mirror of
https://github.com/LCTT/TranslateProject.git
synced 2024-12-26 21:30:55 +08:00
Merge pull request #4445 from wcnnbdk1/master
Translated 20160506 Setup honeypot in Kali Linux.md
This commit is contained in:
commit
1cd1f9a5de
@ -1,85 +0,0 @@
|
||||
wcnnbdk1 Translating
|
||||
Setup honeypot in Kali Linux
|
||||
====
|
||||
|
||||
The Pentbox is a safety kit containing various tools for streamlining PenTest conducting a job easily. It is programmed in Ruby and oriented to GNU / Linux, with support for Windows, MacOS and every systems where Ruby is installed. In this small article we will explain how to set up a honeypot in Kali Linux. If you don’t know what is a honeypot, “a honeypot is a computer security mechanism set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems.”
|
||||
|
||||
### Download Pentbox:
|
||||
|
||||
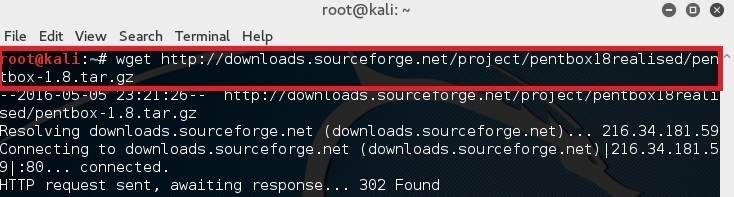
Simply type in the following command in your terminal to download pentbox-1.8.
|
||||
|
||||
```
|
||||
root@kali:~# wget http://downloads.sourceforge.net/project/pentbox18realised/pentbox-1.8.tar.gz
|
||||
```
|
||||
|
||||
|
||||
|
||||
### Uncompress pentbox files
|
||||
|
||||
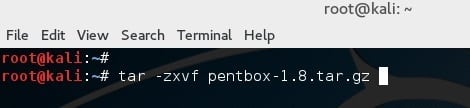
Decompressing the file with the following command:
|
||||
|
||||
```
|
||||
root@kali:~# tar -zxvf pentbox-1.8.tar.gz
|
||||
```
|
||||
|
||||
|
||||
|
||||
### Run pentbox ruby script
|
||||
|
||||
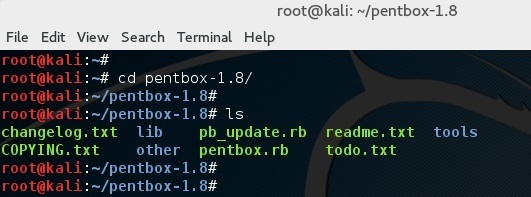
Change directory into pentbox folder
|
||||
|
||||
```
|
||||
root@kali:~# cd pentbox-1.8/
|
||||
```
|
||||
|
||||
|
||||
|
||||
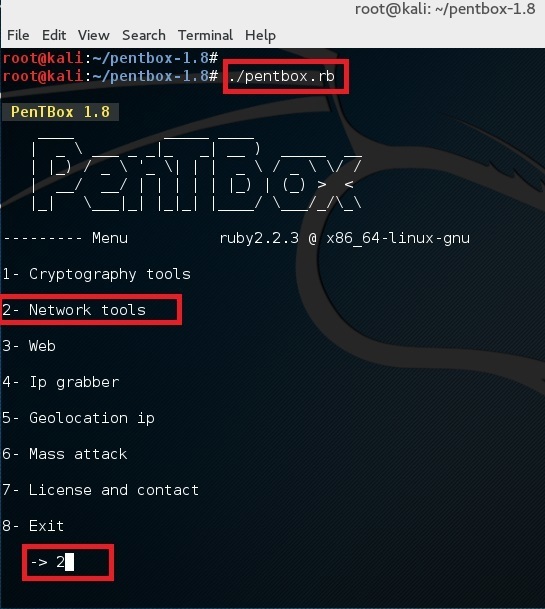
Run pentbox using the following command
|
||||
|
||||
```
|
||||
root@kali:~# ./pentbox.rb
|
||||
```
|
||||
|
||||
|
||||
|
||||
### Setup a honeypot
|
||||
|
||||
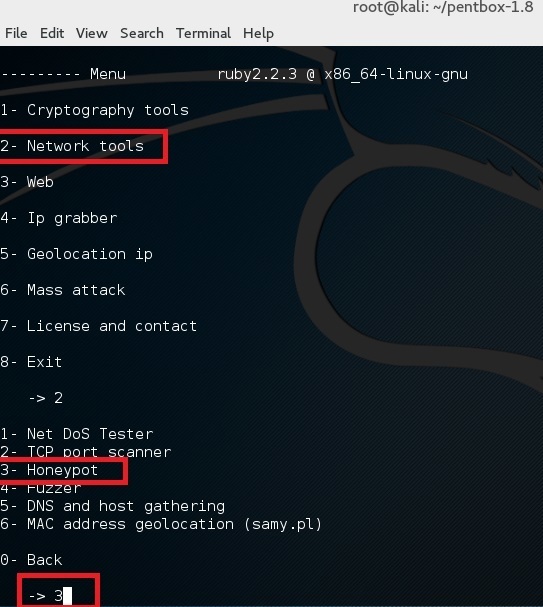
Use option 2 (Network Tools) and then option 3 (Honeypot).
|
||||
|
||||
|
||||
|
||||
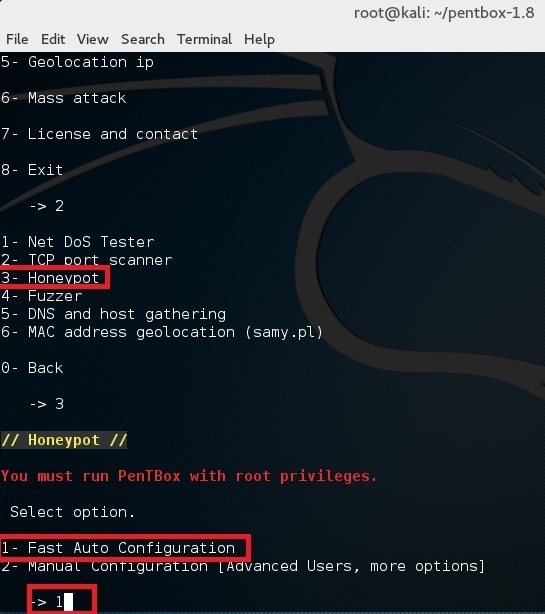
Finally for first test, choose option 1 (Fast Auto Configuration)
|
||||
|
||||
|
||||
|
||||
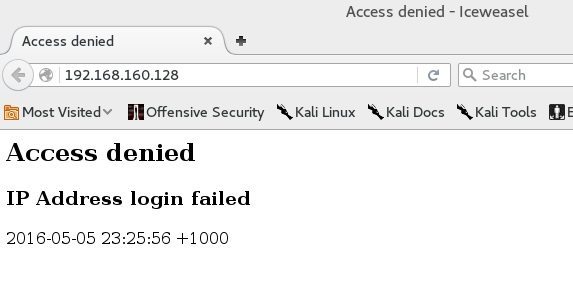
This opens up a honeypot in port 80. Simply open browser and browse to http://192.168.160.128 (where 192.168.160.128 is your IP Address. You should see an Access denied error.
|
||||
|
||||
|
||||
|
||||
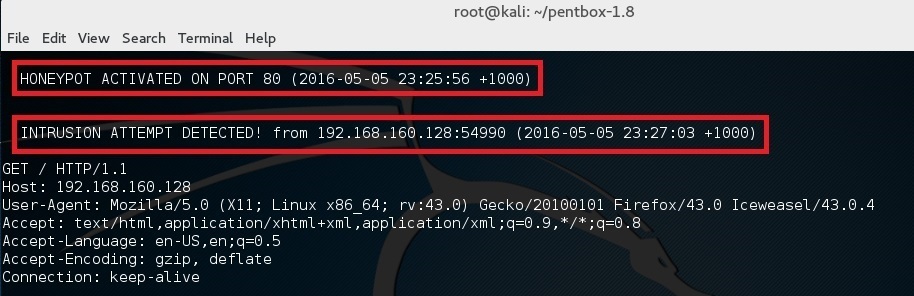
and in the terminal you should see “HONEYPOT ACTIVATED ON PORT 80” followed by “INTRUSION ATTEMPT DETECTED”.
|
||||
|
||||
|
||||
|
||||
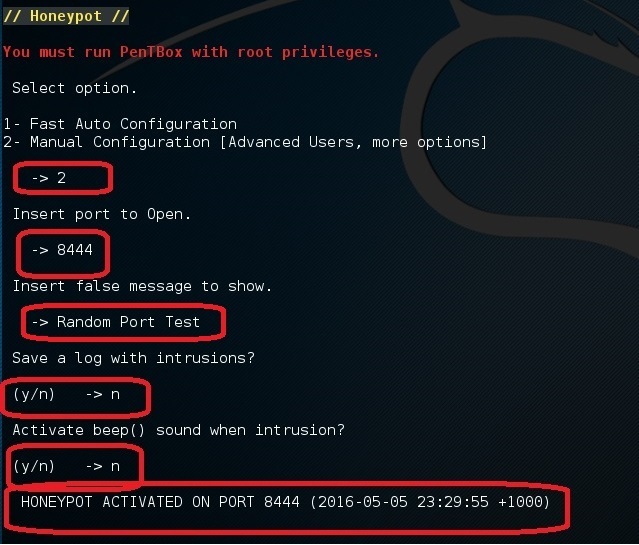
Now, if you do the same steps but this time select Option 2 (Manual Configuration), you should see more extra options
|
||||
|
||||
|
||||
|
||||
Do the same steps but select port 22 this time (SSH Port). Then do a port forwarding in your home router to forward port external port 22 to this machines’ port 22. Alternatively, set it up in a VPS in your cloud server.
|
||||
|
||||
You’d be amazed how many bots out there scanning port SSH continuously. You know what you do then? You try to hack them back for the lulz!
|
||||
|
||||
Here’s a video of setting up honeypot if video is your thing:
|
||||
|
||||
<https://youtu.be/NufOMiktplA>
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.blackmoreops.com/2016/05/06/setup-honeypot-in-kali-linux/
|
||||
|
||||
作者:[blackmoreops.com][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: blackmoreops.com
|
||||
85
translated/tech/20160506 Setup honeypot in Kali Linux.md
Normal file
85
translated/tech/20160506 Setup honeypot in Kali Linux.md
Normal file
@ -0,0 +1,85 @@
|
||||
|
||||
在 Kali Linux 环境下设置蜜罐
|
||||
====
|
||||
|
||||
Pentbox 是一个为了使工作变得简单流程化渗透测试的包含了许多工具的安全套件。它是用 Ruby 编写并且面向 GNU / Linux, 同时支持 Windows, MacOS 和其它任何安装有 Ruby 的系统。在这篇短文中我们将讲解如何在 Kali Linux 环境下设置蜜罐。如果你还不知道什么是蜜罐(如下解释仅供参考),“蜜罐是一种计算机安全机制设置用来发现,转移,或者,以某种方式,抵消非授权的信息系统的尝试。"
|
||||
|
||||
### 下载 Pentbox:
|
||||
|
||||
在你的终端中简单的键入下面的命令来下载 pentbox-1.8。
|
||||
|
||||
```
|
||||
root@kali:~# wget http://downloads.sourceforge.net/project/pentbox18realised/pentbox-1.8.tar.gz
|
||||
```
|
||||
|
||||

|
||||
|
||||
### 解压 pentbox 文件
|
||||
|
||||
使用如下命令解压文件:
|
||||
|
||||
```
|
||||
root@kali:~# tar -zxvf pentbox-1.8.tar.gz
|
||||
```
|
||||
|
||||

|
||||
|
||||
### 运行 pentbox 的 ruby 脚本
|
||||
|
||||
改变目录到 pentbox 文件夹
|
||||
|
||||
```
|
||||
root@kali:~# cd pentbox-1.8/
|
||||
```
|
||||
|
||||

|
||||
|
||||
使用下面的命令来运行 pentbox
|
||||
|
||||
```
|
||||
root@kali:~# ./pentbox.rb
|
||||
```
|
||||
|
||||

|
||||
|
||||
### 设置一个蜜罐
|
||||
|
||||
使用选项 2 (Network Tools) 然后是选项 3 (Honeypot)。(这里的 2(Network Tools) 和 3(Honeypot) 就想不翻译了因为引用的图上也是英文)
|
||||
|
||||

|
||||
|
||||
最后让我们执行第一次测试,选择选项 1 (Fast Auto Configuration) (同上理由)
|
||||
|
||||

|
||||
|
||||
这样就在 80 端口上开启了一个蜜罐。打开浏览器并且打开链接 http://192.168.160.128 (这里的 192.168.160.128 是你自己的 IP 地址.)(感觉这里少了一个‘)’就加上了)你应该会看到一个 Access denied 的报错(这里的 Access denied 没有翻译也是因为配图上是英文可能会更好些)
|
||||
|
||||

|
||||
|
||||
并且在你的终端应该会看到 “HONEYPOT ACTIVATED ON PORT 80” 和跟着的 “INTRUSION ATTEMPT DETECTED”。
|
||||
|
||||

|
||||
|
||||
现在,如果你再次执行相同的步骤但是这次选择了选项 2 (Manual Configuration), 你应该看见更多的其它选项
|
||||
|
||||

|
||||
|
||||
执行相同的步骤但是这次选择 22 端口 (SSH 端口)。接着在你家里的路由器上做一个端口转发将外部的 22 端口转发到这台机器的 22 端口上。或者,把这个蜜罐设置在你的云端服务器的一个 VPS 上。
|
||||
|
||||
你将会被有如此多的机器在持续的扫描着 SSH 端口而震惊。 你知道接着会干什么么? 你会试着攻破它们桀桀桀!
|
||||
|
||||
如果时评是你的菜的话,这里有一个设置蜜罐的视频:
|
||||
|
||||
<https://youtu.be/NufOMiktplA>
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.blackmoreops.com/2016/05/06/setup-honeypot-in-kali-linux/
|
||||
|
||||
作者:[blackmoreops.com][a]
|
||||
译者:[wcnnbdk1](https://github.com/wcnnbdk1)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: blackmoreops.com
|
||||
Loading…
Reference in New Issue
Block a user