mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-25 00:50:15 +08:00
20140709-2 选题
This commit is contained in:
parent
6404fd3972
commit
1d3350233a
@ -0,0 +1,25 @@
|
||||
Dwarf Fortress Sees First New Release In 2 Years
|
||||
================================================================================
|
||||
|
||||
|
||||
[Dwarf Fortress][1] is a single-player fantasy game. You can control a dwarven outpost or an adventurer in a randomly generated, persistent world. The kicker is that the graphics are all text, no actual graphics. There are of course mods to make it graphical however.
|
||||
|
||||
I have to say I don't get the fuss at all with this one. The interface is confusing and it's not nice to look at, but I am guessing with plenty of graphical mods it could get pretty good considering everything you can do in it. I understand it will have a massive amount of replayability due to generating a new world each time, but it just doesn't look inviting to someone who hasn't played a game like it before.
|
||||
|
||||
This new release is the first in 2 years and has massive changes as you might imagine. See the [full rundown here][1].
|
||||
|
||||
What do people see in it exactly? I know plenty of you play it as the amount of people to email it in was crazy. I'm just going to sit back and let the "omg your crazy" comments come in.
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.gamingonlinux.com/articles/dwarf-fortress-sees-first-new-release-in-2-years.3997
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.bay12games.com/dwarves/index.html
|
||||
@ -0,0 +1,37 @@
|
||||
Red Hat Announces Availability of its OpenStack Platform 5
|
||||
================================================================================
|
||||

|
||||
|
||||
Red Hat has [announced][1] the general availability of Red Hat Enterprise Linux OpenStack Platform 5, which is the third enterprise release of the company's OpenStack offering. Aside from new features, the platform is clearly being aimed at many types of organizations, including "advanced cloud users, telecommunications companies, Internet service providers (ISPs), and public cloud hosting providers."
|
||||
|
||||
OpenStack Platform 5 is based on the latest OpenStack Icehouse release and provides more evidence of how very focused on cloud computing Red Hat has become.
|
||||
|
||||
The new release includes a three-year support lifecycle, and [I've made the point before][2] that because of its legendary support for Linux, Red Hat's OpenStack support will be a key differentiator in wooing enterprises. There has been controversy over whether Red Hat will support OpenStack distributions other than its own, which is significant because a recent OpenStack user survey showed that [90% of OpenStack deployments today are not running on RHEL][3], but rather use other flavors of Linux and KVM, such as Ubuntu or CentOS.
|
||||
|
||||
Other features in Red Hat's new release include:
|
||||
|
||||
> **Support for integration with VMware infrastructure**, encompassing virtualization, management, networking and storage. Customers may use existing VMware vSphere resources as virtualization drivers for OpenStack Compute (Nova) nodes, managed from the OpenStack Dashboard (Horizon). Additionally, Red Hat Enterprise Linux OpenStack Platform 5 supports the VMware NSX plugin for OpenStack Networking (Neutron) and the VMware Virtual Machine Disk (VMDK) plugin for OpenStack Block Storage (Cinder).
|
||||
>
|
||||
> **Better placement of workloads across cloud resources**. "Server groups enable workloads to be spread broadly across the OpenStack cloud for enhanced resiliency of distributed applications, or located proximately for lower communications latency and better performance of complex applications."
|
||||
>
|
||||
> **Improved support for virtual machines, supporting new cryptographic security requirements from the United States and United Kingdom**. Using the para-virtualized random number generator device added in Red Hat Enterprise Linux 7, cryptographic routines in guest applications will have access to better quality encryption and experience improved performance.
|
||||
>
|
||||
> **Improved interoperability of networking stacks**. Red Hat claims that the new modular plugin architecture for Neutron eases the addition of new networking technologies to OpenStack deployments. The new architecture provides a path for customers with heterogeneous networking environments who want to use a mix of networking solutions in their OpenStack environment.
|
||||
|
||||
Radhesh Balakrishnan, general manager, Virtualization and OpenStack, Red Hat, said in a statement:
|
||||
|
||||
> “We see momentum behind OpenStack as a private cloud platform of choice from enterprise customers and service providers alike. Red Hat Enterprise Linux OpenStack Platform 5 not only offers a production-ready, supported version of OpenStack Icehouse, but it brings a number of features that will simplify its use, and enhance dependability for enterprise users. Alongside those new features, we’re extending our support lifecycle for Red Hat Enterprise Linux OpenStack Platform, giving users confidence that the solution they deploy will be supported by our global team for the next three years.”
|
||||
|
||||
You can bet on that last point--a three-year support plan--as a key reason why some enterprises will go with Red Hat in the increasingly competitive OpenStack race. And, clearly, Red Hat is tying its future to cloud computing and the OpenStack platform.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ostatic.com/blog/red-hat-announces-availability-of-its-openstack-platform-5
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.marketwatch.com/story/red-hat-announces-general-availability-of-red-hat-enterprise-linux-openstack-platform-5-2014-07-08
|
||||
[2]:http://ostatic.com/blog/why-red-hats-openstack-support-must-be-as-inclusive-as-possible
|
||||
[3]:http://www.openstack.org/blog/2013/11/openstack-user-survey-october-2013/
|
||||
@ -0,0 +1,110 @@
|
||||
How to set up two-factor authentication for SSH login on Linux
|
||||
================================================================================
|
||||
With many high-profile password leaks nowadays, there is a lot of buzz in the industry on "multi-factor" authentication. In a multi-factor authentication system, users are required to go through two distinct authentication procedures: providing something they know (e.g., username/password), and leveraging something they have "physical" access to (e.g., one-time passcode generated by their mobile phone). This scheme is also commonly known as two-factor authentication or two-step verification.
|
||||
|
||||
To encourage the wide adoption of two-factor authentication, Google released [Google Authenticator][1], an open-source application that can generate one-time passcode based on open standards (e.g., HMAP/time-based). It is available on multiple platforms including Linux, [Android][2], [iOS][3]. Google also offers a pluggable authentication module (PAM) for Google Authenticator, allowing it to be integrated with other PAM-enabled applications such as OpenSSH.
|
||||
|
||||
In this tutorial, I will describe **how to set up two-factor authentication for an SSH server** by integrating Google Authenticator with OpenSSH. I am going to use a [Android][4] device to generate one-time passcode. In this tutorial, you will need two things: (1) a Linux host where OpenSSH server is running, and (2) an Android device.
|
||||
|
||||
### Install Google Authenticator on Linux ###
|
||||
|
||||
The first step is to install Google Authenticator on the Linux host where OpenSSH server is running. Follow [this guide][5] to install Google Authenticator and its PAM module on your system.
|
||||
|
||||
Once Google Authenticator is ready, you need to go through one-time configuration which involves creating an authentication key from this Linux host, and registering it with an Android device. This will be explained next.
|
||||
|
||||
### Generate an Authentication Key ###
|
||||
|
||||
To start, simply run Google Authenticator on the Linux server host.
|
||||
|
||||
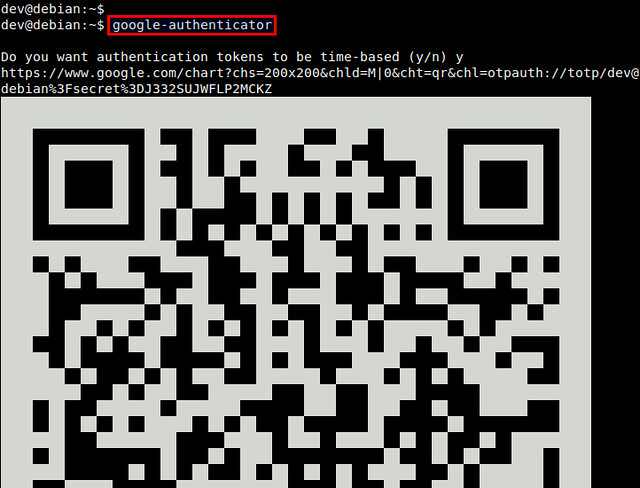
$ google-authenticator
|
||||
|
||||
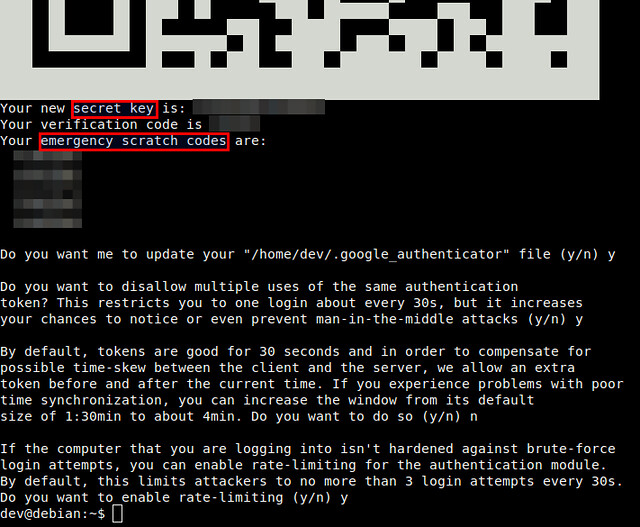
You will see a QR code, as well as a secret key underneath it. The displayed QR code simply represents the numeric secret key. You will need either information to finalize configuration with an Android device.
|
||||
|
||||
|
||||
|
||||
|
||||
Google Authenticator will ask you several questions. If you are not sure, you an answer "Yes" to all questions. The emergency scratch codes can be used to regain access to the SSH server in case you lose your Android device, and so cannot generate one-time passcode. So it's better to write them down somewhere.
|
||||
|
||||
### Run Google Authenticator on Android ###
|
||||
|
||||
As we are going to use an Android device for two-factor authentication, you will need to install [Google Authenticator app][6] on Android. Go to Google Play to install it on Android.
|
||||
|
||||
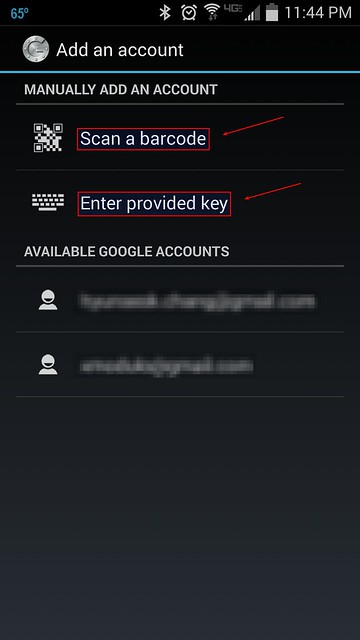
When you start Google Authenticator on Android, you will see the following configuration menu.
|
||||
|
||||
|
||||
|
||||
You can choose either "Scan a barcode" or "Enter provided key" option. The first option allows you to enter the security key, simply by scanning the generated QR code. In this case, you will need to install [Barcode Scanner app][7] first. If you choose the second option, you can type the security key using Android keyboard as follows.
|
||||
|
||||
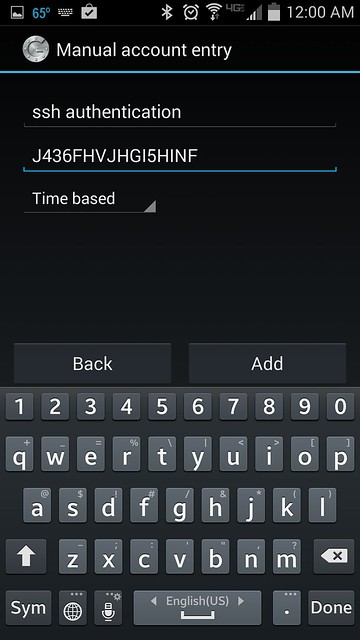
|
||||
|
||||
Once you register a secret key either way, you will see the following screen on Android.
|
||||
|
||||
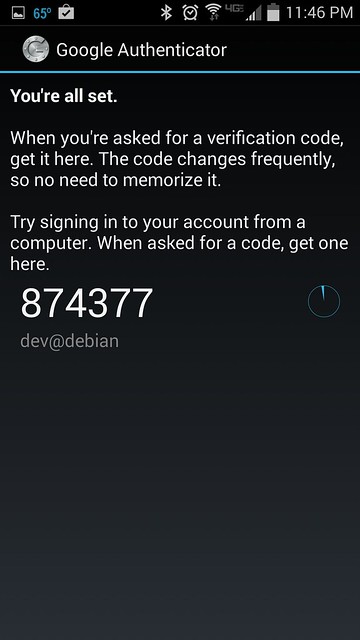
|
||||
|
||||
### Enable Google Authenticator on SSH Server ###
|
||||
|
||||
The final step is to integrate Google Authenticator with OpenSSH server. For that, you need to edit two files.
|
||||
|
||||
First, edit a PAM configuration file, and append the line below.
|
||||
|
||||
$ sudo vi /etc/pam.d/sshd
|
||||
|
||||
----------
|
||||
|
||||
auth required pam_google_authenticator.so
|
||||
|
||||
Then open an SSH server config file, search for ChallengeResponseAuthentication, and enable it.
|
||||
|
||||
$ sudo vi /etc/ssh/sshd_config
|
||||
|
||||
----------
|
||||
|
||||
ChallengeResponseAuthentication yes
|
||||
|
||||
Finally, restart SSH server.
|
||||
|
||||
On Ubuntu, Debian or Linux Mint:
|
||||
|
||||
$ sudo service ssh restart
|
||||
|
||||
On Fedora:
|
||||
|
||||
$ sudo systemctl restart sshd
|
||||
|
||||
On CentOS or RHEL:
|
||||
|
||||
$ sudo service sshd restart
|
||||
|
||||
### Test Two-factor Authentication ###
|
||||
|
||||
Here is how you use two-factor authentication for SSH logins.
|
||||
|
||||
Run Google Authenticator app on Android to obtain one-time verification code. Once generated, a given passcode is valid for 30 seconds. Once it expires, Google Authenticator will automatically generate a new one.
|
||||
|
||||
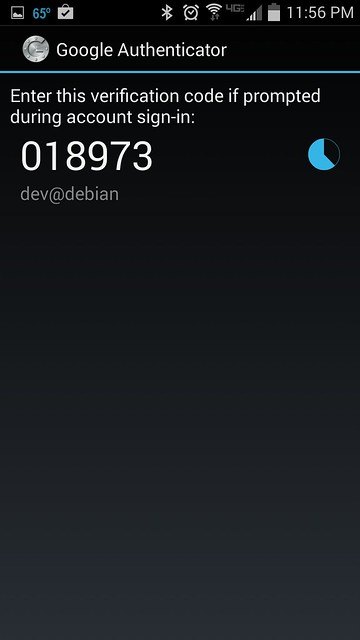
|
||||
|
||||
Now log in to the SSH server as you normally do.
|
||||
|
||||
$ ssh user@ssh_server
|
||||
|
||||
When you are asked to enter "Verification code", type in the verification code generated by Android. After successful verification, then you can type in your SSH login password.
|
||||
|
||||
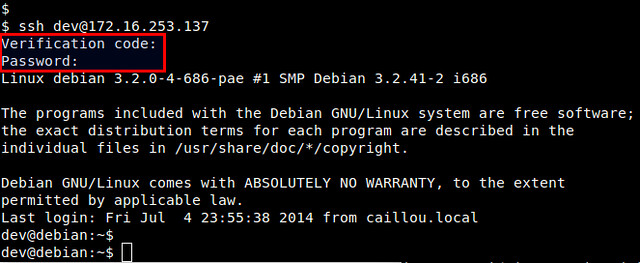
|
||||
|
||||
To conclude, two-factor authentication can be an effective means to secure password authentication by adding an extra layer of protection. You can use Google Authenticator to secure other logins such as Google account, WordPress.com, Dropbox.com, Outlook.com, etc. Whether you decide to use it or not, it's up to you, but there is a clear industry trend towards the adoption of two-factor authentication.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/07/two-factor-authentication-ssh-login-linux.html
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://code.google.com/p/google-authenticator/
|
||||
[2]:https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2
|
||||
[3]:https://itunes.apple.com/us/app/google-authenticator/id388497605
|
||||
[4]:http://xmodulo.com/go/android_guide
|
||||
[5]:http://ask.xmodulo.com/install-google-authenticator-linux.html
|
||||
[6]:https://play.google.com/store/apps/details?id=com.google.android.apps.authenticator2
|
||||
[7]:https://play.google.com/store/apps/details?id=com.google.zxing.client.android
|
||||
Loading…
Reference in New Issue
Block a user