mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-02-28 01:01:09 +08:00
Merge pull request #1755 from GOLinux/master
[Translated] 20140926 How to monitor user login history on CentOS with utmpdump.md
This commit is contained in:
commit
05174186c3
@ -1,121 +0,0 @@
|
||||
Translating by GOLinux!
|
||||
How to monitor user login history on CentOS with utmpdump
|
||||
================================================================================
|
||||
Keeping, maintaining and analyzing logs (i.e., accounts of events that have happened during a certain period of time or are currently happening) are among the most basic and essential tasks of a Linux system administrator. In case of user management, examining user logon and logout logs (both failed and successful) can alert us about any potential security breaches or unauthorized use of our system. For example, remote logins from unknown IP addresses or accounts being used outside working hours or during vacation leave should raise a red flag.
|
||||
|
||||
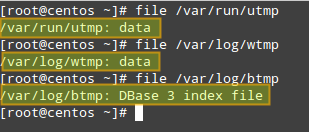
On a CentOS system, user login history is stored in the following binary files:
|
||||
|
||||
- /var/run/utmp (which logs currently open sessions) is used by who and w tools to show who is currently logged on and what they are doing, and also by uptime to display system up time.
|
||||
- /var/log/wtmp (which stores the history of connections to the system) is used by last tool to show the listing of last logged-in users.
|
||||
- /var/log/btmp (which logs failed login attempts) is used by lastb utility to show the listing of last failed login attempts. `
|
||||
|
||||
|
||||
|
||||
In this post I'll show you how to use utmpdump, a simple program from the sysvinit-tools package that can be used to dump these binary log files in text format for inspection. This tool is available by default on stock CentOS 6 and 7. The information gleaned from utmpdump is more comprehensive than the output of the tools mentioned earlier, and that's what makes it a nice utility for the job. Besides, utmpdump can be used to modify utmp or wtmp, which can be useful if you want to fix any corrupted entries in the binary logs.
|
||||
|
||||
### How to Use Utmpdump and Interpret its Output ###
|
||||
|
||||
As we mentioned earlier, these log files, as opposed to other logs most of us are familiar with (e.g., /var/log/messages, /var/log/cron, /var/log/maillog), are saved in binary file format, and thus we cannot use pagers such as less or more to view their contents. That is where utmpdump saves the day.
|
||||
|
||||
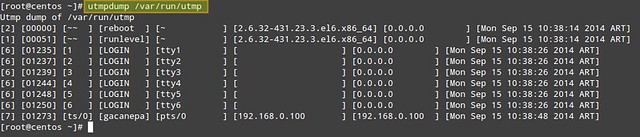
In order to display the contents of /var/run/utmp, run the following command:
|
||||
|
||||
# utmpdump /var/run/utmp
|
||||
|
||||
|
||||
|
||||
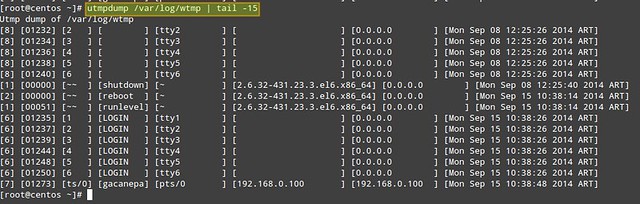
To do the same with /var/log/wtmp:
|
||||
|
||||
# utmpdump /var/log/wtmp
|
||||
|
||||
|
||||
|
||||
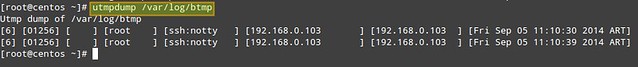
and finally with /var/log/btmp:
|
||||
|
||||
# utmpdump /var/log/btmp
|
||||
|
||||
|
||||
|
||||
As you can see, the output formats of three cases are identical, except for the fact that the records in the utmp and btmp are arranged chronologically, while in the wtmp, the order is reversed.
|
||||
|
||||
Each log line is formatted in multiple columns described as follows. The first field shows a session identifier, while the second holds PID. The third field can hold one of the following values: ~~ (indicating a runlevel change or a system reboot), bw (meaning a bootwait process), a digit (indicates a TTY number), or a character and a digit (meaning a pseudo-terminal). The fourth field can be either empty or hold the user name, reboot, or runlevel. The fifth field holds the main TTY or PTY (pseudo-terminal), if that information is available. The sixth field holds the name of the remote host (if the login is performed from the local host, this field is blank, except for run-level messages, which will return the kernel version). The seventh field holds the IP address of the remote system (if the login is performed from the local host, this field will show 0.0.0.0). If DNS resolution is not provided, the sixth and seventh fields will show identical information (the IP address of the remote system). The last (eighth) field indicates the date and time when the record was created.
|
||||
|
||||
### Usage Examples of Utmpdump ###
|
||||
|
||||
Here are a few simple use cases of utmpdump.
|
||||
|
||||
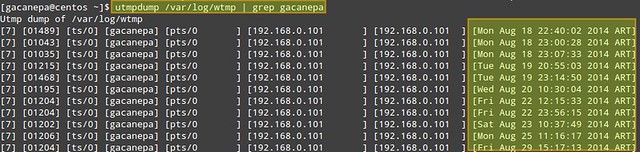
1. Check how many times (and at what times) a particular user (e.g., gacanepa) logged on to the system between August 18 and September 17.
|
||||
|
||||
# utmpdump /var/log/wtmp | grep gacanepa
|
||||
|
||||
|
||||
|
||||
If you need to review login information from prior dates, you can check the wtmp-YYYYMMDD (or wtmp.[1...N]) and btmp-YYYYMMDD (or btmp.[1...N]) files in /var/log, which are the old archives of wtmp and btmp files, generated by [logrotate][1].
|
||||
|
||||
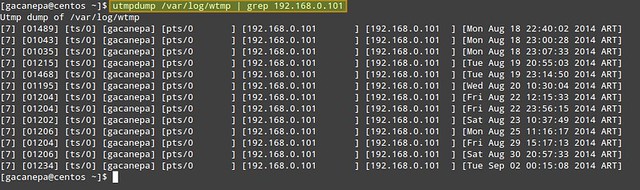
2. Count the number of logins from IP address 192.168.0.101.
|
||||
|
||||
# utmpdump /var/log/wtmp | grep 192.168.0.101
|
||||
|
||||
|
||||
|
||||
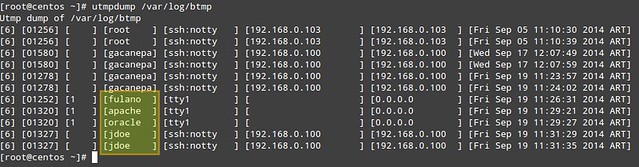
3. Display failed login attempts.
|
||||
|
||||
# utmpdump /var/log/btmp
|
||||
|
||||
|
||||
|
||||
In the output of /var/log/btmp, every log line corresponds to a failed login attempt (e.g., using incorrect password or a non-existing user ID). Logon using non-existing user IDs are highlighted in the above impage, which can alert you that someone is attempting to break into your system by guessing commonly-used account names. This is particularly serious in the cases when the tty1 was used, since it means that someone had access to a terminal on your machine (time to check who has keys to your datacenter, maybe?).
|
||||
|
||||
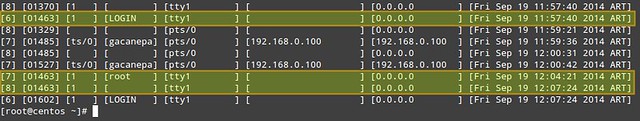
4. Display login and logout information per user session.
|
||||
|
||||
# utmpdump /var/log/wtmp
|
||||
|
||||
|
||||
|
||||
In /var/log/wtmp, a new login event is characterized by '7' in the first field, a terminal number (or pseudo-terminal id) in the third field, and username in the fourth. The corresponding logout event will be represented by '8' in the first field, the same PID as the login in the second field, and a blank terminal number field. For example, take a close look at PID 1463 in the above image.
|
||||
|
||||
- On [Fri Sep 19 11:57:40 2014 ART] the login prompt appeared in tty1.
|
||||
- On [Fri Sep 19 12:04:21 2014 ART], user root logged on.
|
||||
- On [Fri Sep 19 12:07:24 2014 ART], root logged out.
|
||||
|
||||
On a side note, the word LOGIN in the fourth field means that a login prompt is present in the terminal specified in the fifth field.
|
||||
|
||||
So far I covered somewhat trivial examples. You can combine utmpdump with other text sculpting tools such as awk, sed, grep or cut to produce filtered and enhanced output.
|
||||
|
||||
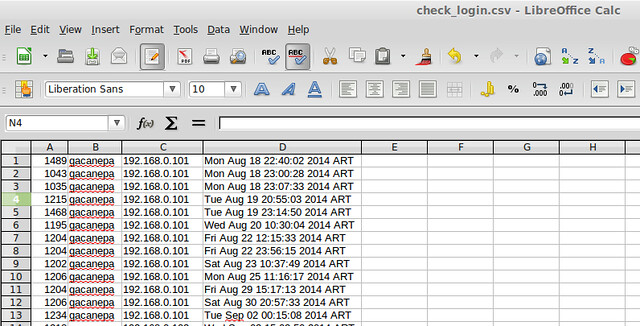
For example, you can use the following command to list all login events of a particular user (e.g., gacanepa) and send the output to a .csv file that can be viewed with a pager or a workbook application, such as LibreOffice's Calc or Microsoft Excel. Let's display PID, username, IP address and timestamp only:
|
||||
|
||||
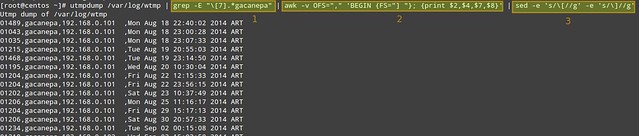
# utmpdump /var/log/wtmp | grep -E "\[7].*gacanepa" | awk -v OFS="," 'BEGIN {FS="] "}; {print $2,$4,$7,$8}' | sed -e 's/\[//g' -e 's/\]//g'
|
||||
|
||||
|
||||
|
||||
As represented with three blocks in the image, the filtering logic is composed of three pipelined steps. The first step is used to look for login events ([7]) triggered by user gacanepa. The second and third steps are used to select desired fields, remove square brackets in the output of utmpdump, and set the output field separator to a comma.
|
||||
|
||||
Of course, you need to redirect the output of the above command to a file if you want to open it later (append "> [name_of_file].csv" to the command).
|
||||
|
||||
|
||||
|
||||
In more complex examples, if you want to know what users (as listed in /etc/passwd) have not logged on during the period of time, you could extract user names from /etc/passwd, and then run grep the utmpdump output of /var/log/wtmp against user list. As you see, possibility is limitless.
|
||||
|
||||
Before concluding, let's briefly show yet another use case of utmpdump: modify utmp or wtmp. As these are binary log files, you cannot edit them as is. Instead, you can export their content to text format, modify the text output, and then import the modified content back to the binary logs. That is:
|
||||
|
||||
# utmpdump /var/log/utmp > tmp_output
|
||||
<modify tmp_output using a text editor>
|
||||
# utmpdump -r tmp_output > /var/log/utmp
|
||||
|
||||
This can be useful when you want to remove or fix any bogus entry in the binary logs.
|
||||
|
||||
To sum up, utmpdump complements standard utilities such as who, w, uptime, last, lastb by dumping detailed login events stored in utmp, wtmp and btmp log files, as well as in their rotated old archives, and that certainly makes it a great utility.
|
||||
|
||||
Feel free to enhance this post with your comments.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/09/monitor-user-login-history-centos-utmpdump.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/gabriel
|
||||
[1]:http://xmodulo.com/2014/09/logrotate-manage-log-files-linux.html
|
||||
@ -0,0 +1,120 @@
|
||||
CentOS监控用户登录历史之utmpdump
|
||||
================================================================================
|
||||
保留、维护和分析日志(如某个特定时期内发生过的,或正在发生的帐号事件),是Linux系统管理员最基础和最重要的任务之一。对于用户管理,检查用户的登入和登出日志(不管是失败的,还是成功的)可以让我们对任何潜在的安全隐患或未经授权使用系统的情况保持警惕。例如,工作时间之外或例假期间的来自未知IP地址或帐号的远程登录应当发出红色警报。
|
||||
|
||||
在CentOS系统上,用户登录历史存储在以下这些文件中:
|
||||
|
||||
- /var/run/utmp(用于记录当前打开的会话)who和w工具用来记录当前有谁登录以及他们正在做什么,而uptime用来记录系统启动时间。
|
||||
- /var/log/wtmp (用于存储系统连接历史记录)last工具用来记录最后登录的用户的列表。
|
||||
- /var/log/btmp(记录失败的登录尝试)lastb工具用来记录最后失败的登录尝试的列表。
|
||||
|
||||

|
||||
|
||||
在本帖中,我将介绍如何使用utmpdump,这个小程序来自sysvinit-tools包,可以用于转储二进制日志文件到文本格式的文件以便检查。此工具默认在CentOS 6和7家族上可用。utmpdump收集到的信息比先前提到过的工具的输出要更全面,这让它成为一个胜任该工作的很不错的工具。除此之外,utmpdump可以用于修改utmp或wtmp。如果你想要修复二进制日志中的任何损坏条目,它会很有用。
|
||||
|
||||
### Utmpdump的使用及其输出说明 ###
|
||||
|
||||
正如我们之前提到的,这些日志文件,与我们大多数人熟悉的其它日志相比(如/var/log/messages,/var/log/cron,/var/log/maillog),是以二进制格式存储的,因而我们不能使用像less或more这样的文件命令来查看它们的内容。那样看来,utmpdump拯救了世界。
|
||||
|
||||
为了要显示/var/run/utmp的内容,请运行以下命令:
|
||||
|
||||
# utmpdump /var/run/utmp
|
||||
|
||||

|
||||
|
||||
同样要显示/var/log/wtmp的内容:
|
||||
|
||||
# utmpdump /var/log/wtmp
|
||||
|
||||

|
||||
|
||||
最后,对于/var/log/btmp:
|
||||
|
||||
# utmpdump /var/log/btmp
|
||||
|
||||

|
||||
|
||||
正如你所能看到的,三种情况下的输出结果是一样的,除了utmp和btmp的记录是按时间排序,而wtmp的顺序是颠倒的这个原因外。
|
||||
|
||||
每个日志行格式化成了多列,说明如下。第一个字段显示了会话识别符,而第二个字段则是PID。第三个字段可以是以下值:~~(表示运行等级改变或系统重启),bw(启动守候进程),数字(表示TTY编号),或者字符和数字(表示伪终端)。第四个字段可以为空或用户名、重启或运行级别。第五个字段是主TTY或PTY(伪终端),如果此信息可获得的话。第六个字段是远程主机名(如果是本地登录,该字段为空,运行级别信息除外,它会返回内核版本)。第七个字段是远程系统的IP地址(如果是本地登录,该字段为0.0.0.0)。如果没有提供DNS解析,第六和第七字段会显示相同的信息(远程系统的IP地址)。最后一个(第八)字段指明了记录创建的日期和时间。
|
||||
|
||||
### Utmpdump使用样例 ###
|
||||
|
||||
下面提供了一些utmpdump的简单使用情况。
|
||||
|
||||
1. 检查8月18日到9月17日之间某个特定用户(如gacanepa)的登录次数。
|
||||
|
||||
# utmpdump /var/log/wtmp | grep gacanepa
|
||||
|
||||

|
||||
|
||||
如果你需要回顾先前日期的登录信息,你可以检查/var/log下的wtmp-YYYYMMDD(或wtmp.[1...N])和btmp-YYYYMMDD(或btmp.[1...N])文件,这些是由[logrotate][1]生成的旧wtmp和btmp的归档文件。
|
||||
|
||||
2. 统计来自IP地址192.168.0.101的登录次数。
|
||||
|
||||
# utmpdump /var/log/wtmp | grep 192.168.0.101
|
||||
|
||||

|
||||
|
||||
3. 显示失败的登录尝试。
|
||||
|
||||
# utmpdump /var/log/btmp
|
||||
|
||||

|
||||
|
||||
在/var/log/btmp输出中,每个日志行都与一个失败的登录尝试相关(如使用不正确的密码,或者一个不存在的用户ID)。上面图片中高亮部分显示了使用不存在的用户ID登录,这警告你有人尝试猜测常用帐号名来闯入系统。这在使用tty1的情况下是个极其严重的问题,因为这意味着某人对你机器上的终端具有访问权限(该检查一下谁拿到了进入你数据中心的钥匙了,也许吧?)
|
||||
|
||||
4. 显示每个用户会话的登入和登出信息
|
||||
|
||||
# utmpdump /var/log/wtmp
|
||||
|
||||

|
||||
|
||||
在/var/logwtmp中,一次新的登录事件的特征是,第一个字段为‘7’,第三个字段是一个终端编号(或伪终端id),第四个字段为用户名。相关的登出事件会在第一个字段显示‘8’,第二个字段显示与登录一样的PID,而终端编号字段空白。例如,仔细观察上面图片中PID 1463的行。
|
||||
|
||||
- On [Fri Sep 19 11:57:40 2014 ART] the login prompt appeared in tty1.
|
||||
- On [Fri Sep 19 12:04:21 2014 ART], user root logged on.
|
||||
- On [Fri Sep 19 12:07:24 2014 ART], root logged out.
|
||||
|
||||
旁注:第四个字段的LOGIN意味着出现了一次登录到第五字段指定的终端的提示。
|
||||
|
||||
到目前为止,我介绍一些有点琐碎的例子。你可以将utmpdump和其它一些文本处理工具,如awk、sed、grep或cut组合,来产生过滤和加强的输出。
|
||||
|
||||
例如,你可以使用以下命令来列出某个特定用户(如gacanepa)的所有登录事件,并发送输出结果到.csv文件,它可以用像LibreOffice Calc或Microsoft Excel之类的文字或工作簿应用程序打开查看。让我们只显示PID、用户名、IP地址和时间戳:
|
||||
|
||||
# utmpdump /var/log/wtmp | grep -E "\[7].*gacanepa" | awk -v OFS="," 'BEGIN {FS="] "}; {print $2,$4,$7,$8}' | sed -e 's/\[//g' -e 's/\]//g'
|
||||
|
||||

|
||||
|
||||
就像上面图片中三个块描绘的那样,过滤逻辑操作是由三个管道步骤组成的。第一步用于查找由用户gacanepa触发的登录事件([7]);第二步和第三部用于选择期望的字段,移除utmpdump输出的方括号并设置输出字段分隔符为逗号。
|
||||
|
||||
当然,如果你想要在以后打开来看,你需要重定向上面的命令输出到文件(添加“>[文件名].csv”到命令后面)。
|
||||
|
||||

|
||||
|
||||
在更为复杂的例子中,如果你想要知道在特定时间内哪些用户(在/etc/passwd中列出)没有登录,你可以从/etc/passwd中提取用户名,然后运行grep命令来获取/var/log/wtmp输出中对应用户的列表。就像你看到的那样,有着无限可能。
|
||||
|
||||
在进行总结之前,让我们简要地展示一下utmpdump的另外一种使用情况:修改utmp或wtmp。由于这些都是二进制日志文件,你不能像编辑文件一样来编辑它们。取而代之是,你可以将其内容输出成为文本格式,并修改文本输出内容,然后将修改后的内容导入回二进制日志中。如下:
|
||||
|
||||
# utmpdump /var/log/utmp > tmp_output
|
||||
<modify tmp_output using a text editor>
|
||||
# utmpdump -r tmp_output > /var/log/utmp
|
||||
|
||||
这在你想要移除或修复二进制日志中的任何伪造条目时很有用。
|
||||
|
||||
下面小结一下,utmpdump通过转储详细的登录事件到utmp、wtmp和btmp日志文件,也可以是轮循的旧归档文件,来补充如who,w,uptime,last,lastb之类的标准工具的不足,这也使得它成为一个很棒的工具。
|
||||
|
||||
你可以随意添加评论以加强本帖的含金量。
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: http://xmodulo.com/2014/09/monitor-user-login-history-centos-utmpdump.html
|
||||
|
||||
作者:[Gabriel Cánepa][a]
|
||||
译者:[GOLinux](https://github.com/GOLinux)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创翻译,[Linux中国](http://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:http://xmodulo.com/author/gabriel
|
||||
[1]:http://xmodulo.com/2014/09/logrotate-manage-log-files-linux.html
|
||||
Loading…
Reference in New Issue
Block a user