mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-24 02:20:09 +08:00
commit
33f90af9f2
published
20190103 How to use Magit to manage Git projects.md20190110 5 useful Vim plugins for developers.md20190123 Book Review- Fundamentals of Linux.md20190131 Will quantum computing break security.md
sources/tech
20180112 8 KDE Plasma Tips and Tricks to Improve Your Productivity.md20180531 Qalculate- - The Best Calculator Application in The Entire Universe.md20190116 The Evil-Twin Framework- A tool for improving WiFi security.md20190122 How To Copy A File-Folder From A Local System To Remote System In Linux.md
translated
talk
tech
@ -0,0 +1,95 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (lujun9972)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10564-1.html)
|
||||
[#]: subject: (How to use Magit to manage Git projects)
|
||||
[#]: via: (https://opensource.com/article/19/1/how-use-magit)
|
||||
[#]: author: (Sachin Patil https://opensource.com/users/psachin)
|
||||
|
||||
如何在 Emacs 中使用 Magit 管理 Git 项目
|
||||
======
|
||||
|
||||
> Emacs 的 Magit 扩展插件使得使用 Git 进行版本控制变得简单起来。
|
||||
|
||||

|
||||
|
||||
[Git][1] 是一个很棒的用于项目管理的 [版本控制][2] 工具,就是新人学习起来太难。Git 的命令行工具很难用,你不仅需要熟悉它的标志和选项,还需要知道什么环境下使用它们。这使人望而生畏,因此不少人只会非常有限的几个用法。
|
||||
|
||||
好在,现今大多数的集成开发环境 (IDE) 都包含了 Git 扩展,大大地简化了使用使用的难度。Emacs 中就有这么一款 Git 扩展名叫 [Magit][3]。
|
||||
|
||||
Magit 项目成立有差不多 10 年了,它将自己定义为 “一件 Emacs 内的 Git 瓷器”。也就是说,它是一个操作界面,每个操作都能一键完成。本文会带你领略一下 Magit 的操作界面并告诉你如何使用它来管理 Git 项目。
|
||||
|
||||
若你还没有做,请在开始本教程之前先 [安装 Emacs][4],再 [安装 Magit][5]。
|
||||
|
||||
### Magit 的界面
|
||||
|
||||
首先用 Emacs 的 [Dired 模式][6] 访问一个项目的目录。比如我所有的 Emacs 配置存储在 `~/.emacs.d/` 目录中,就是用 Git 来进行管理的。
|
||||
|
||||
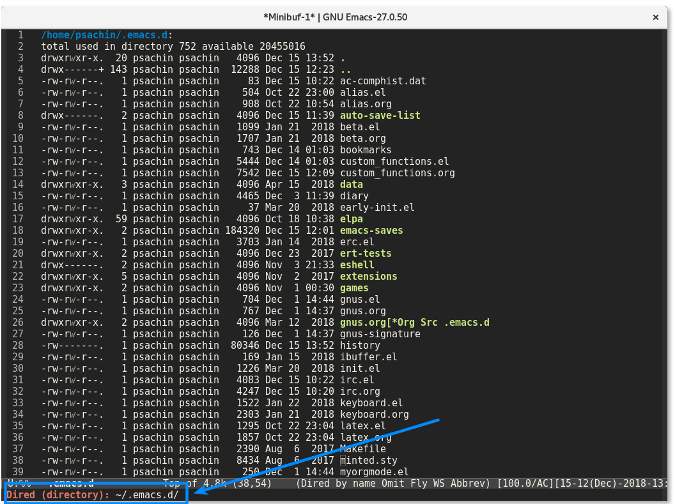
|
||||
|
||||
若你在命令行下工作,则你需要输入 `git status` 来查看项目的当前状态。Magit 也有类似的功能:`magit-status`。你可以通过 `M-x magit-status` (快捷方式是 `Alt+x magit-status` )来调用该功能。结果看起来像下面这样:
|
||||
|
||||
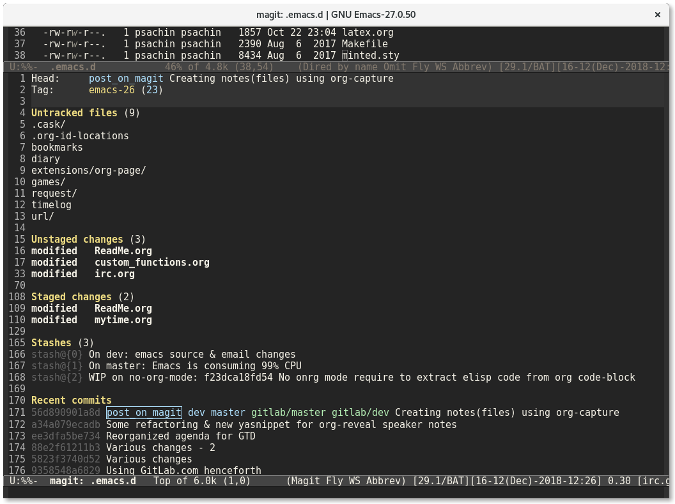
|
||||
|
||||
Magit 显示的信息比 `git status` 命令的要多得多。它分别列出了未追踪文件列表、未暂存文件列表以及已暂存文件列表。它还列出了<ruby>储藏<rt>stash</rt></ruby>列表以及最近几次的提交 —— 所有这些信息都在一个窗口中展示。
|
||||
|
||||
如果你想查看修改了哪些内容,按下 `Tab` 键。比如,我移动光标到未暂存的文件 `custom_functions.org` 上,然后按下 `Tab` 键,Magit 会显示修改了哪些内容:
|
||||
|
||||
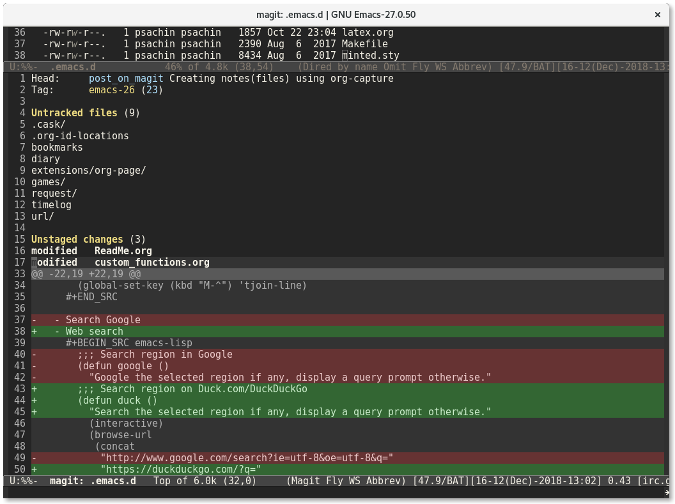
|
||||
|
||||
这跟运行命令 `git diff custom_functions.org` 类似。储藏文件更简单。只需要移动光标到文件上然后按下 `s` 键。该文件就会迅速移动到已储藏文件列表中:
|
||||
|
||||
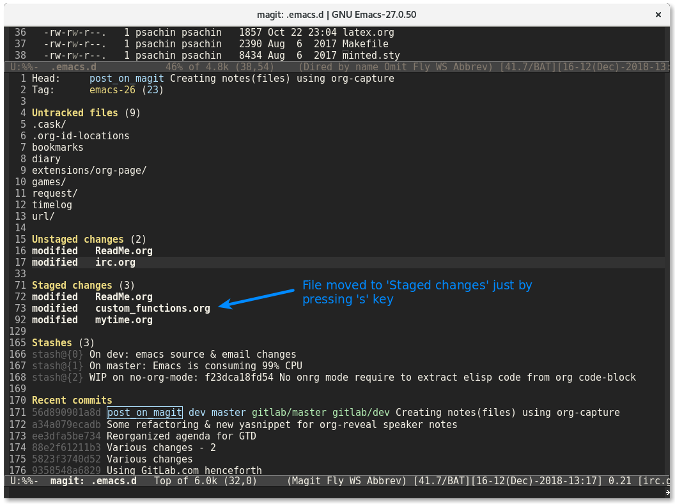
|
||||
|
||||
要<ruby>反储藏<rt>unstage</rt></ruby>某个文件,使用 `u` 键。按下 `s` 和 `u` 键要比在命令行输入 `git add -u <file>` 和 `git reset HEAD <file>` 快的多也更有趣的多。
|
||||
|
||||
### 提交更改
|
||||
|
||||
在同一个 Magit 窗口中,按下 `c` 键会显示一个提交窗口,其中提供了许多标志,比如 `--all` 用来暂存所有文件或者 `--signoff` 来往提交信息中添加签名行。
|
||||
|
||||
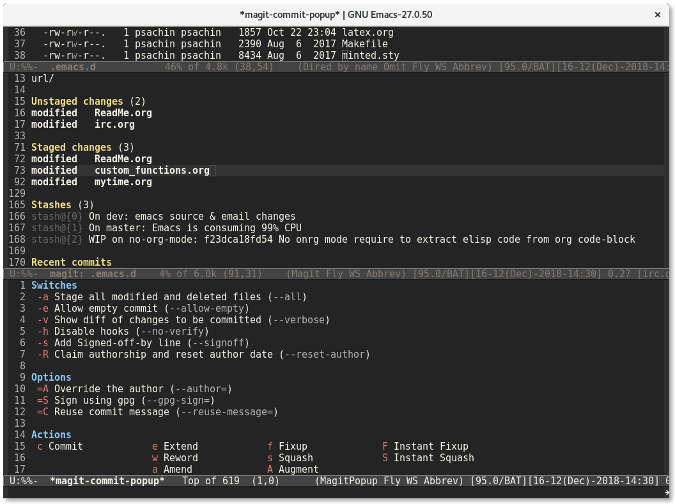
|
||||
|
||||
将光标移动到想要启用签名标志的行,然后按下回车。`--signoff` 文本会变成高亮,这说明该标志已经被启用。
|
||||
|
||||
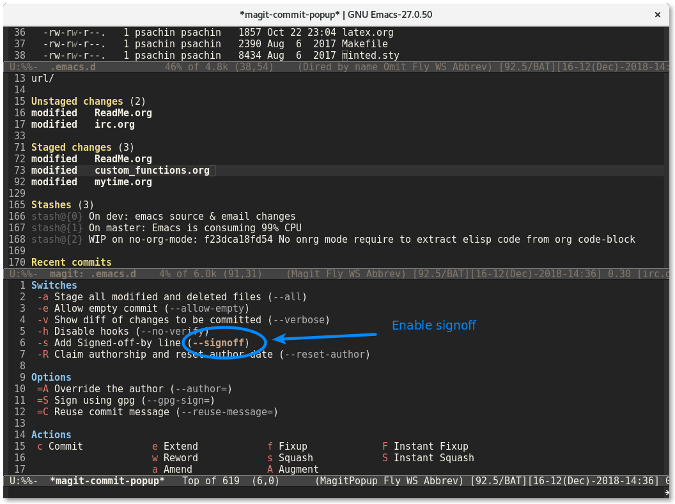
|
||||
|
||||
再次按下 `c` 键会显示一个窗口供你输入提交信息。
|
||||
|
||||
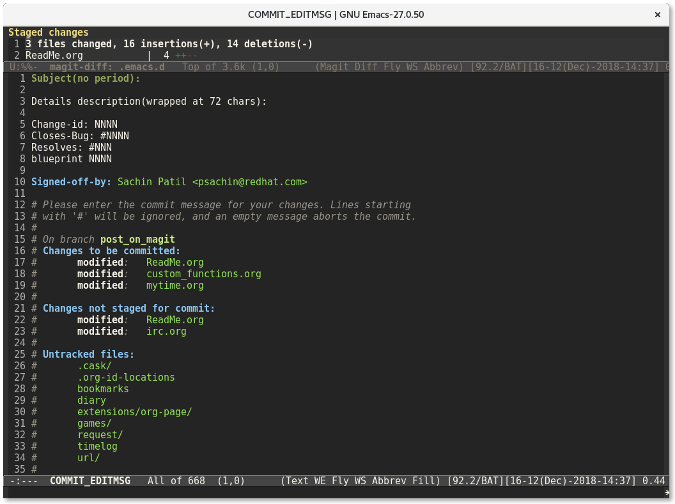
|
||||
|
||||
最后,使用 `C-c C-c `(按键 `Ctrl+cc` 的缩写形式) 来提交更改。
|
||||
|
||||
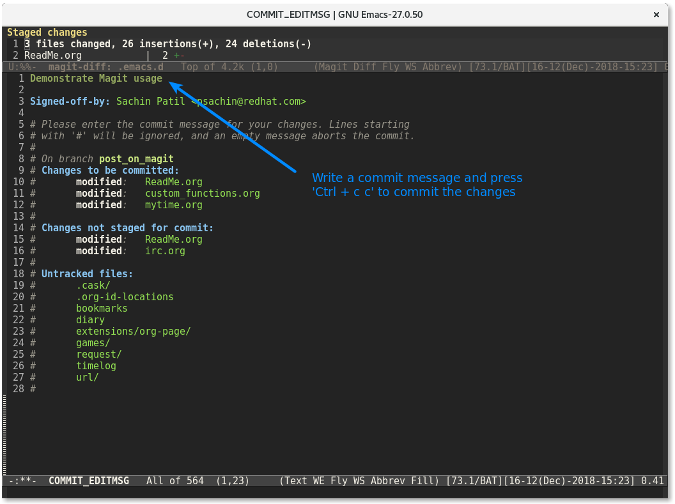
|
||||
|
||||
### 推送更改
|
||||
|
||||
更改提交后,提交行将会显示在 `Recent commits` 区域中显示。
|
||||
|
||||
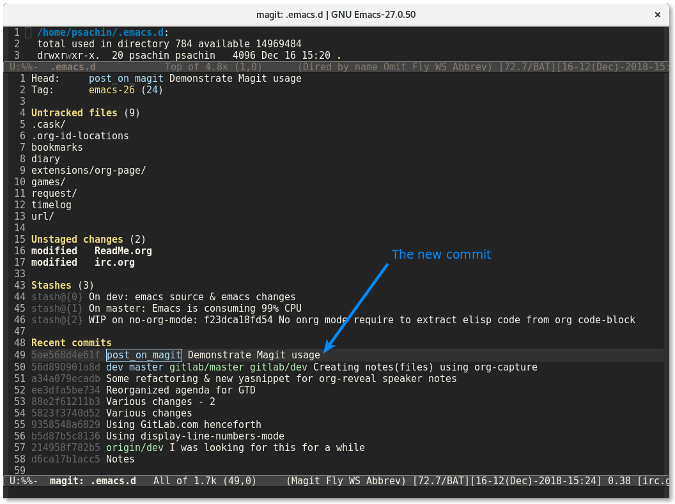
|
||||
|
||||
将光标放到该提交处然后按下 `p` 来推送该变更。
|
||||
|
||||
若你想感受一下使用 Magit 的感觉,我已经在 YouTube 上传了一段 [演示][7]。本文只涉及到 Magit 的一点皮毛。它有许多超酷的功能可以帮你使用 Git 分支、变基等功能。你可以在 Magit 的主页上找到 [文档、支持,以及更多][8] 的链接。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/how-use-magit
|
||||
|
||||
作者:[Sachin Patil][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[lujun9972](https://github.com/lujun9972)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/psachin
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://git-scm.com
|
||||
[2]: https://git-scm.com/book/en/v2/Getting-Started-About-Version-Control
|
||||
[3]: https://magit.vc
|
||||
[4]: https://www.gnu.org/software/emacs/download.html
|
||||
[5]: https://magit.vc/manual/magit/Installing-from-Melpa.html#Installing-from-Melpa
|
||||
[6]: https://www.gnu.org/software/emacs/manual/html_node/emacs/Dired-Enter.html#Dired-Enter
|
||||
[7]: https://youtu.be/Vvw75Pqp7Mc
|
||||
[8]: https://magit.vc/
|
||||
@ -1,28 +1,28 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (pityonline)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10563-1.html)
|
||||
[#]: subject: (5 useful Vim plugins for developers)
|
||||
[#]: via: (https://opensource.com/article/19/1/vim-plugins-developers)
|
||||
[#]: author: (Ricardo Gerardi https://opensource.com/users/rgerardi)
|
||||
|
||||
5 个好用的 Vim 插件
|
||||
5 个好用的开发者 Vim 插件
|
||||
======
|
||||
|
||||
通过这 5 个插件扩展 Vim 功能来提升你的编码效率。
|
||||
> 通过这 5 个插件扩展 Vim 功能来提升你的编码效率。
|
||||
|
||||

|
||||
|
||||
我用 Vim 已经超过 20 年了,两年前我决定把它作为我的首要文本编辑器。我用 Vim 来编写代码,配置文件,博客文章及其它任意可以用纯文本表达的东西。Vim 有很多超级棒的功能,一旦你适合了它,你的工作会变得非常高效。
|
||||
我用 Vim 已经超过 20 年了,两年前我决定把它作为我的首要文本编辑器。我用 Vim 来编写代码、配置文件、博客文章及其它任意可以用纯文本表达的东西。Vim 有很多超级棒的功能,一旦你适合了它,你的工作会变得非常高效。
|
||||
|
||||
在日常编辑工作中,我更倾向于使用 Vim 稳定的原生扩展,但开源社区对 Vim 开发了大量可以提升工作效率的插件。
|
||||
在日常编辑工作中,我更倾向于使用 Vim 稳定的原生功能,但开源社区对 Vim 开发了大量的插件,可以扩展 Vim 的功能、改进你的工作流程和提升工作效率。
|
||||
|
||||
以下列举 5 个非常好用的可以用于编写任意编程语言的插件。
|
||||
|
||||
### 1. Auto Pairs
|
||||
### 1、Auto Pairs
|
||||
|
||||
[Auto Pairs][2] 插件可以帮助你插入和删除成对的文字,如花括号,圆括号或引用标记。这在编写代码时非常有用,因为很多编程语言都有成对标记的语法,就像圆括号用于函数调用,或引号用于字符串定义。
|
||||
[Auto Pairs][2] 插件可以帮助你插入和删除成对的文字,如花括号、圆括号或引号。这在编写代码时非常有用,因为很多编程语言都有成对标记的语法,就像圆括号用于函数调用,或引号用于字符串定义。
|
||||
|
||||
Auto Pairs 最基本的功能是在你输入一个左括号时会自动补全对应的另一半括号。比如,你输入了一个 `[`,它会自动帮你补充另一半 `]`。相反,如果你用退格键删除开头的一半括号,Auto Pairs 会删除另一半。
|
||||
|
||||
@ -39,9 +39,9 @@ func main() {
|
||||
x := true
|
||||
items := []string{"tv", "pc", "tablet"}
|
||||
|
||||
if x {
|
||||
if x {
|
||||
for _, i := range items
|
||||
}
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
@ -57,7 +57,7 @@ func main() {
|
||||
items := []string{"tv", "pc", "tablet"}
|
||||
|
||||
if x {
|
||||
for _, i := range items {
|
||||
for _, i := range items {
|
||||
| (cursor here)
|
||||
}
|
||||
}
|
||||
@ -66,17 +66,17 @@ func main() {
|
||||
|
||||
Auto Pairs 提供了大量其它选项(你可以在 [GitHub][3] 上找到),但最基本的功能已经很让人省时间了。
|
||||
|
||||
### 2. NERD Commenter
|
||||
### 2、NERD Commenter
|
||||
|
||||
[NERD Commenter][4] 插件增加了方便注释的功能,类似在 <ruby>IDE<rt>integrated development environment</rt></ruby> 中注释功能。有了这个插件,你可以一键注释单行或多行代码。
|
||||
[NERD Commenter][4] 插件给 Vim 增加了代码注释的功能,类似在 <ruby>IDE<rt>integrated development environment</rt></ruby> 中注释功能。有了这个插件,你可以一键注释单行或多行代码。
|
||||
|
||||
NERD Commenter 使用了标准的 Vim [filetype][5],所以它能理解一些编程语言并使用合适的方式来注释代码。
|
||||
NERD Commenter 可以与标准的 Vim [filetype][5] 插件配合,所以它能理解一些编程语言并使用合适的方式来注释代码。
|
||||
|
||||
最易上手的方法是按 `Leader+Space` 组合键来开关当前行的注释。Vim 默认的 Leader 键是 `\`。
|
||||
最易上手的方法是按 `Leader+Space` 组合键来切换注释当前行。Vim 默认的 Leader 键是 `\`。
|
||||
|
||||
在<ruby>可视化模式<rt>Visual mode</rt></ruby>中,你可以选择多行一并注释。NERD Commenter 也可以按计数注释,所以你可以加个数量 n 来注释 n 行。
|
||||
|
||||
还有个有用的特性 Sexy Comment 可以用 `Leader+cs` 来触发,它的块注释风格更漂亮一些。例如下面这段代码:
|
||||
还有个有用的特性 “Sexy Comment” 可以用 `Leader+cs` 来触发,它的块注释风格更漂亮一些。例如下面这段代码:
|
||||
|
||||
```
|
||||
package main
|
||||
@ -85,13 +85,13 @@ import "fmt"
|
||||
|
||||
func main() {
|
||||
x := true
|
||||
items := []string{"tv", "pc", "tablet"}
|
||||
items := []string{"tv", "pc", "tablet"}
|
||||
|
||||
if x {
|
||||
for _, i := range items {
|
||||
fmt.Println(i)
|
||||
}
|
||||
}
|
||||
if x {
|
||||
for _, i := range items {
|
||||
fmt.Println(i)
|
||||
}
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
@ -104,15 +104,15 @@ import "fmt"
|
||||
|
||||
func main() {
|
||||
/*
|
||||
* x := true
|
||||
* items := []string{"tv", "pc", "tablet"}
|
||||
*
|
||||
* if x {
|
||||
* for _, i := range items {
|
||||
* fmt.Println(i)
|
||||
* }
|
||||
* }
|
||||
*/
|
||||
* x := true
|
||||
* items := []string{"tv", "pc", "tablet"}
|
||||
*
|
||||
* if x {
|
||||
* for _, i := range items {
|
||||
* fmt.Println(i)
|
||||
* }
|
||||
* }
|
||||
*/
|
||||
}
|
||||
```
|
||||
|
||||
@ -120,9 +120,9 @@ func main() {
|
||||
|
||||
NERD Commenter 是任何使用 Vim 写代码的开发者都必装的插件。
|
||||
|
||||
### 3. VIM Surround
|
||||
### 3、VIM Surround
|
||||
|
||||
[Vim Surround][6] 插件可以帮你在现有文本中实现环绕插入成对的符号(如括号或双引号)或标签(如 HTML 或 XML 标签)。它和 Auto Pairs 有点儿类似,但在编辑文本时更有用。
|
||||
[Vim Surround][6] 插件可以帮你“环绕”现有文本插入成对的符号(如括号或双引号)或标签(如 HTML 或 XML 标签)。它和 Auto Pairs 有点儿类似,但是用于处理已有文本,在编辑文本时更有用。
|
||||
|
||||
比如你有以下一个句子:
|
||||
|
||||
@ -130,7 +130,7 @@ NERD Commenter 是任何使用 Vim 写代码的开发者都必装的插件。
|
||||
"Vim plugins are awesome !"
|
||||
```
|
||||
|
||||
当你的光标处理句中任何位置时,你可以用 `ds"` 组合键删除句子两端的双引号。
|
||||
当你的光标处于引起来的句中任何位置时,你可以用 `ds"` 组合键删除句子两端的双引号。
|
||||
|
||||
```
|
||||
Vim plugins are awesome !
|
||||
@ -142,7 +142,7 @@ Vim plugins are awesome !
|
||||
'Vim plugins are awesome !'
|
||||
```
|
||||
|
||||
或者用 `cs'[` 替换成中括号:
|
||||
或者再用 `cs'[` 替换成中括号:
|
||||
|
||||
```
|
||||
[ Vim plugins are awesome ! ]
|
||||
@ -154,7 +154,7 @@ Vim plugins are awesome !
|
||||
<p>Vim plugins are awesome !</p>
|
||||
```
|
||||
|
||||
当光标在 awesome 这个单词的任何位置时,你可以按 `ysiw <em>` 直接给它加上着重标签:
|
||||
当光标在 “awesome” 这个单词的任何位置时,你可以按 `ysiw<em>` 直接给它加上着重标签(`<em>`):
|
||||
|
||||
```
|
||||
<p>Vim plugins are <em>awesome</em> !</p>
|
||||
@ -162,13 +162,13 @@ Vim plugins are awesome !
|
||||
|
||||
注意它聪明地加上了 `</em>` 闭合标签。
|
||||
|
||||
Vim Surround 也可以用 `ySS` 缩进文本。比如你有以下文本:
|
||||
Vim Surround 也可以用 `ySS` 缩进文本并加上标签。比如你有以下文本:
|
||||
|
||||
```
|
||||
<p>Vim plugins are <em>awesome</em> !</p>
|
||||
```
|
||||
|
||||
你可以用 `ySS <div class="normal">` 加上 `div` 标签,注意生成的段落是自动缩进的。
|
||||
你可以用 `ySS<div class="normal">` 加上 `div` 标签,注意生成的段落是自动缩进的。
|
||||
|
||||
```
|
||||
<div class="normal">
|
||||
@ -178,9 +178,9 @@ Vim Surround 也可以用 `ySS` 缩进文本。比如你有以下文本:
|
||||
|
||||
Vim Surround 有很多其它选项,你可以参照 [GitHub][7] 上的说明尝试它们。
|
||||
|
||||
### 4. Vim Gitgutter
|
||||
### 4、Vim Gitgutter
|
||||
|
||||
[Vim Gitgutter][8] 插件对使用 Git 作为版本控制工具的人来说非常有用。它会在 Vim 显示行号的列旁 `git diff` 的差异标记。假设你有如下已提交过的代码:
|
||||
[Vim Gitgutter][8] 插件对使用 Git 作为版本控制工具的人来说非常有用。它会在 Vim 的行号列旁显示 `git diff` 的差异标记。假设你有如下已提交过的代码:
|
||||
|
||||
```
|
||||
1 package main
|
||||
@ -218,15 +218,15 @@ _ 5 func main() {
|
||||
14 }
|
||||
```
|
||||
|
||||
`-` 标记表示在第 5 行和第 6 行之间删除了一行。`~` 表示第 8 行有修改,`+` 表示新增了第 11 行。
|
||||
`_` 标记表示在第 5 行和第 6 行之间删除了一行。`~` 表示第 8 行有修改,`+` 表示新增了第 11 行。
|
||||
|
||||
另外,Vim Gitgutter 允许你用 `[c` 和 `]c` 在多个有修改的块之间跳转,甚至可以用 `Leader+hs` 来暂存某个变更集。
|
||||
|
||||
这个插件提供了对变更的即时视觉反馈,如果你用 Git 的话,有了它简直是如虎添翼。
|
||||
|
||||
### 5. VIM Fugitive
|
||||
### 5、VIM Fugitive
|
||||
|
||||
[Vim Fugitive][9] 是另一个超棒的将 Git 工作流集成到 Vim 中的插件。它对 Git 做了一些封装,可以让你在 Vim 里直接执行 Git 命令并将结果集成在 Vim 界面里。这个插件有超多的特性,更多信息请访问它的 [GitHub][10] 项目页面。
|
||||
[Vim Fugitive][9] 是另一个将 Git 工作流集成到 Vim 中的超棒插件。它对 Git 做了一些封装,可以让你在 Vim 里直接执行 Git 命令并将结果集成在 Vim 界面里。这个插件有超多的特性,更多信息请访问它的 [GitHub][10] 项目页面。
|
||||
|
||||
这里有一个使用 Vim Fugitive 的基础 Git 工作流示例。设想我们已经对下面的 Go 代码做出修改,你可以用 `:Gblame` 调用 `git blame` 来查看每行最后的提交信息:
|
||||
|
||||
@ -277,7 +277,7 @@ _ 5 func main() {
|
||||
14 }
|
||||
```
|
||||
|
||||
Vim Fugitive 在分割的窗口里显示 `git status` 的输出结果。你可以在某文件名所在的行用 `-` 键暂存这个文件,再按一次 `-` 可以取消暂存。这个信息会随着你的操作自动更新:
|
||||
Vim Fugitive 在分割的窗口里显示 `git status` 的输出结果。你可以在该行按下 `-` 键用该文件的名字暂存这个文件的提交,再按一次 `-` 可以取消暂存。这个信息会随着你的操作自动更新:
|
||||
|
||||
```
|
||||
1 # On branch master
|
||||
@ -342,7 +342,7 @@ Vim Fugitive 的 GitHub 项目主页有很多屏幕录像展示了它的更多
|
||||
|
||||
### 接下来?
|
||||
|
||||
这些 Vim 插件都是程序开发者的神器!还有其它几类开发者常用的插件:自动完成插件和语法检查插件。它些大都是和具体的编程语言相关的,以后我会在一些文章中介绍它们。
|
||||
这些 Vim 插件都是程序开发者的神器!还有另外两类开发者常用的插件:自动完成插件和语法检查插件。它些大都是和具体的编程语言相关的,以后我会在一些文章中介绍它们。
|
||||
|
||||
你在写代码时是否用到一些其它 Vim 插件?请在评论区留言分享。
|
||||
|
||||
@ -353,7 +353,7 @@ via: https://opensource.com/article/19/1/vim-plugins-developers
|
||||
作者:[Ricardo Gerardi][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[pityonline](https://github.com/pityonline)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
75
published/20190123 Book Review- Fundamentals of Linux.md
Normal file
75
published/20190123 Book Review- Fundamentals of Linux.md
Normal file
@ -0,0 +1,75 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (mySoul8012)
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10565-1.html)
|
||||
[#]: subject: (Book Review: Fundamentals of Linux)
|
||||
[#]: via: (https://itsfoss.com/fundamentals-of-linux-book-review)
|
||||
[#]: author: (John Paul https://itsfoss.com/author/john/)
|
||||
|
||||
书评:《Linux 基础》
|
||||
======
|
||||
|
||||
介绍 Linux 的基础知识以及它的工作原理的书很多,今天,我们将会点评这样一本书。这次讨论的主题为 Oliver Pelz 所写的 《<ruby>[Linux 基础][1]<rt>Fundamentals of Linux</rt></ruby>》,由 [PacktPub][2] 出版。
|
||||
|
||||
[Oliver Pelz][3] 是一位拥有超过十年软件开发经验的开发者和系统管理员,拥有生物信息学学位证书。
|
||||
|
||||
### 《Linux 基础》
|
||||
|
||||
![Fundamental of Linux books][4]
|
||||
|
||||
正如可以从书名中猜到那样,《Linux 基础》的目标是为读者打下一个从了解 Linux 到学习 Linux 命令行的坚实基础。这本书一共有两百多页,因此它专注于教给用户日常任务和解决经常遇到的问题。本书是为想要成为 Linux 管理员的读者而写的。
|
||||
|
||||
第一章首先概述了虚拟化。本书作者指导了读者如何在 [VirtualBox][6] 中创建 [CentOS][5] 实例。如何克隆实例,如何使用快照。并且同时你也会学习到如何通过 SSH 命令连接到虚拟机。
|
||||
|
||||
第二章介绍了 Linux 命令行的基础知识,包括 shell 通配符,shell 展开,如何使用包含空格和特殊字符的文件名称。如何来获取命令手册的帮助页面。如何使用 `sed`、`awk` 这两个命令。如何浏览 Linux 的文件系统。
|
||||
|
||||
第三章更深入的介绍了 Linux 文件系统。你将了解如何在 Linux 中文件是如何链接的,以及如何搜索它们。你还将获得用户、组,以及文件权限的大概了解。由于本章的重点介绍了如何与文件进行交互。因此还将会介绍如何从命令行中读取文本文件,以及初步了解如何使用 vim 编辑器。
|
||||
|
||||
第四章重点介绍了如何使用命令行。以及涵盖的重要命令。如 `cat`、`sort`、`awk`、`tee`、`tar`、`rsync`、`nmap`、`htop` 等。你还将会了解到进程,以及它们如何彼此通讯。这一章还介绍了 Bash shell 脚本编程。
|
||||
|
||||
第五章同时也是本书的最后一章,将会介绍 Linux 和其他高级命令,以及网络的概念。本书的作者讨论了 Linux 是如何处理网络,并提供使用多个虚拟机的示例。同时还将会介绍如何安装新的程序,如何设置防火墙。
|
||||
|
||||
### 关于这本书的思考
|
||||
|
||||
Linux 的基础知识只有五章和少少的 200 来页可能看起来有些短,但是也涵盖了相当多的信息。同时也将会获得如何使用命令行所需要的知识的一切。
|
||||
|
||||
使用本书的时候,需要注意一件事情,即,本书专注于对命令行的关注,没有任何关于如何使用图形化的用户界面的任何教程。这是因为在 Linux 中有太多不同的桌面环境,以及很多的类似的系统应用,因此很难编写一本可以涵盖所有变种的书。此外,还有部分原因还因为本书的面向的用户群体为潜在的 Linux 管理员。
|
||||
|
||||
当我看到作者使用 Centos 教授 Linux 的时候有点惊讶。我原本以为他会使用更为常见的 Linux 的发行版本,例如 Ubuntu、Debian 或者 Fedora。原因在于 Centos 是为服务器设计的发行版本。随着时间的推移变化很小,能够为 Linux 的基础知识打下一个非常坚实的基础。
|
||||
|
||||
我自己使用 Linux 已经操作五年了。我大部分时间都在使用桌面版本的 Linux。我有些时候会使用命令行操作。但我并没有花太多的时间在那里。我使用鼠标完成了本书中涉及到的很多操作。现在呢。我同时也知道了如何通过终端做到同样的事情。这种方式不会改变我完成任务的方式,但是会有助于自己理解幕后发生的事情。
|
||||
|
||||
如果你刚刚使用 Linux,或者计划使用。我不会推荐你阅读这本书。这可能有点绝对化。但是如何你已经花了一些时间在 Linux 上。或者可以快速掌握某种技术语言。那么这本书很适合你。
|
||||
|
||||
如果你认为本书适合你的学习需求。你可以从以下链接获取到该书:
|
||||
|
||||
- [下载《Linux 基础》](https://www.packtpub.com/networking-and-servers/fundamentals-linux)
|
||||
|
||||
我们将在未来几个月内尝试点评更多 Linux 书籍,敬请关注我们。
|
||||
|
||||
你最喜欢的关于 Linux 的入门书籍是什么?请在下面的评论中告诉我们。
|
||||
|
||||
如果你发现这篇文章很有趣,请花一点时间在社交媒体、Hacker News或 [Reddit][8] 上分享。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/fundamentals-of-linux-book-review
|
||||
|
||||
作者:[John Paul][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[mySoul8012](https://github.com/mySoul8012)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/john/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.packtpub.com/networking-and-servers/fundamentals-linux
|
||||
[2]: https://www.packtpub.com/
|
||||
[3]: http://www.oliverpelz.de/index.html
|
||||
[4]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/01/fundamentals-of-linux-book-review.jpeg?resize=800%2C450&ssl=1
|
||||
[5]: https://centos.org/
|
||||
[6]: https://www.virtualbox.org/
|
||||
[7]: https://www.centos.org/
|
||||
[8]: http://reddit.com/r/linuxusersgroup
|
||||
@ -1,8 +1,8 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (HankChow)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: reviewer: (wxy)
|
||||
[#]: publisher: (wxy)
|
||||
[#]: url: (https://linux.cn/article-10566-1.html)
|
||||
[#]: subject: (Will quantum computing break security?)
|
||||
[#]: via: (https://opensource.com/article/19/1/will-quantum-computing-break-security)
|
||||
[#]: author: (Mike Bursell https://opensource.com/users/mikecamel)
|
||||
@ -10,42 +10,36 @@
|
||||
量子计算会打破现有的安全体系吗?
|
||||
======
|
||||
|
||||
> 你会希望黑客冒充成你的银行吗?
|
||||
> 你会希望<ruby>[某黑客][6]<rt>J. Random Hacker</rt></ruby>假冒你的银行吗?
|
||||
|
||||

|
||||
|
||||
近年来,量子计算机已经出现在大众的视野当中。量子计算机被认为是第六类计算机,这六类计算机包括:
|
||||
|
||||
1. **人力:** 在人造的计算工具出现之前,人类只能使用人力去进行计算。而承担计算工作的人,只能被称为“计算者”。
|
||||
|
||||
2. **模拟计算工具:** 由人类制造的一些模拟计算过程的小工具,例如<ruby>[安提凯希拉装置][1]<rt>Antikythera mechanism</rt></ruby>、星盘、计算尺等等。
|
||||
|
||||
3. **机械工具:** 在这一个类别中包括了运用到离散数学但未使用电子技术进行计算的工具,例如算盘、Charles Babbage 的<ruby>差分机<rt>Difference Engine</rt></ruby>等等。
|
||||
|
||||
4. **电子模拟计算工具:** 这一个类别的计算机多数用于军事方面的用途,例如炸弹瞄准器、枪炮瞄准装置等等。
|
||||
|
||||
5. **电子计算机:** 这个类别包含的种类就太多了,几乎包含现代所有的电子设备,从移动电话到超级计算机,都在这个类别当中。
|
||||
|
||||
6. **量子计算机:** 即将进入我们的生活,而且与之前的几类完全不同。
|
||||
近年来,<ruby>量子计算机<rt>quantum computer</rt></ruby>已经出现在大众的视野当中。量子计算机被认为是第六类计算机,这六类计算机包括:
|
||||
|
||||
1. <ruby>人力<rt>Humans</rt></ruby>:在人造的计算工具出现之前,人类只能使用人力去进行计算。而承担计算工作的人,只能被称为“计算者”。
|
||||
2. <ruby>模拟计算工具<rt>Mechanical analogue</rt></ruby>:由人类制造的一些模拟计算过程的小工具,例如<ruby>[安提凯希拉装置][1]<rt>Antikythera mechanism</rt></ruby>、<ruby>星盘<rt>astrolabe</rt></ruby>、<ruby>计算尺<rt>slide rule</rt></ruby>等等。
|
||||
3. <ruby>机械工具<rt>Mechanical digital</rt></ruby>:在这一个类别中包括了运用到离散数学但未使用电子技术进行计算的工具,例如<ruby>算盘<rt>abacus</rt></ruby>、Charles Babbage 的<ruby>差分机<rt>Difference Engine</rt></ruby>等等。
|
||||
4. <ruby>电子模拟计算工具<rt>Electronic analogue</rt></ruby>:这一个类别的计算机多数用于军事方面的用途,例如炸弹瞄准器、枪炮瞄准装置等等。
|
||||
5. <ruby>电子计算机<rt>Electronic digital</rt></ruby>:我在这里会稍微冒险一点,我觉得 Colossus 是第一台电子计算机,[^1] :这一类几乎包含现代所有的电子设备,从移动电话到超级计算机,都在这个类别当中。
|
||||
6. <ruby>量子计算机<rt>Quantum computer</rt></ruby>:即将进入我们的生活,而且与之前的几类完全不同。
|
||||
|
||||
### 什么是量子计算?
|
||||
|
||||
量子计算的概念来源于量子力学,因此使用的计算方式和我们平常使用的普通计算并不相同。如果想要深入理解,建议从参考[维基百科上的定义][2]开始。对我们来说,最重要的是理解这一点:量子计算机使用<ruby>量子位<rt>qubit</rt></ruby>进行计算。在这样的前提下,对于很多数学算法和运算操作,量子计算机的计算速度会比普通计算机要快得多。
|
||||
<ruby>量子计算<rt>Quantum computing</rt></ruby>的概念来源于<ruby>量子力学<rt>quantum mechanics</rt></ruby>,使用的计算方式和我们平常使用的普通计算非常不同。如果想要深入理解,建议从参考[维基百科上的定义][2]开始。对我们来说,最重要的是理解这一点:量子计算机使用<ruby>量子位<rt>qubit</rt></ruby>进行计算。在这样的前提下,对于很多数学算法和运算操作,量子计算机的计算速度会比普通计算机要快得多。
|
||||
|
||||
这里的“快得多”是按数量级来说的“快得多”。在某些情况下,一个计算任务如果由普通计算机来执行,可能要耗费几年或者几十年才能完成,但如果由量子计算机来执行,就只需要几秒钟。这样的速度甚至令人感到可怕。因为量子计算机会非常擅长信息的加密解密计算,即使在没有密钥的情况下,也能快速完成繁重的计算任务。
|
||||
|
||||
这意味着,如果拥有足够强大的量子计算机,那么你的所有信息都会被一览无遗,任何被加密的数据都可以被正确解密出来,甚至伪造数字签名也会成为可能。这确实是一个严重的问题。毕竟谁也不想被黑客冒充成自己在用的银行,更不希望自己在区块链上的交易被篡改得面目全非。
|
||||
这意味着,如果拥有足够强大的量子计算机,那么你的所有信息都会被一览无遗,任何被加密的数据都可以被正确解密出来,甚至伪造数字签名也会成为可能。这确实是一个严重的问题。谁也不想被某个黑客冒充成自己在用的银行,更不希望自己在区块链上的交易被篡改得面目全非。
|
||||
|
||||
### 好消息
|
||||
|
||||
尽管上面的提到的问题非常可怕,但也不需要太担心。
|
||||
|
||||
首先,如果要实现上面提到的能力,一台可以操作大量量子位的量子计算机是必不可少的,而这个硬件上的要求就是一个很高的门槛。目前普遍认为,规模大得足以有效破解经典加密算法的量子计算机在最近几年还不可能出现。
|
||||
首先,如果要实现上面提到的能力,一台可以操作大量量子位的量子计算机是必不可少的,而这个硬件上的要求就是一个很高的门槛。[^4] 目前普遍认为,规模大得足以有效破解经典加密算法的量子计算机在最近几年还不可能出现。
|
||||
|
||||
其次,除了攻击现有的加密算法需要大量的量子位以外,还需要很多量子位来保证容错性。
|
||||
|
||||
还有,尽管确实有一些理论上的模型阐述了量子计算机如何对一些现有的算法作出攻击,但是要让这样的理论模型实际运作起来的难度会比我们想象中大得多。事实上,有一些攻击手段也是未被完全确认是可行的,又或者这些攻击手段还需要继续耗费很多年的改进才能到达如斯恐怖的程度。
|
||||
还有,尽管确实有一些理论上的模型阐述了量子计算机如何对一些现有的算法作出攻击,但是要让这样的理论模型实际运作起来的难度会比我们[^5] 想象中大得多。事实上,有一些攻击手段也是未被完全确认是可行的,又或者这些攻击手段还需要继续耗费很多年的改进才能到达如斯恐怖的程度。
|
||||
|
||||
最后,还有很多专业人士正在研究能够防御量子计算的算法(这样的算法也被称为“<ruby>后量子算法<rt>post-quantum algorithms</rt></ruby>”)。如果这些防御算法经过测试以后投入使用,我们就可以使用这些算法进行加密,来对抗量子计算了。
|
||||
|
||||
@ -55,23 +49,25 @@
|
||||
|
||||
但我们也并不是高枕无忧了,以下两个问题就值得我们关注:
|
||||
|
||||
1. 人们在设计应用系统的时候仍然没有对量子计算作出太多的考量。如果设计的系统可能会使用 10 年以上,又或者数据存储和加密的时间跨度在 10 年以上,那么就必须考虑量子计算在未来会不会对系统造成不利的影响。
|
||||
|
||||
2. 新出现的防御量子计算的算法可能会是专有的。也就是说,如果基于这些防御量子计算的算法来设计系统,那么在系统落地的时候,可能会需要为此付费。尽管我是支持开源的,尤其是[开源密码学][3],但我最担心的就是这方面的内容无法被开源。而且,在建立新的协议标准时,无论是故意的,无意的,还是别无选择,都很可能不会使用开源的专有算法。
|
||||
|
||||
|
||||
|
||||
1. 人们在设计应用系统的时候仍然没有对量子计算作出太多的考量。如果设计的系统可能会使用 10 年以上,又或者数据加密和签名的时间跨度在 10 年以上,那么就必须考虑量子计算在未来会不会对系统造成不利的影响。
|
||||
2. 新出现的防御量子计算的算法可能会是专有的。也就是说,如果基于这些防御量子计算的算法来设计系统,那么在系统落地的时候,可能会需要为此付费。尽管我是支持开源的,尤其是[开源密码学][3],但我最担心的就是无法开源这方面的内容。而且最糟糕的是,在建立新的协议标准时(不管是事实标准还是通过标准组织建立的标准),无论是故意的,还是无意忽略,或者是没有好的开源替代品,他们都很可能使用专有算法而排除使用开源算法。
|
||||
|
||||
### 我们要怎样做?
|
||||
|
||||
幸运的是,针对上述两个问题,我们还是有应对措施的。首先,在整个系统的设计阶段,就需要考虑到它是否会受到量子计算的影响,并作出相应的规划。当然了,不需要现在就立即采取行动,因为当前的技术水平也没法实现有效的方案,但至少也要[在加密方面保持敏捷性][4],以便在任何需要的时候为你的协议和系统更换更有效的加密算法。
|
||||
幸运的是,针对上述两个问题,我们还是有应对措施的。首先,在整个系统的设计阶段,就需要考虑到它是否会受到量子计算的影响,并作出相应的规划。当然了,不需要现在就立即采取行动,因为当前的技术水平也没法实现有效的方案,但至少也要[在加密方面保持敏捷性][4],以便在任何需要的时候为你的协议和系统更换更有效的加密算法。[^7]
|
||||
|
||||
其次是参与开源运动。尽可能鼓励密码学方面的有识之士团结起来,支持开放标准,并投入对非专有的防御量子计算的算法研究当中去。这一点也算是当务之急,因为号召更多的人重视起来并加入研究,比研究本身更为重要。
|
||||
|
||||
|
||||
|
||||
本文首发于《[Alice, Eve, and Bob][5]》,并在作者同意下重新发表。
|
||||
|
||||
[^1]: 我认为把它称为第一台电子可编程计算机是公平的。我知道有早期的非可编程的,也有些人声称是 ENIAC,但我没有足够的空间或精力在这里争论这件事。
|
||||
[^2]: No。
|
||||
[^3]: See 2. Don't get me wrong, by the way—I grew up near Weston-super-Mare, and it's got things going for it, but it's not Mayfair.
|
||||
[^4]: 如果量子物理学家说很难,那么在我看来,就很难。
|
||||
[^5]: 而且我假设我们都不是量子物理学家或数学家。
|
||||
[^6]: I'm definitely not.
|
||||
[^7]: 而且不仅仅是出于量子计算的原因:我们现有的一些经典算法很可能会陷入其他非量子攻击,例如新的数学方法。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/will-quantum-computing-break-security
|
||||
@ -79,7 +75,7 @@ via: https://opensource.com/article/19/1/will-quantum-computing-break-security
|
||||
作者:[Mike Bursell][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[HankChow](https://github.com/HankChow)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -90,4 +86,4 @@ via: https://opensource.com/article/19/1/will-quantum-computing-break-security
|
||||
[3]: https://opensource.com/article/17/10/many-eyes
|
||||
[4]: https://aliceevebob.com/2017/04/04/disbelieving-the-many-eyes-hypothesis/
|
||||
[5]: https://aliceevebob.com/2019/01/08/will-quantum-computing-break-security/
|
||||
|
||||
[6]: https://www.techopedia.com/definition/20225/j-random-hacker
|
||||
@ -1,99 +0,0 @@
|
||||
translating by Cycoe
|
||||
Cycoe 翻译中
|
||||
8 KDE Plasma Tips and Tricks to Improve Your Productivity
|
||||
======
|
||||
|
||||
[#] leon-shi is translating
|
||||

|
||||
|
||||
KDE's Plasma is easily one of the most powerful desktop environments available for Linux. It's highly configurable, and it looks pretty good, too. That doesn't amount to a whole lot unless you can actually get things done.
|
||||
|
||||
You can easily configure Plasma and make use of a lot of its convenient and time-saving features to boost your productivity and have a desktop that empowers you, rather than getting in your way.
|
||||
|
||||
These tips aren't in any particular order, so you don't need to prioritize. Pick the ones that best fit your workflow.
|
||||
|
||||
**Related** : [10 of the Best KDE Plasma Applications You Should Try][1]
|
||||
|
||||
### 1. Multimedia Controls
|
||||
|
||||
This isn't so much of a tip as it is something that's good to keep in mind. Plasma keeps multimedia controls everywhere. You don't need to open your media player every time you need to pause, resume, or skip a song; you can mouse over the minimized window or even control it via the lock screen. There's no need to scramble to log in to change a song or because you forgot to pause one.
|
||||
|
||||
### 2. KRunner
|
||||
|
||||
![KDE Plasma KRunner][2]
|
||||
|
||||
KRunner is an often under-appreciated feature of the Plasma desktop. Most people are used to digging through the application launcher menu to find the program that they're looking to launch. That's not necessary with KRunner.
|
||||
|
||||
To use KRunner, make sure that your focus is on the desktop itself. (Click on it instead of a window.) Then, start typing the name of the program that you want. KRunner will automatically drop down from the top of your screen with suggestions. Click or press Enter on the one you're looking for. It's much faster than remembering which category your program is under.
|
||||
|
||||
### 3. Jump Lists
|
||||
|
||||
![KDE Plasma Jump Lists][3]
|
||||
|
||||
Jump lists are a fairly recent addition to the Plasma desktop. They allow you to launch an application directly to a specific section or feature.
|
||||
|
||||
So if you have a launcher on a menu bar, you can right-click and get a list of places to jump to. Select where you want to go, and you're off.
|
||||
|
||||
### 4. KDE Connect
|
||||
|
||||
![KDE Connect Menu Android][4]
|
||||
|
||||
[KDE Connect][5] is a massive help if you have an Android phone. It connects the phone to your desktop so you can share things seamlessly between the devices.
|
||||
|
||||
With KDE Connect, you can see your [Android device's notification][6] on your desktop in real time. It also enables you to send and receive text messages from Plasma without ever picking up your phone.
|
||||
|
||||
KDE Connect also lets you send files and share web pages between your phone and your computer. You can easily move from one device to the other without a lot of hassle or losing your train of thought.
|
||||
|
||||
### 5. Plasma Vaults
|
||||
|
||||
![KDE Plasma Vault][7]
|
||||
|
||||
Plasma Vaults are another new addition to the Plasma desktop. They are KDE's simple solution to encrypted files and folders. If you don't work with encrypted files, this one won't really save you any time. If you do, though, vaults are a much simpler approach.
|
||||
|
||||
Plasma Vaults let you create encrypted directories as a regular user without root and manage them from your task bar. You can mount and unmount the directories on the fly without the need for external programs or additional privileges.
|
||||
|
||||
### 6. Pager Widget
|
||||
|
||||
![KDE Plasma Pager][8]
|
||||
|
||||
Configure your desktop with the pager widget. It allows you to easily access three additional workspaces for even more screen room.
|
||||
|
||||
Add the widget to your menu bar, and you can slide between multiple workspaces. These are all the size of your screen, so you gain multiple times the total screen space. That lets you lay out more windows without getting confused by a minimized mess or disorganization.
|
||||
|
||||
### 7. Create a Dock
|
||||
|
||||
![KDE Plasma Dock][9]
|
||||
|
||||
Plasma is known for its flexibility and the room it allows for configuration. Use that to your advantage. If you have programs that you're always using, consider setting up an OS X style dock with your most used applications. You'll be able to get them with a single click rather than going through a menu or typing in their name.
|
||||
|
||||
### 8. Add a File Tree to Dolphin
|
||||
|
||||
![Plasma Dolphin Directory][10]
|
||||
|
||||
It's much easier to navigate folders in a directory tree. Dolphin, Plasma's default file manager, has built-in functionality to display a directory listing in the form of a tree on the side of the folder window.
|
||||
|
||||
To enable the directory tree, click on the "Control" tab, then "Configure Dolphin," "View Modes," and "Details." Finally, select "Expandable Folders."
|
||||
|
||||
Remember that these tips are just tips. Don't try to force yourself to do something that's getting in your way. You may hate using file trees in Dolphin. You may never use Pager. That's alright. There may even be something that you personally like that's not listed here. Do what works for you. That said, at least a few of these should shave some serious time out of your work day.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.maketecheasier.com/kde-plasma-tips-tricks-improve-productivity/
|
||||
|
||||
作者:[Nick Congleton][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.maketecheasier.com/author/nickcongleton/
|
||||
[1]:https://www.maketecheasier.com/10-best-kde-plasma-applications/ (10 of the Best KDE Plasma Applications You Should Try)
|
||||
[2]:https://www.maketecheasier.com/assets/uploads/2017/10/pe-krunner.jpg (KDE Plasma KRunner)
|
||||
[3]:https://www.maketecheasier.com/assets/uploads/2017/10/pe-jumplist.jpg (KDE Plasma Jump Lists)
|
||||
[4]:https://www.maketecheasier.com/assets/uploads/2017/05/kde-connect-menu-e1494899929112.jpg (KDE Connect Menu Android)
|
||||
[5]:https://www.maketecheasier.com/send-receive-sms-linux-kde-connect/
|
||||
[6]:https://www.maketecheasier.com/android-notifications-ubuntu-kde-connect/
|
||||
[7]:https://www.maketecheasier.com/assets/uploads/2017/10/pe-vault.jpg (KDE Plasma Vault)
|
||||
[8]:https://www.maketecheasier.com/assets/uploads/2017/10/pe-pager.jpg (KDE Plasma Pager)
|
||||
[9]:https://www.maketecheasier.com/assets/uploads/2017/10/pe-dock.jpg (KDE Plasma Dock)
|
||||
[10]:https://www.maketecheasier.com/assets/uploads/2017/10/pe-dolphin.jpg (Plasma Dolphin Directory)
|
||||
@ -1,3 +1,4 @@
|
||||
name1e5s translating
|
||||
Qalculate! – The Best Calculator Application in The Entire Universe
|
||||
======
|
||||
I have been a GNU-Linux user and a [Debian][1] user for more than a decade. As I started using the desktop more and more, it seemed to me that apart from few web-based services most of my needs were being met with [desktop applications][2] within Debian itself.
|
||||
|
||||
@ -1,236 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (hopefully2333)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (The Evil-Twin Framework: A tool for improving WiFi security)
|
||||
[#]: via: (https://opensource.com/article/19/1/evil-twin-framework)
|
||||
[#]: author: (André Esser https://opensource.com/users/andreesser)
|
||||
|
||||
The Evil-Twin Framework: A tool for improving WiFi security
|
||||
======
|
||||
Learn about a pen-testing tool intended to test the security of WiFi access points for all types of threats.
|
||||

|
||||
|
||||
The increasing number of devices that connect over-the-air to the internet over-the-air and the wide availability of WiFi access points provide many opportunities for attackers to exploit users. By tricking users to connect to [rogue access points][1], hackers gain full control over the users' network connection, which allows them to sniff and alter traffic, redirect users to malicious sites, and launch other attacks over the network..
|
||||
|
||||
To protect users and teach them to avoid risky online behaviors, security auditors and researchers must evaluate users' security practices and understand the reasons they connect to WiFi access points without being confident they are safe. There are a significant number of tools that can conduct WiFi audits, but no single tool can test the many different attack scenarios and none of the tools integrate well with one another.
|
||||
|
||||
The **Evil-Twin Framework** (ETF) aims to fix these problems in the WiFi auditing process by enabling auditors to examine multiple scenarios and integrate multiple tools. This article describes the framework and its functionalities, then provides some examples to show how it can be used.
|
||||
|
||||
### The ETF architecture
|
||||
|
||||
The ETF framework was written in [Python][2] because the development language is very easy to read and make contributions to. In addition, many of the ETF's libraries, such as **[Scapy][3]** , were already developed for Python, making it easy to use them for ETF.
|
||||
|
||||
The ETF architecture (Figure 1) is divided into different modules that interact with each other. The framework's settings are all written in a single configuration file. The user can verify and edit the settings through the user interface via the **ConfigurationManager** class. Other modules can only read these settings and run according to them.
|
||||
|
||||
![Evil-Twin Framework Architecture][5]
|
||||
|
||||
Figure 1: Evil-Twin framework architecture
|
||||
|
||||
The ETF supports multiple user interfaces that interact with the framework. The current default interface is an interactive console, similar to the one on [Metasploit][6]. A graphical user interface (GUI) and a command line interface (CLI) are under development for desktop/browser use, and mobile interfaces may be an option in the future. The user can edit the settings in the configuration file using the interactive console (and eventually with the GUI). The user interface can interact with every other module that exists in the framework.
|
||||
|
||||
The WiFi module ( **AirCommunicator** ) was built to support a wide range of WiFi capabilities and attacks. The framework identifies three basic pillars of Wi-Fi communication: **packet sniffing** , **custom packet injection** , and **access point creation**. The three main WiFi communication modules are **AirScanner** , **AirInjector** , and **AirHost** , which are responsible for packet sniffing, packet injection, and access point creation, respectively. The three classes are wrapped inside the main WiFi module, AirCommunicator, which reads the configuration file before starting the services. Any type of WiFi attack can be built using one or more of these core features.
|
||||
|
||||
To enable man-in-the-middle (MITM) attacks, which are a common way to attack WiFi clients, the framework has an integrated module called ETFITM (Evil-Twin Framework-in-the-Middle). This module is responsible for the creation of a web proxy used to intercept and manipulate HTTP/HTTPS traffic.
|
||||
|
||||
There are many other tools that can leverage the MITM position created by the ETF. Through its extensibility, ETF can support them—and, instead of having to call them separately, you can add the tools to the framework just by extending the Spawner class. This enables a developer or security auditor to call the program with a preconfigured argument string from within the framework.
|
||||
|
||||
The other way to extend the framework is through plugins. There are two categories of plugins: **WiFi plugins** and **MITM plugins**. MITM plugins are scripts that can run while the MITM proxy is active. The proxy passes the HTTP(S) requests and responses through to the plugins where they can be logged or manipulated. WiFi plugins follow a more complex flow of execution but still expose a fairly simple API to contributors who wish to develop and use their own plugins. WiFi plugins can be further divided into three categories, one for each of the core WiFi communication modules.
|
||||
|
||||
Each of the core modules has certain events that trigger the execution of a plugin. For instance, AirScanner has three defined events to which a response can be programmed. The events usually correspond to a setup phase before the service starts running, a mid-execution phase while the service is running, and a teardown or cleanup phase after a service finishes. Since Python allows multiple inheritance, one plugin can subclass more than one plugin class.
|
||||
|
||||
Figure 1 above is a summary of the framework's architecture. Lines pointing away from the ConfigurationManager mean that the module reads information from it and lines pointing towards it mean that the module can write/edit configurations.
|
||||
|
||||
### Examples of using the Evil-Twin Framework
|
||||
|
||||
There are a variety of ways ETF can conduct penetration testing on WiFi network security or work on end users' awareness of WiFi security. The following examples describe some of the framework's pen-testing functionalities, such as access point and client detection, WPA and WEP access point attacks, and evil twin access point creation.
|
||||
|
||||
These examples were devised using ETF with WiFi cards that allow WiFi traffic capture. They also utilize the following abbreviations for ETF setup commands:
|
||||
|
||||
* **APS** access point SSID
|
||||
* **APB** access point BSSID
|
||||
* **APC** access point channel
|
||||
* **CM** client MAC address
|
||||
|
||||
|
||||
|
||||
In a real testing scenario, make sure to replace these abbreviations with the correct information.
|
||||
|
||||
#### Capturing a WPA 4-way handshake after a de-authentication attack
|
||||
|
||||
This scenario (Figure 2) takes two aspects into consideration: the de-authentication attack and the possibility of catching a 4-way WPA handshake. The scenario starts with a running WPA/WPA2-enabled access point with one connected client device (in this case, a smartphone). The goal is to de-authenticate the client with a general de-authentication attack then capture the WPA handshake once it tries to reconnect. The reconnection will be done manually immediately after being de-authenticated.
|
||||
|
||||
![Scenario for capturing a WPA handshake after a de-authentication attack][8]
|
||||
|
||||
Figure 2: Scenario for capturing a WPA handshake after a de-authentication attack
|
||||
|
||||
The consideration in this example is the ETF's reliability. The goal is to find out if the tools can consistently capture the WPA handshake. The scenario will be performed multiple times with each tool to check its reliability when capturing the WPA handshake.
|
||||
|
||||
There is more than one way to capture a WPA handshake using the ETF. One way is to use a combination of the AirScanner and AirInjector modules; another way is to just use the AirInjector. The following scenario uses a combination of both modules.
|
||||
|
||||
The ETF launches the AirScanner module and analyzes the IEEE 802.11 frames to find a WPA handshake. Then the AirInjector can launch a de-authentication attack to force a reconnection. The following steps must be done to accomplish this on the ETF:
|
||||
|
||||
1. Enter the AirScanner configuration mode: **config airscanner**
|
||||
2. Configure the AirScanner to not hop channels: **config airscanner**
|
||||
3. Set the channel to sniff the traffic on the access point channel (APC): **set fixed_sniffing_channel = <APC>**
|
||||
4. Start the AirScanner module with the CredentialSniffer plugin: **start airscanner with credentialsniffer**
|
||||
5. Add a target access point BSSID (APS) from the sniffed access points list: **add aps where ssid = <APS>**
|
||||
6. Start the AirInjector, which by default lauches the de-authentication attack: **start airinjector**
|
||||
|
||||
|
||||
|
||||
This simple set of commands enables the ETF to perform an efficient and successful de-authentication attack on every test run. The ETF can also capture the WPA handshake on every test run. The following code makes it possible to observe the ETF's successful execution.
|
||||
|
||||
```
|
||||
███████╗████████╗███████╗
|
||||
██╔════╝╚══██╔══╝██╔════╝
|
||||
█████╗ ██║ █████╗
|
||||
██╔══╝ ██║ ██╔══╝
|
||||
███████╗ ██║ ██║
|
||||
╚══════╝ ╚═╝ ╚═╝
|
||||
|
||||
|
||||
[+] Do you want to load an older session? [Y/n]: n
|
||||
[+] Creating new temporary session on 02/08/2018
|
||||
[+] Enter the desired session name:
|
||||
ETF[etf/aircommunicator/]::> config airscanner
|
||||
ETF[etf/aircommunicator/airscanner]::> listargs
|
||||
sniffing_interface = wlan1; (var)
|
||||
probes = True; (var)
|
||||
beacons = True; (var)
|
||||
hop_channels = false; (var)
|
||||
fixed_sniffing_channel = 11; (var)
|
||||
ETF[etf/aircommunicator/airscanner]::> start airscanner with
|
||||
arpreplayer caffelatte credentialsniffer packetlogger selfishwifi
|
||||
ETF[etf/aircommunicator/airscanner]::> start airscanner with credentialsniffer
|
||||
[+] Successfully added credentialsniffer plugin.
|
||||
[+] Starting packet sniffer on interface 'wlan1'
|
||||
[+] Set fixed channel to 11
|
||||
ETF[etf/aircommunicator/airscanner]::> add aps where ssid = CrackWPA
|
||||
ETF[etf/aircommunicator/airscanner]::> start airinjector
|
||||
ETF[etf/aircommunicator/airscanner]::> [+] Starting deauthentication attack
|
||||
- 1000 bursts of 1 packets
|
||||
- 1 different packets
|
||||
[+] Injection attacks finished executing.
|
||||
[+] Starting post injection methods
|
||||
[+] Post injection methods finished
|
||||
[+] WPA Handshake found for client '70:3e:ac:bb:78:64' and network 'CrackWPA'
|
||||
```
|
||||
|
||||
#### Launching an ARP replay attack and cracking a WEP network
|
||||
|
||||
The next scenario (Figure 3) will also focus on the [Address Resolution Protocol][9] (ARP) replay attack's efficiency and the speed of capturing the WEP data packets containing the initialization vectors (IVs). The same network may require a different number of caught IVs to be cracked, so the limit for this scenario is 50,000 IVs. If the network is cracked during the first test with less than 50,000 IVs, that number will be the new limit for the following tests on the network. The cracking tool to be used will be **aircrack-ng**.
|
||||
|
||||
The test scenario starts with an access point using WEP encryption and an offline client that knows the key—the key for testing purposes is 12345, but it can be a larger and more complex key. Once the client connects to the WEP access point, it will send out a gratuitous ARP packet; this is the packet that's meant to be captured and replayed. The test ends once the limit of packets containing IVs is captured.
|
||||
|
||||
![Scenario for capturing a WPA handshake after a de-authentication attack][11]
|
||||
|
||||
Figure 3: Scenario for capturing a WPA handshake after a de-authentication attack
|
||||
|
||||
ETF uses Python's Scapy library for packet sniffing and injection. To minimize known performance problems in Scapy, ETF tweaks some of its low-level libraries to significantly speed packet injection. For this specific scenario, the ETF uses **tcpdump** as a background process instead of Scapy for more efficient packet sniffing, while Scapy is used to identify the encrypted ARP packet.
|
||||
|
||||
This scenario requires the following commands and operations to be performed on the ETF:
|
||||
|
||||
1. Enter the AirScanner configuration mode: **config airscanner**
|
||||
2. Configure the AirScanner to not hop channels: **set hop_channels = false**
|
||||
3. Set the channel to sniff the traffic on the access point channel (APC): **set fixed_sniffing_channel = <APC>**
|
||||
4. Enter the ARPReplayer plugin configuration mode: **config arpreplayer**
|
||||
5. Set the target access point BSSID (APB) of the WEP network: **set target_ap_bssid <APB>**
|
||||
6. Start the AirScanner module with the ARPReplayer plugin: **start airscanner with arpreplayer**
|
||||
|
||||
|
||||
|
||||
After executing these commands, ETF correctly identifies the encrypted ARP packet, then successfully performs an ARP replay attack, which cracks the network.
|
||||
|
||||
#### Launching a catch-all honeypot
|
||||
|
||||
The scenario in Figure 4 creates multiple access points with the same SSID. This technique discovers the encryption type of a network that was probed for but out of reach. By launching multiple access points with all security settings, the client will automatically connect to the one that matches the security settings of the locally cached access point information.
|
||||
|
||||
![Scenario for capturing a WPA handshake after a de-authentication attack][13]
|
||||
|
||||
Figure 4: Scenario for capturing a WPA handshake after a de-authentication attack
|
||||
|
||||
Using the ETF, it is possible to configure the **hostapd** configuration file then launch the program in the background. Hostapd supports launching multiple access points on the same wireless card by configuring virtual interfaces, and since it supports all types of security configurations, a complete catch-all honeypot can be set up. For the WEP and WPA(2)-PSK networks, a default password is used, and for the WPA(2)-EAP, an "accept all" policy is configured.
|
||||
|
||||
For this scenario, the following commands and operations must be performed on the ETF:
|
||||
|
||||
1. Enter the APLauncher configuration mode: **config aplauncher**
|
||||
2. Set the desired access point SSID (APS): **set ssid = <APS>**
|
||||
3. Configure the APLauncher as a catch-all honeypot: **set catch_all_honeypot = true**
|
||||
4. Start the AirHost module: **start airhost**
|
||||
|
||||
|
||||
|
||||
With these commands, the ETF can launch a complete catch-all honeypot with all types of security configurations. ETF also automatically launches the DHCP and DNS servers that allow clients to stay connected to the internet. ETF offers a better, faster, and more complete solution to create catch-all honeypots. The following code enables the successful execution of the ETF to be observed.
|
||||
|
||||
```
|
||||
███████╗████████╗███████╗
|
||||
██╔════╝╚══██╔══╝██╔════╝
|
||||
█████╗ ██║ █████╗
|
||||
██╔══╝ ██║ ██╔══╝
|
||||
███████╗ ██║ ██║
|
||||
╚══════╝ ╚═╝ ╚═╝
|
||||
|
||||
|
||||
[+] Do you want to load an older session? [Y/n]: n
|
||||
[+] Creating ne´,cxzw temporary session on 03/08/2018
|
||||
[+] Enter the desired session name:
|
||||
ETF[etf/aircommunicator/]::> config aplauncher
|
||||
ETF[etf/aircommunicator/airhost/aplauncher]::> setconf ssid CatchMe
|
||||
ssid = CatchMe
|
||||
ETF[etf/aircommunicator/airhost/aplauncher]::> setconf catch_all_honeypot true
|
||||
catch_all_honeypot = true
|
||||
ETF[etf/aircommunicator/airhost/aplauncher]::> start airhost
|
||||
[+] Killing already started processes and restarting network services
|
||||
[+] Stopping dnsmasq and hostapd services
|
||||
[+] Access Point stopped...
|
||||
[+] Running airhost plugins pre_start
|
||||
[+] Starting hostapd background process
|
||||
[+] Starting dnsmasq service
|
||||
[+] Running airhost plugins post_start
|
||||
[+] Access Point launched successfully
|
||||
[+] Starting dnsmasq service
|
||||
```
|
||||
|
||||
### Conclusions and future work
|
||||
|
||||
These scenarios use common and well-known attacks to help validate the ETF's capabilities for testing WiFi networks and clients. The results also validate that the framework's architecture enables new attack vectors and features to be developed on top of it while taking advantage of the platform's existing capabilities. This should accelerate development of new WiFi penetration-testing tools, since a lot of the code is already written. Furthermore, the fact that complementary WiFi technologies are all integrated in a single tool will make WiFi pen-testing simpler and more efficient.
|
||||
|
||||
The ETF's goal is not to replace existing tools but to complement them and offer a broader choice to security auditors when conducting WiFi pen-testing and improving user awareness.
|
||||
|
||||
The ETF is an open source project [available on GitHub][14] and community contributions to its development are welcomed. Following are some of the ways you can help.
|
||||
|
||||
One of the limitations of current WiFi pen-testing is the inability to log important events during tests. This makes reporting identified vulnerabilities both more difficult and less accurate. The framework could implement a logger that can be accessed by every class to create a pen-testing session report.
|
||||
|
||||
The ETF tool's capabilities cover many aspects of WiFi pen-testing. On one hand, it facilitates the phases of WiFi reconnaissance, vulnerability discovery, and attack. On the other hand, it doesn't offer a feature that facilitates the reporting phase. Adding the concept of a session and a session reporting feature, such as the logging of important events during a session, would greatly increase the value of the tool for real pen-testing scenarios.
|
||||
|
||||
Another valuable contribution would be extending the framework to facilitate WiFi fuzzing. The IEEE 802.11 protocol is very complex, and considering there are multiple implementations of it, both on the client and access point side, it's safe to assume these implementations contain bugs and even security flaws. These bugs could be discovered by fuzzing IEEE 802.11 protocol frames. Since Scapy allows custom packet creation and injection, a fuzzer can be implemented through it.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/evil-twin-framework
|
||||
|
||||
作者:[André Esser][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/andreesser
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Rogue_access_point
|
||||
[2]: https://www.python.org/
|
||||
[3]: https://scapy.net
|
||||
[4]: /file/417776
|
||||
[5]: https://opensource.com/sites/default/files/uploads/pic1.png (Evil-Twin Framework Architecture)
|
||||
[6]: https://www.metasploit.com
|
||||
[7]: /file/417781
|
||||
[8]: https://opensource.com/sites/default/files/uploads/pic2.png (Scenario for capturing a WPA handshake after a de-authentication attack)
|
||||
[9]: https://en.wikipedia.org/wiki/Address_Resolution_Protocol
|
||||
[10]: /file/417786
|
||||
[11]: https://opensource.com/sites/default/files/uploads/pic3.png (Scenario for capturing a WPA handshake after a de-authentication attack)
|
||||
[12]: /file/417791
|
||||
[13]: https://opensource.com/sites/default/files/uploads/pic4.png (Scenario for capturing a WPA handshake after a de-authentication attack)
|
||||
[14]: https://github.com/Esser420/EvilTwinFramework
|
||||
@ -1,398 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( luming)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To Copy A File/Folder From A Local System To Remote System In Linux?)
|
||||
[#]: via: (https://www.2daygeek.com/linux-scp-rsync-pscp-command-copy-files-folders-in-multiple-servers-using-shell-script/)
|
||||
[#]: author: (Prakash Subramanian https://www.2daygeek.com/author/prakash/)
|
||||
|
||||
How To Copy A File/Folder From A Local System To Remote System In Linux?
|
||||
======
|
||||
|
||||
Copying a file from one server to another server or local to remote is one of the routine task for Linux administrator.
|
||||
|
||||
If anyone says no, i won’t accept because this is one of the regular activity wherever you go.
|
||||
|
||||
It can be done in many ways and we are trying to cover all the possible options.
|
||||
|
||||
You can choose the one which you would prefer. Also, check other commands as well that may help you for some other purpose.
|
||||
|
||||
I have tested all these commands and script in my test environment so, you can use this for your routine work.
|
||||
|
||||
By default every one go with SCP because it’s one of the native command that everyone use for file copy. But commands which is listed in this article are be smart so, give a try if you would like to try new things.
|
||||
|
||||
This can be done in below four ways easily.
|
||||
|
||||
* **`SCP:`** scp copies files between hosts on a network. It uses ssh for data transfer, and uses the same authentication and provides the same security as ssh.
|
||||
* **`RSYNC:`** rsync is a fast and extraordinarily versatile file copying tool. It can copy locally, to/from another host over any remote shell, or to/from a remote rsync daemon.
|
||||
* **`PSCP:`** pscp is a program for copying files in parallel to a number of hosts. It provides features such as passing a password to scp, saving output to files, and timing out.
|
||||
* **`PRSYNC:`** prsync is a program for copying files in parallel to a number of hosts. It provides features such as passing a password to ssh, saving output to files, and timing out.
|
||||
|
||||
|
||||
|
||||
### Method-1: Copy Files/Folders From A Local System To Remote System In Linux Using SCP Command?
|
||||
|
||||
scp command allow us to copy files/folders from a local system to remote system.
|
||||
|
||||
We are going to copy the `output.txt` file from my local system to `2g.CentOS.com` remote system under `/opt/backup` directory.
|
||||
|
||||
```
|
||||
# scp output.txt root@2g.CentOS.com:/opt/backup
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
```
|
||||
|
||||
We are going to copy two files `output.txt` and `passwd-up.sh` files from my local system to `2g.CentOS.com` remote system under `/opt/backup` directory.
|
||||
|
||||
```
|
||||
# scp output.txt passwd-up.sh root@2g.CentOS.com:/opt/backup
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
passwd-up.sh 100% 877 0.9KB/s 00:00
|
||||
```
|
||||
|
||||
We are going to copy the `shell-script` directory from my local system to `2g.CentOS.com` remote system under `/opt/backup` directory.
|
||||
|
||||
This will copy the `shell-script` directory and associated files under `/opt/backup` directory.
|
||||
|
||||
```
|
||||
# scp -r /home/daygeek/2g/shell-script/ [email protected]:/opt/backup/
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
ovh.sh 100% 76 0.1KB/s 00:00
|
||||
passwd-up.sh 100% 877 0.9KB/s 00:00
|
||||
passwd-up1.sh 100% 7 0.0KB/s 00:00
|
||||
server-list.txt 100% 23 0.0KB/s 00:00
|
||||
```
|
||||
|
||||
### Method-2: Copy Files/Folders From A Local System To Multiple Remote System In Linux Using Shell Script with scp Command?
|
||||
|
||||
If you would like to copy the same file into multiple remote servers then create the following small shell script to achieve this.
|
||||
|
||||
To do so, get the servers list and add those into `server-list.txt` file. Make sure you have to update the servers list into `server-list.txt` file. Each server should be in separate line.
|
||||
|
||||
Finally mention the file location which you want to copy like below.
|
||||
|
||||
```
|
||||
# file-copy.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
scp /home/daygeek/2g/shell-script/output.txt [email protected]$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
Once you done, set an executable permission to password-update.sh file.
|
||||
|
||||
```
|
||||
# chmod +x file-copy.sh
|
||||
```
|
||||
|
||||
Finally run the script to achieve this.
|
||||
|
||||
```
|
||||
# ./file-copy.sh
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
```
|
||||
|
||||
Use the following script to copy the multiple files into multiple remote servers.
|
||||
|
||||
```
|
||||
# file-copy.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
scp /home/daygeek/2g/shell-script/output.txt passwd-up.sh [email protected]$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
The below output shows all the files twice as this copied into two servers.
|
||||
|
||||
```
|
||||
# ./file-cp.sh
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
passwd-up.sh 100% 877 0.9KB/s 00:00
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
passwd-up.sh 100% 877 0.9KB/s 00:00
|
||||
```
|
||||
|
||||
Use the following script to copy the directory recursively into multiple remote servers.
|
||||
|
||||
```
|
||||
# file-copy.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
scp -r /home/daygeek/2g/shell-script/ [email protected]$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
Output for the above script.
|
||||
|
||||
```
|
||||
# ./file-cp.sh
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
ovh.sh 100% 76 0.1KB/s 00:00
|
||||
passwd-up.sh 100% 877 0.9KB/s 00:00
|
||||
passwd-up1.sh 100% 7 0.0KB/s 00:00
|
||||
server-list.txt 100% 23 0.0KB/s 00:00
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
ovh.sh 100% 76 0.1KB/s 00:00
|
||||
passwd-up.sh 100% 877 0.9KB/s 00:00
|
||||
passwd-up1.sh 100% 7 0.0KB/s 00:00
|
||||
server-list.txt 100% 23 0.0KB/s 00:00
|
||||
```
|
||||
|
||||
### Method-3: Copy Files/Folders From A Local System To Multiple Remote System In Linux Using PSCP Command?
|
||||
|
||||
pscp command directly allow us to perform the copy to multiple remote servers.
|
||||
|
||||
Use the following pscp command to copy a single file to remote server.
|
||||
|
||||
```
|
||||
# pscp.pssh -H 2g.CentOS.com /home/daygeek/2g/shell-script/output.txt /opt/backup
|
||||
|
||||
[1] 18:46:11 [SUCCESS] 2g.CentOS.com
|
||||
```
|
||||
|
||||
Use the following pscp command to copy a multiple files to remote server.
|
||||
|
||||
```
|
||||
# pscp.pssh -H 2g.CentOS.com /home/daygeek/2g/shell-script/output.txt ovh.sh /opt/backup
|
||||
|
||||
[1] 18:47:48 [SUCCESS] 2g.CentOS.com
|
||||
```
|
||||
|
||||
Use the following pscp command to copy a directory recursively to remote server.
|
||||
|
||||
```
|
||||
# pscp.pssh -H 2g.CentOS.com -r /home/daygeek/2g/shell-script/ /opt/backup
|
||||
|
||||
[1] 18:48:46 [SUCCESS] 2g.CentOS.com
|
||||
```
|
||||
|
||||
Use the following pscp command to copy a single file to multiple remote servers.
|
||||
|
||||
```
|
||||
# pscp.pssh -h server-list.txt /home/daygeek/2g/shell-script/output.txt /opt/backup
|
||||
|
||||
[1] 18:49:48 [SUCCESS] 2g.CentOS.com
|
||||
[2] 18:49:48 [SUCCESS] 2g.Debian.com
|
||||
```
|
||||
|
||||
Use the following pscp command to copy a multiple files to multiple remote servers.
|
||||
|
||||
```
|
||||
# pscp.pssh -h server-list.txt /home/daygeek/2g/shell-script/output.txt passwd-up.sh /opt/backup
|
||||
|
||||
[1] 18:50:30 [SUCCESS] 2g.Debian.com
|
||||
[2] 18:50:30 [SUCCESS] 2g.CentOS.com
|
||||
```
|
||||
|
||||
Use the following pscp command to copy a directory recursively to multiple remote servers.
|
||||
|
||||
```
|
||||
# pscp.pssh -h server-list.txt -r /home/daygeek/2g/shell-script/ /opt/backup
|
||||
|
||||
[1] 18:51:31 [SUCCESS] 2g.Debian.com
|
||||
[2] 18:51:31 [SUCCESS] 2g.CentOS.com
|
||||
```
|
||||
|
||||
### Method-4: Copy Files/Folders From A Local System To Multiple Remote System In Linux Using rsync Command?
|
||||
|
||||
Rsync is a fast and extraordinarily versatile file copying tool. It can copy locally, to/from another host over any remote shell, or to/from a remote rsync daemon.
|
||||
|
||||
Use the following rsync command to copy a single file to remote server.
|
||||
|
||||
```
|
||||
# rsync -avz /home/daygeek/2g/shell-script/output.txt [email protected]:/opt/backup
|
||||
|
||||
sending incremental file list
|
||||
output.txt
|
||||
|
||||
sent 598 bytes received 31 bytes 1258.00 bytes/sec
|
||||
total size is 2468 speedup is 3.92
|
||||
```
|
||||
|
||||
Use the following pscp command to copy a multiple files to remote server.
|
||||
|
||||
```
|
||||
# rsync -avz /home/daygeek/2g/shell-script/output.txt passwd-up.sh root@2g.CentOS.com:/opt/backup
|
||||
|
||||
sending incremental file list
|
||||
output.txt
|
||||
passwd-up.sh
|
||||
|
||||
sent 737 bytes received 50 bytes 1574.00 bytes/sec
|
||||
total size is 2537 speedup is 3.22
|
||||
```
|
||||
|
||||
Use the following rsync command to copy a single file to remote server overh ssh.
|
||||
|
||||
```
|
||||
# rsync -avzhe ssh /home/daygeek/2g/shell-script/output.txt root@2g.CentOS.com:/opt/backup
|
||||
|
||||
sending incremental file list
|
||||
output.txt
|
||||
|
||||
sent 598 bytes received 31 bytes 419.33 bytes/sec
|
||||
total size is 2.47K speedup is 3.92
|
||||
```
|
||||
|
||||
Use the following pscp command to copy a directory recursively to remote server over ssh. This will copy only files not the base directory.
|
||||
|
||||
```
|
||||
# rsync -avzhe ssh /home/daygeek/2g/shell-script/ root@2g.CentOS.com:/opt/backup
|
||||
|
||||
sending incremental file list
|
||||
./
|
||||
output.txt
|
||||
ovh.sh
|
||||
passwd-up.sh
|
||||
passwd-up1.sh
|
||||
server-list.txt
|
||||
|
||||
sent 3.85K bytes received 281 bytes 8.26K bytes/sec
|
||||
total size is 9.12K speedup is 2.21
|
||||
```
|
||||
|
||||
### Method-5: Copy Files/Folders From A Local System To Multiple Remote System In Linux Using Shell Script with rsync Command?
|
||||
|
||||
If you would like to copy the same file into multiple remote servers then create the following small shell script to achieve this.
|
||||
|
||||
```
|
||||
# file-copy.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
rsync -avzhe ssh /home/daygeek/2g/shell-script/ root@2g.CentOS.com$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
Output for the above shell script.
|
||||
|
||||
```
|
||||
# ./file-copy.sh
|
||||
|
||||
sending incremental file list
|
||||
./
|
||||
output.txt
|
||||
ovh.sh
|
||||
passwd-up.sh
|
||||
passwd-up1.sh
|
||||
server-list.txt
|
||||
|
||||
sent 3.86K bytes received 281 bytes 8.28K bytes/sec
|
||||
total size is 9.13K speedup is 2.21
|
||||
|
||||
sending incremental file list
|
||||
./
|
||||
output.txt
|
||||
ovh.sh
|
||||
passwd-up.sh
|
||||
passwd-up1.sh
|
||||
server-list.txt
|
||||
|
||||
sent 3.86K bytes received 281 bytes 2.76K bytes/sec
|
||||
total size is 9.13K speedup is 2.21
|
||||
```
|
||||
|
||||
### Method-6: Copy Files/Folders From A Local System To Multiple Remote System In Linux Using Shell Script with scp Command?
|
||||
|
||||
In the above two shell script, we need to mention the file and folder location as a prerequiesties but here i did a small modification that allow the script to get a file or folder as a input. It could be very useful when you want to perform the copy multiple times in a day.
|
||||
|
||||
```
|
||||
# file-copy.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
scp -r $1 root@2g.CentOS.com$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
Run the shell script and give the file name as a input.
|
||||
|
||||
```
|
||||
# ./file-copy.sh output1.txt
|
||||
|
||||
output1.txt 100% 3558 3.5KB/s 00:00
|
||||
output1.txt 100% 3558 3.5KB/s 00:00
|
||||
```
|
||||
|
||||
### Method-7: Copy Files/Folders From A Local System To Multiple Remote System In Linux With Non-Standard Port Number?
|
||||
|
||||
Use the below shell script to copy a file or folder if you are using Non-Standard port.
|
||||
|
||||
If you are using `Non-Standard` port, make sure you have to mention the port number as follow for SCP command.
|
||||
|
||||
```
|
||||
# file-copy-scp.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
scp -P 2222 -r $1 root@2g.CentOS.com$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
Run the shell script and give the file name as a input.
|
||||
|
||||
```
|
||||
# ./file-copy.sh ovh.sh
|
||||
|
||||
ovh.sh 100% 3558 3.5KB/s 00:00
|
||||
ovh.sh 100% 3558 3.5KB/s 00:00
|
||||
```
|
||||
|
||||
If you are using `Non-Standard` port, make sure you have to mention the port number as follow for rsync command.
|
||||
|
||||
```
|
||||
# file-copy-rsync.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
rsync -avzhe 'ssh -p 2222' $1 root@2g.CentOS.com$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
Run the shell script and give the file name as a input.
|
||||
|
||||
```
|
||||
# ./file-copy-rsync.sh passwd-up.sh
|
||||
sending incremental file list
|
||||
passwd-up.sh
|
||||
|
||||
sent 238 bytes received 35 bytes 26.00 bytes/sec
|
||||
total size is 159 speedup is 0.58
|
||||
|
||||
sending incremental file list
|
||||
passwd-up.sh
|
||||
|
||||
sent 238 bytes received 35 bytes 26.00 bytes/sec
|
||||
total size is 159 speedup is 0.58
|
||||
```
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/linux-scp-rsync-pscp-command-copy-files-folders-in-multiple-servers-using-shell-script/
|
||||
|
||||
作者:[Prakash Subramanian][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/prakash/
|
||||
[b]: https://github.com/lujun9972
|
||||
@ -1,73 +0,0 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (mySoul8012)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (Book Review: Fundamentals of Linux)
|
||||
[#]: via: (https://itsfoss.com/fundamentals-of-linux-book-review)
|
||||
[#]: author: (John Paul https://itsfoss.com/author/john/)
|
||||
|
||||
书评:linux的基础知识
|
||||
======
|
||||
有很多很棒的书籍涵盖了Linux的基础知识以及它的工作原理,今天,我们将会书评这样一本书,讨论的主题为Oliver Pelz所写的[linux的基础知识][1],由[PacktPub][2]发布。
|
||||
|
||||
[Oliver Pelz][3] 是一位超过十年软件开发人员和系统管理员经验人员,同时拥有生物信息学学位证书。
|
||||
|
||||
### 什么是linux基础知识一书
|
||||
|
||||
![Fundamental of Linux books][4]
|
||||
正如可以从标题中猜到那样,该书(Linux基础知识)的目标是为读者打下一个了解Linux命令行的坚实基础。这本书一共有两百多页。因此它专注于教授用户日常遇到的问题,以及任务。本书为想要成为Linux管理员的读者而书写。
|
||||
|
||||
第一章首先概述了虚拟化。本书作者指导了读者如何在[VirtualBox][6]中创建[CentOS][5]实例。如何克隆实例,如何使用快照。并且同时你也会学习到如何通过SSH命令连接到虚拟机。
|
||||
|
||||
第二章介绍了Linux的命令行的基础知识,包括shell GLOB模式,shell扩展,如何使用包含空格和特殊字符的文件名称。如何来获取命令手册的帮助页面。如何使用`sed`, `awk`这两个命令。如何浏览Linux的文件系统。
|
||||
|
||||
第三章更深入的介绍了Linux文件系统。您将了解如何在Linux中链接文件,以及如何搜索它们。您还将获得用户,组,以及文件权限的概述。由于本章的重点介绍了如何与文件进行交互。因此还将会介绍如何从命令行中读取文本文件,以及如何使用vim编辑器。
|
||||
|
||||
第四章重点介绍了如何使用命令行。以及涵盖的重要命令。如`cat`, `sort`, `awk`. `tee`, `tar`,`rsync`, `nmap`, `htop`等。您还将会了解这些命令的流程,以及如何相互使用,还将介绍Bash shell脚本。
|
||||
|
||||
第五章同时也是本书的最后一章,将会介绍Linux和其他高级命令,以及网络的概念。本书的作者讨论了Linux如何处理网络并提供使用多个虚拟机的示例。同时还将会介绍如何安装新的程序,如何设置防火墙。
|
||||
|
||||
### 关于这本书的想法
|
||||
|
||||
Linux的基础知识可能看起来很见到,但是涵盖了相当多的信息。同时也将会获得如何使用命令行所需要的知识的一切。
|
||||
|
||||
使用本书的时候,需要注意一件事情,即,本书专注于对命令行的关注,没有任何关于如何使用图形化的用户界面的任何教程。这是因为在Linux中有太多不同的桌面环境,以及很多的类似的操作系统。因此很难编写一本可以涵盖所有变量的书。部分原因还因为本书的面向的用户群体为Linux管理员。
|
||||
|
||||
当我看到作者使用Centos教授Linux的时候有点惊讶。我原本以为他会使用更为常见的Linux的发行版本,例如Ubuntu,Debian或者Fedora。原因在于Centos是为服务器设计的发行版本。随着时间的推移变化很小。能够为Linux的基础知识打下一个非常坚实的基础。
|
||||
|
||||
自己使用Linux已经操作五年了。我大部分时间都在使用桌面版本的Linux。我有些时候会使用命令行操作。但我并没有花太多的时间在哪里。我使用鼠标执行了本书中很多的操作。现在呢。我同时也知道了如何通过终端做出同样的事情。这种方式不会改变我完成任务的路径。但是会更加帮助自己理解幕后发生的事情。
|
||||
|
||||
如果您刚刚使用Linux,或者计划使用。我不会推荐您阅读这本书。这可能有点绝对化。但是如何您已经花了一些时间在Linux上。或者可以快速掌握某种技术语言。那么这本书很适合你。
|
||||
|
||||
如果您认为本书适合您的学习需求。您可以从以下链接获取到该书。
|
||||
|
||||
我们将在未来几个月内尝试查看更多Linux书籍,敬请关注我们。
|
||||
|
||||
你最喜欢的关于Linux的入门书籍是什么?请在下面的评论中告诉我们。
|
||||
|
||||
如果您发现这篇文章很有趣,请花一点时间在社交媒体,黑客新闻或[Reddit][8]上分享
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/fundamentals-of-linux-book-review
|
||||
|
||||
作者:[John Paul][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/john/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.packtpub.com/networking-and-servers/fundamentals-linux
|
||||
[2]: https://www.packtpub.com/
|
||||
[3]: http://www.oliverpelz.de/index.html
|
||||
[4]: https://i1.wp.com/itsfoss.com/wp-content/uploads/2019/01/fundamentals-of-linux-book-review.jpeg?resize=800%2C450&ssl=1
|
||||
[5]: https://centos.org/
|
||||
[6]: https://www.virtualbox.org/
|
||||
[7]: https://www.centos.org/
|
||||
[8]: http://reddit.com/r/linuxusersgroup
|
||||
@ -0,0 +1,96 @@
|
||||
8 个在 KDE Plasma 桌面环境下提高生产力的技巧和提示
|
||||
======
|
||||
|
||||

|
||||
|
||||
众所周知,KDE 的 Plasma 是 Linux 下最强大的桌面环境之一。它是高度可定制的,并且看起来也很棒。当你完成所有的配置工作后,你才能体会到它的所有特性。
|
||||
|
||||
你能够轻松地配置 Plasma 桌面并且使用它大量方便且节省时间的特性来加速你的工作,拥有一个能够帮助你而非阻碍你的桌面环境。
|
||||
|
||||
这些提示并没有特定顺序,因此你无需按次序阅读。你只需要挑出最适合你的工作流的那几个即可。
|
||||
|
||||
**相关阅读** : [10 个你应该尝试的最佳 KDE Plasma 应用][1]
|
||||
|
||||
### 1. 多媒体控制
|
||||
|
||||
这点算不太上是一条提示,因为它是很容易被记在脑海里的。Plasma 可在各处进行多媒体控制。当你需要暂停、继续或跳过一首歌时,你不需要每次都打开你的媒体播放器。你能够通过将鼠标移至最小化窗口之上,甚至通过锁屏进行控制。当你需要切换歌曲或忘了暂停时,你也不必麻烦地登录再进行操作。
|
||||
|
||||
### 2. KRunner
|
||||
|
||||
![KDE Plasma KRunner][2]
|
||||
|
||||
KRunner 是 Plasma 桌面中一个经常受到赞誉的特性。大部分人习惯于深挖应用启动菜单来找到想要启动的程序。当你使用 KRunner 时就不需要这么做。
|
||||
|
||||
为了使用 KRunner,确保你当前的焦点在桌面本身(点击桌面而不是窗口)。然后开始输入你想要启动的应用名称,KRunner 将会带着建议项从你的屏幕顶部自动下拉。在你寻找的匹配项上点击或敲击 Enter 键。这比记住你每个应用所属的类别要更快。
|
||||
|
||||
### 3. 跳转列表
|
||||
|
||||
![KDE Plasma 的跳转列表][3]
|
||||
|
||||
跳转列表功能是最近才被添加进 Plasma 桌面的。它允许你在启动应用时直接跳转至特定的区域或特性部分。
|
||||
|
||||
因此如果你在菜单栏上有一个应用启动图标,你可以通过右键得到可跳转位置的列表。选择你想要跳转的位置,然后就可以“起飞”了。
|
||||
|
||||
### 4. KDE Connect
|
||||
|
||||
![KDE Connect Android 客户端菜单][4]
|
||||
|
||||
如果你有一个安卓手机,那么 [KDE Connect][5] 会为你提供大量帮助。它可以将你的手机连接至你的桌面,由此你可以在两台设备间无缝地共享。
|
||||
|
||||
通过 KDE Connect,你能够在你的桌面上实时地查看 [Android 设备通知][6]。它同时也让你能够从 Plasma 中收发文字信息,甚至不需要拿起你的手机。
|
||||
|
||||
KDE Connect 也允许你在手机和电脑间发送文件或共享网页。你可以轻松地从一个设备转移至另一设备,而无需烦恼或打乱思绪。
|
||||
|
||||
### 5. Plasma Vaults
|
||||
|
||||
![KDE Plasma Vault][7]
|
||||
|
||||
Plasma Vaults 是 Plasma 桌面的另一个新功能。它的 KDE 为加密文件和文件夹提供的简单解决方案。如果你不使用加密文件,此项功能不会为你节省时间。如果你使用,Vaults是一个更简单的途径。
|
||||
|
||||
Plasma Vaults 允许你以无 root 权限的普通用户创建加密目录,并通过你的任务栏来管理它们。你能够快速地挂载或卸载目录,而无需外部程序或附加权限。
|
||||
|
||||
### 6. Pager 控件
|
||||
|
||||
![KDE Plasma Pager][8]
|
||||
|
||||
配置你的桌面的 pager 控件。它允许你轻松地切换至另三个附加工作区,带来更大的屏幕空间。
|
||||
|
||||
将控件添加到你的菜单栏上,然后你就可以在多个工作区间滑动切换。每个工作区都与你原桌面的尺寸相同,因此你能够得到数倍于完整屏幕的空间。这就使你能够排布更多的窗口,而不必受到一堆混乱的最小化窗口的困扰。
|
||||
|
||||
### 7. 创建一个 Dock
|
||||
|
||||
![KDE Plasma Dock][9]
|
||||
|
||||
Plasma 以其灵活性和可配置性出名,同时也是它的优势。如果你有常用的程序,你可以考虑将常用程序设置为 OS X 风格的 dock。你能够通过单击启动,而不必深入菜单或输入它们的名字。
|
||||
|
||||
### 8. 为 Dolphin 添加文件树
|
||||
|
||||
![Plasma Dolphin 目录][10]
|
||||
|
||||
通过目录树来浏览文件夹会更加简单。Dolphin 作为 Plasma 的默认文件管理器,具有在文件夹窗口一侧,以树的形式展示目录列表的内置功能。
|
||||
|
||||
为了启用目录树,点击“控制”标签,然后“配置 Dolphin”,“显示模式”,“详细”,最后选择“可展开文件夹”。
|
||||
|
||||
记住这些仅仅是提示,不要强迫自己做阻碍自己的事情。你可能讨厌在 Dolphin 中使用文件树,你也可能从不使用 Pager,这都没关系。当然也可能会有你喜欢但是此处没列举出来的功能。选择对你有用处的,也就是说,这些技巧中总有一些能帮助你度过日常工作中的艰难时刻。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.maketecheasier.com/kde-plasma-tips-tricks-improve-productivity/
|
||||
|
||||
作者:[Nick Congleton][a]
|
||||
译者:[cycoe](https://github.com/cycoe)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.maketecheasier.com/author/nickcongleton/
|
||||
[1]:https://www.maketecheasier.com/10-best-kde-plasma-applications/ (10 of the Best KDE Plasma Applications You Should Try)
|
||||
[2]:https://www.maketecheasier.com/assets/uploads/2017/10/pe-krunner.jpg (KDE Plasma KRunner)
|
||||
[3]:https://www.maketecheasier.com/assets/uploads/2017/10/pe-jumplist.jpg (KDE Plasma Jump Lists)
|
||||
[4]:https://www.maketecheasier.com/assets/uploads/2017/05/kde-connect-menu-e1494899929112.jpg (KDE Connect Menu Android)
|
||||
[5]:https://www.maketecheasier.com/send-receive-sms-linux-kde-connect/
|
||||
[6]:https://www.maketecheasier.com/android-notifications-ubuntu-kde-connect/
|
||||
[7]:https://www.maketecheasier.com/assets/uploads/2017/10/pe-vault.jpg (KDE Plasma Vault)
|
||||
[8]:https://www.maketecheasier.com/assets/uploads/2017/10/pe-pager.jpg (KDE Plasma Pager)
|
||||
[9]:https://www.maketecheasier.com/assets/uploads/2017/10/pe-dock.jpg (KDE Plasma Dock)
|
||||
[10]:https://www.maketecheasier.com/assets/uploads/2017/10/pe-dolphin.jpg (Plasma Dolphin Directory)
|
||||
@ -1,93 +0,0 @@
|
||||
[#]:collector:(lujun9972)
|
||||
[#]:translator:(lujun9972)
|
||||
[#]:reviewer:( )
|
||||
[#]:publisher:( )
|
||||
[#]:url:( )
|
||||
[#]:subject:(How to use Magit to manage Git projects)
|
||||
[#]:via:(https://opensource.com/article/19/1/how-use-magit)
|
||||
[#]:author:(Sachin Patil https://opensource.com/users/psachin)
|
||||
|
||||
如何使用 Magit 管理 Git 项目
|
||||
======
|
||||
Emacs 的 Magit 扩展插件使得使用 Git 进行版本控制变得简单起来。
|
||||

|
||||
|
||||
[Git][1] 是一个很棒的用于项目管理的 [版本控制 ][2] 工具,就是新人学习起来太难。Git 的命令行工具很难用,你不仅需要熟悉它的标志和选项还需要知道什么环境下使用他们。这使人望而生畏,因此不少人只在有限的几个场景中才使用它。
|
||||
|
||||
还在,现今大多数的集成开发环境 (IDE) 都包含了 Git 扩展,大大地简化了使用使用的难度。Emacs 中就有这么一款 Git 扩展名叫 [Magit][3]。
|
||||
|
||||
Magit 项目成立有差不多 10 年了,它将自己定义为 "一件 Emacs 内的 Git 瓷器。" 也就是说,它是一个操作界面,每个操作都能一键完成。本文会带你领略一下 Magit 的操作界面并告诉你如何使用它来管理 Git 项目。
|
||||
|
||||
若你还未 [安装 Emacs][4],则开始本教程之前请先 [安装 Magit][5]。
|
||||
|
||||
### Magit 的界面
|
||||
|
||||
首先用 Emacs 的 [Dired mode][6] 访问一个项目目录。比如我所有的 Emacs 配置存储在 **~/.emacs.d/** 目录中,就是用 Git 来进行管理的。
|
||||
|
||||

|
||||
|
||||
若你在命令行下工作,则你需要输入 **git status** 来查看项目的当前状态。Magit 也有类似的函数:**magit-status**。你可以通过 **M-x magit-status** (快捷方式是 **Alt+x magit-status** )来调用该函数。结果看起来像下面这样:
|
||||
|
||||

|
||||
|
||||
Magit 显示的信息比 **git status** 命令的要多得多。它分别列出了未追踪文件列表、未暂存文件列表以及已暂存文件列表。它还列出了储藏 (stash) 列表以及最近几次的提交—所有这些信息都在一个窗口中展示。
|
||||
|
||||
如果你想查看修改了哪些内容,按下 Tab 键。比如,我移动光标到未暂存文件 **custom_functions.org** 上然后按下 Tab 键,Magit 会显示修改了哪些内容:
|
||||
|
||||

|
||||
|
||||
这跟运行命令 **git diff custom_functions.org** 类似。储藏文件更简单。只需要移动光标到文件上然后按下 **s** 键。该文件就会迅速移动到被储藏文件列表中:
|
||||
|
||||

|
||||
|
||||
要反储藏 (unstage) 某个文件,使用 **u** 键。按下 **s** 和 **u** 键要比在命令行输入 **git add -u <file>** 和 **git reset HEAD <file>** 快的多也更有趣的多。
|
||||
|
||||
### 提交更改
|
||||
|
||||
在同一个 Magit 窗口中,按下 **c** 键会显示一个提交窗口,其中提供了许多标志,比如 **--all** 用来暂存所有文件或者 **--signoff** 来往提交信息中添加签名行。
|
||||
|
||||

|
||||
|
||||
将光标移动到想要启动的行,比如 signoff 标签行,然后按下回车。**--signoff** 文本会变成高亮,这说明该标志已经被启用。
|
||||
|
||||

|
||||
|
||||
再次按下 **c** 键会显示一个窗口供你输入提交信息。
|
||||
|
||||

|
||||
|
||||
最后,使用 **C-c C-c **(按键 Ctrl+cc 的缩写形式) 来提交更改。
|
||||
|
||||

|
||||
|
||||
### 推送更改
|
||||
|
||||
更改提交后,提交行将会显示在 **Recent commits** 段中显示。
|
||||
|
||||

|
||||
|
||||
将光标放到该提交处然后按下 **p** 来推送该变更。
|
||||
|
||||
若你想感受一下使用 Magit 的感觉,我已经在 YouTube 上上传了一段 [演示 ][7]。本文只涉及到 Magit 的一点皮毛。它有许多超酷的功能可以帮你使用 Git 分支,变基等功能。你可以在 Magit 的主页上找到 [文档,支持,以及更多 ][8] 链接。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/how-use-magit
|
||||
|
||||
作者:[Sachin Patil][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[lujun9972](https://github.com/lujun9972)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/psachin
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://git-scm.com
|
||||
[2]: https://git-scm.com/book/en/v2/Getting-Started-About-Version-Control
|
||||
[3]: https://magit.vc
|
||||
[4]: https://www.gnu.org/software/emacs/download.html
|
||||
[5]: https://magit.vc/manual/magit/Installing-from-Melpa.html#Installing-from-Melpa
|
||||
[6]: https://www.gnu.org/software/emacs/manual/html_node/emacs/Dired-Enter.html#Dired-Enter
|
||||
[7]: https://youtu.be/Vvw75Pqp7Mc
|
||||
[8]: https://magit.vc/
|
||||
@ -0,0 +1,236 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: (hopefully2333)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (The Evil-Twin Framework: A tool for improving WiFi security)
|
||||
[#]: via: (https://opensource.com/article/19/1/evil-twin-framework)
|
||||
[#]: author: (André Esser https://opensource.com/users/andreesser)
|
||||
|
||||
Evil-Twin 框架:一个用于提升 WiFi 安全性的工具
|
||||
======
|
||||
了解一款用于对 WiFi 安全性进行手动测试的工具,这款工具可以通过不同类型安全威胁的漏洞点进行测试。
|
||||

|
||||
|
||||
越来越多的设备通过无线传输的方式连接到互联网,以及,WiFi 接入点大范围的可用,这两者为攻击者攻击用户提供了很多机会。通过欺骗用户连接到虚假的 WiFi 接入点,攻击者可以完全控制用户的网络连接,这将使得攻击者可以嗅探和篡改用户通过无线连接进行发送和接收的数据包,将用户的连接重定向到一个恶意的网站,并通过网络发起其他的攻击。
|
||||
|
||||
为了保护用户并告诉他们如何避免线上的危险操作,安全审计人员和安全研究员必须评估用户的安全实践能力,用户常常在没有确认该 WiFi 接入点为安全的情况下就连接上了该网络,安全审计人员和研究员需要去了解这背后的原因。有很多工具都可以对 WiFi 的安全性进行审计,但是没有一款工具可以测试大量不同的攻击场景,也没有能和其他工具集成得很好的工具。
|
||||
|
||||
Evil-Twin Framework(ETF)用于在 WiFi 审计过程中解决这些问题。审计者能够使用 ETF 来集成多种工具并测试该 WiFi 在不同场景下的安全性。本文会介绍 ETF 的框架和功能,然后会提供一些案例来说明该如何使用这款工具。
|
||||
|
||||
### ETF 的架构
|
||||
|
||||
ETF 的框架是用 python 写的,因为这门开发语言的代码读起来非常容易,也方便其他开发者向这个项目贡献代码。除此之外,很多 ETF 的库,比如 Scapy,都是为 python 开发的,很容易就能将它们用于 ETF。
|
||||
|
||||
ETF 的架构(图1)分为不同的模块,模块之间相互作用。框架的设置都写在一个单独的配置文件里。用户可以通过 ConfigurationManager 类里的用户界面验证并修改这些配置。其他模块只能读取这些设置并根据这些设置进行运行。
|
||||
|
||||
![Evil-Twin Framework Architecture][5]
|
||||
|
||||
图 1:Evil-Twin 的框架架构
|
||||
|
||||
ETF 支持多种用户界面来与框架交互,当前的默认界面是一个交互式控制台界面,类似于 Metasploit 那种。正在开发用于桌面/浏览器使用的图形用户界面(GUI)和命令行界面(CLI),移动端界面也是未来的一个备选项。用户可以使用交互式控制台界面来修改配置文件里的设置(最终会使用 GUI)。用户界面可以与框架里存在的每个模块进行交互。
|
||||
|
||||
WiFi 模块(AirCommunicator)用于支持多种 WiFi 功能和攻击。该框架确定了 Wi-Fi 通信的三个基本支柱:数据包嗅探,自定义数据包注入和创建接入点。三个主要的 WiFi 通信模块是 AirScanner,AirInjector,和 AirHost,它们分别用于数据包嗅探,数据包注入,和接入点创建。这三个类包含在主 WiFi 模块 AirCommunicator 中,AirCommunicator 在启动这些服务之前会先读取这些服务的配置文件。使用这些核心功能的一个或多个就可以构造任意类型的 WiFi 攻击。
|
||||
|
||||
使用中间人(MITM)攻击,这是一种攻击 WiFi 客户端的常见手法。ETF 有一个叫做 ETFITM(Evil-Twin Framework-in-the-Middle)的集成模块,这个模块用于创建一个 web 代理,来拦截和修改经过的 HTTP/HTTPS 数据包。
|
||||
|
||||
许多其他的工具也可以使用 ETF 创建 MITM。通过它的可扩展性,ETF 能够支持它们,而不必单独地调用它们,你可以通过扩展 Spawner 类来将这些工具添加到框架里。这使得开发者和安全审计人员可以使用框架里预先配置好的参数字符来调用程序。
|
||||
|
||||
扩展 ETF 的另一种方法就是通过插件。有两类插件:WiFi 插件和 MITM 插件。MITM 插件是在 MITM 代理运行时可以执行的脚本。代理会将 HTTP(s)请求和响应传递给可以记录和处理它们的插件。WiFi 插件遵循一个更加复杂的执行流程,但仍然会给想参与开发并且使用自己插件的贡献者提供一个相对简单的 API。WiFi 插件还可以进一步地划分为三类,其中一类用于每个核心 WiFi 通信模块。
|
||||
|
||||
每个核心模块都有一些事件能触发响应的插件的执行。举个栗子,AirScanner 有三个已定义的事件,可以对其进行编程。事件通常对应于服务开始运行之前的设置阶段,服务正在运行时的中间执行阶段,服务完成后的卸载或清理阶段。因为 python 允许多重继承,所以一个插件可以继承多个插件类。
|
||||
|
||||
图 1 是框架架构的摘要。指向远离 ConfigurationManager 的行意味着模块会从中读取信息,指向它的行意味着模块会编写/修改配置。
|
||||
|
||||
### 使用 ETF 的实例
|
||||
|
||||
ETF 可以通过多种方式对 WiFi 的网络安全或者终端用户的 WiFi 安全意识进行渗透测试。下面的例子描述了这个框架的一些手动测试的功能,例如接入点和客户端检测,对使用 WPA 和 WEP 类型协议的接入点进行攻击,和创建恶意的双接入点。
|
||||
|
||||
这些例子是使用 ETF 设计的,WiFi 卡允许进行 WiFi 数据捕获。它们同样为 ETF 设置命令使用了下面这些缩写:
|
||||
|
||||
* **APS** access point SSID
|
||||
* **APB** access point BSSID
|
||||
* **APC** access point channel
|
||||
* **CM** client MAC address
|
||||
|
||||
|
||||
|
||||
在实际的测试场景中,确保你使用了正确的信息来替换这些缩写。
|
||||
|
||||
#### 在解除认证攻击后捕获 WPA 四次握手的数据包。
|
||||
|
||||
这个场景(图 2)做了两个方面的考虑:解除认证攻击和捕获 WPA 四次握手数据包的可能性。这个场景从一个运行 WPA/WPA2 的接入点开始,这个接入点有一个已经连上的客户端设备(在本例中是一台智能手机)。目的是通过一般的解除认证攻击(译者注:类似于 DOS 攻击)来让客户端断开和 WiFi 的网络,然后在客户端尝试重连的时候捕获 WPA 的握手包。重连会在断开连接后马上手动完成。
|
||||
|
||||
![Scenario for capturing a WPA handshake after a de-authentication attack][8]
|
||||
|
||||
图 2:在解除认证攻击后捕获 WPA 握手包的场景
|
||||
|
||||
在这个例子中需要考虑的是 ETF 的可靠性。目的是确认工具是否一直都能捕获 WPA 的握手数据包。每个工具都会用来多次复现这个场景,以此来检查它们在捕获 WPA 握手数据包时的可靠性。
|
||||
|
||||
使用 ETF 来捕获 WPA 握手数据包的方法不止一种。一种方法是使用 AirScanner 和 AirInjector 两个模块的组合;另一种方法是只使用 AirInjector。下面这个场景是使用了两个模块的组合。
|
||||
|
||||
ETF 启用了 AirScanner 模块并分析 IEEE 802.11 数据帧来发现 WPA 握手包。然后 AirInjecto 就可以使用解除认证攻击来强制客户端断开连接,以进行重连。必须在 ETF 上执行下面这些步骤才能完成上面的目标:
|
||||
|
||||
1. 进入 AirScanner 配置模式: **config airscanner**
|
||||
2. 设置 AirScanner 不跳信道: **config airscanner**
|
||||
3. 设置信道以嗅探经过 WiFi 接入点信道的数据(APC): **set fixed_sniffing_channel = <APC>**
|
||||
4. 使用 CredentialSniffer 插件来启动 AirScanner 模块: **start airscanner with credentialsniffer**
|
||||
5. 从已嗅探的接入点列表中添加目标接入点的 BSSID(APS): **add aps where ssid = <APS>**
|
||||
6. 启用 AirInjector 模块,在默认情况下,它会启用解除认证攻击: **start airinjector**
|
||||
|
||||
|
||||
|
||||
这些简单的命令设置能让 ETF 在每次测试时执行成功且有效的解除认证攻击。ETF 也能在每次测试的时候捕获 WPA 的握手数据包。下面的代码能让我们看到 ETF 成功的执行情况。
|
||||
|
||||
```
|
||||
███████╗████████╗███████╗
|
||||
██╔════╝╚══██╔══╝██╔════╝
|
||||
█████╗ ██║ █████╗
|
||||
██╔══╝ ██║ ██╔══╝
|
||||
███████╗ ██║ ██║
|
||||
╚══════╝ ╚═╝ ╚═╝
|
||||
|
||||
|
||||
[+] Do you want to load an older session? [Y/n]: n
|
||||
[+] Creating new temporary session on 02/08/2018
|
||||
[+] Enter the desired session name:
|
||||
ETF[etf/aircommunicator/]::> config airscanner
|
||||
ETF[etf/aircommunicator/airscanner]::> listargs
|
||||
sniffing_interface = wlan1; (var)
|
||||
probes = True; (var)
|
||||
beacons = True; (var)
|
||||
hop_channels = false; (var)
|
||||
fixed_sniffing_channel = 11; (var)
|
||||
ETF[etf/aircommunicator/airscanner]::> start airscanner with
|
||||
arpreplayer caffelatte credentialsniffer packetlogger selfishwifi
|
||||
ETF[etf/aircommunicator/airscanner]::> start airscanner with credentialsniffer
|
||||
[+] Successfully added credentialsniffer plugin.
|
||||
[+] Starting packet sniffer on interface 'wlan1'
|
||||
[+] Set fixed channel to 11
|
||||
ETF[etf/aircommunicator/airscanner]::> add aps where ssid = CrackWPA
|
||||
ETF[etf/aircommunicator/airscanner]::> start airinjector
|
||||
ETF[etf/aircommunicator/airscanner]::> [+] Starting deauthentication attack
|
||||
- 1000 bursts of 1 packets
|
||||
- 1 different packets
|
||||
[+] Injection attacks finished executing.
|
||||
[+] Starting post injection methods
|
||||
[+] Post injection methods finished
|
||||
[+] WPA Handshake found for client '70:3e:ac:bb:78:64' and network 'CrackWPA'
|
||||
```
|
||||
|
||||
#### 使用 ARP 重放攻击并破解 WEP 无线网络
|
||||
|
||||
下面这个场景(图 3)将关注地址解析协议(ARP)重放攻击的效率和捕获包含初始化向量(IVs)的 WEP 数据包的速度。相同的网络可能需要破解不同数量的捕获的 IVs,所以这个场景的 IVs 上限是 50000。如果这个网络在首次测试期间,还未捕获到 50000IVs 就崩溃了,那么实际捕获到的 IVs 数量会成为这个网络在接下来的测试里的新的上限。我们使用 aircrack-ng 对数据包进行破解。
|
||||
|
||||
测试场景从一个使用 WEP 协议进行加密的 WiFi 接入点和一台知道其密钥的离线客户端设备开始-为了测试密钥使用了 12345,但它可以是更长且更复杂的密钥。一旦客户端连接到了 WEP 接入点,它会发送一个 ARP 数据包;这是要捕获和重放的数据包。一旦被捕获的包含 IVs 的数据包数量达到了设置的上限,测试就结束了。
|
||||
|
||||
![Scenario for capturing a WPA handshake after a de-authentication attack][11]
|
||||
|
||||
图 3:在进行解除认证攻击后捕获 WPA 握手包的场景
|
||||
|
||||
ETF 使用 Python 的 Scapy 库来进行包嗅探和包注入。为了最大限度地解决 Scapy 里的已知性能问题,ETF 微调了一些低级库,来大大加快包注入的速度。对于这个特定的场景,ETF 为了更有效率地嗅探,使用了 tcpdump 作为后台进程而不是 Scapy,Scapy 用于识别加密的 ARP 数据包。
|
||||
|
||||
这个场景需要在 ETF 上执行下面这些命令和操作:
|
||||
|
||||
1. 进入 AirScanner 设置模式: **config airscanner**
|
||||
2. 设置 AirScanner 不跳信道: **set hop_channels = false**
|
||||
3. 设置信道以嗅探经过接入点信道的数据(APC): **set fixed_sniffing_channel = <APC>**
|
||||
4. 进入 ARPReplayer 插件设置模式: **config arpreplayer**
|
||||
5. 设置 WEP 网络目标接入点的 BSSID(APB): **set target_ap_bssid <APB>**
|
||||
6. 使用 ARPReplayer 插件启动 AirScanner 模块: **start airscanner with arpreplayer**
|
||||
|
||||
|
||||
|
||||
在执行完这些命令后,ETF 会正确地识别加密的 ARP 数据包,然后成功执行 ARP 重放攻击,以此破坏这个网络。
|
||||
|
||||
#### 使用一款全能型蜜罐
|
||||
|
||||
图 4 中的场景使用相同的 SSID 创建了多个接入点,对于那些可以探测到但是无法接入的 WiFi 网络,这个技术可以发现网络的加密类型。通过启动具有所有安全设置的多个接入点,客户端会自动连接和本地缓存的接入点信息相匹配的接入点。
|
||||
|
||||
![Scenario for capturing a WPA handshake after a de-authentication attack][13]
|
||||
|
||||
图 4:在解除认证攻击后捕获 WPA 握手包数据。
|
||||
|
||||
使用 ETF,可以去设置 hostapd 配置文件,然后在后台启动该程序。Hostpad 支持在一张无线网卡上通过设置虚拟接口开启多个接入点,并且因为它支持所有类型的安全设置,因此可以设置完整的全能蜜罐。对于使用 WEP 和 WPA(2)-PSK 的网络,使用默认密码,和对于使用 WPA(2)-EAP 的网络,配置“全部接受”策略。
|
||||
|
||||
对于这个场景,必须在 ETF 上执行下面的命令和操作:
|
||||
|
||||
1. 进入 APLauncher 设置模式: **config aplauncher**
|
||||
2. 设置目标接入点的 SSID(APS): **set ssid = <APS>**
|
||||
3. 设置 APLauncher 为全部接收的蜜罐: **set catch_all_honeypot = true**
|
||||
4. 启动 AirHost 模块: **start airhost**
|
||||
|
||||
|
||||
|
||||
使用这些命令,ETF 可以启动一个包含所有类型安全配置的完整全能蜜罐。ETF 同样能自动启动 DHCP 和 DNS 服务器,从而让客户端能与互联网保持连接。ETF 提供了一个更好、更快、更完整的解决方案来创建全能蜜罐。下面的代码能够看到 ETF 的成功执行。
|
||||
|
||||
```
|
||||
███████╗████████╗███████╗
|
||||
██╔════╝╚══██╔══╝██╔════╝
|
||||
█████╗ ██║ █████╗
|
||||
██╔══╝ ██║ ██╔══╝
|
||||
███████╗ ██║ ██║
|
||||
╚══════╝ ╚═╝ ╚═╝
|
||||
|
||||
|
||||
[+] Do you want to load an older session? [Y/n]: n
|
||||
[+] Creating ne´,cxzw temporary session on 03/08/2018
|
||||
[+] Enter the desired session name:
|
||||
ETF[etf/aircommunicator/]::> config aplauncher
|
||||
ETF[etf/aircommunicator/airhost/aplauncher]::> setconf ssid CatchMe
|
||||
ssid = CatchMe
|
||||
ETF[etf/aircommunicator/airhost/aplauncher]::> setconf catch_all_honeypot true
|
||||
catch_all_honeypot = true
|
||||
ETF[etf/aircommunicator/airhost/aplauncher]::> start airhost
|
||||
[+] Killing already started processes and restarting network services
|
||||
[+] Stopping dnsmasq and hostapd services
|
||||
[+] Access Point stopped...
|
||||
[+] Running airhost plugins pre_start
|
||||
[+] Starting hostapd background process
|
||||
[+] Starting dnsmasq service
|
||||
[+] Running airhost plugins post_start
|
||||
[+] Access Point launched successfully
|
||||
[+] Starting dnsmasq service
|
||||
```
|
||||
|
||||
### 结论和以后的工作
|
||||
|
||||
这些场景使用常见和总所周知的攻击方式来帮助验证 ETF 测试 WIFI 网络和客户端的能力。这个结果同样证明了框架的架构能在平台现有功能的优势上开发新的攻击向量和功能。这会加快新的 WiFi 渗透测试工具的开发,因为很多的代码已经写好了。除此之外,将 WiFi 技术相关的东西都集成到一个单独的工具里,会使 WiFi 渗透测试更加简单高效。
|
||||
|
||||
ETF 的目标不是取代现有的工具,而是为它们提供补充,并为安全审计人员在进行 WiFi 测试和提升用户安全意识时,提供一个更好的选择。
|
||||
|
||||
ETF 是 GitHub 上的一个开源项目,欢迎社区为它的开发做出贡献。下面是一些您可以提供帮助的方法。
|
||||
|
||||
当前 WiFi 手动测试的一个限制是无法在测试期间记录重要的事件。这使得报告已经识别到的漏洞更加困难且准确性更低。这个框架可以实现一个登陆器,每个类都可以来访问它并创建一个手动测试会话报告。
|
||||
|
||||
ETF 工具的功能涵盖了 WiFi 手动测试的方方面面。一方面,它让 WiFi 目标侦察,漏洞挖掘和攻击这些阶段变得更加容易。另一方面,它没有提供一个便于提交报告的功能。增加会话的概念和会话报告的功能,比如在一个会话期间记录重要的事件,会极大地增加这个工具对于真实手动测试场景的价值。
|
||||
|
||||
另一个有价值的贡献是扩展框架来促进 WiFi 模糊测试。IEEE 802.11 协议非常的复杂,考虑到它在客户端和接入点两方面都会有多种实现方式。可以假设这些实现都包含 bug 甚至是安全漏洞。这些 bug 可以通过对 IEEE 802.11 协议的数据帧进行模糊测试来进行发现。因为 Scapy 允许自定义的数据包创建和数据包注入,可以通过它实现一个模糊测试器。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/19/1/evil-twin-framework
|
||||
|
||||
作者:[André Esser][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[hopefully2333](https://github.com/hopefully2333)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/andreesser
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://en.wikipedia.org/wiki/Rogue_access_point
|
||||
[2]: https://www.python.org/
|
||||
[3]: https://scapy.net
|
||||
[4]: /file/417776
|
||||
[5]: https://opensource.com/sites/default/files/uploads/pic1.png (Evil-Twin Framework Architecture)
|
||||
[6]: https://www.metasploit.com
|
||||
[7]: /file/417781
|
||||
[8]: https://opensource.com/sites/default/files/uploads/pic2.png (Scenario for capturing a WPA handshake after a de-authentication attack)
|
||||
[9]: https://en.wikipedia.org/wiki/Address_Resolution_Protocol
|
||||
[10]: /file/417786
|
||||
[11]: https://opensource.com/sites/default/files/uploads/pic3.png (Scenario for capturing a WPA handshake after a de-authentication attack)
|
||||
[12]: /file/417791
|
||||
[13]: https://opensource.com/sites/default/files/uploads/pic4.png (Scenario for capturing a WPA handshake after a de-authentication attack)
|
||||
[14]: https://github.com/Esser420/EvilTwinFramework
|
||||
@ -0,0 +1,385 @@
|
||||
[#]: collector: (lujun9972)
|
||||
[#]: translator: ( luming)
|
||||
[#]: reviewer: ( )
|
||||
[#]: publisher: ( )
|
||||
[#]: url: ( )
|
||||
[#]: subject: (How To Copy A File/Folder From A Local System To Remote System In Linux?)
|
||||
[#]: via: (https://www.2daygeek.com/linux-scp-rsync-pscp-command-copy-files-folders-in-multiple-servers-using-shell-script/)
|
||||
[#]: author: (Prakash Subramanian https://www.2daygeek.com/author/prakash/)
|
||||
|
||||
如何在 Linux 上拷贝文件/文件夹到远程系统?
|
||||
======
|
||||
|
||||
从一个服务器拷贝文件到另一个服务器,或是从本地到远程是 Linux 管理员的日常任务之一。
|
||||
|
||||
如果有人说不,我不接受。因为无论去哪这都是你的日常操作之一。
|
||||
有很多办法都能解决,我们就试着加以概括。
|
||||
你可以挑一个喜欢的方法。当然,看看其他命令也能在别的地方帮到你。
|
||||
我已经在自己的环境下测试过所有的命令和脚本了,因此你可以直接用到日常工作当中。
|
||||
通常大家都倾向 `scp` ,因为它是文件拷贝的<ruby>原生命令<rt>native command</rt></ruby>之一。但本文所列出的其它命令也很好用,建议你尝试一下。
|
||||
文件拷贝可以轻易地用以下四种方法。
|
||||
**`SCP`**:`scp` 在网络上的两个主机之间拷贝文件,与 `ssh` 使用相同的认证方式,具有相同的安全性。
|
||||
**`RSYNC`**:`rsync`是一个即快速又出众的多功能文件拷贝工具。它能本地拷贝,通过远程 shell 在其它主机之间拷贝,或者远程 `rsync` <ruby>守护进程<rt>daemon</rt></ruby>。
|
||||
**`PSCP`**:`pscp` 是一个并行拷贝文件到多个主机上的程序。它提供了诸多特性,例如为 scp 配置免密传输,保存输出到 文件,统计时长。
|
||||
**`PRSYNC`**:`prsync` 也是一个并行拷贝文件到多个主机上的程序。它也提供了诸多特性,例如为 ssh 配置免密传输,保存输出到 文件,统计时长。
|
||||
|
||||
### 方式1:如何在 Linux 上使用 scp 命令从本地系统向远程系统拷贝文件/文件夹?
|
||||
|
||||
`scp` 命令可以让我们拷贝文件/文件夹到远程系统上。
|
||||
|
||||
我会把 `output.txt` 文件从本地系统拷贝到 `2g.CentOS.com` 远程系统的 `/opt/backup` 文件夹下。
|
||||
|
||||
```
|
||||
# scp output.txt root@2g.CentOS.com:/opt/backup
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
```
|
||||
|
||||
拷贝两个文件 `output.txt` 和 `passwd-up.sh` 到远程系统 `2g.CentOs.com` 的 `/opt/backup` 文件夹下。
|
||||
|
||||
```
|
||||
# scp output.txt passwd-up.sh root@2g.CentOS.com:/opt/backup
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
passwd-up.sh 100% 877 0.9KB/s 00:00
|
||||
```
|
||||
|
||||
拷贝 `shell-script` 文件夹到远程系统`2g.CentOs.com` 的 `/opt/back` 文件夹下。
|
||||
这会连同`/opt/backup`文件夹下所有的文件一同拷贝进去。
|
||||
|
||||
```
|
||||
# scp -r /home/daygeek/2g/shell-script/ root@:/opt/backup/
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
ovh.sh 100% 76 0.1KB/s 00:00
|
||||
passwd-up.sh 100% 877 0.9KB/s 00:00
|
||||
passwd-up1.sh 100% 7 0.0KB/s 00:00
|
||||
server-list.txt 100% 23 0.0KB/s 00:00
|
||||
```
|
||||
|
||||
### 方式2:如何在 Linux 上使用 scp 命令和 Shell 脚本拷贝文件/文件夹到多个远程系统上?
|
||||
|
||||
如果你想拷贝同一个文件到多个远程服务器上,那就需要创建一个如下面那样的小 shell 脚本。
|
||||
|
||||
并且,需要将服务器添加进 `server-list.txt` 文件。确保添加成功后,每个服务器之间应当空一行。
|
||||
|
||||
最终,你想要的脚本就像下面这样:
|
||||
```
|
||||
# file-copy.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
scp /home/daygeek/2g/shell-script/output.txt root@$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
完成之后,给 `file-copy.sh` 文件设置可执行权限。
|
||||
```
|
||||
# chmod +x file-copy.sh
|
||||
```
|
||||
|
||||
最后运行脚本完成拷贝。
|
||||
|
||||
```
|
||||
# ./file-copy.sh
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
```
|
||||
|
||||
使用下面的脚本可以拷贝多个文件到多个远程服务器上。
|
||||
|
||||
```
|
||||
# file-copy.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
scp /home/daygeek/2g/shell-script/output.txt passwd-up.sh root@$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
下面结果显示所有的两个文件都拷贝到两个服务器上。
|
||||
```
|
||||
# ./file-cp.sh
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
passwd-up.sh 100% 877 0.9KB/s 00:00
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
passwd-up.sh 100% 877 0.9KB/s 00:00
|
||||
```
|
||||
|
||||
使用下面的脚本递归地拷贝文件夹到多个远程服务器上。
|
||||
|
||||
```
|
||||
# file-copy.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
scp -r /home/daygeek/2g/shell-script/ root@$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
上面脚本的输出。
|
||||
```
|
||||
# ./file-cp.sh
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
ovh.sh 100% 76 0.1KB/s 00:00
|
||||
passwd-up.sh 100% 877 0.9KB/s 00:00
|
||||
passwd-up1.sh 100% 7 0.0KB/s 00:00
|
||||
server-list.txt 100% 23 0.0KB/s 00:00
|
||||
|
||||
output.txt 100% 2468 2.4KB/s 00:00
|
||||
ovh.sh 100% 76 0.1KB/s 00:00
|
||||
passwd-up.sh 100% 877 0.9KB/s 00:00
|
||||
passwd-up1.sh 100% 7 0.0KB/s 00:00
|
||||
server-list.txt 100% 23 0.0KB/s 00:00
|
||||
```
|
||||
|
||||
### 方式3:如何在 Linux 上使用 pscp 命令拷贝文件/文件夹到多个远程系统上?
|
||||
|
||||
`pscp` 命令可以直接让我们拷贝文件到多个远程服务器上。
|
||||
|
||||
使用下面的 `pscp` 命令拷贝单个文件到远程服务器。
|
||||
|
||||
```
|
||||
# pscp.pssh -H 2g.CentOS.com /home/daygeek/2g/shell-script/output.txt /opt/backup
|
||||
|
||||
[1] 18:46:11 [SUCCESS] 2g.CentOS.com
|
||||
```
|
||||
|
||||
使用下面的 `pscp` 命令拷贝多个文件到远程服务器。
|
||||
|
||||
```
|
||||
# pscp.pssh -H 2g.CentOS.com /home/daygeek/2g/shell-script/output.txt ovh.sh /opt/backup
|
||||
|
||||
[1] 18:47:48 [SUCCESS] 2g.CentOS.com
|
||||
```
|
||||
|
||||
递归地拷贝整个文件夹到远程服务器。
|
||||
|
||||
```
|
||||
# pscp.pssh -H 2g.CentOS.com -r /home/daygeek/2g/shell-script/ /opt/backup
|
||||
|
||||
[1] 18:48:46 [SUCCESS] 2g.CentOS.com
|
||||
```
|
||||
|
||||
使用下面的命令拷贝单个文件到多个远程服务器。
|
||||
|
||||
```
|
||||
# pscp.pssh -h server-list.txt /home/daygeek/2g/shell-script/output.txt /opt/backup
|
||||
|
||||
[1] 18:49:48 [SUCCESS] 2g.CentOS.com
|
||||
[2] 18:49:48 [SUCCESS] 2g.Debian.com
|
||||
```
|
||||
|
||||
使用下面的 `pscp` 命令拷贝多个文件到多个远程服务器。
|
||||
|
||||
```
|
||||
# pscp.pssh -h server-list.txt /home/daygeek/2g/shell-script/output.txt passwd-up.sh /opt/backup
|
||||
|
||||
[1] 18:50:30 [SUCCESS] 2g.Debian.com
|
||||
[2] 18:50:30 [SUCCESS] 2g.CentOS.com
|
||||
```
|
||||
|
||||
使用下面的命令递归地拷贝文件夹到多个远程服务器。
|
||||
|
||||
```
|
||||
# pscp.pssh -h server-list.txt -r /home/daygeek/2g/shell-script/ /opt/backup
|
||||
|
||||
[1] 18:51:31 [SUCCESS] 2g.Debian.com
|
||||
[2] 18:51:31 [SUCCESS] 2g.CentOS.com
|
||||
```
|
||||
|
||||
### 方式4:如何在 Linux 上使用 rsync 命令拷贝文件/文件夹到多个远程系统上?
|
||||
|
||||
`rsync`是一个即快速又出众的多功能文件拷贝工具。它能本地拷贝,通过远程 shell 在其它主机之间拷贝,或者远程 `rsync` <ruby>守护进程<rt>daemon</rt></ruby>。
|
||||
|
||||
使用下面的 `rsync` 命令拷贝单个文件到远程服务器。
|
||||
|
||||
```
|
||||
# rsync -avz /home/daygeek/2g/shell-script/output.txt root@:/opt/backup
|
||||
|
||||
sending incremental file list
|
||||
output.txt
|
||||
|
||||
sent 598 bytes received 31 bytes 1258.00 bytes/sec
|
||||
total size is 2468 speedup is 3.92
|
||||
```
|
||||
|
||||
使用下面的 `rsync` 命令拷贝多个文件到远程服务器。
|
||||
|
||||
```
|
||||
# rsync -avz /home/daygeek/2g/shell-script/output.txt passwd-up.sh root@2g.CentOS.com:/opt/backup
|
||||
|
||||
sending incremental file list
|
||||
output.txt
|
||||
passwd-up.sh
|
||||
|
||||
sent 737 bytes received 50 bytes 1574.00 bytes/sec
|
||||
total size is 2537 speedup is 3.22
|
||||
```
|
||||
|
||||
使用下面的 `rsync` 命令通过 `ssh` 拷贝单个文件到远程服务器。
|
||||
|
||||
```
|
||||
# rsync -avzhe ssh /home/daygeek/2g/shell-script/output.txt root@2g.CentOS.com:/opt/backup
|
||||
|
||||
sending incremental file list
|
||||
output.txt
|
||||
|
||||
sent 598 bytes received 31 bytes 419.33 bytes/sec
|
||||
total size is 2.47K speedup is 3.92
|
||||
```
|
||||
|
||||
使用下面的 `rsync` 命令通过 `ssh` 递归地拷贝文件夹到远程服务器。这种方式只拷贝文件不包括文件夹。
|
||||
|
||||
```
|
||||
# rsync -avzhe ssh /home/daygeek/2g/shell-script/ root@2g.CentOS.com:/opt/backup
|
||||
|
||||
sending incremental file list
|
||||
./
|
||||
output.txt
|
||||
ovh.sh
|
||||
passwd-up.sh
|
||||
passwd-up1.sh
|
||||
server-list.txt
|
||||
|
||||
sent 3.85K bytes received 281 bytes 8.26K bytes/sec
|
||||
total size is 9.12K speedup is 2.21
|
||||
```
|
||||
|
||||
### 如何在 Linux 上使用 rsync 命令和 Shell 脚本拷贝文件/文件夹到多个远程系统上?
|
||||
|
||||
如果你想拷贝同一个文件到多个远程服务器上,那也需要创建一个如下面那样的小 shell 脚本。
|
||||
|
||||
```
|
||||
# file-copy.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
rsync -avzhe ssh /home/daygeek/2g/shell-script/ root@2g.CentOS.com$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
上面脚本的输出。
|
||||
|
||||
```
|
||||
# ./file-copy.sh
|
||||
|
||||
sending incremental file list
|
||||
./
|
||||
output.txt
|
||||
ovh.sh
|
||||
passwd-up.sh
|
||||
passwd-up1.sh
|
||||
server-list.txt
|
||||
|
||||
sent 3.86K bytes received 281 bytes 8.28K bytes/sec
|
||||
total size is 9.13K speedup is 2.21
|
||||
|
||||
sending incremental file list
|
||||
./
|
||||
output.txt
|
||||
ovh.sh
|
||||
passwd-up.sh
|
||||
passwd-up1.sh
|
||||
server-list.txt
|
||||
|
||||
sent 3.86K bytes received 281 bytes 2.76K bytes/sec
|
||||
total size is 9.13K speedup is 2.21
|
||||
```
|
||||
|
||||
### 方式6:如何在 Linux 上使用 scp 命令和 Shell 脚本从本地系统向多个远程系统拷贝文件/文件夹?
|
||||
|
||||
在上面两个 shell 脚本中,我们需要事先指定好文件和文件夹的路径,这儿我做了些小修改,让脚本可以接收文件或文件夹的输入。当你每天需要多次执行拷贝时,这将会非常有用。
|
||||
|
||||
```
|
||||
# file-copy.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
scp -r $1 root@2g.CentOS.com$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
输入文件名并运行脚本。
|
||||
|
||||
```
|
||||
# ./file-copy.sh output1.txt
|
||||
|
||||
output1.txt 100% 3558 3.5KB/s 00:00
|
||||
output1.txt 100% 3558 3.5KB/s 00:00
|
||||
```
|
||||
|
||||
### 方式7:如何在Linux 系统上用非标准端口拷贝文件/文件夹到远程系统?
|
||||
|
||||
如果你想使用非标准端口,使用下面的 shell 脚本拷贝文件或文件夹。
|
||||
|
||||
如果你使用了<ruby>非标准<rt>Non-Standard</rt></ruby>端口,确保像下面 `SCP` 命令那样指定好了端口号。
|
||||
|
||||
```
|
||||
# file-copy-scp.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
scp -P 2222 -r $1 root@2g.CentOS.com$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
运行脚本,输入文件名。
|
||||
|
||||
```
|
||||
# ./file-copy.sh ovh.sh
|
||||
|
||||
ovh.sh 100% 3558 3.5KB/s 00:00
|
||||
ovh.sh 100% 3558 3.5KB/s 00:00
|
||||
```
|
||||
|
||||
如果你使用了<ruby>非标准<rt>Non-Standard</rt></ruby>端口,确保像下面 `rsync` 命令那样指定好了端口号。
|
||||
|
||||
```
|
||||
# file-copy-rsync.sh
|
||||
|
||||
#!/bin/sh
|
||||
for server in `more server-list.txt`
|
||||
do
|
||||
rsync -avzhe 'ssh -p 2222' $1 root@2g.CentOS.com$server:/opt/backup
|
||||
done
|
||||
```
|
||||
|
||||
运行脚本,输入文件名
|
||||
|
||||
```
|
||||
# ./file-copy-rsync.sh passwd-up.sh
|
||||
sending incremental file list
|
||||
passwd-up.sh
|
||||
|
||||
sent 238 bytes received 35 bytes 26.00 bytes/sec
|
||||
total size is 159 speedup is 0.58
|
||||
|
||||
sending incremental file list
|
||||
passwd-up.sh
|
||||
|
||||
sent 238 bytes received 35 bytes 26.00 bytes/sec
|
||||
total size is 159 speedup is 0.58
|
||||
```
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/linux-scp-rsync-pscp-command-copy-files-folders-in-multiple-servers-using-shell-script/
|
||||
|
||||
作者:[Prakash Subramanian][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[LuuMing](https://github.com/LuuMing)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.2daygeek.com/author/prakash/
|
||||
[b]: https://github.com/lujun9972
|
||||
Loading…
Reference in New Issue
Block a user