mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-30 02:40:11 +08:00
一个多月没翻译了,真丧尸,==!~
This commit is contained in:
parent
d7a96cad71
commit
3f24e8fb7f
sources/tech
translated/tech
@ -1,270 +0,0 @@
|
||||
翻译ing by Luoxcat
|
||||
|
||||
Linux / Unix: chroot Command Examples
|
||||
================================================================================
|
||||
I am a new Linux and Unix user. How do I change the root directory of a command? How do I change the root directory of a process such as web-server using a chroot command to isolate file system? How do I use a chroot to recover password or fix the damaged Linux/Unix based environment?
|
||||
|
||||

|
||||
|
||||
Each process/command on Linux and Unix-like system has current working directory called root directory of a process/command. You can change the root directory of a command using `chroot` command, which ends up changing the root directory for both current running process and its children.
|
||||
|
||||
chroot command details
|
||||
Description:Change root directory
|
||||
Category:Processes Management
|
||||
Difficulty:Advanced
|
||||
Root privileges:Yes
|
||||
|
||||
A process/command that is run in such a modified environment cannot access files outside the root directory. This modified environment is commonly known as "jailed directory" or "chroot jail". Only a privileged process and root user can use chroot command. This is useful to:
|
||||
|
||||
1. Privilege separation for unprivileged process such as Web-server or DNS server.
|
||||
1. Setting up a test environment.
|
||||
1. Run old programs or ABI in-compatibility programs without crashing application or system.
|
||||
1. System recovery.
|
||||
1. Reinstall the bootloader such as Grub or Lilo.
|
||||
1. Password recovery Reset a forgotten password and more.
|
||||
|
||||
### Purpose ###
|
||||
|
||||
> The chroot command **changes its current and root directories to the provided directory and then run command**, if supplied, or an interactive copy of the user's login shell. Please note that not every application can be chrooted.
|
||||
|
||||
### Syntax ###
|
||||
|
||||
The basic syntax is as follows:
|
||||
|
||||
chroot /path/to/new/root command
|
||||
|
||||
OR
|
||||
|
||||
chroot /path/to/new/root /path/to/server
|
||||
|
||||
OR
|
||||
|
||||
chroot [options] /path/to/new/root /path/to/server
|
||||
|
||||
#### chroot command examples ####
|
||||
|
||||
In this example, build a mini-jail for testing purpose with bash and ls command only. First, set jail location using mkdir command:
|
||||
|
||||
$ J=$HOME/jail
|
||||
|
||||
Create directories inside $J:
|
||||
|
||||
$ mkdir -p $J
|
||||
$ mkdir -p $J/{bin,lib64,lib}
|
||||
$ cd $J
|
||||
|
||||
Copy /bin/bash and /bin/ls into $J/bin/ location using [cp command][1]:
|
||||
|
||||
$ cp -v /bin/{bash,ls} $J/bin
|
||||
|
||||
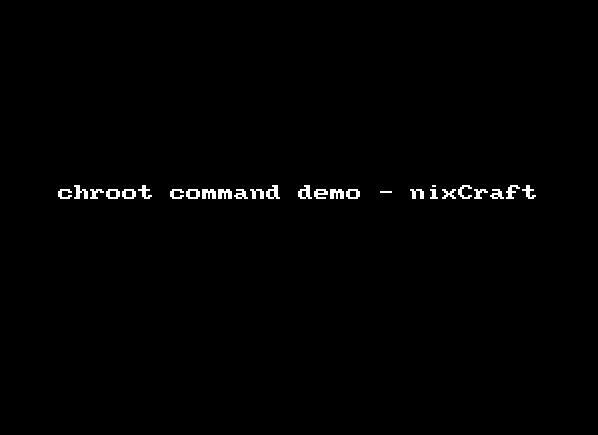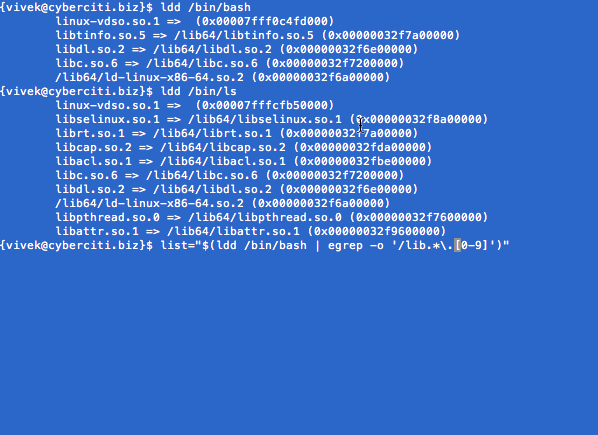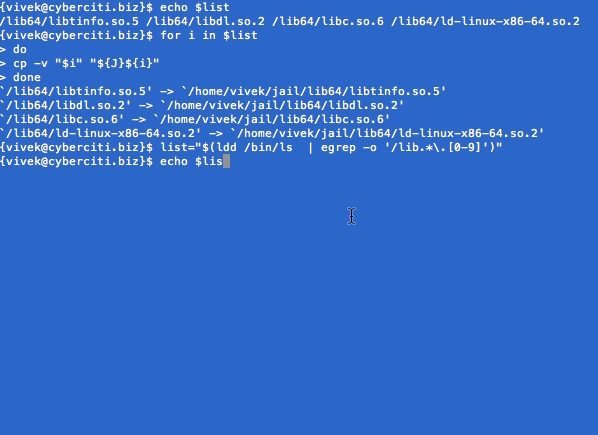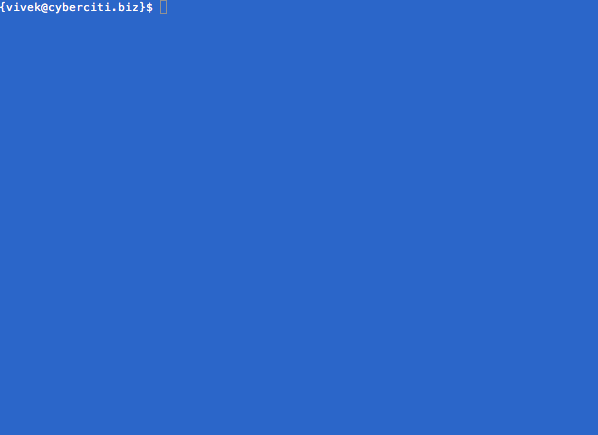
Copy required libs in $J. Use ldd command to print shared library dependencies for bash:
|
||||
|
||||
$ ldd /bin/bash
|
||||
|
||||
Sample outputs:
|
||||
|
||||
linux-vdso.so.1 => (0x00007fff8d987000)
|
||||
libtinfo.so.5 => /lib64/libtinfo.so.5 (0x00000032f7a00000)
|
||||
libdl.so.2 => /lib64/libdl.so.2 (0x00000032f6e00000)
|
||||
libc.so.6 => /lib64/libc.so.6 (0x00000032f7200000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00000032f6a00000)
|
||||
|
||||
Copy libs in $J correctly from the above output:
|
||||
|
||||
$ cp -v /lib64/libtinfo.so.5 /lib64/libdl.so.2 /lib64/libc.so.6 /lib64/ld-linux-x86-64.so.2 $J/lib64/
|
||||
|
||||
Sample outputs:
|
||||
|
||||
`/lib64/libtinfo.so.5' -> `/home/vivek/jail/lib64/libtinfo.so.5'
|
||||
`/lib64/libdl.so.2' -> `/home/vivek/jail/lib64/libdl.so.2'
|
||||
`/lib64/libc.so.6' -> `/home/vivek/jail/lib64/libc.so.6'
|
||||
`/lib64/ld-linux-x86-64.so.2' -> `/home/vivek/jail/lib64/ld-linux-x86-64.so.2'
|
||||
|
||||
Copy required libs in $J for ls command. Use ldd command to print shared library dependencies for ls command:
|
||||
|
||||
$ ldd /bin/ls
|
||||
|
||||
Sample outputs:
|
||||
|
||||
linux-vdso.so.1 => (0x00007fff68dff000)
|
||||
libselinux.so.1 => /lib64/libselinux.so.1 (0x00000032f8a00000)
|
||||
librt.so.1 => /lib64/librt.so.1 (0x00000032f7a00000)
|
||||
libcap.so.2 => /lib64/libcap.so.2 (0x00000032fda00000)
|
||||
libacl.so.1 => /lib64/libacl.so.1 (0x00000032fbe00000)
|
||||
libc.so.6 => /lib64/libc.so.6 (0x00000032f7200000)
|
||||
libdl.so.2 => /lib64/libdl.so.2 (0x00000032f6e00000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00000032f6a00000)
|
||||
libpthread.so.0 => /lib64/libpthread.so.0 (0x00000032f7600000)
|
||||
libattr.so.1 => /lib64/libattr.so.1 (0x00000032f9600000)
|
||||
|
||||
You can copy libs one-by-one or try [bash shell for loop][2] as follows:
|
||||
|
||||
list="$(ldd /bin/ls | egrep -o '/lib.*\.[0-9]')"
|
||||
for i in $list; do cp -v "$i" "${J}${i}"; done
|
||||
|
||||
Sample outputs:
|
||||
|
||||
`/lib64/libselinux.so.1' -> `/home/vivek/jail/lib64/libselinux.so.1'
|
||||
`/lib64/librt.so.1' -> `/home/vivek/jail/lib64/librt.so.1'
|
||||
`/lib64/libcap.so.2' -> `/home/vivek/jail/lib64/libcap.so.2'
|
||||
`/lib64/libacl.so.1' -> `/home/vivek/jail/lib64/libacl.so.1'
|
||||
`/lib64/libc.so.6' -> `/home/vivek/jail/lib64/libc.so.6'
|
||||
`/lib64/libdl.so.2' -> `/home/vivek/jail/lib64/libdl.so.2'
|
||||
`/lib64/ld-linux-x86-64.so.2' -> `/home/vivek/jail/lib64/ld-linux-x86-64.so.2'
|
||||
`/lib64/libpthread.so.0' -> `/home/vivek/jail/lib64/libpthread.so.0'
|
||||
`/lib64/libattr.so.1' -> `/home/vivek/jail/lib64/libattr.so.1'
|
||||
|
||||
Finally, chroot into your new jail:
|
||||
|
||||
$ sudo chroot $J /bin/bash
|
||||
|
||||
Try browsing /etc or /var:
|
||||
|
||||
# ls /
|
||||
# ls /etc/
|
||||
# ls /var/
|
||||
|
||||
A chrooted bash and ls application is locked into a particular directory called $HOME/$J and unable to wander around the rest of the directory tree, and sees that directory as its "/" (root) directory. This is a tremendous boost to security if configured properly. I usually lock down the following applications using the same techniques:
|
||||
|
||||
1. [Apache - Red Hat / CentOS: Chroot Apache 2 Web Server][3]
|
||||
1. [Nginx - Linux nginx: Chroot (Jail) Setup][4]
|
||||
1. [Chroot Lighttpd web server on a Linux based system][5]
|
||||
1. Chroot mail server.
|
||||
1. Chroot Bind DNS server and more.
|
||||
|
||||
### How do I exit from chrooted jail? ###
|
||||
|
||||
Type exit
|
||||
|
||||
$ exit
|
||||
|
||||
Sample session from above commands:
|
||||
|
||||
[][6]
|
||||
|
||||
Animated gif 01: Linux / Unix: Bash Chroot ls Command Demo
|
||||
|
||||
### Find out if service in chrooted jail or not ###
|
||||
|
||||
You can [easily find out if Postfix mail server is chrooted or not][7] using the following two commands:
|
||||
|
||||
pid=$(pidof -s master)
|
||||
ls -ld /proc/$pid/root
|
||||
|
||||
Sample outputs from my Linux based server:
|
||||
|
||||
lrwxrwxrwx. 1 root root 0 Mar 9 11:16 /proc/8613/root -> /
|
||||
|
||||
The PID 8613 pointing out to / (root) i.e. the root directory for application is not changed or chrooted. This is a quick and dirty way to find out if application is chrooted or not without opening configuration files. Here is another example from chrooted nginx server:
|
||||
|
||||
pid=$(pidof -s master)
|
||||
ls -ld /proc/$pid/root
|
||||
|
||||
Sample outputs:
|
||||
|
||||
lrwxrwxrwx 1 nginx nginx 0 Mar 9 11:17 /proc/4233/root -> /nginxjail
|
||||
|
||||
The root directory for application is changed to /nginxjail.
|
||||
|
||||
### Rescue and fix software RAID system with chroot ###
|
||||
|
||||
I'm assuming that software RAID based Linux system is not booting. So you [booted system either using the Live CD or networked based remote rescue kernel mode][8] to fix the system. In this example, I booting RHEL based system using live Linux DVD/CD and chroot into /dev/sda1 and/or /dev/md0 to fix the problem:
|
||||
|
||||
## Recover data, at live cd prompt type the following commands. ##
|
||||
## /dev/sda1 main system partition ##
|
||||
## /dev/md0 /data partition ##
|
||||
# Set jail dir
|
||||
d=/chroot
|
||||
mkdir $d
|
||||
|
||||
# Mount sda1 and required dirs
|
||||
mount /dev/sda1 $d
|
||||
mount -o bind /dev $d/dev
|
||||
mount -o bind /sys $d/sys
|
||||
mount -o bind /dev/shm $d/dev/shm
|
||||
mount -o bind /proc $d/proc
|
||||
|
||||
# Mount software raid /dev/md0
|
||||
mount /dev/md0 $d/data
|
||||
|
||||
# Chroot to our newly created jail. This allows us to fix bootloader or grab data before everything goes to /dev/null
|
||||
chroot $d
|
||||
|
||||
# Can you see?
|
||||
ls
|
||||
df
|
||||
|
||||
# Get files to safe location
|
||||
rsync -avr /path/to/my_precious_data_dir user@safe.location.cyberciti.biz:/path/to/dest
|
||||
|
||||
# Get out of chrooted jail and reboot or format the server as per your needs ;)
|
||||
exit
|
||||
umount {dev,sys,[...],}
|
||||
reboot
|
||||
|
||||
But wait, there's more!
|
||||
|
||||
See all other chroot command related examples on nixCraft:
|
||||
|
||||
1. [Ubuntu: Mount Encrypted Home Directory (~/.private) From an Ubuntu Live CD][9]
|
||||
1. [Linux Configure rssh Chroot Jail To Lock Users To Their Home Directories Only][10]
|
||||
1. [Fix a dual boot MS-Windows XP/Vista/7/Server and Linux problem][11]
|
||||
1. [Restore Debian Linux Grub boot loader][12]
|
||||
|
||||
### A note about chrooting apps on a Linux or Unix-like systems ###
|
||||
|
||||
Should you use the chroot feature all the time? In the above example, the program is fairly simple but you may end up with several different kinds of problems such as:
|
||||
|
||||
1. Missing libs in jail can result into broken jail.
|
||||
1. Complex program are difficult to chroot. I suggest you either try real [jail such as provided by FreeBSD][13] or use virtualization soultuon such as [KVM on Linux][14].
|
||||
1. App running in jail can not run any other programs, can not alter any files, and can not assume another user's identity. Loosen these restrictions, you have lessened your security, chroot or no chroot.
|
||||
|
||||
Also note that:
|
||||
|
||||
1. Do not forgot, to updated chrooted apps when you upgrade apps locally.
|
||||
1. Not every app can or should be chrooted.
|
||||
1. Any app which has to assume root privileges to operate is pointless to attempt to chroot, as root can generally escape a chroot.
|
||||
1. Chroot is not a silver bullet. Learn [how to secure and harden rest of the system too][15].
|
||||
|
||||
### chroot command options ###
|
||||
|
||||
From the [chroot(8)][16] command man page:
|
||||
|
||||
--userspec=USER:GROUP specify user and group (ID or name) to use
|
||||
--groups=G_LIST specify supplementary groups as g1,g2,..,gN
|
||||
--help display this help and exit
|
||||
--version output version information and exit
|
||||
|
||||
### See also ###
|
||||
|
||||
- [chroot(8) Linux/Unix command man page][17]
|
||||
- [Man pages chroot(2)][18]
|
||||
- [OpenBSD documentation See Apache chrooting faq for more information.][19]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via:
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.cyberciti.biz/faq/cp-copy-command-in-unix-examples/
|
||||
[2]:http://www.cyberciti.biz/faq/bash-for-loop/
|
||||
[3]:http://www.cyberciti.biz/tips/chroot-apache-under-rhel-fedora-centos-linux.html
|
||||
[4]:http://www.cyberciti.biz/faq/howto-run-nginx-in-a-chroot-jail/
|
||||
[5]:http://www.cyberciti.biz/tips/howto-setup-lighttpd-php-mysql-chrooted-jail.html
|
||||
[6]:http://www.cyberciti.biz/faq/?attachment_id=28148
|
||||
[7]:http://www.cyberciti.biz/tips/linux-chroot-service.html
|
||||
[8]:http://www.cyberciti.biz/faq/centos-rhel-linux-mount-raid-hard-disk-from-livecd/
|
||||
[9]:http://www.cyberciti.biz/faq/ubuntu-mounting-your-encrypted-home-from-livecd/
|
||||
[10]:http://www.cyberciti.biz/tips/howto-linux-unix-rssh-chroot-jail-setup.html
|
||||
[11]:http://www.cyberciti.biz/tips/howto-fix-dual-boot-windows-vista-linux.html
|
||||
[12]:http://www.cyberciti.biz/tips/restore-debian-linux-grub-boot-loader.html
|
||||
[13]:http://www.cyberciti.biz/faq/how-to-upgrade-freebsd-jail-vps/
|
||||
[14]:http://www.cyberciti.biz/faq/kvm-virtualization-in-redhat-centos-scientific-linux-6/
|
||||
[15]:http://www.cyberciti.biz/tips/linux-security.html
|
||||
[16]:http://www.manpager.com/linux/man8/chroot.8.html
|
||||
[17]:http://www.manpager.com/linux/man8/chroot.8.html
|
||||
[18]:http://www.manpager.com/linux/man2/chroot.2.html
|
||||
[19]:http://www.openbsd.org/faq/
|
||||
267
translated/tech/Linux or Unix--chroot Command Examples.md
Normal file
267
translated/tech/Linux or Unix--chroot Command Examples.md
Normal file
@ -0,0 +1,267 @@
|
||||
Linux / Unix:chroot 命令实例讲解
|
||||
================================================================================
|
||||
我是刚接触 Linux 和 Unix 的新手。我该如何改变一个命令的根目录?我要怎样改变一个进程的根目录呢,比如用 chroot 命令将web服务与文件系统隔离?我要如何使用 chroot 恢复密码或修复基于 Linux/Unix的受损坏的环境?
|
||||
|
||||

|
||||
|
||||
在 Linux和类 Unix 系统下每一个进程/命令的当前工作目录称之为进程/命令的根目录。你可以使用 chroot 命令改变一个命令的根目录,这最终将会改变当前运行的进程及其子进程的根目录。
|
||||
|
||||
chroot 命令详情
|
||||
描述:更改根目录
|
||||
类型:进程管理
|
||||
难度:高级
|
||||
Root 授权:Yes
|
||||
|
||||
如果一个进程/命令运行在一个不能访问外部根目录文件的已修改环境中。这个修改环境通常被称为"监禁目录"或是"chroot jail"。只有特权进程和根用户才能使用 chroot 命令。然而这通常是很有用的:
|
||||
|
||||
1. 将特权分配给未授权的进程,例如 Web 服务或 DNS 服务。
|
||||
1. 建立测试环境。
|
||||
1. 不使程序或系统崩溃下,运行旧程序或不兼容 ABI 的程序。
|
||||
1. 系统恢复。
|
||||
1. 重新安装引导装载程序,例如 Grub 或 Lilo。
|
||||
1. 密码找回,重置一个已丢失的密码等。
|
||||
|
||||
### 用途 ###
|
||||
|
||||
> chroot 命令 **改变其当前的根目录到指定目录,然后运行命令**,如果支持的话,可以运行一个用户的登陆shell的交互式副本。请注意并不是每一个程序都可以使用 chroot 命令。
|
||||
### 语法 ###
|
||||
|
||||
基本语法如下:
|
||||
|
||||
chroot /path/to/new/root command
|
||||
|
||||
或者
|
||||
|
||||
chroot /path/to/new/root /path/to/server
|
||||
|
||||
或者
|
||||
|
||||
chroot [options] /path/to/new/root /path/to/server
|
||||
|
||||
#### chroot 命令实例 ####
|
||||
|
||||
在这个例子中,建立了一个"迷你监狱"用来测试一个只有 ls 命令的 Bash shell。首先用 mkdir 命令设定好 jail "监狱" 路径。
|
||||
|
||||
$ J=$HOME/jail
|
||||
|
||||
在 $J 内创建目录:
|
||||
|
||||
$ mkdir -p $J
|
||||
$ mkdir -p $J/{bin,lib64,lib}
|
||||
$ cd $J
|
||||
|
||||
用[cp 命令][1]将/bin/bash 和 /bin/ls 复制到 $J/bin/ 路径下:
|
||||
|
||||
$ cp -v /bin/{bash,ls} $J/bin
|
||||
|
||||
将所需库文件拷贝到$J。可以用 ldd 命令打印出 bash 所依赖的共享库。
|
||||
|
||||
$ ldd /bin/bash
|
||||
|
||||
输出样例:
|
||||
|
||||
linux-vdso.so.1 => (0x00007fff8d987000)
|
||||
libtinfo.so.5 => /lib64/libtinfo.so.5 (0x00000032f7a00000)
|
||||
libdl.so.2 => /lib64/libdl.so.2 (0x00000032f6e00000)
|
||||
libc.so.6 => /lib64/libc.so.6 (0x00000032f7200000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00000032f6a00000)
|
||||
|
||||
直接拷贝上面输出中的库文件到 $J 目录:
|
||||
|
||||
$ cp -v /lib64/libtinfo.so.5 /lib64/libdl.so.2 /lib64/libc.so.6 /lib64/ld-linux-x86-64.so.2 $J/lib64/
|
||||
|
||||
输出样例:
|
||||
|
||||
`/lib64/libtinfo.so.5' -> `/home/vivek/jail/lib64/libtinfo.so.5'
|
||||
`/lib64/libdl.so.2' -> `/home/vivek/jail/lib64/libdl.so.2'
|
||||
`/lib64/libc.so.6' -> `/home/vivek/jail/lib64/libc.so.6'
|
||||
`/lib64/ld-linux-x86-64.so.2' -> `/home/vivek/jail/lib64/ld-linux-x86-64.so.2'
|
||||
|
||||
复制 ls 命令所需的库文件到 $J 目录下。用 ldd 命令打印出 ls 命令依赖的共享库:
|
||||
|
||||
$ ldd /bin/ls
|
||||
|
||||
输出样例:
|
||||
|
||||
linux-vdso.so.1 => (0x00007fff68dff000)
|
||||
libselinux.so.1 => /lib64/libselinux.so.1 (0x00000032f8a00000)
|
||||
librt.so.1 => /lib64/librt.so.1 (0x00000032f7a00000)
|
||||
libcap.so.2 => /lib64/libcap.so.2 (0x00000032fda00000)
|
||||
libacl.so.1 => /lib64/libacl.so.1 (0x00000032fbe00000)
|
||||
libc.so.6 => /lib64/libc.so.6 (0x00000032f7200000)
|
||||
libdl.so.2 => /lib64/libdl.so.2 (0x00000032f6e00000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00000032f6a00000)
|
||||
libpthread.so.0 => /lib64/libpthread.so.0 (0x00000032f7600000)
|
||||
libattr.so.1 => /lib64/libattr.so.1 (0x00000032f9600000)
|
||||
|
||||
你可以一个个的复制库文件,为了更高效的作业,我们也可以使用[bash shell 的循环指令][2]实现:
|
||||
|
||||
list="$(ldd /bin/ls | egrep -o '/lib.*\.[0-9]')"
|
||||
for i in $list; do cp -v "$i" "${J}${i}"; done
|
||||
|
||||
输出样例:
|
||||
|
||||
`/lib64/libselinux.so.1' -> `/home/vivek/jail/lib64/libselinux.so.1'
|
||||
`/lib64/librt.so.1' -> `/home/vivek/jail/lib64/librt.so.1'
|
||||
`/lib64/libcap.so.2' -> `/home/vivek/jail/lib64/libcap.so.2'
|
||||
`/lib64/libacl.so.1' -> `/home/vivek/jail/lib64/libacl.so.1'
|
||||
`/lib64/libc.so.6' -> `/home/vivek/jail/lib64/libc.so.6'
|
||||
`/lib64/libdl.so.2' -> `/home/vivek/jail/lib64/libdl.so.2'
|
||||
`/lib64/ld-linux-x86-64.so.2' -> `/home/vivek/jail/lib64/ld-linux-x86-64.so.2'
|
||||
`/lib64/libpthread.so.0' -> `/home/vivek/jail/lib64/libpthread.so.0'
|
||||
`/lib64/libattr.so.1' -> `/home/vivek/jail/lib64/libattr.so.1'
|
||||
|
||||
最后,chroot 到你的新jail:
|
||||
|
||||
$ sudo chroot $J /bin/bash
|
||||
|
||||
尝试浏览一下 /etc 或 /var:
|
||||
|
||||
# ls /
|
||||
# ls /etc/
|
||||
# ls /var/
|
||||
|
||||
改变了根目录的 bash 和 ls 程序现在被锁定在$HOME/$J这个特殊目录中,而且不能再访问外部的目录树,这个目录可以看做是它们的"/"(root)目录。如果配置正确的话,这会极大增强安全性。我通常用这种技术锁定以下的应用程序。
|
||||
|
||||
1. [Apache - Red Hat / CentOS: Chroot Apache 2 Web Server][3]
|
||||
1. [Nginx - Linux nginx: Chroot (Jail) Setup][4]
|
||||
1. [Chroot Lighttpd web server on a Linux based system][5]
|
||||
1. Chroot mail server.
|
||||
1. Chroot Bind DNS server and more.
|
||||
|
||||
### 如何退出 chroot jail呢? ###
|
||||
|
||||
键入 exit 即可
|
||||
|
||||
$ exit
|
||||
|
||||
会话样例:
|
||||
|
||||
[][6]
|
||||
|
||||
Gif 动画01: Linux / Unix: Bash Chroot ls 命令演示
|
||||
|
||||
### 查找服务是否存在于 chrooted jail 内###
|
||||
|
||||
你可以用下面两个命令[轻松的找出 Postfix 邮件服务是否已经 chrooted]:
|
||||
|
||||
pid=$(pidof -s master)
|
||||
ls -ld /proc/$pid/root
|
||||
|
||||
从基本Linux服务中输出样例:
|
||||
|
||||
lrwxrwxrwx. 1 root root 0 Mar 9 11:16 /proc/8613/root -> /
|
||||
|
||||
PID 8613 指向了 / (root) 也就是说这个程序的根目录并没有被改变或是被 chroot。这个方法非常的快速而又直接,不需要打开配置文件。下面是从已经 chroot 的 ngnix 服务中得到的另一个例子:
|
||||
|
||||
pid=$(pidof -s master)
|
||||
ls -ld /proc/$pid/root
|
||||
|
||||
输出样例:
|
||||
|
||||
lrwxrwxrwx 1 nginx nginx 0 Mar 9 11:17 /proc/4233/root -> /nginxjail
|
||||
|
||||
程序的根目录已经改为 /nginxjail。
|
||||
|
||||
### 用 chroot 救援和修复软件RAID(磁盘阵列)系统 ###
|
||||
|
||||
我先假设基于软阵列的 Linux 系统无法正常启动。所以你[需要用Live CD或用网络远程进入内核应急模式][8]来修复系统。在这个例子中,我用了 Live Linux DVD/CD 启动基于 RHEL 的系统,然后再 chroot 到 /dev/sda1 和/或 /dev/md0 修复问题:
|
||||
|
||||
## 在 Live CD 的提示符下,键入以下命令来恢复数据。##
|
||||
## /dev/sda1 系统主分区##
|
||||
# 建立 jail 目录
|
||||
d=/chroot
|
||||
mkdir $d
|
||||
|
||||
# 挂载 sda1 和其他所需目录
|
||||
mount /dev/sda1 $d
|
||||
mount -o bind /dev $d/dev
|
||||
mount -o bind /sys $d/sys
|
||||
mount -o bind /dev/shm $d/dev/shm
|
||||
mount -o bind /proc $d/proc
|
||||
|
||||
# 挂载软件RAID /dev/md0
|
||||
mount /dev/md0 $d/data
|
||||
|
||||
# Chroot 到我们新建的 jail 中。这将允许我们修复引导装载系统(bootloader),或者在所有文件被/dev/null吞噬之前抓取数据。
|
||||
chroot $d
|
||||
|
||||
#你能看见吗?
|
||||
ls
|
||||
df
|
||||
|
||||
# 将文件置入安全路径
|
||||
rsync -avr /path/to/my_precious_data_dir user@safe.location.cyberciti.biz:/path/to/dest
|
||||
|
||||
# 退出 jail ,然后重启或者根据个人所需格式化服务 ;)
|
||||
exit
|
||||
umount {dev,sys,[...],}
|
||||
reboot
|
||||
|
||||
别急,还有更精彩的内容!
|
||||
|
||||
查看nixCraft下所有其他有关 chroot 命令的文章:
|
||||
|
||||
1. [Ubuntu: Mount Encrypted Home Directory (~/.private) From an Ubuntu Live CD][9]
|
||||
1. [Linux Configure rssh Chroot Jail To Lock Users To Their Home Directories Only][10]
|
||||
1. [Fix a dual boot MS-Windows XP/Vista/7/Server and Linux problem][11]
|
||||
1. [Restore Debian Linux Grub boot loader][12]
|
||||
|
||||
### 在 Linux 和 类Unix 系统下 chroot 应用程序的注意事项 ###
|
||||
|
||||
你应该一直用 chroot 特性吗?从上面的例子看出,这个程序是相当简单的,但是最终可能出现几种不同的问题而结束,例如:
|
||||
|
||||
1.在 jail 中缺失库文件可能直接导致 jail 崩溃。
|
||||
1.一些复杂的程序不好被 chroot。所以我建议你要么尝试[真正的jail,例如FreeBSD提供的][13],要么用虚拟化解决,比如[Linux 下的 KVM][14]。
|
||||
1.正在运行某一程序的 jail 不能再运行其他程序,不能更改任何文件,也不能"假设"另一个用户的身份。放宽这些限制,会降低你的安全性,请根据具体情况 chroot。
|
||||
|
||||
还要注意:
|
||||
|
||||
1. 当你升级本地程序时,不要忘记升级已 chroot 的程序。
|
||||
1. 并非所有程序能够或者应该被 chroot。
|
||||
1. 任何需要 root 权限操作的程序,对其 chroot 是没意义的。因为通常 root 用户都能脱离 chroot。
|
||||
1. Chroot 并不一个高招。更精的可以学习[如何保护和加强系统的各个部分][15]
|
||||
|
||||
### choort 命令选项 ###
|
||||
|
||||
取自 man 帮助页面[chroot(8)][16]:
|
||||
|
||||
|
||||
--userspec=USER:GROUP 使用指定的 用户 和 组 (ID 或 名称)
|
||||
--groups=G_LIST 指定补充组 g1,g2,..,gN
|
||||
--help 显示帮助并退出
|
||||
--version 显示版本信息并退出
|
||||
|
||||
### 参见 ###
|
||||
|
||||
- [chroot(8) Linux/Unix 命令 man 页面][17]
|
||||
- [Man页面 chroot(2)][18]
|
||||
- [OpenBSD文档参见Apache chrooting FAQ 提取更多信息][19]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via:
|
||||
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.cyberciti.biz/faq/cp-copy-command-in-unix-examples/
|
||||
[2]:http://www.cyberciti.biz/faq/bash-for-loop/
|
||||
[3]:http://www.cyberciti.biz/tips/chroot-apache-under-rhel-fedora-centos-linux.html
|
||||
[4]:http://www.cyberciti.biz/faq/howto-run-nginx-in-a-chroot-jail/
|
||||
[5]:http://www.cyberciti.biz/tips/howto-setup-lighttpd-php-mysql-chrooted-jail.html
|
||||
[6]:http://www.cyberciti.biz/faq/?attachment_id=28148
|
||||
[7]:http://www.cyberciti.biz/tips/linux-chroot-service.html
|
||||
[8]:http://www.cyberciti.biz/faq/centos-rhel-linux-mount-raid-hard-disk-from-livecd/
|
||||
[9]:http://www.cyberciti.biz/faq/ubuntu-mounting-your-encrypted-home-from-livecd/
|
||||
[10]:http://www.cyberciti.biz/tips/howto-linux-unix-rssh-chroot-jail-setup.html
|
||||
[11]:http://www.cyberciti.biz/tips/howto-fix-dual-boot-windows-vista-linux.html
|
||||
[12]:http://www.cyberciti.biz/tips/restore-debian-linux-grub-boot-loader.html
|
||||
[13]:http://www.cyberciti.biz/faq/how-to-upgrade-freebsd-jail-vps/
|
||||
[14]:http://www.cyberciti.biz/faq/kvm-virtualization-in-redhat-centos-scientific-linux-6/
|
||||
[15]:http://www.cyberciti.biz/tips/linux-security.html
|
||||
[16]:http://www.manpager.com/linux/man8/chroot.8.html
|
||||
[17]:http://www.manpager.com/linux/man8/chroot.8.html
|
||||
[18]:http://www.manpager.com/linux/man2/chroot.2.html
|
||||
[19]:http://www.openbsd.org/faq/
|
||||
Loading…
Reference in New Issue
Block a user