mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-21 02:10:11 +08:00
commit
1e48c7cc5d
@ -1,19 +1,19 @@
|
||||
Square 2.0图标包更漂亮了
|
||||
更漂亮的 Square 2.0图标包
|
||||
================================================================================
|
||||

|
||||
|
||||
优雅、现代的[Square图标主题][1]最近更新到了2.0版,这让它比以前更漂亮了。Square图标包与其他主要的桌面环境如**Unity、 GNOME、KDE、 MATE等等**兼容。这意味着你可以在所有的流行Linux发行版如Ubuntu、Fedora、Linux Mint、elementary OS等等中使用它。 这个图标包估计包含超过了15000个图标。
|
||||
优雅、现代的[Square图标主题][1]最近更新到了2.0版,它比以前更漂亮了。Square图标包与其他主要的桌面环境如**Unity、 GNOME、KDE、 MATE等等**兼容。这意味着你可以在所有的流行Linux发行版如Ubuntu、Fedora、Linux Mint、elementary OS等等中使用它。 这个图标包估计包含超过了15000个图标。
|
||||
|
||||
### 在Linux中安装Square 2.0图标包 ###
|
||||
|
||||
有两种不同的Square图标,暗色和亮色。基于你的洗好,你可以选择二者之一。出于实验,我建议你两个主题包都下载。
|
||||
有两种不同的Square图标,暗色和亮色。基于你的喜好,你可以选择二者之一。出于体验的目的,我建议你两个主题包都下载。
|
||||
|
||||
你可以用下面的链接下载图标包。文件存储在Google Drive,因此如果你没有看见像[SourceForge][2]这样标准的下载网站时怀疑。
|
||||
你可以用下面的链接下载图标包。文件存储在Google Drive,因此如果你没有看见像[SourceForge][2]这样标准的下载网站时不要怀疑。
|
||||
|
||||
- [Square Dark Icons][3]
|
||||
- [Square Light Icons][4]
|
||||
|
||||
要使用图标主题,解压下载的文件到~/.icons文件夹下。如果它不存在,就创建它。当你在正确的地方有这些文件后,基于你的桌面环境,使用一个工具来改变图标主题。我以前写了一些关于这个主题的教程。如果你需要额外的帮助,那么欢迎指出来:
|
||||
要使用图标主题,解压下载的文件到~/.icons文件夹下。如果它不存在,就创建它。当这些文件放好后,基于你的桌面环境,使用一个工具来改变图标主题。我以前写了一些关于这个主题的教程。如果你需要额外的帮助,那么欢迎指出来:
|
||||
|
||||
- [如何在Ubuntu Unity中改变主题][5]
|
||||
- [如何在GNOME Shell中改变主题][6]
|
||||
@ -30,8 +30,7 @@ Square主题中几个图标的样子:
|
||||
|
||||

|
||||
|
||||
你怎么找到它的?你认为它是[Ubuntu 14.04中最佳的图标主题][10]之一么?你会分享它病期待更多关于自定义Linux桌面的文章么?
|
||||
|
||||
你觉得怎么样?你认为它是[Ubuntu 14.04中最佳的图标主题][10]之一么?你会分享它并期待更多关于自定义Linux桌面的文章么?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -39,7 +38,7 @@ via: http://itsfoss.com/square-2-0-icon-pack-linux/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,10 +1,10 @@
|
||||
使用 SSH 和一次性密码安全登录 Linux
|
||||
使用一次性密码本通过 SSH 安全登录 Linux
|
||||
================================================================================
|
||||
有人说,安全不是一个产品,而是一个过程(LCTT 注:安全公司 McAfee 认为,安全风险管理是一个方法论,而不是安全产品的堆叠)。虽然 SSH 协议被设计成使用加密技术来确保安全,但如果使用不当,别人还是能够破坏你的系统:比如弱密码、密钥泄露、使用的 SSH 客户端过时等,都能引发安全问题。
|
||||
有人说,安全不是一个产品,而是一个过程(LCTT 注:安全公司 McAfee 认为,安全风险管理是一个方法论,而不是安全产品的堆叠)。虽然 SSH 协议被设计成使用加密技术来确保安全,但如果使用不当,别人还是能够破坏你的系统:比如弱密码、密钥泄露、使用过时的 SSH 客户端等,都能引发安全问题。
|
||||
|
||||
在考虑 SSH 认证方案时,大家普遍认为[公钥认证][1]比密码认证更安全。然而,公钥认证技术并不是为公共环境设置的,如果你在一台公用电脑上使用公钥认证登录 SSH 服务器,你的服务器已经毫无安全可言了,公用的电脑可能会记录你的公钥,或从你的内存中读取公钥。如果你不信任本地电脑,那你最好还是使用其他方式登录服务器。现在就是“一次性密码”派上用场的时候了,就像名字所示,一次性密码只能被使用一次。这种一次性密码非常合适在不安全的环境下发挥作用,就算它被窃取,也无法再次使用。
|
||||
在考虑 SSH 认证方案时,大家普遍认为[公钥认证][1]比密码认证更安全。然而,公钥认证技术并不是为公共环境设置的,如果你在一台公用电脑上使用公钥认证登录 SSH 服务器,你的服务器已经毫无安全可言了,公用的电脑可能会记录你的公钥,或从你的内存中读取公钥。如果你不信任本地电脑,那你最好还是使用其他方式登录服务器。现在就是“一次性密码(OTP)”派上用场的时候了,就像名字所示,一次性密码只能被使用一次。这种一次性密码非常合适在不安全的环境下发挥作用,就算它被窃取,也无法再次使用。
|
||||
|
||||
有个一次性密码方案叫[谷歌认证][2],但在本文中,我要介绍的是另一种 SSH 登录方案:[OTPW][3],它是个一次性密码登录的软件包。不像谷歌认证,OTPW 不需要依赖任何第三方库。
|
||||
有个生成一次性密码的方法是通过[谷歌认证器][2],但在本文中,我要介绍的是另一种 SSH 登录方案:[OTPW][3],它是个一次性密码登录的软件包。不像谷歌认证,OTPW 不需要依赖任何第三方库。
|
||||
|
||||
### OTPW 是什么 ###
|
||||
|
||||
@ -39,7 +39,7 @@ OTPW 由一次性密码生成器和 PAM 认证规则组成。在 OTPW 中一次
|
||||
$ git clone https://www.cl.cam.ac.uk/~mgk25/git/otpw
|
||||
$ cd otpw
|
||||
|
||||
打开 Makefile 文件,编辑以“PAMLIB=”开头的那行配置:
|
||||
打开 Makefile 文件,编辑以“PAMLIB=”开头的那行配置:
|
||||
|
||||
64 位系统:
|
||||
|
||||
@ -49,12 +49,12 @@ OTPW 由一次性密码生成器和 PAM 认证规则组成。在 OTPW 中一次
|
||||
|
||||
PAMLIB=/usr/lib/security
|
||||
|
||||
编译安装。需要注意的是安装过程会把 SSH 服务重启一下,所以如果你是使用 SSH 连接到服务器,做好被断开连接的准备吧。
|
||||
编译安装。需要注意的是安装过程会自动重启 SSH 服务一下,所以如果你是使用 SSH 连接到服务器,做好被断开连接的准备吧(LCTT 译注:也许不会被断开连接,即便被断开连接,请使用原来的方式重新连接即可,现在还没有换成一次性口令方式。)。
|
||||
|
||||
$ make
|
||||
$ sudo make install
|
||||
|
||||
现在你需要更新 SELinux 策略,因为 /usr/sbin/sshd 会往你的 home 目录写数据,而 SELinux 默认是不允许这么做的。如果你使用了 SELinux 服务(LCTT 注:使用 getenforce 命令查看结果,如果是 enforcing,就是打开了 SELinux 服务),如果没有使用 SELinux 服务,请跳过这一步。
|
||||
现在你需要更新 SELinux 策略,因为 /usr/sbin/sshd 会往你的 home 目录写数据,而 SELinux 默认是不允许这么做的。如果没有使用 SELinux 服务(LCTT 注:使用 getenforce 命令查看结果,如果是 enforcing,就是打开了 SELinux 服务),请跳过这一步。
|
||||
|
||||
$ sudo grep sshd /var/log/audit/audit.log | audit2allow -M mypol
|
||||
$ sudo semodule -i mypol.pp
|
||||
@ -90,6 +90,8 @@ Debian, Ubuntu 或 Linux Mint 发行版:
|
||||
Fedora 或 CentOS/RHEL 7 发行版:
|
||||
|
||||
$ sudo systemctl restart sshd
|
||||
|
||||
(LCTT 译注:虽然这里重启了 sshd 服务,但是你当前的 ssh 连接应该不受影响,只是在你完成下述步骤之前,无法按照原有方式建立新的连接了。因此,保险起见,要么多开一个 ssh 连接,避免误退出当前连接;要么将重启 sshd 服务器步骤放到步骤3完成之后。)
|
||||
|
||||
#### 步骤3:使用 OTPW 产生一次性密码 ####
|
||||
|
||||
@ -102,7 +104,7 @@ Fedora 或 CentOS/RHEL 7 发行版:
|
||||
|
||||
这个命令会让你输入密码前缀,当你以后登录的时候,你需要同时输入这个前缀以及一次性密码。密码前缀是另外一层保护,就算你的一次性密码表被泄漏,别人也无法通过暴力破解你的 SSH 密码。
|
||||
|
||||
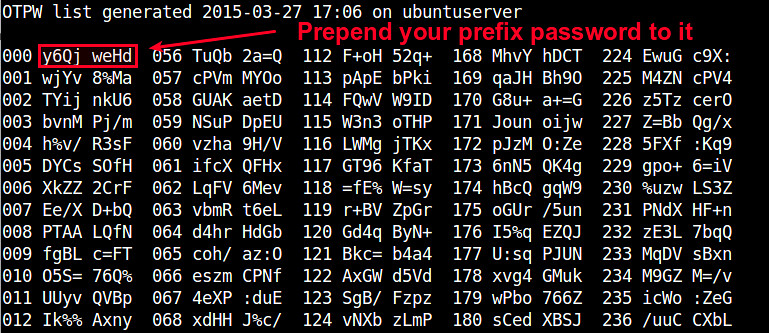
设置好密码前缀后,这个命令会产生 280 个一次性密码,并将它们保存在一个文本文件中(如 temporary_password.txt)。每个密码(默认是 8 个字符)由一个 3 位十进制数索引。你需要将这个密码表打印出来,并随身携带。
|
||||
设置好密码前缀后,这个命令会产生 280 个一次性密码(LCTT 译注:保存到 ~/.otpw 下),并将它们导出到一个文本文件中(如 temporary_password.txt)。每个密码(默认是 8 个字符)由一个 3 位十进制数索引。你需要将这个密码表打印出来,并随身携带。
|
||||
|
||||
|
||||
|
||||
@ -160,7 +162,7 @@ Fedora 或 CentOS/RHEL 7 发行版:
|
||||
|
||||
### 总结 ###
|
||||
|
||||
在这个教程中,我介绍了如何使用 OTPW 工具来设置一次性登录密码。你也许意识到了在这种两个因子的认证方式中,打印一张密码表让人感觉好 low,但是这种方式是最简单的,并且不用依赖任何第三方软件。无论你用哪种方式创建一次性密码,在你需要在一个不被信任的环境登录 SSH 服务器的时候,它们都很有用。你可以就这个主题来分享你的经验和观点。
|
||||
在这个教程中,我介绍了如何使用 OTPW 工具来设置一次性登录密码。你也许意识到了在这种双因子的认证方式中,打印一张密码表让人感觉好 low,但是这种方式是最简单的,并且不用依赖任何第三方软件。无论你用哪种方式创建一次性密码,在你需要在一个不可信任的环境登录 SSH 服务器的时候,它们都很有用。你可以就这个主题来分享你的经验和观点。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -168,11 +170,11 @@ via: http://xmodulo.com/secure-ssh-login-one-time-passwords-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[bazz2](https://github.com/bazz2)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/how-to-force-ssh-login-via-public-key-authentication.html
|
||||
[2]:http://xmodulo.com/two-factor-authentication-ssh-login-linux.html
|
||||
[1]:https://linux.cn/article-5444-1.html
|
||||
[2]:https://linux.cn/article-2642-1.html
|
||||
[3]:http://www.cl.cam.ac.uk/~mgk25/otpw.html
|
||||
@ -1,22 +1,26 @@
|
||||
如何在 CentOS Linux 中配置 MariADB 复制
|
||||
如何在 CentOS Linux 中配置 MariaDB 复制
|
||||
================================================================================
|
||||
这是一个创建数据库重复版本的过程。复制过程不仅仅是复制一个数据库,同时也包括从主节点到一个从节点的更改同步。但这并不意味着从数据库就是和主数据库完全相同的副本,因为复制可以配置为只有表或者行或者列的一个模式将被复制,例如,局部复制。复制保证了特定的配置对象在不同的数据库之间保持同步。
|
||||
这是一个创建数据库重复版本的过程。复制过程不仅仅是复制一个数据库,同时也包括从主节点到一个从节点的更改同步。但这并不意味着从数据库就是和主数据库完全相同的副本,因为复制可以配置为只复制表结构、行或者列,这叫做局部复制。复制保证了特定的配置对象在不同的数据库之间保持一致。
|
||||
|
||||
### Mariadb 复制概念 ###
|
||||
|
||||
**备份** :复制可以用来进行数据库备份。例如,你有主->从复制。如果主节点丢失(比如hdd损坏),你可以从从节点中恢复你的数据库。
|
||||
**备份** :复制可以用来进行数据库备份。例如,当你做了主->从复制。如果主节点数据丢失(比如硬盘损坏),你可以从从节点中恢复你的数据库。
|
||||
|
||||
**扩展** :你可以使用主->从复制作为扩展的解决方案。例如,如果你有一些大的数据库以及SQL查询,使用复制你可以将这些查询单独分到每个复制节点。写SQL应该只在主节点进行,而只读查询可以在从节点上进行。
|
||||
**扩展** :你可以使用主->从复制作为扩展解决方案。例如,如果你有一些大的数据库以及SQL查询,使用复制你可以将这些查询分离到每个复制节点。写入操作的SQL应该只在主节点进行,而只读查询可以在从节点上进行。
|
||||
|
||||
**传播解决方案** :你可以用复制来进行分发。例如,你可以将不同的销售数据分发到不同的数据库。
|
||||
**分发解决方案** :你可以用复制来进行分发。例如,你可以将不同的销售数据分发到不同的数据库。
|
||||
|
||||
**故障解决方案** : 假如你有主节点->从节点1->从节点2->从节点3的复制。你可以为主节点写脚本监控,如果主节点出故障了,脚本可以快速的将从节点1作为新的主节点,有主节点->从节点1->从节点2,你的应用可以继续工作而不会停机。
|
||||
**故障解决方案** : 假如你建立有主节点->从节点1->从节点2->从节点3的复制结构。你可以为主节点写脚本监控,如果主节点出故障了,脚本可以快速的将从节点1切换为新的主节点,这样复制结构变成了主节点->从节点1->从节点2,你的应用可以继续工作而不会停机。
|
||||
|
||||
### 复制的简单图解示范 ###
|
||||
|
||||

|
||||
|
||||
开始之前,你应该知道什么是**二进制日志文件**以及 Ibdata1。二进制日志文件中包括关于数据库,数据和结构的所有更改的记录,以及每条语句的执行时间。二进制日志文件包括设置日志文件和一个索引。这意味着主要的SQL语句,例如CREATE, ALTER, INSERT, UPDATE 和 DELETE 会放到这个日志文件中,而例如SELECT语句就不会被记录。这些信息可以被记录到普通的query.log文件。简单的说 **Ibdata1** 是一个包括所有表和所有数据库信息的文件。
|
||||
开始之前,你应该知道什么是**二进制日志文件**以及 Ibdata1。
|
||||
|
||||
二进制日志文件中包括关于数据库,数据和结构的所有更改的记录,以及每条语句的执行了多长时间。二进制日志文件包括一系列日志文件和一个索引文件。这意味着主要的SQL语句,例如CREATE, ALTER, INSERT, UPDATE 和 DELETE 会放到这个日志文件中;而例如SELECT这样的语句就不会被记录,它们可以被记录到普通的query.log文件中。
|
||||
|
||||
而 **Ibdata1** 简单的说据是一个包括所有表和所有数据库信息的文件。
|
||||
|
||||
### 主服务器配置 ###
|
||||
|
||||
@ -39,7 +43,7 @@
|
||||
sudo systemctl start mariadb.service
|
||||
sudo systemctl enable mariadb.service
|
||||
|
||||
输出:
|
||||
输出如下:
|
||||
|
||||
ln -s '/usr/lib/systemd/system/mariadb.service' '/etc/systemd/system/multi-user.target.wants/mariadb.service'
|
||||
|
||||
@ -51,7 +55,7 @@
|
||||
|
||||
sudo systemctl is-active mariadb.service
|
||||
|
||||
输出:
|
||||
输出如下:
|
||||
|
||||
Redirecting to /bin/systemctl status mariadb.service
|
||||
mariadb.service - MariaDB database server
|
||||
@ -65,11 +69,11 @@
|
||||
mysql> flush privileges;
|
||||
mysql> exit
|
||||
|
||||
SOME_ROOT_PASSWORD - 你的 root 密码。 例如我用"q"作为密码,然后尝试登陆:
|
||||
这里 SOME_ROOT_PASSWORD 是你的 root 密码。 例如我用"q"作为密码,然后尝试登录:
|
||||
|
||||
sudo mysql -u root -pSOME_ROOT_PASSWORD
|
||||
|
||||
输出:
|
||||
输出如下:
|
||||
|
||||
Welcome to the MariaDB monitor. Commands end with ; or \g.
|
||||
Your MariaDB connection id is 5
|
||||
@ -89,7 +93,7 @@ SOME_ROOT_PASSWORD - 你的 root 密码。 例如我用"q"作为密码,然后
|
||||
|
||||
test_repl - 将要被复制的模式的名字
|
||||
|
||||
输出:
|
||||
输出:如下
|
||||
|
||||
Query OK, 1 row affected (0.00 sec)
|
||||
|
||||
@ -105,7 +109,7 @@ SOME_ROOT_PASSWORD - 你的 root 密码。 例如我用"q"作为密码,然后
|
||||
City varchar(255)
|
||||
);
|
||||
|
||||
输出:
|
||||
输出如下:
|
||||
|
||||
mysql> MariaDB [test_repl]> CREATE TABLE Persons (
|
||||
-> PersonID int,
|
||||
@ -124,7 +128,7 @@ SOME_ROOT_PASSWORD - 你的 root 密码。 例如我用"q"作为密码,然后
|
||||
mysql> INSERT INTO Persons VALUES (4, "LastName4", "FirstName4", "Address4", "City4");
|
||||
mysql> INSERT INTO Persons VALUES (5, "LastName5", "FirstName5", "Address5", "City5");
|
||||
|
||||
输出:
|
||||
输出如下:
|
||||
|
||||
Query OK, 5 row affected (0.00 sec)
|
||||
|
||||
@ -132,7 +136,7 @@ SOME_ROOT_PASSWORD - 你的 root 密码。 例如我用"q"作为密码,然后
|
||||
|
||||
mysql> select * from Persons;
|
||||
|
||||
输出:
|
||||
输出如下:
|
||||
|
||||
+----------+-----------+------------+----------+-------+
|
||||
| PersonID | LastName | FirstName | Address | City |
|
||||
@ -145,9 +149,9 @@ SOME_ROOT_PASSWORD - 你的 root 密码。 例如我用"q"作为密码,然后
|
||||
| 5 | LastName5 | FirstName5 | Address5 | City5 |
|
||||
+----------+-----------+------------+----------+-------+
|
||||
|
||||
### 配置 MariaDB 重复 ###
|
||||
### 配置 MariaDB 复制 ###
|
||||
|
||||
你需要在主结点服务器上编辑 my.cnf文件来启用二进制日志以及设置服务器id。我会使用vi文本编辑器,但你可以使用任何你喜欢的,例如nano,joe。
|
||||
你需要在主节点服务器上编辑 my.cnf文件来启用二进制日志以及设置服务器id。我会使用vi文本编辑器,但你可以使用任何你喜欢的,例如nano,joe。
|
||||
|
||||
sudo vi /etc/my.cnf
|
||||
|
||||
@ -159,7 +163,7 @@ SOME_ROOT_PASSWORD - 你的 root 密码。 例如我用"q"作为密码,然后
|
||||
binlog-format=row
|
||||
server_id=1
|
||||
|
||||
输出:
|
||||
输出如下:
|
||||
|
||||

|
||||
|
||||
@ -173,7 +177,7 @@ sudo mysql -u root -pq test_repl
|
||||
|
||||
mysql> SHOW MASTER STATUS;
|
||||
|
||||
输出:
|
||||
输出如下:
|
||||
|
||||
+--------------------+----------+--------------+------------------+
|
||||
| File | Position | Binlog_Do_DB | Binlog_Ignore_DB |
|
||||
@ -183,12 +187,12 @@ mysql> SHOW MASTER STATUS;
|
||||
|
||||
**记住** : "File" 和 "Position" 的值。在从节点中你需要使用这些值
|
||||
|
||||
创建用来重复的用户
|
||||
创建用来复制的用户
|
||||
|
||||
mysql> GRANT REPLICATION SLAVE ON *.* TO replication_user IDENTIFIED BY 'bigs3cret' WITH GRANT OPTION;
|
||||
mysql> flush privileges;
|
||||
|
||||
输出:
|
||||
输出如下:
|
||||
|
||||
Query OK, 0 rows affected (0.00 sec)
|
||||
Query OK, 0 rows affected (0.00 sec)
|
||||
@ -197,7 +201,7 @@ mysql> SHOW MASTER STATUS;
|
||||
|
||||
mysql> select * from mysql.user WHERE user="replication_user"\G;
|
||||
|
||||
输出:
|
||||
输出如下:
|
||||
|
||||
mysql> select * from mysql.user WHERE user="replication_user"\G;
|
||||
*************************** 1. row ***************************
|
||||
@ -220,11 +224,11 @@ mysql> SHOW MASTER STATUS;
|
||||
|
||||
### 从节点配置 ###
|
||||
|
||||
所有这些命令需要在从节点中进行
|
||||
所有这些命令需要在从节点中进行。
|
||||
|
||||
假设我们已经更新/升级了包括有最新的MariaDB服务器的 CentOS 7.x,而且你可以用root账号登陆到MariaDBs服务器(这在这篇文章的第一部分已经介绍过)
|
||||
假设我们已经更新/升级了包括有最新的MariaDB服务器的 CentOS 7.x,而且你可以用root账号登陆到MariaDB服务器(这在这篇文章的第一部分已经介绍过)
|
||||
|
||||
登陆到Maria 数据库控制台并创建数据库
|
||||
登录到Maria 数据库控制台并创建数据库
|
||||
|
||||
mysql -u root -pSOME_ROOT_PASSWORD;
|
||||
mysql> create database test_repl;
|
||||
@ -264,7 +268,7 @@ full-dump.sql - 你在测试服务器中创建的DB Dump。
|
||||
|
||||
mysql> slave start;
|
||||
|
||||
输出:
|
||||
输出如下:
|
||||
|
||||
Query OK, 0 rows affected (0.00 sec)
|
||||
|
||||
@ -272,7 +276,7 @@ full-dump.sql - 你在测试服务器中创建的DB Dump。
|
||||
|
||||
mysql> show slave status\G;
|
||||
|
||||
输出:
|
||||
输出如下:
|
||||
|
||||
*************************** 1. row ***************************
|
||||
Slave_IO_State: Waiting for master to send event
|
||||
@ -352,7 +356,7 @@ via: http://linoxide.com/how-tos/configure-mariadb-replication-centos-linux/
|
||||
|
||||
作者:[Bobbin Zachariah][a]
|
||||
译者:[ictlyh](https://github.com/ictlyh)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,26 @@
|
||||
微软开源了WCF框架
|
||||
================================================================================
|
||||
微软于今日(2015/5/20)宣布了针对 .NET Core 重大开源:WCF(Windows Communication Foundation)。
|
||||
|
||||
如[MSDN][1]中的描述:“WCF是一个构建面向服务应用的框架。使用WCF,你可以从一个服务终端给另一个发送异步消息。服务终端可以是托管在IIS中连续可用的服务的一部分,也可以是托管在某个程序上的服务。服务终端可以是请求服务端数据的客户端。消息可以是一个字符或者XML,也可以是复杂的二进制流。”
|
||||
|
||||
它的[代码放在GitHub][2],“包含了Window桌面中完整WCF框架的一部分,它支持已经可用于构建Window Store上的WCF应用的库。这些主要是基于客户端,方便移动设备和中间层服务器使用WCF进行通信。”
|
||||
|
||||
更多的关于微软开源 WCF 的细节查看[dotNETFoundation.org blog][3]的公告。
|
||||
|
||||
WCF听上去有点像Linux中用于进程/服务之间的进程间通讯的D-BUS。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.phoronix.com/scan.php?page=news_item&px=Microsoft-Open-Source-WCF
|
||||
|
||||
作者:[Michael Larabel][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.michaellarabel.com/
|
||||
[1]:https://msdn.microsoft.com/en-us/library/ms731082%28v=vs.110%29.aspx
|
||||
[2]:https://github.com/dotnet/wcf
|
||||
[3]:http://www.dotnetfoundation.org/blog/wcf-is-open-source
|
||||
@ -1,26 +0,0 @@
|
||||
Microsoft Open-Sources The Windows Communication Foundation
|
||||
================================================================================
|
||||
Microsoft has today announced they've open-sourced the important WCF (Windows Communication Foundation) code that now targets .NET Core.
|
||||
|
||||
As described by [MSDN][1], "Windows Communication Foundation (WCF) is a framework for building service-oriented applications. Using WCF, you can send data as asynchronous messages from one service endpoint to another. A service endpoint can be part of a continuously available service hosted by IIS, or it can be a service hosted in an application. An endpoint can be a client of a service that requests data from a service endpoint. The messages can be as simple as a single character or word sent as XML, or as complex as a stream of binary data."
|
||||
|
||||
The [code on GitHub][2], "contains a subset of the full Windows Communication Foundation product available on the Windows desktop, and it supports the library profiles already available for building WCF apps for the Windows Store. These profiles are primarily client-based, making them suited for mobile devices or on mid-tier servers to communicate with existing WCF services."
|
||||
|
||||
More details on Microsoft opening up the Windows Communication Foundation can be found via the announcement posted this morning to the [dotNETFoundation.org blog][3].
|
||||
|
||||
Windows Communication Foundation sounds a bit like D-Bus on Linux for inter-process communication between programs/services.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.phoronix.com/scan.php?page=news_item&px=Microsoft-Open-Source-WCF
|
||||
|
||||
作者:[Michael Larabel][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.michaellarabel.com/
|
||||
[1]:https://msdn.microsoft.com/en-us/library/ms731082%28v=vs.110%29.aspx
|
||||
[2]:https://github.com/dotnet/wcf
|
||||
[3]:http://www.dotnetfoundation.org/blog/wcf-is-open-source
|
||||
@ -1,71 +0,0 @@
|
||||
This Ubuntu App Applies Instagram Style Filters to Your Photos
|
||||
================================================================================
|
||||
**Looking for an Ubuntu app to apply Instagram style filters to your photos in Ubuntu?**
|
||||
|
||||
Grab your selfie stick and step this way…
|
||||
|
||||

|
||||
XnRetro is a photo editing app
|
||||
|
||||
### XnRetro Photo Editor ###
|
||||
|
||||
**XnRetro** is a simple image editing application that lets you quickly add “Instagram like” effects to your photos.
|
||||
|
||||
You know the sort of effects I’m talking about: scratches, noises, and frames, over processing, vintage washes and nostalgic tints (because in this age of digital transience we must know that endless selfies and sandwich snaps are unlikely to ever become nostalgic of themselves).
|
||||
|
||||
Whether you consider such effects to be of asinine artistic value or shortcut to being creative, these kinds of filters are popular and can help add a splash of personality to an otherwise so-so photo.
|
||||
|
||||
#### XnRetro Features ####
|
||||
|
||||
**XnRetro features the following:**
|
||||
|
||||
- 20 color filters
|
||||
- 15 light effects (bokeh, leaks, etc)
|
||||
- 28 frames and borders
|
||||
- 5 Vignettes (with strength control)
|
||||
- Image adjustments for contrast, gamma, saturation, etc
|
||||
- Square crop option
|
||||
|
||||

|
||||
Small tweak to make light effects work
|
||||
|
||||
You can save edited images (in theory) as .jpg or .png files and share them straight to social media from within the app.
|
||||
|
||||
I say “in theory” because .jpg saving doesn’t actually work in the Linux version of the app (you can save edited images as .png files though). Similarly, most of the built-in social networking links are borked or just flat out fail on export.
|
||||
|
||||
To get the **15 light leaks** to work you will need to re-save each .jpg image in XnRetro ‘light’ folder as a .png file. Edit the ‘light.xml’ to match the new file names, hit save and the light effects will load up in XnRetro without issue.
|
||||
|
||||
> ‘For user-friendly image editing XnRetro is hard to beat — once you make it work.’
|
||||
|
||||
**Is XnRetro Worth Installing?**
|
||||
|
||||
XnRetro is not perfect. It’s is pretty old-looking, difficult to properly install and has not been updated for several years.
|
||||
|
||||
It does still work, barring .jpg saving, and is a nimble alternative to an advanced app like The Gimp or Shotwell’s set of ‘serious’ image adjustment tools.
|
||||
|
||||
While web apps and Chrome Apps¹ like [Pixlr Touch Up][1] and [Polarr][2] offer similar features you may be looking for a truly native solution.
|
||||
|
||||
And for that, for user-friendly image editing based around easy-to-apply filters, XnRetro is hard to beat.
|
||||
|
||||
### Download XnRetro for Ubuntu ###
|
||||
|
||||
XnRetro is not available as an installable .deb package. It is distributed as a binary file, meaning you need to double-click on the program file run it each and every time. It’s also 32-bit only.
|
||||
|
||||
You can download XnRetro using the link below. Once completed you need to extract the archive and enter the folder it creates. Double-click on the ‘xnretro’ program binary inside.
|
||||
|
||||
- [Download XnRetro for Linux (32bit, tar.gz)][3]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2015/05/instagram-photo-filters-ubuntu-desktop-app
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.omgchrome.com/?s=pixlr
|
||||
[2]:http://www.omgchrome.com/the-best-chrome-apps-of-2014/
|
||||
[3]:http://www.xnview.com/en/xnretro/#downloads
|
||||
@ -1,146 +0,0 @@
|
||||
translating by wwy-hust
|
||||
|
||||
How to share a directory with Samba on Fedora or CentOS
|
||||
================================================================================
|
||||
Nowadays sharing data across different computers is not something new at home or many work places. Riding on this trend, modern operating systems make it easy to share and exchange data transparently across computers via network file systems. If your work environment involves a mix of Microsoft Windows and Linux computers, one way to share files and folders among them is via SMB/CIFS, a cross-platform network file sharing protocol. Windows Microsoft natively supports SMB/CIFS, while Linux offers free software implementation of SMB/CIFS network protocol in Samba.
|
||||
|
||||
In this article, we will demonstrate **how to share a directory using Samba**. The Linux platform we will use is **Fedora or CentOS**. This article is dividied into four parts. First, we will install Samba under Fedora/CentOS environment. Next, we discuss how to adjust SELinux and firewall configurations to allow file sharing with Samba. Finally, we cover how to enable Samba to share a directory.
|
||||
|
||||
### Step One: Install Samba on Fedora or CentOS ###
|
||||
|
||||
First thing first. Let's install Samba and configure basic settings.
|
||||
|
||||
Check whether Samba application is already installed on your system by running:
|
||||
|
||||
$ rpm -q samba samba-common samba-client
|
||||
|
||||
If the above command doesn't show anything at all, it means that Samba is not installed. In that case, install Samba using the command below.
|
||||
|
||||
$ sudo yum install samba samba-common samba-client
|
||||
|
||||
Next, creates a local directory which will share data over network. This directory will be exported to remote users as a Samba share. In this tutorial, we will create this directory in the top-level directory '/', so make sure that you have the privileges to do it.
|
||||
|
||||
$ sudo mkdir /shared
|
||||
|
||||
If you want to create a shared directory inside your home directory (e.g., ~/shared), you must activate Samba home directory sharing in the SELinux options, which will be described below in more detail.
|
||||
|
||||
After creating /shared directory, set the privileges of the directory so other users can access it.
|
||||
|
||||
$ sudo chmod o+rw /shared
|
||||
|
||||
If you don't want other users to be able to have write to the directory, just remove the 'w' option in chmod command as follows.
|
||||
|
||||
$ sudo chmod o+r /shared
|
||||
|
||||
Next, create one empty file as a test. This file will be used to verify that he Samba share is mounted properly.
|
||||
|
||||
$ sudo touch /shared/file1
|
||||
|
||||
### Step Two: Configure SELinux for Samba ###
|
||||
|
||||
Next, we need to re-configure SELinux which is enabled by default in Fedora and CentOS distributions. SELinux allows Samba to read and modify files or directories only when they have the right security context (e.g., labeled with the 'samba_share_t' attribute).
|
||||
|
||||
The following command adds the necessary label to file-context configuration:
|
||||
|
||||
$ sudo semanage fcontext -a -t samba_share_t "<directory>(/.*)?"
|
||||
|
||||
Replace the <directory> with the local directory we created earlier for Samba share (e.g., /shared):
|
||||
|
||||
$ sudo semanage fcontext -a -t samba_share_t "/shared(/.*)?"
|
||||
|
||||
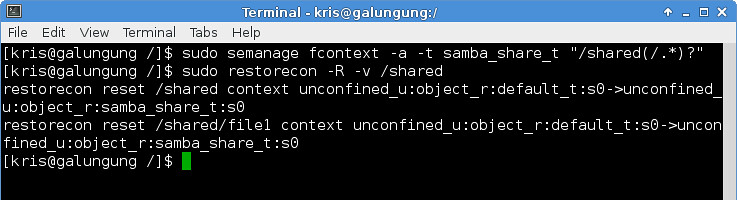
To activate the label change, we then must run the restorecon command like below.
|
||||
|
||||
$ sudo restorecon -R -v /shared
|
||||
|
||||
|
||||
|
||||
To share a directory inside our home directory via Samba, we must enable sharing home directory option in SELinux because it is disabled by default. The following command achieves the desired effect. Skip this step if you are not sharing your home directory.
|
||||
|
||||
$ sudo setsebool -P samba_enable_home_dirs 1
|
||||
|
||||
### Step Three: Configure Firewall for Samba ###
|
||||
|
||||
The next step is to open necessary TCP/UDP ports in the firewall settings for Samba to operate.
|
||||
|
||||
If you are using firewalld (e.g., on Fedora or CentOS 7), the following command will take care of permanent firewall rule change for Samba service.
|
||||
|
||||
$ sudo firewall-cmd --permanent --add-service=samba
|
||||
|
||||
If you are using iptables for your firewall (e.g., CentOS 6 or earlier), use the following commands to open up necessary Samba ports to the world.
|
||||
|
||||
$ sudo vi /etc/sysconfig/iptables
|
||||
|
||||
----------
|
||||
|
||||
-A RH-Firewall-1-INPUT -m state --state NEW -m tcp -p tcp --dport 445 -j ACCEPT
|
||||
-A RH-Firewall-1-INPUT -m state --state NEW -m udp -p udp --dport 445 -j ACCEPT
|
||||
-A RH-Firewall-1-INPUT -m state --state NEW -m udp -p udp --dport 137 -j ACCEPT
|
||||
-A RH-Firewall-1-INPUT -m state --state NEW -m udp -p udp --dport 138 -j ACCEPT
|
||||
-A RH-Firewall-1-INPUT -m state --state NEW -m tcp -p tcp --dport 139 -j ACCEPT
|
||||
|
||||
Then restart iptables service:
|
||||
|
||||
$ sudo service iptables restart
|
||||
|
||||
### Step Four: Change Samba Configuration ###
|
||||
|
||||
The last step is to configure Samba to export a created local directory as a Samba-share.
|
||||
|
||||
Open the Samba configuration file with a text editor, and add the following lines at the bottom of the file.
|
||||
|
||||
$ sudo nano /etc/samba/smb.conf
|
||||
|
||||
----------
|
||||
|
||||
[myshare]
|
||||
comment=my shared files
|
||||
path=/shared
|
||||
public=yes
|
||||
writeable=yes
|
||||
|
||||
In the above the text inside a pair of brackets (e.g., "myshare") is the name of the Samba-shared resource, which will be used to access the Samba share from a remote host.
|
||||
|
||||
Create a Samba user account which is required to mount and export the Samba file system. To create a Samba user, use the smbpasswd tool. Note that the Samba user account must be the same as any existing Linux user. If you try to add a non-existing user with smbpasswd, it will give an error message.
|
||||
|
||||
If you don't want to use any existing Linux user as a Samba user, you can create a new dedicated user in your system. For safety, set the new user's login shell to /sbin/nologin, and do not create its home directory.
|
||||
|
||||
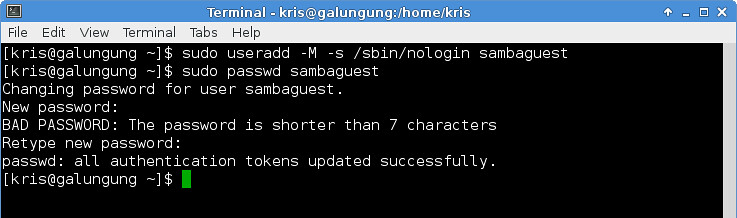
In this example, we are creating a new user named "sambaguest" as follows.
|
||||
|
||||
$ sudo useradd -M -s /sbin/nologin sambaguest
|
||||
$ sudo passwd sambaguest
|
||||
|
||||
|
||||
|
||||
After creating a new user, add the user as a Samba user using smbpasswd command. When this command asks a password, you can type a different password than the user's password.
|
||||
|
||||
$ sudo smbpasswd -a sambaguest
|
||||
|
||||
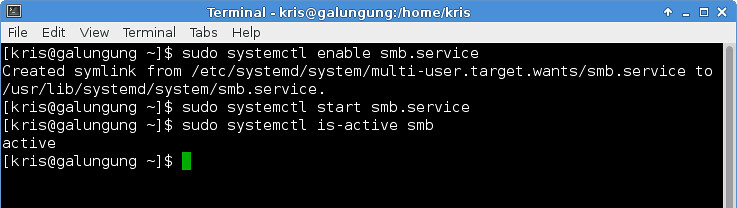
4. Activate the Samba service, and check whether the Samba service is running or not.
|
||||
|
||||
$ sudo systemctl enable smb.service
|
||||
$ sudo systemctl start smb.service
|
||||
$ sudo systemctl is-active smb
|
||||
|
||||
|
||||
|
||||
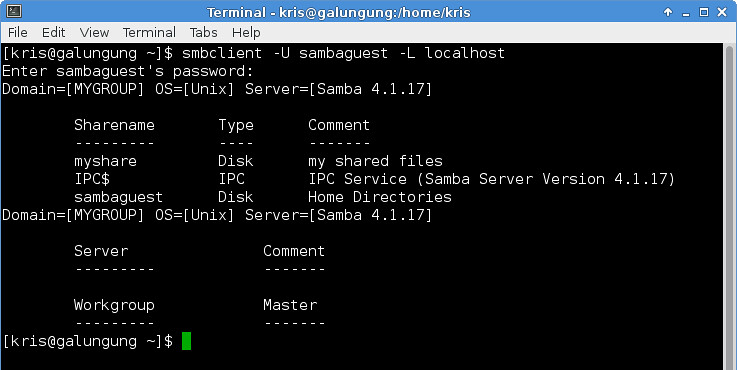
To see the list of shared directories in Samba, type the following command.
|
||||
|
||||
$ smbclient -U sambaguest -L localhost
|
||||
|
||||
|
||||
|
||||
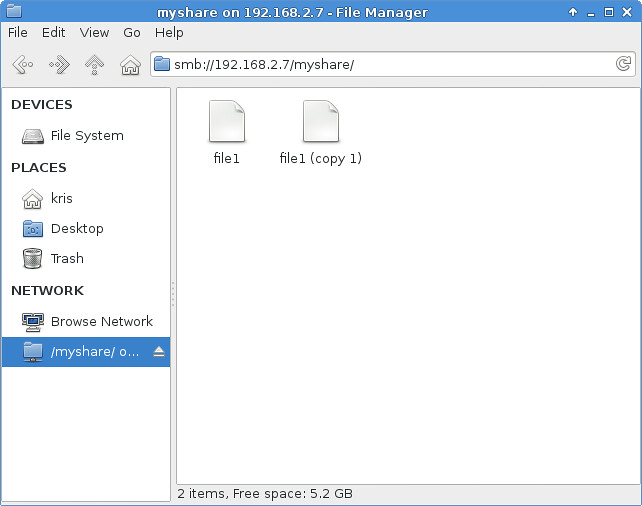
The following is a screenshot of accessing the Samba-shared directory on Thunar file manager, and doing copy-paste of file1. Note that the Samba share is accessible via "smb://<samba-server-IP-address>/myshare" address on Thunar.
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/share-directory-samba-fedora-centos.html
|
||||
|
||||
作者:[Kristophorus Hadiono][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/kristophorus
|
||||
@ -1,3 +1,5 @@
|
||||
FSSlc Translating
|
||||
|
||||
Sleuth Kit - Open Source Forensic Tool to Analyze Disk Images and Recover Files
|
||||
================================================================================
|
||||
SIFT is a Ubuntu based forensics distribution provided by SANS Inc. It consist of many forensics tools such as Sleuth kit / Autopsy etc . However, Sleuth kit/Autopsy tools can be installed on Ubuntu/Fedora distribution instead of downloading complete distribution of SIFT.
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
translating by wwy-hust
|
||||
|
||||
10 Amazing and Mysterious Uses of (!) Symbol or Operator in Linux Commands
|
||||
================================================================================
|
||||
The `'!'` symbol or operator in Linux can be used as Logical Negation operator as well as to fetch commands from history with tweaks or to run previously run command with modification. All the commands below have been checked explicitly in bash Shell. Though I have not checked but a major of these won’t run in other shell. Here we go into the amazing and mysterious uses of `'!'` symbol or operator in Linux commands.
|
||||
@ -190,4 +192,4 @@ via: http://www.tecmint.com/mysterious-uses-of-symbol-or-operator-in-linux-comma
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/avishek/
|
||||
[1]:http://www.tecmint.com/12-top-command-examples-in-linux/
|
||||
[1]:http://www.tecmint.com/12-top-command-examples-in-linux/
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
Translating by goreliu ...
|
||||
|
||||
How to Use Docker Machine with a Cloud Provider
|
||||
================================================================================
|
||||
Hi everyone, today we'll learn how we can use Docker Machine to deploy Docker host in various Cloud Provider Platforms. Docker Machine is an application that helps to create Docker hosts on our computer, on cloud providers and inside our own data center. It provides easy solution for creating servers, installing Docker on them and then configuring the Docker client according the users configuration and requirements. The driver APIs works for provisioning Docker on a local machine, on a virtual machine in the data center, or on a public cloud instance. Docker Machine is supported on Windows, OSX, and Linux and is available for installation as one standalone binary. It enables us to take full advantage of ecosystem partners providing Docker-ready infrastructure, while still accessing everything through the same interface. It makes people able to deploy the docker containers in the respective cloud platform pretty fast and in pretty easy way with just a single command.
|
||||
@ -138,7 +140,7 @@ Docker Machine is really and awesome tool for deploying servers with Docker Cont
|
||||
via: http://linoxide.com/linux-how-to/use-docker-machine-cloud-provider/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
译者:[goreliu](https://github.com/goreliu)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
182
sources/tech/20150522 Analyzing Linux Logs.md
Normal file
182
sources/tech/20150522 Analyzing Linux Logs.md
Normal file
@ -0,0 +1,182 @@
|
||||
translating by zhangboyue
|
||||
Analyzing Linux Logs
|
||||
================================================================================
|
||||
There’s a great deal of information waiting for you within your logs, although it’s not always as easy as you’d like to extract it. In this section we will cover some examples of basic analysis you can do with your logs right away (just search what’s there). We’ll also cover more advanced analysis that may take some upfront effort to set up properly, but will save you time on the back end. Examples of advanced analysis you can do on parsed data include generating summary counts, filtering on field values, and more.
|
||||
|
||||
We’ll show you first how to do this yourself on the command line using several different tools and then show you how a log management tool can automate much of the grunt work and make this so much more streamlined.
|
||||
|
||||
### Searching with Grep ###
|
||||
|
||||
Searching for text is the most basic way to find what you’re looking for. The most common tool for searching text is [grep][1]. This command line tool, available on most Linux distributions, allows you to search your logs using regular expressions. A regular expression is a pattern written in a special language that can identify matching text. The simplest pattern is to put the string you’re searching for surrounded by quotes
|
||||
|
||||
#### Regular Expressions ####
|
||||
|
||||
Here’s an example to find authentication logs for “user hoover” on an Ubuntu system:
|
||||
|
||||
$ grep "user hoover" /var/log/auth.log
|
||||
Accepted password for hoover from 10.0.2.2 port 4792 ssh2
|
||||
pam_unix(sshd:session): session opened for user hoover by (uid=0)
|
||||
pam_unix(sshd:session): session closed for user hoover
|
||||
|
||||
It can be hard to construct regular expressions that are accurate. For example, if we searched for a number like the port “4792” it could also match timestamps, URLs, and other undesired data. In the below example for Ubuntu, it matched an Apache log that we didn’t want.
|
||||
|
||||
$ grep "4792" /var/log/auth.log
|
||||
Accepted password for hoover from 10.0.2.2 port 4792 ssh2
|
||||
74.91.21.46 - - [31/Mar/2015:19:44:32 +0000] "GET /scripts/samples/search?q=4972HTTP/1.0" 404 545 "-" "-”
|
||||
|
||||
#### Surround Search ####
|
||||
|
||||
Another useful tip is that you can do surround search with grep. This will show you what happened a few lines before or after a match. It can help you debug what lead up to a particular error or problem. The B flag gives you lines before, and A gives you lines after. For example, we can see that when someone failed to login as an admin, they also failed the reverse mapping which means they might not have a valid domain name. This is very suspicious!
|
||||
|
||||
$ grep -B 3 -A 2 'Invalid user' /var/log/auth.log
|
||||
Apr 28 17:06:20 ip-172-31-11-241 sshd[12545]: reverse mapping checking getaddrinfo for 216-19-2-8.commspeed.net [216.19.2.8] failed - POSSIBLE BREAK-IN ATTEMPT!
|
||||
Apr 28 17:06:20 ip-172-31-11-241 sshd[12545]: Received disconnect from 216.19.2.8: 11: Bye Bye [preauth]
|
||||
Apr 28 17:06:20 ip-172-31-11-241 sshd[12547]: Invalid user admin from 216.19.2.8
|
||||
Apr 28 17:06:20 ip-172-31-11-241 sshd[12547]: input_userauth_request: invalid user admin [preauth]
|
||||
Apr 28 17:06:20 ip-172-31-11-241 sshd[12547]: Received disconnect from 216.19.2.8: 11: Bye Bye [preauth]
|
||||
|
||||
#### Tail ####
|
||||
|
||||
You can also pair grep with [tail][2] to get the last few lines of a file, or to follow the logs and print them in real time. This is useful if you are making interactive changes like starting a server or testing a code change.
|
||||
|
||||
$ tail -f /var/log/auth.log | grep 'Invalid user'
|
||||
Apr 30 19:49:48 ip-172-31-11-241 sshd[6512]: Invalid user ubnt from 219.140.64.136
|
||||
Apr 30 19:49:49 ip-172-31-11-241 sshd[6514]: Invalid user admin from 219.140.64.136
|
||||
|
||||
A full introduction on grep and regular expressions is outside the scope of this guide, but [Ryan’s Tutorials][3] include more in-depth information.
|
||||
|
||||
Log management systems have higher performance and more powerful searching abilities. They often index their data and parallelize queries so you can quickly search gigabytes or terabytes of logs in seconds. In contrast, this would take minutes or in extreme cases hours with grep. Log management systems also use query languages like [Lucene][4] which offer an easier syntax for searching on numbers, fields, and more.
|
||||
|
||||
### Parsing with Cut, AWK, and Grok ###
|
||||
|
||||
#### Command Line Tools ####
|
||||
|
||||
Linux offers several command line tools for text parsing and analysis. They are great if you want to quickly parse a small amount of data but can take a long time to process large volumes of data
|
||||
|
||||
#### Cut ####
|
||||
|
||||
The [cut][5] command allows you to parse fields from delimited logs. Delimiters are characters like equal signs or commas that break up fields or key value pairs.
|
||||
|
||||
Let’s say we want to parse the user from this log:
|
||||
|
||||
pam_unix(su:auth): authentication failure; logname=hoover uid=1000 euid=0 tty=/dev/pts/0 ruser=hoover rhost= user=root
|
||||
|
||||
We can use the cut command like this to get the text after the eighth equal sign. This example is on an Ubuntu system:
|
||||
|
||||
$ grep "authentication failure" /var/log/auth.log | cut -d '=' -f 8
|
||||
root
|
||||
hoover
|
||||
root
|
||||
nagios
|
||||
nagios
|
||||
|
||||
#### AWK ####
|
||||
|
||||
Alternately, you can use [awk][6], which offers more powerful features to parse out fields. It offers a scripting language so you can filter out nearly everything that’s not relevant.
|
||||
|
||||
For example, let’s say we have the following log line on an Ubuntu system and we want to extract the username that failed to login:
|
||||
|
||||
Mar 24 08:28:18 ip-172-31-11-241 sshd[32701]: input_userauth_request: invalid user guest [preauth]
|
||||
|
||||
Here’s how you can use the awk command. First, put a regular expression /sshd.*invalid user/ to match the sshd invalid user lines. Then print the ninth field using the default delimiter of space using { print $9 }. This outputs the usernames.
|
||||
|
||||
$ awk '/sshd.*invalid user/ { print $9 }' /var/log/auth.log
|
||||
guest
|
||||
admin
|
||||
info
|
||||
test
|
||||
ubnt
|
||||
|
||||
You can read more about how to use regular expressions and print fields in the [Awk User’s Guide][7].
|
||||
|
||||
#### Log Management Systems ####
|
||||
|
||||
Log management systems make parsing easier and enable users to quickly analyze large collections of log files. They can automatically parse standard log formats like common Linux logs or web server logs. This saves a lot of time because you don’t have to think about writing your own parsing logic when troubleshooting a system problem.
|
||||
|
||||
Here you can see an example log message from sshd which has each of the fields remoteHost and user parsed out. This is a screenshot from Loggly, a cloud-based log management service.
|
||||
|
||||

|
||||
|
||||
You can also do custom parsing for non-standard formats. A common tool to use is [Grok][8] which uses a library of common regular expressions to parse raw text into structured JSON. Here is an example configuration for Grok to parse kernel log files inside Logstash:
|
||||
|
||||
filter{
|
||||
grok {
|
||||
match => {"message" => "%{CISCOTIMESTAMP:timestamp} %{HOST:host} %{WORD:program}%{NOTSPACE} %{NOTSPACE}%{NUMBER:duration}%{NOTSPACE} %{GREEDYDATA:kernel_logs}"
|
||||
}
|
||||
}
|
||||
|
||||
And here is what the parsed output looks like from Grok:
|
||||
|
||||

|
||||
|
||||
### Filtering with Rsyslog and AWK ###
|
||||
|
||||
Filtering allows you to search on a specific field value instead of doing a full text search. This makes your log analysis more accurate because it will ignore undesired matches from other parts of the log message. In order to search on a field value, you need to parse your logs first or at least have a way of searching based on the event structure.
|
||||
|
||||
#### How to Filter on One App ####
|
||||
|
||||
Often, you just want to see the logs from just one application. This is easy if your application always logs to a single file. It’s more complicated if you need to filter one application among many in an aggregated or centralized log. Here are several ways to do this:
|
||||
|
||||
1. Use the rsyslog daemon to parse and filter logs. This example writes logs from the sshd application to a file named sshd-messages, then discards the event so it’s not repeated elsewhere. You can try this example by adding it to your rsyslog.conf file.
|
||||
|
||||
:programname, isequal, “sshd” /var/log/sshd-messages
|
||||
&~
|
||||
|
||||
2. Use command line tools like awk to extract the values of a particular field like the sshd username. This example is from an Ubuntu system.
|
||||
|
||||
$ awk '/sshd.*invalid user/ { print $9 }' /var/log/auth.log
|
||||
guest
|
||||
admin
|
||||
info
|
||||
test
|
||||
ubnt
|
||||
|
||||
3. Use a log management system that automatically parses your logs, then click to filter on the desired application name. Here is a screenshot showing the syslog fields in a log management service called Loggly. We are filtering on the appName “sshd” as indicated by the Venn diagram icon.
|
||||
|
||||

|
||||
|
||||
#### How to Filter on Errors ####
|
||||
|
||||
One of the most common thing people want to see in their logs is errors. Unfortunately, the default syslog configuration doesn’t output the severity of errors directly, making it difficult to filter on them.
|
||||
|
||||
There are two ways you can solve this problem. First, you can modify your rsyslog configuration to output the severity in the log file to make it easier to read and search. In your rsyslog configuration you can add a [template][9] with pri-text such as the following:
|
||||
|
||||
"<%pri-text%> : %timegenerated%,%HOSTNAME%,%syslogtag%,%msg%n"
|
||||
|
||||
This example gives you output in the following format. You can see that the severity in this message is err.
|
||||
|
||||
<authpriv.err> : Mar 11 18:18:00,hoover-VirtualBox,su[5026]:, pam_authenticate: Authentication failure
|
||||
|
||||
You can use awk or grep to search for just the error messages. In this example for Ubuntu, we’re including some surrounding syntax like the . and the > which match only this field.
|
||||
|
||||
$ grep '.err>' /var/log/auth.log
|
||||
<authpriv.err> : Mar 11 18:18:00,hoover-VirtualBox,su[5026]:, pam_authenticate: Authentication failure
|
||||
|
||||
Your second option is to use a log management system. Good log management systems automatically parse syslog messages and extract the severity field. They also allow you to filter on log messages of a certain severity with a single click.
|
||||
|
||||
Here is a screenshot from Loggly showing the syslog fields with the error severity highlighted to show we are filtering for errors:
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.loggly.com/ultimate-guide/logging/analyzing-linux-logs/
|
||||
|
||||
作者:[Jason Skowronski][a] [Amy Echeverri][b] [ Sadequl Hussain][c]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linkedin.com/in/jasonskowronski
|
||||
[b]:https://www.linkedin.com/in/amyecheverri
|
||||
[c]:https://www.linkedin.com/pub/sadequl-hussain/14/711/1a7
|
||||
[1]:http://linux.die.net/man/1/grep
|
||||
[2]:http://linux.die.net/man/1/tail
|
||||
[3]:http://ryanstutorials.net/linuxtutorial/grep.php
|
||||
[4]:https://lucene.apache.org/core/2_9_4/queryparsersyntax.html
|
||||
[5]:http://linux.die.net/man/1/cut
|
||||
[6]:http://linux.die.net/man/1/awk
|
||||
[7]:http://www.delorie.com/gnu/docs/gawk/gawk_26.html#IDX155
|
||||
[8]:http://logstash.net/docs/1.4.2/filters/grok
|
||||
[9]:http://www.rsyslog.com/doc/v8-stable/configuration/templates.html
|
||||
@ -0,0 +1,74 @@
|
||||
一个Ubuntu中给你的照片加Instagram风格滤镜的程序
|
||||
================================================================================
|
||||
**在Ubuntu中寻找一个给你的照片加Instagram风格的滤镜程序么?**
|
||||
|
||||
拿起你的自拍棒跟着这个来。
|
||||
|
||||

|
||||
XnRetro是一个照片编辑应用
|
||||
|
||||
### XnRetro 照片编辑器 ###
|
||||
|
||||
**XnRetro** 是一个可以让你快速给你照片添加“类Instagram”效果的程序。
|
||||
|
||||
你知道我说的这些效果:划痕、噪点、框架、过处理、复古和怀旧色调(因为在这个数字时代,我们必须知道无尽的自拍不能称为怀旧的自己。)
|
||||
|
||||
无论你认为这些效果是愚蠢的艺术价值或者创作的捷径,这些滤镜非常流行切可以帮助那些平平照片添加个性。
|
||||
|
||||
|
||||
#### XnRetro的功能 ####
|
||||
|
||||
**XnRetro有下面那些功能**
|
||||
|
||||
- 20色彩滤镜
|
||||
- 15中光效果(虚化、泄露等等)
|
||||
- 28框架和边框
|
||||
- 5中插图 (带力度控制)
|
||||
- Image adjustments for contrast, gamma, saturation, etc
|
||||
- 对比度、伽马、饱和度等图像调整
|
||||
- 矩形修剪选项
|
||||
|
||||

|
||||
灯光效果调整
|
||||
|
||||
你可以(理论上)编辑。jpg或者.png文件并且直接在app中等想到社交媒体上。
|
||||
|
||||
我说“理论”上的意思是保存.jpg图像无法正常在linux版的程序上工作(你可以保存.png的图像)。相似的,大多数内置的社交链接失效或者无法导出。
|
||||
|
||||
要使用**15中光影效果**你需要在XnRetro的‘light’文件夹下重新保存.jpg文件成.png文件。编辑‘light.xml’来匹配新的文件名,点击保存那没灯光效果就可以没有问题的加载进XnRetro了。
|
||||
|
||||
> ‘用户友好的XnRetro很难打败-一旦你用顺之后。’
|
||||
|
||||
**XnRetro值得安装么?**
|
||||
|
||||
XnRetro并不是完美的。它看上去很丑、很难正确的安装并且已经纪念没有更新了。
|
||||
|
||||
它还可以使用,输了保存.jpg文件外。同时也是那些像Gimp或者Shotwell的那些‘正规’图片调整工具的一个灵活替代品。
|
||||
|
||||
While web apps and Chrome Apps¹ like [Pixlr Touch Up][1] and [Polarr][2] offer similar features you may be looking for a truly native solution.
|
||||
虽然web应用和Chrome Apps¹像[Pixlr Touch Up][1] 和 [Polarr][2]提供另外相似的功能,而你也许正在寻找真正原生的解决方案。
|
||||
|
||||
对于此,用户友好带有容易使用滤镜的XnRetro很难被打败。
|
||||
|
||||
### 下载Ubuntu下的XnRetro ###
|
||||
|
||||
XnRetro没有可用的.deb安装包。它以二进制文件的形式发型,这意味着你需要每次双击程序来运行。它也只有32位的版本。
|
||||
|
||||
你可以使用下面的XnRetro下载链接。下载完成后你需要解压压缩包并进入。双击里面的‘xnretro’程序。
|
||||
|
||||
- [下载Linux版XnRetro (32位, tar.gz)][3]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2015/05/instagram-photo-filters-ubuntu-desktop-app
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.omgchrome.com/?s=pixlr
|
||||
[2]:http://www.omgchrome.com/the-best-chrome-apps-of-2014/
|
||||
[3]:http://www.xnview.com/en/xnretro/#downloads
|
||||
@ -0,0 +1,144 @@
|
||||
如何在Fedora或CentOS上使用Samba共享文件夹
|
||||
================================================================================
|
||||
如今,无论在家里或者是办公场所,不同的电脑之间共享文件夹已不是什么新鲜事了。在这种趋势下,现代操作系统通过网络文件系统的方式使得电脑间数据的交换变得简单而透明。如果您工作的环境中既有微软的Windows又有Linux,那么,一个共享文件及目录的方式便是通过一个跨平台网络文件共享协议,SMB/CIFS。Windows天然的支持SMB/CIFS,Linux也通过开源的软件Samba实现了SMB/CIFS协议。
|
||||
|
||||
在这篇文章中,我们将展示**如何使用Samba共享文件夹**。我们使用的Linux平台是**Fedora或CentOS**。这篇文章分为四部分。首先,我们在Fedora/CentOS环境下安装Sambe。接着,我们讨论如何调整SELinux和防火墙配置以允许Samba的文件共享。最后我们介绍如何使用Samba来共享文件夹。
|
||||
|
||||
### 步骤1:在Fedora和CentOS上安装Samba ###
|
||||
|
||||
首先,安装Samba以及进行一些基本的配置。
|
||||
|
||||
检验Samba是否已经安装在您的系统中:
|
||||
|
||||
$ rpm -q samba samba-common samba-client
|
||||
|
||||
如果上面的命令没有任何输出,这意味着Samba并未安装。这时,应使用下面的命令来安装Samba。
|
||||
|
||||
$ sudo yum install samba samba-common samba-client
|
||||
|
||||
接下来,创建一个用于在网络中共享的本地文件夹。这个文件夹应该以Samba共享的方式导出到远程的用户。在这个指南中,我们会在顶层文件夹'/'中创建这个文件夹,因此,请确保您有相应的权限。
|
||||
|
||||
$ sudo mkdir /shared
|
||||
|
||||
如果您想在您的home文件夹内创建共享文件夹(例如,~/shared),您必须激活SELinux中Samba的home文件夹共享选项,具体将在后面提到。
|
||||
|
||||
在创建/shared文件夹后,设置文件夹权限以保证其余用户可以访问它。
|
||||
|
||||
$ sudo chmod o+rw /shared
|
||||
|
||||
如果您不想其他用户对该文件夹拥有写权限,您需要移除命令中的'w'选项。
|
||||
|
||||
$ sudo chmod o+r /shared
|
||||
|
||||
接下来,创建一个空文件来测试。这个文件可以被用来验证Samba的共享已经被挂载。
|
||||
|
||||
$ sudo touch /shared/file1
|
||||
|
||||
### 步骤2:为Samba配置SELinux ###
|
||||
|
||||
接下来,我们需要再次配置SELinux。在Fedora和CentOS发行版中SELinux是默认开启的。SELinux仅在正确的安全配置下才允许Samba读取和修改文件或文件夹。(例如,加上'samba_share_t'属性标签)。
|
||||
|
||||
下面的命令为文件的配置添加必要的标签:
|
||||
|
||||
$ sudo semanage fcontext -a -t samba_share_t "<directory>(/.*)?"
|
||||
|
||||
将<directory>替换为我们之前为Samba共享创建的本地文件夹(例如,/shared):
|
||||
|
||||
$ sudo semanage fcontext -a -t samba_share_t "/shared(/.*)?"
|
||||
|
||||
我们必须执行restorecon命令来激活修改的标签,命令如下:
|
||||
|
||||
$ sudo restorecon -R -v /shared
|
||||
|
||||

|
||||
|
||||
为了通过Samba共享在我们home文件夹内的文件夹,我们必须在SELinux中开启共享home文件夹的选项,该选项默认被关闭。下面的命令能达到该效果。如果您并未共享您的home文件夹,那么您可以跳过该步骤。
|
||||
|
||||
$ sudo setsebool -P samba_enable_home_dirs 1
|
||||
|
||||
### 步骤3:为Samba配置防火墙 ###
|
||||
|
||||
下面的命令用来打开防火墙中Samba为共享需要的TCP/UDP端口。
|
||||
|
||||
如果您在使用firewalld(例如,在Fedora和CentOS7下),接下来的命令将会永久的修改Samba相关的防火墙规则。
|
||||
|
||||
$ sudo firewall-cmd --permanent --add-service=samba
|
||||
|
||||
如果您在防火墙中使用iptables(例如,CentOS6或者更早的版本),可以使用下面的命令来打开Samba必要的向外的端口。
|
||||
|
||||
$ sudo vi /etc/sysconfig/iptables
|
||||
|
||||
----------
|
||||
|
||||
-A RH-Firewall-1-INPUT -m state --state NEW -m tcp -p tcp --dport 445 -j ACCEPT
|
||||
-A RH-Firewall-1-INPUT -m state --state NEW -m udp -p udp --dport 445 -j ACCEPT
|
||||
-A RH-Firewall-1-INPUT -m state --state NEW -m udp -p udp --dport 137 -j ACCEPT
|
||||
-A RH-Firewall-1-INPUT -m state --state NEW -m udp -p udp --dport 138 -j ACCEPT
|
||||
-A RH-Firewall-1-INPUT -m state --state NEW -m tcp -p tcp --dport 139 -j ACCEPT
|
||||
|
||||
然后重启iptables服务:
|
||||
|
||||
$ sudo service iptables restart
|
||||
|
||||
### 步骤4:更改Samba配置 ###
|
||||
|
||||
后面的步骤用来配置Samba以将本地文件夹导出为Samba共享文件夹。
|
||||
|
||||
使用文件编辑器打开Samba配置文件,并将下面的行添加到文件的末尾。
|
||||
|
||||
$ sudo nano /etc/samba/smb.conf
|
||||
|
||||
----------
|
||||
|
||||
[myshare]
|
||||
comment=my shared files
|
||||
path=/shared
|
||||
public=yes
|
||||
writeable=yes
|
||||
|
||||
上面在括号内的文本(例如,"myshare")是Samba共享的资源的名字,它被用来从远程主机存取Samba共享。
|
||||
|
||||
创建Samba用户帐户,这是挂载和导出Samba文件系统所必须的。我们可以使用smbpasswd工具来创建一个Samba用户。注意,Samba用户帐户必须是Linux用户管理中已存在的。如果您尝试使用smbpasswd添加一个不存在的用户,它会返回一个错误的消息。
|
||||
|
||||
如果您不想使用任何已存在的Linux用户作为Samba用户,您可以在您的系统中创建一个新的用户。为安全起见,设置新用户的登录脚本为/sbin/nologin,并且不创建该用户的home文件夹。
|
||||
|
||||
在这个例子中,我们正在创建一个名叫"sambaguest"的用户,如下:
|
||||
|
||||
$ sudo useradd -M -s /sbin/nologin sambaguest
|
||||
$ sudo passwd sambaguest
|
||||
|
||||

|
||||
|
||||
在创建一个新用户后,使用smbpasswd命令添加Samba用户。当这个命令询问一个密码时,您可以键入一个不同于该用户的密码。
|
||||
|
||||
$ sudo smbpasswd -a sambaguest
|
||||
|
||||
4. 激活Samba服务,并检测Samba服务是否在运行。
|
||||
|
||||
$ sudo systemctl enable smb.service
|
||||
$ sudo systemctl start smb.service
|
||||
$ sudo systemctl is-active smb
|
||||
|
||||

|
||||
|
||||
使用下面的命令来查看Samba中共享的文件夹列表。
|
||||
|
||||
$ smbclient -U sambaguest -L localhost
|
||||
|
||||

|
||||
|
||||
接下来是在Thunar文件管理器中存取Samba共享文件夹以及对file1进行拷贝复制的截图。注意,Samba的共享内容可以通过在Thunar中通过"smb://<samba-server-IP-address>/myshare"这个地址来存取。
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/share-directory-samba-fedora-centos.html
|
||||
|
||||
作者:[Kristophorus Hadiono][a]
|
||||
译者:[wwy-hust](https://github.com/wwy-hust)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/kristophorus
|
||||
File diff suppressed because it is too large
Load Diff
Loading…
Reference in New Issue
Block a user