mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-06 23:50:16 +08:00
commit
1da6d877ce
@ -1,4 +1,4 @@
|
||||
伴随Apple Watch的揭幕,下一个智能手表会是Ubuntu吗?
|
||||
Apple Watch之后,下一个智能手表会是Ubuntu吗?
|
||||
===
|
||||
|
||||
**苹果借助‘Apple Watch’的发布,证实了其进军穿戴式电子设备市场的长期传言**
|
||||
@ -1,10 +1,10 @@
|
||||
Linux有问必答-- 如何在Linux上安装内核头文件
|
||||
Linux有问必答:如何在Linux上安装内核头文件
|
||||
================================================================================
|
||||
> **提问**:我在安装一个设备驱动前先要安装内核头文件。怎样安装合适的内核头文件?
|
||||
|
||||
当你在编译一个设备驱动模块时,你需要在系统中安装内核头文件。内核头文件同样在你编译与内核直接链接的用户空间程序时需要。当你在这些情况下安装内核头文件时,你必须确保内核头文件精确地与你当前内核版本匹配(比如:3.13.0-24-generic)。
|
||||
|
||||
如果你的内核发行版自带的内核版本,或者使用默认的包管理器的基础仓库升级的(比如:apt-ger、aptitude或者yum),你也可以使用包管理器来安装内核头文件。另一方面,如果下载的是[kernel源码][1]并且手动编译的,你可以使用[make命令][2]来安装匹配的内核头文件。
|
||||
如果你的内核是发行版自带的内核版本,或者使用默认的包管理器的基础仓库升级的(比如:apt-ger、aptitude或者yum),你也可以使用包管理器来安装内核头文件。另一方面,如果下载的是[kernel源码][1]并且手动编译的,你可以使用[make命令][2]来安装匹配的内核头文件。
|
||||
|
||||
现在我们假设你的内核是发行版自带的,让我们看下该如何安装匹配的头文件。
|
||||
|
||||
@ -41,7 +41,7 @@ Debian、Ubuntu、Linux Mint默认头文件在**/usr/src**下。
|
||||
|
||||
假设你没有手动编译内核,你可以使用yum命令来安装匹配的内核头文件。
|
||||
|
||||
首先,用下面的命令检查系统是否已经按炸ung了头文件。如果下面的命令没有任何输出,这就意味着还没有头文件。
|
||||
首先,用下面的命令检查系统是否已经安装了头文件。如果下面的命令没有任何输出,这就意味着还没有头文件。
|
||||
|
||||
$ rpm -qa | grep kernel-headers-$(uname -r)
|
||||
|
||||
@ -66,7 +66,7 @@ Fedora、CentOS 或者 RHEL上默认内核头文件的位置是**/usr/include/li
|
||||
via: http://ask.xmodulo.com/install-kernel-headers-linux.html
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,155 +0,0 @@
|
||||
How to Backup and Restore Your Apps and PPAs in Ubuntu Using Aptik
|
||||
================================================================================
|
||||

|
||||
|
||||
If you need to reinstall Ubuntu or if you just want to install a new version from scratch, wouldn’t it be useful to have an easy way to reinstall all your apps and settings? You can easily accomplish this using a free tool called Aptik.
|
||||
|
||||
Aptik (Automated Package Backup and Restore), an application available in Ubuntu, Linux Mint, and other Debian- and Ubuntu-based Linux distributions, allows you to backup a list of installed PPAs (Personal Package Archives), which are software repositories, downloaded packages, installed applications and themes, and application settings to an external USB drive, network drive, or a cloud service like Dropbox.
|
||||
|
||||
NOTE: When we say to type something in this article and there are quotes around the text, DO NOT type the quotes, unless we specify otherwise.
|
||||
|
||||
To install Aptik, you must add the PPA. To do so, press Ctrl + Alt + T to open a Terminal window. Type the following text at the prompt and press Enter.
|
||||
|
||||
sudo apt-add-repository –y ppa:teejee2008/ppa
|
||||
|
||||
Type your password when prompted and press Enter.
|
||||
|
||||

|
||||
|
||||
Type the following text at the prompt to make sure the repository is up-to-date.
|
||||
|
||||
sudo apt-get update
|
||||
|
||||

|
||||
|
||||
When the update is finished, you are ready to install Aptik. Type the following text at the prompt and press Enter.
|
||||
|
||||
sudo apt-get install aptik
|
||||
|
||||
NOTE: You may see some errors about packages that the update failed to fetch. If they are similar to the ones listed on the following image, you should have no problem installing Aptik.
|
||||
|
||||

|
||||
|
||||
The progress of the installation displays and then a message displays saying how much disk space will be used. When asked if you want to continue, type a “y” and press Enter.
|
||||
|
||||

|
||||
|
||||
When the installation if finished, close the Terminal window by typing “Exit” and pressing Enter, or by clicking the “X” button in the upper-left corner of the window.
|
||||
|
||||

|
||||
|
||||
Before running Aptik, you should set up a backup directory on a USB flash drive, a network drive, or on a cloud account, such as Dropbox or Google Drive. For this example, will will use Dropbox.
|
||||
|
||||

|
||||
|
||||
Once your backup directory is set up, click the “Search” button at the top of the Unity Launcher bar.
|
||||
|
||||

|
||||
|
||||
Type “aptik” in the search box. Results of the search display as you type. When the icon for Aptik displays, click on it to open the application.
|
||||
|
||||

|
||||
|
||||
A dialog box displays asking for your password. Enter your password in the edit box and click “OK.”
|
||||
|
||||

|
||||
|
||||
The main Aptik window displays. Select “Other…” from the “Backup Directory” drop-down list. This allows you to select the backup directory you created.
|
||||
|
||||
NOTE: The “Open” button to the right of the drop-down list opens the selected directory in a Files Manager window.
|
||||
|
||||

|
||||
|
||||
On the “Backup Directory” dialog box, navigate to your backup directory and then click “Open.”
|
||||
|
||||
NOTE: If you haven’t created a backup directory yet, or you want to add a subdirectory in the selected directory, use the “Create Folder” button to create a new directory.
|
||||
|
||||

|
||||
|
||||
To backup the list of installed PPAs, click “Backup” to the right of “Software Sources (PPAs).”
|
||||
|
||||

|
||||
|
||||
The “Backup Software Sources” dialog box displays. The list of installed packages and the associated PPA for each displays. Select the PPAs you want to backup, or use the “Select All” button to select all the PPAs in the list.
|
||||
|
||||

|
||||
|
||||
Click “Backup” to begin the backup process.
|
||||
|
||||

|
||||
|
||||
A dialog box displays when the backup is finished telling you the backup was created successfully. Click “OK” to close the dialog box.
|
||||
|
||||
A file named “ppa.list” will be created in the backup directory.
|
||||
|
||||

|
||||
|
||||
The next item, “Downloaded Packages (APT Cache)”, is only useful if you are re-installing the same version of Ubuntu. It backs up the packages in your system cache (/var/cache/apt/archives). If you are upgrading your system, you can skip this step because the packages for the new version of the system will be newer than the packages in the system cache.
|
||||
|
||||
Backing up downloaded packages and then restoring them on the re-installed Ubuntu system will save time and Internet bandwidth when the packages are reinstalled. Because the packages will be available in the system cache once you restore them, the download will be skipped and the installation of the packages will complete more quickly.
|
||||
|
||||
If you are reinstalling the same version of your Ubuntu system, click the “Backup” button to the right of “Downloaded Packages (APT Cache)” to backup the packages in the system cache.
|
||||
|
||||
NOTE: When you backup the downloaded packages, there is no secondary dialog box. The packages in your system cache (/var/cache/apt/archives) are copied to an “archives” directory in the backup directory and a dialog box displays when the backup is finished, indicating that the packages were copied successfully.
|
||||
|
||||

|
||||
|
||||
There are some packages that are part of your Ubuntu distribution. These are not checked, since they are automatically installed when you install the Ubuntu system. For example, Firefox is a package that is installed by default in Ubuntu and other similar Linux distributions. Therefore, it will not be selected by default.
|
||||
|
||||
Packages that you installed after installing the system, such as the [package for the Chrome web browser][1] or the package containing Aptik (yes, Aptik is automatically selected to back up), are selected by default. This allows you to easily back up the packages that are not included in the system when installed.
|
||||
|
||||
Select the packages you want to back up and de-select the packages you don’t want to backup. Click “Backup” to the right of “Software Selections” to back up the selected top-level packages.
|
||||
|
||||
NOTE: Dependency packages are not included in this backup.
|
||||
|
||||

|
||||
|
||||
Two files, named “packages.list” and “packages-installed.list”, are created in the backup directory and a dialog box displays indicating that the backup was created successfully. Click “OK” to close the dialog box.
|
||||
|
||||
NOTE: The “packages-installed.list” file lists all the packages. The “packages.list” file also lists all the packages, but indicates which ones were selected.
|
||||
|
||||

|
||||
|
||||
To backup settings for installed applications, click the “Backup” button to the right of “Application Settings” on the main Aptik window. Select the settings you want to back up and click “Backup”.
|
||||
|
||||
NOTE: Click the “Select All” button if you want to back up all application settings.
|
||||
|
||||

|
||||
|
||||
The selected settings files are zipped into a file called “app-settings.tar.gz”.
|
||||
|
||||

|
||||
|
||||
When the zipping is complete, the zipped file is copied to the backup directory and a dialog box displays telling you that the backups were created successfully. Click “OK” to close the dialog box.
|
||||
|
||||

|
||||
|
||||
Themes from the “/usr/share/themes” directory and icons from the “/usr/share/icons” directory can also be backed up. To do so, click the “Backup” button to the right of “Themes and Icons”. The “Backup Themes” dialog box displays with all the themes and icons selected by default. De-select any themes or icons you don’t want to back up and click “Backup.”
|
||||
|
||||

|
||||
|
||||
The themes are zipped and copied to a “themes” directory in the backup directory and the icons are zipped and copied to an “icons” directory in the backup directory. A dialog box displays telling you that the backups were created successfully. Click “OK” to close the dialog box.
|
||||
|
||||

|
||||
|
||||
Once you’ve completed the desired backups, close Aptik by clicking the “X” button in the upper-left corner of the main window.
|
||||
|
||||

|
||||
|
||||
Your backup files are available in the backup directory you chose.
|
||||
|
||||

|
||||
|
||||
When you re-install your Ubuntu system or install a new version of Ubuntu, install Aptik on the newly installed system and make the backup files you generated available to the system. Run Aptik and use the “Restore” button for each item to restore your PPAs, applications, packages, settings, themes, and icons.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.howtogeek.com/206454/how-to-backup-and-restore-your-apps-and-ppas-in-ubuntu-using-aptik/
|
||||
|
||||
作者:Lori Kaufman
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.howtogeek.com/203768
|
||||
@ -1,75 +0,0 @@
|
||||
(translating by runningwater)
|
||||
Linux FAQs with Answers--How to install 7zip on Linux
|
||||
================================================================================
|
||||
> **Question**: I need to extract files from an ISO image, and for that I want to use 7zip program. How can I install 7zip on [insert your Linux distro]?
|
||||
|
||||
7zip is an open-source archive program originally developed for Windows, which can pack or unpack a variety of archive formats including its native format 7z as well as XZ, GZIP, TAR, ZIP and BZIP2. 7zip is also popularly used to extract RAR, DEB, RPM and ISO files. Besides simple archiving, 7zip can support AES-256 encryption as well as self-extracting and multi-volume archiving. For POSIX systems (Linux, Unix, BSD), the original 7zip program has been ported as p7zip (short for "POSIX 7zip").
|
||||
|
||||
Here is how to install 7zip (or p7zip) on Linux.
|
||||
|
||||
### Install 7zip on Debian, Ubuntu or Linux Mint ###
|
||||
|
||||
Debian-based distributions come with three packages related to 7zip.
|
||||
|
||||
- **p7zip**: contains 7zr (a minimal 7zip archive tool) which can handle its native 7z format only.
|
||||
- **p7zip-full**: contains 7z which can support 7z, LZMA2, XZ, ZIP, CAB, GZIP, BZIP2, ARJ, TAR, CPIO, RPM, ISO and DEB.
|
||||
- **p7zip-rar**: contains a plugin for extracting RAR files.
|
||||
|
||||
It is recommended to install p7zip-full package (not p7zip) since this is the most complete 7zip package which supports many archive formats. In addition, if you want to extract RAR files, you also need to install p7zip-rar package as well. The reason for having a separate plugin package is because RAR is a proprietary format.
|
||||
|
||||
$ sudo apt-get install p7zip-full p7zip-rar
|
||||
|
||||
### Install 7zip on Fedora or CentOS/RHEL ###
|
||||
|
||||
Red Hat-based distributions offer two packages related to 7zip.
|
||||
|
||||
- **p7zip**: contains 7za command which can support 7z, ZIP, GZIP, CAB, ARJ, BZIP2, TAR, CPIO, RPM and DEB.
|
||||
- **p7zip-plugins**: contains 7z command and additional plugins to extend 7za command (e.g., ISO extraction).
|
||||
|
||||
On CentOS/RHEL, you need to enable [EPEL repository][1] before running yum command below. On Fedora, there is not need to set up additional repository.
|
||||
|
||||
$ sudo yum install p7zip p7zip-plugins
|
||||
|
||||
Note that unlike Debian based distributions, Red Hat based distributions do not offer a RAR plugin. Therefore you will not be able to extract RAR files using 7z command.
|
||||
|
||||
### Create or Extract an Archive with 7z ###
|
||||
|
||||
Once you installed 7zip, you can use 7z command to pack or unpack various types of archives. The 7z command uses other plugins to handle the archives.
|
||||
|
||||
|
||||
|
||||
To create an archive, use "a" option. Supported archive types for creation are 7z, XZ, GZIP, TAR, ZIP and BZIP2. If the specified archive file already exists, it will "add" the files to the existing archive, instead of overwriting it.
|
||||
|
||||
$ 7z a <archive-filename> <list-of-files>
|
||||
|
||||
To extract an archive, use "e" option. It will extract the archive in the current directory. Supported archive types for extraction are a lot more than those for creation. The list includes 7z, XZ, GZIP, TAR, ZIP, BZIP2, LZMA2, CAB, ARJ, CPIO, RPM, ISO and DEB.
|
||||
|
||||
$ 7z e <archive-filename>
|
||||
|
||||
Another way to unpack an archive is to use "x" option. Unlike "e" option, it will extract the content with full paths.
|
||||
|
||||
$ 7z x <archive-filename>
|
||||
|
||||
To see a list of files in an archive, use "l" option.
|
||||
|
||||
$ 7z l <archive-filename>
|
||||
|
||||
You can update or remove file(s) in an archive with "u" and "d" options, respectively.
|
||||
|
||||
$ 7z u <archive-filename> <list-of-files-to-update>
|
||||
$ 7z d <archive-filename> <list-of-files-to-delete>
|
||||
|
||||
To test the integrity of an archive:
|
||||
|
||||
$ 7z t <archive-filename>
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via:http://ask.xmodulo.com/install-7zip-linux.html
|
||||
|
||||
译者:[runningwater](https://github.com/runningwater)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
|
||||
@ -1,134 +0,0 @@
|
||||
翻译中 by小眼儿
|
||||
|
||||
Docker Image Insecurity
|
||||
================================================================================
|
||||
Recently while downloading an “official” container image with Docker I saw this line:
|
||||
|
||||
ubuntu:14.04: The image you are pulling has been verified
|
||||
|
||||
I assumed this referenced Docker’s [heavily promoted][1] image signing system and didn’t investigate further at the time. Later, while researching the cryptographic digest system that Docker tries to secure images with, I had the opportunity to explore further. What I found was a total systemic failure of all logic related to image security.
|
||||
|
||||
Docker’s report that a downloaded image is “verified” is based solely on the presence of a signed manifest, and Docker never verifies the image checksum from the manifest. An attacker could provide any image alongside a signed manifest. This opens the door to a number of serious vulnerabilities.
|
||||
|
||||
Images are downloaded from an HTTPS server and go through an insecure streaming processing pipeline in the Docker daemon:
|
||||
|
||||
[decompress] -> [tarsum] -> [unpack]
|
||||
|
||||
This pipeline is performant but completely insecure. Untrusted input should not be processed before verifying its signature. Unfortunately Docker processes images three times before checksum verification is supposed to occur.
|
||||
|
||||
However, despite [Docker’s claims][2], image checksums are never actually checked. This is the only section[0][3] of Docker’s code related to verifying image checksums, and I was unable to trigger the warning even when presenting images with mismatched checksums.
|
||||
|
||||
if img.Checksum != "" && img.Checksum != checksum {
|
||||
log.Warnf("image layer checksum mismatch: computed %q,
|
||||
expected %q", checksum, img.Checksum)
|
||||
}
|
||||
|
||||
### Insecure processing pipeline ###
|
||||
|
||||
**Decompress**
|
||||
|
||||
Docker supports three compression algorithms: gzip, bzip2, and xz. The first two use the Go standard library implementations, which are [memory-safe][4], so the exploit types I’d expect to see here are denial of service attacks like crashes and excessive CPU and memory usage.
|
||||
|
||||
The third compression algorithm, xz, is more interesting. Since there is no native Go implementation, Docker [execs][5] the `xz` binary to do the decompression.
|
||||
|
||||
The xz binary comes from the [XZ Utils][6] project, and is built from approximately[1][7] twenty thousand lines of C code. C is not a memory-safe language. This means malicious input to a C program, in this case the Docker image XZ Utils is unpacking, could potentially execute arbitrary code.
|
||||
|
||||
Docker exacerbates this situation by *running* `xz` as root. This means that if there is a single vulnerability in `xz`, a call to `docker pull` could result in the complete compromise of your entire system.
|
||||
|
||||
**Tarsum**
|
||||
|
||||
The use of tarsum is well-meaning but completely flawed. In order to get a deterministic checksum of the contents of an arbitrarily encoded tar file, Docker decodes the tar and then hashes specific portions, while excluding others, in a [deterministic order][8].
|
||||
|
||||
Since this processing is done in order to generate the checksum, it is decoding untrusted data which could be designed to exploit the tarsum code[2][9]. Potential exploits here are denial of service as well as logic flaws that could cause files to be injected, skipped, processed differently, modified, appended to, etc. without the checksum changing.
|
||||
|
||||
**Unpacking**
|
||||
|
||||
Unpacking consists of decoding the tar and placing files on the disk. This is extraordinarily dangerous as there have been three other vulnerabilities reported[3][10] in the unpack stage at the time of writing.
|
||||
|
||||
There is no situation where data that has not been verified should be unpacked onto disk.
|
||||
|
||||
### libtrust ###
|
||||
|
||||
[libtrust][11] is a Docker package that claims to provide “authorization and access control through a distributed trust graph.” Unfortunately no specification appears to exist, however it looks like it implements some parts of the [Javascript Object Signing and Encryption][12] specifications along with other unspecified algorithms.
|
||||
|
||||
Downloading an image with a manifest signed and verified using libtrust is what triggers this inaccurate message (only the manifest is checked, not the actual image contents):
|
||||
|
||||
ubuntu:14.04: The image you are pulling has been verified
|
||||
|
||||
Currently only “official” image manifests published by Docker, Inc are signed using this system, but from discussions I participated in at the last Docker Governance Advisory Board meeting[4][13], my understanding is that Docker, Inc is planning on deploying this more widely in the future. The intended goal is centralization with Docker, Inc controlling a Certificate Authority that then signs images and/or client certificates.
|
||||
|
||||
I looked for the signing key in Docker’s code but was unable to find it. As it turns out the key is not embedded in the binary as one would expect. Instead the Docker daemon fetches it [over HTTPS from a CDN][14] before each image download. This is a terrible approach as a variety of attacks could lead to trusted keys being replaced with malicious ones. These attacks include but are not limited to: compromise of the CDN vendor, compromise of the CDN origin serving the key, and man in the middle attacks on clients downloading the keys.
|
||||
|
||||
### Remediation ###
|
||||
|
||||
I [reported][15] some of the issues I found with the tarsum system before I finished this research, but so far nothing I have reported has been fixed.
|
||||
|
||||
Some steps I believe should be taken to improve the security of the Docker image download system:
|
||||
Drop tarsum and actually verify image digests
|
||||
|
||||
Tarsum should not be used for security. Instead, images must be fully downloaded and their cryptographic signatures verified before any processing takes place.
|
||||
|
||||
**Add privilege isolation**
|
||||
|
||||
Image processing steps that involve decompression or unpacking should be run in isolated processes (containers?) that have only the bare minimum required privileges to operate. There is no scenario where a decompression tool like `xz` should be run as root.
|
||||
|
||||
**Replace libtrust**
|
||||
|
||||
Libtrust should be replaced with [The Update Framework][16] which is explicitly designed to solve the real problems around signing software binaries. The threat model is very comprehensive and addresses many things that have not been considered in libtrust. There is a complete specification as well as a reference implementation written in Python, and I have begun work on a [Go implementation][17] and welcome contributions.
|
||||
|
||||
As part of adding TUF to Docker, a local keystore should be added that maps root keys to registry URLs so that users can have their own signing keys that are not managed by Docker, Inc.
|
||||
|
||||
I would like to note that using non-Docker, Inc hosted registries is a very poor user experience in general. Docker, Inc seems content with relegating third party registries to second class status when there is no technical reason to do so. This is a problem both for the ecosystem in general and the security of end users. A comprehensive, decentralized security model for third party registries is both necessary and desirable. I encourage Docker, Inc to take this into consideration when redesigning their security model and image verification system.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
Docker users should be aware that the code responsible for downloading images is shockingly insecure. Users should only download images whose provenance is without question. At present, this does *not* include “trusted” images hosted by Docker, Inc including the official Ubuntu and other base images.
|
||||
|
||||
The best option is to block `index.docker.io` locally, and download and verify images manually before importing them into Docker using `docker load`. Red Hat’s security blog has [a good post about this][18].
|
||||
|
||||
Thanks to Lewis Marshall for pointing out the tarsums are never verified.
|
||||
|
||||
- [Checksum code context][19].
|
||||
- [cloc][20] says 18,141 non-blank, non-comment lines of C and 5,900 lines of headers in v5.2.0.
|
||||
- Very similar bugs been [found in Android][21], which allowed arbitrary files to be injected into signed packages, and [the Windows Authenticode][22] signature system, which allowed binary modification.
|
||||
- Specifically: [CVE-2014-6407][23], [CVE-2014-9356][24], and [CVE-2014-9357][25]. There were two Docker [security releases][26] in response.
|
||||
- See page 8 of the [notes from the 2014-10-28 DGAB meeting][27].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://titanous.com/posts/docker-insecurity
|
||||
|
||||
作者:[titanous][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://twitter.com/titanous
|
||||
[1]:https://blog.docker.com/2014/10/docker-1-3-signed-images-process-injection-security-options-mac-shared-directories/
|
||||
[2]:https://blog.docker.com/2014/10/docker-1-3-signed-images-process-injection-security-options-mac-shared-directories/
|
||||
[3]:https://titanous.com/posts/docker-insecurity#fn:0
|
||||
[4]:https://en.wikipedia.org/wiki/Memory_safety
|
||||
[5]:https://github.com/docker/docker/blob/0874f9ab77a7957633cd835241a76ee4406196d8/pkg/archive/archive.go#L91-L95
|
||||
[6]:http://tukaani.org/xz/
|
||||
[7]:https://titanous.com/posts/docker-insecurity#fn:1
|
||||
[8]:https://github.com/docker/docker/blob/0874f9ab77a7957633cd835241a76ee4406196d8/pkg/tarsum/tarsum_spec.md
|
||||
[9]:https://titanous.com/posts/docker-insecurity#fn:2
|
||||
[10]:https://titanous.com/posts/docker-insecurity#fn:3
|
||||
[11]:https://github.com/docker/libtrust
|
||||
[12]:https://tools.ietf.org/html/draft-ietf-jose-json-web-signature-11
|
||||
[13]:https://titanous.com/posts/docker-insecurity#fn:4
|
||||
[14]:https://github.com/docker/docker/blob/0874f9ab77a7957633cd835241a76ee4406196d8/trust/trusts.go#L38
|
||||
[15]:https://github.com/docker/docker/issues/9719
|
||||
[16]:http://theupdateframework.com/
|
||||
[17]:https://github.com/flynn/go-tuf
|
||||
[18]:https://securityblog.redhat.com/2014/12/18/before-you-initiate-a-docker-pull/
|
||||
[19]:https://github.com/docker/docker/blob/0874f9ab77a7957633cd835241a76ee4406196d8/image/image.go#L114-L116
|
||||
[20]:http://cloc.sourceforge.net/
|
||||
[21]:http://www.saurik.com/id/17
|
||||
[22]:http://blogs.technet.com/b/srd/archive/2013/12/10/ms13-098-update-to-enhance-the-security-of-authenticode.aspx
|
||||
[23]:https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6407
|
||||
[24]:https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-9356
|
||||
[25]:https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-9357
|
||||
[26]:https://groups.google.com/d/topic/docker-user/nFAz-B-n4Bw/discussion
|
||||
[27]:https://docs.google.com/document/d/1JfWNzfwptsMgSx82QyWH_Aj0DRKyZKxYQ1aursxNorg/edit?pli=1
|
||||
@ -1,76 +0,0 @@
|
||||
How to deduplicate files on Linux with dupeGuru
|
||||
================================================================================
|
||||
Recently, I was given the task to clean up my father's files and folders. What made it difficult was the abnormal amount of duplicate files with incorrect names. By keeping a backup on an external drive, simultaneously editing multiple versions of the same file, or even changing the directory structure, the same file can get copied many times, change names, change locations, and just clog disk space. Hunting down every single one of them can become a problem of gigantic proportions. Hopefully, there exists nice little software that can save your precious hours by finding and removing duplicate files on your system: [dupeGuru][1]. Written in Python, this file deduplication software switched to a GPLv3 license a few hours ago. So time to apply your new year's resolutions and clean up your stuff!
|
||||
|
||||
### Installation of dupeGuru ###
|
||||
|
||||
On Ubuntu, you can add the Hardcoded Software PPA:
|
||||
|
||||
$ sudo apt-add-repository ppa:hsoft/ppa
|
||||
$ sudo apt-get update
|
||||
|
||||
And then install with:
|
||||
|
||||
$ sudo apt-get install dupeguru-se
|
||||
|
||||
On Arch Linux, the package is present in the [AUR][2].
|
||||
|
||||
If you prefer compiling it yourself, the sources are on [GitHub][3].
|
||||
|
||||
### Basic Usage of dupeGuru ###
|
||||
|
||||
DupeGuru is conceived to be fast and safe. Which means that the program is not going to run berserk on your system. It has a very low risk of deleting stuff that you did not intend to delete. However, as we are still talking about file deletion, it is always a good idea to stay vigilant and cautious: a good backup is always necessary.
|
||||
|
||||
Once you took your precautions, you can launch dupeGuru via the command:
|
||||
|
||||
$ dupeguru_se
|
||||
|
||||
You should be greeted by the folder selection screen, where you can add folders to scan for deduplication.
|
||||
|
||||

|
||||
|
||||
Once you selected your directories and launched the scan, dupeGuru will show its results by grouping duplicate files together in a list.
|
||||
|
||||

|
||||
|
||||
Note that by default dupeGuru matches files based on their content, and not their name. To be sure that you do not accidentally delete something important, the match column shows you the accuracy of the matching algorithm. From there, you can select the duplicate files that you want to take action on, and click on "Actions" button to see available actions.
|
||||
|
||||

|
||||
|
||||
The choice of actions is quite extensive. In short, you can delete the duplicates, move them to another location, ignore them, open them, rename them, or even invoke a custom command on them. If you choose to delete a duplicate, you might get as pleasantly surprised as I was by available deletion options.
|
||||
|
||||

|
||||
|
||||
You can not only send the duplicate files to the trash or delete them permanently, but you can also choose to leave a link to the original file (either using a symlink or a hardlink). In oher words, the duplicates will be erased, and a link to the original will be left instead, saving a lot of disk space. This can be particularly useful if you imported those files into a workspace, or have dependencies based on them.
|
||||
|
||||
Another fancy option: you can export the results to a HTML or CSV file. Not really sure why you would do that, but I suppose that it can be useful if you prefer keeping track of duplicates rather than use any of dupeGuru's actions on them.
|
||||
|
||||
Finally, last but not least, the preferences menu will make all your dream about duplicate busting come true.
|
||||
|
||||

|
||||
|
||||
There you can select the criterion for the scan, either content based or name based, and a threshold for duplicates to control the number of results. It is also possible to define the custom command that you can select in the actions. Among the myriad of other little options, it is good to notice that by default, dupeGuru ignores files less than 10KB.
|
||||
|
||||
For more information, I suggest that you go check out the [official website][4], which is filled with documention, support forums, and other goodies.
|
||||
|
||||
To conclude, dupeGuru is my go-to software whenever I have to prepare a backup or to free some space. I find it powerful enough for advanced users, and yet intuitive to use for newcomers. Cherry on the cake: dupeGuru is cross platform, which means that you can also use it for your Mac or Windows PC. If you have specific needs, and want to clean up music or image files, there exists two variations: [dupeguru-me][5] and [dupeguru-pe][6], which respectively find duplicate audio tracks and pictures. The main difference from the regular version is that it compares beyond file formats and takes into account specific media meta-data like quality and bit-rate.
|
||||
|
||||
What do you think of dupeGuru? Would you consider using it? Or do you have any alternative deduplication software to suggest? Let us know in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/dupeguru-deduplicate-files-linux.html
|
||||
|
||||
作者:[Adrien Brochard][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/adrien
|
||||
[1]:http://www.hardcoded.net/dupeguru/
|
||||
[2]:https://aur.archlinux.org/packages/dupeguru-se/
|
||||
[3]:https://github.com/hsoft/dupeguru
|
||||
[4]:http://www.hardcoded.net/dupeguru/
|
||||
[5]:http://www.hardcoded.net/dupeguru_me/
|
||||
[6]:http://www.hardcoded.net/dupeguru_pe/
|
||||
@ -1,71 +0,0 @@
|
||||
How to Install SSL on Apache 2.4 in Ubuntu 14.0.4
|
||||
================================================================================
|
||||
Today I will show you how to install a **SSL certificate** on your personal website or blog, to help secure the communications between your visitors and your website.
|
||||
|
||||
Secure Sockets Layer or SSL, is the standard security technology for creating an encrypted connection between a web server and a web browser. This ensures that all data passed between the web server and the web browser remain private and secure. It is used by millions of websites in the protection of their online communications with their customers. In order to be able to generate an SSL link, a web server requires a SSL Certificate.
|
||||
|
||||
You can create your own SSL Certificate, but it will not be trusted by default in web browsers, to fix this you will have to buy a digital certificate from a trusted Certification Authority (CA), we will show you below how to get the certificate and install it in apache.
|
||||
|
||||
### Generating a Certificate Signing Request ###
|
||||
|
||||
The Certification Authority (CA) will ask you for a Certificate Signing Request (CSR) generated on your web server. This is a simple step and only takes a minute, you will have to run the following command and input the requested information:
|
||||
|
||||
# openssl req -new -newkey rsa:2048 -nodes -keyout yourdomainname.key -out yourdomainname.csr
|
||||
|
||||
The output should look something like this:
|
||||
|
||||

|
||||
|
||||
This begins the process of generating two files: the Private-Key file for the decryption of your SSL Certificate, and a certificate signing request (CSR) file (used to apply for your SSL Certificate) with apache openssl.
|
||||
|
||||
Depending on the authority you apply to, you will either have to upload your csr file or paste it's content in a web form.
|
||||
|
||||
### Installing the actual certificate in Apache ###
|
||||
|
||||
After the generation process is finished you will receive your new digital certificate, for this article we have used [Comodo SSL][1] and received the certificate in a zip file. To use it in apache you will first have to create a bundle of the certificates you received in the zip file with the following command:
|
||||
|
||||
# cat COMODORSADomainValidationSecureServerCA.crt COMODORSAAddTrustCA.crt AddTrustExternalCARoot.crt > bundle.crt
|
||||
|
||||

|
||||
|
||||
Now make sure that the ssl module is loaded in apache by running the following command:
|
||||
|
||||
# a2enmod ssl
|
||||
|
||||
If you get the message "Module ssl already enabled" you are ok, if you get the message "Enabling module ssl." you will also have to run the following command to restart apache:
|
||||
|
||||
# service apache2 restart
|
||||
|
||||
Finally modify your virtual host file (generally found in /etc/apache2/sites-enabled) to look something like this:
|
||||
|
||||
DocumentRoot /var/www/html/
|
||||
ServerName linoxide.com
|
||||
SSLEngine on
|
||||
SSLCertificateFile /usr/local/ssl/crt/yourdomainname.crt
|
||||
SSLCertificateKeyFile /usr/local/ssl/yourdomainname.key
|
||||
SSLCACertificateFile /usr/local/ssl/bundle.crt
|
||||
|
||||
You should now access your website using https://YOURDOMAIN/ (be careful to use 'https' not http) and see the SSL in progress (generally indicated by a lock in your web browser).
|
||||
|
||||
**NOTE:** All the links must now point to https, if some of the content on the website (like images or css files) still point to http links you will get a warning in the browser, to fix this you have to make sure that every link points to https.
|
||||
|
||||
### Redirect HTTP requests to HTTPS version of your website ###
|
||||
|
||||
If you wish to redirect the normal HTTP requests to HTTPS version of your website, add the following text to either the virtual host you wish to apply it to or to the apache.conf if you wish to apply it for all websites hosted on the server:
|
||||
|
||||
RewriteEngine On
|
||||
RewriteCond %{HTTPS} off
|
||||
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/ubuntu-how-to/install-ssl-apache-2-4-in-ubuntu/
|
||||
|
||||
作者:[Adrian Dinu][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/adriand/
|
||||
[1]:https://ssl.comodo.com/
|
||||
@ -1,129 +0,0 @@
|
||||
How to Install Scrapy a Web Crawling Tool in Ubuntu 14.04 LTS
|
||||
================================================================================
|
||||
It is an open source software which is used for extracting the data from websites. Scrapy framework is developed in Python and it perform the crawling job in fast, simple and extensible way. We have created a Virtual Machine (VM) in virtual box and Ubuntu 14.04 LTS is installed on it.
|
||||
|
||||
### Install Scrapy ###
|
||||
|
||||
Scrapy is dependent on Python, development libraries and pip software. Python latest version is pre-installed on Ubuntu. So we have to install pip and python developer libraries before installation of Scrapy.
|
||||
|
||||
Pip is the replacement for easy_install for python package indexer. It is used for installation and management of Python packages. Installation of pip package is shown in Figure 1.
|
||||
|
||||
sudo apt-get install python-pip
|
||||
|
||||

|
||||
|
||||
Fig:1 Pip installation
|
||||
|
||||
We have to install python development libraries by using following command. If this package is not installed then installation of scrapy framework generates error about python.h header file.
|
||||
|
||||
sudo apt-get install python-dev
|
||||
|
||||

|
||||
|
||||
Fig:2 Python Developer Libraries
|
||||
|
||||
Scrapy framework can be installed either from deb package or source code. However we have installed deb package using pip (Python package manager) which is shown in Figure 3.
|
||||
|
||||
sudo pip install scrapy
|
||||
|
||||

|
||||
|
||||
Fig:3 Scrapy Installation
|
||||
|
||||
Scrapy successful installation takes some time which is shown in Figure 4.
|
||||
|
||||

|
||||
|
||||
Fig:4 Successful installation of Scrapy Framework
|
||||
|
||||
### Data extraction using Scrapy framework ###
|
||||
|
||||
**(Basic Tutorial)**
|
||||
|
||||
We will use Scrapy for the extraction of store names (which are providing Cards) item from fatwallet.com web site. First of all, we created new scrapy project “store_name” using below given command and shown in Figure 5.
|
||||
|
||||
$sudo scrapy startproject store_name
|
||||
|
||||

|
||||
|
||||
Fig:5 Creation of new project in Scrapy Framework
|
||||
|
||||
Above command creates a directory with title “store_name” at current path. This main directory of the project contains files/folders which are shown in the following Figure 6.
|
||||
|
||||
$sudo ls –lR store_name
|
||||
|
||||

|
||||
|
||||
Fig:6 Contents of store_name project.
|
||||
|
||||
A brief description of each file/folder is given below;
|
||||
|
||||
- scrapy.cfg is the project configuration file
|
||||
- store_name/ is another directory inside the main directory. This directory contains python code of the project.
|
||||
- store_name/items.py contains those items which will be extracted by the spider.
|
||||
- store_name/pipelines.py is the pipelines file.
|
||||
- Setting of store_name project is in store_name/settings.py file.
|
||||
- and the store_name/spiders/ directory, contains spider for the crawling
|
||||
|
||||
As we are interested to extract the store names of the Cards from fatwallet.com site, so we updated the contents of the file as shown below.
|
||||
|
||||
import scrapy
|
||||
|
||||
class StoreNameItem(scrapy.Item):
|
||||
|
||||
name = scrapy.Field() # extract the names of Cards store
|
||||
|
||||
After this, we have to write new spider under store_name/spiders/ directory of the project. Spider is python class which consist of following mandatory attributes :
|
||||
|
||||
1. Name of the spider (name )
|
||||
1. Starting url of spider for crawling (start_urls)
|
||||
1. And parse method which consist of regex for the extraction of desired items from the page response. Parse method is the important part of spider.
|
||||
|
||||
We created spider “store_name.py” under store_name/spiders/ directory and added following python code for the extraction of store name from fatwallet.com site. The output of the spider is written in the file (**StoreName.txt**) which is shown in Figure 7.
|
||||
|
||||
from scrapy.selector import Selector
|
||||
from scrapy.spider import BaseSpider
|
||||
from scrapy.http import Request
|
||||
from scrapy.http import FormRequest
|
||||
import re
|
||||
class StoreNameItem(BaseSpider):
|
||||
name = "storename"
|
||||
allowed_domains = ["fatwallet.com"]
|
||||
start_urls = ["http://fatwallet.com/cash-back-shopping/"]
|
||||
|
||||
def parse(self,response):
|
||||
output = open('StoreName.txt','w')
|
||||
resp = Selector(response)
|
||||
|
||||
tags = resp.xpath('//tr[@class="storeListRow"]|\
|
||||
//tr[@class="storeListRow even"]|\
|
||||
//tr[@class="storeListRow even last"]|\
|
||||
//tr[@class="storeListRow last"]').extract()
|
||||
for i in tags:
|
||||
i = i.encode('utf-8', 'ignore').strip()
|
||||
store_name = ''
|
||||
if re.search(r"class=\"storeListStoreName\">.*?<",i,re.I|re.S):
|
||||
store_name = re.search(r"class=\"storeListStoreName\">.*?<",i,re.I|re.S).group()
|
||||
store_name = re.search(r">.*?<",store_name,re.I|re.S).group()
|
||||
store_name = re.sub(r'>',"",re.sub(r'<',"",store_name,re.I))
|
||||
store_name = re.sub(r'&',"&",re.sub(r'&',"&",store_name,re.I))
|
||||
#print store_name
|
||||
output.write(store_name+""+"\n")
|
||||
|
||||

|
||||
|
||||
Fig:7 Output of the Spider code .
|
||||
|
||||
*NOTE: The purpose of this tutorial is only the understanding of Scrapy Framework*
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/ubuntu-how-to/scrapy-install-ubuntu/
|
||||
|
||||
作者:[nido][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/naveeda/
|
||||
@ -1,68 +1,68 @@
|
||||
ChromeOS 对战 Linux : 孰优孰劣,仁者见仁,智者见智
|
||||
ChromeOS 对战 Linux : 孰优孰劣,仁者见仁,智者见智(校对意见:真善美假恶丑)
|
||||
================================================================================
|
||||
> 在 ChromeOS 和 Linux 的斗争过程中,不管是哪一家的操作系统都是有优有劣。
|
||||
> 在 ChromeOS 和 Linux 的斗争过程中,两个桌面环境都有强有弱,这两者又有怎样的真善美假恶丑?
|
||||
|
||||
任何不关注Google 的人都不会相信Google在桌面用户当中扮演着一个很重要的角色。在近几年,我们见到的[ChromeOS][1]制造的[Google Chromebook][2]相当的轰动。和同期的人气火爆的Amazon 一样,似乎ChromeOS 势不可挡。
|
||||
只要稍加留意,任何人都会相信,Google在桌面领域绝不是“玩玩而已”。在近几年,我们见到的[ChromeOS][1]制造的[Google Chromebook][2]相当的轰动。和同期人气火爆的Amazon 一样,ChromeOS 似乎势不可挡。
|
||||
|
||||
在本文中,我们要了解的是ChromeOS 的概念市场,ChromeOS 怎么影响着Linux 的份额,和整个 ChromeOS 对于linux 社区来说,是好事还是坏事。另外,我将会谈到一些重大的事情,和为什么没人去为他做点什么事情。
|
||||
在本文中,我们要了解的是ChromeOS 的概念市场,ChromeOS 怎么影响着Linux 的份额,整个 ChromeOS 对于linux 社区来说,是好事还是坏事。另外,我将会谈到一些重大问题,以及为什么没人针对这些问题做点什么。
|
||||
|
||||
### ChromeOS 并非真正的Linux ###
|
||||
|
||||
每当有朋友问我说是否ChromeOS 是否是Linux 的一个版本时,我都会这样回答:ChromeOS 对于Linux 就好像是 OS X 对于BSD 。换句话说,我认为,ChromeOS 是linux 的一个派生操作系统,运行于Linux 内核的引擎之下。而很多操作系统就组成了Google 的专利代码和软件。
|
||||
每当有朋友问我说ChromeOS 是否是Linux 的一个发行版时,我都会这样回答:ChromeOS 对于Linux 就好像是 OS X 对于BSD 。换句话说,我认为,ChromeOS 是linux 的一个派生操作系统,运行于Linux 内核的引擎之下。而多个操作系统则组成了Google 的专利代码及软件。
|
||||
|
||||
尽管ChromeOS 是利用了Linux 内核引擎,但是它仍然有很大的不同和现在流行的Linux 分支版本。
|
||||
尽管ChromeOS 是利用了Linux 的内核引擎,但是和现在流行的Linux 分支版本相比,它仍然有很大的不同。
|
||||
|
||||
尽管ChromeOS 的差异化越来越明显,是在于它给终端用户提供的app,包括Web 应用。因为ChromeOS 的每一个操作都是开始于浏览器窗口,这对于Linux 用户来说,可能会有很多不一样的感受,但是,对于没有Linux 经验的用户来说,这与他们使用的旧电脑并没有什么不同。
|
||||
其实,ChromeOS 的差异化越来越明显,是在于它给终端用户提供的包括Web 应用在内的app。因为ChromeOS 的每一个操作都是开始于浏览器窗口,这对于Linux 用户来说,可能会有很多不一样的感受,但是,对于没有Linux 经验的用户来说,这与他们使用的旧电脑并没有什么不同。
|
||||
|
||||
就是说,每一个以Google-centric 为生活方式的人来说,在ChromeOS上的感觉将会非常良好,就好像是回家一样。这样的优势就是这个人已经接受了Chrome 浏览器,Google 驱动器和Gmail 。久而久之,他们的亲朋好友使用ChromeOs 也就是很自然的事情了,就好像是他们很容易接受Chrome 浏览器,因为他们觉得早已经用过。
|
||||
比方说,每一个以“依赖Google产品”为生活方式的人来说,在ChromeOS上的感觉将会非常良好,就好像是回家一样。这样的优势就是这个人已经接受了Chrome 浏览器,Google Drive 云存储和Gmail 。久而久之,他们使用ChromeOS 也就是很自然的事情了,因为他们很容易接受使用早已习惯的Chrome 浏览器。
|
||||
|
||||
然而,对于Linux 爱好者来说,这样的约束就立即带来了不适应。因为软件的选择被限制,有范围的,在加上要想玩游戏和VoIP 是完全不可能的。那么对不起,因为[GooglePlus Hangouts][3]是代替不了VoIP 软件的。甚至在很长的一段时间里。
|
||||
然而,对于Linux 爱好者来说,这样的约束就立即带来了不适应。因为软件的选择是被限制、被禁锢的,再加上要想玩游戏和VoIP 是完全不可能的。对不起,因为[GooglePlus Hangouts][3]是代替不了VoIP 软件的。甚至这种情况将持续很长一段时间。
|
||||
|
||||
### ChromeOS 还是Linux 桌面 ###
|
||||
|
||||
有人断言,ChromeOS 要是想在桌面系统的浪潮中对Linux 产生影响,只有在Linux 停下来浮出水面栖息的时候或者是满足某个非技术用户的时候。
|
||||
有人断言,ChromeOS 要是想在桌面系统的浪潮中对Linux 产生影响,只有在Linux 停下来浮出水面栖息的时候,或者是满足某个非技术用户的时候。
|
||||
|
||||
是的,桌面Linux 对于大多数休闲型的用户来说绝对是一个好东西。然而,它必须有专人帮助你安装操作系统,并且提供“维修”服务,从windows 和 OS X 的阵营来看。但是,令人失望的是,在美国Linux 正好在这个方面很缺乏。所以,我们看到,ChromeOS 正慢慢的走入我们的视线。
|
||||
是的,桌面Linux 对于大多数休闲型的用户来说绝对是一个好东西。然而,它必须有专人帮助你安装操作系统,并且提供“维修”服务,就如同我们在windows 和 OS X 阵营看到的一样。但是,令人失望的是,在美国Linux 正好在这个方面很缺乏。所以,我们看到,ChromeOS 正慢慢的走入我们的视线。
|
||||
|
||||
我发现Linux 桌面系统最适合做网上技术支持来管理。比如说:家里的高级用户可以操作和处理更新政府和学校的IT 部门。Linux 还可以应用于这样的环境,Linux桌面系统可以被配置给任何技能水平和背景的人使用。
|
||||
我发现Linux 桌面系统最适合那些能够提供在线技术支持的环境中。比如说:可以在家里操作和处理更新的高级用户、政府和学校的IT 部门等等。这些环境中,Linux桌面系统可以被配置给任何技能水平和背景的人使用。
|
||||
|
||||
相比之下,ChromeOS 是建立在完全免维护的初衷之下的,因此,不需要第三者的帮忙,你只需要允许更新,然后让他静默完成即可。这在一定程度上可能是由于ChromeOS 是为某些特定的硬件结构设计的,这与苹果开发自己的PC 电脑也有异曲同工之妙。因为Google 的ChromeOS 附带一个硬件脉冲,它允许“犯错误”。对于某些人来说,这是一个很奇妙的地方。
|
||||
|
||||
滑稽的是,有些人却宣称,ChomeOs 的远期的市场存在很多问题。简言之,这只是一些Linux 激情的爱好者在找对于ChomeOS 的抱怨罢了。在我看来,停止造谣这些子虚乌有的事情才是关键。
|
||||
然而有些人则认为这是一个很严重的问题,不过滑稽的是,对ChomeOS来说,这些人压根就不在它的目标市场里。简言之,这只是一些狂热的Linux爱好者在对ChomeOS 鸡蛋里挑骨头罢了。要我说,还是停止这些子虚乌有的造谣吧。
|
||||
|
||||
问题是:ChromeOS 的市场份额和Linux 桌面系统在很长的一段时间内是不同的。这个存在可能会在将来被打破,然而在现在,仍然会是两军对峙的局面。
|
||||
问题的关键在于:ChromeOS 的市场份额和Linux 桌面系统在很长的一段时间内是不同的。这个局面可能会在将来被打破,然而在现在,仍然会是两军对峙的局面。
|
||||
|
||||
### ChromeOS 的使用率正在增长 ###
|
||||
|
||||
不管你对ChromeOS 有怎么样的看法,事实是,ChromeOS 的使用率正在增长。专门针对ChromeOS 的电脑也一直有发布。最近,戴尔(Dell)也发布了一款针对ChromeOS 的电脑。命名为[Dell Chromebox][5],这款ChromeOS 设备将会是另一些传统设备的终结者。它没有软件光驱,没有反病毒软件,offers 能够无缝的在屏幕后面自动更新。对于一般的用户,Chromebox 和Chromebook 正逐渐成为那些工作在web 浏览器上的人的一个选择。
|
||||
不管你对ChromeOS 有怎么样的看法,事实是,ChromeOS 的使用率正在增长。专门针对ChromeOS 的电脑也一直有发布。最近,戴尔(Dell)也发布了一款针对ChromeOS 的电脑。命名为[Dell Chromebox][5],这款ChromeOS 设备将会是对传统设备的又一次冲击。它没有软件光驱,没有反病毒软件,能够提供无缝的幕后自动更新。对于一般的用户,Chromebox 和Chromebook 正逐渐成为那些工作在web 浏览器上的人们的一个可靠选择。
|
||||
|
||||
尽管增长速度很快,ChromeOS 设备仍然面临着一个很严峻的问题 - 存储。受限于有限的硬盘的大小和严重依赖于云存储,并且ChromeOS 不会为了任何使用它们电脑的人消减基本的web 浏览器的功能。
|
||||
尽管增长速度很快,ChromeOS 设备仍然面临着一个很严峻的问题 - 存储。受限于有限的硬盘大小和严重依赖于云存储,ChromeOS 不会为了任何使用它们电脑的人消减基本的web 浏览器功能。
|
||||
|
||||
### ChromeOS 和Linux 的异同点 ###
|
||||
|
||||
以前,我注意到ChromeOS 和Linux 桌面系统分别占有着两个完全不同的市场。出现这样的情况是源于,Linux 社区的致力于提升Linux 桌面系统的脱机性能。
|
||||
以前,我注意到ChromeOS 和Linux 桌面系统分别占有着两个完全不同的市场。出现这样的情况是源于,Linux 社区在线下的桌面支持上一直都有着极其糟糕的表现。
|
||||
|
||||
是的,偶然的,有些人可能会第一时间发现这个“Linux 的问题”。但是,并没有一个人接着跟进这些问题,确保得到问题的答案,确保他们得到Linux 最多的帮助。
|
||||
是的,偶然的,有些人可能会第一时间发现这个“Linux特点”。但是,并没有一个人接着跟进这些问题,确保得到问题的答案,确保他们得到Linux 最多的帮助。
|
||||
|
||||
事实上,脱机故障可能是这样发现的:
|
||||
事实上,线下问题的出现可能是这样的:
|
||||
|
||||
- 有些用户偶然的在Linux 本地事件发现了Linux 的问题。
|
||||
- 有些用户偶然的在当地的Linux活动中发现了Linux。
|
||||
- 他们带回了DVD/USB 设备,并尝试安装这个操作系统。
|
||||
- 当然,有些人很幸运的成功的安装成功了这个进程,但是,据我所知大多数的人并没有那么幸运。
|
||||
- 令人失望的是,这些人希望在网上论坛里搜索帮助。很难做一个主计算机,没有网络和视频的问题。
|
||||
- 我真的是受够了,后来有很多失望的用户拿着他们的电脑到windows 商店来“维修”。除了重装一个windows 操作系统,他们很多时候都会听到一句话,“Linux 并不适合你们”,应该尽量避免。
|
||||
- 当然,有些人很幸运的成功完成了安装过程,但是,据我所知大多数的人并没有那么幸运。
|
||||
- 令人失望的是,这些人只能寄希望于在网上论坛里搜索帮助。他们很难通过主流的计算机网络经验或视频教程解决这些问题。
|
||||
-于是这些人受够了。后来有很多失望的用户拿着他们的电脑到windows 商店来“维修”。除了重装一个windows 操作系统,他们很多时候都会听到一句话,“Linux 并不适合你们”,应该尽量避免。
|
||||
|
||||
有些人肯定会说,上面的举例肯定夸大其词了。让我来告诉你:这是发生在我身边真实的事的,而且是经常发生。醒醒吧,Linux 社区的人们,我们的这种模式已经过时了。
|
||||
有些人肯定会说,上面的举例肯定夸大其词了。让我来告诉你:这是发生在我身边的真事,而且是经常发生。醒醒吧,Linux 社区的人们,我们的采纳模式早已破败、疲软了。
|
||||
|
||||
### 伟大的平台,强大的营销和结论 ###
|
||||
### 伟大的平台,糟糕的营销和最终结论 ###
|
||||
|
||||
如果非要说ChromeOS 和Linux 桌面系统相同的地方,除了它们都使用了Linux 内核,就是它们都伟大的产品却拥有极其差劲的市场营销。而Google 的好处就是,他们投入大量的资金在网上构建大面积存储空间。
|
||||
如果非要找一个ChromeOS 和Linux 桌面系统的共同点,除了它们都使用了Linux 内核,那就是它们都是伟大的产品却拥有极其差劲的市场营销。对此,Google 认为自己的优势是,它能投入大量的资金在网上构建大面积存储空间。
|
||||
|
||||
Google 相信他们拥有“网上的优势”,而线下的影响不是很重要。这真是一个让人难以置信的目光短浅,这也成了Google 历史上最大的一个失误之一。相信,如果你没有接触到他们在线的努力,你不值得困扰,仅仅就当是他们在是在选择网上存储空间上做出反击。
|
||||
Google 相信他们拥有“网上的优势”,而线下的努力不是很重要。这真是一个让人难以置信的目光短浅,这也成了Google 最严重的失误之一。而当地的Linux零售商则坚信,对于不怎么上网的人,自然不必担心他们会受到Google巨大的在线存储的诱惑。
|
||||
|
||||
我的建议是:通过Google 的线下影响,提供Linux 桌面系统给ChromeOS 的市场。这就意味着Linux 社区的人需要筹集资金来出席县博览会、商场展览,在节日季节,和在社区中进行免费的教学课程。这会立即使Linux 桌面系统走入人们的视线,否则,最终将会是一个ChromeOS 设备出现在人们的面前。
|
||||
我的建议是:Linux 可以通过线下的努力,提供桌面系统,渗透ChromeOS 市场。这就意味着Linux 社区需要在节假日筹集资金来出席博览会、商场展览,并且在社区中进行免费的教学课程。这会立即使Linux 桌面系统走入人们的视线,否则,最终将会是一个ChromeOS 设备出现在人们的面前。
|
||||
|
||||
如果说本地的线下市场并没有想我说的这样,别担心。Linux 桌面系统的市场仍然会像ChromeOS 一样增长。最坏也能保持现在这种两军对峙的市场局面。
|
||||
如果说本地的线下市场并没有像我说的这样,别担心。Linux 桌面系统的市场仍然会像ChromeOS 一样增长。最坏也能保持现在这种两军对峙的市场局面。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -70,7 +70,7 @@ via: http://www.datamation.com/open-source/chromeos-vs-linux-the-good-the-bad-an
|
||||
|
||||
作者:[Matt Hartley][a]
|
||||
译者:[barney-ro](https://github.com/barney-ro)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[Mr小眼儿](https://github.com/tinyeyeser)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
|
||||
@ -0,0 +1,155 @@
|
||||
如何使用Aptik来备份和恢复Ubuntu中的Apps和PPAs
|
||||
================================================================================
|
||||

|
||||
|
||||
当你想重装Ubuntu或者仅仅是想安装它的一个新版本的时候,寻到一个便捷的方法去重新安装之前的应用并且重置其设置是很有用的。此时 *Aptik* 粉墨登场,它可以帮助你轻松实现。
|
||||
|
||||
Aptik(自动包备份和回复)是一个可以用在Ubuntu,Linux Mint, 和其他基于Debian以及Ubuntu的Linux发行版上的应用,它允许你将已经安装过的包括软件库、下载包、安装的应用及其主题和设置在内的PPAs(个人软件包存档)备份到外部的U盘、网络存储或者类似于Dropbox的云服务上。
|
||||
|
||||
注意:当我们在此文章中说到输入某些东西的时候,如果被输入的内容被引号包裹,请不要将引号一起输入进去,除非我们有特殊说明。
|
||||
|
||||
想要安装Aptik,需要先添加其PPA。使用Ctrl + Alt + T快捷键打开一个新的终端窗口。输入以下文字,并按回车执行。
|
||||
|
||||
sudo apt-add-repository –y ppa:teejee2008/ppa
|
||||
|
||||
当提示输入密码的时候,输入你的密码然后按回车。
|
||||
|
||||

|
||||
|
||||
输入下边的命令到提示符旁边,来确保资源库已经是最新版本。
|
||||
|
||||
sudo apt-get update
|
||||
|
||||

|
||||
|
||||
更新完毕后,你就完成了安装Aptik的准备工作。接下来输入以下命令并按回车:
|
||||
|
||||
sudo apt-get install aptik
|
||||
|
||||
注意:你可能会看到一些有关于获取不到包更新的错误提示。不过别担心,如果这些提示看起来跟下边图片中类似的话,你的Aptik的安装就没有任何问题。
|
||||
|
||||

|
||||
|
||||
安装过程会被显示出来。其中一个被显示出来的消息会提到此次安装会使用掉多少磁盘空间,然后提示你是否要继续,按下“y”再按回车,继续安装。
|
||||
|
||||

|
||||
|
||||
当安装完成后,输入“Exit”并按回车或者按下左上角的“X”按钮,关闭终端窗口。
|
||||
|
||||

|
||||
|
||||
在正式运行Aptik前,你需要设置好备份目录到一个U盘、网络驱动器或者类似于Dropbox和Google Drive的云帐号上。这儿的例子中,我们使用的是Dropbox。
|
||||
|
||||

|
||||
|
||||
一旦设置好备份目录,点击启动栏上方的“Search”按钮。
|
||||
|
||||

|
||||
|
||||
在搜索框中键入 “aptik”。结果会随着你的输入显示出来。当Aptik图标显示出来的时候,点击它打开应用。
|
||||
|
||||

|
||||
|
||||
此时一个对话框会显示出来要求你输入密码。输入你的密码并按“OK”按钮。
|
||||
|
||||

|
||||
|
||||
Aptik的主窗口显示出来了。从“Backup Directory”下拉列表中选择“Other…”。这个操作允许你选择你已经建立好的备份目录。
|
||||
|
||||
注意:在下拉列表的右侧的 “Open” 按钮会在一个文件管理窗口中打开选择目录功能。
|
||||
|
||||

|
||||
|
||||
在 “Backup Directory” 对话窗口中,定位到你的备份目录,然后按“Open”。
|
||||
|
||||
注意:如果此时你尚未建立备份目录或者想在备份目录中新建个子目录,你可以点“Create Folder”来新建目录。
|
||||
|
||||

|
||||
|
||||
点击“Software Sources (PPAs).”右侧的 “Backup”来备份已安装的PPAs。
|
||||
|
||||

|
||||
|
||||
然后“Backup Software Sources”对话窗口显示出来。已安装的包和对应的源(PPA)同时也显示出来了。选择你需要备份的源(PPAs),或者点“Select All”按钮选择所有源。
|
||||
|
||||

|
||||
|
||||
点击 “Backup” 开始备份。
|
||||
|
||||

|
||||
|
||||
备份完成后,一个提示你备份完成的对话窗口会蹦出来。点击 “OK” 关掉。
|
||||
|
||||
一个名为“ppa.list”的文件出现在了备份目录中。
|
||||
|
||||

|
||||
|
||||
接下来,“Downloaded Packages (APT Cache)”的项目只对重装同样版本的Ubuntu有用处。它会备份下你系统缓存(/var/cache/apt/archives)中的包。如果你是升级系统的话,可以跳过这个条目,因为针对新系统的包会比现有系统缓存中的包更加新一些。
|
||||
|
||||
备份和回复下载过的包,这可以在重装Ubuntu,并且重装包的时候节省时间和网络带宽。因为一旦你把这些包恢复到系统缓存中之后,他们可以重新被利用起来,这样下载过程就免了,包的安装会更加快捷。
|
||||
|
||||
如果你是重装相同版本的Ubuntu系统的话,点击 “Downloaded Packages (APT Cache)” 右侧的 “Backup” 按钮来备份系统缓存中的包。
|
||||
|
||||
注意:当你备份下载过的包的时候是没有二级对话框出现。你系统缓存 (/var/cache/apt/archives) 中的包会被拷贝到备份目录下一个名叫 “archives” 的文件夹中,当整个过程完成后会出现一个对话框来告诉你备份已经完成。
|
||||
|
||||

|
||||
|
||||
有一些包是你的Ubuntu发行版的一部分。因为安装Ubuntu系统的时候会自动安装它们,所以它们是不会被备份下来的。例如,火狐浏览器在Ubuntu和其他类似Linux发行版上都是默认被安装的,所以默认情况下,它不会被选择备份。
|
||||
|
||||
像[package for the Chrome web browser][1]这种系统安装完后才安装的包或者包含 Aptik 的包会默认被选择上。这可以方便你备份这些后安装的包。
|
||||
|
||||
按照需要选择想要备份的包。点击 “Software Selections” 右侧的 “Backup” 按钮备份顶层包。
|
||||
|
||||
注意:依赖包不会出现在这个备份中。
|
||||
|
||||

|
||||
|
||||
名为 “packages.list” and “packages-installed.list” 的两个文件出现在了备份目录中,并且一个用来通知你备份完成的对话框出现。点击 ”OK“关闭它。
|
||||
|
||||
注意:“packages-installed.list”文件包含了所有的包,而 “packages.list” 在包含了所有包的前提下还指出了那些包被选择上了。
|
||||
|
||||

|
||||
|
||||
要备份已安装软件的设置的话,点击 Aptik 主界面 “Application Settings” 右侧的 “Backup” 按钮,选择你要备份的设置,点击“Backup”。
|
||||
|
||||
注意:如果你要选择所有设置,点击“Select All”按钮。
|
||||
|
||||

|
||||
|
||||
被选择的配置文件统一被打包到一个名叫 “app-settings.tar.gz” 的文件中。
|
||||
|
||||

|
||||
|
||||
当打包完成后,打包后的文件被拷贝到备份目录下,另外一个备份成功的对话框出现。点击”OK“,关掉。
|
||||
|
||||

|
||||
|
||||
来自 “/usr/share/themes” 目录的主题和来自 “/usr/share/icons” 目录的图标也可以备份。点击 “Themes and Icons” 右侧的 “Backup” 来进行此操作。“Backup Themes” 对话框默认选择了所有的主题和图标。你可以安装需要取消到一些然后点击 “Backup” 进行备份。
|
||||
|
||||

|
||||
|
||||
主题被打包拷贝到备份目录下的 “themes” 文件夹中,图标被打包拷贝到备份目录下的 “icons” 文件夹中。然后成功提示对话框出现,点击”OK“关闭它。
|
||||
|
||||

|
||||
|
||||
一旦你完成了需要的备份,点击主界面左上角的”X“关闭 Aptik 。
|
||||
|
||||

|
||||
|
||||
备份过的文件已存在于你选择的备份目录中,可以随时取阅。
|
||||
|
||||

|
||||
|
||||
当你重装Ubuntu或者安装新版本的Ubuntu后,在新的系统中安装 Aptik 并且将备份好的文件置于新系统中让其可被使用。运行 Aptik,并使用每个条目的 “Restore” 按钮来恢复你的软件源、应用、包、设置、主题以及图标。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.howtogeek.com/206454/how-to-backup-and-restore-your-apps-and-ppas-in-ubuntu-using-aptik/
|
||||
|
||||
作者:Lori Kaufman
|
||||
译者:[Ping](https://github.com/mr-ping)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.howtogeek.com/203768
|
||||
@ -6,7 +6,7 @@
|
||||
|
||||
虽然对于本教程,我只会演示怎样来添加**64位**网络安装镜像,但对于Ubuntu或者Debian的**32位**系统,或者其它架构的镜像,操作步骤也基本相同。同时,就我而言,我会解释添加Ubuntu 32位源的方法,但不会演示配置。
|
||||
|
||||
从PXE服务器安装 **Ubuntu**或者**Debian**要求你的客户机必须激活网络连接,最好是使用**DHCP**通过**NAT**来进行动态分配地址。以便安装器拉取需求包并完成安装进程。
|
||||
从PXE服务器安装 **Ubuntu**或者**Debian**要求你的客户机必须激活网络连接,最好是使用**DHCP**通过**NAT**来进行动态分配地址。以便安装器拉取所需的包并完成安装过程。
|
||||
|
||||
#### 需求 ####
|
||||
|
||||
@ -14,11 +14,11 @@
|
||||
|
||||
## 步骤 1: 添加Ubuntu 14.10和Ubuntu 14.04服务器到PXE菜单 ##
|
||||
|
||||
**1.** 为**Ubuntu 14.10**何**Ubuntu 14.04**添加网络安装源到PXE菜单可以通过两种方式实现:其一是通过下载Ubuntu CD ISO镜像并挂载到PXE服务器机器上以便可以读取Ubuntu网络启动文件,其二是通过直接下载Ubuntu网络启动归档包并将其解压缩到系统中。下面,我将进一步讨论这两种方法:
|
||||
**1.** 为**Ubuntu 14.10**和**Ubuntu 14.04**添加网络安装源到PXE菜单可以通过两种方式实现:其一是通过下载Ubuntu CD ISO镜像并挂载到PXE服务器机器上以便可以读取Ubuntu网络启动文件,其二是通过直接下载Ubuntu网络启动归档包并将其解压缩到系统中。下面,我将进一步讨论这两种方法:
|
||||
|
||||
### 使用Ubuntu 14.10和Ubuntu 14.04 CD ISO镜像 ###
|
||||
|
||||
为了能使用此方法,你的PXE服务器需要有一台可工作的CD/DVD驱动器。在一台专有计算机上,转到[Ubuntu 14.10下载][2]和[Ubuntu 14.04 下载][3]页,抓取64位**服务器安装镜像**,将它烧录到CD,并将CD镜像放到PXE服务器DVD/CD驱动器,然后使用以下命令挂载到系统。
|
||||
为了能使用此方法,你的PXE服务器需要有一台可工作的CD/DVD驱动器。在一台专有计算机上,转到[Ubuntu 14.10下载][2]和[Ubuntu 14.04 下载][3]页,获取64位**服务器安装镜像**,将它烧录到CD,并将CD镜像放到PXE服务器DVD/CD驱动器,然后使用以下命令挂载到系统。
|
||||
|
||||
# mount /dev/cdrom /mnt
|
||||
|
||||
@ -26,28 +26,28 @@
|
||||
|
||||
#### 在Ubuntu 14.10上 ####
|
||||
|
||||
------------------ 32位上 ------------------
|
||||
------------------ 32位 ------------------
|
||||
|
||||
# wget http://releases.ubuntu.com/14.10/ubuntu-14.10-server-i386.iso
|
||||
# mount -o loop /path/to/ubuntu-14.10-server-i386.iso /mnt
|
||||
|
||||
----------
|
||||
|
||||
------------------ 64位上 ------------------
|
||||
------------------ 64位 ------------------
|
||||
|
||||
# wget http://releases.ubuntu.com/14.10/ubuntu-14.10-server-amd64.iso
|
||||
# mount -o loop /path/to/ubuntu-14.10-server-amd64.iso /mnt
|
||||
|
||||
#### 在Ubuntu 14.04上 ####
|
||||
|
||||
------------------ 32位上 ------------------
|
||||
------------------ 32位 ------------------
|
||||
|
||||
# wget http://releases.ubuntu.com/14.04/ubuntu-14.04.1-server-i386.iso
|
||||
# mount -o loop /path/to/ubuntu-14.04.1-server-i386.iso /mnt
|
||||
|
||||
----------
|
||||
|
||||
------------------ 64位上 ------------------
|
||||
------------------ 64位 ------------------
|
||||
|
||||
# wget http://releases.ubuntu.com/14.04/ubuntu-14.04.1-server-amd64.iso
|
||||
# mount -o loop /path/to/ubuntu-14.04.1-server-amd64.iso /mnt
|
||||
@ -58,33 +58,33 @@
|
||||
|
||||
#### 在Ubuntu 14.04上 ####
|
||||
|
||||
------------------ 32位上 ------------------
|
||||
------------------ 32位 ------------------
|
||||
|
||||
# cd
|
||||
# wget http://archive.ubuntu.com/ubuntu/dists/utopic/main/installer-i386/current/images/netboot/netboot.tar.gz
|
||||
|
||||
----------
|
||||
|
||||
------------------ 64位上 ------------------
|
||||
------------------ 64位 ------------------
|
||||
|
||||
# cd
|
||||
# http://archive.ubuntu.com/ubuntu/dists/utopic/main/installer-amd64/current/images/netboot/netboot.tar.gz
|
||||
|
||||
#### 在Ubuntu 14.04上 ####
|
||||
|
||||
------------------ 32位上 ------------------
|
||||
------------------ 32位 ------------------
|
||||
|
||||
# cd
|
||||
# wget http://archive.ubuntu.com/ubuntu/dists/trusty-updates/main/installer-i386/current/images/netboot/netboot.tar.gz
|
||||
|
||||
----------
|
||||
|
||||
------------------ 64位上 ------------------
|
||||
------------------ 64位 ------------------
|
||||
|
||||
# cd
|
||||
# wget http://archive.ubuntu.com/ubuntu/dists/trusty-updates/main/installer-amd64/current/images/netboot/netboot.tar.gz
|
||||
|
||||
对于其它处理器架构,请访问下面的Ubuntu 14.10和Ubuntu 14.04网络启动官方页面,选择你的架构类型并下载需求文件。
|
||||
对于其它处理器架构,请访问下面的Ubuntu 14.10和Ubuntu 14.04网络启动官方页面,选择你的架构类型并下载所需文件。
|
||||
|
||||
- [http://cdimage.ubuntu.com/netboot/14.10/][4]
|
||||
- [http://cdimage.ubuntu.com/netboot/14.04/][5]
|
||||
@ -101,7 +101,7 @@
|
||||
# tar xfz netboot.tar.gz
|
||||
# cp -rf ubuntu-installer/ /var/lib/tftpboot/
|
||||
|
||||
如果你想要在PXE服务器上同时使用两种Ubuntu服务器架构,先请下载,然后根据不同的情况挂载并解压缩32位并拷贝**ubuntu-installer**目录到**/var/lib/tftpboot**,然后卸载CD或删除网络启动归档以及解压缩的文件和文件夹。对于64位架构,请重复上述步骤,以便让最终的**tftp**路径形成以下结构。
|
||||
如果你想要在PXE服务器上同时使用两种Ubuntu服务器架构,先请下载,然后根据不同的情况挂载或解压缩32位架构,然后拷贝**ubuntu-installer**目录到**/var/lib/tftpboot**,然后卸载CD或删除网络启动归档以及解压缩的文件和文件夹。对于64位架构,请重复上述步骤,以便让最终的**tftp**路径形成以下结构。
|
||||
|
||||
/var/lib/tftpboot/ubuntu-installer/amd64
|
||||
/var/lib/tftpboot/ubuntu-installer/i386
|
||||
@ -238,7 +238,7 @@ via: http://www.tecmint.com/add-ubuntu-to-pxe-network-boot/
|
||||
|
||||
作者:[Matei Cezar][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[Mr小眼儿](https://github.com/tinyeyeser)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
|
||||
@ -0,0 +1,74 @@
|
||||
Linux 有问必答--Linux 中如何安装 7zip
|
||||
================================================================================
|
||||
> **问题**: 我需要要从 ISO 映像中获取某些文件,为此我想要使用 7zip 程序。那么我应该如何安装 7zip 软件呢,[在 Linux 发布版本上完全安装]?
|
||||
|
||||
7zip 是一款开源的归档应用程序,开始是为 Windows 系统而开发的。它能对多种格式的档案文件进行打包或解包处理,除了支持原生的 7z 格式的文档外,还支持包括 XZ、GZIP、TAR、ZIP 和 BZIP2 等这些格式。 一般地,7zip 也常用来解压 RAR、DEB、RPM 和 ISO 等格式的文件。除了简单的归档功能,7zip 还具有支持 AES-256 算法加密以及自解压和建立多卷存档功能。在以 POSIX 协议为标准的系统上(Linux、Unix、BSD),原生的 7zip 程序被移植过来并被命名为 p7zip(“POSIX 7zip” 的简称)。
|
||||
|
||||
下面介绍如何在 Linux 中安装 7zip (或 p7zip)。
|
||||
|
||||
### 在 Debian、Ubuntu 或 Linux Mint 系统中安装 7zip ###
|
||||
|
||||
在基于的 Debian 的发布系统中存在有三种 7zip 的软件包。
|
||||
|
||||
- **p7zip**: 包含 7zr(最小的 7zip 归档工具),仅仅只能处理原生的 7z 格式。
|
||||
- **p7zip-full**: 包含 7z ,支持 7z、LZMA2、XZ、ZIP、CAB、GZIP、BZIP2、ARJ、TAR、CPIO、RPM、ISO 和 DEB 格式。
|
||||
- **p7zip-rar**: 包含一个能解压 RAR 文件的插件。
|
||||
|
||||
建议安装 p7zip-full 包(不是 p7zip),因为这是最完全的 7zip 程序包,它支持很多归档格式。此外,如果您想处理 RAR 文件话,还需要安装 p7zip-rar 包,做成一个独立的插件包的原因是因为 RAR 是一种专有格式。
|
||||
|
||||
$ sudo apt-get install p7zip-full p7zip-rar
|
||||
|
||||
### 在 Fedora 或 CentOS/RHEL 系统中安装 7zip ###
|
||||
|
||||
基于红帽的发布系统上提供了两个 7zip 的软件包。
|
||||
|
||||
- **p7zip**: 包含 7za 命令,支持 7z、ZIP、GZIP、CAB、ARJ、BZIP2、TAR、CPIO、RPM 和 DEB 格式。
|
||||
- **p7zip-plugins**: 包含 7z 命令,额外的插件,它扩展了 7za 命令(例如 支持 ISO 格式的抽取)。
|
||||
|
||||
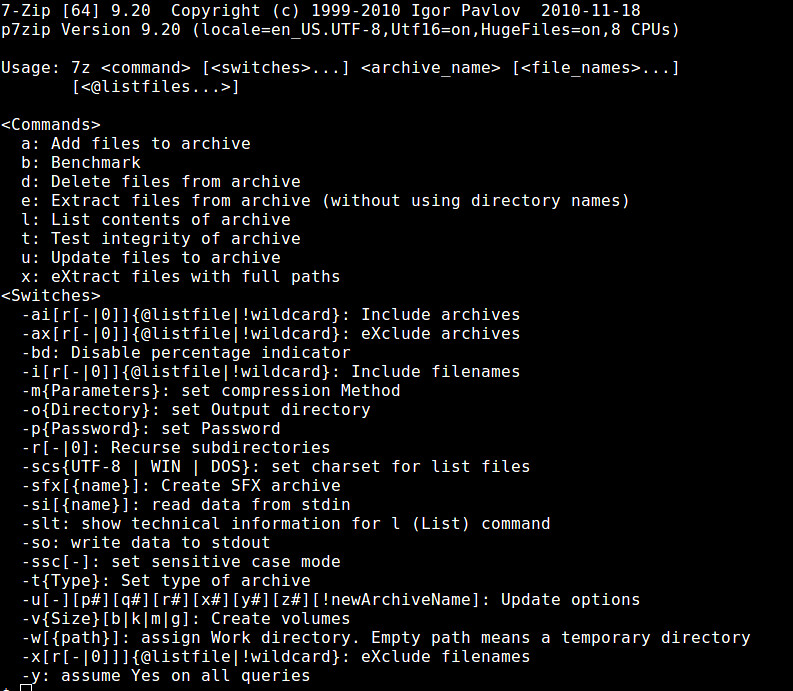
在 CentOS/RHEL 系统中,在运行下面命令前您需要确保 [EPEL 资源库][1] 可用,但在 Fedora 系统中就不需要额外的资源库了。
|
||||
|
||||
$ sudo yum install p7zip p7zip-plugins
|
||||
|
||||
注意,跟基于 Debian 的发布系统不同的是,基于红帽的发布系统没有提供 RAR 插件,所以您不能使用 7z 命令来抽取解压 RAR 文件。
|
||||
|
||||
### 使用 7z 创建或提取归档文件 ###
|
||||
|
||||
一旦安装好 7zip 软件后,就可以使用 7z 命令来打包解包各式各样的归档文件了。7z 命令会使用不同的插件来辅助处理对应格式的归档文件。
|
||||
|
||||

|
||||
|
||||
使用 “a” 选项就可以创建一个归档文件,它可以创建 7z、XZ、GZIP、TAR、 ZIP 和 BZIP2 这几种格式的文件。如果指定的归档文件已经存在的话,它会把文件“添加”到存在的归档中,而不是覆盖原有归档文件。
|
||||
|
||||
$ 7z a <archive-filename> <list-of-files>
|
||||
|
||||
使用 “e” 选项可以抽取出一个归档文件,抽取出的文件会放在当前目录。抽取支持的格式比创建时支持的格式要多的多,包括 7z、XZ、GZIP、TAR、ZIP、BZIP2、LZMA2、CAB、ARJ、CPIO、RPM、ISO 和 DEB 这些格式。
|
||||
|
||||
$ 7z e <archive-filename>
|
||||
|
||||
解包的另外一种方式是使用 “x” 选项。和 “e” 选项不同的是,它使用的是全路径来抽取归档的内容。
|
||||
|
||||
$ 7z x <archive-filename>
|
||||
|
||||
要查看归档的文件列表,使用 “l” 选项。
|
||||
|
||||
$ 7z l <archive-filename>
|
||||
|
||||
要更新或删除归档文件,分别使用 “u” 和 “d” 选项。
|
||||
|
||||
$ 7z u <archive-filename> <list-of-files-to-update>
|
||||
$ 7z d <archive-filename> <list-of-files-to-delete>
|
||||
|
||||
要测试归档的完整性,使用:
|
||||
|
||||
$ 7z t <archive-filename>
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via:http://ask.xmodulo.com/install-7zip-linux.html
|
||||
|
||||
译者:[runningwater](https://github.com/runningwater)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
|
||||
135
translated/tech/20150104 Docker Image Insecurity.md
Normal file
135
translated/tech/20150104 Docker Image Insecurity.md
Normal file
@ -0,0 +1,135 @@
|
||||
Docker的镜像并不安全!
|
||||
================================================================================
|
||||
最近使用Docker下载“官方”容器镜像的时候,我发现这样一句话:
|
||||
|
||||
ubuntu:14.04: The image you are pulling has been verified (您所拉取的镜像已经经过验证)
|
||||
|
||||
起初我以为这条信息引自Docker[大力推广][1]的镜像签名系统,因此也就没有继续跟进。后来,研究加密摘要系统的时候——Docker用这套系统来对镜像进行安全加固——我才有机会更深入的发现,逻辑上整个与镜像安全相关的部分具有一系列系统性问题。
|
||||
|
||||
Docker所报告的,一个已下载的镜像经过“验证”,它基于的仅仅是一个标记清单(signed manifest),而Docker却从未根据清单对镜像的校验和进行验证。一名攻击者以此可以提供任意所谓具有标记清单的镜像。一系列严重漏洞的大门就此敞开。
|
||||
|
||||
镜像经由HTTPS服务器下载后,通过一个未加密的管道流进入Docker守护进程:
|
||||
|
||||
[decompress] -> [tarsum] -> [unpack]
|
||||
|
||||
这条管道的性能没有问题,但是却完全没有经过加密。不可信的输入在签名验证之前是不应当进入管道的。不幸的是,Docker在上面处理镜像的三个步骤中,都没有对校验和进行验证。
|
||||
|
||||
然而,不论Docker如何[声明][2],实际上镜像的校验和从未经过校验。下面是Docker与镜像校验和的验证相关的代码[片段][3],即使我提交了校验和不匹配的镜像,都无法触发警告信息。
|
||||
|
||||
if img.Checksum != "" && img.Checksum != checksum {
|
||||
log.Warnf("image layer checksum mismatch: computed %q,
|
||||
expected %q", checksum, img.Checksum)
|
||||
}
|
||||
|
||||
### 不安全的处理管道 ###
|
||||
|
||||
**解压缩**
|
||||
|
||||
Docker支持三种压缩算法:gzip、bzip2和xz。前两种使用Go的标准库实现,是[内存安全(memory-safe)][4]的,因此这里我预计的攻击类型应该是拒绝服务类的攻击,包括CPU和内存使用上的当机或过载等等。
|
||||
|
||||
第三种压缩算法,xz,比较有意思。因为没有现成的Go实现,Docker 通过[执行(exec)][5]`xz`二进制命令来实现解压缩。
|
||||
|
||||
xz二进制程序来自于[XZ Utils][6]项目,由[大概][7]2万行C代码生成而来。而C语言不是一门内存安全的语言。这意味着C程序的恶意输入,在这里也就是Docker镜像的XZ Utils解包程序,潜在地可能会执行任意代码。
|
||||
|
||||
Docker以root权限*运行* `xz` 命令,更加恶化了这一潜在威胁。这意味着如果在`xz`中出现了一个漏洞,对`docker pull`命令的调用就会导致用户整个系统的完全沦陷。
|
||||
|
||||
**Tarsum**
|
||||
|
||||
对tarsum的使用,其出发点是好的,但却是最大的败笔。为了得到任意一个加密tar文件的准确校验和,Docker先对tar文件进行解密,然后求出特定部分的哈希值,同时排除剩余的部分,而这些步骤的[顺序都是固定的][8]。
|
||||
|
||||
由于其生成校验和的步骤固定,它解码不可信数据的过程就有可能被设计成[攻破tarsum的代码][9]。这里潜在的攻击既包括拒绝服务攻击,还有逻辑上的漏洞攻击,可能导致文件被感染、忽略、进程被篡改、植入等等,这一切攻击的同时,校验和可能都是不变的。
|
||||
|
||||
|
||||
**解包**
|
||||
|
||||
解包的过程包括tar解码和生成硬盘上的文件。这一过程尤其危险,因为在解包写入硬盘的过程中有另外三个[已报告的漏洞][10]。
|
||||
|
||||
任何情形下未经验证的数据都不应当解包后直接写入硬盘。
|
||||
|
||||
### libtrust ###
|
||||
|
||||
Docker的工具包[libtrust][11],号称“通过一个分布式的信任图表进行认证和访问控制”。很不幸,对此官方没有任何具体的说明,看起来它好像是实现了一些[javascript对象标记和加密][12]规格以及其他一些未说明的算法。
|
||||
|
||||
使用libtrust下载一个清单经过签名和认证的镜像,就可以触发下面这条不准确的信息(说不准确,是因为事实上它验证的只是清单,并非真正的镜像):
|
||||
|
||||
ubuntu:14.04: The image you are pulling has been verified(您所拉取的镜像已经经过验证)
|
||||
|
||||
目前只有Docker公司“官方”发布的镜像清单使用了这套签名系统,但是上次我参加Docker[管理咨询委员会][13]的会议讨论时,我所理解的是,Docker公司正计划在未来扩大部署这套系统。他们的目标是以Docker公司为中心,控制一个认证授权机构,对镜像进行签名和(或)客户认证。
|
||||
|
||||
我试图从Docker的代码中找到签名秘钥,但是没找到。好像它并不像我们所期望的把密钥嵌在二进制代码中,而是在每次镜像下载前,由Docker守护进程[通过HTTPS从CDN][14]远程获取。这是一个多么糟糕的方案,有无数种攻击手段可能会将可信密钥替换成恶意密钥。这些攻击包括但不限于:CDN供应商出问题、CDN初始密钥出现问题、客户端下载时的中间人攻击等等。
|
||||
|
||||
### 补救 ###
|
||||
|
||||
研究结束前,我[报告][15]了一些在tarsum系统中发现的问题,但是截至目前我报告的这些问题仍然
|
||||
没有修复。
|
||||
|
||||
要改进Docker镜像下载系统的安全问题,我认为应当有以下措施:
|
||||
|
||||
**摒弃tarsum并且真正对镜像本身进行验证**
|
||||
|
||||
出于安全原因tarsum应当被摒弃,同时,镜像在完整下载后、其他步骤开始前,就对镜像的加密签名进行验证。
|
||||
|
||||
**添加权限隔离**
|
||||
|
||||
镜像的处理过程中涉及到解压缩或解包的步骤必须在隔离的进程(容器?)中进行,即只给予其操作所需的最小权限。任何场景下都不应当使用root运行`xz`这样的解压缩工具。
|
||||
|
||||
**替换 libtrust**
|
||||
|
||||
应当用[更新框架(The Update Framework)][16]替换掉libtrust,这是专门设计用来解决软件二进制签名此类实际问题的。其威胁模型非常全方位,能够解决libtrust中未曾考虑到的诸多问题,目前已经有了完整的说明文档。除了已有的Python实现,我已经开始着手用[Go语言实现][17]的工作,也欢迎大家的贡献。
|
||||
|
||||
作为将更新框架加入Docker的一部分,还应当加入一个本地密钥存储池,将root密钥与registry的地址进行映射,这样用户就可以拥有他们自己的签名密钥,而不必使用Docker公司的了。
|
||||
|
||||
我注意到使用Docker公司非官方的宿主仓库往往会是一种非常糟糕的用户体验。当没有技术上的原因时,Docker也会将第三方的仓库内容降为二等地位来看待。这个问题不仅仅是生态问题,还是一个终端用户的安全问题。针对第三方仓库的全方位、去中心化的安全模型即必须又迫切。我希望Docker公司在重新设计他们的安全模型和镜像认证系统时能采纳这一点。
|
||||
|
||||
### 结论 ###
|
||||
|
||||
Docker用户应当意识到负责下载镜像的代码是非常不安全的。用户们应当只下载那些出处没有问题的镜像。目前,这里的“没有问题”并不包括Docker公司的“可信(trusted)”镜像,例如官方的Ubuntu和其他基础镜像。
|
||||
|
||||
最好的选择就是在本地屏蔽 `index.docker.io`,然后使用`docker load`命令在导入Docker之前手动下载镜像并对其进行验证。Red Hat的安全博客有一篇[很好的文章][18],大家可以看看。
|
||||
|
||||
感谢Lewis Marshall指出tarsum从未真正验证。
|
||||
|
||||
- [校验和的代码][19]
|
||||
- [cloc][20]介绍了18141行没有空格没有注释的C代码,以及5900行的header代码,版本号为v5.2.0。
|
||||
- [Android中也发现了][21]类似的bug,能够感染已签名包中的任意文件。同样出现问题的还有[Windows的Authenticode][22]认证系统,二进制文件会被篡改。
|
||||
- 特别的:[CVE-2014-6407][23]、 [CVE-2014-9356][24]以及 [CVE-2014-9357][25]。目前已有两个Docker[安全发布][26]有了回应。
|
||||
- 参见[2014-10-28 DGAB会议记录][27]的第8页。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://titanous.com/posts/docker-insecurity
|
||||
|
||||
作者:[titanous][a]
|
||||
译者:[Mr小眼儿](http://blog.csdn.net/tinyeyeser)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://twitter.com/titanous
|
||||
[1]:https://blog.docker.com/2014/10/docker-1-3-signed-images-process-injection-security-options-mac-shared-directories/
|
||||
[2]:https://blog.docker.com/2014/10/docker-1-3-signed-images-process-injection-security-options-mac-shared-directories/
|
||||
[3]:https://titanous.com/posts/docker-insecurity#fn:0
|
||||
[4]:https://en.wikipedia.org/wiki/Memory_safety
|
||||
[5]:https://github.com/docker/docker/blob/0874f9ab77a7957633cd835241a76ee4406196d8/pkg/archive/archive.go#L91-L95
|
||||
[6]:http://tukaani.org/xz/
|
||||
[7]:https://titanous.com/posts/docker-insecurity#fn:1
|
||||
[8]:https://github.com/docker/docker/blob/0874f9ab77a7957633cd835241a76ee4406196d8/pkg/tarsum/tarsum_spec.md
|
||||
[9]:https://titanous.com/posts/docker-insecurity#fn:2
|
||||
[10]:https://titanous.com/posts/docker-insecurity#fn:3
|
||||
[11]:https://github.com/docker/libtrust
|
||||
[12]:https://tools.ietf.org/html/draft-ietf-jose-json-web-signature-11
|
||||
[13]:https://titanous.com/posts/docker-insecurity#fn:4
|
||||
[14]:https://github.com/docker/docker/blob/0874f9ab77a7957633cd835241a76ee4406196d8/trust/trusts.go#L38
|
||||
[15]:https://github.com/docker/docker/issues/9719
|
||||
[16]:http://theupdateframework.com/
|
||||
[17]:https://github.com/flynn/go-tuf
|
||||
[18]:https://securityblog.redhat.com/2014/12/18/before-you-initiate-a-docker-pull/
|
||||
[19]:https://github.com/docker/docker/blob/0874f9ab77a7957633cd835241a76ee4406196d8/image/image.go#L114-L116
|
||||
[20]:http://cloc.sourceforge.net/
|
||||
[21]:http://www.saurik.com/id/17
|
||||
[22]:http://blogs.technet.com/b/srd/archive/2013/12/10/ms13-098-update-to-enhance-the-security-of-authenticode.aspx
|
||||
[23]:https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6407
|
||||
[24]:https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-9356
|
||||
[25]:https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-9357
|
||||
[26]:https://groups.google.com/d/topic/docker-user/nFAz-B-n4Bw/discussion
|
||||
[27]:https://docs.google.com/document/d/1JfWNzfwptsMgSx82QyWH_Aj0DRKyZKxYQ1aursxNorg/edit?pli=1
|
||||
@ -0,0 +1,76 @@
|
||||
如何在Linux上使用dupeGuru删除重复文件
|
||||
================================================================================
|
||||
最近,我被要求清理我父亲的文件和文件夹。有一个难题是,里面存在很多不正确的名字的重复文件。有移动硬盘的备份,同时还为同一个文件编辑了多个版本,甚至改变的目录结构,同一个文件被复制了好几次,改变名字,改变位置等,这些挤满了磁盘空间。追踪每一个文件成了一个最大的问题。万幸的是,有一个小巧的软件可以帮助你省下很多时间来找到删除你系统中重复的文件:[dupeGuru][1]。它用Python写成,这个去重软件几个小时钱前切换到了GPLv3许可证。因此是时候用它来清理你的文件了!
|
||||
|
||||
### dupeGuru的安装 ###
|
||||
|
||||
在Ubuntu上, 你可以加入Hardcoded的软件PPA:
|
||||
|
||||
$ sudo apt-add-repository ppa:hsoft/ppa
|
||||
$ sudo apt-get update
|
||||
|
||||
接着用下面的命令安装:
|
||||
|
||||
$ sudo apt-get install dupeguru-se
|
||||
|
||||
在ArchLinux中,这个包在[AUR][2]中。
|
||||
|
||||
如果你想自己编译,源码在[GitHub][3]上。
|
||||
|
||||
### dupeGuru的基本使用 ###
|
||||
|
||||
DupeGuru的构想是既快又安全。这意味着程序不会在你的系统上疯狂地运行。它很少会删除你不想要删除的文件。然而,既然在讨论文件删除,保持谨慎和小心总是好的:备份总是需要的。
|
||||
|
||||
你看完注意事项后,你可以用下面的命令运行duprGuru了:
|
||||
|
||||
$ dupeguru_se
|
||||
|
||||
你应该看到要你选择文件夹的欢迎界面,在这里加入你你想要扫描的重复文件夹。
|
||||
|
||||

|
||||
|
||||
一旦你选择完文件夹并启动扫描后,dupeFuru会以列表的形式显示重复文件的组:
|
||||
|
||||

|
||||
|
||||
注意的是默认上dupeGuru基于文件的内容匹配,而不是他们的名字。为了防止意外地删除了重要的文件,匹配那列列出了使用的匹配算法。在这里,你可以选择你想要删除的匹配文件,并按下“Action” 按钮来看到可用的操作。
|
||||
|
||||

|
||||
|
||||
可用的选项是相当广泛的。简而言之,你可以删除重复、移动到另外的位置、忽略它们、打开它们、重命名它们甚至用自定义命令运行它们。如果你选择删除重复文件,你可能会像我一样非常意外竟然还有删除选项。
|
||||
|
||||

|
||||
|
||||
你不及可以将删除文件移到垃圾箱或者永久删除,还可以选择留下指向原文件的链接(软链接或者硬链接)。也就是说,重复文件按将会删除但是会保留下指向原文件的链接。这将会省下大量的磁盘空间。如果你将这些文件导入到工作空间或者它们有一些依赖时很有用。
|
||||
|
||||
还有一个奇特的选项:你可以用HTML或者CSV文件导出结果。不确定你会不会这么做,但是我假设你想追踪重复文件而不是想让dupeGuru处理它们时会有用。
|
||||
|
||||
最后但并不是最不重要的是,偏好菜单可以让你对去重的想法成真。
|
||||
|
||||

|
||||
|
||||
这里你可以选择扫描的标准,基于内容还是基于文字,并且有一个阈值来控制结果的数量。这里同样可以定义自定义在执行中可以选择的命令。在无数其他小的选项中,要注意的是dupeGuru默认忽略小于10KB的文件。
|
||||
|
||||
要了解更多的信息,我建议你到[official website][4]官方网站看下,这里有很多文档、论坛支持和其他好东西。
|
||||
|
||||
总结一下,dupeGuru是我无论何时准备备份或者释放空间时想到的软件。我发现这对高级用户而言也足够强大了,对新人而言也很直观。锦上添花的是:dupeGuru是跨平台的额,这意味着你可以在Mac或者在Windows PC上都可以使用。如果你有特定的需求,想要清理音乐或者图片。这里有两个变种:[dupeguru-me][5]和 [dupeguru-pe][6], 相应地可以清理音频和图片文件。与常规版本的不同是它不仅比较文件格式还比较特定的媒体数据像质量和码率。
|
||||
|
||||
你dupeGuru怎么样?你会考虑使用它么?或者你有任何可以替代的软件的建议么?让我在评论区知道你们的想法。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/dupeguru-deduplicate-files-linux.html
|
||||
|
||||
作者:[Adrien Brochard][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/adrien
|
||||
[1]:http://www.hardcoded.net/dupeguru/
|
||||
[2]:https://aur.archlinux.org/packages/dupeguru-se/
|
||||
[3]:https://github.com/hsoft/dupeguru
|
||||
[4]:http://www.hardcoded.net/dupeguru/
|
||||
[5]:http://www.hardcoded.net/dupeguru_me/
|
||||
[6]:http://www.hardcoded.net/dupeguru_pe/
|
||||
@ -0,0 +1,73 @@
|
||||
如何在Ubuntu 14.04 上为Apache 2.4 安装SSL
|
||||
================================================================================
|
||||
今天我会站如如何为你的个人网站或者博客安装**SSL 证书**,来保护你的访问者和网站之间通信的安全。
|
||||
|
||||
安全套接字层或称SSL,是一种加密网站和浏览器之间连接的标准安全技术。这确保服务器和浏览器之间传输的数据保持隐私和安全。这被成千上万的人使用来保护他们与客户的通信。要启用SSL链接,web服务器需要安装SSL证书。
|
||||
|
||||
你可以创建你自己的SSL证书,但是这默认不会被浏览器信任,要修复这个问题,你需要从受信任的证书机构(CA)处购买证书,我们会向你展示如何
|
||||
或者证书并在apache中安装。
|
||||
|
||||
### 生成一个证书签名请求 ###
|
||||
|
||||
证书机构(CA)会要求你在你的服务器上生成一个证书签名请求(CSR)。这是一个很简单的过程,只需要一会就行,你需要运行下面的命令并输入需要的信息:
|
||||
|
||||
# openssl req -new -newkey rsa:2048 -nodes -keyout yourdomainname.key -out yourdomainname.csr
|
||||
|
||||
输出看上去会像这样:
|
||||
|
||||

|
||||
|
||||
这一步会生成两个文件按:一个用于解密SSL证书的私钥文件,一个证书签名请求(CSR)文件(用于申请你的SSL证书)。
|
||||
|
||||
根据你申请的机构,你会需要上传csr文件或者在网站表格中粘帖他的内容。
|
||||
|
||||
### 在Apache中安装实际的证书 ###
|
||||
|
||||
生成步骤完成之后,你会收到新的数字证书,本篇教程中我们使用[Comodo SSL][1]并在一个zip文件中收到了证书。要在apache中使用它,你首先需要用下面的命令为收到的证书创建一个组合的证书:
|
||||
|
||||
# cat COMODORSADomainValidationSecureServerCA.crt COMODORSAAddTrustCA.crt AddTrustExternalCARoot.crt > bundle.crt
|
||||
|
||||

|
||||
|
||||
用下面的命令确保ssl模块已经加载进apache了:
|
||||
|
||||
# a2enmod ssl
|
||||
|
||||
如果你看到了“Module ssl already enabled”这样的信息就说明你成功了,如果你看到了“Enabling module ssl”,那么你还需要用下面的命令重启apache:
|
||||
|
||||
# service apache2 restart
|
||||
|
||||
最后像下面这样修改你的虚拟主机文件(通常在/etc/apache2/sites-enabled 下):
|
||||
|
||||
DocumentRoot /var/www/html/
|
||||
ServerName linoxide.com
|
||||
SSLEngine on
|
||||
SSLCertificateFile /usr/local/ssl/crt/yourdomainname.crt
|
||||
SSLCertificateKeyFile /usr/local/ssl/yourdomainname.key
|
||||
SSLCACertificateFile /usr/local/ssl/bundle.crt
|
||||
|
||||
你现在应该可以用https://YOURDOMAIN/(注意使用‘https’而不是‘http’)来访问你的网站了,并可以看到SSL的进度条了(通常在你浏览器中用一把锁来表示)。
|
||||
|
||||
**NOTE:** All the links must now point to https, if some of the content on the website (like images or css files) still point to http links you will get a warning in the browser, to fix this you have to make sure that every link points to https.
|
||||
**注意:** 现在所有的链接都必须指向https,如果网站上的一些内容(像图片或者css文件等)仍旧指向http链接的话,你会在浏览器中得到一个警告,要修复这个问题,请确保每个链接都指向了https。
|
||||
|
||||
### 在你的网站上重定向HTTP请求到HTTPS中 ###
|
||||
|
||||
如果你希望重定向常规的HTTP请求到HTTPS,添加下面的文本到你希望的虚拟主机或者如果希望给服务器上所有网站都添加的话就加入到apache.conf中:
|
||||
|
||||
RewriteEngine On
|
||||
RewriteCond %{HTTPS} off
|
||||
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI}
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/ubuntu-how-to/install-ssl-apache-2-4-in-ubuntu/
|
||||
|
||||
作者:[Adrian Dinu][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/adriand/
|
||||
[1]:https://ssl.comodo.com/
|
||||
@ -0,0 +1,130 @@
|
||||
如何在Ubuntu 14.04 LTS安装网络爬虫工具
|
||||
================================================================================
|
||||
这是一款提取网站数据的开源工具。Scrapy框架用Python开发而成,它使抓取工作又快又简单,且可扩展。我们已经在virtual box中创建一台虚拟机(VM)并且在上面安装了Ubuntu 14.04 LTS。
|
||||
|
||||
### 安装 Scrapy ###
|
||||
|
||||
Scrapy依赖于Python、开发库和pip。Python最新的版本已经在Ubuntu上预装了。因此我们在安装Scrapy之前只需安装pip和python开发库就可以了。
|
||||
|
||||
pip是作为python包索引器easy_install的替代品。用于安装和管理Python包。pip包的安装可见图 1。
|
||||
|
||||
sudo apt-get install python-pip
|
||||
|
||||

|
||||
|
||||
图:1 pip安装
|
||||
|
||||
我们必须要用下面的命令安装python开发库。如果包没有安装那么就会在安装scrapy框架的时候报关于python.h头文件的错误。
|
||||
|
||||
sudo apt-get install python-dev
|
||||
|
||||

|
||||
|
||||
图:2 Python 开发库
|
||||
|
||||
scrapy框架即可从deb包安装也可以从源码安装。然而在图3中我们已经用pip(Python 包管理器)安装了deb包了。
|
||||
|
||||
sudo pip install scrapy
|
||||
|
||||

|
||||
|
||||
图:3 Scrapy 安装
|
||||
|
||||
图4中scrapy的成功安装需要一些时间。
|
||||
|
||||

|
||||
|
||||
图:4 成功安装Scrapy框架
|
||||
|
||||
### 使用scrapy框架提取数据 ###
|
||||
|
||||
**(基础教程)**
|
||||
|
||||
我们将用scrapy从fatwallet.com上提取店名(提供卡的店)。首先,我们使用下面的命令新建一个scrapy项目“store name”, 见图5。
|
||||
|
||||
$sudo scrapy startproject store_name
|
||||
|
||||

|
||||
|
||||
图:5 Scrapy框架新建项目
|
||||
|
||||
Above command creates a directory with title “store_name” at current path. This main directory of the project contains files/folders which are shown in the following Figure 6.
|
||||
上面的命令在当前路径创建了一个“store_name”的目录。项目主目录下包含的文件/文件夹见图6。
|
||||
|
||||
$sudo ls –lR store_name
|
||||
|
||||

|
||||
|
||||
图:6 store_name项目的内容
|
||||
|
||||
每个文件/文件夹的概要如下:
|
||||
|
||||
- scrapy.cfg 是项目配置文件
|
||||
- store_name/ 主目录下的另一个文件夹。 这个目录包含了项目的python代码
|
||||
- store_name/items.py 包含了将由蜘蛛爬取的项目
|
||||
- store_name/pipelines.py 是管道文件
|
||||
- store_name/settings.py 是项目的配置文件
|
||||
- store_name/spiders/, 包含了用于爬取的蜘蛛
|
||||
|
||||
由于我们要从fatwallet.com上如提取店名,因此我们如下修改文件。
|
||||
|
||||
import scrapy
|
||||
|
||||
class StoreNameItem(scrapy.Item):
|
||||
|
||||
name = scrapy.Field() # extract the names of Cards store
|
||||
|
||||
之后我们要在项目的store_name/spiders/文件夹下写一个新的蜘蛛。蜘蛛是一个python类,它包含了下面几个必须的属性:
|
||||
|
||||
1. 蜘蛛名 (name )
|
||||
2. 爬取起点url (start_urls)
|
||||
3. 包含了从响应中提取需要内容相应的正则表达式的解析方法。解析方法对爬虫而言很重要。
|
||||
|
||||
我们在store_name/spiders/目录下创建了“store_name.py”爬虫,并添加如下的代码来从fatwallet.com上提取点名。爬虫的输出到文件(**StoreName.txt**)中,见图7。
|
||||
|
||||
from scrapy.selector import Selector
|
||||
from scrapy.spider import BaseSpider
|
||||
from scrapy.http import Request
|
||||
from scrapy.http import FormRequest
|
||||
import re
|
||||
class StoreNameItem(BaseSpider):
|
||||
name = "storename"
|
||||
allowed_domains = ["fatwallet.com"]
|
||||
start_urls = ["http://fatwallet.com/cash-back-shopping/"]
|
||||
|
||||
def parse(self,response):
|
||||
output = open('StoreName.txt','w')
|
||||
resp = Selector(response)
|
||||
|
||||
tags = resp.xpath('//tr[@class="storeListRow"]|\
|
||||
//tr[@class="storeListRow even"]|\
|
||||
//tr[@class="storeListRow even last"]|\
|
||||
//tr[@class="storeListRow last"]').extract()
|
||||
for i in tags:
|
||||
i = i.encode('utf-8', 'ignore').strip()
|
||||
store_name = ''
|
||||
if re.search(r"class=\"storeListStoreName\">.*?<",i,re.I|re.S):
|
||||
store_name = re.search(r"class=\"storeListStoreName\">.*?<",i,re.I|re.S).group()
|
||||
store_name = re.search(r">.*?<",store_name,re.I|re.S).group()
|
||||
store_name = re.sub(r'>',"",re.sub(r'<',"",store_name,re.I))
|
||||
store_name = re.sub(r'&',"&",re.sub(r'&',"&",store_name,re.I))
|
||||
#print store_name
|
||||
output.write(store_name+""+"\n")
|
||||
|
||||

|
||||
|
||||
图:7 爬虫的输出
|
||||
|
||||
*注意: 本教程的目的仅用于理解scrapy框架*
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/ubuntu-how-to/scrapy-install-ubuntu/
|
||||
|
||||
作者:[nido][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/naveeda/
|
||||
Loading…
Reference in New Issue
Block a user