mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-03 23:40:14 +08:00
Merge branch 'master' of https://github.com/LCTT/TranslateProject
merge from lctt
This commit is contained in:
commit
1466a2593f
@ -0,0 +1,156 @@
|
||||
如何在 Linux 上使用 Gmail SMTP 服务器发送邮件通知
|
||||
================================================================================
|
||||
假定你想配置一个 Linux 应用,用于从你的服务器或桌面客户端发送邮件信息。邮件信息可能是邮件简报、状态更新(如 [Cachet][1])、监控警报(如 [Monit][2])、磁盘时间(如 [RAID mdadm][3])等等。当你要建立自己的 [邮件发送服务器][4] 传递信息时 ,你可以替代使用一个免费的公共 SMTP 服务器,从而避免遭受维护之苦。
|
||||
|
||||
谷歌的 Gmail 服务就是最可靠的 **免费 SMTP 服务器** 之一。想要从应用中发送邮件通知,你仅需在应用中添加 Gmail 的 SMTP 服务器地址和你的身份凭证即可。
|
||||
|
||||
使用 Gmail 的 SMTP 服务器会遇到一些限制,这些限制主要用于阻止那些经常滥用服务器来发送垃圾邮件和使用邮件营销的家伙。举个例子,你一次只能给至多 100 个地址发送信息,并且一天不能超过 500 个收件人。同样,如果你不想被标为垃圾邮件发送者,你就不能发送过多的不可投递的邮件。当你达到任何一个限制,你的 Gmail 账户将被暂时的锁定一天。简而言之,Gmail 的 SMTP 服务器对于你个人的使用是非常棒的,但不适合商业的批量邮件。
|
||||
|
||||
说了这么多,是时候向你们展示 **如何在 Linux 环境下使用 Gmail 的 SMTP 服务器** 了。
|
||||
|
||||
### Google Gmail SMTP 服务器设置 ###
|
||||
|
||||
如果你想要通过你的应用使用 Gmail 的 SMTP 服务器发送邮件,请牢记接下来的详细说明。
|
||||
|
||||
- **邮件发送服务器 (SMTP 服务器)**: smtp.gmail.com
|
||||
- **使用认证**: 是
|
||||
- **使用安全连接**: 是
|
||||
- **用户名**: 你的 Gmail 账户 ID (比如 "alice" ,如果你的邮箱为 alice@gmail.com)
|
||||
- **密码**: 你的 Gmail 密码
|
||||
- **端口**: 587
|
||||
|
||||
确切的配置根据应用会有所不同。在本教程的剩余部分,我将向你展示一些在 Linux 上使用 Gmail SMTP 服务器的应用示例。
|
||||
|
||||
### 从命令行发送邮件 ###
|
||||
|
||||
作为第一个例子,让我们尝试最基本的邮件功能:使用 Gmail SMTP 服务器从命令行发送一封邮件。为此,我将使用一个称为 mutt 的命令行邮件客户端。
|
||||
|
||||
先安装 mutt:
|
||||
|
||||
对于 Debian-based 系统:
|
||||
|
||||
$ sudo apt-get install mutt
|
||||
|
||||
对于 Red Hat based 系统:
|
||||
|
||||
$ sudo yum install mutt
|
||||
|
||||
创建一个 mutt 配置文件(~/.muttrc),并和下面一样,在文件中指定 Gmail SMTP 服务器信息。将 \<gmail-id> 替换成自己的 Gmail ID。注意该配置只是为了发送邮件而已(而非接收邮件)。
|
||||
|
||||
$ vi ~/.muttrc
|
||||
|
||||
----------
|
||||
|
||||
set from = "<gmail-id>@gmail.com"
|
||||
set realname = "Dan Nanni"
|
||||
set smtp_url = "smtp://<gmail-id>@smtp.gmail.com:587/"
|
||||
set smtp_pass = "<gmail-password>"
|
||||
|
||||
一切就绪,使用 mutt 发送一封邮件:
|
||||
|
||||
$ echo "This is an email body." | mutt -s "This is an email subject" alice@yahoo.com
|
||||
|
||||
想在一封邮件中添加附件,使用 "-a" 选项
|
||||
|
||||
$ echo "This is an email body." | mutt -s "This is an email subject" alice@yahoo.com -a ~/test_attachment.jpg
|
||||
|
||||

|
||||
|
||||
使用 Gmail SMTP 服务器意味着邮件将显示是从你 Gmail 账户发出的。换句话说,收件人将视你的 Gmail 地址为发件人地址。如果你想要使用自己的域名作为邮件发送方,你需要使用 Gmail SMTP 转发服务。
|
||||
|
||||
### 当服务器重启时发送邮件通知 ###
|
||||
|
||||
如果你在 [虚拟专用服务器(VPS)][5] 上跑了些重要的网站,建议监控 VPS 的重启行为。作为一个更为实用的例子,让我们研究如何在你的 VPS 上为每一次重启事件建立邮件通知。这里假设你的 VPS 上使用的是 systemd,并向你展示如何为自动邮件通知创建一个自定义的 systemd 启动服务。
|
||||
|
||||
首先创建下面的脚本 reboot_notify.sh,用于负责邮件通知。
|
||||
|
||||
$ sudo vi /usr/local/bin/reboot_notify.sh
|
||||
|
||||
----------
|
||||
|
||||
#!/bin/sh
|
||||
|
||||
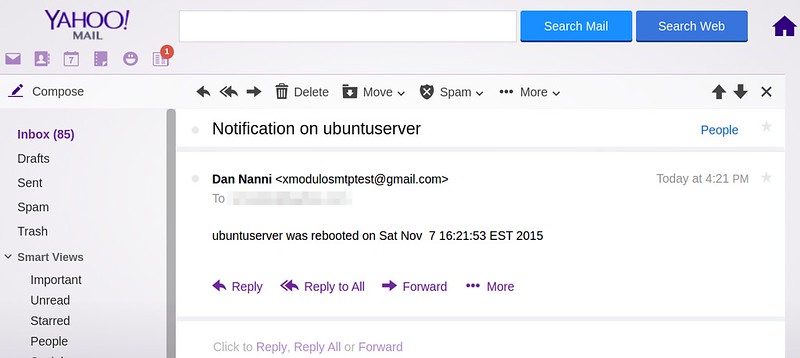
echo "`hostname` was rebooted on `date`" | mutt -F /etc/muttrc -s "Notification on `hostname`" alice@yahoo.com
|
||||
|
||||
----------
|
||||
|
||||
$ sudo chmod +x /usr/local/bin/reboot_notify.sh
|
||||
|
||||
在这个脚本中,我使用 "-F" 选项,用于指定系统级的 mutt 配置文件位置。因此不要忘了创建 /etc/muttrc 文件,并如前面描述的那样填入 Gmail SMTP 信息。
|
||||
|
||||
现在让我们创建如下一个自定义的 systemd 服务。
|
||||
|
||||
$ sudo mkdir -p /usr/local/lib/systemd/system
|
||||
$ sudo vi /usr/local/lib/systemd/system/reboot-task.service
|
||||
|
||||
----------
|
||||
|
||||
[Unit]
|
||||
Description=Send a notification email when the server gets rebooted
|
||||
DefaultDependencies=no
|
||||
Before=reboot.target
|
||||
|
||||
[Service]
|
||||
Type=oneshot
|
||||
ExecStart=/usr/local/bin/reboot_notify.sh
|
||||
|
||||
[Install]
|
||||
WantedBy=reboot.target
|
||||
|
||||
在创建服务后,添加并启动该服务。
|
||||
|
||||
$ sudo systemctl enable reboot-task
|
||||
$ sudo systemctl start reboot-task
|
||||
|
||||
从现在起,在每次 VPS 重启时,你将会收到一封通知邮件。
|
||||
|
||||
|
||||
|
||||
### 通过服务器使用监控发送邮件通知 ###
|
||||
|
||||
作为最后一个例子,让我展示一个现实生活中的应用程序,[Monit][6],这是一款极其有用的服务器监控应用程序。它带有全面的 [VPS][7] 监控能力(比如 CPU、内存、进程、文件系统)和邮件通知功能。
|
||||
|
||||
如果你想要接收 VPS 上由 Monit 产生的任何事件的邮件通知,你可以在 Monit 配置文件中添加以下 SMTP 信息。
|
||||
|
||||
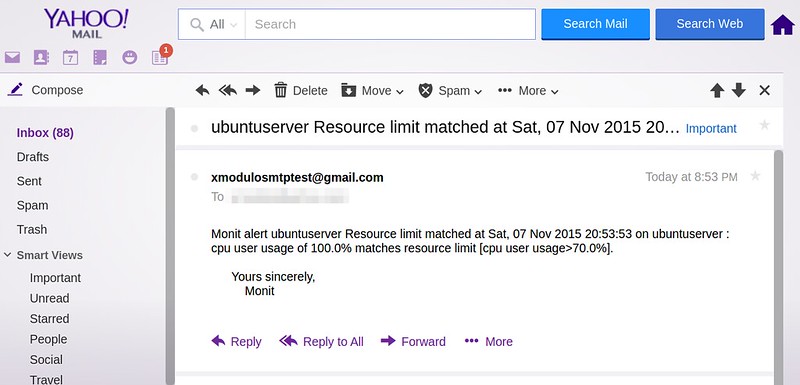
set mailserver smtp.gmail.com port 587
|
||||
username "<your-gmail-ID>" password "<gmail-password>"
|
||||
using tlsv12
|
||||
|
||||
set mail-format {
|
||||
from: <your-gmail-ID>@gmail.com
|
||||
subject: $SERVICE $EVENT at $DATE on $HOST
|
||||
message: Monit $ACTION $SERVICE $EVENT at $DATE on $HOST : $DESCRIPTION.
|
||||
|
||||
Yours sincerely,
|
||||
Monit
|
||||
}
|
||||
|
||||
# the person who will receive notification emails
|
||||
set alert alice@yahoo.com
|
||||
|
||||
这是一个因为 CPU 负载超载而由 Monit 发送的邮件通知的例子。
|
||||
|
||||
|
||||
|
||||
### 总结 ###
|
||||
|
||||
如你所见,类似 Gmail 这样免费的 SMTP 服务器有着这么多不同的运用方式 。但再次重申,请牢记免费的 SMTP 服务器不适用于商业用途,仅仅适用于个人项目。无论你正在哪款应用中使用 Gmail SMTP 服务器,欢迎自由分享你的用例。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/send-email-notifications-gmail-smtp-server-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[cposture](https://github.com/cposture)
|
||||
校对:[martin2011qi](https://github.com/martin2011qi), [wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/setup-system-status-page.html
|
||||
[2]:http://xmodulo.com/server-monitoring-system-monit.html
|
||||
[3]:http://xmodulo.com/create-software-raid1-array-mdadm-linux.html
|
||||
[4]:http://xmodulo.com/mail-server-ubuntu-debian.html
|
||||
[5]:http://xmodulo.com/go/digitalocean
|
||||
[6]:http://xmodulo.com/server-monitoring-system-monit.html
|
||||
[7]:http://xmodulo.com/go/digitalocean
|
||||
@ -0,0 +1,90 @@
|
||||
2016:如何选择 Linux 桌面环境
|
||||
=============================================
|
||||
|
||||
|
||||
|
||||
Linux 创建了一个友好的环境,为我们提供了选择的可能。比方说,现代大多数的 Linux 发行版都提供不同桌面环境给我们来选择。在本文中,我将挑选一些你可能会在 Linux 中见到的最棒的桌面环境来介绍。
|
||||
|
||||
## Plasma
|
||||
|
||||
我认为,[KDE 的 Plasma 桌面](https://www.kde.org/workspaces/plasmadesktop/) 是最先进的桌面环境 (LCTT 译注:译者认为,没有什么是最好的,只有最合适的,毕竟每个人的喜好都不可能完全相同)。它是我见过功能最完善和定制性最高的桌面环境;在用户完全自主控制方面,即使是 Mac OS X 和 Windows 也无法与之比拟。
|
||||
|
||||
我爱 Plasma,因为它自带了一个非常好的文件管理器 —— Dolphin。而相对应 Gnome 环境,我更喜欢 Plasma 的原因就在于这个文件管理器。使用 Gnome 最大的痛苦就是,它的文件管理器——Files——使我无法完成一些基本任务,比如说,批量文件重命名操作。而这个操作对我来说相当重要,因为我喜欢拍摄,但 Gnome 却让我无法批量重命名这些图像文件。而使用 Dolphin 的话,这个操作就像在公园散步一样简单。
|
||||
|
||||
而且,你可以通过插件来增强 Plasma 的功能。Plasma 有大量的基础软件,如 Krita、Kdenlive、Calligra 办公套件、digiKam、Kwrite 以及由 KDE 社区开发维护的大量应用。
|
||||
|
||||
Plasma 桌面环境唯一的缺陷就是它默认的邮件客户端——Kmail。它的设置比较困难,我希望 Kmail 设置可以配置地址簿和日历。
|
||||
|
||||
包括 openSUSE 在内的多数主流发行版多使用 Plasma 作为默认桌面。
|
||||
|
||||
## GNOME
|
||||
|
||||
[GNOME](https://www.gnome.org/) (GNU Network Object Model Environment,GNU 网络对象模型环境) 由 [Miguel de Icaza](https://en.wikipedia.org/wiki/Miguel_de_Icaza) 和 Federico Mena 在 1997 年的时候创立,这是因为 KDE 使用了 Qt 工具包,而这个工具包是使用专属许可证 (proprietary license) 发布的。不像提供了大量定制的 KDE,GNOME 专注于让事情变得简单。因为其自身的简单性和易用性,GNOME 变得相当流行。而我认为 GNOME 之所以流行的原因在于,Ubuntu——使用 GNOME 作为默认桌面的主流 Linux 发行版之一——对其有着巨大的推动作用。
|
||||
|
||||
随着时代变化,GNOME 也需要作出相应的改变了。因此,开发者在 GNOME 3 中推出了 GNOME 3 Shell,从而引出了它的全新设计规范。但这同时与 Canonical 的 Ubuntu 计划存在者一些冲突,所以 Canonical 为 GNOME 开发了叫做 Unity 的自己的 Shell。最初,GNOME 3 Shell 因很多争议 (issues) 而困扰不已——最明显的是,升级之后会导致很多扩展无法正常工作。由于设计上的重大改版以及各种问题的出现,GNOME 便产生了很多分支(fork),比如 Cinnamon 和 Mate 桌面。
|
||||
|
||||
另外,使得 GNOME 让人感兴趣的是,它针对触摸设备做了优化,所以,如果你有一台触屏笔记本电脑的话,GNOME 则是最合适你这台电脑的桌面环境。
|
||||
|
||||
在 3.18 版本中,GNOME 已经作出了一些令人印象深刻的改动。其中他们所做的最让人感兴趣的是集成了 Google Drive,用户可以把他们的 Google Drive 挂载为远程存储设备,这样就不必再使用浏览器来查看里边的文件了。我也很喜欢 GNOME 里边自带的那个优秀的邮件客户端,它带有日历和地址簿功能。尽管有这么多些优秀的特性,但它的文件管理器使我不再使用 GNOME ,因为我无法处理批量文件重命名。我会坚持使用 Plasma,一直到 GNOME 的开发者修复了这个小缺陷。
|
||||
|
||||

|
||||
|
||||
## Unity
|
||||
|
||||
从技术上来说,[Unity](https://unity.ubuntu.com/) 并不是一个桌面环境,它只是 Canonical 为 Ubuntu 开发的一个图形化 Shell。Unity 运行于 GNOME 桌面之上,并使用很多 GNOME 的应用和工具。Ubuntu 团队分支了一些 GNOME 组件,以便更好的满足 Unity 用户的需求。
|
||||
|
||||
Unity 在 Ubuntu 的融合(convergence)计划中扮演着重要角色, 在 Unity 8 中,Canonical 公司正在努力将电脑桌面和移动世界结合到一起。Canonical 同时还为 Unity 开发了许多的有趣技术,比如 HUD (Head-up Display,平视显示)。他们还在 lenses 和 scopes 中通过一种独特的技术来让用户方便地找到特定内容。
|
||||
|
||||
即将发行的 Ubuntu 16.04,将会搭载 Unity 8,那时候用户就可以完全体验开发者为该开源软件添加的所有特性了。其中最大的争议之一,Unity 可选取消集成了 Amazon Ads 和其他服务。而在即将发行的版本,Canonical 从 Dash 移除了 Amazon ads,但却默认保证了系统的隐私性。
|
||||
|
||||
## Cinnamon
|
||||
|
||||
最初,[Cinnamon](https://en.wikipedia.org/wiki/Cinnamon_(software\)) 由 [Linux Mint](http://www.linuxmint.com/) 开发 —— 这是 DistroWatch.com 上统计出来最流行的发行版。就像 Unity,Cinnamon 是 GNOME Shell 的一个分支。但最后进化为一个独立的桌面环境,这是因为 Linux Mint 的开发者分支了 GNOME 桌面中很多的组件到 Cinnamon,包括 Files ——以满足自身用户的需求。
|
||||
|
||||
由于 Linux Mint 基于普通版本的 Ubuntu,开发者仍需要去完成 Ubuntu 尚未完成的目标。结果,尽管前途光明,但 Cinnamon 却充满了 Bugs 和问题。随着 17.x 本版的发布,Linux Mint 开始转移到 Ubuntu 的 LTS 版本上,从而他们可以专注于开发 Cinnamon 的核心组件,而不必再去担心代码库。转移到 LTS 的好处是,Cinnamon 变得非常稳定并且基本没有 Bugs 出现。现在,开发者已经开始向桌面环境中添加更多的新特性了。
|
||||
|
||||
对于那些更喜欢在 GNOME 基础上有一个很好的类 Windows 用户界面的用户来说,Cinnamon 是他们最好的桌面环境。
|
||||
|
||||
## MATE 桌面
|
||||
|
||||
[MATE 桌面](http://mate-desktop.com/) 同样是 GNOME 的一个分支,然而,它并不像 Cinnamon 那样由 GNOME 3 分支而来,而是现在已经没有人维护的 GNOME 2 代码库的一个分支。MATE 桌面中的一些开发者并不喜欢 GNOME 3 并且想要“继续坚持” GNOME 2,所以他们使用这个代码库来创建来 MATE。为避免和 GNOME 3 的冲突,他们重命名了全部的包:Nautilus 改为 Caja、Gedit 改为 Pluma 以及 Evince 改为 Atril 等。
|
||||
|
||||
尽管 MATE 延续了 GNOME 2,但这并不意味着他们使用过时的技术;相反,他们使用了更新的技术来提供一个现代的 GNOME 2 体验。
|
||||
|
||||
拥有相当高的资源使用率才是 MATE 最令人印象深刻之处。你可将它运行在老旧硬件或者更新一些的但不太强大的硬件上,如树梅派 (Raspberry Pi) 或者 Chromebook Flip。使得它更有让人感兴趣的是,把它运行在一些强大的硬件上,可以节省大多数的资源给其他应用,而桌面环境本身只占用很少的资源。
|
||||
|
||||
## LXQt
|
||||
|
||||
[LXQt](http://lxqt.org/) 继承了 LXDE ——最轻量级的桌面环境之一。它融合了 LXDE 和 Razor-Qt 两个开源项目。LXQt 的首个可用本版(v 0.9)发布于 2015 年。最初,开发者使用了 Qt4 ,之后为了加快开发速度,而放弃了兼容性,他们移动到 Qt5 和 KDE 框架上。我也在自己的 Arch 系统上尝试使用了 LXQt,它的确是一个非常好的轻量级桌面环境。但在完全接过 LXDE 的传承之前,LXQt 仍有一段很长的路需要走。
|
||||
|
||||
## Xfce
|
||||
|
||||
[Xfce](http://www.xfce.org/) 早于 KDE 桌面环境,它是最古老和最轻量级的桌面环境。Xfce 的最新版本是 4.15,发布于 2015 年,使用了诸如 GTK+ 3 的大量的现代科技。很多发行版都使用了 Xfce 环境以满足特定需求,比如 Ubuntu Studio ——与 MATE 类似——尽量节省系统资源给其他的应用。并且,许多的著名的 Linux 发行版——包括 Manjaro Linux、PC/OS、Salix 和 Mythbuntu ——都把它作为默认桌面环境。
|
||||
|
||||
## Budgie
|
||||
|
||||
[Budgie](https://solus-project.com/budgie/) 是一个新型的桌面环境,由 Solus Linux 团队开发和维护。Solus 是一个从零开始构建的新型发行版,而 Budgie 则是它的一个核心组件。Budgie 使用了大量的 GNOME 组件,从而提供一个华丽的用户界面。由于没有该桌面环境的更多信息,我特地联系了 Solus 的核心开发者—— Ikey Doherty。他解释说:“我们搭载了自己的桌面环境—— Budgie 桌面。与其他桌面环境不同的是,Budgie 并不是其他桌面的一个分支,它的目标是彻底融入到 GNOME 协议栈之中。它完全从零开始编写,并特意设计来迎合 Solus 提供的体验。我们会尽可能的和 GNOME 的上游团队协同工作,修复 Bugs,并提倡和支持他们的工作”。
|
||||
|
||||
## Pantheon
|
||||
|
||||
我想,[Pantheon](https://elementary.io/) 不需要特别介绍了吧,那个优美的 elementary OS 就使用它作为桌面。类似于 Budgie,很多人都认为 Pantheon 也不是 GNOME 的一个分支。elementary OS 团队大多拥有良好的设计从业背景,所以他们会近距离关注每一个细节,这使得 Pantheon 成为一个非常优美的桌面环境。偶尔,它可能缺少像 Plasma 等桌面中的某些特性,但开发者实际上是尽其所能的去坚持设计原则。
|
||||
|
||||

|
||||
|
||||
## 结论
|
||||
|
||||
当我写完本文后,我突然意识到来开源和 Linux 的重大好处。总有一些东西适合你。就像 Jon “maddog” Hall 在最近的 SCaLE 14 上说的那样:“是的,现在有 300 多个 Linux 发行版。我可以一个一个去尝试,然后坚持使用我最喜欢的那一个”。
|
||||
|
||||
所以,尽情享受 Linux 的多样性吧,最后使用最合你意的那一个。
|
||||
|
||||
------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.com/news/software/applications/881107-best-linux-desktop-environments-for-2016
|
||||
|
||||
作者:[Swapnil Bhartiya][a]
|
||||
译者:[GHLandy](https://github.com/GHLandy)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linux.com/community/forums/person/61003
|
||||
@ -0,0 +1,24 @@
|
||||
Ubuntu 16.04 为更好支持容器化而采用 ZFS
|
||||
=======================================================
|
||||
|
||||

|
||||
|
||||
Ubuntu 开发者正在为 [Ubuntu 16.04 加上 ZFS 支持](http://www.phoronix.com/scan.php?page=news_item&px=ZFS-For-Ubuntu-16.04) ,并且对该文件系统的所有支持都已经准备就绪。
|
||||
|
||||
Ubuntu 16.04 的默认安装将会继续是 ext4,但是 ZFS 支持将会自动构建进 Ubuntu 发布中,模块将在需要时自动加载,zfsutils-linux 将放到 Ubuntu 主分支内,并且通过 Canonical 对商业客户提供支持。
|
||||
|
||||
对于那些对 Ubuntu 中的 ZFS 感兴趣的人,Canonical 的 Dustin Kirkland 已经写了[一篇新的博客](http://blog.dustinkirkland.com/2016/02/zfs-is-fs-for-containers-in-ubuntu-1604.html),介绍了一些细节及为何“ZFS 是 Ubuntu 16.04 中面向容器使用的文件系统!”
|
||||
|
||||
------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.phoronix.com/scan.php?page=news_item&px=Ubuntu-ZFS-Continues-16.04&utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+Phoronix+%28Phoronix%29
|
||||
|
||||
作者:[Michael Larabel][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.michaellarabel.com/
|
||||
|
||||
|
||||
@ -1,9 +1,11 @@
|
||||
Xubuntu 16.04 Beta 1 开发发布
|
||||
Xubuntu 16.04 Beta 1 开发者版本发布
|
||||
============================================
|
||||
|
||||
Ubuntu 发布组宣布为选定的社区版本而准备的最新的 beta 测试镜像已经可以使用了。新的发布版名称是 16.04 beta 1 ,这个版本只推荐给测试人员测试用,并不适合普通人进行日常使用。
|
||||
Ubuntu 发布团队宣布为选定的社区版本而准备的最新的 beta 测试镜像已经可以使用了。新的发布版本名称是 16.04 beta 1 ,这个版本只推荐给测试人员测试用,并不适合普通人进行日常使用。
|
||||
|
||||
“这个 beta 特性的镜像主要是为 [Lubuntu][1], Ubuntu Cloud, [Ubuntu GNOME][2], [Ubuntu MATE][3], [Ubuntu Kylin][4], [Ubuntu Studio][5] 和 [Xubuntu][6] 这几个发布版准备的。Xenial Xerus (LCTT 注: ubuntu 16.04 的开发代号) 的这个预发布版本并不推荐那些需要稳定版本的人员使用,同时那些不希望在系统运行中偶尔或频繁的出现 bug 的人也不建议使用这个版本。这个版本主要还是推荐给那些喜欢 ubuntu 的开发人员,以及那些想协助我们测试、报告 bug 和修改 bug 的人使用,和我们一起努力让这个发布版本早日准备就绪。” 更多的信息可以从 [发布日志][7] 获取。
|
||||
|
||||
|
||||
“这个 beta 特性的镜像主要是为 [Lubuntu][1], Ubuntu Cloud, [Ubuntu GNOME][2], [Ubuntu MATE][3], [Ubuntu Kylin][4], [Ubuntu Studio][5] 和 [Xubuntu][6] 这几个发布版准备的。Xenial Xerus (LCTT 译注: ubuntu 16.04 的开发代号)的这个预发布版本并不推荐那些需要稳定版本的人员使用,同时那些不希望在系统运行中偶尔或频繁的出现 bug 的人也不建议使用这个版本。这个版本主要还是推荐给那些喜欢 ubuntu 的开发人员,以及那些想协助我们测试、报告 bug 和修改 bug 的人使用,和我们一起努力让这个发布版本早日准备就绪。” 更多的信息可以从 [发布日志][7] 获取。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -0,0 +1,30 @@
|
||||
OpenSSH 7.2发布,支持 SHA-256/512 的 RSA 签名
|
||||
========================================================
|
||||
|
||||
**2016.2.29,OpenBSD 项目很高兴地宣布 OpenSSH 7.2发布了,并且很块可在所有支持的平台下载。**
|
||||
|
||||
根据内部[发布公告][1],OpenSSH 7.2 主要是 bug 修复,修改了自 OpenSSH 7.1p2 以来由用户报告和开发团队发现的问题,但是我们可以看到几个新功能。
|
||||
|
||||
这其中,我们可以提到使用了 SHA-256 或者 SHA-256 512 哈希算法的 RSA 签名;增加了一个 AddKeysToAgent 客户端选项,以添加用于身份验证的 ssh-agent 的私钥;和实现了一个“restrict”级别的 authorized_keys 选项,用于存储密钥限制。
|
||||
|
||||
此外,现在 ssh_config 中 CertificateFile 选项可以明确列出证书,ssh-keygen 现在能够改变所有支持的格式的密钥注释、密钥指纹现在可以来自标准输入,多个公钥可以放到一个文件。
|
||||
|
||||
### ssh-keygen 现在支持多证书
|
||||
|
||||
除了上面提到的,OpenSSH 7.2 增加了 ssh-keygen 多证书的支持,一个一行,实现了 sshd_config ChrootDirectory 及Foreground 的“none”参数,“-c”标志允许 ssh-keyscan 获取证书而不是文本密钥。
|
||||
|
||||
最后但并非最不重要的,OpenSSH 7.3 不再默认启用 rijndael-cbc(即 AES),blowfish-cbc、cast128-cbc 等古老的算法,同样的还有基于 MD5 和截断的 HMAC 算法。在 Linux 中支持 getrandom() 系统调用。[下载 OpenSSH 7.2][2] 并查看更新日志中的更多细节。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/openssh-7-2-out-now-with-support-for-rsa-signatures-using-sha-256-512-algorithms-501111.shtml
|
||||
|
||||
作者:[Marius Nestor][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: http://news.softpedia.com/editors/browse/marius-nestor
|
||||
[1]: http://www.openssh.com/txt/release-7.2
|
||||
[2]: http://linux.softpedia.com/get/Security/OpenSSH-4474.shtml
|
||||
@ -0,0 +1,25 @@
|
||||
逾千万使用 https 的站点受到新型解密攻击的威胁
|
||||
===========================================================================
|
||||
|
||||
|
||||
|
||||
|
||||
低成本的 DROWN 攻击能在数小时内完成数据解密,该攻击对采用了 TLS 的邮件服务器也同样奏效。
|
||||
|
||||
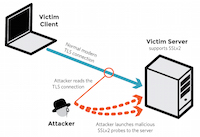
一个国际研究小组于周二发出警告,据称逾 1100 万家网站和邮件服务采用的用以保证服务安全的 [传输层安全协议 TLS][1],对于一种新发现的、成本低廉的攻击而言异常脆弱,这种攻击会在几个小时内解密敏感的通信,在某些情况下解密甚至能瞬间完成。 前一百万家最大的网站中有超过 81,000 个站点正处于这种脆弱的 HTTPS 协议保护之下。
|
||||
|
||||
这种攻击主要针对依赖于 [RSA 加密系统][2]的 TLS 所保护的通信,密钥会间接的通过 SSLv2 暴露,这是一种在 20 年前就因为自身缺陷而退休了的 TLS 前代协议。该漏洞允许攻击者可以通过反复使用 SSLv2 创建与服务器连接的方式,解密截获的 TLS 连接。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/news/software/applications/889455--more-than-11-million-https-websites-imperiled-by-new-decryption-attack
|
||||
|
||||
作者:[ArsTechnica][a]
|
||||
译者:[Ezio](https://github.com/oska874)
|
||||
校对:[martin2011qi](https://github.com/martin2011qi), [wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/community/forums/person/112
|
||||
[1]: https://en.wikipedia.org/wiki/Transport_Layer_Security
|
||||
[2]: https://en.wikipedia.org/wiki/RSA_(cryptosystem)
|
||||
@ -1,32 +0,0 @@
|
||||
OpenSSH 7.2 Out Now with Support for RSA Signatures Using SHA-256/512 Algorithms
|
||||
========================================================
|
||||
|
||||
**Today, February 29, 2016, the OpenBSD project had the great pleasure of announcing the release and immediate availability for download of OpenSSH 7.2 for all supported platforms.**
|
||||
|
||||
According to the internal [release notes][1], also attached at the end of the article for reference, OpenSSH 7.2 is primarily a bugfix release, fixing most of the issues reported by users or discovered by the development team since the release of OpenSSH 7.1p2, but we can see several new features as well.
|
||||
|
||||
Among these, we can mention support for RSA signatures using SHA-256 or SHA-256 512 hash algorithms, the addition of an AddKeysToAgent client option to add private keys used for authentication to the ssh-agent, and the implementation of the "restrict" authorized_keys option for storing key restrictions.
|
||||
|
||||
Furthermore, there's now an ssh_config CertificateFile option for explicitly listing certificates, the ssh-keygen is now capable of changing the key comment for all supported formats, fingerprinting is now allowed from standard input and for multiple public keys in a file.
|
||||
|
||||
### ssh-keygen now supports multiple certificates
|
||||
|
||||
In addition to the changes mentioned above, OpenSSH 7.2 adds support for multiple certificates to ssh-keygen, one per line, implements the "none" argument for sshd_config ChrootDirectory and Foreground, and the "-c" flag allows ssh-keyscan to fetch certificates instead of plain keys.
|
||||
|
||||
Last but not least, OpenSSH 7.2 no longer enables by default all flavors of the rijndael-cbc aliases for AES, blowfish-cbc, and cast128-cbc legacy ciphers, as well as MD5-based and truncated HMAC algorithms. The getrandom() syscall is now supported under Linux. [Download OpenSSH 7.2][2] and check the changelog below for some additional details about exactly what has been fixed in this major release.
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/openssh-7-2-out-now-with-support-for-rsa-signatures-using-sha-256-512-algorithms-501111.shtml
|
||||
|
||||
作者:[Marius Nestor][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: http://news.softpedia.com/editors/browse/marius-nestor
|
||||
[1]: http://www.openssh.com/txt/release-7.2
|
||||
[2]: http://linux.softpedia.com/get/Security/OpenSSH-4474.shtml
|
||||
@ -1,165 +0,0 @@
|
||||
robot527 translating
|
||||
|
||||
|
||||
Bossie Awards 2015: The best open source networking and security software
|
||||
================================================================================
|
||||
InfoWorld's top picks of the year among open source tools for building, operating, and securing networks
|
||||
|
||||

|
||||
|
||||
### The best open source networking and security software ###
|
||||
|
||||
BIND, Sendmail, OpenSSH, Cacti, Nagios, Snort -- open source software seems to have been invented for networks, and many of the oldies and goodies are still going strong. Among our top picks in the category this year, you'll find a mix of stalwarts, mainstays, newcomers, and upstarts perfecting the arts of network management, security monitoring, vulnerability assessment, rootkit detection, and much more.
|
||||
|
||||

|
||||
|
||||
### Icinga 2 ###
|
||||
|
||||
Icinga began life as a fork of system monitoring application Nagios. [Icinga 2][1] was completely rewritten to give users a modern interface, support for multiple databases, and an API to integrate numerous extensions. With out-of-the-box load balancing, notifications, and configuration, Icinga 2 shortens the time to installation for complex environments. Icinga 2 supports Graphite natively, giving administrators real-time performance graphing without any fuss. But what puts Icinga back on the radar this year is its release of Icinga Web 2, a graphical front end with drag-and-drop customizable dashboards and streamlined monitoring tools.
|
||||
|
||||
Administrators can view, filter, and prioritize problems, while keeping track of which actions have already been taken. A new matrix view lets administrators view hosts and services on one page. You can view events over a particular time period or filter incidents to understand which ones need immediate attention. Icinga Web 2 may boast a new interface and zippier performance, but all the usual commands from Icinga Classic and Icinga Web are still available. That means there is no downtime trying to learn a new version of the tool.
|
||||
|
||||
-- Fahmida Rashid
|
||||
|
||||

|
||||
|
||||
### Zenoss Core ###
|
||||
|
||||
Another open source stalwart, [Zenoss Core][2] gives network administrators a complete, one-stop solution for tracking and managing all of the applications, servers, storage, networking components, virtualization tools, and other elements of an enterprise infrastructure. Administrators can make sure the hardware is running efficiently and take advantage of the modular design to plug in ZenPacks for extended functionality.
|
||||
|
||||
Zenoss Core 5, released in February of this year, takes the already powerful tool and improves it further, with an enhanced user interface and expanded dashboard. The Web-based console and dashboards were already highly customizable and dynamic, and the new version now lets administrators mash up multiple component charts onto a single chart. Think of it as the tool for better root cause and cause/effect analysis.
|
||||
|
||||
Portlets give additional insights for network mapping, device issues, daemon processes, production states, watch lists, and event views, to name a few. And new HTML5 charts can be exported outside the tool. The Zenoss Control Center allows out-of-band management and monitoring of all Zenoss components. Zenoss Core has new tools for online backup and restore, snapshots and rollbacks, and multihost deployment. Even more important, deployments are faster with full Docker support.
|
||||
|
||||
-- Fahmida Rashid
|
||||
|
||||

|
||||
|
||||
### OpenNMS ###
|
||||
|
||||
An extremely flexible network management solution, [OpenNMS][3] can handle any network management task, whether it's device management, application performance monitoring, inventory control, or events management. With IPv6 support, a robust alerts system, and the ability to record user scripts to test Web applications, OpenNMS has everything network administrators and testers need. OpenNMS has become, as now a mobile dashboard, called OpenNMS Compass, lets networking pros keep an eye on their network even when they're out and about.
|
||||
|
||||
The iOS version of the app, which is available on the [iTunes App Store][4], displays outages, nodes, and alarms. The next version will offer additional event details, resource graphs, and information about IP and SNMP interfaces. The Android version, available on [Google Play][5], displays network availability, outages, and alarms on the dashboard, as well as the ability to acknowledge, escalate, or clear alarms. The mobile clients are compatible with OpenNMS Horizon 1.12 or greater and OpenNMS Meridian 2015.1.0 or greater.
|
||||
|
||||
-- Fahmida Rashid
|
||||
|
||||

|
||||
|
||||
### Security Onion ###
|
||||
|
||||
Like an onion, network security monitoring is made of many layers. No single tool will give you visibility into every attack or show you every reconnaissance or foot-printing session on your company network. [Security Onion][6] bundles scores of proven tools into one handy Ubuntu distro that will allow you to see who's inside your network and help keep the bad guys out.
|
||||
|
||||
Whether you're taking a proactive approach to network security monitoring or following up on a potential attack, Security Onion can assist. Consisting of sensor, server, and display layers, the Onion combines full network packet capture with network-based and host-based intrusion detection, and it serves up all of the various logs for inspection and analysis.
|
||||
|
||||
The star-studded network security toolchain includes Netsniff-NG for packet capture, Snort and Suricata for rules-based network intrusion detection, Bro for analysis-based network monitoring, OSSEC for host intrusion detection, and Sguil, Squert, Snorby, and ELSA (Enterprise Log Search and Archive) for display, analysis, and log management. It’s a carefully vetted collection of tools, all wrapped in a wizard-driven installer and backed by thorough documentation, that can help you get from zero to monitoring as fast as possible.
|
||||
|
||||
-- Victor R. Garza
|
||||
|
||||

|
||||
|
||||
Kali Linux
|
||||
|
||||
The team behind [Kali Linux][7] revamped the popular security Linux distribution this year to make it faster and even more versatile. Kali sports a new 4.0 kernel, improved hardware and wireless driver support, and a snappier interface. The most popular tools are easily accessible from a dock on the side of the screen. The biggest change? Kali Linux is now a rolling distribution, with a continuous stream of software updates. Kali's core system is based on Debian Jessie, and the team will pull packages continuously from Debian Testing, while continuing to add new Kali-flavored features on top.
|
||||
|
||||
The distribution still comes jam-packed with tools for penetration testing, vulnerability analysis, security forensics, Web application analysis, wireless networking and assessment, reverse engineering, and exploitation tools. Now the distribution has an upstream version checking system that will automatically notify users when updates are available for the individual tools. The distribution also features ARM images for a range of devices, including Raspberry Pi, Chromebook, and Odroids, as well as updates to the NetHunter penetration testing platform that runs on Android devices. There are other changes too: Metasploit Community/Pro is no longer included, because Kali 2.0 is not yet [officially supported by Rapid7][8].
|
||||
|
||||
-- Fahmida Rashid
|
||||
|
||||

|
||||
|
||||
### OpenVAS ###
|
||||
|
||||
[OpenVAS][9], the Open Vulnerability Assessment System, is a framework that combines multiple services and tools to offer vulnerability scanning and vulnerability management. The scanner is coupled with a weekly feed of network vulnerability tests, or you can use a feed from a commercial service. The framework includes a command-line interface (so it can be scripted) and an SSL-secured, browser-based interface via the [Greenbone Security Assistant][10]. OpenVAS accommodates various plug-ins for additional functionality. Scans can be scheduled or run on-demand.
|
||||
|
||||
Multiple OpenVAS installations can be controlled through a single master, which makes this a scalable vulnerability assessment tool for enterprises. The project is as compatible with standards as can be: Scan results and configurations are stored in a SQL database, where they can be accessed easily by external reporting tools. Client tools access the OpenVAS Manager via the XML-based stateless OpenVAS Management Protocol, so security administrators can extend the functionality of the framework. The software can be installed from packages or source code to run on Windows or Linux, or downloaded as a virtual appliance.
|
||||
|
||||
-- Matt Sarrel
|
||||
|
||||

|
||||
|
||||
### OWASP ###
|
||||
|
||||
[OWASP][11], the Open Web Application Security Project, is a nonprofit organization with worldwide chapters focused on improving software security. The community-driven organization provides test tools, documentation, training, and almost anything you could imagine that’s related to assessing software security and best practices for developing secure software. Several OWASP projects have become valuable components of many a security practitioner's toolkit:
|
||||
|
||||
[ZAP][12], the Zed Attack Proxy Project, is a penetration test tool for finding vulnerabilities in Web applications. One of the design goals of ZAP was to make it easy to use so that developers and functional testers who aren't security experts can benefit from using it. ZAP provides automated scanners and a set of manual test tools.
|
||||
|
||||
The [Xenotix XSS Exploit Framework][13] is an advanced cross-site scripting vulnerability detection and exploitation framework that runs scans within browser engines to get real-world results. The Xenotix Scanner Module uses three intelligent fuzzers, and it can run through nearly 5,000 distinct XSS payloads. An API lets security administrators extend and customize the exploit toolkit.
|
||||
|
||||
[O-Saft][14], or the OWASP SSL advanced forensic tool, is an SSL auditing tool that shows detailed information about SSL certificates and tests SSL connections. This command-line tool can run online or offline to assess SSL security such as ciphers and configurations. O-Saft provides built-in checks for common vulnerabilities, and you can easily extend these through scripting. In May 2015 a simple GUI was added as an optional download.
|
||||
|
||||
[OWTF][15], the Offensive Web Testing Framework, is an automated test tool that follows OWASP testing guidelines and the NIST and PTES standards. The framework uses both a Web UI and a CLI, and it probes Web and application servers for common vulnerabilities such as improper configuration and unpatched software.
|
||||
|
||||
-- Matt Sarrel
|
||||
|
||||

|
||||
|
||||
### BeEF ###
|
||||
|
||||
The Web browser has become the most common vector for attacks against clients. [BeEF][15], the Browser Exploitation Framework Project, is a widely used penetration tool to assess Web browser security. BeEF helps you expose the security weaknesses of client systems using client-side attacks launched through the browser. BeEF sets up a malicious website, which security administrators visit from the browser they want to test. BeEF then sends commands to attack the Web browser and use it to plant software on the client machine. Administrators can then launch attacks on the client machine as if they were zombies.
|
||||
|
||||
BeEF comes with commonly used modules like a key logger, a port scanner, and a Web proxy, plus you can write your own modules or send commands directly to the zombified test machine. BeEF comes with a handful of demo Web pages to help you get started and makes it very easy to write additional Web pages and attack modules so you can customize testing to your environment. BeEF is a valuable test tool for assessing browser and endpoint security and for learning how browser-based attacks are launched. Use it to put together a demo to show your users how malware typically infects client devices.
|
||||
|
||||
-- Matt Sarrel
|
||||
|
||||

|
||||
|
||||
### Unhide ###
|
||||
|
||||
[Unhide][16] is a forensic tool that locates open TCP/UDP ports and hidden process on UNIX, Linux, and Windows. Hidden ports and processes can be the result of rootkit or LKM (loadable kernel module) activity. Rootkits can be difficult to find and remove because they are designed to be stealthy, hiding themselves from the OS and user. A rootkit can use LKMs to hide its processes or impersonate other processes, allowing it to run on machines undiscovered for a long time. Unhide can provide the assurance that administrators need to know their systems are clean.
|
||||
|
||||
Unhide is really two separate scripts: one for processes and one for ports. The tool interrogates running processes, threads, and open ports and compares this info to what's registered with the system as active, reporting discrepancies. Unhide and WinUnhide are extremely lightweight scripts that run from the command line to produce text output. They're not pretty, but they are extremely useful. Unhide is also included in the [Rootkit Hunter][17] project.
|
||||
|
||||
-- Matt Sarrel
|
||||
|
||||

|
||||
|
||||
Read about more open source winners
|
||||
|
||||
InfoWorld's Best of Open Source Awards for 2014 celebrate more than 100 open source projects, from the bottom of the stack to the top. Follow these links to more open source winners:
|
||||
|
||||
[Bossie Awards 2015: The best open source applications][18]
|
||||
|
||||
[Bossie Awards 2015: The best open source application development tools][19]
|
||||
|
||||
[Bossie Awards 2015: The best open source big data tools][20]
|
||||
|
||||
[Bossie Awards 2015: The best open source data center and cloud software][21]
|
||||
|
||||
[Bossie Awards 2015: The best open source desktop and mobile software][22]
|
||||
|
||||
[Bossie Awards 2015: The best open source networking and security software][23]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.infoworld.com/article/2982962/open-source-tools/bossie-awards-2015-the-best-open-source-networking-and-security-software.html
|
||||
|
||||
作者:[InfoWorld staff][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.infoworld.com/author/InfoWorld-staff/
|
||||
[1]:https://www.icinga.org/icinga/icinga-2/
|
||||
[2]:http://www.zenoss.com/
|
||||
[3]:http://www.opennms.org/
|
||||
[4]:https://itunes.apple.com/us/app/opennms-compass/id968875097?mt=8
|
||||
[5]:https://play.google.com/store/apps/details?id=com.opennms.compass&hl=en
|
||||
[6]:http://blog.securityonion.net/p/securityonion.html
|
||||
[7]:https://www.kali.org/
|
||||
[8]:https://community.rapid7.com/community/metasploit/blog/2015/08/12/metasploit-on-kali-linux-20
|
||||
[9]:http://www.openvas.org/
|
||||
[10]:http://www.greenbone.net/
|
||||
[11]:https://www.owasp.org/index.php/Main_Page
|
||||
[12]:https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project
|
||||
[13]:https://www.owasp.org/index.php/O-Saft
|
||||
[14]:https://www.owasp.org/index.php/OWASP_OWTF
|
||||
[15]:http://www.beefproject.com/
|
||||
[16]:http://www.unhide-forensics.info/
|
||||
[17]:http://www.rootkit.nl/projects/rootkit_hunter.html
|
||||
[18]:http://www.infoworld.com/article/2982622/bossie-awards-2015-the-best-open-source-applications.html
|
||||
[19]:http://www.infoworld.com/article/2982920/bossie-awards-2015-the-best-open-source-application-development-tools.html
|
||||
[20]:http://www.infoworld.com/article/2982429/bossie-awards-2015-the-best-open-source-big-data-tools.html
|
||||
[21]:http://www.infoworld.com/article/2982923/bossie-awards-2015-the-best-open-source-data-center-and-cloud-software.html
|
||||
[22]:http://www.infoworld.com/article/2982630/bossie-awards-2015-the-best-open-source-desktop-and-mobile-software.html
|
||||
[23]:http://www.infoworld.com/article/2982962/bossie-awards-2015-the-best-open-source-networking-and-security-software.html
|
||||
@ -1,98 +0,0 @@
|
||||
FSSlc translating
|
||||
|
||||
5 great Raspberry Pi projects for the classroom
|
||||
================================================================================
|
||||

|
||||
|
||||
Image by : opensource.com
|
||||
|
||||
### 1. Minecraft Pi ###
|
||||
|
||||
Courtesy of the Raspberry Pi Foundation. [CC BY-SA 4.0.][1]
|
||||
|
||||
Minecraft is the favorite game of pretty much every teenager in the world—and it's one of the most creative games ever to capture the attention of young people. The version that comes with every Raspberry Pi is not only a creative thinking building game, but comes with a programming interface allowing for additional interaction with the Minecraft world through Python code.
|
||||
|
||||
Minecraft: Pi Edition is a great way for teachers to engage students with problem solving and writing code to perform tasks. You can use the Python API to build a house and have it follow you wherever you go, build a bridge wherever you walk, make it rain lava, show the temperature in the sky, and anything else your imagination can create.
|
||||
|
||||
Read more in "[Getting Started with Minecraft Pi][2]."
|
||||
|
||||
### 2. Reaction game and traffic lights ###
|
||||
|
||||

|
||||
|
||||
Courtesy of [Low Voltage Labs][3]. [CC BY-SA 4.0][1].
|
||||
|
||||
It's really easy to get started with physical computing on Raspberry Pi—just connect up LEDs and buttons to the GPIO pins, and with a few lines of code you can turn lights on and control things with button presses. Once you know the code to do the basics, it's down to your imagination as to what you do next!
|
||||
|
||||
If you know how to flash one light, you can flash three. Pick out three LEDs in traffic light colors and you can code the traffic light sequence. If you know how to use a button to a trigger an event, then you have a pedestrian crossing! Also look out for great pre-built traffic light add-ons like [PI-TRAFFIC][4], [PI-STOP][5], [Traffic HAT][6], and more.
|
||||
|
||||
It's not always about the code—this can be used as an exercise in understanding how real world systems are devised. Computational thinking is a useful skill in any walk of life.
|
||||
|
||||

|
||||
|
||||
Courtesy of the Raspberry Pi Foundation. [CC BY-SA 4.0][1].
|
||||
|
||||
Next, try wiring up two buttons and an LED and making a two-player reaction game—let the light come on after a random amount of time and see who can press the button first!
|
||||
|
||||
To learn more, check out "[GPIO Zero recipes][7]. Everything you need is in [CamJam EduKit 1][8].
|
||||
|
||||
### 3. Sense HAT Pixel Pet ###
|
||||
|
||||
The Astro Pi—an augmented Raspberry Pi—is going to space this December, but you haven't missed your chance to get your hands on the hardware. The Sense HAT is the sensor board add-on used in the Astro Pi mission and it's available for anyone to buy. You can use it for data collection, science experiments, games and more. Watch this Gurl Geek Diaries video from Raspberry Pi's Carrie Anne for a great way to get started—by bringing to life an animated pixel pet of your own design on the Sense HAT display:
|
||||
|
||||
注:youtube 视频
|
||||
<iframe width="520" height="315" frameborder="0" src="https://www.youtube.com/embed/gfRDFvEVz-w" allowfullscreen=""></iframe>
|
||||
|
||||
Learn more in "[Exploring the Sense HAT][9]."
|
||||
|
||||
### 4. Infrared bird box ###
|
||||
|
||||

|
||||
Courtesy of the Raspberry Pi Foundation. [CC BY-SA 4.0.][1]
|
||||
|
||||
A great exercise for the whole class to get involved with—place a Raspberry Pi and the NoIR camera module inside a bird box along with some infra-red lights so you can see in the dark, then stream video from the Pi over the network or on the internet. Wait for birds to nest and you can observe them without disturbing them in their habitat.
|
||||
|
||||
Learn all about infrared and the light spectrum, and how to adjust the camera focus and control the camera in software.
|
||||
|
||||
Learn more in "[Make an infrared bird box.][10]"
|
||||
|
||||
### 5. Robotics ###
|
||||
|
||||

|
||||
|
||||
Courtesy of Low Voltage Labs. [CC BY-SA 4.0][1].
|
||||
|
||||
With a Raspberry Pi and as little as a couple of motors and a motor controller board, you can build your own robot. There is a vast range of robots you can make, from basic buggies held together by sellotape and a homemade chassis, all the way to self-aware, sensor-laden metallic stallions with camera attachments driven by games controllers.
|
||||
|
||||
Learn how to control individual motors with something straightforward like the RTK Motor Controller Board (£8/$12), or dive into the new CamJam robotics kit (£17/$25) which comes with motors, wheels and a couple of sensors—great value and plenty of learning potential.
|
||||
|
||||
Alternatively, if you'd like something more hardcore, try PiBorg's [4Borg][11] (£99/$150) or [DiddyBorg][12] (£180/$273) or go the whole hog and treat yourself to their DoodleBorg Metal edition (£250/$380)—and build a mini version of their infamous [DoodleBorg tank][13] (unfortunately not for sale).
|
||||
|
||||
Check out the [CamJam robotics kit worksheets][14].
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/education/15/12/5-great-raspberry-pi-projects-classroom
|
||||
|
||||
作者:[Ben Nuttall][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/bennuttall
|
||||
[1]:https://creativecommons.org/licenses/by-sa/4.0/
|
||||
[2]:https://opensource.com/life/15/5/getting-started-minecraft-pi
|
||||
[3]:http://lowvoltagelabs.com/
|
||||
[4]:http://lowvoltagelabs.com/products/pi-traffic/
|
||||
[5]:http://4tronix.co.uk/store/index.php?rt=product/product&product_id=390
|
||||
[6]:https://ryanteck.uk/hats/1-traffichat-0635648607122.html
|
||||
[7]:http://pythonhosted.org/gpiozero/recipes/
|
||||
[8]:http://camjam.me/?page_id=236
|
||||
[9]:https://opensource.com/life/15/10/exploring-raspberry-pi-sense-hat
|
||||
[10]:https://www.raspberrypi.org/learning/infrared-bird-box/
|
||||
[11]:https://www.piborg.org/4borg
|
||||
[12]:https://www.piborg.org/diddyborg
|
||||
[13]:https://www.piborg.org/doodleborg
|
||||
[14]:http://camjam.me/?page_id=1035#worksheets
|
||||
@ -1,4 +1,3 @@
|
||||
chisper 翻译中
|
||||
How to Install Pure-FTPd with TLS on FreeBSD 10.2
|
||||
================================================================================
|
||||
FTP or File Transfer Protocol is application layer standard network protocol used to transfer file from the client to the server, after user logged in to the FTP server over the TCP-Network, such as internet. FTP has been round long time ago, much longer then P2P Program, or World Wide Web, and until this day it was a primary method for sharing file with other over the internet and it it remain very popular even today. FTP provide an secure transmission, that protect username, password and encrypt the content with SSL/TLS.
|
||||
|
||||
@ -1,3 +1,4 @@
|
||||
zpl1025
|
||||
A new Mindcraft moment?
|
||||
=======================
|
||||
|
||||
|
||||
@ -1,214 +0,0 @@
|
||||
[Translating] Haohong Wang
|
||||
How to Setup Lighttpd Web server on Ubuntu 15.04 / CentOS 7
|
||||
=================================================================================
|
||||
|
||||
Lighttpd is an open source web server which is secure, fast, compliant, and very flexible and is optimized for high-performance environments. It uses very low memory compared to other web servers , small CPU load and speed optimization making it popular among the server for its efficiency and speed. Its advanced feature-set (FastCGI, CGI, Auth, Output-Compression, URL-Rewriting and many more) makes lighttpd the perfect webserver-software for every server that suffers load problems.
|
||||
|
||||
Here are some simple easy setups on how we can setup Lighttpd web server on our machine running Ubuntu 15.04 or CentOS 7 linux distributions.
|
||||
|
||||
### Installing Lighttpd
|
||||
|
||||
#### Installing using Package Manager
|
||||
|
||||
Here, we'll install Lighttpd using package manager as its the easiest method to install it. So, we can simply run the following command under `sudo` mode in a terminal or console to install Lighttpd.
|
||||
|
||||
**CentOS 7**
|
||||
|
||||
As lighttpd is not available in the official repository of CentOS 7, we'll need to install epel additional repository to our system. To do so, we'll need to run the following `yum` command.
|
||||
|
||||
# yum install epel-release
|
||||
|
||||
Then, we'll gonna update our system and proceed towards the installation of lighttpd.
|
||||
|
||||
# yum update
|
||||
# yum install lighttpd
|
||||
|
||||

|
||||
|
||||
**Ubuntu 15.04**
|
||||
|
||||
Lighttpd is available on the official repository of Ubuntu 15.04 so, we'll simply update our local repository index and then go for the installation of lighttpd using `apt-get` command.
|
||||
|
||||
# apt-get update
|
||||
# apt-get install lighttpd
|
||||
|
||||

|
||||
|
||||
#### Installing from Source
|
||||
|
||||
If we wanna install lighttpd from the latest version of source code ie 1.4.39, we'll need to compile the source code and install it into our system. First of all, we'll need to install the dependencies required to compile it.
|
||||
|
||||
# cd /tmp/
|
||||
# wget http://download.lighttpd.net/lighttpd/releases-1.4.x/lighttpd-1.4.39.tar.gz
|
||||
|
||||
After its downloaded, we'll need to extract it the tarball by running the following.
|
||||
|
||||
# tar -zxvf lighttpd-1.4.39.tar.gz
|
||||
|
||||
Then, we'll compile it by running the following commands.
|
||||
|
||||
# cd lighttpd-1.4.39
|
||||
# ./configure
|
||||
# make
|
||||
|
||||
**Note:** In this tutorial, we are installing lighttpd with its standard configuration. If you wanna configure beyond the standard configuration and want to install more features like support for SSL, `mod_rewrite`, `mod_redirect` then you can configure.
|
||||
|
||||
Once, its compiled, we'll install it in our system.
|
||||
|
||||
# make install
|
||||
|
||||
### Configuring Lighttpd
|
||||
|
||||
If we need to configure our lighttpd web server further as our requirements, we can make changes to the default configuration file ie `/etc/lighttpd/lighttpd.conf` . As wee'll go with the default configuration here in this tutorial, we'll not gonna make changes to it. If we had made any changes and we wanna check for errors in the config file, we'll need to run the following command.
|
||||
|
||||
# lighttpd -t -f /etc/lighttpd/lighttpd.conf
|
||||
|
||||
#### On CentOS 7
|
||||
|
||||
If we are running CentOS 7, we'll need to create a new directory for our webroot defined in our lighttpd's default configuration ie `/src/www/htdocs/` .
|
||||
|
||||
# mkdir -p /srv/www/htdocs/
|
||||
|
||||
Then, we'll copy the default welcome page from `/var/www/lighttpd/` directory to the above created directory.
|
||||
|
||||
# cp -r /var/www/lighttpd/* /srv/www/htdocs/
|
||||
|
||||
### Starting and Enabling Services
|
||||
|
||||
Now, we'll gonna restart our database server by executing the following `systemctl` command.
|
||||
|
||||
# systemctl start lighttpd
|
||||
|
||||
Then, we'll enable it to start automatically in every system boot.
|
||||
|
||||
# systemctl enable lighttpd
|
||||
|
||||
### Allowing Firewall
|
||||
|
||||
To allow our webpages or websites running lighttpd web server on the internet or inside the same network, we'll need to allow port 80 from the firewall program. As both CentOS 7 and Ubuntu 15.04 are shipped with systemd as the default init system, we will have firewalld installed as a firewall solution. To allow port 80 or http service, we'll need to run the following commands.
|
||||
|
||||
# firewall-cmd --permanent --add-service=http
|
||||
success
|
||||
# firewall-cmd --reload
|
||||
success
|
||||
|
||||
### Accessing Web Server
|
||||
|
||||
As we have allowed port 80 which is the default port of lighttpd, we should be able to access lighttpd's welcome page by default. To do so, we'll need to point our browser to the ip address or domain of our machine running lighttpd according to our configuration. In this tutorial, we'll point our browser to [http://lighttpd.linoxide.com/](http://lighttpd.linoxide.com/) as we have pointed our sub-domain to its ip address. On doing so, we'll see the following welcome page in our browser.
|
||||
|
||||

|
||||
|
||||
Further, we can add our website's files to the webroot directory and remove the default lighttpd's index file to make our static website live to the internet.
|
||||
|
||||
If we want to run our PHP application in our lighttpd webserver, we'll need to follow the following steps.
|
||||
|
||||
### Installing PHP5 Modules
|
||||
|
||||
Once our lighttpd is installed successfully, we'll need to install PHP and some PHP modules to run PHP5 scripts in our lighttpd web server.
|
||||
|
||||
#### On Ubuntu 15.04
|
||||
|
||||
# apt-get install php5 php5-cgi php5-fpm php5-mysql php5-curl php5-gd php5-intl php5-imagick php5-mcrypt php5-memcache php-pear
|
||||
|
||||
#### On CentOS 7
|
||||
|
||||
# yum install php php-cgi php-fpm php-mysql php-curl php-gd php-intl php-pecl-imagick php-mcrypt php-memcache php-pear lighttpd-fastcgi
|
||||
|
||||
### Configuring Lighttpd with PHP
|
||||
|
||||
To make PHP work with lighttpd web server, we'll need to follow the following methods respect to the distribution we are running.
|
||||
|
||||
#### On CentOS 7
|
||||
|
||||
First of all, we'll need to edit our php configuration ie `/etc/php.ini` and uncomment a line **cgi.fix_pathinfo=1** using a text editor.
|
||||
|
||||
# nano /etc/php.ini
|
||||
|
||||
After its done, we'll need to change the ownership of PHP-FPM process from apache to lighttpd. To do so, we'll need to open the configuration file `/etc/php-fpm.d/www.conf` using a text editor.
|
||||
|
||||
# nano /etc/php-fpm.d/www.conf
|
||||
|
||||
Then, we'll append the file with the following configurations.
|
||||
|
||||
user = lighttpd
|
||||
group = lighttpd
|
||||
|
||||
Once done, we'll need to save the file and exit the text editor. Then, we'll need to include fastcgi module from `/etc/lighttpd/modules.conf` configuration file.
|
||||
|
||||
# nano /etc/lighttpd/modules.conf
|
||||
|
||||
Then, we'll need to uncomment the following line by removing `#` from it.
|
||||
|
||||
include "conf.d/fastcgi.conf"
|
||||
|
||||
At last, we'll need to configure our fastcgi configuration file using our favorite text editor.
|
||||
|
||||
# nano /etc/lighttpd/conf.d/fastcgi.conf
|
||||
|
||||
Then, we'll need to add the following lines at the end of the file.
|
||||
|
||||
fastcgi.server += ( ".php" =>
|
||||
((
|
||||
"host" => "127.0.0.1",
|
||||
"port" => "9000",
|
||||
"broken-scriptfilename" => "enable"
|
||||
))
|
||||
)
|
||||
|
||||
After its done, we'll save the file and exit the text editor.
|
||||
|
||||
#### On Ubuntu 15.04
|
||||
|
||||
To enable fastcgi with lighttpd web server, we'll simply need to execute the following commands.
|
||||
|
||||
# lighttpd-enable-mod fastcgi
|
||||
|
||||
Enabling fastcgi: ok
|
||||
Run /etc/init.d/lighttpd force-reload to enable changes
|
||||
|
||||
# lighttpd-enable-mod fastcgi-php
|
||||
|
||||
Enabling fastcgi-php: ok
|
||||
Run `/etc/init.d/lighttpd` force-reload to enable changes
|
||||
|
||||
Then, we'll reload our lighttpd by running the following command.
|
||||
|
||||
# systemctl force-reload lighttpd
|
||||
|
||||
### Testing if PHP is working
|
||||
|
||||
In order to see if PHP is working as expected or not, we'll need to create a new php file under the webroot of our lighttpd web server. Here, in this tutorial we have `/var/www/html` in Ubuntu and `/srv/www/htdocs` in CentOS as the default webroot so, we'll create a info.php file under it using a text editor.
|
||||
|
||||
**On CentOS 7**
|
||||
|
||||
# nano /var/www/info.php
|
||||
|
||||
**On Ubuntu 15.04**
|
||||
|
||||
# nano /srv/www/htdocs/info.php
|
||||
|
||||
Then, we'll simply add the following line into the file.
|
||||
|
||||
<?php phpinfo(); ?>
|
||||
|
||||
Once done, we'll simply save the file and exit from the text editor.
|
||||
|
||||
Now, we'll point our web browser to our machine running lighttpd using its ip address or domain name with the info.php file path as [http://lighttpd.linoxide.com/info.php](http://lighttpd.linoxide.com/info.php) If everything was done as described above, we will see our PHP information page as shown below.
|
||||
|
||||

|
||||
|
||||
### Conclusion
|
||||
|
||||
Finally we have successfully installed the world's lightweight, fast and secure web server Lighttpd in our machine running CentOS 7 and Ubuntu 15.04 linux distributions. Once its ready, we can upload our website files into our web root, configure virtual host, enable ssl, connect database, run web apps and much more with our lighttpd web server. If you have any questions, suggestions, feedback please write them in the comment box below so that we can improve or update our contents. Thank you ! Enjoy :-)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/setup-lighttpd-web-server-ubuntu-15-04-centos-7/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
@ -0,0 +1,104 @@
|
||||
Two Outstanding All-in-One Linux Servers
|
||||
================================================
|
||||
|
||||
keywords: Linux Server , SMB , clearos , Zentyal
|
||||
|
||||
|
||||
|
||||
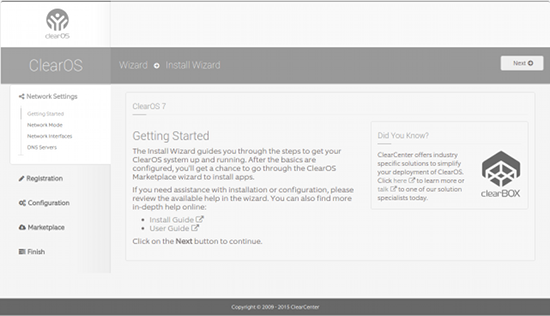
>Figure 1: The ClearOS setup wizard.
|
||||
|
||||
Back in 2000, Microsoft released their Small Business Server. This product changed the way many people viewed how technology could function within the realm of business. Instead of having multiple machines handle different tasks, you could deploy a single server which would handle email, calendaring, file sharing, directory services, VPN, and a whole lot more. For many of small businesses, this was a serious boon, but for some the cost of the Windows SMB was prohibitive. For yet others, the idea of relying on such a server, designed by Microsoft, simply wasn’t an option.
|
||||
|
||||
For that last group, there are alternatives. In fact, within the realm of Linux and open source, you can choose from several solid platforms that can serve your small business as a one-stop server shop. If your small business has between 10 and 50 employees, the all-in-one server might be the ideal solution to meet your needs.
|
||||
|
||||
Here, I’ll look at two Linux all-in-one servers, so you can see if one of them is the perfect match for your company.
|
||||
|
||||
Remember, these servers are not, in any way, suited for big business or enterprise. Larger companies cannot rely on the all-in-one server simply because a single server cannot take the load expected within the realm of enterprise needs. With that said, here’s what SMBs can expect from a Linux all in one.
|
||||
|
||||
### ClearOS
|
||||
|
||||
[ClearOS][1] was originally released in 2009, under the name ClarkConnect, as a router and gateway distribution. Since then, ClearOS has added all the features necessary to define it as an all-in-one server. ClearOS offers more than just a piece of software. You can also purchase a [ClearBox 100][2] or [ClearBox 300][3]. These servers ship complete with ClearOS and are marketed as IT in a box. Check out the feature comparison/price matrix [here][4].
|
||||
|
||||
For those with hardware already in-house, you can download one of the following:
|
||||
|
||||
- [ClearOS Community][5] — The community (free) edition of ClearOS
|
||||
|
||||
- [ClearOS Home][6] — Ideal for home offices (details on features and subscription costs, see here)
|
||||
|
||||
- [ClearOS Business][7] — Ideal for small businesses (details on features and subscription costs, see here)
|
||||
|
||||
What do you get with ClearOS? You get a business-class server with a single, elegantly designed web interface. What is unique about ClearOS is that you will get plenty of features in the base server; beyond that, you must add on features from the [Clear Marketplace][8]. From within the Marketplace, you can install free or paid apps that extend the feature set of the ClearOS server. Here you’ll find add-ons for Windows Server Active Directory, OpenLDAP, Flexshares, Antimalware, Cloud, Web access control, Content filtering, and much more. You’ll even find some third-party add-ons such as Google Apps Synchronization, Zarafa Collaboration Platform, and Kaspersky Anti-virus.
|
||||
|
||||
ClearOS is installed like any other Linux distribution (based on Red Hat’s Anaconda installer). Once the install is complete, you will be prompted to set up the networking interface as well as presented with the address to point your browser (on the same network as the ClearOS server). The address will be in the form:
|
||||
|
||||
[https://IP_OF_CLEAROS_SERVER:81][9]
|
||||
|
||||
Where IP_OF_CLEAROS_SERVER is the actual IP address of the server. NOTE: When you first point your browser to the server, you will receive a “Connection is not private” warning. Proceed on to the address so you can continue the setup.
|
||||
|
||||
When the browser finally connects, you will be prompted for the root user credentials (you set the root user password up during initial installation). Once authenticated, you will be presented with the ClearOS setup wizard (Figure 1 above).
|
||||
|
||||
Click the Next button to begin the process of setting up your ClearOS server. The wizard is self-explanatory and, in the end, you will be asked which version of ClearOS you want to use. Click either Community, Home, or Business. Once selected, you will be required to register for an account. Once you’ve created an account and registered the server, you can then move on to updating the server, configuring the server, and adding modules from the marketplace (Figure 2).
|
||||
|
||||

|
||||
|
||||
>Figure 2: Installing modules from the marketplace.
|
||||
|
||||
At this point, you are ready to start digging deep into the configuration of your ClearOS small business server.
|
||||
|
||||
### Zentyal
|
||||
|
||||
[Zentyal][10] is a Ubuntu-based small business server that was, at one point, distributed under the name eBox. Zentyal offers plenty of servers/services to fit your SMB needs:
|
||||
|
||||
- Email — Webmail; Native MS Exchange protocols and Active Directory support; Calendars and contacts; Mobile device email sync; Antivirus/antispam; IMAP, POP, SMTP, CalDAV, and CardDAV support
|
||||
|
||||
- Domain & Directory — Central domain directory management; Multiple organization units; Single sign-on authentication; File sharing; ACLs, Advanced domain management, Printer management
|
||||
|
||||
- Networking & Firewall — Static and DHCP interfaces; Objects & services; Packet filter; Port forwarding
|
||||
|
||||
- Infrastructure — DNS; DHCP; NTP; Certification authority; VPN
|
||||
|
||||
- Firewall
|
||||
|
||||
The installation of Zentyal is very much like that of Ubuntu Server—it’s text based and quite simple: Boot up the install media, make a few quick selections, and wait for the installation to complete. Once the initial, text-based, installation is finished, you are presented with the GUI desktop where a wizard will appear for package selection. Select all the packages you want to install and allow the installer to finish the job.
|
||||
|
||||
Finally, you can log into your Zentyal server via the web interface (point your browser to [https://IP_OF_SERVER:8443][11] — where IP_OF_SERVER is the LAN address of the Zentyal server) or use the standalone, desktop GUI to administer the server (Zentyal includes quick access to an Administrator and User console as well as a Zentyal Administration console). When all systems have been saved and started, you will be presented with the Zentyal Dashboard (Figure 3).
|
||||
|
||||

|
||||
|
||||
>Figure 3: The Zentyal Dashboard in action.
|
||||
|
||||
The Dashboard allows you to control all aspects of the server, such as updating, managing servers/services, and getting a quick status update of the server. You can also go into the Components area and install components that you opted out of during installation or update the current package list. Click on Software Management > System Updates and select what you want to update (Figure 4), then click the UPDATE button at the bottom of the screen.
|
||||
|
||||

|
||||
|
||||
>Figure 4: Updating your Zentyal server is simple.
|
||||
|
||||
### Which Server Is Right for You?
|
||||
|
||||
The answer to this question depends on what you need. Zentyal is an amazing server that does a great job running your SMB network. If you need a bit more, such as groupware, your best bet is to go with ClearOS. If you don’t need groupware, either server will do an outstanding job.
|
||||
|
||||
I highly recommend installing both of these all-in-one servers to see which will best serve your small company needs.
|
||||
|
||||
|
||||
------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.com/learn/tutorials/882146-two-outstanding-all-in-one-linux-servers
|
||||
|
||||
作者:[Jack Wallen][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: http://www.linux.com/community/forums/person/93
|
||||
[1]: http://www.linux.com/learn/tutorials/882146-two-outstanding-all-in-one-linux-servers#clearfoundation-overview
|
||||
[2]: https://www.clearos.com/products/hardware/clearbox-100-series
|
||||
[3]: https://www.clearos.com/products/hardware/clearbox-300-series
|
||||
[4]: https://www.clearos.com/products/hardware/clearbox-overview
|
||||
[5]: http://mirror.clearos.com/clearos/7/iso/x86_64/ClearOS-DVD-x86_64.iso
|
||||
[6]: http://mirror.clearos.com/clearos/7/iso/x86_64/ClearOS-DVD-x86_64.iso
|
||||
[7]: http://mirror.clearos.com/clearos/7/iso/x86_64/ClearOS-DVD-x86_64.iso
|
||||
[8]: https://www.clearos.com/products/purchase/clearos-marketplace-overview
|
||||
[9]: https://ip_of_clearos_server:81/
|
||||
[10]: http://www.zentyal.org/server/
|
||||
[11]: https://ip_of_server:8443/
|
||||
@ -0,0 +1,90 @@
|
||||
翻译中;by 
|
||||
Top 5 open source command shells for Linux
|
||||
===============================================
|
||||
|
||||
keyword: shell , Linux , bash , zsh , fish , ksh , tcsh , license
|
||||
|
||||

|
||||
|
||||
There are two kinds of Linux users: the cautious and the adventurous.
|
||||
|
||||
On one side is the user who almost reflexively tries out ever new option which hits the scene. They’ve tried handfuls of window managers, dozens of distributions, and every new desktop widget they can find.
|
||||
|
||||
On the other side is the user who finds something they like and sticks with it. They tend to like their distribution’s defaults. If they’re passionate about a text editor, it’s whichever one they mastered first.
|
||||
|
||||
As a Linux user, both on the server and the desktop, for going on fifteen years now, I am definitely more in the second category than the first. I have a tendency to use what’s presented to me, and I like the fact that this means more often than not I can find thorough documentation and examples of most any use case I can dream up. If I used something non-standard, the switch was carefully researched and often predicated by a strong pitch from someone I trust.
|
||||
|
||||
But that doesn’t mean I don’t like to sometimes try and see what I’m missing. So recently, after years of using the bash shell without even giving it a thought, I decided to try out four alternative shells: ksh, tcsh, zsh, and fish. All four were easy installs from my default repositories in Fedora, and they’re likely already packaged for your distribution of choice as well.
|
||||
|
||||
Here’s a little bit on each option and why you might choose it to be your next Linux command-line interpreter.
|
||||
|
||||
### bash
|
||||
|
||||
First, let’s take a look back at the familiar. [GNU Bash][1], the Bourne Again Shell, has been the default in pretty much every Linux distribution I’ve used through the years. Originally released in 1989, bash has grown to easily become the most used shell across the Linux world, and it is commonly found in other unix-like operating systems as well.
|
||||
|
||||
Bash is a perfectly respectable shell, and as you look for documentation of how to do various things across the Internet, almost invariably you’ll find instructions which assume you are using a bash shell. But bash has some shortcomings, as anyone who has ever written a bash script that’s more than a few lines can attest to. It’s not that you can’t do something, it’s that it’s not always particularly intuitive (or at least elegant) to read and write. For some examples, see this list of [common bash pitfalls][2].
|
||||
|
||||
That said, bash is probably here to stay for at least the near future, with its enormous install base and legions of both casual and professional system administrators who are already attuned to its usage, and quirks. The bash project is available under a [GPLv3][3] license.
|
||||
|
||||
### ksh
|
||||
|
||||
[KornShell][4], also known by its command invocation, ksh, is an alternative shell that grew out of Bell Labs in the 1980s, written by David Korn. While originally proprietary software, later versions were released under the [Eclipse Public License][5].
|
||||
|
||||
Proponents of ksh list a number of ways in which they feel it is superior, including having a better loop syntax, cleaner exit codes from pipes, an easier way to repeat commands, and associative arrays. It's also capable of emulating many of the behaviors of vi or emacs, so if you are very partial to a text editor, it may be worth giving a try. Overall, I found it to be very similar to bash for basic input, although for advanced scripting it would surely be a different experience.
|
||||
|
||||
### tcsh
|
||||
|
||||
[Tcsh][6] is a derivative of csh, the Berkely Unix C shell, and sports a very long lineage back to the early days of Unix and computing itself.
|
||||
|
||||
The big selling point for tcsh is its scripting language, which should look very familiar to anyone who has programmed in C. Tcsh's scripting is loved by some and hated by others. But it has other features as well, including adding arguments to aliases, and various defaults that might appeal to your preferences, including the way autocompletion with tab and history tab completion work.
|
||||
|
||||
You can find tcsh under a [BSD license][7].
|
||||
|
||||
### zsh
|
||||
|
||||
[Zsh][8] is another shell which has similarities to bash and ksh. Originating in the early 90s, zsh sports a number of useful features, including spelling correction, theming, namable directory shortcuts, sharing your command history across multiple terminals, and various other slight tweaks from the original Bourne shell.
|
||||
|
||||
The code and binaries for zsh can be distributed under an MIT-like license, though portions are under the GPL; check the [actual license][9] for details.
|
||||
|
||||
### fish
|
||||
|
||||
I knew I was going to like the Friendly Interactive Shell, [fish][10], when I visited the website and found it described tongue-in-cheek with "Finally, a command line shell for the 90s"—fish was written in 2005.
|
||||
|
||||
The authors of fish offer a number of reasons to make the switch, all invoking a bit of humor and poking a bit of fun at shells that don't quite live up. Features include autosuggestions ("Watch out, Netscape Navigator 4.0"), support of the "astonishing" 256 color palette of VGA, but some actually quite helpful features as well including command completion based on the man pages on your machine, clean scripting, and a web-based configuration.
|
||||
|
||||
Fish is licensed primarily unde the GPL version 2 but with portions under other licenses; check the repository for [complete information][11].
|
||||
|
||||
***
|
||||
|
||||
Looking for a more detailed rundown on the precise differences between each option? [This site][12] ought to help you out.
|
||||
|
||||
So where did I land? Well, ultimately, I’m probably going back to bash, because the differences were subtle enough that someone who mostly used the command line interactively as opposed to writing advanced scripts really wouldn't benefit much from the switch, and I'm already pretty comfortable in bash.
|
||||
|
||||
But I’m glad I decided to come out of my shell (ha!) and try some new options. And I know there are many, many others out there. Which shells have you tried, and which one do you prefer? Let us know in the comments!
|
||||
|
||||
|
||||
|
||||
|
||||
via: https://opensource.com/business/16/3/top-linux-shells
|
||||
|
||||
作者:[Jason Baker][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/jason-baker
|
||||
|
||||
[1]: https://www.gnu.org/software/bash/
|
||||
[2]: http://mywiki.wooledge.org/BashPitfalls
|
||||
[3]: http://www.gnu.org/licenses/gpl.html
|
||||
[4]: http://www.kornshell.org/
|
||||
[5]: https://www.eclipse.org/legal/epl-v10.html
|
||||
[6]: http://www.tcsh.org/Welcome
|
||||
[7]: https://en.wikipedia.org/wiki/BSD_licenses
|
||||
[8]: http://www.zsh.org/
|
||||
[9]: https://sourceforge.net/p/zsh/code/ci/master/tree/LICENCE
|
||||
[10]: https://fishshell.com/
|
||||
[11]: https://github.com/fish-shell/fish-shell/blob/master/COPYING
|
||||
[12]: http://hyperpolyglot.org/unix-shells
|
||||
|
||||
@ -0,0 +1,81 @@
|
||||
Image processing at NASA with open source tools
|
||||
=======================================================
|
||||
|
||||
keyword: NASA , Image Process , Node.js , OpenCV
|
||||
|
||||

|
||||
|
||||
This past summer, I was an intern at the [GVIS][1] Lab at [NASA][2] Glenn, where I brought my passion for open source into the lab. My task was to improve our lab's contributions to an open source fluid flow dynamics [simulation][3] developed by Dan Schroeder. The original simulation presents obstacles that users can draw in with their mouse to model computational fluid dynamics. My team contributed by adding image processing code that analyzes each frame of a live video feed to show how a physical object interacts with a fluid. But, there was more for us to do.
|
||||
|
||||
We wanted to make the image processing more robust, so I worked on improving the image processing library.
|
||||
|
||||
With the new library, the simulation would be able to detect contours, perform coordinate transformations in place, and find the center of mass of an object. The image processing doesn't directly relate to the physics of the fluid flow dynamics simulation. It detects the object with a camera and creates a barrier for the fluid flow simulation by getting the outline of the object. Then, the fluid flow simulation runs, and the output is projected down onto the actual object.
|
||||
|
||||
My goal was to improve the simulation in three ways:
|
||||
|
||||
1. to find accurate contours of an object
|
||||
2. to find the center of mass of an object
|
||||
3. to be able to perform accurate transformations about the center of an object
|
||||
|
||||
My mentor recommended that I install [Node.js][4], [OpenCV][5], and the [Node.js bindings for OpenCV][6]. While I was waiting for those to install, I looked at the example code on the OpenCV bindings on their [GitHub page][7]. I discovered that the example code was in JavaScript, so because I didn’t know JavaScript, I started a short course from Codecademy. Two days later, I was sick of JavaScript but ready to start my project... which involved yet more JavaScript.
|
||||
|
||||
The example contour-finding code worked well. In fact, it allowed me to accomplish my first goal in a matter of hours! To get the contours of an image, here's what it looked like:
|
||||
|
||||
|
||||
>The original image with all of the contours.
|
||||
|
||||
The example contour-finding code worked a bit too well. Instead of the contour of the object being detected, all of the contours in the image were detected. This would have resulted in the simulation interacting with all of the unwanted contours. This is a problem because it would return incorrect data. To keep the simulation from interacting with the unwanted contours, I added an area constraint. If the contour was in a certain area range, then it would be drawn. The area constraint resulted in a much cleaner contour.
|
||||
|
||||
|
||||
>The filtered contour with the shadow contour.
|
||||
|
||||
Though the extraneous contours weren't detected, there was still a problem with the image. There was only one contour in the image, but it doubled back on itself and wasn't complete. Area couldn't be a deciding factor here, so it was time to try something else.
|
||||
|
||||
This time around, instead of immediately finding the contours, I first converted the image into a binary image. A binary image is an image where each pixel is either black or white. To get a binary image I first converted the color image to grayscale. Once the image was in grayscale, I called the threshold method on the image. The threshold method went through the image pixel by pixel and if the color value of the pixel was less than 30, the pixel color would be changed to black. Otherwise, the pixel value would be turned to white. After the original image was converted to a binary image, the resulting image looked like this:
|
||||
|
||||

|
||||
>The binary image.
|
||||
|
||||
Then I got the contours from the binary image, which resulted in a much cleaner contour, without the shadow contour.
|
||||
|
||||
|
||||
>The final clean contour.
|
||||
|
||||
At this point, I was able to get clean contours and detect the center of mass. Unfortunately, I didn't have enough time to be able to complete transformations about the center of mass. Since I only had a few days left in my internship, I started to think about other things I could do within a limited time span. One of those things was the bounding rectangle. The bounding rectangle is a quadrilateral with the smallest area that contains the entire contour of an image. The bounding rectangle is important because it is key in scaling the contour on the page. Unfortunately I didn't have time to do much with the bounding rectangle, but I still wanted to learn about it because it's a useful tool.
|
||||
|
||||
Finally, after all of that, I was able to finish processing the image!
|
||||
|
||||
|
||||
>The final image with bounding rectangle and center of mass in red.
|
||||
|
||||
Once the image processing code was complete, I replaced the old image processing code in the simulation with my code. To my surprise, it worked!
|
||||
|
||||
Well, mostly.
|
||||
|
||||
The program had a memory leak in it, which leaked 100MB every 1/10 of a second. I was glad that it wasn’t because of my code. The bad thing was that fixing it was out of my control. The good thing was that there was a workaround that I could use. It was less than ideal, but it checked the amount of memory the simulation was using and when it used more than 1 GiB, the simulation restarted.
|
||||
|
||||
At the NASA lab, we use a lot of open source software, and my work there isn't possible without it.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/life/16/3/image-processing-nasa
|
||||
|
||||
作者:[Lauren Egts][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/laurenegts
|
||||
[1]: https://ocio.grc.nasa.gov/gvis/
|
||||
[2]: http://www.nasa.gov/centers/glenn/home/index.html
|
||||
[3]: http://physics.weber.edu/schroeder/fluids/
|
||||
[4]: http://nodejs.org/
|
||||
[5]: http://opencv.org/
|
||||
[6]: https://github.com/peterbraden/node-opencv
|
||||
[7]: https://github.com/peterbraden/node-opencv
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
GHLandy Translating
|
||||
|
||||
Part 10 - LFCS: Understanding & Learning Basic Shell Scripting and Linux Filesystem Troubleshooting
|
||||
================================================================================
|
||||
The Linux Foundation launched the LFCS certification (Linux Foundation Certified Sysadmin), a brand new initiative whose purpose is to allow individuals everywhere (and anywhere) to get certified in basic to intermediate operational support for Linux systems, which includes supporting running systems and services, along with overall monitoring and analysis, plus smart decision-making when it comes to raising issues to upper support teams.
|
||||
|
||||
@ -1,28 +0,0 @@
|
||||
超过一千万个使用 https 的站点有可能收到新型的加密攻击的影响
|
||||
===========================================================================
|
||||
|
||||

|
||||
|
||||
|
||||
低成本的淹没攻击会在几个小时内完成解密操作,同时这也不利于采用了 TLS 的邮件服务器。
|
||||
|
||||
|
||||
一个国际研究小组在周二发出的警告说,超过 1100 万的网站和邮件服务采用了[传输层安全协议][1],以此来保护自己的服务,而这些都是处于一个新发现的、低成本的攻击的威胁之下,这种攻击会在几个小时内解密敏感的通信,在某些情况下甚至是立即解密。 1 百万个最流行的网站中有超过 81,000 个就处于这些受到威胁的 HTTPS 协议保护之下。
|
||||
|
||||
|
||||
处于 TLS 保护的通信协议,依赖于 [RSA 加密系统][2],如果密钥被泄露了,即使是间接的通过 SSLv2 ——一种在 20 年前就因为自身缺陷而退休了的安全协议,也就是 TLS 的前辈协议——泄露也会处于这种新型攻击的威胁之下。这种危险性在于允许一个入侵者通过反复的使用 SSLv2 来连接到服务器,可以解密一个被中途拦截下来的 TLS 连接。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/news/software/applications/889455--more-than-11-million-https-websites-imperiled-by-new-decryption-attack
|
||||
|
||||
作者:[ArsTechnica][a]
|
||||
译者:[Ezio](https://github.com/oska874)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/community/forums/person/112
|
||||
[1]: https://en.wikipedia.org/wiki/Transport_Layer_Security
|
||||
[2]: https://en.wikipedia.org/wiki/RSA_(cryptosystem)
|
||||
|
||||
@ -0,0 +1,164 @@
|
||||
Martin
|
||||
|
||||
2015 Bossie 评选:最佳开源网络和安全软件
|
||||
================================================================================
|
||||
InfoWorld 在建设网络,运营网络和保障网络安全领域精选出了年度开源工具获奖者。
|
||||
|
||||

|
||||
|
||||
### 最佳开源网络和安全软件 ###
|
||||
|
||||
[BIND](https://en.wikipedia.org/wiki/BIND), [Sendmail](https://en.wikipedia.org/wiki/Sendmail), [OpenSSH](https://en.wikipedia.org/wiki/OpenSSH), [Cacti](https://en.wikipedia.org/wiki/Cactus), [Nagios](https://en.wikipedia.org/wiki/Nagios), [Snort](https://en.wikipedia.org/wiki/Snort_%28software%29) -- 这些为了网络而发明的开源软件,许多老家伙和好东西依然强劲。今年在我们这个范畴的最佳选择中,你会发现中坚支柱,新人,和新贵正在完善网络管理,安全监控,漏洞评估,[rootkit](https://en.wikipedia.org/wiki/Rootkit) 检测,以及更多。
|
||||
|
||||

|
||||
|
||||
### Icinga 2 ###
|
||||
|
||||
Icinga 起先只是系统监控应用 Nagios 的一个分叉。为了给用户一个时尚的界面,对多个数据库的支持,以及一个集成众多扩展的 API,[Icinga 2][1] 被完全重写。凭借开箱即用的负载均衡、通知和配置,Icinga 2 缩短了在复杂环境下的安装时间。Icinga 2 原生支持 [Graphite](https://github.com/graphite-project/graphite-web)(系统监控应用),轻松为管理员呈现实时性能图表。但是 Icinga 今年很火是因为它发布了一个支持可拖放可定制 dashboard 和一些流式监控工具的前端图形界面系统 Icinga Web 2。
|
||||
|
||||
管理员可以查看,过滤,并把问题按优先顺序排好,同时保持跟踪已经进行的动作。一个新的矩阵视图使管理员能够在一个页面上查看主机和服务。您可以查看一个特定时间段的事件或筛选了的事件来了解哪些需要立即关注。Icinga Web 2 能够拥有一个全新界面和更为强劲的性能,然而传统版 Icinga 和 Web 版 Icinga 的所有常用命令仍然可用。这意味着学习新版工具不耗费额外的时间。
|
||||
|
||||
-- Fahmida Rashid
|
||||
|
||||

|
||||
|
||||
### Zenoss Core ###
|
||||
|
||||
另一个强大的开源软件,[Zenoss Core][2] 为网络管理员提供了一个完整的,一站式解决方案来跟踪和管理所有的应用程序、服务器、存储,网络组件、虚拟化工具、以及企业基础架构的其他元素。管理员可以确保硬件的运行效率并利用模块化设计的插件来扩展 ZenPacks 的功能。
|
||||
|
||||
Zenoss Core 5,在今年二月发布,作为已经很强大的工具,并进一步改进以增强用户界面和扩展 dashboard。基于 Web 的控制台和 dashboard 已经是高度可定制的和动态调整的,现在新版本可让管理员混搭多个组件图表到一个图表。可把它作为一种更好的根源分析和因果分析的工具。
|
||||
|
||||
Portlets 为网络映射、设备问题、守护进程、产品状态、监视列表和事件视图等等提供深入的分析。而且新的 HTML5 图表可以从工具导出。Zenoss 的控制中心支持带外管理并且可监控所有 Zenoss 组件。Zenoss Core 拥有在线备份和恢复、快照和回滚和多主机部署的新工具。更重要的是,凭借对 Docker 的全面支持,部署起来更快了。
|
||||
|
||||
-- Fahmida Rashid
|
||||
|
||||

|
||||
|
||||
### OpenNMS ###
|
||||
|
||||
一个非常灵活的网络管理解决方案,[OpenNMS][3] 可以处理任何网络管理任务,无论是设备管理,应用性能监控,库存控制,或事件管理。凭借对 IPv6 的支持,强大的警报系统,和记录用户脚本来测试 Web 应用程序的能力,OpenNMS 拥有网络管理员和测试人员需要的一切。OpenNMS 现在变得像一款移动 dashboard,堪称 OpenNMS 指南针,可让网络专家随时,甚至当他们外出时都可以监视他们的网络。
|
||||
|
||||
该应用程序的 IOS 版本,可从 [iTunes App Store][4] 上获取,显示故障、节点和告警。下一个版本将提供更多的事件细节、资源图表、以及关于 IP 和 SNMP 接口的信息。安卓版可从 [Google Play][5] 上获取,可在仪表板上显示网络可用性,故障和告警,以及确认、提升或清除告警的能力。移动客户端与 OpenNMS Horizon 1.12 或更高版本以及 OpenNMS Meridian 2015.1.0 或更高版本兼容。
|
||||
|
||||
-- Fahmida Rashid
|
||||
|
||||

|
||||
|
||||
### Security Onion ###
|
||||
|
||||
如同一个洋葱,网络安全监控是由许多层组成。没有单一的工具会使你洞察在你公司网络中的每次攻击,或者显示每一次侦查或文本会话给你。[Security Onion][6] 打包了许多经过验证的工具成为一个便于使用的 Ubuntu 发行版,这会让你看到谁留在你的网络里,并帮助你隔离坏家伙。
|
||||
|
||||
无论你是采取主动式的网络安全监测还是追查可能的攻击,Security Onion 都可以帮助你。由传感器、服务器和显示层组成,Onion 结合了基于网络和基于主机的入侵检测,全面的网络数据包捕获,并提供了所有的各种日志进行检查和分析。
|
||||
|
||||
众星云集的的网络安全工具链,包括用于网络抓包的 [Netsniff-NG](http://www.netsniff-ng.org/)、基于规则的网络入侵检测系统 Snort 和 [Suricata](https://en.wikipedia.org/wiki/Suricata_%28software%29),基于分析的网络监控系统 Bro,基于主机的入侵检测系统 OSSEC 和用于显示、分析和日志管理的 Sguil、Squert、Snorby 和 ELSA (企业日志搜索和归档)。它是一个经过精挑细选的工具集,全被打包进一个向导驱动式的安装程序并有完整的文档支持,可以帮助你尽可能快地进行监控。
|
||||
|
||||
-- Victor R. Garza
|
||||
|
||||

|
||||
|
||||
Kali Linux
|
||||
|
||||
[Kali Linux][7] 背后的团队修改了今年流行的安全 Linux 发行版,使其更快,更全能。Kali 采用全新 4.0 版的内核 ,改进了对硬件和无线驱动程序的支持,以及一个更流畅的界面。最流行的工具都可从屏幕的侧边栏上轻松访问。最大的改变?Kali Linux 现在是一个滚动发行版,具有连续的软件更新。Kali 的核心系统是基于 Debian Jessie 发行版,而且该团队会不断地从 Debian 测试版 pull 程序包,同时持续在上面添加新的 Kali 风格的特性。
|
||||
|
||||
该发行版仍然配备满了渗透测试,漏洞分析,安全审查,网络应用分析,无线网络评估,逆向工程,和漏洞利用工具。现在该发行版具有新版本检测系统,当有个别工具可更新时系统会自动通知用户。该发行版还具有一系列设备的 ARM 映像,包括树莓派、[Chromebook](https://en.wikipedia.org/wiki/Chromebook) 和 [Odroid](https://en.wikipedia.org/wiki/ODROID),也可更新在 Android 设备上运行的 [NetHunter](https://www.kali.org/kali-linux-nethunter/) 渗透测试平台。还有其他的变化:Metasploit 的社区版/专业版不再包括在内,因为 Kali 2.0 还没有 [Rapid7 的官方支持][8]。
|
||||
|
||||
-- Fahmida Rashid
|
||||
|
||||

|
||||
|
||||
### OpenVAS ###
|
||||
|
||||
[OpenVAS][9],开源漏洞评估系统,是一种整合多种服务和工具来提供漏洞扫描和漏洞管理的软件框架。该扫描器与每周一次的网络漏洞测试数据配合,或者您可以使用商业数据。该软件框架包括一个命令行界面(所以它可以用脚本运行)和一个带 SSL 安全机制的基于 [Greenbone 安全助手][10] 的浏览器界面。OpenVAS 提供了用于附加功能的各种插件。扫描可以预定运行或按需运行。
|
||||
|
||||
可通过单一的主控来控制多个 OpenVAS 的安装,使得它成为一个可扩展的企业漏洞评估工具。该项目与兼容这样的标准:扫描结果和配置存储在 SQL 数据库中,在那里他们可以容易地被外部报告工具访问。客户端工具通过基于 XML 的无状态 OpenVAS 管理协议访问 OpenVAS 管理器,所以安全管理员可以扩展该框架的功能。该软件能以包或源代码的方式安装在 Windows 或 Linux 上运行,或者作为一个虚拟设备被下载。
|
||||
|
||||
-- Matt Sarrel
|
||||
|
||||

|
||||
|
||||
### OWASP ###
|
||||
|
||||
[OWASP][11],开放的 Web 应用安全项目,是专注于提高软件安全性的全球协会的非营利组织。社区性组织提供测试工具、文档、培训和几乎任何你可以想象的评估软件安全和开发安全软件相关的最佳实践。有几个 OWASP 项目已成为很多安全从业者的工具箱中有价值的组件:
|
||||
|
||||
[ZAP][12],ZED 攻击代理项目,是一个在 Web 应用程序中寻找漏洞的渗透测试工具。ZAP 的设计目标之一是使之易于使用,以便于开发人员和非安全专家的测试人员可以受益于使用它。ZAP 提供了自动扫描器和一套手动测试工具。
|
||||
|
||||
[Xenotix XSS Exploit Framework][13] 是一款运行浏览器引擎内的扫描来获得实际结果的先进的跨站脚本漏洞检测和漏洞利用框架。Xenotix 扫描器模块采用三个智能的 fuzzer,它可以运行近 5000 个不同的XSS有效载荷。一个 API 可以让安全管理员扩展和定制开发工具包。
|
||||
|
||||
[O-Saft][14],OWASP SSL 高级审查工具,一个查看 SSL 证书详细信息和测试 SSL 连接的 SSL 审计工具。这个命令行工具可以在线或离线运行来评估 SSL 安全性,比如密码和配置。O-Saft 提供了常见漏洞的内置检查,你可以容易地通过编写脚本来扩展这些功能。在 2015 年 5 月加入了一个简单的图形用户界面作为可选的下载项。
|
||||
|
||||
[OWTF][15],攻击性的 Web 测试框架,一个遵循 OWASP 测试指南和 NIST 和 PTES 标准的自动化测试工具。该框架使用一个 Web 用户界面和一个命令行,它探测 Web 和应用服务器常见漏洞,如配置不当和未打补丁的软件。
|
||||
|
||||
-- Matt Sarrel
|
||||
|
||||

|
||||
|
||||
### BeEF ###
|
||||
|
||||
Web 浏览器已经成为用于针对客户端的攻击中最常见的载体。[BeEF][15] 浏览器漏洞利用框架项目,是一种广泛使用的用以评估 Web 浏览器安全性的渗透工具。BeEF 帮助你揭露客户端系统的安全弱点,通过启动浏览器来进行客户端攻击。BeEF 建立了一个恶意网站,安全管理员用想要测试的浏览器访问该网站。然后 BeEF 发送命令来攻击 Web 浏览器并使用命令在客户端机器上植入软件。如果他们是僵尸机 ,管理员可以对客户端机器发动攻击。
|
||||
|
||||
BeEF 自带像键盘记录器,一个端口扫描器,和 Web 代理这样的常用模块,此外你可以编写你自己的模块或直接将命令发送到僵尸测试机。BeEF 带有少量的演示网页来帮你快速入门使得编写额外的网页和攻击模块很简单,因此你可以自定义测试你的环境。BeEF 是一个评估浏览器和终端安全、学习如何发起基于浏览器的攻击的宝贵的测试工具。可使用它来展示恶意软件通常如何感染客户端设备的演示给你的用户。
|
||||
|
||||
-- Matt Sarrel
|
||||
|
||||

|
||||
|
||||
### Unhide ###
|
||||
|
||||
[Unhide][16] 是一个定位开放的 TCP/UDP 端口和隐藏在 UNIX、Linux 和 Windows 上的进程的审查工具。隐藏的端口和进程可以是 rootkit 或 LKM(可加载的内核模块)activity 的结果。rootkit 可能很难找到并移除,因为它们被设计成隐蔽的,对操作系统和用户隐藏自己。一个 rootkit 可以使用内核模块隐藏其进程或冒充其他进程,让它在机器上运行很长一段时间而不被发现。Unhide 可以保证管理员需要的干净系统。
|
||||
|
||||
Unhide 实际上是两个单独的脚本:一个用于进程,一个用于端口。该工具查询正在运行的进程、线程和开放的端口并将这些信息与系统中注册的活动比较,报告之间的差异。Unhide 和 WinUnhide 是在运行命令行产生文本输出的非常轻量级的脚本。它们不算优美,但是极为有用。Unhide 还列入了 [Rootkit Hunter][17] 项目中。
|
||||
|
||||
-- Matt Sarrel
|
||||
|
||||

|
||||
|
||||
查看更多的开源软件优胜者
|
||||
|
||||
InfoWorld 网站的 2014 年最佳开源奖从堆栈底部到顶部庆祝了 100 多个开源项目。以下链接指向更多开源软件优胜者:
|
||||
|
||||
[2015 Bossie 评选:最佳开源应用程序][18]
|
||||
|
||||
[2015 Bossie 评选:最佳开源应用程序开发工具][19]
|
||||
|
||||
[2015 Bossie 评选:最佳开源大数据工具][20]
|
||||
|
||||
[2015 Bossie 评选:最佳开源数据中心和云计算软件][21]
|
||||
|
||||
[2015 Bossie 评选:最佳开源桌面和移动端软件][22]
|
||||
|
||||
[2015 Bossie 评选:最佳开源网络和安全软件][23]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.infoworld.com/article/2982962/open-source-tools/bossie-awards-2015-the-best-open-source-networking-and-security-software.html
|
||||
|
||||
作者:[InfoWorld staff][a]
|
||||
译者:[robot527](https://github.com/robot527)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.infoworld.com/author/InfoWorld-staff/
|
||||
[1]:https://www.icinga.org/icinga/icinga-2/
|
||||
[2]:http://www.zenoss.com/
|
||||
[3]:http://www.opennms.org/
|
||||
[4]:https://itunes.apple.com/us/app/opennms-compass/id968875097?mt=8
|
||||
[5]:https://play.google.com/store/apps/details?id=com.opennms.compass&hl=en
|
||||
[6]:http://blog.securityonion.net/p/securityonion.html
|
||||
[7]:https://www.kali.org/
|
||||
[8]:https://community.rapid7.com/community/metasploit/blog/2015/08/12/metasploit-on-kali-linux-20
|
||||
[9]:http://www.openvas.org/
|
||||
[10]:http://www.greenbone.net/
|
||||
[11]:https://www.owasp.org/index.php/Main_Page
|
||||
[12]:https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project
|
||||
[13]:https://www.owasp.org/index.php/O-Saft
|
||||
[14]:https://www.owasp.org/index.php/OWASP_OWTF
|
||||
[15]:http://www.beefproject.com/
|
||||
[16]:http://www.unhide-forensics.info/
|
||||
[17]:http://www.rootkit.nl/projects/rootkit_hunter.html
|
||||
[18]:http://www.infoworld.com/article/2982622/bossie-awards-2015-the-best-open-source-applications.html
|
||||
[19]:http://www.infoworld.com/article/2982920/bossie-awards-2015-the-best-open-source-application-development-tools.html
|
||||
[20]:http://www.infoworld.com/article/2982429/bossie-awards-2015-the-best-open-source-big-data-tools.html
|
||||
[21]:http://www.infoworld.com/article/2982923/bossie-awards-2015-the-best-open-source-data-center-and-cloud-software.html
|
||||
[22]:http://www.infoworld.com/article/2982630/bossie-awards-2015-the-best-open-source-desktop-and-mobile-software.html
|
||||
[23]:http://www.infoworld.com/article/2982962/bossie-awards-2015-the-best-open-source-networking-and-security-software.html
|
||||
@ -0,0 +1,98 @@
|
||||
5 个适合课堂教学的树莓派项目
|
||||
================================================================================
|
||||

|
||||
|
||||
图片来源 : opensource.com
|
||||
|
||||
### 1. Minecraft Pi ###
|
||||
|
||||
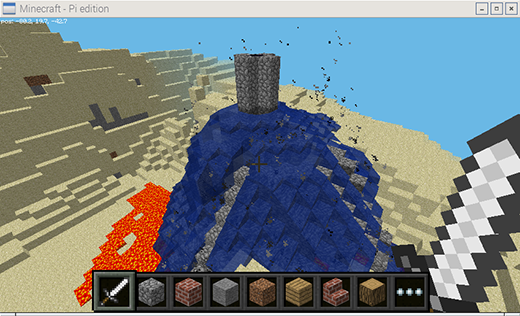
|
||||
|
||||
上图由树莓派基金会提供。遵循 [CC BY-SA 4.0.][1] 协议。
|
||||
|
||||
Minecraft(我的世界)几乎是世界上每个青少年都极其喜爱的游戏 —— 在吸引年轻人注意力方面,它也是最具创意的游戏之一。伴随着每一个树莓派的游戏版本不仅仅是一个关于创造性思维的建筑游戏,它还带有一个编程接口,允许使用者通过 Python 代码来与 Minecraft 世界进行互动。
|
||||
|
||||
对于教师来说,Minecraft: Pi 版本是一个鼓励学生们解决遇到的问题以及通过书写代码来执行特定任务的极好方式。你可以使用 Python API
|
||||
来建造一所房子,让它跟随你到任何地方;或在你所到之处修建一座桥梁;又或者是下一场岩溶雨;或在天空中显示温度;以及其他任何你能想像到的事物。
|
||||
|
||||
可在 "[Minecraft Pi 入门][2]" 中了解更多相关内容。
|
||||
|
||||
### 2. 反应游戏和交通指示灯 ###
|
||||
|
||||

|
||||
|
||||
上图由 [Low Voltage Labs][3] 提供。遵循 [CC BY-SA 4.0][1] 协议。
|
||||
|
||||
在树莓派上进行物理计算是非常容易的 —— 只需将 LED 灯 和按钮连接到 GPIO 针脚上,再加上少量的代码,你就可以点亮 LED 灯并通过按按钮来控制物体。一旦你知道来执行基本操作的代码,下一步就可以随你的想像那样去做了!
|
||||
|
||||
假如你知道如何让一盏灯闪烁,你就可以让三盏灯闪烁。选出三盏交通灯颜色的 LED 灯,你就可以编程出交通灯闪烁序列。假如你知道如何使用一个按钮来触发一个事件,然后你就有一个人行横道了!同时,你还可以找到诸如 [PI-TRAFFIC][4]、[PI-STOP][5]、[Traffic HAT][6] 等预先构建好的交通灯插件。
|
||||
|
||||
这不总是关于代码的 —— 它还可以被用来作为一个的练习,用以理解真实世界中的系统是如何被设计出来的。计算思维在生活中的各种情景中都是一个有用的技能。
|
||||
|
||||

|
||||
|
||||
上图由树莓派基金会提供。遵循 [CC BY-SA 4.0][1] 协议。
|
||||
|
||||
下面尝试将两个按钮和一个 LED 灯连接起来,来制作一个二人制反应游戏 —— 让灯在一段随机的时间中点亮,然后看谁能够先按到按钮!
|
||||
|
||||
想了解更多的话,请查看 [GPIO 新手指南][7]。你所需要的尽在 [CamJam EduKit 1][8]。
|
||||
|
||||
### 3. Sense HAT 像素宠物 ###
|
||||
|
||||
Astro Pi— 一个增强版的树莓派 —将于今年 12 月(注:应该是去年的事了。)问世,但你并没有错过让你的手玩弄硬件的机会。Sense HAT 是一个用在 Astro Pi 任务中的感应器主板插件,且任何人都可以买到。你可以用它来做数据收集、科学实验、游戏或者更多。 观看下面这个由树莓派的 Carrie Anne 带来的 Gurl Geek Diaries 录像来开始一段美妙的旅程吧 —— 通过在 Sense HAT 的显示器上展现出你自己设计的一个动物像素宠物:
|
||||
|
||||
注:youtube 视频
|
||||
<iframe width="520" height="315" frameborder="0" src="https://www.youtube.com/embed/gfRDFvEVz-w" allowfullscreen=""></iframe>
|
||||
|
||||
在 "[探索 Sense HAT][9]" 中可以学到更多。
|
||||
|
||||
### 4. 红外鸟箱 ###
|
||||
|
||||

|
||||
上图由 [Low Voltage Labs][3] 提供。遵循 [CC BY-SA 4.0][1] 协议。
|
||||
|
||||
让全班所有同学都能够参与进来的一个好的练习是 —— 在一个鸟箱中沿着某些红外线放置一个树莓派和 NoIR 照相模块,这样你就可以在黑暗中观看,然后通过网络或在网络中你可以从树莓派那里获取到视频流。等鸟进入笼子,然后你就可以在不打扰到它们的情况下观察它们。
|
||||
|
||||
在这期间,你可以学习到所有关于红外和光谱的知识,以及如何用软件来调整摄像头的焦距和控制它。
|
||||
|
||||
在 "[制作一个红外鸟箱][10]" 中你可以学到更多。
|
||||
|
||||
### 5. 机器人 ###
|
||||
|
||||

|
||||
|
||||
上图由 Low Voltage Labs 提供。遵循 [CC BY-SA 4.0][1] 协议。
|
||||
|
||||
拥有一个树莓派,一些感应器和一个感应器控制电路板,你就可以构建你自己的机器人。你可以制作各种类型的机器人,从用透明胶带和自制底盘组合在一起的简易四驱车,一直到由游戏控制器驱动的具有自我意识,带有传感器和摄像头的金属马儿。
|
||||
|
||||
学习如何直接去控制单个的发动机,例如通过 RTK Motor Controller Board (£8/$12),或者尝试新的 CamJam robotics kit (£17/$25) ,它带有发动机、轮胎和一系列的感应器 — 这些都很有价值并很有学习的潜力。
|
||||
|
||||
另外,如何你喜欢更为骨灰级别的东西,可以尝试 PiBorg 的 [4Borg][11] (£99/$150) 或 [DiddyBorg][12] (£180/$273) 或者一干到底,享受他们的 DoodleBorg 金属版 (£250/$380) — 并构建一个他们声名远扬的 [DoodleBorg tank][13](很不幸的时,这个没有卖的) 的迷你版。
|
||||
|
||||
另外请参考 [CamJam robotics kit worksheets][14]。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/education/15/12/5-great-raspberry-pi-projects-classroom
|
||||
|
||||
作者:[Ben Nuttall][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/bennuttall
|
||||
[1]:https://creativecommons.org/licenses/by-sa/4.0/
|
||||
[2]:https://opensource.com/life/15/5/getting-started-minecraft-pi
|
||||
[3]:http://lowvoltagelabs.com/
|
||||
[4]:http://lowvoltagelabs.com/products/pi-traffic/
|
||||
[5]:http://4tronix.co.uk/store/index.php?rt=product/product&product_id=390
|
||||
[6]:https://ryanteck.uk/hats/1-traffichat-0635648607122.html
|
||||
[7]:http://pythonhosted.org/gpiozero/recipes/
|
||||
[8]:http://camjam.me/?page_id=236
|
||||
[9]:https://opensource.com/life/15/10/exploring-raspberry-pi-sense-hat
|
||||
[10]:https://www.raspberrypi.org/learning/infrared-bird-box/
|
||||
[11]:https://www.piborg.org/4borg
|
||||
[12]:https://www.piborg.org/diddyborg
|
||||
[13]:https://www.piborg.org/doodleborg
|
||||
[14]:http://camjam.me/?page_id=1035#worksheets
|
||||
@ -1,156 +0,0 @@
|
||||
如何在Linux上使用Gmail SMTP服务器发送邮件通知
|
||||
================================================================================
|
||||
假定你想配置一个Linux app从你的服务器或桌面客户端发送邮件信息。邮件信息可以是邮件简报、状态更新(比如[Cachet][1])、监控警报(比如[Monit][2])、磁盘时间(比如[RAID mdadm][3])等等的一部分。当你要建立自己的[邮件发送服务器][4],作为一个免维护的选择,你可以依赖一个免费可用的公共SMTP服务器。
|
||||
|
||||
最可靠的**免费SMTP服务器**之一来自谷歌的Gmail服务。为了在你的app里发送邮件通知,你仅需在app中添加Gmail的SMTP服务器地址和你的凭证即可。
|
||||
|
||||
Gmail的SMTP服务器吸引人的地方之一是有各种各样恰当的限制,这些限制主要用于阻止那些经常滥用服务器的滥发垃圾邮件者和邮件营销者。举个例子,你一次只能给至多100个地址发送信息,并且一天不能超过500个接收者。当你达到任何一个限制,你的Gmail账户将暂时锁一天。简而言之,Gmail的SMTP服务器对于你个人的使用是非常棒的,但不适合商业的批量邮件。
|
||||
|
||||
话虽如此,让我们展示**如何在Linux环境下使用Gmail的SMTP服务器**。
|
||||
|
||||
### Google Gmail SMTP服务器设置 ###
|
||||
|
||||
如果你想要使用Gmail的SMTP服务器从你的app发送邮件,请牢记接下来的详细说明。
|
||||
|
||||
- **邮件发送服务器 (SMTP服务器)**: smtp.gmail.com
|
||||
- **使用认证**: 是
|
||||
- **使用安全连接**: 是
|
||||
- **用户名**: 你的Gmail账户ID (比如 "alice" 如果你的邮箱为alice@gmail.com)
|
||||
- **密码**: 你的Gmail密码
|
||||
- **端口**: 587
|
||||
|
||||
确切的配置语法可能要依据app而不同。在本教程的剩下部分,我将会向你展示各种在Linux上使用Gmail SMTP服务器的有用示例。
|
||||
|
||||
### 从命令行发送邮件 ###
|
||||
|
||||
作为第一个例子,让我们尝试最基本的邮件功能:使用Gmail SMTP服务器从命令行发送一封邮件。为此,我将使用一个称为mutt的命令行邮件客户端。
|
||||
|
||||
先安装mutt:
|
||||
|
||||
对于 Debian-based 系统:
|
||||
|
||||
$ sudo apt-get install mutt
|
||||
|
||||
对于 Red Hat based 系统:
|
||||
|
||||
$ sudo yum install mutt
|
||||
|
||||
创建一个mutt配置文件(~/.muttrc),并和下面一样,在文件中指定Gmail SMTP服务器信息。将gmail-id替换成自己的Gmail ID。注意这配置只是为了发送邮件而已(而非接收邮件)。
|
||||
|
||||
$ vi ~/.muttrc
|
||||
|
||||
----------
|
||||
|
||||
set from = "<gmail-id>@gmail.com"
|
||||
set realname = "Dan Nanni"
|
||||
set smtp_url = "smtp://<gmail-id>@smtp.gmail.com:587/"
|
||||
set smtp_pass = "<gmail-password>"
|
||||
|
||||
现在准备使用mutt发送一封邮件:
|
||||
|
||||
$ echo "This is an email body." | mutt -s "This is an email subject" alice@yahoo.com
|
||||
|
||||
为了在一封邮件中添加一个附件,使用"-a"选项
|
||||
|
||||
$ echo "This is an email body." | mutt -s "This is an email subject" alice@yahoo.com -a ~/test_attachment.jpg
|
||||
|
||||

|
||||
|
||||
使用Gmail SMTP服务器意味着邮件显示为从你的Gmail账户发出。换句话说,一个接收者将你的Gmail地址视为发送者地址。如果你想要使用自己的域名作为邮件发送者,你需要使用Gmail SMTP转发服务。
|
||||
|
||||
### 当服务器重启时发送邮件通知 ###
|
||||
|
||||
如果你为了一些重要的网站正在运行一台[虚拟专用服务器(VPS)][5],一个建议是监视VPS的重启活动。作为一个更实用的例子,让我们研究如何在你的VPS上为每一次重启事件建立邮件通知。这里我假设你正在你的VPS上使用systemd,并向你展示如何为自动邮件通知创建一个自定义的systemd启动服务。
|
||||
|
||||
首先创建下面的脚本reboot_notify.sh,用于负责邮件通知。
|
||||
|
||||
$ sudo vi /usr/local/bin/reboot_notify.sh
|
||||
|
||||
----------
|
||||
|
||||
#!/bin/sh
|
||||
|
||||
echo "`hostname` was rebooted on `date`" | mutt -F /etc/muttrc -s "Notification on `hostname`" alice@yahoo.com
|
||||
|
||||
----------
|
||||
|
||||
$ sudo chmod +x /usr/local/bin/reboot_notify.sh
|
||||
|
||||
在这个脚本中,我使用"-F"选项,用于直到系统级的mutt配置文件位置。因此不要忘了创建/etc/muttrc文件并如前面描述填入Gmail SMTP信息。
|
||||
|
||||
现在让我们创建如下一个自定义的systemd服务。
|
||||
|
||||
$ sudo mkdir -p /usr/local/lib/systemd/system
|
||||
$ sudo vi /usr/local/lib/systemd/system/reboot-task.service
|
||||
|
||||
----------
|
||||
|
||||
[Unit]
|
||||
Description=Send a notification email when the server gets rebooted
|
||||
DefaultDependencies=no
|
||||
Before=reboot.target
|
||||
|
||||
[Service]
|
||||
Type=oneshot
|
||||
ExecStart=/usr/local/bin/reboot_notify.sh
|
||||
|
||||
[Install]
|
||||
WantedBy=reboot.target
|
||||
|
||||
一旦创建服务,便使能和启动该服务。
|
||||
|
||||
$ sudo systemctl enable reboot-task
|
||||
$ sudo systemctl start reboot-task
|
||||
|
||||
从现在起,在每次VPS重启时你将会收到一封通知邮件。
|
||||
|
||||

|
||||
|
||||
### 从服务器使用监控发送邮件通知 ###
|
||||
|
||||
作为最后一个例子,让我展示一个称为[Monit][6]的现实生活的应用程序,这是一个极其有用的服务器监控应用程序。它附有广泛的[VPS][7]监控能力(比如CPU、内存、进程、文件系统),包括邮件通知能力。
|
||||
|
||||
如果你想要接收VPS上任何事件导致的且由Monit产生的邮件通知,你可以在Monit配置文件中添加以下SMTP信息。
|
||||
|
||||
set mailserver smtp.gmail.com port 587
|
||||
username "<your-gmail-ID>" password "<gmail-password>"
|
||||
using tlsv12
|
||||
|
||||
set mail-format {
|
||||
from: <your-gmail-ID>@gmail.com
|
||||
subject: $SERVICE $EVENT at $DATE on $HOST
|
||||
message: Monit $ACTION $SERVICE $EVENT at $DATE on $HOST : $DESCRIPTION.
|
||||
|
||||
Yours sincerely,
|
||||
Monit
|
||||
}
|
||||
|
||||
# the person who will receive notification emails
|
||||
set alert alice@yahoo.com
|
||||
|
||||
这是一个因为CPU负载超载而由Monit发送的邮件通知例子。
|
||||
|
||||

|
||||
|
||||
### 总结 ###
|
||||
|
||||
正如你能想象的,像Gmail一样,有许多中不同的方式使用免费的SMTP服务器。但再次说明,请牢记免费的SMTP服务器不适用于商业用途,仅仅适用于个人项目。如果你正在任一app中使用Gmail SMTP服务器,请自由分享你的用例。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/send-email-notifications-gmail-smtp-server-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[cposture](https://github.com/cposture)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/setup-system-status-page.html
|
||||
[2]:http://xmodulo.com/server-monitoring-system-monit.html
|
||||
[3]:http://xmodulo.com/create-software-raid1-array-mdadm-linux.html
|
||||
[4]:http://xmodulo.com/mail-server-ubuntu-debian.html
|
||||
[5]:http://xmodulo.com/go/digitalocean
|
||||
[6]:http://xmodulo.com/server-monitoring-system-monit.html
|
||||
[7]:http://xmodulo.com/go/digitalocean
|
||||
@ -1,90 +0,0 @@
|
||||
2016:如何选择 Linux 桌面环境
|
||||
=============================================
|
||||
|
||||

|
||||
|
||||
Linux 创建了一个相对友好的环境,为我们提供了选择的可能。比方说,现代大多数的 Linux 发行版都提供不同桌面环境给我们来选择。在本文中,我将挑选一些你可能会在 Linux 中见到的相对较好的桌面环境来介绍。
|
||||
|
||||
## Plasma
|
||||
|
||||
我认为,[KDE’s Plasma desktop](https://www.kde.org/workspaces/plasmadesktop/) 是最高级的桌面环境 (LCTT 译注:译者认为,没有什么是最好的,只有最合适的,毕竟每个人的喜好都不可能完全相同)。它是我见过功能最完善和定制性最高的桌面环境;在用户完全自主控制方面,即使是 Mac OS X 和 Windows 也无法与之比拟。
|
||||
|
||||
我爱 Plasma,因为它自带了一个非常好的文件管理器——Dolphin。而相对应 Gnome 环境,我更喜欢 Plasma 的原因就在于文件管理器。使用 Gnome 最大的痛苦就是,它的文件管理器——Files——使我无法完成一些基本任务,比如说,批量文件重命名操作。而这个操作对我来说相当重要,因为我喜欢拍摄,但 Gnome 却让我无法批量重命名这些图像文件。而使用 Dolphin 的话,这个操作就像在公园散步一样简单。
|
||||
|
||||
而且,你可以通过插件来增强 Plasma 的功能。Plasma 有大量的基础软件,如 Krita、Kdenlive、Calligra 办公套件、digiKam、Kwrite 以及由 KDE 社区开发维护的大量应用。
|
||||
|
||||
Plasma 桌面环境唯一的缺陷就是它默认的邮件客户端——Kmail。它的设置比较困难,我希望 Kmail 设置可以配置地址簿和日历。
|
||||
|
||||
包括 openSUSE 在内的多数主流发行版多使用 Plasma 作为默认桌面。
|
||||
|
||||
## GNOME
|
||||
|
||||
[GNOME](https://www.gnome.org/) (GNU Network Object Model Environment,GNU 网络对象模型环境) 由 [Miguel de Icaza](https://en.wikipedia.org/wiki/Miguel_de_Icaza) 和 Federico Mena 在 1997 年的时候创立,这是因为 KDE 使用来 Qt 工具包,而这个工具包是使用专业许可证 (proprietary license) 发布的。和 KDE 不一样的是,GNOME 提供了大量的定制,它专注于让事情变得简单。因为 自身的简单性和易用性,GNOME 变得相当流行。而我认为 GNOME 之所以流行的原因在于,Ubuntu——使用 GNOME 作为默认桌面的主流 Linux 发行版之一——对其有着巨大的推动作用。
|
||||
|
||||
随着时代变化,GNOME 也需要作出相应的改变了。因此,开发者通过 GNOME 3 推出了 GNOME 3 Shell,从而引出它全新的设计规范。但这同时与 Canonical 的 Ubuntu 计划存在者一些冲突,所以 Canonical 为 GNOME 开发来叫做 Unity 的特有 Shell。最初,GNOME 3 Shell 因很多争议 (issues) 而困扰不已——最明显的是,升级之后会导致很多扩展无法正常工作。由于设计上的重大改版以及各种问题的出现,GNOME 便产生来很多分支,比如 Cinnamon 和 Mate 桌面。
|
||||
|
||||
也就是说,使得 GNOME 有趣的是,它针对触摸设备做了优化,所以,如果你有一台触屏笔记本电脑的话,GNOME 则是最合适你这台电脑的桌面环境。
|
||||
|
||||
在 3.18 版本中,GNOME 已经作出了一些令人印象深刻的改动。其中他们所做的最有趣的是集成了 Google Drive,用户可以把他们的 Google Drive 挂载为远程存储设备,这样就不必在使用浏览器来查看里边的文件来。我也很喜欢 GNOME 里边自带的那个优秀的邮件客户端,它带有日历和地址簿功能。尽管有这么多些优秀的特性,但它的文件管理器使我不再使用 GNOME ,因为我无法处理批量文件重命名。我会坚持使用 Plasma,一直到 GNOME 的开发者修复了这个小缺陷。
|
||||
|
||||

|
||||
|
||||
## Unity
|
||||
|
||||
从技术上来说,[Unity](https://unity.ubuntu.com/) 并不是一个桌面环境,它只是 Canonical 为 Ubuntu 开发的一个图形化 Shell。Unity 运行于 GNOME 桌面之上,并使用很多 GNOME 的应用和工具。Ubuntu 团队分支了一些 GNOME 组件,以便更好的满足 Unity 用户的需求。
|
||||
|
||||
Unity 在 Ubuntu 故事集和 Unity 8 中扮演者重要角色,Canonical 公司正在努力将电脑桌面和移动世界结合到一起。Canonical 同时还为 Unity 开发了许多的有趣技术,比如 HUD (Head-up Display,平视显示)。他们还有一种独特的技术来然用户在镜片上的某范围找到特定内容。
|
||||
|
||||
即将发行的 Ubuntu 16.04,将会搭载 Unity 8,那时候用户就可以完全体验开发者为该开源软件添加的所有特性了。其中最大的争议就是,Unity 不再集成 Amazon Ads 和其他服务。即将发行的版本,虽然 Canonical 从 Dash 移除了 Amazon ads,但却默认保证了系统的隐私性。
|
||||
|
||||
## Cinnamon
|
||||
|
||||
最初,[Cinnamon](https://en.wikipedia.org/wiki/Cinnamon_(software)) 由 [Linux Mint](http://www.linuxmint.com/) 开发 —— DistroWatch.com 上统计出来最流行的发行版。就像 Unity,Cinnamon 是 GNOME Shell 的一个分支。但最后进化为一个独立的桌面环境,这是因为 Linux Mint 的开发者分支了 GNOME 桌面中很多的组件到 Cinnamon,包括 Files ——以满足自身用户的需求。
|
||||
|
||||
由于 Linux Mint 基于普通版本的 Ubuntu,开发者仍需要去完成 Ubuntu 尚未完成的目标。结果,尽管前途光明,但 Cinnamon 却充满了 Bugs 和问题。随着 17.x 本版的发布,Linux Mint 开始移动到 Ubuntu 的 LTS 版本上,从而他们可以专注于开发 Cinnamon 的核心组件,而不必再去担心代码库。移动到 LTS 的好处是,Cinnamon 变得非常稳定并且基本没有 Bugs 出现。现在,开发者已经开始向桌面环境中添加更多的新特性来。
|
||||
|
||||
对于那些更喜欢在 GNOME 基础上有一个很好的类 Windows 用户界面的用户来说,Cinnamon 是他们最好的桌面环境。
|
||||
|
||||
## MATE Desktop
|
||||
|
||||
[MATE desktop](http://mate-desktop.com/) 同样是 GNOME 的一个分支,然而,它并不像 Cinnamon 那样由 GNOME 3 分支,而是现在已经没有人维护的 GNOME 2 代码库的一个分支。MATE desktop 中的一些开发者并不喜欢 GNOME 3 并且想要“继续坚持” GNOME 2,所以他们使用这个代码库来创建来 MATE。为避免和 GNOME 3 的冲突,他们重命名了全部的包:Nautilus 改为 Caja、Gedit 改为 Pluma 以及 Evince 改为 Atril 等。
|
||||
|
||||
尽管 MATE 延续了 GNOME 2,但这并不意味着他们使用过时的技术;相反,他们使用了更新的技术来提供一个现代的 GNOME 2 体验。
|
||||
|
||||
拥有相当高的资源效率才是 MATE 最令人印象深刻之处。你可将它运行在老旧硬件或者很少更新的强大硬件上,如树梅派 (Raspberry Pi) 或者 Chromebook Flip。使得它更有趣的是,把它运行在一些强大的硬件上,可以节省大多数的资源给其他应用,而桌面环境本身只占用很少的资源。
|
||||
|
||||
## LXQt
|
||||
|
||||
[LXQt](http://lxqt.org/) 继承了 LXDE ——最轻量级的桌面环境之一。它融合了 LXDE 和 Razor-Qt 两个开源项目。LXQt 的首个可用本版 V 0.9 发布于 2015 年。最初,开发者使用了 Qt4 但向下兼容,之后为了加快开发速度,他们移动到 Qt5 和 KDE 框架上。我也在自己的 Arch 系统上尝试使用了 LXQt,它的确是一个非常好的轻量级桌面环境。但在完全继承 LXDE 之前,LXQt 仍有一段很长的路需要走。
|
||||
|
||||
## Xfce
|
||||
|
||||
[Xfce](http://www.xfce.org/) 早于 KDE 桌面环境,它是最古老和最轻量级的桌面环境。Xfce 的最新版本是 4.15,发布于 2015 年,使用了诸如 GTK + 3 的大量的现代科技。很多发行版都使用了 Xfce 环境以满足特定需求,比如 Ubuntu Studio ——与 MATE 类似——尽量节省系统资源给其他的应用。并且,许多的著名的 Linux 发行版——包括 Manjaro Linux、PC/OS、Salix 和 Mythbuntu ——都把它作为默认桌面环境。
|
||||
|
||||
## Budgie
|
||||
|
||||
[Budgie](https://solus-project.com/budgie/) 是一个新型的桌面环境,由 Solus Linux 团队开发和维护。Solus 是一个从零开始构建的新型发行版,而 Budgie 则是它的一个核心组件。Budgie 使用了大量的 GNOME 组件,从而提供一个华丽的用户界面 (UI)。由于没有该桌面环境的更多信息,我特地联系了 Solus 的核心开发者—— Ikey Doherty。他解释说:“我们搭载了自己的桌面环境—— Budgie。与其他桌面环境不同的是,Budgie 并不是其他桌面的一个分支,它的目标是侧底融入到 GNOME 协议栈之中。它完全从零开始编写,并特意的设计来迎合 Solus 提供的体验。我们会尽可能的和 GNOME 的上游团队协同工作,修复 Bugs,并提倡和支持他们的工作”。
|
||||
|
||||
## Pantheon
|
||||
|
||||
我想,[Pantheon](https://elementary.io/) 不需要特别介绍了吧,那个优美的 elementary OS 就使用它作为桌面。类似于 Budgie,很多人都认为 Pantheon 也不是 GNOME 的一个分支。elementary OS 团队大多拥有良好的设计背景,所以他们会近距离关注每一个细节,这使得 Pantheon 成为一个非常优美的桌面环境。在某个瞬间,它可能缺少像 Plasma 等桌面中的某些特性,但开发者实际上是尽其所能的去坚持设计原则。
|
||||
|
||||

|
||||
|
||||
## 结论
|
||||
|
||||
当我写完本文后,我突然意识到来开源和 Linux 的重大好处。总有一个发行版本适合你。就像 Jon “maddog” Hall 在最近的 SCaLE 14 上说的那样:“是的,现在有 300 多个 Linux 发行版。我可以一个一个去尝试,然后坚持使用我最喜欢的那一个”。
|
||||
|
||||
所以,尽情享受 Linux 的多样性吧,最后使用最合你意的那一个。
|
||||
|
||||
------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.com/news/software/applications/881107-best-linux-desktop-environments-for-2016
|
||||
|
||||
作者:[Swapnil Bhartiya][a]
|
||||
译者:[GHLandy](https://github.com/GHLandy)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linux.com/community/forums/person/61003
|
||||
@ -1,24 +0,0 @@
|
||||
Canonical的ZFS计划将会进入Ubuntu 16.04
|
||||
=======================================================
|
||||
|
||||

|
||||
|
||||
Ubuntu开发者正在为[Ubuntu 16.04 加上支持ZFS](http://www.phoronix.com/scan.php?page=news_item&px=ZFS-For-Ubuntu-16.04) ,并且所遇的文件系统支持都已经准备就绪。
|
||||
|
||||
Ubuntu 16.04的默认安装将会继续是ext4,但是ZFS支持将会自动构建进Ubuntu发布中,模块将在需要时自动加载,zfsutils-linux是Ubuntu的一部分,并且通过Canonical对商业客户提供支持
|
||||
|
||||
对于那些对Ubuntu中的ZFS感兴趣的人,Canonical的Dustin Kirkland已经写了[一篇新的博客](http://blog.dustinkirkland.com/2016/02/zfs-is-fs-for-containers-in-ubuntu-1604.html)覆盖了一些细节及为何“ZFS是Ubuntu 16.04中为容器使用的文件系统!”
|
||||
|
||||
------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.phoronix.com/scan.php?page=news_item&px=Ubuntu-ZFS-Continues-16.04&utm_source=feedburner&utm_medium=feed&utm_campaign=Feed%3A+Phoronix+%28Phoronix%29
|
||||
|
||||
作者:[Michael Larabel][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.michaellarabel.com/
|
||||
|
||||
|
||||
@ -0,0 +1,210 @@
|
||||
[Translated] Haohong Wang
|
||||
如何在Ubuntu 15.04/CentOS 7中安装Lighttpd Web server
|
||||
=================================================================================
|
||||
Lighttpd 是一款开源Web服务器软件。Lighttpd 安全快速,符合行业标准,适配性强并且针对高配置环境进行了优化。Lighttpd因其CPU、内存占用小,针对小型CPU加载的快速适配以及出色的效率和速度而从众多Web服务器中脱颖而出。 而Lighttpd诸如FastCGI,CGI,Auth,Out-Compression,URL-Rewriting等高级功能更是那些低配置的服务器的福音。
|
||||
|
||||
以下便是在我们运行Ubuntu 15.04 或CentOS 7 Linux发行版的机器上安装Lighttpd Web服务器的简要流程。
|
||||
|
||||
### 安装Lighttpd
|
||||
|
||||
#### 使用包管理器安装
|
||||
|
||||
这里我们通过使用包管理器这种最简单的方法来安装Lighttpd。只需以sudo模式在终端或控制台中输入下面的指令即可。
|
||||
|
||||
**CentOS 7**
|
||||
|
||||
由于CentOS 7.0官方repo中并没有提供Lighttpd,所以我们需要在系统中安装额外的软件源epel repo。使用下面的yum指令来安装epel。
|
||||
|
||||
# yum install epel-release
|
||||
|
||||
然后,我们需要更新系统及进程为Lighttpd的安装做准备。
|
||||
|
||||
# yum update
|
||||
# yum install lighttpd
|
||||
|
||||

|
||||
|
||||
**Ubuntu 15.04**
|
||||
|
||||
Ubuntu 15.04官方repo中包含了Lighttpd,所以只需更新本地repo并使用apt-get指令即可安装Lighttpd。
|
||||
|
||||
# apt-get update
|
||||
# apt-get install lighttpd
|
||||
|
||||

|
||||
|
||||
#### 从源代码安装Lighttpd
|
||||
|
||||
如果想从Lighttpd源码安装最新版本(例如1.4.39),我们需要在本地编译源码并进行安装。首先我们要安装编译源码所需的依赖包。
|
||||
|
||||
# cd /tmp/
|
||||
# wget http://download.lighttpd.net/lighttpd/releases-1.4.x/lighttpd-1.4.39.tar.gz
|
||||
|
||||
下载完成后,执行下面的指令解压缩。
|
||||
|
||||
# tar -zxvf lighttpd-1.4.39.tar.gz
|
||||
|
||||
然后使用下面的指令进行编译。
|
||||
|
||||
# cd lighttpd-1.4.39
|
||||
# ./configure
|
||||
# make
|
||||
|
||||
**注:**在这份教程中,我们安装的是默认配置的Lighttpd。其他诸如高级功能或拓展功能,如对SSL的支持,mod_rewrite,mod_redirect等,需自行配置。
|
||||
|
||||
当编译完成后,我们就可以把它安装到系统中了。
|
||||
|
||||
# make install
|
||||
|
||||
### 设置Lighttpd
|
||||
|
||||
如果有更高的需求,我们可以通过修改默认设置文件,如`/etc/lighttpd/lighttpd.conf`,来对Lighttpd进行进一步设置。 而在这份教程中我们将使用默认设置,不对设置文件进行修改。如果你曾做过修改并想检查设置文件是否出错,可以执行下面的指令。
|
||||
|
||||
# lighttpd -t -f /etc/lighttpd/lighttpd.conf
|
||||
|
||||
#### 使用 CentOS 7
|
||||
|
||||
在CentOS 7中,我们需在Lighttpd默认设置中创设一个例如`/src/www/htdocs`的webroot文件夹。
|
||||
|
||||
# mkdir -p /srv/www/htdocs/
|
||||
|
||||
而后将默认欢迎页面从`/var/www/lighttpd`复制至刚刚新建的目录中:
|
||||
|
||||
# cp -r /var/www/lighttpd/* /srv/www/htdocs/
|
||||
|
||||
### 开启服务
|
||||
|
||||
现在,通过执行systemctl指令来重启数据库服务。
|
||||
|
||||
# systemctl start lighttpd
|
||||
|
||||
然后我们将它设置为伴随系统启动自动运行。
|
||||
|
||||
# systemctl enable lighttpd
|
||||
|
||||
### 设置防火墙
|
||||
|
||||
如要让我们运行在Lighttpd上的网页和网站能在Internet或相似的网络上被访问,我们需要在防火墙程序中设置打开80端口。由于CentOS 7和Ubuntu15.04都附带Systemd作为默认初始化系统,所以我们安装firewalld作为解决方案。如果要打开80端口或http服务,我们只需执行下面的命令:
|
||||
|
||||
# firewall-cmd --permanent --add-service=http
|
||||
success
|
||||
# firewall-cmd --reload
|
||||
success
|
||||
|
||||
### 连接至Web Server
|
||||
在将80端口设置为默认端口后,我们就可以默认直接访问Lighttpd的欢迎页了。我们需要根据运行Lighttpd的设备来设置浏览器的IP地址和域名。在本教程中,我们令浏览器指向 [http://lighttpd.linoxide.com/](http://lighttpd.linoxide.com/) 同时将子域名指向它的IP地址。如此一来,我们就可以在浏览器中看到如下的欢迎页面了。
|
||||
|
||||

|
||||
|
||||
此外,我们可以将网站的文件添加到webroot目录下,并删除lighttpd的默认索引文件,使我们的静态网站链接至互联网上。
|
||||
|
||||
如果想在Lighttpd Web Server中运行PHP应用,请参考下面的步骤:
|
||||
|
||||
### 安装PHP5模块
|
||||
在Lighttpd成功安装后,我们需要安装PHP及相关模块以在Lighttpd中运行PHP5脚本。
|
||||
|
||||
#### 使用 Ubuntu 15.04
|
||||
|
||||
# apt-get install php5 php5-cgi php5-fpm php5-mysql php5-curl php5-gd php5-intl php5-imagick php5-mcrypt php5-memcache php-pear
|
||||
|
||||
#### 使用 CentOS 7
|
||||
|
||||
# yum install php php-cgi php-fpm php-mysql php-curl php-gd php-intl php-pecl-imagick php-mcrypt php-memcache php-pear lighttpd-fastcgi
|
||||
|
||||
### 设置Lighttpd的PHP服务
|
||||
|
||||
如要让PHP与Lighttpd协同工作,我们只要根据所使用的发行版执行如下对应的指令即可。
|
||||
|
||||
#### 使用 CentOS 7
|
||||
|
||||
首先要做的便是使用文件编辑器编辑php设置文件(例如`/etc/php.ini`)并取消掉对**cgi.fix_pathinfo=1**的注释。
|
||||
|
||||
# nano /etc/php.ini
|
||||
|
||||
完成上面的步骤之后,我们需要把PHP-FPM进程的所有权从Apache转移至Lighttpd。要完成这些,首先用文件编辑器打开`/etc/php-fpm.d/www.conf`文件。
|
||||
|
||||
# nano /etc/php-fpm.d/www.conf
|
||||
|
||||
然后在文件中增加下面的语句:
|
||||
|
||||
user = lighttpd
|
||||
group = lighttpd
|
||||
|
||||
做完这些,我们保存并退出文本编辑器。然后从`/etc/lighttpd/modules.conf`设置文件中添加FastCGI模块。
|
||||
|
||||
# nano /etc/lighttpd/modules.conf
|
||||
|
||||
然后,去掉下面语句前面的`#`来取消对它的注释。
|
||||
|
||||
include "conf.d/fastcgi.conf"
|
||||
|
||||
最后我们还需在文本编辑器设置FastCGI的设置文件。
|
||||
|
||||
# nano /etc/lighttpd/conf.d/fastcgi.conf
|
||||
|
||||
在文件尾部添加以下代码:
|
||||
|
||||
fastcgi.server += ( ".php" =>
|
||||
((
|
||||
"host" => "127.0.0.1",
|
||||
"port" => "9000",
|
||||
"broken-scriptfilename" => "enable"
|
||||
))
|
||||
)
|
||||
|
||||
在编辑完成后保存并退出文本编辑器即可。
|
||||
|
||||
#### 使用 Ubuntu 15.04
|
||||
|
||||
如需启用Lighttpd的FastCGI,只需执行下列代码:
|
||||
|
||||
# lighttpd-enable-mod fastcgi
|
||||
|
||||
Enabling fastcgi: ok
|
||||
Run /etc/init.d/lighttpd force-reload to enable changes
|
||||
|
||||
# lighttpd-enable-mod fastcgi-php
|
||||
|
||||
Enabling fastcgi-php: ok
|
||||
Run `/etc/init.d/lighttpd` force-reload to enable changes
|
||||
|
||||
然后,执行下列命令来重启Lighttpd。
|
||||
|
||||
# systemctl force-reload lighttpd
|
||||
|
||||
### 检测PHP工作状态
|
||||
|
||||
如需检测PHP是否按预期工作,我们需在Lighttpd的webroot目录下新建一个php文件。本教程中,在Ubuntu下/var/www/html 目录,CentOS下/src/www/htdocs目录下使用文本编辑器创建并打开info.php。
|
||||
|
||||
**使用 CentOS 7**
|
||||
|
||||
# nano /var/www/info.php
|
||||
|
||||
**使用 Ubuntu 15.04**
|
||||
|
||||
# nano /srv/www/htdocs/info.php
|
||||
|
||||
然后只需将下面的语句添加到文件里即可。
|
||||
|
||||
<?php phpinfo(); ?>
|
||||
|
||||
在编辑完成后保存并推出文本编辑器即可。
|
||||
|
||||
现在,我们需根据路径 [http://lighttpd.linoxide.com/info.php](http://lighttpd.linoxide.com/info.php) 下的info.php文件的IP地址或域名,来让我们的网页浏览器指向系统上运行的Lighttpd。如果一切都按照以上说明进行,我们将看到如下图所示的PHP页面信息。
|
||||
|
||||

|
||||
|
||||
### 总结
|
||||
|
||||
至此,我们已经在CentOS 7和Ubuntu 15.04 Linux 发行版上成功安装了轻巧快捷并且安全的Lighttpd Web服务器。现在,我们已经可以利用Lighttpd Web服务器来实现上传网站文件到网站根目录,配置虚拟主机,启用SSL,连接数据库,运行Web应用等功能了。 如果你有任何疑问,建议或反馈请在下面的评论区中写下来以让我们更好的改良Lighttpd。谢谢!(译注:评论网址 http://linoxide.com/linux-how-to/setup-lighttpd-web-server-ubuntu-15-04-centos-7/ )
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-how-to/setup-lighttpd-web-server-ubuntu-15-04-centos-7/
|
||||
|
||||
作者:[Arun Pyasi][a]
|
||||
译者:[HaohongWANG](https://github.com/HaohongWANG)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linoxide.com/author/arunp/
|
||||
Loading…
Reference in New Issue
Block a user