mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-30 02:40:11 +08:00
commit
4084afeb28
published
20190301 Emacs for (even more of) the win.md20190320 4 cool terminal multiplexers.md20190531 Use Firefox Send with ffsend in Fedora.md
201906
20170410 Writing a Time Series Database from Scratch.md20170414 5 projects for Raspberry Pi at home.md20180324 Memories of writing a parser for man pages.md20180416 How To Resize Active-Primary root Partition Using GParted Utility.md20180604 BootISO - A Simple Bash Script To Securely Create A Bootable USB Device From ISO File.md20180831 Get desktop notifications from Emacs shell commands .md20180914 A day in the life of a log message.md20190109 GoAccess - A Real-Time Web Server Log Analyzer And Interactive Viewer.md20190111 Top 5 Linux Distributions for Productivity.md20190219 5 Good Open Source Speech Recognition-Speech-to-Text Systems.md20190308 Blockchain 2.0 - Explaining Smart Contracts And Its Types -Part 5.md20190331 How to build a mobile particulate matter sensor with a Raspberry Pi.md20190404 Running LEDs in reverse could cool computers.md20190405 Blockchain 2.0 - Ongoing Projects (The State Of Smart Contracts Now) -Part 6.md20190409 5 Linux rookie mistakes.md20190409 5 open source mobile apps.md20190409 VSCodium- 100- Open Source Version of Microsoft VS Code.md20190410 How we built a Linux desktop app with Electron.md20190411 Be your own certificate authority.md20190417 Inter-process communication in Linux- Sockets and signals.md20190422 4 open source apps for plant-based diets.md20190423 Edge computing is in most industries- future.md20190423 Epic Games Store is Now Available on Linux Thanks to Lutris.md20190423 How to identify same-content files on Linux.md20190427 Monitoring CPU and GPU Temperatures on Linux.md20190428 Installing Budgie Desktop on Ubuntu -Quick Guide.md20190505 How To Install-Uninstall Listed Packages From A File In Linux.md20190508 Why startups should release their code as open source.md20190509 5 essential values for the DevOps mindset.md20190513 How To Check Whether The Given Package Is Installed Or Not On Debian-Ubuntu System.md20190517 10 Places Where You Can Buy Linux Computers.md20190517 Using Testinfra with Ansible to verify server state.md20190520 Getting Started With Docker.md20190520 When IoT systems fail- The risk of having bad IoT data.md20190520 Zettlr - Markdown Editor for Writers and Researchers.md20190522 French IT giant Atos enters the edge-computing business.md20190522 Securing telnet connections with stunnel.md20190525 4 Ways to Run Linux Commands in Windows.md20190527 20- FFmpeg Commands For Beginners.md20190527 5 GNOME keyboard shortcuts to be more productive.md20190527 A deeper dive into Linux permissions.md20190527 Dockly - Manage Docker Containers From Terminal.md20190527 How To Check Available Security Updates On Red Hat (RHEL) And CentOS System.md20190527 How to write a good C main function.md20190529 NVMe on Linux.md20190530 A short primer on assemblers, compilers, and interpreters.md20190531 Learn Python with these awesome resources.md20190531 Unity Editor is Now Officially Available for Linux.md20190531 Why translation platforms matter.md20190604 How To Verify NTP Setup (Sync) is Working or Not In Linux.md20190604 Kubernetes is a dump truck- Here-s why.md20190604 Two Methods To Check Or List Installed Security Updates on Redhat (RHEL) And CentOS System.md20190605 How to navigate the Kubernetes learning curve.md20190606 Cisco to buy IoT security, management firm Sentryo.md20190606 How Linux can help with your spelling.md20190606 Kubernetes basics- Learn how to drive first.md20190607 5 reasons to use Kubernetes.md20190608 An open source bionic leg, Python data pipeline, data breach detection, and more news.md20190610 Applications for writing Markdown.md20190610 Expand And Unexpand Commands Tutorial With Examples.md20190610 Graviton- A Minimalist Open Source Code Editor.md20190610 Neofetch - Display Linux system Information In Terminal.md20190610 Screen Command Examples To Manage Multiple Terminal Sessions.md20190610 Search Linux Applications On AppImage, Flathub And Snapcraft Platforms.md20190610 Try a new game on Free RPG Day.md20190610 Welcoming Blockchain 3.0.md20190612 Installing alternative versions of RPMs in Fedora.md20190613 Open hardware for musicians and music lovers- Headphone, amps, and more.md20190613 Ubuntu Kylin- The Official Chinese Version of Ubuntu.md20190614 How to send email from the Linux command line.md20190614 Personal assistant with Mycroft and Fedora.md20190617 Exploring -run on Linux.md20190619 Get the latest Ansible 2.8 in Fedora.md20190621 Bash Script to Monitor Memory Usage on Linux.md20190622 Open Source Slack Alternative Mattermost Gets -50M Funding.md20190624 Raspberry Pi 4 is here.md20190624 Using i3 with multiple monitors.md20190628 FreeDOS turns 25 years old- An origin story.md
20190610 5 Easy Ways To Free Up Space (Remove Unwanted or Junk Files) on Ubuntu.md20190612 BitTorrent Client Deluge 2.0 Released- Here-s What-s New.md20190619 Leading in the Python community.md20190621 Three Ways to Lock and Unlock User Account in Linux.md20190624 With Upgraded Specs, Raspberry Pi 4 Takes Aim at Desktop Segment.md20190625 5 tiny Linux distros to try before you die.mdsources
news
20190606 Cisco to buy IoT security, management firm Sentryo.md20190606 Zorin OS Becomes Even More Awesome With Zorin 15 Release.md20190607 Free and Open Source Trello Alternative OpenProject 9 Released.md20190612 BitTorrent Client Deluge 2.0 Released- Here-s What-s New.md20190624 Raspberry Pi 4 is here.md20190628 Undo releases Live Recorder 5.0 for Linux debugging.md
talk
20190604 5G will augment Wi-Fi, not replace it.md20190701 Tempered Networks simplifies secure network connectivity and microsegmentation.md20190702 SD-WAN Buyers Should Think Application Performance as well as Resiliency.md20190703 An eco-friendly internet of disposable things is coming.md
tech
83
published/20190301 Emacs for (even more of) the win.md
Normal file
83
published/20190301 Emacs for (even more of) the win.md
Normal file
@ -0,0 +1,83 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (oneforalone)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11046-1.html)
|
||||
[#]: subject: (Emacs for (even more of) the win)
|
||||
[#]: via: (https://so.nwalsh.com/2019/03/01/emacs)
|
||||
[#]: author: (Norman Walsh https://so.nwalsh.com)
|
||||
|
||||
Emacs 的(更多)胜利
|
||||
======
|
||||
|
||||

|
||||
|
||||
我天天用 Emacs,但我却从意识到。但是每当我用 Emacs 时,它都给我带来了很多乐趣。
|
||||
|
||||
> 如果你是个职业作家……Emacs 与其它的编辑器的相比就如皓日与群星一样。不仅更大、更亮,它轻而易举就让其他所有的东西都消失了。
|
||||
|
||||
我用 [Emacs][1] 已有二十多年了。我用它来写几乎所有的东西(我用 [IntelliJ][2] 编辑 Scala 和 Java )。看邮件的话我是能在 Emacs 里看就在里面看。
|
||||
|
||||
尽管我用 Emacs 已有数十年,我在新年前后才意识到,在过去十几年里,我对 Emacs 的使用几乎没有什么变化。当然,新的编辑模式出现了,我就会选一两个插件,几年前我确实是用了 [Helm][3],但大多数时候,它只是完成了我需要的所有繁重工作,日复一日,没有抱怨,也没有妨碍我。一方面,这证明了它有多好。另一方面,这是一个邀请,让我深入挖掘,看看我错过了什么。
|
||||
|
||||
于此同时,我也决定从以下几方面改进我的工作方式:
|
||||
|
||||
* **更好的议程管理** 我在工作中负责几个项目,这些项目有定期和临时的会议;有些我是我主持的,有些我只要参加就可以。
|
||||
|
||||
我意识到我对参加会议变得有些敷衍。往会议室里一坐很简单,但实际上我是在阅读电子邮件或处理其他事情。(我强烈反对在会议中“禁止携带笔记本电脑”的这条规定,但这是另一个话题。)
|
||||
|
||||
敷衍地去参加会议有几个问题。首先,这是对主持会议的人和其他参会者的不尊重。实际上这是不应该这么做的充分理由,但我还有意识到另一个问题:它掩盖了会议的成本。
|
||||
|
||||
如果你在开会,但同时回复了一封电子邮件,也许修复了一个 bug,那么这个会议就没什么成本(或没那么多)。如果会议成本低廉,那么会议数量将会更多。
|
||||
|
||||
我想要更少、更短的会议。我不想掩盖它们的成本,我想让开会变得很有价值,除非绝对必要,否则就干脆不要开。
|
||||
|
||||
有时,开会是绝对有必要的。而且我认为一个简短的会有时候能够很快的解决问题。但是,如果我一天要开十个短会的话,那我觉得还是不要假装取得了什么效果吧。
|
||||
|
||||
我决定在我参加的所有的会上做笔记。我并不是说一定要做会议记录,但是我肯定会花上几分钟。这会让我把注意力集中在开会上,而忽略其他事。
|
||||
|
||||
* **更好的时间管理** 无论是工作的或私人的,我有很多要做和想做的事。我一直在问题列表中跟踪其中的一些,一些在保存的电子邮件线索中(Emacs 和 [Gmail][4] 中,用于一些稍微不同的提醒),还有一些在日历、手机上各种各样的“待办事项列表”和小纸片上。可能还有其他地方。
|
||||
|
||||
我决定把它们放在一起。不是说我认为放到一个一致的地方就更好,而是我想完成两件事:首先,把它们都集中在一个地方,我能够更好更全面地了解我在哪里投入了更多的精力;其次,我想养成一个记录、跟踪并保存它们的习惯(习惯指“固定或规律的倾向或做法,尤指难以放弃的倾向或做法”)。
|
||||
|
||||
* **更好的问责制** 如果你在某些科学或工程领域工作,你就会养成记笔记的习惯。唉,我没有。但我决定这么做。
|
||||
|
||||
我对法律上鼓励使用装订页面或用永久记号笔涂抹并不感兴趣。我感兴趣的是养成做记录的习惯。我的目标是有一个地方记下想法和设计草图等。如果我突然有了灵感,或者我想到了一个不在测试套件中的边缘情况,我希望我的直觉是把它写在我的日志中,而不是草草写在一张小纸片上,或者自己觉得自己会记住它。
|
||||
|
||||
这些决心让我很快或多或少指向了 [Org][6] 模式。Org 模式有一个庞大的、活跃的、忠诚的用户社区。我以前也用过它(顺带一提,我都[写过][7]关于它的文章,在几年前),我花了很长的一段时间(将 [MarkLogic 集成][8]到其中。(这在过去的一两个星期里得到了回报!)
|
||||
|
||||
但我从没正经用过 Org 模式。
|
||||
|
||||
我现在正在用它。我用了几分钟,我把所有要做的事情都记录下来,我还记了日记。我不确定我争论或列表它的所有功能能有多大价值,你可以通过网页快速地搜索找到很多。
|
||||
|
||||
如果你用 Emacs,那你也应该用 Org 模式。如果没用过 Emacs,我相信你不会是第一个因 Org 模式而使用 Emacs 的人。Org 模式可以做很多。它需要一点时间来学习方法和快捷键,但我认为这是值得的。(如果你的口袋中有一台 [iOS][9] 设备,我推荐你在路上使用 [beorg][10] 来记录。)
|
||||
|
||||
当然,我想出了如何[将 XML 从其中提取出来][11](“working out” 确实是“用 elisp 来编程”的一种有趣的魔法)然后,如何将它转换回我的博客用的标记(当然,在 Emacs 中按下一个按钮就可以做到)。这是用 Org 模式写的第一篇帖子。这也不会是最后一次。
|
||||
|
||||
附注:生日快乐,[小博客][12]。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://so.nwalsh.com/2019/03/01/emacs
|
||||
|
||||
作者:[Norman Walsh][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[oneforalone](https://github.com/oneforalone)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://so.nwalsh.com
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Emacs
|
||||
[2]: https://en.wikipedia.org/wiki/IntelliJ_IDEA
|
||||
[3]: https://emacs-helm.github.io/helm/
|
||||
[4]: https://en.wikipedia.org/wiki/Gmail
|
||||
[5]: https://en.wikipedia.org/wiki/Lab_notebook
|
||||
[6]: https://en.wikipedia.org/wiki/Org-mode
|
||||
[7]: https://www.balisage.net/Proceedings/vol17/html/Walsh01/BalisageVol17-Walsh01.html
|
||||
[8]: https://github.com/ndw/ob-ml-marklogic/
|
||||
[9]: https://en.wikipedia.org/wiki/IOS
|
||||
[10]: https://beorgapp.com/
|
||||
[11]: https://github.com/ndw/org-to-xml
|
||||
[12]: https://so.nwalsh.com/2017/03/01/helloWorld
|
||||
117
published/20190320 4 cool terminal multiplexers.md
Normal file
117
published/20190320 4 cool terminal multiplexers.md
Normal file
@ -0,0 +1,117 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11054-1.html)
|
||||
[#]: subject: (4 cool terminal multiplexers)
|
||||
[#]: via: (https://fedoramagazine.org/4-cool-terminal-multiplexers/)
|
||||
[#]: author: (Paul W. Frields https://fedoramagazine.org/author/pfrields/)
|
||||
|
||||
4 款很酷的终端复用器
|
||||
======
|
||||
|
||||
![][1]
|
||||
|
||||
Fedora 系统对很多用户来说都很舒适。它有一个令人惊叹的桌面,可以轻松地完成日常任务。而在这光鲜的表面之下是由 Linux 系统提供的支持,而终端是高级用户使用这些底层能力的最简单方法。默认的终端简单且功能有限。但是,*终端复用器*能让你的终端变得非常强大。本文展示了一些流行的终端多路复用器以及如何安装它们。
|
||||
|
||||
为什么要用它?嗯,首先,它可以让你注销你的系统,而同时*让你的终端会话不受干扰*。退出你的控制台,这样安全,在其他地方旅行时通过远程登录 SSH 继续之前的操作是非常有用的。这里有一些工具可以看下。
|
||||
|
||||
最古老和最知名的终端多路复用器之一是 `screen`。但是,由于其代码不再维护,本文将重点介绍最近的应用。 (“最近的”是相对而言的,其中一些已存在多年!)
|
||||
|
||||
### Tmux
|
||||
|
||||
`tmux` 是 `screen` 最广泛使用的替代品之一。它有高度可配置的接口。你可以根据需要对 `tmux` 进行编程以启动特定类型的会话。在前面发表的这篇文章中你会发现更多关于 tmux 的信息:
|
||||
|
||||
- [使用 tmux 实现更强大的终端][2]
|
||||
|
||||
已经是 `tmux` 用户?你可能会喜欢[这篇使你的 tmux 会话更有效的文章][3]。
|
||||
|
||||
要安装 `tmux`,由于你可能已经在终端中,请带上 `sudo` 使用 `dnf`:
|
||||
|
||||
```
|
||||
$ sudo dnf install tmux
|
||||
```
|
||||
|
||||
要开始学习,请运行 `tmux` 命令。单窗格窗口以你的默认 shell 启动。tmux 使用*修饰键*来表示接下来会发出命令。默认情况下,此键为 `Ctrl+B`。如果输入 `Ctrl+B, C`,你将创建一个带有 shell 的新窗口。
|
||||
|
||||
提示:使用 `Ctrl+B, ?` 进入帮助模式,会列出你可以使用的所有键。为了简单起见,你先查看 `bind-key -T prefix` 开头的行。这些是你可以在修饰键之后立即使用的键,可以用来配置你的 `tmux` 会话。你可以按 `Ctrl+C` 退出帮助模式回 `tmux`。
|
||||
|
||||
要完全退出 `tmux`,请使用标准 `exit` 命令或 `Ctrl+D` 退出所有 shell。
|
||||
|
||||
### Dvtm
|
||||
|
||||
你可能最近在 Fedroa Magzine 上看到过一篇 [dwm,一个动态窗口管理器][4]的文章。像 `dwm` 一样,`dvtm` 用于平铺窗口管理,但是是用在终端中。它的设计坚持 UNIX 的“做好一件事”的理念,在这里是管理终端中的窗口。
|
||||
|
||||
安装 `dvtm` 也很简单。但是,如果你想要前面提到的注销功能,你还需要 `abduco` 包来处理 dvtm 的会话管理。
|
||||
|
||||
```
|
||||
$ sudo dnf install dvtm abduco
|
||||
```
|
||||
|
||||
`dvtm` 已经映射了许多管理终端窗口的按键。默认情况下,它使用 `Ctrl+G` 作为其修饰键。这个按键告诉 `dvtm` 接下来的字符将成为它应该处理的命令。例如, `Ctrl+G, C` 创建一个新窗口,`Ctrl+G, X` 将其关闭。
|
||||
|
||||
有关使用 `dvtm` 的更多信息,请查看 `dvtm` 的[主页][5],其中包含大量提示和入门信息。
|
||||
|
||||
### Byobu
|
||||
|
||||
虽然 `byobu` 本身并不是真正的多路复用器 —— 它封装了 `tmux` 甚至更老的 `screen` 来添加功能,但它也值得在这里一提。通过帮助菜单和窗口选项卡,以便更加容易地找到那些功能,`byobu` 使终端复用器更适合初学者。
|
||||
|
||||
当然它也可以在 Fedora 仓库中找到。要安装它,请使用以下命令:
|
||||
|
||||
```
|
||||
$ sudo dnf install byobu
|
||||
```
|
||||
|
||||
默认情况下,`byobu` 会在内部运行 `screen`,因此你可能希望运行 `byobu-tmux` 来封装 `tmux`。你可以使用 `F9` 键打开帮助菜单以获取更多信息,来帮助你入门。
|
||||
|
||||
### Mtm
|
||||
|
||||
`mtm` 是你可以找到的最小的复用器之一。事实上,它只有大约 1000 行代码!如果你处于受限的环境(例如旧硬件、最小容器等)中,你可能会发现它很有用。要开始使用,你需要安装一些包。
|
||||
|
||||
```
|
||||
$ sudo dnf install git ncurses-devel make gcc
|
||||
```
|
||||
|
||||
然后克隆 `mtm` 所在的仓库:
|
||||
|
||||
```
|
||||
$ git clone https://github.com/deadpixi/mtm.git
|
||||
```
|
||||
|
||||
进入 `mtm` 文件夹并构建程序:
|
||||
|
||||
```
|
||||
$ make
|
||||
```
|
||||
|
||||
你可能会收到一些警告,但完成后,你将会有一个非常小的 `mtm` 程序。使用以下命令运行它:
|
||||
|
||||
```
|
||||
$ ./mtm
|
||||
```
|
||||
|
||||
你可以在 [GitHub 页面][6]上找到该程序的所有文档。
|
||||
|
||||
这里只是一些终端复用器。你有想推荐的么?请在下面留下你的评论,享受在终端中创建窗口吧!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/4-cool-terminal-multiplexers/
|
||||
|
||||
作者:[Paul W. Frields][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fedoramagazine.org/author/pfrields/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://fedoramagazine.org/wp-content/uploads/2018/08/tmuxers-4-816x345.jpg
|
||||
[2]: https://fedoramagazine.org/use-tmux-more-powerful-terminal/
|
||||
[3]: https://fedoramagazine.org/4-tips-better-tmux-sessions/
|
||||
[4]: https://fedoramagazine.org/lets-try-dwm-dynamic-window-manger/
|
||||
[5]: http://www.brain-dump.org/projects/dvtm/#why
|
||||
[6]: https://github.com/deadpixi/mtm
|
||||
[7]: https://unsplash.com/photos/48yI_ZyzuLo?utm_source=unsplash&utm_medium=referral&utm_content=creditCopyText
|
||||
[8]: https://unsplash.com/search/photos/windows?utm_source=unsplash&utm_medium=referral&utm_content=creditCopyText
|
||||
@ -1,8 +1,8 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11042-1.html)
|
||||
[#]: subject: (Use Firefox Send with ffsend in Fedora)
|
||||
[#]: via: (https://fedoramagazine.org/use-firefox-send-with-ffsend-in-fedora/)
|
||||
[#]: author: (Sylvia Sánchez https://fedoramagazine.org/author/lailah/)
|
||||
@ -12,19 +12,19 @@
|
||||
|
||||
![][1]
|
||||
|
||||
_ffsend_ 是 Firefox Send 的命令行客户端。本文将展示 Firefox Send 和 _ffsend_ 如何工作。还会详细介绍如何在 Fedora 中安装和使用它。
|
||||
`ffsend` 是 Firefox Send 的命令行客户端。本文将展示 Firefox Send 和 `ffsend` 如何工作。还会详细介绍如何在 Fedora 中安装和使用它。
|
||||
|
||||
### 什么是 Firefox Send 和 ffsend?
|
||||
|
||||
Firefox Send 是 Mozilla 的一个文件共享工具,它能将加密文件发送给其他用户。你可以在自己的服务器上安装 Send,也可以使用 Mozilla 托管的链接 [send.firefox.com][2]。它最大支持 1GB 的文件,链接会在可配置的下载次数(默认值为 1)或 24 小时后过期,然后会删除发送服务器上的所有文件。此工具仍_处于实验阶段_,因此不应在生产中使用或共享重要或敏感数据。
|
||||
Firefox Send 是 Mozilla 的一个文件共享工具,它能将加密文件发送给其他用户。你可以在自己的服务器上安装 Send,也可以使用 Mozilla 托管的链接 [send.firefox.com][2]。它最大支持 1GB 的文件,链接会在可配置的下载次数(默认值为 1)或 24 小时后过期,然后会删除发送服务器上的所有文件。此工具仍*处于实验阶段*,因此不应在生产中使用或共享重要或敏感数据。
|
||||
|
||||
虽然 Firefox Send 本身就是工具,并且可以在 Web 中使用,但 _ffsend_ 是一个可以与脚本和参数一起使用的命令行程序。它有多种配置选项,并且可以在后台工作而无需任何人为干预。
|
||||
虽然 Firefox Send 本身就是工具,并且可以在 Web 中使用,但 `ffsend` 是一个可以与脚本和参数一起使用的命令行程序。它有多种配置选项,并且可以在后台工作而无需任何人为干预。
|
||||
|
||||
### 它如何工作?
|
||||
|
||||
ffsend 可以上传和下载文件。远程主机可以使用 Firefox 工具或其他 Web 浏览器来下载文件。 Firefox Send 和 _ffsend_ 都不需要使用 Firefox。
|
||||
`ffsend` 可以上传和下载文件。远程主机可以使用 Firefox 工具或其他 Web 浏览器来下载文件。 Firefox Send 和 `ffsend` 都不需要使用 Firefox。
|
||||
|
||||
值得一提 _ffsend_ 使用了客户端加密。这意味着文件在上传_前_被加密。链接中就有密钥,因此在共享时要小心,因为任何有链接的人都可以下载该文件。作为额外的保护,你可以使用以下参数使用密码保护文件:
|
||||
值得一提 `ffsend` 使用了客户端加密。这意味着文件在上传*前*被加密。链接中就有密钥,因此在共享时要小心,因为任何有链接的人都可以下载该文件。作为额外的保护,你可以使用以下参数使用密码保护文件:
|
||||
|
||||
```
|
||||
ffsend password URL -p PASSWORD
|
||||
@ -34,24 +34,22 @@ ffsend password URL -p PASSWORD
|
||||
|
||||
还有一些值得一提的其他功能:
|
||||
|
||||
* 链接到期前可配置的下载限制,范围从 1 到 20 次之间
|
||||
* 内置解压和归档功能
|
||||
* 跟踪共享文件的历史记录
|
||||
* 检查或删除共享文件
|
||||
* 文件夹也可以按原样共享,也可以作为压缩文件共享
|
||||
* 生成 QR 码,便于在手机上下载
|
||||
|
||||
|
||||
* 链接到期前可配置的下载限制,范围从 1 到 20 次之间
|
||||
* 内置解压和归档功能
|
||||
* 跟踪共享文件的历史记录
|
||||
* 检查或删除共享文件
|
||||
* 文件夹也可以按原样共享,也可以作为压缩文件共享
|
||||
* 生成 QR 码,便于在手机上下载
|
||||
|
||||
### 如何在 Fedora 中安装
|
||||
|
||||
虽然 Fedora Send 可以在 Firefox 中使用而无需安装其他,但你需要安装 CLI 工具才能使用 _ffsend_。此工具在官方仓库中,因此你只需使用 _dnf_ 命令,并使用 _[sudo][3]_。
|
||||
虽然 Fedora Send 可以在 Firefox 中使用而无需安装其他,但你需要安装 CLI 工具才能使用 `ffsend`。此工具在官方仓库中,因此你只需使用 `dnf` 命令,并使用 [sudo][3]。
|
||||
|
||||
```
|
||||
$ sudo dnf install ffsend
|
||||
```
|
||||
|
||||
之后,你可以在终端使用 _ffsend_。
|
||||
之后,你可以在终端使用 `ffsend`。
|
||||
|
||||
|
||||
### 上传文件
|
||||
@ -66,7 +64,7 @@ Share link: https://send.firefox.com/download/05826227d70b9a4b/#RM_HSBq6kuyeBem
|
||||
|
||||
现在可以使用 “Share link” URL 轻松共享该文件。
|
||||
|
||||
## 下载文件
|
||||
### 下载文件
|
||||
|
||||
下载文件和上传一样简单。
|
||||
|
||||
@ -75,7 +73,7 @@ $ ffsend download https://send.firefox.com/download/05826227d70b9a4b/#RM_HSBq6ku
|
||||
Download complete
|
||||
```
|
||||
|
||||
在下载之前,检查文件是否存在并获取有关它的信息会有用。 _ffsend_ 为此提供了 2 个方便的命令。
|
||||
在下载之前,检查文件是否存在并获取有关它的信息会有用。`ffsend` 为此提供了 2 个方便的命令。
|
||||
|
||||
```
|
||||
$ ffsend exists https://send.firefox.com/download/88a6324e2a99ebb6/#YRJDh8ZDQsnZL2KZIA-PaQ
|
||||
@ -87,9 +85,9 @@ Downloads: 0 of 1
|
||||
Expiry: 23h59m (86388s
|
||||
```
|
||||
|
||||
## 上传历史
|
||||
### 上传历史
|
||||
|
||||
_ffsend_ 还提供了一种查看使用工具上传的历史记录的方法。例如,如果你用脚本上传了大量文件并且想要跟踪每个文件的下载状态,那么这非常有用。
|
||||
`ffsend` 还提供了一种查看使用工具上传的历史记录的方法。例如,如果你用脚本上传了大量文件并且想要跟踪每个文件的下载状态,那么这非常有用。
|
||||
|
||||
```
|
||||
$ ffsend history
|
||||
@ -98,7 +96,7 @@ LINK EXPIRY
|
||||
2 https://send.firefox.com/download/KZIA-PaQ 23h54m
|
||||
```
|
||||
|
||||
## 删除文件
|
||||
### 删除文件
|
||||
|
||||
另一个有用的功能是删除文件。
|
||||
|
||||
@ -106,7 +104,7 @@ LINK EXPIRY
|
||||
ffsend delete https://send.firefox.com/download/2d9faa7f34bb1478/#phITKvaYBjCGSRI8TJ9QNw
|
||||
```
|
||||
|
||||
Firefox Send 是一项很棒的服务,_ffsend_ 使得它在终端使用起来非常方便。[Gitlab 仓库[4]中有关于 _ffsend_ 的的更多示例和文档。
|
||||
Firefox Send 是一项很棒的服务,`ffsend` 使得它在终端使用起来非常方便。[Gitlab 仓库][4]中有关于 `ffsend` 的更多示例和文档。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -115,7 +113,7 @@ via: https://fedoramagazine.org/use-firefox-send-with-ffsend-in-fedora/
|
||||
作者:[Sylvia Sánchez][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,99 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (hopefully2333)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11035-1.html)
|
||||
[#]: subject: (Cisco to buy IoT security, management firm Sentryo)
|
||||
[#]: via: (https://www.networkworld.com/article/3400847/cisco-to-buy-iot-security-management-firm-sentryo.html)
|
||||
[#]: author: (Michael Cooney https://www.networkworld.com/author/Michael-Cooney/)
|
||||
|
||||
思科收购了物联网安全管理公司 Sentryo
|
||||
======
|
||||
> 买下 Sentryo 将给思科在工业物联网的异常和实时威胁检测两方面予以支持。
|
||||
|
||||
![IDG Worldwide][1]
|
||||
|
||||
为了扩展自己的物联网安全管理产品,思科计划收购 Sentryo,这是一家总部位于法国的公司,Sentryo 为工业物联网提供异常检测和实时威胁检测。
|
||||
|
||||
Sentryo 成立于 2014 年,产品包括 ICS CyberVision(一种用于资产库存、网络监控和威胁情报的平台)以及 CyberVision 网络边界传感器,这用于分析网络流量。
|
||||
|
||||
**更多关于物联网的信息:**
|
||||
|
||||
* [什么是物联网?物联网如何运行?][4]
|
||||
* [什么是边缘计算,这会如何改变我们的网络?][5]
|
||||
* [最强的物联网公司][6]
|
||||
* [10 个值得关注的热门物联网创业公司][7]
|
||||
* [在物联网领域赚钱的六种方法][8]
|
||||
* [什么是数字双胞胎技术? [以及它为什么重要]][9]
|
||||
* [区块链,以服务为中心的网络是物联网成功的关键][10]
|
||||
* [物联网以网络和安全作为基础][11]
|
||||
* [构建完整的物联网网络必须优先完成][12]
|
||||
* [什么是工业物联网?[为什么风险如此之高]][13]
|
||||
|
||||
“我们通过思科的 IOx 应用框架将 Sentryo 的边缘传感器和我们的工业网络硬件相结合”,思科企业发展和思科投资的副总裁 Rob Salvagno 在一篇关于计划收购的博客中写道。
|
||||
|
||||
“我们相信连接是物联网项目的基础,通过释放网络的力量,我们可以大大提高运作的效率并发现新的商业机会。随着 Sentryo 的加入,思科可以为系统控制工程师提供更加深入的资产可见度,以此来对系统进行优化,检测异常并保护他们的网络。”
|
||||
|
||||
Gartner 对 Sentryo 的系统写道:“ICS CyberVision 产品以其所有 OT 用户都能理解的方式提供对其客户 OT 网络的可视性,而不仅仅是 IT 技术人员。随着黑客和监管机构越来越关注工业控制系统,一个组织的 OT 拥有完整的可见性是至关重要的一件事。很多的 OT 网络不仅在地理上位置分散,而且也很复杂,由成千上万的组件组成。”
|
||||
|
||||
Frost & Sullivan 的工业分析师 Nandini Natarajan 表示,Sentryo 的 ICS CyberVision 让企业能够确保其工业运作的连续性、动态弹性和安全性,并以此预防可能的网络攻击。“它将使用标签形式的独特的 ‘通用 OT 语言’ 来自动描述资产和通信流程,以纯文本的方式描述每个资产在做什么。ICS CyberVision 可以让任何人都能立刻查看一台设备的类别和行为;它利用人工智能算法提供很多不同的分析视图,来让用户深入了解到一个典型的工业控制系统可以产生多么庞大的数据。Sentryo 可以轻松查看重要或相关的信息。”
|
||||
|
||||
Natarajan 表示,除此之外,Sentryo 的平台使用深度数据包检测(DPI)从工业设备之间的通信数据包里提取信息。DPI 引擎通过边缘计算架构进行部署,它可以运行在 Sentryo 传感器设备上,也可以在已经安装好的网络设备上运行。因此,Sentryo 可以将可见性和网络安全特性嵌入进工业网络中,而非部署带外监控网络。
|
||||
|
||||
Sentryo 的技术将扩大思科在物联网上的总体计划。在今年一月,思科推出了一整套的交换机、软件、开发工具和蓝图,这些东西将用于把物联网、基于意图联网的工业网络、传统信息安全、传统信息监控、应用开发支持融为一体。
|
||||
|
||||
这个新平台可以通过思科的 DNA 中心进行管理,让客户能将他们的物联网、工业网络控制和他们的商业 IT 世界融为一体。
|
||||
|
||||
DNA 中心是思科用于企业网络的中央管理工具,具有自动化、确保设置、结构配置、基于策略进行分割的功能。它也是该公司 IBN 计划的核心,用于主动向客户提供动态自动化实施网络和策略变更的能力,并在这个过程中确保数据的交付。IoT Field Network Director 是管理思科工业、连接网格路由器和终端的多服务网络的软件。
|
||||
|
||||
思科物联网业务部的高级副总裁兼总经理 Liz Centoni 表示,公司希望 Sentryo 的技术能以多种方式帮助物联网客户:
|
||||
|
||||
支持网络的被动 DPI 功能,这用于发现 IOT 和 OT 设备,并且在设备和系统之间建立起通信模式。Sentryo 的传感器可以在思科的 IOx 框架里进行本地部署,并且可以内置到这些设备运行的工业网络中,而不是添加额外的硬件。
|
||||
|
||||
随着设备识别和通信模式的建立,思科将把 DNA 中心和身份识别服务引擎(ISE)集成到一起,以便客户能够很轻松地定义分割策略。这种集成将使 OT 团队能够利用 IT 安全团队的专业知识来保护他们的环境,而不会对运营的流程造成风险。
|
||||
|
||||
由于这些物联网设备缺乏现代嵌入式软件和安全功能,网络分段将成为允许运作设备向合法系统进行通信的关键技术,并降低像我们看见的 WannaCry 和 Norsk Hydro 那样网络安全事件的风险。
|
||||
|
||||
据 Crunchbase 称,Sentryo 的每年预计收入为 350 万美元,与 Cymmetria、Team8 和 Indegy 的竞争最为激烈。此次收购预期将在思科 2020 财年的第一季度 - 2019 年 10 月 26 日 - 结束前完成。思科并未详细披露此次收购的财务细节。
|
||||
|
||||
Sentryo 是思科今年的第二次收购。思科在今年一月收购了 Singularity 公司的网络分析技术。在 2018 年,思科收购了包含 Duo security software 在内的 6 家公司。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3400847/cisco-to-buy-iot-security-management-firm-sentryo.html
|
||||
|
||||
作者:[Michael Cooney][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[hopefully2333](https://github.com/hopefully2333)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Michael-Cooney/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://images.idgesg.net/images/article/2018/09/nwan_019_iiot-100771131-large.jpg
|
||||
[2]: https://www.sentryo.net/
|
||||
[3]: https://www.networkworld.com/article/3243928/what-is-the-industrial-iot-and-why-the-stakes-are-so-high.html
|
||||
[4]: https://www.networkworld.com/article/3207535/internet-of-things/what-is-the-iot-how-the-internet-of-things-works.html
|
||||
[5]: https://www.networkworld.com/article/3224893/internet-of-things/what-is-edge-computing-and-how-it-s-changing-the-network.html
|
||||
[6]: https://www.networkworld.com/article/2287045/internet-of-things/wireless-153629-10-most-powerful-internet-of-things-companies.html
|
||||
[7]: https://www.networkworld.com/article/3270961/internet-of-things/10-hot-iot-startups-to-watch.html
|
||||
[8]: https://www.networkworld.com/article/3279346/internet-of-things/the-6-ways-to-make-money-in-iot.html
|
||||
[9]: https://www.networkworld.com/article/3280225/internet-of-things/what-is-digital-twin-technology-and-why-it-matters.html
|
||||
[10]: https://www.networkworld.com/article/3276313/internet-of-things/blockchain-service-centric-networking-key-to-iot-success.html
|
||||
[11]: https://www.networkworld.com/article/3269736/internet-of-things/getting-grounded-in-iot-networking-and-security.html
|
||||
[12]: https://www.networkworld.com/article/3276304/internet-of-things/building-iot-ready-networks-must-become-a-priority.html
|
||||
[13]: https://www.networkworld.com/article/3243928/internet-of-things/what-is-the-industrial-iot-and-why-the-stakes-are-so-high.html
|
||||
[14]: https://blogs.cisco.com/news/cisco-industrial-iot-news
|
||||
[15]: https://www.globenewswire.com/news-release/2018/06/28/1531119/0/en/Sentryo-Named-a-Cool-Vendor-by-Gartner.html
|
||||
[16]: https://www.linkedin.com/pulse/industrial-internet-things-iiot-decoded-nandini-natarajan/
|
||||
[17]: https://pluralsight.pxf.io/c/321564/424552/7490?u=https%3A%2F%2Fwww.pluralsight.com%2Fpaths%2Fcertified-information-systems-security-professional-cisspr
|
||||
[18]: https://www.cisco.com/c/dam/en_us/solutions/iot/ihs-report.pdf
|
||||
[19]: https://www.networkworld.com/article/3336454/cisco-goes-after-industrial-iot.html
|
||||
[20]: https://www.networkworld.com/article/3202699/what-is-intent-based-networking.html
|
||||
[21]: https://blogs.cisco.com/news/securing-the-internet-of-things-cisco-announces-intent-to-acquire-sentryo
|
||||
[22]: https://blogs.cisco.com/security/talos/wannacry
|
||||
[23]: https://www.securityweek.com/norsk-hydro-may-have-lost-40m-first-week-after-cyberattack
|
||||
[24]: https://www.crunchbase.com/organization/sentryo#section-web-traffic-by-similarweb
|
||||
[25]: https://www.facebook.com/NetworkWorld/
|
||||
[26]: https://www.linkedin.com/company/network-world
|
||||
@ -1,22 +1,24 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11036-1.html)
|
||||
[#]: subject: (Kubernetes basics: Learn how to drive first)
|
||||
[#]: via: (https://opensource.com/article/19/6/kubernetes-basics)
|
||||
[#]: author: (Scott McCarty https://opensource.com/users/fatherlinux/users/fatherlinux/users/fatherlinux)
|
||||
|
||||
Kubernetes 基础:首先学习如何使用
|
||||
======
|
||||
放弃专注于新项目,专注于获取你的 Kubernetes 翻斗车商业驾驶执照。
|
||||
|
||||
> 不要被新项目分心,而是专注于取得你的 Kubernetes 翻斗车驾驶执照。
|
||||
|
||||
![Truck steering wheel and dash][1]
|
||||
|
||||
在本系列的前两篇文章中,我解释了为何 Kubernetes [像翻斗车][2]并且要理解优雅、专业的工具,如 [Kubernetes][4](和翻斗车,起重机等)总是有[学习曲线][3]的。本文是下一步:学习如何驾驶。
|
||||
在本系列的前两篇文章中,我解释了为何 Kubernetes [像翻斗车][2],并且想要理解像 [Kubernetes][4](和翻斗车,起重机等)这样优雅、专业工具总是有[学习曲线][3]的。本文是下一步:学习如何驾驶。
|
||||
|
||||
最近,我在 Reddit 上看到了一个关于[重要的 Kubernetes 项目][5]的帖子。人们似乎很想知道他们应该学习如何开始使用 Kubernetes。“驾驶翻斗车的类比”有助于确保问题保持正轨。帖子中的某个人提到你不应该运行自己的镜像仓库,除非你必须这样做,所以人们开始逐渐接受驱动 Kubernetes 而不是构建它。
|
||||
最近,我在 Reddit 上看到了一个关于[重要的 Kubernetes 项目][5]的帖子。人们似乎很想知道他们应该学习如何开始使用 Kubernetes。“驾驶翻斗车的类比”有助于确保这个问题回到轨道上去。在这个帖子中的某个人提到,除非必要,你不应该运行自己的镜像仓库,所以人们开始逐渐接受驾驭 Kubernetes 而不是构建它的想法。
|
||||
|
||||
API 是 Kubernetes 的引擎和变速器。像翻斗车的方向盘、离合器、汽油和制动踏板一样,用于构建应用程序的 YAML 或 JSON 文件是机器的主要接口。当你第一次学习 Kubernetes 时,这应该是你的主要关注点。了解你的控制部件。不要被所有最新和最大的项目所左右。当你刚学会开车时,不要尝试驾驶实验性的翻斗车。相反,专注于基础知识。
|
||||
API 是 Kubernetes 的引擎和变速器。像翻斗车的方向盘、离合器、汽油和制动踏板一样,用于构建应用程序的 YAML 或 JSON 文件是机器的主要接口。当你第一次学习 Kubernetes 时,这应该是你的主要关注点。了解你的控制部件。不要分心于最新和最大的那些项目。当你刚学会开车时,不要尝试驾驶实验性的翻斗车。相反,请专注于基础知识。
|
||||
|
||||
### 定义状态和实际状态
|
||||
|
||||
@ -26,25 +28,25 @@ API 是 Kubernetes 的引擎和变速器。像翻斗车的方向盘、离合器
|
||||
|
||||
人类(开发人员/系统管理员/运维人员)使用他们提交给 Kubernetes API 的 YAML/JSON 文件指定定义的状态。然后,Kubernetes 使用控制器来分析 YAML/JSON 中定义的新状态与集群中的实际状态之间的差异。
|
||||
|
||||
在上面的例子中,Replication Controller 可以看到用户指定的三个 pod 之间的差异,其中一个 pod 正在运行,并调度另外两个 Pod。如果你要登录 Kubernetes 并手动杀死其中一个 Pod,它会不断启动另一个来替换它。在实际状态与定义的状态匹配之前,Kubernetes 不会停止。这是非常强大的。
|
||||
在上面的例子中,Replication Controller 可以看到用户指定的三个 pod 之间的差异,其中一个 pod 正在运行,并调度另外两个 Pod。如果你登录 Kubernetes 并手动杀死其中一个 Pod,它会不断启动另一个来替换它。在实际状态与定义的状态匹配之前,Kubernetes 不会停止。这是非常强大的。
|
||||
|
||||
### **原语**
|
||||
### 原语
|
||||
|
||||
接下来,你需要了解可以在 Kubernetes 中指定的原语。
|
||||
|
||||
![Kubernetes primitives][7]
|
||||
|
||||
它不仅仅有 Pods,还有部署 (Deployments)、持久化卷声明 (Persistent Volume Claims)、服务 (Services),路由 (routes) 等。使用支持 Kubernetes 的平台 [OpenShift][8],你可以添加构建和 BuildConfigs。你大概需要一天左右的时间来了解这些原语。之后,当你的情况变得更加复杂时,你可以深入了解。
|
||||
这些原语不仅仅有 Pod,还有<ruby>部署<rt>Deployment</rt></ruby>、<ruby>持久化卷声明<rt>Persistent Volume Claim</rt></ruby>、<ruby>服务<rt>Service</rt></ruby>,<ruby>路由<rt>route</rt></ruby>等。使用支持 Kubernetes 的平台 [OpenShift][8],你可以添加<ruby>构建<rt>build</rt></ruby>和 BuildConfig。你大概需要一天左右的时间来了解这些原语。你可以在你的用例变得更加复杂时再深入了解。
|
||||
|
||||
### 将开发者映射到传统 IT 环境
|
||||
### 将原生开发者映射到传统 IT 环境
|
||||
|
||||
最后,考虑这该如何映射到你在传统 IT 环境中的操作。
|
||||
|
||||
![Mapping developer-native to traditional IT environments][9]
|
||||
|
||||
尽管是一个技术问题,但用户一直在尝试解决业务问题。从历史上看,我们使用诸如 playbook 之类的东西将业务逻辑与单一语言的 IT 系统绑定起来。对于运维人员来说,这很不错,但是当你尝试将其扩展到开发人员时,它会变得更加繁琐。
|
||||
尽管是一个技术问题,但用户一直在尝试解决业务问题。从历史上看,我们使用诸如<ruby>剧本<rt>playbook</rt></ruby>之类的东西将业务逻辑与单一语言的 IT 系统绑定起来。对于运维人员来说,这很不错,但是当你尝试将其扩展到开发人员时,它会变得更加繁琐。
|
||||
|
||||
直到 Kubernete 出现之前,我们从未能够以开发者的方式真正同时指定一组 IT 系统应如何表现和交互。如果你考虑一下,我们正在使用在 Kubernetes 中编写的 YAML/JSON 文件以非常便携和声明的方式扩展了管理存储、网络和计算资源的能力,但它们总会映射到某处的“真实”资源。我们不必以开发者身份担心它。
|
||||
直到 Kubernete 出现之前,我们从未能够以原生开发者的方式真正同时指定一组 IT 系统应如何表现和交互。如果你考虑一下,我们正在使用在 Kubernetes 中编写的 YAML/JSON 文件以非常便携和声明的方式扩展了管理存储、网络和计算资源的能力,但它们总会映射到某处的“真实”资源。我们不必以开发者身份担心它。
|
||||
|
||||
因此,快放弃关注 Kubernetes 生态系统中的新项目,而是专注开始使用它。在下一篇文章中,我将分享一些可以帮助你使用 Kubernetes 的工具和工作流程。
|
||||
|
||||
@ -55,15 +57,15 @@ via: https://opensource.com/article/19/6/kubernetes-basics
|
||||
作者:[Scott McCarty][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/fatherlinux/users/fatherlinux/users/fatherlinux
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/truck_steering_wheel_drive_car_kubernetes.jpg?itok=0TOzve80 (Truck steering wheel and dash)
|
||||
[2]: https://opensource.com/article/19/6/kubernetes-dump-truck
|
||||
[3]: https://opensource.com/article/19/6/kubernetes-learning-curve
|
||||
[2]: https://linux.cn/article-11011-1.html
|
||||
[3]: https://linux.cn/article-11026-1.html
|
||||
[4]: https://opensource.com/resources/what-is-kubernetes
|
||||
[5]: https://www.reddit.com/r/kubernetes/comments/bsoixc/what_are_the_essential_kubernetes_related/
|
||||
[6]: https://opensource.com/sites/default/files/uploads/defined_state_-_actual_state.png (Defined state and actual state)
|
||||
93
published/201906/20190624 Raspberry Pi 4 is here.md
Normal file
93
published/201906/20190624 Raspberry Pi 4 is here.md
Normal file
@ -0,0 +1,93 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wahailin)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11034-1.html)
|
||||
[#]: subject: (Raspberry Pi 4 is here!)
|
||||
[#]: via: (https://opensource.com/article/19/6/raspberry-pi-4)
|
||||
[#]: author: (Ben Nuttall https://opensource.com/users/bennuttall)
|
||||
|
||||
树莓派 4 来袭!
|
||||
======
|
||||
|
||||
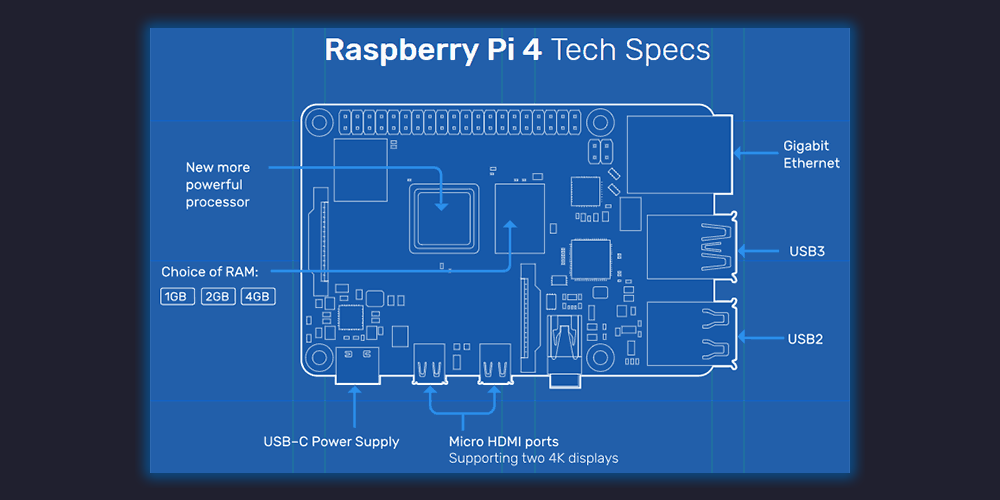
|
||||
|
||||
> 售价 35 美元起的新一代树莓派单板计算机,装载了 1.5 GHz 的 Arm 芯片,并支持双 HDMI 4K 显示,全吞吐量千兆以太网,以及更多新特性。
|
||||
|
||||
![Raspberry Pi 4 board][1]
|
||||
|
||||
树莓派的最新版本树莓派 4 代,已于近日(北京时间 6 月 24 日)发布,这早于此前预期。树莓派 4 装载了 1.5 GHz 的 Arm 芯片和 VideoCore GPU,支持双 4K 显示输出,并引入了 USB 3 接口和全吞吐量千兆以太网,以及最高可达 4G 的多个可选 RAM 配置。
|
||||
|
||||
![Raspberry Pi 4 case][2]
|
||||
|
||||
树莓派 4 是非常强大的单板计算机,其起始售价依然是 35 美元。起始版的 RAM 配置为 1G,2G RAM 配置的树莓派售价为 45 美元,顶配 4G RAM 的树莓派售价为 55 美元,采用这种差异化定价对树莓派尚属首次。
|
||||
|
||||
树莓派 4 的详细配置如下:
|
||||
|
||||
* 1.5 GHz 4 核心 64 位博通 BCM2711 A72 CPU
|
||||
* VideoCore VI GPU
|
||||
* 千兆以太网端口
|
||||
* 1GB/2GB/4GB LPDDR4 SDRAM 内存
|
||||
* 双 Micro-HDMI 接口
|
||||
* 两个 USB 3 接口
|
||||
* 两个 USB 2 接口
|
||||
* 双频(2.4 GHz 和 5 GHz)无线网络
|
||||
* 蓝牙 5.0
|
||||
* USB Type C 电源接口
|
||||
* CSI 摄像头接口
|
||||
* DSI 显示接口
|
||||
* MicroSD 卡槽
|
||||
* PoE(以太网供电)供电针
|
||||
* 完全兼容早期的树莓派产品
|
||||
|
||||
### USB 接口和网络
|
||||
|
||||
树莓派 4 板载了更高速率的 USB 3 接口;它通过 Type C 接口供电,并提供两个 USB 3 接口和两个 USB 2 接口。USB 3 接口可以为连接的硬盘和其它外部设备提供更高的速率。
|
||||
|
||||
![Raspberry Pi 4 USBs][3]
|
||||
|
||||
基于 BCM2835 的树莓派 1 到 3 代的芯片只有一个本地 USB 接口,并且没有以太网接口,因而需要使用板子的 USB 集线器给出更多的 USB 接口和以太网接口。树莓派 3B+ 增加了一个专用的局域网(LAN)芯片,装载了千兆以太网,但它受到 USB 2 速率的限制。树莓派 4 板载了专门的千兆以太网,并且由于它不再受到 USB 速率的限制,网络速度要快得多。
|
||||
|
||||
树莓派 4 采用了 3B+ 中已有的技术 —— 该技术使得树莓派 3B+ 成为了第一个带有双频无线网络的单板计算机,即可以同时连接 2.4 GHz 和 5 GHz 频率的网络。
|
||||
|
||||
### 显示
|
||||
|
||||
设计第一代树莓派时,其 CPU 和 GPU 性能的平衡大大偏向于 GPU。VideoCore IV 是一个非常强大的图形处理器,支持全高清 1080p 多媒体的处理,这就是为什么树莓派一直作为家庭媒体中心而广受欢迎的原因。树莓派 2 代在某种程度上进行了权衡修改,并将 CPU 的性能进行提升,将树莓派从单核发展成四核 ARM 芯片。而树莓派 4 代将 CPU 和 GPU 的性能都进行了大幅提升。新的 VideoCore VI GPU 支持 4K 视频,并允许通过板子上的两个 Micro HDMI 端口(板子特意保持了和旧有型号相同的尺寸)进行双显示输出,这里要用一个适配器或 Micro HDMI 转 full HDMI 的转换线连接到 HDMI 屏幕。
|
||||
|
||||
当你需要同时浏览多个窗口时,需要用到更多的物理显示屏,双显示的好处在此时就得到了绝佳体现。如果你正在编程,你可能会在其中一个屏幕上编写代码,构建网站或应用,而在另一个屏幕上查看数据库、Web 浏览器、电子邮件或其他内容。这是树莓派首次可以不必将开发局限在一台显示器上,从而可以让你在需要时,在不同的屏幕上构建具有不同内容的基于树莓派的项目。
|
||||
|
||||
该树莓派还有一个显示器串行接口(DSI),用于驱动另一个特殊的显示-这里并非指另一个监视器本身,而是通过一根挠性电缆连接的官方树莓派触摸屏显示器。
|
||||
|
||||
### Raspbian Buster
|
||||
|
||||
树莓派 4 发布后,紧接着更新了基于 Debian 的系统 Raspbian Buster,而新的树莓派对 OpenGL ES 3 的支持,使我们在 Raspbian Buster 上为树莓派 4 开发任意软件成为可能。Buster 对界面进行了一些调整,并对很多软件进行了升级,其中包括 Python3.7。
|
||||
|
||||
![Raspbian Buster][4]
|
||||
|
||||
### 开源图形驱动程序
|
||||
|
||||
在过去的五年中,Eric Anholt 一直致力于为树莓派编写开源图形驱动程序。现在,Raspbian 可以使用这个驱动程序加速树莓派上的 Web 浏览、桌面图形和 3D 应用,这取代了以前需要的大量闭源代码。非常感谢 Eric 和博通的贡献。
|
||||
|
||||
按之前预计,树莓派 4 将于明年完成,但由于芯片设计比预期更早投入生产,树莓派 4 因而可以提早到现在发布。
|
||||
|
||||
* * *
|
||||
|
||||
树莓派 4 已经开始发售,你会选择哪个型号呢?在评论中说出你的想法吧。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/6/raspberry-pi-4
|
||||
|
||||
作者:[Ben Nuttall][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wahailin](https://github.com/wahailin)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/bennuttall
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/raspberry-pi-4_lead.jpg?itok=2bkk43om (Raspberry Pi 4 board)
|
||||
[2]: https://opensource.com/sites/default/files/uploads/raspberry-pi-4-case.jpg (Raspberry Pi 4 case)
|
||||
[3]: https://opensource.com/sites/default/files/uploads/raspberry-pi-4-usb.jpg (Raspberry Pi 4 USBs)
|
||||
[4]: https://opensource.com/sites/default/files/uploads/raspbian-buster.png (Raspbian Buster)
|
||||
@ -1,8 +1,8 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11031-1.html)
|
||||
[#]: subject: (Using i3 with multiple monitors)
|
||||
[#]: via: (https://fedoramagazine.org/using-i3-with-multiple-monitors/)
|
||||
[#]: author: (Adam Šamalík https://fedoramagazine.org/author/asamalik/)
|
||||
@ -12,13 +12,13 @@
|
||||
|
||||
![][1]
|
||||
|
||||
你在 Linux 工作站上使用多个显示器吗?一次看到很多东西可能是有益的。但在我们的工作中通常有比实际显示器更多的窗口 - 这是一件好事,因为一次看到太多东西可能会分散注意力。因此能够切换我们在单个显示器上看到的内容似乎很重要。
|
||||
你在 Linux 工作站上使用多个显示器吗?一次看到很多东西可能是有益的。但在我们的工作中通常有比实际显示器更多的窗口 —— 这是一件好事,因为一次看到太多东西可能会分散注意力。因此能够切换我们在单个显示器上看到的内容似乎很重要。
|
||||
|
||||
让我们来谈谈 i3,它是一个流行的平铺窗口管理器,可以与多个显示器配合使用。并且有许多其他窗口管理器没有的便利功能,它能够独立地在各个显示器上切换工作区。
|
||||
让我们来看看 i3,它是一个流行的平铺窗口管理器,可以与多个显示器配合使用。并且有许多其他窗口管理器没有的便利功能,它能够独立地在各个显示器上切换工作区。
|
||||
|
||||
### 快速介绍 i3
|
||||
|
||||
大约三年前,[Fedora Magazine 已经写了一篇关于 i3 的文章][2]。这是有史以来最受欢迎的文章之一!虽然情况并非总是如此,但 i3 非常稳定,而且这篇文章如今也很准确。所以,这次不会重复太多,本篇只涵盖了让 i3 启动和运行,如果你是 i3 的新手,想要了解更多基础知识的话,欢迎你继续阅读。
|
||||
大约三年前,[Fedora Magazine 已经写了一篇关于 i3 的文章][2]。这是有史以来最受欢迎的文章之一!虽然情况并非总是如此,但 i3 非常稳定,而且那篇文章如今也很准确。所以,这次不会重复太多内容,本篇只涵盖了让 i3 启动和运行的极少内容,如果你是 i3 的新手,想要了解更多基础知识的话,欢迎你继续阅读。
|
||||
|
||||
要在系统上安装 i3,请运行以下命令:
|
||||
|
||||
@ -28,7 +28,7 @@ $ sudo dnf install i3
|
||||
|
||||
完成后,注销,然后在登录屏幕上选择 i3 作为窗口管理器,然后重新登录。
|
||||
|
||||
当你第一次运行 i3 时,系统会询问你是否要继续进行自动配置 - 在此处回答是。之后,你将被要求选择 “mod 键”。如果你在这里不确定,只需接受默认值,即将 Windows/Super 键设置为 mod 键。你将主要使用此键用于窗口管理器中的快捷方式。
|
||||
当你第一次运行 i3 时,系统会询问你是否要继续进行自动配置 —— 在此处回答是。之后,你将被要求选择 “mod 键”。如果你不确定,只需接受默认值,即将 Windows/Super 键设置为 mod 键。你将主要使用此键用于窗口管理器中的快捷方式。
|
||||
|
||||
此时,你应该在底部看到一个小条和一个空白屏幕。我们来看看一些基本的快捷方式。
|
||||
|
||||
@ -72,7 +72,7 @@ $mod + shift + q
|
||||
|
||||
还有更多的快捷方式,但这些足够让你开始使用 i3。
|
||||
|
||||
要退出 i3(退出登录)按:
|
||||
要退出 i3(并退出登录)按:
|
||||
|
||||
```
|
||||
$mod + shift + e
|
||||
@ -84,9 +84,9 @@ $mod + shift + e
|
||||
|
||||
现在我们已经启动并运行了 i3,让我们把所有这些屏幕都用到!
|
||||
|
||||
为此,我们需要使用命令行,因为 i3 非常轻量级,并且没有 gui 来管理其他屏幕。如果这听起来很难也不用担心,它实际上非常简单!
|
||||
为此,我们需要使用命令行,因为 i3 非常轻量级,并且没有 GUI 来管理其他屏幕。如果这听起来很难也不用担心,它实际上非常简单!
|
||||
|
||||
我们将使用的命令称为 xrandr。如果你的系统上没有 xrandr,请运行以下命令安装:
|
||||
我们将使用的命令称为 `xrandr`。如果你的系统上没有 `xrandr`,请运行以下命令安装:
|
||||
|
||||
```
|
||||
$ sudo dnf install xrandr
|
||||
@ -98,7 +98,7 @@ $ sudo dnf install xrandr
|
||||
$ xrandr
|
||||
```
|
||||
|
||||
输出列出了所有可用输出,并通过显示支持的分辨率指示哪些输出连接了屏幕(通过电缆连接的显示器)。好消息是,我们不需要关心使它们工作的分辨率。
|
||||
输出列出了所有可用输出设备,并通过显示支持的分辨率指示哪些输出连接了屏幕(通过电缆连接的显示器)。好消息是,我们不需要关心使它们工作的分辨率。
|
||||
|
||||
这个例子显示了笔记本电脑的主屏幕(名为 eDP1),以及连接到 HDMI-2 输出的第二个显示器,它位于笔记本电脑的右侧。要打开它,请运行以下命令:
|
||||
|
||||
@ -108,7 +108,7 @@ $ xrandr --output HDMI-2 --auto --right-of eDP1
|
||||
|
||||
就是这样!你的屏幕现已激活。
|
||||
|
||||
![Second screen active. The commands shown on this screenshot are slightly different than in the article, as they set a smaller resolution to make the screenshots more readable.][3]
|
||||
![第二个屏幕激活。截屏上显示命令与文章中略有不同,它设置了更小的分辨率以使截屏适合阅读][3]
|
||||
|
||||
### 在多个屏幕上管理工作区
|
||||
|
||||
@ -122,11 +122,11 @@ $mod + NUMBER
|
||||
|
||||
你可以独立切换各个显示器上的工作区!
|
||||
|
||||
![Workspace 2 on the left screen, workspace 4 on the right screen.][4]
|
||||
![工作空间 2 在左侧屏幕,工作空间 4 在右侧屏幕][4]
|
||||
|
||||
![Left screen switched to workspace 3, right screen still showing workspace 4.][5]
|
||||
![左侧屏幕切换为工作空间 3,右侧屏幕仍为工作空间 4][5]
|
||||
|
||||
![Right screen switched to workspace 4, left screen still showing workspace 3.][6]
|
||||
![右侧屏幕切换为工作空间 5,左侧屏幕仍为空间空间 3][6]
|
||||
|
||||
### 在显示器之间移动工作区
|
||||
|
||||
@ -138,7 +138,7 @@ $mod + shift + NUMBER
|
||||
|
||||
我们也可以将工作区移动到不同的屏幕。但是,此操作没有默认快捷方式,因此我们必须先创建它。
|
||||
|
||||
要创建自定义快捷方式,你需要在你选择的文本编辑器中打开配置文件(本文使用 _vim_):
|
||||
要创建自定义快捷方式,你需要在你选择的文本编辑器中打开配置文件(本文使用 `vim`):
|
||||
|
||||
```
|
||||
$ vim ~/.config/i3/config
|
||||
@ -163,9 +163,9 @@ $mod + shift + r
|
||||
$mod + p
|
||||
```
|
||||
|
||||
![Workspace 2 with Firefox on the left screen][7]
|
||||
![打开火狐浏览器的工作空间 2 在左侧][7]
|
||||
|
||||
![Workspace 2 with Firefox moved to the second screen][8]
|
||||
![打开火狐浏览器的工作空间 2 移动到第二个屏幕][8]
|
||||
|
||||
就是这些了!享受你的新多显示器体验,并了解更多 i3,欢迎阅读 Fedora Magazine 上之前关于 i3 的文章,或者查看官方 i3 文档。
|
||||
|
||||
@ -176,7 +176,7 @@ via: https://fedoramagazine.org/using-i3-with-multiple-monitors/
|
||||
作者:[Adam Šamalík][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,97 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wxy)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11033-1.html)
|
||||
[#]: subject: (FreeDOS turns 25 years old: An origin story)
|
||||
[#]: via: (https://opensource.com/article/19/6/freedos-anniversary)
|
||||
[#]: author: (Jim Hall https://opensource.com/users/jim-hall)
|
||||
|
||||
25 岁的 FreeDOS:起源故事
|
||||
======
|
||||
|
||||
> 操作系统的历史是开发人员共同造物的开源软件模型的很好例子。
|
||||
|
||||

|
||||
|
||||
6 月 29 日是 [FreeDOS][2] 25 周年的日子。不管对于哪个开源软件项目来说,这都是一个重要的里程碑,我为过去这 1/4 个世纪来我们在这方面所做的工作感到自豪。我也为我们如何构建 FreeDOS 感到自豪,因为它是开源软件模型如何工作的一个很好的例子。
|
||||
|
||||
在它的那个时代,MS-DOS 是一个功能强大的操作系统。自从我的父母用新的 IBM 机器取代了老化的 Apple II 计算机以来,我已经使用 DOS 多年了。MS-DOS 提供了一个灵活的命令行,我非常喜欢它,它可以方便地操作我的文件。多年来,我学会了如何在 C 中编写自己的实用程序,以进一步扩展其命令行功能。
|
||||
|
||||
大约在 1994 年,微软宣布其下一代的 Windows 将取消 MS-DOS。但我喜欢 DOS,即使我已经开始迁移到 Linux,我仍然会启动到 MS-DOS 来运行一些 Linux 尚未拥有的应用程序。
|
||||
|
||||
我想,如果我们想留下 DOS,我们需要自己编写一个。FreeDOS 就是这样诞生的。
|
||||
|
||||
1994 年 6 月 29 日,我向 Usenet 上的 comp.os.msdos.apps 新闻组发表了关于我的想法的一个小小公告:
|
||||
|
||||
> PD-DOS 项目公告:
|
||||
>
|
||||
> 几个月前,我发布了有关启动公共域(PD)版本 DOS 的文章。当时对此的普遍支持很强烈,很多人都赞同:“开始编写吧!”所以,我…
|
||||
>
|
||||
> 宣布开发 PD-DOS 的首次尝试。我写了一个“清单”来描述这样的一个项目的目标和工作大纲,以及一个“任务列表”,它准确地显示了需要编码开发的内容。我会在这里发布,然后讨论。
|
||||
>
|
||||
|
||||
虽然我宣布该项目为 PD-DOS(“公共领域”的意思,缩写是为了模仿 IBM 的“PC-DOS”),但我们很快将名称改为 Free-DOS,再后来又改为 FreeDOS。
|
||||
|
||||
我马上开始开发它。首先,我分享了我编写的用于扩展 DOS 命令行功能的实用程序。它们中的许多程序都重现了 MS-DOS 功能,包括 `CLS`、`DATE`、`DEL`、`FIND`、`HELP` 和 `MORE`。有些是我从 Unix 借来的新功能,比如 `TEE` 和 `TRCH`(Unix 的 `tr` 的简单实现)。我贡献了十几个 FreeDOS 工具。
|
||||
|
||||
通过分享我的实用程序,我给了其他开发人员一个起点。通过在 [GNU 通用公共许可证][3](GNU GPL)下共享我的源代码,我隐含地允许其他人添加新功能并修复错误。
|
||||
|
||||
看到 FreeDOS 开始成型的其他开发人员联系了我并希望提供帮助。Tim Norman 是第一个人,Tim 自愿编写命令行 shell(`COMMAND.COM`,后来命名为 `FreeCOM`)。其他人贡献了复制或扩展了 DOS 命令行的实用程序。
|
||||
|
||||
我们尽快发布了第一个 alpha 版本。在宣布了 FreeDOS 后不到三个月,我们就有了一个集合了我们所编写的功能的 Alpha 1 发行版。当我们发布 Alpha 5 时,FreeDOS 已经拥有了 60 多个实用程序。FreeDOS 包含了 MS-DOS 中从未想过的功能,包括通过 PPP 拨号驱动程序实现的互联网连接,以及使用主 VGA 监视器和辅助单色监视器的双显示器支持。
|
||||
|
||||
新的开发人员加入了该项目,我们很欢迎他们。到 1998 年 10 月,感谢 Pat Villani,FreeDOS 有了一个可以工作的内核。FreeDOS 还提供了许多新功能,不仅带来了与 MS-DOS 的同等性,而且超越了 MS-DOS,包括 ANSI 支持和类似 Unix lpr 的打印后台处理程序。
|
||||
|
||||
你可能熟悉其他的里程碑版本。我们继续向 1.0 版本迈进,终于在 2006 年 9 月发布了 FreeDOS 1.0,在 2012 年 1 月发布了 FreeDOS 1.1,在 2016 年 12 月发布了 FreeDOS 1.2。而 MS-DOS 很久以前就停止了开发,因此我们在 1.0 发布之后不需要经常更新了。
|
||||
|
||||
如今,FreeDOS 已经是一个非常现代的 DOS。我们已经超越了“经典 DOS”,现在 FreeDOS 拥有许多开发工具,如编译器、汇编器和调试器。除了普通的 DOS Edit 编辑器之外,我们还有许多编辑器,包括 Fed、Pico、TDE 以及 Emacs 和 Vi 的一个版本。FreeDOS 支持网络,甚至还提供简单的图形 Web 浏览器(Dillo)。我们有大量的新工具,包括许多可以让 Linux 用户感到熟悉的实用工具。
|
||||
|
||||
正因为开发人员的共同创造,FreeDOS 才走到如今。本着开源软件的精神,我们通过修复错误和添加新功能为彼此的工作做出了贡献。我们将用户视为共同开发者;我们总能找到方法来吸引贡献者,无论是编写代码还是编写文档。我们基于优点达成共识。如果这听起来很熟悉,那是因为这些是开源软件的核心价值:透明度、协作、尽早发布、经常发布、精英管理和社区。这就是[开源方式][4]!
|
||||
|
||||
我鼓励你下载 FreeDOS 1.2 并尝试一下。
|
||||
|
||||
### 更多资源
|
||||
|
||||
* [FreeDOS 官方网站][2]
|
||||
* [FreeDOS wiki][5]
|
||||
* [下载 FreeDOS 1.2][6]
|
||||
* [FreeDOS 的免费电子书][7]
|
||||
* [FreeDOS 的简单介绍][8]
|
||||
* [FreeDOS 起源与革命][9]
|
||||
* [4 个 FreeDOS 的有趣事实][10]
|
||||
* [如何使用 FreeDOS 升级你的系统 BIOS][11]
|
||||
* [庆祝 FreeDOS 24 岁生日:有用的命令速查表][12]
|
||||
* [如何在 Linux 中运行 DOS 程序][13]
|
||||
* [让 DOS 活到现在并通过开源来起步][14]
|
||||
* [在树莓派上运行 DOS][15]
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/6/freedos-anniversary
|
||||
|
||||
作者:[Jim Hall][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wxy](https://github.com/wxy)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/jim-hall
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/freedos-fish-laptop-color.png?itok=vfv_Lpph (FreeDOS fish logo and command prompt on computer)
|
||||
[2]: https://www.freedos.org/
|
||||
[3]: https://www.gnu.org/licenses/licenses.en.html
|
||||
[4]: https://opensource.com/open-source-way
|
||||
[5]: http://wiki.freedos.org/
|
||||
[6]: https://www.freedos.org/download/
|
||||
[7]: https://www.freedos.org/ebook/
|
||||
[8]:https://linux.cn/article-9983-1.html
|
||||
[9]: https://opensource.com/article/17/10/freedos
|
||||
[10]: https://opensource.com/article/17/6/freedos-still-cool-today
|
||||
[11]: https://opensource.com/article/17/6/upgrade-bios-freedos
|
||||
[12]: https://opensource.com/article/18/6/freedos-commands-cheat-sheet
|
||||
[13]: https://linux.cn/article-9014-1.html
|
||||
[14]: https://opensource.com/life/16/9/interview-jim-hall-freedos
|
||||
[15]: https://linux.cn/article-9544-1.html
|
||||
@ -1,34 +1,30 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (robsean)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11051-1.html)
|
||||
[#]: subject: (5 Easy Ways To Free Up Space (Remove Unwanted or Junk Files) on Ubuntu)
|
||||
[#]: via: (https://www.2daygeek.com/linux-remove-delete-unwanted-junk-files-free-up-space-ubuntu-mint-debian/)
|
||||
[#]: author: (Magesh Maruthamuthu https://www.2daygeek.com/author/magesh/)
|
||||
|
||||
5种简单的方法来在 Ubuntu 上释放空间(移除不想要的或没有用的文件)
|
||||
5 种在 Ubuntu 上释放空间的简单方法
|
||||
======
|
||||
|
||||
我们中的大多数人可能在系统磁盘存储不足的情况下执行这个操作。
|
||||
|
||||
|
||||
我们中的大多数人可能在 Linux 系统磁盘存储不足的情况下执行这个操作。
|
||||
大多数人可能在系统磁盘存储不足的情况下执行释放空间这个操作,也可能在 Linux 系统磁盘存储满了的情况下执行这个操作。
|
||||
|
||||
它应该被经常执行,来为安装一个新的应用程序和处理其它文件弥补磁盘存储空间。
|
||||
|
||||
内务处理是 Linux 管理员的一个日常任务,管理员允许内务处理在阈值下维持磁盘利用率。
|
||||
它应该被经常执行,来为安装一个新的应用程序和处理其它文件弥补磁盘存储空间。保持可用空间是 Linux 管理员的一个日常任务,以允许磁盘利用率维持在阈值之下。
|
||||
|
||||
这里有一些我们可以清理我们系统空间的方法。
|
||||
|
||||
当你有 TB 级存储容量时,不需要清理你的系统。
|
||||
|
||||
但是,如果你空间有限,那么释放磁盘空间,变的不可避免。
|
||||
当你有 TB 级存储容量时,可能不需要清理你的系统。但是,如果你空间有限,那么释放磁盘空间就变的不可避免。
|
||||
|
||||
在这篇文章中,我将向你展示一些最容易的或简单的方法来清理你的 Ubuntu 系统,获得更多空间。
|
||||
|
||||
### 在 Ubuntu 系统上如何检查可用的空间?
|
||||
|
||||
在你的系统上使用 **[df 命令][1]** 来检查当前磁盘利用率。
|
||||
在你的系统上使用 [df 命令][1] 来检查当前磁盘利用率。
|
||||
|
||||
```
|
||||
$ df -h
|
||||
@ -42,17 +38,12 @@ tmpfs 997M 0 997M 0% /sys/fs/cgroup
|
||||
```
|
||||
|
||||
图形界面用户可以使用“磁盘利用率分析器工具”来查看当前利用率。
|
||||
[![][2]![][2]][3]
|
||||
|
||||
### 1) 移除不再需要的软件包
|
||||
![][3]
|
||||
|
||||
下面的命令移除系统不再需要依赖的库和软件包。
|
||||
#### 1) 移除不再需要的软件包
|
||||
|
||||
这些软件包自动地安装来使一个被安装软件包满足的依赖关系。
|
||||
|
||||
同样,它移除安装在系统中的旧的 Linux 内核。
|
||||
|
||||
它移除不再被系统需要的孤立的软件包,但是不清除它们。
|
||||
下面的命令移除系统不再需要的依赖库和软件包。这些软件包是自动安装的,以使一个安装的软件包满足依赖关系。同样,它也会移除安装在系统中的 Linux 旧内核。它会移除不再被系统需要的孤儿软件包,但是不会清除它们。
|
||||
|
||||
```
|
||||
$ sudo apt-get autoremove
|
||||
@ -71,7 +62,7 @@ After this operation, 189 MB disk space will be freed.
|
||||
Do you want to continue? [Y/n]
|
||||
```
|
||||
|
||||
为清除它们,与命令一起使用 `--purge` 选项。
|
||||
为清除它们,可以与命令一起使用 `--purge` 选项。
|
||||
|
||||
```
|
||||
$ sudo apt-get autoremove --purge
|
||||
@ -90,26 +81,21 @@ After this operation, 189 MB disk space will be freed.
|
||||
Do you want to continue? [Y/n]
|
||||
```
|
||||
|
||||
### 2) 清空回收站
|
||||
#### 2) 清空回收站
|
||||
|
||||
这可能有风险,你可能有大量的无用数据存在于你的回收站中。
|
||||
|
||||
它占用你的系统空间。这是最好的一个方法来在你的系统上清理这些无用的数据,并获取一些可用的空间。
|
||||
有可能你的回收站里面有大量的无用数据。它会占用你的系统空间。最好解决方法之一是在你的系统上清理这些无用的数据,以获取一些可用的空间。
|
||||
|
||||
为清理这些,简单地使用文件管理器来清空你的回收站。
|
||||
[![][2]![][2]][4]
|
||||
|
||||
### 3) 清理 APT 缓存文件
|
||||
![][4]
|
||||
|
||||
Ubuntu 使用 **[APT 命令][5]** (高级软件包工具)用于软件包管理,像:安装,移除,搜索等等。
|
||||
#### 3) 清理 APT 缓存文件
|
||||
|
||||
默认情况下,每个 Linux 操作系统在它们各自的命令保留下载和安装的软件包的缓冲。
|
||||
Ubuntu 使用 [APT 命令][5](高级软件包工具)用于软件包管理,如:安装、移除、搜索等等。
|
||||
|
||||
Ubuntu 也做相同的事,它以缓冲的形式在你的磁盘上保留它下载和安装的每次更新。
|
||||
一般 Linux 操作系统会在各自的目录下保留下载和安装的软件包的缓冲文件。
|
||||
|
||||
Ubuntu 在 /var/cache/apt/archives 目录中保留 DEB 软件包的缓冲文件。
|
||||
|
||||
随着时间推移,这些缓存可能快速增长,并在你的系统上占有很多空间。
|
||||
Ubuntu 也一样,它在你的磁盘上以缓冲的形式保留它下载和安装的每次更新。Ubuntu 在 `/var/cache/apt/archives` 目录中保留 DEB 软件包的缓冲文件。随着时间推移,这些缓存可能快速增长,并在你的系统上占有很多空间。
|
||||
|
||||
运行下面的命令来检查当前 APT 缓存文件的使用率。
|
||||
|
||||
@ -118,30 +104,29 @@ $ sudo du -sh /var/cache/apt
|
||||
147M /var/cache/apt
|
||||
```
|
||||
|
||||
它清理过时的 deb 软件包。我想说,一点都清理不干净。
|
||||
下面的命令会清理过时的 deb 软件包。我想说,一点都清理不干净。
|
||||
|
||||
```
|
||||
$ sudo apt-get autoclean
|
||||
```
|
||||
|
||||
它移除所有在 apt 缓存中的软件包。
|
||||
下面的命令会移除所有在 apt 缓存中的软件包。
|
||||
|
||||
```
|
||||
$ sudo apt-get clean
|
||||
```
|
||||
|
||||
### 4) 卸载不使用的应用程序
|
||||
#### 4) 卸载不使用的应用程序
|
||||
|
||||
我可能要求你来检查在你的系统上安装的软件包和游戏,,删除它们,如果你很少使用。
|
||||
这需要你来检查在你的系统上安装的软件包和游戏,删除它们,如果你很少使用的话。
|
||||
|
||||
这可以简单地完成,通过 “Ubuntu 软件中心”。
|
||||
[![][2]![][2]][6]
|
||||
这可以通过 “Ubuntu 软件中心” 简单地做到。
|
||||
|
||||
### 5) 清理缩略图缓存
|
||||
![][6]
|
||||
|
||||
缓存文件夹是程序存储它们可能再次需要的数据的地方,它是为速度保留的,而不是必需保留的。它可以被再次生成或再次下载。
|
||||
#### 5) 清理缩略图缓存
|
||||
|
||||
假如它真的填满你的硬盘,那么你可以删除一些东西而不用担心。
|
||||
缓存文件夹是程序存储它们可能再次需要的数据的地方,它是为速度保留的,而不是必需保留的。它可以被再次生成或再次下载。假如它真的填满了你的硬盘,那么你可以删除一些东西而不用担心。
|
||||
|
||||
运行下面的命令来检查当前 APT 缓存的利用率。
|
||||
|
||||
@ -163,7 +148,7 @@ via: https://www.2daygeek.com/linux-remove-delete-unwanted-junk-files-free-up-sp
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[robsean](https://github.com/robsean)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,75 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (geekpi)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11050-1.html)
|
||||
[#]: subject: (BitTorrent Client Deluge 2.0 Released: Here’s What’s New)
|
||||
[#]: via: (https://itsfoss.com/deluge-2-release/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
BitTorrent 客户端 Deluge 2.0 发布:新功能介绍
|
||||
======
|
||||
|
||||
你可能已经知道 [Deluge][1] 是[最适合 Linux 用户的 Torrent 客户端][2]之一。然而,最近的稳定版本差不多是两年前的了。
|
||||
|
||||
尽管它仍在积极开发中,但直到最近才出了一个主要的稳定版本。我们写这篇文章时,最新版本恰好是 2.0.2。所以,如果你还没有下载最新的稳定版本,请尝试一下。
|
||||
|
||||
不管如何,如果你感兴趣的话,让我们看看有哪些新的功能。
|
||||
|
||||
### Deluge 2.0 的主要改进
|
||||
|
||||
新版本引入了多用户支持,这是一个非常需要的功能。除此之外,还有一些性能改进可以更快地加载更多的种子。
|
||||
|
||||
此外,在 2.0 版本中,Deluge 使用了 Python 3,对 Python 2.7 提供最低支持。即使是用户界面,他们也从 GTK UI 迁移到了 GTK3。
|
||||
|
||||
根据发行说明,还有一些更重要的补充/改进,包括:
|
||||
|
||||
* 多用户支持。
|
||||
* 性能提升,可以更快地加载数千个种子。
|
||||
* 一个模拟 GTK/Web UI 的新控制台 UI。
|
||||
* GTK UI 迁移到 GTK3,并带有 UI 改进和补充。
|
||||
* 磁链预获取功能可以在添加种子时选择文件。
|
||||
* 完全支持 libtorrent 1.2。
|
||||
* 语言切换支持。
|
||||
* 改进了在 ReadTheDocs 托管的文档。
|
||||
* AutoAdd 插件取代了内置功能。
|
||||
|
||||
### 如何安装或升级到 Deluge 2.0
|
||||
|
||||
![][4]
|
||||
|
||||
对于任何 Linux 发行版,你都应该遵循官方[安装指南][5](使用 PPA 或 PyPi)。但是,如果你要升级,你应该留意发行说明中提到的:
|
||||
|
||||
> “_Deluge 2.0 与 Deluge 1.x 客户端或守护进程不兼容,因此这些也需要升级。如果第三方脚本直接连接到 Deluge 客户端,那么可能也不兼容且需要迁移。_”
|
||||
|
||||
因此,坚持在升级主版本之前备份你的[配置][6]以免数据丢失。而且,如果你是插件作者,那么需要升级它以使其与新版本兼容。
|
||||
|
||||
直接下载的安装包尚不包含 Windows 和 Mac OS。但是,说明中提到他们正在进行中。
|
||||
|
||||
除此之外,你可以按照更新后的官方文档中的[安装指南][5]来手动安装它们。
|
||||
|
||||
### 总结
|
||||
|
||||
你如何看待最新的稳定版本?你是否将 Deluge 用作 BitTorrent 客户端?或者你是否找到了其他更好的选择?
|
||||
|
||||
请在下面的评论栏告诉我们你的想法。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/deluge-2-release/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://dev.deluge-torrent.org/
|
||||
[2]: https://itsfoss.com/best-torrent-ubuntu/
|
||||
[3]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/06/deluge.jpg?fit=800%2C410&ssl=1
|
||||
[4]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/06/Deluge-2-release.png?resize=800%2C450&ssl=1
|
||||
[5]: https://deluge.readthedocs.io/en/latest/intro/01-install.html
|
||||
[6]: https://dev.deluge-torrent.org/wiki/Faq#WheredoesDelugestoreitssettingsconfig
|
||||
@ -1,43 +1,44 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (chen-ni)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11049-1.html)
|
||||
[#]: subject: (Leading in the Python community)
|
||||
[#]: via: (https://opensource.com/article/19/6/naomi-ceder-python-software-foundation)
|
||||
[#]: author: (Don Watkins https://opensource.com/users/don-watkins)
|
||||
|
||||
Python 社区的领袖
|
||||
领导 Python 社区
|
||||
======
|
||||
对话现任 Python 软件基金会董事会主席 Naomi Ceder
|
||||
|
||||
![Hands together around the word trust][1]
|
||||
> 对话现任 Python 软件基金会董事会主席 Naomi Ceder。
|
||||
|
||||

|
||||
|
||||
和开源软件世界的很多其他领袖一样,[Python 软件基金会][3](PSF)的董事会主席 [Naomi Ceder][2] 通过一种不同寻常的方式走进了 Python 世界。正如她在 2017 年 PyCon España 大会上的 [keynote][4] 的标题所说,她是因为这个编程语言而来,因为这个社区而留下的。在我们和她的一次近期的交流中,她分享了自己成为 Python 社区领袖的历程,并且就“是什么让 Python 如此特别”这个问题提供了一些独到的见解。
|
||||
|
||||
### 从授课到编程
|
||||
|
||||
Naomi 的职业生涯是从古典文学开始的。她取得了拉丁文和古希腊文的博士学位,并且辅修了印欧语言学。在一家私立学校教授拉丁语的同时,她开始接触了计算机,学习如何编程、如何拆机进行升级或者维修。1995 年,她开始在 [Yggdrasil Linux][5] 系统上开发开源软件,并且帮助建立了印第安纳州韦恩堡的 [Linux 用户小组][6]
|
||||
Naomi 的职业生涯是从古典文学开始的。她取得了拉丁文和古希腊文的博士学位,并且辅修了印欧语言学。在一家私立学校教授拉丁语的同时,她开始接触了计算机,学习如何编程、如何拆机进行升级或者维修。1995 年,她开始在 [Yggdrasil Linux][5] 系统上开发开源软件,并且帮助建立了印第安纳州韦恩堡的 [Linux 用户小组][6]。
|
||||
|
||||
作为一名教师,Naomi 相信在中学教授编程课程是非常重要的,因为等到大多数人上大学的时候,他们已经认为编程和科技相关的职业已经不是自己可以从事的了。她表示,更早地教授相关课程有助于增加科技人才的供给,提高人才的多元化和经验的广度,从而更好地满足行业需求。
|
||||
|
||||
大约在 2001 年前后,她决定从学习人类语言转向研究计算机语言,并同时教授计算机课程和管理学校的 IT 系统。在 2001 年的 Linux World 大会上听了一整天 PSF 主席 Guido Van Rossum 关于 Python 的演讲之后,她对 Python 的热情被点燃了。在那个时候,Python 还只是一门晦涩难懂的语言,但是她是如此喜欢 Python,以至于在她的学校开始使用 Python 记录学生信息、进行系统管理。
|
||||
大约在 2001 年前后,她决定从学习人类语言转向研究计算机语言,并同时教授计算机课程和管理学校的 IT 系统。在 2001 年的 Linux World 大会上听了一整天时任 PSF 主席 Guido Van Rossum (LCTT 译注:也是 Python 创始人)关于 Python 的演讲之后,她对 Python 的热情被点燃了。在那个时候,Python 还只是一门晦涩难懂的语言,但是她是如此喜欢 Python,以至于在她的学校开始使用 Python 记录学生信息、进行系统管理。
|
||||
|
||||
### 领导 Python 社区
|
||||
|
||||
Naomi 表示,“社区是 Python 成功背后的关键因素。开源软件的核心思想是分享,很少有人真的喜欢一个人坐在那儿盯着屏幕写代码。真正的满足来源于和别人交流想法,并且共同创造一些东西。”
|
||||
|
||||
她在第一届 [PyCon][7] 大会上发表了演讲,并且从此之后一直是一名参与者和领导者。她组织了一些 birds-of-a-feather 讨论会(LCTT 译注:一种在大会参与者之间进行的基于兴趣的小规模讨论活动)、PyCon 和 PyCon UK 大会的海报展示会、教育峰会,以及 PyCon 大会的西班牙语频道。
|
||||
她在第一届 [PyCon][7] 大会上发表了演讲,并且从此之后一直是一名参与者和领导者。她组织了一些 <ruby>趣味相投<rt>birds-of-a-feather<rt></ruby> 讨论会(LCTT 译注:birds-of-a-feather,一种在大会参与者之间进行的基于兴趣的非正式小规模讨论活动)、PyCon 和 PyCon UK 大会的海报展示会、教育峰会,以及 PyCon 大会的西班牙语频道。
|
||||
|
||||
她同时是 *[The Quick Python Book][9]* 一书的作者,并且联合创立了 [Trans\*Code][10],“英国唯一一个专注于变性者的问题和机遇的黑客节”(LCTT 译注:黑客节是一种让软件开发、设计、项目管理等相关人员相聚在一起,针对软件项目进行高强度合作的活动)。Naomi 表示,“随着科技能够提供越来越多的机遇,确保传统意义上的边缘化群体能够同等地享受到这些机遇成为了一件更为重要的事情。”
|
||||
她同时是 《[The Quick Python Book][9]》一书的作者,并且联合创立了 [Trans*Code][10],“英国唯一一个专注于变性者的问题和机遇的黑客节”(LCTT 译注:<ruby>黑客节<rt>hack event</rt></ruby>是一种让软件开发、设计、项目管理等相关人员相聚在一起,针对软件项目进行高强度合作的活动)。Naomi 表示,“随着科技能够提供越来越多的机遇,确保传统意义上的边缘化群体能够同等地享受到这些机遇成为了一件更为重要的事情。”
|
||||
|
||||
### 通过 PSF 进行贡献
|
||||
|
||||
作为 PSF 的董事会主席,Naomi 积极地参与着该组织对 Python 语言和其使用者的支持工作。除了赞助 PyCon 大会的举办之外,PSF 基金会还为世界各地的小型聚会、大型会议和研习会提供资助。2018 年,该组织发放的资助接近 335000 美元,其中大多数款项的金额都在 500 美元到 5000 美元之间。
|
||||
|
||||
PSF 的短期目标是成为一个由专业员工维护的可持续的、稳定的、成熟的非盈利机构。它的长期目标包括发展可以提供对 Python 开发工作有效支持的各种资源,以及扩展该组织对全世界范围内 Python 教育工作的支持。
|
||||
PSF 的短期目标是成为一个由专业人员维护的可持续的、稳定的、成熟的非盈利机构。它的长期目标包括发展可以提供对 Python 开发工作有效支持的各种资源,以及扩展该组织对全世界范围内 Python 教育工作的支持。
|
||||
|
||||
这些工作都需要来自社区的经济上的支持。Naomi 表示,PSF “最大的资金来源是 PyCon 大会。为了确保 PSF 的可持续性,我们同事也关注使用 Python 的企业的赞助,这是我们增长最快的部分。”会员价格是每年 99 美元,并且 [捐款和募捐人][12] 同样也在帮助维持该组织的工作。
|
||||
这些工作都需要来自社区的经济上的支持。Naomi 表示,PSF “最大的资金来源是 PyCon 大会。为了确保 PSF 的可持续性,我们同时也关注使用 Python 的企业的赞助,这是我们增长最快的部分。”会员费是每年 99 美元,并且 [捐款和募捐人][12] 同样也在帮助维持该组织的工作。
|
||||
|
||||
你可以在 PSF 的 [年度报告][13] 中了解该组织的更多工作情况。
|
||||
|
||||
@ -48,7 +49,7 @@ via: https://opensource.com/article/19/6/naomi-ceder-python-software-foundation
|
||||
作者:[Don Watkins][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[chen-ni](https://github.com/chen-ni)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,33 +1,29 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (heguagnzhi)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11043-1.html)
|
||||
[#]: subject: (Three Ways to Lock and Unlock User Account in Linux)
|
||||
[#]: via: (https://www.2daygeek.com/lock-unlock-disable-enable-user-account-linux/)
|
||||
[#]: author: (Magesh Maruthamuthu https://www.2daygeek.com/author/magesh/)
|
||||
|
||||
|
||||
在Linux中锁定和解锁用户帐户的三种方法
|
||||
在 Linux 中锁定和解锁用户帐户的三种方法
|
||||
======
|
||||
|
||||

|
||||
|
||||
如果密码策略已经在你的组织中实施了,你无需看这篇文章了。
|
||||
如果你已经在你的组织中实施了某种密码策略,你无需看这篇文章了。但是在这种情况下,如果你给账户设置了 24 小时的锁定期,你需要手动解锁用户帐户。
|
||||
|
||||
但是在这种情况下,如果你设置了24小时的锁定期,你需要手动解锁用户帐户。
|
||||
|
||||
本教程将帮助你在Linux中手动锁定和解锁用户帐户。
|
||||
本教程将帮助你在 Linux 中手动锁定和解锁用户帐户。
|
||||
|
||||
这可以通过三种方式使用以下两个 Linux 命令来完成。
|
||||
|
||||
* **`passwd:`** passwd 命令用于更新用户的身份验证令牌。这个任务是通过调用 Linux-PAM 和 Libuser API 来实现。
|
||||
|
||||
* **`usermod:`** usermod 命令用于修改/更新给定用户的帐户信息。它用于将用户添加到特定的组中,等等其他功能,
|
||||
|
||||
* `passwd`:用于更新用户的身份验证令牌。这个任务是通过调用 Linux PAM 和 libuser API 来实现。
|
||||
* `usermod`:用于修改/更新给定用户的帐户信息。它用于将用户添加到特定的组中等等功能。
|
||||
|
||||
为了说明这一点,我们选择 `daygeek` 用户帐户。让我们看看,怎么一步步来实现的。
|
||||
请注意,你必须使用你需要锁定或解锁的用户的帐户,而不是我们自己的帐户。
|
||||
您可以使用 `id Command` 检查给定的用户帐户在系统中是否可用。是的,我的帐户在系统中是可用的。
|
||||
|
||||
请注意,你必须使用你需要锁定或解锁的用户的帐户,而不是我们的帐户。你可以使用 `id` 命令检查给定的用户帐户在系统中是否可用。是的,我的这个帐户在我的系统中是可用的。
|
||||
|
||||
```
|
||||
# id daygeek
|
||||
@ -37,11 +33,9 @@ uid=2240(daygeek) gid=2243(daygeek) groups=2243(daygeek),2244(ladmin)
|
||||
|
||||
### 方法1: 如何使用 passwd 命令锁定、解锁和检查 Linux 中给定用户帐户的状态?
|
||||
|
||||
passwd 命令是 Linux 管理员经常使用的命令之一。
|
||||
`passwd` 命令是 Linux 管理员经常使用的命令之一。它用于更新 `/etc/shadow` 文件中用户的身份验证令牌。
|
||||
|
||||
它用于更新 `/etc/shadow` 文件中用户的身份验证令牌。
|
||||
|
||||
使用 `-l` 开关运行 passwd 命令,锁定给定的用户帐户。
|
||||
使用 `-l` 开关运行 `passwd` 命令,锁定给定的用户帐户。
|
||||
|
||||
```
|
||||
# passwd -l daygeek
|
||||
@ -50,22 +44,23 @@ Locking password for user daygeek.
|
||||
passwd: Success
|
||||
```
|
||||
|
||||
你可以通过 passwd 命令或从 /etc/shadow 文件中获取给定用户名来检查锁定的帐户状态。
|
||||
你可以通过 `passwd` 命令或从 `/etc/shadow` 文件中获取给定用户名来检查锁定的帐户状态。
|
||||
|
||||
使用 passwd 命令检查用户帐户锁定状态。
|
||||
使用 `passwd` 命令检查用户帐户锁定状态。
|
||||
|
||||
```
|
||||
# passwd -S daygeek
|
||||
or
|
||||
或
|
||||
# passwd --status daygeek
|
||||
|
||||
daygeek LK 2019-05-30 7 90 7 -1 (Password locked.)
|
||||
```
|
||||
将输出给定帐户密码状态的简短信息。
|
||||
|
||||
* **`LK:`**` ` 密码锁定
|
||||
* **`NP:`**` ` 没有密码
|
||||
* **`PS:`**` ` 密码设置
|
||||
这将输出给定帐户密码状态的简短信息。
|
||||
|
||||
* `LK`:密码被锁定
|
||||
* `NP`:没有设置密码
|
||||
* `PS`:密码已设置
|
||||
|
||||
使用 `/etc/shadow` 文件检查锁定的用户帐户状态。如果帐户已被锁定,密码前面将添加两个感叹号。
|
||||
|
||||
@ -74,7 +69,8 @@ daygeek LK 2019-05-30 7 90 7 -1 (Password locked.)
|
||||
|
||||
daygeek:!!$6$tGvVUhEY$PIkpI43HPaEoRrNJSRpM3H0YWOsqTqXCxtER6rak5PMaAoyQohrXNB0YoFCmAuh406n8XOvBBldvMy9trmIV00:18047:7:90:7:::
|
||||
```
|
||||
使用 `-u` 开关运行 passwd 命令,解锁给定的用户帐户。
|
||||
|
||||
使用 `-u` 开关运行 `passwd` 命令,可以解锁给定的用户帐户。
|
||||
|
||||
```
|
||||
# passwd -u daygeek
|
||||
@ -83,26 +79,25 @@ Unlocking password for user daygeek.
|
||||
passwd: Success
|
||||
```
|
||||
|
||||
### 方法2:如何使用 usermod 命令在 Linux 中锁定、解锁和检查给定用户帐户的状态?
|
||||
### 方法2:如何使用 usermod 命令在 Linux 中锁定、解锁和检查给定用户帐户的状态?
|
||||
|
||||
甚至,usermod 命令也经常被 Linux 管理员使用。
|
||||
`usermod` 命令也经常被 Linux 管理员使用。`usermod` 命令用于修改/更新给定用户的帐户信息。它用于将用户添加到特定的组中,等等。
|
||||
|
||||
usermod 命令用于修改/更新给定用户的帐户信息。它用于将用户添加到特定的组中,等等。,
|
||||
|
||||
使用 `-L` 开关运行 usermod 命令,锁定给定的用户帐户。
|
||||
使用 `-L` 开关运行 `usermod` 命令,锁定给定的用户帐户。
|
||||
|
||||
```
|
||||
# usermod --lock daygeek
|
||||
or
|
||||
或
|
||||
# usermod -L daygeek
|
||||
```
|
||||
|
||||
你可以通过 passwd 命令或从 /etc/shadow 文件中获取给定用户名来检查锁定的帐户状态。
|
||||
使用 passwd 命令检查用户帐户锁定状态。
|
||||
你可以通过 `passwd` 命令或从 `/etc/shadow` 文件中获取给定用户名来检查锁定的帐户状态。
|
||||
|
||||
使用 `passwd` 命令检查用户帐户锁定状态。
|
||||
|
||||
```
|
||||
# passwd -S daygeek
|
||||
or
|
||||
或
|
||||
# passwd --status daygeek
|
||||
|
||||
daygeek LK 2019-05-30 7 90 7 -1 (Password locked.)
|
||||
@ -110,11 +105,11 @@ daygeek LK 2019-05-30 7 90 7 -1 (Password locked.)
|
||||
|
||||
这将输出给定帐户密码状态的简短信息。
|
||||
|
||||
* **`LK:`**` ` Password locked
|
||||
* **`NP:`**` ` No password
|
||||
* **`PS:`**` ` Password set
|
||||
* `LK`:密码被锁定
|
||||
* `NP`:没有设置密码
|
||||
* `PS`:密码已设置
|
||||
|
||||
使用 /etc/shadow 文件检查锁定的用户帐户状态。如果帐户已被锁定,密码前面将添加两个感叹号。
|
||||
使用 `/etc/shadow` 文件检查锁定的用户帐户状态。如果帐户已被锁定,密码前面将添加两个感叹号。
|
||||
|
||||
```
|
||||
# grep daygeek /etc/shadow
|
||||
@ -122,29 +117,25 @@ daygeek LK 2019-05-30 7 90 7 -1 (Password locked.)
|
||||
daygeek:!!$6$tGvVUhEY$PIkpI43HPaEoRrNJSRpM3H0YWOsqTqXCxtER6rak5PMaAoyQohrXNB0YoFCmAuh406n8XOvBBldvMy9trmIV00:18047:7:90:7:::
|
||||
```
|
||||
|
||||
使用 `-U` 开关运行 usermod 命令以解锁给定的用户帐户。
|
||||
使用 `-U` 开关运行 `usermod` 命令以解锁给定的用户帐户。
|
||||
|
||||
```
|
||||
# usermod --unlock daygeek
|
||||
or
|
||||
或
|
||||
# usermod -U daygeek
|
||||
```
|
||||
|
||||
###方法-3:如何在 Linux 中使用 usermod 命令禁用、启用对给定用户帐户的 SSH 访问?
|
||||
### 方法-3:如何在 Linux 中使用 usermod 命令禁用、启用对给定用户帐户的 SSH 访问?
|
||||
|
||||
甚至,usermod 命令也是经常被 Linux 管理员使用的命令。
|
||||
`usermod` 命令也是经常被 Linux 管理员使用的命令。`usermod` 命令用于修改/更新给定用户的帐户信息。它用于将用户添加到特定的组中,等等。
|
||||
|
||||
usermod 命令用于修改/更新给定用户的帐户信息。它用于将用户添加到特定的组中,等等。,
|
||||
|
||||
|
||||
或者,这可以通过将 `nologin` shell 分配给给定用户来完成。为此,可以运行以下命令。
|
||||
替代的,锁定可以通过将 `nologin` shell 分配给给定用户来完成。为此,可以运行以下命令。
|
||||
|
||||
```
|
||||
# usermod -s /sbin/nologin daygeek
|
||||
```
|
||||
|
||||
You can check the locked user account details by greping the given user name from /etc/passwd file.
|
||||
你可以通过从 /etc/passwd 文件中给定用户名来检查锁定的用户帐户详细信息。
|
||||
你可以通过从 `/etc/passwd` 文件中给定用户名来检查锁定的用户帐户详细信息。
|
||||
|
||||
```
|
||||
# grep daygeek /etc/passwd
|
||||
@ -152,17 +143,15 @@ You can check the locked user account details by greping the given user name fro
|
||||
daygeek:x:2240:2243::/home/daygeek:/sbin/nologin
|
||||
```
|
||||
|
||||
我们可以通过分配回原来的 shell 来启用用户 ssh 访问。
|
||||
我们可以通过分配回原来的 shell 来启用用户的 ssh 访问。
|
||||
|
||||
```
|
||||
# usermod -s /bin/bash daygeek
|
||||
```
|
||||
|
||||
###如何使用 shell 脚本锁定、解锁和检查 Linux 中多个用户帐户的状态?
|
||||
|
||||
如果你想锁定/解锁多个帐户,那么你需要寻找脚本。
|
||||
|
||||
### 如何使用 shell 脚本锁定、解锁和检查 Linux 中多个用户帐户的状态?
|
||||
|
||||
如果你想锁定/解锁多个帐户,那么你需要找个脚本。
|
||||
|
||||
是的,我们可以编写一个小的 shell 脚本来执行这个操作。为此,请使用以下 shell 脚本。
|
||||
|
||||
@ -186,17 +175,17 @@ u5
|
||||
#!/bin/bash
|
||||
for user in `cat user-lists.txt`
|
||||
do
|
||||
passwd -l $user
|
||||
passwd -l $user
|
||||
done
|
||||
```
|
||||
|
||||
将`user-lock.sh` 文件设置为可执行权限 。
|
||||
将 `user-lock.sh` 文件设置为可执行权限。
|
||||
|
||||
```
|
||||
# chmod + user-lock.sh
|
||||
```
|
||||
|
||||
最后运行脚本来实现这一点。
|
||||
最后运行脚本来达成目标。
|
||||
|
||||
```
|
||||
# sh user-lock.sh
|
||||
@ -221,7 +210,7 @@ passwd: Success
|
||||
#!/bin/bash
|
||||
for user in `cat user-lists.txt`
|
||||
do
|
||||
passwd -S $user
|
||||
passwd -S $user
|
||||
done
|
||||
```
|
||||
|
||||
@ -231,7 +220,7 @@ done
|
||||
# chmod + user-lock-status.sh
|
||||
```
|
||||
|
||||
最后运行脚本来实现这一点。
|
||||
最后运行脚本来达成目标。
|
||||
|
||||
```
|
||||
# sh user-lock-status.sh
|
||||
@ -243,7 +232,6 @@ u4 LK 2019-06-10 0 99999 7 -1 (Password locked.)
|
||||
u5 LK 2019-06-10 0 99999 7 -1 (Password locked.)
|
||||
```
|
||||
|
||||
|
||||
使用下面的 shell 脚本来解锁多个用户。
|
||||
|
||||
```
|
||||
@ -252,17 +240,17 @@ u5 LK 2019-06-10 0 99999 7 -1 (Password locked.)
|
||||
#!/bin/bash
|
||||
for user in `cat user-lists.txt`
|
||||
do
|
||||
passwd -u $user
|
||||
passwd -u $user
|
||||
done
|
||||
```
|
||||
|
||||
设置 `user-unlock.sh` 可执行权限。
|
||||
设置 `user-unlock.sh` 可执行权限。
|
||||
|
||||
```
|
||||
# chmod + user-unlock.sh
|
||||
```
|
||||
|
||||
最后运行脚本来实现这一点。
|
||||
最后运行脚本来达成目标。
|
||||
|
||||
```
|
||||
# sh user-unlock.sh
|
||||
@ -279,7 +267,7 @@ Unlocking password for user u5.
|
||||
passwd: Success
|
||||
```
|
||||
|
||||
运行相同的 shell 脚本 `user-lock-status.sh` ,检查这些锁定的用户帐户在 Linux 中是否被解锁。
|
||||
运行相同的 shell 脚本 `user-lock-status.sh`,检查这些锁定的用户帐户在 Linux 中是否被解锁。
|
||||
|
||||
```
|
||||
# sh user-lock-status.sh
|
||||
@ -290,6 +278,7 @@ u3 PS 2019-06-10 0 99999 7 -1 (Password set, SHA512 crypt.)
|
||||
u4 PS 2019-06-10 0 99999 7 -1 (Password set, SHA512 crypt.)
|
||||
u5 PS 2019-06-10 0 99999 7 -1 (Password set, SHA512 crypt.)
|
||||
```
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/lock-unlock-disable-enable-user-account-linux/
|
||||
@ -297,7 +286,7 @@ via: https://www.2daygeek.com/lock-unlock-disable-enable-user-account-linux/
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[heguangzhi](https://github.com/heguangzhi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,102 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wahailin)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11039-1.html)
|
||||
[#]: subject: (With Upgraded Specs, Raspberry Pi 4 Takes Aim at Desktop Segment)
|
||||
[#]: via: (https://itsfoss.com/raspberry-pi-4/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
升级配置后,树莓派 4 瞄准了桌面市场
|
||||
======
|
||||
|
||||
> 树莓派 4 升级配置后开始发售,其 RAM 配置最高可达 4 GB,并支持双 4k 显示。最新硬件配置下,你可以轻松将其作为桌面使用。起售价格依然和旧有型号一样,为 35 美元。
|
||||
|
||||
树莓派基金会已经发布了最新版的[树莓派 4B][1] 单板计算机。
|
||||
|
||||
在升级了几个重要特性后,树莓派 4 成为了 40 美元以下的[单板计算机][2]市场中最强大的产品。
|
||||
|
||||
![Raspberry Pi 4][3]
|
||||
|
||||
### 树莓派 4 的新特性
|
||||
|
||||
树莓派 4 开始支持双 4k 显示器设置 —— 如果你对此有所需求的话。除此外,它还配备了更强大的处理器,其搭载的 RAM 最高可达 4 GB,这几乎可以媲美一个中端的便携电脑。
|
||||
|
||||
本次配置升级使树莓派可以参与[迷你 Linux 机][4]市场的竞争,而依旧 35 美元的起始售价使其比[其它单板计算机][2]更具优势。
|
||||
|
||||
树莓派 4 发布不久,各大主要的在线商店就几乎销售一空。那么,我们来看看它有哪些新卖点吧。
|
||||
|
||||
#### 树莓派 4 的核心配置
|
||||
|
||||
![Raspberry Pi 4 Tech Specs][5]
|
||||
|
||||
* 博通 BCM2711,1.5 GHz 64 位 4 核心 Cortex-A72(ARM v8)
|
||||
* 顶配 4 GB RAM(可选 RAM 配置为 1 GB,2 GB 和 4 GB)
|
||||
* 无线网络和蓝牙 5.0
|
||||
* 两个 USB 3.0 接口,两个 USB 2.0 接口
|
||||
* 40 针 GPIO 引脚(向前兼容)
|
||||
* 两个 Micro-HDMI 接口(支持 4k 显示)
|
||||
* USB-C(供电接口)
|
||||
* 千兆以太网
|
||||
|
||||
如果你想更深入的了解配置信息,可以参考树莓派网站的[官方技术规格][6]。
|
||||
|
||||
### 定价和可用性
|
||||
|
||||
树莓派 4 的板子起始售价为 35 美元,根据可选配置不同(1-4 GB),售价也不同。
|
||||
|
||||
* 1 GB RAM 树莓派 4 售价:35 美元
|
||||
* 2 GB RAM 树莓派 4 售价:45 美元
|
||||
* 4 GB RAM 树莓派 4 售价:55 美元
|
||||
|
||||
根据你所在国家或地区的不同,树莓派 4 有不同的供应商。现有库存即将售罄,如果你想购买一定尽快,否则就要再等上一段时日了,你还可以参考官方页面上的购买信息。
|
||||
|
||||
- [购买树莓派 4][1]
|
||||
|
||||
请注意,[运行树莓派需要额外的配件][7],这就是为什么官方提供了可选的基础套件,套件中包含了所有必需的支持配件。
|
||||
|
||||
#### 树莓派 4 桌面套件
|
||||
|
||||
![Raspberry Pi 4 Desktop Kit][9]
|
||||
|
||||
你可以在购买树莓派 4 时同时购买树莓派 4 的桌面套件:外壳、键盘、鼠标、micro HDMI 线、USB-C 电源、用户指南以及[预装了 Rasbian 的 16 GB microSD 卡][10]。
|
||||
|
||||
![Raspberry Pi Branded Desktop Kit][11]
|
||||
|
||||
整组套件采用红白颜色设计,看起来很美观(如果你关心外观的话)。你可以在树莓派网站上获取更多的购买信息。
|
||||
|
||||
- [树莓派 4 桌面套件][12]
|
||||
|
||||
### 树莓派 4 的前景
|
||||
|
||||
拥有所有这些配置后,树莓派 4 无疑会成为同类产品中最好的之一。同样,相比购买入门级桌面计算机,购买树莓派 4 也会是更好的选择。你可以只花很便宜的价格,就能轻松访问文档、管理电子表格,以及完成更多其它操作。
|
||||
|
||||
我绝对会考虑购买树莓派 4 作为备用(但强大)的入门级桌面计算机,但不会配备 4k 显示器,但依据文档,树莓派 4 肯定是支持双 4k 显示设置的。
|
||||
|
||||
你怎么评价最新版的树莓派 4B? 欢迎在评论中说出你的想法。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/raspberry-pi-4/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[wahailin](https://github.com/wahailin)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.raspberrypi.org/products/raspberry-pi-4-model-b/
|
||||
[2]: https://itsfoss.com/raspberry-pi-alternatives/
|
||||
[3]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/06/raspberry-pi-4.jpeg?resize=800%2C449&ssl=1
|
||||
[4]: https://itsfoss.com/linux-based-mini-pc/
|
||||
[5]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/06/raspberry-pi-4-tech-specs.jpg?ssl=1
|
||||
[6]: https://www.raspberrypi.org/products/raspberry-pi-4-model-b/specifications/
|
||||
[7]: https://itsfoss.com/things-you-need-to-get-your-raspberry-pi-working/
|
||||
[8]: https://itsfoss.com/raspberry-pi-gets-ram-upgrade-in-the-same-price/
|
||||
[9]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/06/raspberry-pi-4-desktop-kit.jpg?resize=800%2C427&ssl=1
|
||||
[10]: https://itsfoss.com/tutorial-how-to-install-raspberry-pi-os-raspbian-wheezy/
|
||||
[11]: https://i0.wp.com/itsfoss.com/wp-content/uploads/2019/06/raspberry-pi-desktop-kit-official.jpg?ssl=1
|
||||
[12]: https://www.raspberrypi.org/products/raspberry-pi-4-desktop-kit/
|
||||
264
published/20190625 5 tiny Linux distros to try before you die.md
Normal file
264
published/20190625 5 tiny Linux distros to try before you die.md
Normal file
@ -0,0 +1,264 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (chen-ni)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-11040-1.html)
|
||||
[#]: subject: (5 tiny Linux distros to try before you die)
|
||||
[#]: via: (https://opensource.com/article/19/6/linux-distros-to-try)
|
||||
[#]: author: (Seth Kenlon https://opensource.com/users/seth/users/marcobravo)
|
||||
|
||||
不容错过的 5 个微型 Linux 发行版
|
||||
======
|
||||
|
||||
> 这些微型 Linux 发行版可以让你的老爷机复活,可以启动一个损坏的系统,或者是确保在公共电脑上进行安全的操作。
|
||||
|
||||

|
||||
|
||||
可供日常使用的 Linux 发行版比比皆是,不过其中有一些发行版常常被我们忽视,因为它们实在是太小了。但这些微型 Linux 发行版其实是一种非常强大的创新:使用一套完整的操作系统驱动一台只有不到 1 GB 存储空间和 512 MB 内存的计算机,真的是终极的黑客作风。
|
||||
|
||||
微型发行版的用法有很多种,比如说:
|
||||
|
||||
* 从垃圾桶边挽救回那些又老又慢的电脑。你可以继续使用那些本来已经计划报废的机器,直到它们彻底解体(而不是在刚开始感觉有点儿慢的时候就扔掉)。
|
||||
* 使用 U盘启动一个损坏的系统来恢复数据或者修复启动分区。
|
||||
* 确保在安全和隐私的操作环境下使用公共电脑。如果使用 U 盘启动酒店大厅或者图书馆里的一台公共电脑,你是可以确定操作环境是安全的。
|
||||
|
||||
轻量级发行版有很多种,比如说 [Lubuntu][2]、[Peppermint OS][3] 和 [Bodhi][4],但是那些真正微型的发行版又有一些独到之处。下面就是你不容错过的五个微型发行版:
|
||||
|
||||
### Tiny Core
|
||||
|
||||
![Tiny Core Linux][5]
|
||||
|
||||
[Tiny Core Linux][6] 小得近乎不可思议:终端版本只有 11 MB,图形界面版本只有 16 MB。我翻了一下之前收集的旧 U盘,最小的一个是 128 MB 的,也有 Tiny Core 镜像文件的八倍之大呢。
|
||||
|
||||
Tiny Core 默认包括只包括了基本的操作系统,你需要通过以太网下载需要的应用程序。由于设计得极端精简,甚至安装完整操作系统的应用程序都没有被包含在内(不过需要的话可以从 Tiny Core 的软件仓库下载)。
|
||||
|
||||
我使用过一个 128 MB 的 U盘在一台只有 512 MB 内存的机器上运行了 Tiny Core,对于一个只有 16 MB 的操作系统来说,效果算是非常棒了。只有在使用网页浏览器的时候速度才会变慢,但这主要是由于大部分现代网站太过复杂,而不是 Tiny Core 的问题。
|
||||
|
||||
如果不使用图形界面,运行 Tiny Core 就只需要 64 MB 的内存了。
|
||||
|
||||
#### 安装
|
||||
|
||||
[下载 Tiny Core][7] 并使用 `dd` 或者 [Etcher][8] 写入 U盘。
|
||||
|
||||
你只需要点击屏幕底部启动栏上的 **Apps** 图标下载 **tc-install** 或者 **tc-install-GUI** 应用,就可以轻松安装 Tiny Core了。
|
||||
|
||||
![Tiny Core installer][9]
|
||||
|
||||
安装 Tiny Core 有几种不同的方式。你可以把它安装在一个格式化为 Linux 驱动器的 U盘里(这要求你的电脑支持使用 USB 驱动启动。大多数现代电脑都支持,但是在老一些的电脑上不太常见),或者安装在微软 FAT 文件系统的 U 盘里(这对于大多数不支持从 USB 驱动启动的电脑来说非常管用),或者甚至安装在一个现有 Linux 分区的一个文件夹里。
|
||||
|
||||
安装过程非常快,完成之后就可以重启计算机,进入到 Tiny Core Linux 系统中啦。
|
||||
|
||||
#### 应用程序
|
||||
|
||||
由于系统自带程序基本上只有一个文本编辑器和一个终端,你所要做的第一件事情就应该是安装一些应用程序。底部启动栏上的 **Apps** 图标展示了 Tiny Core 提供的所有软件包。**Apps** 软件仓库同时包含了一些重要的驱动程序,对于使用 WiFi 网卡或者是打印机等等都很有帮助。
|
||||
|
||||
在安装一个新的应用程序或者实用程序的时候,你可以选择在 Tiny Core 启动的时候就加载软件包,或者是需要的时候才加载。如果选择启动时加载,那么不仅该软件立即就可以使用,并且(不出所料地)下次重启之后也依然可用;如果选择需要时加载,那么在软件包下载完成之后仍然可以马上使用,但是重启之后就不会被自动加载到内存中了。这样可以保持很快的开机速度,并且只占用很少的内存,但同时也意味着每次开机之后,该应用的软件包只有在第一次被使用的时候才会被加载到内存中。
|
||||
|
||||
可供选择的应用程序同时包括像 office 和图像应用之类的用户端应用,以及像 [Samba][10] 和网站服务器这种的服务端应用。
|
||||
|
||||
当然了,随着你在 Tiny Core 上添加的应用程序越来越多,它就不那么“微型”了。不过在 Tiny Core 的网站上我们可以看到,即使是包括了所有 WiFi 驱动程序的 **Tiny Core Plus** 镜像文件也只有大约 100 MB,所以“不那么微型”也仍然很可能比 256 MB 要小很多。
|
||||
|
||||
#### 结论
|
||||
|
||||
Tiny Core 非常适合性能不佳的老爷机、用来通过网络启动的镜像文件,以及任何更看重应用而不是操作系统的人。Tiny Core 可以作为一个很好的周末工程来实践:从 16 MB 开始一步步搭建操作系统,直到你感觉这个操作系统已经足够满足你的需求了。
|
||||
|
||||
### SliTaz
|
||||
|
||||
![SliTaz Linux][11]
|
||||
|
||||
[SliTaz Linux][12] 的镜像文件有大约 51 MB 大小,差不多是 Tiny Core 的四倍,但是包含一整套出色的驱动程序和应用程序。事实上,如果事先不知道的话,你可能会以为是通过一个 1 GB 的 Ubuntu 镜像启动的,因为能想到的任何一个基本启动镜像应该有的东西都在这儿:文本编辑器、网页浏览器、绘画工具、表格工具等等。
|
||||
|
||||
我使用过一个 128 MB 的 U盘 在一个 512 MB 内存的机器上运行了 SliTaz,效果非常不错。浏览复杂网站的时候性能会下降,但是系统包含的轻量级浏览器 [Midori][13] 可以快速加载绝大多数网站。
|
||||
|
||||
你可以在启动的时候选择进入没有图形界面的 SliTaz,这样在仅仅只有 64 MB 的机器上也可以很好地运行。
|
||||
|
||||
#### 安装
|
||||
|
||||
可供下载的 SliTaz 有很多种,因为它的开发者和社区针对可能存在的限制提供了非常多的版本。比如说,有一种低内存版本可以在只有 24 MB 内存的机器上运行;有一种版本使用 Firefox 而不是 Midori;还有一种版本没有包含额外的应用程序,等等。
|
||||
|
||||
如果你挑花了眼,只想赶紧选择一个版本尝试一下的话,那就 [下载滚动发布版本吧][14]。这个版本有差不多 50 MB 大小,每周都会更新。如果你爱上了 SliTaz,而滚动发布版本又更新得 *过快* 了的话,可以再选择一个更符合你需求的版本。
|
||||
|
||||
下载好你选择的 SliTaz 镜像文件之后,你就可以用 `dd` 或者 [Etcher][8] 将它写入 U 盘,然后重启。
|
||||
|
||||
将 SliTaz 安装在 U 盘或者硬盘上需要通过 **TazPanel** 这个应用程序来实现。它会引导你对硬盘进行需要的分区,然后将 SliTaz 安装在你选择的地方。
|
||||
|
||||
![SliTaz installer][15]
|
||||
|
||||
#### 应用程序
|
||||
|
||||
SliTaz 的控制中心是 **TazPanel** 这个应用程序。如果你喜欢 OpenSUSE 或者 Mageia (最初被称为 Mandrake),那 TazPanel 对你来说应该不会陌生(至少在核心思想上):包括系统设置、硬件监测、用户和用户组的管理、系统升级、安装应用程序在内的这些功能,都在这一个应用程序内实现。
|
||||
|
||||
SliTaz 提供的应用程序可以满足大多数基本需求,如果你不是非常在意完成某一项任务必须使用哪一个应用程序的话,那么在 SliTaz 的软件仓库里应该可以找到你想要的应用。如果你有一些特别的需求(比如说想要使用 GIMP 2.10 而不是 GIMP 2.8),那么就需要学习如何生成 SliTaz 软件包了。好消息是,**tazpkg** 命令支持从好几种软件包格式转换过来,包括:
|
||||
|
||||
* Debian 软件包(.deb,.udeb)
|
||||
* RPM 软件包(.rpm)
|
||||
* Slackware 软件包(.tgz)
|
||||
* Puppy 软件包(.sfs,.pet)
|
||||
* NuTyX 软件包(.cards.tar.xz)
|
||||
* Arch 和 Alpine Linux 软件包(.apk,.pkg.tar.gz,.pkg.tar.xz)
|
||||
* OpenWrt 软件包(.ipk,.opk)
|
||||
* Paldo 软件包(.tar.bz2)
|
||||
* Void 软件包(.xbps)
|
||||
* Tiny Core 软件包(.tce,.tcel,.tcem, .tcz)
|
||||
|
||||
#### 结论
|
||||
|
||||
SliTaz 是一个快速而小巧的 Linux 发行版,并且非常容易上手(因为有一个中心化的控制面板)。由于它的软件包工具支持从其它格式的 Linux 软件包转换成自己的格式,它的应用程序理论上来说是非常丰富的,你可以很容易地使用喜欢的工具搭建自己的工作环境。SliTaz 很小,但是也非常具有杀伤力,正如它的蜘蛛 logo 所暗示的那样。
|
||||
|
||||
### Porteus
|
||||
|
||||
![Porteus Linux][16]
|
||||
|
||||
[Porteus][17] 提供了不同的桌面环境可供选择,最小的镜像文件大约在 270 MB 左右,最大的有 350 MB。它是微型 Linux 中镜像文件最大的一个,但是这些额外的空间都被用来确保一个非常顺畅的 Linux 桌面环境的体验,以至于你很可能会忘了自己是在使用一个 live 版本。如果将 Porteus 安装到 SSD 或者是在启动的时候加载到内存里的话,你就会得到一个如此天衣无缝地顺畅的环境,以至于不会相信你的操作系统所占用的空间只有不到半个 CD-ROM 的大小。
|
||||
|
||||
Porteus 的基础镜像文件相对来说比较小,因此被称为是“微型”,但是根据你选择的桌面环境版本,Porteus 有可能会需要 1 GB 之多的内存才可以运行。尽管其它微型 Linux 发行版倾向于通过精简应用程序来节约空间和资源,Porteus 却希望你像普通发行版一样来使用它。忘掉你是在使用一个微型的压缩根文件系统,尽情安装所有你喜欢的应用程序吧。
|
||||
|
||||
#### 安装
|
||||
|
||||
可以在 [离你最近的 Porteus 镜像网站][18] 上下载 Porteus,并且从 MATE、LXQT、LXDE、OpenBox、XFCE、Cinnamon 或者 KDE 里选择自己喜欢的桌面环境。如果没有特殊偏好,MATE 或者是 KDE 桌面都是不错的选择,他们可以提供熟悉的桌面环境体验,并且镜像文件又不至于太大。
|
||||
|
||||
![Porteus installer][19]
|
||||
|
||||
你可以根据 [官方的安装指南][20] 将 Porteus 安装到一个 U盘 或者是内部硬盘里。这两种方式非常相似,都会使用一个不可变的压缩根文件系统。这是一种稳定的、受限制的文件系统,会根据你的使用被修改。你所做的变更和安装的应用程序在重启的时候都会被加载到内存里,从而还原你关机前的使用环境。
|
||||
|
||||
#### 应用程序
|
||||
|
||||
应用程序在 Porteus 里被称为“模块”,由 [Slackware 软件包统一管理器][21](USM)提供。USM 的资源涵盖五个不同的 Slackware 软件仓库,所以可供选择的应用还是很丰富的。
|
||||
|
||||
#### 结论
|
||||
|
||||
Porteus 可以提供完整的 Linux 使用体验,却只使用了正常 Linux 所需要空间的一小部分。这是一个配备了很多种可供选择的桌面环境和很多应用程序的出色的便携式 Linux 发行版。
|
||||
|
||||
### Bodhi Linux
|
||||
|
||||
![Bodhi Linux][22]
|
||||
|
||||
[Bodhi Linux][4] 的 ISO 镜像文件有 740 MB 大小,初看之下并不是很“微型”,不过一旦安装完成之后,你就会惊讶于它是多么微型了。Bodhi 在 512 MB 大小的内存上也可以顺畅运行,并且它的桌面环境看起来就像是来自未来一样。Bodhi 使用的是 [Enlightenment][23] 桌面,这是一个精心制作的优美的用户界面,小巧而强悍。
|
||||
|
||||
不过 Bodhi 并不只是简单地使用 Enlightenment,而是在此基础上增色不少。Bodhi 在配置型应用程序和系统设置面板上都进行了界面处理,避免了 Enlightenment 有时显得过于繁复的选项。Bodhi 替你做了一些很好的默认选择,并且只显示全部选项的一部分。如果你是一个 Enlightenment 狂热分子,那么 Bodhi 这样的做法对你来说可能显得不是很纯粹,但是对于大多数用户来说,Bodhi 这样做可以让人更加专注于 Enlightenment 桌面本身。
|
||||
|
||||
#### 安装
|
||||
|
||||
[下载 Bodhi Linux][24],通过 `dd` 或者 [Etcher][8] 写入 U盘,然后重启。
|
||||
|
||||
Bodhi 安装器可以在 **设置** 页面的 **应用程序** 菜单里找到。安装程序用的是 **Ubiquity**,所以整个过程和安装 Ubuntu 是一样的。如果你没有安装过 Ubuntu 也不必担心,因为这是最好安装的发行版之一了。
|
||||
|
||||
![Bodhi installer][25]
|
||||
|
||||
#### 应用程序
|
||||
|
||||
Bodhi 是基于最新的 Ubuntu 长期维护发布版的,所以可供使用的应用程序简直数不胜数。只要是在 Ubuntu 上可以使用的应用,Bohdi 上就同样可以找到。
|
||||
|
||||
#### 结论
|
||||
|
||||
Bodhi Linux 相比一个标准的 Ubuntu 来说要小不少,但是相比其它微型 Ubuntu 环境来说又好一些(因为使用了 Enlightenment)。如果你在找一个比大多数发行版更轻量的 Linux 发行版,但是又不想使用 OverlayFS 或者是应用程序模块的话,那么 Bodhi 就是一个不错的选择了。
|
||||
|
||||
### Puppy Linux
|
||||
|
||||
![Puppy Linux][26]
|
||||
|
||||
早在 Tiny Core、SliTaz、[AntiX][27] 或者是 Porteus 诞生之前,就已经有 [Puppy Linux][28] 了。作为最早的微型 Linux 发行版之一,Puppy 已经历经了十五年风霜,并且无论是对于老爷机还是新用户来说始终都是一个可靠的、可启动的操作系统。
|
||||
|
||||
为了保证正常运行,Puppy 会在第一次启动之后引导用户完成必要的设置步骤。整个过程涉及很多个窗口,但是一旦完成,你就会对一切功能了如指掌,然后再决定是否需要安装。
|
||||
|
||||
Puppy 几乎有 300 MB 大小,并且在我测试的 1 GB 内存的机器上并不能正常运行,所以它并不是一个特别微型的 Linux 发行版。尽管如此,它仍然是一个非常棒的 1 GB 以下的操作系统,并且在该类系统里算是非常友好的一个。
|
||||
|
||||
#### 安装
|
||||
|
||||
[下载 Puppy Linux][29],然后通过 `dd` 或 [Etcher][8] 写入 U 盘,或者是刻录到 CD 或者 DVD 里,然后重启。
|
||||
|
||||
![Puppy installer][30]
|
||||
|
||||
Puppy 几乎可以安装在支持任何一种数据格式的载体上。你可以在顶部启动栏里找到 **Puppy Installer** 安装程序,这个程序负责安装 Puppy 以及 Puppy 的应用程序。
|
||||
|
||||
Puppy 安装器会一步步引导你将系统安装在你提供的任何一种媒介上。Puppy 可以从 U盘、光盘、硬盘,或者甚至是 SD 卡上启动。我曾经在一台没有硬盘、光驱出了故障,并且也无法从 USB 启动的计算机上成功运行了 Puppy。由于 Puppy 支持在任何载体上写入你的配置选项,我甚至可以在一个拥有长期数据存储的外部设备上使用它。
|
||||
|
||||
#### 应用程序
|
||||
|
||||
**Puppy 安装器** 这个应用同样被用来在 Puppy 上安装应用。由于 Puppy 是基于 Ubuntu 的,它的软件仓库几乎不会缺少任何一个 Linux 软件包,并且如果真的出现了这种情况的话,你也可以使用 [Flatpak][31]。
|
||||
|
||||
#### 结论
|
||||
|
||||
Puppy 是最早的微型 Linux。尽管它已经不是最微型的了,却是目前最易用的一个。
|
||||
|
||||
### 附赠:Silverblue
|
||||
|
||||
![SilverBlue, not tiny, but tiny-adjacent][32]
|
||||
|
||||
微型 Linux 这个概念是随着时间不断变化的。很久以前,微型 Linux 发行版意味着需要下载到 CD-R 里,从光驱启动,然后将修改写入外部媒介中。后来,你可以从 U 盘启动它,并且有专门用来记录永久修改的空间。现在的微型 Linux 不仅支持上面两种方法,还可以被直接安装在内部驱动或者文件夹里。
|
||||
|
||||
大家都没有想到 Linux 开创了容器的热潮 —— 容器里应用程序是在半虚拟化的环境中运行的一套独立的 Linux 系统。曾经只是属于喜欢优化硬盘空间或者重新利用老爷机的人们的小众爱好,很快成为了那些想要开发容器但又不想在应用程序上添加太多负载的人的强烈需求。那些在极简化的、不起眼的 Linux 发行版上所付出的辛苦,一夜之间以一种意想不到的方式得到了回报。
|
||||
|
||||
立足于根文件系统这个概念,Fedora 项目发起的 [Silverblue][33] 试验旨在创造一个不可修改的操作系统。该操作系统主要通过容器的形式来更新系统以及安装应用,系统本身永远不会改变。
|
||||
|
||||
2.1 GB 的 Silverblue 可不是一个微型 Linux 发行版,但是从某种程度上来说,它是微型 Linux 和容器运动的产物。
|
||||
|
||||
#### 安装
|
||||
|
||||
[下载 Silverblue][34],然后通过 `dd` 琥或 [Etcher][8] 写入 U 盘,或者是刻录到 CD 或者 DVD 里,然后重启。
|
||||
|
||||
启动到 Silverblue 之后,使用 [Anaconda][35](标准的、友好的 Fedora 安装器)将它安装在一个内部硬盘里。
|
||||
|
||||
![Anaconda installer][36]
|
||||
|
||||
#### 应用程序
|
||||
|
||||
Silverblue 安装应用的方式和传统意义上不同:它是在基础操作系统之上运行容器。具体来说,它使用 Flatpak 运行 GUI 应用程序,使用 [Toolbox][37] 运行命令。
|
||||
|
||||
由于 Flatpak 并非像传统的 Fedora RPM 软件包一样常见,Silverblue 也提供了一种可以将 Fedora RPM 软件包转换成 Silverblue 形式的方法:**软件包分层**。
|
||||
|
||||
#### 结论
|
||||
|
||||
Silverblue 可能是一个用来尝试前沿科技的有趣实验,或者也可能是桌面操作系统的未来。它之所以被称为微型,只是因为根文件系统的大小不会随着系统升级或者安装应用而改变。不过,透过 Silverblue 来看看对微型 Linux 的迷恋在带领着 Linux 社区和行业往哪个方向走,也是一件挺有意思的事情。对了,走之前不要忘了向 11 MB 大小的微型 Linux 先驱们脱帽致敬。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/6/linux-distros-to-try
|
||||
|
||||
作者:[Seth Kenlon][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[chen-ni](https://github.com/chen-ni)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/seth/users/marcobravo
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/yearbook-haff-rx-linux-file-lead_0.png?itok=-i0NNfDC (Hand putting a Linux file folder into a drawer)
|
||||
[2]: http://lubuntu.net
|
||||
[3]: http://peppermintos.com
|
||||
[4]: https://www.bodhilinux.com/
|
||||
[5]: https://opensource.com/sites/default/files/uploads/tinycore.jpg (Tiny Core Linux)
|
||||
[6]: http://tinycorelinux.net/
|
||||
[7]: http://tinycorelinux.net/welcome.html
|
||||
[8]: https://www.balena.io/etcher/
|
||||
[9]: https://opensource.com/sites/default/files/uploads/tc-install-gui.png (Tiny Core installer)
|
||||
[10]: https://www.samba.org/
|
||||
[11]: https://opensource.com/sites/default/files/uploads/slitaz.jpg (SliTaz Linux)
|
||||
[12]: http://www.slitaz.org/en/
|
||||
[13]: https://github.com/midori-browser/core
|
||||
[14]: http://slitaz.org/en/get/#rolling
|
||||
[15]: https://opensource.com/sites/default/files/uploads/slitaz-install.jpg (SliTaz installer)
|
||||
[16]: https://opensource.com/sites/default/files/uploads/porteus.jpg (Porteus Linux)
|
||||
[17]: http://www.porteus.org/
|
||||
[18]: http://porteus.org/porteus-mirrors.txt
|
||||
[19]: https://opensource.com/sites/default/files/images/porteus-installer.png (Porteus installer)
|
||||
[20]: http://www.porteus.org/component/content/article/26-tutorials/general-info-tutorials/114-official-porteus-installation-guide.html
|
||||
[21]: http://www.porteus.org/tutorials/9-modules/149-usm.html
|
||||
[22]: https://opensource.com/sites/default/files/uploads/bodhi.jpg (Bodhi Linux)
|
||||
[23]: https://www.enlightenment.org/
|
||||
[24]: https://www.bodhilinux.com/download
|
||||
[25]: https://opensource.com/sites/default/files/uploads/bodhi-install.jpg (Bodhi installer)
|
||||
[26]: https://opensource.com/sites/default/files/uploads/puppy.jpg (Puppy Linux)
|
||||
[27]: https://antixlinux.com/
|
||||
[28]: http://puppylinux.com/
|
||||
[29]: http://puppylinux.com/index.html#download
|
||||
[30]: https://opensource.com/sites/default/files/uploads/puppy-install.jpg (Puppy installer)
|
||||
[31]: https://docs.fedoraproject.org/en-US/fedora-silverblue/getting-started/#flatpak
|
||||
[32]: https://opensource.com/sites/default/files/uploads/silverblue.jpg (SilverBlue, not tiny, but tiny-adjacent)
|
||||
[33]: https://silverblue.fedoraproject.org/
|
||||
[34]: https://silverblue.fedoraproject.org/download
|
||||
[35]: https://fedoraproject.org/wiki/Anaconda
|
||||
[36]: https://opensource.com/sites/default/files/uploads/silverblue-install.jpg (Anaconda installer)
|
||||
[37]: https://docs.fedoraproject.org/en-US/fedora-silverblue/toolbox/
|
||||
@ -1,106 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (hopefully2333)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Cisco to buy IoT security, management firm Sentryo)
|
||||
[#]: via: (https://www.networkworld.com/article/3400847/cisco-to-buy-iot-security-management-firm-sentryo.html)
|
||||
[#]: author: (Michael Cooney https://www.networkworld.com/author/Michael-Cooney/)
|
||||
|
||||
Cisco to buy IoT security, management firm Sentryo
|
||||
======
|
||||
Buying Sentryo will give Cisco support for anomaly and real-time threat detection for the industrial internet of things.
|
||||
![IDG Worldwide][1]
|
||||
|
||||
Looking to expand its IoT security and management offerings Cisco plans to acquire [Sentryo][2], a company based in France that offers anomaly detection and real-time threat detection for Industrial Internet of Things ([IIoT][3]) networks.
|
||||
|
||||
Founded in 2014 Sentryo products include ICS CyberVision – an asset inventory, network monitoring and threat intelligence platform – and CyberVision network edge sensors, which analyze network flows.
|
||||
|
||||
**More on IoT:**
|
||||
|
||||
* [What is the IoT? How the internet of things works][4]
|
||||
* [What is edge computing and how it’s changing the network][5]
|
||||
* [Most powerful Internet of Things companies][6]
|
||||
* [10 Hot IoT startups to watch][7]
|
||||
* [The 6 ways to make money in IoT][8]
|
||||
* [What is digital twin technology? [and why it matters]][9]
|
||||
* [Blockchain, service-centric networking key to IoT success][10]
|
||||
* [Getting grounded in IoT networking and security][11]
|
||||
* [Building IoT-ready networks must become a priority][12]
|
||||
* [What is the Industrial IoT? [And why the stakes are so high]][13]
|
||||
|
||||
|
||||
|
||||
“We have incorporated Sentryo’s edge sensor and our industrial networking hardware with Cisco’s IOx application framework,” wrote Rob Salvagno, Cisco vice president of Corporate Development and Cisco Investments in a [blog][14] about the proposed buy.
|
||||
|
||||
“We believe that connectivity is foundational to IoT projects and by unleashing the power of the network we can dramatically improve operational efficiencies and uncover new business opportunities. With the addition of Sentryo, Cisco can offer control systems engineers deeper visibility into assets to optimize, detect anomalies and secure their networks.”
|
||||
|
||||
Gartner [wrote][15] of Sentryo’s system: “ICS CyberVision product provides visibility into its customers'' OT networks in way all OT users will understand, not just technical IT staff. With the increased focus of both hackers and regulators on industrial control systems, it is vital to have the right visibility of an organization’s OT. Many OT networks not only are geographically dispersed, but also are complex and consist of hundreds of thousands of components.”
|
||||
|
||||
Sentryo's ICS CyberVision lets enterprises ensure continuity, resilience and safety of their industrial operations while preventing possible cyberattacks, said [Nandini Natarajan][16] , industry analyst at Frost & Sullivan. "It automatically profiles assets and communication flows using a unique 'universal OT language' in the form of tags, which describe in plain text what each asset is doing. ICS CyberVision gives anyone immediate insights into an asset's role and behaviors; it offers many different analytic views leveraging artificial intelligence algorithms to let users deep-dive into the vast amount of data a typical industrial control system can generate. Sentryo makes it easy to see important or relevant information."
|
||||
|
||||
In addition, Sentryo's platform uses deep packet inspection (DPI) to extract information from communications among industrial assets, Natarajan said. This DPI engine is deployed through an edge-computing architecture that can run either on Sentryo sensor appliances or on network equipment that is already installed. Thus, Sentryo can embed visibility and cybersecurity features in the industrial network rather than deploying an out-of-band monitoring network, Natarajan said.
|
||||
|
||||
**[[Prepare to become a Certified Information Security Systems Professional with this comprehensive online course from PluralSight. Now offering a 10-day free trial!][17] ]**
|
||||
|
||||
Sentryo’s technology will broaden [Cisco’s][18] overarching IoT plan. In January it [launched][19] a family of switches, software, developer tools and blueprints to meld IoT and industrial networking with [intent-based networking][20] (IBN) and classic IT security, monitoring and application-development support.
|
||||
|
||||
The new platforms can be managed by Cisco’s DNA Center, and Cisco IoT Field Network Director, letting customers fuse their IoT and industrial-network control with their business IT world.
|
||||
|
||||
DNA Center is Cisco’s central management tool for enterprise networks, featuring automation capabilities, assurance setting, fabric provisioning and policy-based segmentation. It is also at the center of the company’s IBN initiative offering customers the ability to automatically implement network and policy changes on the fly and ensure data delivery. The IoT Field Network Director is software that manages multiservice networks of Cisco industrial, connected grid routers and endpoints.
|
||||
|
||||
Liz Centoni, senior vice president and general manager of Cisco's IoT business group said the company expects the [Sentryo technology to help][21] IoT customers in a number of ways:
|
||||
|
||||
Network-enabled, passive DPI capabilities to discover IoT and OT assets, and establish communication patterns between devices and systems. Sentryo’s sensor is natively deployable on Cisco’s IOx framework and can be built into the industrial network these devices run on instead of adding additional hardware.
|
||||
|
||||
As device identification and communication patterns are created, Cisco will integrate this with DNA Center and Identity Services Engine(ISE) to allow customers to easily define segmentation policy. This integration will allow OT teams to leverage IT security teams’ expertise to secure their environments without risk to the operational processes.
|
||||
|
||||
With these IoT devices lacking modern embedded software and security capabilities, segmentation will be the key technology to allow communication from operational assets to the rightful systems, and reduce risk of cyber security incidents like we saw with [WannaCry][22] and [Norsk Hydro][23].
|
||||
|
||||
According to [Crunchbase][24], Sentryo has $3.5M in estimated revenue annually and it competes most closely with Cymmetria, Team8, and Indegy. The acquisition is expected to close before the end of Cisco’s Q1 Fiscal Year 2020 -- October 26, 2019. Financial details of the acquisition were not detailed.
|
||||
|
||||
Sentryo is Cisco’s second acquisition this year. It bought Singularity for its network analytics technology in January. In 2018 Cisco bought six companies including Duo security software.
|
||||
|
||||
** **
|
||||
|
||||
Join the Network World communities on [Facebook][25] and [LinkedIn][26] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3400847/cisco-to-buy-iot-security-management-firm-sentryo.html
|
||||
|
||||
作者:[Michael Cooney][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Michael-Cooney/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://images.idgesg.net/images/article/2018/09/nwan_019_iiot-100771131-large.jpg
|
||||
[2]: https://www.sentryo.net/
|
||||
[3]: https://www.networkworld.com/article/3243928/what-is-the-industrial-iot-and-why-the-stakes-are-so-high.html
|
||||
[4]: https://www.networkworld.com/article/3207535/internet-of-things/what-is-the-iot-how-the-internet-of-things-works.html
|
||||
[5]: https://www.networkworld.com/article/3224893/internet-of-things/what-is-edge-computing-and-how-it-s-changing-the-network.html
|
||||
[6]: https://www.networkworld.com/article/2287045/internet-of-things/wireless-153629-10-most-powerful-internet-of-things-companies.html
|
||||
[7]: https://www.networkworld.com/article/3270961/internet-of-things/10-hot-iot-startups-to-watch.html
|
||||
[8]: https://www.networkworld.com/article/3279346/internet-of-things/the-6-ways-to-make-money-in-iot.html
|
||||
[9]: https://www.networkworld.com/article/3280225/internet-of-things/what-is-digital-twin-technology-and-why-it-matters.html
|
||||
[10]: https://www.networkworld.com/article/3276313/internet-of-things/blockchain-service-centric-networking-key-to-iot-success.html
|
||||
[11]: https://www.networkworld.com/article/3269736/internet-of-things/getting-grounded-in-iot-networking-and-security.html
|
||||
[12]: https://www.networkworld.com/article/3276304/internet-of-things/building-iot-ready-networks-must-become-a-priority.html
|
||||
[13]: https://www.networkworld.com/article/3243928/internet-of-things/what-is-the-industrial-iot-and-why-the-stakes-are-so-high.html
|
||||
[14]: https://blogs.cisco.com/news/cisco-industrial-iot-news
|
||||
[15]: https://www.globenewswire.com/news-release/2018/06/28/1531119/0/en/Sentryo-Named-a-Cool-Vendor-by-Gartner.html
|
||||
[16]: https://www.linkedin.com/pulse/industrial-internet-things-iiot-decoded-nandini-natarajan/
|
||||
[17]: https://pluralsight.pxf.io/c/321564/424552/7490?u=https%3A%2F%2Fwww.pluralsight.com%2Fpaths%2Fcertified-information-systems-security-professional-cisspr
|
||||
[18]: https://www.cisco.com/c/dam/en_us/solutions/iot/ihs-report.pdf
|
||||
[19]: https://www.networkworld.com/article/3336454/cisco-goes-after-industrial-iot.html
|
||||
[20]: https://www.networkworld.com/article/3202699/what-is-intent-based-networking.html
|
||||
[21]: https://blogs.cisco.com/news/securing-the-internet-of-things-cisco-announces-intent-to-acquire-sentryo
|
||||
[22]: https://blogs.cisco.com/security/talos/wannacry
|
||||
[23]: https://www.securityweek.com/norsk-hydro-may-have-lost-40m-first-week-after-cyberattack
|
||||
[24]: https://www.crunchbase.com/organization/sentryo#section-web-traffic-by-similarweb
|
||||
[25]: https://www.facebook.com/NetworkWorld/
|
||||
[26]: https://www.linkedin.com/company/network-world
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: translator: (qfzy1233)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
@ -1,85 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Free and Open Source Trello Alternative OpenProject 9 Released)
|
||||
[#]: via: (https://itsfoss.com/openproject-9-release/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
Free and Open Source Trello Alternative OpenProject 9 Released
|
||||
======
|
||||
|
||||
[OpenProject][1] is a collaborative open source project management software. It’s an alternative to proprietary solutions like [Trello][2] and [Jira][3].
|
||||
|
||||
You can use it for free if it’s for personal use and you set it up (and host it) on your own server. This way, you control your data.
|
||||
|
||||
Of course, you get access to premium features and priority help if you are a [Cloud or Enterprise edition user][4].
|
||||
|
||||
The OpenProject 9 release emphasizes on new board views, package list view, and work templates.
|
||||
|
||||
If you didn’t know about this, you can give it a try. But, if you are an existing user – you should know what’s new before migrating to OpenProject 9.
|
||||
|
||||
### What’s New in OpenProject 9?
|
||||
|
||||
Here are some of the major changes in the latest release of OpenProject.
|
||||
|
||||
#### Scrum & Agile Boards
|
||||
|
||||
![][5]
|
||||
|
||||
For Cloud and Enterprise editions, there’s a new [scrum][6] and [agile][7] board view. You also get to showcase your work in a [kanban-style][8] fashion, making it easier to support your agile and scrum teams.
|
||||
|
||||
The new board view makes it easy to know who’s assigned for the task and update the status in a jiffy. You also get different board view options like basic board, status board, and version boards.
|
||||
|
||||
#### Work Package templates
|
||||
|
||||
![Work Package Template][9]
|
||||
|
||||
You don’t have to create everything from scratch for every unique work package. So, instead, you just keep a template – so that you can use it whenever you need to create a new work package. It will save a lot of time.
|
||||
|
||||
#### New Work Package list view
|
||||
|
||||
![Work Package View][10]
|
||||
|
||||
In the work package list, there’s a subtle new addition that lets you view the avatars of the assigned people for a specific work.
|
||||
|
||||
#### Customizable work package view for my page
|
||||
|
||||
Your own page to display what you are working on (and the progress) shouldn’t be always boring. So, now you get the ability to customize it and even add a Gantt chart to visualize your work.
|
||||
|
||||
[][11]
|
||||
|
||||
Suggested read Ubuntu 12.04 Has Reached End of Life
|
||||
|
||||
**Wrapping Up**
|
||||
|
||||
For detailed instructions on migrating and installation, you should follow the [official announcement post][12] covering all the essential details for the users.
|
||||
|
||||
Also, we would love to know about your experience with OpenProject 9, let us know about it in the comments section below! If you use some other project management software, feel free to suggest it to us and rest of your fellow It’s FOSS readers.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/openproject-9-release/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.openproject.org/
|
||||
[2]: https://trello.com/
|
||||
[3]: https://www.atlassian.com/software/jira
|
||||
[4]: https://www.openproject.org/pricing/
|
||||
[5]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/06/open-project-9-scrum-agile.jpeg?fit=800%2C517&ssl=1
|
||||
[6]: https://en.wikipedia.org/wiki/Scrum_(software_development)
|
||||
[7]: https://en.wikipedia.org/wiki/Agile_software_development
|
||||
[8]: https://en.wikipedia.org/wiki/Kanban
|
||||
[9]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/06/work-package-template.jpg?ssl=1
|
||||
[10]: https://i2.wp.com/itsfoss.com/wp-content/uploads/2019/06/work-package-view.jpg?fit=800%2C454&ssl=1
|
||||
[11]: https://itsfoss.com/ubuntu-12-04-end-of-life/
|
||||
[12]: https://www.openproject.org/openproject-9-new-scrum-agile-board-view/
|
||||
@ -1,88 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (BitTorrent Client Deluge 2.0 Released: Here’s What’s New)
|
||||
[#]: via: (https://itsfoss.com/deluge-2-release/)
|
||||
[#]: author: (Ankush Das https://itsfoss.com/author/ankush/)
|
||||
|
||||
BitTorrent Client Deluge 2.0 Released: Here’s What’s New
|
||||
======
|
||||
|
||||
You probably already know that [Deluge][1] is one of the [best Torrent clients available for Linux users][2]. However, the last stable release was almost two years back.
|
||||
|
||||
Even though it was in active development, a major stable release wasn’t there – until recently. The latest version while we write this happens to be 2.0.2. So, if you haven’t downloaded the latest stable version – do try it out.
|
||||
|
||||
In either case, if you’re curious, let us talk about what’s new.
|
||||
|
||||
![Deluge][3]
|
||||
|
||||
### Major improvements in Deluge 2.0
|
||||
|
||||
The new release introduces multi-user support – which was a much needed addition.
|
||||
|
||||
In addition to that, there has been several performance improvements to handle more torrents with faster loading times.
|
||||
|
||||
Also, with version 2.0, Deluge used Python 3 with minimal support for Python 2.7. Even for the user interface, they migrated from GTK UI to GTK3.
|
||||
|
||||
As per the release notes, there are several more significant additions/improvements, which include:
|
||||
|
||||
* Multi-user support.
|
||||
* Performance updates to handle thousands of torrents with faster loading times.
|
||||
* A New Console UI which emulates GTK/Web UIs.
|
||||
* GTK UI migrated to GTK3 with UI improvements and additions.
|
||||
* Magnet pre-fetching to allow file selection when adding torrent.
|
||||
* Fully support libtorrent 1.2 release.
|
||||
* Language switching support.
|
||||
* Improved documentation hosted on ReadTheDocs.
|
||||
* AutoAdd plugin replaces built-in functionality.
|
||||
|
||||
|
||||
|
||||
### How to install or upgrade to Deluge 2.0
|
||||
|
||||
![][4]
|
||||
|
||||
You should follow the official [installation guide][5] (using PPA or PyPi) for any Linux distro. However, if you are upgrading, you should go through the note mentioned in the release note:
|
||||
|
||||
“_Deluge 2.0 is not compatible with Deluge 1.x clients or daemons so these will require upgrading too._ _Also_ _third-party Python scripts may not be compatible if they directly connect to the Deluge client and will need migrating._“
|
||||
|
||||
So, they insist to always make a backup of your [config][6] before a major version upgrade to guard against data loss.
|
||||
|
||||
[][7]
|
||||
|
||||
Suggested read Ubuntu's Snap Apps Website Gets Much Needed Improvements
|
||||
|
||||
And, if you are an author of a plugin, you need to upgrade it make it compatible with the new release.
|
||||
|
||||
Direct download app packages not yet available for Windows and Mac OS. However, the release note mentions that they are being worked on.
|
||||
|
||||
As an alternative, you can install them manually by following the [installation guide][5] in the updated official documentation.
|
||||
|
||||
**Wrapping Up**
|
||||
|
||||
What do you think about the latest stable release? Do you utilize Deluge as your BitTorrent client? Or do you find something else as a better alternative?
|
||||
|
||||
Let us know your thoughts in the comments below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/deluge-2-release/
|
||||
|
||||
作者:[Ankush Das][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/ankush/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://dev.deluge-torrent.org/
|
||||
[2]: https://itsfoss.com/best-torrent-ubuntu/
|
||||
[3]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/06/deluge.jpg?fit=800%2C410&ssl=1
|
||||
[4]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/06/Deluge-2-release.png?resize=800%2C450&ssl=1
|
||||
[5]: https://deluge.readthedocs.io/en/latest/intro/01-install.html
|
||||
[6]: https://dev.deluge-torrent.org/wiki/Faq#WheredoesDelugestoreitssettingsconfig
|
||||
[7]: https://itsfoss.com/snap-store/
|
||||
@ -1,92 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (wahailin)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Raspberry Pi 4 is here!)
|
||||
[#]: via: (https://opensource.com/article/19/6/raspberry-pi-4)
|
||||
[#]: author: (Ben Nuttall https://opensource.com/users/bennuttall)
|
||||
|
||||
Raspberry Pi 4 is here!
|
||||
======
|
||||
A new version of the $35 computer features a 1.5GHz Arm chip and support
|
||||
for dual-HDMI 4K displays, Gigabit Ethernet, and much more.
|
||||
![Raspberry Pi 4 board][1]
|
||||
|
||||
The latest version of the Raspberry Pi—Raspberry Pi 4—was released today, earlier than anticipated, featuring a new 1.5GHz Arm chip and VideoCore GPU with some brand new additions: dual-HDMI 4K display output; USB3 ports; Gigabit Ethernet; and multiple RAM options up to 4GB.
|
||||
|
||||
![Raspberry Pi 4 case][2]
|
||||
|
||||
The Raspberry Pi 4 is a very powerful single-board computer and starts at the usual price of $35. That gets you the standard 1GB RAM, or you can pay $45 for the 2GB model or $55 for the 4GB model—premium-priced models are a first for Raspberry Pi.
|
||||
|
||||
The specs at-a-glance:
|
||||
|
||||
* 64-bit BCM2711 quad-core A72 CPU @ 1.5GHz
|
||||
* VideoCore VI GPU
|
||||
* Gigabit Ethernet port
|
||||
* 1GB, 2GB, or 4GB LPDDR4 RAM
|
||||
* Two Micro-HDMI ports
|
||||
* Two USB3 ports
|
||||
* Two USB2 ports
|
||||
* Dual-band (2.4GHz and 5GHz) WiFi
|
||||
* Bluetooth 5.0
|
||||
* USB Type C power port
|
||||
* CSI camera interface
|
||||
* DSI display interface
|
||||
* MicroSD card slot
|
||||
* Power-over-Ethernet pins
|
||||
* Full compatibility with all previous Raspberry Pi models
|
||||
|
||||
|
||||
|
||||
### USB and networking
|
||||
|
||||
The Raspberry Pi 4 has the benefit of having USB3; it's powered by a USB Type C cable and provides two USB3 ports and two USB2 ports. You can now connect USB3 hard drives and other peripherals and get faster connectivity.
|
||||
|
||||
![Raspberry Pi 4 USBs][3]
|
||||
|
||||
The BCM2835-based chip in Raspberry Pi 1 to 3 provided just one native USB port and no Ethernet, so a USB hub on the board provided more USB ports and an Ethernet port. The 3B+ added a dedicated LAN chip, which gave it Gigabit Ethernet, but this was limited to USB2 speeds. The Pi 4 has dedicated Gigabit Ethernet, and because it's no longer throttled over USB, its networking speeds are much faster.
|
||||
|
||||
The Pi 4 takes advantage of the technology built into the 3B+ that made it the first single-board computer with dual-band WiFi. This means you can connect to both 2.4GHz and 5GHz networks.
|
||||
|
||||
### Displays
|
||||
|
||||
When the first Raspberry Pi launched, the balance of its CPU and GPU performance was tipped heavily in favor of the GPU. The VideoCore IV was a very powerful graphics processor, capable of full-HD 1080p multimedia, which is why the Pi has always been popular as a home media center. The Pi 2 rebalanced things somewhat and brought the CPU in line, taking the Pi from a single-core to a quad-core Arm chip. The Pi 4 takes both factors a big step forward. The new VideoCore VI GPU gives the Pi 4K video and allows two displays via the board's two Micro-HDMI ports (selected to keep the board the same size), so you'll need an adapter or a Micro-to-full HDMI cable to use an HDMI monitor.
|
||||
|
||||
Dual displays are a godsend when you need more screen real estate to keep eye contact with multiple windows—if you're programming you might have your code on one screen and the website or app you're building; your database; your web browser; your emails, or anything else on the other. For the first time, development on Raspberry Pi won't be limited to a single monitor. It's also handy if you want to build a Pi-based project with different things on different screens.
|
||||
|
||||
The Pi also has a Display Serial Interface (DSI) port to drive another special display—not another monitor per se, but the official Raspberry Pi touch screen display connected via a flex cable.
|
||||
|
||||
### Raspbian Buster
|
||||
|
||||
This Raspberry Pi 4's launch coincides with a major Debian release, and the fact the new Pi supports OpenGL ES 3 means it makes sense for any software developed for the Pi 4 to target Raspbian Buster. Buster brings a few user interface tweaks and a whole host of software upgrades, including Python 3.7.
|
||||
|
||||
![Raspbian Buster][4]
|
||||
|
||||
### Open source graphics drivers
|
||||
|
||||
Over the last five years, Eric Anholt has been working to write open source graphics drivers for the Raspberry Pi. Now, Raspbian can use this driver to deliver accelerated web browsing, desktop graphics, and 3D applications on the Pi. This replaces a large chunk of closed-source code that was previously required. Huge thanks to Eric and Broadcom for this effort.
|
||||
|
||||
Previously, the Raspberry Pi 4 was expected to be yet another year away, but the chip design turned out to be ready for production much earlier than anticipated, so here it is!
|
||||
|
||||
* * *
|
||||
|
||||
_The Raspberry Pi 4 is on sale now. Which model will you opt for? Let us know your plans in the comments!_
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/6/raspberry-pi-4
|
||||
|
||||
作者:[Ben Nuttall][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/bennuttall
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://opensource.com/sites/default/files/styles/image-full-size/public/lead-images/raspberry-pi-4_lead.jpg?itok=2bkk43om (Raspberry Pi 4 board)
|
||||
[2]: https://opensource.com/sites/default/files/uploads/raspberry-pi-4-case.jpg (Raspberry Pi 4 case)
|
||||
[3]: https://opensource.com/sites/default/files/uploads/raspberry-pi-4-usb.jpg (Raspberry Pi 4 USBs)
|
||||
[4]: https://opensource.com/sites/default/files/uploads/raspbian-buster.png (Raspbian Buster)
|
||||
@ -0,0 +1,55 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Undo releases Live Recorder 5.0 for Linux debugging)
|
||||
[#]: via: (https://www.networkworld.com/article/3405584/undo-releases-live-recorder-5-0-for-linux-debugging.html)
|
||||
[#]: author: (Sandra Henry-Stocker https://www.networkworld.com/author/Sandra-Henry_Stocker/)
|
||||
|
||||
Undo releases Live Recorder 5.0 for Linux debugging
|
||||
======
|
||||
|
||||
![André Gustavo Stumpf \(CC BY 2.0\)][1]
|
||||
|
||||
Linux debugging has taken a giant step forward with the release of Live Recorder 5.0 from Undo. Just released on Wednesday, this product makes debugging on multi-process systems significantly easier. Based on flight recorder technology, it delves more deeply into processes to provide insight into what’s going on within each process. This includes memory, threads, program flow, service calls and more. To make this possible, Live Recorder 5.0's record, replay and debugging capabilities have been enhanced with the ability to:
|
||||
|
||||
* Record the exact order in which processes altered shared memory variables. It is even possible to zero in on specific variables and skip backward to the last line of code in any process that altered the variable.
|
||||
* Expose potential defects by randomizing thread execution to help reveal race conditions, crashes and other multi-threading defects.
|
||||
* Record and replay the execution of individual Kubernetes and Docker containers to help resolve defects faster in microservices environments
|
||||
|
||||
|
||||
|
||||
The Undo Live Recorder enables engineering teams to record and replay the execution of any software program -- no matter how complex -- and to diagnose and fix the root cause of any issue in test or production.
|
||||
|
||||
Depending on your license, Live Recorder can be used on the command line with the **live-record** command that is somewhat similar to strace though, instead of printing system calls and signals, it creates an "Undo recording". Captured failings in recordings can then be debugged (far more effective than grappling with core dumps!). These recordings can also be can be shared with other members of the staff and can be replayed with the reversible debugger to further investigate the cause of the crash or other problem.
|
||||
|
||||
The Undo Engine is supported on the following Linux distributions:
|
||||
|
||||
* Red Hat Enterprise Linux 6.8, 6.9, 6.10, 7.4, 7.5, 7.6 and 8.0
|
||||
* Fedora 28, 29 and 30
|
||||
* SuSE Linux Enterprise Server 12.3, 12.4 and 15
|
||||
* Ubuntu 16.04 LTS, 18.04 LTS, 18.10 and 19.04
|
||||
|
||||
|
||||
|
||||
Undo is a fast-growing, venture-backed technology start-up based in San Francisco and Cambridge, UK. They claim that the Live Recorder provides 100% certainty about the factors that led to any software failure -- even in the most complex software environments.
|
||||
|
||||
Join the Network World communities on [Facebook][2] and [LinkedIn][3] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3405584/undo-releases-live-recorder-5-0-for-linux-debugging.html
|
||||
|
||||
作者:[Sandra Henry-Stocker][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Sandra-Henry_Stocker/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://images.idgesg.net/images/article/2019/06/flight_data_recorder-100800552-large.jpg
|
||||
[2]: https://www.facebook.com/NetworkWorld/
|
||||
[3]: https://www.linkedin.com/company/network-world
|
||||
@ -1,102 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (GraveAccent)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (5G will augment Wi-Fi, not replace it)
|
||||
[#]: via: (https://www.networkworld.com/article/3399978/5g-will-augment-wi-fi-not-replace-it.html)
|
||||
[#]: author: (Zeus Kerravala https://www.networkworld.com/author/Zeus-Kerravala/)
|
||||
|
||||
5G will augment Wi-Fi, not replace it
|
||||
======
|
||||
Jeff Lipton, vice president of strategy and corporate development at Aruba, adds a dose of reality to the 5G hype, discussing how it and Wi-Fi will work together and how to maximize the value of both.
|
||||
![Thinkstock][1]
|
||||
|
||||
There’s arguably no technology topic that’s currently hotter than [5G][2]. It was a major theme of the most recent [Mobile World Congress][3] show and has reared its head in other events such as Enterprise Connect and almost every vendor event I attend.
|
||||
|
||||
Some vendors have positioned 5G as a panacea to all network problems and predict it will eradicate all other forms of networking. Views like that are obviously extreme, but I do believe that 5G will have an impact on the networking industry and is something that network engineers should be aware of.
|
||||
|
||||
To help bring some realism to the 5G hype, I recently interviewed Jeff Lipton, vice president of strategy and corporate development at Aruba, a Hewlett Packard company, as I know HPE has been deeply involved in the evolution of both 5G and Wi-Fi.
|
||||
|
||||
**[ Also read:[The time of 5G is almost here][3] ]**
|
||||
|
||||
### Zeus Kerravala: 5G is being touted as the "next big thing." Do you see it that way?
|
||||
|
||||
**Jeff Lipton:** The next big thing is connecting "things" and generating actionable insights and context from those things. 5G is one of the technologies that serve this trend. Wi-Fi 6 is another — so are edge compute, Bluetooth Low Energy (BLE), artificial intelligence (AI) and machine learning (ML). These all are important, and they each have a place.
|
||||
|
||||
### Do you see 5G eclipsing Wi-Fi in the enterprise?
|
||||
|
||||
![Jeff Lipton, VP of strategy and corporate development, Aruba][4]
|
||||
|
||||
**Lipton:** No. 5G, like all cellular access, is appropriate if you need macro area coverage and high-speed handoffs. But it’s not ideal for most enterprise applications, where you generally don’t need these capabilities. From a performance standpoint, [Wi-Fi 6][5] and 5G are roughly equal on most metrics, including throughput, latency, reliability, and connection density. Where they aren’t close is economics, where Wi-Fi is far better. I don’t think many customers would be willing to trade Wi-Fi for 5G unless they need macro coverage or high-speed handoffs.
|
||||
|
||||
### Can Wi-Fi and 5G coexist? How would an enterprise use 5G and Wi-Fi together?
|
||||
|
||||
**Lipton:** Wi-Fi and 5G can and should be complementary. The 5G architecture decouples the cellular core and Radio Access Network (RAN). Consequently, Wi-Fi can be the enterprise radio front end and connect tightly with a 5G core. Since the economics of Wi-Fi — especially Wi-Fi 6 — are favorable and performance is extremely good, we envision many service providers using Wi-Fi as the radio front end for their 5G systems where it makes sense, as an alternative to Distributed Antenna (DAS) and small-cell systems.
|
||||
|
||||
Wi-Fi and 5G can and should be complementary." — Jeff Lipton
|
||||
|
||||
### If a business were considering moving to 5G only, how would this be done and how practical is it?
|
||||
|
||||
**Lipton:** To use 5G for primary in-building access, a customer would need to upgrade their network and virtually all of their devices. 5G provides good coverage outdoors, but cellular signals can’t reliably penetrate buildings. And this problem will become worse with 5G, which partially relies on higher frequency radios. So service providers will need a way to provide indoor coverage. To provide this coverage, they propose deploying DAS or small-cell systems — paid for by the end customer. The customers would then connect their devices directly to these cellular systems and pay a service component for each device.
|
||||
|
||||
**[[Take this mobile device management course from PluralSight and learn how to secure devices in your company without degrading the user experience.][6] ]**
|
||||
|
||||
There are several problems with this approach. First, DAS and small-cell systems are significantly more expensive than Wi-Fi networks. And the cost doesn’t stop with the network. Every device would need to have a 5G cellular modem, which costs tens of dollars wholesale and usually over a hundred dollars to an end user. Since few, if any MacBooks, PCs, printers or AppleTVs today have 5G modems, these devices would need to be upgraded. I don’t believe many enterprises would be willing to pay this additional cost and upgrade most of their equipment for an unclear benefit.
|
||||
|
||||
### Are economics a factor in the 5G versus Wi-Fi debate?
|
||||
|
||||
**Lipton:** Economics is always a factor. Let’s focus the conversation on in-building enterprise applications, since this is the use case some carriers intend to target with 5G. We’ve already mentioned that upgrading to 5G would require enterprises to deploy expensive DAS or small-cell systems for in-building coverage, upgrade virtually all of their equipment to contain 5G modems, and pay service contracts for each of these devices. It’s also important to understand 5G cellular networks and DAS systems operate over licensed spectrum, which is analogous to a private highway. Service providers paid billions of dollars for this spectrum, and this expense needs to be monetized and embedded in service costs. So, from both deployment and lifecycle perspectives, Wi-Fi economics are favorable to 5G.
|
||||
|
||||
### Are there any security implications of 5G versus Wi-Fi?
|
||||
|
||||
**Lipton:** Cellular technologies are perceived by some to be more secure than Wi-Fi, but that’s not true. LTE is relatively secure, but it also has weak points. For example, LTE is vulnerable to a range of attacks, including data interception and device tracking, according to researchers at Purdue and the University of Iowa. 5G improves upon LTE security with multiple authentication methods and better key management.
|
||||
|
||||
Wi-Fi security isn’t standing still either and continues to advance. Of course, Wi-Fi implementations that do not follow best practices, such as those without even basic password protection, are not optimal. But those configured with proper access controls and passwords are highly secure. With new standards — specifically, WPA3 and Enhanced Open — Wi-Fi network security has improved even further.
|
||||
|
||||
It’s also important to keep in mind that enterprises have made enormous investments in security and compliance solutions tailored to their specific needs. With cellular networks, including 5G, enterprises lose the ability to deploy their chosen security and compliance solutions, as well as most visibility into traffic flows. While future versions of 5G will offer high-levels of customization with a feature called network slicing, enterprises would still lose the level of security and compliance customization they currently need and have.
|
||||
|
||||
### Any parting thoughts to add to the discussion around 5G versus Wi-Fi?
|
||||
|
||||
**Lipton:** The debate around Wi-Fi versus 5G misses the point. They each have their place, and they are in many ways complementary. The Wi-Fi and 5G markets both will grow, driven by the need to connect and analyze a growing number of things. If a customer needs macro coverage or high-speed handoffs and can pay the additional cost for these capabilities, 5G makes sense.
|
||||
|
||||
5G also could be a fit for certain industrial use cases where customers require physical network segmentation. But for the vast majority of enterprise customers, Wi-Fi will continue to prove its value as a reliable, secure, and cost-effective wireless access technology, as it does today.
|
||||
|
||||
**More about 802.11ax (Wi-Fi 6):**
|
||||
|
||||
* [Why 802.11ax is the next big thing in wireless][7]
|
||||
* [FAQ: 802.11ax Wi-Fi][8]
|
||||
* [Wi-Fi 6 (802.11ax) is coming to a router near you][9]
|
||||
* [Wi-Fi 6 with OFDMA opens a world of new wireless possibilities][10]
|
||||
* [802.11ax preview: Access points and routers that support Wi-Fi 6 are on tap][11]
|
||||
|
||||
|
||||
|
||||
Join the Network World communities on [Facebook][12] and [LinkedIn][13] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3399978/5g-will-augment-wi-fi-not-replace-it.html
|
||||
|
||||
作者:[Zeus Kerravala][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Zeus-Kerravala/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://images.idgesg.net/images/article/2019/05/wireless_connection_speed_connectivity_bars_cell_tower_5g_by_thinkstock-100796921-large.jpg
|
||||
[2]: https://www.networkworld.com/article/3203489/what-is-5g-how-is-it-better-than-4g.html
|
||||
[3]: https://www.networkworld.com/article/3354477/mobile-world-congress-the-time-of-5g-is-almost-here.html
|
||||
[4]: https://images.idgesg.net/images/article/2019/06/headshot_jlipton_aruba-100798360-small.jpg
|
||||
[5]: https://www.networkworld.com/article/3215907/why-80211ax-is-the-next-big-thing-in-wi-fi.html
|
||||
[6]: https://pluralsight.pxf.io/c/321564/424552/7490?u=https%3A%2F%2Fwww.pluralsight.com%2Fcourses%2Fmobile-device-management-big-picture
|
||||
[7]: https://www.networkworld.com/article/3215907/mobile-wireless/why-80211ax-is-the-next-big-thing-in-wi-fi.html
|
||||
[8]: https://%20https//www.networkworld.com/article/3048196/mobile-wireless/faq-802-11ax-wi-fi.html
|
||||
[9]: https://www.networkworld.com/article/3311921/mobile-wireless/wi-fi-6-is-coming-to-a-router-near-you.html
|
||||
[10]: https://www.networkworld.com/article/3332018/wi-fi/wi-fi-6-with-ofdma-opens-a-world-of-new-wireless-possibilities.html
|
||||
[11]: https://www.networkworld.com/article/3309439/mobile-wireless/80211ax-preview-access-points-and-routers-that-support-the-wi-fi-6-protocol-on-tap.html
|
||||
[12]: https://www.facebook.com/NetworkWorld/
|
||||
[13]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,99 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Tempered Networks simplifies secure network connectivity and microsegmentation)
|
||||
[#]: via: (https://www.networkworld.com/article/3405853/tempered-networks-simplifies-secure-network-connectivity-and-microsegmentation.html)
|
||||
[#]: author: (Linda Musthaler https://www.networkworld.com/author/Linda-Musthaler/)
|
||||
|
||||
Tempered Networks simplifies secure network connectivity and microsegmentation
|
||||
======
|
||||
Tempered Networks’ Identity Defined Network platform uses the Host Identity Protocol to partition and isolate the network into trusted microsegments, providing an easy and cost-effective way to secure the network.
|
||||
![Thinkstock][1]
|
||||
|
||||
The TCP/IP protocol is the foundation of the internet and pretty much every single network out there. The protocol was designed 45 years ago and was originally only created for connectivity. There’s nothing in the protocol for security, mobility, or trusted authentication.
|
||||
|
||||
The fundamental problem with TCP/IP is that the IP address within the protocol represents both the device location and the device identity on a network. This dual functionality of the address lacks the basic mechanisms for security and mobility of devices on a network.
|
||||
|
||||
This is one of the reasons networks are so complicated today. To connect to things on a network or over the internet, you need VPNs, firewalls, routers, cell modems, etc. and you have all the configurations that come with ACLs, VLANs, certificates, and so on. The nightmare grows exponentially when you factor in internet of things (IoT) device connectivity and security. It’s all unsustainable at scale.
|
||||
|
||||
Clearly, we need a more efficient and effective way to take on network connectivity, mobility, and security.
|
||||
|
||||
**[ Also read: [What is microsegmentation? How getting granular improves network security][2] | Get regularly scheduled insights: [Sign up for Network World newsletters][3] ]**
|
||||
|
||||
The Internet Engineering Task Force (IETF) tackled this problem with the Host Identity Protocol (HIP). It provides a method of separating the endpoint identifier and the locator roles of IP addresses. It introduces a new Host Identity (HI) name space, based on public keys, from which endpoint identifiers are taken. HIP uses existing IP addressing and forwarding for locators and packet delivery.The protocol is compatible with IPv4 and IPv6 applications and utilizes a customized IPsec tunnel mode for confidentiality, authentication, and integrity of network applications.
|
||||
|
||||
Ratified by IETF in 2015, HIP represents a new security networking layer within the OSI stack. Think of it as Layer 3.5. It’s a flip of the trust model where TCP/IP is inherently promiscuous and will answer to anything that wants to talk to a device on that network. In contrast, HIP is a trust protocol that will not answer to anything on the network unless that connection has been authenticated and authorized based on its cryptographic identity. It is, in effect, a form of a [software-defined perimeter][4] around specific network resources. This is also known as [microsegmentation][5].
|
||||
|
||||
![][6]
|
||||
|
||||
### Tempered Networks’ IDN platform creates segmented, encrypted network
|
||||
|
||||
[Tempered Networks][7] has created a platform utilizing the HIP and a variety of technologies that partitions and isolates the network into trusted microsegments. Tempered Networks’ Identity Defined Networking (IDN) platform is deployed as an overlay technology that layers on top of any IP network. The HIP was designed to be both forward and backward compatible with any IP network without having to make any changes to the underlay network. The overlay network creates a direct tunnel between the two things you want to connect.
|
||||
|
||||
**[ [Prepare to become a Certified Information Security Systems Professional with this comprehensive online course from PluralSight. Now offering a 10-day free trial!][8] ]**
|
||||
|
||||
The IDN platform uses three components to create a segmented and encrypted network: an orchestration engine called the Conductor, the HIPrelay identity-based router, and HIP Services enforcement points.
|
||||
|
||||
The Conductor is a centralized orchestration and intelligence engine that connects, protects, and disconnects any resource globally through a single pane of glass. The Conductor is used to define and enforce policies for HIP Services. Policy configuration is done in a simple point-and-click manner. The Conductor is available as a physical or virtual appliance or in the Amazon Web Services (AWS) cloud.
|
||||
|
||||
HIP Services provide software-based policy enforcement, enabling secure connectivity among IDN-protected devices, as well as cloaking, segmentation, identity-based routing, and IP mobility. They can be deployed on or in-line to any device or system and come in the form of HIPswitch hardware, HIPserver, HIPclient, Cloud HIPswitch, or Virtual HIPswitch. HIP Services also can be embedded in customer hardware or applications.
|
||||
|
||||
Placing HIPswitches in front of any connected device renders the device HIP-enabled and immediately microsegments the traffic, isolating inbound and outbound traffic from the underlying network. HIPswitches deployed on the network automatically register with the Conductor using their cryptographic identity.
|
||||
|
||||
HIPrelay works with the HIP Service-enabled endpoints to deliver peer-to-peer connectivity for any device or system across all networks and transport options. Rather than using Layer 3 or 4 rule sets or traditional routing protocols, HIPrelay routes and connects encrypted communications based on provable cryptographic identities traversing existing infrastructure.
|
||||
|
||||
It sounds complicated, but it really isn’t. A use case example should demonstrate the ease and power of this solution.
|
||||
|
||||
### Use case: Smart Ships
|
||||
|
||||
An international cruise line recently installed Tempered Networks’ IDN solution to provide tighter security around its critical maritime systems. Prior to deployment, the systems for fuel, propulsion, navigation, ballast, weather, and incinerators were on a flat Layer 2 network, which basically allowed authorized users of the network to see everything.
|
||||
|
||||
Given that vendors of the different maritime systems had access to their own system, the lack of microsegmentation allowed them to see the other systems as well. The cruise line needed a simple way to segment access to these different systems — isolating them from each other — and they wanted to do it without having to put the ships in dry dock for the network reconfiguration.
|
||||
|
||||
The original configuration looked like this:
|
||||
|
||||
![][9]
|
||||
|
||||
The company implemented microsegmentation of the network based on the functionality of the systems. This isolated and segmented vendor access to only their own systems — everything else was hidden to them. The implementation involved installing HIPrelay identity routing in the cloud, several HIPswitch wireless devices onboard the ships, and HIPclient software on the vendors’ and crew members’ devices. The Conductor appliance that managed the entire deployment was installed in AWS.
|
||||
|
||||
All of that was done without impacting the underlying network, and no dry dock time was required for the deployment. In addition, the cruise line was able to eliminate internal firewalls and VPNs that had previously been used for segmentation and remote access. The resulting configuration looks like this:
|
||||
|
||||
![][10]
|
||||
|
||||
The color coding of the illustration above indicates what systems are now able to directly see and communicate with their corresponding controllers and sensors. Everything else on the network is hidden from view of those systems.
|
||||
|
||||
The acquisition cost of the Tempered Networks’ solution was one-tenth that of a traditional microsegmentation solution. The deployment time was 2 FTE days per ship compared to the 40 FTE days a traditional solution would have needed. No additional staffing was required to support the solution, and no changes were made to the underlying network.
|
||||
|
||||
### A time-tested microsegmentation solution
|
||||
|
||||
This technology came out of Boeing and was deployed for over 12 years within their manufacturing facilities until 2014, when Boeing allowed the technology to become commercialized. Tempered Networks took the HIP and developed the full platform with easy, centralized management. It was purpose-built to provide secure connectivity to networks. The solution has been successfully deployed in industrial domains such as the utilities sector, oil and gas, electricity generation, and aircraft manufacturing, as well as in enterprise domains and healthcare.
|
||||
|
||||
Join the Network World communities on [Facebook][11] and [LinkedIn][12] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3405853/tempered-networks-simplifies-secure-network-connectivity-and-microsegmentation.html
|
||||
|
||||
作者:[Linda Musthaler][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Linda-Musthaler/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://images.idgesg.net/images/article/2018/01/network_security_hacker_virus_crime-100745979-large.jpg
|
||||
[2]: https://www.networkworld.com/article/3236448/lan-wan/what-to-consider-when-deploying-a-next-generation-firewall.html
|
||||
[3]: https://www.networkworld.com/newsletters/signup.html
|
||||
[4]: https://www.networkworld.com/article/3359363/software-defined-perimeter-brings-trusted-access-to-multi-cloud-applications-network-resources.html
|
||||
[5]: https://www.networkworld.com/article/3247672/what-is-microsegmentation-how-getting-granular-improves-network-security.html
|
||||
[6]: https://images.idgesg.net/images/article/2019/07/hip-slide-100800735-large.jpg
|
||||
[7]: https://www.temperednetworks.com/
|
||||
[8]: https://pluralsight.pxf.io/c/321564/424552/7490?u=https%3A%2F%2Fwww.pluralsight.com%2Fpaths%2Fcertified-information-systems-security-professional-cisspr
|
||||
[9]: https://images.idgesg.net/images/article/2019/07/cruise-ship-before-100800736-large.jpg
|
||||
[10]: https://images.idgesg.net/images/article/2019/07/cruise-ship-after-100800738-large.jpg
|
||||
[11]: https://www.facebook.com/NetworkWorld/
|
||||
[12]: https://www.linkedin.com/company/network-world
|
||||
@ -0,0 +1,49 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (SD-WAN Buyers Should Think Application Performance as well as Resiliency)
|
||||
[#]: via: (https://www.networkworld.com/article/3406456/sd-wan-buyers-should-think-application-performance-as-well-as-resiliency.html)
|
||||
[#]: author: (Zeus Kerravala https://www.networkworld.com/author/Zeus-Kerravala/)
|
||||
|
||||
SD-WAN Buyers Should Think Application Performance as well as Resiliency
|
||||
======
|
||||
|
||||
![istock][1]
|
||||
|
||||
As an industry analyst, not since the days of WAN Optimization have I seen a technology gain as much interest as I am seeing with [SD-WANs][2] today. Although full deployments are still limited, nearly every network manager, and often many IT leaders I talk to, are interested in it. The reason for this is two-fold – the WAN has grown in importance for cloud-first enterprises and is badly in need of an overhaul. This hasn’t gone unnoticed by the vendor community as there has been an explosion of companies bringing a broad range of SD-WAN offerings to market. The great news for buyers is that there is no shortage of choices. The bad news is there are too many choices and making the right decision difficult.
|
||||
|
||||
One area of differentiation for SD-WAN vendors is how they handle application performance. I think of the SD-WAN market as being split into two categories – basic and advanced SD-WANs. A good analogy is to think of the virtualization market. There are many vendors that offer hypervisors – in fact there are a number of free ones. So why do companies pay a premium for VMware? It’s because VMware offers many advanced features and capabilities that make its solution do more than just virtualize servers.
|
||||
|
||||
Similarly, basic SD-WAN solutions do a great job of helping to lower costs and to increase application resiliency through path selection capabilities but do nothing to improve application performance. One myth that needs busting is that all SD-WANs make your applications perform better. That’s simply not true as application availability and performance are two different things. It’s possible to have great performance and poor availability or high availability with lackluster performance.
|
||||
|
||||
Consider the case where a business runs a hybrid WAN and voice and video traffic is sent over the MPLS connection and broadband is used for other traffic. If the MPLS link becomes congested, but doesn’t go down, most SD-WAN solutions will continue to send video and voice over it, which obviously degrades the performance. If multiple broadband connections are used, the chances of congestion related issues are even more likely.
|
||||
|
||||
This is an important point for IT professionals to understand. The business justification for SD-WAN was initially built around saving money but if application performance suffers, the entire return on investment (ROI) for the project might as well be tossed out the window. For many companies, the network is the business, so a poor performing network means equally poor performing applications which results lost productivity, lower revenues and possibly brand damage from customer experience issues.
|
||||
|
||||
I’ve talked to many organizations that had digital initiatives fail because the network wasn’t transformed. For example, a luxury retailer implemented a tablet program for in store personnel to be able to show merchandise to customers. High end retail is almost wholly impulse purchases so the more inventory that can be shown to a customer, the larger the resulting sales. The WAN that was in place was causing the mobile application to perform poorly causing the digital initiative to have a negative effect. Instead of driving sales, the mobile initiative was chasing customers from the store. The idea was right but the poor performing WAN caused the project to fail.
|
||||
|
||||
SD-WAN decision makers need to look to suppliers that have specific technologies integrated into it that can act when congestion occurs. A great example of this is the Silver Peak [Unity EdgeConnect™][3] SD-WAN edge platform with [path conditioning][4], [traffic shaping][5] and sub-second link failover. This ensures the best possible quality for all critical applications, even when an underlying link experiences congestion or an outage, even for [voice and video over broadband][6]. This is a foundational component of advanced SD-WAN providers as they offer the same resiliency and cost benefits as a basic SD-WAN but also ensure application performance remains high.
|
||||
|
||||
The SD-WAN era is here, and organizations should be aggressive with deployments as it will transform the WAN and make it a digital transformation enabler. Decision makers should choose their provider carefully and ensure the vendor also improves application performance. Without it, the digital initiatives will likely fail and negate any ROI the company was hoping to realize.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3406456/sd-wan-buyers-should-think-application-performance-as-well-as-resiliency.html
|
||||
|
||||
作者:[Zeus Kerravala][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Zeus-Kerravala/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://images.idgesg.net/images/article/2019/07/istock-157647179-100800860-large.jpg
|
||||
[2]: https://www.silver-peak.com/sd-wan/sd-wan-explained
|
||||
[3]: https://www.silver-peak.com/products/unity-edge-connect
|
||||
[4]: https://www.silver-peak.com/products/unity-edge-connect/path-conditioning
|
||||
[5]: https://www.silver-peak.com/products-solutions/unity/traffic-shaping
|
||||
[6]: https://www.silver-peak.com/sd-wan/voice-video-over-broadband
|
||||
@ -0,0 +1,92 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (An eco-friendly internet of disposable things is coming)
|
||||
[#]: via: (https://www.networkworld.com/article/3406462/an-eco-friendly-internet-of-disposable-things-is-coming.html)
|
||||
[#]: author: (Patrick Nelson https://www.networkworld.com/author/Patrick-Nelson/)
|
||||
|
||||
An eco-friendly internet of disposable things is coming
|
||||
======
|
||||
Researchers are creating a non-hazardous, bacteria-powered miniature battery that can be implanted into shipping labels and packaging to monitor temperature and track packages in real time.
|
||||
![Thinkstock][1]
|
||||
|
||||
Get ready for a future of disposable of internet of things (IoT) devices, one that will mean everything is connected to networks. It will be particularly useful in logistics, being used in single-use plastics in retail packaging and throw-away shippers’ carboard boxes.
|
||||
|
||||
How it will happen? The answer is when non-hazardous, disposable bio-batteries make it possible. And that moment might be approaching. Researchers say they’re closer to commercializing a bacteria-powered miniature battery that they say will propel the IoDT.
|
||||
|
||||
**[ Learn more: [Download a PDF bundle of five essential articles about IoT in the enterprise][2] ]**
|
||||
|
||||
The “internet of disposable things is a new paradigm for the rapid evolution of wireless sensor networks,” says Seokheun Choi, an associate professor at Binghamton University, [in an article on the school’s website][3].
|
||||
|
||||
“Current IoDTs are mostly powered by expensive and environmentally hazardous batteries,” he says. Those costs can be significant in any kind of large-scale deployment, he says. And furthermore, with exponential growth, the environmental concerns would escalate rapidly.
|
||||
|
||||
The miniaturized battery that Choi’s team has come up with is uniquely charged through power created by bacteria. It doesn’t have metals and acids in it. And it’s designed specifically to provide energy to sensors and radios in single-use IoT devices. Those could be the kinds of sensors ideal for supply-chain logistics where the container is ultimately going to end up in a landfill, creating a hazard.
|
||||
|
||||
Another use case is real-time analysis of packaged food, with sensors monitoring temperature and location, preventing spoilage and providing safer food handling. For example, a farm product could be tracked for on-time delivery, as well as have its temperature measured, all within the packaging, as it moves from packaging facility to consumer. In the event of a food-borne illness outbreak, say, one can quickly find out where the product originated—which apparently is hard to do now.
|
||||
|
||||
Other use cases could be battery-impregnated shipping labels that send real-time data to the internet. Importantly, in both use cases, packaging can be discarded without added environmental concerns.
|
||||
|
||||
### How the bacteria-powered batteries work
|
||||
|
||||
A slow release of nutrients provide the energy to the bacteria-powered batteries, which the researchers say can last up to eight days. “Slow and continuous reactions” convert the microbial nutrients into “long standing power,” they say in [their paper's abstract][4].
|
||||
|
||||
“Our biobattery is low-cost, disposable, and environmentally-friendly,” Choi says.
|
||||
|
||||
Origami, the Japanese paper-folding skill used to create objects, was an inspiration for a similar microbial-based battery project the group wrote about last year in a paper. This one is liquid-based and not as long lasting. A bacteria-containing liquid was absorbed along the porous creases in folded paper, creating the paper-delivered power source, perhaps to be used in a shipping label.
|
||||
|
||||
“Low-cost microbial fuel cells (MFCs) can be done efficiently by using a paper substrate and origami techniques,” [the group wrote then][5].
|
||||
|
||||
Scientists, too, envisage electronics now printed on circuit boards (PCBs) and can be toxic on disposal being printed entirely on eco-friendly paper. Product cycles, such as those found now in mobile devices and likely in future IoT devices, are continually getting tighter—thus PCBs are increasingly being disposed. Solutions are needed, experts say.
|
||||
|
||||
Put the battery in the paper, too, is the argument here. And while you’re at it, get the biodegradation of the used-up biobattery to help break-down the organic-matter paper.
|
||||
|
||||
Ultimately, Choi believes that the power-creating bacteria could even be introduced naturally by the environment—right now it’s added on by the scientists.
|
||||
|
||||
**More on IoT:**
|
||||
|
||||
* [What is the IoT? How the internet of things works][6]
|
||||
* [What is edge computing and how it’s changing the network][7]
|
||||
* [Most powerful Internet of Things companies][8]
|
||||
* [10 Hot IoT startups to watch][9]
|
||||
* [The 6 ways to make money in IoT][10]
|
||||
* [What is digital twin technology? [and why it matters]][11]
|
||||
* [Blockchain, service-centric networking key to IoT success][12]
|
||||
* [Getting grounded in IoT networking and security][2]
|
||||
* [Building IoT-ready networks must become a priority][13]
|
||||
* [What is the Industrial IoT? [And why the stakes are so high]][14]
|
||||
|
||||
|
||||
|
||||
Join the Network World communities on [Facebook][15] and [LinkedIn][16] to comment on topics that are top of mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.networkworld.com/article/3406462/an-eco-friendly-internet-of-disposable-things-is-coming.html
|
||||
|
||||
作者:[Patrick Nelson][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.networkworld.com/author/Patrick-Nelson/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://images.techhive.com/images/article/2017/04/green-data-center-intro-100719502-large.jpg
|
||||
[2]: https://www.networkworld.com/article/3269736/internet-of-things/getting-grounded-in-iot-networking-and-security.html
|
||||
[3]: https://www.binghamton.edu/news/story/1867/everything-will-connect-to-the-internet-someday-and-this-biobattery-could-h
|
||||
[4]: https://www.sciencedirect.com/science/article/abs/pii/S0378775319305580
|
||||
[5]: https://www.sciencedirect.com/science/article/pii/S0960148117311606
|
||||
[6]: https://www.networkworld.com/article/3207535/internet-of-things/what-is-the-iot-how-the-internet-of-things-works.html
|
||||
[7]: https://www.networkworld.com/article/3224893/internet-of-things/what-is-edge-computing-and-how-it-s-changing-the-network.html
|
||||
[8]: https://www.networkworld.com/article/2287045/internet-of-things/wireless-153629-10-most-powerful-internet-of-things-companies.html
|
||||
[9]: https://www.networkworld.com/article/3270961/internet-of-things/10-hot-iot-startups-to-watch.html
|
||||
[10]: https://www.networkworld.com/article/3279346/internet-of-things/the-6-ways-to-make-money-in-iot.html
|
||||
[11]: https://www.networkworld.com/article/3280225/internet-of-things/what-is-digital-twin-technology-and-why-it-matters.html
|
||||
[12]: https://www.networkworld.com/article/3276313/internet-of-things/blockchain-service-centric-networking-key-to-iot-success.html
|
||||
[13]: https://www.networkworld.com/article/3276304/internet-of-things/building-iot-ready-networks-must-become-a-priority.html
|
||||
[14]: https://www.networkworld.com/article/3243928/internet-of-things/what-is-the-industrial-iot-and-why-the-stakes-are-so-high.html
|
||||
[15]: https://www.facebook.com/NetworkWorld/
|
||||
[16]: https://www.linkedin.com/company/network-world
|
||||
@ -1,121 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (4 cool terminal multiplexers)
|
||||
[#]: via: (https://fedoramagazine.org/4-cool-terminal-multiplexers/)
|
||||
[#]: author: (Paul W. Frields https://fedoramagazine.org/author/pfrields/)
|
||||
|
||||
4 cool terminal multiplexers
|
||||
======
|
||||
|
||||
![][1]
|
||||
|
||||
The Fedora OS is comfortable and easy for lots of users. It has a stunning desktop that makes it easy to get everyday tasks done. Under the hood is all the power of a Linux system, and the terminal is the easiest way for power users to harness it. By default terminals are simple and somewhat limited. However, a _terminal multiplexer_ allows you to turn your terminal into an even more incredible powerhouse. This article shows off some popular terminal multiplexers and how to install them.
|
||||
|
||||
Why would you want to use one? Well, for one thing, it lets you logout of your system while _leaving your terminal session undisturbed_. It’s incredibly useful to logout of your console, secure it, travel somewhere else, then remotely login with SSH and continue where you left off. Here are some utilities to check out.
|
||||
|
||||
One of the oldest and most well-known terminal multiplexers is _screen._ However, because the code is no longer maintained, this article focuses on more recent apps. (“Recent” is relative — some of these have been around for years!)
|
||||
|
||||
### Tmux
|
||||
|
||||
The _tmux_ utility is one of the most widely used replacements for _screen._ It has a highly configurable interface. You can program tmux to start up specific kinds of sessions based on your needs. You’ll find a lot more about tmux in this article published earlier:
|
||||
|
||||
> [Use tmux for a more powerful terminal][2]
|
||||
|
||||
Already a tmux user? You might like [this additional article on making your tmux sessions more effective][3].
|
||||
|
||||
To install tmux, use the _sudo_ command along with _dnf_ , since you’re probably in a terminal already:
|
||||
|
||||
```
|
||||
$ sudo dnf install tmux
|
||||
```
|
||||
|
||||
To start learning, run the _tmux_ command. A single pane window starts with your default shell. Tmux uses a _modifier key_ to signal that a command is coming next. This key is **Ctrl+B** by default. If you enter **Ctrl+B, C** you’ll create a new window with a shell in it.
|
||||
|
||||
Here’s a hint: Use **Ctrl+B, ?** to enter a help mode that lists all the keys you can use. To keep things simple, look for the lines starting with _bind-key -T prefix_ at first. These are keys you can use right after the modifier key to configure your tmux session. You can hit **Ctrl+C** to exit the help mode back to tmux.
|
||||
|
||||
To completely exit tmux, use the standard _exit_ command or _Ctrl+D_ keystroke to exit all the shells.
|
||||
|
||||
### Dvtm
|
||||
|
||||
You might have recently seen the Magazine article on [dwm, a dynamic window manager][4]. Like dwm, _dvtm_ is for tiling window management — but in a terminal. It’s designed to adhere to the legacy UNIX philosophy of “do one thing well” — in this case managing windows in a terminal.
|
||||
|
||||
Installing dvtm is easy as well. However, if you want the logout functionality mentioned earlier, you’ll also need the _abduco_ package which handles session management for dvtm.
|
||||
|
||||
```
|
||||
$ sudo dnf install dvtm abduco
|
||||
```
|
||||
|
||||
The dvtm utility has many keystrokes already mapped to allow you to manage windows in the terminal. By default, it uses **Ctrl+G** as its modifier key. This keystroke tells dvtm that the following character is going to be a command it should process. For instance, **Ctrl+G, C** creates a new window and **Ctrl+G, X** removes it.
|
||||
|
||||
For more information on using dvtm, check out the dvtm [home page][5] which includes numerous tips and get-started information.
|
||||
|
||||
### Byobu
|
||||
|
||||
While _byobu_ isn’t truly a multiplexer on its own — it wraps _tmux_ or even the older _screen_ to add functions — it’s worth covering here too. Byobu makes terminal multiplexers better for novices, by adding a help menu and window tabs that are slightly easier to navigate.
|
||||
|
||||
Of course it’s available in the Fedora repos as well. To install, use this command:
|
||||
|
||||
```
|
||||
$ sudo dnf install byobu
|
||||
```
|
||||
|
||||
By default the _byobu_ command runs _screen_ underneath, so you might want to run _byobu-tmux_ to wrap _tmux_ instead. You can then use the **F9** key to open up a help menu for more information to help you get started.
|
||||
|
||||
### Mtm
|
||||
|
||||
The _mtm_ utility is one of the smallest multiplexers you’ll find. In fact, it’s only about 1000 lines of code! You might find it helpful if you’re in a limited environment such as old hardware, a minimal container, and so forth. To get started, you’ll need a couple packages.
|
||||
|
||||
```
|
||||
$ sudo dnf install git ncurses-devel make gcc
|
||||
```
|
||||
|
||||
Then clone the repository where mtm lives:
|
||||
|
||||
```
|
||||
$ git clone https://github.com/deadpixi/mtm.git
|
||||
```
|
||||
|
||||
Change directory into the _mtm_ folder and build the program:
|
||||
|
||||
```
|
||||
$ make
|
||||
```
|
||||
|
||||
You might receive a few warnings, but when you’re done, you’ll have the very small _mtm_ utility. Run it with this command:
|
||||
|
||||
```
|
||||
$ ./mtm
|
||||
```
|
||||
|
||||
You can find all the documentation for the utility [on its GitHub page][6].
|
||||
|
||||
These are just some of the terminal multiplexers out there. Got one you’d like to recommend? Leave a comment below with your tips and enjoy building windows in your terminal!
|
||||
|
||||
* * *
|
||||
|
||||
_Photo by _[ _Michael_][7]_ on [Unsplash][8]._
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/4-cool-terminal-multiplexers/
|
||||
|
||||
作者:[Paul W. Frields][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fedoramagazine.org/author/pfrields/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://fedoramagazine.org/wp-content/uploads/2018/08/tmuxers-4-816x345.jpg
|
||||
[2]: https://fedoramagazine.org/use-tmux-more-powerful-terminal/
|
||||
[3]: https://fedoramagazine.org/4-tips-better-tmux-sessions/
|
||||
[4]: https://fedoramagazine.org/lets-try-dwm-dynamic-window-manger/
|
||||
[5]: http://www.brain-dump.org/projects/dvtm/#why
|
||||
[6]: https://github.com/deadpixi/mtm
|
||||
[7]: https://unsplash.com/photos/48yI_ZyzuLo?utm_source=unsplash&utm_medium=referral&utm_content=creditCopyText
|
||||
[8]: https://unsplash.com/search/photos/windows?utm_source=unsplash&utm_medium=referral&utm_content=creditCopyText
|
||||
@ -1,106 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Blockchain 2.0 – Public Vs Private Blockchain Comparison [Part 7])
|
||||
[#]: via: (https://www.ostechnix.com/blockchain-2-0-public-vs-private-blockchain-comparison/)
|
||||
[#]: author: (editor https://www.ostechnix.com/author/editor/)
|
||||
|
||||
Blockchain 2.0 – Public Vs Private Blockchain Comparison [Part 7]
|
||||
======
|
||||
|
||||
![Public vs Private blockchain][1]
|
||||
|
||||
The previous part of the [**Blockchain 2.0**][2] series explored the [**the state of Smart contracts**][3] now. This post intends to throw some light on the different types of blockchains that can be created. Each of these are used for vastly different applications and depending on the use cases, the protocol followed by each of these differ. Now let us go ahead and learn about **Public vs Private blockchain comparison** with Open source and proprietary technology.
|
||||
|
||||
The fundamental three-layer structure of a blockchain based distributed ledger as we know is as follows:
|
||||
|
||||
![][4]
|
||||
|
||||
Figure 1 – Fundamental structure of Blockchain-based ledgers
|
||||
|
||||
The differences between the types mentioned here is attributable primarily to the protocol that rests on the underlying blockchain. The protocol dictates rules for the participants and the behavior of the blockchain in response to the said participation.
|
||||
|
||||
Remember to keep the following things in mind while reading through this article:
|
||||
|
||||
* Platforms such as these are always created to solve a use-case requirement. There is no one direction that the technology should take that is best. Blockchains for instance have tremendous applications and some of these might require dropping features that seem significant in other settings. **Decentralized storage** is a major example in this regard.
|
||||
* Blockchains are basically database systems keeping track of information by timestamping and organizing data in the form of blocks. Creators of such blockchains can choose who has the right to make these blocks and perform alterations.
|
||||
* Blockchains can be “centralized” as well, and participation in varying extents can be limited to those who this “central authority” deems eligible.
|
||||
|
||||
|
||||
|
||||
Most blockchains are either **public** or **private**. Broadly speaking, public blockchains can be considered as being the equivalent of open source software and most private blockchains can be seen as proprietary platforms deriving from the public ones. The figure below should make the basic difference obvious to most of you.
|
||||
|
||||
![][5]
|
||||
|
||||
Figure 2 – Public vs Private blockchain comparison with Open source and Proprietary Technology
|
||||
|
||||
This is not to say that all private blockchains are derived from open public ones. The most popular ones however usually are though.
|
||||
|
||||
### Public Blockchains
|
||||
|
||||
A public blockchain can be considered as a **permission-less platform** or **network**. Anyone with the knowhow and computing resources can participate in it. This will have the following implications:
|
||||
|
||||
* Anyone can join and participate in a public blockchain network. All the “participant” needs is a stable internet connection along with computing resources.
|
||||
* Participation will include reading, writing, verifying, and providing consensus during transactions. An example for participating individuals would be **Bitcoin miners**. In exchange for participating in the network the miners are paid back in Bitcoins in this case.
|
||||
* The platform is decentralized completely and fully redundant.
|
||||
* Because of the decentralized nature, no one entity has complete control over the data recorded in the ledger. To validate a block all (or most) participants need to vet the data.
|
||||
* This means that once information is verified and recorded, it cannot be altered easily. Even if it is, its impossible to not leave marks.
|
||||
* The identity of participants remains anonymous by design in platforms such as **BITCOIN** and **LITECOIN**. These platforms by design aim for protecting and securing user identities. This is primarily a feature provided by the overlying protocol stack.
|
||||
* Examples for public blockchain networks are **BITCOIN** , **LITECOIN** , **ETHEREUM** etc.
|
||||
* Extensive decentralizations mean that gaining consensus on transactions might take a while compared to what is typically possible over blockchain ledger networks and throughput can be a challenge for large enterprises aiming for pushing a very high number of transactions every instant.
|
||||
* The open participation and often the high number of such participants in open chains such as bitcoin add up to considerable initial investments in computing equipment and energy costs.
|
||||
|
||||
|
||||
|
||||
### Private Blockchain
|
||||
|
||||
In contrast, a private blockchain is a **permissioned blockchain**. Meaning:
|
||||
|
||||
* Permission to participate in the network is restricted and is presided over by the owner or institution overseeing the network. Meaning even though an individual will be able to store data and transact (send and receive payments for example), the validation and storage of these transactions will be done only by select participants.
|
||||
* Participation even once permission is given by the central authority will be limited by terms. For instance, in case of a private blockchain network run by a financial institution, not every customer will have access to the entire blockchain ledger, and even among those with the permission, not everyone will be able to access everything. Permissions to access select services will be given by the central figure in this case. This is often referred to as **“channeling”**.
|
||||
* Such systems have significantly larger throughput capabilities and also showcase much faster transaction speeds compared to their public counterparts because a block of information only needs to be validated by a select few.
|
||||
* Security by design is something the public blockchains are renowned for. They achieve this
|
||||
by:
|
||||
* Anonymizing participants,
|
||||
* Distributed & redundant but encrypted storage on multiple nodes,
|
||||
* Mass consensus required for creating and altering data.
|
||||
|
||||
|
||||
|
||||
Private blockchains usually don’t feature any of these in their protocol. This makes the system only as secure as most cloud-based database systems currently in use.
|
||||
|
||||
### A note for the wise
|
||||
|
||||
An important point to note is this, the fact that they’re named public or private (or open or closed) has nothing to do with the underlying code base. The code or the literal foundations on which the platforms are based on may or may not be publicly available and or developed in either of these cases. **R3** is a **DLT** ( **D** istributed **L** edger **T** echnology) company that leads a public consortium of over 200 multinational institutions. Their aim is to further development of blockchain and related distributed ledger technology in the domain of finance and commerce. **Corda** is the product of this joint effort. R3 defines corda as a blockchain platform that is built specially for businesses. The codebase for the same is open source and developers all over the world are encouraged to contribute to the project. However, given its business facing nature and the needs it is meant to address, corda would be categorized as a permissioned closed blockchain platform. Meaning businesses can choose the participants of the network once it is deployed and choose the kind of information these participants can access through the use of natively available smart contract tools.
|
||||
|
||||
While it is a reality that public platforms like Bitcoin and Ethereum are responsible for the widespread awareness and development going on in the space, it can still be argued that private blockchains designed for specific use cases in enterprise or business settings is what will lead monetary investments in the short run. These are the platforms most of us will see implemented the near future in practical ways.
|
||||
|
||||
Read the next guide about Hyperledger project in this series.
|
||||
|
||||
* [**Blockchain 2.0 – An Introduction To Hyperledger Project (HLP)**][6]
|
||||
|
||||
|
||||
|
||||
We are working on many interesting topics on Blockchain technology. Stay tuned!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/blockchain-2-0-public-vs-private-blockchain-comparison/
|
||||
|
||||
作者:[editor][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/editor/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.ostechnix.com/wp-content/uploads/2019/04/Public-Vs-Private-Blockchain-720x340.png
|
||||
[2]: https://www.ostechnix.com/blockchain-2-0-an-introduction/
|
||||
[3]: https://www.ostechnix.com/blockchain-2-0-ongoing-projects-the-state-of-smart-contracts-now/
|
||||
[4]: http://www.ostechnix.com/wp-content/uploads/2019/04/blockchain-architecture.png
|
||||
[5]: http://www.ostechnix.com/wp-content/uploads/2019/04/Public-vs-Private-blockchain-comparison.png
|
||||
[6]: https://www.ostechnix.com/blockchain-2-0-an-introduction-to-hyperledger-project-hlp/
|
||||
@ -1,5 +1,5 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (arrowfeng)
|
||||
[#]: translator: ( )
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
|
||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
Reference in New Issue
Block a user