mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-25 23:11:02 +08:00
翻译完成 (#4638)
* 翻译完毕 * Delete 20161018 How to Secure Network Services Using TCP Wrappers in Linux.md
This commit is contained in:
parent
c3246218d7
commit
28f5784379
@ -1,153 +0,0 @@
|
||||
LinuxBars翻译中
|
||||
How to Secure Network Services Using TCP Wrappers in Linux
|
||||
===========
|
||||
|
||||
|
||||
In this article we will explain what TCP wrappers are and how to configure them to [restrict access to network services][7] running on a Linux server. Before we start, however, we must clarify that the use of TCP wrappers does not eliminate the need for a properly [configured firewall][6].
|
||||
|
||||
In this regard, you can think of this tool as a [host-based access control list][5], and not as the [ultimate security measure][4] for your system. By using a firewall and TCP wrappers, instead of favoring one over the other, you will make sure that your server is not left with a single point of failure.
|
||||
|
||||
### Understanding hosts.allow and hosts.deny
|
||||
|
||||
When a network request reaches your server, TCP wrappers uses `hosts.allow` and `hosts.deny` (in that order) to determine if the client should be allowed to use a given service.
|
||||
|
||||
By default, these files are empty, all commented out, or do not exist. Thus, everything is allowed through the TCP wrappers layer and your system is left to rely on the firewall for full protection. Since this is not desired, due to the reason we stated in the introduction, make sure both files exist:
|
||||
|
||||
```
|
||||
# ls -l /etc/hosts.allow /etc/hosts.deny
|
||||
|
||||
```
|
||||
|
||||
The syntax of both files is the same:
|
||||
|
||||
```
|
||||
<services> : <clients> [: <option1> : <option2> : ...]
|
||||
|
||||
```
|
||||
|
||||
where,
|
||||
|
||||
1. services is a comma-separated list of services the current rule should be applied to.
|
||||
2. clients represent the list of comma-separated hostnames or IP addresses affected by the rule. The following wildcards are accepted:
|
||||
1. ALL matches everything. Applies both to clients and services.
|
||||
2. LOCAL matches hosts without a period in their FQDN, such as localhost.
|
||||
3. KNOWN indicate a situation where the hostname, host address, or user are known.
|
||||
4. UNKNOWN is the opposite of KNOWN.
|
||||
5. PARANOID causes a connection to be dropped if reverse DNS lookups (first on IP address to determine host name, then on host name to obtain the IP addresses) return a different address in each case.
|
||||
3. Finally, an optional list of colon-separated actions indicate what should happen when a given rule is triggered.
|
||||
|
||||
You may want to keep in mind that a rule allowing access to a given service in `/etc/hosts.allow` takes precedence over a rule in `/etc/hosts.deny` prohibiting it. Additionally, if two rules apply to the same service, only the first one will be taken into account.
|
||||
|
||||
Unfortunately, not all network services support the use of TCP wrappers. To determine if a given service supports them, do:
|
||||
|
||||
```
|
||||
# ldd /path/to/binary | grep libwrap
|
||||
|
||||
```
|
||||
|
||||
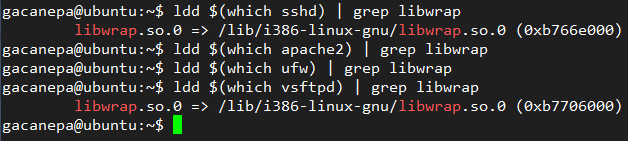
If the above command returns output, it can be TCP-wrapped. An example of this are sshd and vsftpd, as shown here:
|
||||
|
||||
[][3]
|
||||
|
||||
Find Supported Services in TCP Wrapper
|
||||
|
||||
### How to Use TCP Wrappers to Restrict Access to Services
|
||||
|
||||
As you edit `/etc/hosts.allow` and `/etc/hosts.deny`, make sure you add a newline by pressing Enter after the last non-empty line.
|
||||
|
||||
To [allow SSH and FTP access][2] only to 192.168.0.102 and localhost and deny all others, add these two lines in `/etc/hosts.deny`:
|
||||
|
||||
```
|
||||
sshd,vsftpd : ALL
|
||||
ALL : ALL
|
||||
|
||||
```
|
||||
|
||||
and the following line in `/etc/hosts.allow`:
|
||||
|
||||
```
|
||||
sshd,vsftpd : 192.168.0.102,LOCAL
|
||||
|
||||
```
|
||||
|
||||
TCP Wrappers – hosts.deny File
|
||||
```
|
||||
#
|
||||
# hosts.deny This file contains access rules which are used to
|
||||
# deny connections to network services that either use
|
||||
# the tcp_wrappers library or that have been
|
||||
# started through a tcp_wrappers-enabled xinetd.
|
||||
#
|
||||
# The rules in this file can also be set up in
|
||||
# /etc/hosts.allow with a 'deny' option instead.
|
||||
#
|
||||
# See 'man 5 hosts_options' and 'man 5 hosts_access'
|
||||
# for information on rule syntax.
|
||||
# See 'man tcpd' for information on tcp_wrappers
|
||||
#
|
||||
sshd,vsftpd : ALL
|
||||
ALL : ALL
|
||||
|
||||
```
|
||||
|
||||
TCP Wrappers – hosts.allow File
|
||||
```
|
||||
#
|
||||
# hosts.allow This file contains access rules which are used to
|
||||
# allow or deny connections to network services that
|
||||
# either use the tcp_wrappers library or that have been
|
||||
# started through a tcp_wrappers-enabled xinetd.
|
||||
#
|
||||
# See 'man 5 hosts_options' and 'man 5 hosts_access'
|
||||
# for information on rule syntax.
|
||||
# See 'man tcpd' for information on tcp_wrappers
|
||||
#
|
||||
sshd,vsftpd : 192.168.0.102,LOCAL
|
||||
|
||||
```
|
||||
|
||||
These changes take place immediately without the need for a restart.
|
||||
|
||||
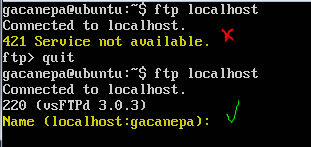
In the following image you can see the effect of removing the word `LOCAL` from the last line: the FTP server will become unavailable for localhost. After we add the wildcard back, the service becomes available again.
|
||||
|
||||
[][1]
|
||||
>Verify FTP Access
|
||||
|
||||
To allow all services to hosts where the name contains `example.com`, add this line in `hosts.allow`:
|
||||
|
||||
```
|
||||
ALL : .example.com
|
||||
|
||||
```
|
||||
|
||||
and to deny access to vsftpd to machines on 10.0.1.0/24, add this line in `hosts.deny`:
|
||||
|
||||
```
|
||||
vsftpd : 10.0.1.
|
||||
|
||||
```
|
||||
|
||||
On the last two examples, notice the dot at the beginning and the end of the client list. It is used to indicate “ALL hosts and / or clients where the name or the IP contains that string”.
|
||||
|
||||
Was this article helpful to you? Do you have any questions or comments? Feel free to drop us a note using the comment form below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/secure-linux-tcp-wrappers-hosts-allow-deny-restrict-access/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
[1]:http://www.tecmint.com/wp-content/uploads/2016/10/Verify-FTP-Access.png
|
||||
[2]:http://www.tecmint.com/block-ssh-and-ftp-access-to-specific-ip-and-network-range/
|
||||
[3]:http://www.tecmint.com/wp-content/uploads/2016/10/Find-Supported-Services-in-TCP-Wrapper.png
|
||||
[4]:http://www.tecmint.com/linux-server-hardening-security-tips/
|
||||
[5]:http://www.tecmint.com/secure-files-using-acls-in-linux/
|
||||
[6]:http://www.tecmint.com/configure-firewalld-in-centos-7/
|
||||
[7]:http://www.tecmint.com/mandatory-access-control-with-selinux-or-apparmor-linux/
|
||||
@ -0,0 +1,151 @@
|
||||
在 Linux 下使用 TCP 封装器来加密网络服务
|
||||
===========
|
||||
|
||||
|
||||
在这篇文章中,我们将会讲述什么是 TCP 封装器以及如何在一台 Linux 服务器上配置他们来[限制网络服务的权限][7]。在开始之前,我们必须澄清 TCP 封装器并不能消除对于正确[配置防火墙][6]的需要。
|
||||
|
||||
就这一点而言,你可以把这个工具看作是一个[基于主机的访问控制列][5],而且并不能作为你的系统的[终极安全措施][4]。通过使用一个防火墙和 TCP 封装器,而不是只喜爱其中的一个,你将会确保你的服务不会被出现单点故障。
|
||||
|
||||
### 正确理解 hosts.allow 和 hosts.deny 文件
|
||||
|
||||
当一个网络请求到达你的主机的时候,TCP 封装器会使用 hosts.allow 和 hosts.deny (按照这样的顺序)来决定客户端是否应该被允许使用一个提供的服务。.
|
||||
|
||||
在默认情况下,这些文件内容是空的,或者被注释掉,或者根本不存在。所以,任何请求都会被允许通过 TCP 过滤器而且你的系统被置于依靠防火墙来提供所有的保护。因为这并不是我们想要的。由于在一开始我们就介绍过的原因,清确保下面两个文件都存在:
|
||||
|
||||
```
|
||||
# ls -l /etc/hosts.allow /etc/hosts.deny
|
||||
|
||||
```
|
||||
|
||||
两个文件的编写语法规则是一样的:
|
||||
|
||||
```
|
||||
<services> : <clients> [: <option1> : <option2> : ...]
|
||||
|
||||
```
|
||||
|
||||
在文件中,
|
||||
|
||||
1. 1.services 是一个逗号分割的当前规则应该被应用的服务的列表。
|
||||
2. clients 代表逗号分割的被规则影响的主机名或者 IP 地址。下面的通配符也可以接受:
|
||||
1. ALL 表示所有事物,应用于客户端和服务器。
|
||||
2. LOCAL 表示匹配在正式域名中没有分段的机器,例如 localhost。
|
||||
3. KNOWN 表示主机名,主机地址,或者用户是已知的。
|
||||
4. UNKNOWN 和 KNOWN 相反。
|
||||
5. PARANOID 如果进行反向 DNS 查找,那么连接就会被断开(首先根据 IP 去决定主机名,然后根据主机名去获得 IP 地址)每次都返回不同的地址。
|
||||
3. 最后,一个逗号分割的动作表示了当一个规则被触发的时候会发生什么事情。
|
||||
|
||||
你可能会记住 /etc/hosts.allow 文件中允许一个服务接入的规则要优先于 /etc/hosts.deny中的规则。另外还有,如果两个规则应用于同一个服务,只有第一个规则会被纳入考虑。
|
||||
|
||||
不幸的是,不是所有的网络服务都支持 TCP 过滤器,为了查看一个给定的服务是否支持他们,可以执行以下命令:
|
||||
|
||||
```
|
||||
# ldd /path/to/binary | grep libwrap
|
||||
|
||||
```
|
||||
|
||||
如果以上命令执行以后得到了以下结果,那么他就可以支持 TCP 过滤器,sshd 和 vsftpd 作为例子,输出如下所示。
|
||||
|
||||
[][3]
|
||||
|
||||
查找 TCP 过滤器支持的服务。
|
||||
|
||||
### 如何使用 TCP 过滤器去限制服务的权限
|
||||
|
||||
当你编辑 /etc/hosts.allow 和 /etc/hosts.deny 的时候,确保你在最后一个非空行后面通过回车键来添加一个新的行。
|
||||
|
||||
为了使得 [SSH 和 FTP][2] 服务只允许 localhost 和 192.168.0.102 并且拒绝所有其他用户,在 /etc/hosts.deny 添加如下内容:
|
||||
|
||||
```
|
||||
sshd,vsftpd : ALL
|
||||
ALL : ALL
|
||||
|
||||
```
|
||||
|
||||
而且在 /etc/hosts.allow 文件中添加如下内容:
|
||||
|
||||
```
|
||||
sshd,vsftpd : 192.168.0.102,LOCAL
|
||||
|
||||
```
|
||||
|
||||
TCP Wrappers -hosts.deny 文件
|
||||
```
|
||||
#
|
||||
# hosts.deny This file contains access rules which are used to
|
||||
# deny connections to network services that either use
|
||||
# the tcp_wrappers library or that have been
|
||||
# started through a tcp_wrappers-enabled xinetd.
|
||||
#
|
||||
# The rules in this file can also be set up in
|
||||
# /etc/hosts.allow with a 'deny' option instead.
|
||||
#
|
||||
# See 'man 5 hosts_options' and 'man 5 hosts_access'
|
||||
# for information on rule syntax.
|
||||
# See 'man tcpd' for information on tcp_wrappers
|
||||
#
|
||||
sshd,vsftpd : ALL
|
||||
ALL : ALL
|
||||
|
||||
```
|
||||
|
||||
TCP wrappers -hosts.allow 文件
|
||||
```
|
||||
#
|
||||
# hosts.allow This file contains access rules which are used to
|
||||
# allow or deny connections to network services that
|
||||
# either use the tcp_wrappers library or that have been
|
||||
# started through a tcp_wrappers-enabled xinetd.
|
||||
#
|
||||
# See 'man 5 hosts_options' and 'man 5 hosts_access'
|
||||
# for information on rule syntax.
|
||||
# See 'man tcpd' for information on tcp_wrappers
|
||||
#
|
||||
sshd,vsftpd : 192.168.0.102,LOCAL
|
||||
|
||||
```
|
||||
|
||||
这些更改会立刻生效并且不需要重新启动。
|
||||
|
||||
在下图中你会看到,在最后一行中删掉 LOCAL 后,FTP 服务器会对于 localhost 不可用。在我们添加了通配符以后,服务又变得可用了。
|
||||
|
||||
[][1]
|
||||
>确认 FTP 权限
|
||||
|
||||
为了允许所有服务对于主机名中含有 example.com 都可用,在 hosts.allow 中添加如下一行:
|
||||
|
||||
```
|
||||
ALL : .example.com
|
||||
|
||||
```
|
||||
|
||||
而且为了禁止 10.0.1.0/24 的机器访问 vsftpd 服务,在 hosts.deny 文件中添加如下一行:
|
||||
```
|
||||
vsftpd : 10.0.1.
|
||||
|
||||
```
|
||||
|
||||
在最后的两个例子中,注意到客户端列表每行开头和结尾的逗号。这是用来表示 “所有主机或者客户端的名字或者 IP 中含有那个字符串的主机”
|
||||
|
||||
这篇文章对你有用吗?你有什么问题或者评论吗?请你尽情在下面留言交流。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/secure-linux-tcp-wrappers-hosts-allow-deny-restrict-access/
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
|
||||
译者:[LinuxBars](https://LinuxBar.org
|
||||
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/gacanepa/
|
||||
[1]:http://www.tecmint.com/wp-content/uploads/2016/10/Verify-FTP-Access.png
|
||||
[2]:http://www.tecmint.com/block-ssh-and-ftp-access-to-specific-ip-and-network-range/
|
||||
[3]:http://www.tecmint.com/wp-content/uploads/2016/10/Find-Supported-Services-in-TCP-Wrapper.png
|
||||
[4]:http://www.tecmint.com/linux-server-hardening-security-tips/
|
||||
[5]:http://www.tecmint.com/secure-files-using-acls-in-linux/
|
||||
[6]:http://www.tecmint.com/configure-firewalld-in-centos-7/
|
||||
[7]:http://www.tecmint.com/mandatory-access-control-with-selinux-or-apparmor-linux/
|
||||
Loading…
Reference in New Issue
Block a user