mirror of
https://github.com/LCTT/TranslateProject.git
synced 2025-03-12 01:40:10 +08:00
Merge remote-tracking branch 'LCTT/master'
This commit is contained in:
commit
026a62d871
@ -1,33 +1,33 @@
|
||||
Flash Player 的两种开源替代方案
|
||||
======
|
||||
> Adobe 将于 2020 年终止对 Flash 媒体播放器的支持,但仍有很多人们希望访问的 Flash 视频。这里有两个开源的替代品或许可以帮到你。
|
||||
|
||||

|
||||
|
||||
2017 年 7 月,Adobe 为 Flash Media Player 敲响了[丧钟][1],宣布将在 2020 年终止对曾经无处不在的在线视频播放器的支持。但事实上,在一系列损害了其声誉的零日攻击后,Flash 的份额在过去的 8 年一直在下跌。苹果公司在 2010 年宣布它不会支持这项技术后,其未来趋于黯淡,并且在谷歌停止在 Chrome 浏览器中默认启用 Flash(支持 HTML5)后,它的消亡在 2016 年加速。
|
||||
2017 年 7 月,Adobe 为 Flash Media Player 敲响了[丧钟][1],宣布将在 2020 年终止对曾经无处不在的在线视频播放器的支持。但事实上,在一系列损害了其声誉的零日攻击后,Flash 的份额在过去的 8 年一直在下跌。苹果公司在 2010 年宣布它不会支持这项技术后,其未来趋于黯淡,并且在谷歌停止在 Chrome 浏览器中默认启用 Flash(支持 HTML5)后,它的消亡在 2016 年进一步加速。
|
||||
|
||||
即便如此,Adobe 仍然每月发布该软件的更新,截至 2018 年 8 月,它在网站的使用率从 2011 年的 28.5% 下降到[仅 4.4%] [2]。还有更多证据表明 Flash 的下滑:谷歌工程总监 [Parisa Tabriz 说][3]通过浏览器访问 Flash 内容的 Chrome 用户数量从 2014 年的 80% 下降到 2018 年的 8%。
|
||||
|
||||
尽管如今很少有视频创作者以 Flash 格式发布,但仍有很多人们希望在未来几年内访问的 Flash 视频。鉴于官方支持的日期已经屈指可数,开源软件创建者有很好的机会介入 Adobe Flash Media Player 的替代品。这其中两个应用是 Lightspark 和 GNU Gnash。它们都不是完美的替代品,但来自贡献者的帮助可以使它们成为可行的替代品。
|
||||
尽管如今很少有视频创作者以 Flash 格式发布,但仍有很多人们希望在未来几年内访问的 Flash 视频。鉴于官方支持的日期已经屈指可数,开源软件创建者有很好的机会涉足 Adobe Flash 媒体播放器的替代品。这其中两个应用是 Lightspark 和 GNU Gnash。它们都不是完美的替代品,但来自贡献者的帮助可以使它们成为可行的替代品。
|
||||
|
||||
### Lightspark
|
||||
|
||||
[Lightspark][4] 是 Linux 上的 Flash Player 替代品。虽然它仍处于 alpha 状态,但自从 Adobe 在 2017 宣布废弃 Adobe 以来,开发速度已经加快。据其网站称,Lightspark 实现了 60% 的 Flash API,可在许多流行网站包括 BBC 新闻、Google Play 音乐和亚马逊音乐上[使用][5]。
|
||||
|
||||
Lightspark 是用 C++/C 编写的,并在 [LGPLv3][6] 下许可。该项目列出了 41 个贡献者,并正在积极征求错误报告和其他贡献。有关更多信息,请查看其[ GitHub 仓库][5]。
|
||||
Lightspark 是用 C++/C 编写的,并在 [LGPLv3][6] 下许可。该项目列出了 41 个贡献者,并正在积极征求错误报告和其他贡献。有关更多信息,请查看其 [GitHub 仓库][5]。
|
||||
|
||||
### GNU Gnash
|
||||
|
||||
[GNU Gnash][7] 是一个用于 GNU/Linux 操作系统,包括 Ubuntu、Fedora 和 Debian 的 Flash Player。它作为独立软件和插件可用于 Firefox 和 Konqueror 浏览器中。
|
||||
|
||||
Gnash 的主要缺点是它不支持最新版本的 Flash 文件 - 它支持大多数 Flash SWF v7 功能,一些 v8 和 v9 功能,不支持 v10 文件。它处于测试阶段,由于它在[ GNU GPLv3 或更高版本][8]下许可,因此你可以帮助实现它的现代化。访问其[项目页面][9]获取更多信息。
|
||||
Gnash 的主要缺点是它不支持最新版本的 Flash 文件 —— 它支持大多数 Flash SWF v7 功能,一些 v8 和 v9 功能,不支持 v10 文件。它处于测试阶段,由于它在 [GNU GPLv3 或更高版本][8]下许可,因此你可以帮助实现它的现代化。访问其[项目页面][9]获取更多信息。
|
||||
|
||||
### 想要创建Flash吗?
|
||||
### 想要创建 Flash 吗?
|
||||
|
||||
* 仅因为大多数人都不会发布 Flash 视频,但这并不意味着永远不需要创建 SWF 文件。如果你发现自己需要,这两个开源工具可能会有所帮助:
|
||||
|
||||
* [Motion-Twin ActionScript 2 编译器][10](MTASC):一个命令行编译器,它可以在没有 Adobe Animate(Adobe 当前的视频创建软件)的情况下生成 SWF 文件。
|
||||
* [Ming][11]:用 C 编写的可以生成 SWF 文件的库。它还包含一些可用于处理 Flash 的[程序][12]。
|
||||
仅因为大多数人都不会发布 Flash 视频,但这并不意味着永远不需要创建 SWF 文件。如果你发现自己需要,这两个开源工具可能会有所帮助:
|
||||
|
||||
* [Motion-Twin ActionScript 2 编译器][10](MTASC):一个命令行编译器,它可以在没有 Adobe Animate(Adobe 当前的视频创建软件)的情况下生成 SWF 文件。
|
||||
* [Ming][11]:用 C 编写的可以生成 SWF 文件的库。它还包含一些可用于处理 Flash 的[程序][12]。
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
@ -37,7 +37,7 @@ via: https://opensource.com/alternatives/flash-media-player
|
||||
作者:[Opensource.com][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[geekpi](https://github.com/geekpi)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
校对:[wxy](https://github.com/wxy)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
76
sources/talk/20180919 5 ways DevSecOps changes security.md
Normal file
76
sources/talk/20180919 5 ways DevSecOps changes security.md
Normal file
@ -0,0 +1,76 @@
|
||||
5 ways DevSecOps changes security
|
||||
======
|
||||
|
||||

|
||||
|
||||
There’s been an ongoing kerfuffle over whether we need to expand [DevOps][1] to explicitly bring in security. After all, the thinking goes, [DevOps][2] has always been something of a shorthand for a broad set of new practices, using new tools (often open source) and built on more collaborative cultures. Why not [DevBizOps][3] for better aligning with business needs? Or DevChatOps to emphasize better and faster communications?
|
||||
|
||||
However, [as John Willis wrote earlier this year][4] on his coming around to the [DevSecOps][5] terminology, “Hopefully, someday we will have a world where we no longer have to use the word DevSecOps and security will be an inherent part of all service delivery discussions. Until that day, and at this point, my general conclusion is that it’s just three new characters. More importantly, the name really differentiates the problem statement in a world where we as an industry are not doing a great job on information security.”
|
||||
|
||||
So why aren’t we doing a great job on [information security][6], and what does it mean to do a great job in a DevSecOps context?
|
||||
|
||||
We’ve arguably never done a great job of information security in spite of (or maybe because of) the vast industry of complex point products addressing narrow problems. But we also arguably did a good enough job during the era when defending against threats focused on securing the perimeter, network connections were limited, and most users were employees using company-provided devices.
|
||||
|
||||
Those circumstances haven’t accurately described most organizations’ reality for a number of years now. But the current era, which brings in not only DevSecOps but new application architectural patterns, development practices, and an increasing number of threats, defines a stark new normal that requires a faster pace of change. It’s not so much that DevSecOps in isolation changes security, but that infosec circa 2018 requires new approaches.
|
||||
|
||||
Consider these five areas.
|
||||
|
||||
### Automation
|
||||
|
||||
Lots of automation is a hallmark of DevOps generally. It’s partly about speed. If you’re going to move fast (and not break things), you need to have repeatable processes that execute without a lot of human intervention. Indeed, automation is one of the best entry points for DevOps, even in organizations that are still mostly working on monolithic legacy apps. Automating routine processes associated with configurations or testing with easy-to-use tools such as [Ansible][7] is a common quick hit for starting down the path to DevOps.
|
||||
|
||||
DevSecOps is no different. Security today is a continuous process rather than a discrete checkpoint in the application lifecycle, or even a weekly or monthly check. When vulnerabilities are found and fixes issued by a vendor, it’s important they be applied quickly given that exploits taking advantage of those vulnerabilities will be out soon.
|
||||
|
||||
### "Shift left"
|
||||
|
||||
Traditional security is often viewed as a gatekeeper at the end of the development process. Check all the boxes and your app goes into production. Otherwise, try again. Security teams have a reputation for saying no a lot.
|
||||
|
||||
Therefore, the thinking goes, why not move security earlier (left in a typical left-to-right drawing of a development pipeline)? Security may still say no, but the consequences of rework in early-stage development are a lot less than they are when the app is complete and ready to ship.
|
||||
|
||||
I don’t like the “shift left” term, though. It implies that security is still a one-time event that’s just been moved earlier. Security needs to be a largely automated process everywhere in the application lifecycle, from the supply chain to the development and test process all the way through deployment.
|
||||
|
||||
### Manage dependencies
|
||||
|
||||
One of the big changes we see with modern app development is that you often don’t write most of the code. Using open source libraries and frameworks is one obvious case in point. But you may also just use external services from public cloud providers or other sources. In many cases, this external code and services will dwarf what you write yourself.
|
||||
|
||||
As a result, DevSecOps needs to include a serious focus on your [software supply chain][8]. Are you getting your software from trusted sources? Is it up to date? Is it integrated into the security processes that you use for your own code? What policies do you have in place for which code and APIs you can use? Is commercial support available for the components that you are using for your own production code?
|
||||
|
||||
No set of answers are going to be appropriate in all cases. They may be different for a proof-of-concept versus an at-scale production workload. But, as has been the case in manufacturing for a long time (and DevSecOps has many analogs in how manufacturing has evolved), the integrity of the supply chain is critical.
|
||||
|
||||
### Visibility
|
||||
|
||||
I’ve talked a lot about the need for automation throughout all the stages of the application lifecycle. That makes the assumption that we can see what’s going on in each of those stages.
|
||||
|
||||
Effective DevSecOps requires effective instrumentation so that automation knows what to do. This instrumentation falls into a number of categories. There are long-term and high-level metrics that help tell us if the overall DevSecOps process is working well. There are critical alerts that require immediate human intervention (the security scanning system is down!). There are alerts, such as for a failed scan, that require remediation. And there are logs of the many parameters we capture for later analysis (what’s changing over time? What caused that failure?).
|
||||
|
||||
### Services vs. monoliths
|
||||
|
||||
While DevSecOps practices can be applied across many types of application architectures, they’re most effective with small and loosely coupled components that can be updated and reused without potentially forcing changes elsewhere in the app. In their purest form, these components can be [microservices][9] or functions, but the general principles apply wherever you have loosely coupled services communicating over a network.
|
||||
|
||||
This pattern does introduce some new security challenges. The interactions between components can be complex and the total attack surface can be larger because there are now more entry points to the application across the network.
|
||||
|
||||
On the other hand, this type of architecture also means that automated security and monitoring also has more granular visibility into the application components because they’re no longer buried deep within a monolithic application.
|
||||
|
||||
Don’t get too wrapped up in the DevSecOps term, but take it as a reminder that security is evolving because the way that we write and deploy applications is evolving.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/9/devsecops-changes-security
|
||||
|
||||
作者:[Gordon Haff][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ghaff
|
||||
[1]: https://opensource.com/resources/devops
|
||||
[2]: https://opensource.com/tags/devops
|
||||
[3]: https://opensource.com/article/18/5/steps-apply-devops-culture-beyond-it
|
||||
[4]: https://www.devsecopsdays.com/articles/its-just-a-name
|
||||
[5]: https://opensource.com/article/18/4/devsecops
|
||||
[6]: https://opensource.com/article/18/6/where-cycle-security-devops
|
||||
[7]: https://opensource.com/tags/ansible
|
||||
[8]: https://opensource.com/article/17/1/be-open-source-supply-chain
|
||||
[9]: https://opensource.com/tags/microservices
|
||||
@ -0,0 +1,51 @@
|
||||
Building a Secure Ecosystem for Node.js
|
||||
======
|
||||
|
||||

|
||||
|
||||
At[Node+JS Interactive][1], attendees collaborate face to face, network, and learn how to improve their skills with JS in serverless, IoT, and more. [Stephanie Evans][2], Content Manager for Back-end Web Development at LinkedIn Learning, will be speaking at the upcoming conference about building a secure ecosystem for Node.js. Here she answers a few questions about teaching and learning basic security practices.
|
||||
|
||||
**Linux.com: Your background is in tech education, can you provide more details on how you would define this and how you got into this area of expertise?**
|
||||
|
||||
**Stephanie Evans:** It sounds cliché, but I’ve always been passionate about education and helping others. After college, I started out as an instructor of a thoroughly analog skill: reading. I worked my way up to hiring and training reading teachers and discovered my passion for helping people share their knowledge and refine their teaching craft. Later, I went to work for McGraw Hill Education, publishing self-study certification books on popular IT certs like CompTIA’s Network+ and Security+, ISAAP’s CISSP, etc. My job was to figure out who the biggest audiences in IT were; what they needed to know to succeed professionally; hire the right book author; and help develop the manuscript with them.
|
||||
|
||||
I moved into online learning/e-learning 4 years ago and shifted to video training courses geared towards developers. I enjoy working with people who spend their time building and solving complex problems. I now manage the video training library for back-end web developers at LinkedIn Learning/Lynda.com and figure out what developers need to know; hire instructors to create that content; and work together to figure out how best to teach it to them. And, then update those courses when they inevitably become out of date.
|
||||
|
||||
**Linux.com: What initially drove you to use your skill set in education to help with security practices?**
|
||||
|
||||
**Evans:** I attend a lot of conferences, watch a lot of talks, and chat to a lot of developers as part of my job. I distinctly remember attending a security best practices talk at a very large, enterprise-tech focused conference and was surprised by the rudimentary content being covered. Poor guy, I’d thought…he’s going to get panned by this audience. But then I looked around and most everyone was engaged. They were learning something new and compelling. And it hit me: I had been in a security echo chamber of my own making. Just like the mainstream developer isn’t working with the cutting-edge technology people are raving about on Twitter, they aren’t necessarily as fluent in basic security practices as I’d assumed. A mix of unawareness, intense time pressure, and perhaps some misplaced trust can lead to a “security later” mentality. But with the global cost of cybercrime up to 6 00 billion a year from 500 billion in 2014 as well as the [exploding amount of data on the web][3]. We can’t afford to be working around security or assuming everyone knows the basics.
|
||||
|
||||
**Linux.com: What do you think are some common misconceptions about security with Node.js and in general with developers?**
|
||||
|
||||
**Evans:** I think one of the biggest misconceptions is that security awareness and practices should come “later” in a developer’s career (and later in the development cycle). Yes, your first priority is to learn that Java and JavaScript are not the same thing—that’s obviously most important. And you do have to understand how to create a form before you can understand how to prevent cross-site -scripting attacks. But helping developers understand—at all stages of their career and learning journey—what the potential vulnerabilities are and how they can be exploited needs to be a much higher priority and come earlier than we may intuitively think.
|
||||
|
||||
I joke with my instructors that we have to sneak in the ‘eat your vegetables’ content to our courses. Security is an exciting, complex and challenging topic, but it can feel like you’re having to eat your vegetables as a developer when you dig into it. Often ‘security’ is a separate department (that can be perceived as ‘slowing things down’ or getting in the way of deploying code) and it can further distance developers from their role in securing their applications.
|
||||
|
||||
I also think that those who truly understand security can feel that it’s overwhelmingly complex to teach—but we have to start somewhere. I attended an introductory npm talk last year that talked about how to work with dependencies and packages…but never once mentioned the possibility of malicious code making it into your application through these packages. I’m all about teaching just enough at the right time and not throwing the kitchen sink of knowledge at new developers. We should stop thinking of security—or even just security awareness—as an intermediate or advanced skill and start bringing it up early and often.
|
||||
|
||||
**Linux.com: How can we infuse tech education into our security practices? Where does this begin?**
|
||||
|
||||
**Evans:** It definitely goes both ways. Clear documentation and practical resources right alongside security recommendations go a long way towards ensuring understanding and adoption. You have to make things as easy as possible if you want people to actually do it. And you have to make those best practices accessible enough to understand.
|
||||
|
||||
The [2018 Node User Survey Report][4] from the Node.js Foundation showed that while learning resources around Node.js and JavaScript development improved, the availability and quality of learning resources for Node.js Security received the lowest scores across the board.
|
||||
|
||||
After documentation and Stack Overflow, many developers rely on online videos and tutorials—we need to push security education to the forefront, rather than expecting developers to seek it out. OWASP, the nodegoat project, and the Node.js Security Working Group are doing great work here to move the needle. I think tech education can do even more to bring security in earlier in the learning journey and create awareness about common exploits and important resources.
|
||||
|
||||
Learn more at [Node+JS Interactive][1], coming up October 10-12, 2018 in Vancouver, Canada.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/node-js/2018/9/building-secure-ecosystem-nodejs
|
||||
|
||||
作者:[The Linux Foundation][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.linux.com/users/ericstephenbrown
|
||||
[1]: https://events.linuxfoundation.org/events/node-js-interactive-2018/?utm_source=Linux.com&utm_medium=article&utm_campaign=jsint18
|
||||
[2]: https://jsi2018.sched.com/speaker/stevans1?iframe=no
|
||||
[3]: https://www.forbes.com/sites/bernardmarr/2018/05/21/how-much-data-do-we-create-every-day-the-mind-blowing-stats-everyone-should-read/#101d261a60ba
|
||||
[4]: https://nodejs.org/en/user-survey-report/
|
||||
@ -0,0 +1,126 @@
|
||||
WinWorld – A Large Collection Of Defunct OSs, Software And Games
|
||||
======
|
||||
|
||||

|
||||
|
||||
The other day, I was testing **Dosbox** which is used to [**run MS-DOS games and programs in Linux**][1]. While searching for some classic programs like Turbo C++, I stumbled upon a website named **WinWorld**. I went through a few links in this site and quite surprised. WinWorld has a plenty of good-old and classic OSs, software, applications, development tools, games and a lot of other miscellaneous utilities which are abandoned by the developers a long time ago. It is an online museum run by community members, volunteers and is dedicated to the preservation and sharing of vintage, abandoned, and pre-release software.
|
||||
|
||||
WinWorld was started back in 2003 and its founder claims that the idea to start this site inspired by Yahoo briefcases. The primary purpose of this site is to preserve and share old software. Over the years, many people volunteered to improve this site in numerous ways and the collection of old software in WinWorld has grown exponentially. The entire WinWorld library is free, open and available to everyone.
|
||||
|
||||
### WinWorld Hosts A Huge Collection Of Defunct OSs, Software, System Applications And Games
|
||||
|
||||
Like I already said, WinWorld hosts a huge collection of abandonware which are no-longer in development.
|
||||
|
||||
**Linux and Unix:**
|
||||
|
||||
Here, I have given the complete list of UNIX and LINUX OSs with brief summary of the each OS and the release year of first version.
|
||||
|
||||
* **A/UX** – An early port of Unix to Apple’s 68k based Macintosh platform, released in 1988.
|
||||
* **AIX** – A Unix port originally developed by IBM, released in 1986.
|
||||
* **AT &T System V Unix** – One of the first commercial versions of the Unix OS, released in 1983.
|
||||
* **Banyan VINES** – A network operating system originally designed for Unix, released in 1984.
|
||||
* **Corel Linux** – A commercial Linux distro, released in 1999.
|
||||
* **DEC OSF-1** – A version of UNIX developed by Digital Equipment Corporation (DEC), released in 1991.
|
||||
* **Digital UNIX** – A renamed version of **OSF-1** , released by DEC in 1995.**
|
||||
**
|
||||
* **FreeBSD** **1.0** – The first release of FreeBSD, released in 1993. It is based on 4.3BSD.
|
||||
* **Gentus Linux** – A distribution that failed to comply with GPL. Developed by ABIT and released in 2000.
|
||||
* **HP-UX** – A UNIX variant, released in 1992.
|
||||
* **IRIX** – An a operating system developed by Silicon Graphics Inc (SGI ) and it is released in 1988.
|
||||
* **Lindows** – Similar to Corel Linux. It is developed for commercial purpose and released in 2002.
|
||||
* **Linux Kernel** – A copy of the Linux Sourcecode, version 0.01. Released in the early 90’s.
|
||||
* **Mandrake Linux** – A Linux distribution based on Red Hat Linux. It was later renamed to Mandriva. Released in 1999.
|
||||
* **NEWS-OS** – A variant of BSD, developed by Sony and released in 1989.
|
||||
* **NeXTStep** – A Unix based OS from NeXT computers headed by **Steve Jobs**. It is released in 1987.
|
||||
* **PC/IX** – A UNIX variant created for IBM PCs. Released in 1984.
|
||||
* **Red Hat Linux 5.0** – A commercial Linux distribution by Red Hat.
|
||||
* **Sun Solaris** – A Unix based OS by Sun Microsystems. Released in 1992.
|
||||
* **SunOS** – A Unix-based OS derived from BSD by Sun Microsystems, released in 1982.
|
||||
* **Tru64 UNIX** – A formerly known OSF/1 by DEC.
|
||||
* **Ubuntu 4.10** – The well-known OS based on Debian.This was a beta pre-release, prior to the very first official Ubuntu release.
|
||||
* **Ultrix** – A UNIX clone developed by DEC.
|
||||
* **UnixWare** – A UNIX variant from Novell.
|
||||
* **Xandros Linux** – A proprietary variant of Linux. It is based on Corel Linux. The first version is released in 2003.
|
||||
* **Xenix** – A UNIX variant originally published by Microsoft released in 1984.
|
||||
|
||||
|
||||
|
||||
Not just Linux/Unix, you can find other operating systems including DOS, Windows, Apple/Mac, OS 2, Novell netware and other OSs and shells.
|
||||
|
||||
**DOS & CP/M:**
|
||||
|
||||
* 86-DOS
|
||||
* Concurrent CPM-86 & Concurrent DOS
|
||||
* CP/M 86 & CP/M-80
|
||||
* DOS Plus
|
||||
* DR-DOS
|
||||
* GEM
|
||||
* MP/M
|
||||
* MS-DOS
|
||||
* Multitasking MS-DOS 4.00
|
||||
* Multiuser DOS
|
||||
* PC-DOS
|
||||
* PC-MOS
|
||||
* PTS-DOS
|
||||
* Real/32
|
||||
* Tandy Deskmate
|
||||
* Wendin DOS
|
||||
|
||||
|
||||
|
||||
**Windows:**
|
||||
|
||||
* BackOffice Server
|
||||
* Windows 1.0/2.x/3.0/3.1/95/98/2000/ME/NT 3.X/NT 4.0
|
||||
* Windows Whistler
|
||||
* WinFrame
|
||||
|
||||
|
||||
|
||||
**Apple/Mac:**
|
||||
|
||||
* Mac OS 7/8/9
|
||||
* Mac OS X
|
||||
* System Software (0-6)
|
||||
|
||||
|
||||
|
||||
**OS/2:**
|
||||
|
||||
* Citrix Multiuser
|
||||
* OS/2 1.x
|
||||
* OS/2 2.0
|
||||
* OS/2 3.x
|
||||
* OS/2 Warp 4
|
||||
|
||||
|
||||
|
||||
Also, WinWorld hosts a huge collection of old software, system applications, development tools and games. Go and check them out as well.
|
||||
|
||||
To be honest, I don’t even know the existence of most of the stuffs listed in this site. Some of the tools listed here were released years before I was born.
|
||||
|
||||
Just in case, If you ever in need of or wanted to test a classic stuff (be it a game, software, OS), look nowhere, just head over to WinWorld library and download them that you want to explore. Good luck!
|
||||
|
||||
**Disclaimer:**
|
||||
|
||||
OSTechNix is not affiliated with WinWorld site in any way. We, at OSTechNix, don’t know the authenticity and integrity of the stuffs hosted in this site. Also, downloading software from third-party sites is not safe or may be illegal in your region. Neither the author nor OSTechNix is responsible for any kind of damage. Use this service at your own risk.
|
||||
|
||||
And, that’s all for now. Hope this was useful. More good stuffs to come. Stay tuned!
|
||||
|
||||
Cheers!
|
||||
|
||||
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.ostechnix.com/winworld-a-large-collection-of-defunct-oss-software-and-games/
|
||||
|
||||
作者:[SK][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://www.ostechnix.com/author/sk/
|
||||
[1]: https://www.ostechnix.com/how-to-run-ms-dos-games-and-programs-in-linux/
|
||||
@ -1,84 +0,0 @@
|
||||
sd886393 is dragging this out to translating
|
||||
Free Resources for Securing Your Open Source Code
|
||||
======
|
||||
|
||||

|
||||
|
||||
While the widespread adoption of open source continues at a healthy rate, the recent [2018 Open Source Security and Risk Analysis Report][1] from Black Duck and Synopsys reveals some common concerns and highlights the need for sound security practices. The report examines findings from the anonymized data of over 1,100 commercial codebases with represented Industries from automotive, Big Data, enterprise software, financial services, healthcare, IoT, manufacturing, and more.
|
||||
|
||||
The report highlights a massive uptick in open source adoption, with 96 percent of the applications scanned containing open source components. However, the report also includes warnings about existing vulnerabilities. Among the [findings][2]:
|
||||
|
||||
* “What is worrisome is that 78 percent of the codebases examined contained at least one open source vulnerability, with an average 64 vulnerabilities per codebase.”
|
||||
|
||||
* “Over 54 percent of the vulnerabilities found in audited codebases are considered high-risk vulnerabilities.”
|
||||
|
||||
* Seventeen percent of the codebases contained a highly publicized vulnerability such as Heartbleed, Logjam, Freak, Drown, or Poodle.
|
||||
|
||||
|
||||
|
||||
|
||||
"The report clearly demonstrates that with the growth in open source use, organizations need to ensure they have the tools to detect vulnerabilities in open source components and manage whatever license compliance their use of open source may require," said Tim Mackey, technical evangelist at Black Duck by Synopsys.
|
||||
|
||||
Indeed, with ever more impactful security threats emerging,the need for fluency with security tools and practices has never been more pronounced. Most organizations are aware that network administrators and sysadmins need to have strong security skills, and, in many cases security certifications. [In this article,][3] we explored some of the tools, certifications and practices that many of them wisely embrace.
|
||||
|
||||
The Linux Foundation has also made available many informational and educational resources on security. Likewise, the Linux community offers many free resources for specific platforms and tools. For example, The Linux Foundation has published a [Linux workstation security checklist][4] that covers a lot of good ground. Online publications ranging from the [Fedora security guide][5] to the[Securing Debian Manual][6] can also help users protect against vulnerabilities within specific platforms.
|
||||
|
||||
The widespread use of cloud platforms such as OpenStack is also stepping up the need for cloud-centric security smarts. According to The Linux Foundation’s[Guide to the Open Cloud][7]: “Security is still a top concern among companies considering moving workloads to the public cloud, according to Gartner, despite a strong track record of security and increased transparency from cloud providers. Rather, security is still an issue largely due to companies’ inexperience and improper use of cloud services.”
|
||||
|
||||
For both organizations and individuals, the smallest holes in implementation of routers, firewalls, VPNs, and virtual machines can leave room for big security problems. Here is a collection of free tools that can plug these kinds of holes:
|
||||
|
||||
* [Wireshark][8], a packet analyzer
|
||||
|
||||
* [KeePass Password Safe][9], a free open source password manager
|
||||
|
||||
* [Malwarebytes][10], a free anti-malware and antivirus tool
|
||||
|
||||
* [NMAP][11], a powerful security scanner
|
||||
|
||||
* [NIKTO][12], an open source web server scanner
|
||||
|
||||
* [Ansible][13], a tool for automating secure IT provisioning
|
||||
|
||||
* [Metasploit][14], a tool for understanding attack vectors and doing penetration testing
|
||||
|
||||
|
||||
|
||||
|
||||
Instructional videos abound for these tools. You’ll find a whole[tutorial series][15] for Metasploit, and [video tutorials][16] for Wireshark. Quite a few free ebooks provide good guidance on security as well. For example, one of the common ways for security threats to invade open source platforms occurs in M&A scenarios, where technology platforms are merged—often without proper open source audits. In an ebook titled [Open Source Audits in Merger and Acquisition Transactions][17], from Ibrahim Haddad and The Linux Foundation, you’ll find an overview of the open source audit process and important considerations for code compliance, preparation, and documentation.
|
||||
|
||||
Meanwhile, we’ve[previously covered][18] a free ebook from the editors at[The New Stack][19] called Networking, Security & Storage with Docker & Containers. It covers the latest approaches to secure container networking, as well as native efforts by Docker to create efficient and secure networking practices. The ebook is loaded with best practices for locking down security at scale.
|
||||
|
||||
All of these tools and resources, and many more, can go a long way toward preventing security problems, and an ounce of prevention is, as they say, worth a pound of cure. With security breaches continuing, now is an excellent time to look into the many security and compliance resources for open source tools and platforms available. Learn more about security, compliance, and open source project health [here][20].
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/2018/5/free-resources-securing-your-open-source-code
|
||||
|
||||
作者:[Sam Dean][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/sam-dean
|
||||
[1]:https://www.blackducksoftware.com/open-source-security-risk-analysis-2018
|
||||
[2]:https://www.prnewswire.com/news-releases/synopsys-report-finds-majority-of-software-plagued-by-known-vulnerabilities-and-license-conflicts-as-open-source-adoption-soars-300648367.html
|
||||
[3]:https://www.linux.com/blog/sysadmin-ebook/2017/8/future-proof-your-sysadmin-career-locking-down-security
|
||||
[4]:http://go.linuxfoundation.org/ebook_workstation_security
|
||||
[5]:https://docs.fedoraproject.org/en-US/Fedora/19/html/Security_Guide/index.html
|
||||
[6]:https://www.debian.org/doc/manuals/securing-debian-howto/index.en.html
|
||||
[7]:https://www.linux.com/publications/2016-guide-open-cloud
|
||||
[8]:https://www.wireshark.org/
|
||||
[9]:http://keepass.info/
|
||||
[10]:https://www.malwarebytes.com/
|
||||
[11]:http://searchsecurity.techtarget.co.uk/tip/Nmap-tutorial-Nmap-scan-examples-for-vulnerability-discovery
|
||||
[12]:https://cirt.net/Nikto2
|
||||
[13]:https://www.ansible.com/
|
||||
[14]:https://www.metasploit.com/
|
||||
[15]:http://www.computerweekly.com/tutorial/The-Metasploit-Framework-Tutorial-PDF-compendium-Your-ready-reckoner
|
||||
[16]:https://www.youtube.com/watch?v=TkCSr30UojM
|
||||
[17]:https://www.linuxfoundation.org/resources/open-source-audits-merger-acquisition-transactions/
|
||||
[18]:https://www.linux.com/news/networking-security-storage-docker-containers-free-ebook-covers-essentials
|
||||
[19]:http://thenewstack.io/ebookseries/
|
||||
[20]:https://www.linuxfoundation.org/projects/security-compliance/
|
||||
@ -0,0 +1,111 @@
|
||||
Host your own cloud with Raspberry Pi NAS
|
||||
======
|
||||
|
||||
Protect and secure your data with a self-hosted cloud powered by your Raspberry Pi.
|
||||
|
||||
In the first two parts of this series, we discussed the [hardware and software fundamentals][1] for building network-attached storage (NAS) on a Raspberry Pi. We also put a proper [backup strategy][2] in place to secure the data on the NAS. In this third part, we will talk about a convenient way to store, access, and share your data with [Nextcloud][3].
|
||||
|
||||
### Prerequisites
|
||||
|
||||
To use Nextcloud conveniently, you have to meet a few prerequisites. First, you should have a domain you can use for the Nextcloud instance. For the sake of simplicity in this how-to, we'll use **nextcloud.pi-nas.com**. This domain should be directed to your Raspberry Pi. If you want to run it on your home network, you probably need to set up dynamic DNS for this domain and enable port forwarding of ports 80 and 443 (if you go for an SSL setup, which is highly recommended; otherwise port 80 should be sufficient) from your router to the Raspberry Pi.
|
||||
|
||||
You can automate dynamic DNS updates from the Raspberry Pi using [ddclient][4].
|
||||
|
||||
### Install Nextcloud
|
||||
|
||||
To run Nextcloud on your Raspberry Pi (using the setup described in the [first part][1] of this series), install the following packages as dependencies to Nextcloud using **apt**.
|
||||
|
||||
```
|
||||
sudo apt install unzip wget php apache2 mysql-server php-zip php-mysql php-dom php-mbstring php-gd php-curl
|
||||
```
|
||||
|
||||
The next step is to download Nextcloud. [Get the latest release's URL][5] and copy it to download via **wget** on the Raspberry Pi. In the first article in this series, we attached two disk drives to the Raspberry Pi, one for current data and one for backups. Install Nextcloud on the data drive to make sure data is backed up automatically every night.
|
||||
|
||||
```
|
||||
sudo mkdir -p /nas/data/nextcloud
|
||||
sudo chown pi /nas/data/nextcloud
|
||||
cd /nas/data/
|
||||
wget https://download.nextcloud.com/server/releases/nextcloud-14.0.0.zip -O /nas/data/nextcloud.zip
|
||||
unzip nextcloud.zip
|
||||
sudo ln -s /nas/data/nextcloud /var/www/nextcloud
|
||||
sudo chown -R www-data:www-data /nas/data/nextcloud
|
||||
```
|
||||
|
||||
When I wrote this, the latest release (as you see in the code above) was 14. Nextcloud is under heavy development, so you may find a newer version when installing your copy of Nextcloud onto your Raspberry Pi.
|
||||
|
||||
### Database setup
|
||||
|
||||
When we installed Nextcloud above, we also installed MySQL as a dependency to use it for all the metadata Nextcloud generates (for example, the users you create to access Nextcloud). If you would rather use a Postgres database, you'll need to adjust some of the modules installed above.
|
||||
|
||||
To access the MySQL database as root, start the MySQL client as root:
|
||||
|
||||
```
|
||||
sudo mysql
|
||||
```
|
||||
|
||||
This will open a SQL prompt where you can insert the following commands—substituting the placeholder with the password you want to use for the database connection—to create a database for Nextcloud.
|
||||
|
||||
```
|
||||
CREATE USER nextcloud IDENTIFIED BY '<insert-password-here>';
|
||||
CREATE DATABASE nextcloud;
|
||||
GRANT ALL ON nextcloud.* TO nextcloud;
|
||||
```
|
||||
|
||||
You can exit the SQL prompt by pressing **Ctrl+D** or entering **quit**.
|
||||
|
||||
### Web server configuration
|
||||
|
||||
Nextcloud can be configured to run using Nginx or other web servers, but for this how-to, I decided to go with the Apache web server on my Raspberry Pi NAS. (Feel free to try out another alternative and let me know if you think it performs better.)
|
||||
|
||||
To set it up, configure a virtual host for the domain you created for your Nextcloud instance **nextcloud.pi-nas.com**. To create a virtual host, create the file **/etc/apache2/sites-available/001-nextcloud.conf** with content similar to the following. Make sure to adjust the ServerName to your domain and paths, if you didn't use the ones suggested earlier in this series.
|
||||
|
||||
```
|
||||
<VirtualHost *:80>
|
||||
ServerName nextcloud.pi-nas.com
|
||||
ServerAdmin admin@pi-nas.com
|
||||
DocumentRoot /var/www/nextcloud/
|
||||
|
||||
<Directory /var/www/nextcloud/>
|
||||
AllowOverride None
|
||||
</Directory>
|
||||
</VirtualHost>
|
||||
```
|
||||
|
||||
To enable this virtual host, run the following two commands.
|
||||
|
||||
```
|
||||
a2ensite 001-nextcloud
|
||||
sudo systemctl reload apache2
|
||||
```
|
||||
|
||||
With this configuration, you should now be able to reach the web server with your domain via the web browser. To secure your data, I recommend using HTTPS instead of HTTP to access Nextcloud. A very easy (and free) way is to obtain a [Let's Encrypt][6] certificate with [Certbot][7] and have a cron job automatically refresh it. That way you don't have to mess around with self-signed or expiring certificates. Follow Certbot's simple how-to [instructions to install it on your Raspberry Pi][8]. During Certbot configuration, you can even decide to automatically forward HTTP to HTTPS, so visitors to **<http://nextcloud.pi-nas.com>** will be redirected to **<https://nextcloud.pi-nas.com>**. Please note, if your Raspberry Pi is running behind your home router, you must have port forwarding enabled for ports 443 and 80 to obtain Let's Encrypt certificates.
|
||||
|
||||
### Configure Nextcloud
|
||||
|
||||
The final step is to visit your fresh Nextcloud instance in a web browser to finish the configuration. To do so, open your domain in a browser and insert the database details from above. You can also set up your first Nextcloud user here, the one you can use for admin tasks. By default, the data directory should be inside the Nextcloud folder, so you don't need to change anything for the backup mechanisms from the [second part of this series][2] to pick up the data stored by users in Nextcloud.
|
||||
|
||||
Afterward, you will be directed to your Nextcloud and can log in with the admin user you created previously. To see a list of recommended steps to ensure a performant and secure Nextcloud installation, visit the Basic Settings tab in the Settings page (in our example: <https://nextcloud.pi-nas.com/>settings/admin) and see the Security & Setup Warnings section.
|
||||
|
||||
Congratulations! You've set up your own Nextcloud powered by a Raspberry Pi. Go ahead and [download a Nextcloud client][9] from the Nextcloud page to sync data with your client devices and access it offline. Mobile clients even provide features like instant upload of pictures you take, so they'll automatically sync to your desktop PC without wondering how to get them there.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/9/host-cloud-nas-raspberry-pi
|
||||
|
||||
作者:[Manuel Dewald][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/ntlx
|
||||
[1]: https://opensource.com/article/18/7/network-attached-storage-Raspberry-Pi
|
||||
[2]: https://opensource.com/article/18/8/automate-backups-raspberry-pi
|
||||
[3]: https://nextcloud.com/
|
||||
[4]: https://sourceforge.net/p/ddclient/wiki/Home/
|
||||
[5]: https://nextcloud.com/install/#instructions-server
|
||||
[6]: https://letsencrypt.org/
|
||||
[7]: https://certbot.eff.org/
|
||||
[8]: https://certbot.eff.org/lets-encrypt/debianother-apache
|
||||
[9]: https://nextcloud.com/install/#install-clients
|
||||
@ -0,0 +1,123 @@
|
||||
8 Python packages that will simplify your life with Django
|
||||
======
|
||||
|
||||
This month's Python column looks at Django packages that will benefit your work, personal, or side projects.
|
||||
|
||||

|
||||
|
||||
Django developers, we're devoting this month's Python column to packages that will help you. These are our favorite [Django][1] libraries for saving time, cutting down on boilerplate code, and generally simplifying our lives. We've got six packages for Django apps and two for Django's REST Framework, and we're not kidding when we say these packages show up in almost every project we work on.
|
||||
|
||||
But first, see our tips for making the [Django Admin more secure][2] and an article on 5 favorite [open source Django packages][3].
|
||||
|
||||
### A kitchen sink of useful time-savers: django-extensions
|
||||
|
||||
[Django-extensions][4] is a favorite Django package chock full of helpful tools like these management commands:
|
||||
|
||||
* **shell_plus** starts the Django shell with all your database models already loaded. No more importing from several different apps to test one complex relationship!
|
||||
* **clean_pyc** removes all .pyc projects from everywhere inside your project directory.
|
||||
* **create_template_tags** creates a template tag directory structure inside the app you specify.
|
||||
* **describe_form** displays a form definition for a model, which you can then copy/paste into forms.py. (Note that this produces a regular Django form, not a ModelForm.)
|
||||
* **notes** displays all comments with stuff like TODO, FIXME, etc. throughout your project.
|
||||
|
||||
|
||||
* **TimeStampedModel** : This base class includes the fields **created** and **modified** and a **save()** method that automatically updates these fields appropriately.
|
||||
* **ActivatorModel** : If your model will need fields like **status** , **activate_date** , and **deactivate_date** , use this base class. It comes with a manager that enables **.active()** and **.inactive()** querysets.
|
||||
* **TitleDescriptionModel** and **TitleSlugDescriptionModel** : These include the **title** and **description** fields, and the latter also includes a **slug** field. The **slug** field will automatically populate based on the **title** field.
|
||||
|
||||
|
||||
|
||||
Django-extensions also includes useful abstract base classes to use for common patterns in your own models. Inherit from these base classes when you create your models to get their:
|
||||
|
||||
Django-extensions has more features you may find useful in your projects, so take a tour through its [docs][5]!
|
||||
|
||||
### 12-factor-app settings: django-environ
|
||||
|
||||
[Django-environ][6] allows you to use [12-factor app][7] methodology to manage your settings in your Django project. It collects other libraries, including [envparse][8] and [honcho][9]. Once you install django-environ, create an .env file at your project's root. Define in that module any settings variables that may change between environments or should remain secret (like API keys, debug status, and database URLs).
|
||||
|
||||
Then, in your project's settings.py file, import **environ** and set up variables for **environ.PATH()** and **environ.Env()** according to the [example][10]. Access settings variables defined in your .env file with **env('VARIABLE_NAME')**.
|
||||
|
||||
### Creating great management commands: django-click
|
||||
|
||||
[Django-click][11], based on [Click][12] (which we have recommended [before][13]… [twice][14]), helps you write Django management commands. This library doesn't have extensive documentation, but it does have a directory of [test commands][15] in its repository that are pretty useful. A basic Hello World command would look like this:
|
||||
|
||||
```
|
||||
# app_name.management.commands.hello.py
|
||||
import djclick as click
|
||||
|
||||
@click.command()
|
||||
@click.argument('name')
|
||||
def command(name):
|
||||
click.secho(f'Hello, {name}')
|
||||
```
|
||||
|
||||
Then in the command line, run:
|
||||
|
||||
```
|
||||
>> ./manage.py hello Lacey
|
||||
Hello, Lacey
|
||||
```
|
||||
|
||||
### Handling finite state machines: django-fsm
|
||||
|
||||
[Django-fsm][16] adds support for finite state machines to your Django models. If you run a news website and need articles to process through states like Writing, Editing, and Published, django-fsm can help you define those states and manage the rules and restrictions around moving from one state to another.
|
||||
|
||||
Django-fsm provides an FSMField to use for the model attribute that defines the model instance's state. Then you can use django-fsm's **@transition** decorator to define methods that move the model instance from one state to another and handle any side effects from that transition.
|
||||
|
||||
Although django-fsm is light on documentation, [Workflows (States) in Django][17] is a gist that serves as an excellent introduction to both finite state machines and django-fsm.
|
||||
|
||||
### Contact forms: #django-contact-form
|
||||
|
||||
A contact form is such a standard thing on a website. But don't write all that boilerplate code yourself—set yours up in minutes with [django-contact-form][18]. It comes with an optional spam-filtering contact form class (and a regular, non-filtering class) and a **ContactFormView** base class with methods you can override or customize, and it walks you through the templates you will need to create to make your form work.
|
||||
|
||||
### Registering and authenticating users: django-allauth
|
||||
|
||||
[Django-allauth][19] is an app that provides views, forms, and URLs for registering users, logging them in and out, resetting their passwords, and authenticating users with outside sites like GitHub or Twitter. It supports email-as-username authentication and is extensively documented. It can be a little confusing to set up the first time you use it; follow the [installation instructions][20] carefully and read closely when you [customize your settings][21] to make sure you're using all the settings you need to enable a specific feature.
|
||||
|
||||
### Handling user authentication with Django REST Framework: django-rest-auth
|
||||
|
||||
If your Django development includes writing APIs, you're probably using [Django REST Framework][22] (DRF). If you're using DRF, you should check out [django-rest-auth][23], a package that enables endpoints for user registration, login/logout, password reset, and social media authentication (by adding django-allauth, which works well with django-rest-auth).
|
||||
|
||||
### Visualizing a Django REST Framework API: django-rest-swagger
|
||||
|
||||
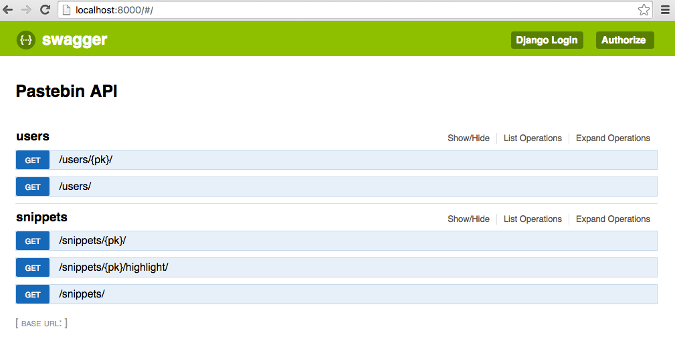
[Django REST Swagger][24] provides a feature-rich user interface for interacting with your Django REST Framework API. Once you've installed Django REST Swagger and added it to installed apps, add the Swagger view and URL pattern to your urls.py file; the rest is taken care of in the docstrings of your APIs.
|
||||
|
||||
|
||||
|
||||
The UI for your API will include all your endpoints and available methods broken out by app. It will also list available operations for those endpoints and enable you to interact with the API (adding/deleting/fetching records, for example). It uses the docstrings in your API views to generate documentation for each endpoint, creating a set of API documentation for your project that's useful to you, your frontend developers, and your users.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://opensource.com/article/18/9/django-packages
|
||||
|
||||
作者:[Jeff Triplett][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://opensource.com/users/laceynwilliams
|
||||
[1]: https://www.djangoproject.com/
|
||||
[2]: https://opensource.com/article/18/1/10-tips-making-django-admin-more-secure
|
||||
[3]: https://opensource.com/business/15/12/5-favorite-open-source-django-packages
|
||||
[4]: https://django-extensions.readthedocs.io/en/latest/
|
||||
[5]: https://django-extensions.readthedocs.io/
|
||||
[6]: https://django-environ.readthedocs.io/en/latest/
|
||||
[7]: https://www.12factor.net/
|
||||
[8]: https://github.com/rconradharris/envparse
|
||||
[9]: https://github.com/nickstenning/honcho
|
||||
[10]: https://django-environ.readthedocs.io/
|
||||
[11]: https://github.com/GaretJax/django-click
|
||||
[12]: http://click.pocoo.org/5/
|
||||
[13]: https://opensource.com/article/18/9/python-libraries-side-projects
|
||||
[14]: https://opensource.com/article/18/5/3-python-command-line-tools
|
||||
[15]: https://github.com/GaretJax/django-click/tree/master/djclick/test/testprj/testapp/management/commands
|
||||
[16]: https://github.com/viewflow/django-fsm
|
||||
[17]: https://gist.github.com/Nagyman/9502133
|
||||
[18]: https://django-contact-form.readthedocs.io/en/1.5/
|
||||
[19]: https://django-allauth.readthedocs.io/en/latest/
|
||||
[20]: https://django-allauth.readthedocs.io/en/latest/installation.html
|
||||
[21]: https://django-allauth.readthedocs.io/en/latest/configuration.html
|
||||
[22]: http://www.django-rest-framework.org/
|
||||
[23]: https://django-rest-auth.readthedocs.io/
|
||||
[24]: https://django-rest-swagger.readthedocs.io/en/latest/
|
||||
@ -0,0 +1,185 @@
|
||||
Record Screen in Ubuntu Linux With Kazam [Beginner’s Guide]
|
||||
======
|
||||
**This tutorial shows you how to install Kazam screen recorder and explains how to record screen in Ubuntu. The guide also lists useful shortcuts and handy tips for using Kazam.**
|
||||
|
||||
![How to record your screen in Ubuntu Linux with Kazam][1]
|
||||
|
||||
[Kazam][2] is one of the [best screen recorders for Linux][3]. To me, it’s the best screen recording tool. I have been using it for years. All the video tutorials on YouTube have been recorded with Kazam.
|
||||
|
||||
Some of the main features of Kazam are:
|
||||
|
||||
* Record entire screen, part of screen, application window or all screens (for multi-monitor setup)
|
||||
* Take screenshots
|
||||
* Keyboard shortcut support for easily pausing and resuming while recording screen
|
||||
* Record in various file formats such as MP4, AVI and more.
|
||||
* Capture audio from speaker or microphone while recording the screen
|
||||
* Capture mouse clicks and key presses
|
||||
* Capture video from webcam
|
||||
* Insert a webcam window on the side
|
||||
* Broadcast to YouTube live video
|
||||
|
||||
|
||||
|
||||
Like the screenshot tool [Shutter][4], Kazam is also not being actively developed for the last couple of years. And like Shutter, the present Kazam release works just fine.
|
||||
|
||||
I am using Ubuntu in the tutorial. The installation instructions should work for other Ubuntu-based distributions such as Linux Mint, elementary OS etc. For all the other distributions, you can still read about using Kazam and its features.
|
||||
|
||||
### Install Kazam in Ubuntu
|
||||
|
||||
Kazam is available in the official repository in Ubuntu. However, the official repository consists Kazam version 1.4.5, the last stable version of Kazam.
|
||||
|
||||
![Kazam Version 1.4.5][5]
|
||||
Kazam Version 1.4.5
|
||||
|
||||
Kazam developer(s) also worked on a newer release, Kazam 1.5.3. The version was almost sable and ready to release, but for unknown reasons, the development stopped after this. There have been [no updates][6] since then.
|
||||
|
||||
You can use either of Kazam 1.4.5 and 1.5.3 without hesitating. Kazam 1.5 provides additional features like recording mouse clicks and key presses, webcam support, live broadcast support, and a refreshed countdown timer.
|
||||
|
||||
![Kazam Version 1.5.3][7]
|
||||
Kazam Version 1.5.3
|
||||
|
||||
It’s up to you to decide which version you want to use. I would suggest go for version 1.5.3 because it has more features.
|
||||
|
||||
You can install the older Kazam 1.4.5 from the Software Center. You can also use the command below:
|
||||
|
||||
```
|
||||
sudo apt install kazam
|
||||
```
|
||||
|
||||
If you want to install the newer Kazam 1.5.3, you can use this [unofficial PPA][8] that is available for Ubuntu 18.04 and 16.04:
|
||||
|
||||
```
|
||||
sudo add-apt-repository ppa:sylvain-pineau/kazam
|
||||
sudo apt-get update
|
||||
sudo apt install kazam
|
||||
```
|
||||
|
||||
You also need to install a few libraries in order to record the mouse clicks and keyboard presses.
|
||||
|
||||
```
|
||||
sudo apt install python3-cairo python3-xlib
|
||||
```
|
||||
|
||||
### Recording your screen with Kazam
|
||||
|
||||
Once you have installed Kazam, search for it in the application menu and start it. You should see a screen like this with some options on it. You can check the options as per your need and click on capture to start recording screen with Kazam.
|
||||
|
||||
![Screen recording with Kazam][9]
|
||||
Screen recording with Kazam
|
||||
|
||||
It will show you a countdown before recording the screen. The default wait time is 5 seconds and you can change it from Kazam interface (see the previous image). It gives you a breathing time so that you can prepare for your recording.
|
||||
|
||||
![Countdown before screen recording][10]
|
||||
Countdown before screen recording
|
||||
|
||||
Once the recording starts,the main Kazam interface disappears and an indicator appears in the panel. If you want to pause the recording or finish the recording, you can do it from this indicator.
|
||||
|
||||
![Pause or finish screen recording][11]
|
||||
Pause or finish screen recording
|
||||
|
||||
If you choose to finish the recording, it will give you the option to “Save for later”. If you have a [video editor installed in Linux][12], you can also start editing the recording from this point.
|
||||
|
||||
![Save screen recording in Kazam][13]
|
||||
Save recording
|
||||
|
||||
By default it prompts you to install the recording in Videos folder but you can change the location and save it elsewhere as well.
|
||||
|
||||
That’s the basic you need to know about screen recording in Linux with Kazam.
|
||||
|
||||
Now let me give you a few tips on how to utilize more features in Kazam.
|
||||
|
||||
### Getting more out of Kazam screen recorder
|
||||
|
||||
Kazam is a featureful screen recorder for Linux. You can access its advanced or additional features from the preferences.
|
||||
|
||||
![Accessing Kazam preferences][14]
|
||||
Accessing Kazam preferences
|
||||
|
||||
#### Autosave screen recording in a specified location
|
||||
|
||||
You can choose to automatically save the screen recordings in Kazam. The default location is Videos but you can change it to any other location.
|
||||
|
||||
![Autosave screen recordings in a chosen location][15]
|
||||
Autosave in a chosen location
|
||||
|
||||
#### Avoid screen recording in RAW mode
|
||||
|
||||
You can save your screen recordings in file formats like WEBM, MP4, AVI etc. You are free to choose what you want. However, I would advise avoiding RAW (AVI) file format. If you use RAW file format, the recorded files will be in GBs even for a few minutes of recordings.
|
||||
|
||||
It’s wise to verify that Kazam is not using the RAW file format for recording. If you ask my suggestion, prefer H264 with MP4 file format.
|
||||
|
||||
![file format in Kazam][16]
|
||||
Don’t use RAW files
|
||||
|
||||
#### Capture mouse clicks and key presses while screen recording
|
||||
|
||||
If you want to highlight when a mouse was clicked, you can easily do that in the newer version of Kazam.
|
||||
|
||||
![Record mouse clicks while screen recording with Kazam][17]
|
||||
Record mouse clicks
|
||||
|
||||
All you have to do is to check the “Key presses and mouse clicks” option on the Kazam interface (the same screen where you press Capture).
|
||||
|
||||
#### Use keyboard shortcuts for more efficient screen recordings
|
||||
|
||||
Imagine you are recording screen in Linux and suddenly you realized that you have to pause the recording for some reasons. Now, you can pause the recording by going to the Kazam indicator and selecting the pause option. But this activity of selecting the pause option will also be recorded.
|
||||
|
||||
You can edit out this part later but it unnecessarily adds to the already cumbersome editing task.
|
||||
|
||||
A better option will be to use the [keyboard shortcuts in Ubuntu][18]. Screen recording becomes a lot better if you use the shortcuts.
|
||||
|
||||
While Kazam is running, you can use the following hotkeys:
|
||||
|
||||
* Super+Ctrl+R: Start recording
|
||||
* Super+Ctrl+P: Pause recording, press again for resuming the recording
|
||||
* Super+Ctrl+F: Finish recording
|
||||
* Super+Ctrl+Q: Quit recording
|
||||
|
||||
|
||||
|
||||
Super key is the Windows key on your keyboard.
|
||||
|
||||
The most important is Super+Ctrl+P for pausing and resuming the recording.
|
||||
|
||||
You can further explore the Kazam preferences for webcam recording and YouTube live broadcasting options.
|
||||
|
||||
### Do you like Kazam?
|
||||
|
||||
I am repeating myself here. I love Kazam. I have used other screen recorders like [SimpleScreenRecorder][19] or [Green Recorder][20] but I feel a lot more comfortable with Kazam.
|
||||
|
||||
I hope you like Kazam for screen recording in Ubuntu or any other Linux distribution. I have tried highlighting some of the additional features here to help you with a better screen recording.
|
||||
|
||||
What features do you like about Kazam? Do you use some other screen recorder? Do they work better than Kazam? Please share your views in the comments section below.
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://itsfoss.com/kazam-screen-recorder/
|
||||
|
||||
作者:[Abhishek Prakash][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/译者ID)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]: https://itsfoss.com/author/abhishek/
|
||||
[1]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/screen-recording-kazam-ubuntu-linux.png
|
||||
[2]: https://launchpad.net/kazam
|
||||
[3]: https://itsfoss.com/best-linux-screen-recorders/
|
||||
[4]: http://shutter-project.org/
|
||||
[5]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/kazam-1-4-5.png
|
||||
[6]: https://launchpad.net/~kazam-team/+archive/ubuntu/unstable-series
|
||||
[7]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/kazam-1-5-3.png
|
||||
[8]: https://launchpad.net/~sylvain-pineau/+archive/ubuntu/kazam
|
||||
[9]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/kazam-start-recording.png
|
||||
[10]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/kazam-countdown.jpg
|
||||
[11]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/kazam-finish-recording.png
|
||||
[12]: https://itsfoss.com/best-video-editing-software-linux/
|
||||
[13]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/kazam-save-recording.jpg
|
||||
[14]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/kazam-preferences.png
|
||||
[15]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/kazam-auto-save.jpg
|
||||
[16]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/select-file-type-kazam.jpg
|
||||
[17]: https://4bds6hergc-flywheel.netdna-ssl.com/wp-content/uploads/2018/09/record-mouse-clicks-kazam.jpeg
|
||||
[18]: https://itsfoss.com/ubuntu-shortcuts/
|
||||
[19]: https://itsfoss.com/record-screen-ubuntu-simplescreenrecorder/
|
||||
[20]: https://itsfoss.com/green-recorder-3/
|
||||
@ -0,0 +1,83 @@
|
||||
一些提高你开源源码安全性的工具
|
||||
======
|
||||
|
||||

|
||||
|
||||
虽然目前开源依然发展势头较好,并被广大的厂商所采用,然而最近由 Black Duck 和 Synopsys 发布的[2018开源安全与风险评估报告][1]指出了一些存在的风险并重点阐述了对于健全安全措施的需求。这份报告的分析资料素材来自经过脱敏后的 1100 个商业代码库,这些代码所涉及:自动化、大数据、企业级软件、金融服务业、健康医疗、物联网、制造业等多个领域。
|
||||
|
||||
这份报告强调开源软件正在被大量的使用,扫描结果中有 96% 的应用都使用了开源组件。然而,报告还指出许多其中存在很多漏洞。具体在 [这里][2]:
|
||||
|
||||
* 令人担心的是扫描的所有结果中,有 78% 的代码库存在至少一个开源的漏洞,平均每个代码库有 64 个漏洞。
|
||||
|
||||
* 在经过代码审计过后代码库中,发现超过 54% 的漏洞经验证是高危漏洞。
|
||||
|
||||
* 17% 的代码库包括一种已经早已公开的漏洞,包括:Heartbleed、Logjam、Freak、Drown、Poddle。
|
||||
|
||||
|
||||
|
||||
|
||||
Tim Mackey,Synopsys 旗下 Black Duck 的技术负责人称,"这份报告清楚的阐述了:随着开源软件正在被企业广泛的使用,企业与组织也应当使用一些工具来检测可能出现在这些开源软件中的漏洞,并且管理其所使用的开源软件的方式是否符合相应的许可证规则"
|
||||
|
||||
确实,随着越来越具有影响力的安全威胁出现,历史上从未有过我们目前对安全工具和实践的需求。大多数的组织已经意识到网络与系统管理员需要具有相应的较强的安全技能和安全证书。[在这篇文章中,][3] 我们给出一些具有较大影响力的工具、认证和实践。
|
||||
|
||||
Linux 基金会已经在安全方面提供了许多关于安全的信息与教育资源。比如,Linux 社区提供许多免费的用来针对一些平台的工具,其中[Linux 服务器安全检查表][4] 其中提到了很多有用的基础信息。线上的一些发表刊物也可以提升用户针对某些平台对于漏洞的保护,如:[Fedora 安全指南][5],[Debian 安全手册][6]。
|
||||
|
||||
目前被广泛使用的私有云平台 OpenStack 也加强了关于基于云的智能安全需求。根据 Linux 基金会发布的 [公有云指南][7]:“据 Gartner 的调研结果,尽管公有云的服务商在安全和审查方面做的都还不错,安全问题是企业考虑向公有云转移的最重要的考量之一”
|
||||
|
||||
无论是对于组织还是个人,千里之堤毁于蚁穴,这些“蚁穴”无论是来自路由器、防火墙、VPNs或虚拟机都可能导致灾难性的后果。以下是一些免费的工具可能对于检测这些漏洞提供帮助:
|
||||
|
||||
* [Wireshark][8], 流量包分析工具
|
||||
|
||||
* [KeePass Password Safe][9], 免费开源的密码管理器
|
||||
|
||||
* [Malwarebytes][10], 免费的反病毒和勒索软件工具
|
||||
|
||||
* [NMAP][11], 安全扫描器
|
||||
|
||||
* [NIKTO][12], 开源 web 扫描器
|
||||
|
||||
* [Ansible][13], 自动化的配置运维工具,可以辅助做安全基线
|
||||
|
||||
* [Metasploit][14], 渗透测试工具,可辅助理解攻击向量
|
||||
|
||||
|
||||
|
||||
这里有一些对上面工具讲解的视频。比如[Metasploit 教学][15]、[Wireshark 教学][16]。还有一些传授安全技能的免费电子书,比如:由 Ibrahim Haddad 博士和 Linux 基金会共同出版的[并购过程中的开源审计][17],里面阐述了多条在技术平台合并过程中,因没有较好的进行开源审计,从而引发的安全问题。当然,书中也记录了如何在这一过程中进行代码合规检查、准备以及文档编写。
|
||||
|
||||
同时,我们 [之前提到的一个免费的电子书][18], 由来自[The New Stack][19] 编写的“Docker与容器中的网络、安全和存储”,里面也提到了关于加强容器网络安全的最新技术,以及Docker本身可提供的关于,提升其网络的安全与效率的最佳实践。这本电子书还记录了关于如何构建安全容器集群的最佳实践。
|
||||
|
||||
所有这些工具和资源,可以在很大的程度上预防安全问题,正如人们所说的未雨绸缪,考虑到一直存在的安全问题,现在就应该开始学习这些安全合规资料与工具。
|
||||
想要了解更多的安全、合规以及开源项目问题,点击[这里][20]
|
||||
|
||||
--------------------------------------------------------------------------------
|
||||
|
||||
via: https://www.linux.com/blog/2018/5/free-resources-securing-your-open-source-code
|
||||
|
||||
作者:[Sam Dean][a]
|
||||
选题:[lujun9972](https://github.com/lujun9972)
|
||||
译者:[译者ID](https://github.com/sd886393)
|
||||
校对:[校对者ID](https://github.com/校对者ID)
|
||||
|
||||
本文由 [LCTT](https://github.com/LCTT/TranslateProject) 原创编译,[Linux中国](https://linux.cn/) 荣誉推出
|
||||
|
||||
[a]:https://www.linux.com/users/sam-dean
|
||||
[1]:https://www.blackducksoftware.com/open-source-security-risk-analysis-2018
|
||||
[2]:https://www.prnewswire.com/news-releases/synopsys-report-finds-majority-of-software-plagued-by-known-vulnerabilities-and-license-conflicts-as-open-source-adoption-soars-300648367.html
|
||||
[3]:https://www.linux.com/blog/sysadmin-ebook/2017/8/future-proof-your-sysadmin-career-locking-down-security
|
||||
[4]:http://go.linuxfoundation.org/ebook_workstation_security
|
||||
[5]:https://docs.fedoraproject.org/en-US/Fedora/19/html/Security_Guide/index.html
|
||||
[6]:https://www.debian.org/doc/manuals/securing-debian-howto/index.en.html
|
||||
[7]:https://www.linux.com/publications/2016-guide-open-cloud
|
||||
[8]:https://www.wireshark.org/
|
||||
[9]:http://keepass.info/
|
||||
[10]:https://www.malwarebytes.com/
|
||||
[11]:http://searchsecurity.techtarget.co.uk/tip/Nmap-tutorial-Nmap-scan-examples-for-vulnerability-discovery
|
||||
[12]:https://cirt.net/Nikto2
|
||||
[13]:https://www.ansible.com/
|
||||
[14]:https://www.metasploit.com/
|
||||
[15]:http://www.computerweekly.com/tutorial/The-Metasploit-Framework-Tutorial-PDF-compendium-Your-ready-reckoner
|
||||
[16]:https://www.youtube.com/watch?v=TkCSr30UojM
|
||||
[17]:https://www.linuxfoundation.org/resources/open-source-audits-merger-acquisition-transactions/
|
||||
[18]:https://www.linux.com/news/networking-security-storage-docker-containers-free-ebook-covers-essentials
|
||||
[19]:http://thenewstack.io/ebookseries/
|
||||
[20]:https://www.linuxfoundation.org/projects/security-compliance/
|
||||
Loading…
Reference in New Issue
Block a user