mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-25 00:50:15 +08:00
Merge remote-tracking branch 'LCTT/master'
This commit is contained in:
commit
25d6fcf84b
@ -1,27 +1,25 @@
|
||||
Hegemon - 使用 Rust 编写的模块化系统监视程序
|
||||
Hegemon:使用 Rust 编写的模块化系统监视程序
|
||||
======
|
||||
|
||||
|
||||
|
||||
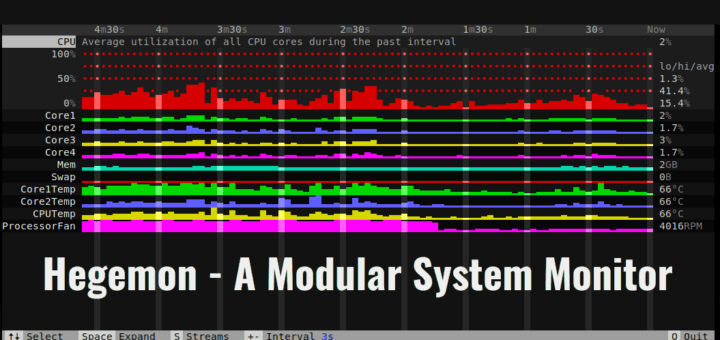
在类 Unix 系统中监视运行进程时,最常用的程序是 **top** 和 top 的增强版 **htop**。我个人最喜欢的是 htop。但是,开发人员不时会发布这些程序的替代品。top 和 htop 工具的一个替代品是 **Hegemon**。它是使用 **Rust** 语言编写的模块化系统监视程序。
|
||||
在类 Unix 系统中监视运行进程时,最常用的程序是 `top` 和它的增强版 `htop`。我个人最喜欢的是 `htop`。但是,开发人员不时会发布这些程序的替代品。`top` 和 `htop` 工具的一个替代品是 `Hegemon`。它是使用 Rust 语言编写的模块化系统监视程序。
|
||||
|
||||
关于 Hegemon 的功能,我们可以列出以下这些:
|
||||
|
||||
* Hegemon 会监控 CPU、内存和交换页的使用情况。
|
||||
* 它监控系统的温度和风扇速度。
|
||||
* 更新间隔时间可以调整。默认值为 3 秒。
|
||||
* 我们可以通过扩展数据流来展示更详细的图表和其他信息。
|
||||
* 单元测试
|
||||
* 干净的界面
|
||||
* 免费且开源。
|
||||
|
||||
|
||||
* Hegemon 会监控 CPU、内存和交换页的使用情况。
|
||||
* 它监控系统的温度和风扇速度。
|
||||
* 更新间隔时间可以调整。默认值为 3 秒。
|
||||
* 我们可以通过扩展数据流来展示更详细的图表和其他信息。
|
||||
* 单元测试。
|
||||
* 干净的界面。
|
||||
* 自由开源。
|
||||
|
||||
### 安装 Hegemon
|
||||
|
||||
确保已安装 **Rust 1.26** 或更高版本。要在 Linux 发行版中安装 Rust,请参阅以下指南:
|
||||
确保已安装 Rust 1.26 或更高版本。要在 Linux 发行版中安装 Rust,请参阅以下指南:
|
||||
|
||||
[Install Rust Programming Language In Linux][2]
|
||||
- [在 Linux 中安装 Rust 编程语言][2]
|
||||
|
||||
另外要安装 [libsensors][1] 库。它在大多数 Linux 发行版的默认仓库中都有。例如,你可以使用以下命令将其安装在基于 RPM 的系统(如 Fedora)中:
|
||||
|
||||
@ -51,10 +49,10 @@ $ hegemon
|
||||
|
||||
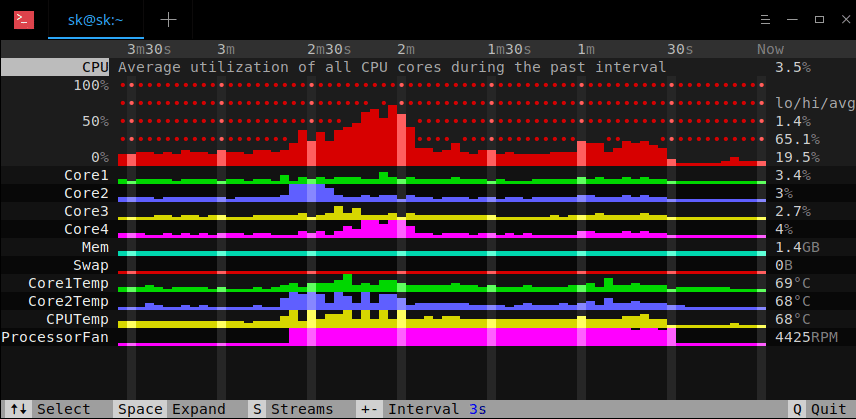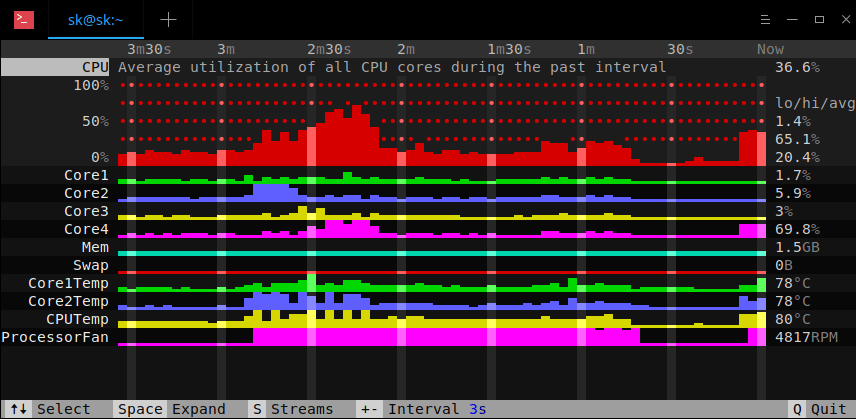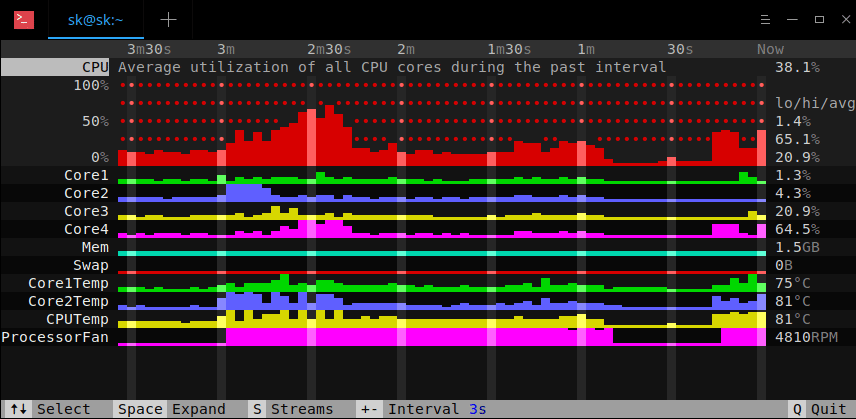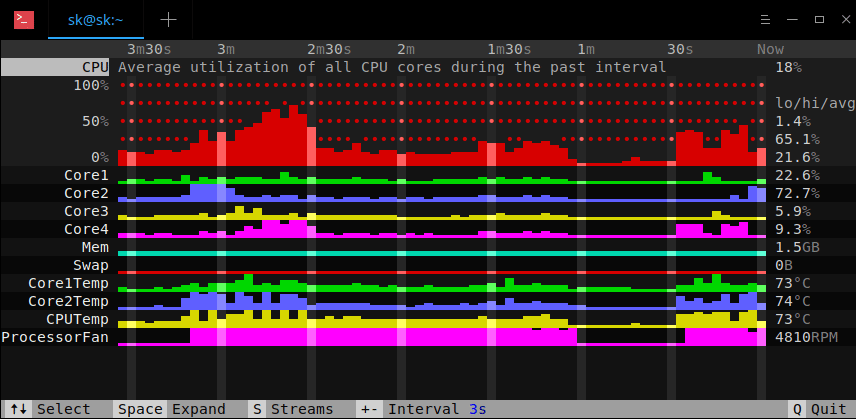
|
||||
|
||||
要退出,请按 **Q**。
|
||||
要退出,请按 `Q`。
|
||||
|
||||
|
||||
请注意,hegemon 仍处于早期开发阶段,并不能完全取代 **top** 命令。它可能存在 bug 和功能缺失。如果你遇到任何 bug,请在项目的 github 页面中报告它们。开发人员计划在即将推出的版本中引入更多功能。所以,请关注这个项目。
|
||||
请注意,hegemon 仍处于早期开发阶段,并不能完全取代 `top` 命令。它可能存在 bug 和功能缺失。如果你遇到任何 bug,请在项目的 GitHub 页面中报告它们。开发人员计划在即将推出的版本中引入更多功能。所以,请关注这个项目。
|
||||
|
||||
就是这些了。希望这篇文章有用。还有更多的好东西。敬请关注!
|
||||
|
||||
@ -69,7 +67,7 @@ via: https://www.ostechnix.com/hegemon-a-modular-system-monitor-application-writ
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,9 +1,9 @@
|
||||
cloc –– 计算不同编程语言源代码的行数
|
||||
cloc:计算不同编程语言源代码的行数
|
||||
======
|
||||
|
||||

|
||||
|
||||
作为一个开发人员,你可能需要不时地向你的领导或者同事分享你目前的工作与代码开发进展,抑或你的领导想对代码进行全方位的分析。这时,你就需要用到一些代码统计的工具,我知道其中一个是 [**Ohcount**][1]。今天,我遇到了另一个程序,**cloc**。你可以用 cloc 很容易地统计多种语言的源代码行数。它还可以计算空行数、代码行数、实际代码的行数,并通过整齐的表格进行结果输出。cloc 是免费的、开源的跨平台程序,使用 **Perl** 进行开发。
|
||||
作为一个开发人员,你可能需要不时地向你的领导或者同事分享你目前的工作与代码开发进展,抑或你的领导想对代码进行全方位的分析。这时,你就需要用到一些代码统计的工具,我知道其中一个是 [**Ohcount**][1]。今天,我遇到了另一个程序,**cloc**。你可以用 cloc 很容易地统计多种语言的源代码行数。它还可以计算空行数、代码行数、实际代码的行数,并通过整齐的表格进行结果输出。cloc 是自由开源的跨平台程序,使用 **Perl** 进行开发。
|
||||
|
||||
### 特点
|
||||
|
||||
@ -1,67 +0,0 @@
|
||||
LuuMing translating
|
||||
9 ways to improve collaboration between developers and designers
|
||||
======
|
||||
|
||||

|
||||
|
||||
This article was co-written with [Jason Porter][1].
|
||||
|
||||
Design is a crucial element in any software project. Sooner or later, the developers' reasons for writing all this code will be communicated to the designers, human beings who aren't as familiar with its inner workings as the development team.
|
||||
|
||||
Stereotypes exist on both side of the divide; engineers often expect designers to be flaky and irrational, while designers often expect engineers to be inflexible and demanding. The truth is considerably more nuanced and, at the end of the day, the fates of designers and developers are forever intertwined.
|
||||
|
||||
Here are nine things that can improve collaboration between the two.
|
||||
|
||||
### 1\. First, knock down the wall. Seriously.
|
||||
|
||||
There are loads of memes about the "wall of confusion" in just about every industry. No matter what else you do, the first step toward tearing down this wall is getting both sides to agree it needs to be gone. Once everyone agrees the existing processes aren't functioning optimally, you can pick and choose from the rest of these ideas to begin fixing the problems.
|
||||
|
||||
### 2\. Learn to empathize.
|
||||
|
||||
Before rolling up any sleeves to build better communication, take a break. This is a great junction point for team building. A time to recognize that we're all people, we all have strengths and weaknesses, and most importantly, we're all on the same team. Discussions around workflows and productivity can become feisty, so it's crucial to build a foundation of trust and cooperation before diving on in.
|
||||
|
||||
### 3\. Recognize differences.
|
||||
|
||||
Designers and developers attack the same problem from different angles. Given a similar problem, designers will seek the solution with the biggest impact while developers will seek the solution with the least amount of waste. These two viewpoints do not have to be mutually exclusive. There is plenty of room for negotiation and compromise, and somewhere in the middle is where the end user receives the best experience possible.
|
||||
|
||||
### 4\. Embrace similarities.
|
||||
|
||||
This is all about workflow. CI/CD, scrum, agile, etc., are all basically saying the same thing: Ideate, iterate, investigate, and repeat. Iteration and reiteration are common denominators for both kinds of work. So instead of running a design cycle followed by a development cycle, it makes much more sense to run them concurrently and in tandem. Syncing cycles allows teams to communicate, collaborate, and influence each other every step of the way.
|
||||
|
||||
### 5\. Manage expectations.
|
||||
|
||||
All conflict can be distilled down to one simple idea: incompatible expectations. Therefore, an easy way to prevent systemic breakdowns is to manage expectations by ensuring that teams are thinking before talking and talking before doing. Setting expectations often evolves organically through everyday conversation. Forcing them to happen by having meetings can be counterproductive.
|
||||
|
||||
### 6\. Meet early and meet often.
|
||||
|
||||
Meeting once at the beginning of work and once at the end simply isn't enough. This doesn't mean you need daily or even weekly meetings. Setting a cadence for meetings can also be counterproductive. Let them happen whenever they're necessary. Great things can happen with impromptu meetings—even at the watercooler! If your team is distributed or has even one remote employee, video conferencing, text chat, or phone calls are all excellent ways to meet. It's important that everyone on the team has multiple ways to communicate with each other.
|
||||
|
||||
### 7\. Build your own lexicon.
|
||||
|
||||
Designers and developers sometimes have different terms for similar ideas. One person's card is another person's tile is a third person's box. Ultimately, the fit and accuracy of a term aren't as important as everyone's agreement to use the same term consistently.
|
||||
|
||||
### 8\. Make everyone a communication steward.
|
||||
|
||||
Everyone in the group is responsible for maintaining effective communication, regardless of how or when it happens. Each person should strive to say what they mean and mean what they say.
|
||||
|
||||
### 9\. Give a darn.
|
||||
|
||||
It only takes one member of a team to sabotage progress. Go all in. If every individual doesn't care about the product or the goal, there will be problems with motivation to make changes or continue the process.
|
||||
|
||||
This article is based on [Designers and developers: Finding common ground for effective collaboration][2], a talk the authors will be giving at [Red Hat Summit 2018][3], which will be held May 8-10 in San Francisco. [Register by May 7][3] to save US$ 500 off of registration. Use discount code **OPEN18** on the payment page to apply the discount.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/5/9-ways-improve-collaboration-developers-designers
|
||||
|
||||
作者:[Jason Brock][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/jkbrock
|
||||
[1]:https://opensource.com/users/lightguardjp
|
||||
[2]:https://agenda.summit.redhat.com/SessionDetail.aspx?id=154267
|
||||
[3]:https://www.redhat.com/en/summit/2018
|
||||
@ -1,47 +0,0 @@
|
||||
translating by belitex
|
||||
How Writing Can Expand Your Skills and Grow Your Career
|
||||
======
|
||||
|
||||

|
||||
|
||||
At the recent [Open Source Summit in Vancouver][1], I participated in a panel discussion called [How Writing can Change Your Career for the Better (Even if You don't Identify as a Writer][2]. The panel was moderated by Rikki Endsley, Community Manager and Editor for Opensource.com, and it included VM (Vicky) Brasseur, Open Source Strategy Consultant; Alex Williams, Founder, Editor in Chief, The New Stack; and Dawn Foster, Consultant, The Scale Factory.
|
||||
|
||||
The talk was [inspired by this article][3], in which Rikki examined some ways that writing can "spark joy" and improve your career in unexpected ways. Full disclosure: I have known Rikki for a long time. We worked at the same company for many years, raised our children together, and remain close friends.
|
||||
|
||||
### Write and learn
|
||||
|
||||
As Rikki noted in the talk description, “even if you don't consider yourself to be ‘a writer,’ you should consider writing about your open source contributions, project, or community.” Writing can be a great way to share knowledge and engage others in your work, but it has personal benefits as well. It can help you meet new people, learn new skills, and improve your communication style.
|
||||
|
||||
I find that writing often clarifies for me what I don’t know about a particular topic. The process highlights gaps in my understanding and motivates me to fill in those gaps through further research, reading, and asking questions.
|
||||
|
||||
“Writing about what you don't know can be much harder and more time consuming, but also much more fulfilling and help your career. I've found that writing about what I don't know helps me learn, because I have to research it and understand it well enough to explain it,” Rikki said.
|
||||
|
||||
Writing about what you’ve just learned can be valuable to other learners as well. In her blog, [Julia Evans][4] often writes about learning new technical skills. She has a friendly, approachable style along with the ability to break down topics into bite-sized pieces. In her posts, Evans takes readers through her learning process, identifying what was and was not helpful to her along the way, essentially removing obstacles for her readers and clearing a path for those new to the topic.
|
||||
|
||||
### Communicate more clearly
|
||||
|
||||
Writing can help you practice thinking and speaking more precisely, especially if you’re writing (or speaking) for an international audience. [In this article,][5] for example, Isabel Drost-Fromm provides tips for removing ambiguity for non-native English speakers. Writing can also help you organize your thoughts before a presentation, whether you’re speaking at a conference or to your team.
|
||||
|
||||
“The process of writing the articles helps me organize my talks and slides, and it was a great way to provide ‘notes’ for conference attendees, while sharing the topic with a larger international audience that wasn't at the event in person,” Rikki stated.
|
||||
|
||||
If you’re interested in writing, I encourage you to do it. I highly recommend the articles mentioned here as a way to get started thinking about the story you have to tell. Unfortunately, our discussion at Open Source Summit was not recorded, but I hope we can do another talk in the future and share more ideas.
|
||||
|
||||
Check out the schedule of talks for Open Source Summit Europe and sign up to receive updates:
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/2018/9/how-writing-can-help-you-learn-new-skills-and-grow-your-career
|
||||
|
||||
作者:[Amber Ankerholz][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/aankerholz
|
||||
[1]: https://events.linuxfoundation.org/events/open-source-summit-north-america-2018/
|
||||
[2]: https://ossna18.sched.com/event/FAOF/panel-discussion-how-writing-can-change-your-career-for-the-better-even-if-you-dont-identify-as-a-writer-moderated-by-rikki-endsley-opensourcecom-red-hat?iframe=no#
|
||||
[3]: https://opensource.com/article/18/2/career-changing-magic-writing
|
||||
[4]: https://jvns.ca/
|
||||
[5]: https://www.linux.com/blog/event/open-source-summit-eu/2017/12/technical-writing-international-audience
|
||||
@ -1,169 +0,0 @@
|
||||
thecyanbird translating
|
||||
|
||||
Linux Has a Code of Conduct and Not Everyone is Happy With it
|
||||
======
|
||||
**Linux kernel has a new code of conduct (CoC). Linus Torvalds took a break from Linux kernel development just 30 minutes after signing this code of conduct. And since **the writer of this code of conduct has had a controversial past,** it has now become a point of heated discussion. With all the politics involved, not many people are happy with this new CoC.**
|
||||
|
||||
If you do not know already, [Linux creator Linus Torvalds has apologized for his past behavior and has taken a temporary break from Linux kernel development to improve his behavior][1].
|
||||
|
||||
### The new code of conduct for Linux kernel development
|
||||
|
||||
Linux kernel developers have a code of conduct. It’s not like they didn’t have a code before, but the previous [code of conflict][2] is now replaced by this new code of conduct to “help make the kernel community a welcoming environment to participate in.”
|
||||
|
||||
> “In the interest of fostering an open and welcoming environment, we as contributors and maintainers pledge to making participation in our project and our community a harassment-free experience for everyone, regardless of age, body size, disability, ethnicity, sex characteristics, gender identity and expression, level of experience, education, socio-economic status, nationality, personal appearance, race, religion, or sexual identity and orientation.”
|
||||
|
||||
You can read the entire code of conduct on this commit page.
|
||||
|
||||
[Linux Code of Conduct][33]
|
||||
|
||||
|
||||
### Was Linus Torvalds forced to apologize and take a break?
|
||||
|
||||
![Linus Torvalds Apologizes][3]
|
||||
|
||||
The code of conduct was signed off by Linus Torvalds and Greg Kroah-Hartman (kind of second-in-command after Torvalds). Dan Williams of Intel and Chris Mason from Facebook were some of the other signees.
|
||||
|
||||
If I have read through the timeline correctly, half an hour after signing this code of conduct, Torvalds sent a [mail apologizing for his past behavior][4]. He also announced taking a temporary break to improve upon his behavior.
|
||||
|
||||
But at this point some people started reading between the lines, with a special attention to this line from his mail:
|
||||
|
||||
> **This week people in our community confronted me about my lifetime of not understanding emotions**. My flippant attacks in emails have been both unprofessional and uncalled for. Especially at times when I made it personal. In my quest for a better patch, this made sense to me. I know now this was not OK and I am truly sorry.
|
||||
|
||||
This particular line could be read as if he was coerced into apologizing and taking a break because of the new code of conduct. Though it could also be a precautionary measure to prevent Torvalds from violating the newly created code of conduct.
|
||||
|
||||
### The controversy around Contributor Convent creator Coraline Ada Ehmke
|
||||
|
||||
The Linux code of conduct is based on the [Contributor Covenant, version 1.4][5]. Contributor Convent has been adopted by hundreds of open source projects. Eclipse, Angular, Ruby, Kubernetes are some of the [many adopters of Contributor Convent][6].
|
||||
|
||||
Contributor Covenant has been created by [Coraline Ada Ehmke][7], a software developer, an open-source advocate, and an [LGBT][8] activist. She has been instrumental in promoting diversity in the open source world.
|
||||
|
||||
Coraline has also been vocal about her stance against [meritocracy][9]. The Latin word meritocracy originally refers to a “system under which advancement within the system turns on “merits”, like intelligence, credentials, and education.” But activists like [Coraline believe][10] that meritocracy is a negative system where the worth of an individual is measured not by their humanity, but solely by their intellectual output.
|
||||
|
||||
[![croraline meritocracy][11]][12]
|
||||
Image credit: Twitter user @nickmon1112
|
||||
|
||||
Remember that [Linus Torvalds has repeatedly said that he cares about the code, not the person who writes it][13]. Clearly, this goes against Coraline’s view on meritocracy.
|
||||
|
||||
Coraline has had a troubled incident in the past with a contributor of [Opal project][14]. There was a [discussion taking place on Twitter][15] where Elia, a core contributor to Opal project from Italy, said “(trans people) not accepting reality is the problem here”.
|
||||
|
||||
Coraline was neither in the discussion nor was she a contributor to the Opal project. But as an LGBT activist, she took it to herself and [demanded that Elia be removed from the Opal Project][16] for his ‘views against trans people’. A lengthy and heated discussion took place on Opal’s GitHub repository. Coraline and her supporters, who never contributed to Opal, tried to coerce the moderators into removing Elia, a core contributor of the project.
|
||||
|
||||
While Elia wasn’t removed from the project, Opal project maintainers agreed to put up a code of conduct in place. And this code of conduct was nothing else but Coraline’s famed Contributor Covenant that she had pitched to the maintainers herself.
|
||||
|
||||
But the story didn’t end here. The Contributor Covenant was then modified and a [new clause added in order to get to Elia][17]. The new clause widened the scope of conduct in public spaces. This malicious change was [spotted by the maintainers][18] and they edited the clause. Opal eventually got rid of the Contributor Covenant and put in place its own guideline.
|
||||
|
||||
This is a classic example of how a few offended people, who never contributed a single line of code to the project, tried to oust its core contributor.
|
||||
|
||||
### People’s reaction on Linux Code of Conduct and Torvalds’ apology
|
||||
|
||||
As soon as Linux code of conduct and Torvalds’ apology went public, Social Media and forums were rife with rumors and [speculations][19]. While many people appreciated this new development, there were some who saw a conspiracy by [SJW infiltrating Linux][20].
|
||||
|
||||
A sarcastic tweet by Caroline only fueled the fire.
|
||||
|
||||
> I can’t wait for the mass exodus from Linux now that it’s been infiltrated by SJWs. Hahahah [pic.twitter.com/eFeY6r4ENv][21]
|
||||
>
|
||||
> — Coraline Ada Ehmke (@CoralineAda) [September 16, 2018][22]
|
||||
|
||||
In the wake of the Linux CoC controversy, Coraline openly said that the Contributor Convent code of conduct is a political document. This did not go down well with the people who want the political stuff out of the open source projects.
|
||||
|
||||
> Some people are saying that the Contributor Covenant is a political document, and they’re right.
|
||||
>
|
||||
> — Coraline Ada Ehmke (@CoralineAda) [September 16, 2018][23]
|
||||
|
||||
Nick Monroe, a freelance journalist, dig up the past of Coraline in order to validate his claim that there is more to Linux CoC than meets the eye. You can go by the entire thread if you want.
|
||||
|
||||
> Alright. You've seen this a million times before. It's a code of conduct blah blah blah
|
||||
>
|
||||
> that has social justice baked right into it. blah blah blah.<https://t.co/KuQqeriYeJ>
|
||||
>
|
||||
> But something is different about this. [pic.twitter.com/8NUL2K1gu2][24]
|
||||
>
|
||||
> — Nick Monroe (@nickmon1112) [September 17, 2018][25]
|
||||
|
||||
Nick wasn’t the only one to disapprove of the new Linux CoC. The [SJW][26] involvement led to more skepticism.
|
||||
|
||||
> I guess the big news in Linux today is that the Linux kernel is now governed by a Code of Conduct and a “post meritocracy” world view.
|
||||
>
|
||||
> In principle these CoCs look great. In practice they are abused tools to hunt people SJWs don’t like. And they don’t like a lot of people.
|
||||
>
|
||||
> — Mark Kern (@Grummz) [September 17, 2018][27]
|
||||
|
||||
While there were many who appreciated Torvalds’ apology, there were a few who blamed Torvalds’ attitude:
|
||||
|
||||
> Am I the only one who thinks Linus Torvalds attitude for decades was a prime contributors to how many of the condescending, rudes, jerks in Linux and open source "communities" behaved? I've never once felt welcomed into the Linux community as a new user.
|
||||
>
|
||||
> — Jonathan Frappier (@jfrappier) [September 17, 2018][28]
|
||||
|
||||
And some were simply not amused with his apology:
|
||||
|
||||
> Oh look, an abusive OSS maintainer finally admitted, after *decades* of abusive and toxic behavior, that his behavior *might* be an issue.
|
||||
>
|
||||
> And a bunch of people I follow are tripping all over themselves to give him cookies for that. 🙄🙄🙄
|
||||
>
|
||||
> — Kelly Ellis (@justkelly_ok) [September 17, 2018][29]
|
||||
|
||||
The entire Torvalds apology episode has raised a genuine concern ;)
|
||||
|
||||
> Do we have to put "I don't/do forgive Linus Torvalds" in our bio now?
|
||||
>
|
||||
> — Verónica. (@maria_fibonacci) [September 17, 2018][30]
|
||||
|
||||
Jokes apart, the genuine concern was raised by Sharp, who had [quit Linux Kernel development][31] in 2015 due to the ‘toxic community’.
|
||||
|
||||
> The real test here is whether the community that built Linus up and protected his right to be verbally abusive will change. Linus not only needs to change himself, but the Linux kernel community needs to change as well. <https://t.co/EG5KO43416>
|
||||
>
|
||||
> — Sage Sharp (@_sagesharp_) [September 17, 2018][32]
|
||||
|
||||
### What do you think of Linux Code of Conduct?
|
||||
|
||||
If you ask my opinion, I do think that a Code of Conduct is the need of the time. It guides people in behaving in a respectable way and helps create a positive environment for all kind of people irrespective of their race, ethnicity, religion, nationality and political views (both left and right).
|
||||
|
||||
What are your views on the entire episode? Do you think the CoC will help Linux kernel development? Or will it deteriorate with the involvement of anti-meritocracy SJWs?
|
||||
|
||||
We don’t have a code of conduct at It’s FOSS but let’s keep the discussion civil :)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/linux-code-of-conduct/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[1]: https://itsfoss.com/torvalds-takes-a-break-from-linux/
|
||||
[2]: https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/tree/Documentation/CodeOfConflict?id=ddbd2b7ad99a418c60397901a0f3c997d030c65e
|
||||
[3]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/linus-torvalds-apologizes.jpeg
|
||||
[4]: https://lkml.org/lkml/2018/9/16/167
|
||||
[5]: https://www.contributor-covenant.org/version/1/4/code-of-conduct.html
|
||||
[6]: https://www.contributor-covenant.org/adopters
|
||||
[7]: https://en.wikipedia.org/wiki/Coraline_Ada_Ehmke
|
||||
[8]: https://en.wikipedia.org/wiki/LGBT
|
||||
[9]: https://en.wikipedia.org/wiki/Meritocracy
|
||||
[10]: https://modelviewculture.com/pieces/the-dehumanizing-myth-of-the-meritocracy
|
||||
[11]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/croraline-meritocracy.jpg
|
||||
[12]: https://pbs.twimg.com/media/DnTTfi7XoAAdk08.jpg
|
||||
[13]: https://arstechnica.com/information-technology/2015/01/linus-torvalds-on-why-he-isnt-nice-i-dont-care-about-you/
|
||||
[14]: https://opalrb.com/
|
||||
[15]: https://twitter.com/krainboltgreene/status/611569515315507200
|
||||
[16]: https://github.com/opal/opal/issues/941
|
||||
[17]: https://github.com/opal/opal/pull/948/commits/817321e27eccfffb3841f663815c17eecb8ef061#diff-a1ee87dafebc22cbd96979f1b2b7e837R11
|
||||
[18]: https://github.com/opal/opal/pull/948#issuecomment-113486020
|
||||
[19]: https://www.reddit.com/r/linux/comments/9go8cp/linus_torvalds_daughter_has_signed_the/
|
||||
[20]: https://snew.github.io/r/linux/comments/9ghrrj/linuxs_new_coc_is_a_piece_of_shit/
|
||||
[21]: https://t.co/eFeY6r4ENv
|
||||
[22]: https://twitter.com/CoralineAda/status/1041441155874009093?ref_src=twsrc%5Etfw
|
||||
[23]: https://twitter.com/CoralineAda/status/1041465346656530432?ref_src=twsrc%5Etfw
|
||||
[24]: https://t.co/8NUL2K1gu2
|
||||
[25]: https://twitter.com/nickmon1112/status/1041668315947708416?ref_src=twsrc%5Etfw
|
||||
[26]: https://www.urbandictionary.com/define.php?term=SJW
|
||||
[27]: https://twitter.com/Grummz/status/1041524170331287552?ref_src=twsrc%5Etfw
|
||||
[28]: https://twitter.com/jfrappier/status/1041486055038492674?ref_src=twsrc%5Etfw
|
||||
[29]: https://twitter.com/justkelly_ok/status/1041522269002985473?ref_src=twsrc%5Etfw
|
||||
[30]: https://twitter.com/maria_fibonacci/status/1041538148121997313?ref_src=twsrc%5Etfw
|
||||
[31]: https://www.networkworld.com/article/2988850/opensource-subnet/linux-kernel-dev-sarah-sharp-quits-citing-brutal-communications-style.html
|
||||
[32]: https://twitter.com/_sagesharp_/status/1041480963287539712?ref_src=twsrc%5Etfw
|
||||
[33]: https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=8a104f8b5867c682d994ffa7a74093c54469c11f
|
||||
@ -0,0 +1,147 @@
|
||||
How to level up your organization's security expertise
|
||||
======
|
||||
These best practices will make your employees more savvy and your organization more secure.
|
||||

|
||||
|
||||
IT security is critical to every company these days. In the words of former FBI director Robert Mueller: “There are only two types of companies: Those that have been hacked, and those that will be.”
|
||||
|
||||
At the same time, IT security is constantly evolving. We all know we need to keep up with the latest trends in cybersecurity and security tooling, but how can we do that without sacrificing our ability to keep moving forward on our business priorities?
|
||||
|
||||
No single person in your organization can handle all of the security work alone; your entire development and operations team will need to develop an awareness of security tooling and best practices, just like they all need to build skills in open source and in agile software delivery. There are a number of best practices that can help you level up the overall security expertise in your company through basic and intermediate education, subject matter experts, and knowledge-sharing.
|
||||
|
||||
### Basic education: Annual cybersecurity education and security contact information
|
||||
|
||||
At IBM, we all complete an online cybersecurity training class each year. I recommend this as a best practice for other companies as well. The online training is taught at a basic level, and it doesn’t assume that anyone has a technical background. Topics include social engineering, phishing and spearfishing attacks, problematic websites, viruses and worms, and so on. We learn how to avoid situations that may put ourselves or our systems at risk, how to recognize signs of an attempted security breach, and how to report a problem if we notice something that seems suspicious. This online education serves the purpose of raising the overall security awareness and readiness of the organization at a low per-person cost. A nice side effect of this education is that this basic knowledge can be applied to our personal lives, and we can share what we learned with our family and friends as well.
|
||||
|
||||
In addition to the general cybersecurity education, all employees should have annual training on data security and privacy regulations and how to comply with those.
|
||||
|
||||
Finally, we make it easy to find the Corporate Security Incident Response team by sharing the link to its website in prominent places, including Slack, and setting up suggested matches to ensure that a search of our internal website will send people to the right place:
|
||||
|
||||
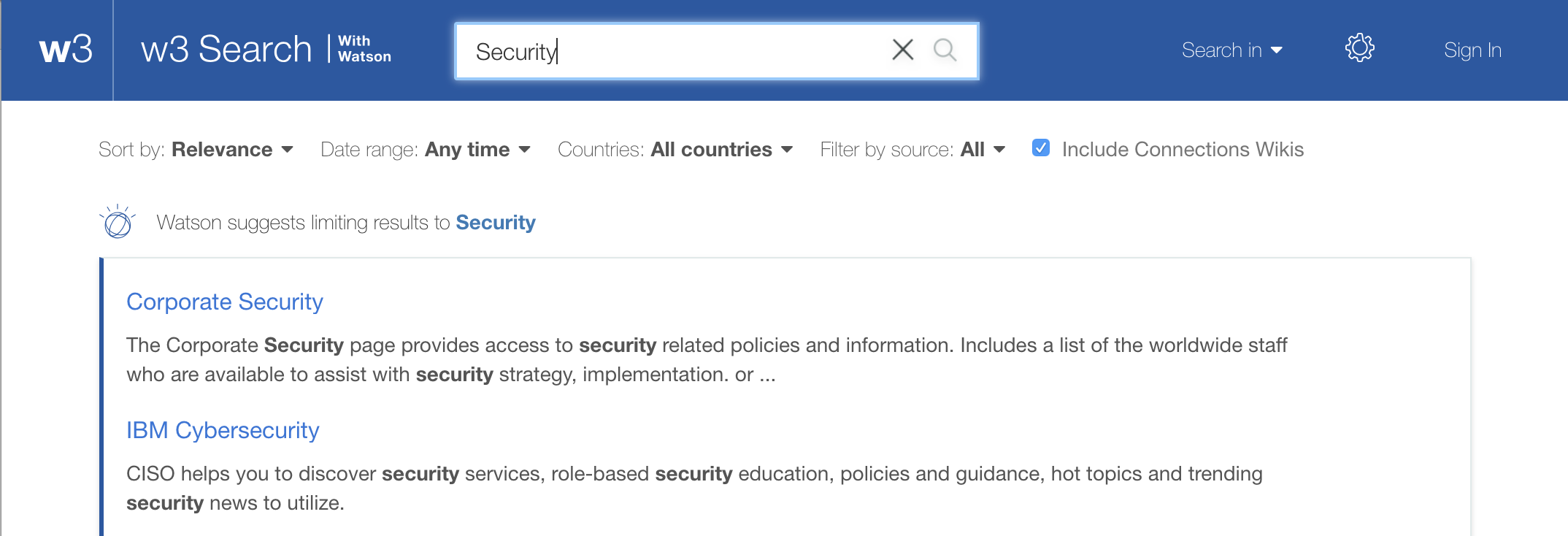
|
||||
|
||||
### Intermediate education: Learn from your tools
|
||||
|
||||
Another great source of security expertise is through pre-built security tools. For example, we have set up a set of automated security tests that run against our web services using IBM AppScan, and the reports it generates include background knowledge about the vulnerabilities it finds, the severity of the threat, how to determine if your application is susceptible to the vulnerability, and how to fix the problem, with code examples.
|
||||
|
||||
Similarly, the free [npm audit command-line tool from npm, Inc.][1] will scan your open source Node.js modules and report any known vulnerabilities it finds. This tool also generates educational audit reports that include the severity of the threat, the vulnerable package, and versions with the vulnerability, an alternative package or versions that do not have the vulnerability, dependencies, and a link to more detailed information about the vulnerability. Here’s an example of a report from npm audit:
|
||||
|
||||
| High | Regular Expression Denial of Service |
|
||||
| --------------| ----------------------------------------- |
|
||||
| Package | minimath |
|
||||
| --------------| ----------------------------------------- |
|
||||
| Dependency of | gulp [dev] |
|
||||
| --------------| ----------------------------------------- |
|
||||
| Path | gulp > vinyl-fs > glob-stream > minimatch |
|
||||
| --------------| ----------------------------------------- |
|
||||
| More info | https://nodesecurity.io/advisories/118 |
|
||||
|
||||
Any good network-level security tool will also give you information on the types of attacks the tool is blocking and how it recognizes likely attacks. This information is available in the marketing materials online as well as the tool’s console and reports if you have access to those.
|
||||
|
||||
Each of your development teams or squads should have at least one subject matter expert who takes the time to read and fully understand the vulnerability reports that are relevant to you. This is often the technical lead, but it could be anyone who is interested in learning more about security. Your local subject matter expert will be able to recognize similar security holes in the future earlier in the development and deployment process.
|
||||
|
||||
Using the npm audit example above, a developer who reads and understands security advisory #118 from this report will be more likely to notice changes that may allow for a Regular Expression Denial of Service when reviewing code in the future. The team’s subject matter expert should also develop the skills needed to determine which of the vulnerability reports don’t actually apply to his or her specific project.
|
||||
|
||||
### Intermediate education: Conferences
|
||||
|
||||
Let’s not forget the value of attending security-related conferences, such as the [OWASP AppSec Conferences][2]. Conferences provide a great way for members of your team to focus on learning for a few days and bring back some of the newest ideas in the field. The “hallway track” of a conference, where we can learn from other practitioners, is also a valuable source of information. As much as most of us dislike being “sold to,” the sponsor hall at a conference is a good place to casually check out new security tools to see which ones you might be interested in evaluating later.
|
||||
|
||||
If your organization is big enough, ask your DevOps and security tool vendors to come to you! If you’ve already procured some great tools, but adoption isn’t going as quickly as you would like, many vendors would be happy to provide your teams with some additional practical training. It’s in their best interests to increase the adoption of their tools (making you more likely to continue paying for their services and to increase your license count), just like it’s in your best interests to maximize the value you get out of the tools you’re paying for. We recently hosted a [Toolbox@IBM][3] \+ DevSecOps summit at our largest sites (those with a couple thousand IT professionals). More than a dozen vendors sponsored each event, came onsite, set up booths, and gave conference talks, just like they would at a technical conference. We also had several of our own presenters speaking about DevOps and security best practices that were working well for them, and we had booths set up by our Corporate Information Security Office, agile coaching, onsite tech support, and internal toolchain teams. We had several hundred attendees at each site. It was great for our technical community because we could focus on the tools that we had already procured, learn how other teams in our company were using them, and make connections to help each other in the future.
|
||||
|
||||
When you send someone to a conference, it’s important to set the expectation that they will come back and share what they’ve learned with the team. We usually do this via an informal brown-bag lunch-and-learn, where people are encouraged to discuss new ideas interactively.
|
||||
|
||||
### Subject-matter experts and knowledge-sharing: The secure engineering guild
|
||||
|
||||
In the IBM Digital Business Group, we’ve adopted the squad model as described by [Spotify][4] and tweaked it to make it work for us. One sometimes-forgotten aspect of the squad model is the guild. Guilds are centers of excellence, focused around one topic or skill set, with members from many squads. Guild members learn together, share best practices with each other and their broader teams, and work to advance the state of the art. If you would like to establish your own secure engineering guild, here are some tips that have worked for me in setting up guilds in the past:
|
||||
|
||||
**Step 1: Advertise and recruit**
|
||||
|
||||
Your co-workers are busy people, so for many of them, a secure engineering guild could feel like just one more thing they have to cram into the week that doesn’t involve writing code. It’s important from the outset that the guild has a value proposition that will benefit its members as well as the organization.
|
||||
|
||||
Zane Lackey from [Signal Sciences][5] gave me some excellent advice: It’s important to call out the truth. In the past, he said, security initiatives may have been more of a hindrance or even a blocker to getting work done. Your secure engineering guild needs to focus on ways to make your engineering team’s lives easier and more efficient instead. You need to find ways to automate more of the busywork related to security and to make your development teams more self-sufficient so you don’t have to rely on security “gates” or hurdles late in the development process.
|
||||
|
||||
Here are some things that may attract people to your guild:
|
||||
|
||||
* Learn about security vulnerabilities and what you can do to combat them
|
||||
* Become a subject matter expert
|
||||
* Participate in penetration testing
|
||||
* Evaluate and pilot new security tools
|
||||
* Add “Secure Engineering Guild” to your resume
|
||||
|
||||
|
||||
|
||||
Here are some additional guild recruiting tips:
|
||||
|
||||
* Reach out directly to your security experts and ask them to join: security architects, network security administrators, people from your corporate security department, and so on.
|
||||
|
||||
* Bring in an external speaker who can get people excited about secure engineering. Advertise it as “sponsored by the Secure Engineering Guild” and collect names and contact information for people who want to join your guild, both before and after the talk.
|
||||
|
||||
* Get executive support for the program. Perhaps one of your VPs will write a blog post extolling the virtues of secure engineering skills and asking people to join the guild (or perhaps you can draft the blog post for her or him to edit and publish). You can combine that blog post with advertising the external speaker if the timing allows.
|
||||
|
||||
* Ask your management team to nominate someone from each squad to join the guild. This hardline approach is important if you have an urgent need to drive rapid improvement in your security posture.
|
||||
|
||||
|
||||
|
||||
|
||||
**Step 2: Build a team**
|
||||
|
||||
Guild meetings should be structured for action. It’s important to keep an agenda so people know what you plan to cover in each meeting, but leave time at the end for members to bring up any topics they want to discuss. Also be sure to take note of action items, and assign an owner and a target date for each of them. Finally, keep meeting minutes and send a brief summary out after each meeting.
|
||||
|
||||
Your first few guild meetings are your best opportunity to set off on the right foot, with a bit of team-building. I like to run a little design thinking exercise where you ask team members to share their ideas for the guild’s mission statement, vote on their favorites, and use those to craft a simple and exciting mission statement. The mission statement should include three components: WHO will benefit, WHAT the guild will do, and the WOW factor. The exercise itself is valuable because you can learn why people have decided to volunteer to be a part of the guild in the first place, and what they hope will come of it.
|
||||
|
||||
Another thing I like to do from the outset is ask people what they’re hoping to achieve as a guild. The guild should learn together, have fun, and do real work. Once you have those ideas out on the table, start putting owners and target dates next to those goals.
|
||||
|
||||
* Would they like to run a book club? Get someone to suggest a book and set up book club meetings.
|
||||
|
||||
* Would they like to share useful articles and blogs? Get someone to set up a Slack channel and invite everyone to it, or set up a shared document where people can contribute their favorite resources.
|
||||
|
||||
* Would they like to pilot a new tool? Get someone to set up a free trial, try it out for their own team, and report back in a few weeks.
|
||||
|
||||
* Would they like to continue a series of talks? Get someone to create a list of topics and speakers and send out the invitations.
|
||||
|
||||
|
||||
|
||||
|
||||
If a few goals end up without owners or dates, that’s OK; just start a to-do list or backlog for people to refer to when they’ve completed their first task.
|
||||
|
||||
Finally, survey the team to find the best time and day of the week for ongoing meetings and set those up. I recommend starting with weekly 30-minute meetings and adjust as needed.
|
||||
|
||||
**Step 3: Keep the energy going, or reboot**
|
||||
|
||||
As the months go on, your guild could start to lose energy. Here are some ways to keep the excitement going or reboot a guild that’s losing energy.
|
||||
|
||||
* Don’t be an echo chamber. Invite people in from various parts of the organization to talk for a few minutes about what they’re doing with respect to security engineering, and where they have concerns or see gaps.
|
||||
|
||||
* Show measurable progress. If you’ve been assigning owners to action items and completing them all along, you’ve certainly made progress, but if you look at it only from week to week, the progress can feel small or insignificant. Once per quarter, take a step back and write a blog about all you’ve accomplished and send it out to your organization. Showing off what you’ve accomplished makes the team proud of what they’ve accomplished, and it’s another opportunity to recruit even more people for your guild.
|
||||
|
||||
* Don’t be afraid to take on a large project. The guild should not be an ivory tower; it should get things done. Your guild may, for example, decide to roll out a new security tool that you love across a large organization. With a little bit of project management and a lot of executive support, you can and should tackle cross-squad projects. The guild members can and should be responsible for getting stories from the large projects prioritized in their own squads’ backlogs and completed in a timely manner.
|
||||
|
||||
* Periodically brainstorm the next set of action items. As time goes by, the most critical or pressing needs of your organization will likely change. People will be more motivated to work on the things they consider most important and urgent.
|
||||
|
||||
* Reward the extra work. You might offer an executive-sponsored cash award for the most impactful secure engineering projects. You might also have the guild itself choose someone to send to a security conference now and then.
|
||||
|
||||
|
||||
|
||||
|
||||
### Go forth, and make your company more secure
|
||||
|
||||
A more secure company starts with a more educated team. Building upon that expertise, a secure engineering guild can drive real changes by developing and sharing best practices, finding the right owners for each action item, and driving them to closure. I hope you found a few tips here that will help you level up the security expertise in your organization. Please add your own helpful tips in the comments.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/10/how-level-security-expertise-your-organization
|
||||
|
||||
作者:[Ann Marie Fred][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/annmarie99
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.npmjs.com/about
|
||||
[2]: https://www.owasp.org/index.php/Category:OWASP_AppSec_Conference
|
||||
[3]: mailto:Toolbox@IBM
|
||||
[4]: https://medium.com/project-management-learnings/spotify-squad-framework-part-i-8f74bcfcd761
|
||||
[5]: https://www.signalsciences.com/
|
||||
@ -1,3 +1,5 @@
|
||||
translating by belitex
|
||||
|
||||
A sysadmin's guide to containers
|
||||
======
|
||||
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
translating by sd886393
|
||||
4 open source monitoring tools
|
||||
======
|
||||
|
||||
|
||||
102
sources/tech/20181004 4 Must-Have Tools for Monitoring Linux.md
Normal file
102
sources/tech/20181004 4 Must-Have Tools for Monitoring Linux.md
Normal file
@ -0,0 +1,102 @@
|
||||
4 Must-Have Tools for Monitoring Linux
|
||||
======
|
||||
|
||||

|
||||
|
||||
Linux. It’s powerful, flexible, stable, secure, user-friendly… the list goes on and on. There are so many reasons why people have adopted the open source operating system. One of those reasons which particularly stands out is its flexibility. Linux can be and do almost anything. In fact, it will (in most cases) go well above what most platforms can. Just ask any enterprise business why they use Linux and open source.
|
||||
|
||||
But once you’ve deployed those servers and desktops, you need to be able to keep track of them. What’s going on? How are they performing? Is something afoot? In other words, you need to be able to monitor your Linux machines. “How?” you ask. That’s a great question, and one with many answers. I want to introduce you to a few such tools—from command line, to GUI, to full-blown web interfaces (with plenty of bells and whistles). From this collection of tools, you can gather just about any kind of information you need. I will stick only with tools that are open source, which will exempt some high-quality, proprietary solutions. But it’s always best to start with open source, and, chances are, you’ll find everything you need to monitor your desktops and servers. So, let’s take a look at four such tools.
|
||||
|
||||
### Top
|
||||
|
||||
We’ll first start with the obvious. The top command is a great place to start, when you need to monitor what processes are consuming resources. The top command has been around for a very long time and has, for years, been the first tool I turn to when something is amiss. What top does is provide a real-time view of all running systems on a Linux machine. The top command not only displays dynamic information about each running process (as well as the necessary information to manage those processes), but also gives you an overview of the machine (such as, how many CPUs are found, and how much RAM and swap space is available). When I feel something is going wrong with a machine, I immediately turn to top to see what processes are gobbling up the most CPU and MEM (Figure 1). From there, I can act accordingly.
|
||||
|
||||
![top][2]
|
||||
|
||||
Figure 1: Top running on Elementary OS.
|
||||
|
||||
[Used with permission][3]
|
||||
|
||||
There is no need to install anything to use the top command, because it is installed on almost every Linux distribution by default. For more information on top, issue the command man top.
|
||||
|
||||
### Glances
|
||||
|
||||
If you thought the top command offered up plenty of information, you’ve yet to experience Glances. Glances is another text-based monitoring tool. In similar fashion to top, glances offers a real-time listing of more information about your system than nearly any other monitor of its kind. You’ll see disk/network I/O, thermal readouts, fan speeds, disk usage by hardware device and logical volume, processes, warnings, alerts, and much more. Glances also includes a handy sidebar that displays information about disk, filesystem, network, sensors, and even Docker stats. To enable the sidebar, hit the 2 key (while glances is running). You’ll then see the added information (Figure 2).
|
||||
|
||||
![glances][5]
|
||||
|
||||
Figure 2: The glances monitor displaying docker stats along with all the other information it offers.
|
||||
|
||||
[Used with permission][3]
|
||||
|
||||
You won’t find glances installed by default. However, the tool is available in most standard repositories, so it can be installed from the command line or your distribution’s app store, without having to add a third-party repository.
|
||||
|
||||
### GNOME System Monitor
|
||||
|
||||
If you're not a fan of the command line, there are plenty of tools to make your monitoring life a bit easier. One such tool is GNOME System Monitor, which is a front-end for the top tool. But if you prefer a GUI, you can’t beat this app.
|
||||
|
||||
With GNOME System Monitor, you can scroll through the listing of running apps (Figure 3), select an app, and then either end the process (by clicking End Process) or view more details about said process (by clicking the gear icon).
|
||||
|
||||
![GNOME System Monitor][7]
|
||||
|
||||
Figure 3: GNOME System Monitor in action.
|
||||
|
||||
[Used with permission][3]
|
||||
|
||||
You can also click any one of the tabs at the top of the window to get even more information about your system. The Resources tab is a very handy way to get real-time data on CPU, Memory, Swap, and Network (Figure 4).
|
||||
|
||||
![GNOME System Monitor][9]
|
||||
|
||||
Figure 4: The GNOME System Monitor Resources tab in action.
|
||||
|
||||
[Used with permission][3]
|
||||
|
||||
If you don’t find GNOME System Monitor installed by default, it can be found in the standard repositories, so it’s very simple to add to your system.
|
||||
|
||||
### Nagios
|
||||
|
||||
If you’re looking for an enterprise-grade networking monitoring system, look no further than [Nagios][10]. But don’t think Nagios is limited to only monitoring network traffic. This system has over 5,000 different add-ons that can be added to expand the system to perfectly meet (and exceed your needs). The Nagios monitor doesn’t come pre-installed on your Linux distribution and although the install isn’t quite as difficult as some similar tools, it does have some complications. And, because the Nagios version found in many of the default repositories is out of date, you’ll definitely want to install from source. Once installed, you can log into the Nagios web GUI and start monitoring (Figure 5).
|
||||
|
||||
![Nagios ][12]
|
||||
|
||||
Figure 5: With Nagios you can even start and stop services.
|
||||
|
||||
[Used with permission][3]
|
||||
|
||||
Of course, at this point, you’ve only installed the core and will also need to walk through the process of installing the plugins. Trust me when I say it’s worth the extra time.
|
||||
The one caveat with Nagios is that you must manually install any remote hosts to be monitored (outside of the host the system is installed on) via text files. Fortunately, the installation will include sample configuration files (found in /usr/local/nagios/etc/objects) which you can use to create configuration files for remote servers (which are placed in /usr/local/nagios/etc/servers).
|
||||
|
||||
Although Nagios can be a challenge to install, it is very much worth the time, as you will wind up with an enterprise-ready monitoring system capable of handling nearly anything you throw at it.
|
||||
|
||||
### There’s More Where That Came From
|
||||
|
||||
We’ve barely scratched the surface in terms of monitoring tools that are available for the Linux platform. No matter whether you’re looking for a general system monitor or something very specific, a command line or GUI application, you’ll find what you need. These four tools offer an outstanding starting point for any Linux administrator. Give them a try and see if you don’t find exactly the information you need.
|
||||
|
||||
Learn more about Linux through the free ["Introduction to Linux" ][13] course from The Linux Foundation and edX.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/learn/intro-to-linux/2018/10/4-must-have-tools-monitoring-linux
|
||||
|
||||
作者:[Jack Wallen][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/jlwallen
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: /files/images/monitoring1jpg
|
||||
[2]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/monitoring_1.jpg?itok=UiyNGji0 (top)
|
||||
[3]: /licenses/category/used-permission
|
||||
[4]: /files/images/monitoring2jpg
|
||||
[5]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/monitoring_2.jpg?itok=K3OxLcvE (glances)
|
||||
[6]: /files/images/monitoring3jpg
|
||||
[7]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/monitoring_3.jpg?itok=UKcyEDcT (GNOME System Monitor)
|
||||
[8]: /files/images/monitoring4jpg
|
||||
[9]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/monitoring_4.jpg?itok=orLRH3m0 (GNOME System Monitor)
|
||||
[10]: https://www.nagios.org/
|
||||
[11]: /files/images/monitoring5jpg
|
||||
[12]: https://www.linux.com/sites/lcom/files/styles/rendered_file/public/monitoring_5.jpg?itok=RGcLLWL7 (Nagios )
|
||||
[13]: https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||
@ -1,3 +1,4 @@
|
||||
distant1219 is translating
|
||||
PyTorch 1.0 Preview Release: Facebook’s newest Open Source AI
|
||||
======
|
||||
Facebook already uses its own Open Source AI, PyTorch quite extensively in its own artificial intelligence projects. Recently, they have gone a league ahead by releasing a pre-release preview version 1.0.
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
thecyanbird translating
|
||||
|
||||
Terminalizer – A Tool To Record Your Terminal And Generate Animated Gif Images
|
||||
======
|
||||
This is know topic for most of us and i don’t want to give you the detailed information about this flow. Also, we had written many article under this topics.
|
||||
|
||||
@ -1,199 +0,0 @@
|
||||
Translating by way-ww
|
||||
How To Create And Maintain Your Own Man Pages
|
||||
======
|
||||
|
||||

|
||||
|
||||
We already have discussed about a few [**good alternatives to Man pages**][1]. Those alternatives are mainly used for learning concise Linux command examples without having to go through the comprehensive man pages. If you’re looking for a quick and dirty way to easily and quickly learn a Linux command, those alternatives are worth trying. Now, you might be thinking – how can I create my own man-like help pages for a Linux command? This is where **“Um”** comes in handy. Um is a command line utility, used to easily create and maintain your own Man pages that contains only what you’ve learned about a command so far.
|
||||
|
||||
By creating your own alternative to man pages, you can avoid lots of unnecessary, comprehensive details in a man page and include only what is necessary to keep in mind. If you ever wanted to created your own set of man-like pages, Um will definitely help. In this brief tutorial, we will see how to install “Um” command line utility and how to create our own man pages.
|
||||
|
||||
### Installing Um
|
||||
|
||||
Um is available for Linux and Mac OS. At present, it can only be installed using **Linuxbrew** package manager in Linux systems. Refer the following link if you haven’t installed Linuxbrew yet.
|
||||
|
||||
Once Linuxbrew installed, run the following command to install Um utility.
|
||||
|
||||
```
|
||||
$ brew install sinclairtarget/wst/um
|
||||
|
||||
```
|
||||
|
||||
If you will see an output something like below, congratulations! Um has been installed and ready to use.
|
||||
|
||||
```
|
||||
[...]
|
||||
==> Installing sinclairtarget/wst/um
|
||||
==> Downloading https://github.com/sinclairtarget/um/archive/4.0.0.tar.gz
|
||||
==> Downloading from https://codeload.github.com/sinclairtarget/um/tar.gz/4.0.0
|
||||
-=#=# # #
|
||||
==> Downloading https://rubygems.org/gems/kramdown-1.17.0.gem
|
||||
######################################################################## 100.0%
|
||||
==> gem install /home/sk/.cache/Homebrew/downloads/d0a5d978120a791d9c5965fc103866815189a4e3939
|
||||
==> Caveats
|
||||
Bash completion has been installed to:
|
||||
/home/linuxbrew/.linuxbrew/etc/bash_completion.d
|
||||
==> Summary
|
||||
🍺 /home/linuxbrew/.linuxbrew/Cellar/um/4.0.0: 714 files, 1.3MB, built in 35 seconds
|
||||
==> Caveats
|
||||
==> openssl
|
||||
A CA file has been bootstrapped using certificates from the SystemRoots
|
||||
keychain. To add additional certificates (e.g. the certificates added in
|
||||
the System keychain), place .pem files in
|
||||
/home/linuxbrew/.linuxbrew/etc/openssl/certs
|
||||
|
||||
and run
|
||||
/home/linuxbrew/.linuxbrew/opt/openssl/bin/c_rehash
|
||||
==> ruby
|
||||
Emacs Lisp files have been installed to:
|
||||
/home/linuxbrew/.linuxbrew/share/emacs/site-lisp/ruby
|
||||
==> um
|
||||
Bash completion has been installed to:
|
||||
/home/linuxbrew/.linuxbrew/etc/bash_completion.d
|
||||
|
||||
```
|
||||
|
||||
Before going to use to make your man pages, you need to enable bash completion for Um.
|
||||
|
||||
To do so, open your **~/.bash_profile** file:
|
||||
|
||||
```
|
||||
$ nano ~/.bash_profile
|
||||
|
||||
```
|
||||
|
||||
And, add the following lines in it:
|
||||
|
||||
```
|
||||
if [ -f $(brew --prefix)/etc/bash_completion.d/um-completion.sh ]; then
|
||||
. $(brew --prefix)/etc/bash_completion.d/um-completion.sh
|
||||
fi
|
||||
|
||||
```
|
||||
|
||||
Save and close the file. Run the following commands to update the changes.
|
||||
|
||||
```
|
||||
$ source ~/.bash_profile
|
||||
|
||||
```
|
||||
|
||||
All done. let us go ahead and create our first man page.
|
||||
|
||||
### Create And Maintain Your Own Man Pages
|
||||
|
||||
Let us say, you want to create your own man page for “dpkg” command. To do so, run:
|
||||
|
||||
```
|
||||
$ um edit dpkg
|
||||
|
||||
```
|
||||
|
||||
The above command will open a markdown template in your default editor:
|
||||
|
||||
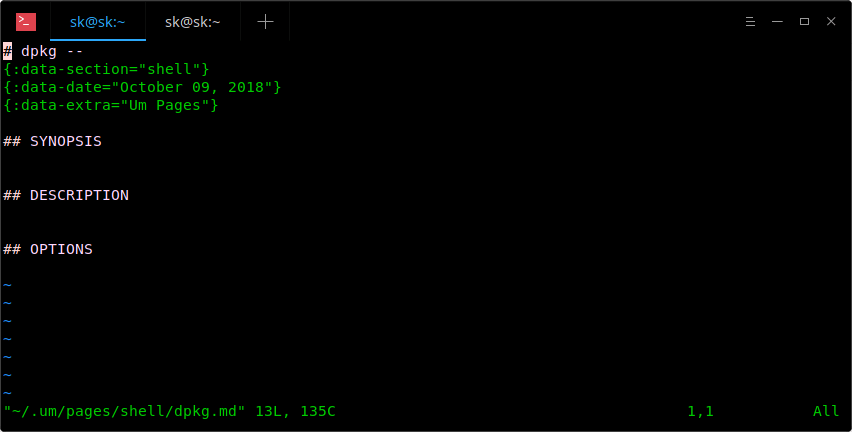
|
||||
|
||||
My default editor is Vi, so the above commands open it in the Vi editor. Now, start adding everything you want to remember about “dpkg” command in this template.
|
||||
|
||||
Here is a sample:
|
||||
|
||||

|
||||
|
||||
As you see in the above output, I have added Synopsis, description and two options for dpkg command. You can add as many as sections you want in the man pages. Make sure you have given proper and easily-understandable titles for each section. Once done, save and quit the file (If you use Vi editor, Press **ESC** key and type **:wq** ).
|
||||
|
||||
Finally, view your newly created man page using command:
|
||||
|
||||
```
|
||||
$ um dpkg
|
||||
|
||||
```
|
||||
|
||||

|
||||
|
||||
As you can see, the the dpkg man page looks exactly like the official man pages. If you want to edit and/or add more details in a man page, again run the same command and add the details.
|
||||
|
||||
```
|
||||
$ um edit dpkg
|
||||
|
||||
```
|
||||
|
||||
To view the list of newly created man pages using Um, run:
|
||||
|
||||
```
|
||||
$ um list
|
||||
|
||||
```
|
||||
|
||||
All man pages will be saved under a directory named**`.um`**in your home directory
|
||||
|
||||
Just in case, if you don’t want a particular page, simply delete it as shown below.
|
||||
|
||||
```
|
||||
$ um rm dpkg
|
||||
|
||||
```
|
||||
|
||||
To view the help section and all available general options, run:
|
||||
|
||||
```
|
||||
$ um --help
|
||||
usage: um <page name>
|
||||
um <sub-command> [ARGS...]
|
||||
|
||||
The first form is equivalent to `um read <page name>`.
|
||||
|
||||
Subcommands:
|
||||
um (l)ist List the available pages for the current topic.
|
||||
um (r)ead <page name> Read the given page under the current topic.
|
||||
um (e)dit <page name> Create or edit the given page under the current topic.
|
||||
um rm <page name> Remove the given page.
|
||||
um (t)opic [topic] Get or set the current topic.
|
||||
um topics List all topics.
|
||||
um (c)onfig [config key] Display configuration environment.
|
||||
um (h)elp [sub-command] Display this help message, or the help message for a sub-command.
|
||||
|
||||
```
|
||||
|
||||
### Configure Um
|
||||
|
||||
To view the current configuration, run:
|
||||
|
||||
```
|
||||
$ um config
|
||||
Options prefixed by '*' are set in /home/sk/.um/umconfig.
|
||||
editor = vi
|
||||
pager = less
|
||||
pages_directory = /home/sk/.um/pages
|
||||
default_topic = shell
|
||||
pages_ext = .md
|
||||
|
||||
```
|
||||
|
||||
In this file, you can edit and change the values for **pager** , **editor** , **default_topic** , **pages_directory** , and **pages_ext** options as you wish. Say for example, if you want to save the newly created Um pages in your **[Dropbox][2]** folder, simply change the value of **pages_directory** directive and point it to the Dropbox folder in **~/.um/umconfig** file.
|
||||
|
||||
```
|
||||
pages_directory = /Users/myusername/Dropbox/um
|
||||
|
||||
```
|
||||
|
||||
And, that’s all for now. Hope this was useful. More good stuffs to come. Stay tuned!
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/how-to-create-and-maintain-your-own-man-pages/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.ostechnix.com/3-good-alternatives-man-pages-every-linux-user-know/
|
||||
[2]: https://www.ostechnix.com/install-dropbox-in-ubuntu-18-04-lts-desktop/
|
||||
@ -0,0 +1,257 @@
|
||||
Exploring the Linux kernel: The secrets of Kconfig/kbuild
|
||||
======
|
||||
Dive into understanding how the Linux config/build system works.
|
||||
|
||||

|
||||
|
||||
The Linux kernel config/build system, also known as Kconfig/kbuild, has been around for a long time, ever since the Linux kernel code migrated to Git. As supporting infrastructure, however, it is seldom in the spotlight; even kernel developers who use it in their daily work never really think about it.
|
||||
|
||||
To explore how the Linux kernel is compiled, this article will dive into the Kconfig/kbuild internal process, explain how the .config file and the vmlinux/bzImage files are produced, and introduce a smart trick for dependency tracking.
|
||||
|
||||
### Kconfig
|
||||
|
||||
The first step in building a kernel is always configuration. Kconfig helps make the Linux kernel highly modular and customizable. Kconfig offers the user many config targets:
|
||||
| config | Update current config utilizing a line-oriented program |
|
||||
| nconfig | Update current config utilizing a ncurses menu-based program |
|
||||
| menuconfig | Update current config utilizing a menu-based program |
|
||||
| xconfig | Update current config utilizing a Qt-based frontend |
|
||||
| gconfig | Update current config utilizing a GTK+ based frontend |
|
||||
| oldconfig | Update current config utilizing a provided .config as base |
|
||||
| localmodconfig | Update current config disabling modules not loaded |
|
||||
| localyesconfig | Update current config converting local mods to core |
|
||||
| defconfig | New config with default from Arch-supplied defconfig |
|
||||
| savedefconfig | Save current config as ./defconfig (minimal config) |
|
||||
| allnoconfig | New config where all options are answered with 'no' |
|
||||
| allyesconfig | New config where all options are accepted with 'yes' |
|
||||
| allmodconfig | New config selecting modules when possible |
|
||||
| alldefconfig | New config with all symbols set to default |
|
||||
| randconfig | New config with a random answer to all options |
|
||||
| listnewconfig | List new options |
|
||||
| olddefconfig | Same as oldconfig but sets new symbols to their default value without prompting |
|
||||
| kvmconfig | Enable additional options for KVM guest kernel support |
|
||||
| xenconfig | Enable additional options for xen dom0 and guest kernel support |
|
||||
| tinyconfig | Configure the tiniest possible kernel |
|
||||
|
||||
I think **menuconfig** is the most popular of these targets. The targets are processed by different host programs, which are provided by the kernel and built during kernel building. Some targets have a GUI (for the user's convenience) while most don't. Kconfig-related tools and source code reside mainly under **scripts/kconfig/** in the kernel source. As we can see from **scripts/kconfig/Makefile** , there are several host programs, including **conf** , **mconf** , and **nconf**. Except for **conf** , each of them is responsible for one of the GUI-based config targets, so, **conf** deals with most of them.
|
||||
|
||||
Logically, Kconfig's infrastructure has two parts: one implements a [new language][1] to define the configuration items (see the Kconfig files under the kernel source), and the other parses the Kconfig language and deals with configuration actions.
|
||||
|
||||
Most of the config targets have roughly the same internal process (shown below):
|
||||
|
||||
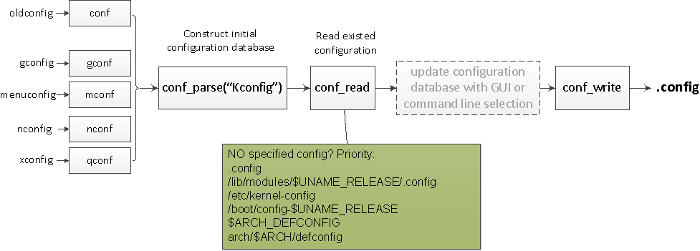
|
||||
|
||||
Note that all configuration items have a default value.
|
||||
|
||||
The first step reads the Kconfig file under source root to construct an initial configuration database; then it updates the initial database by reading an existing configuration file according to this priority:
|
||||
|
||||
> .config
|
||||
> /lib/modules/$(shell,uname -r)/.config
|
||||
> /etc/kernel-config
|
||||
> /boot/config-$(shell,uname -r)
|
||||
> ARCH_DEFCONFIG
|
||||
> arch/$(ARCH)/defconfig
|
||||
|
||||
If you are doing GUI-based configuration via **menuconfig** or command-line-based configuration via **oldconfig** , the database is updated according to your customization. Finally, the configuration database is dumped into the .config file.
|
||||
|
||||
But the .config file is not the final fodder for kernel building; this is why the **syncconfig** target exists. **syncconfig** used to be a config target called **silentoldconfig** , but it doesn't do what the old name says, so it was renamed. Also, because it is for internal use (not for users), it was dropped from the list.
|
||||
|
||||
Here is an illustration of what **syncconfig** does:
|
||||
|
||||
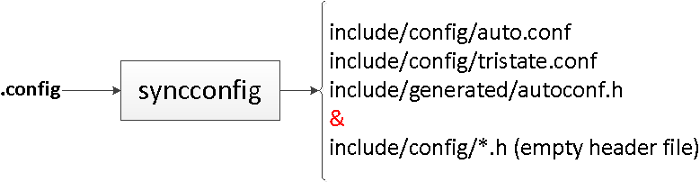
|
||||
|
||||
**syncconfig** takes .config as input and outputs many other files, which fall into three categories:
|
||||
|
||||
* **auto.conf & tristate.conf** are used for makefile text processing. For example, you may see statements like this in a component's makefile:
|
||||
|
||||
```
|
||||
obj-$(CONFIG_GENERIC_CALIBRATE_DELAY) += calibrate.o
|
||||
```
|
||||
|
||||
* **autoconf.h** is used in C-language source files.
|
||||
|
||||
* Empty header files under **include/config/** are used for configuration-dependency tracking during kbuild, which is explained below.
|
||||
|
||||
|
||||
|
||||
|
||||
After configuration, we will know which files and code pieces are not compiled.
|
||||
|
||||
### kbuild
|
||||
|
||||
Component-wise building, called _recursive make_ , is a common way for GNU `make` to manage a large project. Kbuild is a good example of recursive make. By dividing source files into different modules/components, each component is managed by its own makefile. When you start building, a top makefile invokes each component's makefile in the proper order, builds the components, and collects them into the final executive.
|
||||
|
||||
Kbuild refers to different kinds of makefiles:
|
||||
|
||||
* **Makefile** is the top makefile located in source root.
|
||||
* **.config** is the kernel configuration file.
|
||||
* **arch/$(ARCH)/Makefile** is the arch makefile, which is the supplement to the top makefile.
|
||||
* **scripts/Makefile.*** describes common rules for all kbuild makefiles.
|
||||
* Finally, there are about 500 **kbuild makefiles**.
|
||||
|
||||
|
||||
|
||||
The top makefile includes the arch makefile, reads the .config file, descends into subdirectories, invokes **make** on each component's makefile with the help of routines defined in **scripts/Makefile.*** , builds up each intermediate object, and links all the intermediate objects into vmlinux. Kernel document [Documentation/kbuild/makefiles.txt][2] describes all aspects of these makefiles.
|
||||
|
||||
As an example, let's look at how vmlinux is produced on x86-64:
|
||||
|
||||
![vmlinux overview][4]
|
||||
|
||||
(The illustration is based on Richard Y. Steven's [blog][5]. It was updated and is used with the author's permission.)
|
||||
|
||||
All the **.o** files that go into vmlinux first go into their own **built-in.a** , which is indicated via variables **KBUILD_VMLINUX_INIT** , **KBUILD_VMLINUX_MAIN** , **KBUILD_VMLINUX_LIBS** , then are collected into the vmlinux file.
|
||||
|
||||
Take a look at how recursive make is implemented in the Linux kernel, with the help of simplified makefile code:
|
||||
|
||||
```
|
||||
# In top Makefile
|
||||
vmlinux: scripts/link-vmlinux.sh $(vmlinux-deps)
|
||||
+$(call if_changed,link-vmlinux)
|
||||
|
||||
# Variable assignments
|
||||
vmlinux-deps := $(KBUILD_LDS) $(KBUILD_VMLINUX_INIT) $(KBUILD_VMLINUX_MAIN) $(KBUILD_VMLINUX_LIBS)
|
||||
|
||||
export KBUILD_VMLINUX_INIT := $(head-y) $(init-y)
|
||||
export KBUILD_VMLINUX_MAIN := $(core-y) $(libs-y2) $(drivers-y) $(net-y) $(virt-y)
|
||||
export KBUILD_VMLINUX_LIBS := $(libs-y1)
|
||||
export KBUILD_LDS := arch/$(SRCARCH)/kernel/vmlinux.lds
|
||||
|
||||
init-y := init/
|
||||
drivers-y := drivers/ sound/ firmware/
|
||||
net-y := net/
|
||||
libs-y := lib/
|
||||
core-y := usr/
|
||||
virt-y := virt/
|
||||
|
||||
# Transform to corresponding built-in.a
|
||||
init-y := $(patsubst %/, %/built-in.a, $(init-y))
|
||||
core-y := $(patsubst %/, %/built-in.a, $(core-y))
|
||||
drivers-y := $(patsubst %/, %/built-in.a, $(drivers-y))
|
||||
net-y := $(patsubst %/, %/built-in.a, $(net-y))
|
||||
libs-y1 := $(patsubst %/, %/lib.a, $(libs-y))
|
||||
libs-y2 := $(patsubst %/, %/built-in.a, $(filter-out %.a, $(libs-y)))
|
||||
virt-y := $(patsubst %/, %/built-in.a, $(virt-y))
|
||||
|
||||
# Setup the dependency. vmlinux-deps are all intermediate objects, vmlinux-dirs
|
||||
# are phony targets, so every time comes to this rule, the recipe of vmlinux-dirs
|
||||
# will be executed. Refer "4.6 Phony Targets" of `info make`
|
||||
$(sort $(vmlinux-deps)): $(vmlinux-dirs) ;
|
||||
|
||||
# Variable vmlinux-dirs is the directory part of each built-in.a
|
||||
vmlinux-dirs := $(patsubst %/,%,$(filter %/, $(init-y) $(init-m) \
|
||||
$(core-y) $(core-m) $(drivers-y) $(drivers-m) \
|
||||
$(net-y) $(net-m) $(libs-y) $(libs-m) $(virt-y)))
|
||||
|
||||
# The entry of recursive make
|
||||
$(vmlinux-dirs):
|
||||
$(Q)$(MAKE) $(build)=$@ need-builtin=1
|
||||
```
|
||||
|
||||
The recursive make recipe is expanded, for example:
|
||||
|
||||
```
|
||||
make -f scripts/Makefile.build obj=init need-builtin=1
|
||||
```
|
||||
|
||||
This means **make** will go into **scripts/Makefile.build** to continue the work of building each **built-in.a**. With the help of **scripts/link-vmlinux.sh** , the vmlinux file is finally under source root.
|
||||
|
||||
#### Understanding vmlinux vs. bzImage
|
||||
|
||||
Many Linux kernel developers may not be clear about the relationship between vmlinux and bzImage. For example, here is their relationship in x86-64:
|
||||
|
||||
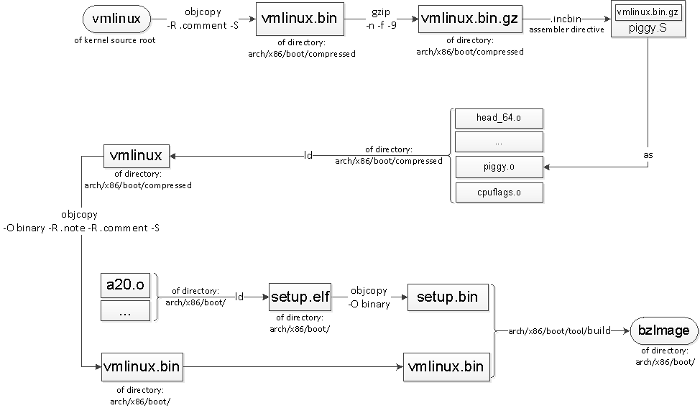
|
||||
|
||||
The source root vmlinux is stripped, compressed, put into **piggy.S** , then linked with other peer objects into **arch/x86/boot/compressed/vmlinux**. Meanwhile, a file called setup.bin is produced under **arch/x86/boot**. There may be an optional third file that has relocation info, depending on the configuration of **CONFIG_X86_NEED_RELOCS**.
|
||||
|
||||
A host program called **build** , provided by the kernel, builds these two (or three) parts into the final bzImage file.
|
||||
|
||||
#### Dependency tracking
|
||||
|
||||
Kbuild tracks three kinds of dependencies:
|
||||
|
||||
1. All prerequisite files (both * **.c** and * **.h** )
|
||||
2. **CONFIG_** options used in all prerequisite files
|
||||
3. Command-line dependencies used to compile the target
|
||||
|
||||
|
||||
|
||||
The first one is easy to understand, but what about the second and third? Kernel developers often see code pieces like this:
|
||||
|
||||
```
|
||||
#ifdef CONFIG_SMP
|
||||
__boot_cpu_id = cpu;
|
||||
#endif
|
||||
```
|
||||
|
||||
When **CONFIG_SMP** changes, this piece of code should be recompiled. The command line for compiling a source file also matters, because different command lines may result in different object files.
|
||||
|
||||
When a **.c** file uses a header file via a **#include** directive, you need write a rule like this:
|
||||
|
||||
```
|
||||
main.o: defs.h
|
||||
recipe...
|
||||
```
|
||||
|
||||
When managing a large project, you need a lot of these kinds of rules; writing them all would be tedious and boring. Fortunately, most modern C compilers can write these rules for you by looking at the **#include** lines in the source file. For the GNU Compiler Collection (GCC), it is just a matter of adding a command-line parameter: **-MD depfile**
|
||||
|
||||
```
|
||||
# In scripts/Makefile.lib
|
||||
c_flags = -Wp,-MD,$(depfile) $(NOSTDINC_FLAGS) $(LINUXINCLUDE) \
|
||||
-include $(srctree)/include/linux/compiler_types.h \
|
||||
$(__c_flags) $(modkern_cflags) \
|
||||
$(basename_flags) $(modname_flags)
|
||||
```
|
||||
|
||||
This would generate a **.d** file with content like:
|
||||
|
||||
```
|
||||
init_task.o: init/init_task.c include/linux/kconfig.h \
|
||||
include/generated/autoconf.h include/linux/init_task.h \
|
||||
include/linux/rcupdate.h include/linux/types.h \
|
||||
...
|
||||
```
|
||||
|
||||
Then the host program **[fixdep][6]** takes care of the other two dependencies by taking the **depfile** and command line as input, then outputting a **. <target>.cmd** file in makefile syntax, which records the command line and all the prerequisites (including the configuration) for a target. It looks like this:
|
||||
|
||||
```
|
||||
# The command line used to compile the target
|
||||
cmd_init/init_task.o := gcc -Wp,-MD,init/.init_task.o.d -nostdinc ...
|
||||
...
|
||||
# The dependency files
|
||||
deps_init/init_task.o := \
|
||||
$(wildcard include/config/posix/timers.h) \
|
||||
$(wildcard include/config/arch/task/struct/on/stack.h) \
|
||||
$(wildcard include/config/thread/info/in/task.h) \
|
||||
...
|
||||
include/uapi/linux/types.h \
|
||||
arch/x86/include/uapi/asm/types.h \
|
||||
include/uapi/asm-generic/types.h \
|
||||
...
|
||||
```
|
||||
|
||||
A **. <target>.cmd** file will be included during recursive make, providing all the dependency info and helping to decide whether to rebuild a target or not.
|
||||
|
||||
The secret behind this is that **fixdep** will parse the **depfile** ( **.d** file), then parse all the dependency files inside, search the text for all the **CONFIG_** strings, convert them to the corresponding empty header file, and add them to the target's prerequisites. Every time the configuration changes, the corresponding empty header file will be updated, too, so kbuild can detect that change and rebuild the target that depends on it. Because the command line is also recorded, it is easy to compare the last and current compiling parameters.
|
||||
|
||||
### Looking ahead
|
||||
|
||||
Kconfig/kbuild remained the same for a long time until the new maintainer, Masahiro Yamada, joined in early 2017, and now kbuild is under active development again. Don't be surprised if you soon see something different from what's in this article.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/10/kbuild-and-kconfig
|
||||
|
||||
作者:[Cao Jin][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/pinocchio
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://github.com/torvalds/linux/blob/master/Documentation/kbuild/kconfig-language.txt
|
||||
[2]: https://www.mjmwired.net/kernel/Documentation/kbuild/makefiles.txt
|
||||
[3]: https://opensource.com/file/411516
|
||||
[4]: https://opensource.com/sites/default/files/uploads/vmlinux_generation_process.png (vmlinux overview)
|
||||
[5]: https://blog.csdn.net/richardysteven/article/details/52502734
|
||||
[6]: https://github.com/torvalds/linux/blob/master/scripts/basic/fixdep.c
|
||||
@ -0,0 +1,118 @@
|
||||
Command line quick tips: Reading files different ways
|
||||
======
|
||||
|
||||

|
||||
|
||||
Fedora is delightful to use as a graphical operating system. You can point and click your way through just about any task easily. But you’ve probably seen there is a powerful command line under the hood. To try it out in a shell, just open the Terminal application in your Fedora system. This article is one in a series that will show you some common command line utilities.
|
||||
|
||||
In this installment you’ll learn how to read files in different ways. If you open a Terminal to do some work on your system, chances are good that you’ll need to read a file or two.
|
||||
|
||||
### The whole enchilada
|
||||
|
||||
The **cat** command is well known to terminal users. When you **cat** a file, you’re simply displaying the whole file to the screen. Really what’s happening under the hood is the file is read one line at a time, then each line is written to the screen.
|
||||
|
||||
Imagine you have a file with one word per line, called myfile. To make this clear, the file will contain the word equivalent for a number on each line, like this:
|
||||
|
||||
```
|
||||
|
||||
one
|
||||
two
|
||||
three
|
||||
four
|
||||
five
|
||||
|
||||
```
|
||||
|
||||
So if you **cat** that file, you’ll see this output:
|
||||
|
||||
```
|
||||
|
||||
$ cat myfile
|
||||
one
|
||||
two
|
||||
three
|
||||
four
|
||||
five
|
||||
|
||||
```
|
||||
|
||||
Nothing too surprising there, right? But here’s an interesting twist. You can also **cat** that file backward. For this, use the **tac** command. (Note that Fedora takes no blame for this debatable humor!)
|
||||
|
||||
```
|
||||
|
||||
$ tac myfile
|
||||
five
|
||||
four
|
||||
three
|
||||
two
|
||||
one
|
||||
|
||||
```
|
||||
|
||||
The **cat** file also lets you ornament the file in different ways, in case that’s helpful. For instance, you can number lines:
|
||||
|
||||
```
|
||||
|
||||
$ cat -n myfile
|
||||
1 one
|
||||
2 two
|
||||
3 three
|
||||
4 four
|
||||
5 five
|
||||
|
||||
```
|
||||
|
||||
There are additional options that will show special characters and other features. To learn more, run the command **man cat** , and when done just hit **q** to exit back to the shell.
|
||||
|
||||
### Picking over your food
|
||||
|
||||
Often a file is too long to fit on a screen, and you may want to be able to go through it like a document. In that case, try the **less** command:
|
||||
|
||||
```
|
||||
|
||||
$ less myfile
|
||||
|
||||
```
|
||||
|
||||
You can use your arrow keys as well as **PgUp/PgDn** to move around the file. Again, you can use the **q** key to quit back to the shell.
|
||||
|
||||
There’s actually a **more** command too, based on an older UNIX command. If it’s important to you to still see the file when you’re done, you might want to use it. The **less** command brings you back to the shell the way you left it, and clears the display of any sign of the file you looked at.
|
||||
|
||||
### Just the appetizer (or dessert)
|
||||
|
||||
Sometimes the output you want is just the beginning of a file. For instance, the file might be so long that when you **cat** the whole thing, the first few lines scroll past before you can see them. The **head** command will help you grab just those lines:
|
||||
|
||||
```
|
||||
|
||||
$ head -n 2 myfile
|
||||
one
|
||||
two
|
||||
|
||||
```
|
||||
|
||||
In the same way, you can use **tail** to just grab the end of a file:
|
||||
|
||||
```
|
||||
|
||||
$ tail -n 3 myfile
|
||||
three
|
||||
four
|
||||
five
|
||||
|
||||
```
|
||||
|
||||
Of course these are only a few simple commands in this area. But they’ll get you started when it comes to reading files.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://fedoramagazine.org/commandline-quick-tips-reading-files-different-ways/
|
||||
|
||||
作者:[Paul W. Frields][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://fedoramagazine.org/author/pfrields/
|
||||
[b]: https://github.com/lujun9972
|
||||
@ -0,0 +1,58 @@
|
||||
Happy birthday, KDE: 11 applications you never knew existed
|
||||
======
|
||||
Which fun or quirky app do you need today?
|
||||
|
||||
|
||||
The Linux desktop environment KDE celebrates its 22nd anniversary on October 14 this year. There are a gazillion* applications created by the KDE community of users, many of which provide fun and quirky services. We perused the list and picked out 11 applications you might like to know exist.
|
||||
|
||||
*Not really, but [there are a lot][1].
|
||||
|
||||
### 11 KDE applications you never knew existed
|
||||
|
||||
1\. [KTeaTime][2] is a timer for steeping tea. Set it by choosing the type of tea you are drinking—green, black, herbal, etc.—and the timer will ding when it's ready to remove the tea bag and drink.
|
||||
|
||||
2\. [KTux][3] is just a screensaver... or is it? Tux is flying in outer space in his green spaceship.
|
||||
|
||||
3\. [Blinken][4] is a memory game based on Simon Says, an electronic game released in 1978. Players are challenged to remember sequences of increasing length.
|
||||
|
||||
4\. [Tellico][5] is a collection manager for organizing your favorite hobby. Maybe you still collect baseball cards. Maybe you're part of a wine club. Maybe you're a serious bookworm. Maybe all three!
|
||||
|
||||
5\. [KRecipes][6] is **not** a simple recipe manager. It's got a lot going on! Shopping lists, nutrient analysis, advanced search, recipe ratings, import/export various formats, and more.
|
||||
|
||||
6\. [KHangMan][7] is based on the classic game Hangman where you guess the word letter by letter. This game is available in several languages, and it can be used to improve your learning of another language. It has four categories, one of which is "animals" which is great for kids.
|
||||
|
||||
7\. [KLettres][8] is another app that may help you learn a new language. It teaches the alphabet and challenges the user to read and pronounce syllables.
|
||||
|
||||
8\. [KDiamond][9] is similar to Bejeweled or other single player puzzle games where the goal of the game is to build lines of a certain number of the same type of jewel or object. In this case, diamonds.
|
||||
|
||||
9\. [KolourPaint][10] is a very simple editing tool for your images or app for creating simple vectors.
|
||||
|
||||
10\. [Kiriki][11] is a dice game for 2-6 players similar to Yahtzee.
|
||||
|
||||
11\. [RSIBreak][12] doesn't start with a K. What!? It starts with an "RSI" for "Repetitive Strain Injury," which can occur from working for long hours, day in and day out, with a mouse and keyboard. This app reminds you to take breaks and can be personalized to meet your needs.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/10/kde-applications
|
||||
|
||||
作者:[Opensource.com][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.kde.org/applications/
|
||||
[2]: https://www.kde.org/applications/games/kteatime/
|
||||
[3]: https://userbase.kde.org/KTux
|
||||
[4]: https://www.kde.org/applications/education/blinken
|
||||
[5]: http://tellico-project.org/
|
||||
[6]: https://www.kde.org/applications/utilities/krecipes/
|
||||
[7]: https://edu.kde.org/khangman/
|
||||
[8]: https://edu.kde.org/klettres/
|
||||
[9]: https://games.kde.org/game.php?game=kdiamond
|
||||
[10]: https://www.kde.org/applications/graphics/kolourpaint/
|
||||
[11]: https://www.kde.org/applications/games/kiriki/
|
||||
[12]: https://userbase.kde.org/RSIBreak
|
||||
@ -0,0 +1,129 @@
|
||||
How To Lock Virtual Console Sessions On Linux
|
||||
======
|
||||
|
||||

|
||||
|
||||
When you’re working on a shared system, you might not want the other users to sneak peak in your console to know what you’re actually doing. If so, I know a simple trick to lock your own session while still allowing other users to use the system on other virtual consoles. Thanks to **Vlock** , stands for **V** irtual Console **lock** , a command line program to lock one or more sessions on the Linux console. If necessary, you can lock the entire console and disable the virtual console switching functionality altogether. Vlock is especially useful for the shared Linux systems which have multiple users with access to the console.
|
||||
|
||||
### Installing Vlock
|
||||
|
||||
On Arch-based systems, the Vlock package is replaced with **kpd** package which is preinstalled by default, so you need not to bother with installation.
|
||||
|
||||
On Debian, Ubuntu, Linux Mint, run the following command to install Vlock:
|
||||
|
||||
```
|
||||
$ sudo apt-get install vlock
|
||||
```
|
||||
|
||||
On Fedora:
|
||||
|
||||
```
|
||||
$ sudo dnf install vlock
|
||||
```
|
||||
|
||||
On RHEL, CentOS:
|
||||
|
||||
```
|
||||
$ sudo yum install vlock
|
||||
```
|
||||
|
||||
### Lock Virtual Console Sessions On Linux
|
||||
|
||||
The general syntax for Vlock is:
|
||||
|
||||
```
|
||||
vlock [ -acnshv ] [ -t <timeout> ] [ plugins... ]
|
||||
```
|
||||
|
||||
Where,
|
||||
|
||||
* **a** – Lock all virtual console sessions,
|
||||
* **c** – Lock current virtual console session,
|
||||
* **n** – Switch to new empty console before locking all sessions,
|
||||
* **s** – Disable SysRq key mechanism,
|
||||
* **t** – Specify the timeout for the screensaver plugins,
|
||||
* **h** – Display help section,
|
||||
* **v** – Display version.
|
||||
|
||||
|
||||
|
||||
Let me show you some examples.
|
||||
|
||||
**1\. Lock current console session**
|
||||
|
||||
When running Vlock without any arguments, it locks the current console session (TYY) by default. To unlock the session, you need to enter either the current user’s password or the root password.
|
||||
|
||||
```
|
||||
$ vlock
|
||||
```
|
||||
|
||||

|
||||
|
||||
You can also use **-c** flag to lock the current console session.
|
||||
|
||||
```
|
||||
$ vlock -c
|
||||
```
|
||||
|
||||
Please note that this command will only lock the current console. You can switch to other consoles by pressing **ALT+F2**. For more details about switching between TTYs, refer the following guide.
|
||||
|
||||
Also, if the system has multiple users, the other users can still access their respective TTYs.
|
||||
|
||||
**2\. Lock all console sessions**
|
||||
|
||||
To lock all TTYs at the same time and also disable the virtual console switching functionality, run:
|
||||
|
||||
```
|
||||
$ vlock -a
|
||||
```
|
||||
|
||||
Again, to unlock the console sessions, just press ENTER key and type your current user’s password or root user password.
|
||||
|
||||
Please keep in mind that the **root user can always unlock any vlock session** at any time, unless disabled at compile time.
|
||||
|
||||
**3. Switch to new virtual console before locking all consoles
|
||||
**
|
||||
|
||||
It is also possible to make Vlock to switch to new empty virtual console from X session before locking all consoles. To do so, use **-n** flag.
|
||||
|
||||
```
|
||||
$ vlock -n
|
||||
```
|
||||
|
||||
**4. Disable SysRq mechanism
|
||||
**
|
||||
|
||||
As you may know, the Magic SysRq key mechanism allows the users to perform some operations when the system freeze. So the users can unlock the consoles using SysRq. In order to prevent this, pass the **-s** option to disable SysRq mechanism. Please remember, this only works if the **-a** option is given.
|
||||
|
||||
```
|
||||
$ vlock -sa
|
||||
```
|
||||
|
||||
For more options and its usage, refer the help section or the man pages.
|
||||
|
||||
```
|
||||
$ vlock -h
|
||||
$ man vlock
|
||||
```
|
||||
|
||||
Vlock prevents the unauthorized users from gaining the console access. If you’re looking for a simple console locking mechanism to your Linux machine, Vlock is worth checking!
|
||||
|
||||
And, that’s all for now. Hope this was useful. More good stuffs to come. Stay tuned!
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/how-to-lock-virtual-console-sessions-on-linux/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[b]: https://github.com/lujun9972
|
||||
@ -0,0 +1,74 @@
|
||||
How to Install GRUB on Arch Linux (UEFI)
|
||||
======
|
||||
|
||||

|
||||
|
||||
Some time ago, I wrote a tutorial on **[how to reinstall Grub][1] on Arch Linux after installing Windows.**
|
||||
|
||||
A few weeks ago, I had to reinstall **Arch Linux** from scratch on my laptop and I discovered installing **Grub** was not as straightforward as I remembered.
|
||||
|
||||
For this reason, I’m going to write this tutorial since **installing Grub on a UEFI bios** during a new **Arch Linux** installation it’s not too easy.
|
||||
|
||||
### Locating the EFI partition
|
||||
|
||||
The first important thing to do for installing **Grub** on **Arch Linux** is to locate the **EFI** partition.
|
||||
Let’s run the following command in order to locate this partition:
|
||||
|
||||
```
|
||||
# fdisk -l
|
||||
```
|
||||
|
||||
We need to check the partition marked as **EFI System
|
||||
**In my case is **/dev/sda2**
|
||||
|
||||
After that, we need to mount this partition, for example, on /boot/efi:
|
||||
|
||||
```
|
||||
# mkdir /boot/efi
|
||||
# mount /dev/sdb2 /boot/efi
|
||||
```
|
||||
|
||||
Another important thing to do is adding this partition into the **/etc/fstab** file.
|
||||
|
||||
#### Installing Grub
|
||||
|
||||
Now we can install Grub in our system:
|
||||
|
||||
```
|
||||
# grub-mkconfig -o /boot/grub/grub.cfg
|
||||
# grub-install --target=x86_64-efi --efi-directory=/boot/efi --bootloader-id=GRUB
|
||||
```
|
||||
|
||||
#### Adding Windows Automatically into the Grub Menu
|
||||
|
||||
In order to automatically add the **Windows entry into the Grub menu** , we need to install the **os-prober** program:
|
||||
|
||||
```
|
||||
# pacman -Sy os-prober
|
||||
```
|
||||
|
||||
In order to add the entry item let’s run the following commands:
|
||||
|
||||
```
|
||||
# os-prober
|
||||
# grub-mkconfig -o /boot/grub/grub.cfg
|
||||
# grub-install --target=x86_64-efi --efi-directory=/boot/efi --bootloader-id=GRUB
|
||||
```
|
||||
|
||||
You can find more about Grub on Arch Linux [here][2].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://fasterland.net/how-to-install-grub-on-arch-linux-uefi.html
|
||||
|
||||
作者:[Francesco Mondello][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: http://fasterland.net/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: http://fasterland.net/reinstall-grub-arch-linux.html
|
||||
[2]: https://wiki.archlinux.org/index.php/GRUB
|
||||
@ -0,0 +1,66 @@
|
||||
9 个方法,提升开发者与设计师之间的协作
|
||||
======
|
||||
|
||||

|
||||
|
||||
本文由我与 [Jason Porter][1] 共同完成。
|
||||
|
||||
在任何软件项目中,设计至关重要。设计师不像开发团队那样熟悉其内部工作,但迟早都要知道开发人员写代码的意图。
|
||||
|
||||
两边都有自己的成见。工程师经常认为设计师们古怪不理性,而设计师也认为工程师们死板要求高。在一天的工作快要结束时,情况会变得更加微妙。设计师和开发者们的命运永远交织在一起。
|
||||
|
||||
做到以下九件事,便可以增强他们之间的合作
|
||||
|
||||
### 1\. 首先,说实在的,打破壁垒。
|
||||
|
||||
几乎每一个行业都有“<ruby>迷惑之墙<rt>wall of confusion</rt></ruby>”的模子。无论你干什么工作,拆除这堵墙的第一步就是要双方都认同它需要拆除。一旦所有的人都认为现有的流程效率低下,你就可以从其他想法中获得灵感,然后解决问题。
|
||||
|
||||
### 2\. 学会共情
|
||||
|
||||
在撸起袖子开始干之前,休息一下。这是团队建设的重要的交汇点。一个时机去认识到:我们都是成人,我们都有自己的优点与缺点,更重要的是,我们是一个团队。围绕工作流程与工作效率的讨论会经常发生,因此在开始之前,建立一个信任与协作的基础至关重要。
|
||||
|
||||
### 3\. 认识差异
|
||||
|
||||
设计师和开发者从不同的角度攻克问题。对于相同的问题,设计师会追求更好的效果,而开发者会寻求更高的效率。这两种观点不必互相排斥。谈判和妥协的余地很大,并且在二者之间必然存在一个用户满意度最佳的中点。
|
||||
|
||||
### 4\. 拥抱共性
|
||||
|
||||
这一切都是与工作流程相关的。<ruby>持续集成<rt>Continuous Integration</rt></ruby>/<ruby>持续交付<rt>Continuous Delivery</rt></ruby>,scrum,agille 等等,都基本上说了一件事:构思,迭代,考察,重复。迭代和重复是两种工作的相同点。因此,不再让开发周期紧跟设计周期,而是同时并行地运行它们,这样会更有意义。<ruby>同步周期<rt>Syncing cycles</rt></ruby>允许团队在每一步上交流、协作、互相影响。
|
||||
|
||||
### 5\. 管理期望
|
||||
|
||||
一切冲突的起因一言以蔽之:期望不符。因此,防止系统性分裂的简单办法就是通过确保团队成员在说之前先想、在做之前先说来管理期望。设定的期望往往会通过日常对话不断演变。强迫团队通过开会以达到其效果可能会适得其反。
|
||||
|
||||
### 6\. 按需开会
|
||||
|
||||
只在工作开始和工作结束开一次会远远不够。但也不意味着每天或每周都要开会。定期开会也可能会适得其反。试着按需开会吧。即兴会议可能会发生很棒的事情,即使是在开水房。如果你的团队是分散式的或者甚至有一名远程员工,视频会议,文本聊天或者打电话都是开会的好方法。团队中的每人都有多种方式互相沟通,这一点非常重要。
|
||||
|
||||
### 7\. 建立词库
|
||||
|
||||
设计师和开发者有时候对相似的想法有着不同的术语,就像把猫叫了个咪。毕竟,所有人都用的惯比起术语的准确度和适应度更重要。
|
||||
|
||||
### 8\. 学会沟通
|
||||
|
||||
无论什么时候,团队中的每个人都有责任去维持一个有效的沟通。每个人都应该努力做到一字一板。
|
||||
|
||||
### 9\. 不断改善
|
||||
|
||||
仅一名团队成员就能破坏整个进度。全力以赴。如果每个人都不关心产品或目标,继续项目或者做出改变的动机就会出现问题。
|
||||
|
||||
本文参考 [Designers and developers: Finding common ground for effective collaboration][2],演讲的作者将会出席在旧金山五月 8-10 号举办的[Red Hat Summit 2018][3]。[五月 7 号][3]注册将节省 500 美元。支付时使用优惠码 **OPEN18** 以获得更多折扣。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/5/9-ways-improve-collaboration-developers-designers
|
||||
|
||||
作者:[Jason Brock][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[LuuMing](https://github.com/LuuMing)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/jkbrock
|
||||
[1]:https://opensource.com/users/lightguardjp
|
||||
[2]:https://agenda.summit.redhat.com/SessionDetail.aspx?id=154267
|
||||
[3]:https://www.redhat.com/en/summit/2018
|
||||
@ -0,0 +1,45 @@
|
||||
写作是如何帮助技能拓展和事业成长的
|
||||
======
|
||||
|
||||

|
||||
|
||||
在最近的[温哥华开源峰会][1]上,我参加了一个小组讨论,叫做“写作是如何改变你的职业生涯的(即使你不是个作家)”。主持人是 Opensource.com 的社区经理兼编辑 Rikki Endsley,成员有开源策略顾问 VM (Vicky) Brasseur,The New Stack 的创始人兼主编 Alex Williams,还有 The Scale Factory 的顾问 Dawn Foster。
|
||||
|
||||
Rikki 在她的[这篇文章][3]中总结了一些能愉悦你,并且能以意想不到的方式改善你职业生涯的写作方法,我在峰会上的发言是受她这篇文章的启发。透露一下,我认识 Rikki 很久了,我们在同一家公司共事了很多年,一起带过孩子,到现在还是很亲密的朋友。
|
||||
|
||||
### 写作和学习
|
||||
|
||||
正如 Rikki 对这个小组讨论的描述,“即使你自认为不是一个‘作家’,你也应该考虑写一下对开源的贡献,还有你的项目或者社区”。写作是一种很好的方式,来分享自己的知识并让别人参与到你的工作中来,当然它对个人也有好处。写作能帮助你结识新人,学习新技能,还能改善你的沟通。
|
||||
|
||||
我发现写作能让我搞清楚自己对某个主题有哪些不懂的地方。写作的过程会让知识体系的空白很突出,这激励了我通过进一步的研究、阅读和提问来填补空白。
|
||||
|
||||
Rikki 说:“写那些你不知道的东西会更加困难也更加耗时,但是也更有成就感,更有益于你的事业。我发现写我不知道的东西有助于自己学习,因为得研究透彻才能给读者解释清楚。”
|
||||
|
||||
把你刚学到的东西写出来对其他也在学习这些知识的人是很有价值的。[Julia Evans][4] 经常在她的博客里写有关学习新技能的文章。她能把主题分解成一个个小的部分,这种方法对读者很友好,容易上手。Evans 在自己的博客中带领读者了解她的学习过程,指出在这个过程中哪些是对她有用的,哪些是没用的,基本消除了读者的学习障碍,为新手清扫了道路。
|
||||
|
||||
### 更明确的沟通
|
||||
|
||||
|
||||
写作有助于练习思考和准确讲话,尤其是面向国际受众写作(或演讲)时。例如,在[这篇文章中][5],Isabel Drost-Fromm 为那些母语不是英语的演讲者提供了几个技巧来消除歧义。不管是在会议上还是在自己团队内发言,写作还能帮你在演示之前理清思路。
|
||||
|
||||
Rikki 说:“写文章的过程有助于我组织整理自己的发言和演示稿,也是一个给参会者提供笔记的好方式,还可以分享给没有参加活动的更多国际观众。”
|
||||
|
||||
如果你有兴趣,我鼓励你去写作。我强烈建议你参考这里提到的文章,开始思考你要写的内容。 不幸的是,我们在开源峰会上的讨论没有记录,但我希望将来能再做一次讨论,分享更多的想法。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/2018/9/how-writing-can-help-you-learn-new-skills-and-grow-your-career
|
||||
|
||||
作者:[Amber Ankerholz][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[belitex](https://github.com/belitex)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/aankerholz
|
||||
[1]: https://events.linuxfoundation.org/events/open-source-summit-north-america-2018/
|
||||
[2]: https://ossna18.sched.com/event/FAOF/panel-discussion-how-writing-can-change-your-career-for-the-better-even-if-you-dont-identify-as-a-writer-moderated-by-rikki-endsley-opensourcecom-red-hat?iframe=no#
|
||||
[3]: https://opensource.com/article/18/2/career-changing-magic-writing
|
||||
[4]: https://jvns.ca/
|
||||
[5]: https://www.linux.com/blog/event/open-source-summit-eu/2017/12/technical-writing-international-audience
|
||||
@ -0,0 +1,166 @@
|
||||
Linux 拥有了新的行为准则,但是许多人都对此表示不满
|
||||
=====
|
||||
|
||||
**Linux 内核有了新的<ruby>行为准则<rt>Code of Conduct</rt></ruby>(CoC)。但在这条行为准则被签署以及发布仅仅 30 分钟之后,Linus Torvalds 就暂时离开了 Linux 内核的开发工作。因为新行为准则的作者那富有争议的过去,现在这件事成为了热点话题。许多人都对这新的行为准则表示不满。**
|
||||
|
||||
如果你还不了解这件事,请参阅 [Linus Torvalds 对于自己之前的不良态度致歉并开始休假,以改善自己的行为态度][1]
|
||||
|
||||
### Linux 内核开发遵守的新行为准则
|
||||
|
||||
Linux 内核开发者并不是以前没有需要遵守的行为准则,但是之前的[<ruby>冲突准则<rt>code of conflict</rt></ruby>][2]现在被替换成了以“给内核开发社区营造更加热情,更方便他人参与的氛围”为目的的行为准则。
|
||||
|
||||
>“为营造一个开放并且热情的社区环境,我们,贡献者与维护者,许诺让每一个参与进我们项目和社区的人享受一个没有骚扰的体验。无关于他们的年纪,体型,身体残疾,种族,性别,性别认知与表达,社会经验,教育水平,社会或者经济地位,国籍,外表,人种,信仰,性认同和性取向。
|
||||
|
||||
你可以在这里阅读整篇行为准则
|
||||
|
||||
[Linux 行为准则][33]
|
||||
|
||||
### Linus Torvalds 是被迫道歉并且休假的吗?
|
||||
|
||||
![Linus Torvalds 的道歉][3]
|
||||
|
||||
这个新的行为准则由 Linus Torvalds 和 Greg Kroah-Hartman (仅次于 Torvalds 的二把手)签发。来自 Intel 的 Dan Williams 和来自 Facebook 的 Chris Mason 也是该准则的签署者。
|
||||
|
||||
如果我正确地解读了时间线,在签署这个行为准则的半小时之后,Torvalds [发送了一封邮件,对自己之前的不良态度致歉][4]。他同时宣布会进行休假,以改善自己的行为态度。
|
||||
|
||||
不过有些人开始阅读这封邮件的话外之音,并对如下文字报以特别关注:
|
||||
|
||||
>**在这周,许多社区成员批评了我之前种种不解人意的行为。我以前在邮件里进行的,对他人轻率的批评是非专业以及不必要的**。这种情况在我将事情放在私人渠道处理的时候尤为严重。我理解这件事情的严重性,这是不好的行为,我对此感到十分抱歉。
|
||||
|
||||
他是否是因为新的行为准则被强迫做出道歉,并且决定休假,可以通过这几行来判断。这也可以让我们采取一些措施,避免 Torvalds 被新的行为准则伤害。
|
||||
|
||||
### 有关贡献者盟约作者 Coraline Ada Ehmke 的争议
|
||||
|
||||
Linux 的行为准则基于[<ruby>贡献者盟约<rt>Contributor Convenant</rt></ruby>1.4 版本][5]。贡献者盟约[被上百个开源项目所接纳][6],包括 Eclipse, Angular, Ruby, Kubernetes等项目。
|
||||
|
||||
贡献者盟约由 [Coraline Ada Ehmke][7] 创作,她是一个软件工程师,开源支持者,以及 [LGBT][8] 活动家。她对于促进开源世界的多样性做了显著的贡献。
|
||||
|
||||
Coraline 对于唯才是用的反对立场同样十分鲜明。[<ruby>唯才是用<rt>meritocracy</rt></ruby>][9]这个词语源自拉丁文,本意为个人在系统内部的进步取决于他的“功绩”,例如智力水平,取得的证书以及教育程度。但[类似 Coraline 的活动家们认为][10]唯才是用是个糟糕的体系,因为他们只是通过人的智力产出来度量一个人,而并不重视他们的人性。
|
||||
|
||||
[![croraline meritocracy][11]][12]
|
||||
图片来源:推特用户@nickmon1112
|
||||
|
||||
[Linus Torvalds 不止一次地说到,他在意的只是代码而并非写代码的人][13]。所以很明显,这忤逆了 Coraline 有关唯才是用体系的观点。
|
||||
|
||||
具体来说,Coraline 那被人关注饱受争议的过去,是一个关于 [Opal 项目][14]的事件。那是一个发生[在推特上的讨论][15],Elia,来自意大利的 Opal 项目核心开发者说“(那些变性人)不接受现实才是问题所在。”
|
||||
|
||||
Coraline 并没有参加讨论,也不是 Opal 项目的贡献者。不过作为 LGBT 活动家,她以 Elia 发表“冒犯变性人群体的发言”为由,[要求他退出 Opal 项目][16]。 Coraline 和她的支持者——他们给这个项目做过贡献,通过在 GitHub 仓库平台上冗长且激烈的争论,试图将 Elia——此项目的核心开发者移出项目。
|
||||
|
||||
虽然 Elia 并没有离开这个项目,不过 Opal 项目的维护者同意实行一个行为准则。这个行为准则就是 Coraline 不停向维护者们宣扬的,她那著名的贡献者盟约。
|
||||
|
||||
不过故事到这里并没有结束。贡献者盟约稍后被更改,[加入了一些针对 Elia 的新条款][17]。这些新条款将行为准则的管束范围扩展到公共领域。不过这些更改稍后[被维护者们标记为恶意篡改][18]。最后 Opal 项目摆脱了贡献者盟约,并用自己的行为准则取而代之。
|
||||
|
||||
这个例子非常好的说明了,某些被冒犯的少数人群——他们并没有给这个项目哪怕一点贡献,是怎样试图去驱逐这个项目的核心开发者的。
|
||||
|
||||
### 人们对于 Linux 新的行为准则的以及 Torvalds 道歉的反映。
|
||||
|
||||
Linux 行为准则以及 Torvalds 的道歉一发布,社交媒体与论坛上就开始盛传种种谣言与[推测][19]。虽然很多人对新的行为准则感到满意,但仍有些人认为这是 [SJW 尝试渗透 Linux 社区][20]的阴谋。
|
||||
|
||||
Caroline 发布的一个富有嘲讽意味的推特让争论愈发激烈。
|
||||
|
||||
>我迫不及待期待看到大批的人离开 Linux 社区的场景了。现在它以及被 SJW 的成员渗透了。哈哈哈哈。
|
||||
[pic.twitter.com/eFeY6r4ENv][21]
|
||||
>
|
||||
>— Coraline Ada Ehmke (@CoralineAda) [9 月 16 日, 2018][22]
|
||||
|
||||
随着对于 Linux 行为准则的争论持续发酵,Carolaine 公开宣称贡献者盟约是一份政治文件。这并不能被那些试图将政治因素排除在开源项目之外的人所接收。
|
||||
|
||||
>有些人说贡献者盟约是一份政治文件,他们说的没错。
|
||||
>
|
||||
>— Coraline Ada Ehmke (@CoralineAda) [9 月 16 日, 2018][23]
|
||||
|
||||
Nick Monroe,一位自由记者,宣称 Linux 行为准则远没有表面上看上去那么简单。为了证明自己的观点,他挖掘出了 Coraline 的过去。如果您愿意,可以阅读以下材料。
|
||||
|
||||
>好啦,你们已经看到过几千次了。这是一个行为准则。
|
||||
>
|
||||
>它包含了社会认同的正义行为。<https://t.co/KuQqeriYeJ>
|
||||
>
|
||||
>不过它或许没有看上去来的那么简单。[pic.twitter.com/8NUL2K1gu2][24]
|
||||
>
|
||||
>— Nick Monroe (@nickmon1112) [9 月 17 日, 2018][25]
|
||||
|
||||
Nick 并不是唯一一个反对 Linux 新的行为准则的人。[SJW][26] 的参与引发了更多的阴谋论猜测。
|
||||
|
||||
>我猜今天关于 Linux 的大新闻就是现在,Linux 内核被一个post meritocracy世界观下的行为准则给掌控了。
|
||||
>
|
||||
>这个行为准则的宗旨看起来不错。不过在实际操作中,它们通常被当作 SJW 分子攻击他们不喜之人的工具。况且,很多人都被 SJW 分子所厌恶。
|
||||
>
|
||||
> — Mark Kern (@Grummz) [September 17, 2018][27]
|
||||
|
||||
虽然很多人对于 Torvalds 的道歉感到欣慰,仍有一些人在责备 Torvalds 的态度。
|
||||
|
||||
>我是不是唯一一个认为 Linus Torvalds 这十几年来的态度恰好就是 Linux 和开源“社区”特有的那种,居高临下,粗鲁,鄙视一切新人的行为作风?反正作为一个新用户,我从来没有在 Linux 社区里感受到自己是受欢迎的。
|
||||
>
|
||||
>— Jonathan Frappier (@jfrappier) [9 月 17 日, 2018][28]
|
||||
|
||||
还有些人并不能接受 Torvalds 的道歉。
|
||||
|
||||
>哦快看啊,一个喜欢辱骂他人的开源软件维护者,在十几年的恶行之后,终于承认了他的行为**可能**是不正确的。
|
||||
>
|
||||
>我关注的那些人因为这件事都惊讶到平地摔,并且决定给他(Linus Torvalds)寄饼干来庆祝。 🙄🙄🙄
|
||||
>
|
||||
>— Kelly Ellis (@justkelly_ok) [9 月 17 日, 2018][29]
|
||||
|
||||
Torvalds 的道歉引起了广泛关注 ;)
|
||||
|
||||
>我现在要在我的个人档案里写上”我不知是否该原谅 Linus Torvalds“ 吗?
|
||||
>
|
||||
>— Verónica. (@maria_fibonacci) [9 月 17 日, 2018][30]
|
||||
|
||||
不继续开玩笑了。有关 Linus 道歉的关注是由 Sharp 挑起的。他因为“恶劣的社区环境”于 2015 年退出了 Linux 内核的开发。
|
||||
|
||||
>现在我们要面对的问题是,这个成就 Linus,给予他肆意辱骂特权的社区能否迎来改变。不仅仅是 Linus 个人,Linux 内核开发社区也急需改变。<https://t.co/EG5KO43416>
|
||||
>
|
||||
>— Sage Sharp (@sagesharp) 9 月 17 日, 2018
|
||||
|
||||
### 你对于 Linux 行为准则怎么看?
|
||||
|
||||
如果你问我的观点,我认为目前社区的确是需要一个行为准则。它能指导人们尊重他人,不因为他人的种族,宗教信仰,国籍,政治观点(左派或者右派)而歧视,营造出一个积极向上的社区氛围。
|
||||
|
||||
对于这个事件,你怎么看?你认为这个行为准则能够帮助 Linux 内核的开发,或者说因为 SJW 成员们的加入,情况会变得更糟?
|
||||
|
||||
在 FOSS 里我们没有行为准则,不过我们都会持着文明友好的态度讨论问题。
|
||||
|
||||
via: https://itsfoss.com/linux-code-of-conduct/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[thecyanbird](https://github.com/thecyanbird)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[1]: https://itsfoss.com/torvalds-takes-a-break-from-linux/
|
||||
[2]: https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/tree/Documentation/CodeOfConflict?id=ddbd2b7ad99a418c60397901a0f3c997d030c65e
|
||||
[3]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/linus-torvalds-apologizes.jpeg
|
||||
[4]: https://lkml.org/lkml/2018/9/16/167
|
||||
[5]: https://www.contributor-covenant.org/version/1/4/code-of-conduct.html
|
||||
[6]: https://www.contributor-covenant.org/adopters
|
||||
[7]: https://en.wikipedia.org/wiki/Coraline_Ada_Ehmke
|
||||
[8]: https://en.wikipedia.org/wiki/LGBT
|
||||
[9]: https://en.wikipedia.org/wiki/Meritocracy
|
||||
[10]: https://modelviewculture.com/pieces/the-dehumanizing-myth-of-the-meritocracy
|
||||
[11]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/croraline-meritocracy.jpg
|
||||
[12]: https://pbs.twimg.com/media/DnTTfi7XoAAdk08.jpg
|
||||
[13]: https://arstechnica.com/information-technology/2015/01/linus-torvalds-on-why-he-isnt-nice-i-dont-care-about-you/
|
||||
[14]: https://opalrb.com/
|
||||
[15]: https://twitter.com/krainboltgreene/status/611569515315507200
|
||||
[16]: https://github.com/opal/opal/issues/941
|
||||
[17]: https://github.com/opal/opal/pull/948/commits/817321e27eccfffb3841f663815c17eecb8ef061#diff-a1ee87dafebc22cbd96979f1b2b7e837R11
|
||||
[18]: https://github.com/opal/opal/pull/948#issuecomment-113486020
|
||||
[19]: https://www.reddit.com/r/linux/comments/9go8cp/linus_torvalds_daughter_has_signed_the/
|
||||
[20]: https://snew.github.io/r/linux/comments/9ghrrj/linuxs_new_coc_is_a_piece_of_shit/
|
||||
[21]: https://t.co/eFeY6r4ENv
|
||||
[22]: https://twitter.com/CoralineAda/status/1041441155874009093?ref_src=twsrc%5Etfw
|
||||
[23]: https://twitter.com/CoralineAda/status/1041465346656530432?ref_src=twsrc%5Etfw
|
||||
[24]: https://t.co/8NUL2K1gu2
|
||||
[25]: https://twitter.com/nickmon1112/status/1041668315947708416?ref_src=twsrc%5Etfw
|
||||
[26]: https://www.urbandictionary.com/define.php?term=SJW
|
||||
[27]: https://twitter.com/Grummz/status/1041524170331287552?ref_src=twsrc%5Etfw
|
||||
[28]: https://twitter.com/jfrappier/status/1041486055038492674?ref_src=twsrc%5Etfw
|
||||
[29]: https://twitter.com/justkelly_ok/status/1041522269002985473?ref_src=twsrc%5Etfw
|
||||
[30]: https://twitter.com/maria_fibonacci/status/1041538148121997313?ref_src=twsrc%5Etfw
|
||||
[31]: https://www.networkworld.com/article/2988850/opensource-subnet/linux-kernel-dev-sarah-sharp-quits-citing-brutal-communications-style.html
|
||||
[32]: https://twitter.com/_sagesharp_/status/1041480963287539712?ref_src=twsrc%5Etfw
|
||||
[33]: https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=8a104f8b5867c682d994ffa7a74093c54469c11f
|
||||
@ -0,0 +1,199 @@
|
||||
如何创建和维护你的Man手册
|
||||
======
|
||||
|
||||

|
||||
|
||||
我们已经讨论了一些[Man手册的替代方案] [1]。 这些替代方案主要用于学习简洁的Linux命令示例,而无需通过全面过于详细的手册页。 如果你正在寻找一种快速而简单的方法来轻松快速地学习Linux命令,那么这些替代方案值得尝试。 现在,你可能正在考虑 - 如何为Linux命令创建自己的man-like帮助页面? 这时**“Um”**就派上用场了。 Um是一个命令行实用程序,用于轻松创建和维护包含你到目前为止所了解的所有命令的Man页面。
|
||||
|
||||
通过创建自己的手册页,你可以在手册页中避免大量不必要的细节,并且只包含你需要记住的内容。 如果你想创建自己的一套man-like页面,“Um”也能为你提供帮助。 在这个简短的教程中,我们将学习如何安装“Um”命令以及如何创建自己的man手册页。
|
||||
|
||||
### 安装 Um
|
||||
|
||||
Um适用于Linux和Mac OS。 目前,它只能在Linux系统中使用** Linuxbrew **软件包管理器来进行安装。 如果你尚未安装Linuxbrew,请参考以下链接。
|
||||
|
||||
安装Linuxbrew后,运行以下命令安装Um实用程序。
|
||||
|
||||
```
|
||||
$ brew install sinclairtarget/wst/um
|
||||
|
||||
```
|
||||
|
||||
如果你会看到类似下面的输出,恭喜你! Um已经安装好并且可以使用了。
|
||||
|
||||
```
|
||||
[...]
|
||||
==> Installing sinclairtarget/wst/um
|
||||
==> Downloading https://github.com/sinclairtarget/um/archive/4.0.0.tar.gz
|
||||
==> Downloading from https://codeload.github.com/sinclairtarget/um/tar.gz/4.0.0
|
||||
-=#=# # #
|
||||
==> Downloading https://rubygems.org/gems/kramdown-1.17.0.gem
|
||||
######################################################################## 100.0%
|
||||
==> gem install /home/sk/.cache/Homebrew/downloads/d0a5d978120a791d9c5965fc103866815189a4e3939
|
||||
==> Caveats
|
||||
Bash completion has been installed to:
|
||||
/home/linuxbrew/.linuxbrew/etc/bash_completion.d
|
||||
==> Summary
|
||||
[] /home/linuxbrew/.linuxbrew/Cellar/um/4.0.0: 714 files, 1.3MB, built in 35 seconds
|
||||
==> Caveats
|
||||
==> openssl
|
||||
A CA file has been bootstrapped using certificates from the SystemRoots
|
||||
keychain. To add additional certificates (e.g. the certificates added in
|
||||
the System keychain), place .pem files in
|
||||
/home/linuxbrew/.linuxbrew/etc/openssl/certs
|
||||
|
||||
and run
|
||||
/home/linuxbrew/.linuxbrew/opt/openssl/bin/c_rehash
|
||||
==> ruby
|
||||
Emacs Lisp files have been installed to:
|
||||
/home/linuxbrew/.linuxbrew/share/emacs/site-lisp/ruby
|
||||
==> um
|
||||
Bash completion has been installed to:
|
||||
/home/linuxbrew/.linuxbrew/etc/bash_completion.d
|
||||
|
||||
```
|
||||
|
||||
在制作你的man手册页之前,你需要为Um启用bash补全。
|
||||
|
||||
要开启bash'补全,首先你需要打开 **~/.bash_profile** 文件:
|
||||
|
||||
```
|
||||
$ nano ~/.bash_profile
|
||||
|
||||
```
|
||||
|
||||
并在其中添加以下内容:
|
||||
|
||||
```
|
||||
if [ -f $(brew --prefix)/etc/bash_completion.d/um-completion.sh ]; then
|
||||
. $(brew --prefix)/etc/bash_completion.d/um-completion.sh
|
||||
fi
|
||||
|
||||
```
|
||||
|
||||
保存并关闭文件。运行以下命令以更新更改。
|
||||
|
||||
```
|
||||
$ source ~/.bash_profile
|
||||
|
||||
```
|
||||
|
||||
准备工作全部完成。让我们继续创建我们的第一个man手册页。
|
||||
|
||||
|
||||
### 创建并维护自己的Man手册
|
||||
|
||||
如果你想为“dpkg”命令创建自己的Man手册。请运行:
|
||||
|
||||
```
|
||||
$ um edit dpkg
|
||||
|
||||
```
|
||||
|
||||
上面的命令将在默认编辑器中打开markdown模板:
|
||||
|
||||

|
||||
|
||||
我的默认编辑器是Vi,因此上面的命令会在Vi编辑器中打开它。现在,开始在此模板中添加有关“dpkg”命令的所有内容。
|
||||
|
||||
下面是一个示例:
|
||||
|
||||

|
||||
|
||||
正如你在上图的输出中看到的,我为dpkg命令添加了概要,描述和两个参数选项。 你可以在Man手册中添加你所需要的所有部分。不过你也要确保为每个部分提供了适当且易于理解的标题。 完成后,保存并退出文件(如果使用Vi编辑器,请按ESC键并键入:wq)。
|
||||
|
||||
最后,使用以下命令查看新创建的Man手册页:
|
||||
|
||||
```
|
||||
$ um dpkg
|
||||
|
||||
```
|
||||
|
||||

|
||||
|
||||
如你所见,dpkg的Man手册页看起来与官方手册页完全相同。 如果要在手册页中编辑和/或添加更多详细信息,请再次运行相同的命令并添加更多详细信息。
|
||||
|
||||
```
|
||||
$ um edit dpkg
|
||||
|
||||
```
|
||||
|
||||
要使用Um查看新创建的Man手册页列表,请运行:
|
||||
|
||||
```
|
||||
$ um list
|
||||
|
||||
```
|
||||
|
||||
所有手册页将保存在主目录中名为**`.um` **的目录下
|
||||
|
||||
以防万一,如果你不想要某个特定页面,只需删除它,如下所示。
|
||||
|
||||
```
|
||||
$ um rm dpkg
|
||||
|
||||
```
|
||||
|
||||
要查看帮助部分和所有可用的常规选项,请运行:
|
||||
|
||||
```
|
||||
$ um --help
|
||||
usage: um <page name>
|
||||
um <sub-command> [ARGS...]
|
||||
|
||||
The first form is equivalent to `um read <page name>`.
|
||||
|
||||
Subcommands:
|
||||
um (l)ist List the available pages for the current topic.
|
||||
um (r)ead <page name> Read the given page under the current topic.
|
||||
um (e)dit <page name> Create or edit the given page under the current topic.
|
||||
um rm <page name> Remove the given page.
|
||||
um (t)opic [topic] Get or set the current topic.
|
||||
um topics List all topics.
|
||||
um (c)onfig [config key] Display configuration environment.
|
||||
um (h)elp [sub-command] Display this help message, or the help message for a sub-command.
|
||||
|
||||
```
|
||||
|
||||
### 配置 Um
|
||||
|
||||
要查看当前配置,请运行:
|
||||
|
||||
```
|
||||
$ um config
|
||||
Options prefixed by '*' are set in /home/sk/.um/umconfig.
|
||||
editor = vi
|
||||
pager = less
|
||||
pages_directory = /home/sk/.um/pages
|
||||
default_topic = shell
|
||||
pages_ext = .md
|
||||
|
||||
```
|
||||
|
||||
在此文件中,你可以根据需要编辑和更改** pager **,** editor **,** default_topic **,** pages_directory **和** pages_ext **选项的值。 比如说,如果你想在** [Dropbox] [2] **文件夹中保存新创建的Um页面,只需更改/.um/umconfig**文件中** pages_directory **的值并将其更改为Dropbox文件夹即可。
|
||||
|
||||
```
|
||||
pages_directory = /Users/myusername/Dropbox/um
|
||||
|
||||
```
|
||||
|
||||
这就是全部内容,希望这些能对你有用,更多好的内容敬请关注!
|
||||
|
||||
干杯!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/how-to-create-and-maintain-your-own-man-pages/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972][b]
|
||||
译者:[way-ww](https://github.com/way-ww)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[b]: https://github.com/lujun9972
|
||||
[1]: https://www.ostechnix.com/3-good-alternatives-man-pages-every-linux-user-know/
|
||||
[2]: https://www.ostechnix.com/install-dropbox-in-ubuntu-18-04-lts-desktop/
|
||||
Loading…
Reference in New Issue
Block a user