mirror of
https://github.com/LCTT/TranslateProject.git
synced 2024-12-26 21:30:55 +08:00
Merge remote-tracking branch 'LCTT/master' into 20170802-Creating-SWAP-partition-using-FDISK---FALLOCATE-commands
This commit is contained in:
commit
186d5537aa
@ -0,0 +1,139 @@
|
||||
关于 Linux 页面表隔离补丁的神秘情况
|
||||
=====
|
||||
|
||||
**[本文勘误与补充][1]**
|
||||
|
||||
_长文预警:_ 这是一个目前严格限制的、禁止披露的安全 bug(LCTT 译注:目前已经部分披露),它影响到目前几乎所有实现虚拟内存的 CPU 架构,需要硬件的改变才能完全解决这个 bug。通过软件来缓解这种影响的紧急开发工作正在进行中,并且最近在 Linux 内核中已经得以实现,并且,在 11 月份,在 NT 内核中也开始了一个类似的紧急开发。在最糟糕的情况下,软件修复会导致一般工作负载出现巨大的减速(LCTT 译注:外在表现为 CPU 性能下降)。这里有一个提示,攻击会影响虚拟化环境,包括 Amazon EC2 和 Google 计算引擎,以及另外的提示是,这种精确的攻击可能涉及一个新的 Rowhammer 变种(LCTT 译注:一个由 Google 安全团队提出的 DRAM 的安全漏洞,在文章的后面部分会简单介绍)。
|
||||
|
||||
我一般不太关心安全问题,但是,对于这个 bug 我有点好奇,而一般会去写这个主题的人似乎都很忙,要么就是知道这个主题细节的人会保持沉默。这让我在新年的第一天(元旦那天)花了几个小时深入去挖掘关于这个谜团的更多信息,并且我将这些信息片断拼凑到了一起。
|
||||
|
||||
注意,这是一件相互之间高度相关的事件,因此,它的主要描述都是猜测,除非过一段时间,它的限制禁令被取消。我所看到的,包括涉及到的供应商、许多争论和这种戏剧性场面,将在限制禁令取消的那一天出现。
|
||||
|
||||
### LWN
|
||||
|
||||
这个事件的线索出现于 12 月 20 日 LWN 上的 [内核页面表的当前状况:页面隔离][2]这篇文章。从文章语气上明显可以看到这项工作的紧急程度,内核的核心开发者紧急加入了 [KAISER 补丁系列][3]的开发——它由奥地利的 [TU Graz][4] 的一组研究人员首次发表于去年 10 月份。
|
||||
|
||||
这一系列的补丁的用途从概念上说很简单:为了阻止运行在用户空间的进程在进程页面表中通过映射得到内核空间页面的各种攻击方式,它可以很好地阻止了从非特权的用户空间代码中识别到内核虚拟地址的攻击企图。
|
||||
|
||||
这个小组在描述 KAISER 的论文《[KASLR 已死:KASLR 永存][5]》摘要中特别指出,当用户代码在 CPU 上处于活动状态的时候,在内存管理硬件中删除所有内核地址空间的信息。
|
||||
|
||||
这个补丁集的魅力在于它触及到了核心,内核的全部基柱(以及与用户空间的接口),显然,它应该被最优先考虑。遍观 Linux 中内存管理方面的变化,通常某个变化的首次引入会发生在该改变被合并的很久之前,并且,通常会进行多次的评估、拒绝、以及因各种原因爆发争论的一系列过程。
|
||||
|
||||
而 KAISER(就是现在的 KPTI)系列(从引入到)被合并还不足三个月。
|
||||
|
||||
### ASLR 概述
|
||||
|
||||
从表面上看,这些补丁设计以确保<ruby>地址空间布局随机化<rt>Address Space Layout Randomization</rt></ruby>(ASLR)仍然有效:这是一个现代操作系统的安全特性,它试图将更多的随机位引入到公共映射对象的地址空间中。
|
||||
|
||||
例如,在引用 `/usr/bin/python` 时,动态链接将对系统的 C 库、堆、线程栈、以及主要的可执行文件进行排布,去接受随机分配的地址范围:
|
||||
|
||||
```
|
||||
$ bash -c ‘grep heap /proc/$$/maps’
|
||||
019de000-01acb000 rw-p 00000000 00:00 0 [heap]
|
||||
$ bash -c 'grep heap /proc/$$/maps’
|
||||
023ac000-02499000 rw-p 00000000 00:00 0 [heap]
|
||||
```
|
||||
注意两次运行的 bash 进程的堆(heap)的开始和结束偏移量上的变化。
|
||||
|
||||
如果一个缓存区管理的 bug 将导致攻击者可以去覆写一些程序代码指向的内存地址,而那个地址之后将在程序控制流中使用,这样这种攻击者就可以使控制流转向到一个包含他们所选择的内容的缓冲区上。而这个特性的作用是,对于攻击者来说,使用机器代码来填充缓冲区做他们想做的事情(例如,调用 `system()` C 库函数)将更困难,因为那个函数的地址在不同的运行进程上不同的。
|
||||
|
||||
这是一个简单的示例,ASLR 被设计用于去保护类似这样的许多场景,包括阻止攻击者了解有可能被用来修改控制流的程序数据的地址或者实现一个攻击。
|
||||
|
||||
KASLR 是应用到内核本身的一个 “简化的” ASLR:在每个重新引导的系统上,属于内核的地址范围是随机的,这样就使得,虽然被攻击者操控的控制流运行在内核模式上,但是,他们不能猜测到为实现他们的攻击目的所需要的函数和结构的地址,比如,定位当前进程的数据段,将活动的 UID 从一个非特权用户提升到 root 用户,等等。
|
||||
|
||||
### 坏消息:缓减这种攻击的软件运行成本过于贵重
|
||||
|
||||
之前的方式,Linux 将内核的内存映射到用户内存的同一个页面表中的主要原因是,当用户的代码触发一个系统调用、故障、或者产生中断时,就不需要改变正在运行的进程的虚拟内存布局。
|
||||
|
||||
因为它不需要去改变虚拟内存布局,进而也就不需要去清洗掉(flush)依赖于该布局的与 CPU 性能高度相关的缓存(LCTT 译注:意即如果清掉这些高速缓存,CPU 性能就会下降),而主要是通过 <ruby>[转换查找缓冲器][6]<rt>Translation Lookaside Buffer</rt></ruby>(TLB)(LCTT 译注:TLB ,将虚拟地址转换为物理地址)。
|
||||
|
||||
随着页面表分割补丁的合并,内核每次开始运行时,需要将内核的缓存清掉,并且,每次用户代码恢复运行时都会这样。对于大多数工作负载,在每个系统调用中,TLB 的实际总损失将导致明显的变慢:[@grsecurity 测量的一个简单的案例][7],在一个最新的 AMD CPU 上,Linux `du -s` 命令变慢了 50%。
|
||||
|
||||
### 34C3
|
||||
|
||||
在今年的 CCC 大会上,你可以找到 TU Graz 的另外一位研究人员,《[描述了一个纯 Javascript 的 ASLR 攻击][8]》,通过仔细地掌握 CPU 内存管理单元的操作时机,遍历了描述虚拟内存布局的页面表,来实现 ASLR 攻击。它通过高度精确的时间掌握和选择性回收的 CPU 缓存行的组合方式来实现这种结果,一个运行在 web 浏览器的 Javascript 程序可以找回一个 Javascript 对象的虚拟地址,使得可以利用浏览器内存管理 bug 进行接下来的攻击。(LCTT 译注:本文作者勘误说,上述链接 CCC 的讲演与 KAISER 补丁完全无关,是作者弄错了)
|
||||
|
||||
因此,从表面上看,我们有一组 KAISER 补丁,也展示了解除 ASLR 化地址的技术,并且,这个展示使用的是 Javascript,它很快就可以在一个操作系统内核上进行重新部署。
|
||||
|
||||
### 虚拟内存概述
|
||||
|
||||
在通常情况下,当一些机器码尝试去加载、存储、或者跳转到一个内存地址时,现代的 CPU 必须首先去转换这个 _虚拟地址_ 到一个 _物理地址_ ,这是通过遍历一系列操作系统托管的数组(被称为页面表)的方式进行的,这些数组描述了虚拟地址和安装在这台机器上的物理内存之间的映射。
|
||||
|
||||
在现代操作系统中,虚拟内存可能是最重要的强大特性:它可以避免什么发生呢?例如,一个濒临死亡的进程崩溃了操作系统、一个 web 浏览器 bug 崩溃了你的桌面环境、或者一个运行在 Amazon EC2 中的虚拟机的变化影响了同一台主机上的另一个虚拟机。
|
||||
|
||||
这种攻击的原理是,利用 CPU 上维护的大量的缓存,通过仔细地操纵这些缓存的内容,它可以去推测内存管理单元的地址,以去访问页面表的不同层级,因为一个未缓存的访问将比一个缓存的访问花费更长的时间(以实时而言)。通过检测页面表上可访问的元素,它可能能够恢复在 MMU(LCTT 译注:存储器管理单元)忙于解决的虚拟地址中的大部分比特(bits)。
|
||||
|
||||
### 这种动机的证据,但是不用恐慌
|
||||
|
||||
我们找到了动机,但是到目前为止,我们并没有看到这项工作引进任何恐慌。总的来说,ASLR 并不能完全缓减这种风险,并且也是一道最后的防线:仅在这 6 个月的周期内,即便是一个没有安全意识的人也能看到一些关于解除(unmasking) ASLR 化的指针的新闻,并且,实际上这种事从 ASLR 出现时就有了。
|
||||
|
||||
单独的修复 ASLR 并不足于去描述这项工作高优先级背后的动机。
|
||||
|
||||
### 它是硬件安全 bug 的证据
|
||||
|
||||
通过阅读这一系列补丁,可以明确许多事情。
|
||||
|
||||
第一,正如 [@grsecurity 指出][9] 的,代码中的一些注释已经被编辑掉了(redacted),并且,描述这项工作的附加的主文档文件已经在 Linux 源代码树中看不到了。
|
||||
|
||||
通过检查代码,它以运行时补丁的方式构建,在系统引导时仅当内核检测到是受影响的系统时才会被应用,与对臭名昭著的 [Pentium F00F bug][10] 的缓解措施,使用完全相同的机制:
|
||||
|
||||
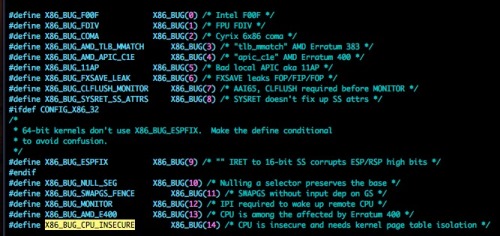
|
||||
|
||||
### 更多的线索:Microsoft 也已经实现了页面表的分割
|
||||
|
||||
通过对 FreeBSD 源代码的一个简单挖掘可以看出,目前,其它的自由操作系统没有实现页面表分割,但是,通过 [Alex Ioniscu 在 Twitter][11] 上的提示,这项工作已经不局限于 Linux 了:从 11 月起,公开的 NT 内核也已经实现了同样的技术。
|
||||
|
||||
### 猜测:Rowhammer
|
||||
|
||||
对 TU Graz 研究人员的工作的进一步挖掘,我们找到这篇 《[当 rowhammer 仅敲一次][12]》,这是 12 月 4 日通告的一个 [新的 Rowhammer 攻击的变种][13]:
|
||||
|
||||
> 在这篇论文中,我们提出了新的 Rowhammer 攻击和漏洞的原始利用方式,表明即便是组合了所有防御也没有效果。我们的新攻击技术,对一个位置的反复 “敲打”(hammering),打破了以前假定的触发 Rowhammer bug 的前提条件。
|
||||
|
||||
快速回顾一下,Rowhammer 是多数(全部?)种类的商业 DRAM 的一类根本性问题,比如,在普通的计算机中的内存上。通过精确操作内存中的一个区域,这可能会导致内存该区域存储的相关(但是逻辑上是独立的)内容被毁坏。效果是,Rowhammer 可能被用于去反转内存中的比特(bits),使未经授权的用户代码可以访问到,比如,这个比特位描述了系统中的其它代码的访问权限。
|
||||
|
||||
我发现在 Rowhammer 上,这项工作很有意思,尤其是它反转的位接近页面表分割补丁时,但是,因为 Rowhammer 攻击要求一个目标:你必须知道你尝试去反转的比特在内存中的物理地址,并且,第一步是得到的物理地址可能是一个虚拟地址,就像在 KASLR 中的解除(unmasking)工作。
|
||||
|
||||
### 猜测:它影响主要的云供应商
|
||||
|
||||
在我能看到的内核邮件列表中,除了该子系统维护者的名字之外,e-mail 地址属于 Intel、Amazon 和 Google 的雇员,这表示这两个大的云计算供应商对此特别感兴趣,这为我们提供了一个强大的线索,这项工作很大的可能是受虚拟化安全驱动的。
|
||||
|
||||
它可能会导致产生更多的猜测:虚拟机 RAM 和由这些虚拟机所使用的虚拟内存地址,最终表示为在主机上大量的相邻的数组,那些数组,尤其是在一个主机上只有两个租户的情况下,在 Xen 和 Linux 内核中是通过内存分配来确定的,这样可能会有(准确性)非常高的可预测行为。
|
||||
|
||||
### 最喜欢的猜测:这是一个提升特权的攻击
|
||||
|
||||
把这些综合到一起,我并不难预测,可能是我们在 2018 年会使用的这些存在提升特权的 bug 的发行版,或者类似的系统推动了如此紧急的进展,并且在补丁集的抄送列表中出现如此多的感兴趣者的名字。
|
||||
|
||||
最后的一个趣闻,虽然我在阅读补丁集的时候没有找到我要的东西,但是,在一些代码中标记,paravirtual 或者 HVM Xen 是不受此影响的。
|
||||
|
||||
### 吃瓜群众表示 2018 将很有趣
|
||||
|
||||
这些猜想是完全有可能的,它离实现很近,但是可以肯定的是,当这些事情被公开后,那将是一个非常令人激动的几个星期。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://pythonsweetness.tumblr.com/post/169166980422/the-mysterious-case-of-the-linux-page-table
|
||||
|
||||
作者:[python sweetness][a]
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://pythonsweetness.tumblr.com/
|
||||
[1]:http://pythonsweetness.tumblr.com/post/169217189597/quiet-in-the-peanut-gallery
|
||||
[2]:https://linux.cn/article-9201-1.html
|
||||
[3]:https://lwn.net/Articles/738975/
|
||||
[4]:https://www.iaik.tugraz.at/content/research/sesys/
|
||||
[5]:https://gruss.cc/files/kaiser.pdf
|
||||
[6]:https://en.wikipedia.org/wiki/Translation_lookaside_buffer
|
||||
[7]:https://twitter.com/grsecurity/status/947439275460702208
|
||||
[8]:https://www.youtube.com/watch?v=ewe3-mUku94
|
||||
[9]:https://twitter.com/grsecurity/status/947147105684123649
|
||||
[10]:https://en.wikipedia.org/wiki/Pentium_F00F_bug
|
||||
[11]:https://twitter.com/aionescu/status/930412525111296000
|
||||
[12]:https://www.tugraz.at/en/tu-graz/services/news-stories/planet-research/singleview/article/wenn-rowhammer-nur-noch-einmal-klopft/
|
||||
[13]:https://arxiv.org/abs/1710.00551
|
||||
[14]:http://pythonsweetness.tumblr.com/post/169166980422/the-mysterious-case-of-the-linux-page-table
|
||||
[15]:http://pythonsweetness.tumblr.com/
|
||||
|
||||
|
||||
@ -0,0 +1,62 @@
|
||||
巴塞罗那城放弃微软,转向 Linux 和开源
|
||||
=============
|
||||
|
||||
> 概述:巴塞罗那城市管理署已为从其现存的来自微软和专有软件的系统转换到 Linux 和开源软件规划好路线图。
|
||||
|
||||
西班牙报纸 [El País][1] 日前报道,[巴塞罗那城][2]已在迁移其计算机系统至开源技术的进程中。
|
||||
|
||||
根据该新闻报道,巴塞罗那城计划首先用开源应用程序替换掉所有的用户端应用。所有的专有软件都会被替换,最后仅剩下 Windows,而最终它也会被一个 Linux 发行版替代。
|
||||
|
||||
![BarcelonaSave][image-1]
|
||||
|
||||
### 巴塞罗那将会在 2019 年春季全面转换到开源
|
||||
|
||||
巴塞罗那城已经计划来年将其软件预算的 70% 投入到开源软件中。根据其城市议会技术和数字创新委员会委员 Francesca Bria 的说法,这一转换的过渡期将会在 2019 年春季本届城市管理署的任期结束前完成。
|
||||
|
||||
### 迁移旨在帮助 IT 人才
|
||||
|
||||
为了完成向开源的迁移,巴塞罗那城将会在中小企业中探索 IT 相关的项目。另外,城市管理署将吸纳 65 名新的开发者来构建软件以满足特定的需求。
|
||||
|
||||
设想中的一项重要项目,是开发一个在线的数字市场平台,小型企业将会利用其参加公开招标。
|
||||
|
||||
### Ubuntu 将成为替代的 Linux 发行版
|
||||
|
||||
由于巴塞罗那已经运行着一个 1000 台规模的基于 Ubuntu 桌面的试点项目,Ubuntu 可能会成为替代 Windows 的 Linux 发行版。新闻报道同时披露,Open-Xchange 将会替代 Outlook 邮件客户端和 Exchange 邮件服务器,而 Firefox 与 LibreOffice 将会替代 Internet Explorer 与微软 Office。
|
||||
|
||||
### 巴塞罗那市政当局成为首个参与「<ruby>公共资产,公共代码<rt>Public Money, Public Code</rt></ruby>」运动的当局
|
||||
|
||||
凭借此次向开源项目迁移,巴塞罗那市政当局成为首个参与欧洲的「[<ruby>公共资产,公共代码<rt>Public Money, Public Code</rt></ruby>](3)」运动的当局。
|
||||
|
||||
[欧洲自由软件基金会](4)发布了一封[公开信](5),倡议公共筹资的软件应该是自由的,并发起了这项运动。已有超过 15,000 人和 100 家组织支持这一号召。你也可以支持一个,只需要[签署请愿书](6)并且为开源发出你的声音。
|
||||
|
||||
### 资金永远是一个理由
|
||||
|
||||
根据 Bria 的说法,从 Windows 到开源软件的迁移,就已开发的程序可以被部署在西班牙或世界上的其他地方当局而言,促进了重复利用。显然,这一迁移也是为了防止大量的金钱被花费在专有软件上。
|
||||
|
||||
### 你的想法如何?
|
||||
|
||||
对于开源社区来讲,巴塞罗那的迁移是一场已经赢得的战争,也是一个有利条件。当[慕尼黑选择回归微软的怀抱](7)时,这一消息是开源社区十分需要的。
|
||||
|
||||
你对巴塞罗那转向开源有什么开发?你有预见到其他欧洲城市也跟随这一变化吗?在评论中和我们分享你的观点吧。
|
||||
|
||||
*來源: [Open Source Observatory][8]*
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
via: https://itsfoss.com/barcelona-open-source/
|
||||
|
||||
作者:[Derick Sullivan M. Lobga][a]
|
||||
译者:[Purling Nayuki](https://github.com/PurlingNayuki)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://itsfoss.com/author/derick/
|
||||
[1]:https://elpais.com/ccaa/2017/12/01/catalunya/1512145439_132556.html
|
||||
[2]:https://en.wikipedia.org/wiki/Barcelona
|
||||
[image-1]:https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/01/barcelona-city-animated.jpg
|
||||
[3]:https://publiccode.eu/
|
||||
[4]:https://fsfe.org/
|
||||
[5]:https://publiccode.eu/openletter/
|
||||
[6]:https://creativecommons.org/2017/09/18/sign-petition-public-money-produce-public-code/
|
||||
[7]:https://itsfoss.com/munich-linux-failure/
|
||||
[8]:https://joinup.ec.europa.eu/news/public-money-public-code
|
||||
@ -1,101 +0,0 @@
|
||||
translating by lujun9972
|
||||
Python Nmon Analyzer: moving away from excel macros
|
||||
======
|
||||
[Nigel's monitor][1], dubbed "Nmon", is a fantastic tool for monitoring, recording and analyzing a Linux/*nix system's performance over time. Nmon was originally developed by IBM and Open Sourced in the summer of 2009. By now Nmon is available on just about every linux platfrom and architecture. It provides a great real-time command line visualization of current system statistics, such as CPU, RAM, Network and Disk I/O. However, Nmon's greatest feature is the capability to record system performance snapshots over time.
|
||||
For example: `nmon -f -s 1`.
|
||||
![nmon CPU and Disk utilization][2]
|
||||
This will create a log file starting of with some system metadata(Section AAA - BBBV), followed by timed snapshots of all monitored system attributes, such as CPU and Memory usage. This produces a file that is hard to directly interpret with a spreadsheet application, hence the birth of the [Nmon_Analyzer][3] excel macro. This tool is great, if you have access to Windows/Mac with Microsoft Office installed. If not there is also the Nmon2rrd tool, which generates RRD input files to generate your graphs. This is a very rigid approach and slightly painful. Now to provide a more flexible tool, I am introducing the pyNmonAnalyzer, which aims to provide a customization solution for generating organized CSV files and simple HTML reports with [matplotlib][4] based graphs.
|
||||
|
||||
### Getting Started:
|
||||
|
||||
System requirements:
|
||||
As the name indicates you will need python. Additionally pyNmonAnalyzer depends on matplotlib and numpy. If you are on a debian-derivative system these are the packages you'll need to install:
|
||||
```
|
||||
$> sudo apt-get install python-numpy python-matplotlib
|
||||
|
||||
```
|
||||
|
||||
##### Getting pyNmonAnalyzer:
|
||||
|
||||
Either clone the git repository:
|
||||
```
|
||||
$> git clone git@github.com:madmaze/pyNmonAnalyzer.git
|
||||
|
||||
```
|
||||
|
||||
or
|
||||
|
||||
Download the current release here: [pyNmonAnalyzer-0.1.zip][5]
|
||||
|
||||
Next we need an an Nmon file, if you do not already have one, either use the example provided in the release or record a sample: `nmon -F test.nmon -s 1 -c 120`, this will record 120 snapshots at 1 second intervals to test.nmon.
|
||||
|
||||
Lets have a look at the basic help output:
|
||||
```
|
||||
$> ./pyNmonAnalyzer.py -h
|
||||
usage: pyNmonAnalyzer.py [-h] [-x] [-d] [-o OUTDIR] [-c] [-b] [-r CONFFNAME]
|
||||
input_file
|
||||
|
||||
nmonParser converts Nmon monitor files into time-sorted
|
||||
CSV/Spreadsheets for easier analysis, without the use of the
|
||||
MS Excel Macro. Also included is an option to build an HTML
|
||||
report with graphs, which is configured through report.config.
|
||||
|
||||
positional arguments:
|
||||
input_file Input NMON file
|
||||
|
||||
optional arguments:
|
||||
-h, --help show this help message and exit
|
||||
-x, --overwrite overwrite existing results (Default: False)
|
||||
-d, --debug debug? (Default: False)
|
||||
-o OUTDIR, --output OUTDIR
|
||||
Output dir for CSV (Default: ./data/)
|
||||
-c, --csv CSV output? (Default: False)
|
||||
-b, --buildReport report output? (Default: False)
|
||||
-r CONFFNAME, --reportConfig CONFFNAME
|
||||
Report config file, if none exists: we will write the
|
||||
default config file out (Default: ./report.config)
|
||||
|
||||
```
|
||||
|
||||
There are 2 main options of using this tool
|
||||
|
||||
1. Turn the nmon file into a set of separate CSV file
|
||||
2. Generate an HTML report with matplotlib graphs
|
||||
|
||||
|
||||
|
||||
The following command does both:
|
||||
```
|
||||
$> ./pyNmonAnalyzer.py -c -b test.nmon
|
||||
|
||||
```
|
||||
|
||||
This will create a directory called ./data in which you will find a folder of CSV files ("./data/csv/"), a folder of PNG graphs ("./data/img/") and an HTML report ("./data/report.html").
|
||||
|
||||
By default the HTML report will include graphs for CPU, Disk Busy, Memory utilization and Network transfers. This is all defined in a self explanitory configuration file, "report.config". At the moment this is not yet very flexible as CPU and MEM are not configurable besides on or off, but one of the next steps will be to refine the plotting approach and to expose more flexibility with which graphs plot which data points.
|
||||
|
||||
### Report Example:
|
||||
|
||||
[![pyNmonAnalyzer Graph output][6]
|
||||
**Click to see the full Report**][7]
|
||||
|
||||
Currently these reports are very bare bones and only prints out basic labeled graphs, but development is on-going. Currently in development is a wizard that will make adjusting the configurations easier. Please do let me know if you have any suggestions, find any bugs or have feature requests.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://matthiaslee.com/python-nmon-analyzer-moving-away-from-excel-macros/
|
||||
|
||||
作者:[Matthias Lee][a]
|
||||
译者:[lujun9972](https://github.com/lujun9972)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://matthiaslee.com/
|
||||
[1]:http://nmon.sourceforge.net/
|
||||
[2]:https://matthiaslee.com//content/images/2015/06/nmon_cpudisk.png
|
||||
[3]:http://www.ibm.com/developerworks/wikis/display/WikiPtype/nmonanalyser
|
||||
[4]:http://matplotlib.org/
|
||||
[5]:https://github.com/madmaze/pyNmonAnalyzer/blob/master/release/pyNmonAnalyzer-0.1.zip?raw=true
|
||||
[6]:https://matthiaslee.com//content/images/2017/04/teaser-short_0.png (pyNmonAnalyzer Graph output)
|
||||
[7]:http://matthiaslee.com/pub/pyNmonAnalyzer/data/report.html
|
||||
@ -1,3 +1,5 @@
|
||||
translated by cyleft
|
||||
|
||||
Top 10 Command Line Games For Linux
|
||||
======
|
||||
Brief: This article lists the **best command line games for Linux**.
|
||||
|
||||
@ -1,156 +0,0 @@
|
||||
Translating by jessie-pang
|
||||
|
||||
What happens when you start a process on Linux?
|
||||
===========================================================
|
||||
|
||||
|
||||
This is about how fork and exec works on Unix. You might already know about this, but some people don’t, and I was surprised when I learned it a few years back!
|
||||
|
||||
So. You want to start a process. We’ve talked a lot about **system calls** on this blog – every time you start a process, or open a file, that’s a system call. So you might think that there’s a system call like this
|
||||
|
||||
```
|
||||
start_process(["ls", "-l", "my_cool_directory"])
|
||||
|
||||
```
|
||||
|
||||
This is a reasonable thing to think and apparently it’s how it works in DOS/Windows. I was going to say that this _isn’t_ how it works on Linux. But! I went and looked at the docs and apparently there is a [posix_spawn][2] system call that does basically this. Shows what I know. Anyway, we’re not going to talk about that.
|
||||
|
||||
### fork and exec
|
||||
|
||||
`posix_spawn` on Linux is behind the scenes implemented in terms of 2 system calls called `fork` and `exec` (actually `execve`), which are what people usually actually use anyway. On OS X apparently people use `posix_spawn` and fork/exec are discouraged! But we’ll talk about Linux.
|
||||
|
||||
Every process in Linux lives in a “process tree”. You can see that tree by running `pstree`. The root of the tree is `init`, with PID 1\. Every process (except init) has a parent, and any process has many children.
|
||||
|
||||
So, let’s say I want to start a process called `ls` to list a directory. Do I just have a baby `ls`? No!
|
||||
|
||||
Instead of having children, what I do is you have a child that is a clone of myself, and then that child gets its brain eaten and turns into `ls`. Really.
|
||||
|
||||
We start out like this:
|
||||
|
||||
```
|
||||
my parent
|
||||
|- me
|
||||
|
||||
```
|
||||
|
||||
Then I run `fork()`. I have a child which is a clone of myself.
|
||||
|
||||
```
|
||||
my parent
|
||||
|- me
|
||||
|-- clone of me
|
||||
|
||||
```
|
||||
|
||||
Then I organize it so that my child runs `exec("ls")`. That leaves us with
|
||||
|
||||
```
|
||||
my parent
|
||||
|- me
|
||||
|-- ls
|
||||
|
||||
```
|
||||
|
||||
and once ls exits, I’ll be all by myself again. Almost
|
||||
|
||||
```
|
||||
my parent
|
||||
|- me
|
||||
|-- ls (zombie)
|
||||
|
||||
```
|
||||
|
||||
At this point ls is actually a zombie process! That means it’s dead, but it’s waiting around for me in case I want to check on its return value (using the `wait` system call.) Once I get its return value, I will really be all alone again.
|
||||
|
||||
```
|
||||
my parent
|
||||
|- me
|
||||
|
||||
```
|
||||
|
||||
### what fork and exec looks like in code
|
||||
|
||||
This is one of the exercises you have to do if you’re going to write a shell (which is a very fun and instructive project! Kamal has a great workshop on Github about how to do it: [https://github.com/kamalmarhubi/shell-workshop][3])
|
||||
|
||||
It turns out that with a bit of work & some C or Python skills you can write a very simple shell (like bash!) in C or Python in just a few hours (at least if you have someone sitting next to you who knows what they’re doing, longer if not :)). I’ve done this and it was awesome.
|
||||
|
||||
Anyway, here’s what fork and exec look like in a program. I’ve written fake C pseudocode. Remember that [fork can fail!][4]
|
||||
|
||||
```
|
||||
int pid = fork();
|
||||
// now i am split in two! augh!
|
||||
// who am I? I could be either the child or the parent
|
||||
if (pid == 0) {
|
||||
// ok I am the child process
|
||||
// ls will eat my brain and I'll be a totally different process
|
||||
exec(["ls"])
|
||||
} else if (pid == -1) {
|
||||
// omg fork failed this is a disaster
|
||||
} else {
|
||||
// ok i am the parent
|
||||
// continue my business being a cool program
|
||||
// I could wait for the child to finish if I want
|
||||
}
|
||||
|
||||
```
|
||||
|
||||
### ok what does it mean for your brain to be eaten julia
|
||||
|
||||
Processes have a lot of attributes!
|
||||
|
||||
You have
|
||||
|
||||
* open files (including open network connections)
|
||||
|
||||
* environment variables
|
||||
|
||||
* signal handlers (what happens when you run Ctrl+C on the program?)
|
||||
|
||||
* a bunch of memory (your “address space”)
|
||||
|
||||
* registers
|
||||
|
||||
* an “executable” that you ran (/proc/$pid/exe)
|
||||
|
||||
* cgroups and namespaces (“linux container stuff”)
|
||||
|
||||
* a current working directory
|
||||
|
||||
* the user your program is running as
|
||||
|
||||
* some other stuff that I’m forgetting
|
||||
|
||||
When you run `execve` and have another program eat your brain, actually almost everything stays the same! You have the same environment variables and signal handlers and open files and more.
|
||||
|
||||
The only thing that changes is, well, all of your memory and registers and the program that you’re running. Which is a pretty big deal.
|
||||
|
||||
### why is fork not super expensive (or: copy on write)
|
||||
|
||||
You might ask “julia, what if I have a process that’s using 2GB of memory! Does that mean every time I start a subprocess all that 2GB of memory gets copied?! That sounds expensive!”
|
||||
|
||||
It turns out that Linux implements “copy on write” for fork() calls, so that for all the 2GB of memory in the new process it’s just like “look at the old process! it’s the same!”. And then if the either process writes any memory, then at that point it’ll start copying. But if the memory is the same in both processes, there’s no need to copy!
|
||||
|
||||
### why you might care about all this
|
||||
|
||||
Okay, julia, this is cool trivia, but why does it matter? Do the details about which signal handlers or environment variables get inherited or whatever actually make a difference in my day-to-day programming?
|
||||
|
||||
Well, maybe! For example, there’s this [delightful bug on Kamal’s blog][5]. It talks about how Python sets the signal handler for SIGPIPE to ignore. So if you run a program from inside Python, by default it will ignore SIGPIPE! This means that the program will **behave differently** depending on whether you started it from a Python script or from your shell! And in this case it was causing a weird bug!
|
||||
|
||||
So, your program’s environment (environment, signal handlers, etc.) can matter! It inherits its environment from its parent process, whatever that was! This can sometimes be a useful thing to know when debugging.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://jvns.ca/blog/2016/10/04/exec-will-eat-your-brain/
|
||||
|
||||
作者:[ Julia Evans][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://jvns.ca
|
||||
[1]:https://jvns.ca/categories/favorite
|
||||
[2]:http://man7.org/linux/man-pages/man3/posix_spawn.3.html
|
||||
[3]:https://github.com/kamalmarhubi/shell-workshop
|
||||
[4]:https://rachelbythebay.com/w/2014/08/19/fork/
|
||||
[5]:http://kamalmarhubi.com/blog/2015/06/30/my-favourite-bug-so-far-at-the-recurse-center/
|
||||
@ -0,0 +1,189 @@
|
||||
How To Find (Top-10) Largest Files In Linux
|
||||
======
|
||||
When you are running out of disk space in system, you may prefer to check with df command or du command or ncdu command but all these will tell you only current directory files and doesn't shows the system wide files.
|
||||
|
||||
You have to spend huge amount of time to get the largest files in the system using the above commands, that to you have to navigate to each and every directory to achieve this.
|
||||
|
||||
It's making you to face trouble and this is not the right way to do it.
|
||||
|
||||
If so, what would be the suggested way to get top 10 largest files in Linux?
|
||||
|
||||
I have spend a lot of time with google but i didn't found this. Everywhere i could see an article which list the top 10 files in the current directory. So, i want to make this article useful for people whoever looking to get the top 10 largest files in the system.
|
||||
|
||||
In this tutorial, we are going to teach you how to find top 10 largest files in Linux system using below four methods.
|
||||
|
||||
### Method-1 :
|
||||
|
||||
There is no specific command available in Linux to do this, hence we are using more than one command (all together) to get this done.
|
||||
```
|
||||
# find / -type f -print0 | xargs -0 du -h | sort -rh | head -n 10
|
||||
|
||||
1.4G /swapfile
|
||||
1.1G /home/magi/ubuntu-17.04-desktop-amd64.iso
|
||||
564M /home/magi/.gdfuse/magi/cache/0B5nso_FPaZFqTFU0XzkzUlJUZzA
|
||||
378M /home/magi/.gdfuse/magi/cache/0B5nso_FPaZFqeldzUmhPeC03Zm8
|
||||
377M /home/magi/.gdfuse/magi/cache/0B5nso_FPaZFqRGd4V0VrOXM4YVU
|
||||
100M /usr/lib/x86_64-linux-gnu/libOxideQtCore.so.0
|
||||
93M /usr/lib/firefox/libxul.so
|
||||
84M /var/lib/snapd/snaps/core_3604.snap
|
||||
84M /var/lib/snapd/snaps/core_3440.snap
|
||||
84M /var/lib/snapd/snaps/core_3247.snap
|
||||
|
||||
```
|
||||
|
||||
**Details :**
|
||||
**`find`** : It 's a command, Search for files in a directory hierarchy.
|
||||
**`/`** : Check in the whole system (starting from / directory)
|
||||
**`-type`** : File is of type
|
||||
|
||||
**`f`** : Regular file
|
||||
**`-print0`** : Print the full file name on the standard output, followed by a null character
|
||||
**`|`** : Control operator that send the output of one program to another program for further processing.
|
||||
|
||||
**`xargs`** : It 's a command, which build and execute command lines from standard input.
|
||||
**`-0`** : Input items are terminated by a null character instead of by whitespace
|
||||
**`du -h`** : It 's a command to calculate disk usage with human readable format
|
||||
|
||||
**`sort`** : It 's a command, Sort lines of text files
|
||||
**`-r`** : Reverse the result of comparisons
|
||||
**`-h`** : Print the output with human readable format
|
||||
|
||||
**`head`** : It 's a command, Output the first part of files
|
||||
**`n -10`** : Print the first 10 files.
|
||||
|
||||
### Method-2 :
|
||||
|
||||
This is an another way to find or check top 10 largest files in Linux system. Here also, we are putting few commands together to achieve this.
|
||||
```
|
||||
# find / -type f -exec du -Sh {} + | sort -rh | head -n 10
|
||||
|
||||
1.4G /swapfile
|
||||
1.1G /home/magi/ubuntu-17.04-desktop-amd64.iso
|
||||
564M /home/magi/.gdfuse/magi/cache/0B5nso_FPaZFqTFU0XzkzUlJUZzA
|
||||
378M /home/magi/.gdfuse/magi/cache/0B5nso_FPaZFqeldzUmhPeC03Zm8
|
||||
377M /home/magi/.gdfuse/magi/cache/0B5nso_FPaZFqRGd4V0VrOXM4YVU
|
||||
100M /usr/lib/x86_64-linux-gnu/libOxideQtCore.so.0
|
||||
93M /usr/lib/firefox/libxul.so
|
||||
84M /var/lib/snapd/snaps/core_3604.snap
|
||||
84M /var/lib/snapd/snaps/core_3440.snap
|
||||
84M /var/lib/snapd/snaps/core_3247.snap
|
||||
|
||||
```
|
||||
|
||||
**Details :**
|
||||
**`find`** : It 's a command, Search for files in a directory hierarchy.
|
||||
**`/`** : Check in the whole system (starting from / directory)
|
||||
**`-type`** : File is of type
|
||||
|
||||
**`f`** : Regular file
|
||||
**`-exec`** : This variant of the -exec action runs the specified command on the selected files
|
||||
**`du`** : It 's a command to estimate file space usage.
|
||||
|
||||
**`-S`** : Do not include size of subdirectories
|
||||
**`-h`** : Print sizes in human readable format
|
||||
**`{}`** : Summarize disk usage of each FILE, recursively for directories.
|
||||
|
||||
**`|`** : Control operator that send the output of one program to another program for further processing.
|
||||
**`sort`** : It 's a command, Sort lines of text files
|
||||
**`-r`** : Reverse the result of comparisons
|
||||
|
||||
**`-h`** : Compare human readable numbers
|
||||
**`head`** : It 's a command, Output the first part of files
|
||||
**`n -10`** : Print the first 10 files.
|
||||
|
||||
### Method-3 :
|
||||
|
||||
It 's an another method to find or search top 10 largest files in Linux system.
|
||||
```
|
||||
# find / -type f -print0 | xargs -0 du | sort -n | tail -10 | cut -f2 | xargs -I{} du -sh {}
|
||||
|
||||
84M /var/lib/snapd/snaps/core_3247.snap
|
||||
84M /var/lib/snapd/snaps/core_3440.snap
|
||||
84M /var/lib/snapd/snaps/core_3604.snap
|
||||
93M /usr/lib/firefox/libxul.so
|
||||
100M /usr/lib/x86_64-linux-gnu/libOxideQtCore.so.0
|
||||
377M /home/magi/.gdfuse/magi/cache/0B5nso_FPaZFqRGd4V0VrOXM4YVU
|
||||
378M /home/magi/.gdfuse/magi/cache/0B5nso_FPaZFqeldzUmhPeC03Zm8
|
||||
564M /home/magi/.gdfuse/magi/cache/0B5nso_FPaZFqTFU0XzkzUlJUZzA
|
||||
1.1G /home/magi/ubuntu-17.04-desktop-amd64.iso
|
||||
1.4G /swapfile
|
||||
|
||||
```
|
||||
|
||||
**Details :**
|
||||
**`find`** : It 's a command, Search for files in a directory hierarchy.
|
||||
**`/`** : Check in the whole system (starting from / directory)
|
||||
**`-type`** : File is of type
|
||||
|
||||
**`f`** : Regular file
|
||||
**`-print0`** : Print the full file name on the standard output, followed by a null character
|
||||
**`|`** : Control operator that send the output of one program to another program for further processing.
|
||||
|
||||
**`xargs`** : It 's a command, which build and execute command lines from standard input.
|
||||
**`-0`** : Input items are terminated by a null character instead of by whitespace
|
||||
**`du`** : It 's a command to estimate file space usage.
|
||||
|
||||
**`sort`** : It 's a command, Sort lines of text files
|
||||
**`-n`** : Compare according to string numerical value
|
||||
**`tail -10`** : It 's a command, output the last part of files (last 10 files)
|
||||
|
||||
**`cut`** : It 's a command, remove sections from each line of files
|
||||
**`-f2`** : Select only these fields value.
|
||||
**`-I{}`** : Replace occurrences of replace-str in the initial-arguments with names read from standard input.
|
||||
|
||||
**`-s`** : Display only a total for each argument
|
||||
**`-h`** : Print sizes in human readable format
|
||||
**`{}`** : Summarize disk usage of each FILE, recursively for directories.
|
||||
|
||||
### Method-4 :
|
||||
|
||||
It 's an another method to find or search top 10 largest files in Linux system.
|
||||
```
|
||||
# find / -type f -ls | sort -k 7 -r -n | head -10 | column -t | awk '{print $7,$11}'
|
||||
|
||||
1494845440 /swapfile
|
||||
1085984380 /home/magi/ubuntu-17.04-desktop-amd64.iso
|
||||
591003648 /home/magi/.gdfuse/magi/cache/0B5nso_FPaZFqTFU0XzkzUlJUZzA
|
||||
395770383 /home/magi/.gdfuse/magi/cache/0B5nso_FPaZFqeldzUmhPeC03Zm8
|
||||
394891761 /home/magi/.gdfuse/magi/cache/0B5nso_FPaZFqRGd4V0VrOXM4YVU
|
||||
103999072 /usr/lib/x86_64-linux-gnu/libOxideQtCore.so.0
|
||||
97356256 /usr/lib/firefox/libxul.so
|
||||
87896064 /var/lib/snapd/snaps/core_3604.snap
|
||||
87793664 /var/lib/snapd/snaps/core_3440.snap
|
||||
87089152 /var/lib/snapd/snaps/core_3247.snap
|
||||
|
||||
```
|
||||
|
||||
**Details :**
|
||||
**`find`** : It 's a command, Search for files in a directory hierarchy.
|
||||
**`/`** : Check in the whole system (starting from / directory)
|
||||
**`-type`** : File is of type
|
||||
|
||||
**`f`** : Regular file
|
||||
**`-ls`** : List current file in ls -dils format on standard output.
|
||||
**`|`** : Control operator that send the output of one program to another program for further processing.
|
||||
|
||||
**`sort`** : It 's a command, Sort lines of text files
|
||||
**`-k`** : start a key at POS1
|
||||
**`-r`** : Reverse the result of comparisons
|
||||
|
||||
**`-n`** : Compare according to string numerical value
|
||||
**`head`** : It 's a command, Output the first part of files
|
||||
**`-10`** : Print the first 10 files.
|
||||
|
||||
**`column`** : It 's a command, formats its input into multiple columns.
|
||||
**`-t`** : Determine the number of columns the input contains and create a table.
|
||||
**`awk`** : It 's a command, Pattern scanning and processing language
|
||||
**`'{print $7,$11}'`** : Print only mentioned column.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.2daygeek.com/how-to-find-search-check-print-top-10-largest-biggest-files-in-linux/
|
||||
|
||||
作者:[Magesh Maruthamuthu][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.2daygeek.com/author/magesh/
|
||||
@ -0,0 +1,374 @@
|
||||
How to Install Snipe-IT Asset Management Software on Debian 9
|
||||
======
|
||||
|
||||
Snipe-IT is a free and open source IT assets management web application that can be used for tracking licenses, accessories, consumables, and components. It is written in PHP language and uses MySQL to store its data. It is a cross-platform application that works on all the major operating system like, Linux, Windows and Mac OS X. It easily integrates with Active Directory, LDAP and supports two-factor authentication with Google Authenticator.
|
||||
|
||||
In this tutorial, we will learn how to install Snipe-IT on Debian 9 server.
|
||||
|
||||
### Requirements
|
||||
|
||||
* A server running Debian 9.
|
||||
* A non-root user with sudo privileges.
|
||||
|
||||
|
||||
|
||||
### Getting Started
|
||||
|
||||
Before installing any packages, it is recommended to update the system package with the latest version. You can do this by running the following command:
|
||||
|
||||
```
|
||||
sudo apt-get update -y
|
||||
sudo apt-get upgrade -y
|
||||
```
|
||||
|
||||
Next, restart the system to apply all the updates. Then install other required packages with the following command:
|
||||
|
||||
```
|
||||
sudo apt-get install git curl unzip wget -y
|
||||
```
|
||||
|
||||
Once all the packages are installed, you can proceed to the next step.
|
||||
|
||||
### Install LAMP Server
|
||||
|
||||
Snipe-IT runs on Apache web server, so you will need to install LAMP (Apache, MariaDB, PHP) to your system.
|
||||
|
||||
First, install Apache, PHP and other PHP libraries with the following command:
|
||||
|
||||
```
|
||||
sudo apt-get install apache2 libapache2-mod-php php php-pdo php-mbstring php-tokenizer php-curl php-mysql php-ldap php-zip php-fileinfo php-gd php-dom php-mcrypt php-bcmath -y
|
||||
```
|
||||
|
||||
Once all the packages are installed, start Apache service and enable it to start on boot with the following command:
|
||||
|
||||
```
|
||||
sudo systemctl start apache2
|
||||
sudo systemctl enable apache2
|
||||
```
|
||||
|
||||
### Install and Configure MariaDB
|
||||
|
||||
Snipe-IT uses MariaDB to store its data. So you will need to install MariaDB to your system. By default, the latest version of the MariaDB is not available in the Debian 9 repository. So you will need to install MariaDB repository to your system.
|
||||
|
||||
First, add the APT key with the following command:
|
||||
|
||||
```
|
||||
sudo apt-get install software-properties-common -y
|
||||
sudo apt-key adv --recv-keys --keyserver hkp://keyserver.ubuntu.com:80 0xcbcb082a1bb943db
|
||||
```
|
||||
|
||||
Next, add the MariaDB repository using the following command:
|
||||
|
||||
```
|
||||
sudo add-apt-repository 'deb [arch=amd64,i386,ppc64el] http://nyc2.mirrors.digitalocean.com/mariadb/repo/10.1/debian stretch main'
|
||||
```
|
||||
|
||||
Next, update the repository with the following command:
|
||||
|
||||
```
|
||||
sudo apt-get update -y
|
||||
```
|
||||
|
||||
Once the repository is updated, you can install MariaDB with the following command:
|
||||
|
||||
```
|
||||
sudo apt-get install mariadb-server mariadb-client -y
|
||||
```
|
||||
|
||||
Next, start the MariaDB service and enable it to start on boot time with the following command:
|
||||
|
||||
```
|
||||
sudo systemctl start mysql
|
||||
sudo systemctl start mysql
|
||||
```
|
||||
|
||||
You can check the status of MariaDB server with the following command:
|
||||
|
||||
```
|
||||
sudo systemctl status mysql
|
||||
```
|
||||
|
||||
If everything is fine, you should see the following output:
|
||||
```
|
||||
? mariadb.service - MariaDB database server
|
||||
Loaded: loaded (/lib/systemd/system/mariadb.service; enabled; vendor preset: enabled)
|
||||
Active: active (running) since Mon 2017-12-25 08:41:25 EST; 29min ago
|
||||
Process: 618 ExecStartPost=/bin/sh -c systemctl unset-environment _WSREP_START_POSITION (code=exited, status=0/SUCCESS)
|
||||
Process: 615 ExecStartPost=/etc/mysql/debian-start (code=exited, status=0/SUCCESS)
|
||||
Process: 436 ExecStartPre=/bin/sh -c [ ! -e /usr/bin/galera_recovery ] && VAR= || VAR=`/usr/bin/galera_recovery`; [ $? -eq 0 ] && systemc
|
||||
Process: 429 ExecStartPre=/bin/sh -c systemctl unset-environment _WSREP_START_POSITION (code=exited, status=0/SUCCESS)
|
||||
Process: 418 ExecStartPre=/usr/bin/install -m 755 -o mysql -g root -d /var/run/mysqld (code=exited, status=0/SUCCESS)
|
||||
Main PID: 574 (mysqld)
|
||||
Status: "Taking your SQL requests now..."
|
||||
Tasks: 27 (limit: 4915)
|
||||
CGroup: /system.slice/mariadb.service
|
||||
??574 /usr/sbin/mysqld
|
||||
|
||||
Dec 25 08:41:07 debian systemd[1]: Starting MariaDB database server...
|
||||
Dec 25 08:41:14 debian mysqld[574]: 2017-12-25 8:41:14 140488893776448 [Note] /usr/sbin/mysqld (mysqld 10.1.26-MariaDB-0+deb9u1) starting as p
|
||||
Dec 25 08:41:25 debian systemd[1]: Started MariaDB database server.
|
||||
|
||||
```
|
||||
|
||||
Next, secure your MariaDB by running the following script:
|
||||
|
||||
```
|
||||
sudo mysql_secure_installation
|
||||
```
|
||||
|
||||
Answer all the questions as shown below:
|
||||
```
|
||||
Set root password? [Y/n] n
|
||||
Remove anonymous users? [Y/n] y
|
||||
Disallow root login remotely? [Y/n] y
|
||||
Remove test database and access to it? [Y/n] y
|
||||
Reload privilege tables now? [Y/n] y
|
||||
|
||||
```
|
||||
|
||||
Once MariaDB is secured, log in to MariaDB shell with the following command:
|
||||
|
||||
```
|
||||
mysql -u root -p
|
||||
```
|
||||
|
||||
Enter your root password when prompt, then create a database for Snipe-IT with the following command:
|
||||
|
||||
```
|
||||
MariaDB [(none)]> create database snipeitdb character set utf8;
|
||||
```
|
||||
|
||||
Next, create a user for Snipe-IT and grant all privileges to the Snipe-IT with the following command:
|
||||
|
||||
```
|
||||
MariaDB [(none)]> GRANT ALL PRIVILEGES ON snipeitdb.* TO 'snipeit'@'localhost' IDENTIFIED BY 'password';
|
||||
```
|
||||
|
||||
Next, flush the privileges with the following command:
|
||||
|
||||
```
|
||||
MariaDB [(none)]> flush privileges;
|
||||
```
|
||||
|
||||
Finally, exit from the MariaDB console using the following command:
|
||||
|
||||
```
|
||||
MariaDB [(none)]> quit
|
||||
```
|
||||
|
||||
### Install Snipe-IT
|
||||
|
||||
You can download the latest version of the Snipe-IT from Git repository with the following command:
|
||||
|
||||
```
|
||||
git clone https://github.com/snipe/snipe-it snipe-it
|
||||
```
|
||||
|
||||
Next, move the downloaded directory to the apache root directory with the following command:
|
||||
|
||||
```
|
||||
sudo mv snipe-it /var/www/
|
||||
```
|
||||
|
||||
Next, you will need to install Composer to your system. You can install it with the following command:
|
||||
|
||||
```
|
||||
curl -sS https://getcomposer.org/installer | php
|
||||
sudo mv composer.phar /usr/local/bin/composer
|
||||
```
|
||||
|
||||
Next, change the directory to snipe-it and Install PHP dependencies using Composer with the following command:
|
||||
|
||||
```
|
||||
cd /var/www/snipe-it
|
||||
sudo composer install --no-dev --prefer-source
|
||||
```
|
||||
Next, generate the "APP_Key" with the following command:
|
||||
|
||||
```
|
||||
sudo php artisan key:generate
|
||||
```
|
||||
|
||||
You should see the following output:
|
||||
```
|
||||
**************************************
|
||||
* Application In Production! *
|
||||
**************************************
|
||||
|
||||
Do you really wish to run this command? (yes/no) [no]:
|
||||
> yes
|
||||
|
||||
Application key [base64:uWh7O0/TOV10asWpzHc0DH1dOxJHprnZw2kSOnbBXww=] set successfully.
|
||||
|
||||
```
|
||||
|
||||
Next, you will need to populate MySQL with Snipe-IT's default database schema. You can do this by running the following command:
|
||||
|
||||
```
|
||||
sudo php artisan migrate
|
||||
```
|
||||
|
||||
Type yes, when prompted to confirm that you want to perform the migration:
|
||||
```
|
||||
**************************************
|
||||
* Application In Production! *
|
||||
**************************************
|
||||
|
||||
Do you really wish to run this command? (yes/no) [no]:
|
||||
> yes
|
||||
|
||||
Migration table created successfully.
|
||||
|
||||
```
|
||||
|
||||
Next, copy sample .env file and make some changes in it:
|
||||
|
||||
```
|
||||
sudo cp .env.example .env
|
||||
sudo nano .env
|
||||
```
|
||||
|
||||
Change the following lines:
|
||||
```
|
||||
APP_URL=http://example.com
|
||||
APP_TIMEZONE=US/Eastern
|
||||
APP_LOCALE=en
|
||||
|
||||
# --------------------------------------------
|
||||
# REQUIRED: DATABASE SETTINGS
|
||||
# --------------------------------------------
|
||||
DB_CONNECTION=mysql
|
||||
DB_HOST=localhost
|
||||
DB_DATABASE=snipeitdb
|
||||
DB_USERNAME=snipeit
|
||||
DB_PASSWORD=password
|
||||
DB_PREFIX=null
|
||||
DB_DUMP_PATH='/usr/bin'
|
||||
|
||||
```
|
||||
|
||||
Save and close the file when you are finished.
|
||||
|
||||
Next, provide the appropriate ownership and file permissions with the following command:
|
||||
|
||||
```
|
||||
sudo chown -R www-data:www-data storage public/uploads
|
||||
sudo chmod -R 755 storage public/uploads
|
||||
```
|
||||
|
||||
### Configure Apache For Snipe-IT
|
||||
|
||||
Next, you will need to create an apache virtual host directive for Snipe-IT. You can do this by creating `snipeit.conf` file inside `/etc/apache2/sites-available` directory:
|
||||
|
||||
```
|
||||
sudo nano /etc/apache2/sites-available/snipeit.conf
|
||||
```
|
||||
|
||||
Add the following lines:
|
||||
```
|
||||
<VirtualHost *:80>
|
||||
ServerAdmin webmaster@example.com
|
||||
<Directory /var/www/snipe-it/public>
|
||||
Require all granted
|
||||
AllowOverride All
|
||||
</Directory>
|
||||
DocumentRoot /var/www/snipe-it/public
|
||||
ServerName example.com
|
||||
ErrorLog /var/log/apache2/snipeIT.error.log
|
||||
CustomLog /var/log/apache2/access.log combined
|
||||
</VirtualHost>
|
||||
|
||||
```
|
||||
|
||||
Save and close the file when you are finished. Then, enable virtual host with the following command:
|
||||
|
||||
```
|
||||
sudo a2ensite snipeit.conf
|
||||
```
|
||||
|
||||
Next, enable PHP mcrypt, mbstring module and Apache rewrite module with the following command:
|
||||
|
||||
```
|
||||
sudo phpenmod mcrypt
|
||||
sudo phpenmod mbstring
|
||||
sudo a2enmod rewrite
|
||||
```
|
||||
|
||||
Finally, restart apache web server to apply all the changes:
|
||||
|
||||
```
|
||||
sudo systemctl restart apache2
|
||||
```
|
||||
|
||||
### Configure Firewall
|
||||
|
||||
By default, Snipe-IT runs on port 80, so you will need to allow port 80 through the firewall. By default, UFW firewall is not installed in Debian 9, so you will need to install it first. You can install it by just running the following command:
|
||||
|
||||
```
|
||||
sudo apt-get install ufw -y
|
||||
```
|
||||
|
||||
Once UFW is installed, enable it to start on boot time with the following command:
|
||||
|
||||
```
|
||||
sudo ufw enable
|
||||
```
|
||||
|
||||
Next, allow port 80 using the following command:
|
||||
|
||||
```
|
||||
sudo ufw allow 80
|
||||
```
|
||||
|
||||
Next, reload the UFW firewall rule with the following command:
|
||||
|
||||
```
|
||||
sudo ufw reload
|
||||
```
|
||||
|
||||
### Access Snipe-IT
|
||||
|
||||
Everything is now installed and configured, it's time to access Snipe-IT web interface.
|
||||
|
||||
Open your web browser and type the <http://example.com> URL, you will be redirected to the following page:
|
||||
|
||||
[![Snipe-IT Checks the system][2]][3]
|
||||
|
||||
The above page will do a system check to make sure your configuration looks correct. Next, click on the **Create Database Table** button you should see the following page:
|
||||
|
||||
[![Create database table][4]][5]
|
||||
|
||||
Here, click on the **Create User** page, you should see the following page:
|
||||
|
||||
[![Create user][6]][7]
|
||||
|
||||
Here, provide your Site name, Domain name, Admin username, and password, then click on the **Save User** button, you should see the Snipe-IT default dashboard as below:
|
||||
|
||||
[![Snipe-IT Dashboard][8]][9]
|
||||
|
||||
### Conclusion
|
||||
|
||||
In the above tutorial, we have learned to install Snipe-IT on Debian 9 server. We have also learned to configure Snipe-IT through web interface.I hope you have now enough knowledge to deploy Snipe-IT in your production environment. For more information you can refer Snipe-IT [Documentation Page][10].
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.howtoforge.com/tutorial/how-to-install-snipe-it-on-debian-9/
|
||||
|
||||
作者:[Hitesh Jethva][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.howtoforge.com
|
||||
[1]:/cdn-cgi/l/email-protection
|
||||
[2]:https://www.howtoforge.com/images/how_to_install_snipe_it_on_debian_9/Screenshot-of-snipeit-page1.png
|
||||
[3]:https://www.howtoforge.com/images/how_to_install_snipe_it_on_debian_9/big/Screenshot-of-snipeit-page1.png
|
||||
[4]:https://www.howtoforge.com/images/how_to_install_snipe_it_on_debian_9/Screenshot-of-snipeit-page2.png
|
||||
[5]:https://www.howtoforge.com/images/how_to_install_snipe_it_on_debian_9/big/Screenshot-of-snipeit-page2.png
|
||||
[6]:https://www.howtoforge.com/images/how_to_install_snipe_it_on_debian_9/Screenshot-of-snipeit-page3.png
|
||||
[7]:https://www.howtoforge.com/images/how_to_install_snipe_it_on_debian_9/big/Screenshot-of-snipeit-page3.png
|
||||
[8]:https://www.howtoforge.com/images/how_to_install_snipe_it_on_debian_9/Screenshot-of-snipeit-page4.png
|
||||
[9]:https://www.howtoforge.com/images/how_to_install_snipe_it_on_debian_9/big/Screenshot-of-snipeit-page4.png
|
||||
[10]:https://snipe-it.readme.io/docs
|
||||
110
sources/tech/20180111 Multimedia Apps for the Linux Console.md
Normal file
110
sources/tech/20180111 Multimedia Apps for the Linux Console.md
Normal file
@ -0,0 +1,110 @@
|
||||
Multimedia Apps for the Linux Console
|
||||
======
|
||||
|
||||

|
||||
The Linux console supports multimedia, so you can enjoy music, movies, photos, and even read PDF files.
|
||||
|
||||
When last we met, we learned that the Linux console supports multimedia. Yes, really! You can enjoy music, movies, photos, and even read PDF files without being in an X session with MPlayer, fbi, and fbgs. And, as a bonus, you can enjoy a Matrix-style screensaver for the console, CMatrix.
|
||||
|
||||
You will probably have make some tweaks to your system to make this work. The examples used here are for Ubuntu Linux 16.04.
|
||||
|
||||
### MPlayer
|
||||
|
||||
You're probably familiar with the amazing and versatile MPlayer, which supports almost every video and audio format, and runs on nearly everything, including Linux, Android, Windows, Mac, Kindle, OS/2, and AmigaOS. Using MPLayer in your console will probably require some tweaking, depending on your Linux distribution. To start, try playing a video:
|
||||
```
|
||||
$ mplayer [video name]
|
||||
|
||||
```
|
||||
|
||||
If it works, then hurrah, and you can invest your time in learning useful MPlayer options, such as controlling the size of the video screen. However, some Linux distributions are managing the framebuffer differently than in the olden days, and you may have to adjust some settings to make it work. This is how to make it work on recent Ubuntu releases.
|
||||
|
||||
First, add yourself to the video group.
|
||||
|
||||
Second, verify that `/etc/modprobe.d/blacklist-framebuffer.conf` has this line: `#blacklist vesafb`. It should already be commented out, and if it isn't then comment it. All the other module lines should be un-commented, which prevents them from loading. Side note: if you want to dig more deeply into managing your framebuffer, the module for your video card may give better performance.
|
||||
|
||||
Add these two modules to the end of `/etc/initramfs-tools/modules`, `vesafb` and `fbcon`, then rebuild the initramfs image:
|
||||
```
|
||||
$ sudo nano /etc/initramfs-tools/modules
|
||||
# List of modules that you want to include in your initramfs.
|
||||
# They will be loaded at boot time in the order below.
|
||||
fbcon
|
||||
vesafb
|
||||
|
||||
$ sudo update-initramfs -u
|
||||
|
||||
```
|
||||
|
||||
[fbcon][1] is the Linux framebuffer console. It runs on top of the framebuffer and adds graphical features. It requires a framebuffer device, which is supplied by the `vesafb` module.
|
||||
|
||||
Now you must edit your GRUB2 configuration. In `/etc/default/grub` you should see a line like this:
|
||||
```
|
||||
GRUB_CMDLINE_LINUX_DEFAULT="quiet splash"
|
||||
|
||||
```
|
||||
|
||||
It may have some other options, but it should be there. Add `vga=789`:
|
||||
```
|
||||
GRUB_CMDLINE_LINUX_DEFAULT="quiet splash vga=789"
|
||||
|
||||
```
|
||||
|
||||
Reboot and enter your console (Ctrl+Alt+F1), and try playing a video. This command selects the `fbdev2` video device; I haven't learned yet how to know which one to use, but I had to use it to play the video. The default screen size is 320x240, so I scaled it to 960:
|
||||
```
|
||||
$ mplayer -vo fbdev2 -vf scale -zoom -xy 960 AlienSong_mp4.mov
|
||||
```
|
||||
|
||||
And behold Figure 1. It's grainy because I have a low-fi copy of this video, not because MPlayer is making it grainy.
|
||||
|
||||
MPLayer plays CDs, DVDs, network streams, and has a giant batch of playback options, which I shall leave as your homework to explore.
|
||||
|
||||
### fbi Image Viewer
|
||||
|
||||
`fbi`, the framebuffer image viewer, comes in the [fbida][2] package on most Linuxes. It has native support for the common image file formats, and uses `convert` (from Image Magick), if it is installed, for other formats. Its simplest use is to view a single image file:
|
||||
```
|
||||
$ fbi filename
|
||||
|
||||
```
|
||||
|
||||
Use the arrow keys to scroll a large image, + and - to zoom, and r and l to rotate 90 degress right and left. Press the Escape key to close the image. You can play a slideshow by giving `fbi` a list of files:
|
||||
```
|
||||
$ fbi --list file-list.txt
|
||||
|
||||
```
|
||||
|
||||
`fbi` supports autozoom. With `-a` `fbi` controls the zoom factor. `--autoup` and `--autodown` tell `fbi` to only zoom up or down. Control the blend time between images with `--blend [time]`, in milliseconds. Press the k and j keys to jump behind and ahead in your file list.
|
||||
|
||||
`fbi` has commands for creating file lists from images you have viewed, and for exporting your commands to a file, and a host of other cool options. Check out `man fbi` for complete options.
|
||||
|
||||
### CMatrix Console Screensaver
|
||||
|
||||
The Matrix screensaver is still my favorite (Figure 2), second only to the bouncing cow. [CMatrix][3] runs on the console. Simply type `cmatrix` to start it, and Ctrl+C stops it. Run `cmatrix -s` to launch it in screensaver mode, which exits on any keypress. `-C` changes the color. Your choices are green, red, blue, yellow, white, magenta, cyan, and black.
|
||||
|
||||
CMatrix supports asynchronous key presses, which means you can change options while it's running.
|
||||
|
||||
`-B` is all bold text, and `-B` is partially bold.
|
||||
|
||||
### fbgs PDF Viewer
|
||||
|
||||
It seems that the addiction to PDF documents is pandemic and incurable, though PDFs are better than they used to be, with live hyperlinks, copy-paste, and good text search. The `fbgs` console PDF viewer is part of the `fbida` package. Options include page size, resolution, page selections, and most `fbi` options, with the exceptions listed in `man fbgs`. The main option I use is page size; you get `-l`, `xl`, and `xxl` to choose from:
|
||||
```
|
||||
$ fbgs -xl annoyingpdf.pdf
|
||||
|
||||
```
|
||||
|
||||
Learn more about Linux through the free ["Introduction to Linux" ][4]course from The Linux Foundation and edX.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/learn/intro-to-linux/2018/1/multimedia-apps-linux-console
|
||||
|
||||
作者:[Carla Schroder][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/cschroder
|
||||
[1]:https://www.mjmwired.net/kernel/Documentation/fb/fbcon.txt
|
||||
[2]:https://www.kraxel.org/blog/linux/fbida/
|
||||
[3]:http://www.asty.org/cmatrix/
|
||||
[4]:https://training.linuxfoundation.org/linux-courses/system-administration-training/introduction-to-linux
|
||||
@ -0,0 +1,112 @@
|
||||
The Fold Command Tutorial With Examples For Beginners
|
||||
======
|
||||
|
||||

|
||||
|
||||
Have you ever found yourself in a situation where you want to fold or break the output of a command to fit within a specific width? I have find myself in this situation few times while running VMs, especially the servers with no GUI. Just in case, if you ever wanted to limit the output of a command to a particular width, look nowhere! Here is where **fold** command comes in handy! The fold command wraps each line in an input file to fit a specified width and prints it to the standard output.
|
||||
|
||||
In this brief tutorial, we are going to see the usage of fold command with practical examples.
|
||||
|
||||
### The Fold Command Tutorial With Examples
|
||||
|
||||
Fold command is the part of GNU coreutils package, so let us not bother about installation.
|
||||
|
||||
The typical syntax of fold command:
|
||||
```
|
||||
fold [OPTION]... [FILE]...
|
||||
```
|
||||
|
||||
Allow me to show you some examples, so you can get a better idea about fold command. I have a file named **linux.txt** with some random lines.
|
||||
|
||||
[![][1]][2]
|
||||
|
||||
To wrap each line in the above file to default width, run:
|
||||
```
|
||||
fold linux.txt
|
||||
```
|
||||
|
||||
**80** columns per line is the default width. Here is the output of above command:
|
||||
|
||||
[![][1]][3]
|
||||
|
||||
As you can see in the above output, fold command has limited the output to a width of 80 characters.
|
||||
|
||||
Of course, we can specify your preferred width, for example 50, like below:
|
||||
```
|
||||
fold -w50 linux.txt
|
||||
```
|
||||
|
||||
Sample output would be:
|
||||
|
||||
[![][1]][4]
|
||||
|
||||
Instead of just displaying output, we can also write the output to a new file as shown below:
|
||||
```
|
||||
fold -w50 linux.txt > linux1.txt
|
||||
```
|
||||
|
||||
The above command will wrap the lines of **linux.txt** to a width of 50 characters, and writes the output to new file named **linux1.txt**.
|
||||
|
||||
Let us check the contents of the new file:
|
||||
```
|
||||
cat linux1.txt
|
||||
```
|
||||
|
||||
[![][1]][5]
|
||||
|
||||
Did you closely notice the output of the previous commands? Some words are broken between lines. To overcome this issue, we can use -s flag to break the lines at spaces.
|
||||
|
||||
The following command wraps each line in a given file to width "50" and breaks the line at spaces:
|
||||
```
|
||||
fold -w50 -s linux.txt
|
||||
```
|
||||
|
||||
Sample output:
|
||||
|
||||
[![][1]][6]
|
||||
|
||||
See? Now, the output is much clear. This command puts each space separated word in a new line and words with length > 50 are wrapped.
|
||||
|
||||
In all above examples, we limited the output width by columns. However, we can enforce the width of the output to the number of bytes specified using **-b** option. The following command breaks the output at 20 bytes.
|
||||
```
|
||||
fold -b20 linux.txt
|
||||
```
|
||||
|
||||
Sample output:
|
||||
|
||||
[![][1]][7]
|
||||
|
||||
**Also read:**
|
||||
|
||||
+ [The Uniq Command Tutorial With Examples For Beginners][8]
|
||||
|
||||
For more details, refer the man pages.
|
||||
```
|
||||
man fold
|
||||
```
|
||||
|
||||
And, that's for now folks. You know now how to use fold command to limit the output of a command to fit in a specific width. I hope this was useful. We will be posting more useful guides everyday. Stay tuned!
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/fold-command-tutorial-examples-beginners/
|
||||
|
||||
作者:[SK][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.ostechnix.com/author/sk/
|
||||
[1]:data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7
|
||||
[2]:http://www.ostechnix.com/wp-content/uploads/2018/01/fold-command-1.png ()
|
||||
[3]:http://www.ostechnix.com/wp-content/uploads/2018/01/fold-command-2.png ()
|
||||
[4]:http://www.ostechnix.com/wp-content/uploads/2018/01/fold-command-3-1.png ()
|
||||
[5]:http://www.ostechnix.com/wp-content/uploads/2018/01/fold-command-4.png ()
|
||||
[6]:http://www.ostechnix.com/wp-content/uploads/2018/01/fold-command-5-1.png ()
|
||||
[7]:http://www.ostechnix.com/wp-content/uploads/2018/01/fold-command-6-1.png ()
|
||||
[8]:https://www.ostechnix.com/uniq-command-tutorial-examples-beginners/
|
||||
@ -0,0 +1,96 @@
|
||||
Linux yes Command Tutorial for Beginners (with Examples)
|
||||
======
|
||||
|
||||
Most of the Linux commands you encounter do not depend on other operations for users to unlock their full potential, but there exists a small subset of command line tool which you can say are useless when used independently, but become a must-have or must-know when used with other command line operations. One such tool is **yes** , and in this tutorial, we will discuss this command with some easy to understand examples.
|
||||
|
||||
But before we do that, it's worth mentioning that all examples provided in this tutorial have been tested on Ubuntu 16.04 LTS.
|
||||
|
||||
### Linux yes command
|
||||
|
||||
The yes command in Linux outputs a string repeatedly until killed. Following is the syntax of the command:
|
||||
|
||||
```
|
||||
yes [STRING]...
|
||||
yes OPTION
|
||||
```
|
||||
|
||||
And here's what the man page says about this tool:
|
||||
```
|
||||
Repeatedly output a line with all specified STRING(s), or 'y'.
|
||||
```
|
||||
|
||||
The following Q&A-type examples should give you a better idea about the usage of yes.
|
||||
|
||||
### Q1. How yes command works?
|
||||
|
||||
As the man page says, the yes command produces continuous output - 'y' by default, or any other string if specified by user. Here's a screenshot that shows the yes command in action:
|
||||
|
||||
[![How yes command works][1]][2]
|
||||
|
||||
I could only capture the last part of the output as the output frequency was so fast, but the screenshot should give you a good idea about what kind of output the tool produces.
|
||||
|
||||
You can also provide a custom string for the yes command to use in output. For example:
|
||||
|
||||
```
|
||||
yes HTF
|
||||
```
|
||||
|
||||
[![Repeat word with yes command][3]][4]
|
||||
|
||||
### Q2. Where yes command helps the user?
|
||||
|
||||
That's a valid question. Reason being, from what yes does, it's difficult to imagine the usefulness of the tool. But you'll be surprised to know that yes can not only save your time, but also automate some mundane tasks.
|
||||
|
||||
For example, consider the following scenario:
|
||||
|
||||
[![Where yes command helps the user][5]][6]
|
||||
|
||||
You can see that user has to type 'y' for each query. It's in situation like these where yes can help. For the above scenario specifically, you can use yes in the following way:
|
||||
|
||||
```
|
||||
yes | rm -ri test
|
||||
```
|
||||
|
||||
[![yes command in action][7]][8]
|
||||
|
||||
So the command made sure user doesn't have to write 'y' each time when rm asked for it. Of course, one would argue that we could have simply removed the '-i' option from the rm command. That's right, I took this example as it's simple enough to make people understand the situations in which yes can be helpful.
|
||||
|
||||
Another - and probably more relevant - scenario would be when you're using the fsck command, and don't want to enter 'y' each time system asks your permission before fixing errors.
|
||||
|
||||
### Q3. Is there any use of yes when it's used alone?
|
||||
|
||||
Yes, there's at-least one use: to tell how well a computer system handles high amount of loads. Reason being, the tool utilizes 100% processor for systems that have a single processor. In case you want to apply this test on a system with multiple processors, you need to run a yes process for each processor.
|
||||
|
||||
### Q4. What command line options yes offers?
|
||||
|
||||
The tool only offers generic command line options: --help and --version. As the names suggests. the former displays help information related to the command, while the latter one outputs version related information.
|
||||
|
||||
[![What command line options yes offers][9]][10]
|
||||
|
||||
### Conclusion
|
||||
|
||||
So now you'd agree that there could be several scenarios where the yes command would be of help. There are no command line options unique to yes, so effectively, there's no learning curve associated with the tool. Just in case you need, here's the command's [man page][11].
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.howtoforge.com/linux-yes-command/
|
||||
|
||||
作者:[Himanshu Arora][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.howtoforge.com
|
||||
[1]:https://www.howtoforge.com/images/command-tutorial/yes-def-output.png
|
||||
[2]:https://www.howtoforge.com/images/command-tutorial/big/yes-def-output.png
|
||||
[3]:https://www.howtoforge.com/images/command-tutorial/yes-custom-string.png
|
||||
[4]:https://www.howtoforge.com/images/command-tutorial/big/yes-custom-string.png
|
||||
[5]:https://www.howtoforge.com/images/command-tutorial/rm-ri-output.png
|
||||
[6]:https://www.howtoforge.com/images/command-tutorial/big/rm-ri-output.png
|
||||
[7]:https://www.howtoforge.com/images/command-tutorial/yes-in-action.png
|
||||
[8]:https://www.howtoforge.com/images/command-tutorial/big/yes-in-action.png
|
||||
[9]:https://www.howtoforge.com/images/command-tutorial/yes-help-version1.png
|
||||
[10]:https://www.howtoforge.com/images/command-tutorial/big/yes-help-version1.png
|
||||
[11]:https://linux.die.net/man/1/yes
|
||||
@ -0,0 +1,83 @@
|
||||
Top 5 Firefox extensions to install now
|
||||
======
|
||||
|
||||
The right extensions can greatly enhance your browser's capabilities, but it's important to choose carefully. Here are five that are worth a look.
|
||||
|
||||

|
||||
|
||||
The web browser has become a critical component of the computing experience for many users. Modern browsers have evolved into powerful and extensible platforms. As part of this, _extensions_ can add or modify their functionality. Extensions for Firefox are built using the WebExtensions API, a cross-browser development system.
|
||||
|
||||
Which extensions should you install? Generally, that decision comes down to how you use your browser, your views on privacy, how much you trust extension developers, and other personal preferences.
|
||||
|
||||
First, I'd like to point out that browser extensions often require the ability to read and/or change everything on the web pages you visit. You should consider the ramifications of this _very_ carefully. If an extension has modify access to all the web pages you visit, it could act as a key logger, intercept credit card information, track you online, insert advertisements, and perform a variety of other nefarious activities.
|
||||
|
||||
That doesn't mean every extension will surreptitiously do these things, but you should carefully consider the installation source, the permissions involved, your risk profile, and other factors before you install any extension. Keep in mind you can use profiles to manage how an extension impacts your attack surface--for example, using a dedicated profile with no extensions to perform tasks such as online banking.
|
||||
|
||||
With that in mind, here are five Firefox extensions that you may want to consider.
|
||||
|
||||
### uBlock Origin
|
||||
|
||||
![ublock origin ad blocker screenshot][2]
|
||||
|
||||
|
||||
Ublock Origin blocks ads and malware while enabling users to define their own content filters.
|
||||
|
||||
[uBlock Origin][3] is a fast, low-memory, wide-spectrum blocker that not only blocks ads but also lets you enforce your own content filtering. The default behavior of uBlock Origin is to block ads, trackers, and malware sites using multiple predefined filter lists. From there it allows you to arbitrarily add lists and rules, or even lock down to a default-deny mode. In addition to being powerful, this extension has proven to be efficient and performant.
|
||||
|
||||
### Privacy Badger
|
||||
|
||||
![privacy badger ad blocker][5]
|
||||
|
||||
|
||||
Privacy Badger uses algorithms to seamlessly block ads and trackers that violate the principles of user consent.
|
||||
|
||||
As its name indicates, [Privacy Badger][6] is a privacy-focused extension that blocks ads and third-party trackers. From the EFF: "Privacy Badger was born out of our desire to be able to recommend a single extension that would automatically analyze and block any tracker or ad that violated the principle of user consent; which could function well without any settings, knowledge, or configuration by the user; which is produced by an organization that is unambiguously working for its users rather than for advertisers; and which uses algorithmic methods to decide what is and isn't tracking."
|
||||
|
||||
Why is Privacy Badger on this list when it may seem so similar to uBlock Origin? One reason is that it fundamentally works differently than uBlock Origin. Another is that a practice of defense in depth is a sound policy to follow.
|
||||
|
||||
### LastPass
|
||||
|
||||
![lastpass password manager screenshot][8]
|
||||
|
||||
|
||||
LastPass is a user-friendly password manager plugin that supports two-factor authorization.
|
||||
|
||||
This is likely a controversial addition for many. Whether you should use a password manager at all--and if you do, whether you should choose one that has a browser plugin--is a hotly debated topic, and the answer very much depends on your personal risk profile. I'd assert that most casual computer users should use one, because it's much better than the most common alternative: using the same weak password everywhere.
|
||||
|
||||
[LastPass][9] is user-friendly, supports two-factor authentication, and is reasonably secure. The company has had a few security incidents in the past, but it responded well and is well-funded moving forward. Keep in mind that using a password manager isn't an all-or-nothing proposition. Many users choose to use it for the majority of their passwords, while keeping a few complicated, well-constructed passwords for important sites such as banking and multi-factor authentication in their head.
|
||||
|
||||
### Xmarks Sync
|
||||
|
||||
[Xmarks Sync][10] is a convenient extension that will sync your bookmarks, open tabs, profiles, and browser history across instances. If you have multiple machines, want to sync across desktop and mobile, or use multiple different browsers on the same machine, take a look at Xmarks Sync. (Note that this extension was recently acquired by LastPass.)
|
||||
|
||||
### Awesome Screenshot Plus
|
||||
|
||||
[Awesome Screenshot Plus][11] allows you to easily capture all or part of any web page, as well as add annotations and comments, blur sensitive information, and more. You can also share images using an optional online service. I've found this tool great for capturing parts of sites for debugging issues, discussing design, and sharing information. It's one of those tools you'll find yourself using more than you might have expected.
|
||||
|
||||
I've found all five of these extensions useful, and I recommend them to others. That said, there are many browser extensions out there. I'm curious about which ones other Opensource.com community members currently use and recommend. Let me know in the comments.
|
||||
|
||||
![Awesome Screenshot Plus screenshot][13]
|
||||
|
||||
|
||||
Awesome Screenshot Plus allows you to easily capture all or part of any web page.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/1/top-5-firefox-extensions
|
||||
|
||||
作者:[Jeremy Garcia][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/jeremy-garcia
|
||||
[2]:https://opensource.com/sites/default/files/ublock.png (ublock origin ad blocker screenshot)
|
||||
[3]:https://addons.mozilla.org/en-US/firefox/addon/ublock-origin/
|
||||
[5]:https://opensource.com/sites/default/files/images/life-uploads/privacy_badger_1.0.1.png (privacy badger ad blocker screenshot)
|
||||
[6]:https://www.eff.org/privacybadger
|
||||
[8]:https://opensource.com/sites/default/files/images/life-uploads/lastpass4.jpg (lastpass password manager screenshot)
|
||||
[9]:https://addons.mozilla.org/en-US/firefox/addon/lastpass-password-manager/
|
||||
[10]:https://addons.mozilla.org/en-US/firefox/addon/xmarks-sync/
|
||||
[11]:https://addons.mozilla.org/en-US/firefox/addon/screenshot-capture-annotate/
|
||||
[13]:https://opensource.com/sites/default/files/screenshot_from_2018-01-04_17-11-32.png (Awesome Screenshot Plus screenshot)
|
||||
@ -0,0 +1,100 @@
|
||||
Python 版的 Nmon 分析器:让你远离 excel 宏
|
||||
======
|
||||
[Nigel's monitor][1],也叫做 "Nmon",是一个很好的监控,记录和分析 Linux/*nix 系统性能随时间变化的工具。Nmon 最初由 IBM 开发并于 2009 年夏天开源。时至今日 Nmon 已经在所有 linux 平台和架构上都可用了。它提供了大量的实时工具来可视化当前系统统计信息,这些统计信息包括 CPU,RAM,网络和磁盘 I/O。然而,Nmon 最棒的特性是可以随着时间的推移记录系统性能快照。
|
||||
比如:`nmon -f -s 1`。
|
||||
![nmon CPU and Disk utilization][2]
|
||||
会创建一个日志文件,该日志文件最开头是一些系统的元数据 T( 章节 AAA - BBBV),后面是定时抓取的监控系统属性的快照,比如 CPU 和内存的使用情况。这个文件很难直接由电子表格应用来处理,因此诞生了 [Nmon_Analyzer][3] excel 宏。如果你用的是 Windows/Mac 并安装了 Microsoft Office,那么这个工具非常不错。如果没有这个环境那也可以使用 Nmon2rrd 工具,这个工具能将日志文件转换 RRD 输入文件,进而生成图形。这个过程很死板而且有点麻烦。现在出现了一个更灵活的工具,像你们介绍一下 pyNmonAnalyzer,它一个可定制化的解决方案来生成结构化的 CSV 文件和基于 [matplotlib][4] 生成图片的简单 HTML 报告。
|
||||
|
||||
### 入门介绍:
|
||||
|
||||
系统需求:
|
||||
从名字中就能看出我们需要有 python。此外 pyNmonAnalyzer 还依赖于 matplotlib 和 numpy。若你使用的是 debian 衍生的系统,则你需要先安装这些包:
|
||||
```
|
||||
$> sudo apt-get install python-numpy python-matplotlib
|
||||
|
||||
```
|
||||
|
||||
##### 获取 pyNmonAnalyzer:
|
||||
|
||||
你可页克隆 git 仓库:
|
||||
```
|
||||
$> git clone git@github.com:madmaze/pyNmonAnalyzer.git
|
||||
|
||||
```
|
||||
|
||||
或者
|
||||
|
||||
直接从这里下载:[pyNmonAnalyzer-0.1.zip][5]
|
||||
|
||||
接下来我们需要一个 Nmon 文件,如果没有的话,可以使用发行版中提供的实例或者自己录制一个样本:`nmon -F test.nmon -s 1 -c 120`,会录制每个 1 秒录制一次,供录制 120 个快照道 test.nmon 文件中 .nmon。
|
||||
|
||||
让我们来看看基本的帮助信息:
|
||||
```
|
||||
$> ./pyNmonAnalyzer.py -h
|
||||
usage: pyNmonAnalyzer.py [-h] [-x] [-d] [-o OUTDIR] [-c] [-b] [-r CONFFNAME]
|
||||
input_file
|
||||
|
||||
nmonParser converts Nmon monitor files into time-sorted
|
||||
CSV/Spreadsheets for easier analysis, without the use of the
|
||||
MS Excel Macro. Also included is an option to build an HTML
|
||||
report with graphs, which is configured through report.config.
|
||||
|
||||
positional arguments:
|
||||
input_file Input NMON file
|
||||
|
||||
optional arguments:
|
||||
-h, --help show this help message and exit
|
||||
-x, --overwrite overwrite existing results (Default: False)
|
||||
-d, --debug debug? (Default: False)
|
||||
-o OUTDIR, --output OUTDIR
|
||||
Output dir for CSV (Default: ./data/)
|
||||
-c, --csv CSV output? (Default: False)
|
||||
-b, --buildReport report output? (Default: False)
|
||||
-r CONFFNAME, --reportConfig CONFFNAME
|
||||
Report config file, if none exists: we will write the
|
||||
default config file out (Default: ./report.config)
|
||||
|
||||
```
|
||||
|
||||
该工具有两个主要的选项
|
||||
|
||||
1。将 nmon 文件传唤成一系列独立的 CSV 文件
|
||||
2。使用 matplotlib 生成带图形的 HTML 报告
|
||||
|
||||
|
||||
|
||||
下面命令既会生成 CSV 文件,也会生成 HTML 报告:
|
||||
```
|
||||
$> ./pyNmonAnalyzer.py -c -b test.nmon
|
||||
|
||||
```
|
||||
|
||||
这会常见一个 `。/data` 目录,其中有一个存放 CSV 文件的目录 ("。/data/csv/"),一个存放 PNG 图片的目录 ("。/data/img/") 以及一个 HTML 报告 ("。/data/report.html")。
|
||||
|
||||
默认情况下,HTML 报告中会用图片展示 CPU,磁盘繁忙度,内存使用情况和网络传输情况。所有这些都定义在一个自解释的配置文件中 ("report.config")。目前这个工具 h 那不是特别的灵活,因为 CPU 和 MEM 除了 on 和 off 外,无法做其他的配置。不过下一步将会改进作图的方法并允许用户灵活地指定针对哪些数据使用哪种作图方法。
|
||||
|
||||
### 报告的例子:
|
||||
|
||||
[![pyNmonAnalyzer Graph output][6]
|
||||
**Click to see the full Report**][7]
|
||||
|
||||
目前这些报告还十分的枯燥而且只能打印出基本的几种标记图表,不过它的功能还在不断的完善中。目前在开发的是一个向导来让配置调整变得更容易。如果有任何建议,找到任何 bug 或者有任何功能需求,欢迎与我交流。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://matthiaslee.com/python-nmon-analyzer-moving-away-from-excel-macros/
|
||||
|
||||
作者:[Matthias Lee][a]
|
||||
译者:[lujun9972](https://github.com/lujun9972)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://matthiaslee.com/
|
||||
[1]:http://nmon.sourceforge.net/
|
||||
[2]:https://matthiaslee.com//content/images/2015/06/nmon_cpudisk.png
|
||||
[3]:http://www.ibm.com/developerworks/wikis/display/WikiPtype/nmonanalyser
|
||||
[4]:http://matplotlib.org/
|
||||
[5]:https://github.com/madmaze/pyNmonAnalyzer/blob/master/release/pyNmonAnalyzer-0.1.zip?raw=true
|
||||
[6]:https://matthiaslee.com//content/images/2017/04/teaser-short_0.png (pyNmonAnalyzer Graph output)
|
||||
[7]:http://matthiaslee.com/pub/pyNmonAnalyzer/data/report.html
|
||||
@ -0,0 +1,153 @@
|
||||
当你在 Linux 上启动一个进程时会发生什么?
|
||||
===========================================================
|
||||
|
||||
|
||||
本文是关于 fork 和 exec 是如何在 Unix 上工作的。你或许已经知道,也有人还不知道。几年前当我了解到这些时,我惊叹不已。
|
||||
|
||||
我们要做的是启动一个进程。我们已经在博客上讨论了很多关于**系统调用**的问题,每当你启动一个进程或者打开一个文件,这都是一个系统调用。所以你可能会认为有这样的系统调用:
|
||||
|
||||
```
|
||||
start_process(["ls", "-l", "my_cool_directory"])
|
||||
|
||||
```
|
||||
|
||||
这是一个合理的想法,显然这是它在 DOS 或 Windows 中的工作原理。我想说的是,这并不是 Linux 上的工作原理。但是,我查阅了文档,确实有一个 [posix_spawn][2] 的系统调用基本上是这样做的,不过这不在本文的讨论范围内。
|
||||
|
||||
### fork 和 exec
|
||||
|
||||
Linux 上的 `posix_spawn` 是通过两个系统调用实现的,分别是 `fork` 和 `exec`(实际上是 execve),这些都是人们常常使用的。尽管在 OS X 上,人们使用 `posix_spawn`,而 fork 和 exec 是不提倡的,但我们将讨论的是 Linux。
|
||||
|
||||
Linux 中的每个进程都存在于“进程树”中。你可以通过运行 `pstree` 命令查看进程树。树的根是 `init`,进程号是 1。每个进程(init 除外)都有一个父进程,一个进程都可以有很多子进程。
|
||||
|
||||
所以,假设我要启动一个名为 `ls` 的进程来列出一个目录。我是不是只要发起一个进程 `ls` 就好了呢?不是的。
|
||||
|
||||
我要做的是,创建一个子进程,这个子进程是我本身的一个克隆,然后这个子进程的“大脑”被替代,变成 `ls`。
|
||||
|
||||
开始是这样的:
|
||||
|
||||
```
|
||||
my parent
|
||||
|- me
|
||||
|
||||
```
|
||||
|
||||
然后运行 `fork()`,生成一个子进程,是我自己的一份克隆:
|
||||
|
||||
```
|
||||
my parent
|
||||
|- me
|
||||
|-- clone of me
|
||||
|
||||
```
|
||||
|
||||
然后我让子进程运行 `exec("ls")`,变成这样:
|
||||
|
||||
```
|
||||
my parent
|
||||
|- me
|
||||
|-- ls
|
||||
|
||||
```
|
||||
|
||||
当 ls 命令结束后,我几乎又变回了我自己:
|
||||
|
||||
```
|
||||
my parent
|
||||
|- me
|
||||
|-- ls (zombie)
|
||||
|
||||
```
|
||||
|
||||
在这时 ls 其实是一个僵尸进程。这意味着它已经死了,但它还在等我,以防我需要检查它的返回值(使用 `wait` 系统调用)。一旦我获得了它的返回值,我将再次恢复独自一人的状态。
|
||||
|
||||
```
|
||||
my parent
|
||||
|- me
|
||||
|
||||
```
|
||||
|
||||
### fork 和 exec 的代码实现
|
||||
|
||||
如果你要编写一个 shell,这是你必须做的一个练习(这是一个非常有趣和有启发性的项目。Kamal 在 Github 上有一个很棒的研讨会:[https://github.com/kamalmarhubi/shell-workshop][3])
|
||||
|
||||
事实证明,有了 C 或 Python 的技能,你可以在几个小时内编写一个非常简单的 shell,例如 bash。(至少如果你旁边能有个人多少懂一点,如果没有的话用时会久一点。)我已经完成啦,真的很棒。
|
||||
|
||||
这就是 fork 和 exec 在程序中的实现。我写了一段 C 的伪代码。请记住,[fork 也可能会失败哦。][4]
|
||||
|
||||
```
|
||||
int pid = fork();
|
||||
// 我要分身啦
|
||||
// “我”是谁呢?可能是子进程也可能是父进程
|
||||
if (pid == 0) {
|
||||
// 我现在是子进程
|
||||
// 我的大脑将被替代,然后变成一个完全不一样的进程“ls”
|
||||
exec(["ls"])
|
||||
} else if (pid == -1) {
|
||||
// 天啊,fork 失败了,简直是灾难!
|
||||
} else {
|
||||
// 我是父进程耶
|
||||
// 继续做一个酷酷的美男子吧
|
||||
// 需要的话,我可以等待子进程结束
|
||||
}
|
||||
|
||||
```
|
||||
|
||||
### 上文提到的“大脑被替代“是什么意思呢?
|
||||
|
||||
进程有很多属性:
|
||||
|
||||
* 打开的文件(包括打开的网络连接)
|
||||
|
||||
* 环境变量
|
||||
|
||||
* 信号处理程序(在程序上运行 Ctrl + C 时会发生什么?)
|
||||
|
||||
* 内存(你的“地址空间”)
|
||||
|
||||
* 寄存器
|
||||
|
||||
* 可执行文件(/proc/$pid/exe)
|
||||
|
||||
* cgroups 和命名空间(与 Linux 容器相关)
|
||||
|
||||
* 当前的工作目录
|
||||
|
||||
* 运行程序的用户
|
||||
|
||||
* 其他我还没想到的
|
||||
|
||||
当你运行 `execve` 并让另一个程序替代你的时候,实际上几乎所有东西都是相同的! 你们有相同的环境变量、信号处理程序和打开的文件等等。
|
||||
|
||||
唯一改变的是,内存、寄存器以及正在运行的程序,这可是件大事。
|
||||
|
||||
### 为何 fork 并非那么耗费资源(写入时复制)
|
||||
|
||||
你可能会问:“如果我有一个使用了 2 GB 内存的进程,这是否意味着每次我启动一个子进程,所有 2 GB 的内存都要被复制一次?这听起来要耗费很多资源!“
|
||||
|
||||
事实上,Linux 为 fork() 调用实现了写入时复制(copy on write),对于新进程的 2 GB 内存来说,就像是“看看旧的进程就好了,是一样的!”。然后,当如果任一进程试图写入内存,此时系统才真正地复制一个内存的副本给该进程。如果两个进程的内存是相同的,就不需要复制了。
|
||||
|
||||
### 为什么你需要知道这么多
|
||||
|
||||
你可能会说,好吧,这些琐事听起来很厉害,但为什么这么重要?关于信号处理程序或环境变量的细节会被继承吗?这对我的日常编程有什么实际影响呢?
|
||||
|
||||
有可能哦!比如说,在 Kamal 的博客上有一个很有意思的 [bug][5]。它讨论了 Python 如何使信号处理程序忽略了 SIGPIPE。也就是说,如果你从 Python 里运行一个程序,默认情况下它会忽略 SIGPIPE!这意味着,程序从 Python 脚本和从 shell 启动的表现会**有所不同**。在这种情况下,它会造成一个奇怪的问题。
|
||||
|
||||
所以,你的程序的环境(环境变量、信号处理程序等)可能很重要,都是从父进程继承来的。知道这些,在调试时是很有用的。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://jvns.ca/blog/2016/10/04/exec-will-eat-your-brain/
|
||||
|
||||
作者:[ Julia Evans][a]
|
||||
译者:[jessie-pang](https://github.com/jessie-pang)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://jvns.ca
|
||||
[1]:https://jvns.ca/categories/favorite
|
||||
[2]:http://man7.org/linux/man-pages/man3/posix_spawn.3.html
|
||||
[3]:https://github.com/kamalmarhubi/shell-workshop
|
||||
[4]:https://rachelbythebay.com/w/2014/08/19/fork/
|
||||
[5]:http://kamalmarhubi.com/blog/2015/06/30/my-favourite-bug-so-far-at-the-recurse-center/
|
||||
@ -1,139 +0,0 @@
|
||||
# [关于 Linux 页面表隔离补丁的神秘情况][14]
|
||||
|
||||
* * *
|
||||
|
||||
_长文预警:_ 这是一个目前严格限制的、禁止披露的安全 bug,它影响到目前几乎所有实现虚拟内存的 CPU 架构,需要硬件的改变才能完全解决这个 bug。通过软件来缓解这种影响的紧急开发工作正在进行中,并且最近在 Linux 内核中已经得以实现,并且,在 11 月份,在 NT 内核中也开始了一个类似的紧急开发。在最糟糕的情况下,软件修复会导致一般工作负载出现巨大的减速(译者注:外在表现为 CPU 性能下降)。这里有一个提示,攻击会影响虚拟化环境,包括 Amazon EC2 和 Google 计算引擎,以及另外的提示是,这种精确的攻击可能涉及一个新的 Rowhammer 变种(译者注:一个由 Google 安全团队提出的 DRAM 的安全漏洞,在文章的后面部分会简单介绍)。
|
||||
|
||||
* * *
|
||||
|
||||
我一般不太关心安全问题,但是,对于这个 bug 我有点好奇,而一般会去写这个主题的人似乎都很忙,要么就是知道这个主题细节的人会保持沉默。这让我在新年的第一天(元旦那天)花了几个小时深入去挖掘关于这个谜团的更多信息,并且我将这些信息片断拼凑到了一起。
|
||||
|
||||
注意,这是一件相互之间高度相关的事件,因此,它的主要描述都是猜测,除非过一段时间,它的限制禁令被取消。我所看到的,包括涉及到的供应商、许多争论和这种戏剧性场面,将在限制禁令取消的那一天出现。
|
||||
|
||||
**LWN**
|
||||
|
||||
这个事件的线索出现于 12 月 20 日 LWN 上的 [内核页面表的当前状况:页面隔离][2](致校对:就是昨天我翻译的那篇) 这篇文章。它在 10 月份被奥地利的 [TU Graz][4] 的一组研究人员第一次发表。从文章语气上明显可以看到这项工作的紧急程度,内核的核心开发者紧急加入了 [KAISER 补丁系列][3]。
|
||||
|
||||
这一系列的补丁的用途从概念上说很简单:为了阻止运行在用户空间的进程在进程页面表中,通过映射得到内核空间页面的各种攻击方式,可以很好地阻止了从非特权的用户空间代码中识别到内核虚拟地址的攻击企图。
|
||||
|
||||
这组论文描述的 KAISER,[KASLR 已死:KASLR 永存][5](致校对:这里我觉得是[ASLR 已死:KASLR 永存],请查看原文出处。),在它的抽象中,通过特定的引用,在内存管理硬件中去删除所有内核地址空间的信息,即便是用户代码在这个 CPU 上处于活动状态的时候。
|
||||
|
||||
这个补丁集的魅力在于它触及到了核心,内核的全部基础核心(和与用户空间的接口),显然,它应该被最优先考虑。在 Linux 中当我读到关于内存管理的变化时,通常,第一个引用发生在变化被合并的很久之前,并且,通常会进行多次的评估、拒绝、以及因各种原因爆发争论的一系列过程。
|
||||
|
||||
KAISER(就是现在的 KPTI)系列被合并还不足三个月。
|
||||
|
||||
**ASLR 概述**
|
||||
|
||||
从表面上看,设计的这些补丁可以确保地址空间布局随机化仍然有效:这是一个现代操作系统的安全特性,它企图去将更多的随机位,引入到公共映射对象的地址空间中。
|
||||
|
||||
例如,在引用 /usr/bin/python 时,动态链接将对系统的 C 库、堆、线程栈、以及主要的可执行文件进行排布,去接受随机分配的地址范围:
|
||||
|
||||
> $ bash -c ‘grep heap /proc/$$/maps’
|
||||
> 019de000-01acb000 rw-p 00000000 00:00 0 [heap]
|
||||
> $ bash -c 'grep heap /proc/$$/maps’
|
||||
> 023ac000-02499000 rw-p 00000000 00:00 0 [heap]
|
||||
|
||||
注意跨 bash 进程的开始和结束偏移量上的堆的变化。
|
||||
|
||||
这个特性的效果是,一个 buffer 管理的 bug 导致一个攻击者可以去覆写一些程序代码指向的内存地址,并且,那个地址将在程序控制流中被使用,诸如这种攻击者可以使控制流转向到一个包含他们选择的内容的 buffer 上,对于攻击者来说,使用机器代码来填充 buffer 将更困难。例如,system() C 库函数将被引用,因为,那个函数的地址在不同的运行进程上不同的。
|
||||
|
||||
这是一个简单的示例,ASLR 被设计用于去保护类似这样的许多场景,包括阻止攻击者从有可能被用来修改控制流或者实现一个攻击的程序数据的地址内容。
|
||||
|
||||
KASLR 是 “简化的” 应用到内核本身的 ASLR:在每个重新引导的系统上,属于内核的地址范围是随机的,这样就使得,虽然被攻击者转向的控制流运行在内核模式上,但是,不能猜测到为实现他们的攻击目的所需要的函数和结构的地址,比如,定位当前进程数据,将活动的 UID 从一个非特权用户提升到 root 用户,等等。
|
||||
|
||||
**坏消息:缓减这种攻击的软件运行成本过于贵重**
|
||||
|
||||
老的 Linux 将内核内存映射在同一个页面表中的这个行为的主要原因是,当用户的代码触发一个系统调用、故障、或者产生中断时,用户内存也是这种行为,这样就不需要改变正在运行的进程的虚拟内存布局。
|
||||
|
||||
因为在那样,它不需要去改变虚拟内存布局,进而也就不需要去清洗掉(flush)与 CPU 性能高度依赖的缓存(致校对:意思是如果清掉这些缓存,CPU 性能就会下降),主要是通过 [转换查找缓冲器][6](译者注:Translation Lookaside Buffer(TLB)(将虚拟地址转换为物理地址)。
|
||||
|
||||
使用已合并的页面表分割补丁后变成,内核每次开始运行时,需要将内核的缓存清掉,并且,每次用户代码恢复运行时都会这样。对于大多数工作负载,在每个系统调用中,TLB 的实际总损失将导致明显的变慢:[@grsecurity 测量的一个简单的案例][7],在一个最新的 AMD CPU 上,Linux “du -s” 变慢了 50%。
|
||||
|
||||
**34C3**
|
||||
|
||||
在今年的 CCC 上,你可以找到 TU Graz 的研究人员的另一篇,[一个纯 Javascript 的 ASLR 攻击描述][8] ,通过仔细地掌握 CPU 内存管理单元的操作时机,遍历了描述虚拟内存布局的页面表,来实现 ASLR 攻击。它通过高度精确的时间掌握和选择性回收的 CPU 缓存行的组合方式来实现这种结果,一个运行在 web 浏览器的 Javascript 程序可以找回一个 Javascript 对象的虚拟地址,使得利用浏览器内存管理 bugs 被允许进行接下来的攻击。
|
||||
|
||||
因此,从表面上看,我们有一组 KAISER 补丁,也展示了解除 ASLR 的地址的技术,并且,这个展示使用的是 Javascript,很快就可以在一个操作系统内核上进行重新部署。
|
||||
|
||||
**虚拟内存概述**
|
||||
|
||||
在通常情况下,当一些机器码尝试去加载、存储、或者跳转到一个内存地址时,现代的 CPUs 必须首先去转换这个 _虚拟地址_ 到一个 _物理地址_ ,通过使用一系列操作系统托管的数组(被称为页面表),来描述一个虚拟地址和安装在这台机器上的物理内存之间的映射。
|
||||
|
||||
在现代操作系统中,虚拟内存可能是仅有的一个非常重要的强大特性:它都阻止了什么呢?例如,一个濒临死亡的进程崩溃了操作系统、一个 web 浏览器 bugs 崩溃了你的桌面环境、或者,一个运行在 Amazon EC2 中的虚拟机的变化影响了同一台主机上的另一个虚拟机。
|
||||
|
||||
这种攻击的原理是,利用 CPU 上维护的大量的缓存,通过仔细地操纵这些缓存的内存,它可以去推测内存管理单元的地址,以去访问页面表的不同层级,因为一个未缓存的访问将比一个缓存的访问花费更长的时间。通过检测页面表上可访问的元素,它可能去恢复在 MMU(译者注:存储器管理单元)忙于解决的虚拟地址中的大部分比特(bits)。
|
||||
|
||||
**这种动机的证据,但是不用恐慌**
|
||||
|
||||
我们找到了动机,但是到目前为止,我们并没有看到这项工作引进任何恐慌。总的来说,ASLR 并不能完全缓减这种风险,并且也是一道最后的防线:仅在这 6 个月的周期内,即便是一个没有安全意识的人也能看到一些关于解除(unmasking) ASLR 的指针的新闻,并且,实际上 ASLR 已经存在了。
|
||||
|
||||
单独的修复 ASLR 并不足于去描述这项工作高优先级背后的动机。
|
||||
|
||||
**它是硬件安全 bug 的证据**
|
||||
|
||||
通过阅读这一系列补丁,可以明确许多事情。
|
||||
|
||||
第一,正如 [@grsecurity 指出][9] 的,代码中的一些注释已经被编辑(redacted),并且,描述这项工作的额外的主文档文件已经在 Linux 源代码树中看不到了。
|
||||
|
||||
测试代码已经以运行时补丁的方式构建,在系统引导时仅当内核检测到是受影响的系统时才会被应用,与对臭名昭著的 [Pentium F00F bug][10] 的缓解措施,使用完全相同的机制:
|
||||
|
||||

|
||||
|
||||
**更多的线索:Microsoft 也已经实现了页面表的分割**
|
||||
|
||||
通过对 FreeBSD 源代码的一个小挖掘可以看出,目前,其它的免费操作系统没有实现页面表分割,但是,通过 [Alex Ioniscu on Twitter][11] 的启示,这项工作已经不局限于 Linux 了:从 11 月起,公开的 NT 内核也已经实现了同样的技术。
|
||||
|
||||
**猜测的结果:Rowhammer**
|
||||
|
||||
在 TU Graz 上进一步挖掘对这项工作的研究,我们找到 [When rowhammer only knocks once][12],12 月 4 日通告的一个 [新的 Rowhammer 攻击的变种][13]:
|
||||
|
||||
> 在这篇论文中,我们提出了新的 Rowhammer 攻击和原始的漏洞利用,表明即便是所有防御的组合也没有效果。我们的新攻击技术,对一个位置的反复 “敲打”(hammering),打破了以前假定的触发 Rowhammer bug 的前提条件。
|
||||
|
||||
作一个快速回顾,Rowhammer 是一个对主要(全部?)种类的商品 DRAMs 的基础问题的一个类别,比如,在普通的计算机中的内存上。通过精确操作内存中的一个区域,这可能会导致内存该区域存储的相关(但是逻辑上是独立的)内容被毁坏。效果是,Rowhammer 可能被用于去反转内存中的比特(bits),使未经授权的用户代码可以访问到,比如,这个比特位描述了系统中的其它代码的访问权限。
|
||||
|
||||
我发现在 Rowhammer 上,这项工作很有意思,尤其是它反转的位接近页面表分割补丁时,但是,因为 Rowhammer 攻击要求一个目标:你必须知道你尝试去反转的比特在内存中的物理地址,并且,第一步是得到的物理地址可能是一个虚拟地址,比如,在 KASLR 中的解除(unmasking)工作。
|
||||
|
||||
**猜测的结果:它影响主要的云供应商**
|
||||
|
||||
在我能看到的内核邮件列表中,除了子系统维护者的名字之外,e-mail 地址是属于 Intel、Amazon、和 Google 的雇员,这表示这两个大的云计算供应商对此特别感兴趣,这为我们提供了一个强大的线索,这项工作很大的可能是受虚拟化安全驱动的。
|
||||
|
||||
它可能会导致产生更多的猜测:虚拟机 RAM 和由这些虚拟机所使用的虚拟内存地址,最终表示为在主机上大量的相邻的数组,那些数组,尤其是在一个主机上只有两个租户的情况下,在 Xen 和 Linux 内核中是通过内存分配来确定的,这样可能会有(准确性)非常高的可预测行为。
|
||||
|
||||
**最喜欢的猜测:这是一个提升特权的攻击**
|
||||
|
||||
把这些综合到一起,我并不难预测,如果我们在 2018 年使用这些存在提升特权的 bug 的发行版,或者类似的系统去驱动如此紧急的情况,并且在补丁集的抄送列表中出现如此多的感兴趣者的名字。
|
||||
|
||||
最后的一个趣闻,虽然我在阅读补丁集的时候没有找到我要的东西,但是,在一些代码中标记,paravirtual 或者 HVM Xen 是不受此影响的。
|
||||
|
||||
**Invest in popcorn, 2018 将很有趣**
|
||||
|
||||
这些猜想是完全有可能的,它离实现很近,但是可以肯定的是,当这些事情被公开后,那将是一个非常令人激动的几个星期。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://pythonsweetness.tumblr.com/post/169166980422/the-mysterious-case-of-the-linux-page-table
|
||||
|
||||
作者:[python sweetness][a]
|
||||
译者:[qhwdw](https://github.com/qhwdw)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://pythonsweetness.tumblr.com/
|
||||
[1]:http://pythonsweetness.tumblr.com/post/169217189597/quiet-in-the-peanut-gallery
|
||||
[2]:http://t.umblr.com/redirect?z=https%3A%2F%2Flwn.net%2FArticles%2F741878%2F&t=ODY1YTM4MjYyYzU2NzNmM2VmYzEyMGIzODJkY2IxNDg0MDhkZDM1MSxXRG55eVpXNw%3D%3D&b=t%3AqBH2b-yWL63V8acbuG-EUQ&p=http%3A%2F%2Fpythonsweetness.tumblr.com%2Fpost%2F169166980422%2Fthe-mysterious-case-of-the-linux-page-table&m=1
|
||||
[3]:http://t.umblr.com/redirect?z=https%3A%2F%2Flwn.net%2FArticles%2F738975%2F&t=MzQxMmMyYThhNDdiMGJkZmRmZWI5NDkzZmQ3ZTM4ZDcwYzFhMjU5OSxXRG55eVpXNw%3D%3D&b=t%3AqBH2b-yWL63V8acbuG-EUQ&p=http%3A%2F%2Fpythonsweetness.tumblr.com%2Fpost%2F169166980422%2Fthe-mysterious-case-of-the-linux-page-table&m=1
|
||||
[4]:http://t.umblr.com/redirect?z=https%3A%2F%2Fwww.iaik.tugraz.at%2Fcontent%2Fresearch%2Fsesys%2F&t=NzEwZjg5YmQ1ZTNlZWIyYWE0YzgzZmZjN2ZmM2E2YjMzNDk5YTk4YixXRG55eVpXNw%3D%3D&b=t%3AqBH2b-yWL63V8acbuG-EUQ&p=http%3A%2F%2Fpythonsweetness.tumblr.com%2Fpost%2F169166980422%2Fthe-mysterious-case-of-the-linux-page-table&m=1
|
||||
[5]:http://t.umblr.com/redirect?z=https%3A%2F%2Fgruss.cc%2Ffiles%2Fkaiser.pdf&t=OTk4NGQwZTQ1NTdlNzE1ZGEyZTdlY2ExMTY1MTJhNzk2ODIzYWY1OSxXRG55eVpXNw%3D%3D&b=t%3AqBH2b-yWL63V8acbuG-EUQ&p=http%3A%2F%2Fpythonsweetness.tumblr.com%2Fpost%2F169166980422%2Fthe-mysterious-case-of-the-linux-page-table&m=1
|
||||
[6]:http://t.umblr.com/redirect?z=https%3A%2F%2Fen.wikipedia.org%2Fwiki%2FTranslation_lookaside_buffer&t=NjEyNGUzNTk2MGY3ODY3ODIxZjQ1Yjc4YWZjMGNmNmI1OWU1M2U0YyxXRG55eVpXNw%3D%3D&b=t%3AqBH2b-yWL63V8acbuG-EUQ&p=http%3A%2F%2Fpythonsweetness.tumblr.com%2Fpost%2F169166980422%2Fthe-mysterious-case-of-the-linux-page-table&m=1
|
||||
[7]:https://twitter.com/grsecurity/status/947439275460702208
|
||||
[8]:http://t.umblr.com/redirect?z=https%3A%2F%2Fwww.youtube.com%2Fwatch%3Fv%3Dewe3-mUku94&t=NjczZmIzNWY3YTA2NGFiZDJmYThlMjlhMWM1YTE3NThhNzY0OGJlMSxXRG55eVpXNw%3D%3D&b=t%3AqBH2b-yWL63V8acbuG-EUQ&p=http%3A%2F%2Fpythonsweetness.tumblr.com%2Fpost%2F169166980422%2Fthe-mysterious-case-of-the-linux-page-table&m=1
|
||||
[9]:https://twitter.com/grsecurity/status/947147105684123649
|
||||
[10]:http://t.umblr.com/redirect?z=https%3A%2F%2Fen.wikipedia.org%2Fwiki%2FPentium_F00F_bug&t=Yjc4MDZhNDZjZDdiYWNkNmJkNjQ3ZDNjZmVlZmRkMGM2NDYwN2I2YSxXRG55eVpXNw%3D%3D&b=t%3AqBH2b-yWL63V8acbuG-EUQ&p=http%3A%2F%2Fpythonsweetness.tumblr.com%2Fpost%2F169166980422%2Fthe-mysterious-case-of-the-linux-page-table&m=1
|
||||
[11]:https://twitter.com/aionescu/status/930412525111296000
|
||||
[12]:http://t.umblr.com/redirect?z=https%3A%2F%2Fwww.tugraz.at%2Fen%2Ftu-graz%2Fservices%2Fnews-stories%2Fplanet-research%2Fsingleview%2Farticle%2Fwenn-rowhammer-nur-noch-einmal-klopft%2F&t=NWM1ZjZlZWU2NzFlMWIyNmI5MGZlNjJlZmM2YTlhOTIzNGY3Yjk4NyxXRG55eVpXNw%3D%3D&b=t%3AqBH2b-yWL63V8acbuG-EUQ&p=http%3A%2F%2Fpythonsweetness.tumblr.com%2Fpost%2F169166980422%2Fthe-mysterious-case-of-the-linux-page-table&m=1
|
||||
[13]:http://t.umblr.com/redirect?z=https%3A%2F%2Farxiv.org%2Fabs%2F1710.00551&t=ZjAyMDUzZWRmYjExNGNlYzRlMjE1NTliMTI2M2Y4YjkxMTFhMjI0OCxXRG55eVpXNw%3D%3D&b=t%3AqBH2b-yWL63V8acbuG-EUQ&p=http%3A%2F%2Fpythonsweetness.tumblr.com%2Fpost%2F169166980422%2Fthe-mysterious-case-of-the-linux-page-table&m=1
|
||||
[14]:http://pythonsweetness.tumblr.com/post/169166980422/the-mysterious-case-of-the-linux-page-table
|
||||
[15]:http://pythonsweetness.tumblr.com/
|
||||
|
||||
|
||||
Loading…
Reference in New Issue
Block a user