mirror of
https://github.com/LCTT/TranslateProject.git
synced 2024-12-26 21:30:55 +08:00
翻译2完0170529 NMAP OS Detection.md
This commit is contained in:
parent
f96699230a
commit
3a57936ec0
@ -1,188 +0,0 @@
|
||||
zhousiyu325 翻译中......
|
||||
|
||||
NMAP OS Detection
|
||||
===================
|
||||
|
||||
Sometimes on a network it is beneficial to know the Operating System (OS) of a machine. Accessing a system is easier when you know the OS because you can specifically search the Internet for known security holes in the OS. Granted, security holes are usually patched quickly, but you need to know when a security hole exists.
|
||||
|
||||
Scanning your own network to detect the OS types can help you to see what a hacker will be able to see about your network.
|
||||
|
||||
**OS Detection Database**
|
||||
|
||||
NMAP has a database which is installed when you install NMAP. The database is used when doing OS detection, but it is not automatically updated.
|
||||
|
||||
The database is located at ‘/usr/share/nmap/nmap-os-db’. The easiest way to manage an update is first to look at the database version number. Open the file in a text editor and the version number is usually listed on the second line. The second line of my database is ‘# $Id: nmap-os-db 35407 2015-11-10 04:26:26Z dmiller $’. The database version for this file is 35407.
|
||||
|
||||
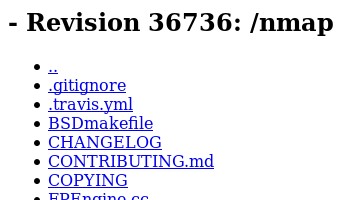
To look on the Internet for an updated version go to ‘[https://svn.nmap.org/nmap][1]’ as shown in Figure 1.
|
||||
|
||||
|
||||
|
||||
**FIGURE 1**
|
||||
|
||||
Here you can see that the version number is 36736\. This seems like quite an update compared to what is currently on my system. The database definitely needs to be updated for proper OS Detection of newer systems.
|
||||
|
||||
It may be a good idea to keep the older database version. Since my current version is 35407 I will perform the following command in a Terminal:
|
||||
|
||||
_sudo mv /usr/share/nmap/nmap-os-db /usr/share/nmap/nmap-os-db-35407_
|
||||
|
||||
The database is ‘moved’ or ‘renamed’ to include the version number. The next step is to download the new version from the website. Perform the following commands in a Terminal:
|
||||
|
||||
_cd /usr/share/nmap
|
||||
sudo su
|
||||
wget _ [_https://svn.nmap.org/nmap/nmap-os-db_][2]
|
||||
|
||||
The new database should be downloaded and ready to go, but you should add the version number. As you saw in Figure 1 the version number is 36736\. Use a text editor to open the database and on the second line add the version number. By adding the version number it will be easier to check later if the version number has changed. When the version number has changed you can update the database and add the version number so you are prepared when checking for updates again.
|
||||
|
||||
**OS Detection Process**
|
||||
|
||||
Before we get into the actual command and performing an OS Detection we should cover some details about what is happening during this scan.
|
||||
|
||||
There are five separate probes being performed. Each probe may consist of one or more packets. The response to each packet by the target system helps to determine the OS type.
|
||||
|
||||
The five different probes are:
|
||||
|
||||
1. Sequence Generation
|
||||
|
||||
2. ICMP Echo
|
||||
|
||||
3. TCP Explicit Congestion Notification
|
||||
|
||||
4. TCP
|
||||
|
||||
5. UDP
|
||||
|
||||
Now we can look at these individually to see what they are doing.
|
||||
|
||||
**Sequence Generation**
|
||||
|
||||
The Sequence Generation Probe consists of six packets. The six packets are sent 100 ms apart and are all TCP SYN packets.
|
||||
|
||||
The result of each TCP SYN packet will help NMAP determine the OS type.
|
||||
|
||||
**ICMP Echo**
|
||||
|
||||
Two ICMP Request packets are sent to the target system with varying settings in the packet.
|
||||
|
||||
The resulting responses will help verify the OS type by NMAP.
|
||||
|
||||
**TCP Explicit Congestion Notification**
|
||||
|
||||
When a lot of packets are being generated and passing through a router causing it to be burdened is known as congestion. The result is that systems slow down to reduce congestion so the router is not dropping packets.
|
||||
|
||||
The packet being sent is only to get a response from the target system. Specific values returned are used to determine the specific OS since each OS handles the packets in different ways.
|
||||
|
||||
**TCP**
|
||||
|
||||
Six packets are sent during this probe.
|
||||
|
||||
Some packets are sent to open or closed ports with specific packet settings. Again, the results will vary depending on the target OS.
|
||||
|
||||
The TCP Packets are all sent with varying flags as follows:
|
||||
|
||||
1. no flags
|
||||
|
||||
2. SYN, FIN, URG and PSH
|
||||
|
||||
3. ACK
|
||||
|
||||
4. SYN
|
||||
|
||||
5. ACK
|
||||
|
||||
6. FIN, PSH, and URG
|
||||
|
||||
**UDP**
|
||||
|
||||
This probe consists of a single packet sent to a closed port.
|
||||
|
||||
If the port used on the target system is closed and an ICMP Port Unreachable message is returned then there is no Firewall.
|
||||
|
||||
**NMAP OS Detection Command**
|
||||
|
||||
Now we need to run the actual command to perform an OS Detection. If you have read any of the other of my NMAP articles then it is best not to perform a PING. To skip the PING we use the parameter ‘-Pn’. To see the extra information we may require you should use the ‘-v’ parameter for adding verbosity. Specifically to get the OS Detection the parameter ‘-O’ is needed.
|
||||
|
||||
For the command to complete properly and perform the TCP SYN Scan you need to perform the command as ROOT. In my case, I will perform the scan on one system only and not the whole network so the command would be:
|
||||
|
||||
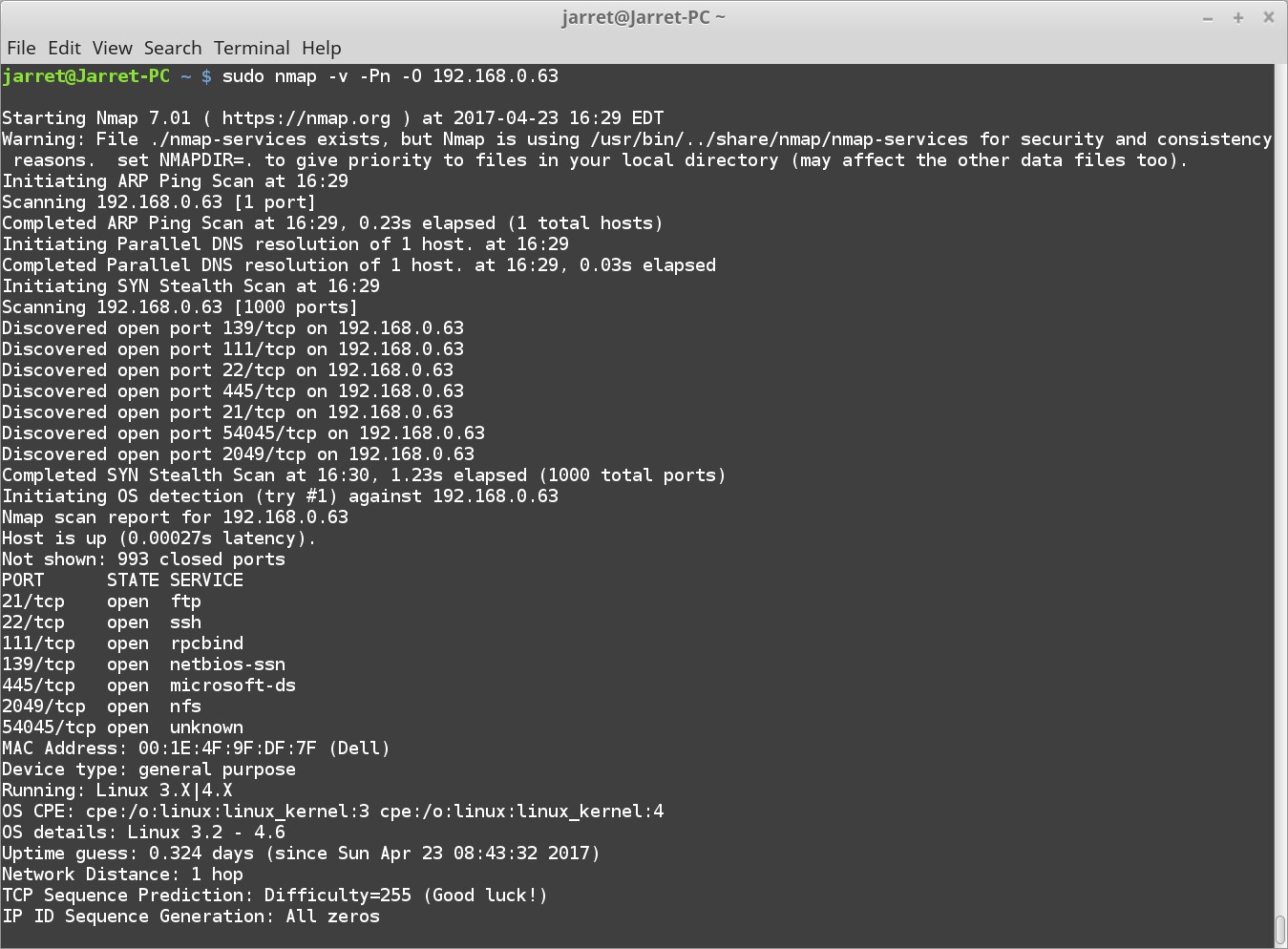
_sudo nmap -v -Pn -O 192.168.0.63_
|
||||
|
||||
The results of the scan are shown in Figure 2\. The scan shows that there are seven open ports using a SYN Stealth Scan.
|
||||
|
||||
|
||||
|
||||
**FIGURE 2**
|
||||
|
||||
The open ports are:
|
||||
|
||||
1. 21/tcp ftp
|
||||
|
||||
2. 22/tcp ssh
|
||||
|
||||
3. 111/tcp rpcbind
|
||||
|
||||
4. 139/tcp netbios-ssn
|
||||
|
||||
5. 445/tcp microsoft-ds
|
||||
|
||||
6. 2049/tcp nfs
|
||||
|
||||
7. 54045/tcp unknown
|
||||
|
||||
The MAC Address of the system is 00:1E:4F:9F
|
||||

|
||||
F:7F.
|
||||
|
||||
The final portion shows the OS type:
|
||||
|
||||
_Device type: general purpose
|
||||
Running: Linux 3.X|4.X
|
||||
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
|
||||
OS details: Linux 3.2 - 4.6
|
||||
Uptime guess: 0.324 days (since Sun Apr 23 08:43:32 2017)_
|
||||
|
||||
The system is running Ubuntu Server 16.10 and the Linux Kernel is 4.8\. The uptime is guessed correctly.
|
||||
|
||||
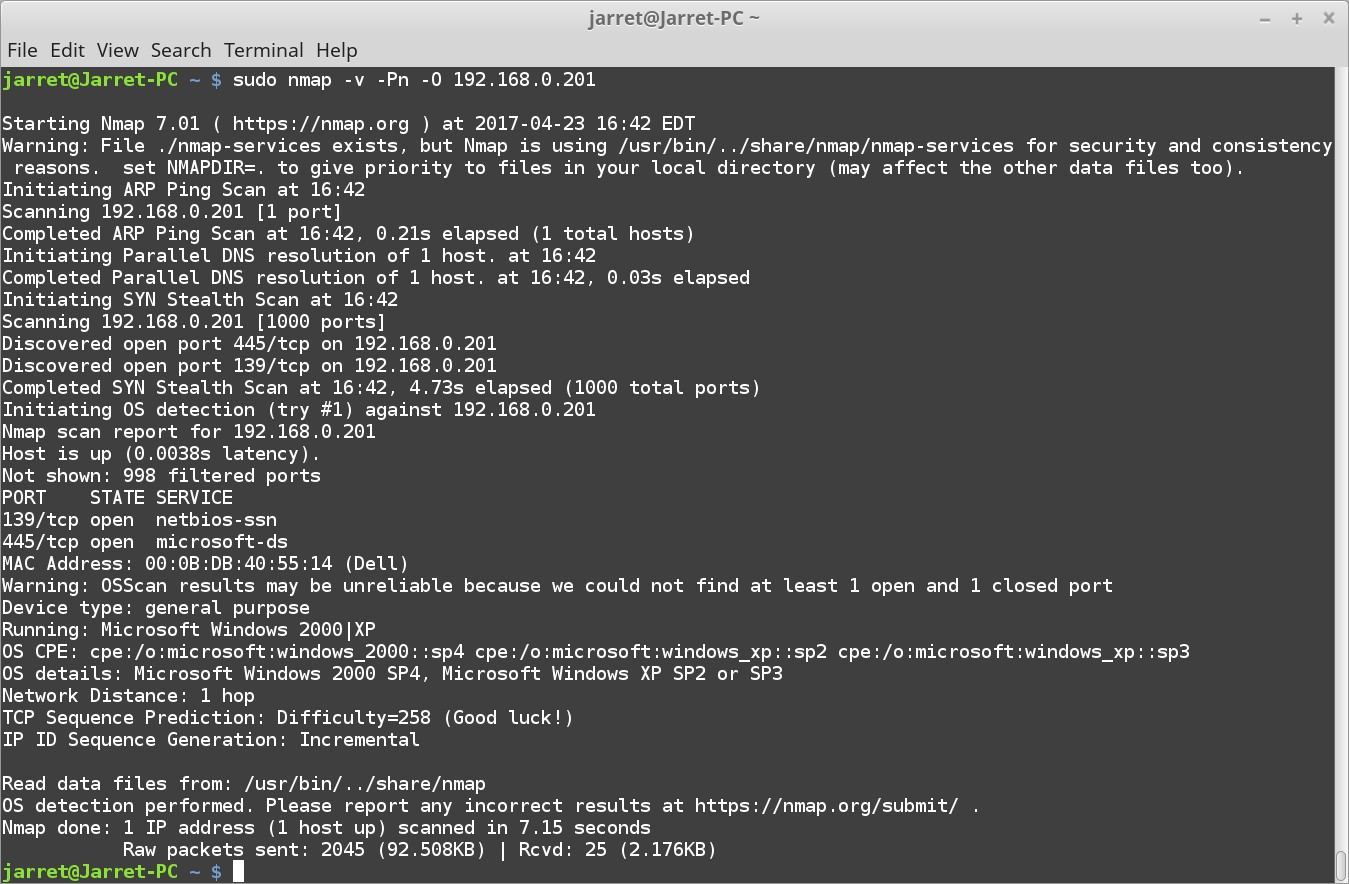
I performed a second test against another system. The results are shown in Figure 3.
|
||||
|
||||
|
||||
|
||||
**FIGURE 3**
|
||||
|
||||
In this scan different ports are open. The system is guessed to be ‘Microsoft Windows 2000|XP’. It is Windows XP running SP3.
|
||||
|
||||
**Port Sniffer Results.**
|
||||
|
||||
Let’s look at what is going on in the background of the first scan shown in Figure 2.
|
||||
|
||||
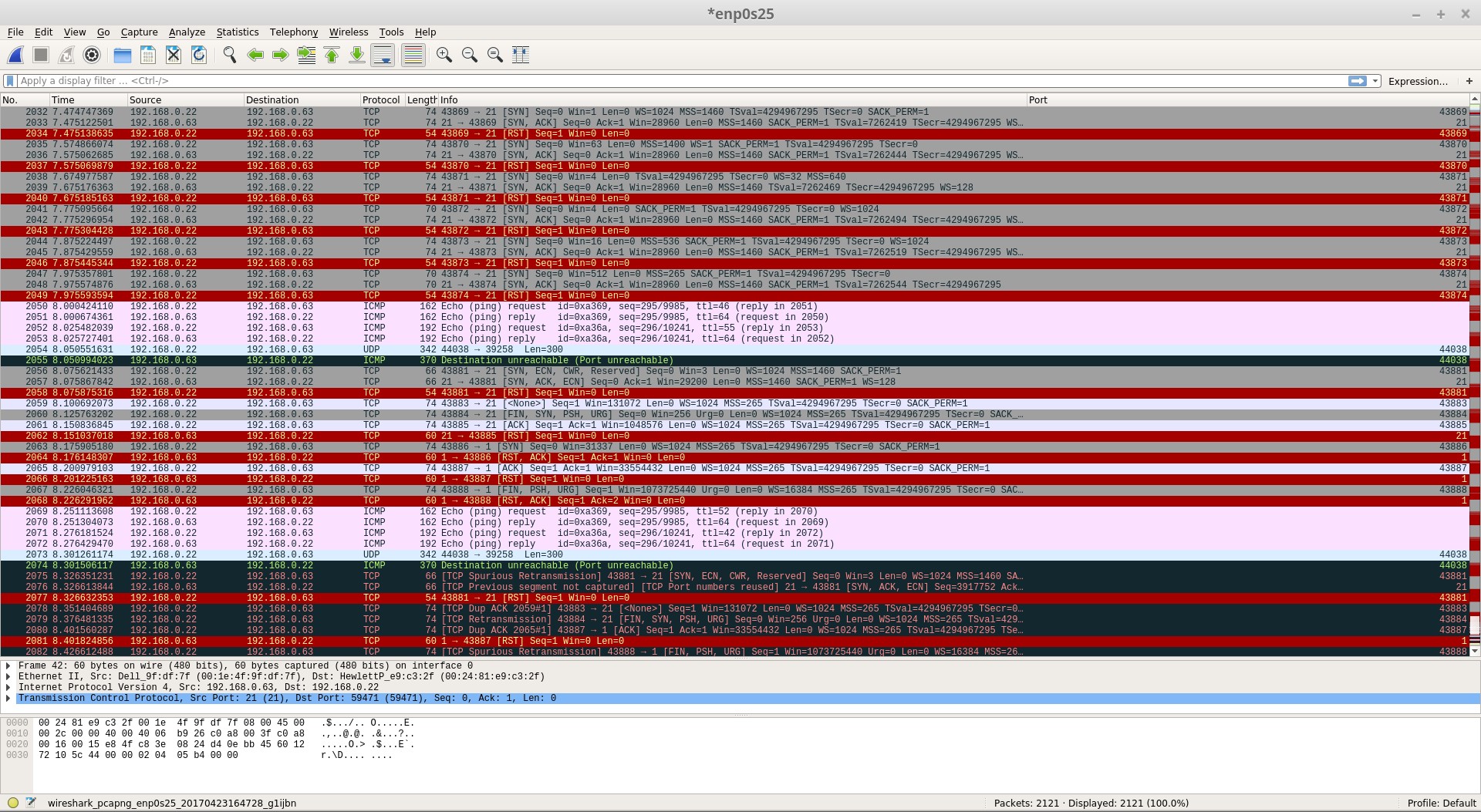
Initially NMAP is performing a TCP Stealth Scan. In this instance the OS Detection Probes start at Packet 2032 in Figure 4.
|
||||
|
||||
|
||||
|
||||
**FIGURE 4**
|
||||
|
||||
The Sequence Generation starts at Packet 2032/2033 and the sixth one is at Packet 2047/2048\. Notice that each one is sent twice and the next packet in the probe is sent 100 ms later.
|
||||
|
||||
The ICMP Packets are sent at 2050-2053\. The two packets are duplicated making a total of four.
|
||||
|
||||
Packets 2056-2057 are the TCP Explicit Congestion Notification packets.
|
||||
|
||||
The six probes for the TCP are on lines 2059, 2060, 2061, 2063, 2065 and 2067.
|
||||
|
||||
The last probe for UDP is line 2073.
|
||||
|
||||
These are the probes that are used to determine the OS of the target system.
|
||||
|
||||
I hope this helps you to understand how to update the NMAP OS Detection Database and perform a scan on systems. Be aware that you can run the scan on systems which are not on your network, so the scan can be performed on systems on the Internet.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.org/threads/nmap-os-detection.4564/
|
||||
|
||||
作者:[Jarret B ][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.org/members/jarret-b.29858/
|
||||
[1]:https://svn.nmap.org/nmap
|
||||
[2]:https://svn.nmap.org/nmap/nmap-os-db
|
||||
175
translated/tech/20170529 NMAP OS Detection.md
Normal file
175
translated/tech/20170529 NMAP OS Detection.md
Normal file
@ -0,0 +1,175 @@
|
||||
NMAP 操作系统探测
|
||||
============================
|
||||
|
||||
有时,能够知道一个网络里的机器的操作系统(OS)是有一定好处的。当你知道一台机器的操作系统后,因为你可以在网上搜索专门针对该系统的安全漏洞,所以入侵系统也会更加容易。当然,安全漏洞通常都会很快被修补,但你需要知道安全漏洞何时存在。
|
||||
|
||||
对你自己的网络进行扫描以便发现操作系统类型可以帮助你了解黑客将如何侵入你的网络。
|
||||
|
||||
**操作系统探测数据库**
|
||||
|
||||
NAMP 带有一个数据库,它在你安装 NAMP 的时候就会被安装。这个数据库是用于操作系统的探测,但是它不会自动更新。
|
||||
|
||||
这个数据库位于`/usr/share/nmap/nmap-os-db`。管理更新的最简单方式是首先找到数据库的版本号,用文本编辑器打开这个文件,版本号通常位于第二行。我的数据库的第二行是`# $Id: nmap-os-db 35407 2015-11-10 04:26:26Z dmiller $`,这个文件的数据库版本是 35407。
|
||||
|
||||
要在网上查找一个可更新版本,可以浏览 `[https://svn.nmap.org/nmap][1]`,如图1所示:
|
||||
|
||||

|
||||
**图1**
|
||||
|
||||
你可以从图中看到版本号为 3676,与我的系统上的版本号相比,这个版本号似乎是一个更新的版本。为了对更新的系统进行准确的操作系统探测,当然需要对这个数据库进行更新。
|
||||
|
||||
保留较旧的数据库版本也是一个不错的主意。我当前和版本是 35407,我将在终端执行下面的命令:
|
||||
|
||||
```
|
||||
sudo mv /usr/share/nmap/nmap-os-db /usr/share/nmap/nmap-os-db-35407
|
||||
```
|
||||
|
||||
这个数据库被以包含版本号的方式重命名了,下一步就是从网站上下载新版本的数据库,在终端执行下面命令:
|
||||
|
||||
```
|
||||
cd /usr/share/nmap
|
||||
sudo su
|
||||
wget https://svn.nmap.org/nmap/nmap-os-db
|
||||
```
|
||||
新的数据库即将开始被下载,但是你应该加上版本号,就像你在图 1 中看到的版本号 36736。使用文本编辑器打开这个数据库,然后在第二行加上版本号。当版本号变化后,你可以更新你的数据库,然后在其中加入版本号,以便在再次检查更新时做好准备。
|
||||
|
||||
**系统探测过程**
|
||||
|
||||
在我们开始使用实际的命令并执行系统探测之前,我们应该详细介绍扫描过程中将会发生的事情。
|
||||
|
||||
会有五种不同的测试正在被执行,每种测试由一个或者多个数据包组成,目标系统对每个数据包作出的响应有助于确定操作系统的类型。
|
||||
|
||||
五种不同的测试是:
|
||||
|
||||
1. Sequence Generation
|
||||
|
||||
2. ICMP Echo
|
||||
|
||||
3. TCP Explicit Congestion Notification
|
||||
|
||||
4. TCP
|
||||
|
||||
5. UDP
|
||||
|
||||
现在让我们分别看看他们各自在做什么。
|
||||
|
||||
**Sequence Generation**
|
||||
|
||||
Sequence Generation 测试由六个数据包组成,这六个包是每隔100毫秒分开发送的,且都是TCP SYN包。
|
||||
|
||||
每个 TCP SYN 包的结果将有助于 NMAP 确定操作系统的类型。
|
||||
|
||||
**ICMP Echo**
|
||||
|
||||
两个有着不同设置的 ICMP Request 包被送到目标系统,由此产生的反应将有助于实现验证操作系统类型。
|
||||
|
||||
**TCP**
|
||||
|
||||
在这个测试中会发送六个数据包。
|
||||
|
||||
一些带有特定包设置的包被发送用来打开或关闭端口。再次,结果将会因为操作系统的不同而不同。
|
||||
|
||||
所有 TCP 包都是以如下不同的标志被发送:
|
||||
|
||||
1. no flags
|
||||
|
||||
2. SYN, FIN, URG and PSH
|
||||
|
||||
3. ACK
|
||||
|
||||
4. SYN
|
||||
|
||||
5. ACK
|
||||
|
||||
6. FIN, PSH, and URG
|
||||
|
||||
**UDP**
|
||||
|
||||
这个测试由一个被发送给一个关闭的端口的数据包组成。
|
||||
|
||||
如果目标系统上的这个端口是关闭的,而且返回一条 ICMP 端口不可达的信息,那么就说明没有防火墙。
|
||||
|
||||
**NMAP OS Detection Command**
|
||||
|
||||
现在我们需要开始实际动手进行系统探测。如果你已经读过一些我写的关于 NMAP 的文章,那么最好不要执行 PING 命令。为了跳过 PING,我们使用参数 'Pn'。为了看到详细的信息,你应该使用'-v'参数用于动态显示。为了获取系统的信息,需要使用'-O'参数。
|
||||
|
||||
为了使命令顺利运行和执行 TCP SYN 扫描,你需要以管理员的身份来执行这个命令。在我的例子中,我将只在一个系统上而不是整个网络上进行扫描,使用的命令是:
|
||||
|
||||
> sudo nmap -v -Pn -O 192.168.0.63
|
||||
|
||||
扫描的结果如图2所示,扫描显示七个开放的端口。
|
||||
|
||||

|
||||
**图2**
|
||||
|
||||
开放的端口是:
|
||||
|
||||
1. 21/tcp ftp
|
||||
|
||||
2. 22/tcp ssh
|
||||
|
||||
3. 111/tcp rpcbind
|
||||
|
||||
4. 139/tcp netbios-ssn
|
||||
|
||||
5. 445/tcp microsoft-ds
|
||||
|
||||
6. 2049/tcp nfs
|
||||
|
||||
7. 54045/tcp unknown
|
||||
|
||||
系统的MAC 地址为为: 00:1E:4F:DF:7F。
|
||||
|
||||
后面部分显示系统类型为:
|
||||
|
||||
_Device type: general purpose
|
||||
Running: Linux 3.X|4.X
|
||||
OS CPE: cpe:/o:linux:linux\_kernel:3 cpe:/o:linux:linux\_kernel:4
|
||||
OS details: Linux 3.2 - 4.6
|
||||
Uptime guess: 0.324 days (since Sun Apr 23 08:43:32 2017)_
|
||||
|
||||
系统当前运行的是 Ubuntu Server 16.04,Linux 内核为4.8,运行时间猜的较准确。
|
||||
|
||||
我在另一个系统了又进行了一次测试,结果如图3所示:
|
||||
|
||||

|
||||
**图3**
|
||||
|
||||
这次扫描中开放的端口与上次不同。所猜的系统为 ‘Microsoft Windows 2000|XP’,实际上是 Windows XP sp3。
|
||||
|
||||
**Port Sniffer Results.**
|
||||
|
||||
让我们来看看图2所示的第一次扫描中在后台正在运行什么。
|
||||
|
||||
首先 NMAP 执行一次 TCP Stealth 扫描,在本次系统探测测试实例中以一个如图4所示的数据包 2032 开始。
|
||||
|
||||

|
||||
**图4**
|
||||
|
||||
Sequence Generation 开始于数据包 2032/2033,第六个数据包是 2047/2048。注意每个都被发送两次,且每隔 100ms 发送下一个数据包。
|
||||
|
||||
发送的 ICMP 数据包是2050*2053,2 个数据包被复制一份组成 4 个数据包。
|
||||
|
||||
2056-2057 是 TCP Explicit Congestion Notification 数据包。
|
||||
|
||||
对 TCP 的 6 个测试是 2059,2060,2061,2063,2065,2067。
|
||||
|
||||
最后的 UDP 测试是 2073.
|
||||
|
||||
这些就是用于确定目标系统上操作系统的类型的测试。
|
||||
|
||||
我希望这将有助于你理解如何更新 NMAP 系统探测数据库和执行对系统的扫描。请注意,你可以和你不在同一个网络中的系统进行扫描,所以可以对互联网上的任何系统进行扫描。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.org/threads/nmap-os-detection.4564/
|
||||
|
||||
作者:[Jarret B ][a]
|
||||
译者:[zhousiyu325](https://github.com/zhousiyu325)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.org/members/jarret-b.29858/
|
||||
[1]:https://svn.nmap.org/nmap
|
||||
[2]:https://svn.nmap.org/nmap/nmap-os-db
|
||||
Loading…
Reference in New Issue
Block a user