mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-25 23:11:02 +08:00
Merge branch 'master' of https://github.com/LCTT/TranslateProject
This commit is contained in:
commit
40b331abdb
@ -1,12 +1,12 @@
|
||||
在CentOS或者Redhat中如何为Apache Tomcat绑定IPv4
|
||||
如何在 CentOS/RHEL 中为 Apache Tomcat 绑定 IPv4 地址
|
||||
================================================================================
|
||||
今天我们来学习一下如何在CentOS 7 Linux分布式系统中为Tomcat绑定IPv4
|
||||
今天我们来学习一下如何在CentOS 7 Linux分布式系统中为Tomcat绑定IPv4。
|
||||
|
||||
**Apache Tomcat** 是由[Apache Software Foundation][1] 开发的开源web服务器和servlet容器。它实现了Java Servlet,JavaServer页面(JSP),Java的统一表达式语言,以及Sun Microsystems的Java的WebSocket规范,并提供了一个运行java代码的web服务器环境。
|
||||
**Apache Tomcat** 是由[Apache 软件基金会][1] 开发的开源web服务器和servlet容器。它实现了Java Servlet,JavaServer页面(JSP),Java的统一表达式语言,以及Sun Microsystems的Java的WebSocket规范,并提供了一个运行java代码的web服务器环境。
|
||||
|
||||
如果由于默认绑定tomcat到IPv6而导致我们的web服务器不能正常工作,就有必要将tomcat绑定到IPv4。众所周知,IPv6是为设备分配IP地址的现代方法,虽然在不久的将来也许会得到应用,但是现在并没有得到完全应用。由于没有用处,目前我们并不需要将我们的Tomcat服务器向IPv6转换,我们应该将其绑定到IPv4。
|
||||
如果由于tomcat默认绑定到IPv6而导致我们的web服务器不能正常工作,就有必要将tomcat绑定到IPv4。众所周知,IPv6是为设备分配IP地址的现代方法,虽然在不久的将来也许会得到应用,但是现在并没有得到完全应用。由于没有用处,目前我们并不需要将我们的Tomcat服务器向IPv6转换,我们应该将其绑定到IPv4。
|
||||
|
||||
在开始将tomcat绑定到IPv4之前,我们应该确保在我们的CentOS 7中已经安装了tomcat。这是一个[如何在CentOS 7.0服务器中安装tomcat 8][2]的指导。
|
||||
在开始将tomcat绑定到IPv4之前,我们应该确保在我们的CentOS 7中已经安装了tomcat。可以看这个[如何在CentOS 7.0服务器中安装tomcat 8][2]的指导。
|
||||
|
||||
### 1. 切换到tomcat用户 ###
|
||||
|
||||
@ -32,13 +32,13 @@
|
||||
|
||||
### 3. 配置 Catalina.sh ###
|
||||
|
||||
如图所示,我们将在catalina.sh脚本文件的最后增加一行 **JAVA_OPTS= "$JAVA_OPTS -Djava.net.preferIPv4Stack=true -Djava.net.preferIPv4Addresses"**。我们可以使用我们喜欢的文本编辑器来编辑这个文件,例如nano,vim等等。这里我们使用nano。
|
||||
如图所示,我们将在catalina.sh脚本文件的最后增加一行 `JAVA_OPTS= "$JAVA_OPTS -Djava.net.preferIPv4Stack=true -Djava.net.preferIPv4Addresses"`。我们可以使用我们喜欢的文本编辑器来编辑这个文件,例如nano、vim等等。这里我们使用nano。
|
||||
|
||||
$ nano catalina.sh
|
||||
|
||||

|
||||
|
||||
然后,如下图所示,将 **JAVA_OPTS= "$JAVA_OPTS -Djava.net.preferIPv4Stack=true -Djava.net.preferIPv4Addresses"** 增加到文件。
|
||||
然后,如下图所示,将该行增加到文件。
|
||||
|
||||

|
||||
|
||||
@ -60,7 +60,7 @@
|
||||
|
||||
### 结尾 ###
|
||||
|
||||
好了,我们终于将我们运行在CentOS 7 Linux分布式系统上的tomcat服务器绑定到IPv4上了。尽管IPv6在不久的将来也许会得到应用,但由于现在还没有使用,如果因为将你的Tomcat服务器绑定到IPv6上而使得你的tomcat服务器不工作,就有必要将tomcat绑定到IPv4上,这也很简单。如果你有任何疑问,建议,反馈,请在下面的评论框中写下来,让我们知道有什么需要增加或者改进。非常感谢!
|
||||
好了,我们终于将我们运行在CentOS 7 Linux发行版上的tomcat服务器绑定到IPv4上了。尽管IPv6在不久的将来也许会得到应用,但由于现在还没有使用,如果因为将你的Tomcat服务器绑定到IPv6上而使得你的tomcat服务器不工作,就有必要将tomcat绑定到IPv4上,这也很简单。如果你有任何疑问,建议,反馈,请在下面的评论框中写下来,让我们知道有什么需要增加或者改进。非常感谢!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -68,7 +68,7 @@ via: http://linoxide.com/linux-how-to/bind-apache-tomcat-ipv4-centos/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[ictlyh](https://github.com/ictlyh)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,161 @@
|
||||
在 Apache、NGINX 和 Lighttpd 上启用 HTTP 公钥固定扩展(HPKP)
|
||||
================================================================================
|
||||
|
||||
公钥固定(Public Key Pinning)是指一个证书链中必须包含一个白名单中的公钥,也就是说只有被列入白名单的证书签发机构(CA)才能为某个域名`*.example.com`签发证书,而不是你的浏览器中所存储的任何 CA 都可以为之签发。本文讲述了这种机制的背景知识,并提供了 Apache、 Lighttpd 和 NGINX 上的配置范例。
|
||||
|
||||
### HTTP 公钥固定扩展 ###
|
||||
|
||||
用你使用的银行做个例子,它一直使用 CA 公司 A 为其签发证书。但是在当前的证书体系下,CA 公司 B、CA 公司 C 和 NSA 的 CA 都能给你的银行创建证书,而你的浏览器会毫无疑虑的接受它们,因为这些公司都是你所信任的根 CA。
|
||||
|
||||
如果你的银行实现了 HPKP 并固定了它们的第一个中级证书(来自 CA 公司 A),那么浏览器将不会接受来自CA 公司 B 和 CA 公司 C 的证书,即便它们也有一个有效的信任链。HPKP 也允许你的浏览器将这种违例行为报告给该银行,以便银行知道被伪造证书攻击了。
|
||||
|
||||
HTTP 公钥固定扩展是一个从2011年开始开发的针对 HTTP 用户代理(即浏览器)的公钥固定标准。它由 Google 发起,甚至在 Chrome 中实现的固定机制可以使用一个人工维护的网站公钥固定列表,这个列表包含了固定的几个网站的公钥签名。(LCTT 译注:Chrome 和 FireFox 32 及以后版本都支持公钥固定机制,并使用内置的人工维护的公钥固定列表数据,这些数据随着浏览器软件的更新而更新,主要包括几个大型站点。目前还只有 Chrome 38+ 支持通过 HTTP 响应头传递公钥固定信息。)
|
||||
|
||||
以下是 HPKP 的几个功能简述:
|
||||
|
||||
- HPKP 是在 HTTP 层面设置的,使用 `Public-Key-Pins` (PKP)响应头。
|
||||
- 该规则的保留周期通过 max-age 参数设置,单位是秒。
|
||||
- PKP 响应头只能用于正确的安全加密通讯里面。
|
||||
- 如果出现了多个这样的响应头,则只处理第一个。
|
||||
- 固定机制可以使用`includeSubDomains`参数扩展到子域。
|
||||
- 当接收到一个新的 PKP 响应头时,它会覆盖之前存储的公钥固定和元数据。
|
||||
- 公钥固定是用哈希算法生成的,其实是一个“主题公钥信息(SKPI)”指纹。
|
||||
|
||||
本文首先会介绍一些 HPKP 工作的原理,接下来我们会展示给你如何得到需要的指纹并配置到 web 服务器中。
|
||||
|
||||
### SPKI 指纹 - 理论 ###
|
||||
|
||||
以下摘自 Adam Langley 的[帖子][1],我们哈希的是一个公钥,而不是证书:
|
||||
|
||||
> 通常来说,对证书进行哈希是一个显而易见的解决方案,但是其实这是错的。不能这样做的原因是 CA 证书可以不断重新签发:同一个公钥、主题名可以对应多个证书,而这些证书有不同的延展或失效时间。浏览器从下至上地在证书池中构建证书链时,另外一个版本的证书可能就替代匹配了你原本所期望的证书。
|
||||
>
|
||||
> 举个例子,StartSSL 有两个根证书:一个是以 SHA1 签名的,另外是一个是 SHA256。如果你希望固定住 StartSSL 作为你的 CA,那么你该使用哪个证书呢?你也许可以使用这两个,但是如果我不告诉你,你怎么会知道还有一个根证书呢?
|
||||
>
|
||||
> 相反地,对公钥进行哈希则不会有这个问题:
|
||||
>
|
||||
> 浏览器假定子证书是固定不动的:它总是证书链的起点。子证书所携带的签名一定是一个有效的签名,它来自其父证书给这个证书专门签发的。这就是说,父证书的公钥相对于子证书来说是固定的。所以可推论公钥链是固定的。
|
||||
>
|
||||
> 唯一的问题是你不能固定到一个交叉认证的根证书上。举个例子,GoDaddy 的根证书是 Valicert 签名的,这是为了让那些不能识别 GoDaddy 根证书的老客户可以信任其证书。然而,你不能固定到 Valicert 上,因为新的客户在证书链上发现了 GoDaddy 证书就会停止上溯(LCTT 译注:所以就找不到固定信息了)。
|
||||
>
|
||||
> 此外,我们是对 SubjectPublicKeyInfo(SPKI)进行哈希而不是对公钥位串。SPKI 包括了公钥类型、公钥自身及其相关参数。这很重要,因为如果对公钥进行哈希就有可能导致发生曲解攻击。对于一个 Diffie-Hellman 公钥而言:如果仅对公钥进行哈希,而不是对完整的 SPKI,那么攻击者可以使用同样的公钥而让客户端将其解释为其它组。同样地,这样也有可能强制将一个 RSA 密钥当成 DSA 密钥解释等等。
|
||||
|
||||
### 固定在哪里 ###
|
||||
|
||||
你应该固定在什么地方?固定你自己的公钥并不是一个最好的办法。你的密钥也许会改变或撤销。你也许会使用多个证书,经常轮换证书的话密钥就改变了。也许由于服务器被入侵而撤销证书。
|
||||
|
||||
最容易但是不是太安全的方法是固定第一个中级 CA 证书。该证书是签名在你的网站证书之上的,所以签发该证书的 CA 的公钥肯定是在证书链上的。
|
||||
|
||||
采用这种方法你可以从同一个 CA 更新你的证书而不用担心固定信息不对。如果该 CA 发行了一个不同的根证书,也许你会遇到一些问题,对此并没有太好的解决方案。不过你可以通过如下做法来减轻这种问题的影响:
|
||||
|
||||
- 从一个不同的 CA 申请一个备用的证书,并固定该备份。
|
||||
|
||||
RFC 里面说你至少需要做两个固定。一个是当前连接所使用的证书链上的,另外一个是备份的。
|
||||
|
||||
另外的固定是对备份公钥的,它可以是来自另外一个给你签发证书的不同 CA 的 SKPI 指纹。
|
||||
|
||||
在这个问题上还有一种**更安全**的方法,就是事先创建好至少三个独立的公钥(使用 OpenSSL,参见[此页][2] 了解 Javascript OpenSSL 命令生成器),并将其中两个备份到一个安全的地方,离线存储、不要放到网上。
|
||||
|
||||
为这三个证书创建 SPKI 指纹并固定它们,然后仅使用第一个作为当前的证书。当需要时,你可以使用备份密钥之一。不过你需要让 CA 给你做签名来生成证书对,这可能需要几天,依你的 CA 的工作情况而定。
|
||||
|
||||
对于 HPKP 来说这没有问题,因为我们使用的是公钥的 SPKI 哈希,而不是证书。失效或不同的 CA 签名链并不影响。
|
||||
|
||||
如果你按照上述方法生成并安全存储了至少三个独立的密钥,并固定它们,也可以防止你的 CA 撤销你的网站证书并签发一个假证书时出现问题。
|
||||
|
||||
### SPKI 指纹 ###
|
||||
|
||||
可以使用如下的 OpenSSL 命令来生成 SPKI 指纹,它出现在 [RFC 草案][3] 中:
|
||||
|
||||
openssl x509 -noout -in certificate.pem -pubkey | \
|
||||
openssl asn1parse -noout -inform pem -out public.key;
|
||||
openssl dgst -sha256 -binary public.key | openssl enc -base64
|
||||
|
||||
结果:
|
||||
|
||||
klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY=
|
||||
|
||||
上面输入的 `certificate.pem` 文件是本站(https://raymii.org)的证书链中第一个证书。(在写本文时, `COMODO RSA Domain Validation Secure Server CA, 序列号 2B:2E:6E:EA:D9:75:36:6C:14:8A:6E:DB:A3:7C:8C:07 。`)。
|
||||
|
||||
你也需要同样对你的另外两个备份公钥生成指纹。
|
||||
|
||||
### 故障 ###
|
||||
|
||||
在写本文时(2015/1),唯一支持 HPKP 的浏览器(chrome)有一个严重的问题:Chrome 并不能够区分 HSTS 和 HPKP 响应头中的 max-age 和 includeSubdomains 参数。也就是说,如果你的 HSTS 和 HPKP 设置了不同的 max-age 和 includeSubdomains 参数,它们会互相搞乱。关于这个故障的更多信息参见:[https://code.google.com/p/chromium/issues/detail?id=444511][4]。感谢 Scott Helme([https://scotthelme.co.uk][5])发现并告诉我这个 Chromium 项目的问题。
|
||||
|
||||
### Web 服务器配置 ###
|
||||
|
||||
下面你可以看到三个主流 Web 服务器的配置方法。这只是一个 HTTP 响应头,绝大多数 Web 服务器都可以设置它。它只需要设置到 HTTPS 网站上。
|
||||
|
||||
下面的例子固定到 `COMODO RSA Domain Validation Secure Server CA` 及备份的 `Comodo PositiveSSL` CA 上,30天失效期,包括所有的子域。
|
||||
|
||||
|
||||
#### Apache ####
|
||||
|
||||
编辑你的 Apache 配置文件(如 `/etc/apache2/sites-enabled/website.conf 或 /etc/apache2/httpd.conf`),并添加下列行到你的 VirtualHost 中:
|
||||
|
||||
# 如需要,载入 headers 模块。
|
||||
LoadModule headers_module modules/mod_headers.so
|
||||
|
||||
Header set Public-Key-Pins "pin-sha256=\"klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY=\"; pin-sha256=\"633lt352PKRXbOwf4xSEa1M517scpD3l5f79xMD9r9Q=\"; max-age=2592000; includeSubDomains"
|
||||
|
||||
#### Lighttpd ####
|
||||
|
||||
Lighttpd 更简单一些,将下列行添加到你的 Lighttpd 配置文件(如 `/etc/lighttpd/lighttpd.conf`):
|
||||
|
||||
server.modules += ( "mod_setenv" )
|
||||
$HTTP["scheme"] == "https" {
|
||||
setenv.add-response-header = ( "Public-Key-Pins" => "pin-sha256=\"klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY=\"; pin-sha256=\"633lt352PKRXbOwf4xSEa1M517scpD3l5f79xMD9r9Q=\"; max-age=2592000; includeSubDomains")
|
||||
}
|
||||
|
||||
#### NGINX ####
|
||||
|
||||
NGINX 的配置更简短。添加以下行到你的 HTTPS 配置的 server 块中:
|
||||
|
||||
add_header Public-Key-Pins 'pin-sha256="klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY="; pin-sha256="633lt352PKRXbOwf4xSEa1M517scpD3l5f79xMD9r9Q="; max-age=2592000; includeSubDomains';
|
||||
|
||||
### 报告功能 ###
|
||||
|
||||
HPKP 报告功能允许浏览器报告任何违例给你。
|
||||
|
||||
如果你在响应头中添加了附加的 `report-uri="http://example.org/hpkp-report"` 参数,并用该 URI 处理接收到的数据的话,客户端会在发现违例时发送报告给你。这个报告是以 POST 方式发送到你指定的 report-uri 上,并以类似下面的 JSON 格式:
|
||||
|
||||
{
|
||||
"date-time": "2014-12-26T11:52:10Z",
|
||||
"hostname": "www.example.org",
|
||||
"port": 443,
|
||||
"effective-expiration-date": "2014-12-31T12:59:59",
|
||||
"include-subdomains": true,
|
||||
"served-certificate-chain": [
|
||||
"-----BEGINCERTIFICATE-----\nMIIAuyg[...]tqU0CkVDNx\n-----ENDCERTIFICATE-----"
|
||||
],
|
||||
"validated-certificate-chain": [
|
||||
"-----BEGINCERTIFICATE-----\nEBDCCygAwIBA[...]PX4WecNx\n-----ENDCERTIFICATE-----"
|
||||
],
|
||||
"known-pins": [
|
||||
"pin-sha256=\"dUezRu9zOECb901Md727xWltNsj0e6qzGk\"",
|
||||
"pin-sha256=\"E9CqVKB9+xZ9INDbd+2eRQozqbQ2yXLYc\""
|
||||
]
|
||||
}
|
||||
|
||||
### 非强制,只报告 ###
|
||||
|
||||
HPKP 也可以设置为非强制的,可以使用 `Public-Key-Pins-Report-Only` 来只发送违例报告给你。
|
||||
|
||||
这样可以让你在网站不可访问或 HPKP 配置不正确时不固定,之后你可以将这个响应头改为 `Public-Key-Pins` 来强制固定。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://raymii.org/s/articles/HTTP_Public_Key_Pinning_Extension_HPKP.html
|
||||
|
||||
作者:[Remy van Elst][a]
|
||||
译者:[wxy](https://github.com/wxy)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://raymii.org/
|
||||
[1]:http://www.imperialviolet.org/2011/05/04/pinning.html
|
||||
[2]:https://raymii.org/s/software/OpenSSL_Command_Generator.html
|
||||
[3]:https://tools.ietf.org/html/draft-ietf-websec-key-pinning-21#appendix-A
|
||||
[4]:https://code.google.com/p/chromium/issues/detail?id=444511
|
||||
[5]:https://scotthelme.co.uk/
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by H-mudcup
|
||||
Ambient Noise Player for Ubuntu Plays Relaxing Sounds to Keep You Creative
|
||||
================================================================================
|
||||

|
||||
@ -52,4 +53,4 @@ via: http://www.omgubuntu.co.uk/2015/04/ambient-noise-player-app-for-ubuntu-linu
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://anoise.tuxfamily.org/
|
||||
[1]:http://anoise.tuxfamily.org/
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
Translating by ictlyh
|
||||
How to Show Dialog Box from Bash Shell Script with Examples
|
||||
================================================================================
|
||||
This tutorial will give couple of examples on how to use utilities like zenity and whiptail in your Bash shell script to provide message / dialog box . With these utilities your script will be able to inform user about the current state of execution, or give an ability to interact. Difference between these two utilities is the way they are displaying message box or dialog. Zenity uses GTK toolkit for creating graphical user interfaces, while whiptail creates message boxes inside terminal window.
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
demon 翻译中
|
||||
How to manage remote MySQL databases on Linux VPS using a GUI tool
|
||||
================================================================================
|
||||
If you need to run a MySQL server on a remote [VPS instance][1], how will you manage databases hosted by the server remotely? Perhaps web-based database administration tools such as [phpMyAdmin][2] or [Adminer][3] will first come to mind. These web-based management tools require a backend web server and PHP engine up and running. However, if your VPS instance is used as a standalone database server (e.g., for a multi-tier app), provisioning a whole LAMP stack for occasional database management is a waste of VPS resource. Worse, the LAMP stack with an additional HTTP port can be a source of security vulnerabilities of your VPS.
|
||||
@ -175,4 +176,4 @@ via: http://xmodulo.com/remote-mysql-databases-gui-tool.html
|
||||
[4]:http://mysqlworkbench.org/
|
||||
[5]:http://dev.mysql.com/downloads/repo/apt/
|
||||
[6]:http://dev.mysql.com/downloads/repo/yum/
|
||||
[7]:http://xmodulo.com/how-to-allow-remote-access-to-mysql.html
|
||||
[7]:http://xmodulo.com/how-to-allow-remote-access-to-mysql.html
|
||||
|
||||
@ -1,158 +0,0 @@
|
||||
HTTP Public Key Pinning Extension HPKP for Apache, NGINX and Lighttpd
|
||||
================================================================================
|
||||
Public Key Pinning means that a certificate chain must include a whitelisted public key. It ensures only whitelisted Certificate Authorities (CA) can sign certificates for `*.example.com`, and not any CA in your browser store. This article has background theory and configuration examples for Apache, Lighttpd and NGINX.
|
||||
|
||||
### HTTP Public Key Pinning Extension ###
|
||||
|
||||
An example might be your bank, which always have their certificate from CA Company A. With the current certificate system, CA Company B, CA Company C and the NSA CA can all create a certificate for your bank, which your browser will hapily accept because those companies are also trusted root CA's.
|
||||
|
||||
If the bank implements HPKP and pin's their first intermidiate certificate (from CA Company A), browsers will not accept certificates from CA Company B and CA Company C, even if they have a valid trust path. HPKP also allows your browser to report back the failure to the bank, so that they know they are under attack.
|
||||
|
||||
Public Key Pinning Extension for HTTP (HPKP) is a standard for public key pinning for HTTP user agents that's been in development since 2011. It was started by Google, which, even though it had implemented pinning in Chrome, understood that manually maintaining a list of pinned sites can't scale.
|
||||
|
||||
Here is a quick feature overview of HPKP:
|
||||
|
||||
- HPKP is set at the HTTP level, using the `Public-Key-Pins` response header.
|
||||
- The policy retention period is set with the max-age parameter, it specifies duration in seconds.
|
||||
- The PKP header can only be used over an error-free secure encryption.
|
||||
- If multiple headers are seen, only the first one is processed.
|
||||
- Pinning can be extended to subdomains with the `includeSubDomains` parameter.
|
||||
- When a new PKP header is received, it overwrites previously stored pins and metadata.
|
||||
- A pin consists out of the hashing algorithm and an "Subject Public Key Info" fingerprint.
|
||||
|
||||
This article first has some theory about the workings of HPKP, down below you'll find the part which shows you how to get the required fingerprints and has web server configuration.
|
||||
|
||||
### SPKI Fingerprint - Theory ###
|
||||
|
||||
As explained by Adam Langley in [his post][1], we hash a public key, not a certificate:
|
||||
|
||||
> In general, hashing certificates is the obvious solution, but the wrong one. The problem is that CA certificates are often reissued: there are multiple certificates with the same public key, subject name etc but different extensions or expiry dates. Browsers build certificates chains from a pool of certificates, bottom up, and an alternative version of a certificate might be substituted for the one that you expect.
|
||||
>
|
||||
> For example, StartSSL has two root certificates: one signed with SHA1 and the other with SHA256. If you wished to pin to StartSSL as your CA, which certificate hash would you use? You would have to use both, but how would you know about the other root if I hadn't just told you?
|
||||
>
|
||||
> Conversely, public key hashes must be correct:
|
||||
>
|
||||
> Browsers assume that the leaf certificate is fixed: it's always the starting point of the chain. The leaf certificate contains a signature which must be a valid signature, from its parent, for that certificate. That implies that the public key of the parent is fixed by the leaf certificate. So, inductively, the chain of public keys is fixed, modulo truncation.
|
||||
>
|
||||
> The only sharp edge is that you mustn't pin to a cross-certifying root. For example, GoDaddy's root is signed by Valicert so that older clients, which don't recognise GoDaddy as a root, still trust those certificates. However, you wouldn't want to pin to Valicert because newer clients will stop their chain at GoDaddy.
|
||||
>
|
||||
> Also, we're hashing the SubjectPublicKeyInfo not the public key bit string. The SPKI includes the type of the public key and some parameters along with the public key itself. This is important because just hashing the public key leaves one open to misinterpretation attacks. Consider a Diffie-Hellman public key: if one only hashes the public key, not the full SPKI, then an attacker can use the same public key but make the client interpret it in a different group. Likewise one could force an RSA key to be interpreted as a DSA key etc.
|
||||
|
||||
### Where to Pin ###
|
||||
|
||||
Where should you pin? Pinning your own public key is not the best idea. The key might change or get compromised. You might have multiple certificates in use. The key might change because you rotate your certificates every so often. It might key compromised because the web server was hacked.
|
||||
|
||||
The easiest, but not most secure place to pin is the first intermediate CA certificate. The signature of that certificate is on your websites certificate so the issuing CA's public key must always be in the chain.
|
||||
|
||||
This way you can renew your end certificate from the same CA and have no pinning issues. If the CA issues a different root, then you have a problem, there is no clear solution for this yet. There is one thing you can do to mitigate this:
|
||||
|
||||
- Always have a backup pin and a spare certificate from a different CA.
|
||||
|
||||
The RFC states that you need to provide at least two pins. One of the pins must be present in the chain used in the connection over which the pins were received, the other pin must not be present.
|
||||
|
||||
This other pin is your backup public key. It can also be the SPKI fingerprint of a different CA where you have a certificate issued.
|
||||
|
||||
An alternative and **more secure** take on this issue is to create at least three seperate public keys beforehand (using OpenSSL, see [this page][2] for a Javascript OpenSSL command generator) and to keep two of those keys as a backup in a safe place, offline and off-site.
|
||||
|
||||
You create the SPKI hashes for the three certificates and pin those. You only use the first key as the active certificate. When it is needed, you can then use one of the alternative keys. You do however need to let that certificate sign by a CA to create a certificate pair and that process can take a few days depending on the certificate.
|
||||
|
||||
This is not a problem for the HPKP because we take the SPKI hash of the public key, and not of the certificate. Expiration or a different chain of CA signer do not matter in this case.
|
||||
|
||||
If you have the means and procedures to create and securely save at least three seperate keys as described above and pin those, it would also protect you from your CA provider getting compromised and giving out a fake certificate for your specific website.
|
||||
|
||||
### SPKI Fingerprint ###
|
||||
|
||||
To get the SPKI fingerprint from a certificate we can use the following OpenSSL command, as shown in [the RFC draft][3]:
|
||||
|
||||
openssl x509 -noout -in certificate.pem -pubkey | \
|
||||
openssl asn1parse -noout -inform pem -out public.key;
|
||||
openssl dgst -sha256 -binary public.key | openssl enc -base64
|
||||
|
||||
Result:
|
||||
|
||||
klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY=
|
||||
|
||||
The input `certificate.pem` file is the first certificate in the chain for this website. (At the time of writing, `COMODO RSA Domain Validation Secure Server CA, Serial 2B:2E:6E:EA:D9:75:36:6C:14:8A:6E:DB:A3:7C:8C:07.`)
|
||||
|
||||
You need to also do this with your backup public key, ending up with two fingerprints.
|
||||
|
||||
### Bugs ###
|
||||
|
||||
At the time of writing this article (2015-Jan) the only browser supporting HPKP (Chrome) has a serious issue where Chrome doesn't treat the max-age and includeSubdomains directives from HSTS and HPKP headers as mutually exclusive. This means that if you have HSTS and HPKP with different policiesfor max-age or includeSubdomains they will be interchanged. See this bug for more info: [https://code.google.com/p/chromium/issues/detail?id=444511][4]. Thanks to Scott Helme from [https://scotthelme.co.uk][5] for finding and notifying me and the Chromium project about it.
|
||||
|
||||
### Webserver configuration ###
|
||||
|
||||
Below you'll find configuration instructions for the three most populair web servers. Since this is just a HTTP header, almost all web servers will allow you to set this. It needs to be set for the HTTPS website.
|
||||
|
||||
The example below pins the `COMODO RSA Domain Validation Secure Server CA` and the `Comodo PositiveSSL` CA 2 as a backup, with a 30 day expire time including all subdomains.
|
||||
|
||||
#### Apache ####
|
||||
|
||||
Edit your apache configuration file (`/etc/apache2/sites-enabled/website.conf or /etc/apache2/httpd.conf` for example) and add the following to your VirtualHost:
|
||||
|
||||
# Optionally load the headers module:
|
||||
LoadModule headers_module modules/mod_headers.so
|
||||
|
||||
Header set Public-Key-Pins "pin-sha256=\"klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY=\"; pin-sha256=\"633lt352PKRXbOwf4xSEa1M517scpD3l5f79xMD9r9Q=\"; max-age=2592000; includeSubDomains"
|
||||
|
||||
#### Lighttpd ####
|
||||
|
||||
The lighttpd variant is just as simple. Add it to your Lighttpd configuration file (`/etc/lighttpd/lighttpd.conf` for example):
|
||||
|
||||
server.modules += ( "mod_setenv" )
|
||||
$HTTP["scheme"] == "https" {
|
||||
setenv.add-response-header = ( "Public-Key-Pins" => "pin-sha256=\"klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY=\"; pin-sha256=\"633lt352PKRXbOwf4xSEa1M517scpD3l5f79xMD9r9Q=\"; max-age=2592000; includeSubDomains")
|
||||
}
|
||||
|
||||
#### NGINX ####
|
||||
|
||||
NGINX is even shorter with its config. Add this in the server block for your HTTPS configuration:
|
||||
|
||||
add_header Public-Key-Pins 'pin-sha256="klO23nT2ehFDXCfx3eHTDRESMz3asj1muO+4aIdjiuY="; pin-sha256="633lt352PKRXbOwf4xSEa1M517scpD3l5f79xMD9r9Q="; max-age=2592000; includeSubDomains';
|
||||
|
||||
### Reporting ###
|
||||
|
||||
HPKP reporting allows the user-agent to report any failures back to you.
|
||||
|
||||
If you add an aditional `report-uri="http://example.org/hpkp-report`" parameter to the header and set up a listener there, clients will send reports if they encounter a failure. A report is sent as a POST request to the report-uri with a JSON body like this:
|
||||
|
||||
{
|
||||
"date-time": "2014-12-26T11:52:10Z",
|
||||
"hostname": "www.example.org",
|
||||
"port": 443,
|
||||
"effective-expiration-date": "2014-12-31T12:59:59",
|
||||
"include-subdomains": true,
|
||||
"served-certificate-chain": [
|
||||
"-----BEGINCERTIFICATE-----\nMIIAuyg[...]tqU0CkVDNx\n-----ENDCERTIFICATE-----"
|
||||
],
|
||||
"validated-certificate-chain": [
|
||||
"-----BEGINCERTIFICATE-----\nEBDCCygAwIBA[...]PX4WecNx\n-----ENDCERTIFICATE-----"
|
||||
],
|
||||
"known-pins": [
|
||||
"pin-sha256=\"dUezRu9zOECb901Md727xWltNsj0e6qzGk\"",
|
||||
"pin-sha256=\"E9CqVKB9+xZ9INDbd+2eRQozqbQ2yXLYc\""
|
||||
]
|
||||
}
|
||||
|
||||
### No Enforcment, report only ###
|
||||
|
||||
HPKP can be set up without enforcement, in reporting mode by using the `Public-Key-Pins-Report-Only` response header.
|
||||
|
||||
This approach allows you to set up pinning without your site being unreachable or HPKP being configured incorrectly. You can later move to enforcement by changing the header back to `Public-Key-Pins`.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://raymii.org/s/articles/HTTP_Public_Key_Pinning_Extension_HPKP.html
|
||||
|
||||
作者:[Remy van Elst][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://raymii.org/
|
||||
[1]:http://www.imperialviolet.org/2011/05/04/pinning.html
|
||||
[2]:https://raymii.org/s/software/OpenSSL_Command_Generator.html
|
||||
[3]:https://tools.ietf.org/html/draft-ietf-websec-key-pinning-21#appendix-A
|
||||
[4]:https://code.google.com/p/chromium/issues/detail?id=444511
|
||||
[5]:https://scotthelme.co.uk/
|
||||
@ -0,0 +1,130 @@
|
||||
14 Useful Examples of Linux ‘sort’ Command – Part 1
|
||||
================================================================================
|
||||
Sort is a Linux program used for printing lines of input text files and concatenation of all files in sorted order. Sort command takes blank space as field separator and entire Input file as sort key. It is important to notice that sort command don’t actually sort the files but only print the sorted output, until your redirect the output.
|
||||
|
||||
This article aims at deep insight of Linux ‘sort‘ command with 14 useful practical examples that will show you how to use sort command in Linux.
|
||||
|
||||
### 1. First we will be creating a text file (tecmint.txt) to execute ‘sort‘ command examples. Our working directory is ‘/home/$USER/Desktop/tecmint. ###
|
||||
|
||||
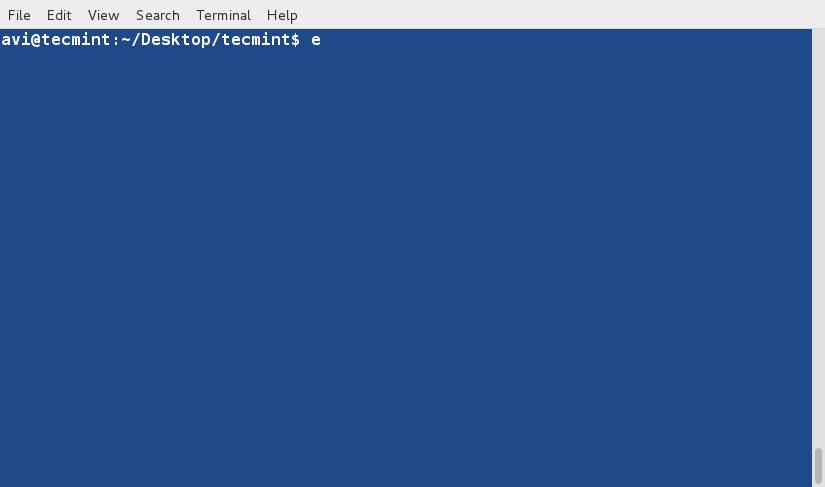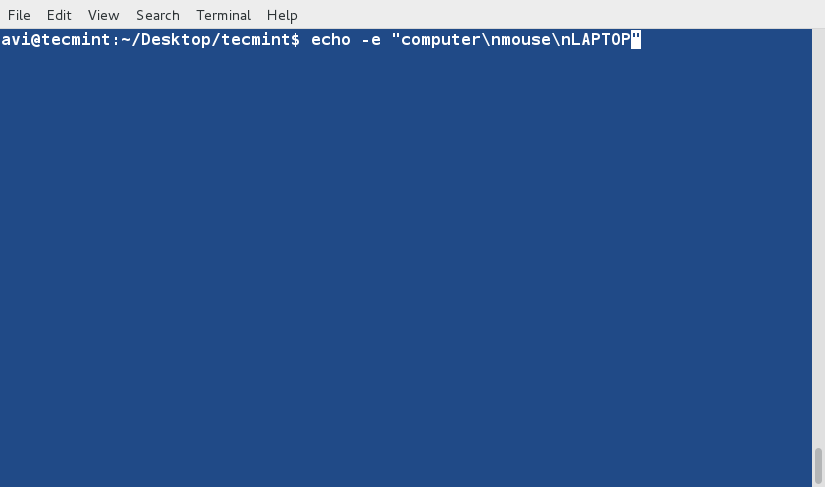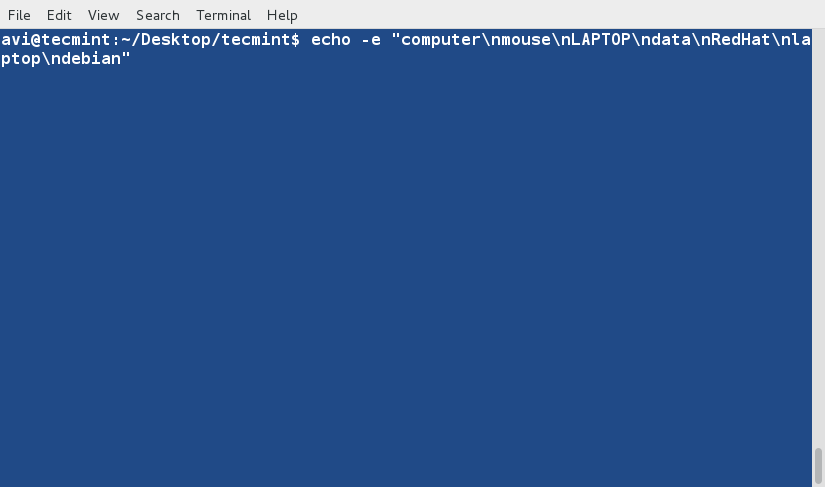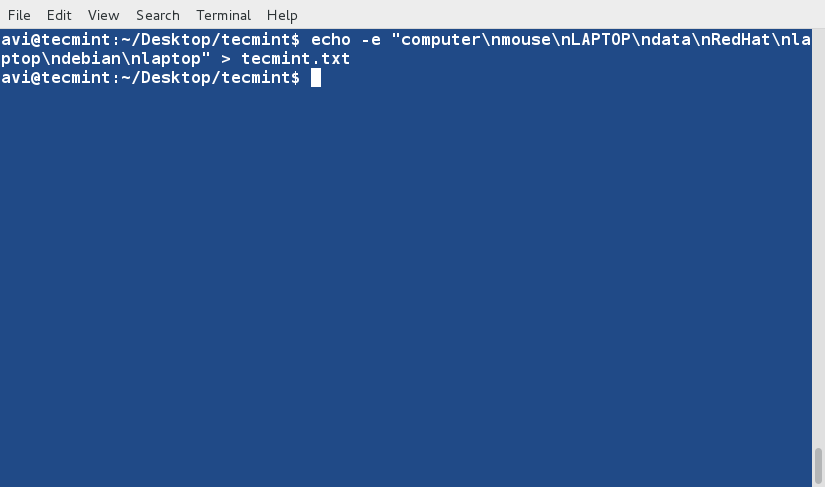
The option ‘-e‘ in the below command enables interpretion of backslash and /n tells echo to write each string to a new line.
|
||||
|
||||
$ echo -e "computer\nmouse\nLAPTOP\ndata\nRedHat\nlaptop\ndebian\nlaptop" > tecmint.txt
|
||||
|
||||
|
||||
|
||||
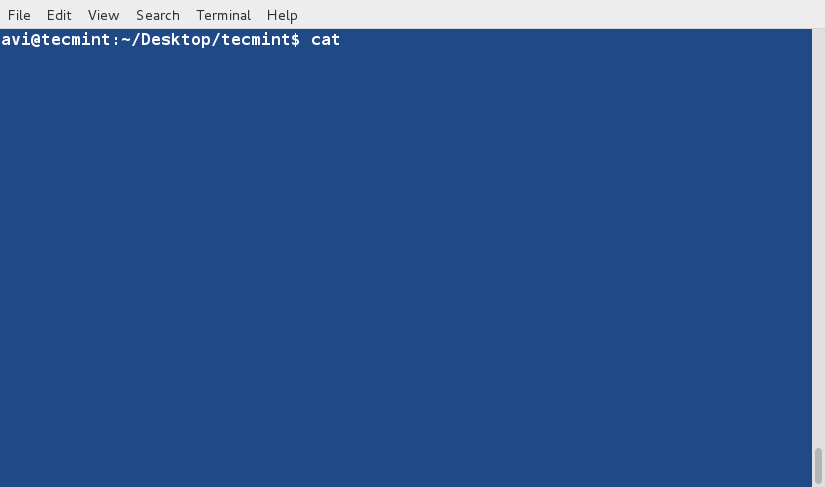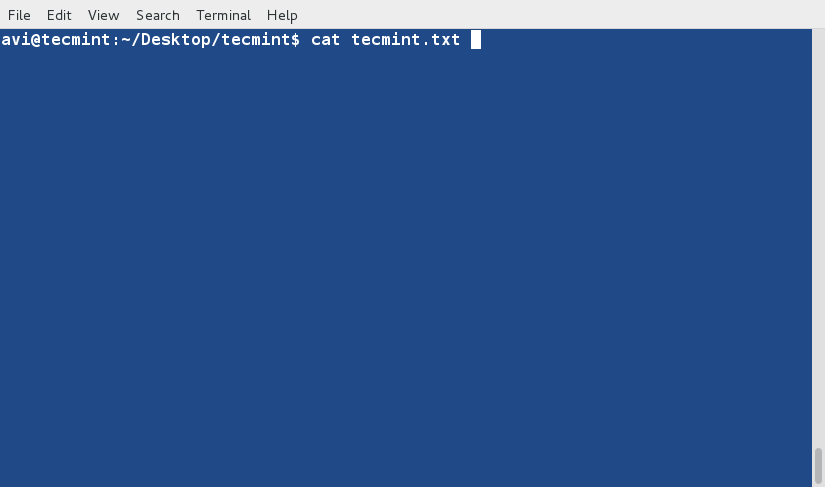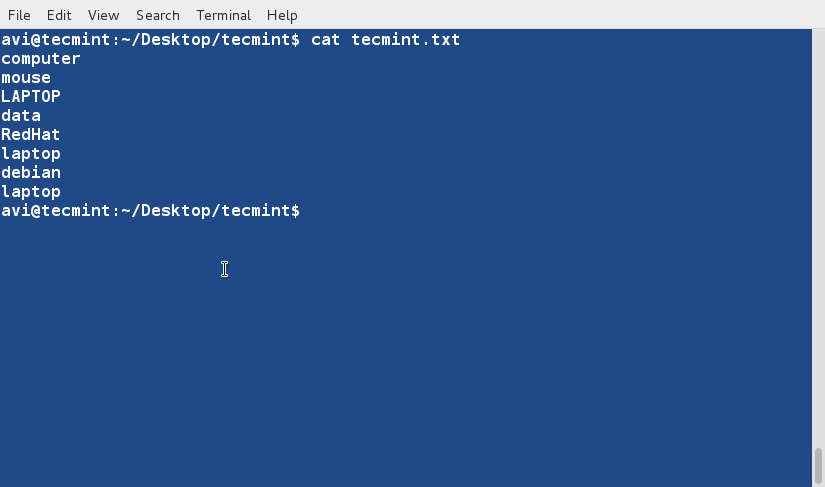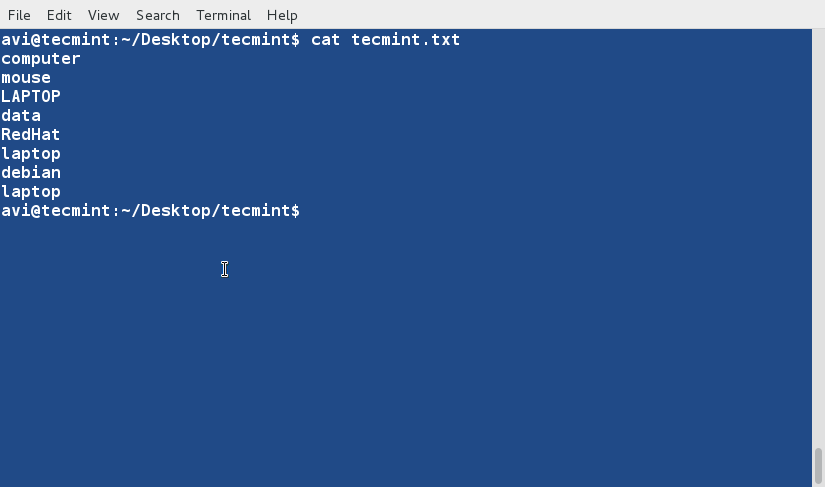
### 2. Before we start with ‘sort‘ lets have a look at the contents of the file and the way it look. ###
|
||||
|
||||
$ cat tecmint.txt
|
||||
|
||||
|
||||
|
||||
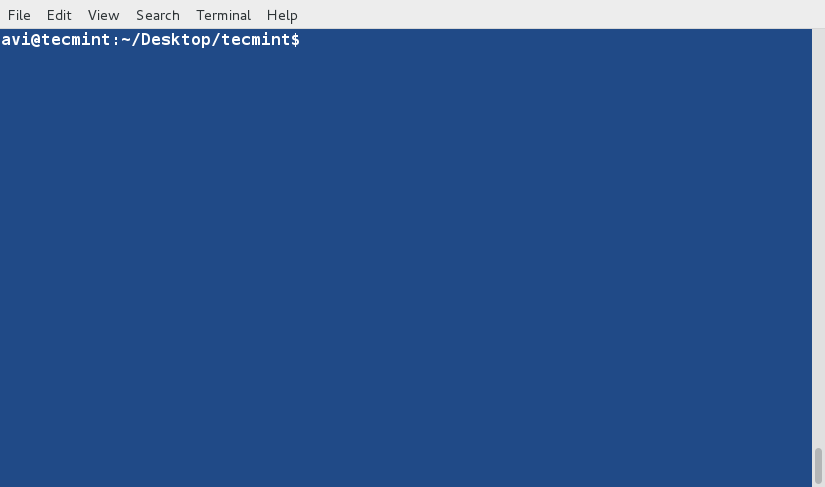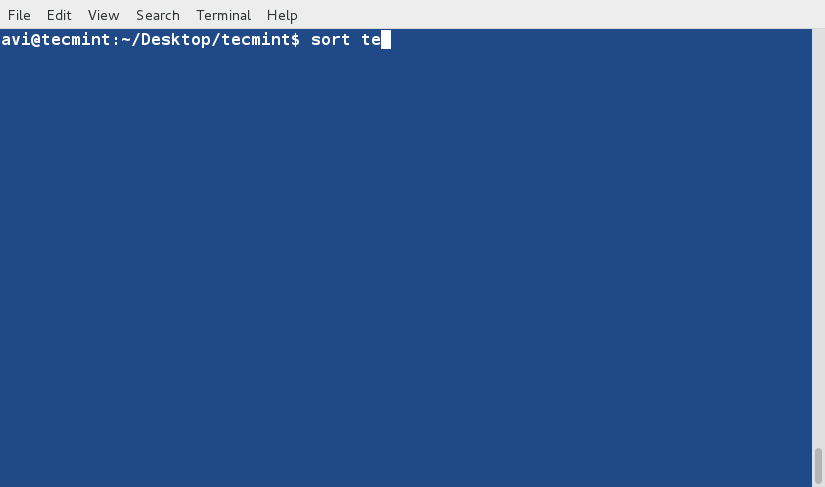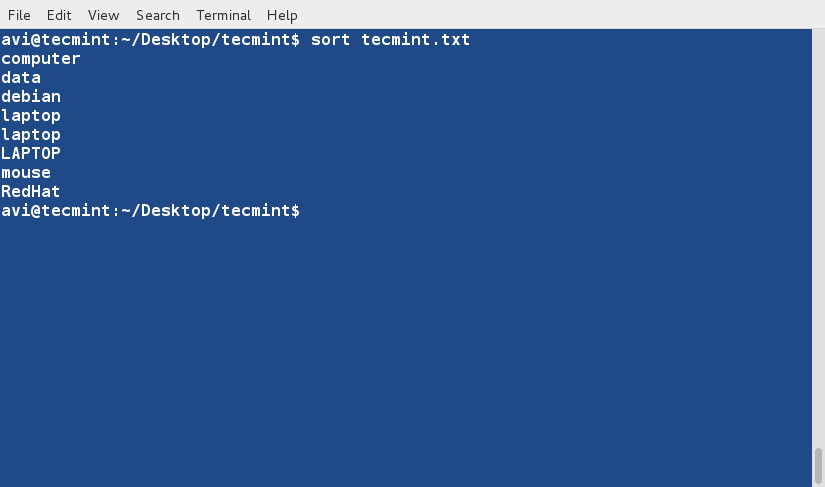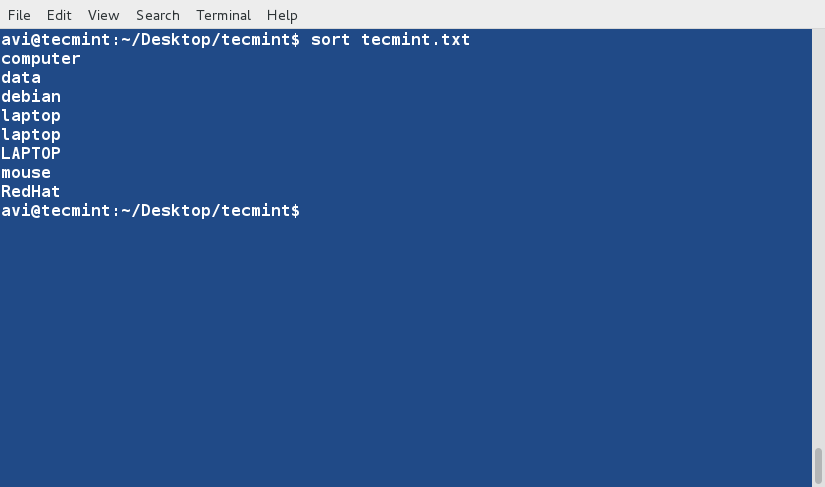
### 3. Now sort the content of the file using following command. ###
|
||||
|
||||
$ sort tecmint.txt
|
||||
|
||||
|
||||
|
||||
**Note**: The above command don’t actually sort the contents of text file but only show the sorted output on terminal.
|
||||
|
||||
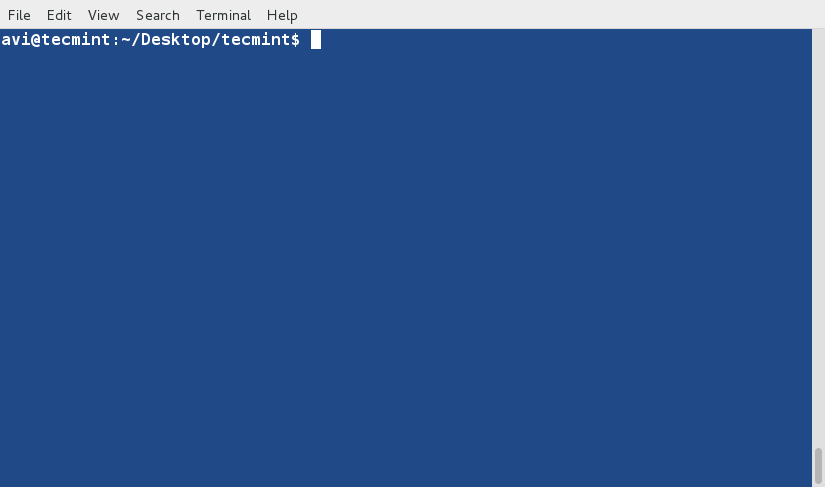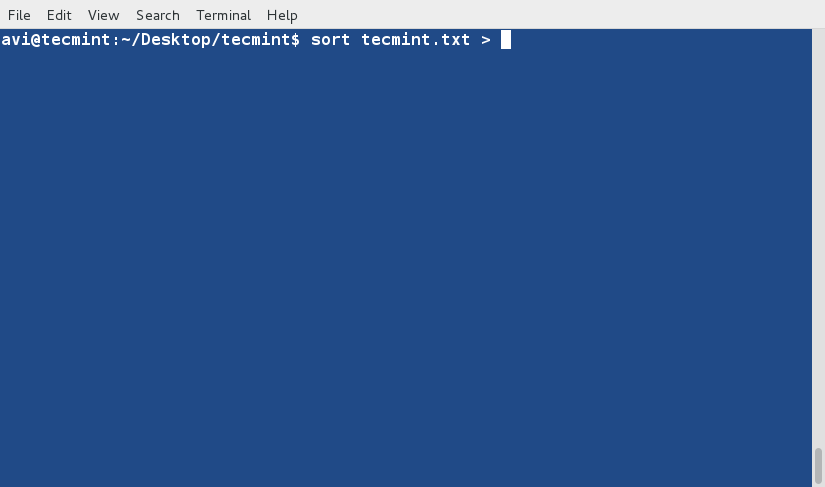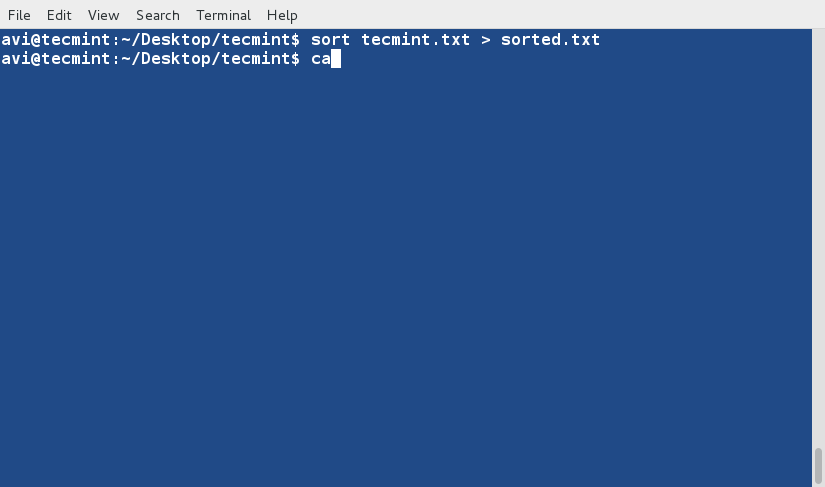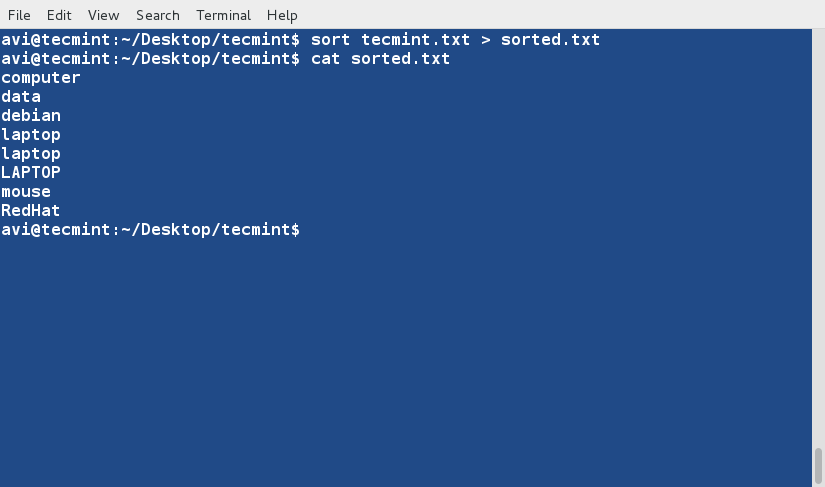
### 4. Sort the contents of the file ‘tecmint.txt‘ and write it to a file called (sorted.txt) and verify the content by using [cat command][1]. ###
|
||||
|
||||
$ sort tecmint.txt > sorted.txt
|
||||
$ cat sorted.txt
|
||||
|
||||
|
||||
|
||||
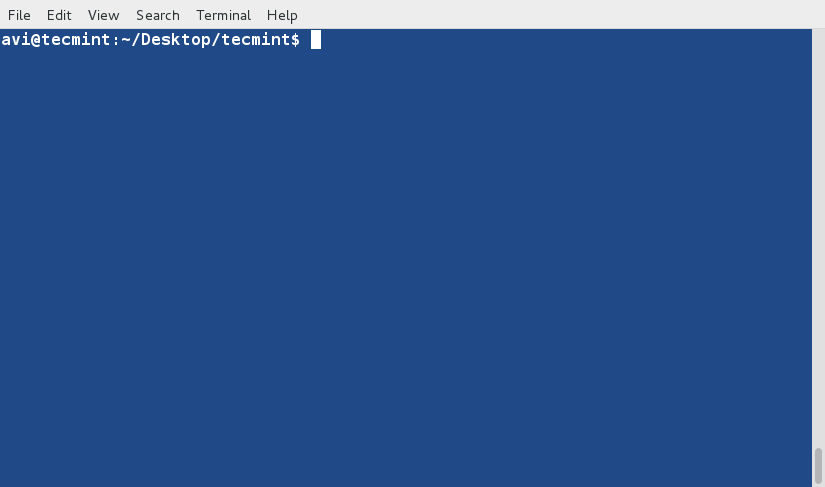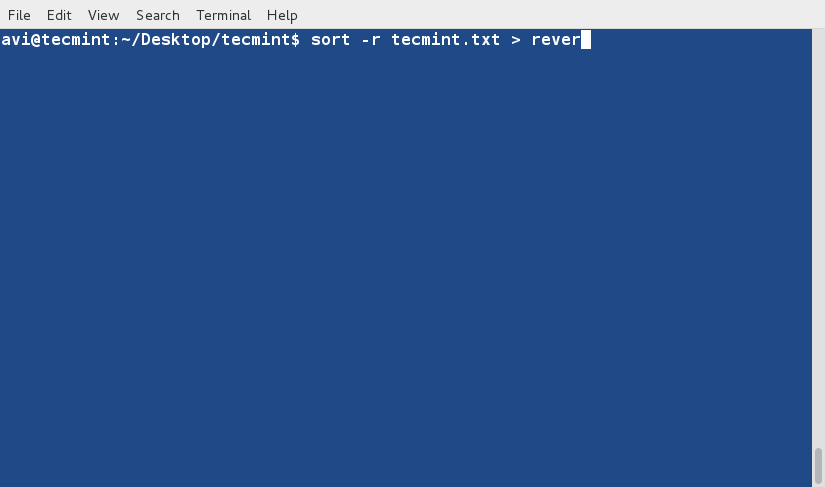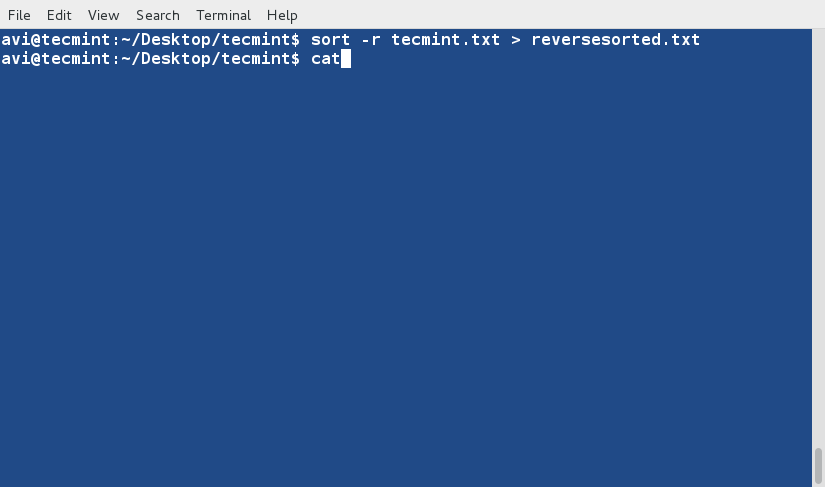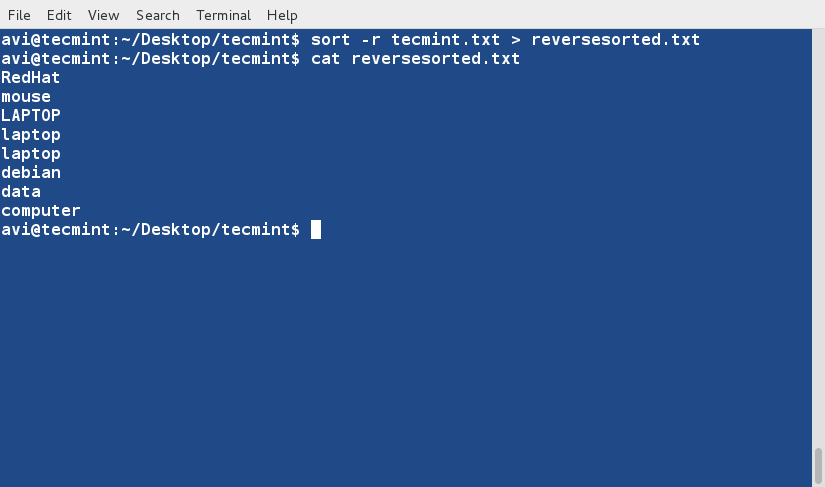
### 5. Now sort the contents of text file ‘tecmint.txt‘ in reverse order by using ‘-r‘ switch and redirect output to a file ‘reversesorted.txt‘. Also check the content listing of the newly created file. ###
|
||||
|
||||
$ sort -r tecmint.txt > reversesorted.txt
|
||||
$ cat reversesorted.txt
|
||||
|
||||
|
||||
|
||||
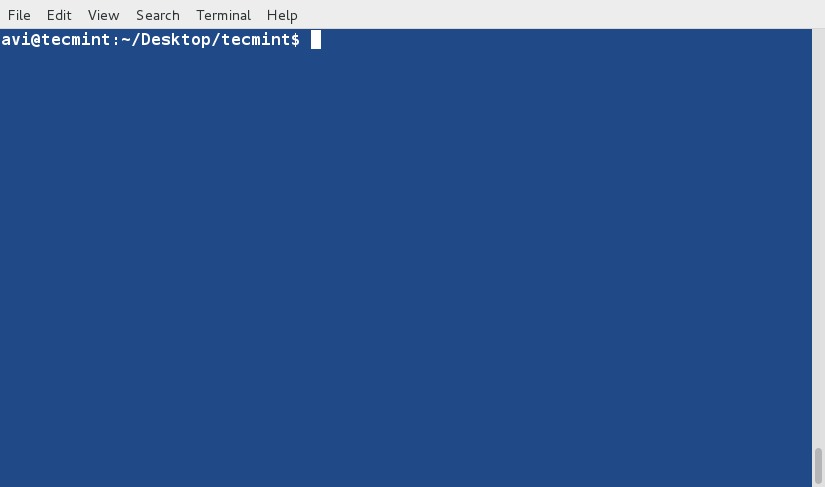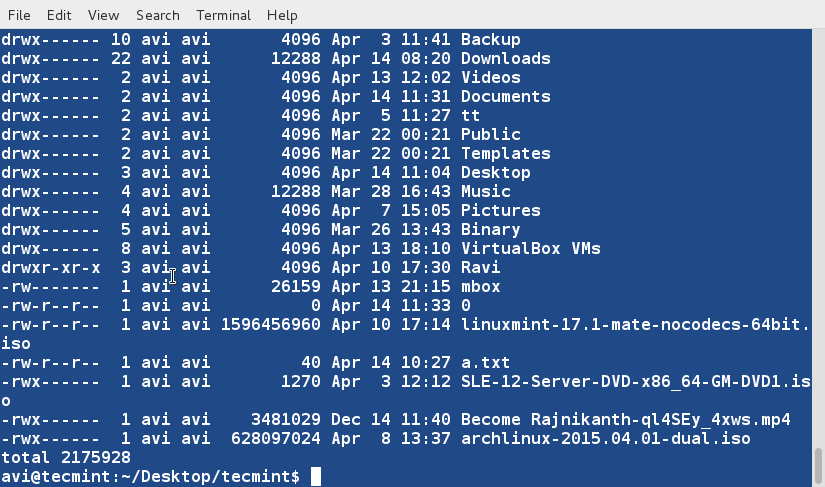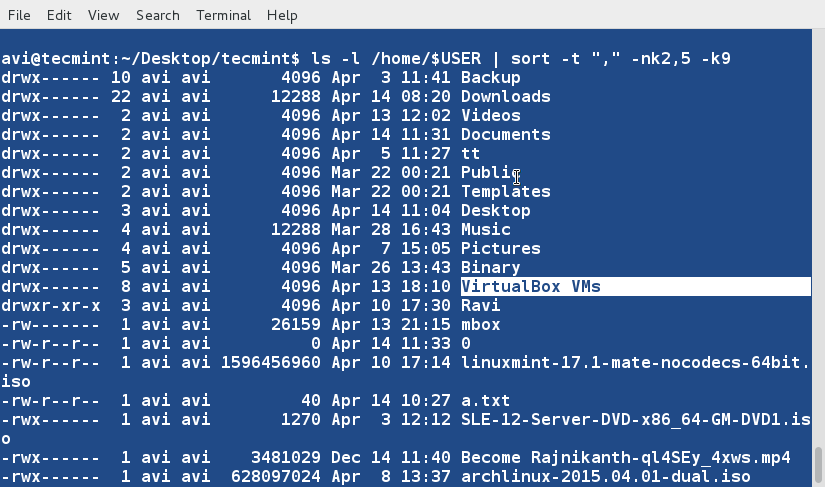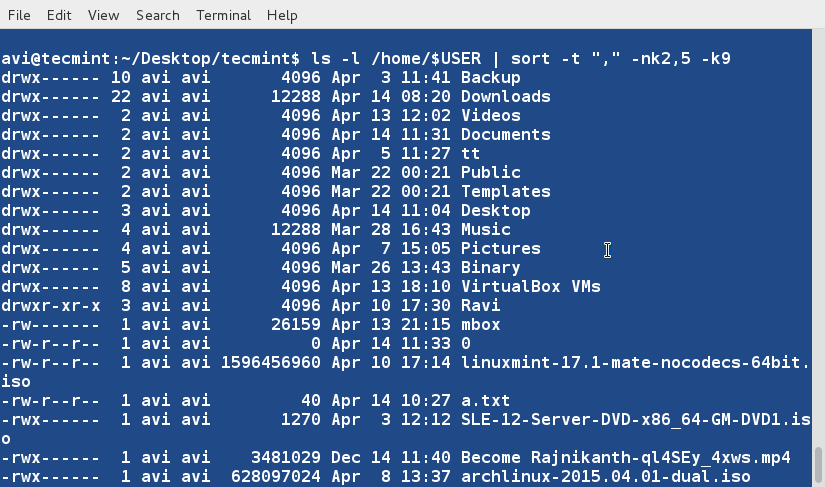
### 6. We are going a create a new file (lsl.txt) at the same location for detailed examples and populate it using the output of ‘ls -l‘ for your home directory. ###
|
||||
|
||||
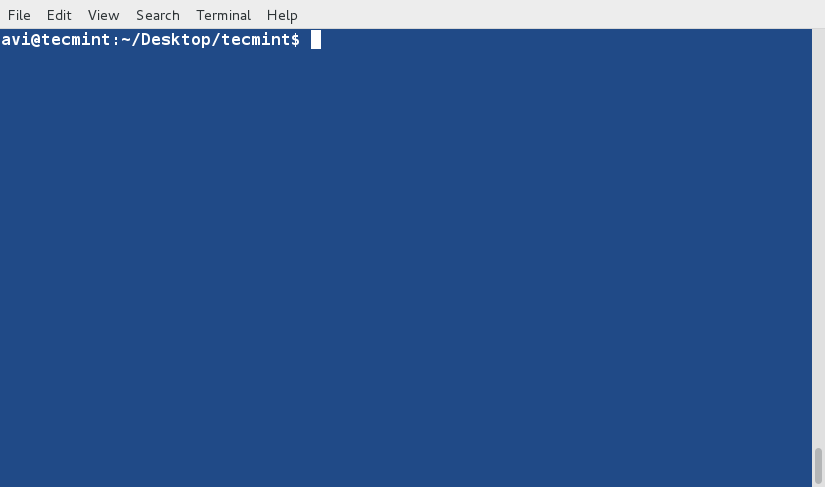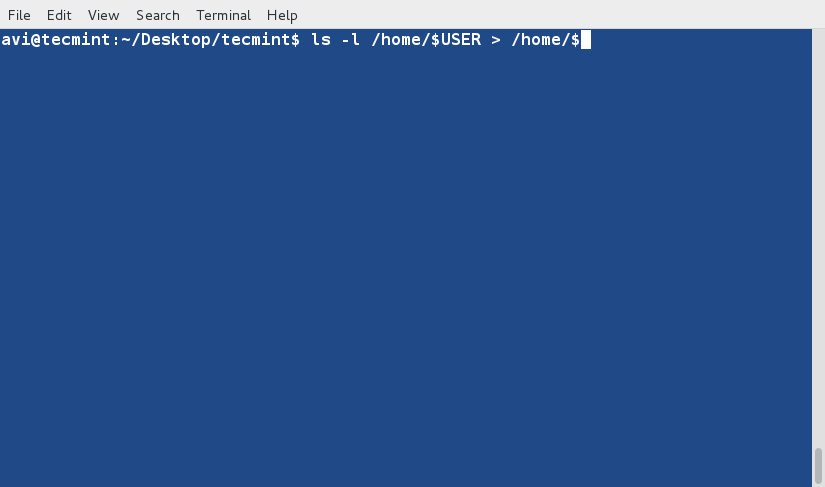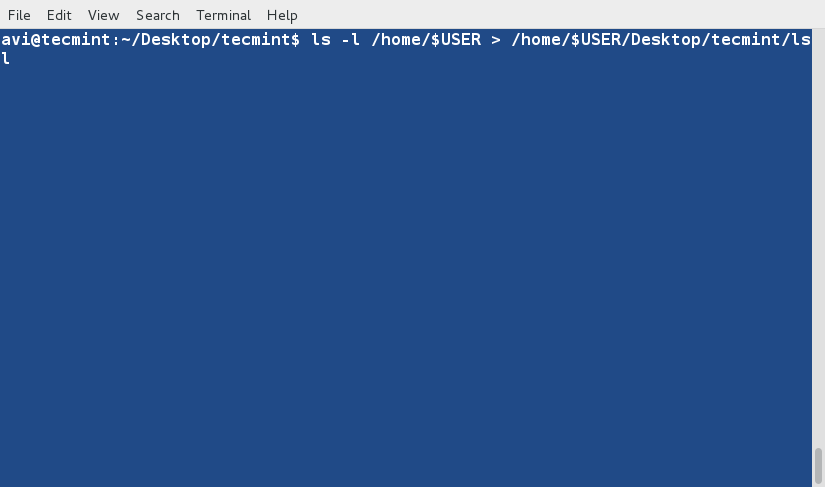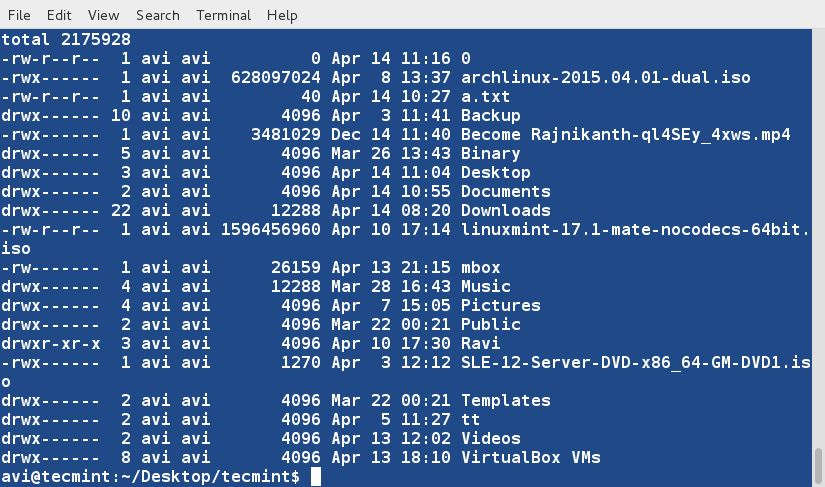
$ ls -l /home/$USER > /home/$USER/Desktop/tecmint/lsl.txt
|
||||
$ cat lsl.txt
|
||||
|
||||
|
||||
|
||||
Now will see examples to sort the contents on the basis of other field and not the default initial characters.
|
||||
|
||||
### 7. Sort the contents of file ‘lsl.txt‘ on the basis of 2nd column (which represents number of symbolic links). ###
|
||||
|
||||
$ sort -nk2 lsl.txt
|
||||
|
||||
**Note**: The ‘-n‘ option in the above example sort the contents numerically. Option ‘-n‘ must be used when we wanted to sort a file on the basis of a column which contains numerical values.
|
||||
|
||||

|
||||
|
||||
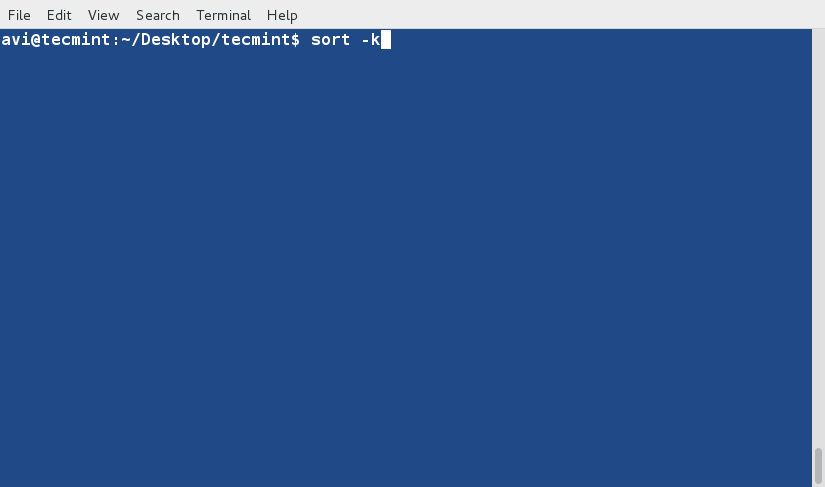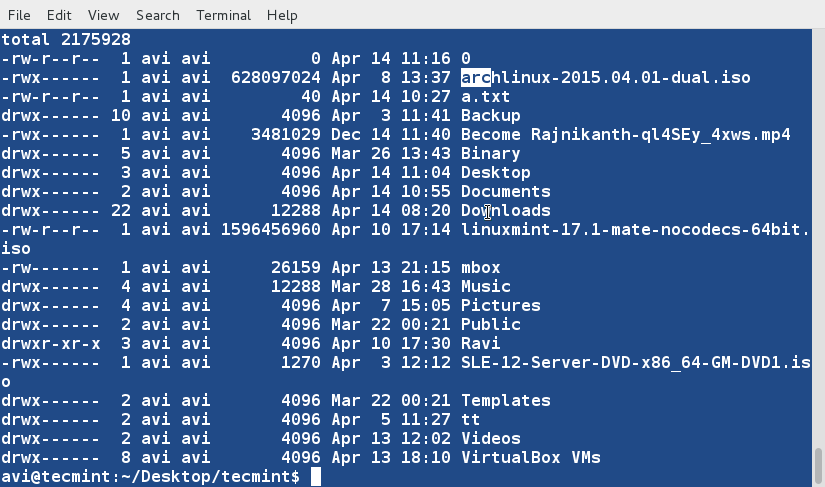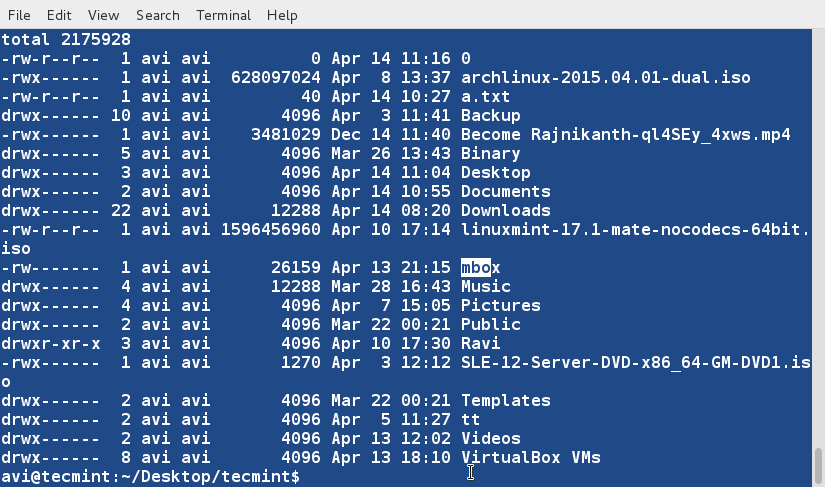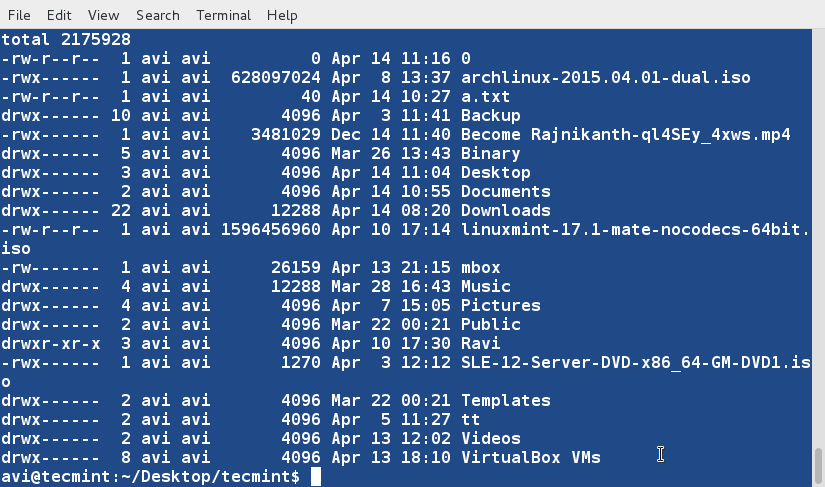
### 8. Sort the contents of file ‘lsl.txt‘ on the basis of 9th column (which is the name of the files and folders and is non-numeric). ###
|
||||
|
||||
$ sort -k9 lsl.txt
|
||||
|
||||
|
||||
|
||||
### 9. It is not always essential to run sort command on a file. We can pipeline it directly on the terminal with actual command. ###
|
||||
|
||||
$ ls -l /home/$USER | sort -nk5
|
||||
|
||||
|
||||
|
||||
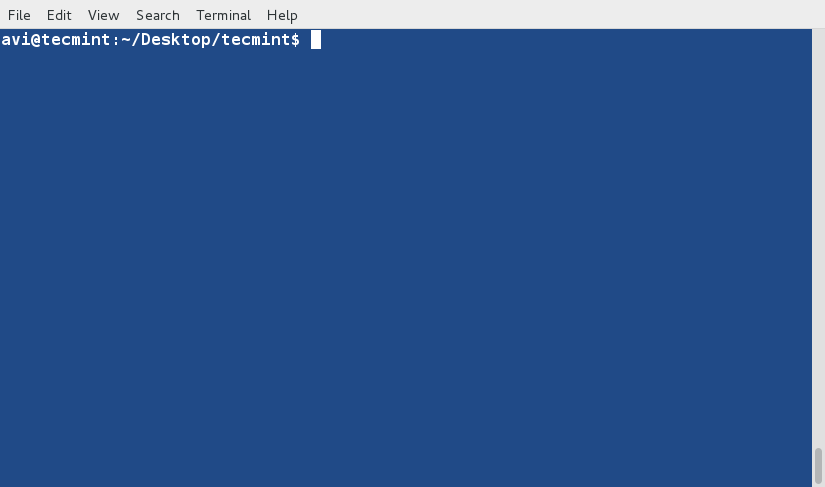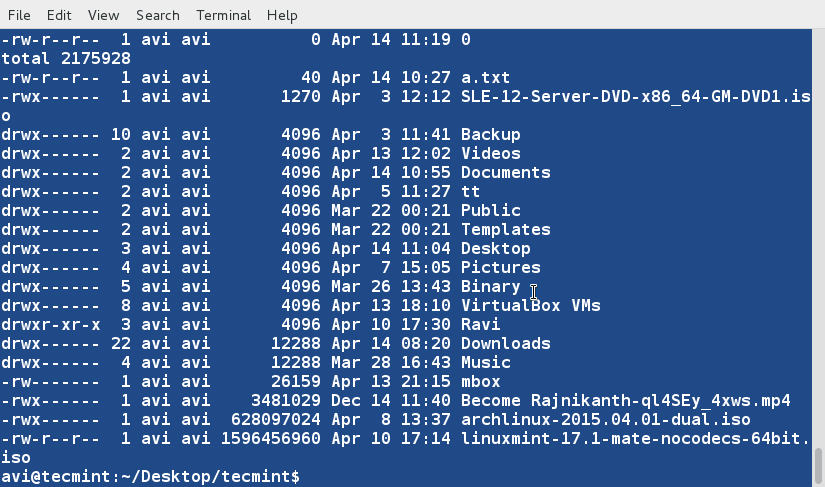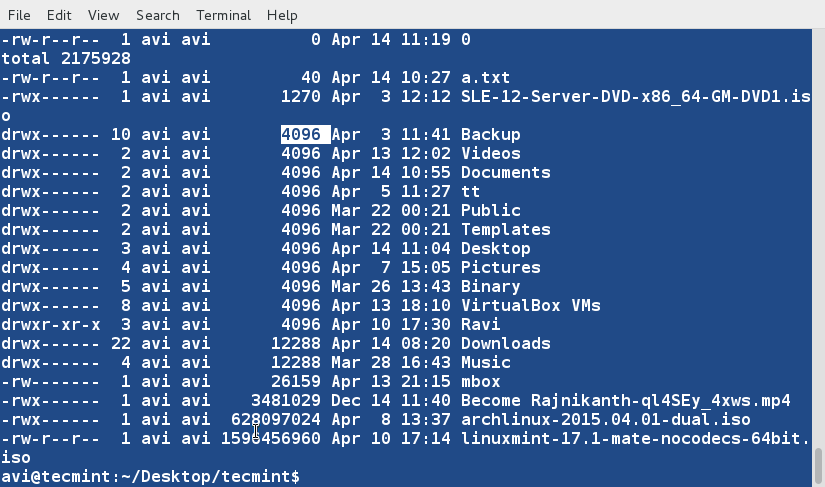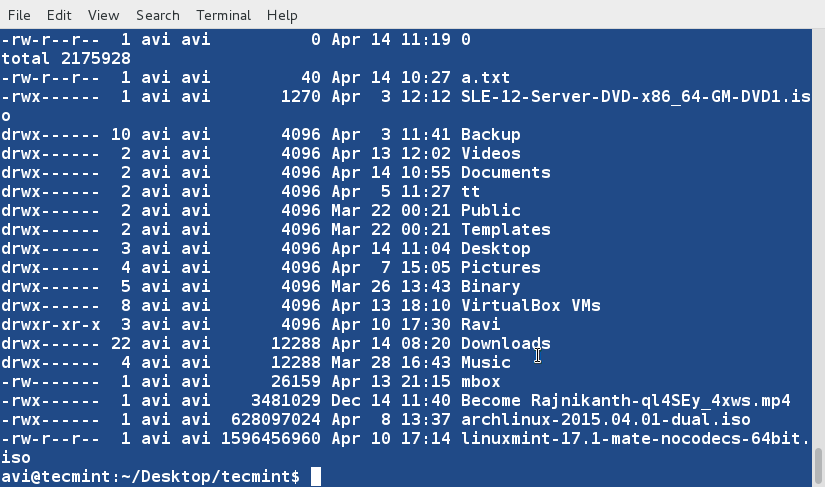
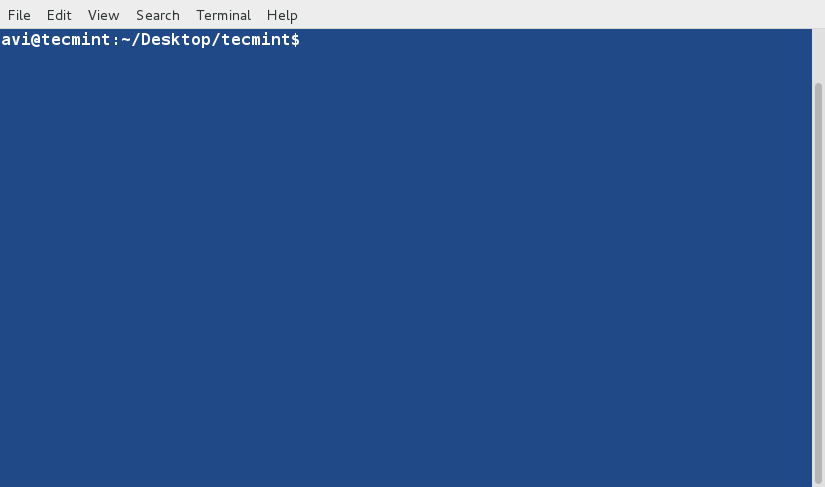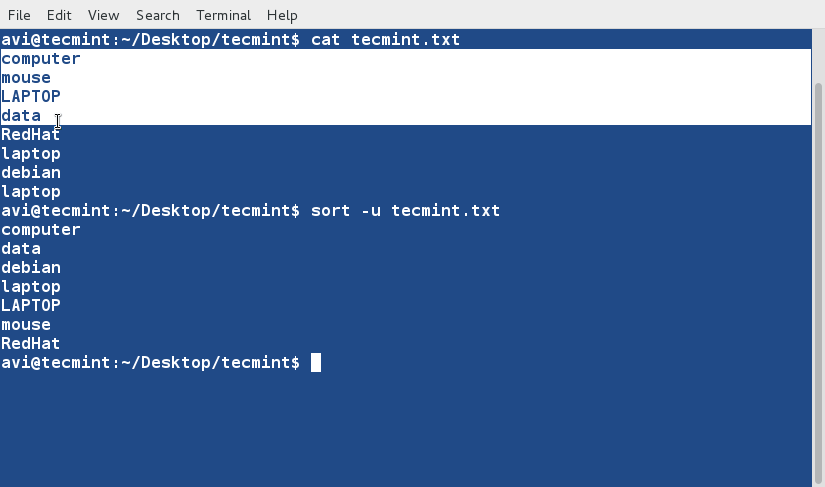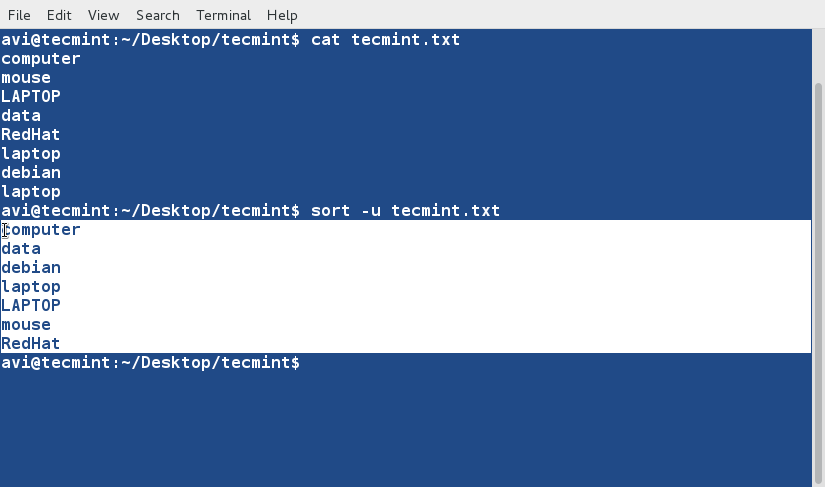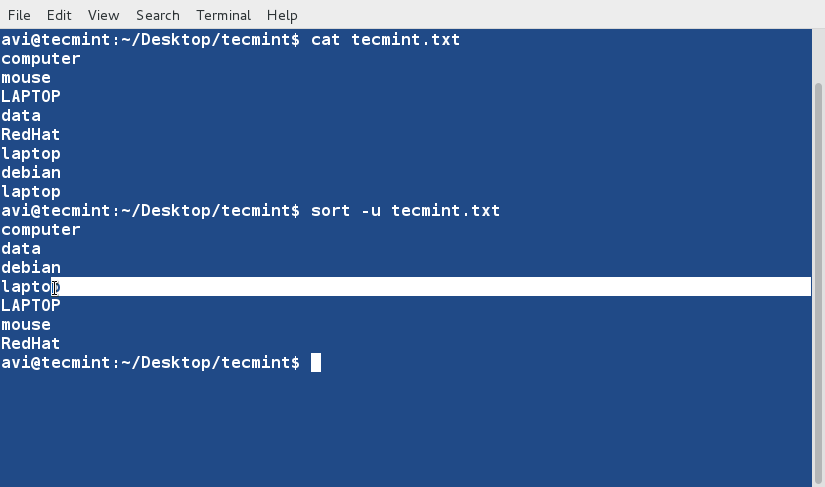
### 10. Sort and remove duplicates from the text file tecmint.txt. Check if the duplicate has been removed or not. ###
|
||||
|
||||
$ cat tecmint.txt
|
||||
$ sort -u tecmint.txt
|
||||
|
||||
|
||||
|
||||
Rules so far (what we have observed):
|
||||
|
||||
- Lines starting with numbers are preferred in the list and lies at the top until otherwise specified (-r).
|
||||
- Lines starting with lowercase letters are preferred in the list and lies at the top until otherwise specified (-r).
|
||||
- Contents are listed on the basis of occurrence of alphabets in dictionary until otherwise specified (-r).
|
||||
- Sort command by default treat each line as string and then sort it depending upon dictionary occurrence of alphabets (Numeric preferred; see rule – 1) until otherwise specified.
|
||||
|
||||
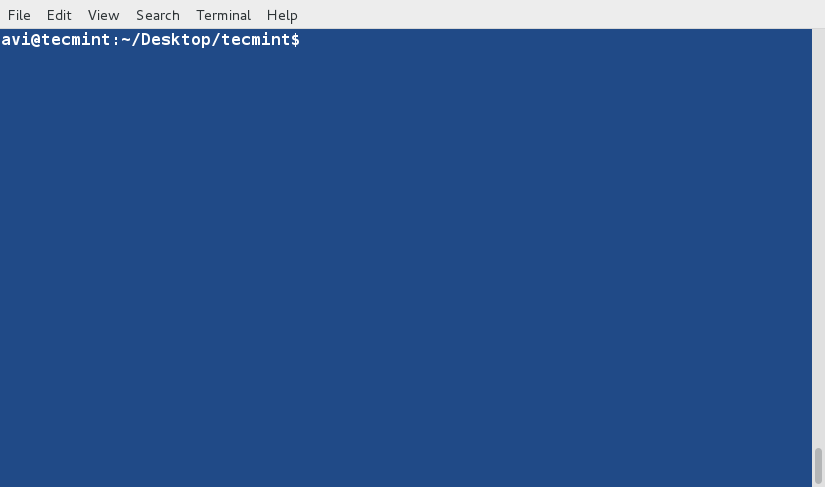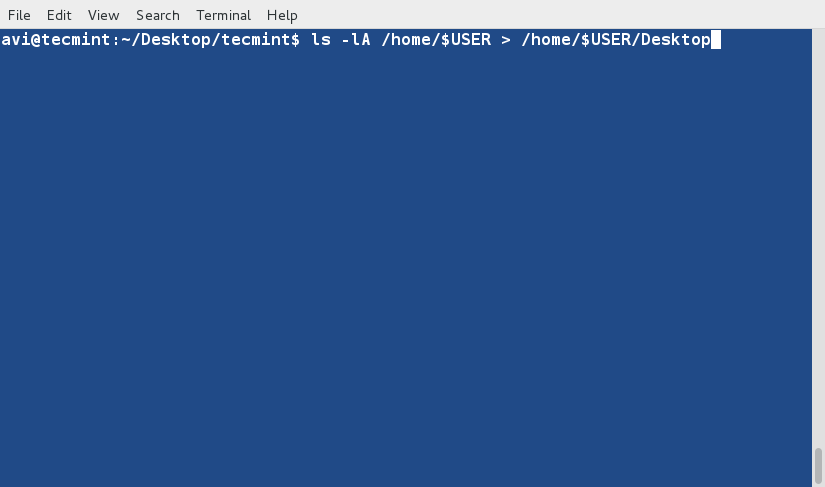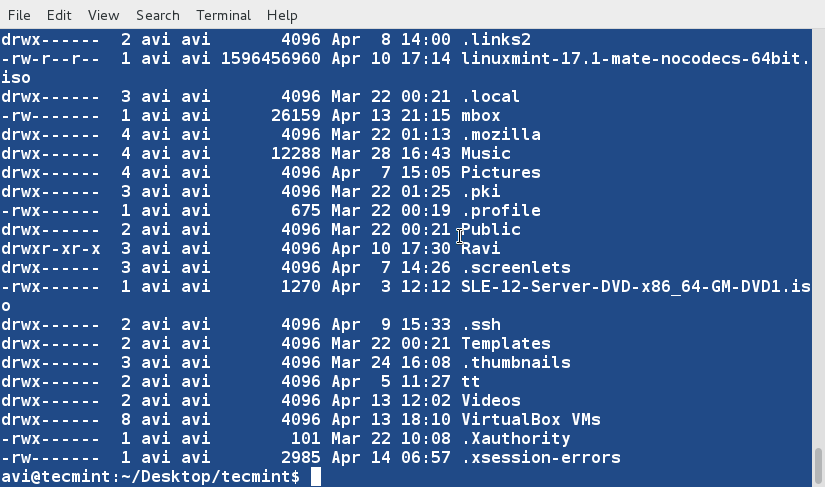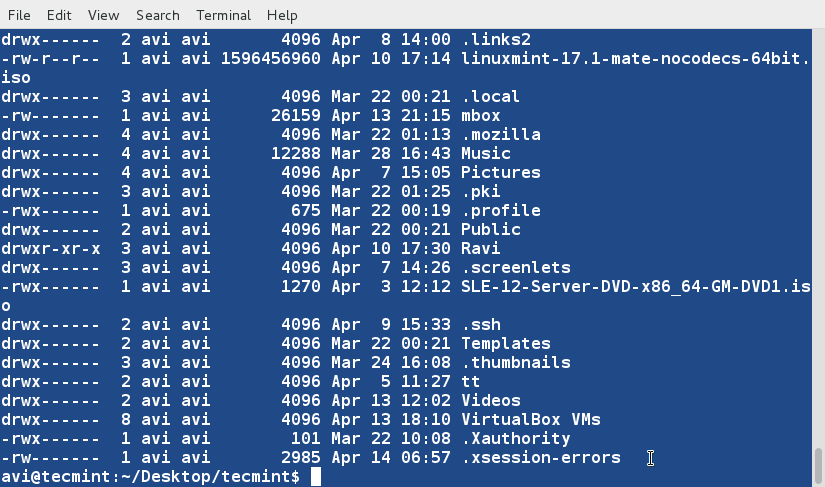
### 11. Create a third file ‘lsla.txt‘ at the current location and populate it with the output of ‘ls -lA‘ command. ###
|
||||
|
||||
$ ls -lA /home/$USER > /home/$USER/Desktop/tecmint/lsla.txt
|
||||
$ cat lsla.txt
|
||||
|
||||
|
||||
|
||||
Those having understanding of ‘ls‘ command knows that ‘ls -lA’=’ls -l‘ + Hidden files. So most of the contents on these two files would be same.
|
||||
|
||||
### 12. Sort the contents of two files on standard output in one go. ###
|
||||
|
||||
$ sort lsl.txt lsla.txt
|
||||
|
||||
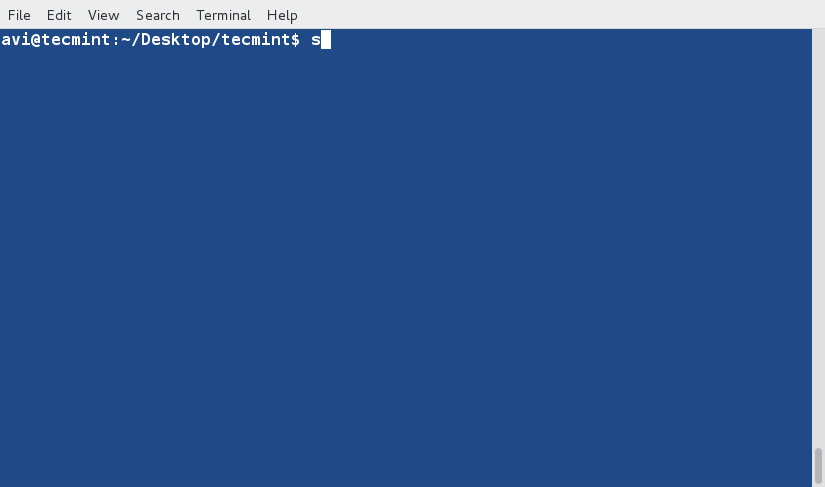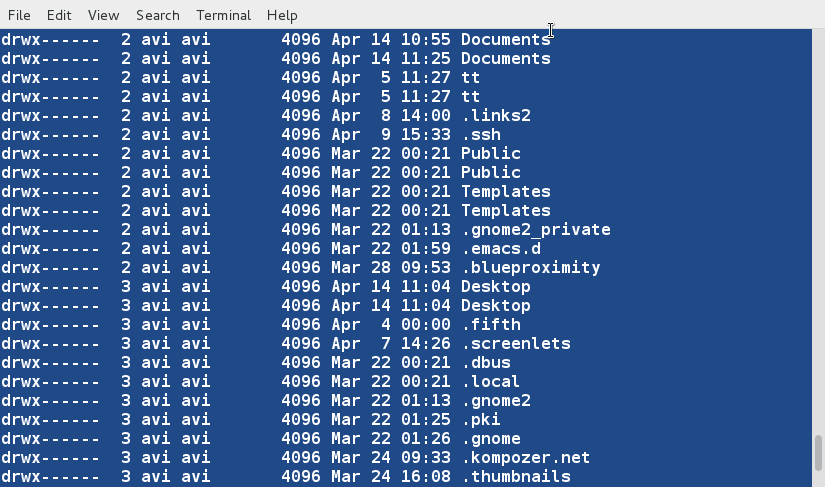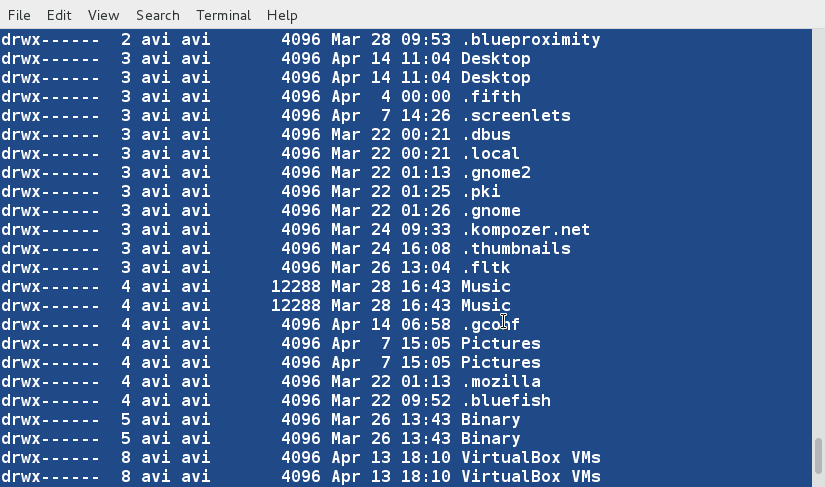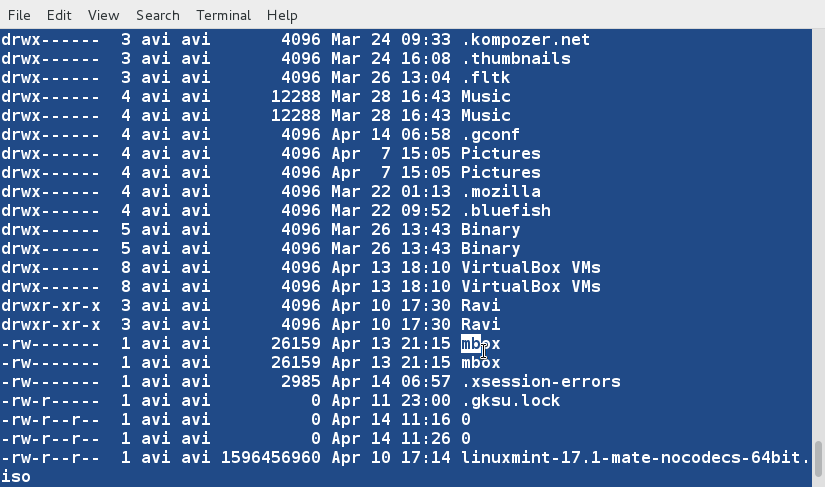
|
||||
|
||||
Notice the repetition of files and folders.
|
||||
|
||||
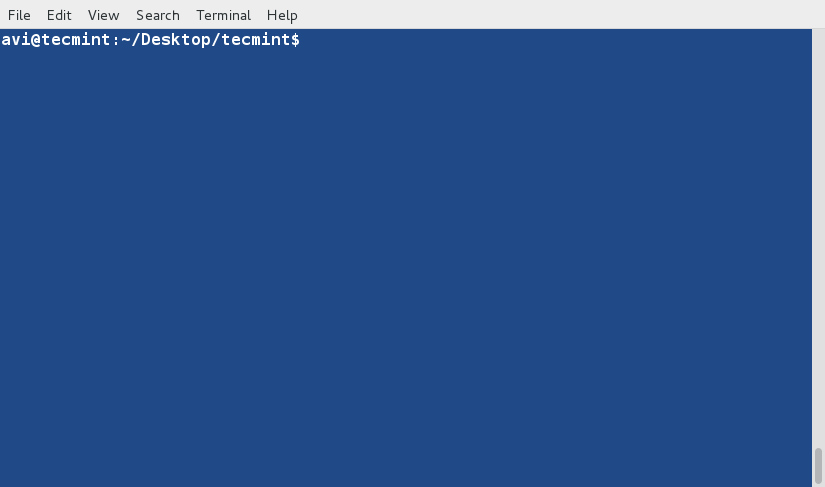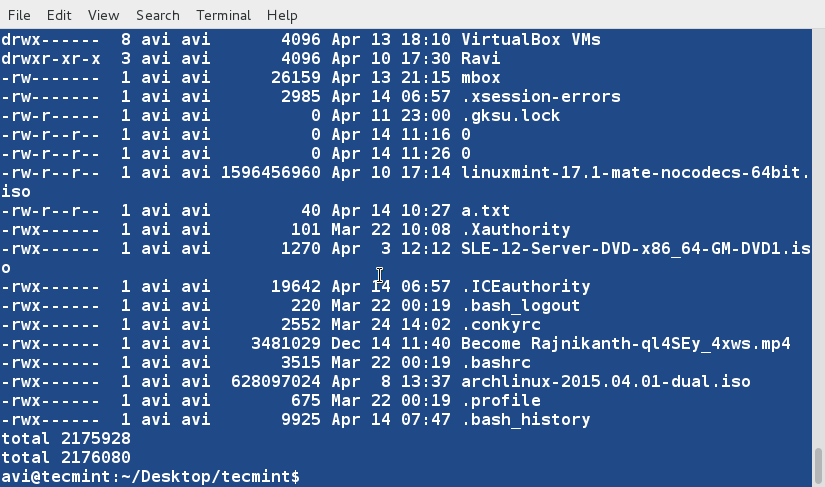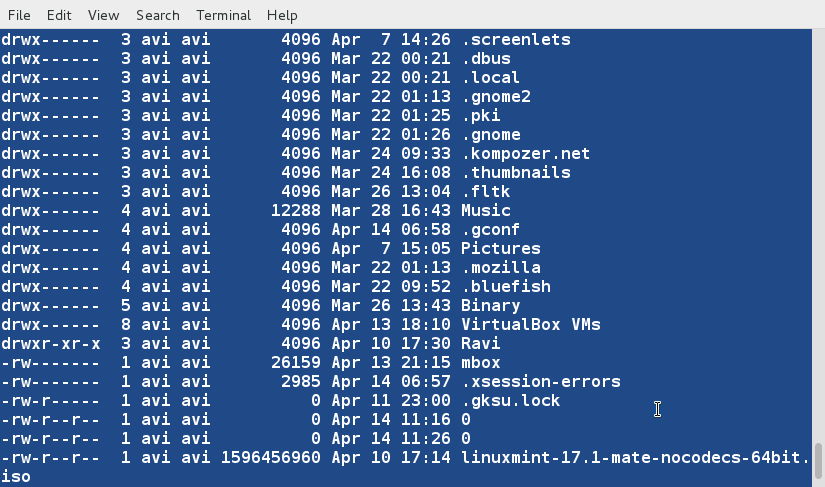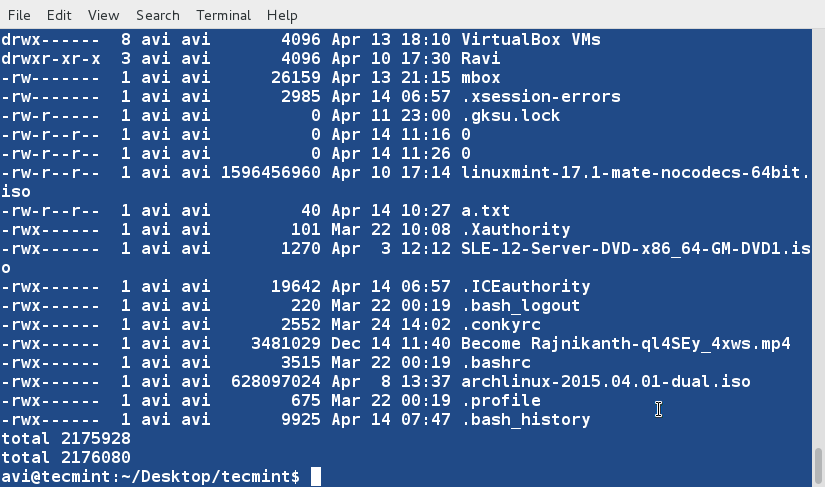
### 13. Now we can see how to sort, merge and remove duplicates from these two files. ###
|
||||
|
||||
$ sort -u lsl.txt lsla.txt
|
||||
|
||||
|
||||
|
||||
Notice that duplicates has been omitted from the output. Also, you can write the output to a new file by redirecting the output to a file.
|
||||
|
||||
### 14. We may also sort the contents of a file or the output based upon more than one column. Sort the output of ‘ls -l‘ command on the basis of field 2,5 (Numeric) and 9 (Non-Numeric). ###
|
||||
|
||||
$ ls -l /home/$USER | sort -t "," -nk2,5 -k9
|
||||
|
||||
|
||||
|
||||
That’s all for now. In the next article we will cover a few more examples of ‘sort‘ command in detail for you. Till then stay tuned and connected to Tecmint. Keep sharing. Keep commenting. Like and share us and help us get spread.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/sort-command-linux/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:http://www.tecmint.com/13-basic-cat-command-examples-in-linux/
|
||||
@ -0,0 +1,359 @@
|
||||
How to Configure MariaDB Replication on CentOS Linux
|
||||
================================================================================
|
||||
Its a process of creating duplicate versions of a the DB. Replication process is not only copies a database, but also synchronizes changes from master to one of the slaves. But this is does not means that slave databases are identical copy of the master, because replication can be configured that only a schema of tables or columns or rows will be replicated, i.e. a partial replication. The replication ensures that those specific configured objects are kept in sync between the different databases.
|
||||
|
||||
### Mariadb Replication Concepts ###
|
||||
|
||||
**Backups** : Replication can be used for DB backups. For example, you have master -> slave replication. If master is lost (hdd fails, for example) you can restore your db from master.
|
||||
|
||||
**Scaling** : You can use master -> slave replication for scaling solution. For example, if you have a few big and have SQL query, using replcation you can separate this queries for each replcations nodes. Write SQL should be performed only on master, for read-only queries slave server can be used.
|
||||
|
||||
**Spreading solution** : You can use replication for distribution. For example, you can distribute different sales data to different databases.
|
||||
|
||||
**Failover solution** : For example you have, master -> slave(1) -> slave(2) -> slave(3) replication. You can write script for master monitoring , if master fails, script can quickly change slave(1) new for master master -> slave(1) -> slave(2) and your application will continue working whit out downtime
|
||||
|
||||
### Simple diagrammatic demonstration of replication ###
|
||||
|
||||

|
||||
|
||||
Before you start good know what is **binary log** and Ibdata1. The binary log contains a record about all changes in the db, data and structure, as well as how long each statement took to execute. Bin log consists set log files and an index. Its means that main SQL statements such as CREATE, ALTER, INSERT, UPDATE and DELETE will be putted to this log, statements, such as SELECT will not be logged. These info can be logged to general query.log file. In simple **Ibdata1** is a file which contains all tables and all info about db.
|
||||
|
||||
### Master server configuration ###
|
||||
|
||||
Good to have server updated
|
||||
|
||||
sudo yum install update -y && sudo yum install upgrade -y
|
||||
|
||||
We are working on centos 7 server
|
||||
|
||||
sudo cat /etc/redhat-release
|
||||
|
||||
CentOS Linux release 7.0.1406 (Core)
|
||||
|
||||
Install MariaDB
|
||||
|
||||
sudo yum install mariadb-server -y
|
||||
|
||||
Start MariaDB and enable it to start on boot of the server
|
||||
|
||||
sudo systemctl start mariadb.service
|
||||
sudo systemctl enable mariadb.service
|
||||
|
||||
Output:
|
||||
|
||||
ln -s '/usr/lib/systemd/system/mariadb.service' '/etc/systemd/system/multi-user.target.wants/mariadb.service'
|
||||
|
||||
Check MariaDB status
|
||||
|
||||
sudo service mariadb status
|
||||
|
||||
or use
|
||||
|
||||
sudo systemctl is-active mariadb.service
|
||||
|
||||
Output:
|
||||
|
||||
Redirecting to /bin/systemctl status mariadb.service
|
||||
mariadb.service - MariaDB database server
|
||||
Loaded: loaded (/usr/lib/systemd/system/mariadb.service; enabled)
|
||||
|
||||
Set MariaDB password
|
||||
|
||||
mysql -u root
|
||||
mysql> use mysql;
|
||||
mysql> update user set password=PASSWORD("SOME_ROOT_PASSWORD") where User='root';
|
||||
mysql> flush privileges;
|
||||
mysql> exit
|
||||
|
||||
SOME_ROOT_PASSWORD - your root password. I my case I'ill use "q" - password, then try to login:
|
||||
|
||||
sudo mysql -u root -pSOME_ROOT_PASSWORD
|
||||
|
||||
Output:
|
||||
|
||||
Welcome to the MariaDB monitor. Commands end with ; or \g.
|
||||
Your MariaDB connection id is 5
|
||||
Server version: 5.5.41-MariaDB MariaDB Server
|
||||
Copyright (c) 2000, 2014, Oracle, MariaDB Corporation Ab and others.
|
||||
|
||||
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
|
||||
|
||||
Lets create database with table with some data
|
||||
|
||||
Create database/schema
|
||||
|
||||
sudo mysql -u root -pSOME_ROOT_PASSWORD
|
||||
mysql> create database test_repl;
|
||||
|
||||
Where:
|
||||
|
||||
test_repl - Name of shcema which will be replicated
|
||||
|
||||
Output:
|
||||
|
||||
Query OK, 1 row affected (0.00 sec)
|
||||
|
||||
Create Persons table
|
||||
|
||||
mysql> use test_repl;
|
||||
|
||||
CREATE TABLE Persons (
|
||||
PersonID int,
|
||||
LastName varchar(255),
|
||||
FirstName varchar(255),
|
||||
Address varchar(255),
|
||||
City varchar(255)
|
||||
);
|
||||
|
||||
Output:
|
||||
|
||||
mysql> MariaDB [test_repl]> CREATE TABLE Persons (
|
||||
-> PersonID int,
|
||||
-> LastName varchar(255),
|
||||
-> FirstName varchar(255),
|
||||
-> Address varchar(255),
|
||||
-> City varchar(255)
|
||||
-> );
|
||||
Query OK, 0 rows affected (0.01 sec)
|
||||
|
||||
Insert some data
|
||||
|
||||
mysql> INSERT INTO Persons VALUES (1, "LastName1", "FirstName1", "Address1", "City1");
|
||||
mysql> INSERT INTO Persons VALUES (2, "LastName2", "FirstName2", "Address2", "City2");
|
||||
mysql> INSERT INTO Persons VALUES (3, "LastName3", "FirstName3", "Address3", "City3");
|
||||
mysql> INSERT INTO Persons VALUES (4, "LastName4", "FirstName4", "Address4", "City4");
|
||||
mysql> INSERT INTO Persons VALUES (5, "LastName5", "FirstName5", "Address5", "City5");
|
||||
|
||||
Output:
|
||||
|
||||
Query OK, 5 row affected (0.00 sec)
|
||||
|
||||
Check data
|
||||
|
||||
mysql> select * from Persons;
|
||||
|
||||
Output:
|
||||
|
||||
+----------+-----------+------------+----------+-------+
|
||||
| PersonID | LastName | FirstName | Address | City |
|
||||
+----------+-----------+------------+----------+-------+
|
||||
| 1 | LastName1 | FirstName1 | Address1 | City1 |
|
||||
| 1 | LastName1 | FirstName1 | Address1 | City1 |
|
||||
| 2 | LastName2 | FirstName2 | Address2 | City2 |
|
||||
| 3 | LastName3 | FirstName3 | Address3 | City3 |
|
||||
| 4 | LastName4 | FirstName4 | Address4 | City4 |
|
||||
| 5 | LastName5 | FirstName5 | Address5 | City5 |
|
||||
+----------+-----------+------------+----------+-------+
|
||||
|
||||
### Configure MariaDB for replication ###
|
||||
|
||||
You'll need to edit the my.cnf file on the Master server to enable binary logging and set the server's id. I will use vi text editor, but use can use any suitable for your such as nano, joe etc.
|
||||
|
||||
sudo vi /etc/my.cnf
|
||||
|
||||
and put to config in [mysqld] section such lines.
|
||||
|
||||
|
||||
log-basename=master
|
||||
log-bin
|
||||
binlog-format=row
|
||||
server_id=1
|
||||
|
||||
Output:
|
||||
|
||||

|
||||
|
||||
Then restart MariaDB:
|
||||
|
||||
sudo service mariadb restart
|
||||
|
||||
Login to MariaDB and check binary logs:
|
||||
|
||||
sudo mysql -u root -pq test_repl
|
||||
|
||||
mysql> SHOW MASTER STATUS;
|
||||
|
||||
Output:
|
||||
|
||||
+--------------------+----------+--------------+------------------+
|
||||
| File | Position | Binlog_Do_DB | Binlog_Ignore_DB |
|
||||
+--------------------+----------+--------------+------------------+
|
||||
| mariadb-bin.000002 | 3913 | | |
|
||||
+--------------------+----------+--------------+------------------+
|
||||
|
||||
**Remember** : "File" and "Position" values. YOU WILL NEED THIS VALUE AT SLAVE SERVER
|
||||
|
||||
Create user for replication
|
||||
|
||||
mysql> GRANT REPLICATION SLAVE ON *.* TO replication_user IDENTIFIED BY 'bigs3cret' WITH GRANT OPTION;
|
||||
mysql> flush privileges;
|
||||
|
||||
Output:
|
||||
|
||||
Query OK, 0 rows affected (0.00 sec)
|
||||
Query OK, 0 rows affected (0.00 sec)
|
||||
|
||||
Check user in db
|
||||
|
||||
mysql> select * from mysql.user WHERE user="replication_user"\G;
|
||||
|
||||
Output:
|
||||
|
||||
mysql> select * from mysql.user WHERE user="replication_user"\G;
|
||||
*************************** 1. row ***************************
|
||||
Host: %
|
||||
User: replication_user
|
||||
Password: *2AF30E7AEE9BF3AF584FB19653881D2D072FA49C
|
||||
Select_priv: N
|
||||
.....
|
||||
|
||||
Create DB dump (snapshot of all data which will be replicated) form master
|
||||
|
||||
mysqldump -uroot -pSOME_ROOT_PASSWORD test_repl > full-dump.sql
|
||||
|
||||
Where:
|
||||
|
||||
SOME_ROOT_PASSWORD - password for root user that you have setup
|
||||
test_repl - name of the data base which will be replicated;
|
||||
|
||||
You need to recover mysql dump (full-dump.sql) at slave server. Its needed for replication.
|
||||
|
||||
### Slave server configuration ###
|
||||
|
||||
All this commands you need to perform at slave server
|
||||
|
||||
Lets assume that we have fresh/updated CentOS 7.x server with latest mariaDB server and you can login as root to maria DB server (this was descripbed in first part of the article)
|
||||
|
||||
Login to Maria DB console and create DB
|
||||
|
||||
mysql -u root -pSOME_ROOT_PASSWORD;
|
||||
mysql> create database test_repl;
|
||||
mysql> exit;
|
||||
|
||||
Recover data from master at slave server
|
||||
|
||||
mysql -u root -pSOME_ROOT_PASSWORD test_repl < full-dump.sql
|
||||
|
||||
Where:
|
||||
|
||||
full-dump.sql - its DB Dump that you have create at test server.
|
||||
|
||||
Login to Maria DB and setup replication
|
||||
|
||||
mysql> CHANGE MASTER TO
|
||||
MASTER_HOST='82.196.5.39',
|
||||
MASTER_USER='replication_user',
|
||||
MASTER_PASSWORD='bigs3cret',
|
||||
MASTER_PORT=3306,
|
||||
MASTER_LOG_FILE='mariadb-bin.000002',
|
||||
MASTER_LOG_POS=3913,
|
||||
MASTER_CONNECT_RETRY=10;
|
||||
|
||||

|
||||
|
||||
Where:
|
||||
|
||||
MASTER_HOST - IP of the master server.
|
||||
MASTER_USER - replication user at master server
|
||||
MASTER_PASSWORD - replication user password
|
||||
MASTER_PORT - mysql port at master
|
||||
MASTER_LOG_FILE - bin-log file name form master
|
||||
MASTER_LOG_POS - bin-log position file at master
|
||||
|
||||
Start slave mode
|
||||
|
||||
mysql> slave start;
|
||||
|
||||
Output:
|
||||
|
||||
Query OK, 0 rows affected (0.00 sec)
|
||||
|
||||
Check slave status
|
||||
|
||||
mysql> show slave status\G;
|
||||
|
||||
Output:
|
||||
|
||||
*************************** 1. row ***************************
|
||||
Slave_IO_State: Waiting for master to send event
|
||||
Master_Host: 82.196.5.39
|
||||
Master_User: replication_user
|
||||
Master_Port: 3306
|
||||
Connect_Retry: 10
|
||||
Master_Log_File: mariadb-bin.000002
|
||||
Read_Master_Log_Pos: 4175
|
||||
Relay_Log_File: mariadb-relay-bin.000002
|
||||
Relay_Log_Pos: 793
|
||||
Relay_Master_Log_File: mariadb-bin.000002
|
||||
Slave_IO_Running: Yes
|
||||
Slave_SQL_Running: Yes
|
||||
Replicate_Do_DB:
|
||||
Replicate_Ignore_DB:
|
||||
Replicate_Do_Table:
|
||||
Replicate_Ignore_Table:
|
||||
Replicate_Wild_Do_Table:
|
||||
Replicate_Wild_Ignore_Table:
|
||||
Last_Errno: 0
|
||||
Last_Error:
|
||||
Skip_Counter: 0
|
||||
Exec_Master_Log_Pos: 4175
|
||||
Relay_Log_Space: 1089
|
||||
Until_Condition: None
|
||||
Until_Log_File:
|
||||
Until_Log_Pos: 0
|
||||
Master_SSL_Allowed: No
|
||||
Master_SSL_CA_File:
|
||||
Master_SSL_CA_Path:
|
||||
Master_SSL_Cert:
|
||||
Master_SSL_Cipher:
|
||||
Master_SSL_Key:
|
||||
Seconds_Behind_Master: 0
|
||||
Master_SSL_Verify_Server_Cert: No
|
||||
Last_IO_Errno: 0
|
||||
Last_IO_Error:
|
||||
Last_SQL_Errno: 0
|
||||
Last_SQL_Error:
|
||||
Replicate_Ignore_Server_Ids:
|
||||
Master_Server_Id: 1
|
||||
1 row in set (0.00 sec)
|
||||
|
||||
At this step all shoul be ok, and not erros should be here.
|
||||
|
||||
### Test the replication ###
|
||||
|
||||
At MAIN/MASTER server add some entities to DB
|
||||
|
||||
mysql -u root -pSOME_ROOT_PASSWORD test_repl
|
||||
|
||||
mysql> INSERT INTO Persons VALUES (6, "LastName6", "FirstName6", "Address6", "City6");
|
||||
mysql> INSERT INTO Persons VALUES (7, "LastName7", "FirstName7", "Address7", "City7");
|
||||
mysql> INSERT INTO Persons VALUES (8, "LastName8", "FirstName8", "Address8", "City8");
|
||||
|
||||
Then go to the SLAVE server and check replicated data
|
||||
|
||||
mysql -u root -pSOME_ROOT_PASSWORD test_repl
|
||||
|
||||
mysql> select * from Persons;
|
||||
|
||||
+----------+-----------+------------+----------+-------+
|
||||
| PersonID | LastName | FirstName | Address | City |
|
||||
+----------+-----------+------------+----------+-------+
|
||||
...................
|
||||
| 6 | LastName6 | FirstName6 | Address6 | City6 |
|
||||
| 7 | LastName7 | FirstName7 | Address7 | City7 |
|
||||
| 8 | LastName8 | FirstName8 | Address8 | City8 |
|
||||
+----------+-----------+------------+----------+-------+
|
||||
|
||||
You can see the data is replicated to slave server. Its mean that replication is working. Hope you enjoyed the article. Let us know if you have any questions.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/how-tos/configure-mariadb-replication-centos-linux/
|
||||
|
||||
作者:[Bobbin Zachariah][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/bobbin/
|
||||
@ -0,0 +1,160 @@
|
||||
How to Install Discourse in a Docker Container
|
||||
================================================================================
|
||||
Hi all, today we'll learn how to install Discourse using Docker Platform. Discourse is the 100% open source discussion platform built for the next decade of the Internet featuring as a mailing list, a discussion forum and a long-form chat room. It is a smart way of attempt to reimagine what a modern, sustainable, fully open-source Internet discussion platform should be today, both from a technology standpoint and a sociology standpoint. Discourse is simple, clean, and straightforward way for discussion. It is really an awesome platform for any kinds of discussions on internet featuring such a cool services out of the box. Docker is an open source platform that provides an open platform to pack, ship and run any application as a lightweight container. Docker containers makes Discourse a lot handy and easy to setup app.
|
||||
|
||||
So, here are some quick and easy steps in order to install Discourse inside a Docker environment.
|
||||
|
||||
### 1. Installing Docker ###
|
||||
|
||||
First of all, we need to make sure that we have Docker installed in our host Operating System. To install, we'll need to the run the following command in a shell or terminal.
|
||||
|
||||
#### On Ubuntu ####
|
||||
|
||||
Package docker is available in Ubuntu's repository so, we'll be using apt manager to install it in sudo or root mode.
|
||||
|
||||
# apt-get install docker
|
||||
|
||||
#### On CentOS 7 ####
|
||||
|
||||
On CentOS 7 machine, we'll use yum manager to install docker as it is also available in CentOS's repository.
|
||||
|
||||
# yum install docker
|
||||
|
||||

|
||||
|
||||
### 2. Setting Swap Memory ###
|
||||
|
||||
If you have RAM size less than 1 GB then, make sure you upgrade your system to 1 GB or above cause Discourse doesn't get installed in 512 MB RAM. If you are now ready to install Discourse with 1 GB or above, follow the following steps to setup swap memory for you VPS or Server.
|
||||
|
||||
We'll create an empty swapfile by running the following command.
|
||||
|
||||
# install -o root -g root -m 0600 /dev/null /swapfile
|
||||
|
||||
If you want your swap memory to be 1 GB, then do the below step and skip the next step.
|
||||
|
||||
# dd if=/dev/zero of=/swapfile bs=1k count=1024k
|
||||
|
||||
if you want it to be 2 GB, follow the below. Make sure you skip the above step.
|
||||
|
||||
# dd if=/dev/zero of=/swapfile bs=1k count=2048k
|
||||
|
||||
Then, we'll point Swap Memory as swapfile .
|
||||
|
||||
#mkswap /swapfile
|
||||
|
||||
To activate it run the following command.
|
||||
|
||||
#swapon /swapfile
|
||||
|
||||
Now, we'll add it to the file system table so its there after reboot:
|
||||
|
||||
# echo "/swapfile swap swap auto 0 0" | sudo tee -a /etc/fstab
|
||||
|
||||
Set the swappiness to 10 so its only uses as an emergency buffer.
|
||||
|
||||
# sudo sysctl -w vm.swappiness=10
|
||||
# echo vm.swappiness = 10 | sudo tee -a /etc/sysctl.conf
|
||||
|
||||
### 3. Installing Discourse ###
|
||||
|
||||
After installing Docker in our host machine, we'll now go further towards installing Discourse. We'll now clone Discourse from the official Discourse Github into /var/discourse directory. To do so, we'll need to run the following command.
|
||||
|
||||
# mkdir /var/discourse/
|
||||
|
||||
# cd /var/discourse/
|
||||
|
||||
# git clone https://github.com/discourse/discourse_docker.git /var/discourse/
|
||||
|
||||
After cloning the git repository, we'll copy the configuration file for our discourse server.
|
||||
|
||||
# cp samples/standalone.yml containers/app.yml
|
||||
|
||||

|
||||
|
||||
### 4. Configuring Discourse ###
|
||||
|
||||
Next, we'll edit the discourse configuration ie app.yml located inside containers directory using our favorite text editor.
|
||||
|
||||
# nano containers/app.yml
|
||||
|
||||
Now, we need to set the developer's email address to DISCOURSE_DEVELOPER_EMAILS as follows.
|
||||
|
||||
DISCOURSE_DEVELOPER_EMAILS: 'arun@linoxide.com'
|
||||
|
||||
Then, we'll set the hostname as the domain name of our server.
|
||||
|
||||
DISCOURSE_HOSTNAME: 'discourse.linoxide.com'
|
||||
|
||||
Then, set the mail credentials per our SMTP Server hosted in the same discourse machine or vps. The SMTP settings are required to send mail from your Discourse instance
|
||||
|
||||
DISCOURSE_SMTP_ADDRESS: smtp.linoxide.com
|
||||
DISCOURSE_SMTP_PORT: 587 # (optional)
|
||||
DISCOURSE_SMTP_USER_NAME: admin@linoxide.com # (optional)
|
||||
DISCOURSE_SMTP_PASSWORD: test123 # (optional)
|
||||
|
||||

|
||||
|
||||
Discourse Configuration
|
||||
|
||||
If you are using a 1 GB instance, set UNICORN_WORKERS to 2 and db_shared_buffers to 128MB so you have more memory room.
|
||||
|
||||
It is compulsory to create a mailing server to run Discourse. If you have a server then its cool, we can use its credentials. If you have no existing mail server, or you don't know what it is? No problem, create a free account on [Mandrill][1] ([Mailgun][2], or [Mailjet][3]), and use the credentials provided in the dashboard.
|
||||
|
||||
### 5. Starting Discourse App ###
|
||||
|
||||
After configuring the discourse configuration file, we'll surely wanna start our Discourse server. To do so, first we'll launch discourse bootstrap by running the following command under the current directory ie /var/discourse/ .
|
||||
|
||||
# ./launcher bootstrap app
|
||||
|
||||

|
||||
|
||||
The above command may take some minutes which automatically configures our Discourse environment. Then, after the processes are finished, we'll need to run the following to start our Discourse App.
|
||||
|
||||
#./launcher start app
|
||||
|
||||

|
||||
|
||||
If everything went as expected accordingly, we'll be able to access our fresh Discourse Web Interface using our favorite Web Browser by pointing the url to http://ip-address/ or http://discourse.linoxide.com/ . Then, we can create a new account and become admin.
|
||||
|
||||

|
||||
|
||||
### Maintenance ###
|
||||
|
||||
Here below are the usages of the launcher command inside /var/discourse/ directory so that we can commit maintenance and control over the Discourse Docker Container.
|
||||
|
||||
Usage: launcher COMMAND CONFIG [--skip-prereqs]
|
||||
Commands:
|
||||
start: Start/initialize a container
|
||||
stop: Stop a running container
|
||||
restart: Restart a container
|
||||
destroy: Stop and remove a container
|
||||
enter: Use nsenter to enter a container
|
||||
ssh: Start a bash shell in a running container
|
||||
logs: Docker logs for container
|
||||
mailtest: Test the mail settings in a container
|
||||
bootstrap: Bootstrap a container for the config based on a template
|
||||
rebuild: Rebuild a container (destroy old, bootstrap, start new)
|
||||
cleanup: Remove all containers that have stopped for > 24 hours
|
||||
|
||||
Options:
|
||||
--skip-prereqs Don't check prerequisites
|
||||
--docker-args Extra arguments to pass when running docker
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Hurray! We have successfully installed Discourse with Docker Technology. Docker technology makes Discourse very much easy to install in any Platform with all the requirement fulfilled. We need our own mailing server or credentials of a mailing server to get started with it. It is a great platform for easy modern mailing list, discussion platform.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/how-tos/install-discourse-docker-container/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
[1]:https://mandrillapp.com/
|
||||
[2]:http://www.mailgun.com/
|
||||
[3]:https://www.mailjet.com/pricing
|
||||
@ -0,0 +1,147 @@
|
||||
How to Install Linux Kernel 4.0 from Elrepo / Source on Ubuntu / CentOs
|
||||
================================================================================
|
||||
Hi everyone, today we'll learn how to install the latest Linux Kernel 4.0 from Elrepo and compiling using Source. Linux Kernel 4.0 is the latest Mainline Kernel codenamed ‘Hurr durr I’m a sheep’ till date. It is the kernel released after the stable released of 3.19.4 . April 12 is considered as a big day for all fans of the Open Source movement, as Linus Torvalds announced the release of Linux Kernel 4.0 and its immediate availability. It is considered as a big release as it consists of some awesome features which includes no-reboot patching (Live Patching), New and Updated Drivers, New and Latest Hardware Support and more interesting features with a new version change. But Kernel 4.0 is not considered as a huge release as expected but Linus announced that 4.1 is expected for a bigger release. The Live Patching feature was already integrated with the SUSE Enterprise Linux operating system. Here is the [release announcement][1] you can check for more details about the release.
|
||||
|
||||
> **WARNING**: Installing a new kernel may render your system unusable or unstable. If you proceed with the installation using the instructions below, make sure you back up any important data you have to an external hard drive.
|
||||
|
||||
### Installing Linux Kernel 4.0 on Ubuntu 15.04 ###
|
||||
|
||||
If you are running an Ubuntu 15.04 Distribution of Linux. You can simply install it straight from Ubuntu Kernel site. To install the latest Linux Kernel 4.0 in your Ubuntu 15.04, you'll need to run the following commands under root access in a shell or a terminal.
|
||||
|
||||
#### On a 64-bit Ubuntu 15.04 ####
|
||||
|
||||
$ wget http://kernel.ubuntu.com/~kernel-ppa/mainline/v4.0-vivid/linux-headers-4.0.0-040000-generic_4.0.0-040000.201504121935_amd64.deb
|
||||
|
||||
$ sudo dpkg -i linux-headers-4.0.0*.deb linux-image-4.0.0*.deb
|
||||
|
||||
#### On a 32-bit Ubuntu 15.04 ####
|
||||
|
||||
$ wget http://kernel.ubuntu.com/~kernel-ppa/mainline/v4.0-vivid/linux-headers-4.0.0-040000-generic_4.0.0-040000.201504121935_i386.deb
|
||||
|
||||
$ sudo dpkg -i linux-headers-4.0.0*.deb linux-image-4.0.0*.deb
|
||||
|
||||
### Installing Linux Kernel 4.0 on CentOS 7 ###
|
||||
|
||||
We can easily install Linux Kernel 4.0 using two ways in CentOS 7 .
|
||||
|
||||
1. Installing from Elrepo Repository
|
||||
1. Compiling and installing from the Source Code
|
||||
|
||||
First we'll gonna go for installing using ELRepo as its the easiest way to do.
|
||||
|
||||
#### Installing using Elrepo ####
|
||||
|
||||
**1. Downloading and Installing ELRepo**
|
||||
|
||||
We'll first gonna download the GPG key of ELRepo and install the relrepo-release package. As we're running CentOS 7, we'll gonna install elrepo-release-7.0-2.el7.elrepo.noarch.rpm using the command below.
|
||||
|
||||
Note: If you have a secure boot enabled please see [this page for more information][2].
|
||||
|
||||
# rpm --import https://www.elrepo.org/RPM-GPG-KEY-elrepo.org
|
||||
# rpm -Uvh http://www.elrepo.org/elrepo-release-7.0-2.el7.elrepo.noarch.rpm
|
||||
|
||||

|
||||
|
||||
**2. Updating Linux Kernel to version 4.0**
|
||||
|
||||
Now, we'll gonna install the latest stable kernel 4.0 from the ELRepo repository. To do so, we'll need to enter the following commands in a shell or terminal of the CentOS 7.
|
||||
|
||||
# yum --enablerepo=elrepo-kernel install kernel-ml
|
||||
|
||||

|
||||
|
||||
The above command will automatically install the Linux Kernel 4.0 build for CentOS 7.
|
||||
|
||||
Now, here below is the another way of installing the latest kernel 4.0 by compiling from the source.
|
||||
|
||||
#### Compiling and Installing from the Source ####
|
||||
|
||||
**1. Installing the Dependencies**
|
||||
|
||||
So, first of all we'll need to install the dependencies required to compile the linux kernel. To do so, we'll need to run the following command in a terminal or a shell.
|
||||
|
||||
# yum groupinstall "Development Tools"
|
||||
|
||||
# yum install gcc ncurses ncurses-devel
|
||||
|
||||

|
||||
|
||||
Then, we'll gonna update our whole system.
|
||||
|
||||
# yum update
|
||||
|
||||
**2. Downloading the source**
|
||||
|
||||
We'll now download the latest release linux kernel 4.0 source using wget command from the official repository of Linux Kernel. You can also download the kernel directly from the site [kernel.org][3] using your web browser also.
|
||||
|
||||
# cd /tmp/
|
||||
# wget https://www.kernel.org/pub/linux/kernel/v4.x/linux-4.0.tar.xz
|
||||
|
||||

|
||||
|
||||
**3. Extracting the tarball**
|
||||
|
||||
Once the file is downloaded we'll extract it under /usr/src/ directory by running the below command.
|
||||
|
||||
# tar -xf linux-4.0.tar.xz -C /usr/src/
|
||||
# cd /usr/src/linux-4.0/
|
||||
|
||||

|
||||
|
||||
**4. Configuring**
|
||||
|
||||
We have two options to configure the Linux Kernel. We can either create a new custom configuration or use the old configuration to build and install the Linux Kernel. It all depends on what you really want.
|
||||
|
||||
**For New Kernel Configuration**
|
||||
|
||||
Now we'll run the make menuconfig command in the shell or terminal to configure the Linux kernel. Once we've executed the below command a pop up window with all the menus appears. Here we can select our new kernel configuration. If you unfamiliar with these menus, just hit double ESC key to exit.
|
||||
|
||||
# make menuconfig
|
||||
|
||||

|
||||
|
||||
**For Old Configuration**
|
||||
|
||||
If you like to configure your latest kernel with your old configuration then simple type the below command. If you were asked any stuff, you can choose with Y or N or you can simply press Enter to continue.
|
||||
|
||||
# make oldconfig
|
||||
|
||||
#### Step 5. Compiling the Linux Kernel ####
|
||||
|
||||
Next, we'll execute the make command to compile the Kernel 4.0 . The compilation would take at least 20-30 minutes depends on your system configuration.
|
||||
|
||||
Note: If you got an error while compiling the kernel saying bc command not found. You can fix that by installing bc using the command **yum install bc** .
|
||||
|
||||
# make
|
||||

|
||||
|
||||
#### 6. Installing Linux Kernel 4.0 ####
|
||||
|
||||
Once the compilation is completed, we'll now finally install the **Kernel** in our Linux System. The below command will create files under /boot directory and also makes a new kernel entry in the Grub Menu.
|
||||
|
||||
# make modules_install install
|
||||
|
||||
#### 7. Verifying Kernel ####
|
||||
|
||||
After installing our latest kernel 4.0 we'll want to verify it. To do so we'll just type the following command on the terminal. If everything went fine, we'll get the kernel version ie. 4.0 enlisted in the output below.
|
||||
|
||||
# uname -r
|
||||
|
||||
#### Conclusion ####
|
||||
|
||||
Hurray, we have successfully installed the latest version of linux kernel ie 4.0 in our CentOS 7 Operating System. Upgrading a linux kernel is always not necessary cause the hardware you got working with the previous version of it may not get working with the newer version. We should make sure that the it includes the features and stuffs that are necessary to make your hardware working. But mostly, the newer stable versions of kernel makes your hardware performance better. So, if you have any questions, comments, feedback please do write on the comment box below and let us know what stuffs needs to be added or improved. Thank You! Enjoy the latest stable version of Linux Kernel 4.0 :-)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/how-tos/install-linux-kernel-4-0-elrepo-source/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
[1]:http://lkml.iu.edu/hypermail/linux/kernel/1504.1/03198.html
|
||||
[2]:http://elrepo.org/tiki/SecureBootKey
|
||||
[3]:http://kernel.org/
|
||||
@ -0,0 +1,93 @@
|
||||
sshuttle – A transparent proxy-based VPN using ssh
|
||||
================================================================================
|
||||
sshuttle allows you to create a VPN connection from your machine to any remote server that you can connect to via ssh, as long as that server has python 2.3 or higher.To work, you must have root access on the local machine, but you can have a normal account on the server.
|
||||
|
||||
It's valid to run sshuttle more than once simultaneously on a single client machine, connecting to a different server every time, so you can be on more than one VPN at once.If run on a router, sshuttle can forward traffic for your entire subnet to the VPN.
|
||||
|
||||
### Install sshuttle on ubuntu ###
|
||||
|
||||
Open the terminal and run the following command
|
||||
|
||||
sudo apt-get install sshuttle
|
||||
|
||||
### Using sshuttle ###
|
||||
|
||||
#### sshuttle Syntax ####
|
||||
|
||||
sshuttle [options...] [-r [username@]sshserver[:port]] [subnets]
|
||||
|
||||
#### Option details ####
|
||||
|
||||
-r, —remote=[username@]sshserver[:port]
|
||||
|
||||
the remote hostname and optional username and ssh port number to use for connecting to the remote server. For example,example.com, testuser@example.com, testuser@example.com:2222, or example.com:2244.
|
||||
|
||||
#### sshuttle Examples ####
|
||||
|
||||
From the machine use the following command
|
||||
|
||||
sudo sshuttle -r username@sshserver 0.0.0.0/0 -vv
|
||||
|
||||
When it starts, sshuttle creates an ssh session to the server specified by the -r option. If -r is omitted, it will start both its client and server locally, which is sometimes useful for testing.
|
||||
|
||||
After connecting to the remote server, sshuttle uploads its (python) source code to the remote end and executes it there. Thus, you don't need to install sshuttle on the remote server, and there are never sshuttle version conflicts between client and server.
|
||||
|
||||
#### More Examples From Man page ####
|
||||
|
||||
Test locally by proxying all local connections, without using ssh:
|
||||
|
||||
$ sudo sshuttle -v 0/0
|
||||
|
||||
Starting sshuttle proxy.
|
||||
Listening on (‘0.0.0.0′, 12300).
|
||||
[local sudo] Password:
|
||||
firewall manager ready.
|
||||
c : connecting to server...
|
||||
s: available routes:
|
||||
s: 192.168.42.0/24
|
||||
c : connected.
|
||||
firewall manager: starting transproxy.
|
||||
c : Accept: ‘192.168.42.106':50035 -> ‘192.168.42.121':139.
|
||||
c : Accept: ‘192.168.42.121':47523 -> ‘77.141.99.22':443.
|
||||
...etc...
|
||||
^C
|
||||
firewall manager: undoing changes.
|
||||
KeyboardInterrupt
|
||||
c : Keyboard interrupt: exiting.
|
||||
c : SW#8:192.168.42.121:47523: deleting
|
||||
c : SW#6:192.168.42.106:50035: deleting
|
||||
|
||||
Test connection to a remote server, with automatic hostname and subnet
|
||||
guessing:
|
||||
|
||||
$ sudo sshuttle -vNHr example.org
|
||||
|
||||
Starting sshuttle proxy.
|
||||
Listening on (‘0.0.0.0′, 12300).
|
||||
firewall manager ready.
|
||||
c : connecting to server...
|
||||
s: available routes:
|
||||
s: 77.141.99.0/24
|
||||
c : connected.
|
||||
c : seed_hosts: []
|
||||
firewall manager: starting transproxy.
|
||||
hostwatch: Found: testbox1: 1.2.3.4
|
||||
hostwatch: Found: mytest2: 5.6.7.8
|
||||
hostwatch: Found: domaincontroller: 99.1.2.3
|
||||
c : Accept: ‘192.168.42.121':60554 -> ‘77.141.99.22':22.
|
||||
^C
|
||||
firewall manager: undoing changes.
|
||||
c : Keyboard interrupt: exiting.
|
||||
c : SW#6:192.168.42.121:60554: deleting
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/sshuttle-a-transparent-proxy-based-vpn-using-ssh.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
@ -0,0 +1,355 @@
|
||||
Linux网络统计工具/命令
|
||||
================================================================================
|
||||
我在Linux(基于CentOS 或者 Debian 的发行版)中该如何查看当前网络端口吞吐量的统计信息?在Linux操作系统中如何查看当前内核snmp计数器以及网络端口的统计信息?
|
||||
|
||||

|
||||
|
||||
你可以使用以下任何一个命令:
|
||||
|
||||
### nstat 命令 : 网络统计工具 ###
|
||||
|
||||
键入以下命令:
|
||||
|
||||
# nstat
|
||||
|
||||
输出样例:
|
||||
|
||||
#kernel
|
||||
IpInReceives 133243 0.0
|
||||
IpInDelivers 133243 0.0
|
||||
IpOutRequests 92904 0.0
|
||||
IcmpOutErrors 97 0.0
|
||||
IcmpOutTimeExcds 97 0.0
|
||||
IcmpMsgOutType3 97 0.0
|
||||
TcpActiveOpens 538 0.0
|
||||
TcpEstabResets 56 0.0
|
||||
TcpInSegs 129837 0.0
|
||||
TcpOutSegs 89720 0.0
|
||||
TcpRetransSegs 42 0.0
|
||||
TcpOutRsts 704 0.0
|
||||
UdpInDatagrams 3255 0.0
|
||||
UdpNoPorts 97 0.0
|
||||
UdpOutDatagrams 3270 0.0
|
||||
Ip6OutNoRoutes 206 0.0
|
||||
TcpExtTW 141 0.0
|
||||
TcpExtDelayedACKs 508 0.0
|
||||
TcpExtDelayedACKLocked 1 0.0
|
||||
TcpExtDelayedACKLost 42 0.0
|
||||
TcpExtTCPHPHits 117659 0.0
|
||||
TcpExtTCPPureAcks 2158 0.0
|
||||
TcpExtTCPHPAcks 605 0.0
|
||||
TcpExtTCPSackRecovery 1 0.0
|
||||
TcpExtTCPLossUndo 16 0.0
|
||||
TcpExtTCPSackFailures 4 0.0
|
||||
TcpExtTCPFastRetrans 1 0.0
|
||||
TcpExtTCPSlowStartRetrans 3 0.0
|
||||
TcpExtTCPTimeouts 33 0.0
|
||||
TcpExtTCPDSACKOldSent 40 0.0
|
||||
TcpExtTCPDSACKRecv 5 0.0
|
||||
TcpExtTCPAbortOnData 120 0.0
|
||||
TcpExtTCPAbortOnClose 55 0.0
|
||||
TcpExtTCPSackShiftFallback 9 0.0
|
||||
IpExtInOctets 180131682 0.0
|
||||
IpExtOutOctets 7289106 0.0
|
||||
|
||||
### ss 命令 : 查询套接字工具 ###
|
||||
|
||||
要查看统计汇总, 输入:
|
||||
|
||||
# ss -s
|
||||
|
||||
输出样例:
|
||||
|
||||
Total: 786 (kernel 804)
|
||||
TCP: 65 (estab 40, closed 7, orphaned 0, synrecv 0, timewait 6/0), ports 56
|
||||
Transport Total IP IPv6
|
||||
* 804 - -
|
||||
RAW 1 1 0
|
||||
UDP 12 9 3
|
||||
TCP 58 52 6
|
||||
INET 71 62 9
|
||||
FRAG 0 0 0
|
||||
|
||||
查看[ss 命令教程][1] 获取更多信息。
|
||||
|
||||
### netstat 命令 : 显示套接字信息的旧的好工具 ###
|
||||
|
||||
查看所有网络端口以及汇总信息表,输入:
|
||||
|
||||
# netstat -i
|
||||
|
||||
输出样例:
|
||||
|
||||
Kernel Interface table
|
||||
Iface MTU Met RX-OK RX-ERR RX-DRP RX-OVR TX-OK TX-ERR TX-DRP TX-OVR Flg
|
||||
eth0 1500 0 941022 0 0 0 688165 0 0 0 BMRU
|
||||
lo 16436 0 9304 0 0 0 9304 0 0 0 LRU
|
||||
ppp0 1496 0 3784 0 0 0 4177 0 0 0 MOPRU
|
||||
|
||||
查看每个协议的汇总统计信息,输入:
|
||||
|
||||
# netstat -s
|
||||
|
||||
输出样例:
|
||||
|
||||
Ip:
|
||||
1092065 total packets received
|
||||
0 forwarded
|
||||
0 incoming packets discarded
|
||||
1091681 incoming packets delivered
|
||||
798913 requests sent out
|
||||
895 dropped because of missing route
|
||||
759 reassemblies required
|
||||
375 packets reassembled ok
|
||||
Icmp:
|
||||
17 ICMP messages received
|
||||
0 input ICMP message failed.
|
||||
ICMP input histogram:
|
||||
timeout in transit: 8
|
||||
echo replies: 9
|
||||
1747 ICMP messages sent
|
||||
0 ICMP messages failed
|
||||
ICMP output histogram:
|
||||
destination unreachable: 1730
|
||||
echo request: 17
|
||||
IcmpMsg:
|
||||
InType0: 9
|
||||
InType11: 8
|
||||
OutType3: 1730
|
||||
OutType8: 17
|
||||
Tcp:
|
||||
4822 active connections openings
|
||||
1129 passive connection openings
|
||||
457 failed connection attempts
|
||||
165 connection resets received
|
||||
7 connections established
|
||||
1062519 segments received
|
||||
771394 segments send out
|
||||
7158 segments retransmited
|
||||
6 bad segments received.
|
||||
2578 resets sent
|
||||
Udp:
|
||||
20846 packets received
|
||||
1730 packets to unknown port received.
|
||||
0 packet receive errors
|
||||
19242 packets sent
|
||||
UdpLite:
|
||||
TcpExt:
|
||||
71 invalid SYN cookies received
|
||||
8 resets received for embryonic SYN_RECV sockets
|
||||
142 packets pruned from receive queue because of socket buffer overrun
|
||||
2109 TCP sockets finished time wait in fast timer
|
||||
84 packets rejects in established connections because of timestamp
|
||||
19454 delayed acks sent
|
||||
6 delayed acks further delayed because of locked socket
|
||||
Quick ack mode was activated 7306 times
|
||||
1 packets directly queued to recvmsg prequeue.
|
||||
1 bytes directly received in process context from prequeue
|
||||
823921 packet headers predicted
|
||||
24412 acknowledgments not containing data payload received
|
||||
10150 predicted acknowledgments
|
||||
242 times recovered from packet loss by selective acknowledgements
|
||||
33 congestion windows recovered without slow start by DSACK
|
||||
335 congestion windows recovered without slow start after partial ack
|
||||
336 TCP data loss events
|
||||
TCPLostRetransmit: 35
|
||||
1 timeouts after reno fast retransmit
|
||||
156 timeouts after SACK recovery
|
||||
116 timeouts in loss state
|
||||
461 fast retransmits
|
||||
5 forward retransmits
|
||||
608 retransmits in slow start
|
||||
2073 other TCP timeouts
|
||||
62 SACK retransmits failed
|
||||
43074 packets collapsed in receive queue due to low socket buffer
|
||||
8499 DSACKs sent for old packets
|
||||
101 DSACKs sent for out of order packets
|
||||
308 DSACKs received
|
||||
9 DSACKs for out of order packets received
|
||||
427 connections reset due to unexpected data
|
||||
122 connections reset due to early user close
|
||||
28 connections aborted due to timeout
|
||||
TCPDSACKIgnoredOld: 3
|
||||
TCPDSACKIgnoredNoUndo: 60
|
||||
TCPSpuriousRTOs: 4
|
||||
TCPSackShifted: 282
|
||||
TCPSackMerged: 740
|
||||
TCPSackShiftFallback: 1017
|
||||
IpExt:
|
||||
InMcastPkts: 47
|
||||
OutMcastPkts: 51
|
||||
InBcastPkts: 1
|
||||
InOctets: 1341508973
|
||||
OutOctets: 72525352
|
||||
InMcastOctets: 8649
|
||||
OutMcastOctets: 7519
|
||||
InBcastOctets: 328
|
||||
|
||||
查看 [netstat 命令教程][2] 获取更多信息。
|
||||
|
||||
### ip / ifconfig 命令 : 配置或者显示网络端口信息 ###
|
||||
|
||||
键入以下命令:
|
||||
|
||||
# ifconfig
|
||||
|
||||
或者
|
||||
|
||||
# /sbin/ifconfig
|
||||
|
||||
或者
|
||||
|
||||
# ifconfig eth0
|
||||
|
||||
----------
|
||||
|
||||
eth0 Link encap:Ethernet HWaddr b8:ac:6f:65:31:e5
|
||||
inet addr:192.168.1.5 Bcast:192.168.1.255 Mask:255.255.255.0
|
||||
inet6 addr: fe80::baac:6fff:fe65:31e5/64 Scope:Link
|
||||
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
|
||||
RX packets:966334 errors:0 dropped:0 overruns:0 frame:0
|
||||
TX packets:703297 errors:0 dropped:0 overruns:0 carrier:0
|
||||
collisions:0 txqueuelen:1000
|
||||
RX bytes:1186255648 (1.1 GiB) TX bytes:73968238 (70.5 MiB)
|
||||
Interrupt:17
|
||||
lo Link encap:Local Loopback
|
||||
inet addr:127.0.0.1 Mask:255.0.0.0
|
||||
inet6 addr: ::1/128 Scope:Host
|
||||
UP LOOPBACK RUNNING MTU:16436 Metric:1
|
||||
RX packets:9666 errors:0 dropped:0 overruns:0 frame:0
|
||||
TX packets:9666 errors:0 dropped:0 overruns:0 carrier:0
|
||||
collisions:0 txqueuelen:0
|
||||
RX bytes:1399578 (1.3 MiB) TX bytes:1399578 (1.3 MiB)
|
||||
ppp0 Link encap:Point-to-Point Protocol
|
||||
inet addr:10.1.11.70 P-t-P:10.0.31.18 Mask:255.255.255.255
|
||||
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1496 Metric:1
|
||||
RX packets:3784 errors:0 dropped:0 overruns:0 frame:0
|
||||
TX packets:4177 errors:0 dropped:0 overruns:0 carrier:0
|
||||
collisions:0 txqueuelen:3
|
||||
RX bytes:2400265 (2.2 MiB) TX bytes:275983 (269.5 KiB)
|
||||
|
||||
显示网络端口统计信息,输入:
|
||||
|
||||
# ip -s link
|
||||
|
||||
输出样例:
|
||||
|
||||
1: lo: mtu 16436 qdisc noqueue state UNKNOWN
|
||||
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
|
||||
RX: bytes packets errors dropped overrun mcast
|
||||
1444187 9960 0 0 0 0
|
||||
TX: bytes packets errors dropped carrier collsns
|
||||
1444187 9960 0 0 0 0
|
||||
2: eth0: mtu 1500 qdisc mq state UP qlen 1000
|
||||
link/ether b8:ac:6f:65:31:e5 brd ff:ff:ff:ff:ff:ff
|
||||
RX: bytes packets errors dropped overrun mcast
|
||||
1221956483 991501 0 0 0 24
|
||||
TX: bytes packets errors dropped carrier collsns
|
||||
75623937 720272 0 0 0 0
|
||||
3: wlan0: mtu 1500 qdisc noop state DOWN qlen 1000
|
||||
link/ether 00:21:6a:ca:9b:10 brd ff:ff:ff:ff:ff:ff
|
||||
RX: bytes packets errors dropped overrun mcast
|
||||
0 0 0 0 0 0
|
||||
TX: bytes packets errors dropped carrier collsns
|
||||
0 0 0 0 0 0
|
||||
4: pan0: mtu 1500 qdisc noop state DOWN
|
||||
link/ether 4a:c7:5f:0e:8e:d8 brd ff:ff:ff:ff:ff:ff
|
||||
RX: bytes packets errors dropped overrun mcast
|
||||
0 0 0 0 0 0
|
||||
TX: bytes packets errors dropped carrier collsns
|
||||
0 0 0 0 0 0
|
||||
8: ppp0: mtu 1496 qdisc pfifo_fast state UNKNOWN qlen 3
|
||||
link/ppp
|
||||
RX: bytes packets errors dropped overrun mcast
|
||||
2419881 3848 0 0 0 0
|
||||
TX: bytes packets errors dropped carrier collsns
|
||||
284151 4287 0 0 0 0
|
||||
|
||||
### sar 命令: 显示网络统计信息 ###
|
||||
|
||||
输入以下命令 (你需要 [通过sysstat包安装并启用sar][3]):
|
||||
sar -n DEV
|
||||
|
||||
Linux 2.6.32-220.2.1.el6.x86_64 (www.cyberciti.biz) Tuesday 13 March 2012 _x86_64_ (2 CPU)
|
||||
12:00:01 CDT IFACE rxpck/s txpck/s rxkB/s txkB/s rxcmp/s txcmp/s rxmcst/s
|
||||
12:10:01 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
12:10:01 CDT eth0 127.13 121.32 95.45 18.34 0.00 0.00 0.00
|
||||
12:10:01 CDT eth1 98.48 110.62 16.72 96.33 0.00 0.00 0.00
|
||||
12:20:01 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
12:20:01 CDT eth0 139.95 133.41 106.30 19.95 0.00 0.00 0.00
|
||||
12:20:01 CDT eth1 110.65 121.85 18.14 107.13 0.00 0.00 0.00
|
||||
12:30:01 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
12:30:01 CDT eth0 147.85 132.49 115.78 20.45 0.00 0.00 0.00
|
||||
12:30:01 CDT eth1 111.88 127.39 18.61 117.65 0.00 0.00 0.00
|
||||
12:40:01 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
12:40:01 CDT eth0 136.75 124.64 105.24 19.48 0.00 0.00 0.00
|
||||
12:40:01 CDT eth1 101.65 115.32 17.58 104.50 0.00 0.00 0.00
|
||||
12:50:01 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
12:50:01 CDT eth0 131.45 125.69 96.49 19.58 0.00 0.00 0.00
|
||||
12:50:01 CDT eth1 101.41 111.31 17.54 96.78 0.00 0.00 0.00
|
||||
01:00:01 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
01:00:01 CDT eth0 140.30 133.27 102.17 20.75 0.00 0.00 0.00
|
||||
01:00:01 CDT eth1 106.90 119.51 18.53 103.09 0.00 0.00 0.00
|
||||
01:10:01 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
01:10:01 CDT eth0 152.03 127.74 125.56 19.85 0.00 0.00 0.00
|
||||
01:10:01 CDT eth1 115.60 134.57 18.73 126.96 0.00 0.00 0.00
|
||||
01:20:01 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
01:20:01 CDT eth0 138.55 130.55 103.03 20.20 0.00 0.00 0.00
|
||||
....
|
||||
..
|
||||
....
|
||||
..
|
||||
.
|
||||
01:00:01 CDT eth1 156.82 169.48 28.83 138.49 0.00 0.00 0.00
|
||||
01:10:01 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
01:10:01 CDT eth0 215.19 194.82 163.11 30.99 0.00 0.00 0.00
|
||||
01:10:01 CDT eth1 162.49 183.79 28.36 163.70 0.00 0.00 0.00
|
||||
01:20:01 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
01:20:01 CDT eth0 200.20 192.23 140.64 30.93 0.00 0.00 0.00
|
||||
01:20:01 CDT eth1 153.60 166.96 27.32 140.26 0.00 0.00 0.00
|
||||
01:30:01 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
01:30:01 CDT eth0 111.98 103.58 79.12 16.52 0.00 0.00 0.48
|
||||
01:30:01 CDT eth1 87.50 95.58 14.74 79.35 0.00 0.00 0.00
|
||||
Average: IFACE rxpck/s txpck/s rxkB/s txkB/s rxcmp/s txcmp/s rxmcst/s
|
||||
Average: lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
Average: eth0 211.21 196.20 156.18 31.20 0.00 0.00 0.01
|
||||
Average: eth1 159.10 174.52 28.00 149.95 0.00 0.00 0.00
|
||||
|
||||
或者输入以下命令:
|
||||
|
||||
# sar -n DEV 1 3
|
||||
|
||||
输出样例:
|
||||
|
||||
Linux 2.6.32-220.2.1.el6.x86_64 (www.cyberciti.biz) Tuesday 13 March 2012 _x86_64_ (2 CPU)
|
||||
01:44:03 CDT IFACE rxpck/s txpck/s rxkB/s txkB/s rxcmp/s txcmp/s rxmcst/s
|
||||
01:44:04 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
01:44:04 CDT eth0 161.70 154.26 105.20 26.63 0.00 0.00 0.00
|
||||
01:44:04 CDT eth1 145.74 142.55 25.11 144.94 0.00 0.00 0.00
|
||||
01:44:04 CDT IFACE rxpck/s txpck/s rxkB/s txkB/s rxcmp/s txcmp/s rxmcst/s
|
||||
01:44:05 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
01:44:05 CDT eth0 162.14 156.31 107.46 42.18 0.00 0.00 0.00
|
||||
01:44:05 CDT eth1 135.92 138.83 39.38 104.92 0.00 0.00 0.00
|
||||
01:44:05 CDT IFACE rxpck/s txpck/s rxkB/s txkB/s rxcmp/s txcmp/s rxmcst/s
|
||||
01:44:06 CDT lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
01:44:06 CDT eth0 303.92 293.14 272.91 37.40 0.00 0.00 0.00
|
||||
01:44:06 CDT eth1 252.94 290.20 34.87 263.50 0.00 0.00 0.00
|
||||
Average: IFACE rxpck/s txpck/s rxkB/s txkB/s rxcmp/s txcmp/s rxmcst/s
|
||||
Average: lo 0.00 0.00 0.00 0.00 0.00 0.00 0.00
|
||||
Average: eth0 210.37 202.34 163.19 35.66 0.00 0.00 0.00
|
||||
Average: eth1 178.93 191.64 33.36 171.60 0.00 0.00 0.00
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.cyberciti.biz/faq/network-statistics-tools-rhel-centos-debian-linux/
|
||||
|
||||
作者:[nixCraft][a]
|
||||
译者:[ictlyh](https://github.com/ictlyh)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.cyberciti.biz/tips/about-us
|
||||
[1]:http://www.cyberciti.biz/tips/linux-investigate-sockets-network-connections.html
|
||||
[2]:http://www.cyberciti.biz/tips/netstat-command-tutorial-examples.html
|
||||
[3]:http://www.cyberciti.biz/tips/identifying-linux-bottlenecks-sar-graphs-with-ksar.html
|
||||
Loading…
Reference in New Issue
Block a user