mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-13 22:30:37 +08:00
commit
2c749e2404
@ -1,224 +0,0 @@
|
||||
translating---geekpi
|
||||
|
||||
How to Fix SambaCry Vulnerability (CVE-2017-7494) in Linux Systems
|
||||
============================================================
|
||||
|
||||
|
||||
Samba has long been the standard for providing shared file and print services to Windows clients on *nix systems. Used by home users, mid-size businesses, and large companies alike, it stands out as the go-to solution in environments where different operating systems coexist.
|
||||
|
||||
As it sadly happens with broadly-used tools, most Samba installations are under risk of an attack that may exploit a known vulnerability, which was not considered to be serious until the WannaCry ransomware attack hit the news not too long ago.
|
||||
|
||||
In this article, we will explain what this Samba vulnerability is and how to protect the systems you are responsible for against it. Depending on your installation type (from repositories or from source), you will need to take a different approach to do it.
|
||||
|
||||
If you are currently using Samba in any environment or know someone who does, read on!
|
||||
|
||||
### The Vulnerability
|
||||
|
||||
Outdated and unpatched systems are vulnerable to a remote code execution vulnerability. In simple terms, this means that a person with access to a writeable share can upload a piece of arbitrary code and execute it with root permissions in the server.
|
||||
|
||||
The issue is described in the Samba website as [CVE-2017-7494][1] and is known to affect Samba versions 3.5 (released in early March 2010) and onwards. Unofficially, it has been named SambaCry due to its similarities with WannaCry: both target the SMB protocol and are potentially wormable – which can cause it to spread from system to system.
|
||||
|
||||
Debian, Ubuntu, CentOS and Red Hat have taken rapid action to protect its users and have released patches for their supported versions. Additionally, security workarounds have also been provided for unsupported ones.
|
||||
|
||||
### Updating Samba
|
||||
|
||||
As mentioned earlier, there are two approaches to follow depending on the previous installation method:
|
||||
|
||||
If you installed Samba from your distribution’s repositories.
|
||||
|
||||
Let’s take a look at what you need to do in this case:
|
||||
|
||||
#### Fix Sambacry in Debian
|
||||
|
||||
Make sure [apt][2] is set to get the latest security updates by adding the following lines to your sources list (/etc/apt/sources.list):
|
||||
|
||||
```
|
||||
deb http://security.debian.org stable/updates main
|
||||
deb-src http://security.debian.org/ stable/updates main
|
||||
```
|
||||
|
||||
Next, update the list of available packages:
|
||||
|
||||
```
|
||||
# aptitude update
|
||||
```
|
||||
|
||||
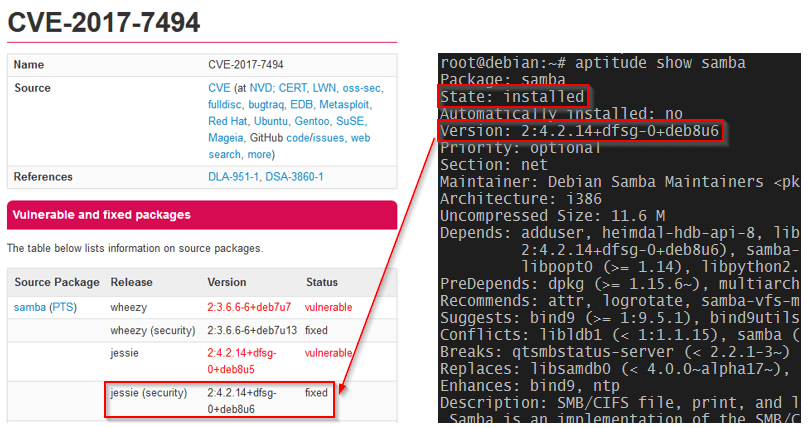
Finally, make sure the version of the samba package matches the version where the vulnerability has been fixed (see [CVE-2017-7494][3]):
|
||||
|
||||
```
|
||||
# aptitude show samba
|
||||
```
|
||||
|
||||
|
||||
|
||||
Fix Sambacry in Debian
|
||||
|
||||
#### Fix Sambacry in Ubuntu
|
||||
|
||||
To begin, check for new available packages and update the samba package as follows:
|
||||
|
||||
```
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install samba
|
||||
```
|
||||
|
||||
The Samba versions where the fix for CVE-2017-7494 has already been applied are the following:
|
||||
|
||||
* 17.04: samba 2:4.5.8+dfsg-0ubuntu0.17.04.2
|
||||
|
||||
* 16.10: samba 2:4.4.5+dfsg-2ubuntu5.6
|
||||
|
||||
* 16.04 LTS: samba 2:4.3.11+dfsg-0ubuntu0.16.04.7
|
||||
|
||||
* 14.04 LTS: samba 2:4.3.11+dfsg-0ubuntu0.14.04.8
|
||||
|
||||
Finally, run the following command to verify that your Ubuntu box now has the right Samba version installed.
|
||||
|
||||
```
|
||||
$ sudo apt-cache show samba
|
||||
```
|
||||
|
||||
#### Fix Sambacry on CentOS/RHEL 7
|
||||
|
||||
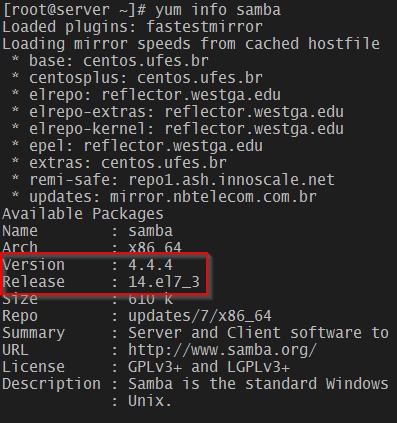
The patched Samba version in EL 7 is samba-4.4.4-14.el7_3. To install it, do
|
||||
|
||||
```
|
||||
# yum makecache fast
|
||||
# yum update samba
|
||||
```
|
||||
|
||||
As before, make sure you have now the patched Samba version:
|
||||
|
||||
```
|
||||
# yum info samba
|
||||
```
|
||||
|
||||
|
||||
|
||||
Fix Sambacry in CentOS
|
||||
|
||||
Older, still supported versions of CentOS and RHEL have available fixes as well. Check [RHSA-2017-1270][4] to find out more.
|
||||
|
||||
##### If you installed Samba from source
|
||||
|
||||
Note: The following procedure assumes that you have previously built Samba from source. You are highly encouraged to try it out extensively in a testing environment BEFORE deploying it to a production server.
|
||||
|
||||
Additionally, make sure you back up the smb.conf file before you start.
|
||||
|
||||
In this case, we will compile and update Samba from source as well. Before we begin, however, we must ensure all the dependencies are previously installed. Note that this may take several minutes.
|
||||
|
||||
#### In Debian and Ubuntu:
|
||||
|
||||
```
|
||||
# aptitude install acl attr autoconf bison build-essential \
|
||||
debhelper dnsutils docbook-xml docbook-xsl flex gdb krb5-user \
|
||||
libacl1-dev libaio-dev libattr1-dev libblkid-dev libbsd-dev \
|
||||
libcap-dev libcups2-dev libgnutls28-dev libjson-perl \
|
||||
libldap2-dev libncurses5-dev libpam0g-dev libparse-yapp-perl \
|
||||
libpopt-dev libreadline-dev perl perl-modules pkg-config \
|
||||
python-all-dev python-dev python-dnspython python-crypto xsltproc \
|
||||
zlib1g-dev libsystemd-dev libgpgme11-dev python-gpgme python-m2crypto
|
||||
```
|
||||
|
||||
#### In CentOS 7 or similar:
|
||||
|
||||
```
|
||||
# yum install attr bind-utils docbook-style-xsl gcc gdb krb5-workstation \
|
||||
libsemanage-python libxslt perl perl-ExtUtils-MakeMaker \
|
||||
perl-Parse-Yapp perl-Test-Base pkgconfig policycoreutils-python \
|
||||
python-crypto gnutls-devel libattr-devel keyutils-libs-devel \
|
||||
libacl-devel libaio-devel libblkid-devel libxml2-devel openldap-devel \
|
||||
pam-devel popt-devel python-devel readline-devel zlib-devel
|
||||
```
|
||||
|
||||
Stop the service:
|
||||
|
||||
```
|
||||
# systemctl stop smbd
|
||||
```
|
||||
|
||||
Download and untar the source (with 4.6.4 being the latest version at the time of this writing):
|
||||
|
||||
```
|
||||
# wget https://www.samba.org/samba/ftp/samba-latest.tar.gz
|
||||
# tar xzf samba-latest.tar.gz
|
||||
# cd samba-4.6.4
|
||||
```
|
||||
|
||||
For informative purposes only, check the available configure options for the current release with.
|
||||
|
||||
```
|
||||
# ./configure --help
|
||||
```
|
||||
|
||||
You may include some of the options returned by the above command if they were used in the previous build, or you may choose to go with the default:
|
||||
|
||||
```
|
||||
# ./configure
|
||||
# make
|
||||
# make install
|
||||
```
|
||||
|
||||
Finally, restart the service.
|
||||
|
||||
```
|
||||
# systemctl restart smbd
|
||||
```
|
||||
|
||||
and verify you’re running the updated version:
|
||||
|
||||
```
|
||||
# smbstatus --version
|
||||
```
|
||||
|
||||
which should return 4.6.4.
|
||||
|
||||
### General Considerations
|
||||
|
||||
If you are running an unsupported version of a given distribution and are unable to upgrade to a more recent one for some reason, you may want to take the following suggestions into account:
|
||||
|
||||
* If SELinux is enabled, you are protected!
|
||||
|
||||
* Make sure Samba shares are mounted with the noexec option. This will prevent the execution of binaries residing on the mounted filesystem.
|
||||
|
||||
Add,
|
||||
|
||||
```
|
||||
nt pipe support = no
|
||||
```
|
||||
|
||||
to the [global] section of your smb.conf file and restart the service. You may want to keep in mind that this “may disable some functionality in Windows clients”, as per the Samba project.
|
||||
|
||||
Important: Be aware that the option “nt pipe support = no” would disable shares listing from Windows clients. Eg: When you type \\10.100.10.2\ from Windows Explorer on a samba server you would get a permission denied. Windows clients would have to manually specify the share as \\10.100.10.2\share_name to access the share.
|
||||
|
||||
##### Summary
|
||||
|
||||
In this article, we have described the vulnerability known as SambaCry and how to mitigate it. We hope that you will be able to use this information to protect the systems you’re responsible for.
|
||||
|
||||
If you have any questions or comments about this article, feel free to use the form below to let us know.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:
|
||||
|
||||
|
||||
Gabriel Cánepa is a GNU/Linux sysadmin and web developer from Villa Mercedes, San Luis, Argentina. He works for a worldwide leading consumer product company and takes great pleasure in using FOSS tools to increase productivity in all areas of his daily work.
|
||||
|
||||
--------------
|
||||
|
||||
via: https://www.tecmint.com/fix-sambacry-vulnerability-cve-2017-7494-in-linux/
|
||||
|
||||
作者:[Gabriel Cánepa ][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.tecmint.com/author/gacanepa/
|
||||
[1]:https://www.samba.org/samba/security/CVE-2017-7494.html
|
||||
[2]:https://www.tecmint.com/apt-advanced-package-command-examples-in-ubuntu/
|
||||
[3]:https://security-tracker.debian.org/tracker/CVE-2017-7494
|
||||
[4]:https://rhn.redhat.com/errata/RHSA-2017-1270.html
|
||||
[5]:https://www.tecmint.com/author/gacanepa/
|
||||
[6]:https://www.tecmint.com/10-useful-free-linux-ebooks-for-newbies-and-administrators/
|
||||
[7]:https://www.tecmint.com/free-linux-shell-scripting-books/
|
||||
@ -0,0 +1,222 @@
|
||||
Linux 系统中修复 SambaCry 漏洞(CVE-2017-7494)
|
||||
============================================================
|
||||
|
||||
|
||||
Samba 很久以来是为 *nix 系统上的 Windows 客户端提供共享文件和打印服务的标准。家庭用户,中型企业和大型公司都在使用它,它作为最佳解决方案在不同操作系统共存的环境中脱颖而出。
|
||||
|
||||
由于广泛使用的工具很可能发生这种情况,大多数 Samba 安装都面临着可能利用已知漏洞的攻击的风险,这个漏洞直到 WannaCry 勒索软件攻击的新闻出来之前都被认为是不重要的。
|
||||
|
||||
在本文中,我们将解释这个 Samba 漏洞是什么以及如何保护你负责的系统。根据你的安装类型(从仓库或者源码),你需要采取不同的方法。
|
||||
|
||||
如果你目前有在任何环境中使用 Samba 或者知道有人在使用,请继续阅读!
|
||||
|
||||
### 漏洞
|
||||
|
||||
过时和未修补的系统容易受到远程代码执行漏洞的攻击。简单来说,这意味着访问可写共享的人可以上传一段任意代码,并使用服务器中的 root 权限执行该代码。
|
||||
|
||||
这个问题在 Samba 网站上被描述为 [CVE-2017-7494][1],并且已知会影响 Samba v3.5(2010 年 3 月初发布)及以后版本。由于与 WannaCry 有相似之处,它被非官方地被命名为 SambaCry:它们均针对 SMB 协议,并且可能是蠕虫病毒 - 这可能导致其从一个系统传播到另一个系统中。
|
||||
|
||||
Debian、Ubuntu、CentOS 和 Red Hat 已采取快速的行动来保护它们的用户,并为其支持的版本发布了补丁。另外,还提供了不受支持的安全临时解决方案。
|
||||
|
||||
### 更新 Samba
|
||||
|
||||
如先前提到的那样,根据你之前安装的方法有两种方式更新:
|
||||
|
||||
如果你从发行版的仓库中安装的 Samba。
|
||||
|
||||
让我们看下在这种情况下你需要做什么:
|
||||
|
||||
#### 在 Debian 下修复 Sambacry
|
||||
|
||||
添加下面的行到你的源列表中(/etc/apt/sources.list)以确保 [apt][2] 能够获得最新的安全更新:
|
||||
|
||||
```
|
||||
deb http://security.debian.org stable/updates main
|
||||
deb-src http://security.debian.org/ stable/updates main
|
||||
```
|
||||
|
||||
接下来,更新可用的软件包:
|
||||
|
||||
```
|
||||
# aptitude update
|
||||
```
|
||||
|
||||
最后,确保 samba 软件包的版本符合漏洞修复的版本(见 [CVE-2017-7494][3]):
|
||||
|
||||
```
|
||||
# aptitude show samba
|
||||
```
|
||||
|
||||

|
||||
|
||||
在 Debian 中修复 Sambacry
|
||||
|
||||
#### 在 Ubuntu 中修复 Sambacry
|
||||
|
||||
要开始修复,如下检查新的可用软件包并更新 samba 软件包:
|
||||
|
||||
```
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install samba
|
||||
```
|
||||
|
||||
已经修复 CVE-2017-7494 的 Samba 版本有下面这些:
|
||||
|
||||
* 17.04: samba 2:4.5.8+dfsg-0ubuntu0.17.04.2
|
||||
|
||||
* 16.10: samba 2:4.4.5+dfsg-2ubuntu5.6
|
||||
|
||||
* 16.04 LTS: samba 2:4.3.11+dfsg-0ubuntu0.16.04.7
|
||||
|
||||
* 14.04 LTS: samba 2:4.3.11+dfsg-0ubuntu0.14.04.8
|
||||
|
||||
最后,运行下面命令验证你的 Ubuntu 已经安装了正确的版本。
|
||||
|
||||
```
|
||||
$ sudo apt-cache show samba
|
||||
```
|
||||
|
||||
#### 在 CentOS/RHEL 7 中修复 Sambacry
|
||||
|
||||
在 EL 7 中打过补丁的 Samba 版本是 samba-4.4.4-14.el7_3。要安装它,这些做:
|
||||
|
||||
```
|
||||
# yum makecache fast
|
||||
# yum update samba
|
||||
```
|
||||
|
||||
像先前那样,确保你已经安装了打补丁的 Samba 版本:
|
||||
|
||||
```
|
||||
# yum info samba
|
||||
```
|
||||
|
||||

|
||||
|
||||
在 CentOS 中修复 Sambacry
|
||||
|
||||
旧支持的 CentOS 以及 RHEL 更老的版本也有修复。参见 [RHSA-2017-1270][4] 获取更多。
|
||||
|
||||
##### 如果你从源码安装的 Samba
|
||||
|
||||
注意:下面的过程假设你先前从源码构建的 Samba。强烈建议你在部署到生产服务器之前先在测试环境尝试。
|
||||
|
||||
额外地,开始之前确保你备份了 smb.conf 文件。
|
||||
|
||||
在这种情况下,我们也会从源码编译并更新 Samba。然而在开始之前,我们必须先确保安装了所有的依赖。注意这也许会花费几分钟。
|
||||
|
||||
#### 在 Debian 和 Ubuntu 中:
|
||||
|
||||
```
|
||||
# aptitude install acl attr autoconf bison build-essential \
|
||||
debhelper dnsutils docbook-xml docbook-xsl flex gdb krb5-user \
|
||||
libacl1-dev libaio-dev libattr1-dev libblkid-dev libbsd-dev \
|
||||
libcap-dev libcups2-dev libgnutls28-dev libjson-perl \
|
||||
libldap2-dev libncurses5-dev libpam0g-dev libparse-yapp-perl \
|
||||
libpopt-dev libreadline-dev perl perl-modules pkg-config \
|
||||
python-all-dev python-dev python-dnspython python-crypto xsltproc \
|
||||
zlib1g-dev libsystemd-dev libgpgme11-dev python-gpgme python-m2crypto
|
||||
```
|
||||
|
||||
#### 在 CentOS 7 或相似的版本中:
|
||||
|
||||
```
|
||||
# yum install attr bind-utils docbook-style-xsl gcc gdb krb5-workstation \
|
||||
libsemanage-python libxslt perl perl-ExtUtils-MakeMaker \
|
||||
perl-Parse-Yapp perl-Test-Base pkgconfig policycoreutils-python \
|
||||
python-crypto gnutls-devel libattr-devel keyutils-libs-devel \
|
||||
libacl-devel libaio-devel libblkid-devel libxml2-devel openldap-devel \
|
||||
pam-devel popt-devel python-devel readline-devel zlib-devel
|
||||
```
|
||||
|
||||
停止服务:
|
||||
|
||||
```
|
||||
# systemctl stop smbd
|
||||
```
|
||||
|
||||
下载并解压源码(在写作时 4.6.4 是最新的版本):
|
||||
|
||||
```
|
||||
# wget https://www.samba.org/samba/ftp/samba-latest.tar.gz
|
||||
# tar xzf samba-latest.tar.gz
|
||||
# cd samba-4.6.4
|
||||
```
|
||||
|
||||
出于了解信息的目的,用以下命令检查可用的配置选项。
|
||||
|
||||
```
|
||||
# ./configure --help
|
||||
```
|
||||
|
||||
如果你在先前的版本的构建中有使用到一些选项,你或许可以在上面命令的返回中包含一些选项,或者你可以选择使用默认值:
|
||||
|
||||
```
|
||||
# ./configure
|
||||
# make
|
||||
# make install
|
||||
```
|
||||
|
||||
最后重启服务。
|
||||
|
||||
```
|
||||
# systemctl restart smbd
|
||||
```
|
||||
|
||||
并验证你正在使用的是更新后的版本:
|
||||
|
||||
```
|
||||
# smbstatus --version
|
||||
```
|
||||
|
||||
这里返回的应该是 4.6.4。
|
||||
|
||||
### 概论
|
||||
|
||||
如果你使用的是不受支持的发行版本,并且由于某些原因无法升级到最新版本,你或许要考虑下面这些建议:
|
||||
|
||||
* 如果 SELinux 是启用的,你是受保护的!
|
||||
|
||||
* 确保 Samba 共享是用 noexec 选项挂载的。这会阻止二进制文件从被挂载的文件系统中执行。
|
||||
|
||||
还有将
|
||||
|
||||
```
|
||||
nt pipe support = no
|
||||
```
|
||||
|
||||
添加到 smb.conf 的 [global] 字段中。你或许要记住,根据 Samba 项目,这“或许禁用 Windows 客户端的某些功能”。
|
||||
|
||||
重要:注意 “nt pipe support = no” 选项会禁用 Windows 客户端的共享列表。比如:当你在一台 Samba 服务器的 Windows Explorer 中输入 \\10.100.10.2\ 时,你会看到 “permission denied”。Windows 客户端不得不手动执行共享,如 \\10.100.10.2\share_name 来访问共享。
|
||||
|
||||
##### 总结
|
||||
|
||||
在本篇中,我们已经描述了 SambaCry 漏洞以及如何减轻影响。我们希望你可以使用这个信息来保护你负责的系统。
|
||||
|
||||
如果你有关于这篇文章的任何提问以及评论,欢迎使用下面的评论栏让我们知道。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
作者简介:
|
||||
|
||||
|
||||
Gabriel Cánepa 是一名 GNU/Linux 系统管理员,阿根廷圣路易斯 Villa Mercedes 的 web 开发人员。他为一家国际大型消费品公司工作,在日常工作中使用 FOSS 工具以提高生产力,并从中获得极大乐趣。
|
||||
|
||||
--------------
|
||||
|
||||
via: https://www.tecmint.com/fix-sambacry-vulnerability-cve-2017-7494-in-linux/
|
||||
|
||||
作者:[Gabriel Cánepa ][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.tecmint.com/author/gacanepa/
|
||||
[1]:https://www.samba.org/samba/security/CVE-2017-7494.html
|
||||
[2]:https://www.tecmint.com/apt-advanced-package-command-examples-in-ubuntu/
|
||||
[3]:https://security-tracker.debian.org/tracker/CVE-2017-7494
|
||||
[4]:https://rhn.redhat.com/errata/RHSA-2017-1270.html
|
||||
[5]:https://www.tecmint.com/author/gacanepa/
|
||||
[6]:https://www.tecmint.com/10-useful-free-linux-ebooks-for-newbies-and-administrators/
|
||||
[7]:https://www.tecmint.com/free-linux-shell-scripting-books/
|
||||
Loading…
Reference in New Issue
Block a user