mirror of
https://github.com/LCTT/TranslateProject.git
synced 2024-12-26 21:30:55 +08:00
20141219-6 选题
This commit is contained in:
parent
08a34699d6
commit
08115c8554
@ -0,0 +1,162 @@
|
||||
How to block unwanted IP addresses on Linux efficiently
|
||||
================================================================================
|
||||
You may want to block IP addresses on your Linux box under various circumstances. For example, as an end user you may want to protect yourself from known spyware or tracker IP addresses. Or when you are running P2P software, you may want to filter out connections from networks associated with anti-P2P activity. If you are a sysadmin, you may want to ban access from spam IP addresses to your production mail server. Or you may wish to block web server access from certain countries for some reason. In many cases, however, your IP address block list can grow quickly to tens of thousands of IP addresses or IP address blocks. How can you deal with it?
|
||||
|
||||
### Problems of Netfilter/IPtables ###
|
||||
|
||||
In Linux, banning an IP address can be done very easily with netfilter/iptables framework:
|
||||
|
||||
$ sudo iptables -A INPUT -s 1.1.1.1 -p TCP -j DROP
|
||||
|
||||
If you want to ban a whole IP address block, you can also do it as easily:
|
||||
|
||||
$ sudo iptables -A INPUT -s 1.1.2.0/24 -p TCP -j DROP
|
||||
|
||||
However, what if you have 1,000 independent IP addresses with no common CIDR prefix that you want to ban? You would have 1,000 iptables rules! Clearly this does not scale.
|
||||
|
||||
$ sudo iptables -A INPUT -s 1.1.1.1 -p TCP -j DROP
|
||||
$ sudo iptables -A INPUT -s 2.2.2.2 -p TCP -j DROP
|
||||
$ sudo iptables -A INPUT -s 3.3.3.3 -p TCP -j DROP
|
||||
. . . .
|
||||
|
||||
### What are IP Sets? ###
|
||||
|
||||
That is when [IP sets][1] come in handy. IP sets are a kernel feature which allows multiple (independent) IP addresses, MAC addresses or even port numbers to be encoded and stored efficiently within bitmap/hash kernel data structures. Once an IP set is created, you can create an iptables rule which matches against the set.
|
||||
|
||||
You should immediately see the benefit of using IP sets, which is that you can match against multiple IP addresses in an IP set by using a single iptables rule! You can construct IP sets using combinations of multiple IP addresses and port numbers, and can dynamically update iptables rules with IP sets without any performance impact.
|
||||
|
||||
### Install IPset Tool on Linux ###
|
||||
|
||||
To create and manage IP sets, you need to use a userspace tool called ipset.
|
||||
|
||||
To install ipset on Debian, Ubuntu or Linux Mint:
|
||||
|
||||
$ sudo apt-get install ipset
|
||||
|
||||
To install ipset on Fedora or CentOS/RHEL 7:
|
||||
|
||||
$ sudo yum install ipset
|
||||
|
||||
### Ban IP Addresses using IPset Command ###
|
||||
|
||||
Let me walk you through on how to use ipset command using simple examples.
|
||||
|
||||
First, let's create a new IP set named banthis (name can be arbitrary):
|
||||
|
||||
$ sudo ipset create banthis hash:net
|
||||
|
||||
The second argument (hash:net) in the above is required, and represents the type of a set being created. There are [multiple types][2] of IP sets. An IP set of hash:net type uses a hash to store multiple CIDR blocks. If you want to store individual IP addresses in a set, you can use hash:ip type instead.
|
||||
|
||||
Once you have created an IP set, you can check up on the set with:
|
||||
|
||||
$ sudo ipset list
|
||||
|
||||
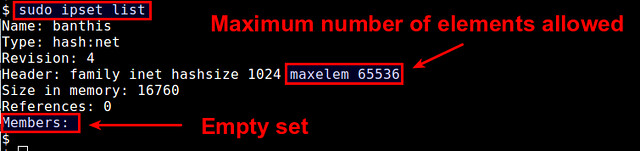
|
||||
|
||||
This shows a list of available IP sets, along with detailed information of each set including set membership. By default, each IP set can contain up to 65536 elements (CIDR blocks in this case). You can increase this limit by appending "maxelem N" option.
|
||||
|
||||
$ sudo ipset create banthis hash:net maxelem 1000000
|
||||
|
||||
Now let's add IP address blocks to the set:
|
||||
|
||||
$ sudo ipset add banthis 1.1.1.1/32
|
||||
$ sudo ipset add banthis 1.1.2.0/24
|
||||
$ sudo ipset add banthis 1.1.3.0/24
|
||||
$ sudo ipset add banthis 1.1.4.10/24
|
||||
|
||||
You will see that the set membership has been changed.
|
||||
|
||||
$ sudo ipset list
|
||||
|
||||
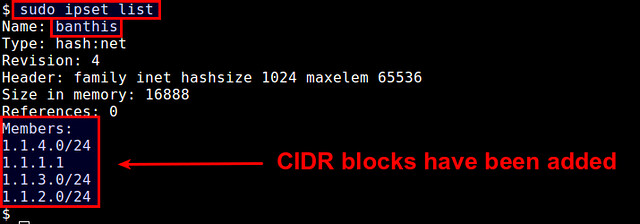
|
||||
|
||||
Now it is time to create an iptables rule using this IP set. The key here is to use "-m set --match-set <name>" option.
|
||||
|
||||
Let's create an iptables rule which prevents all those IP blocks in the set from accessing a web server at port 80. This can be achieved by:
|
||||
|
||||
$ sudo iptables -I INPUT -m set --match-set banthis src -p tcp --destination-port 80 -j DROP
|
||||
|
||||
If you want, you can save a specific IP set to a file, and then later restore it from the file:
|
||||
|
||||
$ sudo ipset save banthis -f banthis.txt
|
||||
$ sudo ipset destroy banthis
|
||||
$ sudo ipset restore -f banthis.txt
|
||||
|
||||
In the above, I tried removing an existing IP set using destroy option to see if I can restore the IP set.
|
||||
|
||||
### Automate IP Address Banning ###
|
||||
|
||||
By now you should see how powerful the concept of IP sets is. Still maintaining a up-to-date IP blacklist can be a cumbersome and time-consuming process. In fact, there are free or paid services out there which maintain these IP blacklists for you. As a bonus, let's see how we can automatically translate available IP blacklists into IP sets.
|
||||
|
||||
Let me grab free IP lists from [iblocklist.com][3] which publish various IP block lists for free or for a fee. Free versions are available in P2P format.
|
||||
|
||||
Here I am going to use an open-source python tool called iblocklist2ipset which converts P2P versions of iblocklist into IP sets.
|
||||
|
||||
First, you need to have pip installed (see [this guideline][4] to install pip).
|
||||
|
||||
Then install iblocklist2ipset as follows.
|
||||
|
||||
$ sudo pip install iblocklist2ipset
|
||||
|
||||
On some distros like Fedora, you may need to run:
|
||||
|
||||
$ sudo python-pip install iblocklist2ipset
|
||||
|
||||
Now go to [iblocklist.com][5], and grab any P2P list URL (e.g., "level1" list).
|
||||
|
||||
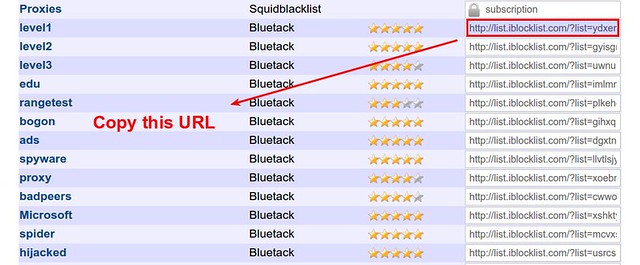
|
||||
|
||||
Then paste the URL into the following command.
|
||||
|
||||
$ iblocklist2ipset generate \
|
||||
--ipset banthis "http://list.iblocklist.com/?list=ydxerpxkpcfqjaybcssw&fileformat=p2p&archiveformat=gz" \
|
||||
> banthis.txt
|
||||
|
||||
After you run the above command, you will get a file named bandthis.txt created. If you check its content, you will see something like:
|
||||
|
||||
create banthis hash:net family inet hashsize 131072 maxelem 237302
|
||||
add banthis 1.2.4.0/24
|
||||
add banthis 1.2.8.0/24
|
||||
add banthis 1.9.75.8/32
|
||||
add banthis 1.9.96.105/32
|
||||
add banthis 1.9.102.251/32
|
||||
add banthis 1.9.189.65/32
|
||||
add banthis 1.16.0.0/14
|
||||
|
||||
You can simply load this file with ipset command:
|
||||
|
||||
$ sudo ipset restore -f banthis.txt
|
||||
|
||||
Now check the automatically created IP set with:
|
||||
|
||||
$ sudo ipset list banthis
|
||||
|
||||
As of this writing, the "level1" block list contains more than 237,000 IP address blocks. You will see that that many IP address blocks have been added to the IP set.
|
||||
|
||||
Finally, go ahead and create a single iptables rule to block them all!
|
||||
|
||||
### Summary ###
|
||||
|
||||
In this tutorial, I demonstrated how you can block unwanted IP addresses using a powerful tool called ipset. Combine that with a third-party tool like iblocklist2ipset, and you can easily streamline the process of maintaining your IP block list. For those of you who are curious about the speed improvement of ipset, the figure below shows the benchmark result comparing iptables without and with ipset (credit to [daemonkeeper.net][6]).
|
||||
|
||||
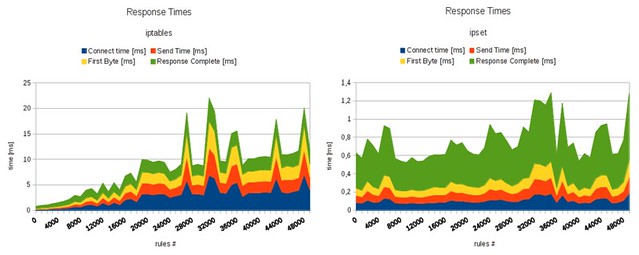
|
||||
|
||||
Tell me how much you like it. :-)
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/block-unwanted-ip-addresses-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://ipset.netfilter.org/
|
||||
[2]:http://ipset.netfilter.org/features.html
|
||||
[3]:https://www.iblocklist.com/lists.php
|
||||
[4]:http://ask.xmodulo.com/install-pip-linux.html
|
||||
[5]:https://www.iblocklist.com/lists.php
|
||||
[6]:http://daemonkeeper.net/781/mass-blocking-ip-addresses-with-ipset/
|
||||
@ -0,0 +1,99 @@
|
||||
How to filter, split or merge pcap files on Linux
|
||||
================================================================================
|
||||
If you are a network admin who is involved in testing an [intrusion detection system][1] or network access control policy, you may often rely on offline analysis using collected packet dumps. When it comes to storing packet dumps, libpcap's packet dump format (pcap format) is the most widely used by many open-source packet sniffing and capture programs. If pcap files are used as part of penetration testing or any kind of offline analysis, there's often need for manipulating pcap files before [injecting][2] them into the network.
|
||||
|
||||
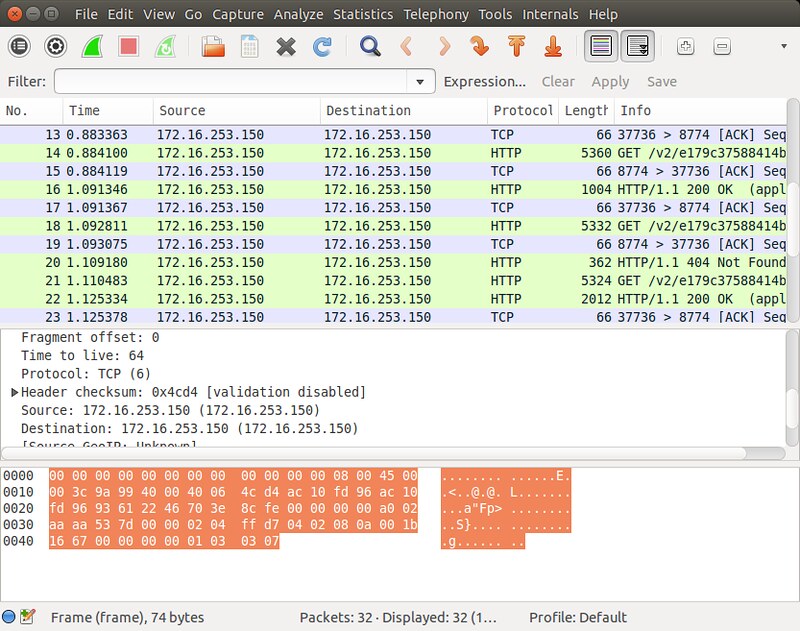
|
||||
|
||||
In this tutorial, I am going to introduce useful pcap manipulation tools and show their use cases.
|
||||
|
||||
### Editcap and Mergecap ###
|
||||
|
||||
Wireshark, the most popular GUI-based packet sniffer, actually comes with a suite of very useful command-line tools. Among them are editcap and mergecap. The former is a versatile pcap editor which can filter or split a pcap file in various fashions. The latter allows you to merge multiple pcap files into one. This tutorial is based on these Wireshark CLI tools.
|
||||
|
||||
If you already have Wireshark installed, these tools are already available for you. If not, go ahead and install Wireshark command-line tools on Linux. Note that on Debian-based distributions, you can install Wireshark command-line tools without installing Wireshark GUI, while on Red Hat based distributions, you need to install the whole Wireshark package.
|
||||
|
||||
**Debian, Ubunu or Linux Mint**
|
||||
|
||||
$ sudo apt-get install wireshark-common
|
||||
|
||||
**Fedora, CentOS or RHEL**
|
||||
|
||||
$ sudo yum install wireshark
|
||||
|
||||
Once you install Wireshark CLI tools, you can start using editcap and mergecap tools.
|
||||
|
||||
### Filter a Pcap File ###
|
||||
|
||||
editcap allows you to filter an input pcap file in various fashions, and save the result in a new pcap file.
|
||||
|
||||
First of all, you can filter an input pcap file based on start time and/or end time. "-A <start-time> and "-B <end-time> options are used to capture only those packets whose arrival time falls within a specific time range (e.g., between 2:30pm and 2:35pm). The time format to use is 'YYYY-MM-DD HH:MM:SS'.
|
||||
|
||||
$ editcap -A '2014-12-10 10:11:01' -B '2014-12-10 10:21:01' input.pcap output.pcap
|
||||
|
||||
If you want to extract specific N packets from an input pcap file, you can also do that. The command below extracts 100 packets (from 401 to 500) from input.pcap and save them as output.pcap:
|
||||
|
||||
$ editcap input.pcap output.pcap 401-500
|
||||
|
||||
If you want to filter out duplicate packets in a pcap file, use "-D <dup-window>" option. This will compare each packet against the previous (<dup-window> - 1) packets in terms of packet length and MD5 hash, and discard the packet if any match is found.
|
||||
|
||||
$ editcap -D 10 input.pcap output.pcap
|
||||
|
||||
> 37568 packets seen, 1 packets skipped with duplicate window of 10 packets.
|
||||
|
||||
Alternatively, you can define <dup-window> in terms of time interval. If you use "-w <dup-time-window> option, it will compare each packet against all the packets which arrived within <dup-time-window> seconds to determine its duplicity.
|
||||
|
||||
$ editcap -w 0.5 input.pcap output.pcap
|
||||
|
||||
> 50000 packets seen, 0 packets skipped with duplicate time window equal to or less than 0.500000000 seconds.
|
||||
|
||||
### Split a Pcap File ###
|
||||
|
||||
editcap can be also useful if you want to split a large pcap file into multiple smaller pcap files.
|
||||
|
||||
To split a pcap file into multiple pcap files of the same packet count:
|
||||
|
||||
$ editcap -c <packets-per-file> <input-pcap-file> <output-prefix>
|
||||
|
||||
Each output pcap file will have the same packet count, and be named as <output-prefix>-NNNN.
|
||||
|
||||
To split a pcap file into multiple pcap files with the same time interval:
|
||||
|
||||
$ editcap -i <seconds-per-file> <input-pcap-file> <output-prefix>
|
||||
|
||||
### Merge Pcap Files ###
|
||||
|
||||
If you want to combine multiple pcap files into one, mergecap is handy.
|
||||
|
||||
When combining pcap files, mergecap, by default, relies on per-packet timestamp information in pcap files to sort packets in chronological order.
|
||||
|
||||
$ mergecap -w output.pcap input.pcap input2.pcap [input3.pcap . . .]
|
||||
|
||||
If you want to ignore timestamp information, and simply merge multiple pcap files in their order in the command line, use '-a' option.
|
||||
|
||||
For example, the following command will write all packets from input.pcap to output.pcap, followed by all packets in input2.pcap.
|
||||
|
||||
$ mergecap -a -w output.pcap input.pcap input2.pcap
|
||||
|
||||
### Summary ###
|
||||
|
||||
In this tutorial, I presented several use cases of pcap file manipulation using editcap and mergecap. Besides these, there are other pcap related tools out there, for example, [reordercap][3] for reordering packets, [text2pcap][4] for text to pcap conversion), [pcap-diff][5] for diff pcap files, etc. Some of these pcap tools can be really handy along with [packet injection tools][6] for network penetration testing and various network troubleshooting purposes, so better to know they exist!
|
||||
|
||||
Do you use any pcap tool out there? If so, what is your use case?
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/filter-split-merge-pcap-linux.html
|
||||
|
||||
作者:[Dan Nanni][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/nanni
|
||||
[1]:http://xmodulo.com/how-to-compile-and-install-snort-from-source-code-on-ubuntu.html
|
||||
[2]:http://xmodulo.com/how-to-capture-and-replay-network-traffic-on-linux.html
|
||||
[3]:https://www.wireshark.org/docs/man-pages/reordercap.html
|
||||
[4]:https://www.wireshark.org/docs/man-pages/text2pcap.html
|
||||
[5]:https://github.com/isginf/pcap-diff
|
||||
[6]:http://xmodulo.com/how-to-capture-and-replay-network-traffic-on-linux.html
|
||||
@ -0,0 +1,120 @@
|
||||
How to schedule appointments and to-do tasks in a Linux terminal
|
||||
================================================================================
|
||||
If you are a Linux system administrator who enjoys spending your time in terminal-land, but also needs a way to stay on top of your everyday tasks, appointments and meetings, you will find [calcurse][1] to be a very useful tool. calcurse combines a calendar, a to-do list manager, a scheduler and a configurable notification system into one piece of software with a nice ncurses-based interface. At the same time, it does not confine you in a terminal, but also allows you to export your calendars and notes into other printer-friendly formats.
|
||||
|
||||
In this article we will explore how to install calcurse on Linux, and teach you how to take advantage of some of its incredible features.
|
||||
|
||||
### Instaling Calcurse on Linux ###
|
||||
|
||||
calcurse is available in standard repositories of most Linux distributions. In case calcurse is not available on your distribution (like in CentOS/RHEL), you can build it from the source easily once you have gcc and ncurses development files installed.
|
||||
|
||||
Debian, Ubuntu or Linux Mint
|
||||
|
||||
# aptitude install calcurse
|
||||
|
||||
Fedora
|
||||
|
||||
# yum install calcurse
|
||||
|
||||
CentOS/RHEL
|
||||
|
||||
# yum install gcc ncurses-devel
|
||||
# wget http://calcurse.org/files/calcurse-3.2.1.tar.gz
|
||||
# tar xvfvz calcurse-3.2.1.tar.gz
|
||||
# cd calcurse-3.2.1
|
||||
# ./configure
|
||||
# make
|
||||
# make install
|
||||
|
||||
### Launching Calcurse ###
|
||||
|
||||
Once the installation is complete, you can launch calcurse as a normal user by simply running:
|
||||
|
||||
$ calcurse
|
||||
|
||||
You will be presented with the following empty interface. If the color scheme does not seem appealing to you, you will be able to change it later.
|
||||
|
||||
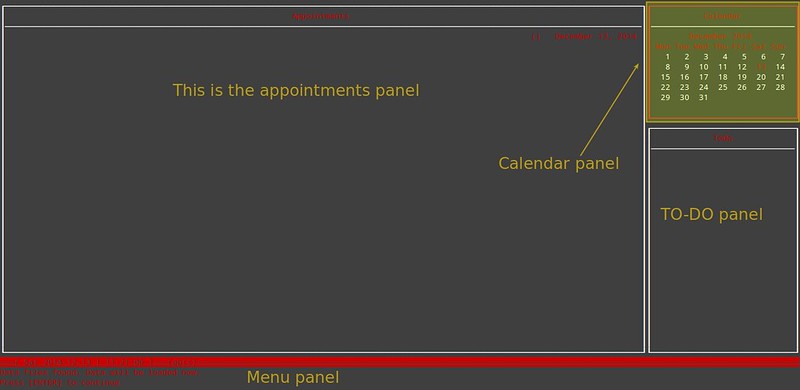
|
||||
|
||||
We will exit the main interface for now by pressing ENTER, 'q', ENTER again, and 'y'. This sequence activates the main menu at the bottom of the interface, tells calcurse to quit, saves our currently opened notes, and finally confirm about exit.
|
||||
|
||||
When we run calcurse for the first time, the following directory structure is created in our home directory:
|
||||
|
||||

|
||||
|
||||
Here is a brief description of each item:
|
||||
|
||||
- The **apts** file contains all of the user's appointments and events, while the todo file contains the **todo** list.
|
||||
- The **conf** file, as you probably already guessed, contains the current user's individual settings for his/her calcurse environment.
|
||||
- The **keys** file contains the key bindings that the user has defined (e.g., q or Q to quit, x or X to export contents, and so forth).
|
||||
- In the **notes** subdirectory you will find text files containing description of notes that you can attach to each scheduled item.
|
||||
|
||||
### Changing the Color Scheme ###
|
||||
|
||||
To change the color scheme for calcurse, follow these steps:
|
||||
|
||||

|
||||
|
||||
Use the key bindings in the last image to select a foreground and background configuration that better suits your needs:
|
||||
|
||||

|
||||
|
||||
### Adding Appointments and To-do Tasks ###
|
||||
|
||||
While navigating the command menus in the previous section, we saw that pressing the letter 'o' takes us from one menu to the next one. We can think of the second menu as the **schedule edit menu**:
|
||||
|
||||
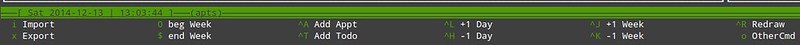
|
||||
|
||||
Thus, we will add a new appointment for today and a new to-do task with the Ctrl + A and Ctrl + T key combinations, respectively. If we want to add an appointment for a date other than today, we can navigate the calendar using the Ctrl + L (+1 day), Ctrl + H (-1 day), Ctrl + J (+1 week), and Ctrl + K (-1 week) key combinations before adding an appointment or to-do task:
|
||||
|
||||

|
||||
|
||||
The necessary steps to add a to-do task are similar, only starting with Ctrl + T, as explained earlier:
|
||||
|
||||

|
||||
|
||||
You will then be asked to enter a priority number, and the to-do task will be added to the main screen:
|
||||
|
||||

|
||||
|
||||
You can now verify that the to-do task and the appointment have been saved in the todo and apts files, respectively, under .calcurse:
|
||||
|
||||

|
||||
|
||||
Note that you can edit those files either through your favorite text editor or using the menu in the bottom of the calcurse screen. You can switch between panels by pressing the TAB key, and then choose the item you wish to edit:
|
||||
|
||||

|
||||
|
||||
### Setting up Notifications for Events ###
|
||||
|
||||
You can configure notifications via the Notify menu. To do so, follow the same steps as in the case of changing the color scheme, but choosing **Notify** instead of **Colour**:
|
||||
|
||||
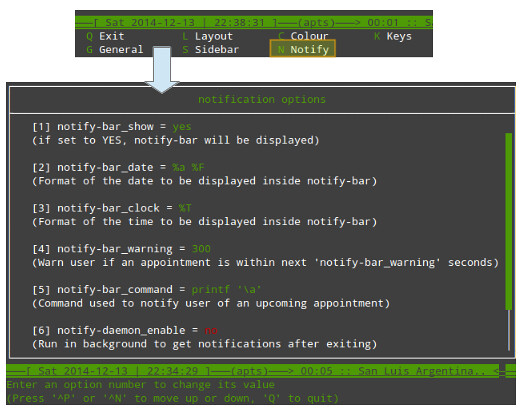
|
||||
|
||||
Suppose you want to set up email notifications. Press the number 5 to edit the value of the **notify-bar_command** as follows:
|
||||
|
||||

|
||||
|
||||
With the settings outlined above, root@localhost will receive an email notification 300 seconds (or 5 minutes) before the next scheduled task if such task is flagged as important. If you wish to enable this functionality even when calcurse is not running, change the value of notify-daemon_enable to yes. In the current example, dev2 is the localhost's hostname.
|
||||
|
||||

|
||||
|
||||
Please note that for the sake of demonstration purposes, I have changed the start and/or end time of the original appointment as needed during each step of this tutorial.
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
In this article we have shown how to set up a versatile scheduler and reminder to help you organize your daily activities and to plan ahead of important events. You may also want to check calcurse's [PDF manual][2], but feel free to drop me a line using the comment form below if you have any questions. Your comments are always more than welcome and I'll be glad to hear from you!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/schedule-appointments-todo-tasks-linux-terminal.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/gabriel
|
||||
[1]:http://calcurse.org/
|
||||
[2]:http://calcurse.org/files/manual.pdf
|
||||
@ -0,0 +1,81 @@
|
||||
What is good audio editing software on Linux
|
||||
================================================================================
|
||||
Whether you are an amateur musician or just a student recording his professor, you need to edit and work with audio recordings. If for a long time such task was exclusively attributed to Macintosh, this time is over, and Linux now has what it takes to do the job. In short, here is a non-exhaustive list of good audio editing software, fit for different tasks and needs.
|
||||
|
||||
### 1. Audacity ###
|
||||
|
||||
|
||||
|
||||
Let's get started head on with my personal favorite. [Audacity][1] works on Windows, Mac, and Linux. It is open source. It is easy to use. You get it: Audacity is almost perfect. This program lets you manipulate the audio waveform from a clean interface. In short, you can overlay tracks, cut and edit them easily, apply effects, perform advanced sound analysis, and finally export to a plethora of format. The reason I like it so much is that it combines both basic features with more complicated ones, but maintain an easy leaning curve. However, it is not a fully optimized software for hardcore musicians, or people with professional knowledge.
|
||||
|
||||
### 2. Jokosher ###
|
||||
|
||||
|
||||
|
||||
On a different level, [Jokosher][2] focuses more on the multi-track aspect for musical artists. Developed in Python and using the GTK+ interface with GStreamer for audio back-end, Jokosher really impressed me with its slick interface and its extensions. If the editing features are not the most advanced, the language is clear and directed to musicians. And I really like the association between tracks and instruments for example. In short, if you are starting as a musician, it might be a good place to get some experience before moving on to more complex suites.
|
||||
|
||||
### 3. Ardour ###
|
||||
|
||||
|
||||
|
||||
And talking about compex suites, [Ardour][3] is complete software for recording, editing, and mixing. Designed this time to appeal to all professionals, Ardour features in term of sound routing and plugins go way beyond my comprehension. So if you are looking for a beast and are not afraid to tame it, Ardour is probably a good pick. Again, the interface contributes to its charm, as well as its extensive documentation. I particularly appreciated the first-launch configuration tool.
|
||||
|
||||
### 4. Kwave ###
|
||||
|
||||

|
||||
|
||||
For all KDE lovers, [KWave][4] corresponds to your idea of design and features. There are plenty of shortcuts and interesting options, like memory management. Even if the few effects are nice, we are more dealing with a simple tool to cut/paste audio together. It becomes shard not to compare it with Audacity unfortunately. And on top of that, the interface did not appeal to me that much.
|
||||
|
||||
### 5. Qtractor ###
|
||||
|
||||

|
||||
|
||||
If Kwave is too simplistic for you but a Qt-based program really has some appeal, then [Qtractor][5] might be your option. It aims to be "simple enough for the average home user, and yet powerful enough for the professional user." Indeed the quantity of features and options is almost overwhelming. My favorite being of course customizable shortcuts. Apart from that, Qtractor is probably one of my favorite tools to deal with MIDI files.
|
||||
|
||||
### 6. LMMS ###
|
||||
|
||||
|
||||
|
||||
Standing for Linux MultiMedia Studio, LMMS is directly targeted for music production. If you do not have prior experience and do not want to spend too much time getting some, go elsewhere. LMMS is one of those complex but powerful software that only a few will truly master. The number of features and effects is simply too long to list, but if I had to pick one, I would say that the Freeboy plugin to emulate Game Boy sound system is just magical. Past that, go see their amazing documentation.
|
||||
|
||||
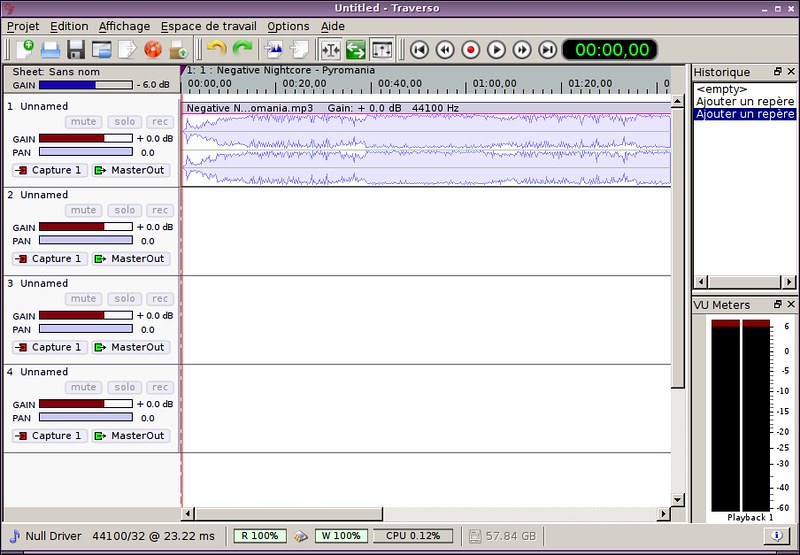
### 7. Traverso ###
|
||||
|
||||
|
||||
|
||||
Finally, Traverso stood out to me for its unlimited track count and its direct integration with CD burning capacities. Aside from that, it appeared to me as a middle man between a simplistic software and a professional program. The interface is very KDE-like, and the keyboard configuration is always welcome. And cherry on the cake, Traverso monitors your resources and make sure that your CPU or hard drive does not go overboard.
|
||||
|
||||
To conclude, it is always a pleasure to see such a large diversity of applications on Linux. It makes finding the software that best fits your needs always possible. While my personal favorite stays Audacity, I was very surprised by the design of programs like LMMS or Jokosher.
|
||||
|
||||
Did we miss one? What do you use for audio editing on Linux? And why? Let us know in the comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/good-audio-editing-software-linux.html
|
||||
|
||||
作者:[Adrien Brochard][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/adrien
|
||||
[1]:http://audacity.sourceforge.net/
|
||||
[2]:https://launchpad.net/jokosher/
|
||||
[3]:http://ardour.org/
|
||||
[4]:http://kwave.sourceforge.net/
|
||||
[5]:http://qtractor.sourceforge.net/qtractor-index.html
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
[13]:
|
||||
[14]:
|
||||
[15]:
|
||||
[16]:
|
||||
[17]:
|
||||
[18]:
|
||||
[19]:
|
||||
[20]:
|
||||
Loading…
Reference in New Issue
Block a user