mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-24 02:20:09 +08:00
commit
43f6a9b936
sources/tech
20151109 How to send email notifications using Gmail SMTP server on Linux.md20151208 How to Install Bugzilla with Apache and SSL on FreeBSD 10.2.md20151215 Fix--Cannot establish FTP connection to an SFTP server.md20151215 How to Install Light Table 0.8 in Ubuntu 14.04, 15.10.md20151215 How to block network traffic by country on Linux.md20151215 How to enable Software Collections (SCL) on CentOS.md20151215 Linux Desktop Fun--Summon Swarms Of Penguins To Waddle About The Desktop.md20151215 Linux or UNIX Desktop Fun--Let it Snow On Your Desktop.md20151215 Linux or UNIX Desktop Fun--Steam Locomotive.md20151215 Linux or UNIX Desktop Fun--Terminal ASCII Aquarium.md20151215 Linux or Unix Desktop Fun--Cat And Mouse Chase All Over Your Screen.md20151215 Linux or Unix Desktop Fun--Text Mode ASCII-art Box and Comment Drawing.md20151215 Securi-Pi--Using the Raspberry Pi as a Secure Landing Point.md
translated/tech
@ -1,3 +1,4 @@
|
||||
Translating by KnightJoker
|
||||
How to send email notifications using Gmail SMTP server on Linux
|
||||
================================================================================
|
||||
Suppose you want to configure a Linux app to send out email messages from your server or desktop. The email messages can be part of email newsletters, status updates (e.g., [Cachet][1]), monitoring alerts (e.g., [Monit][2]), disk events (e.g., [RAID mdadm][3]), and so on. While you can set up your [own outgoing mail server][4] to deliver messages, you can alternatively rely on a freely available public SMTP server as a maintenance-free option.
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by ZTinoZ
|
||||
How to Install Bugzilla with Apache and SSL on FreeBSD 10.2
|
||||
================================================================================
|
||||
Bugzilla is open source web base application for bug tracker and testing tool, develop by mozilla project, and licensed under Mozilla Public License. It is used by high tech company like mozilla, redhat and gnome. Bugzilla was originally created by Terry Weissman in 1998. It written in perl, use MySQL as the database back-end. It is a server software designed to help you manage software development. Bugzilla has a lot of features, optimized database, excellent security, advanced search tool, integrated with email capabilities etc.
|
||||
@ -264,4 +265,4 @@ via: http://linoxide.com/tools/install-bugzilla-apache-ssl-freebsd-10-2/
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arulm/
|
||||
[a]:http://linoxide.com/author/arulm/
|
||||
|
||||
@ -0,0 +1,49 @@
|
||||
Fix: Cannot establish FTP connection to an SFTP server
|
||||
================================================================================
|
||||
### Problem ###
|
||||
|
||||
The other day I had to connect to my web server. I use [FileZilla][1] for connecting to FTP servers. When I entered the hostname and password and tried to connect to the FTP server, it gave me the following error:
|
||||
|
||||
> Error: Cannot establish FTP connection to an SFTP server. Please select proper protocol.
|
||||
>
|
||||
> Error: Critical error: Could not connect to server
|
||||
|
||||

|
||||
|
||||
### Reason ###
|
||||
|
||||
By reading the error message itself made me realize my mistake. I was trying to establish an [FTP][2] connection with an [SFTP][3] server. Clearly, I was not using the correct protocol (which should have been SFTP and not FTP).
|
||||
|
||||
As you can see in the picture above, FileZilla defaults to FTP protocol.
|
||||
|
||||
### Solution for “Cannot establish FTP connection to an SFTP server” ###
|
||||
|
||||
Solution is simple. Use SFTP protocol instead of FTP. The one problem you might face is to know how to change the protocol to SFTP. This is where I am going to help you.
|
||||
|
||||
In FileZilla menu, go to **File->Site Manager**.
|
||||
|
||||

|
||||
|
||||
In the Site Manager, go in General tab and select SFTP in Protocol. Also fill in the host server, port number, user password etc.
|
||||
|
||||

|
||||
|
||||
I hope you can handle things from here onward.
|
||||
|
||||
I hope this quick tutorial helped you to fix “Cannot establish FTP connection to an SFTP server. Please select proper protocol.” problem. In related articles, you can read this post to [know how to set up FTP server in Linux][4].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/fix-establish-ftp-connection-sftp-server/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/abhishek/
|
||||
[1]:https://filezilla-project.org/
|
||||
[2]:https://en.wikipedia.org/wiki/File_Transfer_Protocol
|
||||
[3]:https://en.wikipedia.org/wiki/SSH_File_Transfer_Protocol
|
||||
[4]:http://itsfoss.com/set-ftp-server-linux/
|
||||
@ -0,0 +1,104 @@
|
||||
How to Install Light Table 0.8 in Ubuntu 14.04, 15.10
|
||||
================================================================================
|
||||

|
||||
|
||||
The Light Table IDE has just reached a new stable release after more than one year of development. Now it provides 64-bit only binary for Linux.
|
||||
|
||||
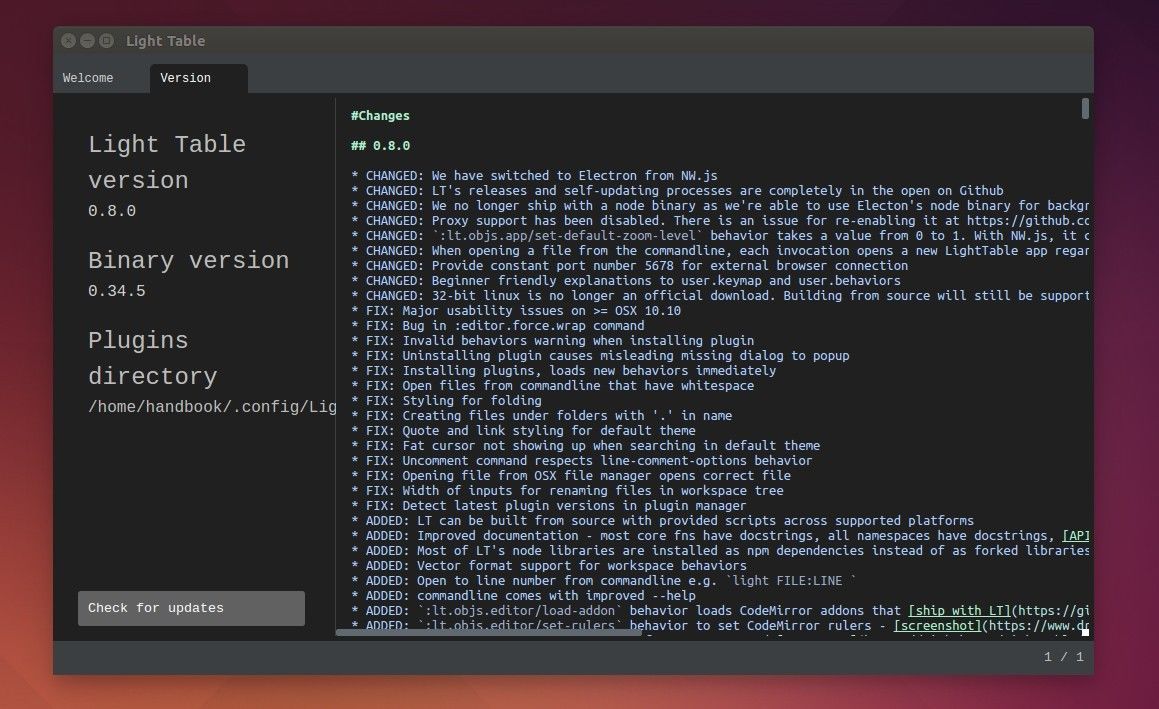
Changes in LightTable 0.8.0:
|
||||
|
||||
- CHANGED: We have switched to Electron from NW.js
|
||||
- CHANGED: LT’s releases and self-updating processes are completely in the open on Github
|
||||
- ADDED: LT can be built from source with provided scripts across supported platforms
|
||||
- ADDED: Most of LT’s node libraries are installed as npm dependencies instead of as forked libraries
|
||||
- ADDED: Significant documentation. See more below
|
||||
- FIX: Major usability issues on >= OSX 10.10
|
||||
- CHANGED: 32-bit linux is no longer an official download. Building from source will still be supported
|
||||
- FIX: ClojureScript eval for modern versions of ClojureScript
|
||||
- More details at [github.com/LightTable/LightTable/releases][1]
|
||||
|
||||
|
||||
|
||||
### How to Install Light Table 0.8.0 in Ubuntu: ###
|
||||
|
||||
Below steps show you how to install the official binary in Ubuntu. Works on all current Ubuntu releases (**64-bit only**).
|
||||
|
||||
Before getting started, please make a backup if you have a previous release installed.
|
||||
|
||||
**1.** Download the Linux binary from link below:
|
||||
|
||||
- [lighttable-0.8.0-linux.tar.gz][2]
|
||||
|
||||
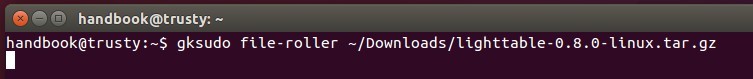
**2.** Open terminal from Unity Dash, App Launcher, or via Ctrl+Alt+T keys. When it opens, paste below command and hit enter:
|
||||
|
||||
gksudo file-roller ~/Downloads/lighttable-0.8.0-linux.tar.gz
|
||||
|
||||
|
||||
|
||||
Install `gksu` from Ubuntu Software Center if the command does not work.
|
||||
|
||||
**3.** Previous command opens the downloaded archive via Archive Manager using root user privilege.
|
||||
|
||||
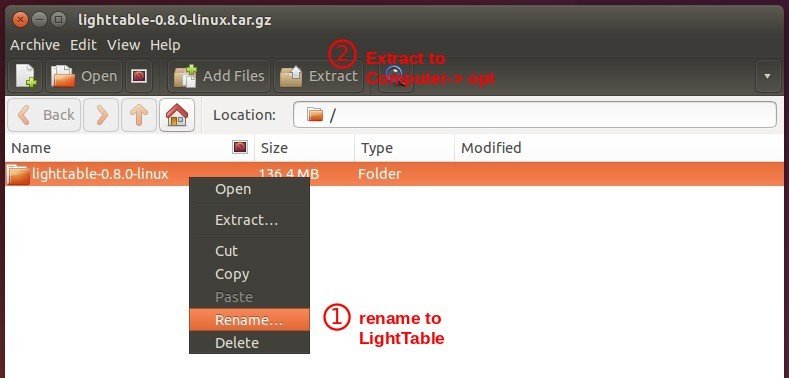
When it opens, do:
|
||||
|
||||
- right-click and rename the folder name to **LightTable**
|
||||
- extract it to **Computer -> /opt/** directory.
|
||||
|
||||
|
||||
|
||||
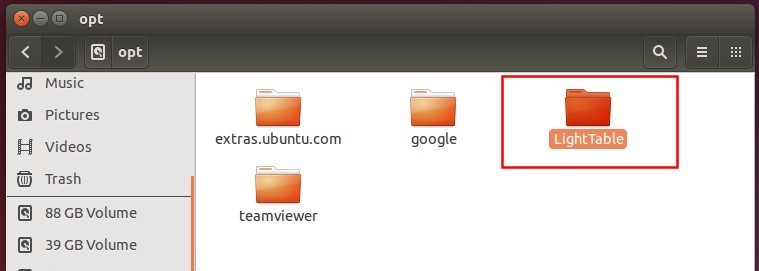
Finally you should have the LightTable installed to /opt/ directory:
|
||||
|
||||
|
||||
|
||||
**4.** Create a launcher so you can start LightTable from Unity Dash or App Launcher.
|
||||
|
||||
Open terminal and run below command to create & edit a launcher file for LightTable:
|
||||
|
||||
gksudo gedit /usr/share/applications/lighttable.desktop
|
||||
|
||||
When the file opens via Gedit text editor, paste below and save the file:
|
||||
|
||||
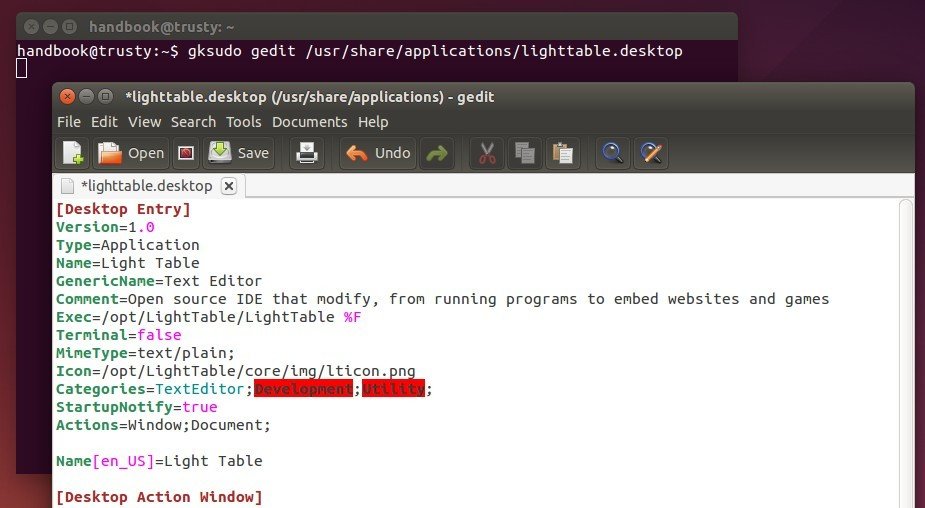
[Desktop Entry]
|
||||
Version=1.0
|
||||
Type=Application
|
||||
Name=Light Table
|
||||
GenericName=Text Editor
|
||||
Comment=Open source IDE that modify, from running programs to embed websites and games
|
||||
Exec=/opt/LightTable/LightTable %F
|
||||
Terminal=false
|
||||
MimeType=text/plain;
|
||||
Icon=/opt/LightTable/resources/app/core/img/lticon.png
|
||||
Categories=TextEditor;Development;Utility;
|
||||
StartupNotify=true
|
||||
Actions=Window;Document;
|
||||
|
||||
Name[en_US]=Light Table
|
||||
|
||||
[Desktop Action Window]
|
||||
Name=New Window
|
||||
Exec=/opt/LightTable/LightTable -n
|
||||
OnlyShowIn=Unity;
|
||||
|
||||
[Desktop Action Document]
|
||||
Name=New File
|
||||
Exec=/opt/LightTable/LightTable --command new_file
|
||||
OnlyShowIn=Unity;
|
||||
|
||||
So it looks like:
|
||||
|
||||
|
||||
|
||||
Finally launch the IDE from Unity Dash or Application Launcher and enjoy!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ubuntuhandbook.org/index.php/2015/12/install-light-table-0-8-ubuntu-14-04/
|
||||
|
||||
作者:[Ji m][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ubuntuhandbook.org/index.php/about/
|
||||
[1]:https://github.com/LightTable/LightTable/releases
|
||||
[2]:https://github.com/LightTable/LightTable/releases/download/0.8.0/lighttable-0.8.0-linux.tar.gz
|
||||
@ -0,0 +1,110 @@
|
||||
How to block network traffic by country on Linux
|
||||
================================================================================
|
||||
As a system admin who maintains production Linux servers, there are circumstances where you need to **selectively block or allow network traffic based on geographic locations**. For example, you are experiencing denial-of-service attacks mostly originating from IP addresses registered with a particular country. You want to block SSH logins from unknown foreign countries for security reasons. Your company has a distribution right to online videos, which requires it to legally stream to particular countries only. You need to prevent any local host from uploading documents to any non-US remote cloud storage due to geo-restriction company policies.
|
||||
|
||||
All these scenarios require an ability to set up a firewall which does **country-based traffic filtering**. There are a couple of ways to do that. For one, you can use TCP wrappers to set up conditional blocking for individual applications (e.g., SSH, NFS, httpd). The downside is that the application you want to protect must be built with TCP wrappers support. Besides, TCP wrappers are not universally available across different platforms (e.g., Arch Linux [dropped][2] its support). An alternative approach is to set up [ipset][3] with country-based GeoIP information and apply it to iptables rules. The latter approach is more promising as the iptables-based filtering is application-agnostic and easy to set up.
|
||||
|
||||
In this tutorial, I am going to present **another iptables-based GeoIP filtering which is implemented with xtables-addons**. For those unfamiliar with it, xtables-addons is a suite of extensions for netfilter/iptables. Included in xtables-addons is a module called xt_geoip which extends the netfilter/iptables to filter, NAT or mangle packets based on source/destination countries. For you to use xt_geoip, you don't need to recompile the kernel or iptables, but only need to build xtables-addons as modules, using the current kernel build environment (/lib/modules/`uname -r`/build). Reboot is not required either. As soon as you build and install xtables-addons, xt_geoip is immediately usable with iptables.
|
||||
|
||||
As for the comparison between xt_geoip and ipset, the [official source][3] mentions that xt_geoip is superior to ipset in terms of memory foot print. But in terms of matching speed, hash-based ipset might have an edge.
|
||||
|
||||
In the rest of the tutorial, I am going to show **how to use iptables/xt_geoip to block network traffic based on its source/destination countries**.
|
||||
|
||||
### Install Xtables-addons on Linux ###
|
||||
|
||||
Here is how you can compile and install xtables-addons on various Linux platforms.
|
||||
|
||||
To build xtables-addons, you need to install a couple of dependent packages first.
|
||||
|
||||
#### Install Dependencies on Debian, Ubuntu or Linux Mint ####
|
||||
|
||||
$ sudo apt-get install iptables-dev xtables-addons-common libtext-csv-xs-perl pkg-config
|
||||
|
||||
#### Install Dependencies on CentOS, RHEL or Fedora ####
|
||||
|
||||
CentOS/RHEL 6 requires EPEL repository being set up first (for perl-Text-CSV_XS).
|
||||
|
||||
$ sudo yum install gcc-c++ make automake kernel-devel-`uname -r` wget unzip iptables-devel perl-Text-CSV_XS
|
||||
|
||||
#### Compile and Install Xtables-addons ####
|
||||
|
||||
Download the latest `xtables-addons` source code from the [official site][4], and build/install it as follows.
|
||||
|
||||
$ wget http://downloads.sourceforge.net/project/xtables-addons/Xtables-addons/xtables-addons-2.10.tar.xz
|
||||
$ tar xf xtables-addons-2.10.tar.xz
|
||||
$ cd xtables-addons-2.10
|
||||
$ ./configure
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
Note that for Red Hat based systems (CentOS, RHEL, Fedora) which have SELinux enabled by default, it is necessary to adjust SELinux policy as follows. Otherwise, SELinux will prevent iptables from loading xt_geoip module.
|
||||
|
||||
$ sudo chcon -vR --user=system_u /lib/modules/$(uname -r)/extra/*.ko
|
||||
$ sudo chcon -vR --type=lib_t /lib64/xtables/*.so
|
||||
|
||||
### Install GeoIP Database for Xtables-addons ###
|
||||
|
||||
The next step is to install GeoIP database which will be used by xt_geoip for IP-to-country mapping. Conveniently, the xtables-addons source package comes with two helper scripts for downloading GeoIP database from MaxMind and converting it into a binary form recognized by xt_geoip. These scripts are found in geoip folder inside the source package. Follow the instructions below to build and install GeoIP database on your system.
|
||||
|
||||
$ cd geoip
|
||||
$ ./xt_geoip_dl
|
||||
$ ./xt_geoip_build GeoIPCountryWhois.csv
|
||||
$ sudo mkdir -p /usr/share/xt_geoip
|
||||
$ sudo cp -r {BE,LE} /usr/share/xt_geoip
|
||||
|
||||
According to [MaxMind][5], their GeoIP database is 99.8% accurate on a country-level, and the database is updated every month. To keep the locally installed GeoIP database up-to-date, you want to set up a monthly [cron job][6] to refresh the local GeoIP database as often.
|
||||
|
||||
### Block Network Traffic Originating from or Destined to a Country ###
|
||||
|
||||
Once xt_geoip module and GeoIP database are installed, you can immediately use the geoip match options in iptables command.
|
||||
|
||||
$ sudo iptables -m geoip --src-cc country[,country...] --dst-cc country[,country...]
|
||||
|
||||
Countries you want to block are specified using [two-letter ISO3166 code][7] (e.g., US (United States), CN (China), IN (India), FR (France)).
|
||||
|
||||
For example, if you want to block incoming traffic from Yemen (YE) and Zambia (ZM), the following iptables command will do.
|
||||
|
||||
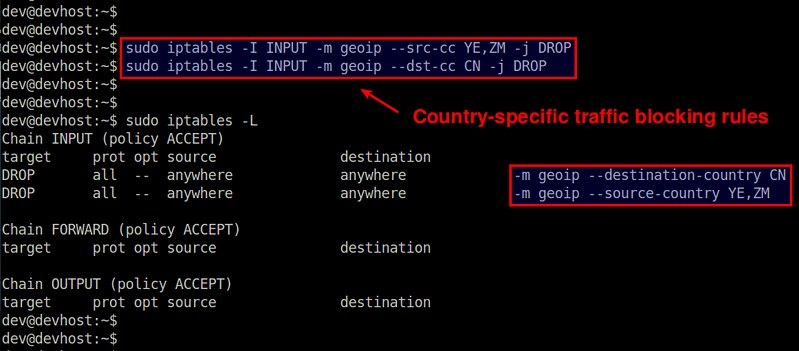
$ sudo iptables -I INPUT -m geoip --src-cc YE,ZM -j DROP
|
||||
|
||||
If you want to block outgoing traffic destined to China (CN), run the following command.
|
||||
|
||||
$ sudo iptables -A OUTPUT -m geoip --dst-cc CN -j DROP
|
||||
|
||||
The matching condition can also be "negated" by prepending "!" to "--src-cc" or "--dst-cc". For example:
|
||||
|
||||
If you want to block all incoming non-US traffic on your server, run this:
|
||||
|
||||
$ sudo iptables -I INPUT -m geoip ! --src-cc US -j DROP
|
||||
|
||||
|
||||
|
||||
#### For Firewall-cmd Users ####
|
||||
|
||||
Some distros such as CentOS/RHEL 7 or Fedora have replaced iptables with firewalld as the default firewall service. On such systems, you can use firewall-cmd to block traffic using xt_geoip similarly. The above three examples can be rewritten with firewall-cmd as follows.
|
||||
|
||||
$ sudo firewall-cmd --direct --add-rule ipv4 filter INPUT 0 -m geoip --src-cc YE,ZM -j DROP
|
||||
$ sudo firewall-cmd --direct --add-rule ipv4 filter OUTPUT 0 -m geoip --dst-cc CN -j DROP
|
||||
$ sudo firewall-cmd --direct --add-rule ipv4 filter INPUT 0 -m geoip ! --src-cc US -j DROP
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
In this tutorial, I presented iptables/xt_geoip which is an easy way to filter network packets based on their source/destination countries. This can be a useful arsenal to deploy in your firewall system if needed. As a final word of caution, I should mention that GeoIP-based traffic filtering is not a foolproof way to ban certain countries on your server. GeoIP database is by nature inaccurate/incomplete, and source/destination geography can easily be spoofed using VPN, Tor or any compromised relay hosts. Geography-based filtering can even block legitimate traffic that should not be banned. Understand this limitation before you decide to deploy it in your production environment.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/block-network-traffic-by-country-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:https://www.archlinux.org/news/dropping-tcp_wrappers-support/
|
||||
[2]:http://xmodulo.com/block-unwanted-ip-addresses-linux.html
|
||||
[3]:http://xtables-addons.sourceforge.net/geoip.php
|
||||
[4]:http://xtables-addons.sourceforge.net/
|
||||
[5]:https://support.maxmind.com/geoip-faq/geoip2-and-geoip-legacy-databases/how-accurate-are-your-geoip2-and-geoip-legacy-databases/
|
||||
[6]:http://ask.xmodulo.com/add-cron-job-linux.html
|
||||
[7]:https://en.wikipedia.org/wiki/ISO_3166-1
|
||||
@ -0,0 +1,105 @@
|
||||
How to enable Software Collections (SCL) on CentOS
|
||||
================================================================================
|
||||
Red Hat Enterprise Linux (RHEL) and its community fork, CentOS, offer 10-year life cycle, meaning that each version of RHEL/CentOS is updated with security patches for up to 10 years. While such long life cycle guarantees much needed system compatibility and reliability for enterprise users, a downside is that core applications and run-time environments grow antiquated as the underlying RHEL/CentOS version becomes close to end-of-life (EOF). For example, CentOS 6.5, whose EOL is dated to November 30th 2020, comes with python 2.6.6 and MySQL 5.1.73, which are already pretty old by today's standard.
|
||||
|
||||
On the other hand, attempting to manually upgrade development toolchains and run-time environments on RHEL/CentOS may potentially break your system unless all dependencies are resolved correctly. Under normal circumstances, manual upgrade is not recommended unless you know what you are doing.
|
||||
|
||||
The [Software Collections][1] (SCL) repository came into being to help with RHEL/CentOS users in this situation. The SCL is created to provide RHEL/CentOS users with a means to easily and safely install and use multiple (and potentially more recent) versions of applications and run-time environments "without" messing up the existing system. This is in contrast to other third party repositories which could cause conflicts among installed packages.
|
||||
|
||||
The latest SCL offers:
|
||||
|
||||
- Python 3.3 and 2.7
|
||||
- PHP 5.4
|
||||
- Node.js 0.10
|
||||
- Ruby 1.9.3
|
||||
- Perl 5.16.3
|
||||
- MariaDB and MySQL 5.5
|
||||
- Apache httpd 2.4.6
|
||||
|
||||
In the rest of the tutorial, let me show you how to set up the SCL repository and how to install and enable the packages from the SCL.
|
||||
|
||||
### Set up the Software Collections (SCL) Repository ###
|
||||
|
||||
The SCL is available on CentOS 6.5 and later. To set up the SCL, simply run:
|
||||
|
||||
$ sudo yum install centos-release-SCL
|
||||
|
||||
To enable and run applications from the SCL, you also need to install the following package.
|
||||
|
||||
$ sudo yum install scl-utils-build
|
||||
|
||||
You can browse a complete list of packages available from the SCL repository by running:
|
||||
|
||||
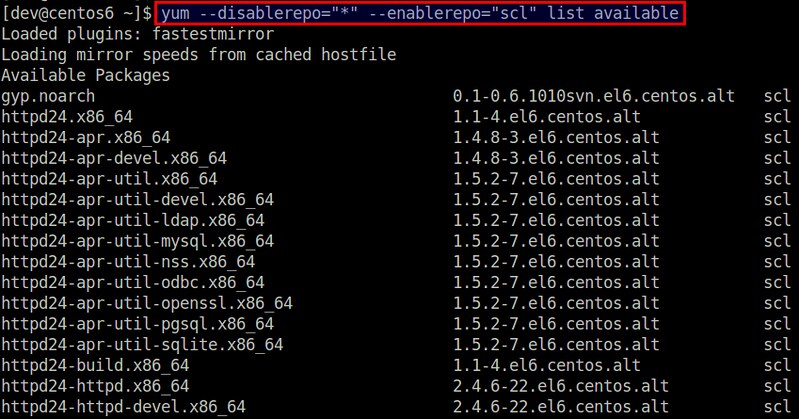
$ yum --disablerepo="*" --enablerepo="scl" list available
|
||||
|
||||
|
||||
|
||||
### Install and Enable a Package from the SCL ###
|
||||
|
||||
Now that you have set up the SCL, you can go ahead and install any package from the SCL.
|
||||
|
||||
You can search for SCL packages with:
|
||||
|
||||
$ yum --disablerepo="*" --enablerepo="scl" search <keyword>
|
||||
|
||||
Let's say you want to install python 3.3.
|
||||
|
||||
Go ahead and install it as usual with yum:
|
||||
|
||||
$ sudo yum install python33
|
||||
|
||||
At any time you can check the list of packages you installed from the SCL by running:
|
||||
|
||||
$ scl --list
|
||||
|
||||
----------
|
||||
|
||||
python33
|
||||
|
||||
A nice thing about the SCL is that installing a package from the SCL does NOT overwrite any system files, and is guaranteed to not cause any conflicts with other system libraries and applications.
|
||||
|
||||
For example, if you check the default python version after installing python33, you will see that the default version is still the same:
|
||||
|
||||
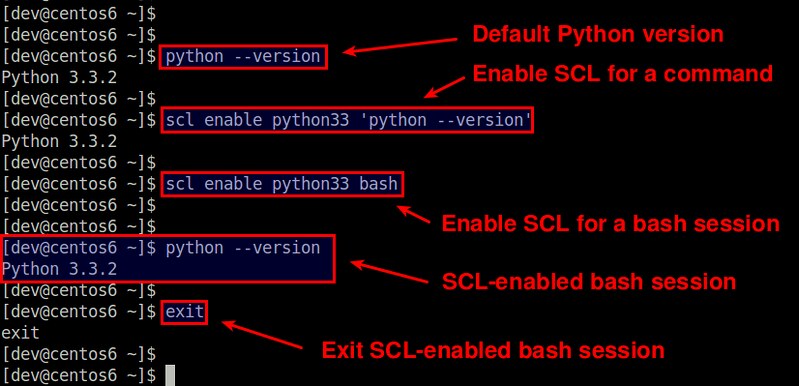
$ python --version
|
||||
|
||||
----------
|
||||
|
||||
Python 2.6.6
|
||||
|
||||
If you want to try an installed SCL package, you need to explicitly enable it "on a per-command basis" using scl:
|
||||
|
||||
$ scl enable <scl-package-name> <command>
|
||||
|
||||
For example, to enable python33 package for python command:
|
||||
|
||||
$ scl enable python33 'python --version'
|
||||
|
||||
----------
|
||||
|
||||
Python 3.3.2
|
||||
|
||||
If you want to run multiple commands while enabling python33 package, you can actually create an SCL-enabled bash session as follows.
|
||||
|
||||
$ scl enable python33 bash
|
||||
|
||||
Within this bash session, the default python will be switched to 3.3 until you type exit and kill the session.
|
||||
|
||||
|
||||
|
||||
In short, the SCL is somewhat similar to the virtualenv of Python, but is more general in that you can enable/disable SCL sessions for a far greater number of applications than just Python.
|
||||
|
||||
For more detailed instructions on the SCL, refer to the official [quick start guide][2].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/enable-software-collections-centos.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:https://www.softwarecollections.org/
|
||||
[2]:https://www.softwarecollections.org/docs/
|
||||
@ -0,0 +1,100 @@
|
||||
Linux Desktop Fun: Summon Swarms Of Penguins To Waddle About The Desktop
|
||||
================================================================================
|
||||
XPenguins is a program for animating cute cartoons animals in your root window. By default it will be penguins they drop in from the top of the screen, walk along the tops of your windows, up the side of your windows, levitate, skateboard, and do other similarly exciting things. Now you can send an army of cute little penguins to invade the screen of someone else on your network.
|
||||
|
||||
### Install XPenguins ###
|
||||
|
||||
Open a command-line terminal (select Applications > Accessories > Terminal), and then type the following commands to install XPenguins program. First, type the command apt-get update to tell apt to refresh its package information by querying the configured repositories and then install the required program:
|
||||
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install xpenguins
|
||||
|
||||
### How do I Start XPenguins Locally? ###
|
||||
|
||||
Type the following command:
|
||||
|
||||
$ xpenguins
|
||||
|
||||
Sample outputs:
|
||||
|
||||

|
||||
|
||||
An army of cute little penguins invading the screen
|
||||
|
||||

|
||||
|
||||
Linux: Cute little penguins walking along the tops of your windows
|
||||
|
||||

|
||||
|
||||
Xpenguins Screenshot
|
||||
|
||||
Be careful when you move windows as the little guys squash easily. If you send the program an interupt signal (Ctrl-C) they will burst.
|
||||
|
||||
### Themes ###
|
||||
|
||||
To list themes, enter:
|
||||
|
||||
$ xpenguins -l
|
||||
|
||||
Sample outputs:
|
||||
|
||||
Big Penguins
|
||||
Bill
|
||||
Classic Penguins
|
||||
Penguins
|
||||
Turtles
|
||||
|
||||
You can use alternative themes as follows:
|
||||
|
||||
$ xpenguins --theme "Big Penguins" --theme "Turtles"
|
||||
|
||||
You can install additional themes as follows:
|
||||
|
||||
$ cd /tmp
|
||||
$ wget http://xpenguins.seul.org/xpenguins_themes-1.0.tar.gz
|
||||
$ tar -zxvf xpenguins_themes-1.0.tar.gz
|
||||
$ mkdir ~/.xpenguins
|
||||
$ mv -v themes ~/.xpenguins/
|
||||
$ xpenguins -l
|
||||
|
||||
Sample outputs:
|
||||
|
||||
Lemmings
|
||||
Sonic the Hedgehog
|
||||
The Simpsons
|
||||
Winnie the Pooh
|
||||
Worms
|
||||
Big Penguins
|
||||
Bill
|
||||
Classic Penguins
|
||||
Penguins
|
||||
Turtles
|
||||
|
||||
To start with a random theme, enter:
|
||||
|
||||
$ xpenguins --random-theme
|
||||
|
||||
To load all available themes and run them simultaneously, enter:
|
||||
|
||||
$ xpenguins --all
|
||||
|
||||
More links and information:
|
||||
|
||||
- [XPenguins][1] home page.
|
||||
- man penguins
|
||||
- More Linux / UNIX desktop fun with [Steam Locomotive][2] and [Terminal ASCII Aquarium][3].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.cyberciti.biz/tips/linux-cute-little-xpenguins-walk-along-tops-ofyour-windows.html
|
||||
|
||||
作者:Vivek Gite
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://xpenguins.seul.org/
|
||||
[2]:http://www.cyberciti.biz/tips/displays-animations-when-accidentally-you-type-sl-instead-of-ls.html
|
||||
[3]:http://www.cyberciti.biz/tips/linux-unix-apple-osx-terminal-ascii-aquarium.html
|
||||
@ -0,0 +1,75 @@
|
||||
Linux / UNIX Desktop Fun: Let it Snow On Your Desktop
|
||||
================================================================================
|
||||
Feeling lonely this holiday season? Try Xsnow. This little app will let it snow on the Unix / Linux desktop. Santa and his reindeer will complete your festive season feeling with moving snowflakes on your desktop, with Santa Claus running all over the screen.
|
||||
|
||||
I first installed this 13 or 14 years ago. It was was originally created for Macintosh systems in 1984. You can install it as follows:
|
||||
|
||||
### Install xsnow ###
|
||||
|
||||
Debian / Ubuntu / Mint users type the following command:
|
||||
|
||||
$ sudo apt-get install xsnow
|
||||
|
||||
Freebsd users type the following command to install the same:
|
||||
|
||||
# cd /usr/ports/x11/xsnow/
|
||||
# make install clean
|
||||
|
||||
OR, try to add the package:
|
||||
|
||||
# pkg_add -r xsnow
|
||||
|
||||
#### A Note About Other Distros ####
|
||||
|
||||
1. Fedora / RHEL / CentOS Linux desktop users may find the package using [rpmfusion][1] repo.
|
||||
1. Gentoo user try Gentoo portage i.e. [emerge -p xsnow][2]
|
||||
1. OpenSuse Linux user try Yast and search for xsnow.
|
||||
|
||||
### How Do I Use xsnow? ###
|
||||
|
||||
Open a command-line terminal (select Applications > Accessories > Terminal), and then type the following to starts xsnow:
|
||||
|
||||
$ xsnow
|
||||
|
||||
Sample outputs:
|
||||
|
||||

|
||||
|
||||
Fig.01: Snow for your Linux and Unix desktop systems
|
||||
|
||||
You can set the background to a blue color and lets it snow white, type:
|
||||
|
||||
$ xsnow -bg blue -sc snow
|
||||
|
||||
To set the maximum number of snowflakes and runs as fast as possible, type:
|
||||
|
||||
$ xsnow -snowflakes 10000 -delay 0
|
||||
|
||||
Do not display the trees and Santa Claus running all over the screen, enter:
|
||||
|
||||
$ xsnow -notrees -nosanta
|
||||
|
||||
For more information about xsnow and other options, please see the manual page by typing man xsnow from the command line:
|
||||
|
||||
$ man xsnow
|
||||
|
||||
Recommended readings:
|
||||
|
||||
- [Download Xsnow][1] from the official site.
|
||||
- Please note that [MS-Windows][2] and [Mac OS X version][3] attracts one time shareware fee.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.cyberciti.biz/tips/linux-unix-xsnow.html
|
||||
|
||||
作者:Vivek Gite
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://rpmfusion.org/Configuration
|
||||
[2]:http://www.gentoo.org/doc/en/handbook/handbook-x86.xml?part=2&chap=1
|
||||
[3]:http://dropmix.xs4all.nl/rick/Xsnow/
|
||||
[4]:http://dropmix.xs4all.nl/rick/WinSnow/
|
||||
[5]:http://dropmix.xs4all.nl/rick/MacOSXSnow/
|
||||
@ -0,0 +1,39 @@
|
||||
Linux / UNIX Desktop Fun: Steam Locomotive
|
||||
================================================================================
|
||||
One of the most [common mistake][1] is typing sl instead of ls command. I actually set [an alias][2] i.e. alias sl=ls; but then you may miss out the steam train with whistle.
|
||||
|
||||
sl is a joke software or classic UNIX game. It is a steam locomotive runs across your screen if you type "sl" (Steam Locomotive) instead of "ls" by mistake.
|
||||
|
||||
### Install sl ###
|
||||
|
||||
Type the following command under Debian / Ubuntu Linux, enter:
|
||||
|
||||
# apt-get install sl
|
||||
|
||||
It is also available on FreeBSD and other UNIX like operating systems. Next, mistyped ls command as sl:
|
||||
|
||||
$ sl
|
||||
|
||||

|
||||
|
||||
Fig.01: Run steam locomotive across the screen if you type "sl" instead of "ls"
|
||||
|
||||
It also supports the following options:
|
||||
|
||||
- **-a** : An accident seems to happen. You'll feel pity for people who cry for help.
|
||||
- **-l** : shows little one.
|
||||
- **-F** : It flies.
|
||||
- **-e** : Allow interrupt by Ctrl+C.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.cyberciti.biz/tips/displays-animations-when-accidentally-you-type-sl-instead-of-ls.html
|
||||
|
||||
作者:Vivek Gite
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.cyberciti.biz/tips/my-10-unix-command-line-mistakes.html
|
||||
[2]:http://bash.cyberciti.biz/guide/Create_and_use_aliases
|
||||
@ -0,0 +1,64 @@
|
||||
Linux / UNIX Desktop Fun: Terminal ASCII Aquarium
|
||||
================================================================================
|
||||
You can now enjoy mysteries of the sea from the safety of your own terminal using ASCIIQuarium. It is an aquarium/sea animation in ASCII art created using perl.
|
||||
|
||||
### Install Term::Animation ###
|
||||
|
||||
First, you need to install Perl module called Term-Animation. Open a command-line terminal (select Applications > Accessories > Terminal), and then type:
|
||||
|
||||
$ sudo apt-get install libcurses-perl
|
||||
$ cd /tmp
|
||||
$ wget http://search.cpan.org/CPAN/authors/id/K/KB/KBAUCOM/Term-Animation-2.4.tar.gz
|
||||
$ tar -zxvf Term-Animation-2.4.tar.gz
|
||||
$ cd Term-Animation-2.4/
|
||||
$ perl Makefile.PL && make && make test
|
||||
$ sudo make install
|
||||
|
||||
### Download and Install ASCIIQuarium ###
|
||||
|
||||
While still at bash prompt, type:
|
||||
|
||||
$ cd /tmp
|
||||
$ wget http://www.robobunny.com/projects/asciiquarium/asciiquarium.tar.gz
|
||||
$ tar -zxvf asciiquarium.tar.gz
|
||||
$ cd asciiquarium_1.0/
|
||||
$ sudo cp asciiquarium /usr/local/bin
|
||||
$ sudo chmod 0755 /usr/local/bin/asciiquarium
|
||||
|
||||
### How do I view my ASCII Aquarium? ###
|
||||
|
||||
Simply type the following command:
|
||||
|
||||
$ /usr/local/bin/asciiquarium
|
||||
|
||||
OR
|
||||
|
||||
$ perl /usr/local/bin/asciiquarium
|
||||
|
||||
|
||||
|
||||
### Related media ###
|
||||
|
||||
注:youtube 视频
|
||||
<iframe width="596" height="335" frameborder="0" allowfullscreen="" src="//www.youtube.com/embed/MzatWgu67ok"></iframe>
|
||||
|
||||
[Video 01: ASCIIQuarium - Sea Animation on Linux / Unix Desktop][1]
|
||||
|
||||
### Download: erminal ASCII Aquarium KDE and Mac OS X Version ###
|
||||
|
||||
[Download asciiquarium][2]. If you're running Mac OS X, try a packaged [version][3] that will run out of the box. For KDE users, try a [KDE Screensaver][4] based on the Asciiquarium.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.cyberciti.biz/tips/linux-unix-apple-osx-terminal-ascii-aquarium.html
|
||||
|
||||
作者:Vivek Gite
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://youtu.be/MzatWgu67ok
|
||||
[2]:http://www.robobunny.com/projects/asciiquarium/html/
|
||||
[3]:http://habilis.net/macasciiquarium/
|
||||
[4]:http://kde-look.org/content/show.php?content=29207
|
||||
@ -0,0 +1,89 @@
|
||||
Linux / Unix Desktop Fun: Cat And Mouse Chase All Over Your Screen
|
||||
================================================================================
|
||||
Oneko is a little fun app. It will change your cursor into mouse and creates a little cute cat and the cat start chasing around your mouse cursor. The word "neko" means "cat" in Japanese and it was originally written by a Japanese author as a Macintosh desktop accessory.
|
||||
|
||||
### Install oneko ###
|
||||
|
||||
Type the following command:
|
||||
|
||||
$ sudo apt-get install oneko
|
||||
|
||||
Sample outputs:
|
||||
|
||||
[sudo] password for vivek:
|
||||
Reading package lists... Done
|
||||
Building dependency tree
|
||||
Reading state information... Done
|
||||
The following NEW packages will be installed:
|
||||
oneko
|
||||
0 upgraded, 1 newly installed, 0 to remove and 10 not upgraded.
|
||||
Need to get 38.6 kB of archives.
|
||||
After this operation, 168 kB of additional disk space will be used.
|
||||
Get:1 http://debian.osuosl.org/debian/ squeeze/main oneko amd64 1.2.sakura.6-7 [38.6 kB]
|
||||
Fetched 38.6 kB in 1s (25.9 kB/s)
|
||||
Selecting previously deselected package oneko.
|
||||
(Reading database ... 274152 files and directories currently installed.)
|
||||
Unpacking oneko (from .../oneko_1.2.sakura.6-7_amd64.deb) ...
|
||||
Processing triggers for menu ...
|
||||
Processing triggers for man-db ...
|
||||
Setting up oneko (1.2.sakura.6-7) ...
|
||||
Processing triggers for menu ...
|
||||
|
||||
FreeBSD unix user type the following command to install oneko:
|
||||
|
||||
# cd /usr/ports/games/oneko
|
||||
# make install clean
|
||||
|
||||
### How do I use oneko? ###
|
||||
|
||||
Simply type the following command:
|
||||
|
||||
$ oneko
|
||||
|
||||
You can make cat into "tora-neko", a cat wite tiger-like stripe:
|
||||
|
||||
$ oneko -tora
|
||||
|
||||
### Not a cat person? ###
|
||||
|
||||
You can run a dog instead of a cat:
|
||||
|
||||
$ oneko -dog
|
||||
|
||||
The followin will runs Sakura Kinomoto instead of a cat:
|
||||
|
||||
$ oneko -sakura
|
||||
|
||||
Runs Tomoyo Daidouji instead of a cat:
|
||||
|
||||
$ oneko -tomoyo
|
||||
|
||||
### Check out related media ###
|
||||
|
||||
This tutorial also available in video format:
|
||||
|
||||
注:youtube 视频
|
||||
<iframe width="596" height="335" frameborder="0" allowfullscreen="" src="http://www.youtube.com/embed/Nm3SkXThL0s"></iframe>
|
||||
|
||||
(Video.01: Demo - Install and use oneko under Linux)
|
||||
|
||||
### Other options ###
|
||||
|
||||
You can pass the following options:
|
||||
|
||||
1. **-tofocus** : Makes cat run to and on top of focus window. When focus window is not in sight, cat chases mouse as usually.
|
||||
1. **-position geometry** : Specify X and Y offsets in pixels to adjust position of cat relative to mouse pointer./li>
|
||||
1. **-rv** : Reverse background color and foreground color.
|
||||
1. **-fg color** : Foreground color (e.g., oneko -dog -fg red).
|
||||
1. **-bg color** : Background color (e.g., oneko -dog -bg green).
|
||||
1. See oneko man page for more information.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.cyberciti.biz/open-source/oneko-app-creates-cute-cat-chasing-around-your-mouse/
|
||||
|
||||
作者:Vivek Gite
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,201 @@
|
||||
Linux / Unix Desktop Fun: Text Mode ASCII-art Box and Comment Drawing
|
||||
================================================================================
|
||||
Boxes command is a text filter and a little known tool that can draw any kind of ASCII art box around its input text or code for fun and profit. You can quickly create email signatures, or create regional comments in any programming language. This command was intended to be used with the vim text editor, but can be tied to any text editor which supports filters, as well as from the command line as a standalone tool.
|
||||
|
||||
### Task: Install boxes ###
|
||||
|
||||
Use the [apt-get command][1] to install boxes under Debian / Ubuntu Linux:
|
||||
|
||||
$ sudo apt-get install boxes
|
||||
|
||||
Sample outputs:
|
||||
|
||||
Reading package lists... Done
|
||||
Building dependency tree
|
||||
Reading state information... Done
|
||||
The following NEW packages will be installed:
|
||||
boxes
|
||||
0 upgraded, 1 newly installed, 0 to remove and 6 not upgraded.
|
||||
Need to get 0 B/59.8 kB of archives.
|
||||
After this operation, 205 kB of additional disk space will be used.
|
||||
Selecting previously deselected package boxes.
|
||||
(Reading database ... 224284 files and directories currently installed.)
|
||||
Unpacking boxes (from .../boxes_1.0.1a-2.3_amd64.deb) ...
|
||||
Processing triggers for man-db ...
|
||||
Setting up boxes (1.0.1a-2.3) ...
|
||||
|
||||
RHEL / CentOS / Fedora Linux users, use the [yum command to install boxes][2] (first [enable EPEL repo as described here][3]):
|
||||
|
||||
# yum install boxes
|
||||
|
||||
Sample outputs:
|
||||
|
||||
Loaded plugins: rhnplugin
|
||||
Setting up Install Process
|
||||
Resolving Dependencies
|
||||
There are unfinished transactions remaining. You might consider running yum-complete-transaction first to finish them.
|
||||
--> Running transaction check
|
||||
---> Package boxes.x86_64 0:1.1-8.el6 will be installed
|
||||
--> Finished Dependency Resolution
|
||||
Dependencies Resolved
|
||||
==========================================================================
|
||||
Package Arch Version Repository Size
|
||||
==========================================================================
|
||||
Installing:
|
||||
boxes x86_64 1.1-8.el6 epel 64 k
|
||||
Transaction Summary
|
||||
==========================================================================
|
||||
Install 1 Package(s)
|
||||
Total download size: 64 k
|
||||
Installed size: 151 k
|
||||
Is this ok [y/N]: y
|
||||
Downloading Packages:
|
||||
boxes-1.1-8.el6.x86_64.rpm | 64 kB 00:00
|
||||
Running rpm_check_debug
|
||||
Running Transaction Test
|
||||
Transaction Test Succeeded
|
||||
Running Transaction
|
||||
Installing : boxes-1.1-8.el6.x86_64 1/1
|
||||
Installed:
|
||||
boxes.x86_64 0:1.1-8.el6
|
||||
Complete!
|
||||
|
||||
FreeBSD user can use the port as follows:
|
||||
|
||||
cd /usr/ports/misc/boxes/ && make install clean
|
||||
|
||||
Or, add the package using the pkg_add command:
|
||||
|
||||
# pkg_add -r boxes
|
||||
|
||||
### Draw any kind of box around some given text ###
|
||||
|
||||
Type the following command:
|
||||
|
||||
echo "This is a test" | boxes
|
||||
|
||||
Or specify the name of the design to use:
|
||||
|
||||
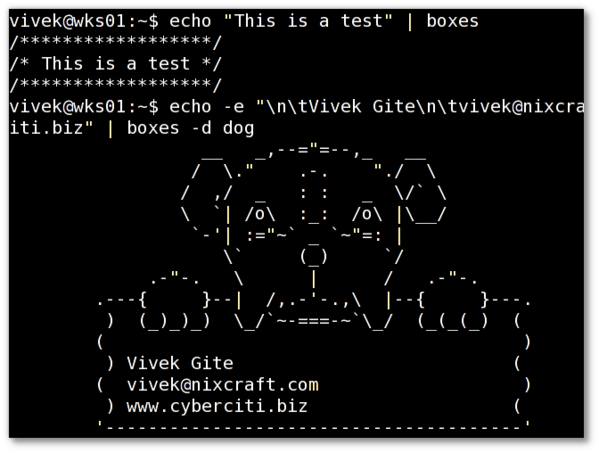
echo -e "\n\tVivek Gite\n\tvivek@nixcraft.com\n\twww.cyberciti.biz" | boxes -d dog
|
||||
|
||||
Sample outputs:
|
||||
|
||||
|
||||
|
||||
Fig.01: Unix / Linux: Boxes Command To Draw Various Designs
|
||||
|
||||
#### How do I list all designs? ####
|
||||
|
||||
The syntax is:
|
||||
|
||||
boxes option
|
||||
pipe | boxes options
|
||||
echo "text" | boxes -d foo
|
||||
boxes -l
|
||||
|
||||
The -d design option sets the name of the design to use. The syntax is:
|
||||
|
||||
echo "Text" | boxes -d design
|
||||
pipe | boxes -d desig
|
||||
|
||||
The -l option list designs. It produces a listing of all available box designs in the config file, along with a sample box and information about it's creator:
|
||||
|
||||
boxes -l
|
||||
boxes -l | more
|
||||
boxes -l | less
|
||||
|
||||
Sample outputs:
|
||||
|
||||
43 Available Styles in "/etc/boxes/boxes-config":
|
||||
-------------------------------------------------
|
||||
ada-box (Neil Bird ):
|
||||
---------------
|
||||
-- --
|
||||
-- --
|
||||
---------------
|
||||
ada-cmt (Neil Bird ):
|
||||
--
|
||||
-- regular Ada
|
||||
-- comments
|
||||
--
|
||||
boy (Joan G. Stark ):
|
||||
.-"""-.
|
||||
/ .===. \
|
||||
\/ 6 6 \/
|
||||
( \___/ )
|
||||
_________ooo__\_____/______________
|
||||
/ \
|
||||
| joan stark spunk1111@juno.com |
|
||||
| VISIT MY ASCII ART GALLERY: |
|
||||
| http://www.geocities.com/SoHo/7373/ |
|
||||
\_______________________ooo_________/ jgs
|
||||
| | |
|
||||
|_ | _|
|
||||
| | |
|
||||
|__|__|
|
||||
/-'Y'-\
|
||||
(__/ \__)
|
||||
....
|
||||
...
|
||||
output truncated
|
||||
..
|
||||
|
||||
### How do I filter text via boxes while using vi/vim text editor? ###
|
||||
|
||||
You can use any external command with vi or vim. In this example, [insert current date and time][4], enter:
|
||||
|
||||
!!date
|
||||
|
||||
OR
|
||||
|
||||
:r !date
|
||||
|
||||
You need to type above command in Vim to read the output from the date command. This will insert the date and time after the current line:
|
||||
|
||||
Tue Jun 12 00:05:38 IST 2012
|
||||
|
||||
You can do the same with boxes command. Create a sample shell script or a c program as follows:
|
||||
|
||||
#!/bin/bash
|
||||
Purpose: Backup mysql database to remote server.
|
||||
Author: Vivek Gite
|
||||
Last updated on: Tue Jun, 12 2012
|
||||
|
||||
Now type the following (move cursor to the second line i.e. line which starts with "Purpose: ...")
|
||||
|
||||
3!!boxes
|
||||
|
||||
And voila you will get the output as follows:
|
||||
|
||||
#!/bin/bash
|
||||
/****************************************************/
|
||||
/* Purpose: Backup mysql database to remote server. */
|
||||
/* Author: Vivek Gite */
|
||||
/* Last updated on: Tue Jun, 12 2012 */
|
||||
/****************************************************/
|
||||
|
||||
This video will give you an introduction to boxes command:
|
||||
|
||||
注:youtube 视频
|
||||
<iframe width="595" height="446" frameborder="0" src="http://www.youtube.com/embed/glzXjNvrYOc?rel=0"></iframe>
|
||||
|
||||
(Video:01: boxes command in action. BTW, this is my first video so go easy on me and let me know what you think.)
|
||||
|
||||
See also
|
||||
|
||||
- boxes man page
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.cyberciti.biz/tips/unix-linux-draw-any-kind-of-boxes-around-text-editor.html
|
||||
|
||||
作者:Vivek Gite
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.cyberciti.biz/tips/linux-debian-package-management-cheat-sheet.html
|
||||
[2]:http://www.cyberciti.biz/faq/rhel-centos-fedora-linux-yum-command-howto/
|
||||
[3]:http://www.cyberciti.biz/faq/fedora-sl-centos-redhat6-enable-epel-repo/
|
||||
[4]:http://www.cyberciti.biz/faq/vim-inserting-current-date-time-under-linux-unix-osx/
|
||||
@ -0,0 +1,497 @@
|
||||
Securi-Pi: Using the Raspberry Pi as a Secure Landing Point
|
||||
================================================================================
|
||||
|
||||
Like many LJ readers these days, I've been leading a bit of a techno-nomadic lifestyle as of the past few years—jumping from network to network, access point to access point, as I bounce around the real world while maintaining my connection to the Internet and other networks I use on a daily basis. As of late, I've found that more and more networks are starting to block outbound ports like SMTP (port 25), SSH (port 22) and others. It becomes really frustrating when you drop into a local coffee house expecting to be able to fire up your SSH client and get a few things done, and you can't, because the network's blocking you.
|
||||
|
||||
However, I have yet to run across a network that blocks HTTPS outbound (port 443). After a bit of fiddling with a Raspberry Pi 2 I have at home, I was able to get a nice clean solution that lets me hit various services on the Raspberry Pi via port 443—allowing me to walk around blocked ports and hobbled networks so I can do the things I need to do. In a nutshell, I have set up this Raspberry Pi to act as an OpenVPN endpoint, SSH endpoint and Apache server—with all these services listening on port 443 so networks with restrictive policies aren't an issue.
|
||||
|
||||
### Notes
|
||||
This solution will work on most networks, but firewalls that do deep packet inspection on outbound traffic still can block traffic that's tunneled using this method. However, I haven't been on a network that does that...yet. Also, while I use a lot of cryptography-based solutions here (OpenVPN, HTTPS, SSH), I haven't done a strict security audit of this setup. DNS may leak information, for example, and there may be other things I haven't thought of. I'm not recommending this as a way to hide all your traffic—I just use this so that I can connect to the Internet in an unfettered way when I'm out and about.
|
||||
|
||||
### Getting Started
|
||||
Let's start off with what you need to put this solution together. I'm using this on a Raspberry Pi 2 at home, running the latest Raspbian, but this should work just fine on a Raspberry Pi Model B, as well. It fits within the 512MB of RAM footprint quite easily, although performance may be a bit slower, because the Raspberry Pi Model B has a single-core CPU as opposed to the Pi 2's quad-core. My Raspberry Pi 2 is behind my home's router/firewall, so I get the added benefit of being able to access my machines at home. This also means that any traffic I send to the Internet appears to come from my home router's IP address, so this isn't a solution designed to protect anonymity. If you don't have a Raspberry Pi, or don't want this running out of your home, it's entirely possible to run this out of a small cloud server too. Just make sure that the server's running Debian or Ubuntu, as these instructions are targeted at Debian-based distributions.
|
||||
|
||||

|
||||
|
||||
Figure 1. The Raspberry Pi, about to become an encrypted network endpoint.
|
||||
|
||||
### Installing and Configuring BIND
|
||||
Once you have your platform up and running—whether it's a Raspberry Pi or otherwise—next you're going to install BIND, the nameserver that powers a lot of the Internet. You're going to install BIND as a caching nameserver only, and not have it service incoming requests from the Internet. Installing BIND will give you a DNS server to point your OpenVPN clients at, once you get to the OpenVPN step. Installing BIND is easy; it's just a simple `apt-get `command to install it:
|
||||
|
||||
```
|
||||
root@test:~# apt-get install bind9
|
||||
Reading package lists... Done
|
||||
Building dependency tree
|
||||
Reading state information... Done
|
||||
The following extra packages will be installed:
|
||||
bind9utils
|
||||
Suggested packages:
|
||||
bind9-doc resolvconf ufw
|
||||
The following NEW packages will be installed:
|
||||
bind9 bind9utils
|
||||
0 upgraded, 2 newly installed, 0 to remove and
|
||||
↪0 not upgraded.
|
||||
Need to get 490 kB of archives.
|
||||
After this operation, 1,128 kB of additional disk
|
||||
↪space will be used.
|
||||
Do you want to continue [Y/n]? y
|
||||
```
|
||||
|
||||
There are a couple minor configuration changes that need to be made to one of the config files of BIND before it can operate as a caching nameserver. Both changes are in `/etc/bind/named.conf.options`. First, you're going to uncomment the "forwarders" section of this file, and you're going to add a nameserver on the Internet to which to forward requests. In this case, I'm going to add Google's DNS (8.8.8.8). The "forwarders" section of the file should look like this:
|
||||
|
||||
```
|
||||
forwarders {
|
||||
8.8.8.8;
|
||||
};
|
||||
```
|
||||
|
||||
The second change you're going to make allows queries from your internal network and localhost. Simply add this line to the bottom of the configuration file, right before the `}`; that ends the file:
|
||||
|
||||
```
|
||||
allow-query { 192.168.1.0/24; 127.0.0.0/16; };
|
||||
```
|
||||
|
||||
That line above allows this DNS server to be queried from the network it's on (in this case, my network behind my firewall) and localhost. Next, you just need to restart BIND:
|
||||
|
||||
```
|
||||
root@test:~# /etc/init.d/bind9 restart
|
||||
[....] Stopping domain name service...: bind9waiting
|
||||
↪for pid 13209 to die
|
||||
. ok
|
||||
[ ok ] Starting domain name service...: bind9.
|
||||
```
|
||||
|
||||
Now you can test `nslookup` to make sure your server works:
|
||||
|
||||
```
|
||||
root@test:~# nslookup
|
||||
> server localhost
|
||||
Default server: localhost
|
||||
Address: 127.0.0.1#53
|
||||
> www.google.com
|
||||
Server: localhost
|
||||
Address: 127.0.0.1#53
|
||||
|
||||
Non-authoritative answer:
|
||||
Name: www.google.com
|
||||
Address: 173.194.33.176
|
||||
Name: www.google.com
|
||||
Address: 173.194.33.177
|
||||
Name: www.google.com
|
||||
Address: 173.194.33.178
|
||||
Name: www.google.com
|
||||
Address: 173.194.33.179
|
||||
Name: www.google.com
|
||||
Address: 173.194.33.180
|
||||
```
|
||||
|
||||
That's it! You've got a working nameserver on this machine. Next, let's move on to OpenVPN.
|
||||
|
||||
### Installing and Configuring OpenVPN
|
||||
|
||||
OpenVPN is an open-source VPN solution that relies on SSL/TLS for its key exchange. It's also easy to install and get working under Linux. Configuration of OpenVPN can be a bit daunting, but you're not going to deviate from the default configuration by much. To start, you're going to run an apt-get command and install OpenVPN:
|
||||
|
||||
```
|
||||
root@test:~# apt-get install openvpn
|
||||
Reading package lists... Done
|
||||
Building dependency tree
|
||||
Reading state information... Done
|
||||
The following extra packages will be installed:
|
||||
liblzo2-2 libpkcs11-helper1
|
||||
Suggested packages:
|
||||
resolvconf
|
||||
The following NEW packages will be installed:
|
||||
liblzo2-2 libpkcs11-helper1 openvpn
|
||||
0 upgraded, 3 newly installed, 0 to remove and
|
||||
↪0 not upgraded.
|
||||
Need to get 621 kB of archives.
|
||||
After this operation, 1,489 kB of additional disk
|
||||
↪space will be used.
|
||||
Do you want to continue [Y/n]? y
|
||||
```
|
||||
|
||||
Now that OpenVPN is installed, you're going to configure it. OpenVPN is SSL-based, and it relies on both server and client certificates to work. To generate these certificates, you need to configure a Certificate Authority (CA) on the machine. Luckily, OpenVPN ships with some wrapper scripts known as "easy-rsa" that help to bootstrap this process. You'll start by making a directory on the filesystem for the easy-rsa scripts to reside in and by copying the scripts from the template directory there:
|
||||
|
||||
```
|
||||
root@test:~# mkdir /etc/openvpn/easy-rsa
|
||||
root@test:~# cp -rpv
|
||||
↪/usr/share/doc/openvpn/examples/easy-rsa/2.0/*
|
||||
↪/etc/openvpn/easy-rsa/
|
||||
```
|
||||
|
||||
Next, copy the vars file to a backup copy:
|
||||
|
||||
```
|
||||
root@test:/etc/openvpn/easy-rsa# cp vars vars.bak
|
||||
```
|
||||
|
||||
Now, edit vars so it's got information pertinent to your installation. I'm going specify only the lines that need to be edited, with sample data, below:
|
||||
|
||||
```
|
||||
KEY_SIZE=4096
|
||||
KEY_COUNTRY="US"
|
||||
KEY_PROVINCE="CA"
|
||||
KEY_CITY="Silicon Valley"
|
||||
KEY_ORG="Linux Journal"
|
||||
KEY_EMAIL="bill.childers@linuxjournal.com"
|
||||
```
|
||||
|
||||
The next step is to source the vars file, so that the environment variables in the file are in your current environment:
|
||||
|
||||
```
|
||||
root@test:/etc/openvpn/easy-rsa# source ./vars
|
||||
NOTE: If you run ./clean-all, I will be doing a
|
||||
↪rm -rf on /etc/openvpn/easy-rsa/keys
|
||||
```
|
||||
|
||||
### Building the Certificate Authority
|
||||
|
||||
You're now going to run clean-all to ensure a clean working environment, and then you're going to build the CA. Note that I'm changing changeme prompts to something that's appropriate for this installation:
|
||||
|
||||
```
|
||||
root@test:/etc/openvpn/easy-rsa# ./clean-all
|
||||
root@test:/etc/openvpn/easy-rsa# ./build-ca
|
||||
Generating a 4096 bit RSA private key
|
||||
...................................................++
|
||||
...................................................++
|
||||
writing new private key to 'ca.key'
|
||||
-----
|
||||
You are about to be asked to enter information that
|
||||
will be incorporated into your certificate request.
|
||||
What you are about to enter is what is called a
|
||||
Distinguished Name or a DN.
|
||||
There are quite a few fields but you can leave some
|
||||
blank. For some fields there will be a default value,
|
||||
If you enter '.', the field will be left blank.
|
||||
-----
|
||||
Country Name (2 letter code) [US]:
|
||||
State or Province Name (full name) [CA]:
|
||||
Locality Name (eg, city) [Silicon Valley]:
|
||||
Organization Name (eg, company) [Linux Journal]:
|
||||
Organizational Unit Name (eg, section)
|
||||
↪[changeme]:SecTeam
|
||||
Common Name (eg, your name or your server's hostname)
|
||||
↪[changeme]:test.linuxjournal.com
|
||||
Name [changeme]:test.linuxjournal.com
|
||||
Email Address [bill.childers@linuxjournal.com]:
|
||||
```
|
||||
|
||||
### Building the Server Certificate
|
||||
|
||||
Once the CA is created, you need to build the OpenVPN server certificate:
|
||||
|
||||
```root@test:/etc/openvpn/easy-rsa#
|
||||
↪./build-key-server test.linuxjournal.com
|
||||
Generating a 4096 bit RSA private key
|
||||
...................................................++
|
||||
writing new private key to 'test.linuxjournal.com.key'
|
||||
-----
|
||||
You are about to be asked to enter information that
|
||||
will be incorporated into your certificate request.
|
||||
What you are about to enter is what is called a
|
||||
Distinguished Name or a DN.
|
||||
There are quite a few fields but you can leave some
|
||||
blank. For some fields there will be a default value,
|
||||
If you enter '.', the field will be left blank.
|
||||
-----
|
||||
Country Name (2 letter code) [US]:
|
||||
State or Province Name (full name) [CA]:
|
||||
Locality Name (eg, city) [Silicon Valley]:
|
||||
Organization Name (eg, company) [Linux Journal]:
|
||||
Organizational Unit Name (eg, section)
|
||||
↪[changeme]:SecTeam
|
||||
Common Name (eg, your name or your server's hostname)
|
||||
↪[test.linuxjournal.com]:
|
||||
Name [changeme]:test.linuxjournal.com
|
||||
Email Address [bill.childers@linuxjournal.com]:
|
||||
|
||||
Please enter the following 'extra' attributes
|
||||
to be sent with your certificate request
|
||||
A challenge password []:
|
||||
An optional company name []:
|
||||
Using configuration from
|
||||
↪/etc/openvpn/easy-rsa/openssl-1.0.0.cnf
|
||||
Check that the request matches the signature
|
||||
Signature ok
|
||||
The Subject's Distinguished Name is as follows
|
||||
countryName :PRINTABLE:'US'
|
||||
stateOrProvinceName :PRINTABLE:'CA'
|
||||
localityName :PRINTABLE:'Silicon Valley'
|
||||
organizationName :PRINTABLE:'Linux Journal'
|
||||
organizationalUnitName:PRINTABLE:'SecTeam'
|
||||
commonName :PRINTABLE:'test.linuxjournal.com'
|
||||
name :PRINTABLE:'test.linuxjournal.com'
|
||||
emailAddress
|
||||
↪:IA5STRING:'bill.childers@linuxjournal.com'
|
||||
Certificate is to be certified until Sep 1
|
||||
↪06:23:59 2025 GMT (3650 days)
|
||||
Sign the certificate? [y/n]:y
|
||||
|
||||
1 out of 1 certificate requests certified, commit? [y/n]y
|
||||
Write out database with 1 new entries
|
||||
Data Base Updated
|
||||
```
|
||||
|
||||
The next step may take a while—building the Diffie-Hellman key for the OpenVPN server. This takes several minutes on a conventional desktop-grade CPU, but on the ARM processor of the Raspberry Pi, it can take much, much longer. Have patience, as long as the dots in the terminal are proceeding, the system is building its Diffie-Hellman key (note that many dots are snipped in these examples):
|
||||
|
||||
```
|
||||
root@test:/etc/openvpn/easy-rsa# ./build-dh
|
||||
Generating DH parameters, 4096 bit long safe prime,
|
||||
↪generator 2
|
||||
This is going to take a long time
|
||||
....................................................+
|
||||
<snipped out many more dots>
|
||||
```
|
||||
|
||||
### Building the Client Certificate
|
||||
|
||||
Now you're going to generate a client key for your client to use when logging in to the OpenVPN server. OpenVPN is typically configured for certificate-based auth, where the client presents a certificate that was issued by an approved Certificate Authority:
|
||||
|
||||
```
|
||||
root@test:/etc/openvpn/easy-rsa# ./build-key
|
||||
↪bills-computer
|
||||
Generating a 4096 bit RSA private key
|
||||
...................................................++
|
||||
...................................................++
|
||||
writing new private key to 'bills-computer.key'
|
||||
-----
|
||||
You are about to be asked to enter information that
|
||||
will be incorporated into your certificate request.
|
||||
What you are about to enter is what is called a
|
||||
Distinguished Name or a DN. There are quite a few
|
||||
fields but you can leave some blank.
|
||||
For some fields there will be a default value,
|
||||
If you enter '.', the field will be left blank.
|
||||
-----
|
||||
Country Name (2 letter code) [US]:
|
||||
State or Province Name (full name) [CA]:
|
||||
Locality Name (eg, city) [Silicon Valley]:
|
||||
Organization Name (eg, company) [Linux Journal]:
|
||||
Organizational Unit Name (eg, section)
|
||||
↪[changeme]:SecTeam
|
||||
Common Name (eg, your name or your server's hostname)
|
||||
↪[bills-computer]:
|
||||
Name [changeme]:bills-computer
|
||||
Email Address [bill.childers@linuxjournal.com]:
|
||||
|
||||
Please enter the following 'extra' attributes
|
||||
to be sent with your certificate request
|
||||
A challenge password []:
|
||||
An optional company name []:
|
||||
Using configuration from
|
||||
↪/etc/openvpn/easy-rsa/openssl-1.0.0.cnf
|
||||
Check that the request matches the signature
|
||||
Signature ok
|
||||
The Subject's Distinguished Name is as follows
|
||||
countryName :PRINTABLE:'US'
|
||||
stateOrProvinceName :PRINTABLE:'CA'
|
||||
localityName :PRINTABLE:'Silicon Valley'
|
||||
organizationName :PRINTABLE:'Linux Journal'
|
||||
organizationalUnitName:PRINTABLE:'SecTeam'
|
||||
commonName :PRINTABLE:'bills-computer'
|
||||
name :PRINTABLE:'bills-computer'
|
||||
emailAddress
|
||||
↪:IA5STRING:'bill.childers@linuxjournal.com'
|
||||
Certificate is to be certified until
|
||||
↪Sep 1 07:35:07 2025 GMT (3650 days)
|
||||
Sign the certificate? [y/n]:y
|
||||
|
||||
1 out of 1 certificate requests certified,
|
||||
↪commit? [y/n]y
|
||||
Write out database with 1 new entries
|
||||
Data Base Updated
|
||||
root@test:/etc/openvpn/easy-rsa#
|
||||
```
|
||||
|
||||
Now you're going to generate an HMAC code as a shared key to increase the security of the system further:
|
||||
|
||||
```
|
||||
root@test:~# openvpn --genkey --secret
|
||||
↪/etc/openvpn/easy-rsa/keys/ta.key
|
||||
```
|
||||
|
||||
### Configuration of the Server
|
||||
|
||||
Finally, you're going to get to the meat of configuring the OpenVPN server. You're going to create a new file, /etc/openvpn/server.conf, and you're going to stick to a default configuration for the most part. The main change you're going to do is to set up OpenVPN to use TCP rather than UDP. This is needed for the next major step to work—without OpenVPN using TCP for its network communication, you can't get things working on port 443. So, create a new file called /etc/openvpn/server.conf, and put the following configuration in it: Garrick, shrink below.
|
||||
|
||||
```
|
||||
port 1194
|
||||
proto tcp
|
||||
dev tun
|
||||
ca easy-rsa/keys/ca.crt
|
||||
cert easy-rsa/keys/test.linuxjournal.com.crt ## or whatever
|
||||
↪your hostname was
|
||||
key easy-rsa/keys/test.linuxjournal.com.key ## Hostname key
|
||||
↪- This file should be kept secret
|
||||
management localhost 7505
|
||||
dh easy-rsa/keys/dh4096.pem
|
||||
tls-auth /etc/openvpn/certs/ta.key 0
|
||||
server 10.8.0.0 255.255.255.0 # The server will use this
|
||||
↪subnet for clients connecting to it
|
||||
ifconfig-pool-persist ipp.txt
|
||||
push "redirect-gateway def1 bypass-dhcp" # Forces clients
|
||||
↪to redirect all traffic through the VPN
|
||||
push "dhcp-option DNS 192.168.1.1" # Tells the client to
|
||||
↪use the DNS server at 192.168.1.1 for DNS -
|
||||
↪replace with the IP address of the OpenVPN
|
||||
↪machine and clients will use the BIND
|
||||
↪server setup earlier
|
||||
keepalive 30 240
|
||||
comp-lzo # Enable compression
|
||||
persist-key
|
||||
persist-tun
|
||||
status openvpn-status.log
|
||||
verb 3
|
||||
```
|
||||
|
||||
And last, you're going to enable IP forwarding on the server, configure OpenVPN to start on boot and start the OpenVPN service:
|
||||
|
||||
```
|
||||
root@test:/etc/openvpn/easy-rsa/keys# echo
|
||||
↪"net.ipv4.ip_forward = 1" >> /etc/sysctl.conf
|
||||
root@test:/etc/openvpn/easy-rsa/keys# sysctl -p
|
||||
↪/etc/sysctl.conf
|
||||
net.core.wmem_max = 12582912
|
||||
net.core.rmem_max = 12582912
|
||||
net.ipv4.tcp_rmem = 10240 87380 12582912
|
||||
net.ipv4.tcp_wmem = 10240 87380 12582912
|
||||
net.core.wmem_max = 12582912
|
||||
net.core.rmem_max = 12582912
|
||||
net.ipv4.tcp_rmem = 10240 87380 12582912
|
||||
net.ipv4.tcp_wmem = 10240 87380 12582912
|
||||
net.core.wmem_max = 12582912
|
||||
net.core.rmem_max = 12582912
|
||||
net.ipv4.tcp_rmem = 10240 87380 12582912
|
||||
net.ipv4.tcp_wmem = 10240 87380 12582912
|
||||
net.ipv4.ip_forward = 0
|
||||
net.ipv4.ip_forward = 1
|
||||
|
||||
root@test:/etc/openvpn/easy-rsa/keys# update-rc.d
|
||||
↪openvpn defaults
|
||||
update-rc.d: using dependency based boot sequencing
|
||||
|
||||
root@test:/etc/openvpn/easy-rsa/keys#
|
||||
↪/etc/init.d/openvpn start
|
||||
[ ok ] Starting virtual private network daemon:.
|
||||
```
|
||||
|
||||
### Setting Up OpenVPN Clients
|
||||
|
||||
Your client installation depends on the host OS of your client, but you'll need to copy your client certs and keys created above to your client, and you'll need to import those certificates and create a configuration for that client. Each client and client OS does it slightly differently and documenting each one is beyond the scope of this article, so you'll need to refer to the documentation for that client to get it running. Refer to the Resources section for OpenVPN clients for each major OS.
|
||||
|
||||
### Installing SSLH—the "Magic" Protocol Multiplexer
|
||||
|
||||
The really interesting piece of this solution is SSLH. SSLH is a protocol multiplexer—it listens on port 443 for traffic, and then it can analyze whether the incoming packet is an SSH packet, HTTPS or OpenVPN, and it can forward that packet onto the proper service. This is what enables this solution to bypass most port blocks—you use the HTTPS port for all of this traffic, since HTTPS is rarely blocked.
|
||||
|
||||
To start, `apt-get` install SSLH:
|
||||
|
||||
```
|
||||
root@test:/etc/openvpn/easy-rsa/keys# apt-get
|
||||
↪install sslh
|
||||
Reading package lists... Done
|
||||
Building dependency tree
|
||||
Reading state information... Done
|
||||
The following extra packages will be installed:
|
||||
apache2 apache2-mpm-worker apache2-utils
|
||||
↪apache2.2-bin apache2.2-common
|
||||
libapr1 libaprutil1 libaprutil1-dbd-sqlite3
|
||||
↪libaprutil1-ldap libconfig9
|
||||
Suggested packages:
|
||||
apache2-doc apache2-suexec apache2-suexec-custom
|
||||
↪openbsd-inetd inet-superserver
|
||||
The following NEW packages will be installed:
|
||||
apache2 apache2-mpm-worker apache2-utils
|
||||
↪apache2.2-bin apache2.2-common
|
||||
libapr1 libaprutil1 libaprutil1-dbd-sqlite3
|
||||
↪libaprutil1-ldap libconfig9 sslh
|
||||
0 upgraded, 11 newly installed, 0 to remove
|
||||
↪and 0 not upgraded.
|
||||
Need to get 1,568 kB of archives.
|
||||
After this operation, 5,822 kB of additional
|
||||
↪disk space will be used.
|
||||
Do you want to continue [Y/n]? y
|
||||
```
|
||||
|
||||
After SSLH is installed, the package installer will ask you if you want to run it in inetd or standalone mode. Select standalone mode, because you want SSLH to run as its own process. If you don't have Apache installed, the Debian/Raspbian package of SSLH will pull it in automatically, although it's not strictly required. If you already have Apache running and configured, you'll want to make sure it only listens on localhost's interface and not all interfaces (otherwise, SSLH can't start because it can't bind to port 443). After installation, you'll receive an error that looks like this:
|
||||
|
||||
```
|
||||
[....] Starting ssl/ssh multiplexer: sslhsslh disabled,
|
||||
↪please adjust the configuration to your needs
|
||||
[FAIL] and then set RUN to 'yes' in /etc/default/sslh
|
||||
↪to enable it. ... failed!
|
||||
failed!
|
||||
```
|
||||
|
||||
This isn't an error, exactly—it's just SSLH telling you that it's not configured and can't start. Configuring SSLH is pretty simple. Its configuration is stored in `/etc/default/sslh`, and you just need to configure the `RUN` and `DAEMON_OPTS` variables. My SSLH configuration looks like this:
|
||||
|
||||
```
|
||||
# Default options for sslh initscript
|
||||
# sourced by /etc/init.d/sslh
|
||||
|
||||
# Disabled by default, to force yourself
|
||||
# to read the configuration:
|
||||
# - /usr/share/doc/sslh/README.Debian (quick start)
|
||||
# - /usr/share/doc/sslh/README, at "Configuration" section
|
||||
# - sslh(8) via "man sslh" for more configuration details.
|
||||
# Once configuration ready, you *must* set RUN to yes here
|
||||
# and try to start sslh (standalone mode only)
|
||||
|
||||
RUN=yes
|
||||
|
||||
# binary to use: forked (sslh) or single-thread
|
||||
↪(sslh-select) version
|
||||
DAEMON=/usr/sbin/sslh
|
||||
|
||||
DAEMON_OPTS="--user sslh --listen 0.0.0.0:443 --ssh
|
||||
↪127.0.0.1:22 --ssl 127.0.0.1:443 --openvpn
|
||||
↪127.0.0.1:1194 --pidfile /var/run/sslh/sslh.pid"
|
||||
```
|
||||
|
||||
Save the file and start SSLH:
|
||||
|
||||
```
|
||||
root@test:/etc/openvpn/easy-rsa/keys#
|
||||
↪/etc/init.d/sslh start
|
||||
[ ok ] Starting ssl/ssh multiplexer: sslh.
|
||||
```
|
||||
|
||||
Now, you should be able to ssh to port 443 on your Raspberry Pi, and have it forward via SSLH:
|
||||
|
||||
```
|
||||
$ ssh -p 443 root@test.linuxjournal.com
|
||||
root@test:~#
|
||||
```
|
||||
|
||||
SSLH is now listening on port 443 and can direct traffic to SSH, Apache or OpenVPN based on the type of packet that hits it. You should be ready to go!
|
||||
|
||||
### Conclusion
|
||||
|
||||
Now you can fire up OpenVPN and set your OpenVPN client configuration to port 443, and SSLH will route it to the OpenVPN server on port 1194. But because you're talking to your server on port 443, your VPN traffic won't get blocked. Now you can land at a strange coffee shop, in a strange town, and know that your Internet will just work when you fire up your OpenVPN and point it at your Raspberry Pi. You'll also gain some encryption on your link, which will improve the privacy of your connection. Enjoy surfing the Net via your new landing point!
|
||||
|
||||
Resources
|
||||
|
||||
Installing and Configuring OpenVPN: [https://wiki.debian.org/OpenVPN](https://wiki.debian.org/OpenVPN) and [http://cryptotap.com/articles/openvpn](http://cryptotap.com/articles/openvpn)
|
||||
|
||||
OpenVPN client downloads: [https://openvpn.net/index.php/open-source/downloads.html](https://openvpn.net/index.php/open-source/downloads.html)
|
||||
|
||||
OpenVPN Client for iOS: [https://itunes.apple.com/us/app/openvpn-connect/id590379981?mt=8](https://itunes.apple.com/us/app/openvpn-connect/id590379981?mt=8)
|
||||
|
||||
OpenVPN Client for Android: [https://play.google.com/store/apps/details?id=net.openvpn.openvpn&hl=en](https://play.google.com/store/apps/details?id=net.openvpn.openvpn&hl=en)
|
||||
|
||||
Tunnelblick for Mac OS X (OpenVPN client): [https://tunnelblick.net](https://tunnelblick.net)
|
||||
|
||||
SSLH—Protocol Multiplexer: [http://www.rutschle.net/tech/sslh.shtml](http://www.rutschle.net/tech/sslh.shtml) and [https://github.com/yrutschle/sslh](https://github.com/yrutschle/sslh)
|
||||
|
||||
|
||||
----------
|
||||
via: http://www.linuxjournal.com/content/securi-pi-using-raspberry-pi-secure-landing-point?page=0,0
|
||||
|
||||
作者:[Bill Childers][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxjournal.com/users/bill-childers
|
||||
|
||||
|
||||
@ -1,15 +1,16 @@
|
||||
Linux / Unix Desktop Fun: Christmas Tree For Your Terminal
|
||||
Linux / Unix桌面之趣:终端上的圣诞树
|
||||
================================================================================
|
||||
Let us create Linux or Unix console Christmas tree just for fun and profit. First, you need to install a Perl module called Acme::POE::Tree. It is an animated Christmas tree module. I've tested this on Linux, OS X and Unix-like system.
|
||||
给你的Linux或Unix控制台创造一棵圣诞树玩玩吧。在此之前,需要先安装一个Perl模块,命名为Acme::POE::Tree。这是一棵很喜庆的圣诞树,我已经在Linux、OSX和类Unix系统上验证过了。
|
||||
|
||||
### Install Acme::POE::Tree ###
|
||||
|
||||
The easiest way to install any perl module is to use the cpan (Comprehensive Perl Archive Network). Open the terminal application and type the following command to install Acme::POE::Tree:
|
||||
### 安装 Acme::POE::Tree ###
|
||||
|
||||
## run as root ##
|
||||
安装perl模块最简单的办法就是使用cpan(Perl综合典藏网)。打开终端,把下面的指令敲进去便可安装Acme::POE::Tree。
|
||||
|
||||
## 以root身份运行 ##
|
||||
perl -MCPAN -e 'install Acme::POE::Tree'
|
||||
|
||||
**Sample outputs:**
|
||||
**案例输出:**
|
||||
|
||||
Installing /home/vivek/perl5/man/man3/POE::NFA.3pm
|
||||
Installing /home/vivek/perl5/man/man3/POE::Kernel.3pm
|
||||
@ -42,21 +43,21 @@ The easiest way to install any perl module is to use the cpan (Comprehensive Per
|
||||
RCAPUTO/Acme-POE-Tree-1.022.tar.gz
|
||||
[dependencies] -- NA
|
||||
|
||||
### Show Christmas tree in the shell ###
|
||||
### 在Shell中显示圣诞树 ###
|
||||
|
||||
Simply type the following command:
|
||||
只需要在终端上运行以下命令:
|
||||
|
||||
perl -MAcme::POE::Tree -e 'Acme::POE::Tree->new()->run()'
|
||||
|
||||
**Sample outputs:**
|
||||
**案例输出**
|
||||
|
||||

|
||||
|
||||
Gif 01: An animated christmas tree in Perl
|
||||
Gif 01: 一棵用Perl写的喜庆圣诞树
|
||||
|
||||
### Tree customization ###
|
||||
### 树的定制 ###
|
||||
|
||||
Here is my tree.pl:
|
||||
以下是我的脚本文件tree.pl的内容:
|
||||
|
||||
#!/usr/bin/perl
|
||||
|
||||
@ -70,14 +71,14 @@ Here is my tree.pl:
|
||||
);
|
||||
$tree->run();
|
||||
|
||||
Now can play with your tree modifying star_delay, run_for, and light_delay. And ,there you have it a a Christmas tree in your shell for fun.
|
||||
这样就可以通过修改star_delay、run_for和light_delay参数的值来自定义你的树了。一棵提供消遣的终端圣诞树就此诞生。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.cyberciti.biz/open-source/command-line-hacks/linux-unix-desktop-fun-christmas-tree-for-your-terminal/
|
||||
|
||||
作者:Vivek Gite
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[soooogreen](https://github.com/soooogreen)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
Loading…
Reference in New Issue
Block a user