This tutorial documents the process of installing OpenVAS 8.0 on Kali Linux rolling. OpenVAS is open source[vulnerability assessment][6]application that automates the process of performing network security audits and vulnerability assessments. Note, a vulnerability assessment also known as VA is not a penetration test, a penetration test goes a step further and validates the existence of a discovered vulnerability, see[what is penetration testing][7]for an overview of what pen testing consists of and the different types of security testing.
### What is Kali Linux?
Kali Linux is a Linux penetration testing distribution. It's Debian based and comes pre-installed with many commonly used penetration testing tools such as Metasploit Framework and other command line tools typically used by penetration testers during a security assessment.
For most use cases Kali runs in a VM, you can grab the latest VMWare or Vbox image of Kali from here:[https://www.offensive-security.com/kali-linux-vmware-virtualbox-image-download/][8]
Download the full version not Kali light, unless you have a specific reason for wanting a smaller virtual machine footprint. After the download finishes you will need to extract the contents and open the vbox or VMWare .vmx file, when the machine boots the default credentials are root / toor. Change the root password to a secure password.
Alternatively, you can download the ISO version and perform an installation of Kali on the bare metal.
### Updating Kali Linux
After installation, perform a full update of Kali Linux.
Updating Kali:
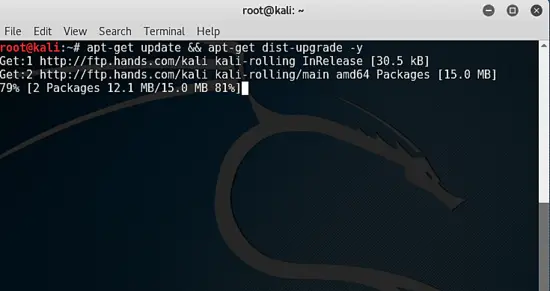
apt-get update && apt-get dist-upgrade -y
[
][9]
The update process might take some time to complete. Kali is now a rolling release meaning you can update to the current version from any version of Kali rolling. However, there are release numbers but these are point in time versions of Kali rolling for VMWare snapshots. You can update to the current stable release from any of the VMWare images.
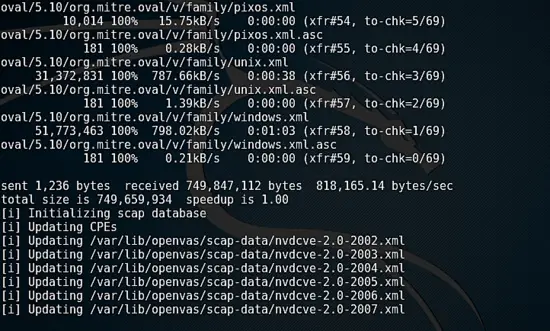
Even on a fast connection openvas-setup takes a long time to download and update all the required CVE, SCAP definitions.
[
][12]
Pay attention to the command output during openvas-setup, the password is generated during installation and printed to console near the end of the setup.
[
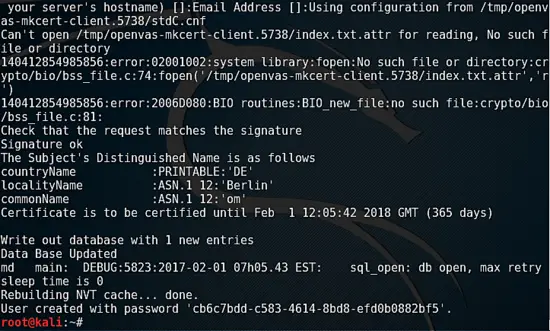
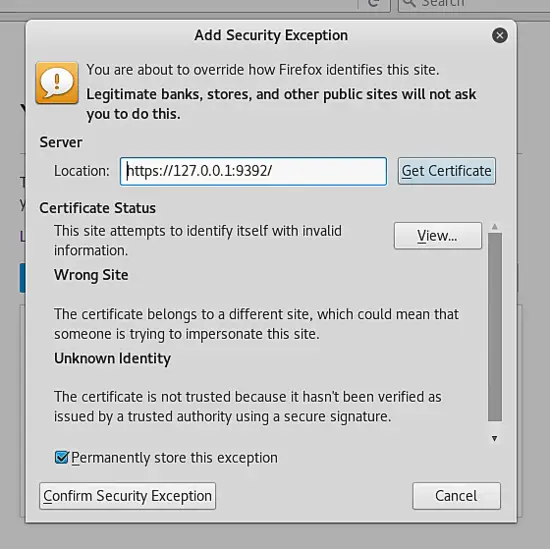
Accept the self-signed certificate and login to the application using the credentials admin and the password displayed during openvas-setup.
[
][15]
After accepting the self-signed certificate, you should be presented with the login screen:
From this point you should be able to configure your own vulnerability scans using the wizard.
It's recommended to read the documentation. Be aware of what a vulnerability assessment conductions (depending on configuration OpenVAS could attempt exploitation) and the traffic it will generate on a network as well as the DOS effect it can have on services / servers and hosts / devices on a network.