mirror of
https://github.com/LCTT/TranslateProject.git
synced 2024-12-29 21:41:00 +08:00
commit
114aee6cea
@ -1,39 +0,0 @@
|
|||||||
Translating----------geekpi
|
|
||||||
|
|
||||||
|
|
||||||
Canonical Closes nginx Exploit in Ubuntu 14.04 LTS
|
|
||||||
================================================================================
|
|
||||||
> Users have to upgrade their systems to fix the issue
|
|
||||||
|
|
||||||
|
|
||||||
|
|
||||||
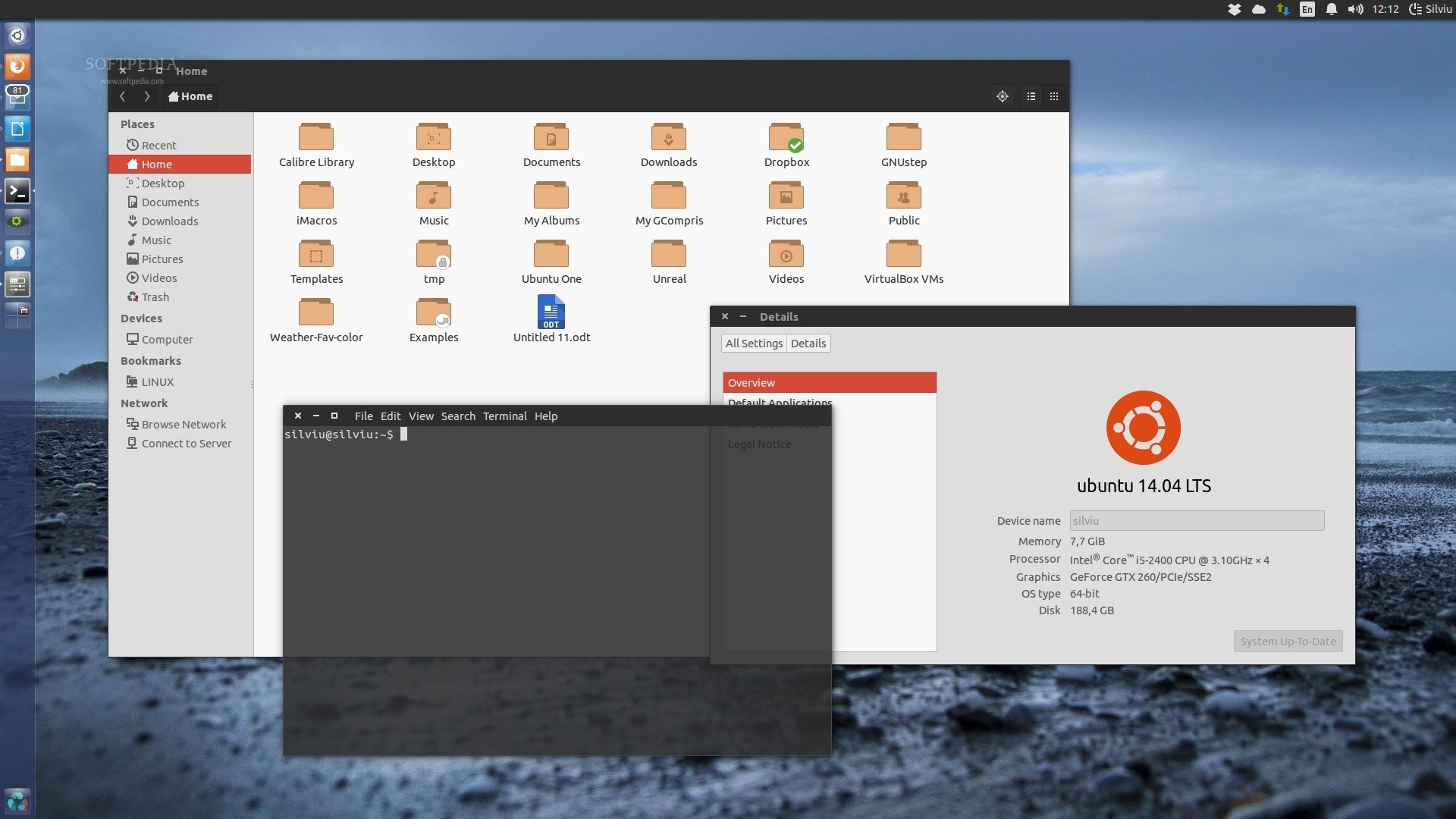
Ubuntu 14.04 LTS
|
|
||||||
|
|
||||||
**Canonical has published details in a security notice about an nginx vulnerability that affected Ubuntu 14.04 LTS (Trusty Tahr). The problem has been identified and fixed.**
|
|
||||||
|
|
||||||
The Ubuntu developers have fixed a small nginx exploit. They explain that nginx could have been made to expose sensitive information over the network.
|
|
||||||
|
|
||||||
According to the security notice, “Antoine Delignat-Lavaud and Karthikeyan Bhargavan discovered that nginx incorrectly reused cached SSL sessions. An attacker could possibly use this issue in certain configurations to obtain access to information from a different virtual host.”
|
|
||||||
|
|
||||||
For a more detailed description of the problems, you can see Canonical's security [notification][1]. Users should upgrade their Linux distribution in order to correct this issue.
|
|
||||||
|
|
||||||
The problem can be repaired by upgrading the system to the latest nginx package (and dependencies). To apply the patch, you can simply run the Update Manager application.
|
|
||||||
|
|
||||||
If you don't want to use the Software Updater, you can open a terminal and enter the following commands (you will need to be root):
|
|
||||||
|
|
||||||
sudo apt-get update
|
|
||||||
sudo apt-get dist-upgrade
|
|
||||||
|
|
||||||
In general, a standard system update will make all the necessary changes. You don't have to restart the PC in order to implement this fix.
|
|
||||||
--------------------------------------------------------------------------------
|
|
||||||
|
|
||||||
via: http://news.softpedia.com/news/Canonical-Closes-Nginx-Exploit-in-Ubuntu-14-04-LTS-459677.shtml
|
|
||||||
|
|
||||||
作者:[Silviu Stahie][a]
|
|
||||||
译者:[译者ID](https://github.com/译者ID)
|
|
||||||
校对:[校对者ID](https://github.com/校对者ID)
|
|
||||||
|
|
||||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
|
||||||
|
|
||||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
|
||||||
[1]:http://www.ubuntu.com/usn/usn-2351-1/
|
|
||||||
@ -0,0 +1,37 @@
|
|||||||
|
Canonical在Ubuntu 14.04 LTS中关闭了一个nginx漏洞
|
||||||
|
================================================================================
|
||||||
|
> 用户不得不升级他们的系统来修复这个漏洞
|
||||||
|
|
||||||
|

|
||||||
|
|
||||||
|
Ubuntu 14.04 LTS
|
||||||
|
|
||||||
|
**Canonical已经在安全公告中公布了这个影响到Ubuntu 14.04 LTS (Trusty Tahr)的nginx漏洞的细节。这个问题已经被确定并被修复了**
|
||||||
|
|
||||||
|
Ubuntu的开发者已经修复了nginx的一个小漏洞。他们解释nginx可能已经被用来暴露网络上的敏感信息。
|
||||||
|
|
||||||
|
|
||||||
|
根据安全公告,“Antoine Delignat-Lavaud和Karthikeyan Bhargavan发现nginx错误地重复使用了缓存的SSL会话。攻击者可能利用此问题,在特定的配置下,可以从不同的虚拟主机获得信息“。
|
||||||
|
|
||||||
|
对于这些问题的更详细的描述,可以看到Canonical的安全[公告][1]。用户应该升级自己的Linux发行版以解决此问题。
|
||||||
|
|
||||||
|
这个问题可以通过在系统升级到最新nginx包(和依赖v包)进行修复。要应用该补丁,你可以直接运行升级管理程序。
|
||||||
|
|
||||||
|
如果你不想使用软件更新器,您可以打开终端,输入以下命令(需要root权限):
|
||||||
|
|
||||||
|
sudo apt-get update
|
||||||
|
sudo apt-get dist-upgrade
|
||||||
|
|
||||||
|
在一般情况下,一个标准的系统更新将会进行必要的更改。要应用此修补程序您不必重新启动计算机。
|
||||||
|
--------------------------------------------------------------------------------
|
||||||
|
|
||||||
|
via: http://news.softpedia.com/news/Canonical-Closes-Nginx-Exploit-in-Ubuntu-14-04-LTS-459677.shtml
|
||||||
|
|
||||||
|
作者:[Silviu Stahie][a]
|
||||||
|
译者:[geekpi](https://github.com/geekpi)
|
||||||
|
校对:[校对者ID](https://github.com/校对者ID)
|
||||||
|
|
||||||
|
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||||
|
|
||||||
|
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||||
|
[1]:http://www.ubuntu.com/usn/usn-2351-1/
|
||||||
Loading…
Reference in New Issue
Block a user