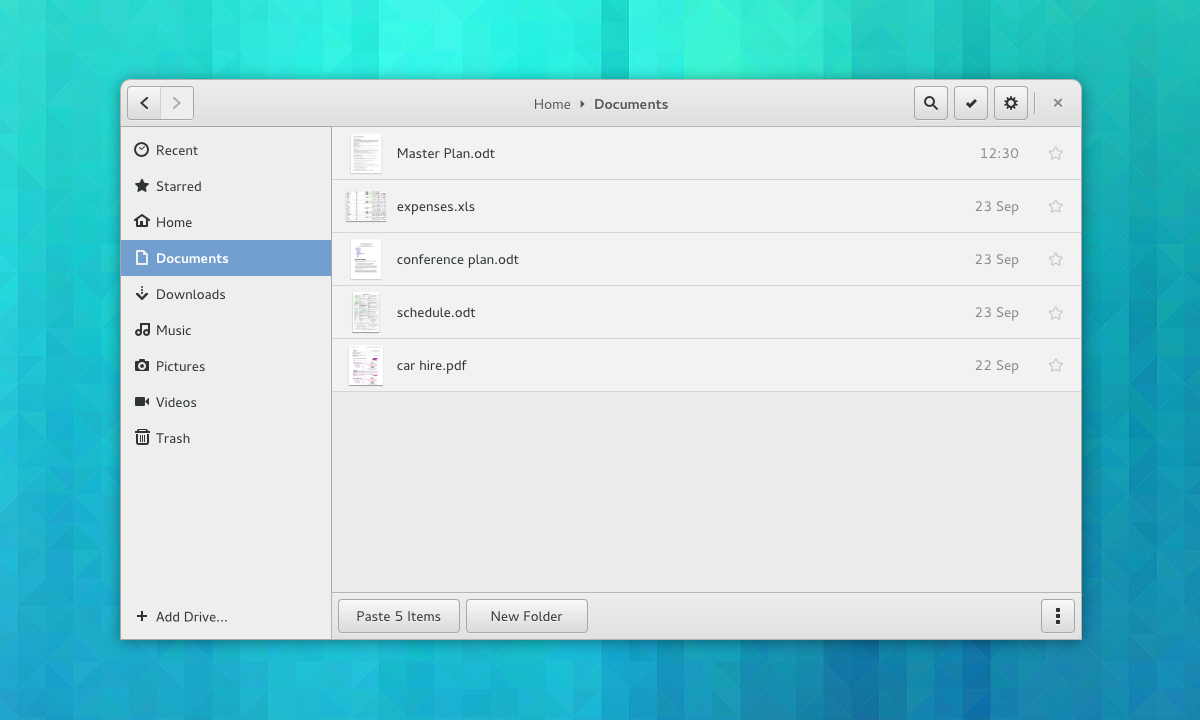
|
||||
*Nautilus list view*
|
||||
|
||||
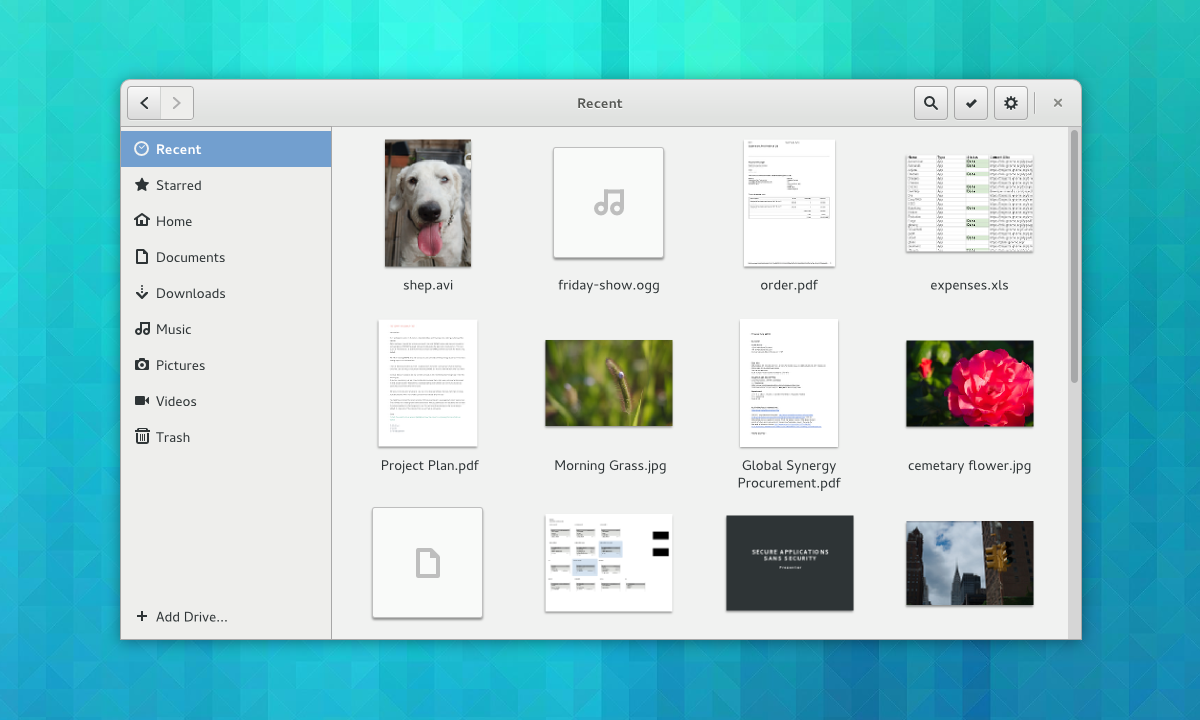
|
||||
*Nautilus grid view*
|
||||
|
||||
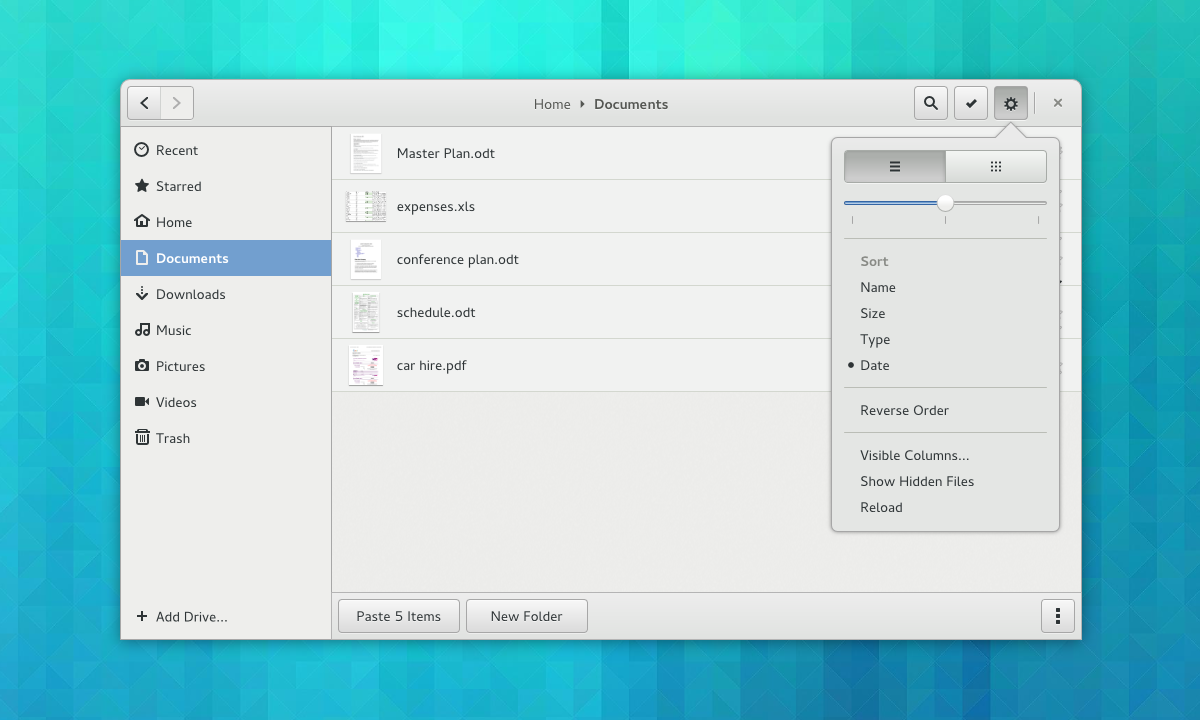
|
||||
Nautilus gear menu
|
||||
|
||||
Another important feature that will be implemented in Nautilus (Files) will be all kind of helpful buttons, such as Copy To, Move To, Create New Folder, or Open With, so it can make file operations more user friendly. Also, previewing files will be more straightforward, including a highly anticipated navigation function, so you can easily browse through multiple photos or documents
|
||||
|
||||
Moreover, the sidebar will be more customizable, allowing users to add or remove network drives, partitions or remote connections from it, making it as uncluttered as possible. A “Starred” entry will also be available for all your favorite files, along with an improved content selection function, allowing users to select items from multiple sources.
|
||||
|
||||
|
||||
*Nautilus add drive dialog*
|
||||
|
||||
|
||||
*Nautilus content selection*
|
||||
|
||||
Unfortunately, there’s no way for us to compile and test the upcoming Nautilus file manager at this moment, but we will let you know when the first development version is out. We remind everyone that Nautilus is also the default file manager for the Ubuntu Linux operating system.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/GNOME-s-File-Manager-Will-Be-More-User-Friendly-409360.shtml
|
||||
|
||||
译者:[zsJacky](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://afaikblog.wordpress.com/2013/12/11/nautilus-next/
|
||||
42
sources/GNOME’s File Manager Will Be More User Friendly.md
Normal file
42
sources/GNOME’s File Manager Will Be More User Friendly.md
Normal file
@ -0,0 +1,42 @@
|
||||
GNOME’s File Manager Will Be More User Friendly
|
||||
================================================================================
|
||||
**Allan Day, a GNOME designer, posted a few days ago on his blog a very long article about [what’s coming next in the Nautilus (now known as Files) file manager for the GNOME desktop environment][1].**
|
||||
|
||||
What you will read in this article is a short summary of the new design features that will be implemented in upcoming releases of Nautilus, which will be part of the GNOME 3.12 desktop environment.
|
||||
|
||||
Apparently, a team of GNOME developers decided to revamp the default file manager of the controversial desktop environment, and bring some of its background functionality to the spotlight, making them obvious to new users.
|
||||
|
||||
Believe it or not, there are a lot of new users, those who are trying to discover the wonders of the Linux world, that have no idea what to do in Nautilus, how to copy, paste, rename, move or even access their files… and this is a big and embarrassing problem that needs to be fixed!
|
||||
|
||||
Therefore, future versions of the Nautilus file manager will have improved, responsive grids and lists views with big and clear thumbnails, as well as helpful zoom levels, so you can easily recognize your files. An updated View menu, with nicer controls, will also be implemented.
|
||||
|
||||

|
||||
*Nautilus list view*
|
||||
|
||||

|
||||
*Nautilus grid view*
|
||||
|
||||

|
||||
Nautilus gear menu
|
||||
|
||||
Another important feature that will be implemented in Nautilus (Files) will be all kind of helpful buttons, such as Copy To, Move To, Create New Folder, or Open With, so it can make file operations more user friendly. Also, previewing files will be more straightforward, including a highly anticipated navigation function, so you can easily browse through multiple photos or documents
|
||||
|
||||
Moreover, the sidebar will be more customizable, allowing users to add or remove network drives, partitions or remote connections from it, making it as uncluttered as possible. A “Starred” entry will also be available for all your favorite files, along with an improved content selection function, allowing users to select items from multiple sources.
|
||||
|
||||

|
||||
*Nautilus add drive dialog*
|
||||
|
||||

|
||||
*Nautilus content selection*
|
||||
|
||||
Unfortunately, there’s no way for us to compile and test the upcoming Nautilus file manager at this moment, but we will let you know when the first development version is out. We remind everyone that Nautilus is also the default file manager for the Ubuntu Linux operating system.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/GNOME-s-File-Manager-Will-Be-More-User-Friendly-409360.shtml
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://afaikblog.wordpress.com/2013/12/11/nautilus-next/
|
||||
@ -1,4 +1,3 @@
|
||||
[Translating by SteveArcher]
|
||||
Gnu: toward the post-scarcity world – the Free Software Column
|
||||
================================================================================
|
||||
**It is 30 years since Richard Stallman announced that he was going to write a complete UNIX-compatible software system called GNU, pioneering the idea of free and open source software, but the struggle continues **
|
||||
|
||||
83
sources/How to Install SteamOS in VirtualBox.md
Normal file
83
sources/How to Install SteamOS in VirtualBox.md
Normal file
@ -0,0 +1,83 @@
|
||||
How to Install SteamOS in VirtualBox
|
||||
================================================================================
|
||||
**The following tutorial will teach all Linux users how to install Valve's brand new SteamOS GNU/Linux operating system in a virtual machine, using the powerful and popular VirtualBox software.**
|
||||
|
||||
As you already know, the [SteamOS Linux has been officially released on December 13][1] and is based on Debian GNU/Linux operating system, using GNOME as its (optional) desktop environment.
|
||||
|
||||
SteamOS is very easy to install if you have the right hardware components, which involves a UEFI-capable computer with a powerful video card for playing games. However, as Valve did not publish an ISO image of SteamOS, many have encountered difficulties in installing the system.
|
||||
|
||||
The following tutorial is comprised of two important sections, one that helps you create an ISO image from the SteamOSInstaller.zip file provided by Valve, and a second one where you learn how to install SteamOS in VirtualBox if you don't want to install it on a real computer.
|
||||
|
||||
To get started, you need to have a working installation of the latest VirtualBox software. Also, you need to install a software called [GNU xorriso][2], which you'll use to generate the ISO image from the SteamOSInstaller folder.
|
||||
|
||||
### Step 1 – Generate SteamOS ISO image ###
|
||||
|
||||
[Download the SteamOSInstaller.zip from Softpedia][3], save it on your home folder, and extract the files. A folder named “SteamOSInstaller” will be output. Now, open a terminal in the home folder and execute the following command:
|
||||
|
||||
xorriso -as mkisofs -r -checksum_algorithm_iso md5,sha1 -V 'Steam OS' -o ~/SteamOSInstaller.iso -J -joliet-long -cache-inodes -no-emul-boot -boot-load-size 4 -boot-info-table -eltorito-alt-boot --efi-boot boot/grub/efi.img -append_partition 2 0x01 ~/SteamOSInstaller/boot/grub/efi.img -partition_offset 16 ~/SteamOSInstaller
|
||||
|
||||
The SteamOS.iso file will be generated in a few seconds on your home folder and will have approximately 1GB in size. That's all, you can now proceed to the next step.
|
||||
|
||||
### Step 2 – Install SteamOS in VirtualBox ###
|
||||
|
||||
Considering the fact that you already have a working VirtualBox installation and that you already know how to use the software, you must create a new virtual machine with UEFI support. On VirtualBox's main window, press the New button to start the process of creating a new virtual machine.
|
||||
|
||||
In the name field type SteamOS, choose Linux as the operating system type, select Debian 64-bit from the Linux version drop-down box, and click Next to continue. Set 1024 or 2048 for the memory size (this depends on how much physical RAM your computer has), create a virtual hard drive of VDI file type and fixed size with 15GB. Click the Continue button and wait for the hard drive creation process to finish.
|
||||
|
||||
|
||||
*Create a new virtual machine*
|
||||
|
||||
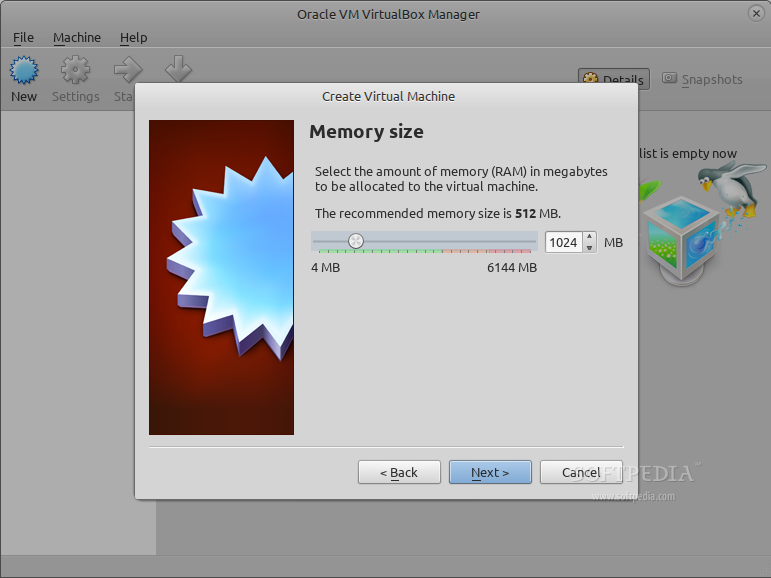
|
||||
*Set the memory size*
|
||||
|
||||
Now that the virtual machine has been created, let’s make a few adjustments for the SteamOS operating system. Go to Settings, click the System section in the sidebar, and uncheck the “Floppy” entry from the Boot Order box, and make sure you check the “Enable EFI (special OSes only)” option.
|
||||
|
||||
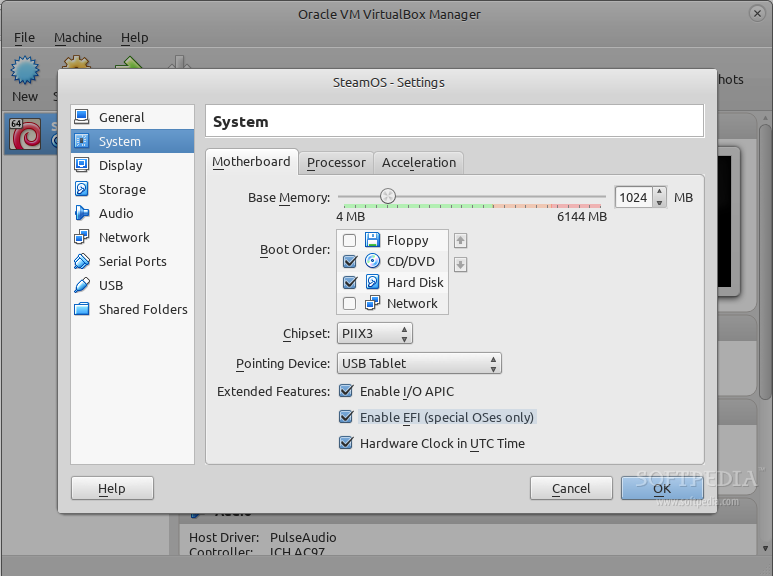
|
||||
*Enable EFI and remove Floppy*
|
||||
|
||||
Next, click the Display section in the sidebar, set the Video Memory to 128MB, and check the “Enable 3D Acceleration” option. Then, go to the Storage section in the sidebar, click the “Empty” line under “Controller: IDE” and add the SteamOSInstaller.iso image generated in the first step by clicking on the small CD icon next to the CD/DVD Drive drop-down box. Click OK when done.
|
||||
|
||||
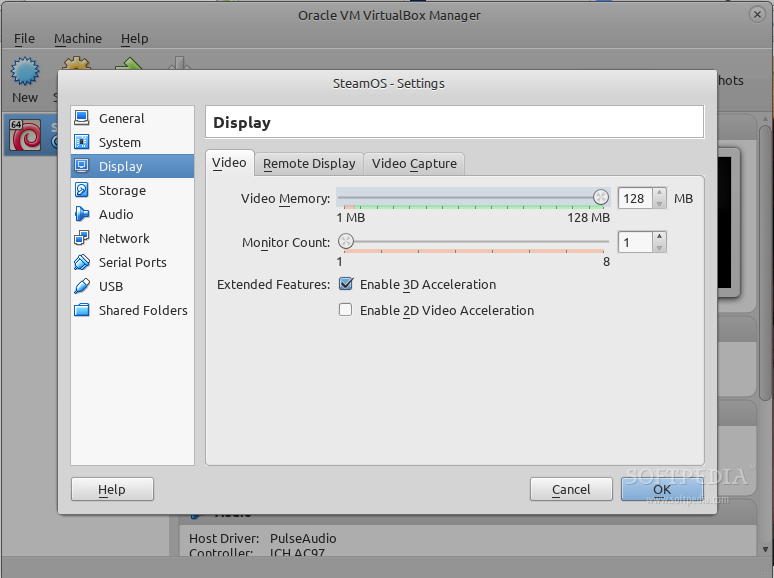
|
||||
*Set Video Memory size and 3D acceleration*
|
||||
|
||||
And now, let’s start the virtual machine by pressing the big “Start” button on the main window. You will immediately see the SteamOS boot screen. Just press Enter with the “Automated install (WILL ERASE DISK!) option highlighted, sit back, and relax until the system is installed, which will take some time, depending on your computer’s specs.
|
||||
|
||||
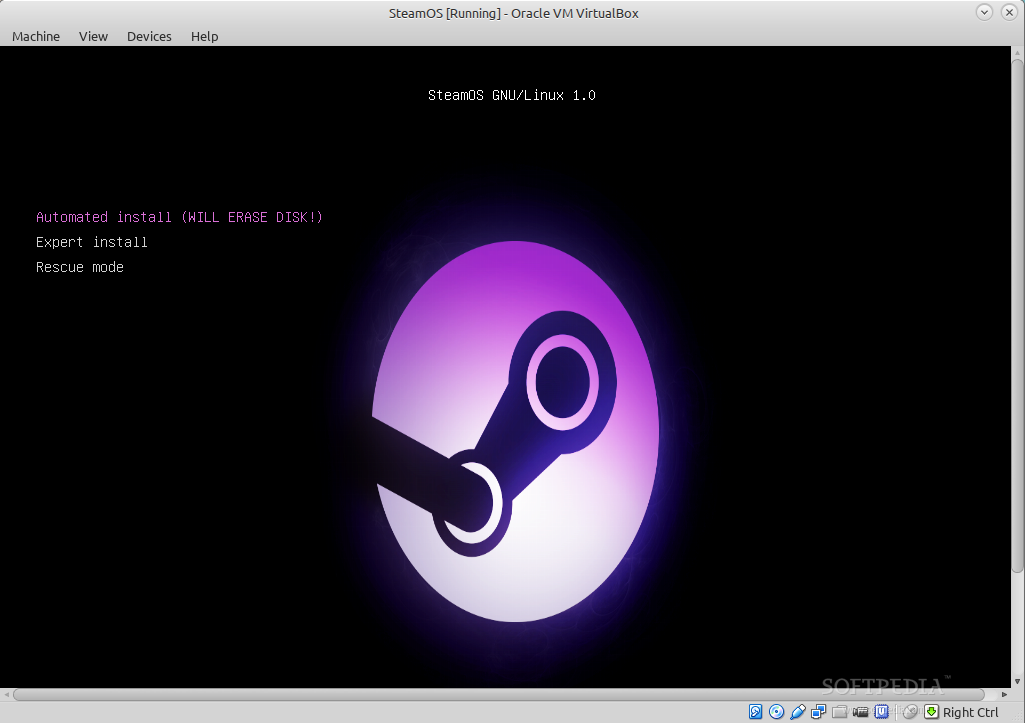
|
||||
*Prepare to install SteamOS*
|
||||
|
||||
Once the installation process is finished, you can close the virtual machine, remove the ISO image from the Storage section, and boot into your new SteamOS. But, before you start exploring SteamOS, you will need to install the VirtualBox Guest Additions. To do that, start the SteamOS virtual machine, select the second entry on the GRUB boot loader screen (Recovery), and type the following commands when you hit the SteamOS command-line prompt:
|
||||
|
||||
|
||||
|
||||
dpkg --get-selections | grep nvidia
|
||||
apt-get purge <name of the packages outputted by the above command>
|
||||
rm /usr/share/X11/xorg.conf.d/55-nvidia.conf
|
||||
dpkg-reconfigure xserver-xorg
|
||||
|
||||
Go to Devices and click on Insert Guest Additions CD image. Download the Guest Additions image when prompted, mount it and run the following command:
|
||||
|
||||
sh /media/cdrom/VBoxLinuxAdditions.run
|
||||
|
||||
Wait for the Guest Additions to install its drivers and reboot the virtual machine with the following command:
|
||||
|
||||
shutdown now -r
|
||||
|
||||

|
||||
*SteamOS command-line shell prompt*
|
||||
|
||||
The virtual machine will reboot, let it boot into the SteamOS and, when you arrive at the login prompt, use desktop/desktop or steam/steam as the username and password to login. Do not hesitate to comment below if you encounter problems during the installation.
|
||||
|
||||
|
||||
*SteamOS with GNOME 3*
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/How-to-Install-SteamOS-in-VirtualBox-409363.shtml
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://news.softpedia.com/news/Download-SteamOS-1-0-Based-on-Debian-Linux-409214.shtml
|
||||
[2]:http://linux.softpedia.com/get/Programming/Libraries/GNU-xorriso-36759.shtml
|
||||
[3]:http://linux.softpedia.com/get/System/Operating-Systems/Linux-Distributions/SteamOS-103040.shtml
|
||||
@ -1,3 +1,4 @@
|
||||
(translating by runningwater)
|
||||
How to Install and Configure UFW – An Un-complicated FireWall in Debian/Ubuntu
|
||||
================================================================================
|
||||
Since computers are connected to each other, services are growing fast. **Email, Social Media, Online Shop, Chat** until **Web Conferencing** are services that used by user. But on the other side this connectivity just likes a double-side knife. It’s also possible to send bad messages to those computers like **Virus, malware, trojan-apps** are one of them.
|
||||
@ -266,7 +267,7 @@ As I stated above, the ufw firewall can able to do whatever that iptables can do
|
||||
|
||||
via: http://www.tecmint.com/how-to-install-and-configure-ufw-firewall/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[runningwater](https://github.com/runningwater) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
|
||||
@ -1,99 +0,0 @@
|
||||
How to Upgrade to GNOME 3.10 in Ubuntu 13.10
|
||||
================================================================================
|
||||
|
||||
|
||||
**Ubuntu 13.10 ships with the GNOME 3.8 desktop available in its archives. While a dependable, stable and featured alternative to Unity, it’s also outdated.**
|
||||
|
||||
The newer version of the GNOME desktop was released back in September 2013 and comes with a raft of improved features, apps and usability tweaks. From hi-res screen support to new client-side decoration of app windows, GNOME 3.10 is a compelling upgrade.
|
||||
|
||||
The good news is that – providing you’re running Ubuntu 13.10, have a decent internet connection, and some command line aptitude (pun fully intended) – you don’t have to stick with a stale version of GNOME.
|
||||
|
||||
### How To Upgrade to GNOME 3.10 in Ubuntu 13.10 ###
|
||||
|
||||
For the benefit of the skim readers whose eyes dropped straight to the point I’ll reiterate: you **need to be running Ubuntu 13.10 to install GNOME 3.10**.
|
||||
|
||||
First, let’s add the GNOME 3 PPA to Ubuntu’s Software Sources. This can be done using a GUI but it is far easier to achieve using the command line.
|
||||
|
||||
Open a new *Terminal* window and enter the following command, entering your user password when asked:
|
||||
|
||||
sudo add-apt-repository ppa:gnome3-team/gnome3-next && sudo apt-get update
|
||||
|
||||
With the PPA added and our package list updated we can move on to installing GNOME 3.10 itself. To do this run the following command, again entering your user password when prompted:
|
||||
|
||||
sudo apt-get update && sudo apt-get install gnome-shell ubuntu-gnome-desktop
|
||||
|
||||
It can take a while for all the necessary packages and components to be fetched and installed, so try to be patient.
|
||||
|
||||
Midway through the installation a prompt will appear in the Terminal asking you to choose what display manager – aka “login screen” – should be used by default.
|
||||
|
||||
This decision is entirely up to you; both Ubuntu’s Unity Greeter and the **GNOME Display Manager** let you easily switch between desktop sessions (handy if you want to keep Unity or another desktop around) but only GDM offers GNOME-specific features such as lock-screen notifications.
|
||||
|
||||
When you’re ready to decide make your selection using the up/down arrow keys and hit ‘Enter/Return’ to confirm. The installation will then proceed.
|
||||
|
||||
### Adding The Extra Stuff ###
|
||||
|
||||
|
||||
|
||||
GNOME 3.10 comes with some great new features, applications – [including GNOME Weather, Music and Maps][1] – and other miscellaneous changes. Because not all of these are considered ‘stable’ enough to be included in the main GNOME 3 PPA we added earlier, you’ll need to make use of an additional pair of GNOME PPAs if you want to use them.
|
||||
|
||||
Now – and it’s important you’re aware of this – some of the packages in these repositories are reported to have stability issues. Most of these will be minor – i.e., the odd app crash or broken feature – but the potential for more major issues, like making GNOME crash entirely, is possible.
|
||||
|
||||
Warning out of the way, open up a new tab in a Terminal and punch in the following:
|
||||
|
||||
sudo add-apt-repository ppa:gnome3-team/gnome3-staging
|
||||
sudo add-apt-repository ppa:gnome3-team/gnome3
|
||||
sudo apt-get update && sudo apt-get dist-upgrade
|
||||
|
||||
To add some of the cool apps we mentioned earlier run:
|
||||
|
||||
sudo apt-get install gnome-weather gnome-music gnome-maps cheese gnome-documents
|
||||
|
||||
With that we’re done!
|
||||
|
||||
You may wish to log out and back in (remembering to select the ‘GNOME’ session) to ensure that everything takes effect correctly.
|
||||
|
||||
### Minor Differences ###
|
||||
|
||||
If you’ve kept Unity installed alongside GNOME 3.10 then there are a few things you’ll need to note down.
|
||||
|
||||
First off, you’ll find **two entries for ‘Online Accounts’ in System Settings**. The one with the key-themed icon is the Unity version, and the one with the plug emblem is GNOME’s.
|
||||
|
||||
Some apps will require you to add accounts to the Unity version (Shotwell, Gwibber, Empathy) and some to the GNOME one (Evolution, Documents, Contacts).
|
||||
|
||||

|
||||
|
||||
The ‘Notifications’ and ‘Search’ entries are GNOME-specific, both letting you pick and choose which applications and sources are able to show notifications or appear in the Activities Overlay.
|
||||
|
||||
### Uninstalling GNOME 3.10 ###
|
||||
|
||||
So you’ve tried it and didn’t like it. Now what?
|
||||
|
||||
Removing GNOME 3.10 is a fairly straightforward processing providing we use a command-line tool called ‘PPA Purge’. It can be found in the Ubuntu Software Center and is by far the easiest way to automatically remove and/or downgrade packages installed from PPAs.
|
||||
|
||||
- [Install PPA Purge from Ubuntu Software Center][2]
|
||||
|
||||
To use the tool we’ll need to go back to the terminal and enter the following, taking care to look out for any prompts that may appear during the downgrade process.
|
||||
|
||||
sudo ppa-purge ppa:gnome3-team/gnome3-next
|
||||
|
||||
If you also added the optional extra PPAs you will also need to purge those as well:
|
||||
|
||||
sudo ppa-purge ppa:gnome3-team/gnome3-staging
|
||||
sudo ppa-purge ppa:gnome3-team/gnome3
|
||||
|
||||
Once completed you should be left with the stock GNOME 3.8 desktop. If you don’t want to keep GNOME Shell around at all you can proceed to remove it:
|
||||
|
||||
sudo apt-get remove gnome-shell ubuntu-gnome-desktop
|
||||
|
||||
Finally, manually remove any remaining applications that persist after downgrade (e.g., Epiphany and GNOME Documents), then reboot.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2013/12/upgrade-gnome-3-10-ubuntu-13-10
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.omgubuntu.co.uk/2013/09/gnome-3-10-released-with-new-apps-experimental-wayland-support
|
||||
[2]:apt:ppa-purge
|
||||
@ -1,4 +1,3 @@
|
||||
Translating by icybreaker
|
||||
How to install and configure Nagios on Linux
|
||||
================================================================================
|
||||
[Nagios][1] is one of the most powerful network monitoring systems, which is widely used in the industry. It can actively monitor any network, and generate audio/email warnings and alerts when any problem is detected. The check types and alert timers are fully customizable.
|
||||
|
||||
118
sources/How to open a large text file on Linux.md
Normal file
118
sources/How to open a large text file on Linux.md
Normal file
@ -0,0 +1,118 @@
|
||||
How to open a large text file on Linux
|
||||
================================================================================
|
||||
In the era of "big data", large text files (GB or more) could be commonly encountered around us. Suppose you somehow need to search and edit one of those big text files by hand. Or you could be analyzing multi-GB log files manually for specific troubleshooting purposes. A typical text editor may not be designed to deal with such large text files efficiently, and may simply get choked while attempting to open a big file, due to insufficient memory.
|
||||
|
||||
If you are a savvy system admin, you can probably open or touch an arbitrary text file with a combination of cat, tail, grep, sed, awk, etc. In this tutorial, I will discuss more user-friendly ways to **open (and possibly edit) a large text file on Linux**.
|
||||
|
||||
### Vim with LargeFile Plugin ###
|
||||
|
||||
Vim text editor boasts of various plugins (or scripts) which can extend Vim's functionality. One such Vim plugin is [LargeFile plugin][1].
|
||||
|
||||
The LargeFile plugin allows you to load and edit large files more quickly, by turning off several Vim features such as events, undo, syntax highlighting, etc.
|
||||
|
||||
To install the LargeFile plugin on Vim, first make sure that you have Vim installed.
|
||||
|
||||
On Debian, Ubuntu or Linux Mint:
|
||||
|
||||
$ sudo apt-get install vim
|
||||
|
||||
On Fedora, CentOS or RHEL:
|
||||
|
||||
$ sudo yum install vim-enhanced
|
||||
|
||||
Then download the LargFile plugin from [Vim website][2]. The latest version of the plugin is 5, and it will be saved in Vimball format (.vba extension).
|
||||
|
||||
To install the plugin in your home directory, you can open the .vba file with Vim as follows.
|
||||
|
||||
$ gunzip LargeFile.vba.gz
|
||||
$ vim LargeFile.vba
|
||||
|
||||
Enter ":so %" and press ENTER within Vim window to install the plugin in your home directory.
|
||||
|
||||
[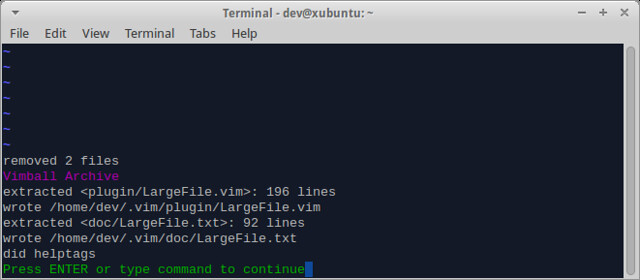][3]
|
||||
|
||||
After this, enter ":q" to quit Vim.
|
||||
|
||||
The plugin will be installed at ~/.vim/plugin/LargeFile.vim. Now you can start using Vim as usual.
|
||||
|
||||
What this plugin does is to turn off events, undo, syntax highlighting, etc. when a "large" file is loaded on Vim. By default, files bigger than 100MB are considered "large" by the plugin. To change this setting, you can edit ~/.vimrc file (create one if it does not exist).
|
||||
|
||||
To change the minimum size of large files to 10MB, add the following entry to ~/.vimrc.
|
||||
|
||||
> let g:LargeFile=10
|
||||
|
||||
While the LargeFile plugin can help you speed up file loading, Vim itself still cannot handle editing an extremely large file very well, because it tries to load the entire file in memory. For example, when a 1GB file is loaded on Vim, it takes as much memory and swap space, as shown in the top output below.
|
||||
|
||||
So if your files are significantly bigger than the physical memory of your Linux system, you can consider other options, as explained below.
|
||||
|
||||
### glogg Log Explorer ###
|
||||
|
||||
If all you need is "read-only" access to a text file, and you don't have to edit it, you can consider [glogg][4], which is a GUI-based standalone log analyzer. The glogg analyzer supports filtered views of an input text file, based on extended regular expressions and wildcards.
|
||||
|
||||
To install glogg on Debian (Wheezy and higher), Ubuntu or Linux Mint:
|
||||
|
||||
$ sudo apt-get install glogg
|
||||
|
||||
To install glogg on Fedora (17 or higher):
|
||||
|
||||
$ sudo yum install glogg
|
||||
|
||||
To open a text file with glogg:
|
||||
|
||||
$ glogg test.log
|
||||
|
||||
glogg can open a large text file pretty fast. It took me around 12 seconds to open a 1GB log file.
|
||||
|
||||
[][5]
|
||||
|
||||
You can enter a regular expression in the "Text" field, and press "Search" button. It supports case-insensitive search and auto-refresh features. After searching, you will see a filtered view at the bottom window.
|
||||
|
||||
Compared to Vim, glogg is much more lightweight after a file is loaded. It was using only 83MB of physical memory after loading a 1GB log file.
|
||||
|
||||
[][6]
|
||||
|
||||
### JOE Text Editor ###
|
||||
|
||||
[JOE][7] is a light-weight terminal based text editor released under GPL. JOE is one of few text editors with large file support, allows opening and editing files larger than memory.
|
||||
|
||||
Besides, JOE supports various powerful text editing features, such as non-destructive editing, search and replace with regular expression, unlimited undo/redo, syntax highlighting, etc.
|
||||
|
||||
To install JOE on Debian, Ubuntu or Linux Mint:
|
||||
|
||||
$ sudo apt-get install joe
|
||||
|
||||
To install JOE on Fedora, CentOS or RHEL:
|
||||
|
||||
$ sudo yum install joe
|
||||
|
||||
To open a text file for editing, run:
|
||||
|
||||
$ joe test.log
|
||||
|
||||
[][8]
|
||||
|
||||
Loading a large file on JOE is a little bit sluggish, compared to glogg above. It took around 30 seconds to load a 1GB file. Still, that's not too bad, considering that a file is fully editable now. Once a file is loaded, you can start editing a file in terminal mode, which is quite fast.
|
||||
|
||||
The memory consumption of JOE is impressive. To load and edit a 1GB text file, it only takes 47MB of physical memory.
|
||||
|
||||
[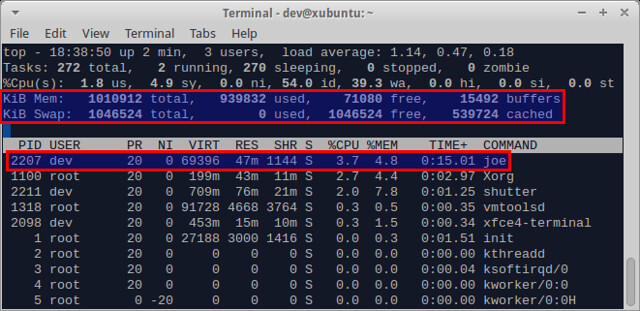][9]
|
||||
|
||||
If you know any other way to open/edit a large text file on Linux, share your knowledge!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2013/12/open-large-text-file-linux.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.vim.org/scripts/script.php?script_id=1506
|
||||
[2]:http://www.vim.org/scripts/script.php?script_id=1506
|
||||
[3]:http://www.flickr.com/photos/xmodulo/11313669824/
|
||||
[4]:http://glogg.bonnefon.org/
|
||||
[5]:http://www.flickr.com/photos/xmodulo/11313640286/
|
||||
[6]:http://www.flickr.com/photos/xmodulo/11313594455/
|
||||
[7]:http://joe-editor.sourceforge.net/
|
||||
[8]:http://www.flickr.com/photos/xmodulo/11317402126/
|
||||
[9]:http://www.flickr.com/photos/xmodulo/11317483233/
|
||||
@ -1,45 +0,0 @@
|
||||
Linux Mint Respond to Ubuntu Developer’s ‘Vulnerable’ Claim
|
||||
================================================================================
|
||||
**It’s never a particularly tasty task having to write a news article on something that you know is going to cause headache and upset in the wider community.**
|
||||
|
||||
Earlier today I had to grin and bear it as I did just that in an article relaying comments made by Canonical engineer Oliver Grawert in which he branded Linux Mint a “‘vulnerable’ system” due to the way the distro provides security updates to users.
|
||||
|
||||
*Tl;dr: they don’t. (At least, not automatically.)*
|
||||
|
||||
A Canonical developer highlighting security concerns with another distro might sound like pure click bait on paper, but in practice it has important ramifications for users. Security is important, even on a platform that most perceive as invincible.
|
||||
|
||||
> ‘To put my own Top Trumps cards on the table, I was unaware that Mint held back security updates…’
|
||||
|
||||
Whether you agreed with Oliver’s take on Mint’s approach or not, **his comments were worth relaying**. These weren’t made by someone with an axe to grind.. They were informed by his esteemed position as an Ubuntu engineer. He knows what he’s talking about. Whether correct or misplaced, his comments have resulted in positive discussions about how security update practices should be handled.
|
||||
|
||||
To put my own Top *Trump™* cards on the table, I was unaware that Mint held back security updates for packages like Xorg and the Linux Kernel. So, at the very least, this mini-furore – borne largely out of knee-jerk reaction to the comments rather than their content in intent – has served a purpose.
|
||||
|
||||
### Mint Respond ###
|
||||
|
||||
Linux Mint head-honco Clement Lefebvre has since responded to the remarks, saying that he and his team of developers are “very happy with the filtering system” for security updates in Mint.
|
||||
|
||||
> ” We explained why the Ubuntu update policy was not good enough for us and we consequently developed the update manager to solve that particular problem.
|
||||
>
|
||||
> Firefox doesn’t come to you later in Mint than it does in Ubuntu (it’s a level 2 update).
|
||||
>
|
||||
> Yes, by default you get updates in Ubuntu for kernels and Xorg and not in Mint. Yes, there’s a very good reason for that.”
|
||||
|
||||
While Lefebvre doesn’t expand on precisely what that “very good reason” is, the general consensus on the web seems to be that Kernel and Xorg updates are held back because of the stability and performance issues that sometimes arise after upgrading.
|
||||
|
||||
Which, in many ways, is understandable.
|
||||
|
||||
Linux Mint don’t prevent their users from installing these updates but they are not enabled by default.
|
||||
|
||||
For further information on Linux Mint’s approach to security refer to the following blog post.
|
||||
|
||||
- [Linux Mint – Security Vs Stability][1]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2013/11/linux-mint-responds-ubuntu-developers-security-claims
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://segfault.linuxmint.com/2013/11/answering-controversy-stability-vs-security-is-something-you-configure/
|
||||
@ -0,0 +1,112 @@
|
||||
Linux mpstat Command – Reports Processors Related Statistics
|
||||
================================================================================
|
||||
Generally today computer is using multiple processors. Or maybe 1 physical processor with 4 cores inside. On server side, more processors or cores means more power. But the other side, application also more power consumption. You may find a situation when your cpu utilization is high but you feel that you don’t running anything. On Linux system, you can monitor this activity using **mpstat**.
|
||||
|
||||

|
||||
|
||||
### What is mpstat ###
|
||||
|
||||
**mpstat** is used to monitor cpu utilization on your system. It will be more usefull if your system has multiple processors. The first processors will signed as CPU 0. The second one will be signed CPU 1 and so on. From its manual page, mpstat is described as :
|
||||
|
||||
> The mpstat command writes to standard output activities for each available processor, processor 0 being the first one. Global average activities among all processors are also reported. The mpstat command can be used both on SMP and UP machines, but in the latter, only global average activities will be printed. If no activity has been selected, then the default report is the CPU utilization report
|
||||
|
||||
### How to run mpstat ###
|
||||
|
||||
Just type **mpstat** on your console to run mpstat.
|
||||
|
||||
$ mpstat
|
||||
|
||||
Linux 3.2.0-57-generic (USERNB01) 12/12/2013 _x86_64_ (2 CPU)
|
||||
|
||||
03:29:29 PM CPU %usr %nice %sys %iowait %irq %soft %steal %guest %idle
|
||||
03:29:29 PM all 6.30 0.06 1.94 3.75 0.00 0.06 0.00 0.00 87.88
|
||||
|
||||
If you found an error such as : **command not found** or similar you may not install mpstat in your system.
|
||||
|
||||
If you are using **CentOS, RedHat or Fedora**, run this command to install mpstat
|
||||
|
||||
# yum install sysstat
|
||||
|
||||
If you are using **Debian, Ubuntu or its derivative**, run this command to install mpstat
|
||||
|
||||
# apt-get install sysstat
|
||||
|
||||
And here’s how to read the information above.
|
||||
|
||||
- **03:29:29 PM** : means the time that mpstat was run
|
||||
- **all** : means All CPUs
|
||||
- **%usr** : show the percentage of CPU utilization that occurred while executing at the user level (application)
|
||||
- **%nice** : show the percentage of CPU utilization that occurred while executing at the user level with nice priority
|
||||
- **%sys** : show the percentage of CPU utilization that occurred while executing at the system level (kernel)
|
||||
- **%iowait** : show the percentage of time that the CPU or CPUs were idle during which the system had an outstanding disk I/O request
|
||||
- **%irq** : show the percentage of time spent by the CPU or CPUs to service hardware interrupts
|
||||
- **%soft** : show the percentage of time spent by the CPU or CPUs to service software interrupts
|
||||
- **%steal** : show the percentage of time spent in involuntary wait by the virtual CPU or CPUs while the hypervisor was servicing another virtual processor
|
||||
- **%guest** : show the percentage of time spent by the CPU or CPUs to run a virtual processor
|
||||
- **%idle** : show the percentage of time that the CPU or CPUs were idle and the system did not have an outstanding disk I/O equest
|
||||
|
||||
### Print CPU utilization per processors ###
|
||||
|
||||
As you can see above, our system has 2 CPUs. If you want, you can use -P parameter followed by CPU number to see specific CPU utilization.
|
||||
|
||||
$ mpstat -P 0
|
||||
|
||||
Linux 3.2.0-57-generic (USERNB01) 12/12/2013 _x86_64_ (2 CPU)
|
||||
|
||||
03:54:00 PM CPU %usr %nice %sys %iowait %irq %soft %steal %guest %idle
|
||||
03:54:00 PM 0 3.82 0.01 1.16 3.88 0.00 0.06 0.00 0.00 91.06
|
||||
|
||||
$ mpstat -P 1
|
||||
Linux 3.2.0-57-generic (USERNB01) 12/12/2013 _x86_64_ (2 CPU)
|
||||
|
||||
03:53:58 PM CPU %usr %nice %sys %iowait %irq %soft %steal %guest %idle
|
||||
03:53:58 PM 1 16.52 0.20 4.48 0.46 0.00 0.04 0.00 0.00 78.30
|
||||
|
||||
### Print all CPU Utilization ###
|
||||
|
||||
You can also print every CPU utilization of processors in a single page. Just use **-P ALL** parameter to do it
|
||||
|
||||
$ mpstat -P ALL
|
||||
|
||||
Linux 3.2.0-57-generic (USERNB01) 12/12/2013 _x86_64_ (2 CPU)
|
||||
|
||||
04:07:36 PM CPU %usr %nice %sys %iowait %irq %soft %steal %guest %idle
|
||||
04:07:36 PM all 6.02 0.04 1.72 2.99 0.00 0.05 0.00 0.00 89.17
|
||||
04:07:36 PM 0 3.84 0.01 1.15 3.72 0.00 0.06 0.00 0.00 91.21
|
||||
04:07:36 PM 1 13.55 0.15 3.66 0.46 0.00 0.03 0.00 0.00 82.15
|
||||
|
||||
### Print CPU utilization using intervals ###
|
||||
|
||||
You may want to see the CPU utilization movement. To do this, you can use intervals. Here’s an example.
|
||||
|
||||
$ mpstat 3 4
|
||||
|
||||
Linux 3.2.0-57-generic (USERNB01) 12/12/2013 _x86_64_ (2 CPU)
|
||||
|
||||
04:27:11 PM CPU %usr %nice %sys %iowait %irq %soft %steal %guest %idle
|
||||
04:27:14 PM all 0.67 0.00 0.34 0.00 0.00 0.00 0.00 0.00 98.99
|
||||
04:27:17 PM all 1.17 0.00 0.33 1.33 0.00 0.00 0.00 0.00 97.17
|
||||
04:27:20 PM all 0.84 0.00 0.17 0.00 0.00 0.00 0.00 0.00 98.99
|
||||
04:27:23 PM all 1.00 0.00 0.17 1.51 0.00 0.00 0.00 0.00 97.32
|
||||
Average: all 0.92 0.00 0.25 0.71 0.00 0.00 0.00 0.00 98.12
|
||||
|
||||
The above command is to show you **4 reports** about CPU utilization with **3 seconds intervals**
|
||||
|
||||
### Print mpstat version ###
|
||||
|
||||
Finally, to print mstat version, use -V parameter
|
||||
|
||||
$ mpstat -V
|
||||
|
||||
sysstat version 10.0.3
|
||||
(C) Sebastien Godard (sysstat orange.
|
||||
|
||||
That’s a quick usage of mpstat command in Linux system. You may see msptat manual page by typing **man mpstat** to explore more detail.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/linux-mpstat-command/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,33 @@
|
||||
New Ubuntu 14.04 Icons Are Drop-Dead Gorgeous, Might Not Arrive in Desktop Version
|
||||
================================================================================
|
||||
**Canonical is preparing a facelift for the Ubuntu 14.04 LTS and the new icons that are being designed right now surpass anything that's been done before.**
|
||||
|
||||
During the last UDS (Ubuntu developer summit), James Mathieu, a designer who has been working fervently on a new look for Ubuntu, presented a set of icons that were simply beautiful, for lack of a better word. Now he is showing us in much greater detail the work he has been doing.
|
||||
|
||||
“This project’s main goal is to create a single modern, high-resolution icon theme for desktop and touch devices that can adapt to various screen densities and reinforces the Ubuntu user experience. We want our icons to express our values and convey Ubuntu’s personality in a unique way.”
|
||||
|
||||
“We already had mobile icons for the applications and symbols, but, because they evolved over time without strong guidelines, did not form a consistent set. On the desktop, even though the style is clean and consistent, the icons looked dated and needed to be replaced too,” said James Mathieu in a post on the official Ubuntu website.
|
||||
|
||||
Canonical's goal right now is to update the old icons for all the platforms which now include phone and tablet, and get them up to today's standards, without losing their identity. Users must be able to identify an Ubuntu system just by looking at the icons and nothing more.
|
||||
|
||||
The old set that has been used so far doesn't look half-bad, but the ones that have been presented so far are drop-dead gorgeous.
|
||||
|
||||
“We’ve been working on this on-going project for the past year. We’ve done extensive research on the subject with a focus on learning how best to classify the icons; and we’ve gone through several design iterations and explorations,” [also][1] said Mathieu in his post.
|
||||
|
||||
These are not the final versions of the icons and the design might change. There’s also a chance that the new icons might not be ready in time for the desktop version, but we can only hope.
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/New-Ubuntu-14-04-Icons-Are-Drop-dead-Gorgeous-Might-Not-Arrive-in-Desktop-Version-410435.shtml
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://design.canonical.com/2013/12/the-new-ubuntu-icons/
|
||||
@ -1,61 +0,0 @@
|
||||
Open Source Is Here To Stay On IBM i
|
||||
================================================================================
|
||||
For years, open source software has been a bit of a redheaded stepchild in the button-down IBM midrange community. IBM i shops were hesitant to use it, and vendors were afraid to adopt it. But with so much of the computing world now running on open source, the aversion to open source has gradually melted away, and it has steadily crept into use among large corporations, and the IBM i world too.
|
||||
|
||||
It is tough to measure the adoption of open source software, which flows freely across networks by its very nature. Nobody requires you to register to use open source software, and there's no central clearinghouse of information about open source software.
|
||||
|
||||
However, recent surveys and audits point to greater adoption of open source across all industries. Open source software components are widely used in in the financial services industry, according to Julian Brook, associate director at SQS Software, which conducts software quality audits for financial software vendors. "I would say that, arguably, open source is used in every organization that is developing software, especially in the financial services world," Brook [told Out-Law.com recently][1].
|
||||
|
||||
Governmental agencies lead the way in use of open source software, according to [Black Duck Software][2]'s 2013 Future of Open Source survey. More than 35 percent of government representatives queried for the survey say they use open source, followed by medical (15.2 percent), media (13 percent), financial (8.8 percent), and retail (5.9 percent). You can view more of the survey at [Slideshare][3].
|
||||
|
||||
Increasingly, users are adopting open source software because they expect higher software quality and security with open source, according to surveys like those from Black Duck. That's very interesting, because for many years, open source software was largely avoided for those two very reasons.
|
||||
|
||||
These are opinion surveys, mind you. They're not necessarily reflections of actual reality. But it is clear than many of the shortcomings that people previously associated with open source software products are disappearing. And slowly but surely, this trend is bleeding over into the competitive world of IBM i software, too.
|
||||
|
||||
### Open Source Impacts On IBM i ###
|
||||
|
||||
The IBM i server is one of the last great bastions of proprietary technology in a world heading in the direction of open source. IBM does not share with the world the guts of the IBM i OS and the System Licensed Internal Code (SLIC) it runs on. You can take what access IBM provides developers to the machine, or you can leave it, but you can't get access to the internals.
|
||||
|
||||
What goes on above the OS and SLIC layers is another matter entirely. We're not seeing a big influx of open source software in the world of ERP and business applications. But in many other software categories, open source options are proliferating.
|
||||
|
||||
One IBM i proponent of open source software is [Raz-Lee][4]. The security software vendor, which relies on the open source [ClamAV][5] offering to power its IBM i-based anti-virus offering, called iSecurity Anti-Virus, says ClamAV had an update for an evolving security threat--the W32/Autorun.worm.aaeh Trojan Horse--months before its competitor had updated the signature library for its IBM i-based antivirus offering.
|
||||
|
||||
"It turns out that ClamAV has been handling this threat . . . as of about eight to nine months ago," Raz-Lee vice president of business development Eli Spitz wrote in an email to IT Jungle last month. "In fact, one of our technicians here at Raz-Lee actually added his own unofficial signature to ClamAV's database before ClamAV included their formal signature for this virus."
|
||||
|
||||
Another IBM i software vendor using open source tools is [Arpeggio Software][6] . The Atlanta, Georgia-based company uses lots of open source components in its various IBM i utilities, which aren't available under an open source license, but which Arpeggio gives away and then charges customers to get technical support, a common approach taken by commercial open source vendors.
|
||||
|
||||
Arpeggio's latest offering, called ARP-DROP, uses the open source OAuth authentication method to help secure communication channels between IBM i servers and [DropBox][7] service running on the Internet. It also uses the OpenSSH encryption technology with ARP-SFTP client for IBM i. Arpeggio's founders (who also founded Trailblazer Systems, now part of [Liaison Technologies][8]) acknowledge that IBM i professionals could adopt the same open source tools to write similar tools. But they argue that Arpeggio does it better, so why not adopt their free tools and save yourself the time?
|
||||
|
||||
In many cases, an IBM i shop's first conscious exposure to open source is the server side scripting language PHP. IBM and [Zend Technology][9] have worked for years to make PHP run well on IBM i, and Zend's entry-level PHP runtime is shipped along with every Power Systems server and IBM i license.
|
||||
|
||||
One of the most popular PHP applications that run on IBM i servers is [SugarCRM][10]. Representatives with the Cupertino, California, company recently said that it has nearly 1,000 customers running the CRM software on IBM i servers. This includes paid enterprise licenses along with free community edition licenses.
|
||||
|
||||
### Fighting Perceptions ###
|
||||
|
||||
Most IBM i shops are big users of IBM i software, whether they know it or not. Some of the biggest, most important IT infrastructure components come from open source, including the Apache Web server, the Linux OS, the Java and PHP programming languages, the MySQL database, and the Eclipse development environment.
|
||||
|
||||
There's no reason not to call open source "commercial grade" anymore, Raz-Lee's Spitz said. "A few weeks ago Sourcefire, the owners of ClamAV, was purchased by [Cisco Systems][11]. That's obviously a 'certification' by a large commercial organization for open source software. So open source anti-virus software seems to be valuable to a multi-national company."
|
||||
|
||||
While open source software is making inroads in the IBM i community, it still has a ways to go to match the momentum that open source enjoys in the IT market as a whole. "It seems that the IBM i community is often less involved with open source and is not exposed to its importance and prevalence in the current computing area," Spitz said. "In many cases, open source is the 'playground' of very large companies who join to create a better arena for us all."
|
||||
|
||||
As the corporations of the world gradually becomes amenable to open source, the IBM i community will have no choice but to follow.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.itjungle.com/tfh/tfh120213-story01.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.out-law.com/en/articles/2013/september/open-source-code-use-within-financial-services-organisations-visibility-only-50-at-best-says-software-quality-expert/
|
||||
[2]:http://www.blackducksoftware.com/
|
||||
[3]:http://www.slideshare.net/blackducksoftware/the-2013-future-of-open-source-survey-results
|
||||
[4]:http://www.razlee.com/
|
||||
[5]:http://www.clamav.net/
|
||||
[6]:http://www.arpeggiosoftware.com/
|
||||
[7]:http://www.dropbox.com/
|
||||
[8]:http://www.liaison.com/
|
||||
[9]:http://www.zend.com/
|
||||
[10]:http://www.sugarcrm.com/
|
||||
[11]:http://www.cisco.com/
|
||||
@ -1,31 +0,0 @@
|
||||
Oracle Linux 6.5 Arrives with Unbreakable Enterprise Linux Kernel 3.8
|
||||
================================================================================
|
||||
**Oracle has announced a few days ago that its Oracle Linux operating system has reached version 6.5, bringing lots of new features, updated packages and several improvements over previus releases.**
|
||||
|
||||

|
||||
|
||||
First of all, we should mention that Oracle Linux 6.5 is now powered by three separate kernels, the unbreakable enterprise kernel version 2.6.39-400.211.1.el6uek only for the x86 (32-bit) platform, the unbreakable enterprise kernel version 3.8.13-16.2.1.el6uek for both 64-bit and 32-bit architectures, and the Red Hat compatible kernel 2.6.32-431.el6 for x86 and x86_64.
|
||||
|
||||
Unbreakable Enterprise Kernel Release 3 (UEK R3) introduces major improvements over UEK R2, including integrated DTrace support, device mapper support, Btrfs quota groups, Btrfs send and receive subcommands, support for replacing devices without unmounting in Btrfs, EXT4 quotas, TCP controlled delay management, TCP connection repair, STCP and TCP early retransmit, TCP fast open, and TCP small queue algorithm.
|
||||
|
||||
The loop driver has been update to provide the same I/O functionality as the dm-nfs project, simply by extending the AIO interface to perform direct I/O. Moreover, the secure computing mode feature has been added, and the OpenFabrics Enterprise Distribution (OFED) 2.0 stack supports the following protocols: SRP (SCSI RDMA Protocol), iSER (iSCSI Extensions), RDS (Reliable Datagram Sockets), SDP (Sockets Direct Protocol), EoIB (Ethernet over InfiniBand), IPoIB (IP encapsulation over InfiniBand), and eIPoIB (Ethernet tunneling over InfiniBand).
|
||||
|
||||
The OFED (OpenFabrics Enterprise Distribution) 2.0 stack also supports the following RDS features: AS (Async Send), APM (Automatic Path Migration), QoS (Quality of Service), SRQ (Shared Request Queue), AB (Active Bonding), and NF (Netfilter).
|
||||
|
||||
Last but not least, paravirtualization support has been enabled for Oracle Linux guests on Windows Server 2008 R2 Hyper-V or Windows Server 2008 Hyper-V.
|
||||
|
||||
**Download Oracle Linux 6.5 right now:**
|
||||
|
||||
- [Oracle Enterprise Linux 6.5 (ISO) i386][1][iso] [3 GB]
|
||||
- [Oracle Enterprise Linux 6.5 (ISO) amd64][2][iso] [3.60 GB]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Oracle-Linux-6-5-Arrives-with-Unbreakable-Enterprise-Linux-Kernel-3-8-406093.shtml
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://mirrors.dotsrc.org/oracle-linux/OL6/U5/i386/OracleLinux-R6-U5-Server-i386-dvd.iso
|
||||
[2]:http://mirrors.dotsrc.org/oracle-linux/OL6/U5/x86_64/OracleLinux-R6-U5-Server-x86_64-dvd.iso
|
||||
@ -1,25 +0,0 @@
|
||||
(申领 by runningwater)
|
||||
Proprietary Unix Continues to Fall
|
||||
================================================================================
|
||||
Analysts at International Data Corporation (IDC) posted a [press release][1] Wednesday highlighting the rapid decline of IBM's AIX and P-Series hardware. Along side the drop in proprietary Unix systems is an associated rise in sales of X86 servers running Linux. IBM has clearly identified this as a long term trend, investing $1 billion dollars in Linux development on Power systems. With the reported 20% drop in sales, the writing my finally be on the wall for AIX.
|
||||
|
||||
I've had the dubious pleasure of administering both AIX and Linux systems for the past several years, and if I could pick and choose, I would take the flexibility and ease of use of Linux and the stability of Power. In my experience, AIX is difficult to set up, and difficult to change after it is set up, but once it is up and running it just runs. A properly configured AIX server can run for years without intervention, but when that time for modification comes, which it always does, prepare for a long hard slog. By contrast, Linux has become exponentially easier to manage over the years, thanks to the contributions of thousands of developers and sysadmins, as well as the contributions of big name corporations. As reported by [Infoworld][2]:
|
||||
|
||||
> The Linux server market is solidly on the rise as a percentage of total server sales up to 28 percent of total revenue so any investment that can improve market share is going to be worthwhile, even as the lion's share of Linux servers continues to be commodity x86 hardware.
|
||||
|
||||
Intel and AMD hardware has also grown by leaps and bounds, narrowing the performance gap with Power. I'm always a bit surprised when I hear that 10GB ethernet comes standard on a new blade, or that 256 GB of RAM is not considered unusual, or that it is considered the normal course of business to order a few servers with 16 cores each. Intel servers are nearly as powerful as IBM's Power, and normally cost much less. To businesses interested in escaping "consultingware" and IBM's vendor lock in, open source software running on industry standard x86 hardware is becoming increasingly attractive. However, IBM has lowered the prices of Power systems to remain competitive.
|
||||
|
||||
It is telling that IBM chose to invest in Linux on Power instead of AIX. IBM could have chosen to modernize AIX and provide better interoperability with common open source tools. While IBM claims that AIX is still important, the continuing drop in Power sales along with the Linux investment is beginning to tell a different story.
|
||||
|
||||
IBM may not be able to turn things around for AIX, but they could prolong its life indefinitely. It would be interesting to see how the market would react if AIX was released as open source.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ostatic.com/blog/proprietary-unix-continues-to-fall
|
||||
|
||||
译者:[runningwater](https://github.com/runningwater) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.idc.com/getdoc.jsp?containerId=prUS24476413
|
||||
[2]:http://www.infoworld.com/t/unix/ibms-losing-ground-unix-and-oracle-may-follow-232234
|
||||
@ -1,31 +0,0 @@
|
||||
Senior researchers analyzed LibreOffice with interesting conclusions
|
||||
================================================================================
|
||||
Users, editors, state departments, teams and city administrations are enjoying [LibreOffice][1], free open-source office suite proving itself a clear success across the globe with more and more adoptions, more and more positive feedback.
|
||||
|
||||
While the users perceive LibreOffice as no-compromise and powerful, it seems that serious researchers have also found and described LibreOffice as a true success, as in the case of the "**Sustainability of Open Source software communities beyond a fork: How and why has the LibreOffice project evolved?**" document, too.
|
||||
|
||||
Essentially, "Sustainability of Open Source software communities beyond a fork: How and why has the LibreOffice project evolved?" is a research document [focused][2] on LibreOffice and its components, ranging from status to public perception, future capabilities, ability to attract supporters and contributors.
|
||||
|
||||
The conclusions of the mentioned document, while natural, talk about LibreOffice as a success on all fronts, conclusions such as:
|
||||
|
||||
- "The LibreOffice project, which was forked from the OpenOffice.org project, shows no sign of
|
||||
- long-term decline"
|
||||
- "LibreOffice has attracted the long-term and most active committers in OpenOffice.org"
|
||||
- "Open Source communities can outlive Open Source software projects"
|
||||
- "LibreOffice is perceived by its community as supportive, diversified, and independent"
|
||||
|
||||

|
||||
|
||||
The serious 60-pages-long document (available for download on [http://www.sciencedirect.com/science/article/pii/S0164121213002744/pdfft...][3]) presents LibreOffice as detailed, being an in-depth accurate analysis of the robust office suite, document written by senior researchers from the University of Skövde’s Informatics Research Centre.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://iloveubuntu.net/senior-researchers-analyzed-libreoffice-interesting-conclusions
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.libreoffice.org/
|
||||
[2]:http://www.sciencedirect.com/science/article/pii/S0164121213002744
|
||||
[3]:http://www.sciencedirect.com/science/article/pii/S0164121213002744/pdfft?md5=4b986a117fb06cc127b854cb5f622bec&pid=1-s2.0-S0164121213002744-main.pdf
|
||||
@ -1,4 +1,3 @@
|
||||
Crowner's crown
|
||||
Setup Apache 2.4 and Php FPM with mod proxy fcgi on Ubuntu 13.10
|
||||
================================================================================
|
||||
### mod_proxy_fcgi ###
|
||||
@ -206,4 +205,4 @@ via: http://www.binarytides.com/setup-apache-php-fpm-mod-proxy-fcgi-ubuntu/
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://issues.apache.org/bugzilla/show_bug.cgi?id=54101
|
||||
[2]:https://wiki.apache.org/httpd/PHP-FPM
|
||||
[2]:https://wiki.apache.org/httpd/PHP-FPM
|
||||
|
||||
@ -0,0 +1,76 @@
|
||||
Software May Be Eating The World, But Open Source Software Is Eating Itself
|
||||
================================================================================
|
||||
**Nothing sits still for long in the world of open source.**
|
||||
|
||||
Software may be eating the world, as [Marc Andreessen posits][1], but open-source software seems to be eating itself. And at a far faster clip. While the software world has grown used to products and their vendors dominating for long stretches (think: Microsoft in operating systems and Oracle in databases), the new world of open source is moving at an accelerated, Darwinian pace, leaving no project to rest on its laurels.
|
||||
|
||||
In this fast-changing open source world, how should enterprises decide where to invest?
|
||||
|
||||
### Open Source Picks Up The Pace ###
|
||||
|
||||
Though [Dirk Riehle's analysis][2] of the total growth in open source projects is a few years old, if anything the trend he plots has [accelerated][3]:
|
||||
|
||||

|
||||
|
||||
Today much of the interesting code in technology’s most important markets—Big Data, cloud, mobile—is open source. With more activity focused on areas like Hadoop or OpenStack, we should expect the pace and volume of open code creation to increase.
|
||||
|
||||
Which may be good or bad.
|
||||
|
||||
### No Rest For The Open Source Developer ###
|
||||
|
||||
Take, for example, the configuration management market. Redmonk’s Stephen O’Grady sifts a number of data sources that measure the popularity of Chef, Puppet, Ansible and Salt, the latter two being very new to the market, yet demonstrating considerable community enthusiasm and adoption.
|
||||
|
||||
This prompts O’Grady to [speculate][4] that “Where it once was reasonable to conclude that the configuration management space would evolve in similar fashion to the open source relational database market—i.e. with two dominant projects—that future is now in question.”
|
||||
|
||||
O’Grady goes on to suggest:
|
||||
|
||||
> The most interesting conclusion to be taken from this brief look at a variety of community data sources, however, may well be the relevance of both Ansible and Salt. That these projects appear to have viable prospects in front of them speaks to the demand for solutions in the area, as well as the strong influence of personal preferences—e.g. the affinity for Salt amongst Python developers.
|
||||
|
||||
Actually, I’d argue that the most interesting conclusion is that no open-source project has guaranteed longevity. Puppet came out in 2005 and is still making headway against entrenched proprietary incumbents, yet now it has to fight off Chef (which came out four years later), Ansible (last two years) and Salt (last two years).
|
||||
|
||||
Yes, incumbents in any important market, proprietary or otherwise, will always have new market entrants nibbling at their heels. But in open source, the competition doesn’t wait for billion-dollar markets to form before it launches attacks. The rise of Salt and Ansible in a market already well-served by Chef and Puppet is a testament to this.
|
||||
|
||||
### The Community Giveth, And The Community Taketh Away ###
|
||||
|
||||
You will find this same dynamic in content management (Drupal vs. Joomla vs. Alfresco vs. Wordpress vs. countless other CMSes), cloud (Eucalyptus vs. OpenStack vs. CloudStack vs. CloudFoundry vs. OpenShift vs. many others), [web servers][5] and databases, both relational and NoSQL.
|
||||
|
||||
The ranks of open-source databases swell with new entrants almost daily, as can be seen on the [DB-Engines database tracking service][6]. Perhaps most interesting is the open-source relational database market. Up until recently, MySQL dominated that market. Postgres was a viable runner up to MySQL, but it was a very distant second.
|
||||
|
||||
Today things are in motion. Or commotion. Largely due to Oracle’s alleged fumbling of the MySQL community, Postgres is on a tear, booming even with the hipster crowd that welcomed MySQL. But so is MariaDB. Though still a comparative gnat, leading [Linux distributions like Red Hat’s Fedora and Ubuntu have embraced MariaDB][7], as has Google, replacing MySQL.
|
||||
|
||||
Perhaps, as O’Grady implies, this comes down to developer preferences. If developers rule, then little impedes them from switching to new projects that may fit their needs better, throwing a given market into disarray. If this is correct, it would explain why open source resists long term monopolies:
|
||||
|
||||
It’s hard to keep developers happy.
|
||||
|
||||
### Building A Community-Friendly Business ###
|
||||
|
||||
What does this mean for enterprises that are looking to make long-term investments on a given open-source project? An easy, if unsatisfying, answer is that enterprises should contribute to the projects they care about, ensuring their sustainability as well as giving the enterprise the ability to support themselves should the project dwindle.
|
||||
|
||||
But most enterprises don’t want to have to code the winner themselves.
|
||||
|
||||
Instead they should look for popular projects that are good technical fits for their enterprise requirements and that have strong communities. Popularity can be fleeting if a project grows callous to its community. One of the primary reasons Linux has endured so long at the top of the operating system heap is that it has been so accommodating to community influence and requirements.
|
||||
|
||||
Unfortunately, there’s no One True Way to measure vitality in an open source community. Some successful projects, like OpenStack, lean on a strong foundation. Others, like Linux, depend upon a strong individual and her lieutenants.
|
||||
|
||||
But all successful open-source projects that maintain their lead innovate quickly, with regular releases every few months. While a fast-moving project may be more difficult for enterprises to support, it may also be a key indication that the project will remain relevant.
|
||||
|
||||
How else should enterprises hedge against the risk of obsolescence of an open-source project?
|
||||
|
||||
Lede image courtesy of [Shutterstock][8].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://readwrite.com/2013/12/12/open-source-innovation
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://online.wsj.com/news/articles/SB10001424053111903480904576512250915629460
|
||||
[2]:http://dirkriehle.com/publications/2008-2/the-total-growth-of-open-source/
|
||||
[3]:http://www.techrepublic.com/blog/linux-and-open-source/driving-forces-behind-linux-and-open-source-growth/
|
||||
[4]:http://redmonk.com/sogrady/2013/12/06/configuration-management-2013/
|
||||
[5]:http://www.theregister.co.uk/2013/02/06/open_and_shut/
|
||||
[6]:http://db-engines.com/en/ranking
|
||||
[7]:http://www.zdnet.com/oracle-who-fedora-and-opensuse-will-replace-mysql-with-mariadb-7000010640/
|
||||
[8]:http://www.shutterstock.com/
|
||||
@ -0,0 +1,55 @@
|
||||
Solving HIPPA, HITECH, SSAE16 Server Compliance Issues with Next Generation Datacenters
|
||||
================================================================================
|
||||

|
||||
|
||||
HIPPA stands for Health Insurance Portability and Accountability Act, and HITECH stands for Health Information Technology for Economic and Clinical Health Act. Both acts have to do with how health records and data are handled. SSAE16 is similar. It’s an accounting standard created by the Auditing Standards Board (ASB) of the American Institute of Certified Public Accountants (AICPA). The parameters of all three have enormous implications both for healthcare and for web hosting. Dedicated server and managed hosting services that use next generation datacenters must ensure that they can meet the requirements as outlined in the compliance requirements of each one of them.
|
||||
|
||||
### The Basics ###
|
||||
|
||||
It is important to ensure that you are using a datacenter that will comply with the standards of HIPAA, HITECH and SSAE16. When discussing your needs with a datacenter, such as Atlantic.net, you should confirm that the datacenters conform to the standard contingency plan; data backup plan; disaster recovery plan; emergency mode operation plan; testing and revision procedures and applications; and data criticality analysis. Data servers have their own compliance requirements when it comes to managing your data, and you need to ensure that their performance standards can match up with your compliance requirements.
|
||||
|
||||
Achieving SSAE16 Type II Certification to ensure that SSAE16 will not present a problem for the server in the current time or immediate future is important. If you are in healthcare, you are probably familiar with the increasing demand for server and datacenter compliance. The new generation of data centers has helped to pave the way for many healthcare IT companies that needed to find a rock solid solution for their businesses’ hosting solution needs.
|
||||
|
||||
HIPAA was designed to provide better access to health insurance, reduce the occurrence of fraud and abuse, and lower the cost of obtaining health care in the USA. HITECH further reinforces the HIPAA regulations and provides some additional rules for you to follow. The data center you choose should help make the transition to become a fully compliant business, at least through your online presence. This may raise a few eyebrows and some people are even a bit nervous about whether or not their business can meet the demand in time for compliance testing. With the proper structure completed ahead of time, the hard part is done; all you need to do is plug into the tools and features we have available for you to use.
|
||||
|
||||
### What Does Compliance Involve? ###
|
||||
|
||||
Being HIPPA, SSAE16 and HITECH compliant means going the extra mile in server colocation, delivering dedicated servers, managed server hosting, and compliance through a credible datacenter. A datacenter must be reliable, with certified and trained staff who know how to handle customer problems and inquiries.
|
||||
|
||||
Being HIPPA, HITECH and SSAE16 compliant is vital in today’s environment, and everyone is fully aware of the legal boundaries in which healthcare organizations must operate. More efficient cooling procedures ensure that the compliance sequences are followed without a possibility for failure.
|
||||
|
||||
Dynamic allocation of resources where they are needed helps solve many resource issues. Additionally, the resources are used in the coolest parts of the datacenter, meaning more efficient use of the resources as well.
|
||||
|
||||
Optimizing application performance is one of the main advancements that next generation datacenters do incredibly well. These next generation datacenters that have been brought into operation have data security as one of their incredible strong points.
|
||||
|
||||
The new healthcare reform mandates implement even tighter security with HITECH, and service providers has vested large amounts in these regulations. Ample controls and checks/balances to help the patients and healthcare providers will be ensured for obvious reasons. The government understands that companies need to be encouraged to take things to the next level, and as a result, there are tax incentives to deploy EMR/EHR (Electronic Medical Records and Electronic Health Records).
|
||||
|
||||
Using cloud servers, you are able to scale up and scale out according to what your business needs. Even more so, quality datacenters can keep your healthcare organization safe! Using virtualization, companies have dedicated themselves to the continued success of your business. This means they have left no stone unturned to bring you an unprecedented level of services from which you can choose.
|
||||
|
||||
Being [HIPAA compliant][1] is partly the job of the hosting company and partly yours as well. They provide you with the services – the datacenter, the managed hosting and the tech support to ensure you have what you need to bring your healthcare business to the compliance level. They can only offer you the services that are required by the HIPAA, HITECH and SSAE16 regulations. They need your help to make sure both parties are up to speed in the quest to keep your business in complete compliance.
|
||||
|
||||
Cloud computing is a really big part of next generation datacenters. Virtualization technology has made it possible for everyone to have their resources delivered at the most optimum moment through more efficient handling of server resources. If you are new to cloud computing, you should know that this technology in no way endangers your ability to stay HIPAA, HITECH and SSAE16 compliant. Cloud computing is simply the new way of handling server requests and scaling additional resources up and out.
|
||||
|
||||
Have you ever stopped to consider what would happen if you were tagged with a violation of the HIPAA, HITECH or [SSAE16 compliance][2] standards? It would be a catastrophic blow to your business that would land you in court! Additionally, the people affected by the violation could possibly sue for damages. Quality web hosting services are now structured around ensuring that everything in the facility is certified to the new standards of operation.
|
||||
|
||||
Being in business for over 15 years, since 1994, has given us a chance to really perfect the art of hosting, server virtualization, data security, compliance, and the ability to provide a carrier-neutral datacenter.
|
||||
|
||||
### Conclusions ###
|
||||
|
||||
Atlantic.Net and other serious hosting companies have been a step ahead of the compliance standards from day one. Business expertise has allowed us to keep the healthcare IT businesses that we already have under our wing and ahead of the flames. We can help your business stay in line with these compliance standards as well.
|
||||
|
||||
All in all, server compliance issues won’t be much of a big deal once you realize what they are all about. The compliance issues would generally arise from a datacenter not having sufficient hardware or software to accommodate regulatory compliance; or the customer themselves may not be able to get the business into a state of compliance. Either way, a next generation datacenter must be able to offer the services in demand to meet the compliance requirements in order to be compliant with the regulations themselves.
|
||||
|
||||
By [Brett Haines][3]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.atlantic.net/blog/2013/12/04/solving-hippa-hitech-ssae16-server-compliance-issues-generation-datacenters/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.atlantic.net/hipaa-compliant-hosting/
|
||||
[2]:http://www.atlantic.net/ssae-16-type-2-compliant/
|
||||
[3]:https://plus.google.com/u/0/100137311390909550920?rel=author
|
||||
@ -1,99 +0,0 @@
|
||||
TeamViewer 9 Released – Install on RHEL/CentOS/Fedora and Debian/Ubuntu
|
||||
================================================================================
|
||||
This guide shows how to install **Teamviewer 9** on **RedHat, CentOS, Fedora** and **Debian**, **Ubuntu**, **Linux Mint**, **Xubuntu** systems. **Teamviewer** is a one of the most popular application for remote assistant, Desktop sharing or transferring files between computers, web conferencing and online meetings etc. Teamviewer is a proprietary application.
|
||||
|
||||
However, it’s a freeware for personal use. Teamviewer is available for **Windows, Linux, Mac OS, Android** and **iPhone**. Teamviewer uses **WINE** application which is integrated within it. We don’t have to [install WINE application][1]separately. **Teamviewer** is not a native **Linux** application.
|
||||
|
||||
Recently, the latest stable version of **TeamViewer 9** released with new features and many improvements. Following are some of the new features are added in **TeamViewer 9** which are highlighted below:
|
||||
|
||||
### Features for Windows, Linux and Mac ###
|
||||
|
||||
- Open multiple connections in different tabs
|
||||
- Support for Wake-on-LAN
|
||||
- Added two factor authentication for TeamViewer accounts
|
||||
- Support for Windows 8.1 and Mac OS X Mavericks
|
||||
- Save custom modules such as QuickSupport, QuickJoin, etc.
|
||||
- API Integration
|
||||
- Stronger security of the Teamviewer account
|
||||
- Quick connection via desktop shortcut
|
||||
- Visual notification
|
||||
- Copy and paste files and text between computers
|
||||
- Initiating file transfers to computers
|
||||
- Quick connection via desktop shortcut
|
||||
- Faster video transfers
|
||||
|
||||
### How do I Install Teamviewer 9 on RedHat, CentOS, Fedora ###
|
||||
|
||||
You may download package for rpm based Linux distributions at [teamviewer_linux.rpm][2].
|
||||
|
||||
Let us start installation. Go to the directory from where you have downloaded package and execute following yum command to install it. It will install missing dependencies.
|
||||
|
||||
# wget http://www.teamviewer.com/download/teamviewer_linux.rpm
|
||||
# yum install teamviewer_linux.rpm
|
||||
|
||||
If you get missing public key error, you can download public key and import it using the following command.
|
||||
|
||||
# wget http://www.teamviewer.com/link/?url=354858
|
||||
# rpm --import TeamViewer_Linux_PubKey.asc
|
||||
|
||||
After importing the public key, please run the “**yum install**” command again to install the Teamviewer rpm.
|
||||
|
||||
To start Teamviewer application, run the following command from the terminal.
|
||||
|
||||
# teamviewer
|
||||
|
||||
Teamviewer application running on my **Fedora 18** system.
|
||||
|
||||

|
||||
*Running TeamViewer in Fedora 18*
|
||||
|
||||
### How do I Install Teamviewer 9 on Ubuntu, Linux Mint, Xubuntu ###
|
||||
|
||||
You may download teamviewer package for **32-bit** or **64-bit** systems at [teamviewer linux .deb][3] packages. or you can download the package using **wget** command as shown below.
|
||||
|
||||
## 32 Bit System ##
|
||||
$ sudo wget http://www.teamviewer.com/download/teamviewer_linux.deb
|
||||
|
||||
## 64 Bit System ##
|
||||
$ sudo wget http://www.teamviewer.com/download/teamviewer_linux_x64.deb
|
||||
|
||||
Once you’ve downloaded the package, go to the directory where you’ve downloaded Teamviewer package and run the following command to install it.
|
||||
|
||||
## 32 Bit System ##
|
||||
$ sudo dpkg -i teamviewer_linux.deb
|
||||
|
||||
## 64 Bit System ##
|
||||
$ sudo dpkg -i teamviewer_linux_x64.deb
|
||||
|
||||
If you get missing dependencies error, please use the following command to install those dependencies.
|
||||
|
||||
sudo apt-get install -f
|
||||
|
||||
Once installation is done. To start Teamviewer package on **Ubuntu** Linux, go to **Dash Home** and type **teamviewer** and click on **teamviewer** icon to run application.
|
||||
|
||||

|
||||
*Running TeamViewer in Ubuntu 13.10*
|
||||
|
||||
Teamviewer application running on my **Ubuntu 13.10** system.
|
||||
|
||||

|
||||
*TeamViewer 9 Under Ubuntu 13.10*
|
||||
|
||||
To start on **Linux Mint**, Go to **Menu >> Internet >> Teamviewer** and click on **Accept License Agreement** to run application.
|
||||
|
||||
Teamviewer application running on my **Linux Mint 15**.
|
||||
|
||||

|
||||
*Running TeamViewer in Linux Mint 15*
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/how-to-install-teamviewer-on-linux-distributions/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.tecmint.com/install-wine-in-rhel-centos-and-fedora/
|
||||
[2]:http://www.teamviewer.com/download/teamviewer_linux.rpm
|
||||
[3]:http://www.teamviewer.com/hi/download/linux.aspx
|
||||
@ -0,0 +1,139 @@
|
||||
24 The Linux Kernel: Configuring the Kernel Part 20
|
||||
================================================================================
|
||||
|
||||
|
||||
Aloha and welcome to the next Linux kernel article! In this article, we will continue configuring filesystem support.
|
||||
|
||||
First, we can enable "General filesystem local caching manager" which allows the kernel to store filesystem cache. This can enhance performance at the cost of storage space.
|
||||
|
||||
The caching system can be monitored with statistical information used for debugging purposes (Gather statistical information on local caching). Generally, this feature should only be enabled if you plan to debug the caching system.
|
||||
|
||||
|
||||
|
||||
This next feature is a lot like the above, but this feature stores latency information (Gather latency information on local caching). Again, this is a debugging feature.
|
||||
|
||||
The "Debug FS-Cache" driver offers many other debugging abilities for the cache system.
|
||||
|
||||
The next cache debugging tool keeps a global list (any process can access the list) of filesystem cache objects (Maintain global object list for debugging purposes).
|
||||
|
||||
To enhance the speed of network filesystems, enable this next driver (Filesystem caching on files). This feature allows a whole local filesystem to be used as cache for remote filesystem and storage units. The Linux kernel will manage this partition.
|
||||
|
||||
Two different debugging drivers exist for this local cache system for remote filesystems (Debug CacheFiles) and (Gather latency information on CacheFiles).
|
||||
|
||||
The most common optical disc filesystem is ISO-9660 which is ISO standard 9660, hence the name (ISO 9660 CDROM file system support). This driver is needed to read/write the major of optical discs.
|
||||
|
||||
When reading an optical disc with files using long Unicode filenames or writing such files, this driver is required (Microsoft Joliet CDROM extensions). This is an extension to the ISO-9660 filesystem.
|
||||
|
||||
The "Transparent decompression extension" allows data to be written to a disc in a compressed form and read off the disc and decompressed transparently. This will allow more data to be placed on the disc.
|
||||
|
||||
"UDF file system support" allows the kernel to read/write rewritable-optical-discs that are using the UDF filesystem. UDF is designed to manage incremental writes. UDF allows the rewritable optical disc to be used more like flash drives. The system can write and update the optical disc's data more quickly than regular writing on ISO-9660 filesystems. However, this is not faster than using flash drives.
|
||||
|
||||
As many of you know, Windows is a very popular system, so many storage units are using the FAT filesystem of NTFS. Thankfully, Linux supports such filesystems. The "MSDOS fs support" driver is a general driver for MS-DOS filesystems. This will increase the kernel size significantly, but since the FAT filesystems are very common, this size increase is usually worth the cost. [http://www.linux.org/threads/file-allocation-table-fat.4472/][1]
|
||||
|
||||
To support the FAT filesystems, enable this driver (VFAT (Windows-95) fs support). At the time this article was written, this driver does not support FAT64 (commonly called exFAT).
|
||||
|
||||
|
||||
|
||||
The size of the codepage can be set here (Default codepage for FAT).
|
||||
|
||||
After that, the default character set is configured for the FAT filesystems (Default iocharset for FAT).
|
||||
|
||||
The NTFS file system is offered with this driver (NTFS file system support). The driver provides read-only abilities. To write to NTFS, enable this driver (NTFS write support).
|
||||
|
||||
The Linux kernel offers debugging tools for the NTFS filesystem (NTFS debugging support).
|
||||
|
||||
To have a proc folder in the root, this feature must be enabled (/proc file system support). Some other similar drivers that rely on this one include (/proc/kcore support), (/proc/vmcore support), and (Sysctl support (/proc/sys)). The proc system (short for “process”) uses the proc-filesystem sometimes called procfs. This filesystem is in the hardware's memory and is created when Linux boots up. So, when viewing files in proc, the user is browsing the memory as if it were like other storage units. Proc acts as an interface between userspace and the kernelspace. Proc is in the kernelspace.
|
||||
|
||||
The "Enable /proc page monitoring" driver offers some proc files that monitor the memory utilization of processes.
|
||||
|
||||
The "sysfs file system support" driver creates the /sys/ folder. The sysfs filesystem is in memory and provides an interface to the kernel objects.
|
||||
|
||||
The tmp directory is needed by many applications and Linux itself, so it is strongly recommended that this driver be enabled (Tmpfs virtual memory file system support (former shm fs)). The tmp filesystem maybe stored on the hard-drive or in memory and is used only to store temporary files.
|
||||
|
||||
The "Tmpfs POSIX Access Control Lists" driver offers extra permission features for the files in the tmpfs virtual filesystem.
|
||||
|
||||
The "Tmpfs extended attributes" driver provides more attributes to tmpfs files than what they would normally have without he driver.
|
||||
|
||||
The "HugeTLB file system support" driver provides the hugetlbfs filesystem, which is ramfs based. This virtual filesystem contains HugeTLB pages.
|
||||
|
||||
|
||||
The configfs filesystem is a kernel object manager in the form of a filesystem (Userspace-driven configuration filesystem). It is highly recommended that this driver be enabled. ConfigFS is a lot like sysfs. However, ConfigFS is used to create and delete kernel object while sysfs is used to view and modify kernel objects.
|
||||
|
||||
Next, we can move back to "real" filesystems. That is, the filesystems users themselves use to store their personal files. Next, the kernel can be given the ability to read ADFS filesystems (ADFS file system support).
|
||||
|
||||
The ability to write to ADFS filesystems is provided by a separate and unstable driver (ADFS write support (DANGEROUS)). ADFS stands for Advanced Disc Filing System.
|
||||
|
||||
Linux also supports the Amiga Fast FileSystem (Amiga FFS file system support). [http://www.linux.org/threads/amiga-fast-file-system-affs.4429/][2]
|
||||
|
||||
The "eCrypt filesystem layer support" driver offers a POSIX-compliant cryptographic filesystem layer. This eCrypt can be placed on every and any filesystem no matter what partition table the filesystem resides on. [http://www.linux.org/threads/intro-to-encryption.4376/][3]
|
||||
|
||||
The eCrypt layer can have a device file if this driver is enabled (Enable notifications for userspace key wrap/unwrap). The device path is /dev/ecryptfs.
|
||||
|
||||
Linux also supports HFS and HFS+ (Apple Macintosh file system support) and (Apple Extended HFS file system support). [http://www.linux.org/threads/hierarchical-file-system-hfs.4480/][4] and [http://www.linux.org/threads/hierarchical-file-system-plus-hfs.4493/][5]
|
||||
|
||||
The BeFS filesystem can be used by Linux as a read-only filesystem (BeOS file system (BeFS) support (read only)). Generally, it is easier to program the reading abilities for a filesystem than the writing features.
|
||||
|
||||
Special debugging features exist for BeFS (Debug BeFS).
|
||||
|
||||
EFS is another filesystem that Linux can only read, not write (EFS file system support (read only)). [http://www.linux.org/threads/extent-file-system-efs.4447/][5]
|
||||
|
||||
Some flash drives may use the JFFS2 filesystem (Journalling Flash File System v2 (JFFS2) support). Next, the debugging level can be set (JFFS2 debugging verbosity). [http://www.linux.org/threads/journaling-flash-file-system-version-2-jffs2.4495/][6]
|
||||
|
||||
To use JFFS2 on NAND and NOR flash drives, this driver is needed (JFFS2 write-buffering support).
|
||||
|
||||
This next driver offers better error protection (Verify JFFS2 write-buffer reads).
|
||||
|
||||
JFFS filesystems can be mounted faster with "JFFS2 summary support" enabled. This driver stores information about the filesystem.
|
||||
|
||||
Like the other extended/extra attributes drivers for some filesystems, JFFS2 has such a driver (JFFS2 XATTR support).
|
||||
|
||||
The JFFS2 filesystem supports various transparent compression systems. This allows files to be smaller on JFFS2 filesystems and be read without the user needing to perform any special actions. (Advanced compression options for JFFS2), (JFFS2 ZLIB compression support), (JFFS2 LZO compression support), (JFFS2 RTIME compression support), and (JFFS2 RUBIN compression support). The default compression format can be defined in the following option (JFFS2 default compression mode).
|
||||
|
||||
A successor for JFFS2 exists and is supported by the kernel (UBIFS file system support). The Unsorted Block Image File System (UBIFS) also competes with LogFS.
|
||||
|
||||
The Linux kernel also supports LogFS (LogFS file system).
|
||||
|
||||
ROM-based embedded systems need support for CramFS (Compressed ROM file system support (cramfs)).
|
||||
|
||||
Alternately, embedded systems could use SquashFS which is a read-only compression filesystem (SquashFS 4.0 - Squashed file system support). The Linux kernel also offers extended attributes for SquashFS (Squashfs XATTR support).
|
||||
|
||||
There are three different compression formats supported by SquashFS - (Include support for ZLIB compressed file systems), (Include support for LZO compressed file systems), and (Include support for XZ compressed file systems). The block size for SquashFS can be set to four kilobytes (Use 4K device block size?). Also, the cache size can be set (Additional option for memory-constrained systems).
|
||||
|
||||
The Linux kernel supports FreeVxFS (FreeVxFS file system support (VERITAS VxFS(TM) compatible)), Minix (Minix file system support), MPEG filesystem (SonicBlue Optimized MPEG File System support), HPFS (OS/2 HPFS file system support), QNX4 (QNX4 file system support (read only)), QNX6 (QNX6 file system support (read only)), and the ROM filesystem (ROM file system support). [http://www.linux.org/threads/qnx-file-systems.4577/][8] and [http://www.linux.org/threads/minix-mini-unix-file-system.4545/][9]
|
||||
|
||||
"RomFS backing stores (Block device-backed ROM file system support)" offers a list of various ROMfs extra features and abilities.
|
||||
|
||||
The "Persistent store support" driver provides support for the pstore filesystem which allows access to platform level persistent storage.
|
||||
|
||||
The pstore filesystem can store kernel logs/messages (Log kernel console messages).
|
||||
|
||||
When a kernel panic takes place (equivalent to the "Blue-Screen-of-Death" on Windows), the "Log panic/oops to a RAM buffer" driver will store a log in the RAM.
|
||||
|
||||
This next single driver offers support for the Xenix, Coherent, Version 7, and System V filesystems (System V/Xenix/V7/Coherent file system support).
|
||||
|
||||
The Linux kernel also supports UFS (UFS file system support (read only)), (UFS file system write support (DANGEROUS)), and (UFS debugging).
|
||||
|
||||
exofs is also supported by the kernel (exofs: OSD based file system support).
|
||||
|
||||
The Flash-Friendly FileSystem is a special filesystem for flash drives (F2FS filesystem support (EXPERIMENTAL)), (F2FS Status Information ), (F2FS extended attributes), and (F2FS Access Control Lists). [http://www.linux.org/threads/flash-friendly-file-system-f2fs.4477/][10]
|
||||
|
||||
In the next article, we will configure network filesystems. Mahalo!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.org/threads/the-linux-kernel-configuring-the-kernel-part-20.4957/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.linux.org/threads/file-allocation-table-fat.4472/
|
||||
[2]:http://www.linux.org/threads/amiga-fast-file-system-affs.4429/
|
||||
[3]:http://www.linux.org/threads/intro-to-encryption.4376/
|
||||
[4]:http://www.linux.org/threads/hierarchical-file-system-hfs.4480/
|
||||
[5]:http://www.linux.org/threads/hierarchical-file-system-plus-hfs.4493/
|
||||
[6]:http://www.linux.org/threads/extent-file-system-efs.4447/
|
||||
[7]:http://www.linux.org/threads/journaling-flash-file-system-version-2-jffs2.4495/
|
||||
[8]:http://www.linux.org/threads/qnx-file-systems.4577/
|
||||
[9]:http://www.linux.org/threads/minix-mini-unix-file-system.4545/
|
||||
[10]:http://www.linux.org/threads/flash-friendly-file-system-f2fs.4477/
|
||||
@ -0,0 +1,120 @@
|
||||
25 The Linux Kernel: Configuring the Kernel Part 21
|
||||
================================================================================
|
||||
|
||||
|
||||
Aloha! In this next article, we will configure network filesystem support for the Linux kernel. A network filesystem is a remote filesystem that computers access via the network.
|
||||
|
||||
First, the "NFS client support" driver allows the Linux system to use the NFS network filesystem. There are also three other drivers for different versions of NFS - (NFS client support for NFS version 2), (NFS client support for NFS version 3), (NFS client support for NFS version 4), and (NFS client support for NFSv4.1). If you have a network that possess NFS, either figure out what version of NFS you are using, or enable all of the NFS drivers.
|
||||
|
||||
Swap space is not required to be on a local storage unit. This driver allows Linux to use NFS support to use remote swap spaces (Provide swap over NFS support).
|
||||
|
||||
The NFS system can be sped up by using a cache system (Provide NFS client caching support). This is local cache.
|
||||
|
||||
Enable this driver to allow DNS to use host-names for NFS servers (Use the legacy NFS DNS resolver).
|
||||
|
||||
"NFS server support" gives the server providing NFS the features it needs to fulfill such a task. Some other NFS drivers include (NFS server support for NFS version 3) and (NFS server support for NFS version 4).
|
||||
|
||||
The "NFS server manual fault injection" driver is a debugging tool that allows developers to make the NFS server think an error occurred with NFS. Specifically, this is used to test how the server handles NFS errors.
|
||||
|
||||
The "Secure RPC: Kerberos V mechanism" is needed to make the RPC calls secure. NFS cannot be added to the kernel without this feature for security reasons.
|
||||
|
||||
There is a special debugging tool for RPC (RPC: Enable dprintk debugging).
|
||||
|
||||
The Linux kernel supports the Ceph filesystem (Ceph distributed file system).
|
||||
|
||||
CIFS is a virtual filesystem used by Samba and Windows servers (CIFS support (advanced network filesystem, SMBFS successor)). CIFS stands for Common Internet FileSystem.
|
||||
|
||||
There are two features that can be used to debug or monitor the CIFS driver (CIFS statistics) and (Extended statistics).
|
||||
|
||||
|
||||
A special driver is needed to support servers with LANMAN security (Support legacy servers which use weaker LANMAN security). LANMAN or LM hash is a special password hashing function that has some weaknesses.
|
||||
|
||||
CIFS requires that Kerberos tickets be used before mounting to secure servers (Kerberos/SPNEGO advanced session setup). This driver offers the ability for CIFS to use userspace tools which is needed to provide the tickets.
|
||||
|
||||
Like other filesystems, CIFS can have extended abilities (CIFS extended attributes) and (CIFS POSIX Extensions).
|
||||
|
||||
This driver gets the Access Control List (ACL) from the CIFS server (Provide CIFS ACL support).
|
||||
|
||||
CIFS has two other debugging tools (Enable CIFS debugging routines) and (Enable additional CIFS debugging routines).
|
||||
|
||||
CIFS can have "DFS feature support" which allows shares to be accessed even when they are moved. DFS stands for Distributed FileSystem.
|
||||
|
||||
SMB2 is an improved alternative to CIFS (SMB2 network file system support). SMB2 stands for Server Message Block version 2.
|
||||
|
||||
Clients can store CIFS cache with this driver enabled (Provide CIFS client caching support).
|
||||
|
||||
Novell NetWare clients need this driver to access NetWare volumes (NCP file system support (to mount NetWare volumes)). NCP stands for NetWare Core Protocol. NCP is a protocol that allows clients to communicate with the servers hosting NetWare volumes.
|
||||
|
||||
NetWare servers can use NFS namespaces if this driver is enabled (Use NFS namespace if available).
|
||||
|
||||
NetWare servers can use the OS/2 long namespaces if this driver is enabled (Use LONG (OS/2) namespace if available).
|
||||
|
||||
If this driver is enabled, then filenames made by DOS or on storage units owned by a DOS system will be converted to lowercase (Lowercase DOS filenames).
|
||||
|
||||
Many filesystems depend on native language support (Use Native Language Support). Specifically, Native Language Support (NLS) allows the different character-sets to be used in filenames.
|
||||
|
||||
NCP filesystems can support the execute flag and symbolic links with this driver enabled (Enable symbolic links and execute flags).
|
||||
|
||||
The Linux kernel offers support for the Coda filesystem (Coda file system support (advanced network fs)). Coda is one of many network filesystems.
|
||||
|
||||
The Linux kernel can support the Andrew Filesystem (Andrew File System support (AFS)). However, the Linux kernel can only read such filesystems in an insecure manner. This driver is intended to allow Linux systems to access AFS. If your network only contains Linux systems, then select a different network filesystem that the kernel can fully support.
|
||||
|
||||
The Linux kernel has an experimental driver for accessing Plan 9 resources via the 9P2000 protocol (Plan 9 Resource Sharing Support (9P2000)). The kernel also has cache support (Enable 9P client caching support) and control lists (9P POSIX Access Control Lists) for the previously mentioned Plan 9 feature.
|
||||
|
||||
|
||||
|
||||
After the network filesystems have been configured, the next part of the kernel to setup is the "Native Language Support". This whole menu contains the drivers for most or all of the character-sets and encodings. Enabling these encodings allows these character sets to be used by the system and applications. UTF-8 is the most commonly used encoding, but it is not the only one. Most applications and driver need UTF-8, so this encoding is already set to be added to the kernel.
|
||||
|
||||
After that menu, the "Distributed Lock Manager (DLM)" can be configured. A DLM is used to keep shared resources in sync and performing well. This driver manages the userspace and kernelspace applications that access or manipulate shared resources (like network filesystems). Clusters strongly depend on this driver.
|
||||
|
||||
Now that we have finally finished configuring the filesystems and related features, we can now move on to the "Kernel hacking" menu seen on the main (first) screen on the kernel configuration tool (when using the command "make menuconfig"). I am using the ncurses interface (seen in the screenshot) which is initiated with the "make menuconfig" command, so other interfaces may be a little different. Many of the features and settings in the kernel hacking menu contain various settings concerning the kernel itself. Some of these features are debugging tools and some control the kernel's behavior.
|
||||
|
||||
This first setting adds the pritnk time stamps to the syslog system call output (Show timing information on printks).
|
||||
|
||||
The next three features control various debugging features (Default message log level (1-7)), (Enable __deprecated logic), and (Enable __must_check logic).
|
||||
|
||||
|
||||
|
||||
The next feature is a debugging feature that is active at compiling time ((1024) Warn for stack frames larger than (needs gcc 4.4)). If stack frames are larger than the specified amount, then the compiler will warn the user.
|
||||
|
||||
The "Magic SysRq key" driver will enable support for the Magic SysRq key. This allows users to send the kernel special commands when Alt+PrintScreen is pressed. This works in most cases regardless of the kernel's state. However, exceptions exist. It is highly recommended that the Magic SysRq Key be enabled.
|
||||
|
||||
During compilation, the assembler's symbolic links will be removed during a link to reduce the output of get_wchan() (Strip assembler-generated symbols during link).
|
||||
|
||||
This next feature is for debugging purposes (Generate readable assembler code). If enabled, some kernel optimizations will be disabled so some of the assembly code will be human-readable. This will harm the kernel's speed. Only enable this if you have a specific reason for doing so.
|
||||
|
||||
This setting enables/disables commonly unneeded or obsolete symbols (Enable unused/obsolete exported symbols). However, some modules may need such symbols. Enabling this will increase the kernel's size. It is very unlikely that a Linux user will need such symbols. In general, disable this unless you know for a fact the user needs a symbol for an important module.
|
||||
|
||||
Sanity checks will be performed on user kernel headers if this setting is enabled (Run 'make headers_check' when building vmlinux).
|
||||
|
||||
During compilation, this feature will check for invalid references (Enable full Section mismatch analysis).
|
||||
|
||||
The kernel can be configured to detect soft and hard lockups (Detect Hard and Soft Lockups). When the system is frozen for more than twenty second and other tasks cannot execute, this is called a soft-lockup. If the CPU is in a loop that lasts for more than ten seconds and interrupts fail to get execution time, then this is called a hard-lockup.
|
||||
|
||||
The next to features set the kernel to reboot on hard and soft lockups respectively, (Panic (Reboot) On Hard Lockups) and (Panic (Reboot) On Soft Lockups).
|
||||
|
||||
When the kernel experiences major problems, it can be set to start a kernel panic (Panic on Oops). It is highly recommended that this setting be enabled. This will help to prevent the kernel from causing system damage and data loss.
|
||||
|
||||
The kernel can be set to detect hung tasks (Detect Hung Tasks). This is when a process or application locks-up or is frozen. Specifically, the application becomes uninterruptable. The following setting allows the user to define how much time must pass before a process is deemed "hung" (Default timeout for hung task detection (in seconds)).
|
||||
|
||||
The kernel can be set to restart when a process hangs (Panic (Reboot) On Hung Tasks). Generally, users will not want to enabled this. Would you like your computer to restart every time an application becomes frozen?
|
||||
|
||||
The "Kernel memory leak detector" finds and logs memory leaks.
|
||||
|
||||
The kernel uses frame pointers to help report errors more efficiently and include more information (Compile the kernel with frame pointers). I will skip a lot of the debugging tools because they are self-explanatory.
|
||||
|
||||
As many Linux users know, when the system boots up, the boot messages appear too quickly to be read. This feature sets the delay time which will give users more time to read the messages (Delay each boot printk message by N milliseconds).
|
||||
|
||||
This is a special developmental feature for testing backtrace code (Self test for the backtrace code). Backtrace code is a self-test.
|
||||
|
||||
Block device number can be extended (Force extended block device numbers and spread them). However, this may cause booting issues, so use with caution.
|
||||
|
||||
We will continue to configure the kernel itself in the next article. I hope you have enjoyed this article. Mahalo!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.org/threads/the-linux-kernel-configuring-the-kernel-part-21.4988/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,119 @@
|
||||
26 The Linux Kernel: Configuring the Kernel Part 22
|
||||
================================================================================
|
||||
|
||||
|
||||
Aloha! In this article, we will continue to configure the kernel hacks and then we will configure the whole security system.
|
||||
|
||||
The next feature to configure is needed by Alpha and s390 processor (Force weak per-cpu definitions). This feature offers a fix for an addressing issue commonly seen in such processors. Other processors do not need this feature enabled.
|
||||
|
||||
Kernel dumps can be tested with this special debugging tool (Linux Kernel Dump Test Tool Module). This software will allow a kernel developer to trigger a fake error that will cause a kernel dump. The kernel developers can then ensure that the dumps complete successfully.
|
||||
|
||||
The kernel offers some different error injection modules that allow kernel developers to test the notifiers (CPU notifier error injection module), (PM notifier error injection module), and (Memory hotplug notifier error injection module). A notifier informs the system that the hardware is present, which is important for hotplugging. These error injection modules trigger an error in this notification system so developers can test the notification system's error handling abilities.
|
||||
|
||||
The "Fault-injection framework" driver offers various tools for testing fault-handling.
|
||||
|
||||
The "Latency measuring infrastructure" driver provides the LatencyTOP tool used to find the userspace object that is blocking/interfering with a kernel execution/task.
|
||||
|
||||
Next, we have a sub-menu titled "Tracers" that contains a list of various tracers. A tracer is a piece of code that watches various kernel functions. Every time a particular function starts, a tracer will be called to watch the function.
|
||||
|
||||
This next module tests the performance of the Red-Black tree library (Red-Black tree test). The Red-Black tree library is a sorting and searching algorithm.
|
||||
|
||||
The next feature is the same except that it tests the interval tree library (Interval tree test).
|
||||
|
||||
The kernel can also debug FireWire on other systems while that particular remote system is booting (Remote debugging over FireWire early on boot) and (Remote debugging over FireWire with firewire-ohci).
|
||||
|
||||
The printk() function can be made to print various debugging messages if this feature is enabled (Enable dynamic printk() support). “printk()” is a commonly discussed system call, so remember that it prints debugging messages about the kernel.
|
||||
|
||||
Here is a Direct Memory Access (DMA) debugging driver (Enable debugging of DMA-API usage).
|
||||
|
||||
The Atomic64 self-tests checks if the system supports atomic operations (Perform an atomic64_t self-test at boot). This is where a 32-bit system performs a 64-bit operation.
|
||||
|
||||
This driver provides a self-test for all of the possible RAID6 recovery systems (Self test for hardware accelerated raid6 recovery).
|
||||
|
||||
NOTE: Self-tests are low-level tests and detection software that executes before most of the system's hardware and software turns on and executes. Self-tests search for hardware, failing devices, etc. A self-test may also be code an application uses to test itself.
|
||||
|
||||
In the Kernel Hacking menu (if you are using a menu-like interface such as ncurses), there is a sub-menu titled "Sample kernel code". If you make your own personal modules, this is where you can enable them. In a later article, we will discuss how to implement custom/home-made kernel modules. Just remember this is where you enable your module.
|
||||
|
||||
|
||||
|
||||
The Kernel GNU DeBugger (KGDB) has many features that can be enabled or disabled (KGDB: kernel debugger). This debugger only works with two Linux systems plugged into each other via serial connection.
|
||||
|
||||
This feature provides extra boot-up messages for the decompression of the bzimage (Enable verbose x86 bootup info messages). You set the kernel encryption near the beginning of the configuration process.
|
||||
|
||||
Printk() prints various information to the boot-screen of dmesg, but after the serial and console drivers load. Enable this driver to make printk start printing messages sooner (Early printk).
|
||||
|
||||
This next driver is the same as above, but uses the EHCI port (Early printk via EHCI debug port).
|
||||
|
||||
The kernel can be set to watch for stack overflows so the kernel can manage the error better (Check for stack overflows). The kernel will execute more slowly, but overflows will not cause as much damage.
|
||||
|
||||
The page-table for the kernel can be seen on debugfs with this enabled (Export kernel pagetable layout to userspace via debugfs). However, this will slow down the kernel. This is needed for debugging purposes.
|
||||
|
||||
The kernel's written mistakes can be caught with this feature (Write protect kernel read-only data structures). This option turns the kernel's read-only data to write-protected mode. This debugging tool harms the kernel's speed. That debugging tool has a tool to debug itself (Testcase for the DEBUG_RODATA feature).
|
||||
|
||||
To prevent the execution of modules with modified code (due to an error), then enable this protective feature (Set loadable kernel module data as NX and text as RO). The debugging tool for that feature is provided by this driver (Testcase for the NX non-executable stack feature).
|
||||
|
||||
The kernel can be set to flush one of the TLB entries at a time or the whole table using this option (Set upper limit of TLB entries to flush one-by-one).
|
||||
|
||||
The next feature is an IOMMU debugging feature (Enable IOMMU debugging). There is another debugging test that disables some IOMMU features to test for extra stability (Enable IOMMU stress-test mode). The IOMMU stands for input/output memory management unit.
|
||||
|
||||
Enabling this option will make the kernel perform selt-tests on the change_page_attr() system call on thirty second intervals (CPA self-test code). This system call changes page attributes.
|
||||
|
||||
Any kernel code marked as "inline" can not be manipulated as much as it would by GCC than if it were not marked (Allow gcc to uninline functions marked). The GCC compiler adds code that it feels will make the code better (GCC is good at doing so). However, some code is not meant to be manipulated by GCC.
|
||||
|
||||
This next driver offers sanity checks for the "copy_from_user()" system call (Strict copy size checks). copy_from_user() copies a block of userspace data to kernelspace.
|
||||
|
||||
Here is another self-test; this one is for NMI (NMI Selftest).
|
||||
|
||||
Now, we can move on to the "Security Options" which is seen as a sub-menu in the main menu if you are using a menu-based interface, like ncurses. The first option allows access keys and authentication tokens to be stored in the kernel (Enable access key retention support). This is used for many reasons like accessing encrypted filesystems.
|
||||
|
||||
The following option is for creating and sealing/unsealing keys (TRUSTED KEYS). Encrypted keys are encrypted/decrypted using this driver (ENCRYPTED KEYS).
|
||||
|
||||
Keys can be viewed in proc with this feature enabled (Enable the /proc/keys file by which keys may be viewed).
|
||||
|
||||
Extra restrictions can be applied to syslog with this security feature (Restrict unprivileged access to the kernel syslog).
|
||||
|
||||
If this option is enabled, then the user can select different security models (Enable different security models). Otherwise, the defaults will be used. Disable this if you do not fully understand security or if you are fine with your kernel using the defaults.
|
||||
|
||||
The securityfs filesystem is offered by this driver (Enable the securityfs filesystem).
|
||||
|
||||
Hooks are added to networking and socket security when this feature is enabled (Socket and Networking Security Hooks). These hooks are access controls.
|
||||
|
||||
IPSec networking hooks (also called XFRM networking hooks) are implemented when this option is enabled (XFRM (IPSec) Networking Security Hooks). Security hooks are also available for files (Security hooks for pathname based access control).
|
||||
|
||||
The next driver provides support for Intel's Trusted Execution Technology (Enable Intel(R) Trusted Execution Technology (Intel(R) TXT)).
|
||||
|
||||
The user can set the range of memory addresses that cannot be reserved for userspace (Low address space for LSM to protect from user allocation). The starting point is 0. The user types the end point for this option. For most platforms, 65536 is a recommended choice.
|
||||
|
||||
SELinux (mentioned in the Kernel Security article) is one of the popular Linux-Security-Modules (NSA SELinux Support). Many options and features exist for SELinux. The boot parameter determines whether SELinux is started {1} or not started {0} when the kernel executes (NSA SELinux boot parameter). SELinux can be configured with the ability to be temporarily disabled at times when the Root user needs to do so (NSA SELinux runtime disable). Users can develop and test new policies with this feature enabled (NSA SELinux Development Support). AVC statistics are collected and stored by this feature (NSA SELinux AVC Statistics). A default can be set for the checkreqprot flag; a "1" means SELinux will check the application's requested protection and zero will default to the kernel's protection for mmap and mprotect system calls (NSA SELinux checkreqprot default value). Many SELinux policies exist; the user can set the latest version that they wish SELinux not to excede (NSA SELinux maximum supported policy format version).
|
||||
|
||||
One of the other Linux-Security-Modules (LSM), SMACK, is supported by the kernel (Simplified Mandatory Access Control Kernel Support).
|
||||
|
||||
TOMOYO is another supported LSM (TOMOYO Linux Support). The maximum number of entries permitted to be added during learning-mode is set in the following feature (Default maximal count for learning mode). The amount of log entires can also be set (Default maximal count for audit log). Next, this option allows/disallows TOMOYO to be activated without a policy loader (Activate without calling userspace policy loader). The location of the policy loader is configured here ((/sbin/tomoyo-init) Location of userspace policy loader) and the executable that triggers the execution is set here ((/sbin/init) Trigger for calling userspace policy loader).
|
||||
|
||||
Again, the kernel supports another LSM - AppArmor (AppArmor support). Like with SELinux, the default boot parameter can be set for AppArmor (AppArmor boot parameter default value).
|
||||
|
||||
Yama is another LSM (Yama support). Yama can be used with another LSM if this feature is enabled (Yama stacked with other LSMs).
|
||||
|
||||
This driver gives the kernel the ability to use multiple keyrings for verification processes (Digital signature verification using multiple keyrings).
|
||||
|
||||
Asymmetric keys are supported with this feature (Enable asymmetric keys support).
|
||||
|
||||
The kernel can keep and maintain a list of hashes and important system files (Integrity Measurement Architecture(IMA)). Then, if malware changes an important file, the kernel will know because the hashes are checked before the file or executable are used. It is highly recommended that this feature be enabled.
|
||||
|
||||
Extra security attributes are added to files if this feature is enabled (EVM support). The version can be set using this next option (EVM HMAC version). The two choices are version 1 and 2.
|
||||
|
||||
Remember all of the different Linux Security Modules (LSMs)? Well, the default can be set here (Default security module (AppArmor)).
|
||||
|
||||
In the next article, we can configure the "Cryptographic API". There may be two additional configuration articles left than what I estimated. After that, there are other kernel topics to discuss.
|
||||
|
||||
SNEAK PEAK: After this article, there is one more about the configuration process. Then, we can finally compile and install the kernel.
|
||||
|
||||
MESSAGE TO MY FANS: Feel free to post and/or email suggestions for kernel topics you would like me to cover in the following kernel articles. I still have a list of the suggestions some readers have sent me over the course of this series. Please feel free to send more.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.org/threads/the-linux-kernel-configuring-the-kernel-part-22.5017/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,114 @@
|
||||
27 The Linux Kernel: Configuring the Kernel Part 23
|
||||
================================================================================
|
||||
|
||||
|
||||
Aloha and welcome to the next kernel configuration article! In this article, we will configure the Cryptographic API, Virtualization, and Library Routines. Cryptography refers to encryption and secure communication between desired computers. Users may encrypt data to ensure only the recipient reads the data instead of hackers that may obtain the data.
|
||||
|
||||
The Linux kernel requires the "Cryptographic algorithm manager" to be enabled in the kernel. This feature provides the software needed to operate the cryptographic abilities of the kernel.
|
||||
|
||||
The userspace can configure the cryptography features when this driver is enabled (Userspace cryptographic algorithm configuration). NOTE: This configuration is referring to the cryptographic setup during kernel runtime, not the tool for making the kernel.
|
||||
|
||||
To enhance performance, enable this feature which stops self-tests on cryptographic algorithms (Disable run-time self tests).
|
||||
|
||||
The "GF(2^128) multiplication functions" is a specific algorithm used by some ciphers. GF stands for Galois field and is a set of finite numbers. These sets are called fields and they come in a variety of sizes.
|
||||
|
||||
"Null algorithms" are algorithms used in IPsec. Null encryption means no encryption, so this driver allows IPsec to use no encryption.
|
||||
|
||||
Arbitrary algorithms can be converted to parallel algorithms (Parallel crypto engine). This feature provides that converter.
|
||||
|
||||
Arbitrary algorithms can also be converted to asynchronous algorithms (Software async crypto daemon).
|
||||
|
||||
"Authenc support" is needed by IPsec. Authenc support stands for Authenticated Encryption and offers multiple encryptions to IPsec.
|
||||
|
||||
CCM stands for "Counter with CBC MAC" and is needed by IPsec (CCM support).
|
||||
|
||||
This driver offers "GCM/GMAC support". GCM is "Galois/Counter Mode" and GMAC is "Galois Message Authentication Code".
|
||||
|
||||
NOTE: I will not be able to explain specifically the use and details of some of these features. Cryptography is a detail field of computers and explaining cryptography is beyond the scope of this article.
|
||||
|
||||
The "Sequence Number IV Generator" is a special number generator used by some cryptography software.
|
||||
|
||||
The Linux kernel supports various cipher algorithms (CBC support), (CTR support), (CTS support), (ECB support), (LRW support), (PCBC support), (XTS support), (HMAC support), (XCBC support), and (VMAC support).
|
||||
|
||||
The "CRC32c CRC algorithm" is used specifically with SPARC64 processors.
|
||||
|
||||
"CRC32c INTEL hardware acceleration" is another processor specific algorithm. It works on Intel processors with SSE4.2.
|
||||
|
||||
The kernel also offers many digests, ciphers, and other cryptographic software. Generally, allow the defaults unless you have a specific reason for enabling or disabling features.
|
||||
|
||||
NOTE: A digest (like MD5) generates a hash (sequence of characters) based on a file. Hashes are then used to check files. For example, if you download the Ubuntu installation ISO file from Canonical's website, you may want to know if the file on your hard-drive is an exact replica of the server's file. Users do this because the ISO may become corrupted during the long download. The hash is used to prove that the file is unchanged.
|
||||
|
||||
NOTE: A cipher is an encryption/decryption algorithm. Encryption is the process of making a file unreadable to anyone other than the intended recipients/owners. Decryption is the process used to view an encrypted file.
|
||||
|
||||
The Linux kernel also supports various compression algorithms that users are strongly recommended to enable (Deflate compression algorithm), (Zlib compression algorithm), and (LZO compression algorithm).
|
||||
|
||||
The kernel can generate random numbers which are needed for cryptographic software (Pseudo Random Number Generation for Cryptographic modules), (User-space interface for hash algorithms), and (User-space interface for symmetric key cipher algorithms).
|
||||
|
||||
"Hardware crypto devices" is a sub-menu that contains a list of drivers for hardware-based cryptography tools. This is hardware that has the algorithms in the firmware.
|
||||
|
||||
Various drivers for asymmetric public-keys exist in the "Asymmetric (public-key cryptographic) key type" menu.
|
||||
|
||||
Now, we can move on to the next entry on the main menu of the configuration tool (on menu-based interfaces). Virtualization is the ability to host an operating system. This means Linux (and other systems) can run another operating system as if the guest system is an application.
|
||||
|
||||
"Kernel-based Virtual Machine (KVM) support" allows the kernel itself to manage the guest system. Computers with Intel processors need this driver (KVM for Intel processors support) and AMD processors need (KVM for AMD processors support).
|
||||
|
||||
The memory management unit (MMU) for the Kernel Virtual Machine (KVM) can have an auditing system.
|
||||
|
||||
The guest's network can become faster with this feature enabled (Host kernel accelerator for virtio net).
|
||||
|
||||
After configuring the virtual machine abilities for the kernel, the last menu on the main screen of the configuration tool (when using a menu interface) is the last portion of the kernel to configure. This menu is for the "Library Routines", also called library functions. Parts of the kernel can be used as a linkable library. For example, XZ filters (compression algorithms) can be accessed by external programs. The different libraries are listed below.
|
||||
|
||||
NOTE: The CRC functions are mostly the same but with different features or performance. Generally, it is best to allow the defaults.
|
||||
|
||||
CRC-CCITT functions - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC16 functions - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC calculation for the T10 Data Integrity Field - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC ITU-T V.41 functions - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC32/CRC32c functions - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC32 perform self test on init - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC32 implementation (Slice by 8 bytes) - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC7 functions - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC32c (Castagnoli, et al) Cyclic Redundancy-Check - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
CRC8 function - The Cyclic Redundancy Check function tests for changes in raw data
|
||||
|
||||
* BCJ filter decoder - XZ decoder design for a specific processor where "*" is the processor. The kernel lists a few different architectures.
|
||||
|
||||
XZ decompressor tester - Debug functions for testing the XZ decoder
|
||||
|
||||
Averaging functions - Load average as seen in the output of "uptime"
|
||||
|
||||
CORDIC algorithm - hyperbolic and trigonometry functions
|
||||
|
||||
|
||||
JEDEC DDR data - JEDEC Double Data Rate SD-RAM specification
|
||||
|
||||
|
||||
Guess what? You have finished configuring your kernel. I am sure after twenty-three articles, this is how you feel -
|
||||
|
||||
Video link:[http://www.youtube.com/embed/barWV7RWkq0?wmode=opaque][1]
|
||||
|
||||
Next, we can compile and install.
|
||||
|
||||
In the far distance, I still hear this -
|
||||
|
||||
Video link:[http://www.youtube.com/embed/ELoUppY1esw?wmode=opaque][2]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.org/threads/the-linux-kernel-configuring-the-kernel-part-23.5112/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.youtube.com/embed/barWV7RWkq0?wmode=opaque
|
||||
[2]:http://www.youtube.com/embed/ELoUppY1esw?wmode=opaque
|
||||
159
sources/Top 10 Linux Games of 2013.md
Normal file
159
sources/Top 10 Linux Games of 2013.md
Normal file
@ -0,0 +1,159 @@
|
||||
hyaocuk is TRANSLATING
|
||||
|
||||
Top 10 Linux Games of 2013
|
||||
================================================================================
|
||||
**With 2013 wrapping up, we’ve brought together 10 of our favourite Linux games of the past year.**
|
||||
|
||||
2013 was a huge year for Linux gaming with Valve’s continued commitment to the platform, encouraging words from big studios like Battlefield developers [DICE][1], and Creative Assembly’s commitment to bringing Total War: Rome II to [Linux next year][2].
|
||||
|
||||
Our list contains both indie titles and some of the most influential AAA titles to date. **This list isn’t intended to be comprehensive nor anything other than our opinion.**
|
||||
|
||||
All of the titles are available on Steam and/or the Ubuntu Software Center, so get your wallets and purses and prepare to throw some money at your screen!
|
||||
|
||||
### Garry’s Mod ###
|
||||
|
||||

|
||||
*Prop or not?*
|
||||
|
||||
Garry’s Mod is a sandbox game with little to no objective in itself, but the magic is in all the props you can load up from a number of Source engine games and the growing number of mods created by the community.
|
||||
|
||||
One such mod is [PropHunt][3] – a hide-and-seek game where one team hides as various objects on a map and the other attempts to find the filing cabinet precariously perched on a secluded staircase.
|
||||
|
||||
It’s simple fun, yet the vast array of game mods – be it for prop hunting, spaceship building, or machinima recording – makes Garry’s Mod a fantastic addition to an avid Linux gamer’s collection.
|
||||
|
||||
- [Get Garry’s Mod on Steam][4]
|
||||
|
||||
### Half-Life 2 ###
|
||||
|
||||

|
||||
*Theoretical physics has never been so cool.*
|
||||
|
||||
And speaking of the Source engine, Half-Life 2 might be the oldest game in the list, but is by far one of the most beloved both in Valve’s oeuvre and amongst all the games to come to Linux this year.
|
||||
|
||||
Half-Life 2 continues protagonist and theoretical physicist Gordon Freeman’s story from the first title in the series as he makes his way across a world ravaged by man and alien alike. Everything from physics puzzles to frighteningly agile headcrabs stand in your way, but the journey is *still* one of the most enthralling experiences in any game today.
|
||||
|
||||
The next title in the Half-Life series has a lot to live up to, but judging by the reception of one of the oldest titles to get a Linux port, Linux gamers are ready with crowbar and Gravity Gun in hand.
|
||||
|
||||
- [Get Half-Life 2 on Steam][5]
|
||||
|
||||
### Amnesia: A Machine for Pigs ###
|
||||
|
||||

|
||||
|
||||
When we reviewed Amnesia: A Machine for Pigs [in September][6], we found the title’s atmosphere as nerve-wracking as the first and worth trudging through the easy puzzles to explore the Victorian surroundings and steampunk-like machinery.
|
||||
|
||||
One of the biggest wins was day one Linux support for a title in such a popular series. But the developers at Frictional Games have always been friends to Linux gamers, porting titles from their Penumbra series in 2007 and 2008 soon after launch.
|
||||
|
||||
- [Get Amnesia: AMfP on Steam][7]
|
||||
- [Get Amnesia: AMfP on the Ubuntu Software Center][8]
|
||||
|
||||
### Metro: Last Light ###
|
||||
|
||||

|
||||
|
||||
Metro: Last Light is one the first AAA titles to come to Linux and [relatively quickly][9] to boot. Set in 2034 under the nuclear-devastated city of Moscow, Metro: Last Light twists the tropes of post-apocalyptic narratives into an intense first-person shooter experience.
|
||||
|
||||
Everything from ghosts to mutant arachnids and giant amoebas are prepared to make a normal day in post-apocalyptic Moscow a little less pleasant.
|
||||
|
||||
It’s not as tongue-in-cheek as the similarly post-apocalyptic Fallout series, but just as reflective of the brutal, yet sometimes touching, human experience in trying times.
|
||||
|
||||
- [Get Metro: Last Light on Steam][10]
|
||||
|
||||
### Starbound ###
|
||||
|
||||
|
||||
|
||||
Think of Starbound as Terraria or a 2D Minecraft with a real storyline and set in space. What’s not to love?
|
||||
|
||||
Much like Minecraft, you can hunt, mine, and build in the world, but unlike the popular 3D sandbox game, you can also travel to other planets and participate in an actual storyline. Your spacecraft starts off stranded in orbit and your first set of quests involves familiarising yourself with the gameplay mechanics and finding fuel for your ship before you can start exploring the procedurally generated planets. What’s more, the various monsters on each planet are also procedurally generated, so you’ll encounter some truly bizarre creatures along the way.
|
||||
|
||||
Starbound is an **Early Access Game**, so you’ll probably discover some broken mechanics (the bow and arrow are a bit troublesome to say the least) and experience a crash or two along the way. But it’s still a fun and featureful game despite being in beta.
|
||||
|
||||
- [Get Starbound on Steam][11]
|
||||
|
||||
### 0 A.D. ###
|
||||
|
||||
|
||||
*Workers constructing buildings and picking berries.*
|
||||
|
||||
0 A.D. has been available on Linux for several years, but we think it deserves a place in the list for all its accomplishments in 2013.
|
||||
|
||||
It’s the only free and open source title on the list and recently wrapped up a $33,251 [fundraising drive][12] – enough, they say, to hire one of their programmers for a full year. Though the game didn’t reach its more optimistic fundraising goals, that’s still $33,251 raised to support an open source project.
|
||||
|
||||
And more than anything, it’s fun. Fans of the Age of Empires style of real-time strategy will enjoy the work that’s gone into 0 A.D. over the years. The attention to detail is evident and though the title still has a ways to go, it only stands to improve with another dedicated programmer on board.
|
||||
|
||||
- [Get 0 A.D. on the Ubuntu Software Center][13]
|
||||
|
||||
### War in a Box: Paper Tanks ###
|
||||
|
||||

|
||||
|
||||
Tower defence games are as common as Reversi or Minesweeper, but [War in a Box: Paper Tanks][14] adds a dose of charm to the addictive genre.
|
||||
|
||||
Its unique paper-craft aesthetic works extremely well, giving the 24 levels a tireless appeal as you play and replay each level. At $3.99 it’s an easy sell for anyone who enjoys casual tower defence games. It’s simple fun, but utterly addicting.
|
||||
|
||||
- [Get War in a Box: Paper Tanks][15]
|
||||
|
||||
### FEZ ###
|
||||
|
||||

|
||||
*I like fezes. Fezes are cool.*
|
||||
|
||||
We reviewed FEZ back [in September][16] and the perspective-shifting 2D platformer is every bit as fun as a Pillsbury Doughboy-like character with a fez on makes it sound.
|
||||
|
||||
Jumping puzzles, mind-bending perspective puzzles, and gaming in-jokes all contribute to a title that stays fresh even when you’ve fallen off the map a dozen times or stood too close to a bomb when it goes off.
|
||||
|
||||
- [Get FEZ on Steam][17]
|
||||
|
||||
### Europa Universalis IV ###
|
||||
|
||||

|
||||
|
||||
Imagine Civilization with a bit more micromanagement, a big helping of history, and one gigantic difference: it’s on Linux!
|
||||
|
||||
Unlike the Civilization games, Europa Universalis titles are historical strategy, though by no means a play-by-play of history books. And instead of battling across thousands of years, EUIV only spans the years 1444–1821. But that doesn’t mean EU is any less fun or engaging as the longer running Civilization series.
|
||||
|
||||
EUIV plays out in real-time rather than in turns, so you’ll be pausing often to get a better view of your growing empire or your wealthy nation’s vast trade routes. The EU series can be intimidating to beginners given the scope of “grand strategy” gameplay, but if you ever wanted to play out the colonisation of the Americas or tweak the outcome of the Napoleonic Wars, it’ll be worth the effort.
|
||||
|
||||
- [Get Europa Universalis IV on Steam][18]
|
||||
|
||||
### Kentucky Route Zero ###
|
||||
|
||||

|
||||
|
||||
[Kentucky Route Zero][19] is one of my favourite games of all time. It’s the most artistically-orientated title in the list and one that exemplifies the more poetic side of gaming in addition to all the AAA titles that we can to look forward to in 2014 and beyond.
|
||||
|
||||
Kentucky Route Zero brings the magical realism genre to point-and-click adventures, mixing the surreal with classic adventure game elements. You start out looking for an unknown address to deliver antiques to, but the narrative takes off in unexpected, often fantastical, directions from there.
|
||||
|
||||
It’s a game about discovery rather than achievements or saving a princess who’s inevitably in another castle. It won’t be everyone’s cup of tea – nor will it fit everyone’s definition of a “game” – but it is one of the most meaningful and creative titles I’ve ever had the pleasure of playing.
|
||||
|
||||
- [Get Kentucky Route Zero on Steam][20]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2013/12/top-10-linux-games-2013
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.polygon.com/2013/10/12/4826190/linux-only-needs-one-killer-game-to-explode-says-battlefield-director
|
||||
[2]:http://www.omgubuntu.co.uk/2013/11/total-war-rome-ii-coming-linux-early-next-year
|
||||
[3]:http://steamcommunity.com/sharedfiles/filedetails/?id=135509255
|
||||
[4]:http://store.steampowered.com/app/4000
|
||||
[5]:http://store.steampowered.com/app/220
|
||||
[6]:http://www.omgubuntu.co.uk/2013/09/amnesia-a-machine-for-pigs-review
|
||||
[7]:http://store.steampowered.com/app/239200
|
||||
[8]:https://apps.ubuntu.com/cat/applications/amnesia-amfp/
|
||||
[9]:http://www.omgubuntu.co.uk/2013/11/metro-last-light-steam-linux-download
|
||||
[10]:http://store.steampowered.com/app/43160
|
||||
[11]:http://store.steampowered.com/app/211820
|
||||
[12]:http://www.omgubuntu.co.uk/2013/10/crowd-funding-success-historical-war-game-0-d
|
||||
[13]:https://apps.ubuntu.com/cat/applications/0ad/
|
||||
[14]:http://www.omgubuntu.co.uk/2013/03/war-in-a-box-paper-tanks-ubuntu-review
|
||||
[15]:https://apps.ubuntu.com/cat/applications/war-in-a-box-paper-tanks/
|
||||
[16]:http://www.omgubuntu.co.uk/2013/09/fez-indie-game-review-on-linux
|
||||
[17]:http://store.steampowered.com/app/224760/
|
||||
[18]:http://store.steampowered.com/app/236850
|
||||
[19]:http://www.omgubuntu.co.uk/2013/02/adventures-in-magical-realism-kentucky-route-zero-act-i-review
|
||||
[20]:http://store.steampowered.com/app/231200
|
||||
@ -0,0 +1,158 @@
|
||||
示例说明10个Linux中有用打的链接操作符
|
||||
================================================================================
|
||||
Linux命令中的链接的意思是,结合几个命令并基于它们之间操作符的行为执行。Linux中的链接命令,有些像你在shell中写[短小的shell脚本],并直接在终端中执行。链接使得自动处理变得可能。不仅如此,一个无人看管的机器在链接操作符的帮助下如此有条理地运行。
|
||||
|
||||

|
||||
*Linux中的10个链接操作符*
|
||||
|
||||
本文旨在常用的**链接操作符**,并作简短的描述和相关的肯定能提高你生产力的例子,除了有时能降低系统负载外还能让你写出简短有意义的代码。
|
||||
|
||||
### 1. 和号操作符 (&) ###
|
||||
|
||||
‘**&**‘的作用是使命令在后台运行。只要在命令后面跟上一个空格和 ‘**&**。你可以一口气在后台运行多个命令。
|
||||
|
||||
在后台运行一个命令:
|
||||
|
||||
tecmint@localhost:~$ ping c5 www.tecmint.com &
|
||||
|
||||
同时在后台运行两个命令:
|
||||
|
||||
root@localhost:/home/tecmint# apt-get update & apt-get upgrade &
|
||||
|
||||
### 2. 分号操作符 (;) ###
|
||||
|
||||
分号操作符使你可以一口气运行几个命令,命令顺序执行。
|
||||
|
||||
root@localhost:/home/tecmint# apt-get update ; apt-get upgrade ; mkdir test
|
||||
|
||||
创建了一个‘**test**‘文件夹
|
||||
|
||||
### 3. 与操作符 (&&) ###
|
||||
|
||||
如果第一个命令执行成功(译者注: 原文为“if the execution of first command fails”,译者认为与上下文意思不同),**与操作符 (&&)**会执行第二个命令,也就是说,第一个命令退出状态是**1**。这个命令在检查最后一个命令的执行状态时很有用。
|
||||
|
||||
比如,我想使用**[links command][2]**在终端中访问网站**tecmint.com**,但在这之前我需要检查主机是否**在线**或者**不在线**。
|
||||
|
||||
root@localhost:/home/tecmint# ping -c3 www.tecmint.com && links www.tecmint.com
|
||||
|
||||
### 4. 或操作符 (||) ###
|
||||
|
||||
**或操作符 (||)**很像编程中的**else**语句。上面的操作符允许你在第一个命令失败的情况下执行第二个命令,也就是说,第一个命令的退出状态是**1**。
|
||||
|
||||
举例来说,我想要在非root帐户中执行‘**apt-get update**‘,如果第一个命令失败了,接着会执行第二个命令‘**links www.tecmint.com**‘。
|
||||
|
||||
tecmint@localhost:~$ apt-get update || links tecmint.com
|
||||
|
||||
上面的命令中,由于**用户**不允许**更新**系统,这意味着第一个命令的退出状态是’**1**′,因此最后一个命令‘**links tecmint.com**‘会执行。
|
||||
|
||||
如果第一个命令成功执行并且退出状态是‘**0**‘呢?很明显的,第二个命令不会执行。
|
||||
|
||||
tecmint@localhost:~$ mkdir test || links tecmint.com
|
||||
|
||||
这里,用户在家目录创建了一个‘**test**‘文件夹,这是被允许的。命令成功的执行,退出状态是‘**0**‘,因此,最后的命令不会执行。
|
||||
|
||||
### 5. 非操作符 (!) ###
|
||||
|
||||
**非操作符 (!)**很像**except**语句。这个命令会执行除了提供的条件外的所有的语句。要理解这点,在你的家目录创建一个目录‘**tecmint**‘,并‘**cd**‘到它这里。
|
||||
|
||||
tecmint@localhost:~$ mkdir tecmint
|
||||
tecmint@localhost:~$ cd tecmint
|
||||
|
||||
接下来,在文件夹‘**tecmint**‘下创建不同类型的文件。
|
||||
|
||||
tecmint@localhost:~/tecmint$ touch a.doc b.doc a.pdf b.pdf a.xml b.xml a.html b.html
|
||||
|
||||
看一下我们在文件夹‘**tecmint**‘创建的新文件。
|
||||
|
||||
tecmint@localhost:~/tecmint$ ls
|
||||
|
||||
a.doc a.html a.pdf a.xml b.doc b.html b.pdf b.xml
|
||||
|
||||
用一种聪明的办法马上删除除了 ‘**html**‘之外的所有文件。
|
||||
|
||||
tecmint@localhost:~/tecmint$ rm -r !(*.html)
|
||||
|
||||
验证一下上次的执行结果,使用[ls 命令][3]列出可见所有文件。
|
||||
|
||||
tecmint@localhost:~/tecmint$ ls
|
||||
|
||||
a.html b.html
|
||||
|
||||
### 6. 与 – 或 操作符 (&& – ||) ###
|
||||
|
||||
上面的操作符实际上是‘**与**‘和‘**或**‘操作符的组合。它很像‘**if-else**‘语句。
|
||||
|
||||
比如,让我们ping **tecmint.com**,如果成功打印‘**已验证**‘,否则打印‘**主机故障**‘。
|
||||
|
||||
tecmint@localhost:~/tecmint$ ping -c3 www.tecmint.com && echo "Verified" || echo "Host Down"
|
||||
|
||||
#### 示例输出 ####
|
||||
|
||||
PING www.tecmint.com (212.71.234.61) 56(84) bytes of data.
|
||||
64 bytes from www.tecmint.com (212.71.234.61): icmp_req=1 ttl=55 time=216 ms
|
||||
64 bytes from www.tecmint.com (212.71.234.61): icmp_req=2 ttl=55 time=224 ms
|
||||
64 bytes from www.tecmint.com (212.71.234.61): icmp_req=3 ttl=55 time=226 ms
|
||||
|
||||
--- www.tecmint.com ping statistics ---
|
||||
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
|
||||
rtt min/avg/max/mdev = 216.960/222.789/226.423/4.199 ms
|
||||
Verified
|
||||
|
||||
现在,断开我们现在的网络连接诶,再试一下相同的命令。
|
||||
|
||||
tecmint@localhost:~/tecmint$ ping -c3 www.tecmint.com && echo "verified" || echo "Host Down"
|
||||
|
||||
#### 实例输出 ####
|
||||
|
||||
ping: unknown host www.tecmint.com
|
||||
Host Down
|
||||
|
||||
### 7. 管道操作符 (|) ###
|
||||
|
||||
**PIPE**在第一个命令的输出作为第二个命令的输入时很有用。比如,‘**ls -l**‘的输出通过管道到‘**less**‘,并看一下输出。
|
||||
|
||||
tecmint@localhost:~$ ls -l | less
|
||||
|
||||
### 8. 命令合并操作符 {} ###
|
||||
|
||||
合并两个或多个命令,第二个命令依赖于第一个命令的执行。
|
||||
|
||||
比如,检查一下文件‘**xyz.txt**‘和‘**xyz1.txt**‘是否在**Downloads**目录下,并输出相关的输出。
|
||||
|
||||
tecmint@localhost:~$ [ -f /home/tecmint/Downloads/xyz.txt ] || echo “The file does not exist”
|
||||
|
||||
tecmint@localhost:~$ [ -f /home/tecmint/Downloads/xyz1.txt ] || echo “The file does not exist”
|
||||
|
||||
“The file does not exist”
|
||||
|
||||
### 9. 优先操作符 () ###
|
||||
|
||||
这个操作符可以让命令以优先顺序执行。
|
||||
|
||||
Command_x1 &&Command_x2 || Command_x3 && Command_x4.
|
||||
|
||||
在上面的伪代码中,如果**Command_x1**执行失败了会怎么样,**Command_x2**, **Command_x3**, **Command_x4**没有一个会自行,对于这种,我们使用**优先操作符**。
|
||||
|
||||
(Command_x1 &&Command_x2) || (Command_x3 && Command_x4)
|
||||
|
||||
在上面的伪代码中,如果**Command_x1**执行失败,**Command_x2**同样失败,但是**Command_x3**会继续执行, **Command_x4**会依赖于 **Command_x3**的退出状态。
|
||||
|
||||
### 10. 连接符 (\) ###
|
||||
|
||||
**连接符 (\)**如它名字所说,被用于连接shell中跨越多行的命令。比如,下面的命令会打开文本文件**test(1).txt**。
|
||||
|
||||
tecmint@localhost:~/Downloads$ nano test\(1\).txt
|
||||
|
||||
今天就到这里,我会近日开始另外一个有趣的文章。不要走开,继续关注**Tecmint**。不要忘记在评论栏里提出有价值的反馈。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/chaining-operators-in-linux-with-practical-examples/
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.tecmint.com/category/bash-shell/
|
||||
[2]:http://www.tecmint.com/command-line-web-browsers/
|
||||
[3]:http://www.tecmint.com/15-basic-ls-command-examples-in-linux/
|
||||
@ -1,20 +1,19 @@
|
||||
如何在Debian和Ubuntu下重新打包Deb文件
|
||||
|
||||
================================================================================
|
||||
|
||||
**以下教程会教导Ubuntu,Linux Mint和Debian GUN/Linux用户,如何在它们基于Debian的Linux操作系统上轻松的解开和重建.deb文件。**
|
||||
**以下教程将会教导Ubuntu、Linux Mint和Debian GUN/Linux用户,如何在它们基于Debian的Linux操作系统上轻松的解压和重新打包.deb文件。**
|
||||
|
||||

|
||||
|
||||
有时候你会碰到这样或那样的问题,你想要修改.deb文件的部分内容,然后重新打包。但是,也只有你真正的进入计算机世界之中。
|
||||
有时候你在生活中会碰到这样的问题,你想要修改.deb文件的部分内容,然后重新打包。但是这也只有你真正进入到计算机世界以及黑客世界当中才能完成。
|
||||
|
||||
下面的例子是刚发生在我身上真实的经历。一位Linux的开发者为一个软件构建了一个Debian包(.deb),我也成功得将它安装在我的装载Ubuntu的电脑上。
|
||||
下面的例子是刚发生在我身上的真实经历。一位Linux开发者为一个软件构建了一个Debian包(.deb),我也成功地将它安装在我的装载Ubuntu的电脑上。
|
||||
|
||||
当我试图从一个Git库中检索一些文件时,它总是卡顿,佷显然,该软件并没有正常工作。我知道安装的文件在哪里(/opt目录),所以,我搜查了代码并适当的将部分问题修复。之后,当程序试图检索需要的包时不再卡顿。
|
||||
当我试图从一个Git库中检索一些文件时,它总是卡顿,很显然,该软件并没有正常工作。我知道安装的文件在哪里(/opt目录),所以,我搜查了代码并适当地将部分问题修复。之后,当程序试图检索需要的包时不再卡顿。
|
||||
|
||||
所以,长话短说,我要将.deb文件解包,替换上我的补丁文件,然后再重新打包回来。这样我可以其他电脑上安装,或者将有效的包文件给我的朋友。我要怎么做呢?
|
||||
所以,长话短说,我要将.deb文件解包,替换上我的补丁文件,然后再重新打包回来。这样我可以其它电脑上安装,或者将有效的包文件给我的朋友。我要怎么做呢?
|
||||
|
||||
在网络上搜索问题的答案,我发现一个名叫[ailoo.net][1]的小型博客,类似这样解释:
|
||||
在网络上搜索问题的答案,我发现一个名叫[ailoo.net][1]的小型博客,它给出类似这样解释:
|
||||
|
||||
mkdir -p extract/DEBIAN
|
||||
|
||||
@ -26,27 +25,17 @@
|
||||
|
||||
dpkg-deb -b extract/ build/
|
||||
|
||||
这五个命令像一个魔法来完成工作。让我向你解释:第一条命令创建了一个名为“extract”文件夹和一个名为“DEBIAN”的子文件夹;第二条命令会从你的.deb包提取程序文件到“extract”文件夹;第三条命令会解压.deb包的控制文件到“DEBIAN”子文件夹,在那里你就可以 修改/补丁 你想要的文件;第四条命令建立一个名为“build”的文件夹;而第五条命令会将修改后的文件重新构建到一个新的.deb包中,并在 “build” 文件夹中生成。
|
||||
这五条命令将奇迹般地完成工作。让我为你解释一下:第一条命令创建了一个名为“extract”文件夹和一个名为“DEBIAN”的子文件夹;第二条命令会从你的.deb包提取程序文件到“extract”文件夹;第三条命令会解压.deb包的控制文件到“DEBIAN”子文件夹,在那里你就可以 修改/补丁 你想要的文件;第四条命令建立一个名为“build”的文件夹;而第五条命令会将修改后的文件重新构建到一个新的.deb包中,并在 “build” 文件夹中生成。
|
||||
|
||||
这就是本次的教程!牢牢地记住上面的命令吧,在你执行第三条命令后,可以通过你默认的文件管理器用一个图形化的文本编辑器,可视化的修改文件。如果你在这个教程上遇到问题,你可以毫不犹豫的评论给我们。
|
||||
这就是本次教程!牢牢地记住上面的命令吧,在你执行第三条命令后,可以通过你的默认文件管理器,用一个图形化的文本编辑器可视化地修改文件。如果你在学习本教程时遇到问题,不要犹豫,在下面给我们写下评论。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/How-to-Repack-Deb-Files-on-Debian-and-Ubuntu-404930.shtml
|
||||
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://ailoo.net/2009/06/repack-a-deb-archive-with-dpkg-deb/
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
[1]:http://ailoo.net/2009/06/repack-a-deb-archive-with-dpkg-deb/
|
||||
|
||||
|
||||
101
translated/How to Upgrade to GNOME 3.10 in Ubuntu 13.10.md
Normal file
101
translated/How to Upgrade to GNOME 3.10 in Ubuntu 13.10.md
Normal file
@ -0,0 +1,101 @@
|
||||
How to Upgrade to GNOME 3.10 in Ubuntu 13.10
|
||||
================================================================================
|
||||
|
||||

|
||||
|
||||
**Ubuntu 13.10 在它的归档(archives是这么翻译吗?)中搭载可用的GNOME 3.8桌面。 尽管对于Unity这是一个可靠稳定以及有特色的替代品,但这个版本还是过时了。**
|
||||
|
||||
GNOME桌面的最新版本在2013年9月被发布了,随之而来的是一系列改进的功能、应用程序和可用性的调整。从对高分辨率屏幕的支持到应用窗口上全新的客户端美化,GNOME 3.10是一个引人注目的升级版本。
|
||||
|
||||
好消息是:假设你正在运行Ubuntu 13.10,拥有不错的网络连接和命令行功能(一语双关),那么你无需继续使用一个过时版本的GNOME。
|
||||
|
||||
### 在Ubuntu 13.10 上升级到GNOME 3.10 ###
|
||||
|
||||
为了那些关注点在我会重申的地方上的普通读者的利益(skim未翻译),你**需要运行Ubuntu 13.10来安装GNOME 3.10**.
|
||||
|
||||
首先,让我们添加GNOME 3 的PPA到Ubuntu的软件资源中。这个操作可以使用图形界面完成,但使用命令行会更容易归档一些。
|
||||
|
||||
打开一个新的*终端*窗口,键入下列命令,在被要求的时候输入你的用户密码:
|
||||
|
||||
sudo add-apt-repository ppa:gnome3-team/gnome3-next && sudo apt-get update
|
||||
|
||||
添加完PPA和更新包列表后,我们就可以转向安装GNOME 3.10了。运行下列命令,当弹出提示时再次输入你的用户密码:
|
||||
|
||||
sudo apt-get update && sudo apt-get install gnome-shell ubuntu-gnome-desktop
|
||||
|
||||
获取并安装所有必要的包和部件会花一点时间,所以请耐心一点。
|
||||
|
||||
在安装过程中,在终端可能会弹出一个提示,要求你选择一种显示管理器,默认使用的是“登录窗口”。
|
||||
|
||||
这个决定完全取决于你;UBuntu的Unity Greeter和**GNOME的显示管理器**都能让你很轻松地在桌面会话之间切换(如果你想保持在Unity界面或者另一个桌面将很方便),但仅仅只有GDM提供给GNOME特定的功能,譬如锁屏通知。
|
||||
|
||||
当你准备好你的选择后,使用上下键选择,然后敲击‘确认\返回’键以确认选择。安装便会继续进行。
|
||||
|
||||
### 增加额外的功能 ###
|
||||
|
||||

|
||||
|
||||
GNOME 3.10还有一些不错的新特性,应用-[包括GNOME天气,音乐盒地图][1] 以及其它各种各样的改变。
|
||||
因为并不是所有的特性都足够稳定以致于可以被包含在我们之前添加的GNOME 3 PPA中,所以如果你想使用它们,就需要利用到一对额外的GNOME PPA。
|
||||
|
||||
现在-你需要意识到很重要的是-在这些仓库里的一些包据说已经有了稳定的发行版。它们中的大部分是次要的,譬如应用程序崩溃和损坏的特性。但对于更多主要的发行版来说,像使得GNOME完全崩溃是有可能的。
|
||||
|
||||
除开这个警告,在终端里打开一个新的选项卡,输入下列命令:
|
||||
|
||||
sudo add-apt-repository ppa:gnome3-team/gnome3-staging
|
||||
sudo add-apt-repository ppa:gnome3-team/gnome3
|
||||
sudo apt-get update && sudo apt-get dist-upgrade
|
||||
|
||||
为了添加一些之前提到的很酷的应用,运行这个命令:
|
||||
|
||||
sudo apt-get install gnome-weather gnome-music gnome-maps cheese gnome-documents
|
||||
|
||||
这样之后,就搞定了!
|
||||
|
||||
你可能会想先注销然后重新登录(记得选择“GNOME”会话)以确保改动都已经正确生效了。
|
||||
|
||||
### 细小的差别 ###
|
||||
|
||||
如果你在不卸载Unity的情况下安装GNOME 3.10,那么有一些注意事项你需要记下来。
|
||||
|
||||
首先,你会发现**在系统设置里“Online Accounts”有两个入口**。其中,有key-themed(不知道怎么翻译)的图标是Unity版的,另一个有插件符号的是GNOME版的。
|
||||
|
||||
一些应用程序可能会要求你往Unity中添加账户(Shotwell, Gwibber, Empathy),有一些可能是要求往GNOME中添加(Evolution, Documents, Contacts)。
|
||||
|
||||

|
||||
|
||||
“通知”和“搜索”入口是GNOME指定的,它们让你挑选哪些应用程序和资源能够显示通知或出现在活动区。
|
||||
|
||||
### 卸载GNOME 3.10 ###
|
||||
|
||||
既然你已经尝试了GNOME 3.10,但不喜欢它。这时该怎么办?
|
||||
|
||||
假设我们使用一个叫做“PPA Purge”的命令行工具,那么移除GNOME 3.10 是一个相当简单的过程。这个工具可以在Ubuntu软件中心里找到,是目前为止自动移除或降级从PPA安装的包的最容易的方法。
|
||||
|
||||
- [Install PPA Purge from Ubuntu Software Center][2]
|
||||
|
||||
为了使用这个工具,我们需要返回终端然后键入下面命令,要留意任何出现在降级过程中的提示。
|
||||
|
||||
sudo ppa-purge ppa:gnome3-team/gnome3-next
|
||||
|
||||
如果你也添加了其它可选的PPA,你也需要清楚它们:
|
||||
|
||||
sudo ppa-purge ppa:gnome3-team/gnome3-staging
|
||||
sudo ppa-purge ppa:gnome3-team/gnome3
|
||||
|
||||
一旦完成,你应该在GNOME 3.8 桌面中离开(stock不知怎么翻译)。如果你不再想保留GNOME Shell了,你可以执行下列命令去卸载它:
|
||||
|
||||
sudo apt-get remove gnome-shell ubuntu-gnome-desktop
|
||||
|
||||
最后,手动移除任何在降级之后可能残留的应用程序(譬如,Epiphany and GNOME Documents),然后重启。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2013/12/upgrade-gnome-3-10-ubuntu-13-10
|
||||
|
||||
译者:[KAyGuoWhu](https://github.com/KayGuoWhu) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.omgubuntu.co.uk/2013/09/gnome-3-10-released-with-new-apps-experimental-wayland-support
|
||||
[2]:apt:ppa-purge
|
||||
@ -1,88 +0,0 @@
|
||||
使用PPA在Elementary OS 'Luna'上安装Oracle Java 7
|
||||
================================================================================
|
||||
**问题**: 我该如何在 Elemetary OS Luna 上安装Oracle Java 7?
|
||||
|
||||
**回答**: 在 Elementary OS Luna 安装 Java 7 的步骤如下:
|
||||
由于Elementary OS是基于Ubuntu,所以我们允许使用具有多种Java包的**WEPUD8 PPA**。
|
||||
|
||||
1. 打开终端。
|
||||
|
||||
2. 运行以下指令添加Java的PPA到你的软件仓:
|
||||
|
||||
$ sudo add-apt-repository ppa:webupd8team/java
|
||||
|
||||
You are about to add the following PPA to your system:
|
||||
Oracle Java (JDK) Installer (automatically downloads and installs Oracle JDK6 / JDK7 / JDK8). There are no actual Java files in this PPA. More info: http://www.webupd8.org/2012/01/install-oracle-java-jdk-7-in-ubuntu-via.html
|
||||
Debian installation instructions: http://www.webupd8.org/2012/06/how-to-install-oracle-java-7-in-debian.html
|
||||
More info: https://launchpad.net/~webupd8team/+archive/java
|
||||
Press [ENTER] to continue or ctrl-c to cancel adding it
|
||||
|
||||
3. 按回车继续
|
||||
|
||||
gpg: keyring `/tmp/tmpB5WwDG/secring.gpg' created
|
||||
gpg: keyring `/tmp/tmpB5WwDG/pubring.gpg' created
|
||||
gpg: requesting key EEA14886 from hkp server keyserver.ubuntu.com
|
||||
gpg: /tmp/tmpB5WwDG/trustdb.gpg: trustdb created
|
||||
gpg: key EEA14886: public key "Launchpad VLC" imported
|
||||
gpg: Total number processed: 1
|
||||
gpg: imported: 1 (RSA: 1)
|
||||
OK
|
||||
|
||||
4. 现在更新你的系统
|
||||
|
||||
$ sudo apt-get update
|
||||
|
||||
5. 运行以下命令安装Java 7:
|
||||
|
||||
$ sudo apt-get install oracle-java7-installer
|
||||
|
||||
[sudo] password for enock:
|
||||
Reading package lists... Done
|
||||
Building dependency tree
|
||||
Reading state information... Done
|
||||
The following packages were automatically installed and are no longer required:
|
||||
gir1.2-gstreamer-0.10 libilmbase6 libmagickcore4 libmagickwand4 libcdt4
|
||||
libmagickcore4-extra liblqr-1-0 imagemagick-common libpathplan4 libopenexr6
|
||||
rsync netpbm libgvc5 libnetpbm10 libgraph4
|
||||
Use 'apt-get autoremove' to remove them.
|
||||
The following extra packages will be installed:
|
||||
gsfonts-x11 java-common
|
||||
Suggested packages:
|
||||
default-jre equivs binfmt-support visualvm ttf-baekmuk ttf-unfonts
|
||||
ttf-unfonts-core ttf-kochi-gothic ttf-sazanami-gothic ttf-kochi-mincho
|
||||
ttf-sazanami-mincho ttf-arphic-uming
|
||||
The following NEW packages will be installed:
|
||||
gsfonts-x11 java-common oracle-java7-installer
|
||||
0 upgraded, 3 newly installed, 0 to remove and 196 not upgraded.
|
||||
Need to get 88.5 kB of archives.
|
||||
After this operation, 473 kB of additional disk space will be used.
|
||||
Do you want to continue [Y/n]?
|
||||
|
||||
6. 输入代表Yes的**Y**以及回车键继续安装。
|
||||
|
||||
7. 在安装过程中,你需要同意条款才能继续。选择**OK**。
|
||||
|
||||

|
||||
|
||||
8. 然后选择**Yes**继续。
|
||||
|
||||

|
||||
|
||||
9. 现在请等待安装包的下载与自动安装:
|
||||
|
||||

|
||||
|
||||
10. 安装完成。你可以在终端上查看Java版本:
|
||||
|
||||
$ java -version
|
||||
java version "1.7.0_45"
|
||||
Java(TM) SE Runtime Environment (build 1.7.0_45-b18)
|
||||
Java HotSpot(TM) 64-Bit Server VM (build 24.45-b08, mixed mode)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/install-oracle-java-7-elementary-os-luna-via-ppa/
|
||||
|
||||
译者:[whatever1992](https://github.com/whatever1992) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,252 @@
|
||||
Linux中打印系统中USB信息的lsusb命令
|
||||
================================================================================
|
||||
**通用串行总线**或者**USB**被设计成为连接计算机外设的标准,如键盘、定位装置、打印机、数码相机、便携式媒体播放器、磁盘和网络适配器等等 - 来源:[Wikipedia][1]
|
||||
|
||||

|
||||
|
||||
既然它成为了一个工业标准,那么现在很难看到一个没有USB口的计算机了。USB闪存的使用使得它更加流行。在Linux上,我们使用**lsusb**来列出USB设备和它的属性。
|
||||
|
||||
### lsusb是什么 ###
|
||||
|
||||
从它的手册上,lsusb定义成:
|
||||
|
||||
显示系统中和连接到系统的USB总线信息的工具。
|
||||
|
||||
如何运行lsusb。
|
||||
|
||||
要运行lsusb,你可以直接在控制台输入lsusb。
|
||||
|
||||
$ lsusb
|
||||
|
||||
Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
|
||||
Bus 002 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
|
||||
Bus 003 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
|
||||
Bus 004 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
|
||||
Bus 005 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
|
||||
Bus 006 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
|
||||
Bus 007 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
|
||||
Bus 008 Device 001: ID 1d6b:0001 Linux Foundation 1.1 root hub
|
||||
Bus 002 Device 003: ID 17ef:4811 Lenovo Integrated Webcam [R5U877]
|
||||
Bus 008 Device 002: ID 0a5c:217f Broadcom Corp. Bluetooth Controller
|
||||
|
||||
**lsusb**会显示驱动和内部连接到你系统的设备。
|
||||
|
||||
这是如何理解输出。我抓取了上面输出的最后一行:
|
||||
|
||||
#### Bus 008 Device 002 : ID 0a5c:217f Broadcom Corp. Bluetooth Controller ####
|
||||
|
||||
- **Bus 008** : 设备连接的地方
|
||||
- **Device 002** : 连接到总线上的第二台设备
|
||||
- **ID** : 设备的ID
|
||||
- **Broadcom Corp**. Bluetooth Controller :生产商名字和设备名
|
||||
|
||||
我们同样可以看到在我们的系统中同时使用了USB2.0 root hub驱动和USB 1.1 root hub驱动。
|
||||
|
||||
用[dmsg][2]命令同样可以看到。下面是一个例子。
|
||||
|
||||
$ dmesg |grep -i usb
|
||||
|
||||
[ 0.353138] usbcore: registered new interface driver usbfs
|
||||
[ 0.353150] usbcore: registered new interface driver hub
|
||||
[ 0.353182] usbcore: registered new device driver usb
|
||||
[ 0.730026] ehci_hcd: USB 2.0 ‘Enhanced’ Host Controller (EHCI) Driver
|
||||
[ 0.730116] ehci_hcd 0000:00:1a.7: new USB bus registered, assigned bus number 1
|
||||
[ 0.748019] ehci_hcd 0000:00:1a.7: USB 2.0 started, EHCI 1.00
|
||||
[ 0.748169] hub 1-0:1.0: USB hub found
|
||||
[ 0.748336] ehci_hcd 0000:00:1d.7: new USB bus registered, assigned bus number 2
|
||||
[ 0.768019] ehci_hcd 0000:00:1d.7: USB 2.0 started, EHCI 1.00
|
||||
[ 0.768147] hub 2-0:1.0: USB hub found
|
||||
[ 0.768236] ohci_hcd: USB 1.1 ‘Open’ Host Controller (OHCI) Driver
|
||||
[ 0.768251] uhci_hcd: USB Universal Host Controller Interface driver
|
||||
|
||||
### 如何列出USB详细信息 ###
|
||||
|
||||
使用**-v**选项来开启。下面是一个例子。
|
||||
|
||||
$ lsusb -v
|
||||
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 1
|
||||
bAlternateSetting 5
|
||||
bNumEndpoints 2
|
||||
bInterfaceClass 224 Wireless
|
||||
bInterfaceSubClass 1 Radio Frequency
|
||||
bInterfaceProtocol 1 Bluetooth
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0×83 EP 3 IN
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0×0040 1x 64 bytes
|
||||
bInterval 1
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0×03 EP 3 OUT
|
||||
bmAttributes 1
|
||||
Transfer Type Isochronous
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0×0040 1x 64 bytes
|
||||
bInterval 1
|
||||
|
||||
### 找出连接了多少USB设备 ###
|
||||
|
||||
使用上面的命令来找到
|
||||
|
||||
$ find /dev/bus
|
||||
|
||||
接着你会看到像下面的输出:
|
||||
|
||||
/dev/bus
|
||||
/dev/bus/usb
|
||||
/dev/bus/usb/008
|
||||
/dev/bus/usb/008/002
|
||||
/dev/bus/usb/008/001
|
||||
/dev/bus/usb/007
|
||||
/dev/bus/usb/007/001
|
||||
/dev/bus/usb/006
|
||||
/dev/bus/usb/006/001
|
||||
/dev/bus/usb/005
|
||||
/dev/bus/usb/005/001
|
||||
/dev/bus/usb/004
|
||||
/dev/bus/usb/004/001
|
||||
/dev/bus/usb/003
|
||||
/dev/bus/usb/003/001
|
||||
/dev/bus/usb/002
|
||||
/dev/bus/usb/002/004
|
||||
/dev/bus/usb/002/003
|
||||
/dev/bus/usb/002/001
|
||||
/dev/bus/usb/001
|
||||
/dev/bus/usb/001/001
|
||||
|
||||
使用**lsusb** 命令 **紧接 -D** 选项,你可以打印特定设备的详细信息。下面是一个博通蓝牙设备的示例。
|
||||
|
||||
$ lsusb -D /dev/bus/usb/008/002
|
||||
|
||||
Device: ID 0a5c:217f Broadcom Corp. Bluetooth Controller
|
||||
Couldn’t open device, some information will be missing
|
||||
Device Descriptor:
|
||||
bLength 18
|
||||
bDescriptorType 1
|
||||
bcdUSB 2.00
|
||||
bDeviceClass 224 Wireless
|
||||
bDeviceSubClass 1 Radio Frequency
|
||||
bDeviceProtocol 1 Bluetooth
|
||||
bMaxPacketSize0 64
|
||||
idVendor 0x0a5c Broadcom Corp.
|
||||
idProduct 0x217f Bluetooth Controller
|
||||
bcdDevice 3.60
|
||||
iManufacturer 1
|
||||
iProduct 2
|
||||
iSerial 3
|
||||
bNumConfigurations 1
|
||||
Configuration Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 2
|
||||
wTotalLength 216
|
||||
bNumInterfaces 4
|
||||
bConfigurationValue 1
|
||||
iConfiguration 0
|
||||
bmAttributes 0xe0
|
||||
Self Powered
|
||||
Remote Wakeup
|
||||
MaxPower 0mA
|
||||
Interface Descriptor:
|
||||
bLength 9
|
||||
bDescriptorType 4
|
||||
bInterfaceNumber 0
|
||||
bAlternateSetting 0
|
||||
bNumEndpoints 3
|
||||
bInterfaceClass 224 Wireless
|
||||
bInterfaceSubClass 1 Radio Frequency
|
||||
bInterfaceProtocol 1 Bluetooth
|
||||
iInterface 0
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0×81 EP 1 IN
|
||||
bmAttributes 3
|
||||
Transfer Type Interrupt
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0×0010 1x 16 bytes
|
||||
bInterval 1
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0×82 EP 2 IN
|
||||
bmAttributes 2
|
||||
Transfer Type Bulk
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0×0040 1x 64 bytes
|
||||
bInterval 1
|
||||
Endpoint Descriptor:
|
||||
bLength 7
|
||||
bDescriptorType 5
|
||||
bEndpointAddress 0×02 EP 2 OUT
|
||||
bmAttributes 2
|
||||
Transfer Type Bulk
|
||||
Synch Type None
|
||||
Usage Type Data
|
||||
wMaxPacketSize 0×0040 1x 64 bytes
|
||||
bInterval 1
|
||||
|
||||
### 找出大容量存储设备 ###
|
||||
|
||||
既然 **lsusb -v**给我们很详细的信息,那么你或许会错过一些信息。我们可以使用grep命令指定特定的信息。
|
||||
|
||||
大容量存储设备会有一个供应商名和ID。我们可以用它作为一个起点。
|
||||
|
||||
$ lsusb -v |grep -Ei ‘(idVendor|Mass\ Storage)’
|
||||
|
||||
idVendor 0×1005 Apacer Technology, Inc.
|
||||
bInterfaceClass 8 Mass Storage
|
||||
|
||||
你可以看到,我们系统上有一个来自Apacer Technology, Inc的USB大容量存储设备。
|
||||
|
||||
### 以树层级结构输出USB设备 ###
|
||||
|
||||
使用 **-t**选项满足这个要求
|
||||
|
||||
$ lsusb -t
|
||||
|
||||
/: Bus 08.Port 1: Dev 1, Class=root_hub, Driver=uhci_hcd/2p, 12M
|
||||
/: Bus 07.Port 1: Dev 1, Class=root_hub, Driver=uhci_hcd/2p, 12M
|
||||
/: Bus 06.Port 1: Dev 1, Class=root_hub, Driver=uhci_hcd/2p, 12M
|
||||
/: Bus 05.Port 1: Dev 1, Class=root_hub, Driver=uhci_hcd/2p, 12M
|
||||
/: Bus 04.Port 1: Dev 1, Class=root_hub, Driver=uhci_hcd/2p, 12M
|
||||
/: Bus 03.Port 1: Dev 1, Class=root_hub, Driver=uhci_hcd/2p, 12M
|
||||
/: Bus 02.Port 1: Dev 1, Class=root_hub, Driver=ehci_hcd/6p, 480M
|
||||
|__ Port 1: Dev 4, If 0, Class=stor., Driver=usb-storage, 480M
|
||||
|__ Port 6: Dev 3, If 0, Class=’bInterfaceClass 0x0e not yet handled’, Driver=uvcvideo, 480M
|
||||
|__ Port 6: Dev 3, If 1, Class=’bInterfaceClass 0x0e not yet handled’, Driver=uvcvideo, 480M
|
||||
/: Bus 01.Port 1: Dev 1, Class=root_hub, Driver=ehci_hcd/6p, 480M
|
||||
|
||||
数字**12M和480M** 是**指USB类型的传输速率**。
|
||||
|
||||
- 12M 意味着 USB 1.0 / 1.1的速率是 12Mbit/s
|
||||
- 480M 意味着 USB 2.0的速率是 480Mbit/s
|
||||
|
||||
如果你找到5.0G,那意味这你有USB 3.0类型接口。它有5.0Gbit/s的传输速率。Linux从**/var/lib/usbutils/usb.ids**识别USB设备的详细信息。
|
||||
|
||||
这些就是lsusb命令的基础。你可以用lsusb命令追你的系统上的USB设备做一个诊断。一般来说,你可以通过lsusb的手册探索命令的更多详细细节。只要输入**man lsab**来打开它的手册。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/linux-lsusb-command-print-usb/
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://en.wikipedia.org/wiki/USB
|
||||
[2]:http://linoxide.com/linux-command/linux-dmesg-command/
|
||||
[3]:http://www.linux-usb.org/usb.ids
|
||||
@ -0,0 +1,49 @@
|
||||
Linux系统 whoami 命令 – 知晓当前登陆用户
|
||||
================================================================================
|
||||
通常,在控制台的命令提示符下你会发现 **用户名已经被显示出来** 。但有一些 shell, 比如 **csh**, 默认情况下是不会显示你的用户名的。所以这个命令最应该用在那些不能回显用户名的 shell 终端上。
|
||||
|
||||
### 怎么样使用 whoami ###
|
||||
|
||||
要使用这个命令,仅仅只需要输入 whoami 。下面的例子中我们使用的是 chs shell 终端。
|
||||
|
||||
% whoami
|
||||
|
||||

|
||||
|
||||
### Whoami 的参数选项 ###
|
||||
|
||||
这个命令仅仅只有两个参数选项: **–help** 和 **–version**。
|
||||
|
||||
% whoamin –help
|
||||
|
||||

|
||||
|
||||
下面这选项会输出和 **man whoami** 命令一样的信息
|
||||
|
||||
% whoami –version
|
||||
|
||||

|
||||
|
||||
不同的是 **–version** 会显示你系统上的 whoami 命令的版本信息
|
||||
|
||||
### 相似性 ###
|
||||
|
||||
whoami 命令和 **id -un** 有相同的输出。它们都打印出当前用户的用户名。
|
||||
|
||||
% id -un
|
||||
|
||||

|
||||
|
||||
### 结论 ###
|
||||
|
||||
whoami 命令也用于当你使用 su 命令(切换用户)时, 它能让你确认出你登陆的用户是否正确。 whoami 跟 who 命令不相同, who 命令会显示所有已经登陆的用户名,而 whoami 不是。当你切换用户时, whoami 命令会显示会话所属的当前用户,而 who 命令会显示你切换前的那个源用户。
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/linux-whoami-command/
|
||||
|
||||
译者:[runningwater](https://github.com/runningwater) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,30 @@
|
||||
高级研究员分析 LibreOffice 得出有趣结论
|
||||
================================================================================
|
||||
用户、编辑、国家机关、团队以及城市管理部门都正享用着 [LibreOffice][1] 这样一套免费的开源办公套件。而这款办公套件也通过与日俱增的用户数量和积极的反馈证明了自身的成功。
|
||||
|
||||
用户们不仅感受到 LibreOffice 的不妥协和强大之处,通过“分支之后开源软件社区的可持续发展:LibreOffice 是如何演变的?为什么?”这一文档,认真的研究人员似乎还发现并且把 LibreOffice 描述为真正的成功。
|
||||
|
||||
本质上来说。“分支之后开源软件社区的可持续发展:LibreOffice 是如何演变的?为什么?”是一篇研究 LibreOffice 和它的组成的文档,其中涉及研究的组成部分包括从有声望者到公众的看法、未来的功能、吸引支持者和参与者的能力。
|
||||
|
||||
上述提到的文档得到的结论,自然而然地谈到 LibreOffice 在各个方面的成功,例如:
|
||||
|
||||
- “LibreOffice 项目是 OpenOffice.org 项目的一个分支,并没有显示出长期衰退的迹象。”
|
||||
- “在 OpenOffice.org 中,LibreOffice 吸引了许许多多长期并且非常活跃的提交者。”
|
||||
- “开源社区比开源软件项目长寿”
|
||||
- “LibreOffice 被它的社区视为是可支持的、多元化的和独立的”
|
||||
|
||||

|
||||
|
||||
这份由 Skövde 大学信息研究中心高级研究人员编写的长达60页的文档(可以在[http://www.sciencedirect.com/science/article/pii/S0164121213002744/pdfft...][3]下载)为 LibreOffice 这套强大的办公套件提供了详尽的、深入且精准的分析。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://iloveubuntu.net/senior-researchers-analyzed-libreoffice-interesting-conclusions
|
||||
|
||||
译者:[hyaocuk](https://github.com/hyaocuk) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.libreoffice.org/
|
||||
[2]:http://www.sciencedirect.com/science/article/pii/S0164121213002744
|
||||
[3]:http://www.sciencedirect.com/science/article/pii/S0164121213002744/pdfft?md5=4b986a117fb06cc127b854cb5f622bec&pid=1-s2.0-S0164121213002744-main.pdf
|
||||
@ -1,16 +1,14 @@
|
||||
translating by zsJacky
|
||||
|
||||
在openSUSE 13.1中配置FTP服务器
|
||||
================================================================================
|
||||
**vsftpd** (**非常****安全的****文件****传输****协议****守护进程**) 是Unix/Linux系统中的一个安全快速的FTP服务器。 在这篇 how-to 文章中,让我们看看在openSUSE 13.1中怎样使用vsftpd来配置一个基本的FTP服务器。
|
||||
**vsftpd** ( **非常安全的文件传输协议守护进程**) 是Unix/Linux系统中的一个安全快速的FTP服务器。 在这篇指导教程中,让我们看看在openSUSE 13.1中怎样使用vsftpd来配置一个基本的FTP服务器。
|
||||
|
||||
### 安装 vsftpd ###
|
||||
|
||||
作为root用户登录然后输入以下的命令。
|
||||
作为root用户登录然后输入以下命令。
|
||||
|
||||
# zypper in vsftpd
|
||||
|
||||
启动 vsftpd 服务然后设置让它在每次系统重启时自动启动
|
||||
启动 vsftpd 服务然后通过设置使它在每次系统重启时自动启动。
|
||||
|
||||
# systemctl enable vsftpd.service
|
||||
# systemctl start vsftpd.service
|
||||
@ -21,11 +19,11 @@ translating by zsJacky
|
||||
|
||||
# mkdir /srv/ftp
|
||||
|
||||
创建一个叫 **ftp-users** 的组。
|
||||
创建一个名为 **ftp-users** 的组。
|
||||
|
||||
# groupadd ftp-users
|
||||
|
||||
让我们来创建一个叫unixmen的示例用户 并设置其主目录为 **/srv/ftp** 组为**ftp-users**。
|
||||
让我们来创建一个叫unixmen的示例用户 并设置其主目录为 **/srv/ftp** 组为 **ftp-users** 。
|
||||
|
||||
# useradd -g ftp-users -d /srv/ftp/ unixmen
|
||||
|
||||
@ -33,7 +31,7 @@ translating by zsJacky
|
||||
|
||||
# passwd unixmen
|
||||
|
||||
使ftp主目录 **/srv/ftp/** 可以被ftp用户所访问。
|
||||
使ftp主目录 **/srv/ftp/** 可以被ftp用户所访问。
|
||||
|
||||
# chmod 750 /srv/ftp/
|
||||
# chown unixmen:ftp-users /srv/ftp/
|
||||
@ -71,7 +69,7 @@ translating by zsJacky
|
||||
|
||||
### 测试本地FTP服务器 ###
|
||||
|
||||
首先 让我们按如下步骤尝试登陆FTP服务器
|
||||
首先 让我们按如下步骤尝试登录FTP服务器
|
||||
|
||||
# ftp localhost
|
||||
Trying ::1:21 ...
|
||||
@ -85,10 +83,10 @@ translating by zsJacky
|
||||
Using binary mode to transfer files.
|
||||
ftp>
|
||||
|
||||
正如你在上面所输出的那样, 我们将能够用unixmen用户登录到ftp服务器。
|
||||
正如你在上面所输出的那样, 我们能够用unixmen用户登录到ftp服务器。
|
||||
### 测试远程FTP服务器 ###
|
||||
|
||||
默认地 openSUSE内置的防火墙不允许从远程系统登陆FTP。所以让我们允许vsftpd服务通过suse的防火墙。然后我们需要打开: **Yast -> 安全性与用户 -> 防火墙**.
|
||||
默认 openSUSE 内置的防火墙不允许远程系统登录FTP。所以让我们允许vsftpd服务通过suse的防火墙。然后我们需要打开: **Yast -> 安全性与用户 -> 防火墙**.
|
||||
|
||||

|
||||
|
||||
@ -113,7 +111,7 @@ translating by zsJacky
|
||||
Using binary mode to transfer files.
|
||||
ftp>
|
||||
|
||||
正如你在上面输出中所看到的,我将能够连接到ftp服务器。如果不允许vsftpd服务通过防火墙, 你将会得到一个连接超时的错误。
|
||||
正如你在上面输出中所看到的,我能够连接到ftp服务器。如果不允许vsftpd服务通过防火墙,你将会得到一个连接超时的报错。
|
||||
|
||||
### 从浏览器连接 ###
|
||||
|
||||
@ -125,7 +123,7 @@ translating by zsJacky
|
||||
|
||||
对于新手来说,在命令行模式下工作可能会很烦恼。所以让我们来安装一个叫[**Filezilla**][1]的图形化的FTP客户端。它可以让我们登陆FTP变得更加简单:
|
||||
|
||||
几乎所有的发行版在他们的官方软件仓库中都有filezilla客户端。 为了在基于Linux的系统上安装filezilla 需要键入以下的命令:
|
||||
几乎所有的发行版在它们的官方软件仓库中都有filezilla客户端。 为了在基于Linux的系统上安装filezilla 需要键入以下的命令:
|
||||
|
||||
在基于Ubuntu的系统中:
|
||||
|
||||
@ -134,11 +132,12 @@ translating by zsJacky
|
||||
在Fedora/Redhat系统中:
|
||||
|
||||
$ sudo yum install filezilla
|
||||
|
||||
在openSUSE中:
|
||||
|
||||
# zypper in filezilla
|
||||
|
||||
安装完fielzilla后打开它。输入ftp服务器的IP地址,用户名和密码,然后点击快速链接。
|
||||
安装完fielzilla后打开它。输入ftp服务器的IP地址、用户名和密码,然后点击快速连接。
|
||||
|
||||

|
||||
|
||||
@ -161,7 +160,7 @@ translating by zsJacky
|
||||
|
||||
nano /etc/vsftpd.chroot_list
|
||||
|
||||
添加你希望其能够访问FTP服务器的用户。我添加了用户**unixmen**。
|
||||
添加你希望能够访问FTP服务器的用户。我添加了用户**unixmen**。
|
||||
|
||||
unixmen
|
||||
|
||||
@ -169,21 +168,21 @@ translating by zsJacky
|
||||
|
||||
# systemctl restart vsftpd.service
|
||||
|
||||
现在你将能够使用chroot_list文件中列出的用户来连接到FTP服务器。
|
||||
现在你能够使用chroot_list文件中列出的用户来连接到FTP服务器。
|
||||
|
||||
如果chroot_list以外的用户想访问FTP服务器, 他们将得到如下的错误。
|
||||
如果chroot_list以外的用户想访问FTP服务器,他们将得到如下错误提示。
|
||||
|
||||
500 OOPS: could not read chroot() list file:/etc/vsftpd.chroot_list
|
||||
ftp: Login failed
|
||||
|
||||
现在就是这样。 你的FTP服务器已经可以使用了。 享受吧!
|
||||
就是现在这样,你的FTP服务器已经可以使用了,好好享受吧!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/setup-ftp-server-opensuse-13-1/
|
||||
|
||||
译者:[zsJacky](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[zsJacky](https://github.com/译者ID) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://filezilla-project.org/
|
||||
[1]:https://filezilla-project.org/
|
||||
|
||||
@ -1,266 +0,0 @@
|
||||
在Ubuntu下用jailkit建立一个被监禁的Shell
|
||||
|
||||
================================================================================
|
||||
|
||||
### Jailkit和jailed Shell ###
|
||||
|
||||
监狱性的shell是一类限制性的shell,提供给用户非常真实的Shell模样,但是不允许它查看和修改真正的文件系统。Shell内的文件系统不同于底层的文件系统。这种功能是通过chroot和其他多种程序实现的。举例来说,建立一个用户的linux shell可能仅仅为了玩耍。或者在一个限定的环境里运行一些程序的所有功能等。
|
||||
|
||||
在这个教程里我们将会探讨在Ubuntu下用jailkit建立一个监禁的shell。Jailkit是辅助程序,允许快速的建立一个监禁的shell,监禁的用户,在受监禁的环境里配置程序并运行。
|
||||
|
||||
Jailkit can be downloaded from [http://olivier.sessink.nl/jailkit/][1]
|
||||
|
||||
我们已经谈论过关于在Ubuntu下安装jailkit,如果有不懂,多看看那篇文章。
|
||||
|
||||
### 配置jailed Shell ###
|
||||
|
||||
#### 配置jail环境 ####
|
||||
|
||||
我们需要建立一个目录来存放所有jail环境的配置。这不是重点,我们可以创建个/opt/jail的目录。
|
||||
|
||||
$ sudo mkdir /opt/jail
|
||||
|
||||
这个目录应为Root所有。所以用chown。
|
||||
|
||||
$ sudo chown root:root /opt/jail
|
||||
|
||||
#### 2. 设置在jail中可用的程序 ####
|
||||
|
||||
任何程序想要在jail中执行则必须用jk_init命令拷贝到目录中。
|
||||
|
||||
例如:
|
||||
|
||||
$ sudo jk_init -v /jail basicshell
|
||||
|
||||
$ sudo jk_init -v /jail editors
|
||||
|
||||
$ sudo jk_init -v /jail extendedshell
|
||||
|
||||
$ sudo jk_init -v /jail netutils
|
||||
|
||||
$ sudo jk_init -v /jail ssh
|
||||
|
||||
$ sudo jk_init -v /jail sftp
|
||||
|
||||
$ sudo jk_init -v /jail jk_lsh
|
||||
|
||||
或一次性解决:
|
||||
|
||||
$ sudo jk_init -v /opt/jail netutils basicshell jk_lsh openvpn ssh sftp
|
||||
|
||||
像basicshell, editors, netutils是一些组名,其中包含多个程序。复制到jail shell中的每个组都是可执行文件,库文件等的集合。比如**basicshell**就在jail提供有bash, ls, cat, chmod, mkdir, cp, cpio, date, dd, echo, egrep等程序。
|
||||
|
||||
完整的程序列表设置,你可以在/etc/jailkit/jk_init.ini中查看。
|
||||
|
||||
jk_lsh (Jailkit limited shell) - is an important section, and must be added.
|
||||
|
||||
#### 3. 创建将被监禁的用户 ####
|
||||
|
||||
需要将用户放入jail里。可以先创建一个
|
||||
|
||||
$ sudo adduser robber
|
||||
|
||||
Adding user `robber' ...
|
||||
|
||||
Adding new group `robber' (1005) ...
|
||||
|
||||
Adding new user `robber' (1006) with group `robber' ...
|
||||
|
||||
Creating home directory `/home/robber' ...
|
||||
|
||||
Copying files from `/etc/skel' ...
|
||||
|
||||
Enter new UNIX password:
|
||||
|
||||
Retype new UNIX password:
|
||||
|
||||
passwd: password updated successfully
|
||||
|
||||
Changing the user information for robber
|
||||
|
||||
Enter the new value, or press ENTER for the default
|
||||
|
||||
Full Name []:
|
||||
|
||||
Room Number []:
|
||||
|
||||
Work Phone []:
|
||||
|
||||
Home Phone []:
|
||||
|
||||
Other []:
|
||||
|
||||
Is the information correct? [Y/n] y
|
||||
|
||||
注意:目前创建的是一个活动在文件系统中的普通用户并没有添加到jail中。
|
||||
|
||||
在下一步这个用户会被监禁在jail里。
|
||||
|
||||
这时候如果你查看/etc/passwd文件,你会在文件最后看到跟下面差不多的一个条目。
|
||||
|
||||
robber:x:1006:1005:,,,:/home/robber:/bin/bash
|
||||
|
||||
这是我们新创建的用户,最后部分的/bin/bash指示了这个用户如果登入了那么它可以在系统上正常的Shell访问
|
||||
|
||||
#### 4. 监禁用户 ####
|
||||
|
||||
现在是时候将用户监禁在jail中
|
||||
|
||||
$ sudo jk_jailuser -m -j /opt/jail/ robber
|
||||
|
||||
执行上列命令后,用户robber将会被监禁。
|
||||
|
||||
如果你现在再观察/etc/passwd文件,会发现类似下面的最后条目。
|
||||
|
||||
robber:x:1006:1005:,,,:/opt/jail/./home/robber:/usr/sbin/jk_chrootsh
|
||||
|
||||
注意:最后两部分表明用户主目录和shell类型已经被改变了。现在用户的主目录在/opt/jail(jail环境)中。用户的Shell是一个名叫jk_chrootsh的特殊程序,会提供jailed Shell。
|
||||
|
||||
jk_chrootsh这是个特殊的shell,每当用户登入系统时,它都会将用户放入jail中。
|
||||
|
||||
到目前为止jail配置已经几乎完成了。但是如果你试图用ssh连接,那么注定会失败,像这样:
|
||||
|
||||
$ ssh robber@localhost
|
||||
|
||||
robber@localhost's password:
|
||||
|
||||
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-25-generic x86_64)
|
||||
|
||||
* Documentation: https://help.ubuntu.com/
|
||||
|
||||
13 packages can be updated.
|
||||
|
||||
0 updates are security updates.
|
||||
|
||||
*** /dev/sda7 will be checked for errors at next reboot ***
|
||||
|
||||
*** /dev/sda8 will be checked for errors at next reboot ***
|
||||
|
||||
Last login: Sat Jun 23 12:45:13 2012 from localhost
|
||||
|
||||
Connection to localhost closed.
|
||||
|
||||
$
|
||||
|
||||
连接会立马关闭,这意味着用户已经活动在一个受限制的shell中。
|
||||
|
||||
#### 5. 给在jail中的用户Bash Shell ####
|
||||
|
||||
下个重要的事情是给用户一个正确的bash shell,但是他却在jail中。
|
||||
|
||||
打开下面的文件
|
||||
|
||||
/opt/jail/etc/passwd
|
||||
|
||||
这是个jail中的password文件。类似如下
|
||||
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
|
||||
robber:x:1006:1005:,,,:/home/robber:/usr/sbin/jk_lsh
|
||||
|
||||
将/usr/sbin/jk_lsh改为/bin/bash
|
||||
|
||||
root:x:0:0:root:/root:/bin/bash
|
||||
|
||||
robber:x:1006:1005:,,,:/home/robber:/bin/bash
|
||||
|
||||
保存文件并退出。
|
||||
|
||||
#### 6. 登入jail ####
|
||||
|
||||
现在让我们再次登入jail
|
||||
|
||||
$ ssh robber@localhost
|
||||
|
||||
robber@localhost's password:
|
||||
|
||||
Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-25-generic x86_64)
|
||||
|
||||
* Documentation: https://help.ubuntu.com/
|
||||
|
||||
13 packages can be updated.
|
||||
|
||||
0 updates are security updates.
|
||||
|
||||
*** /dev/sda7 will be checked for errors at next reboot ***
|
||||
|
||||
*** /dev/sda8 will be checked for errors at next reboot ***
|
||||
|
||||
Last login: Sat Jun 23 12:46:01 2012 from localhost
|
||||
|
||||
bash: groups: command not found
|
||||
|
||||
I have no name!@desktop:~$
|
||||
|
||||
jail说'I have no name!',哈哈。现在我们在jail中有个完整功能的bash shell。
|
||||
|
||||
现在通过操作检查环境。jail中的root /实际就是真实文件系统中的/opt/jail.但这只有我们自己知道,jail用户并不知情。
|
||||
|
||||
I have no name!@desktop:~$ cd /
|
||||
|
||||
I have no name!@desktop:/$ ls
|
||||
|
||||
bin dev etc home lib lib64 run usr var
|
||||
|
||||
I have no name!@desktop:/$
|
||||
|
||||
也只有我们通过jk_cp拷贝到jail中的命令能使用。
|
||||
|
||||
如果登入失败,请检查一下/var/log/auth.log的错误信息。
|
||||
|
||||
现在尝试运行一些网络命令,类似wget的命令。
|
||||
|
||||
$ wget http://www.google.com/
|
||||
|
||||
如果你获得类似的错误提示:
|
||||
|
||||
$ wget http://www.google.com/
|
||||
|
||||
--2012-06-23 12:56:43-- http://www.google.com/
|
||||
|
||||
Resolving www.google.com (www.google.com)... failed: Name or service not known.
|
||||
|
||||
wget: unable to resolve host address `www.google.com'
|
||||
|
||||
你可以通过运行下列两条命令来解决这个问题:
|
||||
|
||||
$ sudo jk_cp -v -j /opt/jail /lib/x86_64-linux-gnu/libnss_files.so.2
|
||||
|
||||
$ sudo jk_cp -v -j /opt/jail /lib/x86_64-linux-gnu/libnss_dns.so.2
|
||||
|
||||
这样才能正确的定位到libnss_files.so和libnss_dns.so
|
||||
|
||||
### 在jail中运行程序或服务 ###
|
||||
|
||||
此时此刻配置已经完成了。Jails可以在限制/安全的环境里运行程序或服务。用**jk_chrootlaunch**命令在jail中启动一个程序或守护进程。
|
||||
|
||||
$ sudo jk_chrootlaunch -j /opt/jail -u robber -x /some/command/in/jail
|
||||
|
||||
jk_chrootlaunch工具可以在jail环境中启动一个特殊的进程同时指定用户特权。如果守护进程启动失败,请检查/var/log/syslog/错误信息。
|
||||
|
||||
在jail中运行程序之前,该程序必须已经用jk_cp命令复制到jail中。
|
||||
|
||||
jk_cp - 将文件包括权限信息和库文件复制到jail的工具
|
||||
|
||||
进一步阅读有关其他jailkit命令信息,可以阅读文档,[http://olivier.sessink.nl/jailkit/][1]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.binarytides.com/setup-jailed-shell-jailkit-ubuntu/
|
||||
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://olivier.sessink.nl/jailkit/
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
Loading…
Reference in New Issue
Block a user