mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-27 02:30:10 +08:00
commit
0f79c28187
.gitignoreREADME.md
published
20140901 How to use on-screen virtual keyboard on Linux.md20140910 How to create a cloud-based encrypted file system on Linux.md20141004 Practical Lessons in Peer Code Review.md20141009 How to set up RAID 10 for high performance and fault tolerant disk I or O on Linux.md20141017 How to verify the authenticity and integrity of a downloaded file on Linux.md20141017 Linux ss Tool to Identify Sockets or Network Connections with Examples.md20141017 UbuTricks--Script to install the latest versions of several games and applications in Ubuntu.md20141021 How to create and use Python CGI scripts.md20141022 Linux FAQs with Answers--How to fix sshd error--could not load host key.md20141023 What is a good command-line calculator on Linux.md20141030 How to run SQL queries against Apache log files on Linux.md20141118 Linux FAQs with Answers--How to convert a text file to PDF format on Linux.md20141119 How To Make Raspberry Pi Boot In To GUI By Default.md20141119 Qshutdown--An avanced shutdown tool.md20141119 When Microsoft Went A-Courting.md20141124 15 pwd (Print Working Directory) Command Examples in Linux.md20141125 Linux FAQs with Answers--How to access a NAT guest from host with VirtualBox.md20141125 Linux FAQs with Answers--How to fix ImportError--No module named scapy.all.md20141127 What Makes a Good Programmer.md20141204 Official Ubuntu 14.10 Utopic Unicorn T-Shirts Now Available to Buy.md20141208 Linux FAQs with Answers--How to crop an image from the command line on Linux.md20141208 Nathive--A libre software image editor.md
sources
news
20141204 After an 18 Month Gap, Opera for Linux Returns With New Stable Release.md20141204 Firefox 34 Arrives with Plugin-Free Video Calling and Powerful WebIDE.md20141204 From Mint to Trisquel--The Top Linux Distro Releases in November 2014.md20141204 Readers' Choice Awards 2014--Linux Journal.md20141205 Linus Torvalds Thanks Microsoft for a Great Black Friday Monitor Deal.md20141208 U.S. Marine Corps Wants to Change OS for Radar System from Windows XP to Linux.md20141211 Apparently This Trojan Virus May Have Infected Linux Systems For Years.md20141211 Turla espionage operation infects Linux systems with malware.md20141211 Yes, This Trojan Infects Linux. No, It' s Not The Tuxpocalypse.md
share
20141120 5 Best Open Source Web Browser Security Apps.md20141127 11 Useful Utilities To Supercharge Your Ubuntu Experience.md20141127 Five Magnificent Linux Music Streaming Clients.md20141204 Intense Gameplay--Try these 13 Roguelike games.md20141211 NetHack.md
talk
20141119 When Microsoft Went A-Courting.md20141125 Four ways Linux is headed for no-downtime kernel patching.md20141203 Docker--Present and Future.md20141204 CoreOS breaks with Docker.md20141205 CoreOS Team Develops Rocket, Breaks with Docker.md20141205 Interview--Apache Software Foundation Elevates Drill to Top-Level Project.md20141211 Open source all over the world.md20141211 Was 2014 The Year of Linux Desktop.md
tech
20140901 How to use on-screen virtual keyboard on Linux.md20141029 How to Install and Setup My Weather Indicator in Ubuntu 14.10.md20141114 How To Use Emoji Anywhere With Twitter's Open Source Library.md20141203 Undelete Files on Linux Systems.md20141204 Linux Namespaces.md20141205 How To Create A Bootable Ubuntu USB Drive For Mac In OS X.md20141205 How to configure a syslog server with rsyslog on Linux.md20141205 How to create a custom backup plan for Debian with backupninja.md20141210 How to create a custom backup plan for Debian with backupninja.md20141211 How to Setup Bind Chroot DNS Server on CentOS 7.0 VPS.md20141211 How to use matplotlib for scientific plotting on Linux.md
translated
news
share
20141120 5 Best Open Source Web Browser Security Apps.md20141127 Five Magnificent Linux Music Streaming Clients.md20141208 Getting Started With Ubuntu 14.04 (PDF Guide).md
talk
tech
20141029 How to Install and Setup My Weather Indicator in Ubuntu 14.10.md20141204 How To Delete Oracle 11g Database Manually.md20141204 How To Drop Database In Oracle 11 Without Using DBCA.md20141204 How To Run Linux Programs From The Terminal In Background Mode.md20141204 The Easy Way to Keep Track of Multiple Time Zones in Ubuntu.md20141205 10 free Commands to Check Memory Usage in Linux.md20141205 Find Out Network Adapters Available In Ubuntu Linux.md20141205 What is a good free control panel for VPS.md20141208 Install Jetty 9 (Java servlet engine and webserver) on Ubuntu 14.10 Server.md20141208 Linux FAQs with Answers--How to disable Apport internal error reporting on Ubuntu.md20141210 How to configure rsyslog client for remote logging on CentOS.md20141210 How to use Evernote from the command line on Linux.md
1
.gitignore
vendored
1
.gitignore
vendored
@ -2,3 +2,4 @@
|
||||
members.md
|
||||
*.html
|
||||
*.bak
|
||||
.DS_Store
|
||||
|
||||
73
README.md
73
README.md
@ -40,6 +40,8 @@ LCTT的组成
|
||||
- CORE [geekpi](https://github.com/geekpi),
|
||||
- CORE [GOLinux](https://github.com/GOLinux),
|
||||
- CORE [reinoir](https://github.com/reinoir),
|
||||
- CORE [bazz2](https://github.com/bazz2),
|
||||
- CORE [zpl1025](https://github.com/zpl1025),
|
||||
- Senior [tinyeyeser](https://github.com/tinyeyeser),
|
||||
- Senior [vito-L](https://github.com/vito-L),
|
||||
- Senior [jasminepeng](https://github.com/jasminepeng),
|
||||
@ -47,66 +49,73 @@ LCTT的组成
|
||||
- Senior [vizv](https://github.com/vizv),
|
||||
- [runningwater](https://github.com/runningwater),
|
||||
- [luoxcat](https://github.com/Luoxcat),
|
||||
- [bazz2](https://github.com/bazz2),
|
||||
- [Vic020](https://github.com/Vic020),
|
||||
- [alim0x](https://github.com/alim0x),
|
||||
- [KayGuoWhu](https://github.com/KayGuoWhu),
|
||||
- [zpl1025](https://github.com/zpl1025),
|
||||
- [blueabysm](https://github.com/blueabysm),
|
||||
- [flsf](https://github.com/flsf),
|
||||
- [crowner](https://github.com/crowner),
|
||||
- [Linux-pdz](https://github.com/Linux-pdz),
|
||||
- [Linchenguang](https://github.com/Linchenguang),
|
||||
- [linuhap](https://github.com/linuhap),
|
||||
- [alim0x](https://github.com/alim0x),
|
||||
- [ZTinoZ](https://github.com/ZTinoZ),
|
||||
- [2q1w2007](https://github.com/2q1w2007),
|
||||
- [flsf](https://github.com/flsf),
|
||||
- [blueabysm](https://github.com/blueabysm),
|
||||
- [barney-ro](https://github.com/barney-ro),
|
||||
- [su-kaiyao](https://github.com/su-kaiyao),
|
||||
- [crowner](https://github.com/crowner),
|
||||
- [Linchenguang](https://github.com/Linchenguang),
|
||||
- [Linux-pdz](https://github.com/Linux-pdz),
|
||||
- [linuhap](https://github.com/linuhap),
|
||||
- [yechunxiao19](https://github.com/yechunxiao19),
|
||||
- [woodboow](https://github.com/woodboow),
|
||||
- [su-kaiyao](https://github.com/su-kaiyao),
|
||||
- [SPccman](https://github.com/SPccman),
|
||||
- [disylee](https://github.com/disylee),
|
||||
- [cvsher](https://github.com/cvsher),
|
||||
- [ThomazL](https://github.com/ThomazL),
|
||||
- [Stevearzh](https://github.com/Stevearzh),
|
||||
- [felixonmars](https://github.com/felixonmars),
|
||||
- [scusjs](https://github.com/scusjs),
|
||||
- [johnhoow](https://github.com/johnhoow),
|
||||
- [hyaocuk](https://github.com/hyaocuk),
|
||||
- [MikeCoder](https://github.com/MikeCoder),
|
||||
- [ThomazL](https://github.com/ThomazL),
|
||||
- [theo-l](https://github.com/theo-l),
|
||||
- [wangjiezhe](https://github.com/wangjiezhe),
|
||||
- [jiajia9linuxer](https://github.com/jiajia9linuxer),
|
||||
- [SteveArcher](https://github.com/SteveArcher),
|
||||
- [l3b2w1](https://github.com/l3b2w1),
|
||||
- [NearTan](https://github.com/NearTan),
|
||||
- [l3b2w1](https://github.com/l3b2w1),
|
||||
- [shipsw](https://github.com/shipsw),
|
||||
- [disylee](https://github.com/disylee),
|
||||
- [Love-xuan](https://github.com/Love-xuan),
|
||||
- [boredivan](https://github.com/boredivan),
|
||||
- [cvsher](https://github.com/cvsher),
|
||||
- [owen-carter](https://github.com/owen-carter),
|
||||
- [Love-xuan](https://github.com/Love-xuan),
|
||||
- [JonathanKang](https://github.com/JonathanKang),
|
||||
- [tenght](https://github.com/tenght),
|
||||
- [luoyutiantang](https://github.com/luoyutiantang),
|
||||
- [owen-carter](https://github.com/owen-carter),
|
||||
- [icybreaker](https://github.com/icybreaker),
|
||||
- [liuaiping](https://github.com/liuaiping),
|
||||
- [tenght](https://github.com/tenght),
|
||||
- [rogetfan](https://github.com/rogetfan),
|
||||
- [liuaiping](https://github.com/liuaiping),
|
||||
- [nd0104](https://github.com/nd0104),
|
||||
- [whatever1992](https://github.com/whatever1992),
|
||||
- [szrlee](https://github.com/szrlee),
|
||||
- [lfzark](https://github.com/lfzark),
|
||||
- [CNprober](https://github.com/CNprober),
|
||||
- [213edu](https://github.com/213edu),
|
||||
- [johnhoow](https://github.com/johnhoow),
|
||||
- [yujianxuechuan](https://github.com/yujianxuechuan),
|
||||
- [ggaaooppeenngg](https://github.com/ggaaooppeenngg),
|
||||
- [CNprober](https://github.com/CNprober),
|
||||
- [coloka](https://github.com/coloka),
|
||||
- [213edu](https://github.com/213edu),
|
||||
- [guodongxiaren](https://github.com/guodongxiaren),
|
||||
- [Tanete](https://github.com/Tanete),
|
||||
- [zzlyzq](https://github.com/zzlyzq),
|
||||
- [yujianxuechuan](https://github.com/yujianxuechuan),
|
||||
- [ailurus1991](https://github.com/ailurus1991),
|
||||
- [FineFan](https://github.com/FineFan),
|
||||
- [shaohaolin](https://github.com/shaohaolin),
|
||||
- [tomatoKiller](https://github.com/tomatoKiller),
|
||||
- [CHINAANSHE](https://github.com/CHINAANSHE),
|
||||
- [stduolc](https://github.com/stduolc),
|
||||
- [Maclauring](https://github.com/Maclauring),
|
||||
- [zsJacky](https://github.com/zsJacky),
|
||||
- [Hao-Ding](https://github.com/Hao-Ding),
|
||||
- [luoyutiantang](https://github.com/luoyutiantang),
|
||||
- [zsJacky](https://github.com/zsJacky),
|
||||
- [small-Wood](https://github.com/small-Wood),
|
||||
- [CHINAANSHE](https://github.com/CHINAANSHE),
|
||||
- [guodongxiaren](https://github.com/guodongxiaren),
|
||||
- [cereuz](https://github.com/cereuz),
|
||||
- [lijhg](https://github.com/lijhg),
|
||||
- [fbigun](https://github.com/fbigun),
|
||||
|
||||
|
||||
(更新于2014/09/09)
|
||||
(更新于2014/12/02,以Github contributors列表排名)
|
||||
|
||||
谢谢大家的支持!
|
||||
|
||||
@ -124,5 +133,7 @@ LCTT的组成
|
||||
* 2014/01/02 增加了Core Translators 成员: geekpi。
|
||||
* 2014/05/04 更换了新的QQ群:198889102
|
||||
* 2014/05/16 增加了Core Translators 成员: will.qian、vizv。
|
||||
* 2014/06/18 由于GOLinux令人惊叹的翻译速度和不错的翻译质量,升级为Core Translators 成员。
|
||||
* 2014/09/09 LCTT 一周年,做一年[总结](http://linux.cn/article-3784-1.html)。并将曾任 CORE 的成员分组为 Senior,以表彰他们的贡献。
|
||||
* 2014/06/18 由于GOLinux令人惊叹的翻译速度和不错的翻译质量,升级为Core Translators成员。
|
||||
* 2014/09/09 LCTT 一周年,做一年[总结](http://linux.cn/article-3784-1.html)。并将曾任 CORE 的成员分组为 Senior,以表彰他们的贡献。
|
||||
* 2014/10/08 提升bazz2为Core Translators成员。
|
||||
* 2014/11/04 提升zpl1025为Core Translators成员。
|
||||
@ -0,0 +1,129 @@
|
||||
如何在 Linux 中使用屏幕键盘
|
||||
================================================================================
|
||||
|
||||
屏幕键盘可以作为实体键盘输入的替代方案。在某些时候,屏幕键盘显得非常需要。 比如, 你的键盘刚好坏了;你的机器太多,没有足够的键盘;你的机器没有多余的接口来连接键盘;你是个残疾人,打字有困难;或者你正在组建基于触摸屏的信息服务站。
|
||||
|
||||
屏幕键盘也可以作为一种防范实体键盘记录器的保护手段,键盘记录器会悄悄记录按键来获取密码等敏感信息。一些网上银行页面实际上会强制你使用屏幕键盘来增强交易的安全性。
|
||||
|
||||
在 linux 中有几个可用的开源键盘软件, 比如 [GOK (Gnome 的屏幕键盘)][1],[kvkbd][2],[onboard][3],[Florence][4]。
|
||||
|
||||
我会在这个教程中集中讲解 Florence, 告诉你**如何用 Florence 设置一个屏幕键盘**。 Florence 有着布局方案灵活、输入法多样、自动隐藏等特性。作为教程的一部分,我也将会示范**如何只使用鼠标来操作 Ubuntu 桌面**。
|
||||
|
||||
### 在 Linux 中安装 Florence 屏幕键盘 ###
|
||||
|
||||
幸运的是,Florence 存在于大多数 Linux 发行版的基础仓库中。
|
||||
|
||||
在 Debian,Ubuntu 或者 Linux Mint 中:
|
||||
|
||||
$ sudo apt-get install florence
|
||||
|
||||
在 Fedora,CentOS 或者 RHEL (CentOS/RHEL 需要[EPEL 仓库][5]) 中:
|
||||
|
||||
$ sudo yum install florence
|
||||
|
||||
在 Mandriva 或者 Mageia 中:
|
||||
|
||||
$ sudo urpmi florence
|
||||
|
||||
对于 Archlinux 用户,Florence 存在于 [AUR][6] 中。
|
||||
|
||||
### 配置和加载屏幕键盘 ###
|
||||
|
||||
当你安装好 Florence 之后,你只需要简单的输入以下命令就能加载屏幕键盘:
|
||||
|
||||
$ florence
|
||||
|
||||
默认情况下,屏幕键盘总是在其他窗口的顶部,让你能够在任意活动的窗口上进行输入。
|
||||
|
||||
在键盘的左侧点击工具按键来改变 Florence 的默认配置。
|
||||
|
||||
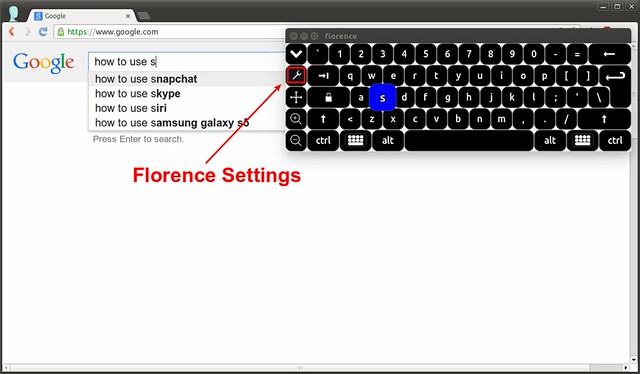
|
||||
|
||||
在 Florence 的 "样式 (style)" 菜单中,你能够自定义键盘样式,启用/取消声音效果。
|
||||
|
||||

|
||||
|
||||
在“窗口 (window)”菜单中,你能够调整键盘背景透明度、按键不透明度,以及控制键盘比例、工具栏、尺寸和总是置顶等特性。如果你的桌面分辨率不是非常高,透明度调整就显得非常有用,因为屏幕键盘会挡住其他窗口。在这个例子中,我切换到透明键盘,并且设置不透明度为 50%。
|
||||
|
||||

|
||||
|
||||
在“行为 (behaviour)”菜单中,你能够改变输入方法。Florence 支持几种不同的输入法: 鼠标 (mouse)、触摸屏 (touch screen)、计时器 (timer) 和漫步 (ramble)。鼠标输入是默认输入法。最后的两种输入法不需要按鼠标键。 计时器输入通过将指针滞留在按键上一定时间来触发按键。漫步输入的原理跟**计时器**输入差不多,但是经过训练和灵巧使用,能够比**计时器**输入更加迅速。
|
||||
|
||||

|
||||
|
||||
在“布局 (layout)”菜单中,你能够改变键盘布局。比如,你能够扩展键盘布局来增加导航键,数字键和功能键。
|
||||
|
||||

|
||||
|
||||
### 只使用鼠标来操作 Ubuntu 桌面
|
||||
|
||||
我将示范如何将 Florence 集成到 Ubuntu 桌面中,然后我们不需要实体键盘就能够进入桌面。这个教程使用 LightDM (Ubuntu 的默认显示管理器) 来进入 Ubuntu,其他桌面环境也能设置类似的环境。
|
||||
|
||||
初始设置时需要实体键盘,但是一旦设置完成,你只需要一个鼠标,而不是键盘。
|
||||
|
||||
当你启动 Ubuntu 桌面时,启动程序最后会停在显示管理器 (或者登录管理器) 的欢迎界面。在这个界面上你需要输入你的登录信息。默认的情况下,Ubuntu 桌面会使用 LightDM 显示管理器和 Unity 欢迎界面。如果没有实体键盘, 你就不能在登录界面输入用户名和密码。
|
||||
|
||||
为了能够在登录界面加载屏幕键盘,安装配备了屏幕键盘支持的 GTK+ 欢迎界面。
|
||||
|
||||
$ sudo apt-get install lightdm-gtk-greeter
|
||||
|
||||
然后用编辑器打开欢迎界面配置文件 (/etc/lightdm/lightdm-gtk-greeter.conf),指定 Florence 作为屏幕键盘来使用。如果你愿意,你也能够使用 Ubuntu 的默认屏幕键盘 onboard 来代替 Florence。
|
||||
|
||||
$ sudo vi /etc/lightdm/lightdm-gtk-greeter.conf
|
||||
|
||||
----------
|
||||
|
||||
[greeter]
|
||||
keyboard=florence --no-gnome --focus &
|
||||
|
||||

|
||||
|
||||
重启 Ubuntu 桌面,然后看看你是否能够在登录界面使用屏幕键盘。
|
||||
|
||||
启动之后当你看到 GTK+ 欢迎界面时, 点击右上角的人形符号。你会看到“使用屏幕键盘 (On Screen Keyboard)”菜单选项,如下:
|
||||
|
||||

|
||||
|
||||
点击这个选项,屏幕键盘就会在登录界面弹出。现在你应该能够用屏幕键盘来登录了。
|
||||
|
||||
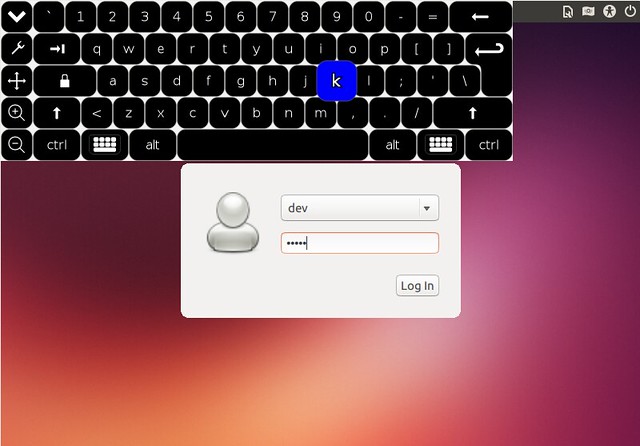
|
||||
|
||||
对于 GDM2/GDM3 用户怎么在 GDM2/GDM3 界面上使用屏幕键盘,Florence 官方网页提供了 [文档 (documentation)][7]。
|
||||
|
||||
Ubuntu 桌面完全无键盘化的最后一步是让屏幕键盘在登录后自动启动,这样我们在登录后能够不使用实体键盘就操作桌面,为了做到这一点,创建以下桌面文件:
|
||||
|
||||
$ mkdir -p ~/.config/autostart
|
||||
$ vi ~/.config/autostart/florence.desktop
|
||||
|
||||
----------
|
||||
|
||||
[Desktop Entry]
|
||||
Type=Application
|
||||
Name=Virtual Keyboard
|
||||
Comment=Auto-start virtual keyboard
|
||||
Exec=florence --no-gnome
|
||||
|
||||
这样可以让你在登录到桌面的时候就看到屏幕键盘。
|
||||
|
||||

|
||||
|
||||
希望这个教程对你有用。与你所看到的一样,Florence 是非常强大的屏幕键盘,可以用于不同目的。请和我分享你使用屏幕键盘的经验。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/08/onscreen-virtual-keyboard-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[forsil](https://github.com/forsil)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:https://developer.gnome.org/gok/
|
||||
[2]:http://homepage3.nifty.com/tsato/xvkbd/
|
||||
[3]:https://launchpad.net/onboard
|
||||
[4]:http://florence.sourceforge.net/
|
||||
[5]:http://xmodulo.com/2013/03/how-to-set-up-epel-repository-on-centos.html
|
||||
[6]:https://aur.archlinux.org/packages/florence/
|
||||
[7]:http://florence.sourceforge.net/english/how-to.html
|
||||
@ -1,6 +1,6 @@
|
||||
如何在 Linux 系统中创建一个云端的加密文件系统
|
||||
如何在 Linux 系统中创建一个云端加密文件系统
|
||||
================================================================================
|
||||
[Amazon S3][1] 和 [Google Cloud Storage][2] 之类的商业云存储服务以能承受的价格提供了高可用性、可扩展、无限容量的对象存储服务。为了加速这些云产品的广泛采用,这些提供商为他们的产品基于明确的 API 和 SDK 培养了一个良好的开发者生态系统。而基于云的文件系统便是这些活跃的开发者社区中的典型产品,已经有了好几个开源的实现。
|
||||
[Amazon S3][1] 和 [Google Cloud Storage][2] 之类的商业云存储服务以能承受的价格提供了高可用性、可扩展、无限容量的对象存储服务。为了加速这些云产品的广泛采用,这些提供商为他们的产品通过明确的 API 和 SDK 培养了一个良好的开发者生态系统。而基于云的文件系统便是这些活跃的开发者社区中的典型产品,已经有了好几个开源的实现。
|
||||
|
||||
[S3QL][3] 便是最流行的开源云端文件系统之一。它是一个基于 FUSE 的文件系统,提供了好几个商业或开源的云存储后端,比如 Amazon S3、Google Cloud Storage、Rackspace CloudFiles,还有 OpenStack。作为一个功能完整的文件系统,S3QL 拥有不少强大的功能:最大 2T 的文件大小、压缩、UNIX 属性、加密、基于写入时复制的快照、不可变树、重复数据删除,以及软、硬链接支持等等。写入 S3QL 文件系统任何数据都将首先被本地压缩、加密,之后才会传输到云后端。当你试图从 S3QL 文件系统中取出内容的时候,如果它们不在本地缓存中,相应的对象会从云端下载回来,然后再即时地解密、解压缩。
|
||||
|
||||
@ -142,7 +142,7 @@ via: http://xmodulo.com/2014/09/create-cloud-based-encrypted-file-system-linux.h
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[felixonmars](https://github.com/felixonmars)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,61 +1,64 @@
|
||||
# Peer Code Review的实战经验 #
|
||||
|
||||
(译者:Code Review中文可以翻译成代码复查,一般由开发待review的代码的成员以外的团队成员来进行这样的工作。由于是专业术语,没有将Code review用中文代替。)
|
||||
# 同等代码审查(Peer Code Review)实战经验 #
|
||||
|
||||
我有时候会听到我们的团队成员这样议论:
|
||||
|
||||
"项目的Code review 只是浪费时间。"
|
||||
|
||||
"我没有时间做Code review。"
|
||||
"我的发布时间延迟了,因为我的同时还没有完成我代码的Code review。"
|
||||
"你相信我的同事居然要求我对我的代码做修改吗?请跟他们说代码中的一些联系会被打断如果在我原来代码的基础之上做修改的话。"
|
||||
|
||||
"我的发布时间延迟了,因为我的同事还没有完成我代码的Code review。"
|
||||
|
||||
"你相信我的同事居然要求我对我的代码做修改吗?请跟他们说代码中的一些联系会被打断——如果在我原来代码的基础之上做修改的话。"
|
||||
|
||||
(LCTT 译注:Code Review中文可以翻译成代码复查,一般由开发待review的代码的成员以外的团队成员来进行这样的工作。由于是专业术语,没有将Code review用中文代替。)
|
||||
|
||||
### 为什么要做Code review? ###
|
||||
|
||||
每个专业软件开发者都有一个重要的目标:持续的提高它们的工作质量。即使你团队中都是一些优秀的程序员,你依然不能将你自己与一个有能力的自由职业者区分开来,除非你从团队的角度来工作。Code review是团队工作的一个重要的方面。尤其是:
|
||||
每个专业软件开发者都有一个重要的目标:持续的提高他们的工作质量。即使你团队中都是一些优秀的程序员,但是你依然不能将你自己与一个有能力的自由职业者区分开来,除非你从团队的角度来工作。Code review是团队工作的一个重要的方面。尤其是:
|
||||
|
||||
代码复查者(reviewer)能从他们的角度来发现问题并且提出更好的解决方案。
|
||||
|
||||
确保至少你团队的另一个其他成员熟悉你的代码,通过给新员工看有经验的开发者的代码能够某种程度上提高他们的水平。
|
||||
|
||||
公开code reviewer和reviewee的想法和经验能够促进团队间的知识的分享。
|
||||
公开reviewer和被复查者的想法和经验能够促进团队间的知识的分享。
|
||||
|
||||
能够鼓励开发者将他们的工作进行的更彻底,因为他们知道他们的代码将被其他的人阅读。
|
||||
|
||||
### 在review的过程中的注意点 ###
|
||||
|
||||
但是,由于Code review的时间有限,上面所说的目标未必能全部达到。就算只是想要打一个补丁,都要确保意图是正确的。如果只是将变量名改成骆驼拼写法(camelCase),不算是code review。在开发过程中进行结对编程是有益处的,它能够使两个人得到公平的锻炼。你能够在code review上花许多时间,并且仍然能够比在结对编程中使用更少的时间。
|
||||
但是,由于Code review的时间有限,上面所说的目标未必能全部达到。就算只是想要打一个补丁,都要确保意图是正确的。如果只是将变量名改成骆驼拼写法(camelCase),那不算是code review。在开发过程中进行结对编程是有益处的,它能够使两个人得到公平的锻炼。你能够在code review上花许多时间,并且仍然能够比在结对编程中使用更少的时间。
|
||||
|
||||
我的感受是,在项目开发的过程中,25%的时间应该花费在code review上。也就是说,如果开发者用两天的时间来开发一个东西,那么复查者应该使用至少四个小时来审查。
|
||||
|
||||
当然,只要你的review结果准确的话,具体花了多少时间就显得不是那么的重要。重要的是,你能够理解你看的那些代码。这里的理解并不是指你看懂了这些代码书写的语法,而是你要知道这段代码在整个庞大的应用程序,组件或者库中起着什么样的作用。如果你不理解每一行代码的作用,那么换句话说,你的code review就是没有价值的。这就是为什么好的code review不能很快完成的原因。需要时间来探讨各种各样的代码路径,让它们触发一个特定的函数,来确保第三方的API得到了正确的使用(包括一些边缘测试)。
|
||||
当然,只要你的review结果准确的话,具体花了多少时间就显得不是那么的重要。重要的是,你能够理解你看的那些代码。这里的理解并不是指你看懂了这些代码书写的语法,而是你要知道这段代码在整个庞大的应用程序、组件或者库中起着什么样的作用。如果你不理解每一行代码的作用,那么换句话说,你的code review就是没有价值的。这就是为什么好的code review不能很快完成的原因。需要时间来探讨各种各样的代码路径,让它们触发一个特定的函数,来确保第三方的API得到了正确的使用(包括一些边缘测试)。
|
||||
|
||||
为了查阅你所审查的代码的缺陷或者是其他问题,你应该确保:
|
||||
|
||||
所有有必要的测试都已经被包含进去。
|
||||
- 所有必要的测试都已经被包含进去。
|
||||
|
||||
合理的设计文档已经被编写。
|
||||
- 合理的设计文档已经被编写。
|
||||
|
||||
再熟练的开发者也不是每次都会记得在他们对代码改动的时候把测试程序和文档更新上去。来自reviewer的一个提醒能够使得测试用例和开发文档不会一直忘了更新。
|
||||
|
||||
### 避免code review负担太大 ###
|
||||
|
||||
如果你的团队没有强制性的code review,当你的code review记录停留在无法管理的节点上时会很危险。如果你已经两周没有进行code review了,你可以花几天的时间来跟上项目的进度。这意味着你自己的开发工作会被阻断,当你想要处理之前遗留下来的code review的时候。这也会使得你很难再确保code review的质量,因为合理的code review需要长期认真的努力。最终会很难持续几天都保持这样的状态。
|
||||
如果你的团队没有强制性的code review,当你的code review记录停留在无法管理的节点上时会很危险。如果你已经两周没有进行code review了,你可以花几天的时间来跟上项目的进度。这意味着你自己的开发工作会被阻断,当你想要处理之前遗留下来的code review的时候。这也会使得你很难再确保code review的质量,因为合理的code review需要长期认真的努力,最终会很难持续几天都保持这样的状态。
|
||||
|
||||
由于这个原因,开发者应当每天都完成他们的review任务。一种好办法就是将code review作为你每天的第一件事。在你开始自己的开发工作之前完成所有的code review工作,能够使你从头到尾都集中注意力。有些人可能更喜欢在午休前或午休后或者在傍晚下班前做review。无论你在哪个时间做,都要将code review看作你的工作之一并且不能分心,你要避免:
|
||||
|
||||
没有足够的时间来处理你的review任务。
|
||||
- 没有足够的时间来处理你的review任务。
|
||||
|
||||
由于你的code review工作没有做完导致版本的推迟发布。
|
||||
- 由于你的code review工作没有做完导致版本的推迟发布。
|
||||
|
||||
提交不在相关的review由于代码在你review期间已经改动太大。
|
||||
- 提交不再相关的review,由于代码在你review期间已经改动太大。
|
||||
|
||||
因为你要在最后一分钟完成他们一直于review质量太差。
|
||||
- 因为你要在最后一分钟完成他们,以至于review质量太差。
|
||||
|
||||
### 书写易于review的代码 ###
|
||||
|
||||
有时候review没有按时完成并不都是因为代码审查者(reviewer)。如果我的同事使用一周时间在一个大工程中添加了一些乱七八糟的代码,且他们提交的补丁实在是太难以阅读。在一段中有太多的东西要浏览。这样会让人难以理解它的作用,自然会拖慢review的进度。
|
||||
有时候review没有按时完成并不都是因为reviewer。如果我的同事使用一周时间在一个大工程中添加了一些乱七八糟的代码,且他们提交的补丁实在是太难以阅读。在一段代码中有太多的东西要浏览。这样会让人难以理解它的作用,自然会拖慢review的进度。
|
||||
|
||||
为什么将你的工作划分成一些易于管理的片段很重要有很多原因。我们使用scrum方法论(一种软件开发过程方法),因此对我们来说一个合理的单元就是一个story。通过努力将我们的工作使用story组织起来并且只是将review提交到我们正在工作的story上,这样,我们写的代码就会更加易于review。你们的可以使用其他的软件开发方法,但是目的是一样的。
|
||||
为什么将你的工作划分成一些易于管理的片段很重要有很多原因。我们使用scrum方法论(一种软件开发过程方法),因此对我们来说一个合理的单元就是一个story。通过努力将我们的工作使用story组织起来,并且只是将review提交到我们正在工作的story上,这样,我们写的代码就会更加易于review。你们也可以使用其他的软件开发方法,但是目的是一样的。
|
||||
|
||||
书写易于review的代码还有其他先决条件。如果要做一些复杂的架构决策,应该让reviewer事先知道并参与讨论。这会让他们之后review你们的代码更加容易,因为他们知道你们正在试图实现什么功能并且知道你们打算如何来实现。这也避免了开发者需要在reviewer提了一个不同的或者更好的解决方案后大片的重写代码。
|
||||
|
||||
@ -63,7 +66,7 @@
|
||||
|
||||
如果你在你的补丁中包含的第三方的代码,记得单独的提交它。当jQuery的9000行代码被插入到了项目代码的中间,毫无疑问会造成难以阅读。
|
||||
|
||||
创建易读的review代码的另一个非常重要的措施是添加相应的注释代码。这就要求你事先自己做一下review并且在一些你认为会帮助reviewer进行review的地方加上相应的注释。我发现加上注释相对与你来说往往只需要很短的时间(通常是几分钟),但是对于review来说会节约很多的时间。当然,代码注释还有其他相似的好处,应该在合理的地方使用,但往往对code review来说更重要。事实上,有研究表明,开发者在重读并注释他们代码的过程中,通常会发现很多问题。
|
||||
创建易读的review代码的另一个非常重要的措施是添加相应的注释代码。这就要求你事先自己做一下review并且在一些你认为会帮助reviewer进行review的地方加上相应的注释。我发现加上注释相对于你来说往往只需要很短的时间(通常是几分钟),但是对于review来说会节约很多的时间。当然,代码注释还有其他相似的好处,应该在合理的地方使用,但往往对code review来说更重要。事实上,有研究表明,开发者在重读并注释他们代码的过程中,通常会发现很多问题。
|
||||
|
||||
### 代码大范围重构的情况 ###
|
||||
|
||||
@ -77,16 +80,17 @@
|
||||
|
||||
你的团队中都是一些有能力的专家,在一些案例中,完全有可能因为对一个具体编码问题的意见的不同而产生争论。作为一个开发者,应该保持一个开发的头脑并且时刻准备着妥协,当你的reviewer更想要另一种解决方法时。不要对你的代码持有专有的态度,也不要自己持有审查的意见。因为有人会觉得你应该将一些重复的代码写入一个能够复用的函数中去,这并不意味着这是你的问题。
|
||||
|
||||
作为一个reviewer,要灵活。在提出修改建议之前,考虑你的建议是否真的更好或者只是无关紧要。如果你把力气和注意力花在那些原来的代码会明确需要改进的地方会更加成功。你应该说"它或许者的考虑..."或者"一些人建议..."而不是”我的宠物都能写一个比这个更加有效的排序方法"。
|
||||
作为一个reviewer,要灵活。在提出修改建议之前,考虑你的建议是否真的更好或者只是无关紧要。如果你把力气和注意力花在那些原来的代码会明确需要改进的地方会更加成功。你应该说"它或许值得考虑..."或者"一些人建议..."而不是”我的宠物都能写一个比这个更加有效的排序方法"。
|
||||
|
||||
如果你真的决定不了,那就询问另一个你和你的reviewee都尊敬的开发者来听一下你意见并给出建议。
|
||||
如果你真的决定不了,那就询问另一个你及你所审查的人都尊敬的开发者来听一下你意见并给出建议。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://blog.salsitasoft.com/practical-lessons-in-peer-code-review/
|
||||
作者:[Matt][a]
|
||||
|
||||
作者:Matt
|
||||
译者:[john](https://github.com/johnhoow)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,6 +1,7 @@
|
||||
在Linux上组成RAID 10阵列以实现高性能和高容错性的磁盘I/O
|
||||
如何在Linux上构建 RAID 10阵列
|
||||
================================================================================
|
||||
RAID 10阵列 (又名RAID 1+0 或先镜像后分区)通过结合RAID 0 (读写操作并行在多个磁盘上同时执行)和RAID 1 (数据被完全相同地写入到两个或更多的磁盘)两者的特点实现高性能和高容错性的磁盘I/O。
|
||||
|
||||
RAID 10阵列(又名RAID 1+0 或先镜像后分区)通过结合RAID 0 (读写操作在多个磁盘上同时并行执行)和RAID 1(数据被完全相同地写入到两个或更多的磁盘)两者的特点实现高性能和高容错性的磁盘I/O。
|
||||
|
||||
这篇文章会指导你如何使用五块相同的8GB磁盘来组成一个软件RAID 10阵列。因为组成一个RAID 10阵列至少需要4块磁盘(比如,两个镜像各有一对分区组合),而且需要添加一块额外的备用磁盘以防某块主要的磁盘出错。本文也会分享一些工具,在稍后用来分析RAID阵列的性能。
|
||||
|
||||
@ -12,15 +13,15 @@ RAID 10阵列 (又名RAID 1+0 或先镜像后分区)通过结合RAID 0 (读写
|
||||
|
||||
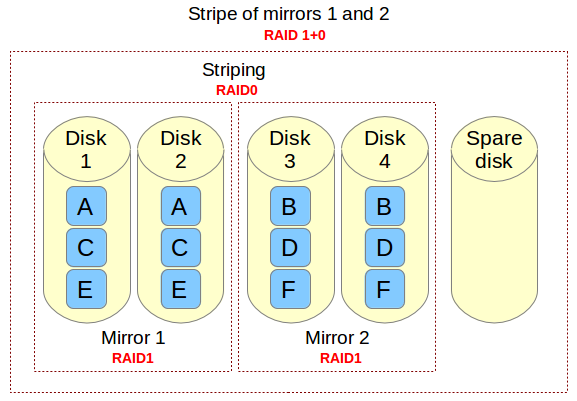
|
||||
|
||||
上图中的文件由A、B、C、D、E和F六种块组成,每一个RAID 1镜像对(如镜像1和2)在两个磁盘上复制相同的块。因为需要这样配置,写操作性能会因为每个块需要写入两次而下降,每个磁盘各一次;而读操作与从单块磁盘中读取相比并未发生改变。不过这种配置的好处是除非一个镜像中有超过一块的磁盘故障,否则都能保持冗余以维持正常的磁盘I/O操作。
|
||||
上图中的文件由A、B、C、D、E和F六种块组成,每一个RAID 1镜像对(如镜像1和2)在两个磁盘上复制相同的块。在这样的配置下,写操作性能会因为每个块需要写入两次而下降,每个磁盘各一次;而读操作与从单块磁盘中读取相比并未发生改变。不过这种配置的好处是除非一个镜像中有超过一块的磁盘故障,否则都能保持冗余以维持正常的磁盘I/O操作。
|
||||
|
||||
RAID 0的分区通过将数据划分到不同的块,然后执行同时将块A写入镜像1、将块B写入镜像2(以此类推)的并行操作以提高整体的读写性能。在另一方面,没有任何一个镜像包含构成主存的数据片的全部信息。这就意味着如果其中一个镜像故障,那么整个RAID 0组件将无法正常工作,数据将遭受不可恢复的损失。
|
||||
|
||||
### 建立RAID 10阵列 ###
|
||||
|
||||
有两种建立RAID 10阵列的可行方案:复杂法(一步完成)和嵌套法(先创建两个或更多的RAID 1阵列,然后使用它们组成RAID 0)。本文会关注复杂法创建RAID 10阵列,因为这种方法能够使用偶数或奇数个磁盘去创建阵列,而且能以单个RAID设备的形式被管理,而嵌套法则恰恰相反(只允许偶数个磁盘,必须以嵌套设备的形式被管理,即分开管理RAID 1和RAID 0)。
|
||||
有两种建立RAID 10阵列的可行方案:复杂法(一步完成)和嵌套法(先创建两个或更多的RAID 1阵列,然后使用它们组成RAID 0)。本文会讲述复杂法创建RAID 10阵列的过程,因为这种方法能够使用偶数或奇数个磁盘去创建阵列,而且能以单个RAID设备的形式被管理,而嵌套法则恰恰相反(只允许偶数个磁盘,必须以嵌套设备的形式被管理,即分开管理RAID 1和RAID 0)。
|
||||
|
||||
假设你的机器已经安装mdadm,并运行着相应的守护进程,细节参见[这篇文章][1]。也假设每个磁盘上已经划分出一个主分区sd[bcdef]1。使用命令
|
||||
假设你的机器已经安装mdadm,并运行着相应的守护进程,细节参见[这篇文章][1]。也假设每个磁盘上已经划分出一个主分区sd[bcdef]1 (LCTT 译注:共计五块磁盘,这里是从sdb - sdf)。使用命令:
|
||||
|
||||
ls -l /dev | grep sd[bcdef]
|
||||
|
||||
@ -28,7 +29,7 @@ RAID 0的分区通过将数据划分到不同的块,然后执行同时将块A
|
||||
|
||||

|
||||
|
||||
然后使用下面的命令创建一个RAID 10阵列:
|
||||
然后使用下面的命令创建一个RAID 10阵列(LCTT 译注:使用了四块磁盘 bcde 创建):
|
||||
|
||||
# mdadm --create --verbose /dev/md0 --level=10 --raid-devices=4 /dev/sd[bcde]1 --spare-devices=1 /dev/sdf1
|
||||
|
||||
@ -46,29 +47,29 @@ RAID 0的分区通过将数据划分到不同的块,然后执行同时将块A
|
||||
|
||||
1. **Used Dev Space**表示阵列所使用的每一块磁盘的容量。
|
||||
|
||||
2. **Array Size**表示阵列的整体大小。RAID 10阵列的大小通过(N*C)/M计算,其中N是活跃磁盘的数目,C是活跃磁盘的总容量,M是每一个镜像中磁盘的数目。在本文的情形下,这个值等于(4*8GiB)/2 = 16GiB。
|
||||
2. **Array Size**表示阵列的整体大小。RAID 10阵列的大小通过(N\*C)/M计算,其中N是活跃磁盘的数目,C是每个活跃磁盘的容量,M是每一个镜像中磁盘的数目。在本文的情形下,这个值等于(4*8GiB)/2 = 16GiB。
|
||||
|
||||
3. **Layout**是整个数据布局的详细信息。可能的布局数值如下所示。
|
||||
|
||||
----------
|
||||
|
||||
- **n**(默认选项):代表就近拷贝。一个数据块的多个拷贝在不同磁盘里有相同的偏移量。这种布局提供和RAID 0阵列相似的读写性能。
|
||||
- **n**(默认选项):代表就近(near)拷贝。一个数据块的多个拷贝在不同磁盘里有相同的偏移量。这种布局提供和RAID 0阵列相似的读写性能。
|
||||
|
||||

|
||||
|
||||
- **o**代表偏移量拷贝。不是复制一个分区里的块,所有的分区都被复制,但会被循环打乱,所以同一个分区中复制的块会出现在不同的磁盘。因此,一个块的后续拷贝会出现在下一个磁盘中,一个块接着一个块。为了在RAID 10阵列中使用这种布局,在创建阵列的命令中添加--layout=o2选项。
|
||||
- **o**代表偏移量(offset)拷贝。块并不是在条带里面复制的,而是整个条带一起复制,但是循环会打乱,所以同一个分区中复制的块会出现在不同的磁盘。因此,一个块的后续拷贝会出现在下一个磁盘中,一个块接着一个块。为了在RAID 10阵列中使用这种布局,在创建阵列的命令中添加--layout=o2选项。
|
||||
|
||||

|
||||
|
||||
- **f**代表远端拷贝(多个拷贝在不同的磁盘中具有不同的偏移量)。这种布局提供更好的读性能但带来更差的写性能。因此,对于读远远多于写的系统来说是最好的选择。为了在RAID 10阵列中使用这种布局,在创建阵列的命令中添加--layout=f2。
|
||||
- **f**代表远端(far)拷贝(多个拷贝在不同的磁盘中具有不同的偏移量)。这种布局提供更好的读性能但带来更差的写性能。因此,对于读远远多于写的系统来说是最好的选择。为了在RAID 10阵列中使用这种布局,在创建阵列的命令中添加--layout=f2。
|
||||
|
||||

|
||||
|
||||
跟在布局选项**n**、**f**和**o**后面的数字代表所需的每一个数据块的副本数目。默认值是2,但可以是2到阵列中磁盘数目之间的某个值。提供足够的副本数目可以最小化单个磁盘上的I/O影响。
|
||||
|
||||
4. **Chunk Size**,以[Linux RAID wiki][2]为准,是写入磁盘的最小数据单元。最佳的chunk大小取决于I/O操作的速率和相关的文件大小。对于大量的写操作,通过设置相对较大的chunks可以得到更低的开销,但对于主要存储小文件的阵列来说更小的chunk性能更好。为了给RAID 10指定一个chunk大小,在创建阵列的命令中添加**--chunk=desired_chunk_size**。
|
||||
4. **Chunk Size**,参考[Linux RAID wiki][2]的说明,是写入磁盘的最小数据单元。最佳的chunk大小取决于I/O操作的速率和相关的文件大小。对于大量的写操作,通过设置相对较大的chunk可以得到更低的开销,但对于主要存储小文件的阵列来说更小的chunk性能更好。为了给RAID 10指定一个chunk大小,在创建阵列的命令中添加**--chunk=desired_chunk_size**。
|
||||
|
||||
不幸的是,并没有设置一个大小就能适合全局的策略用来提高性能,但可以参考下面的一些方案。
|
||||
不幸的是,并没有设置一个大小就能适合全局的策略来提高性能,但可以参考下面的一些方案。
|
||||
|
||||
- 文件系统:就整体而言,[XFS][3]据说是最好的,当然EXT4也是不错的选择。
|
||||
- 最佳布局:远端布局能提高读性能,但会降低写性能。
|
||||
@ -127,7 +128,7 @@ via: http://xmodulo.com/setup-raid10-linux.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[KayGuoWhu](https://github.com/KayGuoWhu)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,19 +1,19 @@
|
||||
如何在Linux上验证下载文件的可靠性和完整性
|
||||
使用 GnuPG 加密签名来验证下载文件的可靠性和完整性
|
||||
================================================================================
|
||||
当你从网上下载一个文件后(比如:安装程序、ISO镜像或者一个压缩包),文件可能在不同的情况下发生了损坏,比如:由于线路传输错误、中断的下载、存储硬件错误、文件系统错误等等。除了这些错误,文件还可能在下载前或者下载中的攻击而被有意地篡改了。比如,一个攻破证书颁发机构的攻击者可以实施一个MITM攻击(中间人攻击),欺骗你从HTTPS网站上下载隐藏恶意软件的文件。
|
||||
|
||||
要保护你自己免受这些问题的困扰,建议你验证你从网上下载的文件的可靠性和完整性。特别是你下载了一个非常敏感的文件的时候)(比如:操作系统镜像、二进制应用程序、可执行安装包等等),盲目地相信下载的文件不是一个好习惯。
|
||||
要保护你自己免受这些问题的困扰,建议你去验证从网上下载的文件的可靠性和完整性。特别是你下载了一个非常敏感的文件的时候)(比如:操作系统镜像、二进制应用程序、可执行安装包等等),盲目地相信下载的文件不是一个好习惯。
|
||||
|
||||
一个快速和简单地验证下载文件的完整性的方法是使用不同的校验工具(比如:md5sum、sha356sum、cksum)来计算和比较校验码(比如:MD5、SHA、CRC)。然而,然而校验容易受到[碰撞攻击][1],而且同样不能用于验证文件的可靠性(比如:拥有者)。
|
||||
|
||||
integrity by using GnuPG (GNU Privacy Guard).
|
||||
|
||||
如果你想要同时验证下载文件的可靠性(拥有者)和完整性(内容),你需要依赖于加密签名。本教程中,我会描述如何使用GnuPG(GNU Privacy Guard)来检查文件的可靠性和完整性。
|
||||
|
||||
本例中我会验证一个从https://onionshare.org上下载的磁盘镜像。这个网站中,发行商会提供他们的公钥,还有它用于密钥验证的指纹。
|
||||
本例中我会验证一个从 https://onionshare.org 上下载的磁盘镜像。这个网站中,发行商会提供他们的公钥,还有它用于密钥验证的指纹。
|
||||
|
||||

|
||||
|
||||
至于下载的文件,发行上也会提供它相关的PGP签名。
|
||||
至于下载的文件,发行商也会提供它相关的PGP签名。
|
||||
|
||||
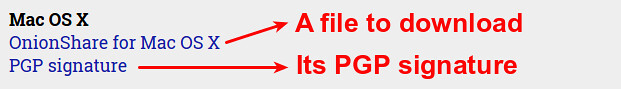
|
||||
|
||||
@ -35,7 +35,7 @@ integrity by using GnuPG (GNU Privacy Guard).
|
||||
|
||||
|
||||
|
||||
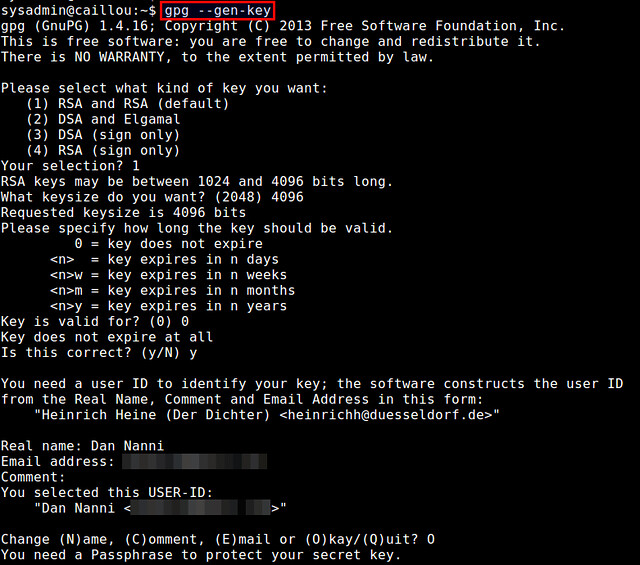
在生成中间,你会被要求提供你的姓名和email,还有保护你私钥的密码。你同样也可以在键对要过期的时候选择(默认不会过期)。依赖于你选择的key的大小(在1024和4096位之间),key生成会花上几分钟或者更多,这由于它要求收集来自你桌面活动的大量的随机数据。(比如键盘输入、鼠标移动、磁盘访问等等)。
|
||||
在生成键对期间,你会被要求提供你的姓名和email,还有保护你私钥的密码。你同样也可以选择键对何时过期(默认不会过期)。依赖于你选择的key的大小(在1024和4096位之间),key生成会花上几分钟或者更多,同时它要求收集来自你桌面活动的大量的随机数据。(比如键盘输入、鼠标移动、磁盘访问等等,所以这个时候随便动动鼠标键盘什么的)。
|
||||
|
||||
一旦key生成完毕后,公钥和私钥会存储在~/.gnupg目录。
|
||||
|
||||
@ -45,7 +45,7 @@ integrity by using GnuPG (GNU Privacy Guard).
|
||||
|
||||
验证下载文件的第一步是与任何提供文件下载的人建立信任。出于此,我们下载了这个文件的公钥,并且验证公钥的拥有者是否是他或者她自称的。
|
||||
|
||||
在下载玩文件拥有者的公钥后:
|
||||
在下载完文件拥有者的公钥后:
|
||||
|
||||
$ wget https://onionshare.org/signing-key.asc
|
||||
|
||||
@ -55,7 +55,7 @@ integrity by using GnuPG (GNU Privacy Guard).
|
||||
|
||||
|
||||
|
||||
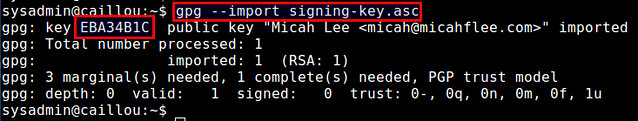
一旦拥有者的共要导入后,他会像下面那样打印出一个key ID(比如:"EBA34B1C")。记住这个key ID。
|
||||
一旦拥有者的公钥导入后,他会像下面那样打印出一个key ID(比如:"EBA34B1C")。记住这个key ID。
|
||||
|
||||
现在,运行下面的命令检查导入的公钥的指纹:
|
||||
|
||||
@ -65,7 +65,7 @@ integrity by using GnuPG (GNU Privacy Guard).
|
||||
|
||||
你会看到key的指纹字符串。把这个和网站上显示的指纹做对比。如果匹配,你可以选择信任这个文件拥有者的公钥。
|
||||
|
||||
一旦你决定相信这个公钥,你可以通过编辑key来标记它:
|
||||
一旦你决定相信这个公钥,你可以通过编辑key来设置信任级别:
|
||||
|
||||
$ gpg --edit-key EBA34B1C
|
||||
|
||||
@ -83,7 +83,7 @@ integrity by using GnuPG (GNU Privacy Guard).
|
||||
|
||||
要注意的是不需要这样明确地给一个公钥指派信任,通过key的导入隐式地信任往往就够了。
|
||||
|
||||
给一个key隐式地分配给“完全”的信任就是任何其他由这个完全信任签名的key X都会被认为是对你有效的。通常上,key验证依赖于一个复杂的机制称之为“[信任网][2]”
|
||||
给一个key隐式地分配给“完全”的信任就是任何其他由这个完全信任签名的key X都会被认为是对你有效的。通常上,key验证依赖于一个称之为“[信任网][2]”的复杂机制。
|
||||
|
||||
回到教程,现在让我们检查导入的key列表。
|
||||
|
||||
@ -97,7 +97,7 @@ integrity by using GnuPG (GNU Privacy Guard).
|
||||
|
||||
一旦你建立了与文件拥有者和他的/她的公钥之间的信任关系,我们需要验证你从拥有者那边下载的文件的可靠性和完整性了。
|
||||
|
||||
本例中,文件拥有者分别公布了一个文件和它相关的PGP签名(.asc)。签名的角色就是认证并且在文件中加入一个时间戳
|
||||
本例中,文件拥有者分别公布了一个文件和它相关的PGP签名(.asc)。签名所起的作用就是认证(文件)并且在其中加入一个时间戳。
|
||||
|
||||
一个典型的签名(*.asc)看上去像这样。
|
||||
|
||||
@ -139,7 +139,7 @@ via: http://xmodulo.com/verify-authenticity-integrity-downloaded-file.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,24 +1,25 @@
|
||||
Linux中的鉴别套接字/网络的ss工具示例
|
||||
在Linux中的使用 ss 命令检查套接字/网络连接
|
||||
================================================================================
|
||||
ss是iproute2包的一部分(控制TCP/IP网络和流量的工具)。iproute2目标是替代先前用于配置网络接口,路由表和管理ARP表的标准Unix网络工具套装(通常称之为“net-tools”)。ss工具用于导出套接字统计,它可以显示与netstat类似的信息,且可以显示更多的TCP和状态信息。它也应该更加快因为它工作与内核空间。ss的操作和netstat很像所以这让它可以很容易就可以取代。
|
||||
ss是iproute2包的一部分(控制TCP/IP网络和流量的工具)。iproute2的目标是替代先前用于配置网络接口、路由表和管理ARP表的标准Unix网络工具套装(通常称之为“net-tools”)。ss工具用于导出套接字统计,它可以显示与netstat类似的信息,且可以显示更多的TCP和状态信息。因为它直接从内核空间获取信息,所以会更快。ss的操作和netstat很像,所以这让它可以很容易就可以取代。
|
||||
|
||||
### 使用和常见选项 ###
|
||||
|
||||
ss和netstat很像,默认他会显示已经建立连接的开放的非监听TCP套接字列表。并且你可以用下面的选项过滤输出:
|
||||
ss和netstat很像,默认它会显示已经建立连接的开放的非监听TCP套接字列表。并且你可以用下面的选项过滤输出:
|
||||
|
||||
- **-n** - 尝试解析服务名。
|
||||
- **-r** - 尝试解析数字地址/端口。
|
||||
- **-n** - 不要尝试解析服务名。
|
||||
- **-r** - 尝试解析数字的地址/端口。
|
||||
- **-a** - 显示所有套接字。
|
||||
- **-l** - 显示监听套接字。
|
||||
- **-p** - 显示进程人使用的套接字。
|
||||
- **-s** - 打印统计
|
||||
- **-p** - 显示使用该套接字的进程。
|
||||
- **-s** - 打印统计数据
|
||||
- **-t** - 只显示TCP套接字。
|
||||
- **-u** - 只显示UDP套接字。
|
||||
- **-d** - 只显示DCCP套接字
|
||||
- **-w** - 只显示原始套接字。
|
||||
- **-w** - 只显示RAW套接字。
|
||||
- **-x** - 只显示Unix域套接字
|
||||
- **-f FAMILY** - 显示FAMILY套接字的类型。目前支持下面这些家族:unix、inet、inet6、link、netlink。
|
||||
- **-A QUERY** - 导出套接字列表,通过逗号分隔。可以识别下面的标识符:all、inet、tcp、udp、raw、unix、packet、netlink、unix_dgram、unix_stream、packet_raw、packet_dgram。
|
||||
- **-f FAMILY** - 显示FAMILY套接字的类型。目前支持下面这些族:unix、inet、inet6、link、netlink。
|
||||
- **-A QUERY** - 指定要列出的套接字列表,通过逗号分隔。可以识别下面的标识符:all、inet、tcp、udp、raw、unix、packet、netlink、unix_dgram、unix_stream、packet_raw、packet_dgram。
|
||||
- **-o STATUS** - 列出指定状态的套接字
|
||||
|
||||
### ss 命令示例 ###
|
||||
|
||||
@ -34,13 +35,13 @@ ss和netstat很像,默认他会显示已经建立连接的开放的非监听TC
|
||||
|
||||

|
||||
|
||||
**3.** 跟上面的行为一样,你只需用n代替t就会显示所有开放的UDP端口。
|
||||
**3.** 跟上面的行为一样,你只需用u代替t就会显示所有开放的UDP端口。
|
||||
|
||||
# ss -tnap
|
||||
# ss -unap
|
||||
|
||||

|
||||
|
||||
**4.** 你可以使用-s标志来打印不同的有用的统计:
|
||||
**4.** 你可以使用-s标志来打印各种有用的统计数据:
|
||||
|
||||
# ss -s
|
||||
|
||||
@ -58,7 +59,7 @@ via: http://linoxide.com/linux-command/ss-sockets-network-connection/
|
||||
|
||||
作者:[Adrian Dinu][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,10 +1,10 @@
|
||||
UbuTricks - 在ubuntu上安装几个最新游戏和应用的脚本
|
||||
使用 UbuTricks 在ubuntu上安装最新游戏和应用
|
||||
===
|
||||
UbuTricks是一个可以帮助你在ubuntu上安装几个最新版本的游戏和应用的程序。
|
||||
|
||||
UbuTricks是一个有简单界面,基于Zenity的图形脚本。虽然早期开发中,它的目标是通过简单的界面操作来安装Ubuntu14.04 及以后发行版上应用程序的更新。
|
||||
|
||||
应用程序会自动下载安装。一些更新可能会需要ppa。其它的将会通过编译源代码安装。编译过程可能会需要一些时间,当从ppa或者deb文件安装应该会快一点,取决于你的下载速度。
|
||||
应用程序会自动下载安装。一些更新可能会需要ppa,其它的将会通过编译源代码安装。编译过程可能会需要一些时间,当从ppa或者deb文件安装应该会快一点,取决于你的下载速度。
|
||||
|
||||
###一共有以下几种安装方式:
|
||||
|
||||
@ -29,7 +29,7 @@ UbuTricks是一个有简单界面,基于Zenity的图形脚本。虽然早期
|
||||
|
||||
- PCManFM
|
||||
|
||||
###互联网
|
||||
###互联网应用
|
||||
|
||||
- Geary
|
||||
- HexChat
|
||||
@ -86,7 +86,7 @@ via: http://www.ubuntugeek.com/ubutricks-script-to-install-the-latest-versions-o
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[DoubleShit](https://github.com/DoubleShit)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -46,7 +46,7 @@
|
||||
$ python -V
|
||||
$ python --version
|
||||
|
||||
如果你的Python CGI脚本要用来处理用户输入的数据(从一个web输入表单),然后你将需要导入Python cgi模块。这个模块可以处理用户通过web输入表单输入的数据。你可以在你的脚本中通过下面的语句导入该脚本:
|
||||
如果你的Python CGI脚本要用来处理用户输入的数据(从一个web输入表单),那么你将需要导入Python cgi模块。这个模块可以处理用户通过web输入表单输入的数据。你可以在你的脚本中通过下面的语句导入该脚本:
|
||||
|
||||
import cgi
|
||||
|
||||
@ -110,7 +110,7 @@
|
||||
</form>
|
||||
</html>
|
||||
|
||||
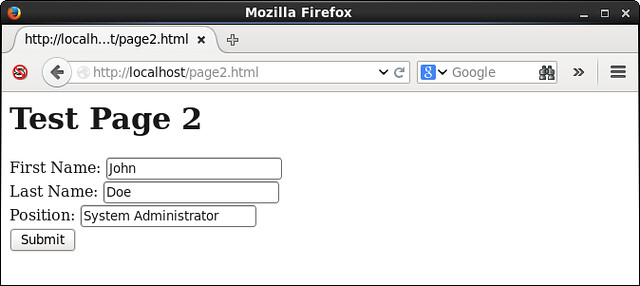
当"Submit"按钮点击,/var/www/cgi-bin/myscript-2.py脚本将被执行(通过action参数指定)。/var/www//html/page2.html显示在web浏览器中的图片如下所示(注意,三个输入域已经被填写了):
|
||||
当"Submit"按钮点击,/var/www/cgi-bin/myscript-2.py脚本将被执行(通过action参数指定)。/var/www//html/page2.html显示在web浏览器中的图片如下所示(注意,三个输入域已经被填写好了):
|
||||
|
||||
|
||||
|
||||
@ -131,7 +131,7 @@
|
||||
print "</p>"
|
||||
print "</html>"
|
||||
|
||||
正如前面提到,import cgi语句需要用来确保能够处理用户通过web输入表单输入的数据。web输入表单被封装在一个表单对象中,叫做cgi.FieldStorage对象。一旦开始,"Content-Type: text/html"是必需的,因为web服务器需要知道接受自CGI脚本的输出格式。用户输入的数据在包含form["firstName"].value,form["lastName"].value, and form["position"].value的语句中被接受。那些中括号中的名称和**/var/www/html/page2.html**文本输入域中定义的名称参数一致。
|
||||
正如前面提到,import cgi语句用来确保能够处理用户通过web输入表单输入的数据。web输入表单被封装在一个表单对象中,叫做cgi.FieldStorage对象。一旦开始输出,"Content-Type: text/html"是必需的,因为web服务器需要知道接受自CGI脚本的输出格式。用户输入的数据在包含form["firstName"].value,form["lastName"].value,和 form["position"].value的语句中可以得到。那些中括号中的名称和**/var/www/html/page2.html**文本输入域中定义的名称参数一致。
|
||||
|
||||
当网页上的"Submit"按钮被点击,下面的网页将被返回。
|
||||
|
||||
@ -149,7 +149,7 @@ via: http://xmodulo.com/create-use-python-cgi-scripts.html
|
||||
|
||||
作者:[Joshua Reed][a]
|
||||
译者:[su-kaiyao](https://github.com/su-kaiyao)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,6 +1,6 @@
|
||||
怎么样称得上是Linux下优秀的命令行计算器
|
||||
================================================================================
|
||||
每个现代的Linux桌面发行版都预装着一个带有图形界面的计算器程序。不过如果你的工作区中全是命令行窗口,那么你一定会在其中的一个命令行窗口中处理一些数字相关的问题。或许你在寻找一款基于命令行的计算器程序。如果是这样的话,[GNU bc][1](“basic calculator”的缩写)会是你不二的选择。当然Linux下又很多基于命令行的计算器应用,我认为GNU bc是功能最强大和最有用的。
|
||||
每个现代的Linux桌面发行版都预装着一个带有图形界面的计算器程序。不过如果你的工作区中全是命令行窗口,那么你一定会在其中的一个命令行窗口中处理一些数字相关的问题。或许你在寻找一款基于命令行的计算器程序。如果是这样的话,[GNU bc][1](“basic calculator”的缩写)会是你不二的选择。当然Linux下有很多基于命令行的计算器应用,我认为GNU bc是功能最强大和最有用的。
|
||||
|
||||
在GNU时代之前,bc实际上是一个著名的精密计算语言。它的诞生要追溯到70年代的Unix时期了。最初bc作为一个语法和C语言相似的编程语言而著名。随着时间的改变,最开始的bc演化成POSIX bc,最后变成了今天的GNU bc。
|
||||
|
||||
@ -8,19 +8,19 @@
|
||||
|
||||
现在的GNU bc是早期bc经过若干次改进和功能增强的结果。目前它被所有的主流GNU/Linux发行版所收纳。GNU bc支持高精度数字和多种数值类型(例如二进制、十进制、十六进制)的输入输出。
|
||||
|
||||
如果你对C语言很熟悉的话,你会发现bc使用了和C语言一样或相似的算术操作符。受支持的操作符包括算术运算符(+,-,*,/,%,++,--)、比较运算符(<,>,==,!=,<=,>=)、逻辑运算符(!,&&,||)、位运算符(&,|,^,~,<<,>>)和复合赋值运算符(+=,-=,*=,/=,%=,&=,|=,^=,&&=,||=,<<=,>>=)。bc内置了很多有用的函数,像是平方根、正弦、余弦、反正弦、自然对数、指数等。
|
||||
如果你对C语言很熟悉的话,你会发现bc使用了和C语言一样或相似的算术操作符。所支持的操作符包括算术运算符(+, -, *, /, %, ++, --)、比较运算符(<, >, ==, !=, <=, >=)、逻辑运算符(!, &&, ||)、位运算符(&, |, ^, ~, <<, >>)和复合赋值运算符(+=, -=, *=, /=, %=, &=, |=, ^=, &&=, ||=, <<=, >>=)。bc内置了很多有用的函数,像是平方根、正弦、余弦、反正弦、自然对数、指数等。
|
||||
|
||||
### 如何使用GNU bc ###
|
||||
|
||||
作为一个基于命令行的计算器,GNU bc的使用是没有限制的。在本文中,我会向大家介绍bc命令的几个常用的特性。如果你想要更加详细的指导,你可以查阅[官方指南][2]。
|
||||
作为一个基于命令行的计算器,GNU bc的使用没有限制。在本文中,我会向大家介绍bc命令的几个常用的特性。如果你想要更加详细的指导,你可以查阅[官方指南][2]。
|
||||
|
||||
如果你没有一个预先写好的bc脚本,那么你需要在交互模式下运行bc。在这种模式下,你输入的以回车结束的任何声明或者表达式会被立刻计算出结果。你需要输入以下命令来进入bc的交互界面。如果向退出bc,你可以输入'quit'并且按回车。
|
||||
如果你没有一个预先写好的bc脚本,那么你可以在交互模式下运行bc。在这种模式下,你输入的以回车结束的任何声明或者表达式会被立刻计算出结果。你需要输入以下命令来进入bc的交互界面。如果想退出bc,你可以输入'quit'并且按回车。
|
||||
|
||||
$ bc
|
||||
|
||||
|
||||
|
||||
本文下面展示的例子应该在bc交互界面中输入。
|
||||
本文下面展示的例子请在bc交互界面中输入。
|
||||
|
||||
### 输入表达式 ###
|
||||
|
||||
@ -28,15 +28,15 @@
|
||||
|
||||

|
||||
|
||||
在一个bc的交互界面中,存在没有个数限制的命令历史记录。使用上方向键来查看之前输入的命令。如果你想限制历史记录保存的命令数量,你可以将一个名为history的特殊变量设置成你希望的数值。该变量默认为-1,也就是“历史记录数量没有限制”。
|
||||
在一个bc的交互界面中,保存着没有个数限制的命令历史记录。使用上方向键来查看之前输入的命令。如果你想限制历史记录保存的命令数量,你可以将一个名为history的特殊变量设置成你希望的数值。该变量默认为-1,也就是“历史记录数量没有限制”。
|
||||
|
||||
### 输入输出进制切换 ###
|
||||
|
||||
经常会发生的是,你输入一个表达式并且想使用二进制或者十六进制来显示结果。bc允许你在输入输出数字的进制间转换。输入和输出的数系基分别存储在ibase和obase变量中,默认值为10,有效的数值是2到16(或者环境变量BC_BASE_MAX的值).你只需要更改ibase和obase的值就可以在不同进制之间转换了。下面是一个求两个十六进制/二进制数和的例子:
|
||||
经常会发生的是,你输入一个表达式并且想使用二进制或者十六进制来显示结果。bc允许你在输入输出数字的进制间转换。输入和输出的数系基分别存储在ibase和obase变量中,默认值为10,有效的数值是2到16(或者环境变量BC_BASE_MAX的值)。你只需要更改ibase和obase的值就可以在不同进制之间转换了。下面是一个求两个十六进制/二进制数和的例子:
|
||||
|
||||
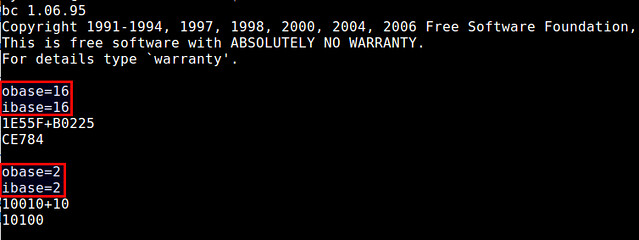
|
||||
|
||||
需要注意的是,我有意地将obase=16放到了ibase=16前面,反过来则是不可以的。这个是因为如果我先输入ibase=16,那么随后输入的obase=16中的16会被认为是16进制的数字,也就是十进制的22。当然这个不是我们所期望的。
|
||||
需要注意的是,我有意地将obase=16放到了ibase=16前面,**反过来则是不可以的**。这个是因为如果我先输入ibase=16,那么随后输入的obase=16中的16会被认为是16进制的数字,也就是十进制的22。当然这个不是我们所期望的。
|
||||
|
||||
### 调整精度 ###
|
||||
|
||||
@ -76,7 +76,7 @@ X的指数对数:
|
||||
|
||||
e(X)
|
||||
|
||||
### Other goodies as a language ###
|
||||
### 当做语言来用 ###
|
||||
|
||||
作为一个计算语言,GNU bc支持简单的声明(变量赋值、中断、返回等)、复合语句(if、while、for loop等)和自定义函数。在这里我不会涉及到这些特性的细节,不过你可以通过[官方指南][2]来学习如何使用这些特性。下面是一个简单的函数示例:
|
||||
|
||||
@ -98,7 +98,7 @@ X的指数对数:
|
||||
|
||||
|
||||
|
||||
总结以下,GNU bc是一款强大并且通用的基于命令行的计算器应用,因此它绝对不会让你失望。它预装在所有的现代Linux发行版中,bc可以让你不用离开命令行就可以进行高效的数学计算。所以,GNU bc一定会是你的最爱。
|
||||
总结一下,GNU bc是一款强大并且通用的基于命令行的计算器应用,它绝对不会让你失望。它预装在所有的现代Linux发行版中,bc可以让你不用离开命令行就可以进行高效的数学计算。所以,GNU bc一定会是你的最爱。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -106,7 +106,7 @@ via: http://xmodulo.com/command-line-calculator-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[JonathanKang](https://github.com/JonathanKang)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,32 +1,32 @@
|
||||
如何在 Linux 上针对 Apache 日志文件运行 SQL 查询语句
|
||||
如何在 Linux 上用 SQL 语句来查询 Apache 日志
|
||||
================================================
|
||||
|
||||
Linux 有一个显著的特点,在正常情况下,你可以通过分析系统日志来了解你的系统中发生了什么,或正在发生什么。的确,系统日志是系统管理员在解决系统和应用问题时最需要的第一手资源。我们将在这篇文章中着重讲解 Apache HTTP web server 生成的 Apache access 日志。
|
||||
Linux 有一个显著的特点,在正常情况下,你可以通过日志分析系统日志来了解你的系统中发生了什么,或正在发生什么。的确,系统日志是系统管理员在解决系统和应用问题时最需要的第一手资源。我们将在这篇文章中着重讲解 Apache HTTP web server 生成的 Apache access 日志。
|
||||
|
||||
我们会通过另类的途径分析 Apache access 日志,我们使用的工具是 [asql][1]。asql 是一个开源的工具,它能够允许使用者针对日志运行 SQL 查询,从而通过更加友好的格式展现相同的信息。
|
||||
这次,我们会通过另类的途径来分析 Apache access 日志,我们使用的工具是 [asql][1]。asql 是一个开源的工具,它能够允许使用者使用 SQL 语句来查询日志,从而通过更加友好的格式展现相同的信息。
|
||||
|
||||
### Apache 日志背景知识 ###
|
||||
|
||||
Apache 有两种日志:
|
||||
|
||||
- **Access log**:存放在路径 /var/log/apache2/access.log (Debian) 或者 /var/log/httpd/access_log (Red Hat)。Access Log 记录所有 Apache web server 执行的请求。
|
||||
- **Error log**:存放在路径 /var/log/apache2/error.log (Debian) 或者 /var/log/httpd/error_log (Red Hat)。Error log 记录所有 Apache web server 报告的错误以及错误的情况。Error 情况包括(不限于)403(Forbidden,通常在有效请求丢失访问许可时被报告),404(Not found,在请求资源不存在时被报告)。
|
||||
- **Error log**:存放在路径 /var/log/apache2/error.log (Debian) 或者 /var/log/httpd/error_log (Red Hat)。Error log 记录所有 Apache web server 报告的错误以及错误的情况。Error 情况包括(不限于)403(Forbidden,通常在请求被拒绝访问时被报告),404(Not found,在请求资源不存在时被报告)。
|
||||
|
||||
虽然管理员可以通过配置 Apache 的配置文件来自定义 Apache access log 的罗嗦程度,在这篇文章中,我们会使用默认的配置,如下:
|
||||
虽然管理员可以通过配置 Apache 的配置文件来自定义 Apache access log 的详细程度,不过在这篇文章中,我们会使用默认的配置,如下:
|
||||
|
||||
Remote IP - Request date - Request type - Response code - Requested resource - Remote browser (may also include operating system)
|
||||
远程 IP - 请求时间 - 请求类型 - 响应代码 - 请求的 URL - 远程的浏览器信息 (也许包含操作系统信息)
|
||||
|
||||
因此一个典型的 Apache 日志条目就是下面这个样子:
|
||||
|
||||
192.168.0.101 - - [22/Aug/2014:12:03:36 -0300] "GET /icons/unknown.gif HTTP/1.1" 200 519 "http://192.168.0.10/test/projects/read_json/" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:30.0) Gecko/20100101 Firefox/30.0"
|
||||
|
||||
但是 Apache error log 又是怎么样的呢?因为 error log 条目主要记录 access log 中特殊的请求(你可以自定义),你可以通过 access log 来获得关于错误情况的更多信息(example 5 有更多细节)。
|
||||
但是 Apache error log 又是怎么样的呢?因为 error log 条目主要记录 access log 中特殊的请求(你可以自定义),所以你可以通过 access log 来获得关于错误情况的更多信息(example 5 有更多细节)。
|
||||
|
||||
话在前头, access log 是系统级别的日志文件。要分析 virtual hosts 的日志文件,你需要检查它们相应的配置文件(e.g. 在 /etc/apache2/sites-available/[virtual host name] 里(Debian))。
|
||||
此外要提前说明的, access log 是系统级别的日志文件。要分析虚拟主机的日志文件,你需要检查它们相应的配置文件(例如: 在 /etc/apache2/sites-available/[virtual host name] 里(Debian))。
|
||||
|
||||
### 在 Linux 上安装 asql ###
|
||||
|
||||
asql 由 Perl 编写,而且需求以下两个 Perl module:SQLite 的 DBI 驱动以及 GNU readline.
|
||||
asql 由 Perl 编写,而且需求以下两个 Perl 模块:SQLite 的 DBI 驱动以及 GNU readline。
|
||||
|
||||
### 在 Debian, Ubuntu 以及其衍生发行版上安装 asql ###
|
||||
|
||||
@ -46,7 +46,7 @@ asql 由 Perl 编写,而且需求以下两个 Perl module:SQLite 的 DBI 驱
|
||||
|
||||
### asql 是如何工作的? ###
|
||||
|
||||
从上面代码中的依赖中你就可以看出来,asql 转换未结构化的明文 Apache 日志成结构化的 SQLite 数据库信息。生成的 SQLite 数据库接受正常的 SQL 查询语句。数据库可以通过当前以及曾经的日志文件生成,其中包括压缩转换过的日志文件,类似 access.log.X.gz 或者 access_log.old。
|
||||
从上面代码中的依赖中你就可以看出来,asql 转换未结构化的明文 Apache 日志为结构化的 SQLite 数据库信息。生成的 SQLite 数据库可以接受正常的 SQL 查询语句。数据库可以通过当前以及之前的日志文件生成,其中也包括压缩转换过的日志文件,类似 access.log.X.gz 或者 access_log.old。
|
||||
|
||||
首先,从命令行启动 asql:
|
||||
|
||||
@ -62,7 +62,7 @@ asql 由 Perl 编写,而且需求以下两个 Perl module:SQLite 的 DBI 驱
|
||||
|
||||
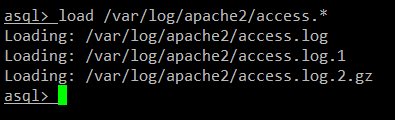
首先在 asql 中加载所有的 access 日志:
|
||||
|
||||
asql > load <path/to/apache-access-logs>
|
||||
asql > load <apache-access-logs 的路径>
|
||||
|
||||
比如在 Debian 下:
|
||||
|
||||
@ -72,7 +72,7 @@ asql 由 Perl 编写,而且需求以下两个 Perl module:SQLite 的 DBI 驱
|
||||
|
||||
asql > load /var/log/httpd/access_log*
|
||||
|
||||
当 asql 完成对 access 日志的加载后,我们就可以开始数据库查询了。注意一下,加载后生成的数据库是 "temporary" 的,意思就是数据库会在你退出 asql 的时候被清除。如果你想要保留数据库,你必须先将其保存为一个文件。我们会在后面介绍如何这么做(参考 example 3 和 4)。
|
||||
当 asql 完成对 access 日志的加载后,我们就可以开始数据库查询了。注意一下,加载后生成的数据库是 "temporary" (临时)的,意思就是数据库会在你退出 asql 的时候被清除。如果你想要保留数据库,你必须先将其保存为一个文件。我们会在后面介绍如何这么做(参考 example 3 和 4)。
|
||||
|
||||
|
||||
|
||||
@ -80,7 +80,7 @@ asql 由 Perl 编写,而且需求以下两个 Perl module:SQLite 的 DBI 驱
|
||||
|
||||
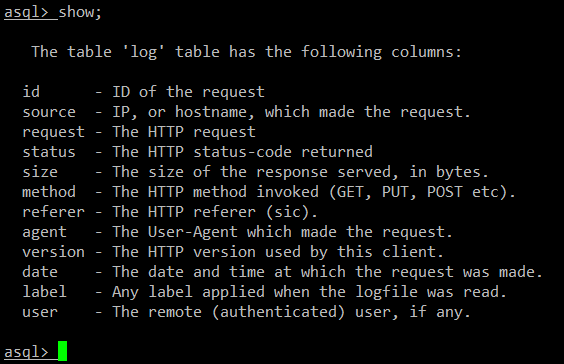
|
||||
|
||||
名为 .asql 的隐藏文件,保存于用户的 home 目录下,记录用户在 asql shell 中输入的命令历史。因此你可以使用方向键浏览历史命令,按下 ENTER 来重复执行之前的命令。
|
||||
一个名为 .asql 的隐藏文件,保存于用户的 home 目录下,记录用户在 asql shell 中输入的命令历史。因此你可以使用方向键浏览命令历史,按下 ENTER 来重复执行之前的命令。
|
||||
|
||||
### asql 上的示例 SQL 查询 ###
|
||||
|
||||
@ -106,7 +106,7 @@ asql 由 Perl 编写,而且需求以下两个 Perl module:SQLite 的 DBI 驱
|
||||
|
||||
这样做可以避免使用 load 命令对日志的语法分析所占用的处理时间。
|
||||
|
||||
**Example 4**:在重新启动 asql 后载入数据库。
|
||||
**Example 4**:在重新进入 asql 后载入数据库。
|
||||
|
||||
restore [filename]
|
||||
|
||||
@ -135,7 +135,7 @@ via: http://xmodulo.com/sql-queries-apache-log-files-linux.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[ThomazL](https://github.com/ThomazL)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,9 +1,8 @@
|
||||
Linux FAQs with Answers--How to convert a text file to PDF format on Linux
|
||||
Linux 有问必答 --如何在Linux上将文本文件转换成PDF格式
|
||||
Linux 有问必答:在Linux上如何将文本文件转换成PDF格式
|
||||
================================================================================
|
||||
> **提问**: 我想要将一个纯文本文件转换成PDF文档。是否有一个简单的方法在Linux命令行下将文本文件转换成PDF文件?
|
||||
> **提问**: 我想要将一个纯文本文件转换成PDF文档。在Linux命令行下是否有一个简单的方法将文本文件转换成PDF文件?
|
||||
|
||||
当你有一打文本文件要维护的时候,把它们转换成PDF文档有一些好处。比如,PDF对打印更友好因为PDF文档有预定义布局。除此之外,还可以减少文档被意外修改的风险。
|
||||
当你有一大堆文本文件要维护的时候,把它们转换成PDF文档会好一些。比如,PDF更适合打印,因为PDF文档有预定义布局。除此之外,还可以减少文档被意外修改的风险。
|
||||
|
||||
要将文本文件转换成PDF格式,你要按照下面的两步。
|
||||
|
||||
@ -27,7 +26,7 @@ Linux 有问必答 --如何在Linux上将文本文件转换成PDF格式
|
||||
|
||||
准备工作完成之后,按照下面的两步从文本文件生成一个PDF文件
|
||||
|
||||
首先,将文本文件使用enscript命令行工具转换成postscript格式。
|
||||
首先,使用enscript命令行工具将文本文件转换成postscript格式。
|
||||
|
||||
$ enscript -p output.ps input.txt
|
||||
|
||||
@ -40,6 +39,6 @@ Linux 有问必答 --如何在Linux上将文本文件转换成PDF格式
|
||||
via: http://ask.xmodulo.com/convert-text-to-pdf-linux.html
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,14 +1,14 @@
|
||||
如何让树莓派默认以图形界面启动
|
||||
如何让树莓派默认启动进入图形界面
|
||||
================================================================================
|
||||

|
||||
|
||||
我买树莓派已经有一段时间了,但是实话说我几乎还没有用它做过什么事情。自从我的Dell超级本送到Dell服务中心后(已经有数星期了),我再次开始使用树莓派作为替代。
|
||||
|
||||
我之前已经写过一篇[如何在Ubuntu中在SD卡上安装Raspbian系统][1]。我也重装了一次树莓派。第一次启动的时候我漏掉了一件事情就是设置图形界面。这样当我再次启动树莓派的时候,我直接进入了命令行。我该接下来如何运行Respbian图形界面呢?
|
||||
我之前已经写过一篇[在Ubuntu中如何在SD卡上安装Raspbian系统][1]。我也重装了一次树莓派。第一次启动的时候我漏掉了一件事情就是设置图形界面。这样当我再次启动树莓派的时候,我直接进入了命令行。我该接下来如何运行Respbian图形界面呢?
|
||||
|
||||
### 设置Raspbian图形启动 ###
|
||||
|
||||
入Raspbian系统的命令行界面,不用失望,因为很容易设置树莓派以图形界面启动。让我们看看该如何做。
|
||||
当你第一次安装Raspbian系统时,确实有一些选项需要你来配置,由于匆忙,我没有注意到这些,只是快速完成屏幕上的选项。如果你遇到了和我一样的情况,最终只是进入到了Raspbian操作系统的命令行界面,不要失望,因为设置树莓派以图形界面启动很容易。让我们看看该如何操作。
|
||||
|
||||
### 第一步: ###
|
||||
|
||||
@ -24,14 +24,13 @@
|
||||
|
||||
#### 第三步: ####
|
||||
|
||||
在这个配置界面下, 寻找**Enable Boot to Desktop/Scratch**这个选项。用箭头、tab和/或者回车键的组合来选中它(我忘记该使用哪一个了)。
|
||||
在这个配置界面下, 寻找**Enable Boot to Desktop/Scratch**这个选项。用箭头、tab和/或者回车键的组合来选中它(我忘记使用的是哪些了)。
|
||||
|
||||

|
||||
|
||||
#### 第四步: ####
|
||||
|
||||
下一屏中,选择**Desktop Login as user ‘Pi’ at the graphical desktop.
|
||||
**
|
||||
下一屏中,选择** Desktop Login as user ‘Pi’ at the graphical desktop. **
|
||||
|
||||

|
||||
|
||||
@ -45,7 +44,7 @@
|
||||
|
||||

|
||||
|
||||
我希望这边教程能够帮助你设置你的树莓派默认以图形界面启动。欢迎在评论区留下你的问题和建议。
|
||||
我希望这个教程能够帮助设置你的树莓派默认启动进入图形界面。欢迎在评论区留下你的问题和建议。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -53,9 +52,9 @@ via: http://itsfoss.com/raspberry-pi-gui-boot/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/Abhishek/
|
||||
[1]:http://itsfoss.com/tutorial-how-to-install-raspberry-pi-os-raspbian-wheezy/
|
||||
[1]:http://itsfoss.com/tutorial-how-to-install-raspberry-pi-os-raspbian-wheezy/
|
||||
@ -1,18 +1,19 @@
|
||||
Qshutdown – 一个先进的关机神器
|
||||
================================================================================
|
||||
qshutdown是一个QT程序,用于让计算机在指定时间或者在几分钟后关机/重启/挂起/睡眠。它会一直显示时间,直到相应的请求被发送到Gnome或KDE会话管理器,或者发送到HAL或DeviceKit。而如果这一切都没有发生,将会使用‘sudo shutdown -P now’进行关机。对于那些只在特定时间使用计算机工作的人而言,可能很有用。
|
||||
qshutdown是一个QT程序,用于让计算机在指定时间或者在几分钟后关机/重启/挂起/睡眠。对于那些只在特定时间使用计算机工作的人而言,可能很有用。
|
||||
|
||||
qshutdown将在最后70秒时显示3次警告提醒。(如果设置了1分钟或者本地时间+1,它只会显示一次。)
|
||||

|
||||
|
||||
该程序使用qdbus来发送关机/重启/挂起/睡眠请求到gnome或kde会话管理器,或者到HAL或DeviceKit,而如果这些都没有工作,那么就会使用‘sudo shutdown’命令进行关机(注意,但发送请求到HAL或DeviceKit,或者使用shutdown命令时,会话不会被保存。如果使用shutdown命令,该程序只会被关机或重启)。所以,如果在shutdown或reboot时间到时什么都没发生,这就意味着用户缺少使用shutdown命令的权限。
|
||||
qshutdown将在最后70秒时显示3次警告提醒。(如果设置了1分钟或者“本地时间+1”,它只会显示一次。)
|
||||
|
||||
该程序使用qdbus来发送关机/重启/挂起/睡眠请求到gnome或kde会话管理器,或者到HAL或DeviceKit,而如果这些都没有工作,那么就会使用‘sudo shutdown -P now’命令进行关机(注意,当发送请求到HAL或DeviceKit,或者使用shutdown命令时,会话不会被保存。如果使用shutdown命令,该程序只会被关机或重启)。所以,如果在shutdown或reboot时间到时却什么都没发生,这就意味着用户缺少使用shutdown命令的权限。
|
||||
|
||||
在这种情况下,你可以进行以下操作:
|
||||
|
||||
粘贴以下信息到终端:“EDITOR:nano sudo -E visudo”并添加此行:“* ALL = NOPASSWD:/sbin/shutdown”这里*替换username或%groupname。
|
||||
粘贴以下信息到终端:“EDITOR:nano sudo -E visudo”并添加此行:“* ALL = NOPASSWD:/sbin/shutdown”这里*替换为你的“用户名”或“%组名”。
|
||||
|
||||
配置文件qshutdown.conf
|
||||
|
||||
倒计时最大计数为1440分钟(24小时)。配置文件(和日志文件)位于~/.qshutdown。
|
||||
倒计时最大计数为1440分钟(24小时)。配置文件(和日志文件)位于~/.qshutdown,配置文件为:qshutdown.conf。
|
||||
|
||||
对于管理员:
|
||||
|
||||
@ -26,7 +27,6 @@ qshutdown将在最后70秒时显示3次警告提醒。(如果设置了1分钟
|
||||
|
||||
### 屏幕截图 ###
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
@ -40,7 +40,7 @@ via: http://www.ubuntugeek.com/qshutdown-an-avanced-shutdown-tool.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
106
published/20141119 When Microsoft Went A-Courting.md
Normal file
106
published/20141119 When Microsoft Went A-Courting.md
Normal file
@ -0,0 +1,106 @@
|
||||
当微软离去时
|
||||
================================================================================
|
||||

|
||||
|
||||
**开源.Net,“这与Linux无关——它与SaaS相关,也和一位并不偏执和狂热的90后CEO相关,”SoylentNews博主hairyfeet道,“纳德拉很明智,而且意识到了编程语言的价值不在于专利或OS排他性,而在于服务和对语言的支持……越多的平台使用该语言,它就会越好。”**
|
||||
|
||||
如果自由和开源软件迷们在过去的那些日子里感到有些许困惑的话,这也许是可以理解的,即便是头昏、头痛以及头晕也算是常见的。
|
||||
|
||||
你或许会问,这又是什么新的病症?
|
||||
|
||||
好吧,Linux女孩很高兴告诉你,它不是什么病症。不过,然而它并不意味着它很容易治愈。
|
||||
|
||||
原因无他,而是微软开源.Net并让它可以在Linux或Mac OS上运行的消息。
|
||||
|
||||
是的,你没听错:史蒂夫·鲍尔默曾经可能[称Linux为“癌症”][1],但今天雷蒙德(微软总部,代称微软)有个新发现,曾经不被包容的,但是却转头[“爱”上了Linux][2]!
|
||||
|
||||
它让微软看起来很奇怪——它也驱使FOSS迷们聚拢到博客圈的破败的Broken Windows Lounge,而去的人的数量更是空前的。
|
||||
|
||||
一杯龙舌兰可以让你不再头疼么?这是现在众多探究的问题之一。
|
||||
|
||||
### ‘繁荣的机遇’ ###
|
||||
|
||||
“这是个重大的消息,虽然有点过时了,”克里斯·特拉弗斯,一位[博主][3],他为[LedgerSMB][4]项目工作,告诉Linux女孩。
|
||||
|
||||

|
||||
|
||||
“我们生活的世界中,即使没有大的商业公司支持,新的开源编程语言也很兴旺,而闭源的编程语言仅能在大的商业公司的帮助下得到支持,”特拉弗斯说,“例如,Bing闭源杀死了REBOL 2.x。”
|
||||
|
||||
“这项运动很明显酝酿已久——一家像微软这样庞大的公司不会有‘突然开源’这种复杂的东西——而我想,在某种程度上,微软一定看到了Sun开源OpenJDK时的一些前兆了。”他暗示道。
|
||||
|
||||
同时,“这也为诸如C#和F#这样的语言提供了比当前市场更为兴盛的机会,”特拉弗斯说。
|
||||
|
||||
### ‘我仍然不相信你’ ###
|
||||
|
||||
“我首先想说,‘谢谢你,微软!’”[Linux Rants][5]博主麦克·斯通开篇说,“我们真的很欣赏你开源.Net并推动它跨平台,这是迈向正确方向的一步!”
|
||||
|
||||
“然而,我仍然不相信你。”他补充道。
|
||||
|
||||
“我很喜欢微软在考虑开源,但是我没有见到它向GPL迈进,”斯通告诉Linux女孩,“这让我想到了这么个可能性,微软提供了多个平台的软件供你使用,但却会把开发者和它捆绑起来。”
|
||||
|
||||
此外,微软不会作出任何保证,保证.Net常年开源,他指出。
|
||||
|
||||
“这意味着微软可以退出,并让开发出来的应用程序成为跨平台的Windows专有软件,”他警告道,“我不会相信微软的承诺,我会翘首期盼微软他们的突然而必然的背叛。”
|
||||
|
||||
### ‘留心不怀好意的礼物’ ###
|
||||
|
||||
该运动明显带有失望的气息,Google+博主阿里桑德罗·埃伯索尔暗示道。
|
||||
|
||||
“他们来得太晚了,”埃伯索尔说,“Java已经先下手为强了,当.Net还是Windows/Microsoft专有产品时,Java已经遍布四处了。试着让人采用,希望好运吧。”
|
||||
|
||||
此外,“如果它打上GPL烙印来保护代码创建者的话我才会相信它,”他补充道,“一个脆弱的MIT许可证任何时候都是逆天而行的。”
|
||||
|
||||
无论如何,“在该公司产生的对FLOSS社区的全部的敌意下,他们会过河拆桥,”埃伯索尔总结道,“底线是:送礼的希腊人也很可畏——仔细留心希腊人不怀好意的礼物……”
|
||||
|
||||
### ‘就像猫爱上老鼠’ ###
|
||||
|
||||
微软爱上Linux“就像猫爱上老鼠,”博主[罗伯特·伯格森][6]打趣道,“当然,他们会玩玩*/Linux,但是他们不是我们的朋友。”
|
||||
|
||||
所发生的事情是,FOSS和LInux社区已经击溃了“MS自从和IBM达成提供OS的交易后放置在竞争道路入口上的所有障碍,”伯格森说,“MS肯定是在绝望地试着和‘敌人’‘做朋友’,因为它们的位置被侵占了。”
|
||||
|
||||
“一切都会好的,”他补充道,“MS仍然可以通过愚蠢地花大量的金钱来制造麻烦,或者他们可以进行常规商业运作并在价格/性能上开展竞争。那不是‘爱’——那是接受现实。”
|
||||
|
||||
### 适应或者灭亡 ###
|
||||
|
||||
对于微软而言,问题在于“开源开发包对于开发者而言开始变得足够好用了,”参团顾问和[Slashdot][7]博主格哈德·麦克。
|
||||
|
||||
“在我的最后一份职业中,大多数的程序员想要Eclipse,而不是Visual Studio,即使客户端软件是Windows专用的。用Windows做测试的开发者们迁移到Linux的数量在缓慢增长。”麦克回忆道。
|
||||
|
||||
“很要有人想被固定在一个平台中,因此单一平台的语言的份额会越来越少,”他补充道,“微软现在必须在适应与灭亡中作出选择。”
|
||||
|
||||
### 这里没有温暖的毛球 ###
|
||||
|
||||
驱动此项运动的策略也在于“各种云大量地在Linux上部署,即便在微软自己的Azure云,Linux也被大量部署,”Google+博主凯文·奥布莱恩暗示道。
|
||||
|
||||
“纳德拉清楚地指出,他正将微软向云方向推进,因为他几乎不得不如此,以期继续将游戏玩下去。”奥布莱恩坚信。
|
||||
|
||||
那就是说,不管怎样,“我都不期待微软变得可爱又善意——他们将做所有他们认为能获得最佳公司利益的事情。”他说。
|
||||
|
||||
事实上,“根本没Linux什么事——它只和SaaS相关,也和一位并不偏执和狂热的90后CEO相关,”SoylentNews博主hairyfeet告诉Linux女孩。
|
||||
|
||||
“纳德拉很明智,而且意识到了编程语言的价值不在于专利或OS排他性,而在于服务和对语言的支持,”hairyfeet解释道,“考虑到这一点,越多的平台使用该语言,它就会越好,因为那会增加该语言的价值,并且为你的服务带来更多客户。”
|
||||
|
||||
### 帝国的没落 ###
|
||||
|
||||
总得来说,一切都很明了,那就是“微软帝国正在摇摇欲坠,”Google+博主贡萨洛·维拉斯科 C说。
|
||||
|
||||
“我不知道,或者不关心他们为什么会说谎,说他们热爱Linux,”他补充道,“我只希望GNU/Linux社区变得比现今更聪明些(咳,Systemd,咳咳),拒绝微软.Net和其它产生影响的东西。GNU/Linux必须只用FLOSS工具。”
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxinsider.com/story/When-Microsoft-Went-A-Courting-81374.html
|
||||
|
||||
作者:[Katherine Noyes][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://twitter.com/noyesk
|
||||
[1]:http://www.linuxinsider.com/perl/story/35697.html
|
||||
[2]:http://www.theregister.co.uk/2014/10/20/microsoft_cloud_event/
|
||||
[3]:http://ledgersmbdev.blogspot.com/
|
||||
[4]:http://www.ledgersmb.org/
|
||||
[5]:http://linuxrants.com/
|
||||
[6]:http://mrpogson.com/
|
||||
[7]:http://slashdot.org/
|
||||
@ -1,14 +1,14 @@
|
||||
15条Linux下的‘pwd’命令(打印工作目录)示例
|
||||
菜鸟教程:全面学习 pwd 命令
|
||||
================================================================================
|
||||
对于那些使用Linux命令行的人来说,‘**pwd**‘命令是非常有用的,它告诉你你现在在那个目录,从根目录(**/**)开始。特别对于或许会在目录的切换间容易糊涂的Linux新手而言,‘**pwd**‘ 可以拯救他们。
|
||||
对于那些使用Linux命令行的人来说,‘**pwd**‘命令是非常有用的,它告诉你你现在在那个目录,从根目录(**/**)如何到达。特别是对于或许会在目录的切换间容易糊涂的Linux新手而言,‘**pwd**‘ 可以拯救他们。
|
||||
|
||||

|
||||
|
||||
15 pwd 命令示例
|
||||
*15个 pwd 命令示例*
|
||||
|
||||
### 什么是pwd? ###
|
||||
|
||||
‘**pwd**‘ 代表的是‘**Print Working Directory**’(打印当前目录)。如它的名字那样,‘**pwd**’会打印出当前工作目录或仅是目录用户。它会打印出以root (**/**)为起始的完整目录名。这条命令是一条shell内建命令,并且在大多数shell中都可以使用,如bash、Bourne shell,ksh、zsh等等。
|
||||
‘**pwd**‘ 代表的是‘**Print Working Directory**’(打印当前目录)。如它的名字那样,‘**pwd**’会打印出当前工作目录,或简单的来说就是当前用户所位于的目录。它会打印出以根目录 (**/**)为起点的完整目录名(绝对目录)。这条命令是一条shell内建命令,并且在大多数shell中都可以使用,如bash、Bourne shell,ksh、zsh等等。
|
||||
|
||||
#### pwd的基本语法: ####
|
||||
|
||||
@ -25,11 +25,11 @@
|
||||
<td align="LEFT" style="border: 1px solid #000000;"><b><span style="font-size: small;"> 描述</span></b></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td height="19" align="LEFT" style="border: 1px solid #000000;"><span style="font-family: Liberation Serif,Times New Roman; font-size: small;"> -L (logical)</span></td>
|
||||
<td height="19" align="LEFT" style="border: 1px solid #000000;"><span style="font-family: Liberation Serif,Times New Roman; font-size: small;"> -L (即逻辑路径logical )</span></td>
|
||||
<td align="LEFT" style="border: 1px solid #000000;"><span style="font-family: Liberation Serif,Times New Roman; font-size: small;"> 使用环境中的路径,即使包含了符号链接</span></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td height="19" align="LEFT" style="border: 1px solid #000000;"><span style="font-family: Liberation Serif,Times New Roman; font-size: small;"> -P (physical)</span></td>
|
||||
<td height="19" align="LEFT" style="border: 1px solid #000000;"><span style="font-family: Liberation Serif,Times New Roman; font-size: small;"> -P (即物理路径physical)</span></td>
|
||||
<td align="LEFT" style="border: 1px solid #000000;"><span style="font-family: Liberation Serif,Times New Roman; font-size: small;"> 避免所有的符号链接</span></td>
|
||||
</tr>
|
||||
<tr>
|
||||
@ -56,7 +56,7 @@ pwd的退出状态:
|
||||
<td align="CENTER" style="border: 1px solid #000000;"><span style="font-size: small;">成功</span></td>
|
||||
</tr>
|
||||
<tr>
|
||||
<td height="19" align="CENTER" style="border: 1px solid #000000;"><span style="font-size: small;">Non-zero</span></td>
|
||||
<td height="19" align="CENTER" style="border: 1px solid #000000;"><span style="font-size: small;">非零值</span></td>
|
||||
<td align="CENTER" style="border: 1px solid #000000;"><span style="font-size: small;">失败</span></td>
|
||||
</tr>
|
||||
</tbody>
|
||||
@ -64,7 +64,7 @@ pwd的退出状态:
|
||||
|
||||
本篇的目的是采用例子让你对‘**pwd**‘有更深入的领悟。
|
||||
|
||||
**1.** 打印放钱工作目录.
|
||||
**1.** 打印当前工作目录.
|
||||
|
||||
avi@tecmint:~$ /bin/pwd
|
||||
|
||||
@ -72,7 +72,7 @@ pwd的退出状态:
|
||||
|
||||

|
||||
|
||||
打印工作目录
|
||||
*打印工作目录*
|
||||
|
||||
**2.** 为文件夹创建一个符号链接(比如说在home目录下创建一个**htm**链接指向**/var/www/html**)。进入新创建的目录并打印出含有以及不含符号链接的目录。
|
||||
|
||||
@ -83,9 +83,9 @@ pwd的退出状态:
|
||||
|
||||

|
||||
|
||||
创建符号链接
|
||||
*创建符号链接*
|
||||
|
||||
**3.** 从当前环境中答应目录即使它含有符号链接。
|
||||
**3.** 从当前环境中打印目录即使它含有符号链接。
|
||||
|
||||
avi@tecmint:~$ /bin/pwd -L
|
||||
|
||||
@ -93,7 +93,7 @@ pwd的退出状态:
|
||||
|
||||
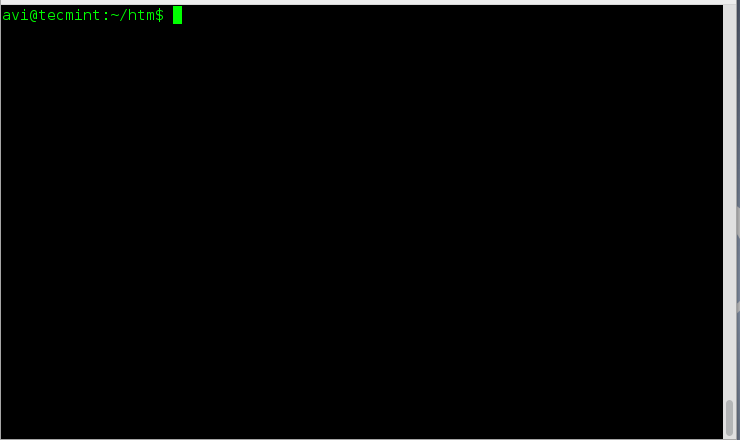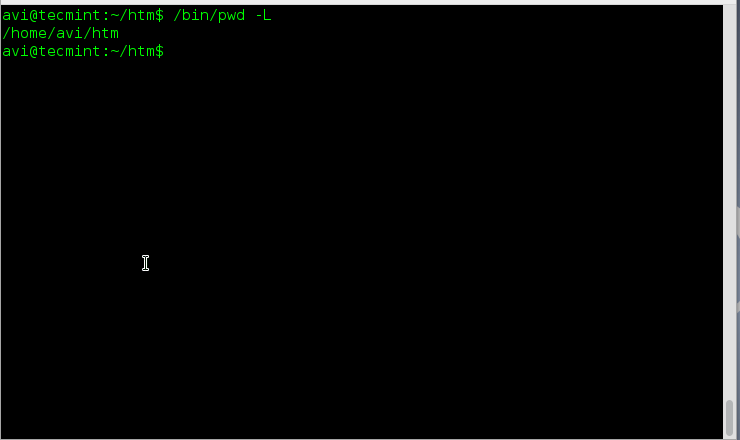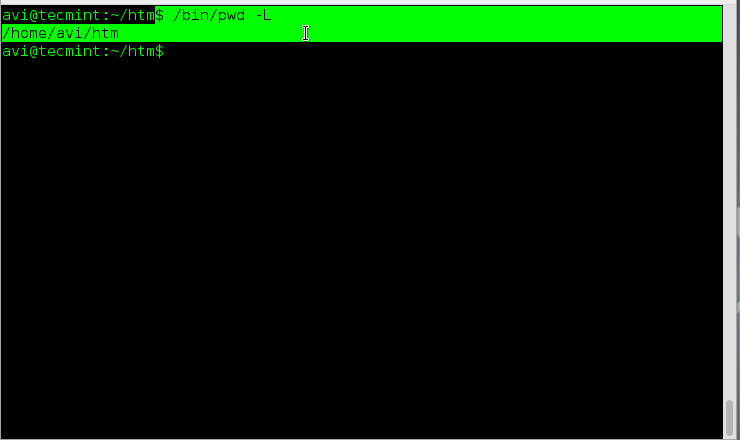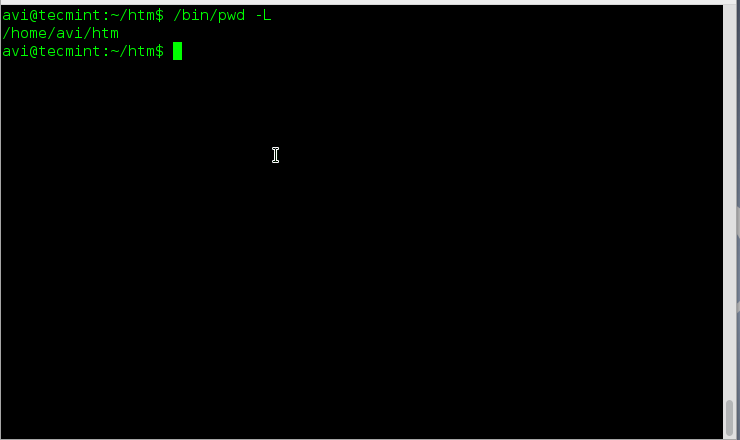
|
||||
|
||||
打印工作目录
|
||||
*打印工作目录*
|
||||
|
||||
**4.** 解析符号链接并打印出物理目录。
|
||||
|
||||
@ -103,7 +103,7 @@ pwd的退出状态:
|
||||
|
||||

|
||||
|
||||
打印物理工作目录
|
||||
*打印物理工作目录*
|
||||
|
||||
**5.** 查看一下“**pwd**”和“**pwd -P**”的输出是否一致,也就是说,如果没有跟上选项,“**pwd**”时候会自动采用**-P**选项。
|
||||
|
||||
@ -113,7 +113,7 @@ pwd的退出状态:
|
||||
|
||||
|
||||
|
||||
检查pwd输出
|
||||
*检查pwd输出*
|
||||
|
||||
**结论:** 上面例子4和5的输出很明显(结果相同),当你“**pwd**”后面不带参数时,pwd会使用“**-P**”选项。
|
||||
|
||||
@ -131,7 +131,7 @@ pwd的退出状态:
|
||||
|
||||

|
||||
|
||||
检查pwd命令版本
|
||||
*检查pwd命令版本*
|
||||
|
||||
**注意:** ‘pwd’ 通常不带选项运行,且没有任何参数
|
||||
|
||||
@ -148,9 +148,9 @@ pwd的退出状态:
|
||||
|
||||

|
||||
|
||||
打印可执行文件路径
|
||||
*打印可执行文件路径*
|
||||
|
||||
**8.** 存储“**pwd**”命令的值到变量中(比如说:**a** ),并从中打印i变量的值(对于观察shell脚本很重要)。
|
||||
**8.** 存储“**pwd**”命令的值到变量中(比如说:**a** ),并从中打印变量的值(对于观察shell脚本很重要)。
|
||||
|
||||
avi@tecmint:~$ a=$(pwd)
|
||||
avi@tecmint:~$ echo "Current working directory is : $a"
|
||||
@ -159,19 +159,19 @@ pwd的退出状态:
|
||||
|
||||

|
||||
|
||||
存储pwd的值到变量中。
|
||||
*存储pwd的值到变量中*
|
||||
|
||||
下面的例子中也可以用**printf**来替代。
|
||||
|
||||
**9.** 将工作路径切换到其他地方(比如说 **/home**),并在命令行中显示。通过执行命令(比如说 ‘**ls**‘)来验证一切**OK**。
|
||||
|
||||
avi@tecmint:~$ cd /home
|
||||
avi@tecmint:~$ PS1='$pwd> ' [Notice single quotes in the example]
|
||||
avi@tecmint:~$ PS1='$pwd> ' [注意例子中的单引号]
|
||||
> ls
|
||||
|
||||

|
||||
|
||||
改变当前工作路径
|
||||
*改变当前工作路径*
|
||||
|
||||
**10.** 设置多行显示 (就像下面这样),
|
||||
|
||||
@ -190,7 +190,7 @@ pwd的退出状态:
|
||||
|
||||

|
||||
|
||||
设置多行显示
|
||||
*设置多行显示*
|
||||
|
||||
**11.** 一下子检查当前工作路径以及先前的工作路径。
|
||||
|
||||
@ -200,8 +200,7 @@ pwd的退出状态:
|
||||
|
||||

|
||||
|
||||
Check Present Previous Working Directory
|
||||
检查当前工作路径
|
||||
*检查当前工作路径*
|
||||
|
||||
**12.** pwd文件的绝对路径(以**/**开始)。
|
||||
|
||||
@ -211,7 +210,7 @@ Check Present Previous Working Directory
|
||||
|
||||
/usr/include/pwd.h
|
||||
|
||||
**13.** 打印pwd手册的绝对路径(以**/**开始)。
|
||||
**13.** pwd手册的绝对路径(以**/**开始)。
|
||||
|
||||
/usr/share/man/man1/pwd.1.gz
|
||||
|
||||
@ -241,7 +240,7 @@ Check Present Previous Working Directory
|
||||
}
|
||||
fi
|
||||
|
||||
给予他执行权限并运行。
|
||||
给予执行权限并运行。
|
||||
|
||||
avi@tecmint:~$ chmod 755 pwd.sh
|
||||
avi@tecmint:~$ ./pwd.sh
|
||||
@ -251,7 +250,7 @@ Check Present Previous Working Directory
|
||||
|
||||
#### 总结 ####
|
||||
|
||||
**pwd**是一个最简单且会广泛用到的命令。掌握好pwd是使用Linux终端的基础。就是这些了。我很快会再带来另外有趣的注意,请不要走开继续关注Tecmint。
|
||||
**pwd**是一个最简单且会广泛用到的命令。掌握好pwd是使用Linux终端的基础。就是这些了。我很快会再带来另外有趣的文章,请不要走开继续关注我们。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -259,7 +258,7 @@ via: http://www.tecmint.com/pwd-command-examples/
|
||||
|
||||
作者:[Avishek Kumar][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,8 +1,8 @@
|
||||
Linux 有问必答 -- 如何从VirtualBox中从主机访问NAT客户机
|
||||
Linux 有问必答:如何从VirtualBox中从主机访问NAT客户机
|
||||
================================================================================
|
||||
> **提问**: 我有一台运行在VirtualBox上的使用NAT的虚拟机。因此虚拟机会被VirtualBox分配一个私有IP地址(10.x.x.x)。如果我想要从主机SSH到虚拟机中,我该怎么做?
|
||||
> **提问**: 我有一台运行在VirtualBox上的使用NAT的虚拟机,因此虚拟机会被VirtualBox分配一个私有IP地址(10.x.x.x)。如果我想要从主机SSH到虚拟机中,我该怎么做?
|
||||
|
||||
VirtualBox对虚拟机支持几种不同的网络方式,其中一种是NAT网络。当虚拟机启用NAT后,VirtualBox会自动在虚拟机和主机之间进行网络翻译,因此你不于必在虚拟机和主机之间配置任何东西。这也意味着NAT中的虚拟机对于外部网络以及主机本身是不可见的。这会在你想要从主机访问虚拟机时会产生问题(比如SSH)。
|
||||
VirtualBox对虚拟机支持几种不同的网络方式,其中一种是NAT网络。当虚拟机启用NAT后,VirtualBox会自动在虚拟机和主机之间进行网络翻译,因此你不必在虚拟机和主机之间配置任何东西。这也意味着NAT中的虚拟机对于外部网络以及主机本身是不可见的。这会在你想要从主机访问虚拟机时会产生问题(比如SSH)。
|
||||
|
||||
如果你想从VirtualBox的NAT环境的虚拟机,你可以在GUI或者命令行下启用VirtualBox NAT的端口转发。本篇教程将会演示**如何通过启用22端口转发而从主机SSH连接到NAT环境的客户机**。如果你先想要从HTTP访问NAT的客户机,用80端口代替22端口即可。
|
||||
|
||||
@ -62,6 +62,6 @@ VirtualBox有一个称为VBoxManage的命令行管理工具。使用命令行工
|
||||
via: http://ask.xmodulo.com/access-nat-guest-from-host-virtualbox.html
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,10 +1,11 @@
|
||||
Linux有问必答——如何修复“ImportError: No module named scapy.all”
|
||||
Linux有问必答:如何修复“ImportError: No module named scapy.all”
|
||||
================================================================================
|
||||
> **问题**:当我运行一个Python应用程序时,出现了这个提示消息“ImportError: No module named scapy.all”。我怎样才能修复这个导入错误呢?
|
||||
|
||||
[Scapy][1]是一个用Python写的灵活包生成和嗅探程序。使用Scapy,你可以完成创建专有包,发送上线,从线上或转储文件中读取包,转换包等工作。使用Scapy的通用包处理能力,你可以很容易地完成像SYN扫描、TCP路由跟踪以及OS指纹打印之类的工作。你也可以通过导入,将Scapy整合到其它工具中。
|
||||
[Scapy][1]是一个用Python写的灵活的数据包生成及嗅探程序。使用Scapy,你可以完成创建任意数据包并发送到网络上、从网络上或转储文件中读取数据包、转换数据包等工作。使用Scapy的通用包处理能力,你可以很容易地完成像SYN扫描、TCP路由跟踪以及OS指纹检测之类的工作。你也可以通过导入,将Scapy整合到其它工具中。
|
||||
|
||||
该导入错误表明:你还没有在你的Linux系统上安装Scapy。下面介绍安装方法。
|
||||
|
||||
### 安装Scapy到Debian, Ubuntu或Linux Mint ###
|
||||
|
||||
$ sudo apt-get install python-scapy
|
||||
@ -30,7 +31,7 @@ Linux有问必答——如何修复“ImportError: No module named scapy.all”
|
||||
via: http://ask.xmodulo.com/importerror-no-module-named-scapy-all.html
|
||||
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,49 +1,48 @@
|
||||
什么造就一个优秀的程序员?
|
||||
|
||||
是什么造就了一个优秀的程序员?
|
||||
================================================================================
|
||||
是什么造成一个优秀的程序员?首先问问你自己吧,这会是个有趣的问题。它让你反思自己软件开发的能力。这个问题也适合问问你的同事。它可以带来一些关于如何协同工作的有趣讨论。下面是五个我认为成为一个优秀程序员必备的重要技能。
|
||||
是什么造就了一个优秀的程序员?首先问问你自己吧,这会是个有趣的问题。它让你反思自己的软件开发技术。这个问题也适合问问你的同事们。它可以带来一些关于如何协同工作的有趣讨论。下面是我认为成为一个优秀程序员必备的五个重要技能。
|
||||
|
||||
### 1. 分解问题 ###
|
||||
|
||||
编程是为了解决问题,但在你开始写代码前,需要明白如何解决问题。优秀程序员的一项技能是把大的问题逐层分解成一个个更小的部分,直到每一部分都可以很容易解决。但找到解决问题的方式往往并没有那么简单。优秀程序员能找到方法去建立问题模型,这种方法使得输出结果的程序容易解释、实现和测试。
|
||||
|
||||
我写过的某些最复杂的程序在局部上都是难懂的,因为代码实现并不能很好地描述问题,也就导致了编写的代码难以理解。当问题很好建模的时候,我赞同伯尼·科赛尔所说的话(取自著名的[程序员在工作][1]中的访谈记录):
|
||||
我写过的某些最复杂的程序在局部上都是难懂的,因为代码实现并不能很好地匹配这个问题,也就导致了编写的代码难以理解。当问题很好地建模的时候,我赞同伯尼·科赛尔所说的话(取自著名的[程序员在工作][1]中的访谈记录):
|
||||
|
||||
> “……很少有本质上很难的程序。如果你盯着某一块代码,它看起来确实很难;如果你无法理解某件事情应该产生什么结果,这基本上就暗示这件事情很难思考清楚了。在这个时候,你不应该卷起袖子,尝试修复代码;你需要只是往回一步,再仔细考虑清楚。当你已经深思熟虑后,你会发现问题变得很简单”。
|
||||
> “……很少有本质上很难的程序。如果你盯着某一块代码,它看起来确实很难;如果你无法理解这段代码应该产生什么结果,这基本上就是暗示它很难被理解了。在这个时候,你不应该卷起袖子,尝试修复代码;你需要只是往回一步,再仔细考虑清楚。当你已经深思熟虑后,你会发现问题变得很简单”。
|
||||
|
||||
### 2. 场景分析 ###
|
||||
|
||||
优秀开发者能考虑到如何使程序适合多种不同的场景。这项能力既适用于处理程序本身的逻辑,又适用于处理发生的外部和内部事件。为了考虑逻辑上的不同思路,他们问自己这样的问题:如果这个参数为空会发生什么?如果所有条件都为假呢?这个方法在线程上是安全的吗?为了发现软件需要处理的各种类型的事件,他们问自己这样的问题:如果队列占满了会怎样?如果请求收不到响应会怎样?如果在这台服务器重启的同时另外一台服务器也重启了会怎样?
|
||||
优秀开发者能考虑到如何使程序适合多种不同的场景。这项能力既适用于处理程序本身的逻辑,又适用于处理可能会发生的外部和内部事件。为了考虑逻辑上的不同思路,他们问自己这样的问题:如果这个参数为空会发生什么?如果所有条件都为假呢?这个方法在线程上是安全的吗?为了发现软件需要处理的各种类型的事件,他们问自己这样的问题:如果队列占满了会怎样?如果请求收不到响应会怎样?如果在这台服务器重启的同时另外一台服务器也重启了会怎样?
|
||||
|
||||
优秀程序员问他们自己:如何打破自己的程序?换句话说,他们有能力像测试人员一样思考。相反,缺少经验的程序员通常只考虑正确的路径——在一切都按照预期进行时正常的控制流(当然这也是程序在大部分时候做的事情)。当然,异常不可避免要发生,所以需要程序能处理这些情况。
|
||||
优秀程序员问他们自己:如何发现程序的缺陷?换句话说,他们有能力像测试人员一样思考。相反,缺少经验的程序员通常只考虑正确的路径——在一切都按照预期进行时正常的控制流(当然这也是程序在大部分时候的情况)。当然,异常不可避免要发生,所以需要程序能处理这些情况。
|
||||
|
||||
### 3. 命名 ###
|
||||
|
||||
编程由大量的命名对象组成:类、方法和变量。当编码完成时,程序也具备了自我描述的能力,也就是说通过阅读源代码可以清楚地明白程序中函数的含义。自描述代码的一个好处就是很自然地产生许多体积更小的方法,而不是少数体积大的方法,因为你有更多空间去放置有意义的名字(还有[其它原因][2]解释为什么短小方法更好)。
|
||||
编程由大量的命名对象组成:类、方法和变量。当编码完成得很好时,程序也具备了自我描述的能力,也就是说通过阅读源代码可以清楚地明白程序中函数的含义。自描述代码的一个好处就是很自然地产生许多更短的命名方法,而不是少数更长的方法,因为你有更多空间去放置有意义的名字(还有[其它原因][2]解释为什么短小方法更好)。
|
||||
|
||||
想出好的名字比它听起来更困难一些。我喜欢这段引用(来自菲尔·卡尔顿):“在计算机科学领域只有两件困难的事情:缓存失效和命名对象。”命名在一定程度上很困难是因为你需要清楚地明白每一个名字究竟要代表什么。有时候命名不是清楚,只有随着软件开发进展才会慢慢显现。因此,重命名和命名一样重要。
|
||||
想出好的名字比它听起来更困难一些。我喜欢这段引用(来自菲尔·卡尔顿):“在计算机科学领域只有两件困难的事情:缓存失效和命名对象。”命名在一定程度上很困难是因为你需要清楚地明白每一个名字究竟要代表什么。有时候命名不是一下子就清晰明了,只有随着软件开发进展才会慢慢显现。因此,重命名和命名一样重要。
|
||||
|
||||
命名对象也包含提出要用的概念和这些概念该如何称呼。通过深思熟虑,清楚命名所使用的惯用概念(在程序中和与程序员、非程序员讨论时使用),这使得编写程序变得更加容易。
|
||||
|
||||
### 4. 一致性 ###
|
||||
|
||||
也许编程中最大的挑战是管理复杂性。保持一致性是处理复杂性的一种方法。它通过允许我们看到对象命名、使用和处理所采用的模式和推理来降低了某些复杂性。有了一致性,我们就无需用脑袋去记住异常和随机变量。取而代之,我们可以更关注[程序本身的复杂性,而不是偶然产生的复杂性][3]。
|
||||
也许编程中最大的挑战是管理复杂性。保持一致性是处理复杂性的一种方法。它通过允许我们看到对象命名、使用和处理所采用的模式和推理来降低了某些复杂性。有了一致性,我们就无需用脑去记住异常和随机变量。取而代之,我们可以更关注[程序本身的复杂性,而不是偶然产生的复杂性][3]。
|
||||
|
||||
保持一致性是很重要的。它应用在变量名字和分组、方法命名、模块划分、目录结构、GUI、错误处理、日志输出和文档等很多方面。比如,如果某些变量是的相关,并一起出现(在声明、方法调用或数据库中的列),而且总是以相同的顺序使用它们。那么当其中一个消失或者整体被打乱时,你就会很容易发现。对于一个操作,如果在一个地方叫delete,就不要在另一个地方叫remove:务必使用相同的名字。史蒂夫·麦克奈尔在[代码大全][4]中对于使用相反命名有相同的建议。比如,begin和end是相反的,就如同start和stop一样。当使用相反对时不要混用不同对的名字(比如使用begin和stop)。
|
||||
保持一致性从整体看来是很重要的。它应用在变量名字和分组、方法命名、模块划分、目录结构、GUI、错误处理、日志输出和文档等很多方面。比如,如果某些变量是的相关,并一起出现(在声明、方法调用或数据库中的列),而且总是以相同的顺序使用它们。那么当其中一个消失或者整体被打乱时,你就会很容易发现。对于一个操作,如果在一个地方叫delete,就不要在另一个地方叫remove:务必使用相同的名字。史蒂夫·麦克奈尔在[代码大全][4]中对于使用相反命名有相同的建议。比如,begin和end是相反的,就如同start和stop一样。当使用相反对时不要混用不同对的名字(比如使用begin和stop)。
|
||||
|
||||
当修改一段程序时可能会引入非一致性。粗心大意的程序员不会注意到他们添加的代码是否和已有的代码保持一致。优秀程序员会严苛地确保在这些看似很小的细节上都要做得恰到好处。他们知道保持一致性对于在软件开发的整个过程中处理复杂性是多么的重要。
|
||||
当修改一段程序时可能会引入非一致性。粗心大意的程序员不会注意到他们添加的代码是否和已有的代码保持一致。优秀程序员会严苛地确保在这些看似很小的细节上都要做到精益求精。他们知道保持一致性对于在软件开发的整个过程中处理复杂性是多么的重要。
|
||||
|
||||
### 5. 学习能力 ###
|
||||
|
||||
作为一名软件开发者,你需要持续学习。在为软件添加一项新功能前,你必须明白为什么要这么做。在给一个已有程序添加代码前,你通常必须学习已有代码在做什么,以便合适地嵌入新功能。你还需要学习相关系统,以便正确地与它们交互。因此,快速学习的能力使你成为一名更加高效的开发者。
|
||||
作为一名软件开发者,你需要持续学习。在为软件添加一项新功能前,你必须明白为什么要这么做。在给一个已有程序添加代码前,你通常必须知道已有代码在做什么,以便合适地嵌入新功能。你还需要学习相关系统,以便正确地与它们交互。因此,快速学习的能力使你成为一名更加高效的开发者。
|
||||
|
||||
而且,因为软件工程领域的开发速度是如此的快速,所以新的编程语言、工具、技术和框架需要学习层出不穷。这是好还是坏,就看你怎么看。佛瑞德·布鲁克斯把学习能力列为[技能的快乐之一][5],对此我深表赞同。学习新事物本身就是令人心满意足的,它也意味着开发者的生活从不无聊。
|
||||
|
||||
### 总结 ###
|
||||
|
||||
上面所有的技能都是通用的——它们中没有一项是针对某种语言、某个框架或某种技术。如果你拥有它们,你就能快速学习一门新的语言或工具,在新的环境下写出优秀的软件。而且,因为它们在本质上是通用的,所以不会在若干年以后变得不实用。
|
||||
上面所有的技能都是通用的——它们中没有一项是针对某种语言、某个框架或某种技术。如果你拥有它们,你就能快速学习一门新的语言或工具,在新的环境下写出优秀的软件。而且,因为它们在本质上是通用的,所以不会在若干年以后过时。
|
||||
|
||||
这就是我对什么因素造就一个优秀程序员的回答。你认为造就一个优秀程序员的因素是哪些?在评论里让我知道吧。
|
||||
是什么造就了一个优秀的程序员?以上便是我的观点。你认为造就一个优秀程序员的因素有哪些?在评论里告诉我吧。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -51,7 +50,7 @@ via: http://henrikwarne.com/2014/06/30/what-makes-a-good-programmer/
|
||||
|
||||
作者:[Henrik Warne][a]
|
||||
译者:[KayGuoWhu](https://github.com/KayGuoWhu)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,34 @@
|
||||
Ubuntu 14.10 ‘乌托邦的独角兽’官方 T 恤开始发售
|
||||
================================================================================
|
||||

|
||||
|
||||
**Ubuntu 14.10 发布以来,很少能见到随同发布的带有官方吉祥物的 T 恤。不过今天 Canonical 商店终于上架了这件粉丝喜欢的商品。**
|
||||
|
||||
现在有两种T恤,一种是‘dusk blue’(男士版本)或者‘hot pink’(女士版本),但是审美与设计的形式是相同的。每种T恤印有由Canonical定制设计的折纸型的‘乌托邦的独角兽’。每件衬衫的背面是Ubuntu的标识以及含有“Utopic Unicorn 14.10”文字,从前到后帮你推广系统-我喜欢!
|
||||
|
||||

|
||||
|
||||
男士的尺寸有从S到XXL, 女士的尺寸有8-10与14-16,每件T恤在英国的价格是£11,美国的价格是$17.45,欧洲的价格是$17.45。这个价格较往年高一点,与以往一样这是减去了运费和包装的费用。
|
||||
|
||||
- [购买男士的 Ubuntu 14.10 T恤][1]
|
||||
|
||||
- [购买女士的 Ubuntu 14.10 T恤][2]
|
||||
|
||||
吉祥物 T 恤已经成为自Ubuntu 8.04 Hardy Heron后每个Ubuntu版本发布的传统,虽然它一般在系统发布前发布。
|
||||
|
||||
如果你不是特定版本的粉丝,你会发现可以购买的老版本吉祥物商品的数量有限且降价出售。如果你想在你的衬衫上印一条蝾螈,推广穿山甲或者塔尔羊,可以在[出售页面][3]看看。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/12/last-ubuntu-14-10-unicorn-t-shirts-now-available
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://shop.canonical.com/product_info.php?products_id=1153
|
||||
[2]:http://shop.canonical.com/product_info.php?products_id=1159
|
||||
[3]:http://shop.canonical.com/index.php?cPath=29
|
||||
@ -0,0 +1,44 @@
|
||||
Linux有问必答——如何在Linux命令行中剪裁图像
|
||||
================================================================================
|
||||
> **问题**:我想要去除图像文件中的白色空白,有没有什么便捷的方法能在Linux命令行中对图像文件进行剪裁?
|
||||
|
||||
当涉及到在Linux中转换或编辑图像文件时,ImageMagick毫无疑问是最为熟知的一体化软件之一。它包含了一整套命令行工具,用以显示、转换,或复制超过200中类型的光栅或矢量图像文件,所有这一切都在命令行下完成。ImageMagick可以用于多样化的图像编辑工作,如转换文件格式,添加特殊效果,添加文本,以及改变图像(调整大小、旋转、翻转、剪裁)。
|
||||
|
||||
如果你想要剪裁映像以去除空白,你可以使用ImageMagick自带的两个命令行工具。如果你还没有安装ImageMagick,请参照[本指南][1]来安装。
|
||||
|
||||
在本教程中,让我们来剪裁以下PNG图像。我们想要去除图像右边和底部的边缘,以便让图标居中。
|
||||
|
||||
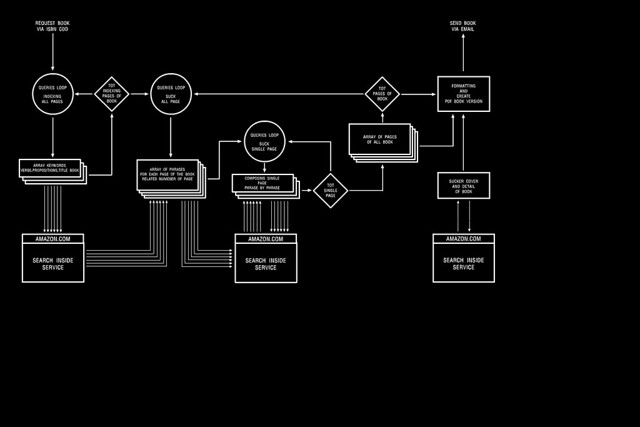
|
||||
|
||||
首先,鉴定图像文件的尺寸(宽度和高度)。你可以使用identity命令来完成。
|
||||
|
||||
$ identify chart.png
|
||||
|
||||
----------
|
||||
|
||||
chart.png PNG 1500x1000 1500x1000+0+0 8-bit DirectClass 31.7KB 0.000u 0:00.000
|
||||
|
||||
就像上面显示的那样,输入的图像是1500x1000px。
|
||||
|
||||
接下来,确定图像剪裁要做的两件事:(1)剪裁图像开始的位置(2)剪裁矩形区域的大小。
|
||||
|
||||
在本实例中,让我们假定图像剪裁从左上角开始,更精确点是在x=20px和y=10px,那样的话,剪裁后的图像尺寸为1200x700px。
|
||||
|
||||
用于剪裁图像的工具是convert。使用“-crop”选项后,convert命令会在输入图像中剪裁出一个矩形区域。
|
||||
|
||||
$ convert chart.png -crop 1200x700+20+10 chart-cropped.png
|
||||
|
||||
指定输入图像为chart.png,convert命令会将剪裁后的图像存储为chart-cropped.png。
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/crop-image-command-line-linux.html
|
||||
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://ask.xmodulo.com/install-imagemagick-linux.html
|
||||
32
published/20141208 Nathive--A libre software image editor.md
Normal file
32
published/20141208 Nathive--A libre software image editor.md
Normal file
@ -0,0 +1,32 @@
|
||||
Nathive——libre软件图像编辑器
|
||||
================================================================================
|
||||
Nathive是一个libre软件图像编辑器,类似于 Adobe Photoshop、Corel Photo-Paint 或 GIMP,但是侧重于适用性和逻辑性,并为每个用户提供平滑的学习曲线。该项目在 GNOME 桌面环境中运行,并欢迎每个人参与到合作中,分享代码、翻译或想法等方面。
|
||||
|
||||
该项目尚处于测试阶段,所以它还是个未完成的工作,还不适用于终端用户。直到现在,开发始终专注于积淀应用的核心功能和创建便捷的开发工具。所以,目前我们将致力于创建新的插件,因为很明显在这方面还很缺乏。
|
||||
|
||||
其目的是在不放弃最初的可用性的情况下,逐步将该软件打造成一个专业的图像编辑器。Nathive由基于GTK+的Python脚本写成的,它设计为简洁、轻量,而且易于安装和使用。
|
||||
|
||||
### 在 ubuntu 上安装Nathive ###
|
||||
|
||||
你需要从[这里][1]下载.deb包,然后双击来安装。
|
||||
|
||||
### 屏幕截图 ###
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/nathive-a-libre-software-image-editor.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://www.nathive.org/download
|
||||
@ -0,0 +1,64 @@
|
||||
After an 18 Month Gap, Opera for Linux Returns With New Stable Release
|
||||
================================================================================
|
||||
**The first stable release of Opera for Linux in more than 18 months is now available for download.**
|
||||
|
||||

|
||||
|
||||
Hello again, Opera!
|
||||
|
||||
Opera for Computers for Linux 26 (no really, that’s its name) features a complete top-to-bottom overhaul, new features, and better performance thanks to its Aura and Blink underpinnings (yes, it’s no longer based on the proprietary Presto web engine).
|
||||
|
||||
#### Features ####
|
||||
|
||||
The browser [wiggled its toes in tux-friendly waters back in June with the launch of a developer preview][1], but if you last tried Opera when it looked like this, you’ll want to grab some smelling salts: things have changed.
|
||||
|
||||
注:youtube 视频,发布时可换成链接地址
|
||||
<iframe width="750" height="422" src="https://www.youtube.com/embed/-kS10C2BUOs?feature=oembed" frameborder="0" allowfullscreen></iframe>
|
||||
|
||||
Alongside an impressive new look and blazing fast, standards-compliant rendering engine come many new and improved features.
|
||||
|
||||
- **Discover** — Shows articles from around the web in a range of categories
|
||||
- **Speed Dial** — Supports interactive widgets, folders, and themes
|
||||
- **Tab Peek** — Preview the content of an open tab without switching back to it
|
||||
- **Opera Turbo** — Data-saving mode ideal for patchy connections
|
||||
- **Rich bookmarking** — including new sharing functionality
|
||||
- **Add-ons** — compatible with Chrome extensions, too
|
||||
- **Support for HiDPI displays on Linux**
|
||||
|
||||
### Download Opera for Linux 26 ###
|
||||
|
||||
Opera say those running Opera 12.6 on a 64-bit version of Ubuntu still supported by Canonical will automatically receive this new update through the Ubuntu Software Center.
|
||||
|
||||
But in all honesty I’m not sure anyone is in that boat! So, helpfully, a Debian installer can be downloaded from the Opera website. This will also add the Opera repository to your Software Sources to enable you to receive future updates in a timely fashion.
|
||||
|
||||
- [Download Opera for Computers for Linux 26][2]
|
||||
|
||||
Feel free to kit your new browser out with our nifty Opera Add-On, too:
|
||||
|
||||
- [Install OMG! Ubuntu! Opera Extension][3]
|
||||
|
||||
#### Important Notice about Linux Support ####
|
||||
|
||||
**Opera for Linux is 64-bit only**. The company say this decision was made based on ‘what most Linux desktop users have installed’. While annoying it is part of a larger overall trend away from 32-bit software, with Opera for Mac also being 64-bit exclusive, too.
|
||||
|
||||
In another case of “spending limited resources wisely”, this release is only being officially supported on Ubuntu (and ‘buntu-based derivatives, including Linux Mint).
|
||||
|
||||
Users on other distributions, from Arch to openSUSE, can still install Opera for Linux but will need to [use a (fairly simple) workaround][4] or hunt down an unofficial repository.
|
||||
|
||||
**If you give it a spin let us know what you make of it in the comments below.**
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/12/new-opera-for-linux-goes-stable-download-now
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.omgubuntu.co.uk/2014/06/opera-linux-chromium-download-released
|
||||
[2]:http://opera.com/computer/linux
|
||||
[3]:https://addons.opera.com/en/extensions/details/omg-ubuntu-for-opera/?display=en
|
||||
[4]:https://gist.github.com/ruario/99522c94838d0680633c#file-manual-install-of-opera-md
|
||||
@ -0,0 +1,61 @@
|
||||
Firefox 34 Arrives with Plugin-Free Video Calling and Powerful WebIDE
|
||||
================================================================================
|
||||

|
||||
|
||||
**It’s been a busy few months for Mozilla, what with agreeing to a deal to switch its default search provider to Yahoo!, launching a custom version of its browser packed full of developer goodies, and launching Firefox OS handsets in new territories.**
|
||||
|
||||
Today, Mozilla has released Firefox 34 for Windows, Mac and Linux desktops, the first stable release since last month’s security n’ bug fix update.
|
||||
|
||||
### Headline Feature ###
|
||||
|
||||
Despite the rapid release cycle Mozilla once again manages to deliver some great new features.
|
||||
|
||||
Making its first appearance in a stable release is **Firefox Hello**, Mozilla’s WebRTC feature.
|
||||
|
||||
Though not enabled for all (you can manually turn it on via about:config), the feature bring plugin-free video and voice calls to the browser. No Skype, no add-ons, no hassle. You simple click the Firefox Hello icon, send your share link to the recipient to initiate a connection (assuming they’re also using a WebRTC-enabled browser, like Google Chrome or Opera).
|
||||
|
||||
|
||||
|
||||
The ‘Hello Firefox’ Popup
|
||||
|
||||
Signing in with a Firefox account will give you more features, including a contacts book with one-click calling (no need to share links).
|
||||
|
||||
#### Other Changes ####
|
||||
|
||||
Version 34 also makes it easier to **switch themes** (formerly known as ‘personas’), with live previews and a switcher menu now available on the **Customising canvas**:
|
||||
|
||||

|
||||
|
||||
Ad-hoc theme switching
|
||||
|
||||
The first major search engine change arrives in this release, with Yandex shipping as default for Belarusian, Kazakh, and Russian locales. Yahoo! will be enabled for US users in the near future. But remember: [this does not affect the version of Firefox provided in Ubuntu][1].
|
||||
|
||||
US users get secure **HTTPS** Wikipedia searching from the search box:
|
||||
|
||||

|
||||
|
||||
Secure Wikipedia Searches for English US Users
|
||||
|
||||
In addition to improved HTML5 support (largely around WebCrypto features) a [**new WebIDE tool**][2] ships in this release, and is packed full of great tools for developers.
|
||||
|
||||
From Android connectivity and an in-app editor to support for deploying and testing apps in a Firefox OS simulator. If you haven’t tried Firefox OS in a while, v2.2 (unstable) has plenty to play with including edge swiping, new home screen arranging features, and some new APIs.
|
||||
|
||||

|
||||
|
||||
### Download Firefox 34 ###
|
||||
|
||||
Canonical will roll out Firefox 34 to users of Ubuntu 12.04, 14.04 and 14.10 in the next 24 hours or so, so keep an eye out. If you’re super impatient the release can also be downloaded from Mozilla servers directly.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/12/firefox-34-changes-include-hello-html5-webide
|
||||
|
||||
作者:[Joey-Elijah Sneddon ][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.omgubuntu.co.uk/2014/11/firefox-set-yahoo-default-search-engine-ubuntu-not-affected
|
||||
[2]:https://developer.mozilla.org/en-US/docs/Tools/WebIDE
|
||||
@ -0,0 +1,78 @@
|
||||
From Mint to Trisquel: The Top Linux Distro Releases in November 2014
|
||||
================================================================================
|
||||
**November wasn’t heavy on new Linux distribution releases, but still had more than enough to keep distro-hoppers bouncing from download server to ISO mirror and back again.**
|
||||
|
||||
From the free software ethic of **Trisquel** to the nostalgic glow of **Ubuntu MATE**, let’s take a look at the major Linux distribution releases made in November 2014.
|
||||
|
||||

|
||||
|
||||
### Linux Mint 17.1 ###
|
||||
|
||||
Linux Mint 17.1 ‘Rebecca’ is the big hitter on this list, going stable just in time to make it.
|
||||
|
||||
Based on Ubuntu 14.04 and using Linux kernel 3.13, the update also comes loaded with the **latest [Cinnamon 2.4][1] desktop environment, a customisable version of the Nemo file manager**, and improvements to the Update Manager to make package upgrades safer, saner and swifter.
|
||||
|
||||
Other changes see the ‘**Background**’, ‘**Login**’ and ‘**Theme**’ settings panes redesigned, and **‘Privacy’ and ‘Notification’ sections** added. The default **system font has been switched to Noto Sans**, while fans of customisation will enjoy new colors added to the Mint-X theme package.
|
||||
|
||||
Linux Mint 17.1 delivers a set of solid, well thought out changes and performance improvements, important for an LTS release supported until 2019.
|
||||
|
||||
More information and those all important downloads can be found on the official project website.
|
||||
|
||||
- [Visit the Linux Mint Website][2]
|
||||
|
||||
### Ubuntu Mate 14.04 LTS ###
|
||||
|
||||
|
||||
|
||||
It may have [arrived after the release of Ubuntu MATE 14.10][3] (**timey-wimey**), but as the first Long Term Support release of the flavor Ubuntu MATE 14.04 was welcomed with warm arms, especially by those who love to bask in the green-hued glow of GNOME 2 nostalgia.
|
||||
|
||||
Packed with security updates, MATE 1.8.1, and new software included out of the box, Ubuntu MATE 14.04 LTS is a notable update with plenty to tempt those on the newer (but older) 14.10 release.
|
||||
|
||||
For full hardware requirements, support information and download links, head on over to the official project website.
|
||||
|
||||
- [Download Ubuntu MATE 14.04 LTS][4]
|
||||
|
||||
### Trisquel 7.0 ###
|
||||
|
||||

|
||||
|
||||
The [latest stable release of Trisquel][5], an Ubuntu-based distribution endorsed by the Free Software Foundation (FSF), arrived in the middle of November — and was met by **a lot** of interest.
|
||||
|
||||
The free (as in freedom) distribution is built on Ubuntu 14.04 LTS but ships without any of the proprietary bits and pieces. It’s a “pure” Linux experience that may require some workarounds, but serves to flag up the areas where more attention is needed in FOSS hardware support and app alternatives.
|
||||
|
||||
The Libre Linux 3.13 Kernel, GNOME 3.12 ‘Flashback’ desktop and the Firefox-based Abrowser 33 are among the changes to be found in Trisquel 7.
|
||||
|
||||
- [Download Trisquel 7][6]
|
||||
|
||||
### Other Notable Releases ###
|
||||
|
||||

|
||||
|
||||
Outside of the Ubuntu-based bubble November 2014 saw releases of other popular Linux distributions, including beta milestones of Mageia 5 and Fedora 21, and a new stable release of Scientific Linux 6.6.
|
||||
|
||||
Joining them is openSUSE 13.2 (stable) — the first release to follow a change in the way openSUSE development takes place, the first to adopt the new openSUSE design guidelines and the first to ship with a streamlined (if still unwieldy) installer.
|
||||
|
||||
The release has been getting great reviews from the geek press, who gave particular praise for the GNOME 3.14 implementation.
|
||||
|
||||
Coming from Ubuntu, where “everything just works”, the cultural and technical gulf can be daunting at first. But if you have some free time, like the color green and relish a challenge, the official openSUSE 13.2 [release announcement][7] should be your starting point.
|
||||
|
||||
**Have you tried any of these releases above? Let us know what you made of them in the space down below .**
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/11/linux-distro-releases-round-november-2014
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:http://www.omgubuntu.co.uk/2014/11/install-cinnamon-2-4-ubuntu-14-04-lts
|
||||
[2]:http://www.linuxmint.com/download.php
|
||||
[3]:http://www.omgubuntu.co.uk/2014/11/ubuntu-mate-14-04-download-released
|
||||
[4]:https://ubuntu-mate.org/longterm/
|
||||
[5]:http://www.omgubuntu.co.uk/2014/11/download-trisquel-7-0-kernel-3-13
|
||||
[6]:https://trisquel.info/en/download
|
||||
[7]:https://news.opensuse.org/2014/11/04/opensuse-13-2-green-light-to-freedom/
|
||||
@ -0,0 +1,540 @@
|
||||
translating by yupmoon
|
||||
|
||||
|
||||
Readers' Choice Awards 2014--Linux Journal
|
||||
================================================================================
|
||||
It's time for another Readers' Choice issue of Linux Journal! The format last year was well received, so we've followed suit making your voices heard loud again. I couldn't help but add some commentary in a few places, but for the most part, we just reported results. Please enjoy this year's Readers' Choice Awards!
|
||||
|
||||
We'd like to make Readers' Choice Awards even better next year. Please send ideas for new categories and any comments or feedback via [http://www.linuxjournal.com/contact][1].
|
||||
|
||||
Please see the December 2014 issue of Linux Journal for the complete list of winners.
|
||||
|
||||
### Best Linux Distribution ###
|
||||
|
||||

|
||||
|
||||
Although this year the Debian/Ubuntu-based distros took the lion's share of the votes, the "Best Linux Distribution" category is a bit like "Best Kind of Pizza"—even the bottom of the list is still pizza. It's hard to go wrong with Linux, and the wide variety of votes only proves how many different choices exist in our wonderful Open Source world.
|
||||
|
||||
- Ubuntu 16.5%
|
||||
- Debian 16.4%
|
||||
- Linux Mint 11%
|
||||
- Arch Linux 8.5%
|
||||
- Fedora 8.3%
|
||||
- CentOS 6%
|
||||
- openSUSE 5.3%
|
||||
- Kubuntu 4.1%
|
||||
- Gentoo 2.9%
|
||||
- Slackware 2.7%
|
||||
- Xubuntu 2.5%
|
||||
- Other 2.3%
|
||||
- Red Hat Enterprise Linux 1.6%
|
||||
- NixOS 1.4%
|
||||
- elementary OS 1.3%
|
||||
- Lubuntu 1.2%
|
||||
- CrunchBang 1%
|
||||
- Mageia .7%
|
||||
- LXLE .4%
|
||||
- Tails .4%
|
||||
- Android-x86 .3%
|
||||
- Bodhi Linux .3%
|
||||
- Chakra .3%
|
||||
- Kali Linux .3%
|
||||
- PCLinuxOS .3%
|
||||
- SolydK .3%
|
||||
- Mandriva .1%
|
||||
- Oracle Linux .1%
|
||||
|
||||
### Best Mobile Linux OS ###
|
||||
|
||||

|
||||
|
||||
Android is such a dominant force in the mobile world, we decided to allow Android variants to be counted separately. So although the underlying system on some of these are indeed Android, it seems far more informative this way.
|
||||
|
||||
- Stock Android 37.1%
|
||||
- Sailfish OS 27.6%
|
||||
- CyanogenMod 20.2%
|
||||
- Other 3%
|
||||
- Ubuntu Phone 3%
|
||||
- Amazon Fire OS 1.5%
|
||||
- Ubuntu for Android 1.4%
|
||||
- Replicant .8%
|
||||
- Tizen .8%
|
||||
|
||||
### Best Linux Smartphone Manufacturer ###
|
||||
|
||||

|
||||
|
||||
- Samsung 29%
|
||||
- Jolla 26.7%
|
||||
- Nexus 16.5%
|
||||
- Other 7.1%*
|
||||
- HTC 7%
|
||||
- LG 5.3%
|
||||
- Sony 3.7%
|
||||
- Nokia 1.8%
|
||||
- Huawei 1.4%
|
||||
- GeeksPhone 1%
|
||||
- Amazon .6%
|
||||
|
||||
*Under "Other", Motorola got many write-ins, followed by OnePlus.
|
||||
|
||||
### Best Linux Tablet ###
|
||||
|
||||

|
||||
|
||||
- Google Nexus 7 35.3%
|
||||
- Google Nexus 10 14.8%
|
||||
- Samsung Galaxy Tab 14%
|
||||
- Samsung Galaxy Note 9.8%
|
||||
- ASUS Transformer Pad 8.4%
|
||||
- Other 6.4%
|
||||
- Kindle Fire HD 4.7%
|
||||
- ASUS MeMO Pad 2%
|
||||
- Dell Venue 1.6%
|
||||
- Acer Iconia One 1.4%
|
||||
- Samsung Galaxy Note Edge .9%
|
||||
- Ekoore Python S3 .7%
|
||||
|
||||
### Best Other Linux-Based Gadget (not including smartphones or tablets) ###
|
||||
|
||||

|
||||
|
||||
We are a Raspberry Pi-loving bunch, that's for sure! But really, who can blame us? With the new B+ model, the already awesome RPi is getting sleeker and more useful. I'm no fortune teller, but I suspect I know next year's winner already.
|
||||
|
||||
- Raspberry Pi 71.4%
|
||||
- BeagleBone Black 8.1%
|
||||
- Other 4.3%*
|
||||
- Lego Mindstorms Ev3 3.7%
|
||||
- Moto 360 3.4%
|
||||
- Cubieboard 1.7%
|
||||
- Parrot A.R Drone 1.7%
|
||||
- Samsung Gear S 1.4%
|
||||
- Yamaha Motif XF8 1.1%
|
||||
- Nvidia Jetson-K1 Development System .8%
|
||||
- Cloudsto EVO Ubuntu Linux Mini PC .5%
|
||||
- VoCore Open Hardware Computer .5%
|
||||
- LG G Watch .4%
|
||||
- RaZberry .4%
|
||||
- VolksPC .4%
|
||||
- IFC6410 Pico-ITX Board .2%
|
||||
- JetBox 5300 .1%
|
||||
|
||||
*Under "Other", the most popular write-ins were Odroid and CuBox.
|
||||
|
||||
### Best Laptop Vendor ###
|
||||
|
||||

|
||||
|
||||
This category used to be a rating of which vendors worked the best with Linux, but thankfully, now most laptops work fairly well. So, we truly get to see the cream rise to the top and focus on things other than "it works with Linux". It's awesome living in the future.
|
||||
|
||||
- Lenovo 32%
|
||||
- ASUS 19.3%
|
||||
- Dell 18.5%
|
||||
- System76 10.6%
|
||||
- Other 7.9%*
|
||||
- Acer 4.5%
|
||||
- ThinkPenguin 1.9%
|
||||
- LinuxCertified 1.8%
|
||||
- ZaReason 1.6%
|
||||
- EmperorLinux 1.5%
|
||||
- CyberPower .3%
|
||||
- Eurocom .1%
|
||||
|
||||
*Under "Other", the most popular write-ins were (in this order) Apple running Linux, HP, Toshiba and Samsung.
|
||||
|
||||
### Best Content Management System ###
|
||||
|
||||

|
||||
|
||||
- WordPress 34.7%
|
||||
- Drupal 25.3%
|
||||
- Joomla! 11.1%
|
||||
- MediaWiki 10.5%
|
||||
- Other 10%*
|
||||
- Alfresco 4.3%
|
||||
- WebGUI 1.3%
|
||||
- ikiwiki 1.1%
|
||||
- eZ publish .7%
|
||||
- Wolf CMS .4%
|
||||
- Elgg .3%
|
||||
- Blosxom .2%
|
||||
|
||||
*Under "Other", the most popular write-ins were (in this order) DokuWiki, Plone, Django and Typo3.
|
||||
|
||||
### Best Linux-Friendly Web Hosting Company ###
|
||||
|
||||

|
||||
|
||||
When it comes to Web hosting, it's hard to find a company that isn't Linux-friendly these days. In fact, finding a hosting provider running Windows is more of a challenge. As is obvious by our winner ("Other"), the options are amazing. Perhaps a "Worst Web Hosting" category would be more useful!
|
||||
|
||||
- Other 22.8%*
|
||||
- Amazon 22.5%
|
||||
- Rackspace 13.1%
|
||||
- Linode 10.4%
|
||||
- GoDaddy.com 6.5%
|
||||
- OVH 5.6%
|
||||
- DreamHost 5.4%
|
||||
- 1&1 4.8%
|
||||
- LAMP Host 2.9%
|
||||
- Hurricane Electric 2.6%
|
||||
- Liquid Web .6%
|
||||
- RimuHosting .6%
|
||||
- Host Media .5%
|
||||
- Savvis .5%
|
||||
- Blacknight Solutions .4%
|
||||
- Netfirms .4%
|
||||
- Prgmr .4%
|
||||
|
||||
*Under "Other", the most write-ins went to (in this order) Digital Ocean (by a landslide), followed by Hetzner, BlueHost and WebFaction.
|
||||
|
||||
### Best Web Browser ###
|
||||
|
||||

|
||||
|
||||
Firefox takes the gold this year by a significant margin. Even if you combine Chrome and Chromium, Firefox still takes the top spot. There was a time when we worried that the faithful Firefox would fade away, but thankfully, it's remained strong and continues to be a fast, viable, compatible browser.
|
||||
|
||||
- Firefox 53.8%
|
||||
- Chrome 26.9%
|
||||
- Chromium 8.1%
|
||||
- Iceweasel 4%
|
||||
- Opera 3%
|
||||
- Other 2%
|
||||
- SeaMonkey .8%
|
||||
- rekonq .5%
|
||||
- dwb .4%
|
||||
- QupZill .4%
|
||||
- Dillo .2%
|
||||
|
||||
### Best E-mail Client ###
|
||||
|
||||

|
||||
|
||||
If I didn't know firsthand how many hard-core geeks live among us, I might accuse Kyle Rankin of voting fraud. His beloved Mutt e-mail client doesn't take top spot, but for a program without any graphical interface, third place is impressive!
|
||||
|
||||
- Mozilla Thunderbird 44.4%
|
||||
- Gmail 24.7%
|
||||
- Mutt 6.8%
|
||||
- Evolution 5.5%
|
||||
- KMail 5.3%
|
||||
- Other 3.2%
|
||||
- Claws Mail 2.2%
|
||||
- Zimbra 2%
|
||||
- Alpine 1.8%
|
||||
- Geary 1.7%
|
||||
- SeaMonkey 1%
|
||||
- Opera Mail .9%
|
||||
- Sylpheed .4%
|
||||
|
||||
### Best Audio Editing Tool ###
|
||||
|
||||

|
||||
|
||||
- Audacity 69.1%
|
||||
- FFmpeg 10.8%
|
||||
- VLC 9.7%
|
||||
- Ardour 4.9%
|
||||
- Other 1.9%
|
||||
- SoX 1.3%
|
||||
- Mixxx 1.1%
|
||||
- LMMS .7%
|
||||
- Format Junkie .5%
|
||||
|
||||
### Best Audio Player ###
|
||||
|
||||

|
||||
|
||||
We figured VLC would take top spot in the video player category (see below), but it was a bit of a surprise to see how many folks prefer it as an audio player as well. Perhaps it's become the one-stop shop for media playback. Either way, we're thrilled to see VLC on the top.
|
||||
|
||||
- VLC 25.2%
|
||||
- Amarok 15.3%
|
||||
- Rhythmbox 10.4%
|
||||
- Clementine 8.6%
|
||||
- MPlayer 6.1%
|
||||
- Spotify 5.9%
|
||||
- Audacious 5.5%
|
||||
- Banshee 4.6%
|
||||
- Other 4%*
|
||||
- XBMC 3.1%
|
||||
- foobar2000 3%
|
||||
- Xmms 2.4%
|
||||
- DeaDBeeF 1.2%
|
||||
- MOC .9%
|
||||
- cmus .8%
|
||||
- Ncmpcpp .8%
|
||||
- Guayadeque .6%
|
||||
- Mixxx .4%
|
||||
- MPC-HC .4%
|
||||
- Subsonic .4%
|
||||
- Nightingale .3%
|
||||
- Decibel Audio Player .2%
|
||||
|
||||
*Under "Other", Quod Libet had the most write-ins.
|
||||
|
||||
### Best Video Player ###
|
||||
|
||||

|
||||
|
||||
- VLC 64.7%
|
||||
- MPlayer 14.5%
|
||||
- XBMC 6.4%
|
||||
- Totem 2.7%
|
||||
- Other 2.7%*
|
||||
- Plex 2%
|
||||
- Kaffeine 1.9%
|
||||
- mpv 1.6%
|
||||
- MythTV 1.6%
|
||||
- Amarok 1.4%
|
||||
- Xmms .3%
|
||||
- Daum Potplayer .2%
|
||||
- Clementine .1%
|
||||
|
||||
*Under "Other", most write-ins were for SMPlayer.
|
||||
|
||||
### Best Video Editor ###
|
||||
|
||||

|
||||
|
||||
This is another testament to the geek factor when it comes to our readers. We didn't specify "non-linear editor", so by a transcoding technicality, VLC eked out a win in the video editing category. Well played, VLC, well played.
|
||||
|
||||
- VLC 17.5%
|
||||
- Kdenlive 16.4%
|
||||
- Blender 15.1%
|
||||
- Avidemux 13.2%
|
||||
- OpenShot 13.2%
|
||||
- Cinelerra 7.5%
|
||||
- PiTiVi 4.9%
|
||||
- LightWorks 4.8%
|
||||
- Other 4.7%
|
||||
- LiVES 1.4%
|
||||
- Shotcut .6%
|
||||
- Jahshaka .4%
|
||||
- Flowblade .4%
|
||||
|
||||
### Best Cloud-Based File Storage ###
|
||||
|
||||

|
||||
|
||||
In a category that used to have few options, Dropbox still takes top spot, but the margin is closing. It's hard to argue against Dropbox's convenience and stability, but hosting your own data on ownCloud gives it quite a boost into the second-place spot.
|
||||
|
||||
- Dropbox 30.5%
|
||||
- ownCloud 23.6%
|
||||
- Google Drive 16%
|
||||
- rsync 8.3%
|
||||
- Other 7.5%*
|
||||
- Amazon S3 6.6%
|
||||
- SpiderOak 4.4%
|
||||
- Box 1.8%
|
||||
- Copy 1%
|
||||
- AjaXplorer .3%
|
||||
|
||||
*Under "Other", the most write-ins went to Younited and MEGA. Many also said things like "no cloud is the best choice/my files stay on my storage/local only".
|
||||
|
||||
### Best Linux Game ###
|
||||
|
||||

|
||||
|
||||
I rarely play games, so every year I look forward to this category to find the most popular options for those few times I do. I'm personally tickled to see NetHack so high on the list, especially considering the opposition. There's just something about wandering around random tunnels that appeals to the old-school DnD player in all of us.
|
||||
|
||||
- Civilization 5 26.5%
|
||||
- Other 23.5%*
|
||||
- Team Fortress 2 8.7%
|
||||
- NetHack 8.4%
|
||||
- X-Plane 10 7.1%
|
||||
- Dota 6.1%
|
||||
- Bastion 5.4%
|
||||
- Scorched 3D 3.7%
|
||||
- Destiny 3.6%
|
||||
- Ultima IV 1.9%
|
||||
- FreeCol 1.8%
|
||||
- Kpat 1.4%
|
||||
- FreeOrion 1.1%
|
||||
- Ryzom .9%
|
||||
|
||||
*Under "Other", the most write-ins were (in this order) Minecraft, 0 A.D., Frozen Bubble, Battle for Wesnoth, Portal and Counter Strike.
|
||||
|
||||
### Best Virtualization Solution ###
|
||||
|
||||
I think the relationship with Vagrant has helped Oracle's VirtualBox significantly in popularity. Yes, Vagrant works with other virtualization platforms, but since it so seamlessly integrates with VirtualBox, I think it gets quite a boost. Virtualization is such an efficient and reliable way to implement systems, bare-metal solutions are almost a thing of the past!
|
||||
|
||||

|
||||
|
||||
- Oracle VM VirtualBox 33.4%
|
||||
- VMware 22.3%
|
||||
- KVM 21.1%
|
||||
- XEN 5.7%
|
||||
- QEMU 5.3%
|
||||
- OpenStack 4.9%
|
||||
- Other 4.2%*
|
||||
- OpenVZ 1.7%
|
||||
- Linux-VServer 1.3%
|
||||
- Symantec Workspace Virtualization .1%
|
||||
|
||||
*Under "Other", the most write-ins went to Docker, ProxMox and LXC, in that order.
|
||||
|
||||
### Best Monitoring Application ###
|
||||
|
||||

|
||||
|
||||
- Nagios 27.1%
|
||||
- Wireshark 20.7%
|
||||
- htop 12.3%
|
||||
- Zabbix 10.5%
|
||||
- Other 8.6%*
|
||||
- Zenoss 6.2%
|
||||
- Munin 3.4%
|
||||
- PC Monitor 2.8%
|
||||
- New Relic 1.9%
|
||||
- Opsview 1.2%
|
||||
- SaltStack 1%
|
||||
- NTM (Network Traffic Monitor) .7%
|
||||
- xosview .7%
|
||||
- Manage Engine .5%
|
||||
- FlowViewer .3%
|
||||
- Circonus .2%
|
||||
- SysPeek .2%
|
||||
|
||||
*Under "Other", most write-ins went to Icinga and OpenNMS.
|
||||
|
||||
### Best DevOps Configuration Management Tool ###
|
||||
|
||||

|
||||
|
||||
It was interesting to see Git take top spot in this category, because although it certainly would work to use standard version control on configuration files, I always assumed it would be used alongside tools like Chef or Puppet. If nothing else, the DevOps movement has taught crusty old system administrators like myself to treat configuration files like code. Version control is incredible, and it seems as though most readers agree.
|
||||
|
||||
- Git 39.4%
|
||||
- Puppet 17.2%
|
||||
- Ansible 8.9%
|
||||
- cron jobs 8.8%
|
||||
- Subversion 7.6%
|
||||
- Chef 5%
|
||||
- SaltStack 5.4%
|
||||
- Other 4.6%*
|
||||
- CFEngine 3%
|
||||
|
||||
*Under "Other", most write-ins went to NixOps.
|
||||
|
||||
### Best Programming Language ###
|
||||
|
||||

|
||||
|
||||
- Python 30.2%
|
||||
- C++ 17.8%
|
||||
- C 16.7%
|
||||
- Perl 7.1%
|
||||
- Java 6.9%
|
||||
- Other 4.6%
|
||||
- Ruby 4.3%
|
||||
- Go 2.4%
|
||||
- JavaScript 2.4%
|
||||
- QML 2.2%
|
||||
- Fortran 1.4%
|
||||
- Haskell 1.4%
|
||||
- Lisp 1.2%
|
||||
- Erlang .6%
|
||||
- Rust .6%
|
||||
- D .4%
|
||||
- Hack .1%
|
||||
|
||||
*Under "Other", most write-ins went to Scala, PHP and Clojure (in that order).
|
||||
|
||||
### Best Scripting Language ###
|
||||
|
||||

|
||||
|
||||
Python is incredibly powerful, and it appears to be a favorite in both the scripting and programming categories. As someone who knows Bash and a little PHP, I think it's clear what I need to focus on as I delve into the world of development. Meaningful whitespace, here I come!
|
||||
|
||||
- Python 37.1%
|
||||
- Bash/Shell scripts 27%
|
||||
- Perl 11.8%
|
||||
- PHP 8.4%
|
||||
- JavaScript 6.7%
|
||||
- Ruby 4.9%
|
||||
- Other 2.1%
|
||||
- Lua 2%
|
||||
|
||||
### Best New Linux/Open-Source Product/Project ###
|
||||
|
||||

|
||||
|
||||
Docker is clearly our winner here, and rightly so—what a game-changing technology. It's nice to see Jolla/Sailfish get some love as well. We love Android, but having a choice is a vital part of who we are as Open Source advocates.
|
||||
|
||||
- Docker 28%
|
||||
- Jolla and Sailfish OS 19%
|
||||
- LibreOffice 7%
|
||||
- ownCloud 5%
|
||||
- Steam 5%
|
||||
- Zenoss Control Center 5%
|
||||
- Raspberry Pi 4%
|
||||
- Git 4%
|
||||
- Apache Cordova/OpenOffice/Spark/Tika 3%
|
||||
- Ansible 2%
|
||||
- Elementary OS 2%
|
||||
- OpenStack 2%
|
||||
- Zabbix 2%
|
||||
- CoreOS 2%
|
||||
- Firefox OS 2%
|
||||
- KDE Connect 1%
|
||||
- NixOS and NixOps 1%
|
||||
- Open Media Vault 1%
|
||||
|
||||
### Coolest Thing You've Ever Done with Linux ###
|
||||
|
||||

|
||||
|
||||
This is my favorite new category for the Readers' Choice Awards. Imagine attending a Linux conference and asking everyone the coolest thing they've done with Linux. That's basically what happened here! We've listed a handful of our favorites, but for the entire list, check out: [http://www.linuxjournal.com/rc2014/coolest][2].
|
||||
|
||||
Note: the most common answers were "use it"; "rescue data/photos/whatever off broken Windows machines"; "convert friends/family/businesses to Linux"; "learn"; "teach"; "get a job"; "home automation"; and "build a home media server". The following list is of our favorite more-specific and unique answers, not the most common ones.
|
||||
|
||||
- Building my procmail pre-spam spam filter back in the mid-late 1990s.
|
||||
- 450-node compute cluster.
|
||||
- 7.1 channel preamp with integrated mopidy music player.
|
||||
- A robot running Linux (for the Eurobot annual competition).
|
||||
- Accidentally printing on the wrong continent.
|
||||
- Adding an audio channel to a video while also syncing it.
|
||||
- Analyzed NASA satellite data with self-written code.
|
||||
- Annoyed the cat remotely.
|
||||
- Automated my entire lighting setup in my house to respond to voice and my mobile apps.
|
||||
- Automatic window plant irrigation system.
|
||||
- Bathroom radio.
|
||||
- Brewing beer.
|
||||
- Built an application that runs on the International Space Station.
|
||||
- Built a system for real-time toll collection for a major toll highway system.
|
||||
- Built our own smartphone.
|
||||
- Built Web-based home alarm system on Raspberry Pi.
|
||||
- Cluster of Raspberry Pis to crack encrypted office documents.
|
||||
- Controlled my Parrot drone.
|
||||
- Controlled the comms for 186 Wind turbines.
|
||||
- Controlling my Meade Telescope with Stellarium under Linux.
|
||||
- Converted my old VHS family videos, using a laptop more than ten years old.
|
||||
- Created a mesh network in the subarctic.
|
||||
- Created an ocean environmental sensor buoy with radio data transmitter.
|
||||
- Discovered new planets.
|
||||
- Fixed a jabber server in Denver, USA, while in a hotel lobby in Amman, Jordan.
|
||||
- Got Linus' autograph on a Red Hat 5.0 CD.
|
||||
- Hacked my coffee machine to send me a text message when the coffee is ready.
|
||||
- Introduced my daughter to Lego Mindstorm EV3.
|
||||
- Monitor the temp and humidity of my wine cellar and open the doors when too hot or humid.
|
||||
- Replaced the controller in my hot tub with a Raspberry Pi.
|
||||
- Scripted opening and closing of a co-worker's CD tray every 15 seconds for four days.
|
||||
- Used an LFS system to move ACH transfers for a national gas company.
|
||||
- Flushed my toilet from another city.
|
||||
- Remote chicken door.
|
||||
- Web-based sprinkler controller for 16 stations on a Raspberry PI (also control the pool and yard lights).
|
||||
- Chaining SSH tunnels together to get from work to home via three hops due to restrictive network settings.
|
||||
- Built a system that monitors a renewable energy installation with two fixed solar arrays, a two axis sun tracking solar array and a wind turbine. Production and weather data are displayed on a Web site in real time.
|
||||
- Back in the days of modems, I had my computer call up my girlfriend every morning, so she would wake up and go to work.
|
||||
- Used a Wii controller, through Bluetooth with my Linux computer as an Infrared Camera, to detect the movement of my daughter's Fisher Price Sit and Spin Pony, and to control a video game.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxjournal.com/rc2014
|
||||
|
||||
作者:[Shawn Powers][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxjournal.com/users/shawn-powers
|
||||
[1]:http://www.linuxjournal.com/contact
|
||||
[2]:http://www.linuxjournal.com/rc2014/coolest
|
||||
@ -0,0 +1,38 @@
|
||||
Linus Torvalds Thanks Microsoft for a Great Black Friday Monitor Deal
|
||||
================================================================================
|
||||

|
||||
|
||||
> The creator of the Linux kernel now has a UHD display
|
||||
|
||||
**Linus Torvalds is the creator of the Linux Kernel, he advocated for years against Microsoft's practices and he often talked about Windows. These are just some of the reasons why it's funny to see him thank Microsoft, even if it's probably done sarcastically.**
|
||||
|
||||
The rhetoric regarding the Linux vs. Windows subject has subsided a great deal in the last few years. There have been some issues with UEFI and other similar problems, but for the most part things have quieted down.
|
||||
|
||||
There is no one left at the Redmond campus to call Linux a cancer and no one is making fun of Windows for crashing all the time. In fact, there has been some sort of reconciliation between the two sides, which seems to benefit everyone.
|
||||
|
||||
It's not like Microsoft is ready to adopt the Linux kernel for their operating system, but the new management of the company talks about Linux as a friend, especially in the cloud.
|
||||
|
||||
They can no longer ignore it, even if they want to. The same happened with Linus Torvalds who hasn't said anything bad about Microsoft and Windows for a long time, and that is a good thing.
|
||||
|
||||
### Linus Torvalds saying "thanks" to Microsoft is not something you see every day ###
|
||||
|
||||
The creator of the Linux kernel talked about a great Black Friday deal he got from the Microsoft store, for a UHD monitor. He shared this piece of info on Google+ and some of the users also found it amusing to read that he's giving sincere thanks to Microsoft for their great deal.
|
||||
|
||||
"Whee. Just installed a new monitor. 3840x2160 resolution - it's the Dell 28" UHD panel - for $299 (€241) thanks to Microsoft's black Friday deal. Thanks MS! Ok, I have to admit that it's not actually a great panel: very clear color shifts off-center, 30Hz refresh etc. But still - I'm a nut for resolution, and at $299 (€241) I decided that this will carry me over until better panels start showing up at good prices," wrote Linus on [Google+][1].
|
||||
|
||||
In the meantime, he is also working on the latest kernel branch, 3.18, which will probably be released sometime at the end of this week. It's not clear how things will evolve after that, especially given the fact that the holidays are approaching fast, and devs might be a little sluggish when it comes to pushing patches and new features for the next 3.19 branch.
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Linus-Torvalds-Thanks-Microsoft-for-a-Great-Black-Friday-Monitor-Deal-466599.shtml
|
||||
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
[1]:https://plus.google.com/+LinusTorvalds/posts/4MwQKZhGkEr
|
||||
@ -0,0 +1,47 @@
|
||||
U.S. Marine Corps Wants to Change OS for Radar System from Windows XP to Linux
|
||||
================================================================================
|
||||
**A new radar system has been sent back for upgrade**
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
> When it comes to stability and performance, nothing can really beat Linux. This is why the U.S. Marine Corps leaders have decided to ask Northrop Grumman Corp. Electronic Systems to change the operating system of the newly delivered Ground/Air Task-Oriented Radar (G/ATOR) from Windows XP to Linux.
|
||||
|
||||
The Ground/Air Task-Oriented Radar (G/ATOR) system has been in the works for many years and it's very likely that when the project was started, Windows XP could have been considered the logical choice. In the mean time, things changed. Microsoft has pulled the support for Windows XP and very few entities still use it. The operating system is either upgraded or replaced. In this case, Linux is the logical choice, especially since the replacement cost are probably much smaller than an eventual upgrade.
|
||||
|
||||
It's interesting to note that the Ground/Air Task-Oriented Radar (G/ATOR) was just delivered to the U.S. Marine Corps, but the company that built it chose to keep that aging operating system. Someone must have noticed the fact that it was a poor decision and the chain of command was informed of the problems that might have appeared.
|
||||
|
||||
### G/ATOR radar software will be Linux-based ###
|
||||
|
||||
Unix systems, like BSD-based or Linux-based OSes, are usually found in critical areas and technologies that can't fail, under any circumstances. That's why most of the servers out there are running Linux servers, for example. Having a radar system with an operating systems that is very unlikely to crash seems to fit the bill perfectly.
|
||||
|
||||
"Officials of the Marine Corps Systems Command at Quantico Marine Base, Va., announced a $10.2 million contract modification Wednesday to the Northrop Grumman Corp. Electronic Systems segment in Linthicum Heights, Md., to convert the Ground/Air Task-Oriented Radar (G/ATOR) operator command and control computer from Windows XP to Linux. The contract modification will incorporate a change order to switch the G/ATOR control computer from the Microsoft Windows XP operating system to a Defense Information Systems Agency (DISA)-compliant Linux operating system."
|
||||
|
||||
'G/ATOR is an expeditionary, three-dimensional, short-to-medium-range multi-role radar system designed to detect low-observable targets with low radar cross sections such as rockets, artillery, mortars, cruise missiles, and UAVs," reads the entry on [militaryaerospace.com][1].
|
||||
|
||||
This piece of military technology, the Ground/Air Task-Oriented Radar (G/ATOR) was first contracted from the Northrop Grumman Corp. back in 2005, so it's easy to understand why the US Marines might want to hurry this up. No time frame has been proposed for the switch.
|
||||
|
||||
视频链接:[http://youtu.be/H2ppl4x-eu8][2]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/U-S-Marine-Corps-Want-to-Change-OS-for-Radar-System-from-Windows-XP-to-Linux-466756.shtml
|
||||
|
||||
作者:[Silviu Stahie][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
[1]:http://www.militaryaerospace.com/articles/2014/12/gator-linux-software.html
|
||||
[2]:http://youtu.be/H2ppl4x-eu8
|
||||
@ -0,0 +1,42 @@
|
||||
Apparently This Trojan Virus May Have Infected Linux Systems For Years
|
||||
================================================================================
|
||||

|
||||
|
||||
One of the first few argument in [why should you switch to Linux][1] is that Linux is secure and virus free. It is widely perceived by most of the Linux users that Linux is immune to viruses, which is true to an extent but not entirely.
|
||||
|
||||
Like any other OS, Linux too is not immune to malware, trojan, rootkit, virus etc. There have been several [famous Linux viruses][2]. But if you compare those to that of Windows, the number is infinitesimal. So, why am I talking about Linux viruses today then? Because a new trojan has been detected in market which might be impacting Linux systems.
|
||||
|
||||
### Turla infects Linux systems as well ###
|
||||
|
||||
Few months back a sophisticated cyber espionage program, nicknamed [Turla][3], was detected. It was supposed to be originated in Russia, allegedly with Russian government backing. The spyware program was targeting government organizations in Europe and the United States for four years.
|
||||
|
||||
In a recent report, researchers at [Kaspersky][4] has found that Turla was not only affecting Windows system but also Linux operating system. Kaspersky researchers have termed it the ‘missing piece of Turla puzzle’. As per the report:
|
||||
|
||||
> “This newly found Turla component supports Linux for broader system support at victim sites. The attack tool takes us further into the set alongside the Snake rootkit and components first associated with this actor a couple years ago. We suspect that this component was running for years at a victim site, but do not have concrete data to support that statement just yet.”
|
||||
|
||||
### What is this Linux module of Turla and how dangerous it is? ###
|
||||
|
||||
Going by the Kaspersky report,
|
||||
|
||||
> The Linux Turla module is a C/C++ executable statically linked against multiple libraries, greatly increasing its file size. It was stripped of symbol information, more likely intended to increase analysis effort than to decrease file size. Its functionality includes hidden network communications, arbitrary remote command execution, and remote management. Much of its code is based on public sources.
|
||||
|
||||
Report also mentions that this trojan doesn’t require elevated privileges (read root) while running arbitrary remote commands and it cannot be discovered by commonly used administrative tools. Personally, I doubt their claims.
|
||||
|
||||
So, as a Linux desktop user, should you be scared? In my opinion, it is too early to go in to panic mode as we experienced with [ShellShock Linux bug][5]. Turla was originally intended for government organization, not common users. Let’s wait and watch for more concrete news. I’ll keep on updating this article. Till then enjoy Linux.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/apparently-trojan-virus-infected-linux-systems-years/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/Abhishek/
|
||||
[1]:http://itsfoss.com/reasons-switch-linux-windows-xp/
|
||||
[2]:http://www.unixmen.com/meet-linux-viruses/
|
||||
[3]:http://www.reuters.com/article/2014/03/07/us-russia-cyberespionage-insight-idUSBREA260YI20140307
|
||||
[4]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
[5]:http://itsfoss.com/linux-shellshock-check-fix/
|
||||
@ -0,0 +1,35 @@
|
||||
Turla espionage operation infects Linux systems with malware
|
||||
================================================================================
|
||||
|
||||
|
||||
> A newly identified Linux backdoor program is tied to the Turla cyberespionage campaign, researchers from Kaspersky Lab said
|
||||
|
||||
A newly discovered malware program designed to infect Linux systems is tied to a sophisticated cyberespionage operation of Russian origin dubbed Epic Turla, security researchers found.
|
||||
|
||||
The Turla campaign, also known as Snake or Uroburos, [was originally uncovered in February][1], but goes back several years. The massive operation infected computers at government organizations, embassies, military installations, education and research institutions and pharmaceutical companies in over 45 countries.
|
||||
|
||||
The newly identified Turla component for Linux was uploaded recently to a multi-engine antivirus scanning service and was described by security researchers from antivirus vendor Kaspersky Lab as "a previously unknown piece of a larger puzzle."
|
||||
|
||||
"So far, every single Turla sample we've encountered was designed for the Microsoft Windows family, 32 and 64 bit operating systems," the Kaspersky researchers said Monday in a [blog post][2]. "The newly discovered Turla sample is unusual in the fact that it's the first Turla sample targeting the Linux operating system that we have discovered."
|
||||
|
||||
The Turla Linux malware is based on an open-source backdoor program called cd00r developed in 2000. It allows attackers to execute arbitrary commands on a compromised system, but doesn't require elevated privileges or root access to function and listens to commands received via hidden TCP/UDP packets, making it stealthy.
|
||||
|
||||
"It can't be discovered via netstat, a commonly used administrative tool," said the Kaspersky researchers, who are still analyzing the malware's functionality.
|
||||
|
||||
"We suspect that this component was running for years at a victim site, but do not have concrete data to support that statement just yet," they said.
|
||||
|
||||
Since their blog post Monday, the Kaspersky researchers also found a second Turla Linux component that appears to be a separate malware program.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.computerworld.com/article/2857129/turla-espionage-operation-infects-linux-systems-with-malware.html
|
||||
|
||||
作者:[Lucian Constantin][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.computerworld.com/author/Lucian-Constantin/
|
||||
[1]:http://news.techworld.com/security/3505688/invisible-russian-cyberweapon-stalked-us-and-ukraine-since-2005-new-research-reveals/
|
||||
[2]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
@ -0,0 +1,74 @@
|
||||
Yes, This Trojan Infects Linux. No, It’s Not The Tuxpocalypse
|
||||
================================================================================
|
||||

|
||||
|
||||
Is something watching you?
|
||||
|
||||
Grab a crate of canned food, start digging a deep underground bunker and prepare to settle into a world that will never be the same again: [a powerful trojan has been uncovered on Linux][1].
|
||||
|
||||
Yes, the hitherto impregnable fortress of computing nirvana has been compromised in a way that has left security experts a touch perturbed.
|
||||
|
||||
Unplug your PC, disinfect your keyboard and buy a cat (no more YouTube ). The Tuxpocalypse is upon us. We’ve reached the end of days.
|
||||
|
||||
Right? RIGHT? Nah, not quite.
|
||||
|
||||
### A Terrifying Anomalous Thing! ###
|
||||
|
||||
Let me set off by saying that **I am not underplaying the severity of this threat (known by the nickname ‘Turla’)** nor, for the avoidance of doubt, am I suggesting that we as Linux users shouldn’t be concerned by the implications.
|
||||
|
||||
The discovery of a silent trojan infecting Linux systems is terrifying. The fact it was tasked with sucking up and sending off all sorts of sensitive information is horrific. And to learn it’s been doing this for at least four years and doesn’t require root privileges? My seat is wet. I’m sorry.
|
||||
|
||||
But — and along with hyphens and typos, there’s always a ‘but’ on this site — the panic currently sweeping desktop Linux fans, Mexican wave style, is a little out of context.
|
||||
|
||||
Vulnerability may be a new feeling for some of us, yet let’s keep it in check: Linux remains an inherently secure operating system for desktop users. One clever workaround does not negate that and shouldn’t send you scurrying offline.
|
||||
|
||||
### State Sponsored, Targeting Governments ###
|
||||
|
||||

|
||||
|
||||
Is a penguin snake a ‘Penguake’ or a ‘Snaguin’?
|
||||
|
||||
‘Turla’ is a complex APT (Advanced Persistent Threat) that has (thus far) targeted government, embassy and pharmaceutical companies’ systems for around four years using a method based on [14 year old code, no less][2].
|
||||
|
||||
On Windows, where the superhero security researchers at Symantec and Kaspersky Lab first sighted the slimy snake, Turla and components of it were found to have **infected hundreds (100s) of PCs across 45 countries**, many through unpatched zero-day exploits.
|
||||
|
||||
*Nice one Microsoft.*
|
||||
|
||||
Further diligence by Kaspersky Lab has now uncovered that parts of the same trojan have also been active on Linux for some time.
|
||||
|
||||
The Trojan doesn’t require elevated privileges and can “intercept incoming packets and run incoming commands on the system”, but it’s not yet clear how deep its tentacles reach or how many Linux systems are infected, nor is the full extent of its capabilities known.
|
||||
|
||||
“Turla” (and its children) are presumed to be nation-state sponsored due to its choice of targets. US and UK readers shouldn’t assume it’s “*them*“, either. Our own governments are just as happy to play in the mud, too.
|
||||
|
||||
#### Perspective and Responsibility ####
|
||||
|
||||
As terrible a breach as this discovery is emotionally, technically and ethically it remains far, far, far away from being an indication that we’re entering a new “free for all” era of viruses and malware aimed at the desktop.
|
||||
|
||||
**Turla is not a user-focused “i wantZ ur CredIt carD” virus** bundled inside a faux software download. It’s a complex, finessed and adaptable threat with specific targets in mind (ergo grander ambitions than collecting a bunch of fruity tube dot com passwords, sorry ego!).
|
||||
|
||||
Kaspersky Lab explains:
|
||||
|
||||
> “The Linux Turla module is a C/C++ executable statically linked against multiple libraries, greatly increasing its file size. It was stripped of symbol information, more likely intended to increase analysis effort than to decrease file size. Its functionality includes hidden network communications, arbitrary remote command execution, and remote management. Much of its code is based on public sources.”
|
||||
|
||||
Regardless of impact or infection rate its precedes will still raise big, big questions that clever, clever people will now spend time addressing, analysing and (importantly) solving.
|
||||
|
||||
IANACSE (I am not a computer security expert) but IAFOA (I am a fan of acronyms), and AFAICT (as far as I can tell) this news should be viewed as as a cautionary PSA or FYI than the kind of OMGGTFO that some sites are painting it as.
|
||||
|
||||
Until more details are known none of us should panic. Let’s continue to practice safe computing. Avoid downloading/running scripts, apps, or binaries from untrusted sites or PPAs, and don’t venture into dodgy dark parts of the web.
|
||||
|
||||
If you remain super concerned you can check out the [Kaspersky blog][1] for details on how to check that you’re not infected.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/12/government-spying-turla-linux-trojan-found
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
[2]:https://twitter.com/joernchen/status/542060412188262400
|
||||
[3]:https://securelist.com/blog/research/67962/the-penquin-turla-2/
|
||||
@ -1,86 +0,0 @@
|
||||
5 Best Open Source Web Browser Security Apps
|
||||
================================================================================
|
||||
The Web browser acts as the gateway for myriad online services these days. Computer security problems are far from solved, and technology advances provide new ways for malware to infect our devices and enter our business networks. For example, smartphones and tablets offer fresh new fields for malware—and its malicious cousin, "[malvertising][1]"—to exploit.
|
||||
|
||||
Malvertising, or malicious advertising, injects malware into legitimate ads and ad networks. Granted, you could argue that there's a thin line between "legitimate" ads and ad networks and not-legitimate ads and ad networks. But don’t get distracted. Privacy and security are inextricably linked, and protecting your privacy is part of protecting your security.
|
||||
|
||||
Firefox, Chrome, and Opera are the best Web browsers; they offer the best performance, the most compatibility, and the best security. These five open source security apps install in your Web browser, and they protect you from a variety of threats.
|
||||
|
||||
### Protect Your Privacy: Open Source Web Browser Security Apps ###
|
||||
|
||||
#### 1. [AdBlock][2] ####
|
||||
|
||||
Ad networks are wonderful malware vectors. A single ad network serves thousands of sites, so compromising one ad network equals many thousands of compromised machines. AdBlock, and its derivatives—[AdBlock Plus][2], [AdBlock Pro][3], and [AdBlock Edge][4]—are all great tools for blocking ads, which has the added benefit of making cluttery annoying ads-infested sites more usable.
|
||||
|
||||
Of course there is a downside: harming sites that depend on ad revenues. All of them have one-click whitelists, so you can selectively turn off ad-blocking on sites that you want to support. (Really, my dear Webmeisters, if you don't want your site visitors blocking your ads then don't be obnoxious.)
|
||||
|
||||

|
||||
|
||||
Figure 1: Selecting additional filters for your Ad Blocker.
|
||||
|
||||
Ad blockers do more than block ads; they also block Web-tracking bugs and malicious domains. To turn on additional filter lists, click on your ad blocker icon > click **Preferences**, and go to the **Filter Subscriptions** tab. Click the **Add Filter Subscription** button, and then add **Easy Privacy + EasyList**. The Malware Domains filter is a good one to include as well; it blocks domains that are known to host malware and spyware. Adblock works with Firefox, Chrome, Opera, Safari, Internet Explorer, and Android.
|
||||
|
||||
#### 2. [HTTPS Everywhere][5] ####
|
||||
|
||||
HTTPS Everywhere browser extension ensures that you will never accidentally connect to a Web site with HTTP when HTTPS is available. HTTPS means your connection is encrypted with SSL (secure sockets layer), which is a commonly-used protocol for encrypting Web and email connections. HTTPS Everywhere is available for Firefox, Chrome, and Opera.
|
||||
|
||||
When you install HTTPS Everywhere, it asks if you want to enable the SSL Observatory. Say yes, as it offers additional protections against man-in-the-middle and bogus SSL certificate attacks. HTTPS Everywhere works with Firefox, Chrome, Opera, Android.
|
||||
|
||||
#### 3. [Social Fixer][6] ####
|
||||
|
||||
Social Fixer tames Facebook. It gives you mighty powers to filter your news feed so that you see what you want to see, creates tabbed feeds organized by topic, hides whatever you don't want to see, displays pictures full-sized on mouse-over, disables the Theater view of images, and lots more.
|
||||
|
||||
It's not really designed to be a security tool, but Social Fixer offers two important security features:
|
||||
|
||||
- It anonymizes Facebook pages for screenshots by replacing profile pictures with generic icons, and it changes usernames to fake names
|
||||
- It reliably blocks Facebook games, which are notorious sources of trouble
|
||||
|
||||

|
||||
|
||||
Figure 2: Anonymizing a Facebook screen with Social Fixer.
|
||||
|
||||
#### 4. [Privacy Badger][7] ####
|
||||
|
||||
The Electronic Frontier Foundation's Privacy Badger is a superb tracker-and spy-ads blocker. These days Web pages are composed of content from multiple sources: ad servers, comments servers, content farms, image farms, third-party login servers, and gosh knows what-all.
|
||||
|
||||
AdBlock is good at blocking this junk, but Privacy Badger is better. It doesn't rely on filter lists, which have to be maintained by humans somewhere, but rather algorithms and policy methods, and you can easily override it if it blocks something in error. Privacy Badger works with Firefox and Chrome.
|
||||
|
||||

|
||||
|
||||
Figure 3: Privacy Badger blocks tracking sites.
|
||||
|
||||
Privacy Badger should just work. Click on its icon to see what it's blocking on any site you're visiting. Try it on Huffingtonpost.com, one of the champions of stuffing the maximum number of third-party components into each and every page (Figure 3).
|
||||
|
||||
The sliders tell the status of each site: red means that site is completely blocked, so it can't set cookies or serve up any content to you. Yellow indicates a third-party domain that appears to be trying to track you, but it is on Privacy Badger's whitelist of allowed domains. Green is for a third-party domain that is not yet classified as a tracker, but this could change as you visit **multiple** sites and Privacy Badger observes its behavior.
|
||||
|
||||
You can set the sliders yourself according to your preference; for example, on one site I visited Privacy Badger blocked bazaarvoice.com, which some shopping sites use to host their customer reviews.
|
||||
|
||||
#### 5. [Disconnect][8] ####
|
||||
|
||||
Disconnect is another anti-tracker and anti-cookie tool with a great feature set. It runs on Firefox, Chrome, Internet Explorer, and Safari, and offers special iOS and Android versions. Not only does it foil trackers, it also secures your wireless transmissions (Wi-fi, 3G, and 4G) with its own virtual private network, protecting you from wiretapping and malvertising. It protects you from widgetjacking, which is a technique used by attackers to gain access to your sites that require logins. With widgetjacking they don't even need your password; they use stolen cookies.
|
||||
|
||||
Disconnect also provides a safe search feature that lets you use your favorite search engines while blocking their snoopy data-mining habits.
|
||||
|
||||
Just assume that everyone on the Web is out to get you. It's all abstract and behind the scenes, and not obvious like someone bashing a window to get into your house. But the threats are numerous and real, and you have to take precautions to protect yourself.
|
||||
|
||||
Carla Schroder is the author of The Book of Audacity, Linux Cookbook, Linux Networking Cookbook,and hundreds of Linux how-to articles. She's the former managing editor of Linux Planet and Linux Today.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.smallbusinesscomputing.com/biztools/5-best-open-source-web-browser-security-apps.html
|
||||
|
||||
作者:[Carla Schroder][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.smallbusinesscomputing.com/author/Carla-Schroder-6080.html
|
||||
[1]:http://www.webopedia.com/TERM/M/malvertising.html
|
||||
[2]:https://getadblock.com/
|
||||
[3]:https://chrome.google.com/webstore/detail/adblock-pro/ocifcklkibdehekfnmflempfgjhbedch?hl=en-US
|
||||
[4]:https://addons.mozilla.org/en-us/firefox/addon/adblock-edge/
|
||||
[5]:https://www.eff.org/Https-everywhere
|
||||
[6]:http://socialfixer.com/
|
||||
[7]:https://www.eff.org/privacybadger
|
||||
[8]:https://disconnect.me/
|
||||
@ -1,3 +1,4 @@
|
||||
mdjsjdqe translating...
|
||||
11 Useful Utilities To Supercharge Your Ubuntu Experience
|
||||
================================================================================
|
||||
**Whether you’re a relative novice or a seasoned pro, we all want to get the most from our operating system. Ubuntu, like most modern OSes, has more to offer than what is presented at first blush.**
|
||||
@ -151,4 +152,4 @@ via: http://www.omgubuntu.co.uk/2014/11/useful-tools-for-ubuntu-do-you-use-them
|
||||
[7]:https://apps.ubuntu.com/cat/applications/laptop-mode-tools/
|
||||
[8]:https://01.org/linuxgraphics/downloads/2014/intelr-graphics-installer-linux-1.0.7
|
||||
[9]:https://launchpad.net/i-nex
|
||||
[10]:https://apps.ubuntu.com/cat/applications/bleachbit/
|
||||
[10]:https://apps.ubuntu.com/cat/applications/bleachbit/
|
||||
|
||||
@ -1,196 +0,0 @@
|
||||
Five Magnificent Linux Music Streaming Clients
|
||||
================================================================================
|
||||
Digital streams almost totally command my music listening these days. Over the years I have amassed a large collection of CDs at considerable expense; most of them now sit neglected gathering dust. Almost all music streaming services fall short of the audio quality of CDs, but their popularity has more to do with sheer convenience than high-fidelity sound reproduction. Music streaming has not only been to the detriment of CD sales; digital downloads have also experienced a slowing down of sales. This is only set to continue. Audiophiles may be tempted to embrace music streaming given that there are now services such as Tidal which offers high fidelity music streaming, 25 million tracks encoded with the FLAC format streamed at 1,411kbps.
|
||||
|
||||
CDs are not going away though. Music streaming services do experience issues with record labels and artists who are unhappy with the amount of return they receive from letting their music be hosted on the service. This is still in flux; we have seen this year Led Zeppelin, Pink Floyd, Metallica sign up to streaming services, but there are still some notable omissions such as the Beatles, Radiohead and AC/DC who refuse to allow fans to stream their music. Even where a record label or singer has given permission to allow streaming services to access their work, an artist's back catalog can be pulled at a moment's notice. This month, Taylor Swift’s entire catalog of music was pulled from Spotify's streaming service at the pop singer’s request. Some people will still prefer to "possess" their collection, but it's looking like an increasingly old fashioned way to enjoy music.
|
||||
|
||||
The Linux platform has matured into a good way of listening to streaming music services. There are clients available for most of the music streaming services; I hope TIDAL will support Linux on the desktop in due course, and not rely on a web player. All of the applications featured in this article are excellent. An honorable mention should be given to Amarok, pianobar, and Tomahawk.
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Spotify is a proprietary peer-to-peer music streaming service that allows users to listen to tracks or albums on demand. The service describes itself as "A world of music. Instant, simple and free". Spotify uses 96kbps streaming on mobile, 160kbps on desktop and 320kbps for "Premium subscribers" - all encoded in the Ogg Vorbis format. Spotify is free for those who choose to live with adverts, or at a reasonable monthly charge without them.
|
||||
|
||||
Spotify is a fantastic service, offering access to a huge library of music covering all different types of music such as pop, alternative, classical, techno, and rock. It is a great way of dipping into new music. The service has the support of major labels including Sony BMG, EMI, Universal, and Warner Music, as well as independent labels and distribution networks like Labrador Records, The Orchard, Alligator Records, Merlin, CD Baby, INgrooves as well as classical music labels such as Chandos, Naxos, EMI Classic, Warner Classics, Denon Essentials and many more. The breadth of music is continuing to expand at a phenomenal pace.
|
||||
|
||||
Spotify does not officially support Linux at the moment. However, they have developed a preview build of Spotify for Linux, which works well. As its a preview release, this version is still unsupported.
|
||||
|
||||
Spotify is available in Andorra, Argentina, Australia, Austria, Belgium, Bulgaria, Colombia, Cyprus, Denmark, Estonia, Finland, France, Germany, Greece, Hong Kong, Iceland, Ireland, Italy, Latvia, Liechtenstein, Lithuania, Luxembourg, Malaysia, Malta, Mexico, Monaco, Netherlands, New Zealand, Norway, the Philippines, Poland, Portugal, Spain, Singapore, Sweden, Switzerland, Taiwan, Turkey, the United Kingdom, the United States, Uruguay, and a few others.
|
||||
|
||||
**Features include:**
|
||||
|
||||
- A well designed interface makes navigation effortless
|
||||
- Create and edit playlists
|
||||
- Discover new music
|
||||
- Share music and playlists
|
||||
- Radio feature
|
||||
- Top Lists
|
||||
- Additional functionality with large variety of apps
|
||||
|
||||
- Website: [www.spotify.com/uk/download/previews][1]
|
||||
- Developer: Spotify
|
||||
- License: Proprietary
|
||||
- Version Number: Preview
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Pithos is an open source native Pandora Radio client for Linux. It offers a lightweight alternative to the official Pandora.com web client. The graphical user interface integrates with desktop features such as media keys, notifications, and the sound menu.
|
||||
|
||||
The Pandora music service is only intended to be used by US IP addresses. However, users located outside the US can use Pandora with a VPN.
|
||||
|
||||
**Features include: **
|
||||
|
||||
- Play / Pause / Next Song
|
||||
- Switching stations
|
||||
- Remembers your user name and password
|
||||
- Bookmarking of songs and artists
|
||||
- Cover Art
|
||||
- Thumbs Up / Thumbs Down / Tired of this song
|
||||
- Notification popup with song info
|
||||
- Launching pandora.com song info page and station page
|
||||
- Reconnecting when pandora session times out
|
||||
- Editing QuickMix
|
||||
- Creating stations
|
||||
- Media Key support
|
||||
- Proxy support
|
||||
- Last.fm scrobbling support
|
||||
- Volume control
|
||||
- Plugins including Screensaver pause
|
||||
- Two DBUS APIs: MPRIS and Pithos
|
||||
|
||||
- Website: [pithos.github.io][2]
|
||||
- Developer: Kevin Mehall
|
||||
- License: GNU GPL v3
|
||||
- Version Number: 1.0.0
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Clementine is a cross-platform, lightweight, modern music player and library organiser based on Amarok. Clementine focuses on a fast and easy-to-use interface for searching and playing your music.
|
||||
|
||||
It is inspired by Amarok 1.4, focusing on a fast and easy-to-use interface for searching and playing your music.
|
||||
|
||||
Features include:
|
||||
|
||||
- Search and play your local music library
|
||||
- Listen to internet radio from Last.fm and SomaFM
|
||||
- Tabbed playlists, import and export M3U, XSPF, PLS and ASX
|
||||
- Create smart playlists and dynamic playlists
|
||||
- Load M3U and XSPF playlists
|
||||
- Undo and redo in the playlist
|
||||
- Edit tags on MP3 and OGG files, organise your music
|
||||
- Download missing album cover art from Last.fm
|
||||
- Podcast support with integration with gpodder.net
|
||||
- Graphical equalizer
|
||||
- Cross-platform works on Windows, Mac OS X and Linux
|
||||
- Native desktop notifications on Linux (libnotify) and Mac OS X (Growl)
|
||||
- Fetch missing tags from MusicBrainz
|
||||
- Attractive on screen display
|
||||
- Queue manager
|
||||
- Supports MPRIS on Linux, or remote control using the command-line
|
||||
- Supports indexing and playing music from Google Drive
|
||||
- Support for Soundcloud
|
||||
- Support for jazzradio.com
|
||||
- Support for Moodbar
|
||||
- Visualizations from projectM
|
||||
- Copy music to your iPod, iPhone, MTP or mass-storage USB player
|
||||
- Remote control
|
||||
- Transcode music into MP3, Ogg Vorbis, Ogg Speex, FLAC or AAC
|
||||
|
||||
- Website: [www.clementine-player.org][3]
|
||||
- Developer: David Sansome, John Maguire
|
||||
- License: GNU GPL v3
|
||||
- Version Number: 1.2
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Nuvola Player is a free and open source project that offers cloud music integration for your desktop (system tray, Ubuntu sound menu, dock menu and notifications).
|
||||
|
||||
To use all of the streaming services, you need Flash and HTML5 audio support. Some web-based streaming services can utilize HTML5 Audio technology for music playback instead of the Flash plugin. Nuvola Player requires GStreamer with MP3 decoder plugin to provide HTML5 Audio support.
|
||||
|
||||
**Supported Services:**
|
||||
|
||||
- Amazon Cloud Player integrated with the MP3 store and allows users to store their music on Amazon Cloud Drive, and play that music from any supported web browsers
|
||||
- Bandcamp an online music store, as well as a platform for artist promotion, that caters mainly to independent artists
|
||||
- Deezer a French web-based music streaming service. It allows users to listen to music on various devices online or offline. It currently has 18 million licensed tracks, over 30,000 radio channels and 22 million users (1.5 million subscribers)
|
||||
- 8tracks a website that fuses elements of internet radio and social networking revolving around the concept of streaming user-curated playlists consisting of at least 8 tracks
|
||||
- Google Play Music a digital content service from Google which includes an online store for music, movies, books, and Android apps and games, as well as a cloud media player that supports uploading a user's own music and buying music at Google Play Store
|
||||
- Grooveshark an international online music search engine, music streaming service and music recommendation web software application, allowing users to search for, stream, and upload music that can be played immediately or added to a playlist
|
||||
- Grooveshark Mobile the HTML5-based mobile version of Grooveshark which does not require Flash
|
||||
- Hype Machine an amalgamation of Pandora Radio and Pitchfork Media. It aggregates the most recently posted songs from a selection of music blogs (about 1,500) and lists them on the website's main page
|
||||
- Jango a free online music streaming service that allows users to create and share custom radio stations
|
||||
- Logitech Media Server the open source media server for Logitech Squeezebox devices. It supports plug-ins and multiple only services like Deezer or Spotify
|
||||
- Pandora an automated music recommendation service and "custodian" of the Music Genome Project available only in the United States
|
||||
- Rdio an ad-free music subscription service
|
||||
- Spotify a commercial music streaming service providing digital rights management-restricted content from record labels
|
||||
- This is My Jam a place to put your favorite song of the moment & hear great music, handpicked every day by friends
|
||||
|
||||
**Features include:**
|
||||
|
||||
- Multimedia keys
|
||||
- Shows desktop notifications
|
||||
- Integrates with various sound menus, applets and launchers and more
|
||||
- Last FM and Libre FM scrobbling
|
||||
- Lyrics fetching
|
||||
- Support for Amazon Music Prime streaming
|
||||
|
||||
- Website: [tiliado.eu/nuvolaplayer][4]
|
||||
- Developer: Jiří Janoušek and service maintainers
|
||||
- License: 2-Clause BSD license
|
||||
- Version Number: 2.4.3
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Atraci is a multi-platform open source streaming application that lets users listen to more than 60 million songs. It is still in an early stage of development, so the application is not the most feature laden.
|
||||
|
||||
Atraci use iTunes, Last.fm and SoundCloud to display song information - cover, title, artist. Atraci searches the best match for this song on YouTube and streams the highest quality video stream.
|
||||
|
||||
**Features include: **
|
||||
|
||||
- No advertisements, no sign up required
|
||||
- Intuitive user interface
|
||||
- Smart matching search for any song, artist name or album. Atraci checks it against online listings to show correct title, album artwork, track lists and so on, with listed options being the highest quality video streams
|
||||
- Album and artist autosuggestions
|
||||
- Sort results by 'default', 'artist' or ‘track’
|
||||
- View results in 'grid' or 'list' layouts
|
||||
- Accompanying video can be made full screen
|
||||
- Create playlists with shuffle and repeat options
|
||||
- In-app volume slider, track scrubber and album artwork
|
||||
- History of recently played tracks
|
||||
|
||||
- Website: [atraci.github.io/Atraci-website][5]
|
||||
- Developer: The Atraci Team
|
||||
- License: The MIT License
|
||||
- Version Number: 0.7.0
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/20141116052055674/MusicStreaming.html
|
||||
|
||||
作者:Frazer Kline
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://www.spotify.com/uk/download/previews/
|
||||
[2]:http://pithos.github.io/
|
||||
[3]:https://www.clementine-player.org/
|
||||
[4]:https://tiliado.eu/nuvolaplayer/
|
||||
[5]:http://atraci.github.io/Atraci-website/
|
||||
@ -0,0 +1,404 @@
|
||||
Intense Gameplay? Try these 13 Roguelike games
|
||||
================================================================================
|
||||
Roguelike is a sub-genre of role-playing games. It literally means "a game like Rogue". Rogue is a dungeon crawling video game first released in 1980, standing out for being fiendishly addictive. Its goal was to retrieve the Amulet of Yendor, hidden deep in the 26th level, and ascend back to the top.
|
||||
|
||||
There is no exact definition of a roguelike, but this type of game typically has the following characteristics:
|
||||
|
||||
- High fantasy narrative background
|
||||
- Procedural level generation. Most of the game world is generated by the game for every new gameplay session. This is meant to encourage replayability
|
||||
- Turn-based dungeon exploration and combat
|
||||
- Tile-based graphics that are randomly generated
|
||||
- Random conflict outcomes
|
||||
- Permanent death death works realistically, once you're gone, you're gone
|
||||
- High difficulty
|
||||
|
||||
This article compiles a good selection of roguelike games available for Linux. If you enjoy intense, addictive gameplay, try these 13 games. Don't be put off by the primitive graphics, you'll soon forget the visuals once you get immersed. All of them are available to download without charge, and almost all are released under an open source license.
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Dungeon Crawl Stone Soup is an open-source, single-player, role-playing roguelike game of exploration and treasure-hunting in dungeons filled with dangerous and unfriendly monsters in a quest to rescue the mystifyingly fabulous Orb of Zot.
|
||||
|
||||
Dungeon Crawl Stone Soup is a continuation of Linley's Dungeon Crawl. It is openly developed and invites participation from the Crawl community.
|
||||
|
||||
Dungeon Crawl has superb, deep tactical gameplay, innovative magic and religion systems, and a grand variety of monsters to fight. Crawl is also one of the hardest roguelikes to beat. When you finally beat the game and write your victory post on rec.games.roguelike.misc, you know you have achieved something.
|
||||
|
||||
Features include:
|
||||
|
||||
- Well-rounded, deep tactically rich roguelike
|
||||
- Hand-drawn maps
|
||||
- Numerous portal vaults
|
||||
- Slick interface
|
||||
- Innovative magic and religion systems
|
||||
- Wide range of Gods, Characters, Items, and Smart Monsters
|
||||
|
||||
- Website: [crawl.develz.org][1]
|
||||
- Developer: Stone Soup devteam
|
||||
- License: Crawl General Public License
|
||||
- Version Number: 0.15.2
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Dwarf Fortress is a single-player fantasy game, similar to NetHack. You can control a dwarven outpost or an adventurer in a randomly generated, persistent world.
|
||||
|
||||
The game features three modes of play (Dwarf Fortress, Adventurer and Legends modes), a distinct, randomly-generated world (complete with terrain, wildlife and legends), gruesome combat mechanics and vicious schools of carp.
|
||||
|
||||
Features include:
|
||||
|
||||
|
||||
- The world persists as long as you like, over many games, recording historical events and tracking changes
|
||||
- Command your dwarves as they search for wealth in the mountain
|
||||
- Craft treasures and furniture from many materials and improve these objects with precious metals, jewels and more
|
||||
- Defend yourself against attacks from hostile civilizations, the wilderness and the depths
|
||||
- Support the nobility as they make demands of your populace
|
||||
- Keep your dwarves happy and read their thoughts as they work and relax
|
||||
- Z coordinate allows you to dig out fortresses with multiple levels. Build towers or conquer the depths
|
||||
- Build floodgates to divert water for farming or to drown your adversaries
|
||||
- Play an adventurer and explore, quest for glory or seek vengeance
|
||||
- Meet adversaries from previous games
|
||||
- Recruit people in towns to come with you on your journey
|
||||
- Explore without cumbersome plot restrictions
|
||||
- Seamlessly wander the world -up to 197376 x 197376 squares total -or travel more rapidly on the region map
|
||||
- Accept quests from the town and civilization leaders
|
||||
- Retire and meet your old characters. Bring them along on an adventure with a new character or reactivate them and play directly
|
||||
- Z coordinate allows you to move seamlessly between dungeon levels and scale structures fighting adversaries above and below
|
||||
- The combat model uses skills, body parts, wrestling, charging and dodging between squares, bleeding, pain, nausea, and much more
|
||||
- A dynamic weather model tracks wind, humidity and air masses to create fronts, clouds, rain storms and blizzards
|
||||
- Over two hundred rock and mineral types are incorporated into the world, placed in their proper geological environments
|
||||
- Add new creatures, weapons, plants, metals and other objects via modifiable text files
|
||||
- Extended ASCII character set rendered in 16 colors (including black) as well as 8 background colors (including black)
|
||||
|
||||
- Website: [www.bay12games.com/dwarves/][2]
|
||||
- Developer: Tarn Adams
|
||||
- License: Freeware
|
||||
- Version Number: 0.40.19
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Ancient Domains of Mystery (ADOM) is a rogue-like game which has been in development since 1994.
|
||||
|
||||
It is a single-user game featuring the exploration of a dungeon complex. You control a fictional character described by race, class, attributes, skills, and equipment. This fictional character is trying to achieve a specific goal (see below) and succeed in a difficult quest. To fulfill the quest, you have to explore previously undiscovered tunnels and dungeons, fight hideous monsters, uncover long forgotten secrets, and find treasures of all kind.
|
||||
|
||||
During the game, you explore dungeon levels which are randomly generated each game. You might also encounter certain special levels, which present a particular challenge or are built around a certain theme.
|
||||
|
||||
Features include:
|
||||
|
||||
- Huge game world with hundreds of locations such as towns, randomized dungeons, elemental temples, graveyards, ancient ruins, towers and other secrets
|
||||
- Loads of races (dwarves, drakelings, mist elves, hurthlings, orcs, trolls, ratlings and many others) and even more classes (fighters, elementalists, assassins, chaos knights, duelists and much more) allowing for infinite play styles
|
||||
- Hundreds of monsters and items, many with enhanced random features
|
||||
- A corruption system forcing you to balance lust for power with fear of damnation
|
||||
- Spells, prayers, mindcraft, alchemy, crafting and more
|
||||
- Dozens of quests and branching story lines
|
||||
- Numerous wildly different endings that might alter reality itself
|
||||
|
||||
- Website: [www.adom.de][3]
|
||||
- Developer: Thomas Biskup
|
||||
- License: Postcardware
|
||||
- Version Number: 1.20 Prelease 20
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Tales of Maj’Eyal (ToME) is a free, open source roguelike RPG, featuring tactical turn-based combat and advanced character building. It is written as a module that runs in T-Engine 4.0.
|
||||
|
||||
This is the Age of Ascendancy, after over ten thousand years of strife, pain and chaos the known world is at last at relative peace. The Spellblaze last effects are now tamed, the land slowly heals itself and the civilisations rebuild themselves after the Age of Pyre.
|
||||
|
||||
Features include:
|
||||
|
||||
- Suitable for gamers without any rogueline experience
|
||||
- Supports both graphical tiles and ASCII mode
|
||||
- Over 40 abilities available on some characters
|
||||
- Talent system
|
||||
- Combat engine
|
||||
- Online persistent stat/achievement tracking
|
||||
- IRC chat client
|
||||
- Expandable and moddable
|
||||
- Atmospheric music
|
||||
- Unlock new races, classes, starting points, playmodes and features
|
||||
|
||||
- Website: [te4.org][4]
|
||||
- Developer: ToME Development Team
|
||||
- License: GNU GPL v3.0
|
||||
- Version Number: 1.2.5
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Cataclysm is an open source post-apocalyptic roguelike, set in the countryside of fictional New England after a devastating plague of monsters and zombies. It is a continuation of Whale's original Cataclysm, which expands it with numerous new creatures, buildings, gameplay mechanics and many other features.
|
||||
|
||||
While some have described it as a "zombie game", there's far more to Cataclysm than that. Struggle to survive in a harsh, persistent, procedurally generated world. Scavenge the remnants of a dead civilization for for food, equipment, or, if you're lucky, a vehicle with a full tank of gas to get you the hell out of Dodge. Fight to defeat or escape from a wide variety of powerful monstrosities, from zombies to giant insects to killer robots and things far stranger and deadlier, and against the others like yourself, that want what you have...
|
||||
|
||||
Cataclysm is very different from most roguelikes in many ways. Rather than being set in a vertical, linear dungeon, it is set in an unbounded, 3D world. This means that exploration plays a much bigger role than in most roguelikes, and the game is much less linear. As the map is so huge, it is actually completely persistant between games. If you die, and start a new character, your new game will be set in the same game world as your last. Like in many roguelikes, you will be able to loot the dead bodies of previous characters; unlike most roguelikes, you will also be able to retrace their steps completely, and any dramatic changes made to the world will persist into your next game.
|
||||
|
||||
Features include:
|
||||
|
||||
|
||||
- Detailed character creation, with a plethora of traits to choose
|
||||
- Defense mode, a coffeebreak mode with fast-paced combat
|
||||
- Bionics; Similar to the magic system in many games
|
||||
- Mutations, both positive and negative
|
||||
- Unbounded, fully randomized world map that is persistent between characters
|
||||
- Item crafting
|
||||
- New recipes may be acquired by honing your knowledge through practice or learning from books
|
||||
- Realistic fire, smoke, and other dynamic map effects
|
||||
- A day/night cycle with the need to sleep. Use caffeine to stay awake longer if you must but be aware this is not healthy
|
||||
- Over 300 item types, including a multitude of real-world guns, drugs, and tools
|
||||
- Many drugs are addictive, and will require continuous use to avoid withdrawal effects.
|
||||
- Ability to board doors and windows, construct traps and fortify your home base to prevent a rude awakening by a zombie
|
||||
- Ability to construct your own wooden constructions, including walls and a roof
|
||||
- Ability to drive around in vehicles found in the post-apocalyptic landscape
|
||||
- These can be modified to your needs, or you could even build one from scratch
|
||||
- A temperature system, being too cold or too hot is quite hazardous
|
||||
- Preliminary tile support
|
||||
- WorldGen options, and versatile editing methods
|
||||
-
|
||||
- Website: [en.cataclysmdda.com][5]
|
||||
- Authors: Kevin Granade and others
|
||||
- License: Creative Commons Attribution-ShareAlike 3.0 Unported License
|
||||
- Version Number: 0.B
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Goblin Hack is an open source roguelike OpenGL-based smooth-scrolling ASCII graphics game. The game is inspired by the likes of NetHack, but faster with fewer keys.
|
||||
|
||||
Goblin Hack has a simple interface that appears to appeal to players of all ages, and fires their imagination in today's world of over-rendered games.
|
||||
|
||||
Players can choose one of several classes before being thrown into the first floor of a randomized, ongoing dungeon.
|
||||
|
||||
Features include:
|
||||
|
||||
- Impressive graphics (compared with many other roguelike games)
|
||||
- Simple interface
|
||||
- Choose one of several classes before being thrown into the first floor of a randomized, ongoing dungeon
|
||||
- Manually save the game
|
||||
|
||||
- Website: [goblinhack.sourceforge.net][6], [github.com/goblinhack/goblinhack][7]
|
||||
- Authors: Neil McGill
|
||||
- License: GNU GPL v2
|
||||
- Version Number: 1.19
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Super Lotsa Added Stuff Hack - Extended Magic (SLASH'EM) is a role-playing game where you control a single character. SLASH'EM is a variant of NetHack. It also has an interface and gameplay similar to Rogue, ADOM, Anghand and NetHack. You control the actions through the keyboard and view the world from an overhead perspective.
|
||||
|
||||
The problem: The Amulet of Yendor has been stolen. Not only that but it appears that the Wizard of Yendor (not a nice person), who took the amulet, is hiding in the Dungeons of Doom (not a friendly place).
|
||||
|
||||
Features include:
|
||||
|
||||
- Offers extra features, monsters, and items
|
||||
- Novel features inlude the Monk class and Sokoban levels
|
||||
- The main dungeon is much larger than in NetHack
|
||||
|
||||
- Website: [www.slashem.org][8]
|
||||
- Developer: The Slash'EM development team
|
||||
- License: MIT License, NetHack General Public License
|
||||
- Version Number: 0.0.7E7F3
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
NetHack is a wonderfully silly, yet quite addictive Dungeons and Dragons-style adventure game. The "net" element references that its development has been coordinated through the Internet. The "hack" element refers to a genre of role-playing games known as hack and slash for their focus on combat.
|
||||
|
||||
In NetHack you play the part of a fierce fighter, wizard, or any of many other classes, fighting your way down to retrieve the Amulet of Yendor (try saying THAT one backwards!) for your god. On the way, you might encounter a quantum mechanic or two, or perhaps a microscopic space fleet, or -- if you're REALLY lucky -- the Ravenous Bugblatter Beast of Traal.
|
||||
|
||||
Features include:
|
||||
|
||||
- 45-50 levels, most of which are randomly generated
|
||||
- Variety of items: weapons, armour, scrolls, potions, rings, gems, and an assortment of tools such as keys and lamps
|
||||
- Blessings and curses
|
||||
- Permadeath: expired characters cannot be revived without having made backup copies of the actual save files
|
||||
- Interfaces:
|
||||
- Console
|
||||
- Graphical, using X, Qt toolkit or GNOME libraries
|
||||
|
||||
- Website: [www.nethack.org][9]
|
||||
- Developer: The NetHack DevTeam
|
||||
- License: NetHack General Public License
|
||||
- Version Number: 3.4.3
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Ascii Sector is a free space combat/exploration/trading game which is based on the classic computer game Wing Commander: Privateer released by Origin Systems in 1993.
|
||||
|
||||
In Ascii Sector, you start with a simple spaceship and can then accept missions or trade goods to earn enough money to upgrade your ship or buy a new one. You can engage in deadly fights both in space, on the ground and on board spaceships, and using the Ascii Sector scripting language, you can create your own quests for the game or have fun with other players' quests.
|
||||
|
||||
Features include:
|
||||
|
||||
- Uses the ANSI character set for the graphics
|
||||
- Real depth to the gameplay
|
||||
- Offers a wide variety of bases, missions, commodities and ships
|
||||
- Ships include: Broadsword, Centurion, Demon, Dralthi, Drayman, Galaxy, Gladius, Gothri, Kamekh, Nexus, Orion, Paradign, Stileto, Talon, Tarsus, and Ulysses
|
||||
- Four quadrants: Alizarin, Crimson, Mauve, and Viridian
|
||||
- Downloadable quests
|
||||
- Scripting of quests
|
||||
- Ascii Sector quest language, create your own stories in the Ascii Sector universe
|
||||
- NPCs on planets can be attacked and robbed
|
||||
- Persistent fleets that can move around, change control of systems, engage enemy fleets, head back for repairs and rebuilds
|
||||
- Ships whose systems have been disabled can be boarded
|
||||
- Download high quality music files
|
||||
|
||||
- Website: [www.asciisector.net][10]
|
||||
- Developer: Christian Knudsen
|
||||
- License: Freeware
|
||||
- Version Number: 0.7.1.4
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Angband is a free, single-player graphical dungeon exploration game that uses ASCII characters where you take the role of an adventurer, exploring a deep dungeon, fighting monsters, and acquiring the best weaponry you can, in preparation for a final battle with Morgoth, the Lord of Darkness. It has been in development since the 1990s.
|
||||
|
||||
Angband is along the lines of Rogue and NetHack. It is derived from the games Moria and Umoria, which were in turn based on Rogue. It is often described as a "roguelike" game because the look and feel of the game is still quite similar to Rogue. Many of these new creatures and objects are drawn from the writings of J.R.R Tolkien, although some of the monsters come straight from classical mythology, Dungeons & Dragons, Rolemaster, or the minds of the orginal Angband coders.
|
||||
|
||||
Features include:
|
||||
|
||||
- 100 level dungeon
|
||||
- New levels are randomly generated
|
||||
- Choose to be a human, half-elf, elf, hobbit, gnome, dwarf, half-orc, half-troll, dunadan, high-elf, or kobold
|
||||
- Artifacts
|
||||
- Spellcasting
|
||||
- Monsters
|
||||
- Monster pits
|
||||
- Monster nests
|
||||
|
||||
- Website: [rephial.org][11]
|
||||
- Developer: Angband Development Team
|
||||
- License: GNU GPL v2
|
||||
- Version Number: 3.5.0
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
UnNetHack is a fork of NetHack. NetHack was first released in 1987, and is considered by many gamers to be one of the best gaming experiences the computing world offers.
|
||||
|
||||
Features include:
|
||||
|
||||
|
||||
- Adds a number of enhancements to NetHack such as additional monsters, more levels, a few new objects, additional dangers, more challenging gameplay, and most importantly more entertainment than vanilla NetHack
|
||||
- Tutorial to help new players get started
|
||||
|
||||
- Website: [sourceforge.net/apps/trac/unnethack][12]
|
||||
- Authors: Patric Mueller
|
||||
- License: Nethack General Public License
|
||||
- Version Number: 5.1.0
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Hydra Slayer is an open source Roguelike game focused on slaying Hydras. It is inspired by Greek mythology, Dungeon Crawl, MathRL seven day roguelike, and some mathematical puzzles about brave heroes slaying many headed beasts.
|
||||
|
||||
Features include:
|
||||
|
||||
- Unique gameplay mechanics
|
||||
- A theme which mixes Greek mythology and mathematics
|
||||
- Traditional roguelike ASCII graphics, or tiles/3D display
|
||||
- 5 player character races with very distinct tactics, strengths and weaknesses
|
||||
- 28 enemy types:
|
||||
- 10 basic types of elemental hydras (each of them has two special variations)
|
||||
- 8 types of special enemies
|
||||
- Harmless mushrooms for strategic advantage
|
||||
- 28 types of equipment (not counting material and size/power variations)
|
||||
- 15 weapon materials
|
||||
- 18 types of non-equipment items
|
||||
- 3 game geometries to choose
|
||||
- 8 level topologies (including the Mobius strip and Klein bottle)
|
||||
- 11 level generators
|
||||
- 2 endings
|
||||
|
||||
- Website: [www.roguetemple.com/z/hydra][13]
|
||||
- Developer: Zeno Rogue
|
||||
- License: GNU GPL v2
|
||||
- Version Number: 16.1
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Brogue is an open source Roguelike game for Mac OS X, Windows, Linux, iOS and Android.
|
||||
|
||||
Brogue is a direct descendant of Rogue, a dungeon crawling video game first developed by Michael Toy and Glenn Wichman around 1980. Unlike other popular modern roguelikes, Brogue favors simplicity over complexity, while trying to ensure that the interactions between components are interesting and varied.
|
||||
|
||||
The goal of the game is to travel to the 26th subterranean floor of the dungeon, retrieve the Amulet of Yendor and return with it to the surface. For the truly skillful who desire further challenge, depths below 26 contain three lumenstones each, items which confer an increased score upon victory.
|
||||
|
||||
Brogue is a challenging game, but still great fun to play. Try not to be disheartened by the difficulty of the game; with some application, Brogue will become very addictive.
|
||||
|
||||
Features include:
|
||||
|
||||
- Favors simplicity over complexity
|
||||
- User-friendly features
|
||||
- Compared with Rogue, Brogue has a more sophisticated level generation
|
||||
- XP and levelling system removed
|
||||
- Traps, protecting items
|
||||
- Additional monster types and magical items
|
||||
|
||||
- Website: [sites.google.com/site/broguegame][14]
|
||||
- Authors: Brian Walker
|
||||
- License: GNU Affero GPL
|
||||
- Version Number: 1.7.3
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/201412031524381/RoguelikeGames.html
|
||||
|
||||
作者:Frazer Kline
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://crawl.develz.org/
|
||||
[2]:http://www.bay12games.com/dwarves/index.html
|
||||
[3]:http://www.adom.de/
|
||||
[4]:http://te4.org/
|
||||
[5]:http://en.cataclysmdda.com/
|
||||
[6]:http://goblinhack.sourceforge.net/
|
||||
[7]:https://github.com/goblinhack/goblinhack
|
||||
[8]:http://www.slashem.org/
|
||||
[9]:http://www.nethack.org/
|
||||
[10]:http://www.asciisector.net/
|
||||
[11]:http://rephial.org/
|
||||
[12]:http://sourceforge.net/apps/trac/unnethack/
|
||||
[13]:http://www.roguetemple.com/z/hydra/
|
||||
[14]:https://sites.google.com/site/broguegame/
|
||||
104
sources/share/20141211 NetHack.md
Normal file
104
sources/share/20141211 NetHack.md
Normal file
@ -0,0 +1,104 @@
|
||||
[Translating by Stevearzh]
|
||||
NetHack
|
||||
================================================================================
|
||||
## The best game of all time? ##
|
||||
|
||||
**It’s tremendously addictive. It takes a lifetime to master. And people play it for decades without completing it. Welcome to the strange world of NetHack…**
|
||||
|
||||
Believe it or not, it’s possible to be terrified by the sight of the letter D. Or ecstatic about the sight of a % character. (And the less said about ^, the better.) But before you assume we’ve gone totally loopy and close the tab, bear with us for a moment: those characters represent dragons, food rations and traps respectively. Welcome to NetHack, where your imagination needs to play a big role in the gameplay.
|
||||
|
||||
You see, NetHack is a text-mode game: it just uses the standard terminal character set to portray the player, enemies, items and surroundings. Graphical versions of the game exist, but NetHack purists tend to avoid them, and what’s the point of a game if you can’t play it when you’re SSHed into your revived Amiga 3000 running NetBSD? In some ways, NetHack is a lot like Vi – it has been ported to nigh-on every operating system in existence, and its requirements are absolutely minimal.
|
||||
|
||||
Now, given that it looks like utter pants when compared to modern games, what makes NetHack so appealing? Well, this dungeon exploring masterpiece is incredibly rich and detailed. There are so many items to discover, spells to cast, monsters to fight and tricks to learn – and the dungeons are generated randomly. There’s so much to explore, and no two games are ever the same. People play NetHack for years and decades without complete it, still discovering new secrets each time.
|
||||
|
||||
Here we’ll show you how NetHack came about, give you a guided tour of the dungeons, and show you some tricks. Note: by reading this feature, you agree to not sue us when you become addicted to NetHack and your real-life productivity is obliterated.
|
||||
|
||||

|
||||
|
||||
The NetHack interface
|
||||
|
||||
### Possibly the oldest still-developed game ###
|
||||
|
||||
Despite its name, NetHack isn’t an online game. It’s based on an earlier dungeon-exploring romp called Hack, which in turn was a descendant of an 1980 game called Rogue. NetHack’s first release arrived in 1987, and although no new features have been added since version 3.4.3 in 2003, various patches, add-ons and spin-offs are still doing the rounds on the web. This makes it arguably the oldest game that’s still being hacked on and played by a sizeable group of people. Go to [www.reddit.com/r/nethack][1] to see what we mean – long-time NetHack players are still discussing new strategies, discoveries and tricks. Occasionally you’ll see gleeful messages from old timers who have finally, after many years, completed the game.
|
||||
|
||||
But how do you complete it? Well, NetHack is set in a large and deep dungeon. You start at the top – level 1 – and your goal is to keep going down until you find a hugely valuable item called the Amulet of Yendor. This is typically in level 20 or lower, but it can vary. As you traverse through and down the dungeon, you’ll meet all manner of monsters, traps and human characters; some will try to kill you, some will stay out of your way, and some…. well, you don’t know until you get close to them.
|
||||
|
||||
> There’s so much to learn, and many items only work best when combined with others.
|
||||
|
||||
What makes NetHack so compelling is the vast range of items crammed into the game. Weapons, armour, spell books, rings, gems – there’s so much to learn, and many items only work best when combined with others. Monsters often drop useful items when you kill them, although some items can have very negative effects if you don’t use them correctly. You’ll find shops in the dungeon that are packed with potentially useful bits of kit, but don’t expect the shopkeeper to give you great descriptions. You’ve got to learn from experience. Some items aren’t much use at all, and the game is packed with humour – you can even throw a cream pie in your own face.
|
||||
|
||||
But before you even set foot in the dungeon, NetHack asks you what kind of player you want to be. You can take your journey as a knight, a monk, a wizard or even a humble tourist, amongst many other player types. They all have their own strengths and weaknesses, and NetHack addicts love to try completing the game with the weaker types. You know, to show off to other players.
|
||||
|
||||
> ## Spoilers don’t spoil the fun ##
|
||||
|
||||
> In NetHack parlance, “spoilers” provide information on monsters, items, weapons and armour. It’s technically possible to complete the game without using them, but very few players ever achieve this, as the game is monumentally complex. Consequently it’s not regarded as bad form to use spoilers – but it’s still more fun to try to work things out yourself first, and only consult the spoilers when you really need them.
|
||||
|
||||
> A great source is [www.statslab.cam.ac.uk/~eva/nethack/spoilerlist.html][2] which separates spoilers into categories. For things that happen randomly in the game, such as the effects from drinking from fountains, it gives you the odds of a certain thing happening.
|
||||
|
||||
### Your first dungeon crawl ###
|
||||
|
||||
NetHack is available for almost every major OS and Linux distribution in the world, so you should be able to grab it with “apt-get install nethack” or “yum install nethack” or whatever is appropriate for your distro. Then run it in a terminal window by just typing “nethack”. The game will ask if it should pick a player type for you – but as a newcomer, it’s best if you choose one of the tougher characters first. So hit “n” and then hit “v” to choose the Valkyrie type, and “d” to be a dwarf.
|
||||
|
||||
Then NetHack will give you some plot blurb, explaining that your god seeks the Amulet of Yendor, so your goal is to retrieve it and present it to him. Hit space when you’re done reading the text (and any other time you see “–More–” on the screen). And here we go – you’re in the dungeon!
|
||||
|
||||
As described earlier, your character is represented by a @ sign. You can see the walls of a room around you, and the dot characters depict empty space in the room. First of all, get used to the movement keys: h, j, k and l. (Yes, it’s just like Vim, as covered in issue 3 of Linux Voice!) These move you left, down, up and right respectively. You can also move diagonally with y, u, b and n. So walk around the room until you get used to the controls.
|
||||
|
||||
NetHack is turn-based, so if you’re not moving or performing an action, the game stays still. This lets youplan your moves in advance. You will see a “d” or “f” character moving around the room as well: this is your pet dog or cat, which (normally) won’t harm you and can assist you in killing monsters. Pets can be annoying though – they occasionally eat foot rations and tasty corpses before you get to them.
|
||||
|
||||

|
||||
|
||||
Hit “i” to bring up an inventory of your currently carried items
|
||||
|
||||
### What’s behind the door? ###
|
||||
|
||||
Now, let’s go out of the room. There will be gaps around the edge, and possibly “+” signs. That “+” is a closed door, so go up to it and hit “o” to open. You will be asked for a direction, so if the door is to the left of you, press “h”. (And if the door is stuck, try opening it a few times.) You’ll then end up in a corridor, marked by “#” symbols, so walk around it until you find another room.
|
||||
|
||||
On your travels you’ll see various items. Some, such as money (denoted by a “$” symbol) are picked up automatically; for other items, you have to press the comma key whilst standing on them. If there are multiple items, you’ll be given a menu, so press the appropriate keys shown in the menu and then Enter to choose what you want. At any time you can hit “i” to bring up your inventory list – see the screenshot.
|
||||
|
||||
What happens if you see a monster? At these early stages of the game, the monsters you’re likely to come across will be represented by “d”, “x” and “:” characters. To attack, simply walk into them. The game will tell you if your attacks are successful using the messages along the top – and also how the monster is responding. These early monsters are simple to kill, so you shouldn’t have any trouble defeating them, but keep an eye on your HP in the status line at the bottom.
|
||||
|
||||
> Early monsters are simple to kill, but keep an eye on your HP.
|
||||
|
||||
If a monster leaves behind a corpse (“%”), you can hit comma to take it and then press “e” to eat it. (Whenever you’re prompted to choose an item, you can press its corresponding key from the inventory list, or “?” to bring up a mini list.) Warning! Some corpses are poisonous, and these are things you’ll learn on your travels.
|
||||
|
||||
If you’re exploring a corridor and appear to come to a dead end, you can hit “s” to search until you find a door. This can take ages, however, so you can speed things up a bit: type “10” and then “s” and you will perform 10 searches in a row. This takes up 10 moves in game time, however, so if you’re hungry you could get close to starvation!
|
||||
|
||||
Common items you’ll find in the top levels of the dungeon are “{” (fountains) and “!” (potions). For the former, you can stand on it and hit q to “quaff” from it – the effects can vary from useful to deadly. For potions, pick them up and then use “q” to drink them. If you find a shop, you can pick up items and then hit “p” to pay before leaving. Use “d” to drop something.
|
||||
|
||||

|
||||
|
||||
Souped-up versions of NetHack with fancy graphics are available, such as Falcon’s Eye
|
||||
|
||||
> ## Stupid ways to die ##
|
||||
|
||||
> A popular acronym amongst NetHack players is “YASD” – Yet Another Stupid Death. It describes a situation where the player buys the farm due to his/her own silliness or lack of concentration. We’ve had many of these, but our favourite goes as follows:
|
||||
|
||||
> We were browsing a shop, inspecting items, when a snake suddenly jumped out from behind a potion. After killing the snake, a message popped up saying that we were getting hungry, so we opted to eat the snake’s corpse. Bad idea! This made us blind, so we couldn’t see other characters or items in the shop. We tried to get to the exit, but instead bumped into the shopkeeper and accidentally attacked him. This made him furious; he started firing magic missiles at us. We just about managed to get into the corridor outside the shop, but died from the onslaught.
|
||||
|
||||
> If you come to any equally silly ends, let us know on our forums. And don’t worry – nobody will judge you. Dying like this is all part of growing up in the NetHack world.
|
||||
|
||||
### Equip yourself ###
|
||||
|
||||
On your travels, and especially after you kill monsters, you’ll find weapons and armour. Again, use comma to pick these up, and then “w” (lowercase) to wield a weapon or “W” (uppercase) to wear a piece of armour. You can use “T” to remove armour and “t” to throw weapons – often handy if you’re in a very sticky situation.
|
||||
|
||||
Sometimes it’s useful to examine things from a distance before getting close to them. Hit “;” (semicolon) and “Pick an object” will appear at the top of the screen. Use the movement keys until your view lands on the thing you want to inspect, and then hit “:” (colon). A description will appear at the top.
|
||||
|
||||
As your goal is to go further down the dungeon until you find the Amulet of Yendor, keep an eye out for “<” and “>” signs. These are stairs up and down respectively, and you can use the same keys to climb them. Note! Make sure your pet is standing in an adjacent square if you want it to follow you into the next level. If you need a break, use “S” (capital s) to save, and type #quit to exit. Next time you run NetHack, your game will be resumed.
|
||||
|
||||
We won’t spoil what’s ahead, as many of the dungeon levels have amazing designs, characters and secrets. So we’ll leave you with three tips: if you come across an item that completely baffles you, try searching for it on the NetHack wiki at [http://nethack.wikia.com][3]. You’ll also find an excellent (albeit very long) guidebook at [www.nethack.org/v343/Guidebook.html][4]. Happy exploring!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxvoice.com/nethack/
|
||||
|
||||
作者:[Mike Saunders][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linuxvoice.com/author/mike/
|
||||
[1]:http://www.reddit.com/r/nethack
|
||||
[2]:http://www.statslab.cam.ac.uk/~eva/nethack/spoilerlist.html
|
||||
[3]:http://nethack.wikia.com/
|
||||
[4]:http://www.nethack.org/v343/Guidebook.html
|
||||
@ -1,107 +0,0 @@
|
||||
Translating by GOLinux!
|
||||
When Microsoft Went A-Courting
|
||||
================================================================================
|
||||

|
||||
|
||||
**Open-sourcing .Net "doesn't have a thing to do with Linux -- it has to do with SaaS and having a CEO that isn't a whackadoo living in the 90s," said SoylentNews blogger hairyfeet. "Nadella is smart and realizes the value of a programming language is not patents or OS exclusivity but in services and support for the language. ... The more platforms the language can be used on, the better."**
|
||||
|
||||
Fans of free and open source software perhaps may be excused if they've felt a bit confused over the past few days. Dizziness, headaches and vertigo also have been common.
|
||||
|
||||
What strange new ailment is this, you might ask?
|
||||
|
||||
Well, it's no ailment, Linux Girl is glad to report. That, however, doesn't mean it's any simpler to remedy.
|
||||
|
||||
The cause, it turns out, is none other than the news that Microsoft is open sourcing .Net and also expanding it to run on Linux and Mac OS.
|
||||
|
||||
Yes, you heard that right: Steve Ballmer once may have [called Linux a "cancer,"][1] but today Redmond has a newfound "[love" for Linux][2] that can't be contained!
|
||||
|
||||
It's making Microsoft behave in strange new ways -- and it's also driving FOSS fans to the blogosphere's seedy Broken Windows Lounge in greater numbers than ever.
|
||||
|
||||
Can tequila help make sense of it all? That's one of many questions now being investigated.
|
||||
|
||||
### 'A Chance to Thrive' ###
|
||||
|
||||
"This is big news, and somewhat overdue," Chris Travers, a [blogger][3] who works on the [LedgerSMB][4] project, told Linux Girl.
|
||||
|
||||

|
||||
|
||||
"We live in a world where new programming languages which are open sourced thrive even without being backed by big businesses, and closed source programming languages only survive with help from big businesses," Travers said. "Bing closed source killed REBOL 2.x," for example.
|
||||
|
||||
"This move has clearly been in the works for some time -- a large company like Microsoft does not open source something of this complexity overnight -- and I think to some extent Microsoft must have seen the writing on the wall when Sun open sourced the OpenJDK," he suggested.
|
||||
|
||||
Meanwhile, "this gives languages like C# and F# a chance to thrive well beyond their current markets," Travers said.
|
||||
|
||||
### 'I Still Don't Trust You' ###
|
||||
|
||||
"I want to be the first to say, 'Thank you Microsoft!'" [Linux Rants][5] blogger Mike Stone began. "We really appreciate you open sourcing .Net and taking it cross platform. It's a step in the right direction!
|
||||
|
||||
"I still don't trust you, though," he added.
|
||||
|
||||
"I love that Microsoft is considering open source, but I have seen no movement towards the GPL," Stone told Linux Girl. "This strikes me as an opportunity to get their software on multiple platforms but tie the developers down to Microsoft."
|
||||
|
||||
Moreover, there are no guarantees that Microsoft will keep .Net open source over the years, he pointed out.
|
||||
|
||||
"That means that Microsoft could withdraw and leave all applications developed with the intention of being cross platform legally Windows-only," he warned. "I won't put any faith in Microsoft's commitment, and I'll always be looking for their sudden but inevitable betrayal."
|
||||
|
||||
### 'Watch for Greeks Bearing Gifts' ###
|
||||
|
||||
The move reeks of desperation, Google+ blogger Alessandro Ebersol suggested.
|
||||
|
||||
"They arrived too late," Ebersol said. "Java already ate the best dishes, and while .Net was a Windows/Microsoft-only thing, Java was everywhere. Good luck trying to be adopted."
|
||||
|
||||
Besides, "I would only believe it if it was GPL'ed to protect the creators of the code," he added. "A fragile MIT license can be overturned at anytime."
|
||||
|
||||
In any case, "with all the hatred the company generated towards the FLOSS community, they burned the bridge beyond repair," Ebersol concluded. "The bottom line: Timeo Danaos et dona ferentes -- Watch carefully for Greeks bearing gifts..."
|
||||
|
||||
### 'Like a Cat Loves Mice' ###
|
||||
|
||||
Microsoft loves Linux "like a cat loves mice," blogger [Robert Pogson][6] quipped. "Sure, they will play with */Linux, but they are not our friends."
|
||||
|
||||
What's happened is that the FOSS and Linux communities have defeated "all the barriers to entry that M$ placed in the way of competition since M$ first made a deal with IBM to supply an OS," Pogson said. "You bet M$ is trying desperately to 'make friends' with 'the enemy' now that their position is overrun.
|
||||
|
||||
"It's all good," he added. "M$ can still cause a lot of trouble by spending $billions foolishly or they can become a normal business and compete on price/performance. That's not 'love' -- that's accepting reality."
|
||||
|
||||
### Adapt or Die ###
|
||||
|
||||
The problem for Microsoft is that "open source development packages are starting to get good enough for developers," offered consultant and [Slashdot][7] blogger Gerhard Mack.
|
||||
|
||||
"At my last job, most of the programmers wanted Eclipse rather than Visual Studio, even though the client software was Windows-only, and I had a slowly increasing number move their development to Linux while using Windows for testing," Mack recalled.
|
||||
|
||||
"Very few people want to be locked into just one platform, so more of the mindshare is moving away from single-platform languages," he added. "Microsoft must now choose between adapting or dying."
|
||||
|
||||
### No Warm Fuzzies Here ###
|
||||
|
||||
art of what's driving the move is also that "the various cloud implementations are very heavily Linux, and even on Microsoft's own Azure cloud, Linux is a strong presence," Google+ blogger Kevin O'Brien suggested.
|
||||
|
||||
"Nadella has made it clear he is taking Microsoft in a cloud direction, so he almost has to do this to even stay in the game," O'Brien asserted.
|
||||
|
||||
That said, however, "I don't expect Microsoft to be cuddly and nice -- they will do whatever they think is in their best corporate interest," he said.
|
||||
|
||||
In fact, "it doesn't have a thing to do with Linux -- it has to do with SaaS and having a CEO that isn't a whackadoo living in the 90s," SoylentNews blogger hairyfeet told Linux Girl.
|
||||
|
||||
"Nadella is smart and realizes the value of a programming language is not patents or OS exclusivity but in services and support for the language," hairyfeet explained. "With that in mind, the more platforms the language can be used on, the better, as that adds value to the language and will give you that many more you can sell services to."
|
||||
|
||||
### The Fall of an Empire ###
|
||||
|
||||
ll in all, if anything is clear, it's that "Micro$oft's empire is tumbling down," said Google+ blogger Gonzalo Velasco C.
|
||||
|
||||
"I don't know or care about why they are lying and saying they love Linux," he added. "I just hope the GNU/Linux community is smarter than recently (cough, Systemd, cough) and refuses Micro$oft .Net and other infections. GNU/Linux must use only FLOSS tools."
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxinsider.com/story/When-Microsoft-Went-A-Courting-81374.html
|
||||
|
||||
作者:[Katherine Noyes][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://twitter.com/noyesk
|
||||
[1]:http://www.linuxinsider.com/perl/story/35697.html
|
||||
[2]:http://www.theregister.co.uk/2014/10/20/microsoft_cloud_event/
|
||||
[3]:http://ledgersmbdev.blogspot.com/
|
||||
[4]:http://www.ledgersmb.org/
|
||||
[5]:http://linuxrants.com/
|
||||
[6]:http://mrpogson.com/
|
||||
[7]:http://slashdot.org/
|
||||
@ -1,56 +0,0 @@
|
||||
翻译中 by coloka
|
||||
Four ways Linux is headed for no-downtime kernel patching
|
||||
================================================================================
|
||||

|
||||
Credit: Shutterstock
|
||||
|
||||
These technologies are competing to provide the best way to patch the Linux kernel without reboots or downtime
|
||||
|
||||
Nobody loves a reboot, especially not if it involves a late-breaking patch for a kernel-level issue that has to be applied stat.
|
||||
|
||||
To that end, three projects are in the works to provide a mechanism for upgrading the kernel in a running Linux instance without having to reboot anything.
|
||||
|
||||
### Ksplice ###
|
||||
|
||||
The first and original contender is Ksplice, courtesy of a company of the same name founded in 2008. The kernel being replaced does not have to be pre-modified; all it needs is a diff file listing the changes to be made to the kernel source. Ksplice, Inc. offered support for the (free) software as a paid service and supported most common Linux distributions used in production.
|
||||
|
||||
All that changed in 2011, when [Oracle purchased the company][1], rolled the feature into its own Linux distribution, and kept updates for the technology to itself. As a result, other intrepid kernel hackers have been looking for ways to pick up where Ksplice left off, without having to pay the associated Oracle tax.
|
||||
|
||||
### Kgraft ###
|
||||
|
||||
In February 2014, Suse provided the exact solution needed: [Kgraft][2], its kernel-update technology released under a mixed GPLv2/GPLv3 license and not kept close as a proprietary creation. It's since been [submitted][3] as a possible inclusion to the mainline Linux kernel, although Suse has rolled a version of the technology into [Suse Linux Enterprise Server 12][4].
|
||||
|
||||
Kgraft works roughly like Ksplice by using a set of diffs to figure out what parts of the kernel to replace. But unlike Ksplice, Kgraft doesn't need to stop the kernel entirely to replace it. Any running functions can be directed to their old or new kernel-level counterparts until the patching process is finished.
|
||||
|
||||
### Kpatch ###
|
||||
|
||||
Red Hat came up with its own no-reboot kernel-patch mechanism, too. Also introduced earlier this year -- right after Suse's work in that vein, no less -- [Kpatch][5] works in roughly the same manner as Kgraft.
|
||||
|
||||
The main difference, [as outlined][6] by Josh Poimboeuf of Red Hat, is that Kpatch doesn't redirect calls to old kernel functions. Rather, it waits until all function calls have stopped, then swaps in the new kernel. Red Hat's engineers consider this approach safer, with less code to maintain, albeit at the cost of more latency during the patch process.
|
||||
|
||||
Like Kgraft, Kpatch has been submitted for consideration as a possible kernel inclusion and can be used with Linux kernels other than Red Hat's. The bad news is that Kpatch isn't yet considered production-ready by Red Hat. It's included as part of Red Hat Enterprise Linux 7, but only in the form of a technology preview.
|
||||
|
||||
### ...or Kgraft + Kpatch? ###
|
||||
|
||||
A fourth solution [proposed by Red Hat developer Seth Jennings][7] early in November 2014 is a mix of both the Kgraft and Kpatch approaches, using patches built for either one of those solutions. This new approach, Jennings explained, "consists of a live patching 'core' that provides an interface for other 'patch' kernel modules to register patches with the core." This way, the patching process -- specifically, how to deal with any running kernel functions -- can be handled in a more orderly fashion.
|
||||
|
||||
The sheer newness of these proposals means it'll be a while before any of them are officially part of the Linux kernel, although Suse's chosen to move fast and made it a part of its latest enterprise offering. Let's see if Red Hat and Canonical choose to follow suit in the short run as well.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.infoworld.com/article/2851028/linux/four-ways-linux-is-headed-for-no-downtime-kernel-patching.html
|
||||
|
||||
作者:[Serdar Yegulalp][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.infoworld.com/author/Serdar-Yegulalp/
|
||||
[1]:http://www.infoworld.com/article/2622437/open-source-software/oracle-buys-ksplice-for-linux--zero-downtime--tech.html
|
||||
[2]:http://www.infoworld.com/article/2610749/linux/suse-open-sources-live-updater-for-linux-kernel.html
|
||||
[3]:https://lwn.net/Articles/596854/
|
||||
[4]:http://www.infoworld.com/article/2838421/linux/suse-linux-enterprise-12-goes-light-on-docker-heavy-on-reliability.html
|
||||
[5]:https://github.com/dynup/kpatch
|
||||
[6]:https://lwn.net/Articles/597123/
|
||||
[7]:http://lkml.iu.edu/hypermail/linux/kernel/1411.0/04020.html
|
||||
157
sources/talk/20141203 Docker--Present and Future.md
Normal file
157
sources/talk/20141203 Docker--Present and Future.md
Normal file
@ -0,0 +1,157 @@
|
||||
disylee占个坑~
|
||||
Docker: Present and Future
|
||||
================================================================================
|
||||
### Docker - the story so far ###
|
||||
|
||||
Docker is a toolset for Linux containers designed to ‘build, ship and run’ distributed applications. It was first released as an open source project by DotCloud in March 2013. The project quickly became popular, leading to DotCloud rebranded as Docker Inc (and ultimately [selling off their original PaaS business][1]). [Docker 1.0][2] was released in June 2014, and the monthly release cadence that led up to the June release has been sustained since.
|
||||
|
||||
The 1.0 release marked the point where Docker Inc considered the platform sufficiently mature to be used in production (with the company and partners providing paid for support options). The monthly release of point updates shows that the project is still evolving quickly, adding new features, and addressing issues as they are found. The project has however successfully decoupled ‘ship’ from ‘run’, so images sourced from any version of Docker can be used with any other version (with both forward and backward compatibility), something that provides a stable foundation for Docker use despite rapid change.
|
||||
|
||||
The growth of Docker into one of the most popular open source projects could be perceived as hype, but there is a great deal of substance. Docker has attracted support from many brand names across the industry, including Amazon, Canonical, CenturyLink, Google, IBM, Microsoft, New Relic, Pivotal, Red Hat and VMware. This is making it almost ubiquitously available wherever Linux can be found. In addition to the big names many startups are growing up around Docker, or changing direction to be better aligned with Docker. Those partnerships (large and small) are helping to drive rapid evolution of the core project and its surrounding ecosystem.
|
||||
|
||||
### A brief technical overview of Docker ###
|
||||
|
||||
Docker makes use of Linux kernel facilities such as [cGroups][3], namespaces and [SElinux][4] to provide isolation between containers. At first Docker was a front end for the [LXC][5] container management subsystem, but release 0.9 introduced [libcontainer][6], which is a native Go language library that provides the interface between user space and the kernel.
|
||||
|
||||
Containers sit on top of a union file system, such as [AUFS][7], which allows for the sharing of components such as operating system images and installed libraries across multiple containers. The layering approach in the filesystem is also exploited by the [Dockerfile][8] DevOps tool, which is able to cache operations that have already completed successfully. This can greatly speed up test cycles by taking out the wait time usually taken to install operating systems and application dependencies. Shared libraries between containers can also reduce RAM footprint.
|
||||
|
||||
A container is started from an image, which may be locally created, cached locally, or downloaded from a registry. Docker Inc operates the [Docker Hub public registry][9], which hosts official repositories for a variety of operating systems, middleware and databases. Organisations and individuals can host public repositories for images at Docker Hub, and there are also subscription services for hosting private repositories. Since an uploaded image could contain almost anything Docker Hub provides an automated build facility (that was previously called ‘trusted build’) where images are constructed from a Dockerfile that serves as a manifest for the contents of the image.
|
||||
|
||||
### Containers versus VMs ###
|
||||
|
||||
Containers are potentially much more efficient than VMs because they’re able to share a single kernel and share application libraries. This can lead to substantially smaller RAM footprints even when compared to virtualisation systems that can make use of RAM overcommitment. Storage footprints can also be reduced where deployed containers share underlying image layers. IBM’s Boden Russel has done [benchmarking][10] that illustrates these differences.
|
||||
|
||||
Containers also present a lower systems overhead than VMs, so the performance of an application inside a container will generally be the same or better versus the same application running within a VM. A team of IBM researchers have published a [performance comparison of virtual machines and Linux containers][11].
|
||||
|
||||
One area where containers are weaker than VMs is isolation. VMs can take advantage of ring -1 [hardware isolation][12] such as that provided by Intel’s VT-d and VT-x technologies. Such isolation prevents VMs from ‘breaking out’ and interfering with each other. Containers don’t yet have any form of hardware isolation, which makes them susceptible to exploits. A proof of concept attack named [Shocker][13] showed that Docker versions prior to 1.0 were vulnerable. Although Docker 1.0 fixed the particular issue exploited by Shocker, Docker CTO Solomon Hykes [stated][14], “When we feel comfortable saying that Docker out-of-the-box can safely contain untrusted uid0 programs, we will say so clearly.”. Hykes’s statement acknowledges that other exploits and associated risks remain, and that more work will need to be done before containers can become trustworthy.
|
||||
|
||||
For many use cases the choice of containers or VMs is a false dichotomy. Docker works well within a VM, which allows it to be used on existing virtual infrastructure, private clouds and public clouds. It’s also possible to run VMs inside containers, which is something that Google uses as part of its cloud platform. Given the widespread availability of infrastructure as a service (IaaS) that provides VMs on demand it’s reasonable to expect that containers and VMs will be used together for years to come. It’s also possible that container management and virtualisation technologies might be brought together to provide a best of both worlds approach; so a hardware trust anchored micro virtualisation implementation behind libcontainer could integrate with the Docker tool chain and ecosystem at the front end, but use a different back end that provides better isolation. Micro virtualisation (such as Bromium’s [vSentry][15] and VMware’s [Project Fargo][16]) is already used in desktop environments to provide hardware based isolation between applications, so similar approaches could be used along with libcontainer as an alternative to the container mechanisms in the Linux kernel.
|
||||
|
||||
### ‘Dockerizing’ applications ###
|
||||
|
||||
Pretty much any Linux application can run inside a Docker container. There are no limitations on choice of languages or frameworks. The only practical limitation is what a container is allowed to do from an operating system perspective. Even that bar can be lowered by running containers in privileged mode, which substantially reduces controls (and correspondingly increases risk of the containerised application being able to cause damage to the host operating system).
|
||||
|
||||
Containers are started from images, and images can be made from running containers. There are essentially two ways to get applications into containers - manually and Dockerfile..
|
||||
|
||||
#### Manual builds ####
|
||||
|
||||
A manual build starts by launching a container with a base operating system image. An interactive terminal can then be used to install applications and dependencies using the package manager offered by the chosen flavour of Linux. Zef Hemel provides a walk through of the process in his article ‘[Using Linux Containers to Support Portable Application Deployment][17]’. Once the application is installed the container can be pushed to a registry (such as Docker Hub) or exported into a tar file.
|
||||
|
||||
#### Dockerfile ####
|
||||
|
||||
Dockerfile is a system for scripting the construction of Docker containers. Each Dockerfile specifies the base image to start from and then a series of commands that are run in the container and/or files that are added to the container. The Dockerfile can also specify ports to be exposed, the working directory when a container is started and the default command on startup. Containers built with Dockerfiles can be pushed or exported just like manual builds. Dockerfiles can also be used in Docker Hub’s automated build system so that images are built from scratch in a system under the control of Docker Inc with the source of that image visible to anybody that might use it.
|
||||
|
||||
#### One process? ####
|
||||
|
||||
Whether images are built manually or with Dockerfile a key consideration is that only a single process is invoked when the container is launched. For a container serving a single purpose, such as running an application server, running a single process isn’t an issue (and some argue that containers should only have a single process). For situations where it’s desirable to have multiple processes running inside a container a [supervisor][18] process must be launched that can then spawn the other desired processes. There is no init system within containers, so anything that relies on systemd, upstart or similar won’t work without modification.
|
||||
|
||||
### Containers and microservices ###
|
||||
|
||||
A full description of the philosophy and benefits of using a microservices architecture is beyond the scope of this article (and well covered in the [InfoQ eMag: Microservices][19]). Containers are however a convenient way to bundle and deploy instances of microservices.
|
||||
|
||||
Whilst most practical examples of large scale microservices deployments to date have been on top of (large numbers of) VMs, containers offer the opportunity to deploy at a smaller scale. The ability for containers to have a shared RAM and disk footprint for operating systems, libraries common application code also means that deploying multiple versions of services side by side can be made very efficient.
|
||||
|
||||
### Connecting containers ###
|
||||
|
||||
Small applications will fit inside a single container, but in many cases an application will be spread across multiple containers. Docker’s success has spawned a flurry of new application compositing tools, orchestration tools and platform as a service (PaaS) implementations. Behind most of these efforts is a desire to simplify the process of constructing an application from a set of interconnected containers. Many tools also help with scaling, fault tolerance, performance management and version control of deployed assets.
|
||||
|
||||
#### Connectivity ####
|
||||
|
||||
Docker’s networking capabilities are fairly primitive. Services within containers can be made accessible to other containers on the same host, and Docker can also map ports onto the host operating system to make services available across a network. The officially sponsored approach to connectivity is [libchan][20], which is a library that provides Go like [channels][21] over the network. Until libchan finds its way into applications there’s room for third parties to provide complementary network services. For example, [Flocker][22] has taken a proxy based approach to make services portable across hosts (along with their underlying storage).
|
||||
|
||||
#### Compositing ####
|
||||
|
||||
Docker has native mechanisms for linking containers together where metadata about a dependency can be passed into the dependent container and consumed within as environment variables and hosts entries. Application compositing tools like [Fig][23] and [geard][24] express the dependency graph inside a single file so that multiple containers can be brought together into a coherent system. CenturyLink’s [Panamax][25] compositing tool takes a similar underlying approach to Fig and geard, but adds a web based user interface, and integrates directly with GitHub so that applications can be shared.
|
||||
|
||||
#### Orchestration ####
|
||||
|
||||
Orchestration systems like [Decking][26], New Relic’s [Centurion][27] and Google’s [Kubernetes][28] all aim to help with the deployment and life cycle management of containers. There are also numerous examples (such as [Mesosphere][29]) of [Apache Mesos][30] (and particularly its [Marathon][31] framework for long running applications) being used along with Docker. By providing an abstraction between the application needs (e.g. expressed as a requirement for CPU cores and memory) and underlying infrastructure, the orchestration tools provide decoupling that’s designed to simplify both application development and data centre operations. There is such a variety of orchestration systems because many have emerged from internal systems previously developed to manage large scale deployments of containers; for example Kubernetes is based on Google’s [Omega][32] system that’s used to manage containers across the Google estate.
|
||||
|
||||
Whilst there is some degree of functional overlap between the compositing tools and the orchestration tools there are also ways that they can complement each other. For example Fig might be used to describe how containers interact functionally whilst Kubernetes pods might be used to provide monitoring and scaling.
|
||||
|
||||
#### Platforms (as a Service) ####
|
||||
|
||||
A number of Docker native PaaS implementations such as [Deis][33] and [Flynn][34] have emerged to take advantage of the fact that Linux containers provide a great degree of developer flexibility (rather than being ‘opinionated’ about a given set of languages and frameworks). Other platforms such as CloudFoundry, OpenShift and Apcera Continuum have taken the route of integrating Docker based functionality into their existing systems, so that applications based on Docker images (or the Dockerfiles that make them) can be deployed and managed alongside of apps using previously supported languages and frameworks.
|
||||
|
||||
### All the clouds ###
|
||||
|
||||
Since Docker can run in any Linux VM with a reasonably up to date kernel it can run in pretty much every cloud offering IaaS. Many of the major cloud providers have announced additional support for Docker and its ecosystem.
|
||||
|
||||
Amazon have introduced Docker into their Elastic Beanstalk system (which is an orchestration service over underlying IaaS). Google have Docker enabled ‘managed VMs’, which provide a halfway house between the PaaS of App Engine and the IaaS of Compute Engine. Microsoft and IBM have both announced services based on Kubernetes so that multi container applications can be deployed and managed on their clouds.
|
||||
|
||||
To provide a consistent interface to the wide variety of back ends now available the Docker team have introduced [libswarm][35], which will integrate with a multitude of clouds and resource management systems. One of the stated aims of libswarm is to ‘avoid vendor lock-in by swapping any service out with another’. This is accomplished by presenting a consistent set of services (with associated APIs) that attach to implementation specific back ends. For example the Docker server service presents the Docker remote API to a local Docker command line tool so that containers can be managed on an array of service providers.
|
||||
|
||||
New service types based on Docker are still in their infancy. London based Orchard labs offered a Docker hosting service, but Docker Inc said that the service wouldn’t be a priority after acquiring Orchard. Docker Inc has also sold its previous DotCloud PaaS business to cloudControl. Services based on older container management systems such as [OpenVZ][36] are already commonplace, so to a certain extent Docker needs to prove its worth to hosting providers.
|
||||
|
||||
### Docker and the distros ###
|
||||
|
||||
Docker has already become a standard feature of major Linux distributions like Ubuntu, Red Hat Enterprise Linux (RHEL) and CentOS. Unfortunately the distributions move at a different pace to the Docker project, so the versions found in a distribution can be well behind the latest available. For example Ubuntu 14.04 was released with Docker 0.9.1, and that didn’t change on the point release upgrade to Ubuntu 14.04.1 (by which time Docker was at 1.1.2). There are also namespace issues in official repositories since Docker was also the name of a KDE system tray; so with Ubuntu 14.04 the package name and command line tool are both ‘docker.io’.
|
||||
|
||||
Things aren’t much different in the Enterprise Linux world. CentOS 7 comes with Docker 0.11.1, a development release that precedes Docker Inc’s announcement of production readiness with Docker 1.0. Linux distribution users that want the latest version for promised stability, performance and security will be better off following the [installation instructions][37] and using repositories hosted by Docker Inc rather than taking the version included in their distribution.
|
||||
|
||||
The arrival of Docker has spawned new Linux distributions such as [CoreOS][38] and Red Hat’s [Project Atomic][39] that are designed to be a minimal environment for running containers. These distributions come with newer kernels and Docker versions than the traditional distributions. They also have lower memory and disk footprints. The new distributions also come with new tools for managing large scale deployments such as [fleet][40] ‘a distributed init system’ and [etcd][41] for metadata management. There are also new mechanisms for updating the distribution itself so that the latest versions of the kernel and Docker can be used. This acknowledges that one of the effects of using Docker is that it pushes attention away from the distribution and its package management solution, making the Linux kernel (and Docker subsystem using it) more important.
|
||||
|
||||
New distributions might be the best way of running Docker, but traditional distributions and their package managers remain very important within containers. Docker Hub hosts official images for Debian, Ubuntu, and CentOS. There’s also a ‘semi-official’ repository for Fedora images. RHEL images aren’t available in Docker Hub, as they’re distributed directly from Red Hat. This means that the automated build mechanism on Docker Hub is only available to those using pure open source distributions (and willing to trust the provenance of the base images curated by the Docker Inc team).
|
||||
|
||||
Whilst Docker Hub integrates with source control systems such as GitHub and Bitbucket for automated builds the package managers used during the build process create a complex relationship between a build specification (in a Dockerfile) and the image resulting from a build. Non deterministic results from the build process isn’t specifically a Docker problem - it’s a result of how package managers work. A build done one day will get a given version, and a build done another time may get a later version, which is why package managers have upgrade facilities. The container abstraction (caring less about the contents of a container) along with container proliferation (because of lightweight resource utilisation) is however likely to make this a pain point that gets associated with Docker.
|
||||
|
||||
### The future of Docker ###
|
||||
|
||||
Docker Inc has set a clear path on the development of core capabilities (libcontainer), cross service management (libswarm) and messaging between containers (libchan). Meanwhile the company has already shown a willingness to consume its own ecosystem with the Orchard Labs acquisition. There is however more to Docker than Docker Inc, with contributions to the project coming from big names like Google, IBM and Red Hat. With a benevolent dictator in the shape of CTO Solomon Hykes at the helm there is a clear nexus of technical leadership for both the company and the project. Over its first 18 months the project has shown an ability to move fast by using its own output, and there are no signs of that abating.
|
||||
|
||||
Many investors are looking at the features matrix for VMware’s ESX/vSphere platform from a decade ago and figuring out where the gaps (and opportunities) lie between enterprise expectations driven by the popularity of VMs and the existing Docker ecosystem. Areas like networking, storage and fine grained version management (for the contents of containers) are presently underserved by the existing Docker ecosystem, and provide opportunities for both startups and incumbents.
|
||||
|
||||
Over time it’s likely that the distinction between VMs and containers (the ‘run’ part of Docker) will become less important, which will push attention to the ‘build’ and ‘ship’ aspects. The changes here will make the question of ‘what happens to Docker?’ much less important than ‘what happens to the IT industry as a result of Docker?’.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.infoq.com/articles/docker-future
|
||||
|
||||
作者:[Chris Swan][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.infoq.com/author/Chris-Swan
|
||||
[1]:http://blog.dotcloud.com/dotcloud-paas-joins-cloudcontrol
|
||||
[2]:http://www.infoq.com/news/2014/06/docker_1.0
|
||||
[3]:https://www.kernel.org/doc/Documentation/cgroups/cgroups.txt
|
||||
[4]:http://selinuxproject.org/page/Main_Page
|
||||
[5]:https://linuxcontainers.org/
|
||||
[6]:http://blog.docker.com/2014/03/docker-0-9-introducing-execution-drivers-and-libcontainer/
|
||||
[7]:http://aufs.sourceforge.net/aufs.html
|
||||
[8]:https://docs.docker.com/reference/builder/
|
||||
[9]:https://registry.hub.docker.com/
|
||||
[10]:http://bodenr.blogspot.co.uk/2014/05/kvm-and-docker-lxc-benchmarking-with.html?m=1
|
||||
[11]:http://domino.research.ibm.com/library/cyberdig.nsf/papers/0929052195DD819C85257D2300681E7B/$File/rc25482.pdf
|
||||
[12]:https://en.wikipedia.org/wiki/X86_virtualization#Hardware-assisted_virtualization
|
||||
[13]:http://stealth.openwall.net/xSports/shocker.c
|
||||
[14]:https://news.ycombinator.com/item?id=7910117
|
||||
[15]:http://www.bromium.com/products/vsentry.html
|
||||
[16]:http://cto.vmware.com/vmware-docker-better-together/
|
||||
[17]:http://www.infoq.com/articles/docker-containers
|
||||
[18]:http://docs.docker.com/articles/using_supervisord/
|
||||
[19]:http://www.infoq.com/minibooks/emag-microservices
|
||||
[20]:https://github.com/docker/libchan
|
||||
[21]:https://gobyexample.com/channels
|
||||
[22]:http://www.infoq.com/news/2014/08/clusterhq-launch-flocker
|
||||
[23]:http://www.fig.sh/
|
||||
[24]:http://openshift.github.io/geard/
|
||||
[25]:http://panamax.io/
|
||||
[26]:http://decking.io/
|
||||
[27]:https://github.com/newrelic/centurion
|
||||
[28]:https://github.com/GoogleCloudPlatform/kubernetes
|
||||
[29]:https://mesosphere.io/2013/09/26/docker-on-mesos/
|
||||
[30]:http://mesos.apache.org/
|
||||
[31]:https://github.com/mesosphere/marathon
|
||||
[32]:http://static.googleusercontent.com/media/research.google.com/en/us/pubs/archive/41684.pdf
|
||||
[33]:http://deis.io/
|
||||
[34]:https://flynn.io/
|
||||
[35]:https://github.com/docker/libswarm
|
||||
[36]:http://openvz.org/Main_Page
|
||||
[37]:https://docs.docker.com/installation/#installation
|
||||
[38]:https://coreos.com/
|
||||
[39]:http://www.projectatomic.io/
|
||||
[40]:https://github.com/coreos/fleet
|
||||
[41]:https://github.com/coreos/etcd
|
||||
48
sources/talk/20141204 CoreOS breaks with Docker.md
Normal file
48
sources/talk/20141204 CoreOS breaks with Docker.md
Normal file
@ -0,0 +1,48 @@
|
||||
CoreOS breaks with Docker
|
||||
================================================================================
|
||||
> Summary: CoreOS, a new enterprise Linux company and a Docker partner, is now proposing its own alternative to Docker's container technology.
|
||||
|
||||
[Docker][1] exploded out of nowhere in 2014 to make container technology white hot in cloud and datacenter technical circles. Even [Microsoft joined its open-source virtualization revolution][2]. Now, however, early Docker supporter [CoreOS][3], a new large-scale Linux distributor vendor, is turning its back on it and developing its own container technology: [Rocket][4].
|
||||
|
||||

|
||||
|
||||
While [CoreOS][5] is relatively unknown outside of Linux circles and Silicon Valley, it's seen by those in the know as an up and coming Linux distribution for datacenters and clouds. It's not an insignificant company crying foul, because [Docker's take on virtualization has proven to be so popular][6]. Indeed, CoreOS currently requires Docker to work well, and Brandon Philips, CoreOS' co-founder and CTO, has been a top Docker contributor and was serving on the Docker governance board.
|
||||
|
||||
So, why is CoreOS breaking with Docker? First, because "We believe strongly in the Unix philosophy: Tools should be independently useful, but have clean integration points." However, it also said that "Docker now is building tools for launching cloud servers, systems for clustering, and a wide range of functions: Building images, running images, uploading, downloading, and eventually even overlay networking, all compiled into one monolithic binary running primarily as root on your server."
|
||||
|
||||
In short, instead of Docker being a Unix-style, simple reusable component, CoreOS sees Docker becoming a platform. And CoreOS has no interest in that.
|
||||
|
||||
Instead, with Rocket, they propose going back to the [original Docker proposal][7] for what a container should be.
|
||||
|
||||
CoreOS spells out that Rocket will be:
|
||||
|
||||
- **Composable**: All tools for downloading, installing, and running containers should be well integrated, but independent and composable.
|
||||
- **Secure**: Isolation should be pluggable, and the crypto primitives for strong trust, image auditing, and application identity should exist from day one.
|
||||
- **Image distribution**: Discovery of container images should be simple and facilitate a federated namespace and distributed retrieval. This opens the possibility of alternative protocols, such as BitTorrent, and deployments to private environments without the requirement of a registry.
|
||||
- **Open**: The format and runtime should be well specified and developed by a community. We want independent implementations of tools to be able to run the same container consistently.
|
||||
|
||||
To do this, CoreOS is not forking Docker. Alex Polvi, CoreOS' CEO, wrote, "From a security and composability perspective, the Docker process model — where everything runs through a central daemon — is fundamentally flawed. To 'fix' Docker would essentially mean a rewrite of the project, while inheriting all the baggage of the existing implementation."
|
||||
|
||||
CoreOS already has an [alpha version of Rocket on GitHub][8], but it's still open to other ideas on how to build a Docker alternative. At the same time, however, CoreOS states that it won't be leaving Docker behind. "We will continue to make sure CoreOS is the best place to run Docker ... [and] expect Docker to continue to be fully integrated with CoreOS as it is today."
|
||||
|
||||
While I can understand CoreOS' concerns, I find it hard to imagine that its attempt to come up with a successful alternative to Docker will come to anything. Docker certainly isn't perfect, but in a matter of mere months, it gathered support from almost everyone in the enterprise operating system business. The only way I can see CoreOS' Rocket launching successfully will be if Docker falls flat on its face, and I just don't see that happening.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.zdnet.com/coreos-breaks-with-docker-7000036331/#ftag=RSS06bb67b
|
||||
|
||||
作者:[Steven J. Vaughan-Nichols][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.zdnet.com/meet-the-team/us/steven-j-vaughan-nichols/
|
||||
[1]:https://www.docker.com/
|
||||
[2]:http://www.zdnet.com/docker-container-support-coming-to-microsofts-next-windows-server-release-7000034708
|
||||
[3]:https://coreos.com/
|
||||
[4]:https://coreos.com/blog/rocket
|
||||
[5]:http://www.zdnet.com/coreos-linux-for-the-cloud-and-the-datacenter-7000031137/
|
||||
[6]:http://www.zdnet.com/what-is-docker-and-why-is-it-so-darn-popular-7000032269/
|
||||
[7]:https://github.com/docker/docker/commit/0db56e6c519b19ec16c6fbd12e3cee7dfa6018c5
|
||||
[8]:https://github.com/coreos/rocket
|
||||
@ -0,0 +1,49 @@
|
||||
CoreOS Team Develops Rocket, Breaks with Docker
|
||||
================================================================================
|
||||

|
||||
|
||||
[Docker][1] has easily emerged as one of the top open source stories of the year, and has helped many organizations [benefit from container technology][2]. As we’ve reported, even Google is [working closely][3] with it, and Microsoft is as well.
|
||||
|
||||
However, the folks behind CoreOS, a very popular Linux flavor for use in cloud deployments, are developing their own container technology, [dubbed Rocket][4], which will actually compete with Docker. Here are the details.
|
||||
|
||||
Rocket is a new container runtime, designed for composability, security, and speed, according to the CoreOS team. The group has released a [prototype version on GitHub][5] to begin getting community feedback.
|
||||
|
||||
“When Docker was first introduced to us in early 2013, the idea of a “standard container” was striking and immediately attractive: a simple component, a composable unit, that could be used in a variety of systems. The Docker repository [included a manifesto][6] of what a standard container should be. This was a rally cry to the industry, and we quickly followed. We thought Docker would become a simple unit that we can all agree on.”
|
||||
|
||||
“Unfortunately, a simple re-usable component is not how things are playing out. Docker now is building tools for launching cloud servers, systems for clustering, and a wide range of functions: building images, running images, uploading, downloading, and eventually even overlay networking, all compiled into one monolithic binary running primarily as root on your server. The standard container manifesto [was removed][7]. We should stop talking about Docker containers, and start talking about the Docker Platform.”
|
||||
|
||||
“We still believe in the original premise of containers that Docker introduced, so we are doing something about it. Rocket is a command line tool, rkt, for running App Containers. An ‘App Container’ is the specification of an image format, container runtime, and a discovery mechanism.”
|
||||
|
||||
There is a specification coming for App Container Images (ACI). Anyone can [Read about and contribute to the ACI draft][8].
|
||||
|
||||
The Register also [notes this interesting aspect][9] of Rocket:
|
||||
|
||||
“Significantly, all of CoreOS's tools for working with App Container will be integrated, yet independent from one another. Rocket can run as a standalone tool on any flavor of Linux, not just CoreOS.”
|
||||
|
||||
In a [blog post][10], Docker CEO Ben Golub voiced disagreement with CoreOS's move, and he writes:
|
||||
|
||||
“There are technical or philosophical differences, which appears to be the case with the recent announcement regarding Rocket. We hope to address some of the technical arguments posed by the Rocket project in a subsequent post.”
|
||||
|
||||
It sounds like a standards skirmish is going to come of all this, but, as is often the case with standards confrontations, users may benefit from the competition.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ostatic.com/blog/coreos-team-develops-rocket-breaks-with-docker
|
||||
|
||||
作者:[Sam Dean][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ostatic.com/member/samdean
|
||||
[1]:https://www.docker.com/
|
||||
[2]:http://ostatic.com/blog/linux-containers-with-docker
|
||||
[3]:http://ostatic.com/blog/google-sets-sights-squarely-on-docker-with-new-container-engine
|
||||
[4]:https://coreos.com/blog/rocket/
|
||||
[5]:https://github.com/coreos/rocket
|
||||
[6]:https://github.com/docker/docker/commit/0db56e6c519b19ec16c6fbd12e3cee7dfa6018c5
|
||||
[7]:https://github.com/docker/docker/commit/eed00a4afd1e8e8e35f8ca640c94d9c9e9babaf7
|
||||
[8]:https://github.com/coreos/rocket/blob/master/app-container/SPEC.md#app-container-image
|
||||
[9]:http://www.theregister.co.uk/2014/12/01/coreos_rocket_announcement/
|
||||
[10]:http://blog.docker.com/2014/12/initial-thoughts-on-the-rocket-announcement/
|
||||
@ -0,0 +1,57 @@
|
||||
Interview: Apache Software Foundation Elevates Drill to Top-Level Project
|
||||
================================================================================
|
||||

|
||||
|
||||
The Apache Software Foundation (ASF) has [announced][1] that [Apache Drill][2] has graduated from the Apache Incubator to become a Top-Level Project (TLP).
|
||||
|
||||
Apache Drill is billed as the world's first schema-free SQL query engine that delivers real-time insights by removing the constraint of building and maintaining schemas before data can be analyzed.
|
||||
|
||||
Drill enables rapid application development on Apache Hadoop and also allows enterprise BI analysts to access Hadoop in a self-service fashion. OStatic caught up with Tomer Shiran (shown here), a member of the Drill Project Management Committee, to get his thoughts. Here they are in an interview.
|
||||
|
||||
**Can you provide a brief overview of what Drill is and what kinds of users it can make a difference for?**
|
||||
|
||||
Drill is the world's first distributed, schema-free SQL engine. Analysts and developers can use Drill to interactively explore data in Hadoop and other NoSQL databases, such as HBase and MongoDB. There's no need to explicitly define and maintain schemas, as Drill can automatically leverage the structure that's embedded in the data.
|
||||
|
||||
This enables self-service data exploration, which is not possible with traditional data warehouses or SQL-on-Hadoop solutions like Hive and Impala, in which DBAs must manage schemas and transform the data before it can be analyzed.
|
||||
|
||||
**What level of community involvement with Drill already exists?**
|
||||
|
||||
Drill is an Apache project, so it's not owned by any vendor. Developers in the community can contribute to Drill. MapR currently employs the largest number of contributors, but we're seeing an increasing number of contributions from other companies, and that trend has been accelerating in recent months.
|
||||
|
||||
For example, the MongoDB storage plugin (enabling queries on MongoDB) was contributed by developers at Intuit.
|
||||
|
||||
**Hadoop has a lot of momentum on the Big Data front. How can Drill help organizations leveraging Hadoop?**
|
||||
|
||||
Drill is the ideal interactive SQL engine for Hadoop. One of the main reasons organizations choose Hadoop is due to its flexibility and agility. Unlike traditional databases, getting data into Hadoop is easy, and users can load data in any shape or size on their own. Early attempts at SQL on Hadoop (eg, Hive, Impala) force schemas to be created and maintained even for self-describing data like JSON, Parquet and HBase tables.
|
||||
|
||||
These systems also require data to be transformed before it can be queried. Drill is the only SQL engine for Hadoop that doesn't force schemas to be defined before data can be queried, and doesn't require any data transformations. In other words, Drill maintains the flexibility and agility paradigms that made Hadoop popular, thus making it the natural technology for data exploration and BI on Hadoop.
|
||||
|
||||
**What does Drill's status as a top-level project at Apache mean for its development and future?**
|
||||
|
||||
Drill's graduation to a top-level project is an indication that Drill has established a strong community of users and developers. Graduation is a decision made by the Apache Software Foundation (ASF) board, and it provides confidence to Drill's potential users and contributors that the project has a strong foundation. From a governance standpoint, a top-level project has its own board (also known as PMC). The PMC Chair (Jacques Nadeau) is a VP at Apache.
|
||||
|
||||
**How do you think Drill will evolve over the next several years?**
|
||||
|
||||
Drill has a large and growing community of contributors. Drill 1.0 will be out in Q1'15. We'll see many new features over the next several years. Here are a just a few examples of initiatives that are currently under way:
|
||||
|
||||
Drill currently supports HDFS, HBase and MongoDB. Additional data sources are being added, including Cassandra and RDBMS (all JDBC-enabled databases, including Oracle and MySQL). A single query can incorporate/join data from different sources. In the next year, Drill will become the standard SQL engine for modern datastores (which are all schema-free in nature): Hadoop, NoSQL databases - HBase/MongoDB/Cassandra, and search - Elasticsearch/Solr.
|
||||
|
||||
A single enterprise or cloud provider will be able to serve multiple groups/departments/organizations, each having its own workloads and SLA requirements. For example, in Drill 1.0 will support user impersonation, meaning that a query can only access the data that the user is authorized to access, and this will work with all supported data sources (Hadoop, HBase, MongoDB, etc.)
|
||||
|
||||
Drill will support not only SELECT and CREATE TABLE ... AS SELECT (CTAS) queries, but also INSERT/UPDATE/DELETE, enabling Drill to be used for operational applications (in addition to data exploration and analytics). Drill will also support the ultra-low latency and high concurrency required for such use cases.
|
||||
|
||||
Full TPC-DS support. Unlike other SQL-on-Hadoop technologies, Drill is designed to support the ANSI SQL standard as opposed to a SQL-like language. This provides better support for BI and other tools. Drill will be able to run TPC-DS, unmodified, in 2015.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ostatic.com/blog/interview-apache-software-foundation-elevates-drill-to-top-level-project
|
||||
|
||||
作者:[Sam Dean][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://ostatic.com/member/samdean
|
||||
[1]:https://blogs.apache.org/foundation/entry/the_apache_software_foundation_announces66
|
||||
[2]:http://drill.apache.org/
|
||||
148
sources/talk/20141211 Open source all over the world.md
Normal file
148
sources/talk/20141211 Open source all over the world.md
Normal file
@ -0,0 +1,148 @@
|
||||
Open source all over the world
|
||||
================================================================================
|
||||

|
||||
|
||||
Image by : opensource.com
|
||||
|
||||
After a full day at the annual meeting of the Opensource.com [Community Moderators][1], it was time for the the last item on the agenda which simply said "Special Guest: TBD." [Jason Hibbets][2], project lead and community manager for [Opensource.com][3], stood up and began explaining, "In case it wasn't going to happen, I didn't want to say who it was. Months ago I asked for any dates he'd be in town. I got two, and picked one. This was one day out of three weeks that Jim was in town."
|
||||
|
||||
The moderators, in town from all over the world for the [All Things Open conference][4], stirred at the table. Their chairs squeaked and snuck a few inches edgewise.
|
||||
|
||||
"We're going to get a half hour to hear from him and take a couple questions," said Jason.
|
||||
|
||||
The door opened, and as if it had been waiting for him the whole time, the only vacant seat at the head of the table was soon occupied by a tall fellow.
|
||||
|
||||
"How is everyone doing?" said the man. No suit, just a button down shirt and slacks.
|
||||
|
||||
The next tallest man in the room, [Jeff Mackanic][5], senior director of Global Awareness at Red Hat, explained that the majority of the Community Moderator team was present today. He asked everyone to quickly introduce themselves.
|
||||
|
||||
"[Jen Wike Huger][6]. Content Manager for Opensource.com. Happy to have everyone here."
|
||||
|
||||
"[Nicole][7]. Vice president of education at [ByWater Solutions][8]. We do FOSS for libraries. I travel and teach people how to use software."
|
||||
|
||||
"[Robin][9]. I've been participating in the Moderator program since 2013. I do lots of stuff for OSDC and work in the [City of the Hague][10], maintaining their [website][11]."
|
||||
|
||||
"[Marcus Hanwell][12]. Originally from England, I'm now at [Kitware][13]. I'm the technology lead on FOSS science software. I work with national labs and use things like [Titan][14] Z doing [GPU programming][15]. I've worked with [Gentoo][16] and [KDE][17]. Most of all, I'm passionate about joining FOSS and open science."
|
||||
|
||||
"[Phil Shapiro][18]. I administrate 28 Linux work stations at a small library in D.C. I consider these folks my coworkers and colleagues. And it's wonderful to know that we can all feed into the energy and share ideas. My main interests are how FOSS intersects with dignity, and enhancing dignity."
|
||||
|
||||
"[Joshua Holm][19]. I spend most of my time staring at system updates and helping people search for jobs on the Internet."
|
||||
|
||||
"[Mel Chernoff][20]: I work here at Red Hat, primarily on the [government][21] channel with [Jason Hibbets][22] and [Mark Bohannon][23]."
|
||||
|
||||
"[Scott Nesbitt][24]: I write for many things, but have been using FOSS for long time. I'm a 'mere mortal' just trying to be more productive, not a sysadmin or programmer. I help people meld FOSS into their business and personal lives."
|
||||
|
||||
"[Luis Ibanez][25]: I just joined [Google]26], but I'm interested in DIY and FOSS."
|
||||
|
||||
"[Remy DeCausemaker][27]: Resident Hackademic at the [RIT MAGIC Center][28] and Adjunct Professor for the [Department of Interactive Games and Media][29]. Been writing for Opensource.com for about four years now."
|
||||
|
||||
"You teach courses for the [new FOSS Minor then][30]," said Jim. "Very cool."
|
||||
|
||||
"[Jason Baker][31]. I'm a Red Hat cloud expert, mostly doing work around [OpenStack][32]."
|
||||
|
||||
"[Mark Bohannan][33]. I'm with Red Hat Global Public Policy, and I work out of Washington. Like Mel, I spend a good deal of time writing for, or finding folks from, the legal and government channels. I've found an excellent outlet to discuss positive things happening in government."
|
||||
|
||||
"[Jason Hibbets][34]. I organize the organized chaos here."
|
||||
|
||||
The room has a good chuckle.
|
||||
|
||||
"I organize this chaos too, you could say," says the brownish-red haired fellow with a gleaming white smile. The laughs grow then quieten. Breaths become baited.
|
||||
|
||||
I sat to his left and had a moment to look up from transcribing to glance up. I noticed the hint of a smile behind the knowing eyes of a man who has led the company since January 2008, [Jim Whitehurst][35], president and CEO of Red Hat.
|
||||
|
||||
"I have one of the greatest jobs on Earth," began Whitehurst, as he leaned back, crossed his legs, and put his arms behind his head. "I get to lead Red Hat, travel around the world and see what goes on. In my seven years here, the amazing thing about FOSS, and, broadly open innovation, is that it has left the fringe. And now, I would argue, IT is in the same place that FOSS was in its early days. We are seeing FOSS going from an alternative to driving innovation. Our customers are seeing it, too. They're using FOSS not because it is cheaper, but because it provides them with control and innovative solutions. It's a global phenomenon, too. For instance, I was just in India, and discovered that, for them, there were two reasons for embracing of open source: one, access to innovation, and two, the market is somewhat different and wanting full control.”
|
||||
|
||||
"The [Bombay Stock Exchange][36] wants to own all the source and control it. That is not something you would have heard five years ago in a stock exchange, anywhere. Back then, the early knock on FOSS was that it was creating free copies of things that already existed.' If you look today, virtually everything in big data is happening in FOSS. Almost any new framework, language, and methodology, including mobile (though excluding devices), are all happening first in open source.”
|
||||
|
||||
"This is because users have reached size and scale. It's not just Red Hat—it's [Google][37], [Amazon][38], [Facebook][39], and others, they want to solve their own problems, and do it the open source way. And forget licensing—open source is much more than that. We've built a vehicle, and a set of norms. Things like [Hadoop][40], [Cassandra][41], and other tools. Fact is, open source drives innovation. For example, Hadoop was in production before any vendor realized there was a problem of that scale that needed to be solved. They actually have the wherewithal to solve their own problems, and the social tech and principles to do that. "Open source is now the default technology for many categories. This is especially true as the world moves more and more to content importance, such as [3D printing][42] and other physical products that take information content and apply it.”
|
||||
|
||||
"We have this cool thing in one area, source code, but it is limited. But there are still many opportunities in different industries. We must ask ourselves, 'What can open source do for education, government, and legal? What are the parallels? And what can other areas learn with us?'"
|
||||
|
||||
"There's also the matter of content. Content is now free, and we can invest in more free content, sure. But we need free content that has a business model built around it. That is something that more people should care about. If you believe open innovation is better, then we need more models."
|
||||
|
||||
"Education worries me with its fixation on 'content' rather than 'communities.' For example, everywhere I go, I hear university presidents say, 'Wait, education is going to be free?!' The fact that FOSS is free for downstream is great, but the upstream is really powerful. Distributing free courses is great, but we need communities to iterate and make it better. That is something that a lot of different people are doing, and Opensource.com is a place to share what is going on in this space. The question is not so much 'How do we take content?' as it is 'How do you build and distribute it? How do you make sure it is a living thing that gets better, and can morph for different areas?'"
|
||||
|
||||
"But the potential to change the world is limitless, and it's amazing how much progress we've already made. Six years ago we were obsessed about defining a mission statement. We started by saying, 'We are the leader,' but that was the wrong word, because it implied control. Active participant didn't quite get it either... [Máirín Duffy][43] came up with the word [catalyst][44]. And so, we became Red Hat, the company that creates environments to agitate action and catalyze direction.”
|
||||
|
||||
"Opensource.com is a catalyst in other areas, and that is what Opensource.com is about. I hope you see yourselves this way, too. The quality of content then, when we started, versus now, is incredible. You can see it getting better every quarter. Thank you for investing your time. Thank you for being catalysts. This is a chance for us all to make the world a better place. And I'd love to hear from you."
|
||||
|
||||
I stole a glimpse of everyone at the table: more than a few people had tears in their eyes.
|
||||
|
||||
Then, Whitehurst revisits the open education topic of conversation again. "Taking it to an extreme, let's say you have a course about the book [Ulysses][45]. Here, you can explore how to crowdsource a model and get people to work together within the course. Well, it's the same with a piece of code: people work together, and the code itself gets better over time."
|
||||
|
||||
At this point, I get to have my say. Words like fundamental and possibly irreconcilable came up when discussing the differences between FOSS and academic communities.
|
||||
|
||||
**Remy**: "Retraction is career death." Releasing data or code with your paper could be devastating if you make a mistake. School has always been about avoiding failure and divining 'right answers'. Copying is cheating. Wheels are recreated from scratch ritualistically. In FOSS, you work to fail fastest, but in academia, you invite invalidation."
|
||||
|
||||
**Nicole**: "There are a lot of egos in academia. You need a release manager."
|
||||
|
||||
**Marcus**: "To collaborate, you have to show the bits you don't understand, and that happens behind closed doors. The reward model is all about what you can take credit for. We need to change the reward model. Publish as much as you can. We release eventually, but we want to release early."
|
||||
|
||||
**Luis**: "Make teamwork and sharing a priority. And Red Hat can say that to them more."
|
||||
|
||||
**Jim**: "Is there an active role that companies can play in that?"
|
||||
|
||||
[Phil Shapiro][46]: "I'm interested in tipping points in FOSS. It drives me nuts that the Fed hasn't switched to [LibreOffice][47]. We're not spending tax dollars on software, and certainly shouldn't be spending on word processing or Microsoft Office."
|
||||
|
||||
**Jim**: "We have advocated for that. A lot. Can we do more? That's a valid question. Primarily, we've made progress in the places we have products. We have a solid franchise in government. We are larger per IT spend there than the private sector. Banks and telcos are further along than the government. We've done better in Europe, and I think they have less lobbying dollars at work there, than here. This next generation of computing is almost like a 'do-over'. We are making great progress elsewhere, but it is concerning."
|
||||
|
||||
Suddenly, the door to the room opened. Jim turned and nodded towards his executive assistant standing in the doorway; it was time for his next meeting. He uncrossed his legs, leaned forward, and stood. He thanked everyone again for their work and dedication, smiled, and was out the door... leaving us all a bit more inspired.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/business/14/12/jim-whitehurst-inspiration-open-source
|
||||
|
||||
作者:[Remy][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://opensource.com/users/remyd
|
||||
[1]:http://opensource.com/community-moderator-program
|
||||
[2]:https://twitter.com/jhibbets
|
||||
[3]:http://opensource.com/
|
||||
[4]:http://allthingsopen.org/
|
||||
[5]:http://opensource.com/users/mackanic
|
||||
[6]:https://twitter.com/JenWike
|
||||
[7]:http://opensource.com/users/nengard
|
||||
[8]:http://bywatersolutions.com/
|
||||
[9]:http://opensource.com/life/13/7/community-spotlight-robin-muilwijk
|
||||
[10]:https://en.wikipedia.org/wiki/The_Hague
|
||||
[11]:http://www.denhaag.nl/en.htm
|
||||
[12]:https://twitter.com/mhanwell
|
||||
[13]:http://www.kitware.com/
|
||||
[14]:http://www.nvidia.com/gtx-700-graphics-cards/gtx-titan-z/
|
||||
[15]:https://en.wikipedia.org/wiki/General-purpose_computing_on_graphics_processing_units
|
||||
[16]:https://www.gentoo.org/
|
||||
[17]:http://kde.org/
|
||||
[18]:https://twitter.com/philshapiro
|
||||
[19]:http://opensource.com/community/13/9/contributor-spotlight-joshua-holm
|
||||
[20]:http://opensource.com/users/melanie
|
||||
[21]:http://opensource.com/government
|
||||
[22]:https://twitter.com/jhibbets
|
||||
[23]:https://twitter.com/markbotech
|
||||
[24]:http://scottnesbitt.me/
|
||||
[25]:http://opensource.com/users/luis-ibanez
|
||||
[26]:http://google.com/
|
||||
[27]:http://twitter.com/remy_d
|
||||
[28]:http://foss.rit.edu/
|
||||
[29]:http://igm.rit.edu/
|
||||
[30]:http://www.rit.edu/news/story.php?id=50590
|
||||
[31]:https://twitter.com/jehb
|
||||
[32]:http://openstack.org/
|
||||
[33]:https://twitter.com/markbotech
|
||||
[34]:https://twitter.com/jhibbets
|
||||
[35]:http://www.redhat.com/en/about/company/management/james-whitehurst
|
||||
[36]:http://www.bseindia.com/
|
||||
[37]:http://google.com/
|
||||
[38]:https://mail.corp.redhat.com/service/home/%7E/Amazon
|
||||
[39]:https://mail.corp.redhat.com/service/home/%7E/Facebook
|
||||
[40]:https://hadoop.apache.org/
|
||||
[41]:https://cassandra.apache.org/
|
||||
[42]:https://en.wikipedia.org/wiki/3D_printing
|
||||
[43]:https://twitter.com/mairin
|
||||
[44]:http://jobs.redhat.com/life-at-red-hat/our-culture/
|
||||
[45]:http://www.gutenberg.org/ebooks/4300
|
||||
[46]:https://twitter.com/philshapiro
|
||||
[47]:http://libreoffice.org/
|
||||
45
sources/talk/20141211 Was 2014 The Year of Linux Desktop.md
Normal file
45
sources/talk/20141211 Was 2014 The Year of Linux Desktop.md
Normal file
@ -0,0 +1,45 @@
|
||||
Was 2014 "The Year of Linux Desktop"?
|
||||
================================================================================
|
||||
> The Linux desktop is finally hitting all the right notes
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
**Linux has seen a lot of changes during 2014 and many users are saying that this was finally the year that really showed some real progress, but has it been enough to call it "the year of Linux desktop"?**
|
||||
|
||||
This particular phrase, "the year of Linux desktop," has been recited like a mantra in the past couple of years and it's basically trying to mark all the progress registered until now in a way that makes sense. This kind of stuff hasn't happened so far and there is no precedent for the kind of growth we're witnessing, so it's easy to understand why Linux users might look at it from this perspective.
|
||||
|
||||
Most software and hardware domains don't usually go through this kind of fast progress and things happen at a slower pace, but things have been wild even for people who have a better insight into the industry. It's hard, if not impossible, to pinpoint a certain moment or a certain event, but Linux development exploded and changed exponentially in the course of just a couple of years.
|
||||
|
||||
### Year of the Linux desktop is an uncertain term ###
|
||||
|
||||
There is no single authority which can decree that the year of the Linux desktop has arrived or that it has passed. We can only try to deduce it from what we've seen until now and it's actually up to the users. Some are more conservative and not too many things have changed for them, and others are more progressive and they just can't get enough. It really depends on what your outlook is.
|
||||
|
||||
The spark that seems to have put everything in motion appears to be the launch of Steam for Linux, although we've seen some important movement of the Linux gaming scene before that became a reality. In any case, Valve is probably the catalyst of the resurgence of what we're seeing today.
|
||||
|
||||
The Linux desktop has been in a kind of slow evolution in the past decade and nothing really changed. There have been a lot of innovations for sure, but the market share has remained almost the same. No matter how cool the desktop became or how many features Linux had well before anyone else, things have remained largely the same, and that includes the participation of companies making proprietary software. They largely ignored Linux.
|
||||
|
||||
Now, more companies have shown interest in the Linux platform in the past year than they did in the last 10. Maybe it's a natural evolution and Valve had nothing to do with it, but Linux has finally reached a level where it can be used and understood by regular users, not just people fascinated by open source.
|
||||
|
||||
The drivers are better, game studios are porting games now on a regular basis, applications and middleware that we never thought we would see on Linux have started to show up, the Linux kernel development has an incredible pace, the installation process for most of the major distros is usually trivial, and all of these are just the tip of the iceberg.
|
||||
|
||||
So, when someone asks you if 2014 was the year of the Linux desktop, you can say yes. The Linux desktop totally ruled in 2014.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Was-2014-The-Year-of-Linux-Desktop-467036.shtml
|
||||
|
||||
作者:[Silviu Stahie ][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://news.softpedia.com/editors/browse/silviu-stahie
|
||||
@ -1,129 +0,0 @@
|
||||
forsil translating ...
|
||||
How to use on-screen virtual keyboard on Linux
|
||||
================================================================================
|
||||
On-screen virtual keyboard is an alternative input method that can replace a real hardware keyboard. Virtual keyboard may be a necessity in various cases. For example, your hardware keyboard is just broken; you do not have enough keyboards for extra machines; your hardware does not have an available port left to connect a keyboard; you are a disabled person with difficulty in typing on a real keyboard; or you are building a touchscreen-based web kiosk.
|
||||
|
||||
On-screen keyboard can also be a protection mechanism against a hardware keylogger which silently records your keystrokes for sensitive information such as passwords. Some online banking sites actually force you to use a virtual keyboard for security-enhanced transactions.
|
||||
|
||||
In Linux environment, there are a couple of open-source virtual keyboard software available, e.g., [GOK (GNOME Onscreen Keyboard)][1], [kvkbd][2], [onboard][3], [Florence][4].
|
||||
|
||||
In this tutorial, I am going to focus on Florence, and show you **how to set up a virtual keyboard with Florence.**. Florence comes with a number of nice features such as flexible layout, multiple input methods, auto-hide, etc. As part of the tutorial, I will also demonstrate **how to use Ubuntu desktop with a mouse only**.
|
||||
|
||||
### Install Florence Virtual Keyboard on Linux ###
|
||||
|
||||
Fortunately, Florence is available on base repositories of most Linux distros.
|
||||
|
||||
On Debian, Ubuntu or Linux Mint:
|
||||
|
||||
$ sudo apt-get install florence
|
||||
|
||||
On Fedora, CentOS or RHEL ([EPEL repo][5] is required for CentOS/RHEL):
|
||||
|
||||
$ sudo yum install florence
|
||||
|
||||
On Mandriva or Mageia:
|
||||
|
||||
$ sudo urpmi florence
|
||||
|
||||
For Archlinux users, the package is available in [AUR][6].
|
||||
|
||||
Configure and Launch Virtual Keyboard
|
||||
|
||||
Once you install Florence, you can launch virtual keyboard simply by typing:
|
||||
|
||||
$ florence
|
||||
|
||||
By default, the virtual keyboard is always on top of other windows, allowing you to type on any active window easily.
|
||||
|
||||
To change default settings of Florence, click on tool key on the left side of the keyboard.
|
||||
|
||||

|
||||
|
||||
In "style" menu of Florence settings, you can customize keyboard style, and enable/disable sound effect.
|
||||
|
||||

|
||||
|
||||
In "window" menu, you can adjust keyboard background transparency and key opacity, as well as control keyboard ratio, taskbar, resizability and always-on-top features. Transparency and opacity adjustment can be useful if your screen resolution is not high enough, so the virtual keyboard is blocking other windows. In this example, I switch to transparent keyboard, and set opacity to 50%.
|
||||
|
||||

|
||||
|
||||
In "behaviour" menu, you can change an input method. Florence supports several different input methods: mouse, touch screen, timer and ramble. The default input is mouse method. The last two methods do not require button clicks. With timer method, key press is triggered by locating a pointer at the key for a certain amount of time. The ramble method works similar to **timer** input, but with dexterity and training, can type much faster than **timer** method.
|
||||
|
||||

|
||||
|
||||
In "layout" menu, you can change the keyboard layout. For example, you can extend the keyboard layout to include navigation keys, numeric keys, and function keys.
|
||||
|
||||

|
||||
|
||||
### Use Ubuntu Desktop with Mouse Only ###
|
||||
|
||||
I am going to demonstrate how to integrate Florence with Ubuntu desktop, so that we can access the desktop without a hardware keyboard. While this tutorial is specific to Ubuntu desktop with LightDM (Ubuntu's default display manager), a similar environment can be set up for other desktop environments.
|
||||
|
||||
The initial setup requires a hardware keyboard, but once the setup is completed, you only need a mouse, but not the keyboard.
|
||||
|
||||
When you boot up Ubuntu desktop, the boot procedure ends with launch of a display manager (or login manager) with Greeter interface, where you type in your login info. By default, Ubuntu desktop uses LightDM with Unity Greeter interface. Without a hardware keyboard, you cannot enter username and password at the login screen.
|
||||
|
||||
To be able to launch a virtual keyboard at the login screen, install GTK+ Greeter, which comes with on-screen keyboard support.
|
||||
|
||||
$ sudo apt-get install lightdm-gtk-greeter
|
||||
|
||||
Then, open a Greeter configuration file (/etc/lightdm/lightdm-gtk-greeter.conf) with a text editor, and specify Florence as an on-screen keyboard to use. Instead of Florence, you could also use onboard, Ubuntu's default on-screen keyboard.
|
||||
|
||||
$ sudo vi /etc/lightdm/lightdm-gtk-greeter.conf
|
||||
|
||||
----------
|
||||
|
||||
[greeter]
|
||||
keyboard=florence --no-gnome --focus &
|
||||
|
||||

|
||||
|
||||
Let's reboot Ubuntu desktop, and verify whether you can use virtual keyboard at the login screen.
|
||||
|
||||
When you see the GTK+ Greeter's login screen after boot, click on a human symbol icon on the top right corner. You will see "On Screen Keyboard" menu option as follows.
|
||||
|
||||

|
||||
|
||||
Click on this option, and a virtual keyboard will pop up on the login screen. Now you should be able to log in by tapping on the on-screen keyboard.
|
||||
|
||||

|
||||
|
||||
For those GDM2/GDM3 users, the Florence official site offers [documentation][7] on using virtual keyboard at GDM2/GDM3 screen.
|
||||
|
||||
The last step to make our Ubuntu desktop fully keyboard-less is to have virtual keyboard auto-start upon login, so that we can use our desktop without a hardware keyboard even after logging in. For that, create the following desktop file.
|
||||
|
||||
$ mkdir -p ~/.config/autostart
|
||||
$ vi ~/.config/autostart/florence.desktop
|
||||
|
||||
----------
|
||||
|
||||
[Desktop Entry]
|
||||
Type=Application
|
||||
Name=Virtual Keyboard
|
||||
Comment=Auto-start virtual keyboard
|
||||
Exec=florence --no-gnome
|
||||
|
||||
This will make virtual keyboard appear as soon as you log in to the desktop.
|
||||
|
||||

|
||||
|
||||
Hope this tutorial is useful to you. As you can see, Florence is quite powerful virtual keyboard which can be used for different purposes. Let me know if you have any use case for virtual keyboard.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/08/onscreen-virtual-keyboard-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:https://developer.gnome.org/gok/
|
||||
[2]:http://homepage3.nifty.com/tsato/xvkbd/
|
||||
[3]:https://launchpad.net/onboard
|
||||
[4]:http://florence.sourceforge.net/
|
||||
[5]:http://xmodulo.com/2013/03/how-to-set-up-epel-repository-on-centos.html
|
||||
[6]:https://aur.archlinux.org/packages/florence/
|
||||
[7]:http://florence.sourceforge.net/english/how-to.html
|
||||
@ -1,75 +0,0 @@
|
||||
How to Install and Setup ‘My Weather Indicator’ in Ubuntu 14.10
|
||||
================================================================================
|
||||

|
||||
|
||||
**There’s no drought of ways to be kept abreast of the weather on the Ubuntu desktop, with the Unity Dash and desktop apps like [Typhoon][1] all offering to help.**
|
||||
|
||||
But panel applets that offer quick glance condition and temperature stats, with a ream of detailed meteorological data never more than a quick click away, are by far the most popular weather utilities on Linux.
|
||||
|
||||
[My Weather Indicator][2] by Atareao is one of this breed, and arguably the best.
|
||||
|
||||
It displays current temperature and conditions on the Unity panel, and has a menu stuffed full of stats, including ‘feels like’, cloudiness and sunrise/set times. In addition, there’s a desktop widget, multiple location support, a choice of backend data providers, and plenty of configuration options.
|
||||
|
||||
Sounds pretty comprehensive, right? Let’s walk through how to install and set it up on Ubuntu.
|
||||
|
||||
### Install My Weather Indicator in Ubuntu ###
|
||||
|
||||
My Weather Indicator is not available to install from the Ubuntu Software Center directly, but both a .deb installer and an officially maintained PPA (providing packages for both Ubuntu 14.04 LTS and 14.10) are provided by the developers.
|
||||
|
||||
- Download My Weather Indicator (.deb)
|
||||
|
||||
To ensure you’re always kept up-to-date with the latest release I recommend adding the [Atareao PPA][3] to your Software Sources and installing from there.
|
||||
|
||||
How? **Open a new Terminal** window (Unity Dash > Terminal, or press Ctrl+Alt+T) and **enter the following two commands carefully**, entering your system password when prompted:
|
||||
|
||||
sudo add-apt-repository ppa:atareao/atareao
|
||||
|
||||
sudo apt-get update && sudo apt-get install my-weather-indicator
|
||||
|
||||
#### Setting Up My Weather Indicator ####
|
||||
|
||||
Regardless of how you install the tool, once you have you can launch it from the Unity Dash by searching for “weather”.
|
||||
|
||||

|
||||
|
||||
The first time you open the app the following Preferences window will open. From here you can search for a location manually or set it to auto-detect using geo-ip — the latter of which can sometimes be a little imprecise, but saves the need to faff.
|
||||
|
||||
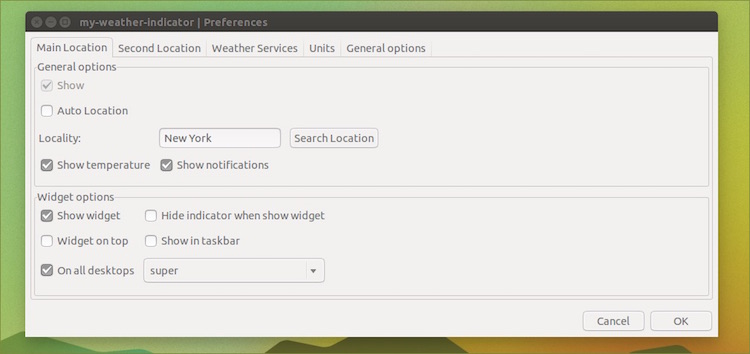
|
||||
|
||||
If you’re travelling (or in need of some small talk fodder) **you can monitor a second locale**, too. This is set up in the same way as the first but in the ‘Second Location’ tab.
|
||||
|
||||
Checking the ‘**Show Widget**’ box in the “**Widget Options**” section adds a small forecast desklet to your desktop. There are a number of different skins included, so be sure to play around to find the one you like the most (note: widget changes are applied on clicking ‘Ok’).
|
||||
|
||||
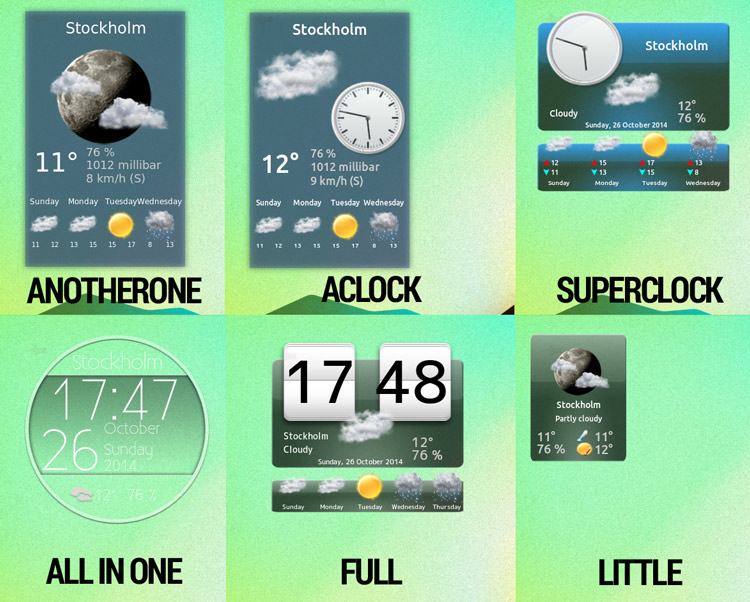
|
||||
|
||||
My Weather Indicator uses [Open Weather Map][4] as its forecast backend by default, but other options can be selected from the ‘**Weather Services**’ pane (*require an API key to function):
|
||||
|
||||
- Open Weather Map
|
||||
- Yahoo! Weather
|
||||
- Weather Underground*
|
||||
- World Weather Online*
|
||||
|
||||
The ‘**Units**’ tab is where you can configure measurements for temperature, pressure, wind speed, etc. These are applied globally to all configured locations; you can’t have one location in Celsius and the other in Fahrenheit.
|
||||
|
||||

|
||||
|
||||
Finally, in the ‘General Options‘ section you can set the refresh interval, set autostart preference, and choose from one of two panel icons.
|
||||
|
||||
MWI not your thing? Why not try [the nerdy way to view weather forecasts on Linux][5]?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/10/install-weather-indicator-ubuntu-14-10
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://launchpad.net/typhoon
|
||||
[2]:https://launchpad.net/my-weather-indicator
|
||||
[3]:https://launchpad.net/~atareao/+archive/ubuntu/atareao
|
||||
[4]:http://openweathermap.org/
|
||||
[5]:http://www.omgubuntu.co.uk/2014/02/get-weather-forecast-terminal-linux
|
||||
@ -1,3 +1,4 @@
|
||||
[felixonmars translating...]
|
||||
How To Use Emoji Anywhere With Twitter's Open Source Library
|
||||
================================================================================
|
||||
> Embed them in webpages and other projects via GitHub.
|
||||
@ -88,4 +89,4 @@ via: http://readwrite.com/2014/11/12/how-to-use-emoji-in-the-browser-window
|
||||
[7]:http://ellekasai.github.io/twemoji-awesome/
|
||||
[8]:https://github.com/ellekasai/twemoji-awesome/blob/gh-pages/twemoji-awesome.css
|
||||
[9]:https://github.com/laurenorsini/Emoji-Everywhere
|
||||
[10]:http://getemoji.com/
|
||||
[10]:http://getemoji.com/
|
||||
|
||||
120
sources/tech/20141203 Undelete Files on Linux Systems.md
Normal file
120
sources/tech/20141203 Undelete Files on Linux Systems.md
Normal file
@ -0,0 +1,120 @@
|
||||
forsil translating ...
|
||||
|
||||
Undelete Files on Linux Systems
|
||||
================================================================================
|
||||
Often times, a computer user will delete a needed file accidentally and not have an easy way to regain or recreate the file. Thankfully, files can be undeleted. When a user deletes a file, it is not gone, only hidden for some time. Here is how it all works. On a filesystem, the system has what is called a file allocation list. This list keeps track of what files are where on the storage unit (hard-drive, MicroSD card, flash-drive, etc.). When a file is deleted, the filesystem will perform one of two tasks on the allocation table. The file's entry on the file allocation table marked as "free space" or the file's entry on the list is erased and then the space is marked as free. Now, if a file needs to be placed on the storage unit, the operating system will put the file in the space marked as empty. After the new file is written to the "empty space", the deleted file is now gone forever. When a deleted file is to be recovered, the user must not manipulate any files because if the "empty space" is used, then the file can never be retrieved.
|
||||
|
||||
### How do undelete programs work? ###
|
||||
|
||||
The majority of filesystems only mark the space as empty. With these filesystems, the undelete program looks at the file allocation list and copies the deleted file to another storage unit. If the files were copied to the same storage unit, then the user could lose other deleted files that are needed.
|
||||
|
||||
Rarely do filesystems erase the allocation table entry. If a filesystem does, this is how an undelete program undeletes the file. The program searches the storage unit for file headers. All files have a specific string of code that is at the very beginning of the file. This is called a magic number. For example, the magic number of a compiled JAVA class is the hex number "CAFEBABE". So, an undelete program would find "CAFEBABE" and copy that file to another storage unit. Some undelete programs can look for a specific file type. The user may want a PDF, so the program searches for the hex magic number "25504446" which is the ASCII code for "%PDF". Other undelete programs search for all magic numbers. Then, the user can select which deleted files to recover.
|
||||
|
||||
If a part of the file has been written over, then the whole file will be corrupted. The file can usually be recovered, but the contents will be useless. For instance, recovering a corrupted JPEG file will be pointless because the image viewer will not be able to generate an image from the file. So, the user has the file, but the file is useless.
|
||||
|
||||
### Device Locations: ###
|
||||
|
||||
Before we continue, here is some information that will aid in directing the undelete utilities to the correct storage unit. All devices are in the /dev/ folder. The name of each device (not the name that the admin gave each partition or device) that is given by the system follows a predictable scheme. The second partition on the first SATA hard-drive would be sda2. The first letter indicates the storage type, in this case SATA, but an "s" could also mean SCSI, FireWire, or USB. The second letter "d" means disk. The third letter indicates the device number, so an "a" would be the first SATA and a "b" would be the second. The number displays the partition. To name the whole device with all partitions type the letters without the number. For this example that would be sda. Other possible letters "h" as the first letter. This means PATA hard-drive (IDE). As some examples of this scheme, a user has a computer with one SATA hard-drive (sda). The drive has four partitions - sda1, sda2, sda3, and sda4. The user deletes the third one, but sda4 remains sda4 until sda4 is reformatted. The user then plugs in a usb memory card (sdb) with one partition - sdb1. The user then adds a IDE hard-drive with one partition - hda1. Next, the user adds a SCSI hard-drive - sdc1. Then, the user removes the USB memory card (sdb). Now, the SCSI remains sdc, but if the SCSI is removed and added back, it will be sdb. Even though other storage device existed, the IDE drive will have the "a" because it is the first IDE drive. IDE devices are numbered separately from SCSI, SATA, FireWire, and USB devices.
|
||||
|
||||
### Recovery: ###
|
||||
|
||||
Each undelete program has different abilities, features, and support for various filesystems. Below are some instructions for using TestDisk to recover files on a set of filesystems.
|
||||
|
||||
**FAT16, FAT32, exFAT (FAT64), NTFS, and ext2/3/4:**
|
||||
|
||||
TestDisk is an open-source, free program that works on Linux, *BSD, SunOS, Mac OS X, DOS, and Windows. TestDisk can be found here: [http://www.cgsecurity.org/wiki/TestDisk][1]. TestDisk can also be installed by typing "sudo apt-get install testdisk". TestDisk has many abilities, but this article is concerned with undeleting files.
|
||||
|
||||
Open TestDisk in a terminal using root privileges by typing “sudo testdisk”.
|
||||
|
||||
Now, the TestDisk command-line application will execute. The terminal appearance will change. TestDisk asks the user if it can keep logs. This is entirely up to the user. If the user is recovering files from the system storage, then do not keep a log. The choices are "Create", "Append", and "No Log". If the user wants a log, it is kept in that user's home folder.
|
||||
|
||||

|
||||
|
||||
In the following screen, the storage devices are listed using the /dev/* method. For my system, the system's storage unit is /dev/sda. This means that my storage unit is a SATA hard-drive (sd) and it is the first hard-drive (a). The size of each storage unit is displayed in Gigabytes. Use the up and down arrows to select a storage device and hit enter.
|
||||
|
||||

|
||||
|
||||
The next screen displays a list of partition table (also called partition map) types. Just as there is the file allocation table for files, there is a table for the partitions. Partitions are dividers on a storage device. For instance, on almost all Linux systems there is at least two partitions - EXT3/4 and Swap. Each partition table will be briefly described. TestDisk does not support all partition tables, so this is not a complete list.
|
||||
|
||||

|
||||
|
||||
- **Intel** - This partition table is very common on Windows systems and many Linux systems. This table is also know as MBR.
|
||||
- **EFI GPT** - This is usually used with Linux systems. This partition map is most recommended for Linux because the concept of logical/extended partitions does not apply to GPT (GUID Partition Table) tables. This means that a Linux user can multiboot many forms of Linux with one Linux OS on each partition. There are other advantages to using GPT, but that is beyond this article.
|
||||
- **Humax** - Humax maps are used with device made by the South Korean company Humax.
|
||||
- **Mac** - The Apple Partition Map (APM) is used by Apple devices.
|
||||
- **None** - Some devices do not have a partition table. For instance, many Subor game consoles do not use a partition map. If a user tried to undelete a file on these devices thinking that the partition map was one of the other choices, the user will be confused by the fact that TestDisk does not find any filesystem or files.
|
||||
- **Sun** - The Sun partition table is used by Sun systems.
|
||||
- **Xbox** - The Xbox uses the Xbox partition map for its storage devices.
|
||||
|
||||
If a user selects "Xbox" even though their system uses GPT, TestDisk will not be able to find a partition or filesystem. If it does, then it will guess incorrectly. (The image below displays the output when the incorrect partition type)
|
||||
|
||||

|
||||
|
||||
Once the user picks the correct choice for their device, on the next screen, select "Advanced".
|
||||
|
||||

|
||||
|
||||
Now, the user should see a list of all of their filesystems/partitions on the storage unit. If the user had chosen the wrong partition map, then here is where they will know if they made the incorrect selection. If there are no errors, highlight the partition that contains the deleted file by placing the text-based cursor on it. Use the left and right arrows to highlight "List" on the bottom of the terminal. Now, hit enter.
|
||||
|
||||

|
||||
|
||||
A new screen is displayed with a list of files and folders. The whitish files are current files that are not deleted. The red files have been deleted. On the far right column is the files' names. The next column over to the left is the creation date of the file. One column over to the left again is the files' sizes in bytes. To the far left is a column with dashes, "d"s, "r"s, "w"s, and "x"s. These are the file permissions. A "d" indicates that the item is a directory. The rest of the permission syntax is irrelevant to this article. The item on the top of the file list titled "." means the current directory. The second object titled ".." means go up one directory, so a user can move up a directory by selecting this line. For an example, I will go into the directory "Xaiml_Dataset". The folder is nearly full of deleted files. I will undelete "computers.xaiml" by pressing "c" on the keyboard. I am now asked to select a destination directory. Of course, I will put it on another partition. I am in my home folder, and I press "c". It does not matter what folder is highlighted. The current folder is the destination directory. Now, I am back to the list of files. At the top of the screen is a message that says "Copy Done!". In my home folder is a folder called "Xaiml_Dataset", and inside is the Xaiml file. If I press "c" on more deleted files, they will be placed in the new folder without a****g me for a destination.
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
When finished press "q" repeatedly until the normal terminal is seen. The folder "Xaiml_Dataset" can only be accessed by the root. To fix this, use root privileges to change the folder permissions and the contained files. After that, the files have been recovered and accessible to the user.
|
||||
|
||||
### ReiserFS: ###
|
||||
|
||||
To undelete a file from a ReiserFS filesystem, make a backup of all of the files on the partition because this method can cause the file to be lost if something goes wrong. Next, execute the following command where DEVICE is the device in the form sda2. Some files will be put in the lost+found directory and other will remain where they were before deletion.
|
||||
|
||||
reiserfsck --rebuild-tree --scan-whole-partition /dev/DEVICE
|
||||
|
||||
### Recover Deleted File that is Open in a Program: ###
|
||||
|
||||
Assume a user accidentally deletes a file that a program has open. The file of the hard-drive was deleted, but the program is using a copy of the file that is on the RAM. Thankfully, there are two easy solutions.
|
||||
|
||||
If the program has save capabilities like a text editor, the user can resave the file. Thus, the file editor will write the file to the hard-drive.
|
||||
|
||||
Assume that this is an MP3 file in a music player. The music player cannot save the MP3 file. This task requires a little more time than the previous situation. Unfortunately, this method does not work on all systems and applications. To begin, type the following command.
|
||||
|
||||
lsof -c smplayer | grep mp3
|
||||
|
||||
This command LiSts all of the Open Files used by Smplayer. This list is piped (given) to grep which searches for mp3. The output looks like the following.
|
||||
|
||||
smplayer 10037 collier mp3 169r 8,1 676376 1704294 /usr/bin/smplayer
|
||||
|
||||
Now, type the following command to recover the file directly from the RAM (on Linux systems, /proc/ is the RAM) and copy it to a folder of choice. The "cp" is the copy command. The 10037 number comes from the process number given in the output. The 169 is the file descriptor shown in the output. The "~/Music/" is the destination directory. Lastly, "music.mp3" is the file name that the user wants for the file.
|
||||
|
||||
cp /proc/10037/fd/169 ~/Music/music.mp3
|
||||
|
||||
### Real Deletion: ###
|
||||
|
||||
To make for sure that a file can never be recovered, use a command that "wipes" the hard-drive. Wiping the hard-drive means writing meaningless data to the disk. For example, many wiping programs write zeros, random letters, or random data to the hard-drive. No space is taken up or lost. The wiping program just overwrites the "empty space". If the storage unit is ever full of files with no free space remaining, then all of the previously deleted files will be gone.
|
||||
|
||||
The purpose of wiping hard-drives is to make sure that private data is never seen. For illustration, a company may order new computers. The manager decides to sell the old computers. However, there is concern that the new owners may view company secrets or customer information like credit card numbers and addresses. Thankfully, a computer technician in the company can wipe the hard-drives before selling the old computers.
|
||||
|
||||
To install secure-delete, a wiping program, type "sudo apt-get install secure-delete". This installs a set of four commands that make sure that deleted files are never recovered.
|
||||
|
||||
- srm - permanently delete a file. Usage: srm -f ./secret_file.txt
|
||||
- sfill - wipe the free space. Usage: sfill -f /mount/point/of/partition
|
||||
- sswap - wipe swap space. Usage: sswap -f /dev/SWAP_DEVICE
|
||||
|
||||
If computers were to truly delete a file selected for deletion, then more time would be required to perform the task. It is quick and easy to mark some space as free, but to make the file gone forever requires time. Wiping a storage unit, for instance, takes a few hours to complete (depending on storage size). Overall, the current system works well because even when a user empties the recycle bin, they still have another chance to change their mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linux.org/threads/undelete-files-on-linux-systems.4316/
|
||||
|
||||
作者:[DevynCJohnson][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.linux.org/members/devyncjohnson.4843/
|
||||
[1]:http://www.cgsecurity.org/wiki/TestDisk
|
||||
238
sources/tech/20141204 Linux Namespaces.md
Normal file
238
sources/tech/20141204 Linux Namespaces.md
Normal file
@ -0,0 +1,238 @@
|
||||
[bazz2222222222]
|
||||
Linux Namespaces
|
||||
================================================================================
|
||||
### Background ###
|
||||
|
||||
Starting from kernel 2.6.24, Linux supports 6 different types of namespaces. Namespaces are useful in creating processes that are more isolated from the rest of the system, without needing to use full low level virtualization technology.
|
||||
|
||||
- **CLONE_NEWIPC**: IPC Namespaces: SystemV IPC and POSIX Message Queues can be isolated.
|
||||
- **CLONE_NEWPID**: PID Namespaces: PIDs are isolated, meaning that a virtual PID inside of the namespace can conflict with a PID outside of the namespace. PIDs inside the namespace will be mapped to other PIDs outside of the namespace. The first PID inside the namespace will be '1' which outside of the namespace is assigned to init
|
||||
- **CLONE_NEWNET**: Network Namespaces: Networking (/proc/net, IPs, interfaces and routes) are isolated. Services can be run on the same ports within namespaces, and "duplicate" virtual interfaces can be created.
|
||||
- **CLONE_NEWNS**: Mount Namespaces. We have the ability to isolate mount points as they appear to processes. Using mount namespaces, we can achieve similar functionality to chroot() however with improved security.
|
||||
- **CLONE_NEWUTS**: UTS Namespaces. This namespaces primary purpose is to isolate the hostname and NIS name.
|
||||
- **CLONE_NEWUSER**: User Namespaces. Here, user and group IDs are different inside and outside of namespaces and can be duplicated.
|
||||
|
||||
Let's look first at the structure of a C program, required to demonstrate process namespaces. The following has been tested on Debian 6 and 7. First, we need to allocate a page of memory on the stack, and set a pointer to the end of that memory page. We use **alloca** to allocate stack memory rather than malloc which would allocate memory on the heap.
|
||||
|
||||
void *mem = alloca(sysconf(_SC_PAGESIZE)) + sysconf(_SC_PAGESIZE);
|
||||
|
||||
Next, we use **clone** to create a child process, passing the location of our child stack 'mem', as well as the required flags to specify a new namespace. We specify 'callee' as the function to execute within the child space:
|
||||
|
||||
mypid = clone(callee, mem, SIGCHLD | CLONE_NEWIPC | CLONE_NEWPID | CLONE_NEWNS | CLONE_FILES, NULL);
|
||||
|
||||
After calling **clone** we then wait for the child process to finish, before terminating the parent. If not, the parent execution flow will continue and terminate immediately after, clearing up the child with it:
|
||||
|
||||
while (waitpid(mypid, &r, 0) < 0 && errno == EINTR)
|
||||
{
|
||||
continue;
|
||||
}
|
||||
|
||||
Lastly, we'll return to the shell with the exit code of the child:
|
||||
|
||||
if (WIFEXITED(r))
|
||||
{
|
||||
return WEXITSTATUS(r);
|
||||
}
|
||||
return EXIT_FAILURE;
|
||||
|
||||
Now, let's look at the **callee** function:
|
||||
|
||||
static int callee()
|
||||
{
|
||||
int ret;
|
||||
mount("proc", "/proc", "proc", 0, "");
|
||||
setgid(u);
|
||||
setgroups(0, NULL);
|
||||
setuid(u);
|
||||
ret = execl("/bin/bash", "/bin/bash", NULL);
|
||||
return ret;
|
||||
}
|
||||
|
||||
Here, we mount a **/proc** filesystem, and then set the uid (User ID) and gid (Group ID) to the value of 'u' before spawning the **/bin/bash** shell. [LXC][1] is an OS level virtualization tool utilizing cgroups and namespaces for resource isolation. Let's put it all together, setting 'u' to 65534 which is user "nobody" and group "nogroup" on Debian:
|
||||
|
||||
#define _GNU_SOURCE
|
||||
#include <unistd.h>
|
||||
#include <stdio.h>
|
||||
#include <stdlib.h>
|
||||
#include <sys/types.h>
|
||||
#include <sys/wait.h>
|
||||
#include <sys/mount.h>
|
||||
#include <grp.h>
|
||||
#include <alloca.h>
|
||||
#include <errno.h>
|
||||
#include <sched.h>
|
||||
static int callee();
|
||||
const int u = 65534;
|
||||
int main(int argc, char *argv[])
|
||||
{
|
||||
int r;
|
||||
pid_t mypid;
|
||||
void *mem = alloca(sysconf(_SC_PAGESIZE)) + sysconf(_SC_PAGESIZE);
|
||||
mypid = clone(callee, mem, SIGCHLD | CLONE_NEWIPC | CLONE_NEWPID | CLONE_NEWNS | CLONE_FILES, NULL);
|
||||
while (waitpid(mypid, &r, 0) < 0 && errno == EINTR)
|
||||
{
|
||||
continue;
|
||||
}
|
||||
if (WIFEXITED(r))
|
||||
{
|
||||
return WEXITSTATUS(r);
|
||||
}
|
||||
return EXIT_FAILURE;
|
||||
}
|
||||
static int callee()
|
||||
{
|
||||
int ret;
|
||||
mount("proc", "/proc", "proc", 0, "");
|
||||
setgid(u);
|
||||
setgroups(0, NULL);
|
||||
setuid(u);
|
||||
ret = execl("/bin/bash", "/bin/bash", NULL);
|
||||
return ret;
|
||||
}
|
||||
|
||||
To execute the code produces the following:
|
||||
|
||||
root@w:~/pen/tmp# gcc -O -o ns.c -Wall -Werror -ansi -c89 ns.c
|
||||
root@w:~/pen/tmp# ./ns
|
||||
nobody@w:~/pen/tmp$ id
|
||||
uid=65534(nobody) gid=65534(nogroup)
|
||||
nobody@w:~/pen/tmp$ ps auxw
|
||||
USER PID %CPU %MEM VSZ RSS TTY STAT START TIME COMMAND
|
||||
nobody 1 0.0 0.0 4620 1816 pts/1 S 21:21 0:00 /bin/bash
|
||||
nobody 5 0.0 0.0 2784 1064 pts/1 R+ 21:21 0:00 ps auxw
|
||||
nobody@w:~/pen/tmp$
|
||||
|
||||
Notice that the UID and GID are set to that of nobody and nogroup. Specifically notice that the full ps output shows only two running processes and that their PIDs are 1 and 5 respectively. Now, let's move on to using ip netns to work with network namespaces. First, let's confirm that no namespaces exist currently:
|
||||
|
||||
root@w:~# ip netns list
|
||||
Object "netns" is unknown, try "ip help".
|
||||
|
||||
In this case, either ip needs an upgrade, or the kernel does. Assuming you have a kernel newer than 2.6.24, it's most likely **ip**. After upgrading, **ip netns list** should by default return nothing. Let's add a new namespace called 'ns1':
|
||||
|
||||
root@w:~# ip netns add ns1
|
||||
root@w:~# ip netns list
|
||||
ns1
|
||||
|
||||
First, let's list the current interfaces:
|
||||
|
||||
root@w:~# ip link list
|
||||
1: lo: mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT
|
||||
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
|
||||
2: eth0: mtu 1500 qdisc pfifo_fast state UNKNOWN mode DEFAULT qlen 1000
|
||||
link/ether 00:0c:29:65:25:9e brd ff:ff:ff:ff:ff:ff
|
||||
|
||||
Now to create a new virtual interface, and add it to our new namespace. Virtual interfaces are created in pairs, and are linked to each other - imagine a virtual crossover cable:
|
||||
|
||||
root@w:~# ip link add veth0 type veth peer name veth1
|
||||
root@w:~# ip link list
|
||||
1: lo: mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT
|
||||
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
|
||||
2: eth0: mtu 1500 qdisc pfifo_fast state UNKNOWN mode DEFAULT qlen 1000
|
||||
link/ether 00:0c:29:65:25:9e brd ff:ff:ff:ff:ff:ff
|
||||
3: veth1: mtu 1500 qdisc noop state DOWN mode DEFAULT qlen 1000
|
||||
link/ether d2:e9:52:18:19:ab brd ff:ff:ff:ff:ff:ff
|
||||
4: veth0: mtu 1500 qdisc noop state DOWN mode DEFAULT qlen 1000
|
||||
link/ether f2:f7:5e:e2:22:ac brd ff:ff:ff:ff:ff:ff
|
||||
|
||||
**ifconfig** -a will also now show the addition of both veth0 and veth1.
|
||||
|
||||
Great, now to assign our new interfaces to the namespace. Note that ip **netns exec** is used to execute commands within the namespace:
|
||||
|
||||
root@w:~# ip link set veth1 netns ns1
|
||||
root@w:~# ip netns exec ns1 ip link list
|
||||
1: lo: mtu 65536 qdisc noop state DOWN mode DEFAULT
|
||||
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
|
||||
3: veth1: mtu 1500 qdisc noop state DOWN mode DEFAULT qlen 1000
|
||||
link/ether d2:e9:52:18:19:ab brd ff:ff:ff:ff:ff:ff
|
||||
|
||||
**ifconfig** -a will now only show veth0, as veth1 is in the ns1 namespace.
|
||||
|
||||
Should we want to delete veth0/veth1:
|
||||
|
||||
ip netns exec ns1 ip link del veth1
|
||||
|
||||
We can now assign IP address 192.168.5.5/24 to veth0 on our host:
|
||||
|
||||
ifconfig veth0 192.168.5.5/24
|
||||
|
||||
And assign veth1 192.168.5.10/24 within ns1:
|
||||
|
||||
ip netns exec ns1 ifconfig veth1 192.168.5.10/24 up
|
||||
|
||||
To execute ip addr **list** on both our host and within our namespace:
|
||||
|
||||
root@w:~# ip addr list
|
||||
1: lo: mtu 65536 qdisc noqueue state UNKNOWN
|
||||
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
|
||||
inet 127.0.0.1/8 scope host lo
|
||||
inet6 ::1/128 scope host
|
||||
valid_lft forever preferred_lft forever
|
||||
2: eth0: mtu 1500 qdisc pfifo_fast state UNKNOWN qlen 1000
|
||||
link/ether 00:0c:29:65:25:9e brd ff:ff:ff:ff:ff:ff
|
||||
inet 192.168.3.122/24 brd 192.168.3.255 scope global eth0
|
||||
inet6 fe80::20c:29ff:fe65:259e/64 scope link
|
||||
valid_lft forever preferred_lft forever
|
||||
6: veth0: mtu 1500 qdisc pfifo_fast state UP qlen 1000
|
||||
link/ether 86:b2:c7:bd:c9:11 brd ff:ff:ff:ff:ff:ff
|
||||
inet 192.168.5.5/24 brd 192.168.5.255 scope global veth0
|
||||
inet6 fe80::84b2:c7ff:febd:c911/64 scope link
|
||||
valid_lft forever preferred_lft forever
|
||||
root@w:~# ip netns exec ns1 ip addr list
|
||||
1: lo: mtu 65536 qdisc noop state DOWN
|
||||
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
|
||||
5: veth1: mtu 1500 qdisc pfifo_fast state UP qlen 1000
|
||||
link/ether 12:bd:b6:76:a6:eb brd ff:ff:ff:ff:ff:ff
|
||||
inet 192.168.5.10/24 brd 192.168.5.255 scope global veth1
|
||||
inet6 fe80::10bd:b6ff:fe76:a6eb/64 scope link
|
||||
valid_lft forever preferred_lft forever
|
||||
|
||||
To view routing tables inside and outside of the namespace:
|
||||
|
||||
root@w:~# ip route list
|
||||
default via 192.168.3.1 dev eth0 proto static
|
||||
192.168.3.0/24 dev eth0 proto kernel scope link src 192.168.3.122
|
||||
192.168.5.0/24 dev veth0 proto kernel scope link src 192.168.5.5
|
||||
root@w:~# ip netns exec ns1 ip route list
|
||||
192.168.5.0/24 dev veth1 proto kernel scope link src 192.168.5.10
|
||||
|
||||
Lastly, to connect our physical and virtual interfaces, we'll require a bridge. Let's bridge eth0 and veth0 on the host, and then use DHCP to gain an IP within the ns1 namespace:
|
||||
|
||||
root@w:~# brctl addbr br0
|
||||
root@w:~# brctl addif br0 eth0
|
||||
root@w:~# brctl addif br0 veth0
|
||||
root@w:~# ifconfig eth0 0.0.0.0
|
||||
root@w:~# ifconfig veth0 0.0.0.0
|
||||
root@w:~# dhclient br0
|
||||
root@w:~# ip addr list br0
|
||||
7: br0: mtu 1500 qdisc noqueue state UP
|
||||
link/ether 00:0c:29:65:25:9e brd ff:ff:ff:ff:ff:ff
|
||||
inet 192.168.3.122/24 brd 192.168.3.255 scope global br0
|
||||
inet6 fe80::20c:29ff:fe65:259e/64 scope link
|
||||
valid_lft forever preferred_lft forever
|
||||
|
||||
br0 has been assigned an IP of 192.168.3.122/24. Now for the namespace:
|
||||
|
||||
root@w:~# ip netns exec ns1 dhclient veth1
|
||||
root@w:~# ip netns exec ns1 ip addr list
|
||||
1: lo: mtu 65536 qdisc noop state DOWN
|
||||
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
|
||||
5: veth1: mtu 1500 qdisc pfifo_fast state UP qlen 1000
|
||||
link/ether 12:bd:b6:76:a6:eb brd ff:ff:ff:ff:ff:ff
|
||||
inet 192.168.3.248/24 brd 192.168.3.255 scope global veth1
|
||||
inet6 fe80::10bd:b6ff:fe76:a6eb/64 scope link
|
||||
valid_lft forever preferred_lft forever
|
||||
|
||||
Excellent! veth1 has been assigned 192.168.3.248/24
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.howtoforge.com/linux-namespaces
|
||||
|
||||
作者:[aziods][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.howtoforge.com/forums/private.php?do=newpm&u=138952
|
||||
[1]:http://en.wikipedia.org/wiki/LXC
|
||||
@ -0,0 +1,146 @@
|
||||
(translating by runningwater)
|
||||
How To Create A Bootable Ubuntu USB Drive For Mac In OS X
|
||||
================================================================================
|
||||

|
||||
|
||||
I bought a Macbook Air yesterday after Dell lost my laptop from their service centre last month. And among the first few things I did was to dual boot Mac OS X with Ubuntu Linux. I’ll cover up Linux installation on Macbook in later articles as first we need to learn **how to create a bootable Ubuntu USB drive for Mac in OS X**.
|
||||
|
||||
While it is fairly easy to create a bootable USB in Ubuntu or in Windows, it is not the same story in Mac OS X. This is why the official Ubuntu guide suggest to use a disk rather than USB for live Ubuntu in Mac. Considering my Macbook Air neither has a CD drive nor do I possess a DVD, I preferred to create a live USB in Mac OS X.
|
||||
|
||||
### Create a Bootable Ubuntu USB Drive in Mac OS X ###
|
||||
|
||||
As I said earlier, creating a bootable USB in Mac OS X is a tricky procedure, be it for Ubuntu or any other bootable OS. But don’t worry, following all the steps carefully will have you going. Let’s see what you need to for a bootable USB:
|
||||
|
||||
#### Step 1: Format the USB drive ####
|
||||
|
||||
Apple is known for defining its own standards and no surprises that Mac OS X has its own file system type known as Mac OS Extended or [HFS Plus][1]. So the first thing you would need to do is to format your USB drive in Mac OS Extended format.
|
||||
|
||||
To format the USB drive, plug in the USB key. Go to **Disk Utility** program from Launchpad (A rocket symboled icon in the bottom plank).
|
||||
|
||||

|
||||
|
||||
- In Disk Utility, from the left hand pane, select the USB drive to format.
|
||||
- Click the **Partition** tab in the right side pane.
|
||||
- From the drop-down menu, select **1 Partition**.
|
||||
- Name this drive anything you desire.
|
||||
- Next, change the **Format to Mac OS Extended (Journaled)**
|
||||
|
||||
The screenshot below should help you.
|
||||
|
||||

|
||||
|
||||
There is one last thing to do before we go with formatting the USB. Click the Options button in the right side pane and make sure that the partition scheme is **GUID Partition Table**.
|
||||
|
||||

|
||||
|
||||
When all is set to go, just hit the **Apply** button. It will give you a warning message about formatting the USB drive. Of course hit the Partition button to format the USB drive.
|
||||
|
||||
#### Step 2: Download Ubuntu ####
|
||||
|
||||
Of course, you need to download ISO image of Ubuntu desktop. Jump to [Ubuntu website to download your favorite Ubuntu desktop OS][2]. Since you are using a Macbook Air, I suggest you to download the 64 Bit version of whichever version you want. Ubuntu 14.04 is the latest LTS version, and this is what I would recommend to you.
|
||||
|
||||
#### Step 3: Convert ISO to IMG ####
|
||||
|
||||
The file you downloaded is in ISO format but we need it to be in IMG format. This can be easily done using [hdiutil][3] command tool. Open a terminal, either from Launchpad or from the Spotlight, and then use the following command to convert the ISO to IMG format:
|
||||
|
||||
hdiutil convert -format UDRW -o ~/Path-to-IMG-file ~/Path-to-ISO-file
|
||||
|
||||
Normally the downloaded file should be in ~/Downloads directory. So for me, the command is like this:
|
||||
|
||||
hdiutil convert -format UDRW -o ~/Downloads/ubuntu-14.10-desktop-amd64 ~/Downloads/ubuntu-14.10-desktop-amd64.iso
|
||||
|
||||

|
||||
|
||||
You might notice that I did not put a IMG extension to the newly converted file. It is fine as the extension is symbolic and it is the file type that matters not the file name extension. Also, the converted file may have an additional .dmg extension added to it by Mac OS X. Don’t worry, it’s normal.
|
||||
|
||||
#### Step 4: Get the device number for USB drive ####
|
||||
|
||||
The next thing is to get the device number for the USB drive. Run the following command in terminal:
|
||||
|
||||
diskutil list
|
||||
|
||||
It will list all the ‘disks’ currently available in the system. You should be able to identify the USB disk by its size. To avoid confusion, I would suggest that you should have just one USB drive plugged in. In my case, the device number is 2 (for a USB of size 8 GB): /dev/disk2
|
||||
|
||||

|
||||
|
||||
When you got the disk number, run the following command:
|
||||
|
||||
diskutil unmountDisk /dev/diskN
|
||||
|
||||
Where N is the device number for the USB you got previously. So, in my case, the above command becomes:
|
||||
|
||||
diskutil unmountDisk /dev/disk2
|
||||
|
||||
The result should be: **Unmount of all volumes on disk2 was successful**.
|
||||
|
||||
#### Step 5: Creating the bootable USB drive of Ubuntu in Mac OS X ####
|
||||
|
||||
And finally we come to the final step of creating the bootable USB drive. We shall be using [dd command][4] which is a very powerful and must be used with caution. Therefore, do remember the correct device number of your USB drive or else you might end up corrupting Mac OS X. Use the following command in terminal:
|
||||
|
||||
sudo dd if=/Path-to-IMG-DMG-file of=/dev/rdiskN bs=1m
|
||||
|
||||
Here, we are using dd (copy and convert) to copy and convert input file (if) IMG to diskN. I hope you remember where you put the converted IMG file, in step 3. For me the command was like this:
|
||||
|
||||
sudo dd if=~/Downloads/ubuntu-14.10-desktop-amd64.dmg of=/dev/rdisk2 bs=1m
|
||||
|
||||
As we are running the above command with super user privileges (sudo), it will require you to enter the password. Similar to Linux, you won’t see any asterisks or something to indicate that you have entered some keyboard input, but that’s the way Unix terminal behaves.
|
||||
|
||||
Even after you enter the password, **you won’t see any immediate output and that’s norma**l. It will take a few minutes for the process to complete.
|
||||
|
||||
#### Step 6: Complete the bootable USB drive process ####
|
||||
|
||||
Once the dd command finishes its process, you may see a dialogue box saying: **The disk you inserted was not readable by this computer**.
|
||||
|
||||

|
||||
|
||||
Don’t panic. Everything is just fine. Just **don’t click either of Initialize, Ignore or Eject just now**. Go back to the terminal. You’ll see some information about the last completed process. For me it was:
|
||||
|
||||
> 1109+1 records in
|
||||
> 1109+1 records out
|
||||
> 1162936320 bytes transferred in 77.611025 secs (14984164 bytes/sec)
|
||||
|
||||

|
||||
|
||||
Now, in the terminal use the following command to eject our USB disk:
|
||||
|
||||
diskutil eject /dev/diskN
|
||||
|
||||
N is of course the device number we have used previously which is 2 in my case:
|
||||
|
||||
diskutil eject /dev/disk2
|
||||
|
||||
Once ejected, click on **Ignore** in the dialogue box that appeared previously. Now your bootable USB disk is ready. Remove it from the system.
|
||||
|
||||
#### Step 7: Checking your newly created bootable USB disk ####
|
||||
|
||||
Once you have completed the mammoth task of creating a live USB of USB in Mac OS X, it is time to test your efforts.
|
||||
|
||||
- Plugin the bootable USB and reboot the system.
|
||||
- At start up when the Apple tune starts up, press and hold option (or alt) key.
|
||||
- This should present you with the available disks to boot in to. I presume you know what to do next.
|
||||
|
||||
For me it showed tow EFI boot:
|
||||
|
||||

|
||||
|
||||
I selected the first one and it took me straight to Grub screen:
|
||||
|
||||

|
||||
|
||||
I hope this guide helped you to create a bootable USB disk of Ubuntu for Mac in OS X. We’ll see how to dual boot Ubuntu with OS X in next article. Stay tuned.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/create-bootable-ubuntu-usb-drive-mac-os/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[runningwater](https://github.com/runningwater)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/Abhishek/
|
||||
[1]:http://en.wikipedia.org/wiki/HFS_Plus
|
||||
[2]:http://www.ubuntu.com/download/desktop
|
||||
[3]:https://developer.apple.com/library/mac/documentation/Darwin/Reference/ManPages/man1/hdiutil.1.html
|
||||
[4]:http://en.wikipedia.org/wiki/Dd_%28Unix%29
|
||||
@ -0,0 +1,156 @@
|
||||
translating by coloka...
|
||||
|
||||
How to configure a syslog server with rsyslog on Linux
|
||||
================================================================================
|
||||
A syslog server represents a central log monitoring point on a network, to which all kinds of devices including Linux or Windows servers, routers, switches or any other hosts can send their logs over network. By setting up a syslog server, you can filter and consolidate logs from different hosts and devices into a single location, so that you can view and archive important log messages more easily.
|
||||
|
||||
On most Linux distributions, **rsyslog** is the standard syslog daemon that comes pre-installed. Configured in a client/server architecture, **rsyslog** can play both roles; as a syslog server **rsyslog** can gather logs from other devices, and as a syslog client, **rsyslog** can transmit its internal logs to a remote syslog server.
|
||||
|
||||
In this tutorial, we cover how to configure a centralized syslog server using **rsyslog** on Linux. Before we go into the details, it is instructive to go over syslog standard first.
|
||||
|
||||
### Basic of Syslog Standard ###
|
||||
|
||||
When logs are collected with syslog mechanism, three important things must be taken into consideration:
|
||||
|
||||
- **Facility level**: what type of processes to monitor
|
||||
- **Severity (priority) level**: what type of log messages to collect
|
||||
- **Destination**: where to send or record log messages
|
||||
|
||||
Let's take a look at how the configuration is defined in more detail.
|
||||
|
||||
The facility levels define a way to categorize internal system processes. Some of the common standard facilities in Linux are:
|
||||
|
||||
- **auth**: messages related to authentication (login)
|
||||
- **cron**: messages related to scheduled processes or applications
|
||||
- **daemon**: messages related to daemons (internal servers)
|
||||
- **kernel**: messages related to the kernel
|
||||
- **mail**: messages related to internal mail servers
|
||||
- **syslog**: messages related to the syslog daemon itself
|
||||
- **lpr**: messages related to print servers
|
||||
- **local0 - local7**: messages defined by user (local7 is usually used by Cisco and Windows servers)
|
||||
|
||||
The severity (priority) levels are standardized, and defined by using standard abbreviation and an assigned number with number 7 being the highest level of all. These levels are:
|
||||
|
||||
- emerg: Emergency - 0
|
||||
- alert: Alerts - 1
|
||||
- crit: Critical - 2
|
||||
- err: Errors - 3
|
||||
- warn: Warnings - 4
|
||||
- notice: Notification - 5
|
||||
- info: Information - 6
|
||||
- debug: Debugging - 7
|
||||
|
||||
Finally, the destination statement enforces a syslog client to perform one of three following tasks: (1) save log messages on a local file, (2) route them to a remote syslog server over TCP/UDP, or (3) send them to stdout such as a console.
|
||||
|
||||
In rsyslog, syslog configuration is structured based on the following schema.
|
||||
|
||||
[facility-level].[severity-level] [destination]
|
||||
|
||||
### Configure Rsyslog on Linux ###
|
||||
|
||||
Now that we understand syslog, it's time to configure a Linux server as a central syslog server using rsyslog. We will also see how to configure a Windows based system as a syslog client to send internal logs to the syslog server.
|
||||
|
||||
#### Step One: Initial System Requirements ####
|
||||
|
||||
To set up a Linux host as a central log server, we need to create a separate /var partition, and allocate a large enough disk size or create a LVM special volume group. That way, the syslog server will be able to sustain the exponential growth of collected logs over time.
|
||||
|
||||
#### Step Two: Enable Rsyslog Daemon ####
|
||||
|
||||
rsyslog daemon comes pre-installed on modern Linux distributions, but is not enabled by default. To enable rsyslog daemon to receive external messages, edit its configuration file located in /etc/rsyslog.conf.
|
||||
|
||||
Once the file is opened for editing, search and uncomment the below two lines by removing the # sign from the beginning of lines.
|
||||
|
||||
$ModLoad imudp
|
||||
$UDPServerRun 514
|
||||
|
||||
This will enable rsyslog daemon to receive log messages on UDP port 514. UDP is way faster than TCP, but does not provide reliability on data flow the same way as TCP does. If you need to reliable delivery, you can enable TCP by uncommenting the following lines.
|
||||
|
||||
$ModLoad imtcp
|
||||
$InputTCPServerRun 514
|
||||
|
||||
Note that both TCP and UDP can be set on the server simultaneously to listen on TCP/UDP connections.
|
||||
|
||||
#### Step Three: Create a Template for Log Receipt ####
|
||||
|
||||
In the next step we need to create a template for remote messages, and tell rsyslog daemon how to record messages received from other client machines.
|
||||
|
||||
Open /etc/rsyslog.conf with a text editor, and append the following template before the GLOBAL DIRECTIVES block:
|
||||
|
||||
$template RemoteLogs,"/var/log/%HOSTNAME%/%PROGRAMNAME%.log" *
|
||||
*.* ?RemoteLogs
|
||||
& ~
|
||||
|
||||
This template needs a little explanation. The $template RemoteLogs directive ("RemoteLogs" string can be changed to any other descriptive name) forces rsyslog daemon to write log messages to separate local log files in /var/log/, where log file names are defined based on the hostname of the remote sending machine as well as the remote application that generated the logs. The second line ("*.* ?RemoteLogs") implies that we apply RemoteLogs template to all received logs.
|
||||
|
||||
The "& ~" sign represents a redirect rule, and is used to tell rsyslog daemon to stop processing log messages further, and not write them locally. If this redirection is not used, all the remote messages would be also written on local log files besides the log files described above, which means they would practically be written twice. Another consequence of using this rule is that the syslog server's own log messages would only be written to dedicated files named after machine's hostname.
|
||||
|
||||
If you want, you can direct log messages with a specific facility or severity level to this new template using the following schema.
|
||||
|
||||
[facility-level].[severity-level] ?RemoteLogs
|
||||
|
||||
For example:
|
||||
|
||||
Direct all internal authentication messages of all priority levels to RemoteLogs template:
|
||||
|
||||
authpriv.* ?RemoteLogs
|
||||
|
||||
Direct informational messages generated by all system processes, except mail, authentication and cron messages to RemoteLogs template:
|
||||
|
||||
*.info,mail.none,authpriv.none,cron.none ?RemoteLogs
|
||||
|
||||
If we want all received messages from remote clients written to a single file named after their IP address, you can use the following template. We assign a new name "IpTemplate" to this template.
|
||||
|
||||
$template IpTemplate,"/var/log/%FROMHOST-IP%.log"
|
||||
*.* ?IpTemplate
|
||||
& ~
|
||||
|
||||
After we have enabled rsyslog daemon and edited its configuration file, we need to restart the daemon.
|
||||
|
||||
On Debian, Ubuntu or CentOS/RHEL 6:
|
||||
|
||||
$ sudo service rsyslog restart
|
||||
|
||||
On Fedora or CentOS/RHEL 7:
|
||||
|
||||
$ sudo systemctl restart rsyslog
|
||||
|
||||
We can verify that rsyslog daemon is functional by using netstat command.
|
||||
|
||||
$ sudo netstat -tulpn | grep rsyslog
|
||||
|
||||
The output should look like the following in case rsyslog daemon listens on UDP port.
|
||||
|
||||
udp 0 0 0.0.0.0:514 0.0.0.0:* 551/rsyslogd
|
||||
udp6 0 0 :::514 :::* 551/rsyslogd
|
||||
|
||||
If rsyslog daemon is set up to listen on TCP connections, the output should look like this.
|
||||
|
||||
tcp 0 0 0.0.0.0:514 0.0.0.0:* LISTEN 1891/rsyslogd
|
||||
tcp6 0 0 :::514 :::* LISTEN 1891/rsyslogd
|
||||
|
||||
#### Send Windows Logs to a Remote Rsyslog Server ####
|
||||
|
||||
To forward a Windows based client's log messages to our rsyslog server, we need a Windows syslog agent. While there are a multitude of syslog agents that can run on Windows, we can use [Datagram SyslogAgent][1], which is a freeware program.
|
||||
|
||||
After downloading and installing the syslog agent, we need to configure it to run as a service. Specify the protocol though which it will send data, the IP address and port of a remote rsyslog server, and what type of event logs should be transmitted as follows.
|
||||
|
||||
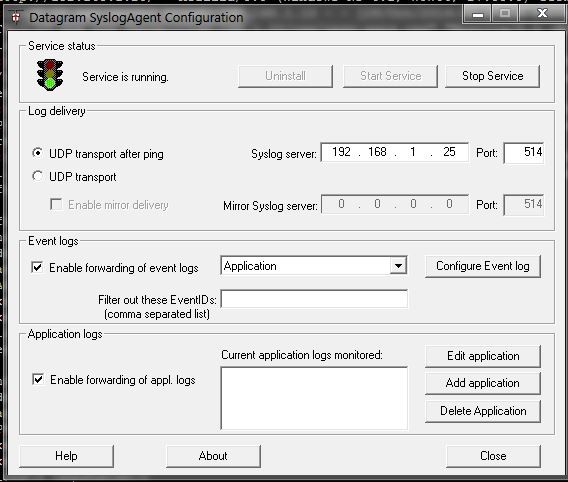
|
||||
|
||||
After we have set up all the configurations, we can start the service and watch the log files on the central rsyslog server using tailf command line utility.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
By creating a central rsyslog server that can collect log files of local or remote hosts, we can get a better idea on what is going on internally in their systems, and can debug their problems more easily should any of them become unresponsive or crash.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/configure-syslog-server-linux.html
|
||||
|
||||
作者:[Caezsar M][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/caezsar
|
||||
[1]:http://www.syslogserver.com/download.html
|
||||
@ -0,0 +1,248 @@
|
||||
SPccman translating
|
||||
How to create a custom backup plan for Debian with backupninja
|
||||
================================================================================
|
||||
Backupninja is a powerful and highly-configurable backup tool for Debian based distributions. In the [previous tutorial][1], we explored how to install backupninja and how to set up two backup actions for the program to perform. However, we should note that those examples were only "the tip of the iceberg," so to speak. In this post we will discuss how to leverage custom handlers and helpers that allow this program to be customized in order to accomplish almost any backup need that you can think of.
|
||||
|
||||
And believe me - that is not an overstatement, so let's begin.
|
||||
|
||||
### A Quick Review of Backupninja ###
|
||||
|
||||
One of backupninja's distinguishing features is the fact that you can just drop plain text configuration or action files in /etc/backup.d, and the program will take care of the rest. In addition, we can write custom scripts (aka "handlers") and place them in /usr/share/backupninja to handle each type of backup action. Furthermore, we can have these scripts be executed via ninjahelper's ncurses-based interactive menus (aka "helpers") to guide us to create the configuration files we mentioned earlier, minimizing the chances of human error.
|
||||
|
||||
### Creating a Custom Handler and Helper ###
|
||||
|
||||
Our goal in this case is to create a script to handle the backup of chosen home directories into a tarball with either **gzip** or **bzip2** compression, excluding music and video files. We will simply name this script home, and place it under /usr/backup/ninja.
|
||||
|
||||
Although you could achieve the same objective with the default tar handler (refer to /usr/share/backupninja/tar and /usr/share/backupninja/tar.helper), we will use this approach to show how to create a useful handler script and ncurses-based helper from scratch. You can then decide how to apply the same principles depending on your specific needs.
|
||||
|
||||
Note that since handlers are sourced from the main script, there is no need to start with #!/bin/bash at the top.
|
||||
|
||||
Our proposed handler (/usr/share/backupninja/home) is as follows. It is heavily commented for clarification. The getconf function is used to read the backup action's configuration file. If you specify a value for a variable here, it will override the corresponding value present in the configuration file:
|
||||
|
||||
# home handler script for backupninja
|
||||
|
||||
# Every backup file will identify the host by its FQDN
|
||||
getconf backupname
|
||||
|
||||
# Directory to store backups
|
||||
getconf backupdir
|
||||
|
||||
# Default compression
|
||||
getconf compress
|
||||
|
||||
# Include /home directory
|
||||
getconf includes
|
||||
|
||||
# Exclude files with *.mp3 and *.mp4 extensions
|
||||
getconf excludes
|
||||
|
||||
# Default extension for the packaged backup file
|
||||
getconf EXTENSION
|
||||
|
||||
# Absolute path to date binary
|
||||
getconf TAR `which tar`
|
||||
|
||||
# Absolute path to date binary
|
||||
getconf DATE `which date`
|
||||
|
||||
# Chosen date format
|
||||
DATEFORMAT="%Y-%m-%d"
|
||||
|
||||
# If backupdir does not exist, exit with fatal error
|
||||
if [ ! -d "$backupdir" ]
|
||||
then
|
||||
mkdir -p "$backupdir" || fatal "Can not make directory $backupdir"
|
||||
fi
|
||||
|
||||
# If backupdir is not writeable, exit with fatal error as well
|
||||
if [ ! -w "$backupdir" ]
|
||||
then
|
||||
fatal "Directory $backupdir is not writable"
|
||||
fi
|
||||
|
||||
# Set the right tar option as per the chosen compression format
|
||||
case $compress in
|
||||
"gzip")
|
||||
compress_option="-z"
|
||||
EXTENSION="tar.gz"
|
||||
;;
|
||||
"bzip")
|
||||
compress_option="-j"
|
||||
EXTENSION="tar.bz2"
|
||||
;;
|
||||
"none")
|
||||
compress_option=""
|
||||
;;
|
||||
*)
|
||||
warning "Unknown compress filter ($tar_compress)"
|
||||
compress_option=""
|
||||
EXTENSION="tar.gz"
|
||||
;;
|
||||
esac
|
||||
|
||||
# Exclude the following file types / directories
|
||||
exclude_options=""
|
||||
for i in $excludes
|
||||
do
|
||||
exclude_options="$exclude_options --exclude $i"
|
||||
done
|
||||
|
||||
# Debugging messages, performing backup
|
||||
debug "Running backup: " $TAR -c -p -v $compress_option $exclude_options \
|
||||
-f "$backupdir/$backupname-"`$DATE "+$DATEFORMAT"`".$EXTENSION" \
|
||||
$includes
|
||||
|
||||
# Redirect standard output to a file with .list extension
|
||||
# and standard error to a file with .err extension
|
||||
$TAR -c -p -v $compress_option $exclude_options \
|
||||
-f "$backupdir/$backupname-"`$DATE "+$DATEFORMAT"`".$EXTENSION" \
|
||||
$includes \
|
||||
> "$backupdir/$backupname-"`$DATE "+$DATEFORMAT"`.list \
|
||||
2> "$backupdir/$backupname-"`$DATE "+$DATEFORMAT"`.err
|
||||
|
||||
[ $? -ne 0 ] && fatal "Tar backup failed"
|
||||
|
||||
Next, we will create our helper file (/usr/share/backupninja/home.helper) so that our handlers shows up as a menu in **ninjahelper**:
|
||||
|
||||
# Backup action's description. Separate words with underscores.
|
||||
HELPERS="$HELPERS home:backup_of_home_directories"
|
||||
|
||||
home_wizard() {
|
||||
home_title="Home action wizard"
|
||||
|
||||
backupname=`hostname --fqdn`
|
||||
|
||||
# Specify default value for the time when this backup actions is supposed to run
|
||||
inputBox "$home_title" "When to run this action?" "everyday at 01"
|
||||
[ $? = 1 ] && return
|
||||
home_when_run="when = $REPLY"
|
||||
|
||||
# Specify default value for backup file name
|
||||
inputBox "$home_title" "\"Name\" of backups" "$backupname"
|
||||
[ $? = 1 ] && return
|
||||
home_backupname="backupname = $REPLY"
|
||||
backupname="$REPLY"
|
||||
|
||||
# Specify default directory to store the backups
|
||||
inputBox "$home_title" "Directory where to store the backups" "/var/backups/home"
|
||||
[ $? = 1 ] && return
|
||||
home_backupdir="backupdir = $REPLY"
|
||||
|
||||
# Specify default values for the radiobox
|
||||
radioBox "$home_title" "Compression" \
|
||||
"none" "No compression" off \
|
||||
"gzip" "Compress with gzip" on \
|
||||
"bzip" "Compress with bzip" off
|
||||
[ $? = 1 ] && return;
|
||||
result="$REPLY"
|
||||
home_compress="compress = $REPLY "
|
||||
|
||||
REPLY=
|
||||
while [ -z "$REPLY" ]; do
|
||||
formBegin "$home_title: Includes"
|
||||
formItem "Include:" /home/gacanepa
|
||||
formDisplay
|
||||
[ $? = 0 ] || return 1
|
||||
home_includes="includes = "
|
||||
for i in $REPLY; do
|
||||
[ -n "$i" ] && home_includes="$home_includes $i"
|
||||
done
|
||||
done
|
||||
|
||||
REPLY=
|
||||
while [ -z "$REPLY" ]; do
|
||||
formBegin "$home_title: Excludes"
|
||||
formItem "Exclude:" *.mp3
|
||||
formItem "Exclude:" *.mp4
|
||||
# Add as many “Exclude” text boxes as needed to specify other exclude options
|
||||
formItem "Exclude:"
|
||||
formItem "Exclude:"
|
||||
formDisplay
|
||||
[ $? = 0 ] || return 1
|
||||
home_excludes="excludes = "
|
||||
for i in $REPLY; do
|
||||
[ -n "$i" ] && home_excludes="$home_excludes $i"
|
||||
done
|
||||
done
|
||||
|
||||
# Save the config
|
||||
get_next_filename $configdirectory/10.home
|
||||
cat > $next_filename <<EOF
|
||||
$home_when_run
|
||||
$home_backupname
|
||||
$home_backupdir
|
||||
$home_compress
|
||||
$home_includes
|
||||
$home_excludes
|
||||
|
||||
# tar binary - have to be GNU tar
|
||||
TAR `which tar`
|
||||
DATE `which date`
|
||||
DATEFORMAT "%Y-%m-%d"
|
||||
EXTENSION tar
|
||||
|
||||
EOF
|
||||
# Backupninja requires that configuration files be chmoded to 600
|
||||
chmod 600 $next_filename
|
||||
}
|
||||
|
||||
### Running Ninjahelper ###
|
||||
|
||||
Once we have created our handler script named home and the corresponding helper named home.helper, let's run ninjahelper command to create a new backup action:
|
||||
|
||||
# ninjahelper
|
||||
|
||||
And choose create a new backup action.
|
||||
|
||||

|
||||
|
||||
We will now be presented with the available action types. Let's select "backup of home directories":
|
||||
|
||||

|
||||
|
||||
The next screens will display the default values as set in the helper (only 3 of them are shown here). Feel free to edit the values in the text box. Particularly, refer to the scheduling section of the documentation for the right syntax for the when variable.
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
When you are done creating the backup action, it will show in ninjahelper's initial menu:
|
||||
|
||||

|
||||
|
||||
Then you can press ENTER to show the options available for this action. Feel free to experiment with them, as their description is quite straightforward.
|
||||
|
||||
Particularly, "run this action now" will execute the backup action in debug mode immediately regardless of the scheduled time:
|
||||
|
||||

|
||||
|
||||
Should the backup action fail for some reason, the debug will display an informative message to help you locate the error and correct it. Consider, for example, the following error messages that were displayed after running a backup action with bugs that have not been corrected yet:
|
||||
|
||||

|
||||
|
||||
The image above tells you that the connection needed to complete the backup action could not be completed because the remote host seems to be down. In addition, the destination directory specified in the helper file does not exist. Once you correct the problems, re-run the backup action.
|
||||
|
||||
A few things to remember:
|
||||
|
||||
- If you create a custom script in /usr/share/backupninja (e.g., foobar) to handle a specific backup action, you also need to write a corresponding helper (e.g., foobar.helper) in order to create, through ninjahelper, a file named 10.foobar (11 and onward for further actions as well) in /etc/backup.d, which is the actual configuration file for the backup action.
|
||||
- You can execute your backups at any given time via ninjahelper as explained earlier, or have them run as per the specified frequency in the when variable.
|
||||
|
||||
### Summary ###
|
||||
|
||||
In this post we have discussed how to create our own backup actions from scratch and how to add a related menu in ninjahelper to facilitate the creation of configuration files. With the previous [backupninja article][2] and the present one I hope I've given you enough good reasons to go ahead and at least try it.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/create-custom-backup-plan-debian.html
|
||||
|
||||
作者:[ Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/gabriel
|
||||
[1]:http://xmodulo.com/backup-debian-system-backupninja.html
|
||||
[2]:http://xmodulo.com/backup-debian-system-backupninja.html
|
||||
@ -0,0 +1,249 @@
|
||||
文章重复
|
||||
How to create a custom backup plan for Debian with backupninja
|
||||
================================================================================
|
||||
Backupninja is a powerful and highly-configurable backup tool for Debian based distributions. In the [previous tutorial][1], we explored how to install backupninja and how to set up two backup actions for the program to perform. However, we should note that those examples were only "the tip of the iceberg," so to speak. In this post we will discuss how to leverage custom handlers and helpers that allow this program to be customized in order to accomplish almost any backup need that you can think of.
|
||||
|
||||
And believe me - that is not an overstatement, so let's begin.
|
||||
|
||||
### A Quick Review of Backupninja ###
|
||||
|
||||
One of backupninja's distinguishing features is the fact that you can just drop plain text configuration or action files in /etc/backup.d, and the program will take care of the rest. In addition, we can write custom scripts (aka "handlers") and place them in /usr/share/backupninja to handle each type of backup action. Furthermore, we can have these scripts be executed via ninjahelper's ncurses-based interactive menus (aka "helpers") to guide us to create the configuration files we mentioned earlier, minimizing the chances of human error.
|
||||
|
||||
### Creating a Custom Handler and Helper ###
|
||||
|
||||
Our goal in this case is to create a script to handle the backup of chosen home directories into a tarball with either gzip or bzip2 compression, excluding music and video files. We will simply name this script home, and place it under /usr/backup/ninja.
|
||||
|
||||
Although you could achieve the same objective with the default tar handler (refer to /usr/share/backupninja/tar and /usr/share/backupninja/tar.helper), we will use this approach to show how to create a useful handler script and ncurses-based helper from scratch. You can then decide how to apply the same principles depending on your specific needs.
|
||||
|
||||
Note that since handlers are sourced from the main script, there is no need to start with #!/bin/bash at the top.
|
||||
|
||||
Our proposed handler (/usr/share/backupninja/home) is as follows. It is heavily commented for clarification. The getconf function is used to read the backup action's configuration file. If you specify a value for a variable here, it will override the corresponding value present in the configuration file:
|
||||
|
||||
# home handler script for backupninja
|
||||
|
||||
# Every backup file will identify the host by its FQDN
|
||||
getconf backupname
|
||||
|
||||
# Directory to store backups
|
||||
getconf backupdir
|
||||
|
||||
# Default compression
|
||||
getconf compress
|
||||
|
||||
# Include /home directory
|
||||
getconf includes
|
||||
|
||||
# Exclude files with *.mp3 and *.mp4 extensions
|
||||
getconf excludes
|
||||
|
||||
# Default extension for the packaged backup file
|
||||
getconf EXTENSION
|
||||
|
||||
# Absolute path to date binary
|
||||
getconf TAR `which tar`
|
||||
|
||||
# Absolute path to date binary
|
||||
getconf DATE `which date`
|
||||
|
||||
# Chosen date format
|
||||
DATEFORMAT="%Y-%m-%d"
|
||||
|
||||
# If backupdir does not exist, exit with fatal error
|
||||
if [ ! -d "$backupdir" ]
|
||||
then
|
||||
mkdir -p "$backupdir" || fatal "Can not make directory $backupdir"
|
||||
fi
|
||||
|
||||
# If backupdir is not writeable, exit with fatal error as well
|
||||
if [ ! -w "$backupdir" ]
|
||||
then
|
||||
fatal "Directory $backupdir is not writable"
|
||||
fi
|
||||
|
||||
# Set the right tar option as per the chosen compression format
|
||||
case $compress in
|
||||
"gzip")
|
||||
compress_option="-z"
|
||||
EXTENSION="tar.gz"
|
||||
;;
|
||||
"bzip")
|
||||
compress_option="-j"
|
||||
EXTENSION="tar.bz2"
|
||||
;;
|
||||
"none")
|
||||
compress_option=""
|
||||
;;
|
||||
*)
|
||||
warning "Unknown compress filter ($tar_compress)"
|
||||
compress_option=""
|
||||
EXTENSION="tar.gz"
|
||||
;;
|
||||
esac
|
||||
|
||||
# Exclude the following file types / directories
|
||||
exclude_options=""
|
||||
for i in $excludes
|
||||
do
|
||||
exclude_options="$exclude_options --exclude $i"
|
||||
done
|
||||
|
||||
# Debugging messages, performing backup
|
||||
debug "Running backup: " $TAR -c -p -v $compress_option $exclude_options \
|
||||
-f "$backupdir/$backupname-"`$DATE "+$DATEFORMAT"`".$EXTENSION" \
|
||||
$includes
|
||||
|
||||
# Redirect standard output to a file with .list extension
|
||||
# and standard error to a file with .err extension
|
||||
$TAR -c -p -v $compress_option $exclude_options \
|
||||
-f "$backupdir/$backupname-"`$DATE "+$DATEFORMAT"`".$EXTENSION" \
|
||||
$includes \
|
||||
> "$backupdir/$backupname-"`$DATE "+$DATEFORMAT"`.list \
|
||||
2> "$backupdir/$backupname-"`$DATE "+$DATEFORMAT"`.err
|
||||
|
||||
[ $? -ne 0 ] && fatal "Tar backup failed"
|
||||
|
||||
Next, we will create our helper file (/usr/share/backupninja/home.helper) so that our handlers shows up as a menu in ninjahelper:
|
||||
|
||||
# Backup action's description. Separate words with underscores.
|
||||
HELPERS="$HELPERS home:backup_of_home_directories"
|
||||
|
||||
home_wizard() {
|
||||
home_title="Home action wizard"
|
||||
|
||||
backupname=`hostname --fqdn`
|
||||
|
||||
# Specify default value for the time when this backup actions is supposed to run
|
||||
inputBox "$home_title" "When to run this action?" "everyday at 01"
|
||||
[ $? = 1 ] && return
|
||||
home_when_run="when = $REPLY"
|
||||
|
||||
# Specify default value for backup file name
|
||||
inputBox "$home_title" "\"Name\" of backups" "$backupname"
|
||||
[ $? = 1 ] && return
|
||||
home_backupname="backupname = $REPLY"
|
||||
backupname="$REPLY"
|
||||
|
||||
# Specify default directory to store the backups
|
||||
inputBox "$home_title" "Directory where to store the backups" "/var/backups/home"
|
||||
[ $? = 1 ] && return
|
||||
home_backupdir="backupdir = $REPLY"
|
||||
|
||||
# Specify default values for the radiobox
|
||||
radioBox "$home_title" "Compression" \
|
||||
"none" "No compression" off \
|
||||
"gzip" "Compress with gzip" on \
|
||||
"bzip" "Compress with bzip" off
|
||||
[ $? = 1 ] && return;
|
||||
result="$REPLY"
|
||||
home_compress="compress = $REPLY "
|
||||
|
||||
REPLY=
|
||||
while [ -z "$REPLY" ]; do
|
||||
formBegin "$home_title: Includes"
|
||||
formItem "Include:" /home/gacanepa
|
||||
formDisplay
|
||||
[ $? = 0 ] || return 1
|
||||
home_includes="includes = "
|
||||
for i in $REPLY; do
|
||||
[ -n "$i" ] && home_includes="$home_includes $i"
|
||||
done
|
||||
done
|
||||
|
||||
REPLY=
|
||||
while [ -z "$REPLY" ]; do
|
||||
formBegin "$home_title: Excludes"
|
||||
formItem "Exclude:" *.mp3
|
||||
formItem "Exclude:" *.mp4
|
||||
# Add as many “Exclude” text boxes as needed to specify other exclude options
|
||||
formItem "Exclude:"
|
||||
formItem "Exclude:"
|
||||
formDisplay
|
||||
[ $? = 0 ] || return 1
|
||||
home_excludes="excludes = "
|
||||
for i in $REPLY; do
|
||||
[ -n "$i" ] && home_excludes="$home_excludes $i"
|
||||
done
|
||||
done
|
||||
|
||||
# Save the config
|
||||
get_next_filename $configdirectory/10.home
|
||||
cat > $next_filename <<EOF
|
||||
$home_when_run
|
||||
$home_backupname
|
||||
$home_backupdir
|
||||
$home_compress
|
||||
$home_includes
|
||||
$home_excludes
|
||||
|
||||
# tar binary - have to be GNU tar
|
||||
TAR `which tar`
|
||||
DATE `which date`
|
||||
DATEFORMAT "%Y-%m-%d"
|
||||
EXTENSION tar
|
||||
|
||||
EOF
|
||||
# Backupninja requires that configuration files be chmoded to 600
|
||||
chmod 600 $next_filename
|
||||
}
|
||||
|
||||
### Running Ninjahelper ###
|
||||
|
||||
Once we have created our handler script named home and the corresponding helper named home.helper, let's run ninjahelper command to create a new backup action:
|
||||
|
||||
# ninjahelper
|
||||
|
||||
And choose create a new backup action.
|
||||
|
||||

|
||||
|
||||
We will now be presented with the available action types. Let's select "backup of home directories":
|
||||
|
||||

|
||||
|
||||
The next screens will display the default values as set in the helper (only 3 of them are shown here). Feel free to edit the values in the text box. Particularly, refer to the scheduling section of the documentation for the right syntax for the when variable.
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
When you are done creating the backup action, it will show in ninjahelper's initial menu:
|
||||
|
||||

|
||||
|
||||
Then you can press ENTER to show the options available for this action. Feel free to experiment with them, as their description is quite straightforward.
|
||||
|
||||
Particularly, "run this action now" will execute the backup action in debug mode immediately regardless of the scheduled time:
|
||||
|
||||

|
||||
|
||||
Should the backup action fail for some reason, the debug will display an informative message to help you locate the error and correct it. Consider, for example, the following error messages that were displayed after running a backup action with bugs that have not been corrected yet:
|
||||
|
||||

|
||||
|
||||
The image above tells you that the connection needed to complete the backup action could not be completed because the remote host seems to be down. In addition, the destination directory specified in the helper file does not exist. Once you correct the problems, re-run the backup action.
|
||||
|
||||
A few things to remember:
|
||||
|
||||
|
||||
- If you create a custom script in /usr/share/backupninja (e.g., foobar) to handle a specific backup action, you also need to write a corresponding helper (e.g., foobar.helper) in order to create, through ninjahelper, a file named 10.foobar (11 and onward for further actions as well) in /etc/backup.d, which is the actual configuration file for the backup action.
|
||||
- You can execute your backups at any given time via ninjahelper as explained earlier, or have them run as per the specified frequency in the when variable.
|
||||
|
||||
### Summary ###
|
||||
|
||||
In this post we have discussed how to create our own backup actions from scratch and how to add a related menu in ninjahelper to facilitate the creation of configuration files. With the previous [backupninja article][2] and the present one I hope I've given you enough good reasons to go ahead and at least try it.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/create-custom-backup-plan-debian.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/gabriel
|
||||
[1]:http://xmodulo.com/backup-debian-system-backupninja.html
|
||||
[2]:http://xmodulo.com/backup-debian-system-backupninja.html
|
||||
@ -0,0 +1,198 @@
|
||||
spccman translating
|
||||
How to Setup Bind Chroot DNS Server on CentOS 7.0 VPS
|
||||
================================================================================
|
||||
BIND (Berkeley Internet Name Daemon) also known as NAMED is the most widely used DNS server in the internet. This tutorial will descibes how we can run BIND in a chroot jail, the process is simply unable to see any part of the filesystem outside the jail. For example, in this post, i will setting up BIND to run chrooted to the directory /var/named/chroot/. Well, to BIND, the contents of this directory will appear to be /, the root directory. A “jail” is a software mechanism for limiting the ability of a process to access resources outside a very limited area, and it’s purposely to enhance the security. Bind Chroot DNS server was by default configured to /var/named/chroot. You may follow this complete steps to implement Bind Chroot DNS Server on CentOS 7.0 virtual private server (VPS).
|
||||
|
||||
1. Install Bind Chroot DNS server :
|
||||
|
||||
[root@centos7 ~]# yum install bind-chroot bind -y
|
||||
|
||||
2. Copy all bind related files to prepare bind chrooted environments :
|
||||
|
||||
[root@centos7 ~]# cp -R /usr/share/doc/bind-*/sample/var/named/* /var/named/chroot/var/named/
|
||||
|
||||
3. Create bind related files into chrooted directory :
|
||||
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/data/cache_dump.db
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/data/named_stats.txt
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/data/named_mem_stats.txt
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/data/named.run
|
||||
[root@centos7 ~]# mkdir /var/named/chroot/var/named/dynamic
|
||||
[root@centos7 ~]# touch /var/named/chroot/var/named/dynamic/managed-keys.bind
|
||||
|
||||
4. Bind lock file should be writeable, therefore set the permission to make it writable as below :
|
||||
|
||||
[root@centos7 ~]# chmod -R 777 /var/named/chroot/var/named/data
|
||||
[root@centos7 ~]# chmod -R 777 /var/named/chroot/var/named/dynamic
|
||||
|
||||
5. Copy /etc/named.conf chrooted bind config folder :
|
||||
|
||||
[root@centos7 ~]# cp -p /etc/named.conf /var/named/chroot/etc/named.conf
|
||||
|
||||
6.Configure main bind configuration in /etc/named.conf. Append the example.local zone information to the file :
|
||||
|
||||
[root@centos7 ~]# vi /var/named/chroot/etc/named.conf
|
||||
|
||||
Create forward and reverse zone into named.conf:
|
||||
|
||||
..
|
||||
..
|
||||
zone "example.local" {
|
||||
type master;
|
||||
file "example.local.zone";
|
||||
};
|
||||
|
||||
zone "0.168.192.in-addr.arpa" IN {
|
||||
type master;
|
||||
file "192.168.0.zone";
|
||||
};
|
||||
..
|
||||
..
|
||||
|
||||
Full named.conf configuration :
|
||||
|
||||
//
|
||||
// named.conf
|
||||
//
|
||||
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
|
||||
// server as a caching only nameserver (as a localhost DNS resolver only).
|
||||
//
|
||||
// See /usr/share/doc/bind*/sample/ for example named configuration files.
|
||||
//
|
||||
|
||||
options {
|
||||
listen-on port 53 { any; };
|
||||
listen-on-v6 port 53 { ::1; };
|
||||
directory "/var/named";
|
||||
dump-file "/var/named/data/cache_dump.db";
|
||||
statistics-file "/var/named/data/named_stats.txt";
|
||||
memstatistics-file "/var/named/data/named_mem_stats.txt";
|
||||
allow-query { any; };
|
||||
|
||||
/*
|
||||
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
|
||||
- If you are building a RECURSIVE (caching) DNS server, you need to enable
|
||||
recursion.
|
||||
- If your recursive DNS server has a public IP address, you MUST enable access
|
||||
control to limit queries to your legitimate users. Failing to do so will
|
||||
cause your server to become part of large scale DNS amplification
|
||||
attacks. Implementing BCP38 within your network would greatly
|
||||
reduce such attack surface
|
||||
*/
|
||||
recursion yes;
|
||||
|
||||
dnssec-enable yes;
|
||||
dnssec-validation yes;
|
||||
dnssec-lookaside auto;
|
||||
|
||||
/* Path to ISC DLV key */
|
||||
bindkeys-file "/etc/named.iscdlv.key";
|
||||
|
||||
managed-keys-directory "/var/named/dynamic";
|
||||
|
||||
pid-file "/run/named/named.pid";
|
||||
session-keyfile "/run/named/session.key";
|
||||
};
|
||||
|
||||
logging {
|
||||
channel default_debug {
|
||||
file "data/named.run";
|
||||
severity dynamic;
|
||||
};
|
||||
};
|
||||
|
||||
zone "." IN {
|
||||
type hint;
|
||||
file "named.ca";
|
||||
};
|
||||
|
||||
zone "example.local" {
|
||||
type master;
|
||||
file "example.local.zone";
|
||||
};
|
||||
|
||||
zone "0.168.192.in-addr.arpa" IN {
|
||||
type master;
|
||||
file "192.168.0.zone";
|
||||
};
|
||||
|
||||
include "/etc/named.rfc1912.zones";
|
||||
include "/etc/named.root.key";
|
||||
|
||||
7. Create Forward and Reverse zone files for domain example.local.
|
||||
|
||||
a) Create Forward Zone :
|
||||
|
||||
[root@centos7 ~]# vi /var/named/chroot/var/named/example.local.zone
|
||||
|
||||
Add the following and save :
|
||||
|
||||
;
|
||||
; Addresses and other host information.
|
||||
;
|
||||
$TTL 86400
|
||||
@ IN SOA example.local. hostmaster.example.local. (
|
||||
2014101901 ; Serial
|
||||
43200 ; Refresh
|
||||
3600 ; Retry
|
||||
3600000 ; Expire
|
||||
2592000 ) ; Minimum
|
||||
|
||||
; Define the nameservers and the mail servers
|
||||
|
||||
IN NS ns1.example.local.
|
||||
IN NS ns2.example.local.
|
||||
IN A 192.168.0.70
|
||||
IN MX 10 mx.example.local.
|
||||
|
||||
centos7 IN A 192.168.0.70
|
||||
mx IN A 192.168.0.50
|
||||
ns1 IN A 192.168.0.70
|
||||
ns2 IN A 192.168.0.80
|
||||
|
||||
b) Create Reverse Zone :
|
||||
|
||||
[root@centos7 ~]# vi /var/named/chroot/var/named/192.168.0.zone
|
||||
|
||||
----------
|
||||
|
||||
;
|
||||
; Addresses and other host information.
|
||||
;
|
||||
$TTL 86400
|
||||
@ IN SOA example.local. hostmaster.example.local. (
|
||||
2014101901 ; Serial
|
||||
43200 ; Refresh
|
||||
3600 ; Retry
|
||||
3600000 ; Expire
|
||||
2592000 ) ; Minimum
|
||||
|
||||
0.168.192.in-addr.arpa. IN NS centos7.example.local.
|
||||
|
||||
70.0.168.192.in-addr.arpa. IN PTR mx.example.local.
|
||||
70.0.168.192.in-addr.arpa. IN PTR ns1.example.local.
|
||||
80.0.168.192.in-addr.arpa. IN PTR ns2.example.local.
|
||||
|
||||
8. Stop and disable named service. Start and enable bind-chroot service at boot :
|
||||
|
||||
[root@centos7 ~]# /usr/libexec/setup-named-chroot.sh /var/named/chroot on
|
||||
[root@centos7 ~]# systemctl stop named
|
||||
[root@centos7 ~]# systemctl disable named
|
||||
[root@centos7 ~]# systemctl start named-chroot
|
||||
[root@centos7 ~]# systemctl enable named-chroot
|
||||
ln -s '/usr/lib/systemd/system/named-chroot.service' '/etc/systemd/system/multi-user.target.wants/named-chroot.service'
|
||||
|
||||
As always if you need any help you can reach us on twitter @ehowstuff or drop us a comment below. [Jumping through archives page to read more articles..][1]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ehowstuff.com/how-to-setup-bind-chroot-dns-server-on-centos-7-0-vps/
|
||||
|
||||
作者:[skytech][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ehowstuff.com/author/mhstar/
|
||||
[1]:http://www.ehowstuff.com/archives/
|
||||
@ -0,0 +1,153 @@
|
||||
ideas4u Translating..
|
||||
How to use matplotlib for scientific plotting on Linux
|
||||
================================================================================
|
||||
If you want an efficient, automatable solution for producing high-quality scientific plots in Linux, then consider using matplotlib. Matplotlib is a Python-based open-source scientific plotting package with a license based on the Python Software Foundation license. The extensive documentation and examples, integration with Python and the NumPy scientific computing package, and automation capability are just a few reasons why this package is a solid choice for scientific plotting in a Linux environment. This tutorial will provide several example plots created with matplotlib.
|
||||
|
||||
### Features ###
|
||||
|
||||
- Numerous plot types (bar, box, contour, histogram, scatter, line plots...)
|
||||
- Python-based syntax
|
||||
- Integration with the NumPy scientific computing package
|
||||
- Source data can be Python lists, Python tuples, or NumPy arrays
|
||||
- Customizable plot format (axes scales, tick positions, tick labels...)
|
||||
- Customizable text (font, size, position...)
|
||||
- TeX formatting (equations, symbols, Greek characters...)
|
||||
- Compatible with IPython (allows interactive plotting from a Python shell)
|
||||
- Automation - use Python loops to iteratively create plots
|
||||
- Save plots to image files (png, pdf, ps, eps, and svg format)
|
||||
|
||||
The Python-based syntax of matplotlib serves as the foundation for many of its features and enables an efficient workflow. There are many scientific plotting packages that can produce quality plots, but do they allow you to do it directly from within your Python code? On top of that, do they allow you to create automated routines for iterative creation of plots that can be saved as image files? Matplotlib allows you to accomplish all of these tasks. You can now look forward to saving time that would have otherwise been spent manually creating multiple plots.
|
||||
|
||||
### Installation ###
|
||||
|
||||
Installation of Python and the NumPy package is a prerequisite for use of matplotlib. Instructions for installing NumPy can be found [here][1].
|
||||
|
||||
To install matplotlib in Debian or Ubuntu, run the following command:
|
||||
|
||||
$ sudo apt-get install python-matplotlib
|
||||
|
||||
To install matplotlib in Fedora or CentOS/RHEL, run the following command:
|
||||
|
||||
$ sudo yum install python-matplotlib
|
||||
|
||||
### Matplotlib Examples ###
|
||||
|
||||
This tutorial will provide several plotting examples that demonstrate how to use matplotlib:
|
||||
|
||||
- Scatter and line plot
|
||||
- Histogram plot
|
||||
- Pie chart
|
||||
|
||||
In these examples we will use Python scripts to execute matplotlib commands. Note that the numpy and matplotlib modules must be imported from within the scripts via the import command. np is specified as a reference to the numpy module and plt is specified as a reference to the matplotlib.pyplot namespace:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
### Example 1: Scatter and Line Plot ###
|
||||
|
||||
The first script, script1.py completes the following tasks:
|
||||
|
||||
- Creates three data sets (xData, yData1, and yData2)
|
||||
- Creates a new figure (assigned number 1) with a width and height of 8 inches and 6 inches, respectively
|
||||
- Sets the plot title, x-axis label, and y-axis label (all with font size of 14)
|
||||
- Plots the first data set, yData1, as a function of the xData dataset as a dotted blue line with circular markers and a label of "y1 data"
|
||||
- Plots the second data set, yData2, as a function of the xData dataset as a solid red line with no markers and a label of "y2 data".
|
||||
- Positions the legend in the upper left-hand corner of the plot
|
||||
- Saves the figure as a PNG file
|
||||
|
||||
Contents of script1.py:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
xData = np.arange(0, 10, 1)
|
||||
yData1 = xData.__pow__(2.0)
|
||||
yData2 = np.arange(15, 61, 5)
|
||||
plt.figure(num=1, figsize=(8, 6))
|
||||
plt.title('Plot 1', size=14)
|
||||
plt.xlabel('x-axis', size=14)
|
||||
plt.ylabel('y-axis', size=14)
|
||||
plt.plot(xData, yData1, color='b', linestyle='--', marker='o', label='y1 data')
|
||||
plt.plot(xData, yData2, color='r', linestyle='-', label='y2 data')
|
||||
plt.legend(loc='upper left')
|
||||
plt.savefig('images/plot1.png', format='png')
|
||||
|
||||
The resulting plot is shown below:
|
||||
|
||||
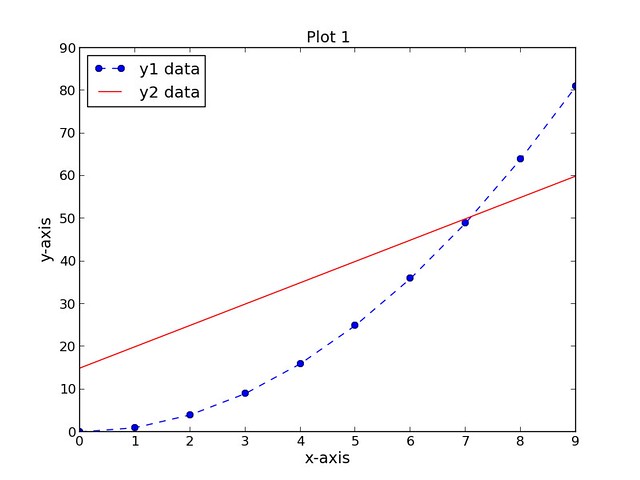
|
||||
|
||||
### Example 2: Histogram Plot ###
|
||||
|
||||
The second script, script2.py completes the following tasks:
|
||||
|
||||
- Creates a data set containing 1000 random samples from a Normal distribution
|
||||
- Creates a new figure (assigned number 1) with a width and height of 8 inches and 6 inches, respectively
|
||||
- Sets the plot title, x-axis label, and y-axis label (all with font size of 14)
|
||||
- Plots the data set, samples, as a histogram with 40 bins and an upper and lower bound of -10 and 10, respectively
|
||||
- Adds text to the plot and uses TeX formatting to display the Greek letters mu and sigma (font size of 16)
|
||||
- Saves the figure as a PNG file
|
||||
|
||||
Contents of script2.py:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
mu = 0.0
|
||||
sigma = 2.0
|
||||
samples = np.random.normal(loc=mu, scale=sigma, size=1000)
|
||||
plt.figure(num=1, figsize=(8, 6))
|
||||
plt.title('Plot 2', size=14)
|
||||
plt.xlabel('value', size=14)
|
||||
plt.ylabel('counts', size=14)
|
||||
plt.hist(samples, bins=40, range=(-10, 10))
|
||||
plt.text(-9, 100, r'$\mu$ = 0.0, $\sigma$ = 2.0', size=16)
|
||||
plt.savefig('images/plot2.png', format='png')
|
||||
|
||||
The resulting plot is shown below:
|
||||
|
||||
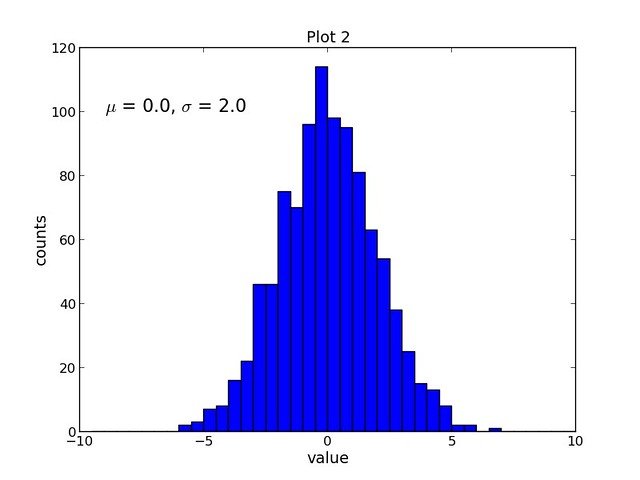
|
||||
|
||||
### Example 3: Pie Chart ###
|
||||
|
||||
The third script, script3.py completes the following tasks:
|
||||
|
||||
- Creates data set containing five integers
|
||||
- Creates a new figure (assigned number 1) with a width and height of 6 inches and 6 inches, respectively
|
||||
- Adds an axes to the figure with an aspect ratio of 1
|
||||
- Sets the plot title (font size of 14)
|
||||
- Plots the data set, data, as a pie chart with labels included
|
||||
- Saves the figure as a PNG file
|
||||
|
||||
Contents of script3.py:
|
||||
|
||||
import numpy as np
|
||||
import matplotlib.pyplot as plt
|
||||
|
||||
data = [33, 25, 20, 12, 10]
|
||||
plt.figure(num=1, figsize=(6, 6))
|
||||
plt.axes(aspect=1)
|
||||
plt.title('Plot 3', size=14)
|
||||
plt.pie(data, labels=('Group 1', 'Group 2', 'Group 3', 'Group 4', 'Group 5'))
|
||||
plt.savefig('images/plot3.png', format='png')
|
||||
|
||||
The resulting plot is shown below:
|
||||
|
||||
|
||||
|
||||
### Summary ###
|
||||
|
||||
This tutorial provides several examples of plots that can be created with the matplotlib scientific plotting package. Matplotlib is a great solution for scientific plotting in a Linux environment given its natural integration with Python and NumPy, its ability to be automated, and its production of a wide variety of customizable high quality plots. Documentation and examples for the matplotlib package can be found [here][2].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/matplotlib-scientific-plotting-linux.html
|
||||
|
||||
作者:[Joshua Reed][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/joshua
|
||||
[1]:http://xmodulo.com/numpy-scientific-computing-linux.html
|
||||
[2]:http://matplotlib.org/
|
||||
@ -0,0 +1,54 @@
|
||||
、Linux 3.18 内核发布了,下面的是更新的内容
|
||||
================================================================================
|
||||

|
||||
|
||||
新的一月意味着新的稳定版Linux内核的发布,今天Linus Torvalds[宣布Linux 3.18 很快就会发布了][1]。
|
||||
|
||||
Torvalds在Linux内核邮件列表中解释到,由于在3.17中还存在几个令一小部分用户烦心的问题,‘**绝不可以在一些人积极解决老问题时其他人无所事事。**’
|
||||
|
||||
### Linux 3.18中有什么新的? ###
|
||||
|
||||
Linux 3.18内核主要致力于硬件支持、电源效率、bug修复和可靠性。
|
||||
|
||||
如往常一样,这些内容跨越很大,容易让人迷惑 。比如:加密层多重缓冲操作 - 到气冲感知, 就像对雷蛇游戏手柄的支持。
|
||||
|
||||
下面我们收集了这个版本的重要的改变。这远远不是所有的,只是选取了一些更相关的内容。
|
||||
|
||||
|
||||
- Nouveau (免费 Nvidia GPU 驱动) 现在支持基础 DisplayPort 音频
|
||||
- 对雷蛇游戏手柄的支持,用在Xbox 360上
|
||||
- Xilinx USB2 外设
|
||||
- 对Microchip AR1021 i2c、PenMount 6000 touch的触摸屏支持。
|
||||
- 音频编码: Cirrus Logic CS35L32、 Everest ES8328and Freescale ES8328
|
||||
- 音频支持: 通用飞思卡尔声卡, A模拟SSM4567音频放大器
|
||||
- 不同的文件系统提升, 包括 Btrfs 和 F2FS
|
||||
- 现在支持了DCTCP拥塞控制算法
|
||||
- JIT 编译64位 eBPF程序
|
||||
- “Tinification” 帮助开发人员编译更精简更小的内核
|
||||
|
||||
#### 在Ubuntu上安装 Linux 3.18 ####
|
||||
|
||||
虽然声称是稳定版并带来了大量的更新,但不要马上急着升级你的系统。除非你擅长处理监控异常,CPU过热、和其他各种系统报出的异常。
|
||||
|
||||
如果你坚持更新,你可以在kernel.org网站上找到源码包。
|
||||
|
||||
- [下载Linux内核源码包][2]
|
||||
|
||||
有一个由Canonical维护的最新Linux内核归档。尽管你可能在其他地方看到过,但是,请注意,这不是针对终端用户的。没有任何保证与支持,你自己承担风险。
|
||||
|
||||
- [访问Ubuntu内核主线归档][3]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/12/linux-kernel-3-18-released-whats-new
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://lkml.org/lkml/2014/12/7/202
|
||||
[2]:https://www.kernel.org/pub/linux/kernel/v3.x/
|
||||
[3]:http://kernel.ubuntu.com/~kernel-ppa/mainline/?C=N;O=D
|
||||
@ -0,0 +1,86 @@
|
||||
5大最佳开源的浏览器安全应用
|
||||
================================================================================
|
||||
浏览器是现在各种在线服务的入口。电脑安全问题迄今仍未得到解决,技术进步为恶意软件提供了新的途径,感染我们的设备,入侵商业网络。例如,智能手机与平板为恶意软件--及其同伙“[恶意广告][1]”--带来一片全新天地,它们在其中腾挪作乱。
|
||||
|
||||
恶意广告在合法广告与合法网络中注入恶意软件。当然你可能会认为“合法”广告与网络与非法广告与网络之间仅有一线之隔。但是请不要偏题哦。隐私与安全天生就是一对兄弟,保护隐私也就是保护你的安全。
|
||||
|
||||
Firefox, Chrome, 以及 Opera当仁不让属最棒的浏览器:性能最佳、兼容性最好、以及安全性最优。以下五个开源安全应用安装于浏览器后会助你抵御种种威胁。
|
||||
|
||||
### 保护隐私: 开源浏览器安全应用 ###
|
||||
|
||||
#### 1. [AdBlock][2] ####
|
||||
|
||||
广告网络为恶意软件提供了肥沃的土壤。一个广告网络可以覆盖数千站点,因此攻陷一个广告网络就相当于攻陷数千台机器。AdBlock及其衍生品—[AdBlock Plus][2], [AdBlock Pro][3], 与 [AdBlock Edge][4]--都是屏蔽广告的优秀工具,可以让那些充斥烦人广告的网站重新还你一片清静。
|
||||
|
||||
当然,凡事都有两面性:上述做法损害了依靠广告收入的站点的利益。这些工具一键式白名单功能,对于那些你希望支持的网站,你可以通过白名单功能关闭这些网站的广告屏蔽。(真的,我亲爱的站长们,如果你不希望网站访问者屏蔽你的广告,那么就适可而止,不要让人反感。)
|
||||
|
||||

|
||||
|
||||
图1:在Ad Blocker中添加其它过滤规则。
|
||||
|
||||
Ad Blocker们不仅能屏蔽广告;它们还能屏蔽网站跟踪爬虫与恶意域名。要打开额外过滤规则,点击ad blocker图标 > 点击**首选项**,转至**过滤规则订阅**标签。点击按纽**添加订阅过滤规则**,然后加入**Easy Privacy + EasyList**规则。加入恶意域名过滤也是个不错的选择;它会屏蔽那些供恶意软件与间谍软件寄生的域名。Adblock可在Firefox, Chrome, Opera, Safari, IE, 以及Android平台下工作。
|
||||
|
||||
#### 2. [HTTPS Everywhere][5] ####
|
||||
|
||||
浏览器扩展HTTPS Everywhere可确保在网站HTTPS可用的时候,总是以HTTPS方式连接到站点。HTTPS意味着你的连接是以SSL(安全套接层)方式加密的,SSL协议通常用于加密网站与电子邮件连接。HTTPS Everywhere可在Firefox, Chrome, 及Opera下使用。
|
||||
|
||||
安装了HTTPS Everywhere之后,它会询问你是否希望启用SSL检测程序。点击是,因为SSL检测程序会提供额外保护,防止中间人攻击与虚假SSL证书攻击。HTTPS Everywhere可在Firefox, Chrome, Opera, Safari, IE, 以及Android平台下工作。
|
||||
|
||||
#### 3. [Social Fixer][6] ####
|
||||
|
||||
Social Fixer驯服Facebook。它给了你一把尚方宝剑,你可以用它过滤“动态汇总”,从而只看到你想看的动态、生成按主题分类的标签动态、隐藏不想查看的动态、鼠标悬停图片时显示完整尺寸的图片、禁止影院方式浏览图像,还有其它更多功能。
|
||||
|
||||
Social Fixer本身不是安全工具,但它具有两个重要的安全特性:
|
||||
|
||||
- 它可以将Facebook网页截图中你的个人资料头像以通用图标代替,并以虚假名字替代你的用户名,从而起到匿名作用。
|
||||
- 它可以很可靠地屏蔽Facebook游戏,而Facebook游戏正是尽人皆知的麻烦制造者。
|
||||
|
||||

|
||||
|
||||
图2: 使用Social Fixer匿名化Facebook网面。
|
||||
|
||||
#### 4. [Privacy Badger][7] ####
|
||||
|
||||
电子前线基金会出品的Privacy Badger是一款优秀的反跟踪与反间谍广告的拦截工具。现在的网页内容来源可谓五花八门:广告服务器、评论服务器、图片工场、第三方登陆服务器,以及其它种种不一而足。
|
||||
|
||||
AdBlock也能拦截这些乌七八糟的东西,不过Privacy Badger在此方面更胜一筹。Privacy Badger依靠算法与策略方法而非过滤规则,这样如果拦截出错的话,可以轻易重写,而过滤规则需要专人维护。Privacy Badger在Firefox与Chrome下均可工作。
|
||||
|
||||

|
||||
|
||||
图3: Privacy Badger拦截跟踪站点。
|
||||
|
||||
Privacy Badger装好后就能使用了。点击图标,看看它对你浏览的网页都拦截了哪些东西。你可以试试访问Huffingtonpost.com,这是一家不在每一个页面塞满第三方组件誓不罢休的网站(图3)。
|
||||
|
||||
滑块显示每个站点的状态:红色表示该站点被彻底拦截,不能设置cookies(缓冲数据),或者向你提供任何内容。黄色意味着第三方域名正试图跟踪,但是它列于Privacy Badger的允许域名的白名单之中。绿色表示第三方目前还未归入跟踪者之列,但是在你访问**若干**网站之后,Privacy Badger会观察其行为,并决定是否将其归为跟踪者。
|
||||
|
||||
你也可以根据你的偏好来设置滑块;例如,在我访问的某个网站,我用Privacy Badger拦截了bazaarvoice.com,一些购物网站使用这家站点来托管他们的客户评论。
|
||||
|
||||
#### 5. [Disconnect][8] ####
|
||||
|
||||
Disconnect是另外一款反跟踪反cookie工具,拥有众多功能。它可在Firefox, Chrome, IE, Safari下工作,并且为iOS与Android平台打造了特殊的版本。Disconnect不但能反跟踪,而且它使用自己的虚拟专用网络(VPN),防止窃听与恶意广告,使你的无线传输(Wi-fi, 3G, 4G)更安全。它可以防止部件劫持,而部件劫持是攻击者用于在需要登陆的网站获得访问权限的技术。通过部件劫持,攻击者无需密码,而只要使用窃取的cookies,就能获得网站访问权限。
|
||||
|
||||
Disconnect还有安全搜索功能,可以阻止搜索引擎爱挖数据的癖好,你可以安心无虞地使用你中意的搜索引擎。
|
||||
|
||||
想象一下,网页上所有东西都腾空而出,奔你而去。当然这一切都是抽象的且在幕后悄然发生,不象有人正在猛击窗户试图进入你家那么明显罢了。但是,威胁倒是实实在在的,而且数不胜数,所以你必须采取预防措施,来保护自己。
|
||||
|
||||
Carla Schroder著有The Book of Audacity, Linux Cookbook, Linux Networking Cookbook等书,并撰写了上百篇Linux指南文章。她曾担任Linux Planet与Linux Today网站总编。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.smallbusinesscomputing.com/biztools/5-best-open-source-web-browser-security-apps.html
|
||||
|
||||
作者:[Carla Schroder][a]
|
||||
译者:[译者ID](https://github.com/yupmoon)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.smallbusinesscomputing.com/author/Carla-Schroder-6080.html
|
||||
[1]:http://www.webopedia.com/TERM/M/malvertising.html
|
||||
[2]:https://getadblock.com/
|
||||
[3]:https://chrome.google.com/webstore/detail/adblock-pro/ocifcklkibdehekfnmflempfgjhbedch?hl=en-US
|
||||
[4]:https://addons.mozilla.org/en-us/firefox/addon/adblock-edge/
|
||||
[5]:https://www.eff.org/Https-everywhere
|
||||
[6]:http://socialfixer.com/
|
||||
[7]:https://www.eff.org/privacybadger
|
||||
[8]:https://disconnect.me/
|
||||
@ -0,0 +1,196 @@
|
||||
Linux 下五款出色的流媒体客户端
|
||||
================================================================================
|
||||
数字流媒体这几天几乎占据了我音乐收听的全部时间。近年来我为了收藏 CD 花费了数量可观的费用;但它们中的大部分现在正静静地躺在满是灰尘的角落里。基本上所有的音乐流媒体服务所提供的的音质都不如 CD 的,但它们受欢迎的原因很大程度上在于其便捷性,而非高度保真的音质再现。音乐流媒体不仅造成了 CD 销量的大幅减少;也使数字音乐的下载开始缓慢下滑。这种趋势还会继续下去。音乐发烧友现在或许也想要拥抱音乐流媒体服务了,某些音乐流媒体服务商如 Tidal 提供了无损的音乐流媒体服务,其中包含了 25 万首比特率为 1411kbps 的 FLAC 格式的音乐。
|
||||
|
||||
尽管 CD 暂时不会消失,但音乐流媒体服务商却无法协调和那些不满从音乐托管服务中收取的租金的唱片公司及音乐家之间的问题。这一切仍然处于变化之中;我们看到了今年 Led Zeppelin, Pink Floyd, Metallica 签名支持流媒体服务,但仍然有部分知名的老牌乐队如 Beatles, Radiohead 以及 AC/DC 拒绝将自己的作品放到流媒体上供粉丝收听。即使当某个唱片公司或者音乐家已经授权给流媒体服务商访问自己的作品,但只要音乐家发表声明就可以在第一时间将其作品从流媒体服务下架。本月(2014 年 11 月),Taylor Swift 请求将她的所有音乐作品从 Spotify 的流媒体服务下架。有些人还是更偏向于“拥有”他们的音乐,但这看起来像是一种快要过时了的欣赏音乐的方式。
|
||||
|
||||
使用 Linux 平台来收听流媒体音乐服务的方法已经逐渐成熟。在 Linux 平台下,你可以找到许多客户端,通过它们你可以使用大部分的音乐流媒体服务;我希望 TIDAL 能在今后合适的时候发行 Linux 桌面客户端,而不是仅仅依赖 web 播放器。本文精选的这些应用都是非常出色的。另外 Amarok,pianobar 还有 Tomahawk 也表现得很不错。
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Spotify 是一种专有的 P2P 音乐流媒体服务,允许用户收听点播曲目或专辑。Spotify 将自己描述为“音乐圣殿。快捷、简易、免费的服务”。Spotify 分别为普通的移动端和桌面端用户提供了 96kbps 和 160kbps 比特率的流媒体服务,并且为高级用户提供了 Ogg Vorbis 格式的 320kbps 比特率的流媒体服务。Spotify 为普通用户提供了免费但是有广告的服务,以及无广告的订阅账户服务。
|
||||
|
||||
Spotify 是很奇妙的服务,向用户们提供了涵盖各种类型的数量众多的音乐,如:流行乐、另类摇滚、古典乐、铁克诺电音、摇滚乐等。这是发现新音乐的好方法。Spotify 得到了包括 Sony BMG,EMI,Universal 以及 Warner Music 在内的主流唱片公司,以及 Labrador Records,The Orchard,Alligator Records,Merlin,CD Baby,INgrooves 等独立唱片唱片公司和分销网络,甚至 Chandos,Naxos,EMI Classic,Warner Classics,Denon Essentials 这些古典唱片公司的支持,还有更多的公司在这里就不一一列举了。
|
||||
Spotify 的音乐涵盖范围还在继续以惊人的步伐扩张着。
|
||||
|
||||
Spotify 现在并没有发行官方版的 Linux 客户端。不过,开发团队已经推出了针对 Linux 的客户端预览版,并且表现得还不错。因为仍然是预览版,所以没有得到官方的支持。
|
||||
|
||||
Spotify 流媒体服务现已支持以下地区/国家:安道尔,阿根廷,澳大利亚,奥地利,比利时,保加利亚,哥伦比亚,塞浦路斯,丹麦,爱沙尼亚,芬兰,法国,德国,希腊,香港,冰岛,爱尔兰,意大利,拉脱维亚,列支敦士登,立陶宛,卢森堡,马来西亚,马耳他,墨西哥,摩纳哥,荷兰,新西兰,挪威,菲律宾,波兰,葡萄牙,西班牙,新加坡,瑞典,瑞士,台湾,土耳其,英国,美国,乌拉圭等。
|
||||
|
||||
**特色包括:**
|
||||
|
||||
- 精心设计的界面,导航时非常方便
|
||||
- 创建和编辑播放列表
|
||||
- 发现新的音乐
|
||||
- 共享音乐及播放列表
|
||||
- 电台功能
|
||||
- 最受欢迎的的列表
|
||||
- 额外功能及种类繁多的应用
|
||||
|
||||
- 网址:[www.spotify.com/uk/download/previews][1]
|
||||
- 开发者:Spotify
|
||||
- 许可证:专有许可证
|
||||
- 当前版本:预览版
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Pithons 是一款开源的的本地 Pandora 电台 Linux 客户端。它提供了一个轻量级的界面以替代 Pandora.com 的 web 客户端。其图形用户界面上集成了多媒体快捷键、通知中心以及声音菜单。
|
||||
|
||||
Pandora 音乐服务只能通过美国的 IP 地址使用。不过,非美国用户可以通过 VPN 连接来使用 Pandora。
|
||||
|
||||
**特色包括:**
|
||||
|
||||
- 播放/暂停/下一首
|
||||
- 切换电台
|
||||
- 记住用户名和密码
|
||||
- 给喜欢的音乐和艺术家添加书签
|
||||
- 获取封面
|
||||
- 喜欢/讨厌/不再播放这首音乐
|
||||
- 在通知中心中弹出歌曲信息
|
||||
- 跳转到 pandora.com 歌曲信息页面/电台页面
|
||||
- 超时后重连 pandora
|
||||
- QuickMix 编辑
|
||||
- 创建电台
|
||||
- 多媒体按键
|
||||
- 代理连接
|
||||
- Last.fm 歌曲记录
|
||||
- 音量控制
|
||||
- 屏保暂停等插件
|
||||
- DBUS 接口:MPRIS 和 Pithos
|
||||
|
||||
- 网址:[pithos.github.io][2]
|
||||
- 开发者:Kevin Mehall
|
||||
- 许可证:GNU GPL v3
|
||||
- 当前版本:1.0.0
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Clementine 基于 Amarok 开发,是一款跨平台的轻量级现代化音乐播放器和媒体库管理工具。Clementine 致力于打造快捷简易的界面,使你可以轻松搜索和播放音乐。
|
||||
|
||||
Clementine 在 Amarok 1.4 的基础上开发。
|
||||
|
||||
**特色包括:**
|
||||
- 检索、播放本地音乐库
|
||||
- 从 Last.fm 和 SomaFM 收听互联网电台
|
||||
- 标签式播放列表,支持导入导出 M3U,XSPF,PLS 及 ASX 格式的播放列表
|
||||
- 创建智能播放列表和动态播放列表
|
||||
- 载入 M3U 和 XSPF 播放列表
|
||||
- 对播放列表的撤销和重做
|
||||
- 编辑 MP3 和 OGG 文件的信息,管理媒体库
|
||||
- 从 Last.fm 下载缺失的专辑封面
|
||||
- 集成 gpodder.net 播客
|
||||
- 图形化均衡器
|
||||
- 支持 Windows,Mac OS X 及 Linux
|
||||
- 支持 Linux(libnotify)及 Mac OS X(Growl)本地桌面通知中心
|
||||
- 从 MusicBrainz 获取缺失的信息
|
||||
- 炫彩屏幕显示
|
||||
- 队列管理
|
||||
- 支持 Linux 下的 MPRIS,以及命令行远程控制
|
||||
- 支持索引和播放 Google Drive 中的音乐
|
||||
- 支持 Soundcloud
|
||||
- 支持 jazzradio.com
|
||||
- 支持 Moodbar
|
||||
- 基于 projectM 的可视化技术
|
||||
- 拷贝音乐至 iPod,iPhone,MTP 或者 大容量 USB 设备
|
||||
- 远程控制
|
||||
- 转码音乐至 MP3,Ogg Vorbis,Ogg Speex,FLAC 以及 AAC
|
||||
|
||||
- 网址:[www.clementine-player.org][3]
|
||||
- 开发者:David Sansome,John Maguire
|
||||
- 许可证:GNU GPL v3
|
||||
- 当前版本:1.2
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Nuvola Player 是一个免费的开源项目,能够整合云端音乐到你的桌面中(支持托盘图标、Ubuntu 声音菜单、dock 菜单以及通知中心)。
|
||||
|
||||
为了使用全部的流媒体服务,你需要安装 Flash 和 HTML5 的音频支持。某些基于 Web 的流媒体服务可以使用 HTML5 的音频技术播放音乐,而非使用 Flash 插件。Nuvola Player 需要 GStreamr 和 MP3 解码器插件来提供 HTML5 音频支持。
|
||||
|
||||
**支持的流媒体服务:**
|
||||
|
||||
- 集成了 MP3 商店的亚马逊云播放器,允许用户在亚马逊云端驱动器中存储他们的音乐,并且在任何支持的浏览器上播放音乐
|
||||
- Bandcamp,是一家在线音乐商店,也是艺人宣传平台,主要适于独立艺术家
|
||||
- Deezer,一家法国的基于 Web 的音乐流媒体服务商。Deezer 允许用户在多台设备上在线或者离线播放音乐,现在拥有 1800 万的曲目,超过 30000 的电台以及 2200 万的用户(150 万订阅用户)
|
||||
- 8tracks,是一家融合了互联网电台和社交元素的网站,坚持至少 8 个曲目的为用户量身定制的流媒体播放列表
|
||||
- Google Play,谷歌运营的一家数字服务商店,其经营项目包括音乐、电影、书籍,以及 Android 应用和游戏,其云端播放器支持播放用户自己上传的音乐和在 Google Play 里购买的音乐
|
||||
- Grooveshark,提供了国际化在线音乐搜索引擎、音乐流媒体服务以及音乐推荐服务,允许用户进行搜索、使用流媒体以及上传音乐,并且能把这些音乐进行立即播放或者添加到一个播放列表中
|
||||
- Grooveshark Mobile,基于 HTML5 的 Grooveshark 移动版,不需要 Flash 插件的支持
|
||||
- Hype Machine,Pandora Radio 和 Pitchfork Media 的融合产物。它从音乐博客上精选了最近发布的歌曲(约 1500 首),并在网站主页上列出了这些歌曲的信息
|
||||
- Jango,一款免费的在线音乐流媒体服务,允许用户创建和分享自己创建的电台
|
||||
- Logitech Media Server,是 Logitech Squeezebox devices 的开源流媒体服务。支持许多插件以及如 Deezer 和 Spotify 等其他流媒体服务
|
||||
- Pandora,智能化音乐推荐服务以及音乐基因组计划“托管人”,服务仅针对美国地区
|
||||
- Rdio,有广告的音乐订阅服务
|
||||
- Spotify,商业化流媒体服务,提供来自唱片公司的被严格限制的数字版权内容
|
||||
- This is My Jam,你可以存放某一刻你非常喜欢的音乐,并且每天都可以收听由朋友们精挑细选的音乐
|
||||
|
||||
**特色包括:**
|
||||
|
||||
- 多媒体快捷键
|
||||
- 显示桌面通知
|
||||
- 集成了众多声音菜单、小程序以及启动器,甚至更多
|
||||
- Last FM 以及 Libre FM 歌曲记录
|
||||
- 获取歌词
|
||||
- 支持 Amazon Music Prime streaming
|
||||
|
||||
- 网址:[tiliado.eu/nuvolaplayer][4]
|
||||
- 开发者:Jiří Janoušek and service maintainers
|
||||
- 许可证:2-Clause BSD license
|
||||
- 当前版本:2.4.3
|
||||
|
||||
----------
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
Atraci 是一款多平台的开源流媒体应用,允许用户收听超过 6000 万首音乐。Atraci 仍然处于基础开发阶段,所以很多功能暂时还未完善。
|
||||
|
||||
Atraci 使用 iTunes,Last.fm 以及 SoundCLoud 显示歌曲信息 —— 专辑封面、歌曲名称以及艺术家。Atraci 在 YouTube 上搜索最匹配这首音乐信息的视频,并使用其中质量最高的。
|
||||
|
||||
**特色包括:**
|
||||
|
||||
- 无广告、无需注册
|
||||
- 直观的用户界面
|
||||
- 智能匹配搜索任何音乐、艺术家或者专辑。Atraci 会在线校对其信息,以显示正确的歌曲名称、专辑封面以及音轨等等,同时列出最高质量的视频流媒体
|
||||
- 自动修正所属专辑与艺术家
|
||||
- 通过默认方式、艺术家姓名或者曲目名称对结果排序
|
||||
- 以网格或列表模式查询结果
|
||||
- 检索视频可以全屏模式观看
|
||||
- 以随机或重复模式创建播放列表
|
||||
- 应用程序内的音量调整滑块、音轨调节以及专辑封面
|
||||
- 播放历史
|
||||
|
||||
- 网址:[atraci.github.io/Atraci-website][5]
|
||||
- 开发者:The Atraci Team
|
||||
- 许可证:The MIT License
|
||||
- 当前版本:0.7.0
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.linuxlinks.com/article/20141116052055674/MusicStreaming.html
|
||||
|
||||
作者:Frazer Kline
|
||||
译者:[Stevearzh](https://github.com/Stevearzh)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://www.spotify.com/uk/download/previews/
|
||||
[2]:http://pithos.github.io/
|
||||
[3]:https://www.clementine-player.org/
|
||||
[4]:https://tiliado.eu/nuvolaplayer/
|
||||
[5]:http://atraci.github.io/Atraci-website/
|
||||
@ -0,0 +1,22 @@
|
||||
开始使用Ubuntu 14.04(PDF指南)
|
||||
================================================================================
|
||||
开始熟悉每天的任务,像上网冲浪,听听音乐,还有扫描文档之类。
|
||||
|
||||
好好享受这份全面而综合的Ubuntu操作系统初学者指南吧。本教程适用于任何经验等级的人,跟着傻瓜式的指令一步一步操作吧。好好探索Ubuntu系统的潜力吧,你不会因为技术细节而陷入困境。
|
||||
|
||||
- [**开始使用Ubuntu 14.04 (PDF指南)**][1]
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/getting-started-with-ubuntu-14-04-pdf-guide.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://ubuntugeek.tradepub.com/free/w_ubun06/
|
||||
@ -0,0 +1,54 @@
|
||||
四招搞定Linux内核热补丁
|
||||
================================================================================
|
||||

|
||||
Credit: Shutterstock
|
||||
|
||||
多种技术在竞争成为实现inux内核热补丁的最优方案。
|
||||
没人喜欢重启机器,尤其是涉及到一个内核问题的最新补丁程序。
|
||||
为达到不重启的目的,目前有3个项目在朝这方面努力,将为大家提供对内核进行运行时打热补丁的机制,这样就可以做到完全不重启机器。
|
||||
|
||||
### Ksplice项目 ###
|
||||
|
||||
首先要介绍的项目是Ksplice,它是热补丁技术的创始者,并于2008年建立了与项目同名的公司。Ksplice在替换新内核时,不需要预先修改;只需要一个diff文件,将内核的修改点列全即可。Ksplice公司免费提供软件,但技术支持是需要收费的,目前能够支持大部分常用的Linux发行版本。
|
||||
|
||||
但在2011年[Oracle收购了这家公司][1]后,情况发生了变化。 这项功能被合入到Oracle的Linux发行版本中,且只对Oralcle的版本提供技术更新。 这就导致,其他内核hacker们开始寻找替代Ksplice的方法,以避免缴纳Oracle税。
|
||||
|
||||
### Kgraft项目 ###
|
||||
|
||||
2014年2月,Suse提供了一个很好的解决方案:[Kgraft][2],该技术以GPLv2/GPLv3混合许可证发布,且Suse不会将其作为一个专有的实现。Kgraft被[提交][3]到Linux内核主线,很有可能被内核主线采用。目前Suse已经把此技术集成到[Suse Linux Enterprise Server 12][4]。
|
||||
|
||||
Kgraft和Ksplice在工作原理上很相似,都是使用一组diff文件来计算内核中需要修改的部分。但与Ksplice不同的是,Kgraft在做替换时,不需要完全停止内核。 在打补丁时,正在运行的函数可以先使用老版本中对应的部分,当补丁打完后就可以切换新的版本。
|
||||
|
||||
### Kpatch项目 ###
|
||||
|
||||
Red Hat也提出了他们的内核热补丁技术。同样是在今年年初 -- 与Suse在这方面的工作差不多 -- [Kpatch][5]的工作原理也和Kgraft相似。
|
||||
|
||||
主要的区别点在于,正如Red Hat的Josh Poimboeuf[总结][6]的那样,Kpatch不能将内核调用重定向到老版本。相反,它会等待所有函数调用都停止时,再切换到新内核。Red Hat的工程师认为这种方法更为安全,且更容易维护,缺点就是在打补丁的过程中会带来更大的延迟。
|
||||
|
||||
和Kgraft一样,Kpatch不仅仅能在Red Hat的发行版本上可以使用,同时也被提交到了内核主线,作为一个可能的候选。 坏消息是Red Hat还未将此技术集成到产品中。 它只是被合入到了Red Hat Enterprise Linux 7的技术预览版中。
|
||||
|
||||
### ...也许 Kgraft + Kpatch更合适? ###
|
||||
|
||||
Red Hat的工程师Seth Jennings在2014年11月初,提出了[第四种解决方案][7]。将Kgraft和Kpatch结合起来, 补丁包用这两种方式都可以。在新的方法中,Jennings提出,“热补丁核心为其他内核模块提供了热补丁的注册机制”, 通过这种方法,打补丁的过程 -- 更准确的说,如何处理运行时内核调用 --可以被更加有序的进行。
|
||||
|
||||
这项新建议也意味着两个方案都还需要更长的时间,才能被linux内核正式采纳。尽管Suse步子迈得更快,并把Kgraft应用到了最新的enterprise版本中。让我们也关注一下Red Hat和Linux官方近期的动态。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.infoworld.com/article/2851028/linux/four-ways-linux-is-headed-for-no-downtime-kernel-patching.html
|
||||
|
||||
作者:[Serdar Yegulalp][a]
|
||||
译者:[coloka](https://github.com/coloka)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.infoworld.com/author/Serdar-Yegulalp/
|
||||
[1]:http://www.infoworld.com/article/2622437/open-source-software/oracle-buys-ksplice-for-linux--zero-downtime--tech.html
|
||||
[2]:http://www.infoworld.com/article/2610749/linux/suse-open-sources-live-updater-for-linux-kernel.html
|
||||
[3]:https://lwn.net/Articles/596854/
|
||||
[4]:http://www.infoworld.com/article/2838421/linux/suse-linux-enterprise-12-goes-light-on-docker-heavy-on-reliability.html
|
||||
[5]:https://github.com/dynup/kpatch
|
||||
[6]:https://lwn.net/Articles/597123/
|
||||
[7]:http://lkml.iu.edu/hypermail/linux/kernel/1411.0/04020.html
|
||||
@ -0,0 +1,75 @@
|
||||
在Ubuntu 14.10中如何安装和配置‘My Weather Indicator’
|
||||
================================================================================
|
||||

|
||||
|
||||
**在Ubuntu桌面中不缺乏若干应用同时提供天气信息的方法,你可以使用Unity Dash和桌面应用,比如[Typhoon][1],来获得天气信息。**
|
||||
|
||||
但是可以提供快速查询天气状况和温度数据,并且只需要一次鼠标点击而获得大量气象数据的面板插件,是到目前为止Linux平台下最受欢迎的天气应用。
|
||||
|
||||
Atareao开发的[My Weather Indicator][2]就是这类应用中的一个,也可以说是最好的一个。
|
||||
|
||||
它在Unity面板上显示实时温度和天气状况,并且有一个包括体感温度、云量和日升日落时间等天气数据的菜单。除此之外,该应用还支持桌面小部件、多地区支持、天气数据提供方选择以及其他很多的配置选项。
|
||||
|
||||
听起来很不错,是吧?那我们下面就来看看如何在Ubuntu上安装和配置它吧。
|
||||
|
||||
### 在Ubuntu上安装My Weather Indicator ###
|
||||
|
||||
My Weather Indicator无法从Ubuntu软件商店中直接获取。不过开发者为我们提供了.deb安装包和官方维护的PPA(为Ubuntu 14.04 LTS和14.10提供安装包)。
|
||||
|
||||
- 下载My Weather Indicator (.deb安装包)
|
||||
|
||||
为了确保你的应用最是最新版本,我建议将[Atareao PPA][3]添加到你的软件镜像源然后通过PPA来安装。
|
||||
|
||||
怎么做?**打开一个新的终端**窗口(Unity Dash > 终端,或者按Ctrl+Alt+T快捷键),然后**输入下面的两行命令**,期间你需要在提示处输入你的系统密码:
|
||||
|
||||
sudo add-apt-repository ppa:atareao/atareao
|
||||
|
||||
sudo apt-get update && sudo apt-get install my-weather-indicator
|
||||
|
||||
#### 配置My Weather Indicator ####
|
||||
|
||||
无论你是通过什么方法安装该应用,你都可以在Unity Dash中搜索“weather”并且点击该应用来打开它。
|
||||
|
||||

|
||||
|
||||
首次打开应用时会出现下面的配置窗口。在这里你可以手动设置地区或者使用geo-ip来自动获取。或者有时可能会不够精确,不过它可以省去手动设置过程。
|
||||
|
||||

|
||||
|
||||
如果你正在旅行(或者是出于聊天需要),**你可以添加一个第二地区**。这个设置和第一地区的设置相同,只不过是在“第二地区”的标签栏罢了。
|
||||
|
||||
在“**小部件设置**”区域勾选“**显示桌面小部件**”选项就会在你的桌面上添加一个小的天气小部件。小部件提供许多不同的皮肤,所以你一定要精心挑选你最喜欢的一个(注释:点击“确定”后对小部件的更改才会保存)。
|
||||
|
||||

|
||||
|
||||
My Weather Indicator使用[Open Weather Map][4]作为默认的天气数据提供方。不过你可以在‘**Weather Services**’面板中选择其他的数据提供方(有*标记的需要提供相关API key):
|
||||
|
||||
- Open Weather Map
|
||||
- Yahoo! Weather
|
||||
- Weather Underground*
|
||||
- World Weather Online*
|
||||
|
||||
在‘**Units**’标签页中,你可以设置温度、压力、风速等数据的单位。这些设置适用于所有添加的地区,也就是说你不能在一个地区使用摄氏度,另一个地区使用华氏度。
|
||||
|
||||

|
||||
|
||||
最后,在‘General Options‘标签页,你可以设置数据更新间隔、设置开机自动运行选项以及从两个图标中选择一个作为面板图标。
|
||||
|
||||
如果你不喜欢该应用,你可以尝试[Linux下查看天气数据的方法][5]。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/10/install-weather-indicator-ubuntu-14-10
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[JonathanKang](https://github.com/JonathanKang)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://launchpad.net/typhoon
|
||||
[2]:https://launchpad.net/my-weather-indicator
|
||||
[3]:https://launchpad.net/~atareao/+archive/ubuntu/atareao
|
||||
[4]:http://openweathermap.org/
|
||||
[5]:http://www.omgubuntu.co.uk/2014/02/get-weather-forecast-terminal-linux
|
||||
@ -0,0 +1,51 @@
|
||||
如何手动删除Oracle 11g数?据库
|
||||
================================================================================
|
||||
下面的步骤会家你如何在Linux环境下手动删除Oracle 11g数据库。
|
||||
|
||||
我在Centos 6上安装了Oralce 11G数据库。
|
||||
|
||||
使用SQL*Plus或者其他你喜欢的命令行工具登录数据库,登录用户是**sysdba**
|
||||
|
||||
输入下面的命令的到不同文件的路径:
|
||||
|
||||
select name from v$datafile;
|
||||
select member from v$logfile;
|
||||
select name from v$controlfile;
|
||||
select name from v$tempfile;
|
||||
|
||||
**在SQL*Plus中关闭数据库,接着退出SQL*Plus**
|
||||
|
||||
sqlplus " / as sysdba'
|
||||
|
||||
----------
|
||||
|
||||
shutdown immediate;
|
||||
quit;
|
||||
|
||||
**在命令行中输入下面的命令停止监听服务:**
|
||||
|
||||
在Oralce Linux账户中:
|
||||
|
||||
lsnrctl stop
|
||||
|
||||
回忆一下之前的文件路径;在删除这些文件的时候作为一个检查项。记住:你备份了数据库了么?当准备好之后,就删除你的数据文件吧,同样还有你的日志文件、控制文件和临时文件。
|
||||
|
||||
- 进入 **$ORACLE_HOME/network/admin** 目录并删除 **tnsnames.ora** 和 **listener.ora** 文件;
|
||||
- 进入 **$ORACLE_HOME/dbs** 目录并删除 **init[db_name].ora**、 **orapw[db_name]**和 **spfile[db_name].ora** 文件;
|
||||
- 进入 **$ORACLE_HOME/admin/[db_name]/pfile** 目录并删除 **init[db_name].ora** 文件;
|
||||
- 进入 **$ORACLE_HOME/admin/[db_name]/adump** 目录并删除所有文件;
|
||||
- 编辑**/etc/oratab** 并移除以你数据库名字开头的行.
|
||||
|
||||
这样就好了。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/manually-delete-oracle-11g-database/
|
||||
|
||||
作者:[M.el Khamlichi][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.unixmen.com/author/pirat9/
|
||||
@ -0,0 +1,95 @@
|
||||
如何不使用DBCA在Oracle 11中删除数据库
|
||||
================================================================================
|
||||
本文简短的教程,将会向你展示如何不使用DBCA(数据库配置助手)在Oracle 11中删除数据
|
||||
|
||||
#### 1- 导入数据库的SID,如果没有定义的话 ####
|
||||
|
||||
命令:
|
||||
export ORACLE_SID=database
|
||||
|
||||
#### 2- 以操作系统认证连接数据库 ####
|
||||
|
||||
命令:
|
||||
[oracle@Oracle11 ~]$ sqlplus / as sysdba
|
||||
|
||||
提示:
|
||||
----------
|
||||
|
||||
SQL*Plus: Release 11.2.0.1.0 Production on Mon Dec 1 17:38:02 2014
|
||||
|
||||
----------
|
||||
|
||||
Copyright (c) 1982, 2009, Oracle. All rights reserved.
|
||||
|
||||
----------
|
||||
|
||||
Connected to an idle instance.
|
||||
|
||||
#### 3- 启动数据库实例 ####
|
||||
|
||||
命令:
|
||||
SQL> startup
|
||||
提示:
|
||||
ORACLE instance started.
|
||||
Total System Global Area 3340451840 bytes
|
||||
Fixed Size 2217952 bytes
|
||||
Variable Size 1828718624 bytes
|
||||
Database Buffers 1493172224 bytes
|
||||
Redo Buffers 16343040 bytes
|
||||
Database mounted.
|
||||
Database opened.
|
||||
|
||||
#### 4- 关闭数据库 ####
|
||||
|
||||
命令:
|
||||
SQL> shutdown immediate;
|
||||
提示:
|
||||
Database closed.
|
||||
Database dismounted.
|
||||
ORACLE instance shut down.
|
||||
|
||||
#### 5- 启动独占模式 ####
|
||||
|
||||
命令:
|
||||
SQL> startup mount exclusive restrict
|
||||
提示:
|
||||
ORACLE instance started.
|
||||
|
||||
----------
|
||||
|
||||
Total System Global Area 3340451840 bytes
|
||||
Fixed Size 2217952 bytes
|
||||
Variable Size 1828718624 bytes
|
||||
Database Buffers 1493172224 bytes
|
||||
Redo Buffers 16343040 bytes
|
||||
Database mounted.
|
||||
|
||||
#### 6- 删除数据库 ####
|
||||
|
||||
命令:
|
||||
SQL> drop database;
|
||||
|
||||
提示:
|
||||
----------
|
||||
|
||||
Database dropped.
|
||||
|
||||
----------
|
||||
|
||||
Disconnected from Oracle Database 11g Enterprise Edition Release 11.2.0.1.0 - 64bit Production
|
||||
With the Partitioning, OLAP, Data Mining and Real Application Testing options
|
||||
SQL>
|
||||
|
||||
完成!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/drop-database-oracle-11-without-using-dcba/
|
||||
|
||||
作者:[M.el Khamlichi][a]
|
||||
译者:[VicYu/Vic020](http://vicyu.net/)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.unixmen.com/author/pirat9/
|
||||
@ -0,0 +1,89 @@
|
||||
如何从终端以后台模式运行Linux程序
|
||||
===
|
||||
|
||||

|
||||
|
||||
Linux终端窗口。
|
||||
|
||||
这是一个简短但是非常有用的教程:它向你展示从终端运行Linux应用程序的同时,如何保证终端仍然在控制之中。
|
||||
|
||||
在Linux中有许多方式可以打开一个终端,这主要取决于你分类的选择和桌面环境。
|
||||
|
||||
使用Ubuntu,你可以使用CTRL + ALT + T组合键打开一个终端。你也可以点击超级键(Windows键)打开一个终端窗口。在键盘上,[打开Ubuntu Dash][1],然后搜索"TERM"。点击"Term"图标将会打开一个终端窗口。
|
||||
|
||||
其他诸如XFCE, KDE, LXDE, Cinnamon和MATE的桌面环境,你将会在菜单中发现终端。还有一些分类会把终端图标放在入口处,或者在面板上放置终端启动器。
|
||||
|
||||
你可以在终端输入一个程序的名字来启动一个应用。举例,你可以通过输入"firefox"启动火狐浏览器。
|
||||
|
||||
从终端运行程序的好处是一可以包含额外的选项。
|
||||
|
||||
举个例子,如果你输入下面的命令,一个新的火狐浏览器将会打开,而且默认的搜索引擎将会搜索引用之间的术语:
|
||||
|
||||
firefox -search "Linux.About.Com"
|
||||
|
||||
你会发现,如果你运行火狐浏览器,应用程序将被打开,并且控制将会回到终端,这将意味着你可以继续在终端工作。
|
||||
|
||||
通常情况下,如果你通过终端运行一个程序,程序将被打开,并且直到那个程序关闭结束,你将不会重新获得终端的控制权。这是因为你是在前台打开程序的。
|
||||
|
||||
想要从终端运行一个程序,并且立即将终端的控制权返回给你,你需要以后台进程的方式打开程序。
|
||||
|
||||
为了以后台进程的方式打开一个程序,只需要添加符号(&)到命令中,如下面所示:
|
||||
|
||||
libreoffice &
|
||||
|
||||
在终端中仅仅提供程序的名字,应用程序可能运行不了。如果程序不存在于一个设置了路径变量的文件夹中,你需要指定完成的路径名来运行程序。
|
||||
|
||||
/path/to/yourprogram &
|
||||
|
||||
如果你并不确定一个程序是否存在于Linux文件结构,使用find或者locate命令来查询应用程序。
|
||||
|
||||
找一个文件的语法如下:
|
||||
|
||||
find /path/to/start/from -name programname
|
||||
|
||||
举个例子,可以使用下面的命令寻找Firefox的位置:
|
||||
|
||||
find / -name firefox
|
||||
|
||||
输出会很快掠过,所以你可以以管道的方式控制输出的多少:
|
||||
|
||||
find / -name firefox | more
|
||||
|
||||
find / -name firefox | less
|
||||
|
||||
find命令将会返回因权限拒绝而发生错误的文件夹数量,这些文件夹你没有权限去搜索。
|
||||
|
||||
你可以使用sudo命令提升你的权限。如果sudo没有安装,你需要切换到拥有权限的用户:
|
||||
|
||||
sudo find / -name firefox | more
|
||||
|
||||
如果你知道你想寻找的文件在你的当前文件夹结构中,你可以一个点代替先前的斜线,如下:
|
||||
|
||||
sudo find . -name firefox | more
|
||||
|
||||
你可能不需要sudo来提升权限。如果你在home文件夹结构中寻找文件,sudo就不需要。
|
||||
|
||||
一些应用程序需要提升用户权限来运行,你可能得到一个缺少权限的错误,除非你使用一个具有足够权限的用户,或者使用sudo提升你的权限。
|
||||
|
||||
下面是一个小花招。如果你运行一个程序,而且它需要提升权限来运行,输入下面命令:
|
||||
|
||||
sudo !!
|
||||
|
||||
---
|
||||
|
||||
via: http://linux.about.com/od/commands/fl/How-To-Run-Linux-Programs-From-T
|
||||
he-Terminal-In-Background-Mode.htm
|
||||
|
||||
作者:[Gary Newell][a]
|
||||
译者:[su-kaiyao](https://github.com/su-kaiyao)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中>
|
||||
国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://linux.about.com/bio/Gary-Newell-132058.htm
|
||||
[1]:http://linux.about.com/od/howtos/fl/Learn-Ubuntu-The-Unity-Dash.htm
|
||||
[2]:http://linux.about.com/od/commands/l/blcmdl1_locate.htm
|
||||
[3]:http://linux.about.com/library/cmd/blcmdl1_less.htm
|
||||
[4]:http://linux.about.com/library/cmd/blcmdl1_more.htm
|
||||
[5]:http://linux.about.com/od/commands/l/blcmdl8_sudo.htm
|
||||
@ -0,0 +1,63 @@
|
||||
Ubuntu中跟踪多个时区的简捷方法
|
||||
================================================================================
|
||||

|
||||
|
||||
**我是否要确保在我醒来时或者安排与*山姆陈*,Ohso的半个开发商,进行Skype通话时,澳大利亚一个关于Chromebook销售的推特已经售罄,我大脑同时在多个时区下工作。**
|
||||
|
||||
那里头有个问题,如果你认识我,你会知道我的脑容量也就那么丁点,跟金鱼差不多,里头却塞着像Windows Vista这样一个臃肿货(也就是,不是很好)。我几乎记不得昨天之前的事情,更记不得我的门和金门大桥脚之间的时间差!
|
||||
|
||||
作为臂助,我使用一些小部件和菜单项来让我保持同步。在我常规工作日的空间里,我在多个操作系统间游弋,涵盖移动系统和桌面系统,但只有一个让我最快速便捷地设置“世界时钟”。
|
||||
|
||||
**而它刚好是那个名字放在门上方的东西。**
|
||||
|
||||

|
||||
|
||||
### 添加世界时钟到Ubuntu日期/时间小应用 ###
|
||||
|
||||
Unity中默认的日期-时间指示器提供了添加并查看多个时区的支持,不需要附加组件,不需要额外的包。
|
||||
|
||||
1. 点击时钟小应用,然后uxuanze‘**时间和日期设置**’条目
|
||||
1. 在‘**时钟**’标签中,选中‘**其它位置的时间**’选框
|
||||
1. 点击‘**选择位置**’按钮
|
||||
1. 点击‘**+**’,然后输入位置名称那个
|
||||
|
||||
#### 其它桌面环境 ####
|
||||
|
||||
**KDE Plasma**中默认的时钟小应用有类似的功能,其它功能如下:
|
||||
|
||||
1. 在数字时钟小部件上右击,然后选择‘**数字时钟设置**’
|
||||
1. 点击‘**时区**’项
|
||||
1. 在搜索区输入城市名
|
||||
1. 点击‘**确定**’
|
||||
|
||||
**GNOME Shell**的可扩展特性可以看到有许多世界时钟选项可用,可以用它的默认时间表填补左边的空白,我个人喜欢‘[多个时钟][1]’。对于**Cinnamon**桌面而言也是一样的,它的‘面板小部件’仓库有丰富的可选部件,如超级顺滑的“**世界时钟日历**”。
|
||||
|
||||

|
||||
|
||||
Cinnamon 2.4中的世界时钟日历
|
||||
|
||||
**XFCE**和**LXDE**就不那么慷慨了,除了自带的“工作区”作为**多个时钟**添加到面板外,每个都需要手动配置以指定位置。两个都支持‘指示器小部件’,所以,如果你没有依赖于Unity,你可以安装/添加单独的日期/时间指示器。
|
||||
|
||||
**Budgie**还刚初出茅庐,不足以胜任角落里的需求,因为Pantheon我还没试过——希望你们通过评论来让我知道得更多。
|
||||
|
||||
#### Desktop Apps, Widgets & Conky Themes桌面应用、不见和Conky主题 ####
|
||||
|
||||
当然,面板小部件只是收纳其它国家多个时区的一种方式。如果你不满意通过面板去访问,那里还有各种各样的**桌面应用**可供使用,其中许多都可以跨版本,甚至跨平台使用。
|
||||
|
||||
**GNOME时钟**就是这样一个应用,在Ubuntu 14.04 LTS及其后续版本中,你可以通过Ubuntu软件中心直接安装。**Conky**是一个很有潜力的备选(尽管我还没发现有哪个预制主题为此目的设计),而其它像[日历时钟][2]这样轻量级的Chrome应用可以在任何安装有Chrome这个免费浏览器的地方工作。
|
||||
|
||||
**你也关注时区吗?如果是,你使用什么应用、采用什么方法或者小部件让它显示在顶层呢?**
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2014/12/add-time-zones-world-clock-ubuntu
|
||||
|
||||
作者:[Joey-Elijah Sneddon][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://plus.google.com/117485690627814051450/?rel=author
|
||||
[1]:https://extensions.gnome.org/extension/605/multiclock/
|
||||
[2]:http://www.omgchrome.com/calendar-clock-chrome-app/
|
||||
@ -0,0 +1,147 @@
|
||||
10个检测Linux内存使用情况的‘free’命令
|
||||
===
|
||||
|
||||
**Linux**是最有名的开源操作系统之一,它拥有着极其巨大的指令集。确定**物理内存**和**交换内存**所有可用空间的最重要,也是唯一的方法是使用“**free**”命令。
|
||||
|
||||
Linux “**free**”命令通过给出**Linux/Unix**操作系统中内核已使用的**buffers**情况,来提供**物理内存**和**交换内存**的总使用量和可用量。
|
||||
|
||||

|
||||
|
||||
这篇文章提供一些带有参数选项的“**free**”命令,这些命令对于你更好地利用你的内存会有帮助。
|
||||
|
||||
### 1. 显示你的系统内存 ###
|
||||
|
||||
free命令用于检测**物理内存**和**交换内存**已使用量和可用量(单位为**KB**)。下面演示命令的使用情况。
|
||||
|
||||
# free
|
||||
|
||||
total used free shared buffers cach
|
||||
ed
|
||||
Mem: 1021628 912548 109080 0 120368 6555
|
||||
48
|
||||
-/+ buffers/cache: 136632 884996
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 2. 以字节为单位显示内存 ###
|
||||
|
||||
加上**-b**参数的free命令,以**字节**为单位显示内存的大小。
|
||||
|
||||
# free -b
|
||||
|
||||
total used free shared buffers cach
|
||||
ed
|
||||
Mem: 1046147072 934420480 111726592 0 123256832 6712811
|
||||
52
|
||||
-/+ buffers/cache: 139882496 906264576
|
||||
Swap: 4294959104 0 4294959104
|
||||
|
||||
### 3. 以千字节为单位显示内存 ###
|
||||
|
||||
加上**-k**参数的free命令,以(KB)**千字节**为单位显示内存大小。
|
||||
|
||||
# free -k
|
||||
|
||||
total used free shared buffers cach
|
||||
ed
|
||||
Mem: 1021628 912520 109108 0 120368 655548
|
||||
-/+ buffers/cache: 136604 885024
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 4. 以兆字节为单位显示内存 ###
|
||||
|
||||
想以**(兆字节)**显示内存大小,使用**-m**参数。
|
||||
|
||||
# free -m
|
||||
|
||||
total used free shared buffers cach
|
||||
ed
|
||||
Mem: 997 891 106 0 117 6
|
||||
40
|
||||
-/+ buffers/cache: 133 864
|
||||
Swap: 4095 0 4095
|
||||
|
||||
### 5. 以千兆字节为单位显示内存 ###
|
||||
|
||||
使用**-g**为参数,将会以**GB(千兆字节)**为单位显示内存大小。
|
||||
|
||||
# free -g
|
||||
total used free shared buffers cached
|
||||
Mem: 0 0 0 0 0
|
||||
0
|
||||
-/+ buffers/cache: 0 0
|
||||
Swap: 3 0 3
|
||||
|
||||
### 6. 显示总计行 ###
|
||||
|
||||
加上-t选项,将会在屏幕最后列出总计一行。
|
||||
|
||||
# free -t
|
||||
|
||||
total used free shared buffers cache
|
||||
d
|
||||
Mem: 1021628 912520 109108 0 120368 6555
|
||||
48
|
||||
-/+ buffers/cache: 136604 885024
|
||||
Swap: 4194296 0 4194296
|
||||
Total: 5215924 912520 4303404
|
||||
|
||||
### 7. 关闭显示缓冲区调整一行 ###
|
||||
|
||||
默认情况下,free命令是显示“**缓冲区调整**”一行的,为了关闭显示,可以加上-o参数。
|
||||
|
||||
# free -o
|
||||
|
||||
total used free shared buffers cache
|
||||
d
|
||||
Mem: 1021628 912520 109108 0 120368 6555
|
||||
48
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 8. 定期时间间隔更新内存状态 ###
|
||||
|
||||
-s选项加上一个整数,用来在定期时间间隔内更新free命令。举个例子,下面的命令将会在每5秒更新一个free命令。
|
||||
|
||||
# free -s 5
|
||||
|
||||
total used free shared buffers cach
|
||||
ed
|
||||
Mem: 1021628 912368 109260 0 120368 6555
|
||||
48
|
||||
-/+ buffers/cache: 136452 885176
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 9. 显示底和高内存统计信息 ###
|
||||
|
||||
-l选项显示了具体的高和低内存的使用统计情况。
|
||||
|
||||
# free -l
|
||||
|
||||
total used free shared buffers cach
|
||||
ed
|
||||
Mem: 1021628 912368 109260 0 120368 6555
|
||||
48
|
||||
Low: 890036 789064 100972
|
||||
High: 131592 123304 8288
|
||||
-/+ buffers/cache: 136452 885176
|
||||
Swap: 4194296 0 4194296
|
||||
|
||||
### 10. 检查free命令版本 ###
|
||||
|
||||
-V选项,显示free命令版本信息。
|
||||
|
||||
# free -V
|
||||
|
||||
procps version 3.2.8
|
||||
|
||||
---
|
||||
|
||||
via: http://www.tecmint.com/check-memory-usage-in-linux/
|
||||
|
||||
作者:[Ravi Saive][a]
|
||||
译者:[su-kaiyao](https://github.com/su-kaiyao)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中>
|
||||
国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.tecmint.com/author/admin/
|
||||
@ -0,0 +1,100 @@
|
||||
在Ubuntu上找出可用的网络适配器
|
||||
================================================================================
|
||||
想知道**在Linux中你正在使用的网卡是什么吗?** 在Linux中很容易就找出网卡的生产商。打开一个终端并输入下面的额命令:
|
||||
|
||||
sudo lshw -C network
|
||||
|
||||
如果上面的命令不能在sudo下使用,那就移除sudo。它的输出看上去有点奇怪但是很有用。
|
||||
|
||||

|
||||
|
||||
> *-network
|
||||
>
|
||||
> description: Wireless interface
|
||||
>
|
||||
> product: BCM4360 802.11ac Wireless Network Adapter
|
||||
>
|
||||
> vendor: Broadcom Corporation
|
||||
>
|
||||
> physical id: 0
|
||||
>
|
||||
> bus info: pci@0000:03:00.0
|
||||
>
|
||||
> logical name: wlan0
|
||||
>
|
||||
> version: 03
|
||||
>
|
||||
> serial: 9c:f3:87:c1:5d:6a
|
||||
>
|
||||
> width: 64 bits
|
||||
>
|
||||
> clock: 33MHz
|
||||
>
|
||||
> capabilities: bus_master cap_list ethernet physical wireless
|
||||
>
|
||||
> configuration: broadcast=yes driver=wl0 driverversion=6.30.223.248 (r487574) ip=192.168.1.23 latency=0 multicast=yes wireless=IEEE 802.11abg
|
||||
>
|
||||
> resources: irq:18 memory:b0600000-b0607fff memory:b0400000-b05fffff
|
||||
|
||||
如你所见,我Macbook Air上的无线网卡是BCM4360,这是一款在Ubuntu下面经常无法检测无线网络的很容易出问题的网卡。
|
||||
|
||||
[lshw][1] 命令实际上死用来列出硬件的,因此命令的名字是lshw。带上网络的选项后,就会只过滤出网络硬件了。
|
||||
|
||||
### 了解网卡的其他方法 ###
|
||||
|
||||
另外你还可以使用lspci命令来显示PCI总线上的信息。你不应该用特权模式来运行这个命令。只需要在命令行下输入:
|
||||
|
||||
lspci
|
||||
|
||||
命令的输出看上去想这样:
|
||||
|
||||

|
||||
|
||||
> 00:00.0 Host bridge: Intel Corporation Haswell-ULT DRAM Controller (rev 09)
|
||||
>
|
||||
> 00:02.0 VGA compatible controller: Intel Corporation Haswell-ULT Integrated Graphics Controller (rev 09)
|
||||
>
|
||||
> 00:03.0 Audio device: Intel Corporation Haswell-ULT HD Audio Controller (rev 09)
|
||||
>
|
||||
> 00:14.0 USB controller: Intel Corporation 8 Series USB xHCI HC (rev 04)
|
||||
>
|
||||
> 00:16.0 Communication controller: Intel Corporation 8 Series HECI #0 (rev 04)
|
||||
>
|
||||
> 00:1b.0 Audio device: Intel Corporation 8 Series HD Audio Controller (rev 04)
|
||||
>
|
||||
> 00:1c.0 PCI bridge: Intel Corporation 8 Series PCI Express Root Port 1 (rev e4)
|
||||
>
|
||||
> 00:1c.1 PCI bridge: Intel Corporation 8 Series PCI Express Root Port 2 (rev e4)
|
||||
>
|
||||
> 00:1c.2 PCI bridge: Intel Corporation 8 Series PCI Express Root Port 3 (rev e4)
|
||||
>
|
||||
> 00:1c.4 PCI bridge: Intel Corporation 8 Series PCI Express Root Port 5 (rev e4)
|
||||
>
|
||||
> 00:1c.5 PCI bridge: Intel Corporation 8 Series PCI Express Root Port 6 (rev e4)
|
||||
>
|
||||
> 00:1f.0 ISA bridge: Intel Corporation 8 Series LPC Controller (rev 04)
|
||||
>
|
||||
> 00:1f.3 SMBus: Intel Corporation 8 Series SMBus Controller (rev 04)
|
||||
>
|
||||
> 02:00.0 Multimedia controller: Broadcom Corporation Device 1570
|
||||
>
|
||||
> 03:00.0 Network controller: Broadcom Corporation BCM4360 802.11ac Wireless Network Adapter (rev 03)
|
||||
>
|
||||
> 04:00.0 SATA controller: Marvell Technology Group Ltd. 88SS9183 PCIe SSD Controller (rev 14)
|
||||
|
||||
这些命令会同时列出有线和无线的网卡。你应该注意到上面的输出中显示我的系统中没有有线网卡。因为我使用的是Macbook Air,他没有以太网端口
|
||||
|
||||
我希望这边文章可以帮助你找到你系统中的网卡。欢迎提出问题和建议。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://itsfoss.com/find-network-adapter-ubuntu-linux/
|
||||
|
||||
作者:[Abhishek][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://itsfoss.com/author/Abhishek/
|
||||
[1]:http://linux.die.net/man/1/lshw
|
||||
@ -0,0 +1,155 @@
|
||||
VPS上好的控制面板是什么
|
||||
================================================================================
|
||||
任何有经验的Linux人员都认为没有一款控制面板可以打败纯命令行界面来管理[虚拟主机][1](VPS)。也有人争论有一款好的面板的一席之地,因为流线型的界面让常规管理操作可以通过点几下鼠标就可以完成。
|
||||
|
||||
至于控制面板,有共恩那个强大的充满警铃和汽笛的商业控制面板,也有不同免费的但也强大多功能的免费开源面板替代。这之中杰出的代表是[Ajenti][2]控制面板。
|
||||
|
||||
Ajenti可以让你很简单地配置不同的通用服务程序,如Apache/nginx、Samba、BIND、Squid、MySQL、cron、防火墙等等,对管理通用VPS实例可以节省大量的时间。对于生产环境,Ajenti同样提供了插件和平台来支持虚拟web主机管理和自定义web UI开发。
|
||||
|
||||
Ajenti有[双重授权][3];一个是个人、企业内部或者教育用途免费使用的AGPLv3。然而,如果你是一家托管企业或者硬件提供商,那么你需要购买商业授权来使用Ajenti作为商业供应。
|
||||
|
||||
### 在Linux上安装Ajenti ###
|
||||
|
||||
为了简化安装,Ajenti为主流Linux发行版提供了自己的仓库。安装Ajenti要做的就是配置目标仓库,并用默认包管理器来安装。
|
||||
|
||||
安装前,一个RSA密钥和证书会生成用于SSL,Ajenti会见在8000端口监听HTTPS的web请求。如果你正在使用防火墙,你需要在防火墙中允许8000端口。为了安全,最好默认禁止8000端口的访问,并添加少数IP地址到白名单中。
|
||||
|
||||
#### 在Debian上安装Ajenti ####
|
||||
|
||||
$ wget http://repo.ajenti.org/debian/key -O- | sudo apt-key add -
|
||||
$ sudo sh -c 'echo "deb http://repo.ajenti.org/debian main main debian" >> /etc/apt/sources.list'
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install ajenti
|
||||
|
||||
#### 在Ubuntu上安装Ajenti ####
|
||||
|
||||
$ wget http://repo.ajenti.org/debian/key -O- | sudo apt-key add -
|
||||
$ sudo sh -c 'echo "deb http://repo.ajenti.org/ng/debian main main ubuntu" >> /etc/apt/sources.list'
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install ajenti
|
||||
|
||||
#### 在 CentOS/RHEL或者Fedora上安装Ajenti ####
|
||||
|
||||
在CentOS/RHEL上,首先[配置][4]EPEL仓库,接着运行下面的命令。在Fedora上,直接使用下面的命令。
|
||||
|
||||
$ wget http://repo.ajenti.org/ajenti-repo-1.0-1.noarch.rpm
|
||||
$ sudo rpm -ivh ajenti-repo-1.0-1.noarch.rpm
|
||||
$ sudo yum install ajenti
|
||||
|
||||
接着配置防火墙。
|
||||
|
||||
在Fedora或者CentOS/RHEL 7上:
|
||||
|
||||
$ sudo firewall-cmd --zone=public --add-port=8000/tcp --permanent
|
||||
$ sudo firewall-cmd --reload
|
||||
|
||||
在CentOS/RHEL 6上:
|
||||
|
||||
$ sudo iptables -I INPUT -p tcp -m tcp --dport 8000 -j ACCEPT
|
||||
$ sudo service iptables save
|
||||
|
||||
### 访问Ajenti web界面 ###
|
||||
|
||||
在访问Ajenti的web界面前,先确保启动了ajenti服务。
|
||||
|
||||
$ sudo service ajenti restart
|
||||
|
||||
直接在浏览器中输入https://<server-ip-address>:8000,你就会看到下面的Ajenti的登录界面。
|
||||
|
||||

|
||||
|
||||
默认的登录凭证是用户名“root”,密码“admin”。当你登录后,你会看到初始化的Ajenti菜单。
|
||||
|
||||
|
||||
|
||||
在左边面板的"SOFTWARE"选项下,你会看接一列安装的服务。当你安装了任何Ajenti支持的服务端程序时,软件会在重启ajenti服务后被自动加入列表。
|
||||
|
||||
$ sudo service ajenti restart
|
||||
|
||||
### 通过Ajenti web界面管理VPS ###
|
||||
|
||||
Ajenti的web界面非常直观且易使用。下面是Ajenti功能的几个例子。
|
||||
|
||||
#### 可插入结构 ####
|
||||
|
||||
Ajenti有许多特定应用的插件,这让AJenti可高度扩展化。当你在VPS上安装一款新软件时。相关的AJenti插件(如果有的话)会自动启用来管理软件。“Plugins”菜单会展示可用/启用的插件,以及和它们关联的软件。
|
||||
|
||||
|
||||
|
||||
#### 包管理 ####
|
||||
|
||||
Ajenti提供了一个web界面来安装和升级VPS上的包。
|
||||
|
||||
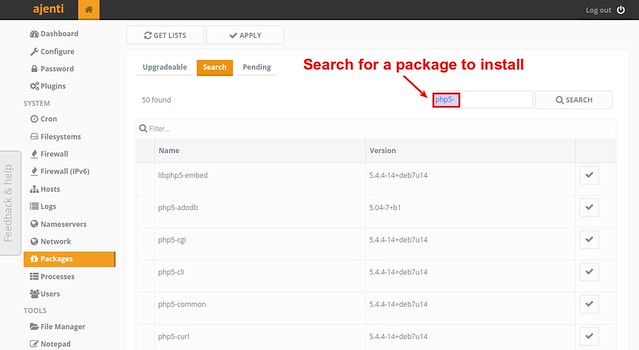
|
||||
|
||||
#### 防火墙配置 ####
|
||||
|
||||
Ajenti允许你用两种方法管理防火墙规则(iptables或者CSF)。一种是使用用户友好的web面板,另一种是直接编辑原生的防火墙规则。
|
||||
|
||||
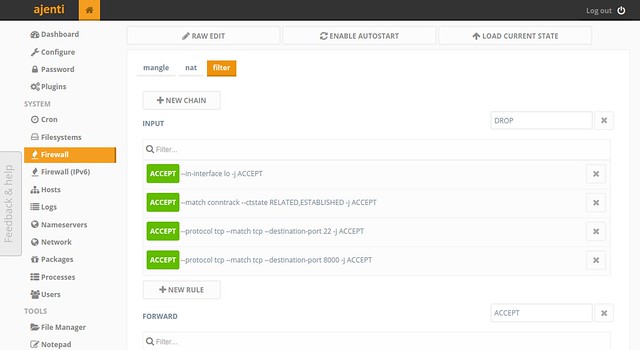
|
||||
|
||||
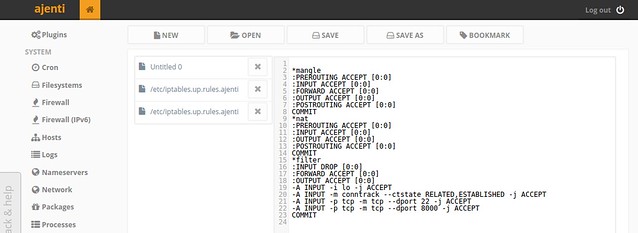
|
||||
|
||||
#### 日志检查 ####
|
||||
|
||||
你可以在Ajenti的web界面中浏览位于/var/log下的系统日志。
|
||||
|
||||
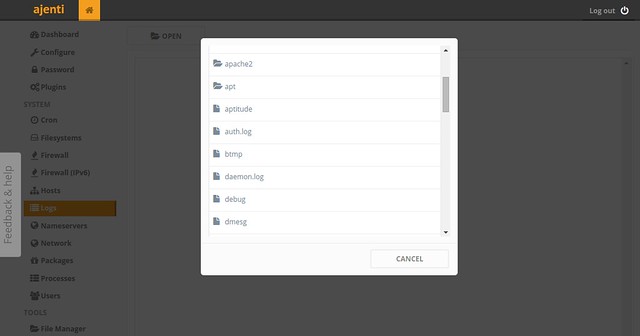
|
||||
|
||||
#### 进程监控 ####
|
||||
|
||||
你可以u看见按照CPU和内存使用率排序的进程列表,按需可以结束它们。
|
||||
|
||||
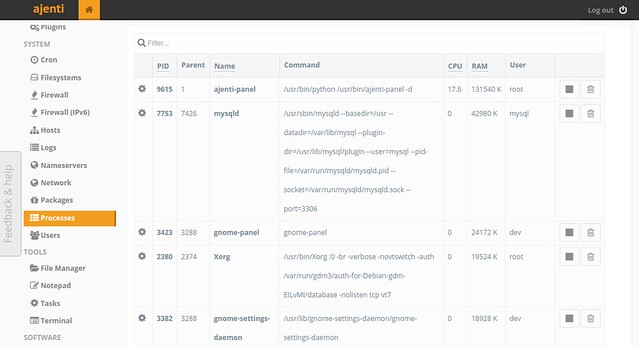
|
||||
|
||||
#### 终端访问 ####
|
||||
|
||||
对于底层VPS访问,Ajenti提供了基于web的终端界面,你在这可以输入Linux命令。你也可以像下面那样在一个面板中打开多个终端。
|
||||
|
||||
|
||||
|
||||
#### Apache Web服务管理 ####
|
||||
|
||||
你可以编辑Apache配额文件,并管理apche2服务。
|
||||
|
||||
|
||||
|
||||
#### MySQL/MariaDB 管理 ####
|
||||
|
||||
你可以访问MySQL/MariaDB服务并直接在上面执行原生SQL命令。
|
||||
|
||||
|
||||
|
||||
#### Squid 配置 ####
|
||||
|
||||
你可以配置Squid代理服务器的ACL、HTTP访问规则,过滤端口。
|
||||
|
||||
|
||||
|
||||
#### 启动服务管理 ####
|
||||
|
||||
你可以浏览、启动、停止、重启安装的服务。
|
||||
|
||||
|
||||
|
||||
### 总结 ###
|
||||
|
||||
Ajenti是一款易于使用的服务器管理控制面板,可以加入你开发的[自定义插件][5]。然而,记住任何好的控制面板都不会排除你学习面板后[VPS][6]上发生的情况的需求。一款面板会在你完全了解你正在做的事情的时候成会一款真正节省时间的利器,并且不依赖于控制面版来处理你行动的结果。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/free-control-panel-for-vps.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/go/digitalocean
|
||||
[2]:http://ajenti.org/
|
||||
[3]:http://ajenti.org/licensing
|
||||
[4]:http://xmodulo.com/how-to-set-up-epel-repository-on-centos.html
|
||||
[5]:http://docs.ajenti.org/en/latest/dev/intro.html
|
||||
[6]:http://xmodulo.com/go/digitalocean
|
||||
@ -0,0 +1,104 @@
|
||||
Ubuntu 14.10 Server上安装Jetty 9(Java服务引擎和Web服务器)
|
||||
================================================================================
|
||||
Jetty提供了一个Web服务器和javax.servlet容器,为SPDY、WebSocket、OSGi、JMX、JNDI、JAAS以及许多其它集成套件添加了支持。这些组件都是开源的,也可用于商业用途和分发。
|
||||
|
||||
Jetty被广泛用于多种项目和产品,都可以在开发环境和生产环境中使用。Jetty可以很容易地嵌入到设备、工具、框架、应用服务器以及集群中。更多用途可参见Jetty网页。
|
||||
|
||||
### Jetty特性 ###
|
||||
|
||||
- 全功能并基于标准
|
||||
- 开源与商用两可
|
||||
- 灵活和可扩展
|
||||
- 小足迹
|
||||
- 可嵌入
|
||||
- 异步
|
||||
- 企业弹性扩展
|
||||
- Apache和Eclipse双重许可
|
||||
|
||||
### ubuntu 14.10 server上安装Jetty 9 ###
|
||||
|
||||
#### 先决条件 ####
|
||||
|
||||
在安装Jetty服务器前,您需要通过以下命令安装Java
|
||||
|
||||
sudo apt-get install openjdk-8-jdk
|
||||
|
||||
Java将会安装到/usr/lib/jvm/java-8-openjdk-i386,同时在该目录下会创建一个名为java-8-openjdk-i386的符号链接,在/usr/bin/java下也会相应创建符号链接。
|
||||
|
||||
现在你需要从[这里][1]下载Jetty9,在下载完成后,你需要使用以下命令来解压缩
|
||||
|
||||
$tar -xvf jetty-distribution-9.2.5.v20141112.tar.gz
|
||||
|
||||
该操作会将它解压到jetty-distribution-9.2.5.v20141112,而你需要使用以下命令将归档文件移动到/opt/jetty
|
||||
|
||||
$mv jetty-distribution-9.2.5.v20141112 /opt/jetty
|
||||
|
||||
你需要创建jetty用户,并将其设置成/opt/jetty目录的属主
|
||||
|
||||
sudo useradd jetty -U -s /bin/false
|
||||
|
||||
sudo chown -R jetty:jetty /opt/jetty
|
||||
|
||||
|
||||
使用以下命令拷贝Jetty脚本到启动目录,以便让它作为一个服务来运行
|
||||
|
||||
$ cp /opt/jetty/bin/jetty.sh /etc/init.d/jetty
|
||||
|
||||
现在,你需要使用以下内容来创建Jetty设置文件
|
||||
|
||||
sudo vi /etc/default/jetty
|
||||
|
||||
添加以下行
|
||||
|
||||
JAVA_HOME=/usr/bin/java
|
||||
JETTY_HOME=/opt/jetty
|
||||
NO_START=0
|
||||
JETTY_ARGS=jetty.port=8085
|
||||
JETTY_HOST=0.0.0.0
|
||||
JETTY_USER=jetty
|
||||
|
||||
保存并退出该文件
|
||||
|
||||
你需要使用以下命令来启动Jetty服务
|
||||
|
||||
sudo service jetty start
|
||||
|
||||
你应该看到和下面类似的输出
|
||||
|
||||
Starting Jetty: OK Mon Nov 24 11:55:48 GMT 2014
|
||||
|
||||
如果你看到了下面的错误
|
||||
|
||||
#### ** ERROR: JETTY_HOME not set, you need to set it or install in a standard location ####
|
||||
|
||||
你需要确保在/etc/default/jetty文件中设置了正确的Jetty家目录路径,
|
||||
你可以使用以下URL来测试jetty
|
||||
|
||||
Jetty现在应该运行在8085端口,打开浏览器并访问http://serverip:8085,你应该可以看到Jetty屏幕。
|
||||
|
||||
#### Jetty服务检查 ####
|
||||
|
||||
使用以下命令来验证并检查配置
|
||||
|
||||
sudo service jetty check
|
||||
|
||||
使用以下命令来让Jetty开重启后自动启动
|
||||
|
||||
sudo update-rc.d jetty defaults
|
||||
|
||||
重启服务器并测试Jetty是否自动启动。
|
||||
|
||||
要检查Jetty运行在哪个端口上,或者该端口是否与其它程序冲突,可以运行netstat -tln
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.ubuntugeek.com/install-jetty-9-java-servlet-engine-and-webserver-on-ubuntu-14-10-server.html
|
||||
|
||||
作者:[ruchi][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://www.ubuntugeek.com/author/ubuntufix
|
||||
[1]:http://download.eclipse.org/jetty/stable-9/dist/
|
||||
@ -0,0 +1,46 @@
|
||||
Linux FAQs with Answers--How to disable Apport internal error reporting on Ubuntu
|
||||
有问必答--如何禁止Ubuntu的Apport内部错误报告程序
|
||||
================================================================================
|
||||
> **问题**:在桌面版Ubuntu中,我经常遇到一些弹窗窗口,警告我Ubuntu发生了内部错误,问我要不要发送错误报告。每次软件崩溃都要烦扰我,我如何才能关掉这个错误报告功能呢?
|
||||
|
||||
Ubuntu桌面版预安装了Apport,它是一个错误收集系统,会收集软件崩溃、未处理异常和其他,包括程序bug,并为调试目的生成崩溃报告。当一个应用程序崩溃或者出现Bug时候,Apport就会通过弹窗警告用户并且询问用户是否提交崩溃报告。你也许也看到过下面的消息。
|
||||
|
||||
- "Sorry, the application XXXX has closed unexpectedly."
|
||||
- "对不起,应用程序XXXX意外关闭了"
|
||||
- "Sorry, Ubuntu XX.XX has experienced an internal error."
|
||||
- "对不起,Ubuntu XX.XX 经历了一个内部错误"
|
||||
- "System program problem detected."
|
||||
- "系统程序问题发现"
|
||||
|
||||
|
||||
|
||||
也许因为应用一直崩溃,频繁的错误报告会使人心烦。也许你担心Apport会收集和上传你的Ubuntu系统的敏感信息。无论什么原因,你需要关掉Apport的错误报告功能。
|
||||
|
||||
### 临时关闭Apport错误报告 ###
|
||||
|
||||
如果你想要临时关闭Apport,使用下列命令
|
||||
|
||||
$ sudo service apport stop
|
||||
|
||||
注意重启Ubuntu系统Apport会继续开启
|
||||
|
||||
### 永久关闭Apport错误报告 ###
|
||||
|
||||
为了永久关闭Apport,编辑/etc/default/apport,修改下列参数
|
||||
|
||||
enabled=0
|
||||
|
||||
重启你的Ubuntu系统,Apport将会自动关闭
|
||||
|
||||
如果你再也不会用Apport,有一种简单的方法完全移除它
|
||||
|
||||
$ sudo apt-get purge apport
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://ask.xmodulo.com/disable-apport-internal-error-reporting-ubuntu.html
|
||||
|
||||
译者:[VicYu/Vic020](http://www.vicyu.net/)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,103 @@
|
||||
CentOS上配置rsyslog客户端用以远程记录日志
|
||||
================================================================================
|
||||
**rsyslog**是一个开源工具,被广泛用于Linux系统以通过TCP/UDP协议转发或接收日志消息。rsyslog守护进程可以被配置称两种环境,一种是配置成日志收集服务器,rsyslog进程可以从网络中收集所有其它主机上的日志数据,这些主机已经将日志配置为发送到服务器。rsyslog的另外一个角色,就是可以配置为客户端,用来过滤和发送内部日志消息到本地文件夹(如/var/log)或一台可以路由到的远程rsyslog服务器上。
|
||||
|
||||
假定你的网络中已经有一台rsyslog服务器[已经起来并且处于运行中][1],本指南将为你展示如何来设置CentOS系统将其内部日志消息路由到一台远程rsyslog服务器上。这将大大改善你的系统磁盘空间的使用,尤其是你还没有一个独立的用于/var目录的大分区。
|
||||
|
||||
### 步骤一: 安装Rsyslog守护进程 ###
|
||||
|
||||
在CentOS 6和7上,rsyslog守护进程已经预先安装了。要验证rsyslog是否已经安装到你的CentOS系统上,请执行如下命令:
|
||||
|
||||
# rpm -qa | grep rsyslog
|
||||
# rsyslogd -v
|
||||
|
||||

|
||||
|
||||
如果处于某种原因,rsyslog守护进程没有出现在你的系统中,请使用以下命令来安装:
|
||||
|
||||
# yum install rsyslog
|
||||
|
||||
### 步骤二: 配置Rsyslog守护进程为客户端 ###
|
||||
|
||||
接下来的步骤,是要将你的CentOS机器转变成rsyslog客户端,将其所有内部日志消息发送到远程中央日志服务器上。
|
||||
|
||||
要实现该功能,请使用你喜爱的文本编辑器打开位于/etc路径下的rsyslog主配置文件:
|
||||
|
||||
# nano /etc/rsyslog.conf
|
||||
|
||||
开启文件用于编辑后,你需要添加以下声明到文件底部。将IP地址替换为你的远程rsyslog服务器的IP地址。
|
||||
|
||||
*.* @192.168.1.25:514
|
||||
|
||||
上面的声明告诉rsyslog守护进程,将系统上各个设备的各种日志消息路由到远程rsyslog服务器(192.168.1.25)的UDP端口514。
|
||||
|
||||
如果出于某种原因,你需要更为可靠的协议,如TCP,而rsyslog服务器也被配置为监听TCP连接,你必须在远程主机的IP地址前添加一个额外的@字符,像下面这样:
|
||||
|
||||
*.* @@192.168.1.25:514
|
||||
|
||||
注意,你也可以将rsyslog服务器的IP地址替换成它的DNS名称(FQDN)。
|
||||
|
||||
如果你只想要转发指定设备的日志消息,比如说内核设备,那么你可以在rsyslog配置文件中使用以下声明。
|
||||
|
||||
kern.* @192.168.1.25:514
|
||||
|
||||
修改配置文件后,你需要重启进程以激活修改:
|
||||
|
||||
**CentOS 7:**
|
||||
|
||||
# systemctl restart rsyslog.service
|
||||
|
||||
**CentOS 6:**
|
||||
|
||||
# service rsyslog restart
|
||||
|
||||
在另外一种环境中,让我们假定你已经在机器上安装了一个名为“foobar”的应用程序,它会在/var/log下生成foobar.log日志文件。现在,你只想要将它的日志定向到rsyslog服务器,这可以通过像下面这样在rsyslog配置文件中加载imfile模块来实现。
|
||||
|
||||
首先,加载imfile模块,这必须只做一次。
|
||||
|
||||
module(load="imfile" PollingInterval="5")
|
||||
|
||||
然后,指定日志文件的路径以便imfile模块可以检测到:
|
||||
|
||||
input(type="imfile"
|
||||
File="/var/log/foobar.log"
|
||||
Tag="foobar"
|
||||
Severity="error"
|
||||
Facility="local7")
|
||||
|
||||
最后,定向local7设备到远程rsyslog服务器:
|
||||
|
||||
local7.* @192.168.1.25:514
|
||||
|
||||
别忘了重启rsyslog进程哦!
|
||||
|
||||
### 步骤三: 让Rsyslog进程自动启动 ###
|
||||
|
||||
To automatically start rsyslog client after every system reboot, run the following command to enable it system-wide:
|
||||
要让rsyslog客户端在每次系统重启后自动启动,请运行以下命令来在系统范围启用:
|
||||
|
||||
**CentOS 7:**
|
||||
|
||||
# systemctl enable rsyslog.service
|
||||
|
||||
**CentOS 6:**
|
||||
|
||||
# chkconfig rsyslog on
|
||||
|
||||
### 小结 ###
|
||||
|
||||
在本教程中,我演示了如何将CentOS系统转变成rsyslog客户端以强制它发送日志消息到远程rsyslog服务器。这里我假定rsyslog客户端和服务器之间的连接是安全的(如,在有防火墙保护的公司网络中)。不管在任何情况下,都不要配置rsyslog客户端将日志消息通过不安全的网络转发,或者,特别是通过互联网转发,因为syslog协议是一个明文协议。要进行安全传输,可以考虑使用[TLS/SSL][2]来加密日志消息。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/configure-rsyslog-client-centos.html
|
||||
|
||||
作者:[Caezsar M][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/caezsar
|
||||
[1]:http://xmodulo.com/configure-syslog-server-linux.html
|
||||
[2]:http://www.rsyslog.com/doc/rsyslog_tls.html
|
||||
@ -0,0 +1,151 @@
|
||||
如何在Linux的命令行中使用Evernote
|
||||
================================================================================
|
||||
这周让我们继续什么学习如个使用Linux命令行管理和组织信息。在命令行中管理[你的个人花费][1]后,我建议你在命令行中管理你的笔记,特别地是,当你笔记放在Evernote中时。为防止你从来没有听说过,[Evernote][2]专门有一个用户有好的在线服务用来在不同的设备间同步笔记。除了提供花哨的基于Web的API,Evernote还发布了在Windows、Mac、[Android][3]和iOS上的客户端。然而至今还没有官方的Linux客户端可用。老实说在众多的非官方Linux程序中,一个程序一出现就吸引了所有的命令行爱好者:[Geeknote][4]
|
||||
|
||||
### Geeknote 的安装 ###
|
||||
|
||||
Geeknote使用Python开发的。因此,在开始之前请确保你已经安装了Python(最好是2.7的版本)和git。
|
||||
|
||||
#### 在 Debian、 Ubuntu 和 Linux Mint 中 ####
|
||||
|
||||
$ sudo apt-get install python2.7 git python-setuptools
|
||||
$ git clone git://github.com/VitaliyRodnenko/geeknote.git
|
||||
$ cd geeknote
|
||||
$ sudo python2.7 setup.py install
|
||||
|
||||
#### 在 Fedora 或者 CentOS/RHEL 中 ####
|
||||
|
||||
$ sudo yum install git
|
||||
$ git clone git://github.com/VitaliyRodnenko/geeknote.git
|
||||
$ cd geeknote
|
||||
$ sudo python setup.py install
|
||||
|
||||
#### 在 Arch Linux 中 ####
|
||||
|
||||
对于ArchLinux用户,只需要使用[AUR][5]中的包。
|
||||
|
||||
### Geeknote 的基本使用 ###
|
||||
|
||||
一旦你安装玩Geeknote后,你应该将Geeknote与你的Evernote账号关联:
|
||||
|
||||
$ geeknote login
|
||||
|
||||
接着输入你的emial地址、密码、和你的二步验证码。如果你没有后者,忽略它并按下回车。
|
||||
|
||||

|
||||
|
||||
很明显,你需要一个Evernote账号来完成这些,因此先去注册。
|
||||
|
||||
一旦完成这一切之后,你就可以开始了,创建新的笔记并编辑它们。
|
||||
|
||||
但是首先,你需要设置你最喜欢的文本编辑器:
|
||||
|
||||
$ geeknote settings --editor vim
|
||||
|
||||
接着,常规创建一条新笔记的语法是:
|
||||
|
||||
$ geeknote create --title [title of the new note] (--content [content] --tags [comma-separated tags] --notebook [comma-separated notebooks])
|
||||
|
||||
上面的命令中,只有‘title’是必须的,它会与一条新笔记的标题相关联。其他的标注可以为笔记添加额外的元数据:添加标签来与你的笔记关联、指定放在那个笔记本里。同样,如果你的标题或者内容还有空格,不要忘记将它们放在引号中。
|
||||
|
||||
|
||||
比如:
|
||||
|
||||
$ geeknote create --title "My note" --content "This is a test note" --tags "finance, business, important" --notebook "Family"
|
||||
|
||||
通常上,下一步就是编辑你的笔记。语法很相似:
|
||||
|
||||
$ geeknote edit --note [title of the note to edit] (--title [new title] --tags [new tags] --notebook [new notebooks])
|
||||
|
||||
注意可选的参数如标题、标签和笔记本,用来修改笔记的元数据。比如,你可以用下面的命令重命名笔记:
|
||||
|
||||
$ geeknote edit --note [old title] --title [new title]
|
||||
|
||||
现在基本的创建和编辑已经完成了,更高级的特性是搜索和删除。你可以下面的语法搜索你的笔记:
|
||||
|
||||
$ geeknote find --search [text-to-search] --tags [comma-separated tags] --notebook [comma-separated notebooks] --date [date-or-date-range] --content-search
|
||||
|
||||
默认上,上面的命令会通过标题搜索笔记。 用"--content-search"选项,就可以搜索它们的内容。
|
||||
|
||||
比如:
|
||||
|
||||
$ geeknote find --search "*restaurant" --notebooks "Family" --date 31.03.2014-31.08.2014
|
||||
|
||||
显示制定标题的笔记:
|
||||
|
||||
$ geeknote show [title]
|
||||
|
||||

|
||||
|
||||
我最喜欢使用的一个技巧是使用:
|
||||
|
||||
$ geeknote show "*"
|
||||
|
||||
这会显示所有的笔记并允许你在这中选择一个。
|
||||
|
||||
删除一条笔记:
|
||||
|
||||
$ geeknote remove --note [title]
|
||||
|
||||
小心这是真正的删除。它会从云存储中删除这条笔记。
|
||||
|
||||
最后有很多的选项来管理标签和笔记本。我想最有用的是显示笔记本列表。
|
||||
|
||||
$ geeknote notebook-list
|
||||
|
||||
|
||||
|
||||
下面的非常相像。你可以猜到,可以用下面的命令列出所有的标签:
|
||||
|
||||
$ geeknote tag-list
|
||||
|
||||
创建一个笔记本:
|
||||
|
||||
$ geeknote notebook-create --title [notebook title]
|
||||
|
||||
创建一个标签:
|
||||
|
||||
$ geeknote tag-create --title [tag title]
|
||||
|
||||
一旦你了解了窍门,很明显语法是非常连贯且明确的。
|
||||
|
||||
如果你想要了解更多,不要忘记查看[官方文档][6]。
|
||||
|
||||
### 福利 ###
|
||||
|
||||
As a bonus, Geeknote comes with the utility gnsync, which allows for file synchronization between your Evernote account and your local computer. However, I find its syntax a bit dry:
|
||||
福利的是,Geeknote自带的gnsync工具可以让你在Evernote和本地计算机之间同步。然而,我发现它的语法有点枯燥:
|
||||
|
||||
$ gnsync --path [where to sync] (--mask [what kind of file to sync] --format [in which format] --logpath [where to write the log] --notebook [which notebook to use])
|
||||
|
||||
下面是这些的意义。
|
||||
|
||||
|
||||
- **--path /home/adrien/Documents/notes/**: 与Evernote同步笔记的位置。
|
||||
- **--mask "*.txt"**: 只同步纯文本文件。默认上,gnsync会尝试同步所有文件。
|
||||
- **--format markdown**: 你希望它们是纯文本或者markdown格式(默认是纯文本)。
|
||||
- **--logpath /home/adrien/gnsync.log**: 同步日志的位置。为防出错,gnsync会在那里写入日志信息。
|
||||
- **--notebook "Family"**: 同步哪个笔记本中的笔记。如果你那里留空,程序会创建一个以你同步文件夹命令的笔记本。
|
||||
|
||||
总结来说,Geeknote是一款花哨的Evernote的命令行客户端。我个人不常使用Evernote,但它仍然很漂亮和有用。命令行一方面让它变得很极客且很容易与shell脚本结合。同样,还有Git上fork出来的Geeknote,在ArchLinux AUR上称为[geeknote-improved-git][7],貌似它有更多的特性和比其他分支更积极的开发。但在我看来,还很值得再看看。
|
||||
|
||||
你认为Geeknote怎么样? 有什么你想用的么?或者你更喜欢使用传统的程序?在评论区中让我们知道。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/evernote-command-line-linux.html
|
||||
|
||||
作者:[Adrien Brochard][a]
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/adrien
|
||||
[1]:http://xmodulo.com/manage-personal-expenses-command-line.html
|
||||
[2]:https://evernote.com/
|
||||
[3]:http://xmodulo.com/go/android_tutorial
|
||||
[4]:http://www.geeknote.me/
|
||||
[5]:https://aur.archlinux.org/packages/geeknote-git/
|
||||
[6]:http://www.geeknote.me/documentation/
|
||||
[7]:https://aur.archlinux.org/packages/geeknote-improved-git/
|
||||
Loading…
Reference in New Issue
Block a user