This tutorial will cover[some basic daily commands][2]you need to use in order to manageSamba4 AD Domain Controllerinfrastructure, such as adding, removing, disabling or listing users and groups.
We’ll also take a look on how to manage domain security policy and how to bind AD users to local PAM authentication in order for AD users to be able to perform local logins on Linux Domain Controller.
#### Requirements
1. [Create an AD Infrastructure with Samba4 on Ubuntu 16.04 – Part 1][1]
### Step 1: Manage Samba AD DC from Command Line
1.Samba AD DCcan be managed throughsamba-toolcommand line utility which offers a great interface for administrating your domain.
With the help of samba-tool interface you can directly manage domain users and groups, domain Group Policy, domain sites, DNS services, domain replication and other critical domain functions.
To review the entire functionality of samba-tool just type the command with root privileges without any option or parameter.
13.In order to modify samba domain password policy, such as the password complexity level, password ageing, length, how many old password to remember and other security features required for a Domain Controller use the below screenshot as a guide.
Never use the password policy rules as illustrated above on a production environment. The above settings are used just for demonstration purposes.
### Step 2: Samba Local Authentication Using Active Directory Accounts
14.By default, AD users cannot perform local logins on the Linux system outsideSamba AD DCenvironment.
In order to login on the system with anActive Directoryaccount you need to make the following changes on your Linux system environment and modify Samba4 AD DC.
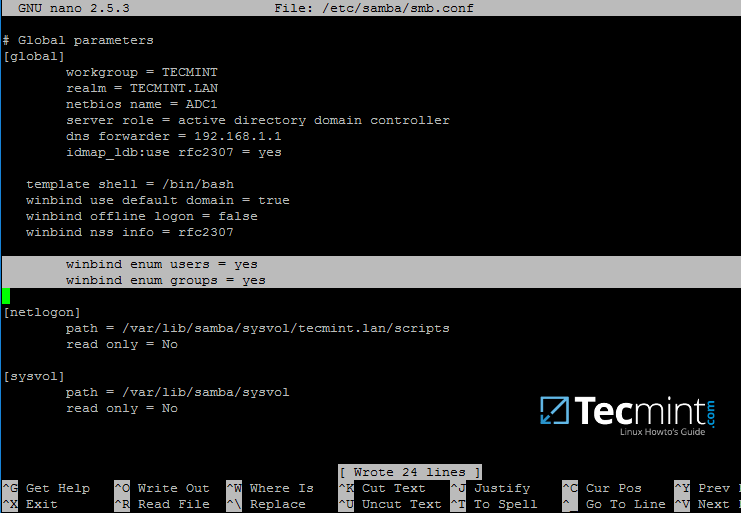
First, open samba main configuration file and add the below lines, if missing, as illustrated on the below screenshot.
```
$ sudo nano /etc/samba/smb.conf
```
Make sure the following statements appear on the configuration file:
```
winbind enum users = yes
winbind enum groups = yes
```
[
][9]
Samba Authentication Using Active Directory User Accounts
15.After you’ve made the changes, usetestparmutility to make sure no errors are found on samba configuration file and restart samba daemons by issuing the below command.
```
$ testparm
$ sudo systemctl restart samba-ad-dc.service
```
[

][10]
Check Samba Configuration for Errors
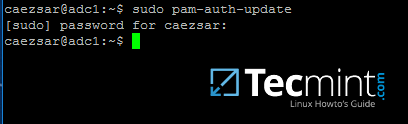
16.Next, we need to modify local PAM configuration files in order forSamba4 Active Directoryaccounts to be able to authenticate and open a session on the local system and create a home directory for users at first login.
Use thepam-auth-updatecommand to open PAM configuration prompt and make sure you enable all PAM profiles using`[space]`key as illustrated on the below screenshot.
When finished hit`[Tab]`key to move toOkand apply changes.
```
$ sudo pam-auth-update
```
[
][11]
Configure PAM for Samba4 AD
[

][12]
Enable PAM Authentication Module for Samba4 AD Users
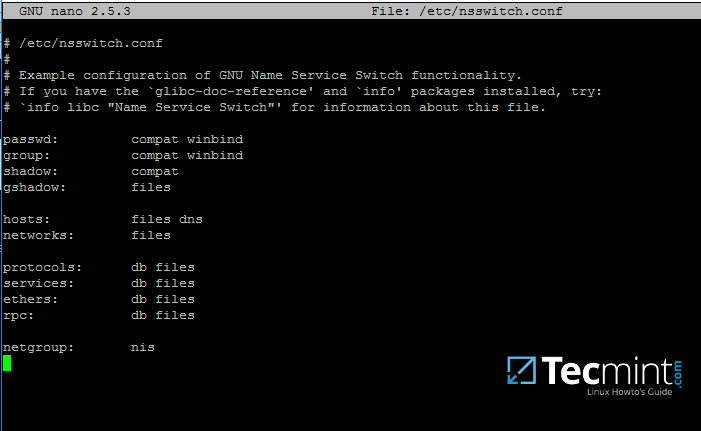
17.Now, open/etc/nsswitch.conffile with a text editor and addwinbind statementat the end of the password and group lines as illustrated on the below screenshot.
```
$ sudo vi /etc/nsswitch.conf
```
[
][13]
Add Windbind Service Switch for Samba
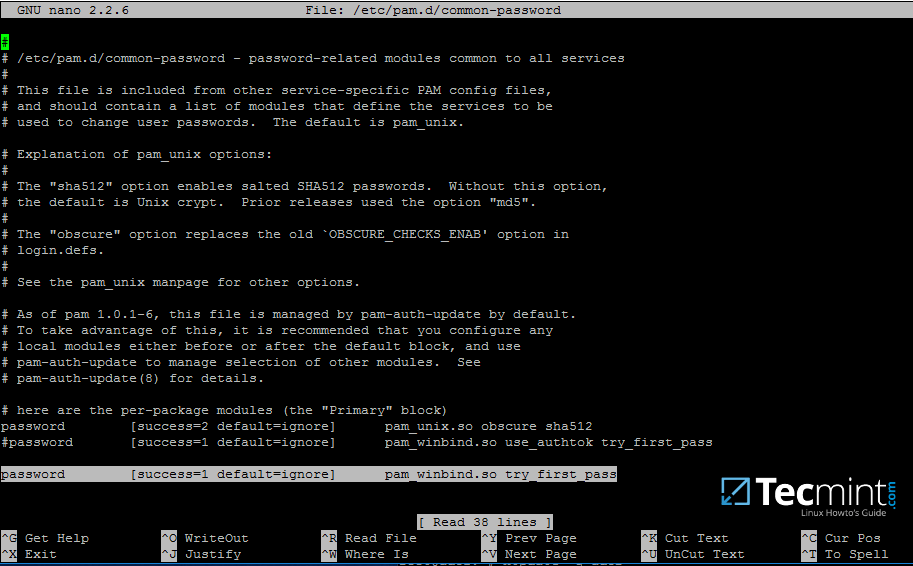
18.Finally, edit/etc/pam.d/common-passwordfile, search for the below line as illustrated on the below screenshot and remove theuse_authtokstatement.
This setting assures that Active Directory users can change their password from command line while authenticated in Linux. With this setting on, AD users authenticated locally on Linux cannot change their password from console.
][14]
Allow Samba AD Users to Change Passwords
Removeuse_authtokoption each time PAM updates are installed and applied to PAM modules or each time you executepam-auth-updatecommand.
19.Samba4 binaries comes with awinbindddaemon built-in and enabled by default.
For this reason you’re no longer required to separately enable and runwinbinddaemon provided bywinbindpackage from official Ubuntu repositories.
In case the old and deprecatedwinbindservice is started on the system make sure you disable it and stop the service by issuing the below commands:
```
$ sudo systemctl disable winbind.service
$ sudo systemctl stop winbind.service
```
Although, we no longer need to run old winbind daemon, we still need to install Winbind package from repositories in order to install and usewbinfotool.
Wbinfoutility can be used to query Active Directory users and groups fromwinbindddaemon point of view.
The following commands illustrates how to query AD users and groups usingwbinfo.
```
$ wbinfo -g
$ wbinfo -u
$ wbinfo -i your_domain_user
```
[

][15]
Check Samba4 AD Information
[
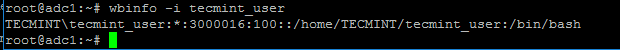
][16]
Check Samba4 AD User Info
20.Apart fromwbinfoutility you can also usegetentcommand line utility to query Active Directory database from Name Service Switch libraries which are represented in/etc/nsswitch.conffile.
Pipegetentcommand through agrepfilter in order to narrow the results regarding just your AD realm user or group database.
```
# getent passwd | grep TECMINT
# getent group | grep TECMINT
```
[

][17]
Get Samba4 AD Details
### Step 3: Login in Linux with an Active Directory User
21.In order to authenticate on the system with aSamba4 ADuser, just use theAD usernameparameter after`su -`command.
At the first login a message will be displayed on the console which notifies you that a home directory has been created on`/home/$DOMAIN/`system path with the mane of your AD username.
Useid commandto display extra information about the authenticated user.
```
# su - your_ad_user
$ id
$ exit
```
[

][18]
Check Samba4 AD User Authentication on Linux
22.To change the password for an authenticated AD user typepasswd commandin console after you have successfully logged into the system.
```
$ su - your_ad_user
$ passwd
```
[
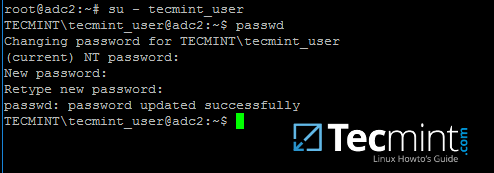
][19]
Change Samba4 AD User Password
23.By default,Active Directoryusers are not granted with root privileges in order to perform administrative tasks on Linux.
To grant root powers to an AD user you must add the username to the localsudogroup by issuing the below command.
Make sure you enclose therealm,slashandAD usernamewith singleASCIIquotes.
```
# usermod -aG sudo 'DOMAIN\your_domain_user'
```
To test if AD user has root privileges on the local system, login and run a command, such asapt-get update, with sudo permissions.
```
# su - tecmint_user
$ sudo apt-get update
```
[
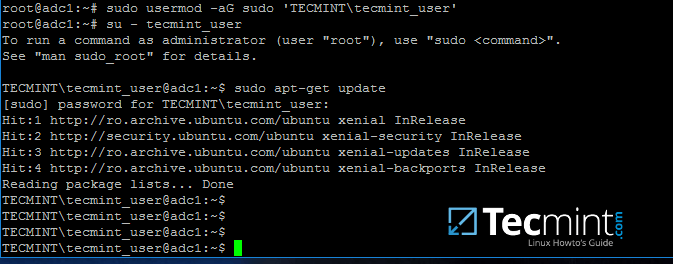
][20]
Grant sudo Permission to Samba4 AD User
24.In case you want to add root privileges for all accounts of an Active Directory group, edit/etc/sudoersfile usingvisudocommand and add the below line after root privileges line, as illustrated on the below screenshot:
```
%DOMAIN\\your_domain\ group ALL=(ALL:ALL) ALL
```
Pay attention tosudoerssyntax so you don’t break things out.
Sudoers file doesn’t handles very well the use ofASCIIquotation marks, so make sure you use`%`to denote that you’re referring to a group and use a backslash to escape the first slash after the domain name and another backslash to escape spaces if your group name contains spaces (most of AD built-in groups contain spaces by default). Also, write the realm with uppercases.
[

][21]
Give Sudo Access to All Samba4 AD Users
That’s all for now!Managing Samba4 ADinfrastructure can be also achieved with several tools from Windows environment, such asADUC,DNS Manager,GPMor other, which can be obtained by installingRSATpackage from Microsoft download page.
To administerSamba4 AD DCthroughRSATutilities, it’s absolutely necessary to join the Windows system intoSamba4 Active Directory. This will be the subject of our next tutorial, till then stay tuned toTecMint.